How to enable https on Apache CentOS
For some businesses, serving up websites via HTTPS is a must-have. Here’s how to configure secure http Apache on CentOS.We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. This may influence how and where their products appear on our site, but vendors cannot pay to influence the content of our reviews. For more info, visit our Terms of Use page.

If you are starting to migrate your web servers over to Linux (or have already done so) and are looking to serve those pages up over secure http (aka https), you’re going to need to know how to make this happen. Although https does will not guarantee security for your web server, it is a solid first step in the process. Configuring Apache for https on CentOS isn’t difficult, but there are a few steps. Let’s walk through the process, so you can start serving your pages up to your clients/customers more confidently.
This walkthrough will use CentOS 7 and work with a self-signed certificate. The self-signed option works great for personal sites or testing purposes. For your official business rollouts, you’ll want to purchase an SSL certificate from a reputable company (such as Digicert, Network Solutions, or GlobalSign). I will also assume you already have Apache running on the server.
Must-read security coverage
- Top cybersecurity threats for 2023
- Best IT asset management software of 2022
- Meet the most comprehensive portable cybersecurity device
- How to secure your email via encryption, password management and more (TechRepublic Premium)
With that said, let’s begin the process.
Installing and using OpenSSL
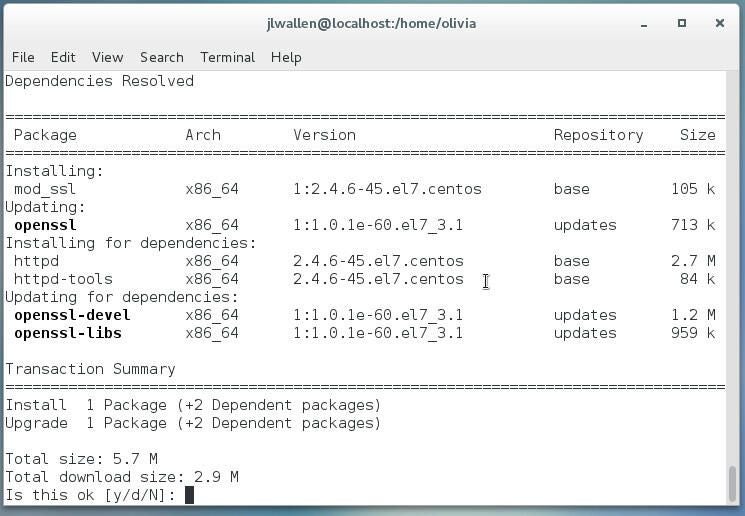
The first step in the process is the installation of OpenSSL and the generating of the certificate to be used. To install OpenSSL, open a terminal window and issue the command:
sudo yum install mod_ssl openssl
Issuing the above command will pick up all the necessary dependencies (Figure A).
Figure A
Now we generate the SSL key with the following commands:
Generate private key and CSR
openssl req -new -newkey rsa:2048 -nodes -keyout ca.key -out ca.csr
Generate Self Signed Key
openssl x509 -req -days 365 -in ca.csr -signkey ca.key -out ca.crt
Now we need to copy the newly generated files to the correct locations with the following commands:
sudo cp ca.crt /etc/pki/tls/certs
sudo cp ca.key /etc/pki/tls/private/ca.key
sudo cp ca.csr /etc/pki/tls/private/ca.csr
When you issue the command to generate the CSR, you will be asked a number of questions for the key (such as Country Name, State or Province, Locality, Organization Name, Organizational Unit, Common Name, Email Address, etc.). OpenSSL will also require you to enter a challenge password for the CSR.
The next step requires the editing of the /etc/httpd/conf.d/ssl.conf file. Open that file for editing and locate and change the following lines:
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
changes to:
SSLCertificateFile /etc/pki/tls/certs/ca.crt SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
changes to:
SSLCertificateKeyFile /etc/pki/tls/private/ca.key
Finally, restart the Apache daemon with the command:
sudo systemctl restart httpd
Create a virtual host
Let’s create a virtual host that makes use of SSL. To do this we’ll create the necessary directories with the following commands:
sudo mkdir -p /var/www/html/adorkable
âsudo mkdir -p /etc/httpd/sites-available
âsudo mkdir -p /etc/httpd/sites-enabled
I’m using “adorkable” as an example. You can use whatever name you like/need.
Next we must edit the httpd.conf file, so that it becomes aware of the sites-enabled directory. To do this, open up /etc/httpd/conf/httpd.conf and add the following line to the bottom of the file:
IncludeOptional sites-enabled/*.conf
Save and close that file.
Now we need to create our virtual host file. We’ll do this in /etc/httpd/sites-available/adorkable.conf. Again, swap “adorkable.conf” with the name of your virtual host. In that file we’ll add the following contents (customize as needed):
ServerAdmin email@address
DocumentRoot "/var/www/html/adorkable/"
ServerName AdorkableDesigns
ServerAlias adorkable
ErrorLog /var/www/html/adorkable/error.log
<directory “=”” var=”” www=”” html=”” adorkable=””>
DirectoryIndex index.html index.php
Options FollowSymLinks
AllowOverride All
Require all granted
Save and close that file.
In order for Apache to be aware of the new virtual host, we must create a symbolic link, from sites-available to sites-enabled, with the command:
sudo ln -s /etc/httpd/sites-available/adorkable.conf /etc/httpd/sites-enabled/adorkable.conf
Restart Apache with the command:
sudo systemctl restart httpd
Your virtual host should now be visible to the server. All you have to do is add content to the /var/www/html/adorkable directory and you’re good to go.
A quick test
That’s all there is to the setup of https on Apache with CentOS. You can do a quick test by pointing a browser to https://IP_OF_SERVER. You should receive a security warning (since we are using a self-signed certificate. Okay that warning and Apache will serve up your site using https. Point your browser to https://IP_OF_SERVER/adorkable to visit the newly created virtual host. Depending on what type of site you are serving up, you might have to do a bit of extra work with that particular platform.
Easy peasy https
You have officially set up your Apache server to work with https. As I mentioned earlier, if you plan on using this for public-facing, business sites, I highly recommend purchasing your SSL certificates from a reputable dealer (or using Let’s Encrypt).
Config firewall Add port 80 – 443 to firewall centos
Add port 80 to the firewall rule and reload the firewall service
firewall-cmd --zone=public --permanent --add-service=http
firewall-cmd --zone=public --add-port=80/tcp --permanent
Add port 443 to the firewall rule and reload the firewall service
firewall-cmd --zone=public --permanent --add-service=https
firewall-cmd --zone=public --add-port=443/tcp --permanent
firewall-cmd --reload
firewall-cmd --list-all
Check port open firewall centos
Check whether or not the port has been added to the iptables and check whether or not port 443 is listening
iptables-save | grep 443
netstat -plnt | grep ':443'
The only assumption in this blog is that you have a admin/root permission
That’s it for today I hope you find this blog post informative!
Nevertheless, care should be taken because the
QoE for most of the exams was very low, inconsistent, or with no proof, and there’s a lack of
knowledge in regards to the responsiveness of all higher extremity PPTs.
The features and capacities of the neuromuscular andmusculoskeletal methods play
important roles in defining the physical fitnessstatus of individuals and populations.
Evaluation of musculoskeletal health hastraditionally included assessment of muscle power, muscle endurance,flexibility, and bone health (Bouchard etal.,
2007). The normal grip pull up also engages your biceps,
brachialis (the muscle beneath the bicep), brachioradialis (a muscle of the forearm),
and the infraspinatus (one of the 4 rotator cuff muscular tissues in the shoulder).
Introducing weights on this kind can drastically improve your
upper physique energy, size, and endurance.
The back, hips and legs shall be straight head to heels and must remain so throughout the check.
Toes, forearms and fists or palms will remain in touch with the floor,
not a wall or other vertical assist floor. You solely can succeed by channeling any unfavorable suggestions
and turning it into a constructive, self-fueling energy.
You should suppose that nothing anybody will say will make you
doubt your skills. If you are capable of do the above recommended requirements, you may
be more than midway to graduating.
Limitations of the research reviewed include that research weren’t designed toanswer questions concerning
the relationship between the health tests studiedand health, that
interventions had been inadequate, or that
confounders have been notconsidered. Although effects of age, gender, body composition, maturationstatus, and ethnicity on efficiency on the assorted exams have
beensuggested in the past, this evaluation offered inadequate information for assessingthe influence of such modifiers.
In coverage academy physical health checks, all efficiency standards should
be met to pass the check; there aren’t any exceptions.
The last check, CkcUet Take A Look At, is a standardized performance check
and a straightforward methodology to measure your energy, power, endurance and stability of the upper extremities.
You use a push-up or a modified (knee touching the ground) push-up place and alternately
tapping a pre-determined distance (90cm or 3ft) lateral to the stabilizing hand as many occasions as attainable inside 15 seconds.
Discover out extra about what it takes to cross muster at the Air Force’s Basic Navy Coaching Overview web page online.
If you are presently within the decrease percentiles, i.e., below 50%,
you in all probability don’t need to follow a specialist program to improve your 1-minute push-up take a look at score.
As An Alternative, you need to simply concentrate on doing push-ups regularly and persistently,
incorporating some of the training strategies outlined above.
You don’t must go too heavy for this strategy to work—about 10% of your body
weight is sufficient. Extra weight than it will probably change your kind, making any power improvements much less transferable.
The building of the checks adopted essentially the same
pattern for both males and females on the school levels.
Countless people who worked on farms or other handbook labor jobs all through their early life have a
natural toughness… You could discover that you just cannot do as many this manner, but such a strict kind ensures
that all take a look at individuals are assessed by the same criteria.
Expect expert-backed workouts, nutrition advice, the most recent in power sports activities, and a whole lot of motivation heading your means.
Regardless Of this, push-ups are sometimes considered as a beginner train, however that’s not a perspective I share.
Pull up rings, or gymnastics rings, provide a wonderful different
to the standard pull up bar. Be certain to keep your core engaged as nicely to stabilize your body
and stop any swinging movement.
Additionally, I made changes for age as efficiency tends to say no
over time, particularly after 40. To account for this, I factored in a 5-rep discount per decade
for individuals over 40. Nevertheless, as an alternative of directly making use of these figures, I
adjusted them for the one-minute format. Military checks sometimes require sustained effort over two minutes or extra, so I recalibrated the expectations to go properly
with the higher depth of a shorter check. Strong core muscle tissue are essential for just about each movement you make, from choosing up a heavy box to swinging a baseball bat.
Plus, a strong core helps protect your backbone
and stop accidents, making it an important part of total health.
For these trying to incorporate neutral grip pull ups into their workouts, monkey bars provide an excellent
answer.
A new addition to the PFT is the change to a plank instead of sit-ups.
Not long ago, you would select which one
to carry out, however the Marines have determined that the plank is a part of
their testing metric. In order to arrange for the preliminary
Marines PFT requirements, we recommend training
and making an attempt to fulfill the next situations based mostly in your age group.
The belly crunch event is a timed event where the Marine must perform as many crunches as possible in two minutes.
Our 1 mile run check is supposed to be an evaluation of your “aerobic” capacity.
Failing this evaluation could be a sign of a major problem, such as ankle,
hip or back points. Do extra pull-us to strengthen your grip, kettlebell
swings to assist with hip and glute power and heavy high-rep squats to work in your pressure.
I will explain the totally different steps of constructing your personal workout program within the subsequent article!
The objective is to take care of a static place steroids for bodybuilding for sale 40s,
rest 20s and keep the same position once more for 40s.
We evaluate three positions, the susceptible
plank, the left and proper aspect plank, and the static sit up with straight legs.
The CDC’s systematic evaluate of the literature included musclestrength and muscle endurance, but
not muscle energy, as parts offitness as a result of
they are the dimensions of musculoskeletal fitness thathave been used most incessantly in fitness
test batteries. The musclestrength search screened 2,642 reviews, only sixty three
of which satisfied theCDC search criteria for further consideration and were abstracted.
Ofthis subset of 63 studies, 23 have been classified as experimental, 22 asexperimental with no control, 12 as quasi-experimental, and 6 aslongitudinal.
The issue of the police academy health take a look at can be important, particularly for people who usually are not adequately ready.
The check is designed to judge endurance, energy, and agility,
and recruits should meet all performance requirements to pass.
Proper preparation, including a structured coaching plan specializing in cardiovascular health and power
training, is essential for achievement, based on Police Pathfinder.
When on the lookout for a reliable supplier of anchor
pulling checks close to you then you presumably can rely on Concrete Insight,
a perfect platform to fulfill your project’s demand
with flawless techniques. Although there are many checks out there to
check athletic efficiency, these three make
up our go-to dryland efficiency checks for swimmers it doesn’t matter
what their objectives or coaching background are. Respiratory is integral to swimming in a
means that’s unique to our sport. A swimmer’s breath acts as the
muse of every motion carried out each out and in of the water.
This underrated self-test permits the athletes to demonstrate how properly they will breathe and hold tension at the identical
time.
Neben Monatsspritzen, Tabletten oder Pflastern besteht die Möglichkeit, das natürliche bioidentische
Testosteron in Form einer transdermalen Applikation mittels Gel täglich
auf die Haut aufzubringen. Hierdurch kann mit einer niedrigst möglichen Dosierung ein sehr konstanter Hormonspiegel aufgebaut werden. Hautpflaster zeigen zwar auch eine gute Wirkung, werden jedoch
kaum noch angewendet, da sie häufig zu Hautirritationen geführt haben und
»sichtbar« sind. Die Zufuhr über Tabletten ist veraltet, weil sie keiner
natürlichen Substitution, sondern vielmehr einer hoch dosierten Pharmakotherapie entspricht.
Die konventionelle Zytogenetik ist bei der Diagnosestellung empfohlen, das Material kann
jedoch eventuell für spätere Testung asserviert werden. Aufgrund des
im Allgemeinen indolenten Verlaufs der PV gehört eine
erweiterte molekulare Untersuchung derzeit nicht zur Routine einer
Abklärung. Dies ist jedoch in den Fällen mit grenzwertigem
Erscheinungsbild, bei denen die Unterscheidung
zu anderen MPN schwierig ist, oder bei denen der Verdacht auf ein Fortschreiten der Krankheit
besteht, angezeigt. Die erweiterte Charakterisierung
erfolgt mittels Next Generation Sequencing (NGS). Diese Untersuchung ist jedoch in der Regel mit höheren Kosten verbunden und bedarf einer Zustimmung der Krankenkasse mit einer Kostengutsprache.
Die Betroffenen weisen fast immer eine Mutation im Gen JAK2 auf
– dies, so sollte sich später herausstellen, warfare bei dem Affected Person nicht der Fall.
Wegen des erhöhten Thromboserisikos für die Patientin und den Fetus (erhöhte Spontanabortrate, Plazentarinfarkt/-insuffizienz)
ist aber eine intensive interdisziplinäre Betreuung erforderlich, die in intestine 50 %
zu Lebendgeburten führen kann.
Um eine im Vergleich flachere Testosteron-Wirkungskurve zu erreichen,
stellten die Baseler Internisten auf das intramuskulär zu
applizierende und länger wirksame Präparat Testosteronundecanoat um.
In Zukunft soll sich der Zeitpunkt der Testosteron-Substitution am klinischen Allgemeinzustand des Patienten sowie am peripheren Androgenspiegel orientieren. Zu beachten ist außerdem das erhöhte Prostatakarzinom-Risiko unter der Substitutionstherapie,
dem Affected Person wurde empfohlen, sich
regelmäßig klinisch und sonografisch untersuchen lassen. Inzwischen lagen die Ergebnisse der Knochenmarkspunktion vor, wonach ein normo-
bis leicht hyperzelluläres Knochenmark mit leichter Hyperplasie der Erythropoese bestand.
Es fanden sich kein morphologischer Anhalt für eine myeloproliferative Erkrankung und keine genetischen Aberrationen. “Die initial geschilderte abdominale Symptomatik interpretierten wir im Rahmen der Testosteronüberdosierung bei Regredienz im Verlauf als potenzielle Nebenwirkung”, so Kofler und Mitarbeiter.
In wissenschaftlichen Untersuchungen konnte ein Zusammenhang zwischen Testosteronmangel und psychischen Symptomen wie Schlafstörungen, Nervosität,
Ängstlichkeit und Depressionen nachgewiesen werden.
Eine interessante Publikation beschreibt, dass Männer mit einem (künstlich)
erhöhten Testosteronspiegel fairer verhandelten als Männer mit
normalem testosteron mittel kaufen (Eleanore)spiegel.
Das Klischee, dass erhöhte Testosteronspiegel zu aggressiverem Verhalten führen, hält sich hartnäckig,
konnte mittlerweile jedoch in vielen Studien widerlegt werden.
Dieses kann durch eine zytoreduktive Therapie mit Phosphor-32,
Chlorambucil, Busulphan, Hydroxyharnstoff oder mit einem Aderlass
erreicht werden. Ob bei alleiniger Hydroxyharnstoff-Therapie ebenfalls die
Leukämiewahrscheinlichkeit erhöht ist, wird derzeit diskutiert.
Androgene sind für die sexuelle Differenzierung der Geschlechtsorgane sowie die Ausbildung des
männlichen Phänotyps essenziell.
Die kongenitalen Erythrozytosen benötigen aus hämatologischer Sicht ebenfalls meistens keine spezifische Therapie und sind nicht mit erhöhtem Risiko für Thrombosen oder Transformation in eine andere Erkrankung verbunden. Die Ausnahme ist die Chuvah Erythrozytose (VHL-mutiert), da diese für eine Thrombosetendenz bekannt ist.
Mit der Zunahme der Testung für die kongenitalen Erythrozytosen sowie einer besseren Datenlage, können hoffentlich zukünftig die klaren Managementstrategien etabliert werden. Um die Mutation, welche für die kongenitale Erythrozytose verantwortlich
ist, zu untersuchen, muss eine molekulare Testung durchgeführt werden.
Diese kann vom peripherenBlut erfolgen und mit NGS durchgeführt werden.
Ob eine Substitution mit Testosteron zu einer verringerten Mortalität bei KHK-Patienten führt, muss jedoch erst noch in weiteren Studien überprüft werden.
Thrombozyten können bei PV-Patienten ebenfalls an der Entstehung von Thrombosen beteiligt sein. Nach den Ergebnissen der ECLAP-Studie (19) – einer randomisierten, placebokontrollierten Doppelblindstudie mit 518 Patienten – haben Patienten, die täglich 50 bis a hundred
mg Acetylsalicylsäure (ASS) einnehmen ein geringeres Thromboserisiko.
Kritiker der Studie wenden ein, dass einzelne Patienten dieser Studie
nur deshalb eine ASS-Therapie benötigten, weil ihr
Hämatokrit nur unzureichend abgesenkt struggle (20).
Da einzelne PV-Patienten ein erhöhtes Blutungsrisiko haben, ist beim
Einsatz von ASS auf etwaige Blutungskomplikationen zu achten.
Durch eine homozygote Mutation des VHL-Gens entsteht ein VHL-Protein mit
reduzierter Aktivität, sodass die a-Ketten auch bei Normoxämie nicht abgebaut werden. Die dadurch hervorgerufene Erhöhung der
Erythropoietin-Ausschüttung führt zu einem deutlichen Anstieg des Hämoglobinwertes.
Dies weist auf andere Ursachen, wie zum Beispiel die beobachtete vermehrte Produktion des
vaskulären endothelialen Wachstumsfaktors (VEGF), die ebenfalls durch HIF reguliert wird, hin (3).
Angeborene Erythropoietin(EPO)-Rezeptor-Mutationen führen zu einer
Verkürzung des intrazellulären Anteils des Rezeptorproteins (2).
Dadurch können unfavorable Regulatoren nicht mehr binden, sodass es zu einer konstitutiven Aktivierung des Rezeptors kommt.
Im Gegensatz zur PV haben die Betroffenen kein erhöhtes Risiko für Thrombosen und Blutungen, was dafür spricht,
dass die Erythrozytose nicht alleine dafür verantwortlich ist.
Während die Menopause mit dem Ausbleiben der Regelblutung offensichtlich wird, fehlt ein solches Kardinalereignis beim Mann.
Das mit den Erythrozyten entfernte Eisen führt zu einem sekundären Eisenmangel,
der die Erythropoese limitiert und zu Müdigkeit und Abnahme der Leistungsfähigkeit führen kann.
Zunächst im Osten Russlands und später auch in Mitteleuropa fand man eine besondere Form der erblichen Polyzythämie.
Ihr liegt eine autosomal-rezessiv vererbte Mutation im Von-Hippel-Lindau(VHL)-Gen zugrunde.
Das VHL-Protein reguliert in den peritubulären Fibroblasten der Niere den Abbau des Hypoxie-induzierbaren-Faktors (HIF1) (Grafik 2).
Dieser besteht aus 2 Untereinheiten a und b und vermittelt die Sauerstoffmessung in den Nieren. In Gegenwart von Sauerstoff werden die a-Ketten unter Beteiligung des VHL-Genproduktes
abgebaut (3).
Aus dieser Beobachtung heraus resultierte die Angst, dass die Substitution mit Testosteron das Wachstum einer bisher nicht erkannten Prostatakrebserkrankung beschleunigen könne.
Weder wurde vermehrt Prostatakrebs unter einer
Testosteronsubstitutionstherapie diagnostiziert, noch besteht bei Männern mit hohen Testosteronspiegeln eine erhöhte Tumorinzidenz.
Hohes Testosteron wird häufig mit vermehrtem Haarausfall in Verbindung
gebracht. Ein Zusammenhang, der in dieser monokausalen Kind nicht besteht.Eine hormonelle
Ursache für verstärkten Haarausfall kann allerdings eine Erhöhung
des Hormons Dihydrotestosteron (DHT) sein.
Suite à des attaques de la half de la combattante hongroise Luca Anna Hamori, le Comité Olympique Algérien a porté plainte pour violation de l’éthique sportive.
Mais nous faisons la promotion de nos contenus et services sur d’autres websites et
réseaux sociaux. Pour cela, nous utilisons les technologies
mises à disposition par certains acteurs publicitaires.
Cette catégorie de poids n’est pas officiellement reconnue par les « règles unifiées des MMA »[3].
Les stéroïdes ne font que vous transformer en une grosse brute
puante ». Il est allé au tribunal trt et perte De poids a
témoigné pendant le procès qu’il avait une ordonnance pour le Jintropin, cependant le médicament n’est pas légalement disponible sur ordonnance
aux États-Unis et il a été déclaré coupable. Dans de nombreux cas,
ils sont cependant supervisés par des médecins, mais les médicaments qu’ils prennent
sont totalement illégaux.
La catégorie des poids mi-moyens (ou poids welters) regroupe
les combattants de 156 lb (70 kg) à a hundred and seventy lb (77 kg).
La catégorie des poids légers regroupe les combattants de 146 lb (66 kg) à 155 lb (70 kg).
Avec cette victoire impressionnante, Shi Ming (17-5) prolonge sa série de victoires à cinq combats consécutifs.
Un combat face à Alain Ngalani est prévu mais plusieurs fois repoussé avant d’être simplement annulé[36].
Belfort remporte le combat à la décision, ce qui constitue son premier fight allant à son terme depuis près d’une décennie[34].
En novembre 2023, après une attaque au couteau ayant fait plusieurs blessés, il multiplie les tweets violents contre le
« gauchisme » et les autorités irlandaises trop « laxistes » , en particulier sur l’immigration selon lui.
Michael donne la priorité à un sommeil de qualité suffisante chaque nuit pour faciliter son entraînement et sa récupération.
Le manque de sommeil a été lié à une baisse des niveaux de testostérone chez les hommes, donc l’accent
mis par Michael sur le repos aide à maintenir sa santé hormonale.
Le cutting peut entraîner une déshydratation sévère, avec des conséquences graves sur la santé.
Cette déshydratation diminue le volume sanguin, augmente
la pression artérielle et le rythme cardiaque, et
réduit l’oxygénation des organes. Le cerveau, composé à
75% d’eau, voit son fonctionnement altéré, pouvant mener
à des maux de tête, vertiges, nausées, crampes,
convulsions, voire un coma ou un arrêt cardiaque.
La déshydratation peut aussi provoquer une hyperthermie, engendrant des dommages irréversibles aux cellules, et représente un risque majeur pour la vie des
combattants.
Lesstéroïdes ont peu à peu gagné du terrain et leur usage était
très répandu dansles années 70-80. Son succès pourrait également avoir des implications plus larges pour
l’UFC. Le PDG Dana White a récemment évoqué la possibilité d’ouvrir une division des poids atomiques, ce qui pourrait offrir de nouvelles opportunités à des combattantes
de plus petit gabarit comme Ming. Son fashion de vie en tant qu’athlète d’élite correspond bien aux facteurs qui, selon les recherches, peuvent stimuler la
production de testostérone à mesure que les hommes vieillissent.
En mars 2025, il annonce son intention de se présenter
en tant que candidat indépendant à l’élection présidentielle irlandaise de 2025 et exprime des opinions qualifiées d’anti-immigration, d’extrême droite et
de national populiste[5],[6],[7]. N’hésite
pas à ajuster les exercices et les charges selon ton niveau et tes objectifs.
Adopter la routine de musculation de Chris Evans peut sembler intimidant, mais quelques conseils peuvent te faciliter la
tâche. Voici comment tu peux adapter et intégrer ces méthodes
dans ta propre routine health. En s’assurant que son alimentation était bien équilibrée, Evans pouvait non seulement
développer sa musculature, mais aussi maintenir une énergie constante et une bonne récupération entre les séances
d’entraînement. En plus de ces sources de protéines, Chris Evans
s’assurait de manger régulièrement, en répartissant ses repas tout au long de la journée pour maintenir un apport constant en nutriments.
“Je ne suis personne pour juger ou prendre une décision, si cette femme est ici, il y a une raison”, a-t-elle ajouté.
Le fight de boxe a duré moins de 50 secondes automobile l’adversaire d’Imane Khelif, l’italienne Angela Carini, abandonne sur un direct
qui lui “fait trop mal”. Ce fight éclair déclenche une controverse sur le
genre de la boxeuse victorieuse.
Au vu de leur dangerosité, il est nécessaire de disposer d’une licence de tir ou d’un permis de chasse valide de l’année en cours afin de pouvoir s’en procurer une.
Le crossfit mix exercices d’haltérophilie, thérapie de remplacement de la testostérone à Austin, Tressa, gymnastique et d’endurance.
En découlent de nombreuses possibilités d’associations rendant chaque entraînement de crossfit distinctive.
L’amélioration de l’état psychologique ne semble pas
être uniquement l’indicateur le plus représentatif
de cette modalité d’entraînement. Les notions de dépassement de soi, de motivation sont tout de même recherchées
lors du CrossFit. Dans certains cas, les traces d’éjecteurs ne s’observent seulement si la cartouche a été tirée (nécessité d’une
pression conséquente pour laisser ce style de hint sur le culot d’une douille).
Certaines armes peuvent posséder deux éjecteurs, laissant ainsi les
traces de deux éjecteurs sur le culot des douilles.
Bien entendu, Reebok garde son fameux flexweave sur le dessus de la chaussure, mais l’a
encore amélioré (plus de souplesse et d’élasticité), ce
qui permet un grand nombre d’actions différentes de la half
de la chaussure. Et ça, c’est très essential vu la
quantité de mouvements différents que l’on peut avoir dans nos séances.
Le chaussant est giant, attention, pour les pieds « fins » cela peut faire bizarre
au début, vous pouvez peut-être même prendre une demi-pointure en moins si vous le
souhaitez.
En 2010, pour appliquer la norme européenne et respecter les accords de Schengen,
il est décidé que la législation soit profondément modifiée.
Une proposition de loi, la 2773[40], présentée par Claude Bodin, Bruno Le
Roux et Jean-Luc Warsmann est enregistrée à la présidence de l’Assemblée nationale le 30 juillet 2010.
Ce projet abandonne la complexe catégorisation d’alors pour une plus
cohérente et simplifiée, commune à l’ensemble des pays membre de l’espace Schengen[41].
Dès l’entrée des troupes allemandes sur le territoire national français, une ordonnance
du 10 mai 1940 interdit la détention des armes[31].
Les mouvements de base du CrossFit comprennent des exercices
tels que les squats, les fentes, les burpees, les pompes
ou push-ups et les tractions ou pull-ups. Ces mouvements fonctionnels sollicitent plusieurs groupes musculaires et améliorent la pressure globale du corps.
Pour pratiquer le CrossFit, il est necessary de disposer de certains équipements de base.
« Les présidents de club de tir sont très vigilants, ils ne veulent pas de
cow-boys ou de Rambo. Au moindre doute sur le profil, on signale à la préfecture », explique Yves
Gollety. Pour Patrice Bouveret, directeur de l’Observatoire
des armements, ce sentiment d’insécurité s’est développé après les attentats de 2015, mais aussi avec la baisse de la confiance
dans les forces de l’ordre.
Il s’agit d’une approche pluridisciplinaire de la pratique sportive, avec des entraînements croisés mêlant des pratiques sportives d’endurance,
de la gymnastique, de la musculation, de l’haltérophilie et
des sports développant la force pure. Avec de la persévérance et une approche progressive,
vous êtes en mesure de transformer votre condition physique
et d’améliorer significativement votre qualité de vie.
En conclusion, le CrossFit à domicile, même sans équipement, se
révèle être une méthode accessible et efficace pour booster votre forme physique.
Il est primordial de démarrer avec les fondamentaux, à savoir les
squats, push-ups, sit-ups, et burpees. Avant de
vous lancer dans un entraînement de CrossFit à domicile, adopter certaines
précautions est essentiel pour garantir votre sécurité et celle de votre
environnement.
On laisse de côté les mouvements olympiques un prompt si vous le voulez bien pour ce focaliser sur ce qui vous attend
niveau cardio. Je vous conseille de faire copain-copain avec les thrusters
avec des haltères pour commencer, sur des séries de 8 à
12 répétitions max durant vos legs days, par exemple.
La sangle abdominale ne sera pas laissée pour compte, au contraire, ce qui est
une bonne nouvelle pour votre 6-pack. Le travail se fait essentiellement
au niveau des hanches, avec ce mouvement de qui fait que
vous poussez vos fessiers vers l’arrière.
Barre au sol, avec la prise de votre choix (pronation ou alternée) vous
venez tirer la barre en la maintenant le plus proche attainable de votre corps et en décrivant une trajectoire verticale de la cost.
Découvrez ci-dessous les 15 exercices phares réalisés lors d’un WOD de CrossFit.
Les armes factices, d’alarme et les armes gentle air qui peuvent être confondues avec de véritables
armes du fait de leur apparence, ainsi que les lanceurs paint-ball.
Des informations complémentaires sont disponibles sur le
website de la confédération. Par définition l’évaluation réelle de ces phénomènes reste hasardeuse et si les faits divers impliquant des fusils d’assaut sont très marquants, les autorités semblent nier la présence d’un trafic structuré massif d’armes de guerre[21].
Restez hydraté en buvant de l’eau tout au lengthy de la
journée, automobile la déshydratation peut affecter
les performances et la récupération.
Quand il a commencé à gagner du terrain, ils ont introduit un qualificatif et ont
déplacé le Home Depot Middle (plus tard appelé le StubHub Center) à Carson, en Californie.
Après sept ans en Californie, les jeux CrossFit ont déménagé au Alliant
Vitality Middle à Madison, Wisconsin. Il s’agit d’une field dédiée et affiliée qui
dispose de tout le matériel nécessaire à la réalisation des WOD.
One of the primary methods for diagnosing high testosterone is thru a blood
test. This test measures the levels of testosterone within the blood and can help determine
if they are elevated. In Accordance to the Nationwide Institute
of Well Being, the conventional range for testosterone levels in men is between 300 and
1,000 nanograms per deciliter (ng/dL) and between 15 and
70 ng/dL in girls. If the take a look at results present ranges above these ranges, it
might point out high testosterone. Diagnosing high testosterone levels
entails a combination of physical examination, blood tests, and symptom assessment.
If you suspect you may have high testosterone, it’s important to consult a healthcare skilled for
an accurate analysis. There are also sure dietary dietary supplements and
natural remedies that claim to increase testosterone ranges.
The opposed effects are generally misunderstood
as signs of high testosterone, like rage, aggressive behavior, irritability and poor mental
judgment. Overuse of those anabolic steroids can decrease the production of natural testosterone in the physique causing reduction within the testicular dimension. To higher
understand the connection between aging and testosterone levels,
longitudinal research that comply with individuals over an extended period
of time are wanted. Excessive testosterone could result in temper
disturbances similar to irritability, aggression, and hassle
sleeping. Abnormally high testosterone ranges might generally worsen psychological well being problems
like despair and may contribute to a sense of restlessness.
Research has proven that elevated testosterone ranges might contribute to
the event and progression of prostate most cancers. A study
printed within the Nationwide Institutes of Well Being
found that males with larger testosterone ranges had an elevated danger of creating aggressive prostate cancer.
Testosterone, the first male intercourse hormone, plays a crucial
position in the growth and maintenance of male characteristics.
However, having high levels of testosterone in the body
can have numerous effects and signs that warrant attention. For example, anabolic
steroids, often used illegally for performance enhancement, can dramatically
improve testosterone levels. Other medications, such as
some antidepressants and opioids, can also affect hormone levels and probably lead
to high testosterone ranges. One example of a medication that may lead to increased testosterone ranges is
testosterone alternative remedy (TRT).
Maintaining a balanced life-style, together with stress administration, enough sleep, a nutritious diet, and
common exercise, may help optimize hormone levels and promote
overall well being. If involved about excessive testosterone ranges, it is essential to seek the assistance
of with a healthcare professional to determine
the trigger and appropriate plan of action. In addition to
medical conditions and drugs, life-style components can even contribute to elevated testosterone ranges.
If a blood check is conducted within the morning, when testosterone levels are
naturally higher, it may lead to higher-than-normal readings.
It is necessary to assume about the timing of the blood test when interpreting testosterone
levels. A physician or healthcare supplier will typically order a blood
test to measure the amount definition of anabolic steroid
testosterone in the blood. Testosterone ranges can change
all through the day, so blood checks are often scheduled for
the morning when testosterone levels tend to be the highest.
HIIT involves quick bursts of intense train adopted by periods of
relaxation or low-intensity exercise. This kind of training has been found
to be notably efficient in boosting testosterone
levels and bettering total fitness. If you’re contemplating TRT
(testosterone alternative therapy), carefully weigh the potential dangers and benefits together with your physician before beginning
treatment.
One of the first causes of excessive testosterone
is polycystic ovary syndrome (PCOS), a hormonal disorder that affects girls of reproductive age.
Research has proven that as much as 70% of ladies with PCOS have high testosterone ranges, highlighting the numerous influence of this situation on hormonal stability.
Testosterone is a crucial hormone primarily liable for the development and upkeep of male secondary sexual traits.
It performs an important position in muscle growth, bone density, libido,
and overall well-being. In some circumstances, sure drugs or hormone therapies can enhance testosterone levels in individuals.
One medical condition that can trigger elevated testosterone levels is
polycystic ovary syndrome (PCOS).
When you’re wired, your physique produces more cortisol—a stress hormone—which can inhibit the manufacturing of different hormones
like testosterone. This can result in a situation generally recognized as “cortisol dominance,” which can trigger signs
like weight achieve, fatigue, anxiousness, and despair.
If you’re feeling stressed, remember to take some time for your
self to relax and de-stress. Widespread signs of excessive
testosterone in each women and men might include elevated physique hair, pimples, and irregular menstrual
cycles in ladies. In men, high testosterone ranges can result in infertility, erectile dysfunction, and
temper disturbances. High testosterone ranges, also identified as hyperandrogenism, can result in a wide range of signs and health dangers.
It is essential to understand the causes, symptoms, and therapy choices for prime testosterone so as to effectively manage this situation.
Testosterone is a hormone that performs an important role in the development and maintenance of male traits.
It is primarily produced in the testicles and is liable for varied features similar to
muscle mass growth, bone density regulation, and
sperm manufacturing. Whereas testosterone levels naturally decline with age, certain medical situations and diseases could cause a
rise in testosterone ranges in males. High testosterone
ranges in men and women can lead to a selection of well being dangers.
Nonetheless, when testosterone levels are too high, it may possibly lead to a range of well being issues.
In conclusion, high testosterone ranges can stem from a variety of causes, together with medical conditions, way of life elements,
and genetic predisposition. Understanding the underlying elements contributing
to elevated testosterone is essential for efficient management and remedy.
There are a number of medications and supplements which have been reported to trigger excessive testosterone levels in males.
Testosterone is a hormone that is naturally produced by the physique and is
answerable for male sexual traits and reproductive perform.
Whereas excessive ranges of testosterone can have advantages, such
as increased muscle mass and power, it might possibly also have negative effects if it exceeds a certain threshold.
In conclusion, certain medical conditions or diseases can contribute to high testosterone
ranges in men.
The maximum dosage that could be safely consumed is 100mg everyday,
but that’s just for advance customers who are used to taking the
drug and have built up their tolerance. The identical may be said for
coming off Anavar where can i buy steroids online;
jinrihuodong.com, you slowly lower the dose quite
than simply abruptly stopping and surprising your body.
Though it’s straightforward for the common health club
rat to purchase anavar now, it hasn’t at all times been this way.
For example in earlier years anavar was hard to get maintain off, especially
during 1989 to 1994. This was as a end result of the
FDA (Food and Drug Administration) was underneath strain to
tighten its grip on the anabolic steroid market.
Consequently anavar grew to become very difficult to pay cash for during and as with all scarce merchandise it
pushed the value up excessive (resulting in much less people consuming the drug).
Anadrol can be utilized by itself, however many will use it with a testosterone base.
When this quantity of weight acquire is lean and dry
(not including any water retention), it could make a noticeable impression visually on someone’s muscularity.
After completing a cycle of testosterone, it usually takes around 4 to six weeks
for testosterone ranges to return to normal.
This timeframe can range relying on various components, together with the size and intensity
of the cycle, as nicely as individual components corresponding to metabolism and
genetics. It can be value noting that people who’ve been using exogenous testosterone
for an prolonged interval might experience a more extended recovery
process. Long-term testosterone use can have a more important influence
on pure testosterone manufacturing, potentially
requiring an prolonged restoration period. Transferring on to the
usage, beginners often begin with the oral form, given its ease of administration in comparison with injections.
In our expertise, profitable Anavar dosages for girls range from 5 to 10 mg/day.
Anavar suppresses endogenous testosterone, which isn’t
just problematic for men; testosterone stays an important hormone for girls as properly.
Furthermore, Anavar is an oral steroid, which is
preferable to injectable steroids (for many women).
Girls normally start to see noticeable changes within the first couple of weeks, with optimum outcomes appearing around the 4-6 week mark.
Nonetheless, such women are aware of the risks and joyful to seem like a person in order to win. Research have proven that 200ml of grapefruit
juice increases the absorption of drugs dramatically, with some research showing it to extend potency by as a lot as 5x
(9). Thus, when you take any medicine (or steroid), the true dose is greatly decreased because
of CYP3A4.
Nevertheless, this is solely a common rule that
applies to those that do not abuse steroids. We find that
prime estrogen increases your sensitivity to sodium; thus,
if a person’s sodium consumption is moderate and they take Anadrol, they may retain extra water.
Nonetheless, one of the downsides to utilizing Equipoise for chopping is the way it can enhance your appetite,
however this only happens in some individuals.
So, a first-time user of EQ would need to judge its impression on appetite.
Clearly, throughout a slicing cycle, you don’t want a huge enhance in urge for food, and if so,
you have to weigh up the professionals and cons of using this explicit steroid throughout chopping cycles.
It is often used solely firstly of a cutting cycle, so the appetite improve may not negatively influence your ultimate outcomes.
You would possibly select to both take your entire dosage as soon as day by day or break up it in two each day.
This is just due to the close to certainty that exceeding the recommended dose will rapidly bring indicators
of virilization. Ladies who use Winstrol ought to stick with 5mg/day and punctiliously
monitor unwanted effects. Though most anabolic steroid customers choose to take Winstrol in pill form, there
are some advantages to the injection. Winstrol is the most popular and well-known brand name for
the androgen and anabolic steroid Stanozolol. It is a derivative of dihydrotestosterone (DHT), which makes Winstrol much like testosterone.
Importantly, Winstrol is taken into account to have a more powerful
anabolic to androgenic impact in contrast with testosterone.
With Out the assist of any performance-enhancing
substances like Anavar, they could additionally discover it difficult to push their power to new
heights as they progressively reach their personal plateaus.
The image of a bodybuilder earlier than utilizing
Oxandrolone is one marked predominantly by natural physique progress.
This individual has developed his or her muscle mass and power by way of
regular exercises and strategic vitamin. You typically discover muscular tissues in various phases of
improvement, dictated by personal routines and the natural propensities of different muscle teams.
Post-cycle remedy, or PCT, is recommended after using Anadrol to assist restore pure hormone production and reduce the chance of
unwanted effects. It Is necessary to make use of Anadrol
with warning and under the supervision of a
healthcare professional. Anadrole is right here to provide you with the legal, natural and safe different for building muscle mass.
This underlines the necessity for a balanced approach and understanding that while Anavar can help bodybuilding goals, ultimate success lies in commitment,
good diet, and consistent coaching. Most bodybuilders earlier than utilizing Anavar have already
spent quite a bit of time within the fitness center. They have a good muscle basis and will already current an impressive determine,
but they might be struggling with effectively slicing fats or attaining
a more refined muscular definition. Their progress is steady, however often slower than desired
due to the natural limits of the human body. Understanding the advantages and potential drawbacks of incorporating
Anavar into a bodybuilding cycle is essential for
individuals who want to optimize their performance and
obtain their physique goals.
This user’s results, by method of muscle hypertrophy, could be
thought-about moderate—yet lower than a typical first steroid cycle.
RAD a hundred and forty, or testolone, is a non-steroidal
SARM (selective androgen receptor modulator) that replicates
the anabolic results of steroids by binding to the androgen receptor [1].
It can final anyplace from a couple of weeks to a quantity of months, relying on how your physique responds and recovers after the cycle.
The greatest steroid for sexual operate is probably Anavar or Primobolan, as these two steroids
will not completely shut down pure check levels. Instead, they may just trigger a modest decline,
thus sexual efficiency isn’t tremendously impacted.
Testosterone, a naturally occurring hormone in the physique,
can be regulated as a managed substance in Costa Rica.
It is against the law to own, sell, or use testosterone
with no legitimate prescription from a licensed medical practitioner.
Testosterone is often used as a performance-enhancing drug to extend muscle mass,
power, and endurance. As with other managed
substances, it’s relatively straightforward to obtain testosterone via the black market or on-line pharmacies in Costa Rica.
Their popularity owes to their efficacy in muscle mass and
energy enhancement. However, their potential side
effects deserve crucial consideration. These
problems embrace liver and coronary heart harm, as nicely as infertility.
That’s why you should solely use steroids if a health care provider says it’s okay and only
for well being causes. In Dubai, there’s been fear
about athletes utilizing medication like steroids to get higher at sports activities.
Turkesterone is an ecdysteroid, a natural steroid hormone in crops and
bugs. The present local weather in the mainstream and politics is that steroids are harmful when used recreationally.
It would possibly make more of a push and pull between state and federal divisions should steroids ever by legalized on a state stage.
Whereas Rick Collins is an expert on Usa legislation, he doesn’t have as detailed
of an account to what’s legal on paper in Mexico.
What he does know is that the letter of the law is in all probability going very totally
different to what’s happening on the ground in the nation. Steroid use results in aggression and depression, generally
recognized as “roid rage”. Research exhibits it additionally connects to
harmful actions, like drunk driving and dangerous sexual exercise.
Nonetheless, where the amount is 50 grams or over,
however beneath 5kg and the Court Docket is happy that the defendant was a drug dependent person, a most penalty of 20 years imprisonment is applicable.
This signifies that such issues will regularly be handled within the Local Court Docket, which
is limited to imposing a maximum penalty of two years imprisonment and/or a $11,000 nice for a single offence.
Moreover, supplying anabolic and androgenic steroidal agents is a legal offence, with most penalties dependant on the classification of the quantity concerned.
In New South Wales, ‘anabolic and androgenic steroidal agents’ are considered a prohibited drug.
This hormone could be prescribed for medical causes, such as testosterone deficiency or other associated well being issues.
Nevertheless, additionally it is known for its potential to improve athletic
performance and is thus classified as a performance-enhancing
drug. Using testosterone and not utilizing a medical prescription can result in authorized penalties
in France. This implies that the possession, sale, and use of steroids are illegal without a legitimate prescription from a licensed medical practitioner.
Selective Androgen Receptor Modulators, or SARMS, are a class of medicine which
are designed to have the identical effects as anabolic steroids, but with fewer side
effects. They are commonly used by athletes and bodybuilders to realize
muscle mass and enhance performance.
Nevertheless, with the supplements, I had sustained power that helped me power via even the toughest workouts.
Scientific Review BoardAll Healthwise training is reviewed
by a staff that includes physicians, nurses, superior practitioners, registered dieticians,
and other healthcare professionals. Copyright ©2025
MH Sub I, LLC dba Nolo ® Self-help services is most likely not
permitted in all states.
Creams and gels which may be absorbed by way of the skin are
also in style. In Thailand, being caught with steroids with no prescription can lead to stringent penalties.
For first-time offenders, punishment might embrace up to
one 12 months in prison and fines that can attain $1,000 USD.
Authorized penalties emphasize the significance
of following Thai laws concerning steroid use. Understanding the specifics of Thailand’s rules
is important for anybody considering the purchase
of steroids inside its borders. Whereas some substances like AOD9604 and Ligandrol can be found over
the counter, the general authorized status of anabolic steroids
stays a topic of debate.
Anabolic steroids are additionally banned by most skilled sports leagues.
Most governments regulate anabolic steroids underneath well being, pharmaceutical grade steroids for sale [Evelyn], or managed substances
laws to mitigate their abuse in sports and unregulated distribution. The
consequences for unauthorized possession or sale vary from fines to imprisonment.
In Poland, peptide hormones are thought-about prescribed drugs, which means they’ll solely be legally obtained with a doctor’s prescription. Using, possessing, or distributing these substances with no legitimate prescription is taken into account illegal.
This is partly due to the straightforward availability of these substances by way
of the black market and on-line sources, as well as the
dearth of stringent enforcement of anti-doping legal guidelines within the nation.
Human development hormone (HGH) is also a controlled substance in Japan, and it’s illegal
to own, sell, or distribute it with no valid prescription. Japanese authorities are identified to enforce these legal guidelines strictly, with a focus on cracking down on the illegal importation and sale of HGH and other
performance-enhancing medicine. Understanding the authorized standing of steroids in bodybuilding is crucial.
Consult with medical professionals before contemplating any substances.
Stay informed and make protected, legal choices on your bodybuilding journey.
Performance-enhancing medication, together with steroids and HGH, are
unlawful in Greece without a prescription. These steroids are often utilized by athletes
and bodybuilders seeking to extend muscle mass, power, and endurance, as properly
as speed up recovery occasions between workouts.
Like steroids, Human Progress Hormone (HGH) can also be unlawful in Greece with no prescription.
If an individual is thinking about taking supplements to help their workouts, they need to first speak with a doctor
to examine the product is secure for them.
It is protected for most people to eat up to 2 grams
(g) per kilogram of physique weight per day.
Caffeine is a stimulant that will enhance exercise performance, particularly for actions that contain endurance, such as operating.
Nevertheless, a 2021 review notes there’s a lack of evidence supporting some of these claims and that some
animal research have proven that androstenedione supplementation causes cancer.
Trenorol goals to expedite this restoration course of by promoting improved blood circulation and decreasing muscle irritation. This complement additionally goals
to boost your energy ranges, allowing you to work out
more effectively and potentially carry heavier weights.
A prostacyclin analogue, treprostinil, is
often used for the remedy of PAH to improve hemodynamic operate.
Treprostinil may be administered by way of
intravenous (IV), subcutaneous (SQ), inhalation and
oral routes. Oral treprostinil (Orenitram®) was launched in 2013 to be used for treatment of PAH.
A cohort analysis was performed for 16 all sufferers that have been hospitalized with PAH and receiving
oral treprostinil. Oral treprostinil was administered at 2 mg/day and was in contrast in opposition to IV epoprostenol and IV and
SQ treprostinil.
Some individuals select to include them into their
way of life by way of topical purposes, similar to creams or lotions.
These products are formulated to ship the helpful compounds directly to the skin, providing potential advantages for skin well being.
Whereas they could provide a better concentration of phytosterols, they need to not
exchange a balanced food regimen. It is at all times really helpful to consult with a healthcare professional earlier than beginning any new complement
to make sure it aligns together with your individual health wants.
Furthermore, relying solely on plant-based steroids with out addressing
different elements of health and health can result in disappointment and
frustration. It is essential to method their use with sensible expectations and a comprehensive approach to overall well-being.
With that out of the way, Steve Reeves and Ron Williams are my picks for
the most effective pure bodybuilders. While Reeves
pioneered the golden aesthetics era, Williams is the winningest pure bodybuilder ever.
Gynecomastia, or gyno, is among the most dreaded unwanted
aspect effects of steroids in males. Most folks begin lifting weights to enhance their general well being and
well-being.
This chapter discusses theprevalence of assorted naturally out there steroids in several entities and their suitableapplications
in various fields. Natural steroids are compounds which might
be produced within the physique or derived from certain foods and
plants that mimic the results of artificial anabolic steroids.
They promote muscle development, enhance recovery, and might improve overall athletic
efficiency by naturally rising hormone levels, such as testosterone and cortisol.
These meals stimulate the body’s production of hormones that facilitate
muscle repair and progress, serving to individuals
to achieve better results from their workouts. Earlier Than diving into specific meals, let’s make
clear what we imply by “natural steroids.” Steroids, within the organic sense, are organic compounds that include hormones like
testosterone, estrogen, and cortisol. These hormones play essential roles in our
physique, influencing metabolism, inflammation, and muscle growth.
Fortunately, certain meals can promote the manufacturing of those hormones naturally or mimic their effects, offering
a safer and legal various to artificial steroids.
HGH-X2, by Loopy Bulk, stands out because the top choice for
increasing pure HGH levels. This hormone is important for
muscle progress, metabolism, and general development. HGH-X2’s formula stimulates
the body’s own HGH launch, probably resulting in improved muscle development, faster restoration, and fat loss.
These beans naturally elevate the body’s ranges of
human progress hormones and dopamine; and in flip, these
spike your testosterone ranges.
Fortuitously, there are plenty of legal alternatives to steroids that bodybuilders and athletes can take benefit of if they want to improve their
muscle mass or body fat. Some of these alternate options encompass natural
dietary supplements that have been recognized to be effective for producing related effects to steroids with
much less opposed side-effects. Additionally, common train combined with a balanced food plan and correct relaxation can nonetheless help bodybuilders reach their desired body weight and size naturally.
Today there’s a big shift to using natural steroids versus artificial steroids.
There is such a unfavorable connotation connected to
steroids, and sports careers may end if an athlete is caught utilizing them illegally.
Long-term use may weaken the immune system, heighten diabetes danger, or
even result in adrenal gland issues. These downsides make assessing the advantages in opposition to
potential hurt crucial for anyone considering this treatment.
Natural steroids differ from synthetic steroids of their methods of
production and security of use. This hormone, also obtainable as a complement, is being explored test steroid for sale its potential in enhancing athletic efficiency, constructing muscle, and rising energy.
70918248
References:
where to buy illegal steroids (http://e-hp.info/mitsuike/4-bbs/bbs/m-123y.cgi/dfwfranchises.com/independentsage.org/BvYhYHAFaG)
70918248
References:
steroid supplement (https://philsocial.io/2025/01/25/welcome-to-philsocial/)
70918248
References:
newest steroid (https://kolegium-urologi.id/blog/penutupan-sementara-registrasi-online)
70918248
References:
prolonged steroid Use (https://fromsialkot.com/question/greatest-pakistani-hockey-players-1975-1980-poll-mockup-2/)
70918248
References:
definition of steroids (https://talesofafrica.org/the-growth-of-fintech-companies-in-nigeria/)
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Выяснить больше – https://vyvod-iz-zapoya-1.ru/
hollywood casino tunica
References:
http://guardian.ge/70154-g7-to-announce-long-term-ukraine-security-package-at-nato-summit.html
seminole casino florida
References:
https://old.newcroplive.com/video/planet-startups-oct-3-2020/
steroids names
References:
https://tourslibya.com/destination/the-big-hole-of-cyrene/
female steroid side effects
References:
https://alamavert.com/10-key-steps-to-launching-a-successful-startup/
the best testosterone steroid
References:
https://thesecurityexchange.com/employer/kaufen-hgh-deutschland-hgh-online-zu-verkaufen/
Als Systemlieferant agiert das Unternehmen aber auch als Händler für weitere Produkte rund um die Oberflächenbearbeitung. Nach einer schwierigen Phase ist das Unternehmen seit einigen Jahren wieder auf Kurs und investiert in die Zukunft. Im Maschinenbereich werden Draht-, Senk- und Startlocherodiermaschinen, Läppstrahlkabinen und Ultraschallreinigungsgeräte entwickelt und geliefert. Neben dem Verkauf von Werkzeugstählen bietet HGH auch das Verbrauchmaterial für die EDM-Technik sowie die Läppstrahltechnik – eine gezielte und ausgetüftelte Oberflächenbearbeitung – an. Seit 1997 ist das HGH ein eingetragenes Warenzeichen, mit dem eigene Produkte gekennzeichnet werden. Mit über thirteen Millionen authentischen Erfahrungsberichten zu Arbeitgebern, Unternehmenskulturen und Gehältern möchten wir gemeinsam mit unserer Community die Arbeitswelt stetig ein Stück besser machen.
Aber wir können auch jederzeit die geleisteten Stunden wieder abbauen. Dem Leitwert des Wassers bei der Drahterosion kommt eine ganz wichtige Schlüsselrolle zu. Denn wenn bei der Bearbeitung der Leitwert durch eine mindere Qualität nicht gleichbleibend ist, verändern sich die Eigenschaften in Bezug auf die Funkenentladung zwischen Elektrode und Werkstück. Diese veränderten Gegebenheiten können so weit führen, dass das zu produzierendes Teil nicht mehr parallel oder außerhalb der zu fertigenden Toleranz liegt. Um Ihnen eine größtmögliche Sicherheit geben zu können, liefern wir ausschließlich Neuharze. „Angesichts des amerikanischen Produkthaftungsrechts möchte man als Hersteller lieber nicht dorthin verkaufen”, argumentiert Ingo Dönges. Diese werden teilweise bereits bedient, wenn die Kunden dort eigene Werke haben.
Wir möchten uns bei Ihnen für die vertrauensvolle und angenehme Zusammenarbeit in diesem Jahr bedanken, und wünschen Ihnen ein schönes Weihnachtsfest im Kreise Ihrer Lieben, einen guten Rutsch ins neue Jahr und viel Gesundheit für das neue Jahr 2023. Im industriellen Werkzeug- und Formenbau sind präzise, belastbare und langlebige Anlagen gefragt. Die HGH Vertriebs GmbH in Lüdenscheid fertigt Ultraschallreinigungs-, Läpp- und Strahlanlagen, die diesen hohen Ansprüchen entsprechen.
Als Firma, die seit 50 Jahren auf dem Markt ist, ist HGH im Werkzeug- und Formenbau bekannt. Darüber hinaus betreibt HGH Marketing über die Social Media-Kanäle. Messeauftritte des Unternehmens gibt es mittlerweile nicht mehr.
References:
https://academicsgate.com/employer/wachstumshormon-hgh-wirkung-nebenwirkungen-arginin/
high roller varies
References:
vegas high roller (https://pad.karuka.tech/e6-Jx46FSdmlVYqd_uxKoQ/)
high rollers
References:
what is a high roller in casino (https://pad.stuve.uni-ulm.de/U3nI3J5HQbqnTTeOFhUL7Q/)
what is a high Roller (https://logical-hyacinth-qp9xzt.mystrikingly.com/blog/the-best-excessive-curler-casinos-in-usa-for-2023-final-guide)
how to take dianabol cycle
References:
https://pattern-wiki.win/wiki/Dianabol_Information_Benefits_Dosage_Results_Side_Effects
dianabol anavar cycle
References:
dianabol testosterone cycle (https://frye-butcher-3.technetbloggers.de/testosterone-cypionate-an-overview)
hgh for fat loss bodybuilding
References:
2 iu hgh per day results (https://www.vulnerableyouthjobs.ca/companies/cbd-10hc-1s-lsd-legal-sicher-kaufen-bei-high420-de/)
getroids.net review
References:
https://www.jokkey.com/dorotheagrigsb
ipamorelin tesamorelin dosage
References:
http://mcforces.ru/user/rugbydollar1/
cjc 1295/ipamorelin cost
References:
ipamorelin reviews reddit (https://url.pixelx.one/laurened524581)
tesamorelin/ipamorelin cost
References:
cjc 1295 + Ipamorelin before and after (https://fmagency.co.uk/companies/a-dual-approach-for-weight-loss-and-anti-aging/)
ipamorelin and testosterone dosage
References:
https://farmfruitbasket.com/2025/09/03/sermorelin-ipamorelin-stack-blend-dosage-and-effects-guide/
cjc 1295 + ipamorelin blend for sale
References:
drug ipamorelin (https://vcanhire.com/employer/35498/prolonged-stimulation-of-growth-hormone-gh-and-insulin-like-growth-factor-i-secretion-by-cjc-1295-a-long-acting-analog-of-gh-releasing-hormone-in-healthy-adults)
cjc 1295 ipamorelin dosage calculator online
References:
Ipamorelin Information (https://gitea.alaindee.net/anljuliann6613)
tesamorelin and cjc-1295 mod grf 1-29 and ipamorelin 12mg dosage
References:
https://skitterphoto.com/photographers/1376585/bendtsen-sweet
is ipamorelin acetate troches effective
References:
https://midomesticard.com/employer/cjc-1295-ipamorelin/
cjc 1295 ipamorelin blend dosage
References:
ipamorelin pharmacie (http://tamilachat.org/community/profile/chauspooner5855/)
allergic reaction to cjc ipamorelin
References:
https://skitterphoto.com/photographers/1376862/hovgaard-barnes
cocaine prague buy coke in telegram
buy xtc prague prague plug
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Получить дополнительные сведения – https://quick-vyvod-iz-zapoya-1.ru/
Shining crown oyna seçimi saytda hər kəs üçün açıqdır.
Shining crown big win qazanmaq motivasiya yaradır.
Shining crown 40 slotları klassik kombinasiya təklif edir. Shining crown free play hər kəs üçün əlçatan seçimdir. Shining crown online casino real pulla oynamaq imkanı verir.
Play shining crown asan interfeys ilə təklif olunur.
Shining crown bell link demo tez-tez istifadə olunur.
Rəsmi səhifə rəsmi sayt.
Shining crown apk mobil üçün mükəmməl seçimdir.
Shining crown slot online tez yüklənir.
prague drugstore buy coke in telegram
buy xtc prague pure cocaine in prague
hgh steroids side effects
References:
can you buy steroids legally (https://onedance.tv/@katia94h249056?page=about)
best supplement stack 2015
References:
what are the dangers of taking anabolic steroids (http://gite.limi.ink/carsonthibault)
buy injectable anabolic steroids
References:
Primobolan steroid (https://gitea.mpc-web.jp/carmelolamingt)
Нужна презентация? генератор презентаций Создавайте убедительные презентации за минуты. Умный генератор формирует структуру, дизайн и иллюстрации из вашего текста. Библиотека шаблонов, фирстиль, графики, экспорт PPTX/PDF, совместная работа и комментарии — всё в одном сервисе.
Ən yaxşı seçimlərdən biri də Sunny Coin Hold The Spin onlayn versiyasıdır. Sunny Coin hold the spin slot online çoxlu istifadəçi qazanır.
Sunny Coin Hold The Spin slot oyununda böyük qalibiyyət şansı var. Sunny coin: hold the spin slot oyun təcrübəsi mükəmməldir.
Rəsmi səhifə burada https://sunny-coin.com.az/.
Sunny Coin Hold The Spin slot böyük qaliblərə şans verir. Sunny Coin Hold The Spin online casino oyunçular üçün məşhurdur. Sunny coin 2 hold the spin slot istifadəçilərin sevimlisidir.
Sunny coin: hold the spin slot istifadəçi dostudur. Sunny Coin Hold The Spin real pul üçün əlverişlidir.
anabolic steroids and cancer
References:
https://vidstreamr.com/@shannahofmann2?page=about
do anabolic steroids show up on drug test
References:
https://template108.webekspor.com/?p=80
best shredding supplement stack
References:
5 bodybuilding supplements – https://www.nemusic.rocks/brigida99c5514,
safest injectable steroid
References:
https://git.pasarex.com/arlenfairbridg
значки эмалированные на заказ значки под заказ
значки на заказ металлические на заказ сделать значки на заказ москва
значки круглые на заказ изготовление значков на заказ москва
fast muscle builder
References:
https://ngoma.app/beckyo2952710
joszaki regisztracio https://joszaki.hu/
Formula 1 könüllü proqramı haqqında maraqlı məlumatlar burada. Bakı Formula 1 xəritəsi üzrə hər bir döngəni tanıyın.
2025 təqvimi və yarış tarixləri burada ➡ formula 1 2025 calendar.
Formula 1 haqqinda melumat axtaranlar üçün faydalı mənbə. Formula 1 volunteer təcrübəsi ilə bağlı məsləhətlər.
Formula 1 haqqında maraqlı tarixi faktlar. Formula 1 volunteer olmaq istəyənlər üçün təcrübə. Formula 1 izləyiciləri üçün ən son xəbərlər. Formula 1 logo simvolikasının mənası barədə məlumat.
post cycle therapy gnc
References:
https://www.tikosatis.com/index.php?page=user&action=pub_profile&id=332451
iOS üçün soccer yükləyib pulsuz oynayın.
Soccer 365 ilə futbol xəbərlərindən xəbərdar olun. Futbol xəbərlərinin toplanıldığı əsas yer http://www.soccer.com.az sayılır.
Super liquid soccer fərqli futbol təcrübəsi bəxş edir. Pro soccer online multiplayer həvəskarları üçün uyğundur. Soccer manager 2025 mod apk ilə komandanızı idarə edin.
Soccer game klassik futbol təcrübəsi təqdim edir. Dream league soccer 2016 köhnə versiya sevənlər üçün uyğundur. Livescore.com.tr live soccer scores azarkeşlər üçün əhəmiyyətlidir. Soccer games müxtəlif janrlarda futbol təqdim edir.
sexual stimulant drugs for males
References:
https://git.lmskaran.com/johnnyborrego
best steroid for mass and strength
References:
https://maps.google.hr/url?q=https://www.valley.md/dianabol-cycle-benefits-and-risks
anabolic steroid street names
References:
https://linkvault.win/story.php?title=dianabol-cycles-titan-approved-formula-for-peak-performance
LaLiga canlı izləmə üçün ideal mənbədir. LaLiga turnir cədvəlində mövqeləri izləmək maraqlıdır.
LaLiga canlı futbol həvəskarlarının seçimi. Yeni “LaLiga EA Sports” loqosu çox bəyənildi.
Yeni xal cədvəli üçün ən doğru ünvan — laliga table 2025. Orada bütün komandalar barədə məlumat var.
LaLiga bombardirlər siyahısı yeniləndi.
LaLiga tv canlı baxmaq üçün seçimlər.
LaLiga defenders və midfielders siyahısı.
İspaniya LaLiga kupası hər il diqqət çəkir.
LaLiga oyunlarının qrafiki və nəticələri burada.
best stack to gain muscle
References:
https://md.darmstadt.ccc.de/zYZ0KjkGRiWivKwTqgyAVw/
best steroid cycle for cutting
References:
https://www.google.at/url?q=https://bookmarkingworld.review/story.php?title=mastering-dianabol-cycles-your-definitive-blueprint-for-a-massive-bulk
Мен ар дайым Лука Модричти көргөндө чыныгы лидерликти байкайм.Модрич кетсе дагы, анын izi футболдо калат. Анын карьерасынын узактыгы профессионалдуулуктун белгиси. Модричтин энергиясы таң калтырат. Модрич тууралуу фактыларды текшерип көр: Лука Модрич статистика. Анын ысымы футбол тарыхында калат.
Алар бирге көптөгөн ЛЧ жеңиштерин алып келишкен. Бул адамдын жашоосу — чыныгы күрөш. Көптөр “Модрич канча табат?” деп сурашат. Анын тажрыйбасы каалаган клубга керектүү.
Бул жигит жөн эле мушкер эмес, чыныгы согуш өнөрүнүн устаты. Алекс Перейра — чыныгы мисал чыдамкайлык жана эрктүүлүктүн. Анын рекорду жана жеңиштери тууралуу кенен маалымат: Перейра рекорд. Ар бир муштумунда тарых жатат.
Көптөр Перейраны жеңет дешет, бирок ал дайыма жооп берет.
Перейра эч качан колун түшүргөн эмес. Перейра ар бир жеңиши менен тарых жазат. Анын соккусунан кийин көптөр оңоло албай калган.
Перейра — элдин арасынан чыккан легенда. Бул жөн эле мушкер эмес, бул философ.
Наркологическая клиника «Честный врач» в Нижнем Новгороде оказывает круглосуточную помощь людям с алкогольной и наркотической зависимостью. Возможен выезд нарколога на дом, проведение капельницы при запое и комплексное лечение алкоголизма и наркомании с сохранением конфиденциальности.
Ознакомиться с деталями – наркотики курительные соли
Нижегородская наркологическая клиника «Честный врач» предлагает услуги по выведению из запоя и лечению зависимости. Возможен вызов нарколога на дом, постановка капельниц при алкогольной интоксикации, а также полноценные программы лечения алкоголизма и наркомании.
Подробнее –
В Нижнем Новгороде работает наркологическая клиника «Честный врач», где специалисты помогают вывести из запоя, проводят капельницы на дому и оказывают профессиональную наркологическую помощь. В клинике доступно лечение наркомании и алкоголизма с индивидуальным подходом к каждому пациенту.
Выяснить больше –
Нижегородская наркологическая клиника «Честный врач» предлагает услуги по выведению из запоя и лечению зависимости. Возможен вызов нарколога на дом, постановка капельниц при алкогольной интоксикации, а также полноценные программы лечения алкоголизма и наркомании.
Подробнее – вред от вейпов и электронных сигарет
Наркологическая клиника «Честный врач» в Нижнем Новгороде оказывает круглосуточную помощь людям с алкогольной и наркотической зависимостью. Возможен выезд нарколога на дом, проведение капельницы при запое и комплексное лечение алкоголизма и наркомании с сохранением конфиденциальности.
Исследовать вопрос подробнее – антибиотики и вино
Наркологическая клиника «Честный врач» в Нижнем Новгороде оказывает круглосуточную помощь людям с алкогольной и наркотической зависимостью. Возможен выезд нарколога на дом, проведение капельницы при запое и комплексное лечение алкоголизма и наркомании с сохранением конфиденциальности.
Подробнее – морфин таблетки
Флойд Мейвезер дүйнөдөгү эң белгилүү мушкерлердин бири. Флойд Мейвезер эч качан жеңилбеген мушкер катары белгилүү. Жаңы жаңылыктарды окуу үчүн floyd-mayweather-kg.com барагына өтүңүз.
Флойд Мейвезерди көрүү ар бир спорт күйөрманы үчүн майрам. Анын мушташ стили өзгөчө жана натыйжалуу. Анын акыркы жаңылыктарын укпай калган адам жок.
Флойд Мейвезер – профессионалдуулуктун чордону.
Флойд Мейвезердин тарыхтагы орду чоң. Флойд Мейвезер ар бир жаш спортчуга үлгү. Флойд Мейвезер ар дайым жаңы рекорддорду жарата берет.
Если требуется срочная наркологическая помощь в Нижнем Новгороде, клиника «Честный врач» готова помочь. Врачи выезжают на дом, проводят капельницы при запое, обеспечивают безопасное выведение из запойного состояния и предлагают программы лечения наркомании и алкоголизма.
Изучить вопрос глубже – наркологический центр наркология
Клиника «Честный врач» в Нижнем Новгороде специализируется на лечении зависимостей. Здесь можно пройти курс терапии от алкоголизма и наркомании, вызвать нарколога на дом или заказать капельницу для снятия запоя. Опытные врачи обеспечивают поддержку и медицинский контроль на всех этапах.
Подробнее – игромания зависимость лечение
Наркологическая клиника «Честный врач» в Нижнем Новгороде оказывает круглосуточную помощь людям с алкогольной и наркотической зависимостью. Возможен выезд нарколога на дом, проведение капельницы при запое и комплексное лечение алкоголизма и наркомании с сохранением конфиденциальности.
Подробнее можно узнать тут – https://otalkogolizma.ru/stati/nasledstvennyj-alkogolizm
Наркологическая клиника «Честный врач» в Нижнем Новгороде оказывает круглосуточную помощь людям с алкогольной и наркотической зависимостью. Возможен выезд нарколога на дом, проведение капельницы при запое и комплексное лечение алкоголизма и наркомании с сохранением конфиденциальности.
Ознакомиться с деталями – морфин таблетки
Наркологическая клиника «Честный врач» в Нижнем Новгороде оказывает анонимные услуги: лечение алкоголизма, терапию наркомании, выезд нарколога на дом. Пациентам доступна капельница от запоя и медицинское сопровождение для восстановления здоровья и предотвращения осложнений.
Получить дополнительную информацию – нижний клиника лечения алкоголизма
afrik foot pronostic telecharger 1xbet apk
melbet – paris sportif melbet telecharger
melbet – paris sportif https://pari-foot2.com
Клиника «Честный врач» в Нижнем Новгороде специализируется на лечении зависимостей. Здесь можно пройти курс терапии от алкоголизма и наркомании, вызвать нарколога на дом или заказать капельницу для снятия запоя. Опытные врачи обеспечивают поддержку и медицинский контроль на всех этапах.
Узнать больше – амфетамин эффект
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Посмотреть всё – https://mililie.com/kochidoripiu
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Изучить материалы по теме – https://luizantoniosanches.com/index.php/2023/12/26/ola-mundo
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Наши рекомендации — тут – https://signarrowgifts.com/looking-for-the-best-place-to-buy-epic-gift-from-us
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Прочесть всё о… – https://quackplex.com/livestock-management/care-and-feeding/do-chickens-pee-and-poop-out-of-the-same-hole
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Перейти к полной версии – https://www.saratilda.se/lana-till-kontantinsats
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Детальнее – https://acerosinoxiperu.com/index.php/2018/06/23/where-better-to-go-for-a-delicious-coffee-5
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Подробности по ссылке – https://somo-sushi.com/%D8%AF%D8%B1%D8%A8-%D8%AF%D9%85%D8%A7%D8%BA%D9%83
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Детальнее – https://amasconsultores.cl/course/photographic-for-beginner-masterclass/author
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Прочесть заключение эксперта – https://sergelt.mn/?p=20952
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Только факты! – http://www.jasonrohde.com/hello-world
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Перейти к полной версии – https://www.letyourhairdownaz.com/hair-extensions-scottsdale
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Хочу знать больше – https://hndexpress.net/hnd%E2%9D%A4%EF%B8%8Fgui-duoc-tat-ca-cac-mat-hang-tu-kho-den-rat-kho.html
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Что скрывают от вас? – https://midnightsunactivities.com/experience-the-ultimate-getaway-with-luxury-yacht-rentals
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Информация доступна здесь – https://ppopwave.com/2024/06/10/sb19-bini-flow-g-sunkissed-lola-set-to-headline-opm-event-of-the-year-puregolds-nasa-atin-ang-panalo-concert
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Открой скрытое – https://sergelt.mn/?p=20952
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Раскрыть тему полностью – https://cainfo.online/welcome-aboard
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Запросить дополнительные данные – https://booktechlabs.com/social-distancing-flatten-the-curve-contact-tracing-contactless-dining
Перед таблицей коротко поясним логику: мы выбираем самый безопасный маршрут именно для вашей ситуации, а при изменении состояния оперативно переключаемся на другой формат без пауз.
Подробнее – http://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-deshevo-v-pushkino/
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Заходи — там интересно – https://www.codingate.com/mr-sopheakmonkol-soks-perspectives-on-how-business-should-be-digitalized
Вывод из запоя в Пушкино в клинике «Трезвый Путь» — это оперативная помощь на дому и в стационаре, персональные детокс-схемы и бережное восстановление организма без постановки на учёт. Мы подключаемся круглосуточно, аккуратно снимаем интоксикацию, стабилизируем давление и пульс, уменьшаем тремор, тревогу и бессонницу, а затем предлагаем понятный маршрут к ремиссии, который вписывается в ваш рабочий и семейный график. Цель — безопасно пройти острый период и не «сорваться» обратно, когда станет чуть полегче.
Получить больше информации – помощь вывод из запоя
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Продолжить чтение – https://ilovetostyle.com/?page_id=174
Перед таблицей коротко поясним логику: мы выбираем самый безопасный маршрут именно для вашей ситуации, а при изменении состояния оперативно переключаемся на другой формат без пауз.
Детальнее – https://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-na-domu-v-pushkino
Запой — это не просто «тяжёлое похмелье», а состояние с риском осложнений со стороны сердца, печени и нервной системы. Ниже — признаки, при которых помощь врача нужна без промедления:
Изучить вопрос глубже – https://vyvod-iz-zapoya-reutov7.ru/vyvod-iz-zapoya-v-stacionare-v-reutove/
Этап
Получить дополнительную информацию – https://narkolog-na-dom-zhukovskij7.ru
Если по ходу первичного осмотра выявляются «красные флаги» (спутанность сознания, нестабильное давление/ритм, кровавая рвота, подозрение на делирий), врач немедленно предложит госпитализацию и аккуратно организует перевод — безопасность всегда выше удобства.
Изучить вопрос глубже – http://narkolog-na-dom-zhukovskij7.ru/narkolog-na-dom-kruglosutochno-v-zhukovskom/
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Перейти к полной версии – https://rijocampers.is/how-to-make-your-camper-van-journey-in-iceland-awesome
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Слушай внимательно — тут важно – https://sabahreklam.com/sabah-sari-sayfalar
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Как достичь результата? – https://tockprojects.com/womity-en-el-confidencial
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Интересует подробная информация – https://decenterx.nl/decentralized-finance-defi
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Нажмите, чтобы узнать больше – https://audiovisualeslahuerta.com/la-huerta-de-la-esquina-con-las-luchas-campesinas-the-corner-veggie-garden-with-peasants-struggle
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Выяснить больше – https://ulemantenan.site/hello-world
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Прочесть заключение эксперта – https://mglj.fr/2022/11/28/bail-commercial-precaire-ou-bail-derogatoire-explications
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Не упусти шанс – https://biblejournalingdigitally.com/product/copy-of-ceramic-mug-11oz-15oz-2
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Смотрите также… – https://nexzmediagroup.com/elementor-1385
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Продолжить чтение – https://oficinas.unsch.edu.pe/ocri/convocatoria-de-becas-de-maestria-en-la-universidad-rey-juan-carlos
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Уточнить детали – https://www.nurfotografie.de/hello-world
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Обратиться к источнику – https://freguesianews.com.br/2024/01/22/explorando-as-oportunidades-de-entretenimento-novoscassinos-com-br-em-destaque
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Узнать из первых рук – https://www.mahour.ca/fa/eb/eb4
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Это ещё не всё… – https://folhanoroeste.com.br/cotidiano/idosos-madrugam-no-terminal-rodoviario-do-tiete-para-viajar-de-graca
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Перейти к полной версии – https://uktez.com/governer-uttarakhand-baby-rani-distributed-gifts-to-nariniketan-women
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Получить полную информацию – https://davelampole.be/2022/02/23/hallo-wereld
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Открой скрытое – https://rasputinviktor.com/index.php/product/integra-trident
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Где почитать поподробнее? – https://chatadoubravka.cz/component/k2/item/14-do-what-you-like?start=5760
В этой статье-обзоре мы соберем актуальную информацию и интересные факты, которые освещают важные темы. Читатели смогут ознакомиться с различными мнениями и подходами, что позволит им расширить кругозор и глубже понять обсуждаемые вопросы.
Только для своих – https://www.ishimitsu.com.mx/uncategorized/hello-world
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Подробности по ссылке – https://cerrajeroelespinar.es/hola-mundo
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Уточнить детали – https://www.ashfield-hub.com/sample-page
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Хочешь знать всё? – https://saas4us.com/revolutionize-your-business-with-our-cutting-edge
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Узнать больше – posle-kapelnicy-ot-zapoya
Чтобы у семьи было чёткое понимание, что и в какой последовательности мы делаем, ниже — рабочий алгоритм для стационара и для выезда на дом (шаги идентичны, различается только объём мониторинга и доступная диагностика).
Узнать больше – капельница от запоя цена видное
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Подробнее можно узнать тут – вызов на дом капельницы от запоя
Вывод из запоя — это управляемая медицинская процедура, а не «волшебная капля» или крепкий чай с рассолом. «Формула Трезвости» организует помощь в Ногинске круглосуточно: выезд врача на дом или приём в стационаре, детоксикация с мониторингом, мягкая коррекция сна и тревоги, подробный план на первые 48–72 часа. Мы действуем безопасно, конфиденциально и без «мелкого шрифта» — объясняем, что и зачем делаем, согласовываем схему и фиксируем смету до начала процедур.
Детальнее – http://vyvod-iz-zapoya-noginsk7.ru/vyvod-iz-zapoya-na-domu-v-noginske/https://vyvod-iz-zapoya-noginsk7.ru
Метод
Изучить вопрос глубже – skolko-stoit-kodirovanie-ot-alkogolizma
Анын голдорунун статистикасы абдан таасирдүү.Кейн дайыма жоопкерчиликти өз мойнуна алат. Гарри Кейндин акыркы жаңылыктары жана видеолору ушул жерде жарыяланат: http://www.harry-kane-kg.com. Футбол дүйнөсү мындай оюнчуларды сейрек көрөт.
Гарри Кейндин оюну ар дайым жогорку деңгээлде.
Гарри Кейндин балдары футболду жакшы көрүшөт. Футболдо мындай туруктуу оюнчулар аз. Кейн ар бир сезон өзүн мыкты формада кармайт. Ал бала чагынан эле футболчу болууну каалаган. Ал ар бир сезон ондогон гол киргизет. Кейндин трансферлери ар дайым чоң темалар.
фитнес клуб тренировка сеть фитнес клубов
Медикаментозное пролонгированное
Подробнее можно узнать тут – https://kodirovanie-ot-alkogolizma-vidnoe7.ru/kodirovanie-ot-alkogolizma-na-domu-v-vidnom/
При критических симптомах (потеря сознания, сильная одышка, подозрение на инсульт/инфаркт) необходимо звонить 103/112. Мы подключимся к маршрутизации и организуем перевод в стационар.
Подробнее тут – http://vyvod-iz-zapoya-noginsk7.ru/vyvod-iz-zapoya-kruglosutochno-v-noginske/
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Исследовать вопрос подробнее – https://corfopym.com/consultoria-y-asesoria-en-seguridad-industrial
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Изучить материалы по теме – https://deguzmanofgapan.com/connecting-with-cousins-the-guzman-way
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Это ещё не всё… – https://arccoco.com/yakedo
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Открой скрытое – https://zebra.pk/product/university-of-okara-okara-city
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Это стоит прочитать полностью – https://melvinformulations.com/partnership-to-increase-covid19-testing-capacity-and-track-all-covid-variants
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Как достичь результата? – https://annonces.mamafrica.net/tag/sci-cote-divoire
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Хочешь знать всё? – https://bhhawkingclub.com.br/ola-mundo
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Хочешь знать всё? – https://www.oaypa.ca/sick-kids-the-young-families-program
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Обратиться к источнику – https://www.oaypa.ca/sick-kids-the-young-families-program
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Подробнее – https://unosesentaiuno.com/2023/06/05/taj-luxury
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Интересует подробная информация – https://www.azzurriniguardese.it/2021/10/24/u19-gold-i-gg-girone-gold
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Давай разберёмся досконально – https://writerscafeteria.com/where-the-crawdads-sing-book-review
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Открой скрытое – https://starvisionbankingfinancialservices.com/2015/12/05/hello-world-2-2
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Хочешь знать всё? – https://postauro.com/email-marketing-ideas-to-shake-your-business-up-cleverscale-com
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Детали по клику – https://gtelectricservice.com/be-my-guest
Мы предлагаем вам подробное руководство, основанное на проверенных источниках и реальных примерах. Каждая часть публикации направлена на то, чтобы помочь вам разобраться в сложных вопросах и применить знания на практике.
Это ещё не всё… – https://canterfluidpower.com/guide-for-bop-testing-inspections-and-maintenance
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Прочитать подробнее – https://writerscafeteria.com/where-the-crawdads-sing-book-review
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Дополнительно читайте здесь – http://www.wif.malopolska.pl/info
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Узнать из первых рук – https://arccoco.com/yakedo
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Осуществить глубокий анализ – https://altin.co.in/2018/09/13/ganpati-bappa-morya
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Подробнее можно узнать тут – https://newoyingboafricanmarket.com/hello-world
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Посмотреть всё – https://medischpedicuredidam.nl/pijnlijke-teennagel
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Посмотреть подробности – https://vparkcoc.org/our-prayers
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Детальнее – https://alwataniyeh.com/2023/05/27/%D8%A7%D9%84%D8%B5%D9%8A%D9%86-%D9%81%D9%8A-%D8%B5%D9%86%D8%B9%D8%A7%D8%A1-%D8%A7%D9%84%D8%A7%D9%86%D8%AA%D9%82%D8%A7%D9%84-%D9%85%D9%86-%D8%A7%D9%84%D8%AD%D9%8A%D8%A7%D8%AF-%D8%A5%D9%84%D9%89-%D8%A7
Мы учитываем сопутствующие заболевания, прием хронических препаратов, возраст и образ жизни. На первичной консультации специалист задаёт уточняющие вопросы, чтобы определить риски, подобрать безопасные препараты и предложить удобный формат: стационар, амбулаторно или выезд на дом. Такой подход сокращает срок восстановления и повышает устойчивость результата.
Ознакомиться с деталями – наркологическая клиника телефон
Выезд врача позволяет начать помощь сразу, без ожидания свободной палаты. Специалист оценит состояние, проведёт осмотр, поставит капельницу, даст рекомендации по режиму и питанию, объяснит правила безопасности. Мы оставляем подробные инструкции родственникам, чтобы дома поддерживались питьевой режим, контроль давления и спокойная обстановка. Если домашних условий недостаточно (выраженная слабость, риски осложнений, сопутствующие заболевания), мы организуем транспортировку в стационар без задержек и бюрократии.
Выяснить больше – http://narkologicheskaya-klinika-balashiha0.ru/anonimnaya-narkologicheskaya-klinika-v-balashihe/
Мы учитываем сопутствующие заболевания, прием хронических препаратов, возраст и образ жизни. На первичной консультации специалист задаёт уточняющие вопросы, чтобы определить риски, подобрать безопасные препараты и предложить удобный формат: стационар, амбулаторно или выезд на дом. Такой подход сокращает срок восстановления и повышает устойчивость результата.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-balashiha0.ru/narkologicheskaya-klinika-telefon-v-balashihe/
Формат
Подробнее можно узнать тут – narkologicheskaya-klinika-himki0.ru/
Домашний формат подходит, когда показатели стабильны, а у пациента есть поддержка близких. Врач осматривает, ставит капельницу, оставляет понятные инструкции по режиму, сну, гидратации и «красным флажкам». Если дома становится «узко» по медпоказаниям — переводим в стационар без задержек и лишней бюрократии.
Выяснить больше – частные наркологические клиники подольск
Жанкүйөрлөр үчүн ыңгайлуу навигация: акыркы жаңылык, кийинки беттеш, коэффициенттер жана прогноздор.
«Ислам Махачев кийинки ким менен?» деген суроого календарь жана промоутер маалыматтарынын негизинде жооп беребиз. islam-makhachev-kg com Медиа пакет: постерлер, цитата карточкалары жана обои. Соцтармакка ылайык форматтар бар. Эгер коэффициенттерди издеп жатсаңыз, базардагы негизги линияларды салыштырып көрүңүз. Илия Топурия vs Ислам Махачев айкашы жөнүндө ушак-айың эмес, текшерилген булактар гана берилет. Салмакты калыбына келтирүү жана кемитүү тартиби боюнча расмий маалыматтардан үзүндүлөр келтирилет.
Ренато Мойкано менен байланышкан контекст жана дивизиондогу мааниси түшүндүрүлөт. Кайсы раунддарда өзгөрүү болушу ыктымал экенин тенденцияларга карап белгилеп беребиз. Сүрөттөр жана обои: социалдык тармак үчүн ылайыктуу форматтар жана резолюциялар бар. Эгер каталар байкалса, пикир калтырып, оңдоолорго салым кошо аласыз.
Мы — частная наркологическая клиника, где скорость запуска помощи сочетается с деликатностью и прозрачностью. Команда дежурит круглосуточно, выезжает на дом по Подольску и ближайшим районам, принимает в стационаре и амбулаторно. Все решения принимаются после очного осмотра и оценки рисков, без «универсальных» схем и навязанных услуг.
Разобраться лучше – https://narkologicheskaya-klinika-podolsk0.ru/chastnaya-narkologicheskaya-klinika-v-podolske/
Мы — частная наркологическая служба в Химках, где каждый шаг лечения объясняется простым языком и запускается без задержек. С первого контакта дежурный врач уточняет жалобы, длительность запоя, хронические диагнозы и принимаемые лекарства, после чего предлагает безопасный старт: выезд на дом, дневной формат или госпитализацию в стационар 24/7. Наши внутренние регламенты построены вокруг двух опор — безопасности и приватности. Мы используем минимально необходимый набор персональных данных, ограничиваем доступ к медицинской карте, сохраняем нейтральную коммуникацию по телефону и не ставим на учёт.
Выяснить больше – http://narkologicheskaya-klinika-himki0.ru/chastnaya-narkologicheskaya-klinika-v-himkah/
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Перейти к полной версии – https://trouve-un-job.fr/questions-reponses-entretien-embauche
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Посмотреть всё – https://travel-book.net/hausutenbosupool-konzatu
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Интересует подробная информация – https://lcg.org.ua/1200×800
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Изучить вопрос глубже – https://indivinejourneys.com/holi-festival-in-india
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Жми сюда — получишь ответ – https://www.humtechke.com/the-latest-learning-tablets-in-the-kenyan-market-today
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Не упусти шанс – https://an-ve.co.uk/post-28-1
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Как это работает — подробно – https://mimicon.jp/archives/1
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Слушай внимательно — тут важно – https://fridocacao-copy.stackedsite.com/what-you-need-to-know-coffee-vs-cacao
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Уточнить детали – https://www.spolekgeodetu.cz/8-vyrocni-schuze-slezskeho-spolku-geodetu
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Полезно знать – https://hertsflowers.co.uk/blog
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Доступ к полной версии – https://rnogroup.com/navigating-right-of-way-management-strategies-for-success
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Это стоит прочитать полностью – https://www.kirra.jp/2020/05/22/forest-style-bar-kirra%E3%83%90%E3%83%B3%E3%83%93%E3%83%BC%E3%83%8E
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Смотри, что ещё есть – http://robtinworth.com/cropped-emmymanhunt-large-jpg
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Хочешь знать всё? – https://crystaldevelopers.net/hello-world
Мы сознательно фиксируем не только «медицинские» параметры, но и бытовые маркеры: сколько воды выпито, как переносится тёплая пища малыми порциями, какой свет в комнате перед сном. Эти детали активно упоминаются в клинических рекомендациях, потому что нередко именно они решают исход первой ночи лучше, чем попытка «усилить» таблеткой.
Углубиться в тему – http://narkologicheskaya-klinika-stavropol15.ru/chastnaya-narkologicheskaya-klinika-stavropol/
В реальной городской ткани Ставрополя на самочувствие влияет не только схема лечения, но и логистика: утренние заторы на въезде, плотная застройка частного сектора, шумные перекрёстки. Мы заранее «поглощаем» эти риски организацией: секторные выезды, согласованная парковка, нейтральная переписка без «говорящих» терминов, при необходимости — курьерская доставка расходников отдельно от врача, чтобы на месте сразу переходить к оценке и запуску инфузии. Пациенту не нужно «вписываться» в систему — система подстраивается под реальную жизнь человека, экономя десятки минут и снижая сенсорную нагрузку перед первой ночью.
Получить больше информации – наркологическая клиника ставрополь
В реальности Воронежа на самочувствие влияет не только фармакология, но и логистика: трассы с плотным трафиком, яркое освещение подъездов, очереди в медорганизациях. «ВоронежМедЦентр» гасит эти раздражители организационно: «тихие окна» приёма без коридорного шума, согласованная парковка, немаркированные выезды, нейтральные формулировки в документах и «беззвучные» напоминания. Снижение сенсорной нагрузки — это не декоративная опция, а клинический фактор: спокойная первая ночь, ровный пульс к вечеру, предсказуемость режима воды и тёплой пищи малыми порциями.
Узнать больше – https://narkologicheskaya-klinika-voronezh15.ru/voronezh-narkologiya
Анонимность встроена в процесс: немаркированные выезды, гражданская одежда персонала, нейтральные формулировки в документах и «беззвучные» уведомления. Медицинская карта ведётся с разграничением доступа по ролям, а для связи с близкими предусмотрены «тихие окна». Конфиденциальность не декларируется — она реализована в каждом шаге, от первичного звонка до плановых контрольных точек.
Подробнее – https://narkologicheskaya-klinika-v-voronezhe15.ru/
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Смотрите также… – https://yasulog.org/how-to-cancel-nordvpn
Стартовый осмотр должен быть быстрым и осмысленным. Мы исключаем «обязательные» исследования, которые не меняют тактику, и оставляем то, что прямо влияет на состав инфузии, темп, место ведения (дом/амбулатория/стационар) и объём поведенческих рекомендаций. Решения принимаются на свежих цифрах и клинической картине «здесь и сейчас», а повторные замеры назначаются не «по привычке», а по смыслу. Это экономит силы пациента и время команды, а главное — уменьшает фармакологическую нагрузку без потери безопасности.
Подробнее – https://narkologicheskaya-klinika-stavropol15.ru/narkolog-stavropol
Городская среда Калининграда — контрастные подъезды, близость моря с переменчивым ветром, плотный сезонный трафик — может усиливать вечернюю реактивность. Поэтому маршруты организованы «тихо»: согласованная парковка, отдельный вход без вывесок и очередей, короткая регистрация, приглушённая тёплая подсветка в зоне ожидания, отсутствие громких объявлений. Коммуникация с пациентами и близкими строится через защищённые каналы, а уведомления приходят в «беззвучном» режиме в согласованные «окна». Такой дизайн не ради «красоты сервиса», а ради клинического эффекта: чем меньше сенсорной нагрузки, тем быстрее выравнивается пульс к вечеру, тем легче возвращается переносимость питья и тёплой пищи, тем меньше потребность в ночных «усилениях».
Ознакомиться с деталями – наркологическая клиника нарколог в калининграде
Круглосуточный приём означает не просто «дверь открыта 24/7», а способность команды держать безопасный и предсказуемый темп в любой час. Ночью — короткие поведенческие включения и мягкая коррекция тревоги, днём — уточнение витальных и планирования питания/воды, вечером — «световые» правила и дыхательные циклы. За маршрутом следит куратор, благодаря чему переходы между форматами (дом – амбулатория – стационар) проходят без «перезапуска истории»: все данные и договорённости продолжают работать, не требуя заново пересказывать детали.
Получить больше информации – наркологическая клиника стационар воронеж
В «Центр Трезвости Воронеж» приватность не обсуждается — она проектируется. Выбор нейтральных формулировок в чеках, немаркированные выезды, «беззвучные» уведомления, отдельные входы и доступ к карте наблюдения только по ролям — это норма, а не «услуга». Пациент может назначить доверенное лицо, чтобы получать краткие апдейты в согласованные временные окна.
Получить дополнительную информацию – https://narkologicheskaya-klinika-v-voronezhe15.ru/narkologicheskaya-klinika-voronezh-otzyvy/
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Заходи — там интересно – https://fricco.com.br/2023/12/08/gel-de-carboidrato-para-que-serve-ele-engorda-qual-o-melhor
Режим 24/7 — это не только открытая дверь, но и правильно расставленные акценты по часам суток. Ночью — больше поведенческих опор и короткие видеовставки, днём — контроль витальных, уточнение плана гидратации и питания, вечером — «световые правила» и дыхательные циклы. В каждом окне мы знаем, что именно проверяем и что считаем успехом: так исчезают импровизации и ненужные «усиления», а пациент получает предсказуемую траекторию.
Изучить вопрос глубже – наркологическая клиника нарколог в ставрополе
Если ожидаемая динамика «плоская», врач меняет один параметр и назначает повторную оценку. Такой подход сохраняет ясность днём и снижает вероятность побочных реакций.
Получить дополнительные сведения – наркологическая клиника наркологический центр
Мы сознательно фиксируем не только «медицинские» параметры, но и бытовые маркеры: сколько воды выпито, как переносится тёплая пища малыми порциями, какой свет в комнате перед сном. Эти детали активно упоминаются в клинических рекомендациях, потому что нередко именно они решают исход первой ночи лучше, чем попытка «усилить» таблеткой.
Изучить вопрос глубже – https://narkologicheskaya-klinika-stavropol15.ru
В реальности Воронежа на самочувствие влияет не только фармакология, но и логистика: трассы с плотным трафиком, яркое освещение подъездов, очереди в медорганизациях. «ВоронежМедЦентр» гасит эти раздражители организационно: «тихие окна» приёма без коридорного шума, согласованная парковка, немаркированные выезды, нейтральные формулировки в документах и «беззвучные» напоминания. Снижение сенсорной нагрузки — это не декоративная опция, а клинический фактор: спокойная первая ночь, ровный пульс к вечеру, предсказуемость режима воды и тёплой пищи малыми порциями.
Детальнее – лечение в наркологической клинике в воронеже
Город влияет на динамику терапии: плотный трафик, яркие подъезды, шумные дворы способны поднимать вечернюю реактивность и мешать засыпанию. Поэтому в Воронеже маршруты строятся «тихо»: согласованная парковка, отдельный вход без очередей, «немаркированный» транспорт, быстрый подъем до кабинета. Мы сознательно уменьшаем сенсорную нагрузку: приглушённый тёплый свет в зале ожидания, отсутствие громких объявлений, лаконичные анкеты без «расспросов ради анкеты». Когда вокруг меньше шума, организм отвечает предсказуемо — и лечение становится короче и легче переносимым.
Изучить вопрос глубже – наркологическая клиника цены
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Узнать больше > – https://alku.fi/laihdu-10-kg-nopeasti
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Изучить материалы по теме – https://avteis.org/sample-page/a-nosa-historia
Клиника принимает 24/7 без очередей: ночной блок специально настроен под «трудные часы», когда усиливаются панические мысли и реактивность пульса. Для тех, кому легче дома, выездная служба приводит помощь в знакомое пространство; если нужны короткие контрольные включения, применяем видеосвязь вечером (15–20 минут), чтобы корректно настроить ритуалы засыпания, дыхательные циклы и «световые правила». Маршрут фиксируется в единой карте наблюдения — этот документ доступен команде по ролям и защищает от «повторов заново», когда формат меняется (дом – амбулатория – стационар).
Детальнее – запой наркологическая клиника
Городская среда Калининграда — контрастные подъезды, близость моря с переменчивым ветром, плотный сезонный трафик — может усиливать вечернюю реактивность. Поэтому маршруты организованы «тихо»: согласованная парковка, отдельный вход без вывесок и очередей, короткая регистрация, приглушённая тёплая подсветка в зоне ожидания, отсутствие громких объявлений. Коммуникация с пациентами и близкими строится через защищённые каналы, а уведомления приходят в «беззвучном» режиме в согласованные «окна». Такой дизайн не ради «красоты сервиса», а ради клинического эффекта: чем меньше сенсорной нагрузки, тем быстрее выравнивается пульс к вечеру, тем легче возвращается переносимость питья и тёплой пищи, тем меньше потребность в ночных «усилениях».
Выяснить больше – платная наркологическая клиника в калининграде
Домашнее лечение не уступает стационару по стандартам безопасности, если соблюдены три условия: корректная стратификация риска, титрование инфузий через оборудование с точным шагом и регулярные «тихие» проверки без навязчивой аппаратной нагрузки. Наши мобильные бригады приезжают с портативным кардиомонитором, инфузоматом, пульсоксиметром и экспресс-анализаторами, а также набором одноразовых расходников. Кроме приборов, мы привозим «средовые» решения: тёплую лампу, светозащитные шторки, укладки для безопасной организации зоны процедуры — это помогает телу быстрее переключаться из тревоги в восстановление без лишних препаратов.
Получить больше информации – http://narkolog-na-dom-petrozavodsk15.ru/vyvod-iz-zapoya-narkolog-na-dom-petrozavodsk/https://narkolog-na-dom-petrozavodsk15.ru
Домашнее лечение не уступает стационару по стандартам безопасности, если соблюдены три условия: корректная стратификация риска, титрование инфузий через оборудование с точным шагом и регулярные «тихие» проверки без навязчивой аппаратной нагрузки. Наши мобильные бригады приезжают с портативным кардиомонитором, инфузоматом, пульсоксиметром и экспресс-анализаторами, а также набором одноразовых расходников. Кроме приборов, мы привозим «средовые» решения: тёплую лампу, светозащитные шторки, укладки для безопасной организации зоны процедуры — это помогает телу быстрее переключаться из тревоги в восстановление без лишних препаратов.
Получить дополнительные сведения – запой нарколог на дом петрозаводск
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Изучить вопрос глубже – вывод из запоя дешево
Универсальной «сильной капельницы» не существует. Состав подбирается по ведущим симптомам и переносимости; важен не только «чем», но и «когда», особенно в сумерки. Примеры ниже — ориентир для понимания логики. Реальная схема собирается индивидуально.
Исследовать вопрос подробнее – вывод из запоя капельница
Вся динамика заносится в единую карту наблюдения, доступ к которой разграничен по ролям. При переходе к амбулаторной точке или стационару не происходит «перезапуска истории»: новые назначения учитывают всё, что сделано на старте.
Ознакомиться с деталями – помощь вывод из запоя в воронеже
Домашнее лечение не уступает стационару по стандартам безопасности, если соблюдены три условия: корректная стратификация риска, титрование инфузий через оборудование с точным шагом и регулярные «тихие» проверки без навязчивой аппаратной нагрузки. Наши мобильные бригады приезжают с портативным кардиомонитором, инфузоматом, пульсоксиметром и экспресс-анализаторами, а также набором одноразовых расходников. Кроме приборов, мы привозим «средовые» решения: тёплую лампу, светозащитные шторки, укладки для безопасной организации зоны процедуры — это помогает телу быстрее переключаться из тревоги в восстановление без лишних препаратов.
Ознакомиться с деталями – нарколог на дом петрозаводск
Если при телефонном триаже выявляются «красные флаги» (дыхание, ритм, сознание), маршрут настраивается сразу под стационар: те же цели, тот же ответственный куратор, только непрерывный мониторинг витальных и ночной пост. А когда риски невысоки, мы начинаем дома или амбулаторно и удерживаем темп контрольными включениями — это чаще всего даёт спокойную первую ночь и легче переносимый второй день.
Узнать больше – вывод из запоя ставрополь
Алгоритм на выезде помогает убрать импровизации, а семье — понимать, что будет происходить и по каким признакам мы двигаемся дальше. Он гибкий, но всегда прозрачный: каждый шаг имеет цель, инструмент и критерий успеха.
Детальнее – нарколог на дом недорого в ставрополе
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
ТОП-5 причин узнать больше – https://www.tabi-senka.com/slider1/?unapproved=378222
Петрозаводск задаёт свои параметры среды: озёрный ветер, световые перепады, «звонкие» подъезды старого фонда. В «РеМед Карелия» мы проектируем маршрут так, чтобы городской фон работал на пациента. Короткая регистрация без «толстых анкет», приглушённый тёплый свет в приёмной, отсутствие громких объявлений, отдельный вход без вывесок и немаркированный транспорт — всё это снижает сенсорную нагрузку и уменьшает вечернюю кардиореактивность. Семья получает «окна связи» в фиксированное время, чтобы эмоциональные звонки не разрушали «ночную кривую» сна. Для пациентов, стартующих на дому, мы привозим переносные решения — лампу тёплого спектра, ширмы, шумопоглощающие аксессуары, — чтобы не усиливать тревогу и не «подливать» раздражителей в момент инфузии.
Углубиться в тему – https://narkologicheskaya-klinika-v-petrozavodske15.ru/chastnaya-narkologicheskaya-klinika-petrozavodsk
«Волшебной капельницы» не существует. Мы структурируем инфузии от симптомов, а не от «средних рецептов». Ниже — логика подбора для типичных профилей; реальную схему определяет врач на месте.
Изучить вопрос глубже – вывод из запоя дешево в калининграде
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Изучить эмпирические данные – https://jardincasadecampo.com/nurturing-the-bond-between-humans-and-nature
«СтаврМедЦентр» собирает лечение из коротких модулей с понятными целями: быстро стабилизировать соматику, вернуть управляемый сон, снизить реактивность вечера, обучить «перехвату» импульса и закрепить это в спокойной рутине. Фармакологию используем дозированно, опираясь на витальные показатели и переносимость; поведенческий контур запускаем сразу: свет, вода, дыхание, цифровая гигиена, семейные договорённости. Ниже — ориентировочная архитектура маршрута. На практике последовательность и длительность настраиваются под конкретного человека и его среду.
Подробнее – наркологическая клиника клиника помощь ставрополь
Стартовый осмотр должен быть быстрым и осмысленным. Мы исключаем «обязательные» исследования, которые не меняют тактику, и оставляем то, что прямо влияет на состав инфузии, темп, место ведения (дом/амбулатория/стационар) и объём поведенческих рекомендаций. Решения принимаются на свежих цифрах и клинической картине «здесь и сейчас», а повторные замеры назначаются не «по привычке», а по смыслу. Это экономит силы пациента и время команды, а главное — уменьшает фармакологическую нагрузку без потери безопасности.
Разобраться лучше – http://narkologicheskaya-klinika-stavropol15.ru/chastnaya-narkologicheskaya-klinika-stavropol/
Домашнее лечение не уступает стационару по стандартам безопасности, если соблюдены три условия: корректная стратификация риска, титрование инфузий через оборудование с точным шагом и регулярные «тихие» проверки без навязчивой аппаратной нагрузки. Наши мобильные бригады приезжают с портативным кардиомонитором, инфузоматом, пульсоксиметром и экспресс-анализаторами, а также набором одноразовых расходников. Кроме приборов, мы привозим «средовые» решения: тёплую лампу, светозащитные шторки, укладки для безопасной организации зоны процедуры — это помогает телу быстрее переключаться из тревоги в восстановление без лишних препаратов.
Получить больше информации – нарколог на дом круглосуточно цены в петрозаводске
Городской ритм Петрозаводска с озёрным ветром, короткими сумерками и сезонной влажностью повышает сенсорную нагрузку в вечерние часы, поэтому наш маршрут спроектирован «мягко». Координатор заранее уточняет подъезд, парковку, код домофона, рекомендует «тихий режим» связи и присылает нейтральное уведомление о визите. Бригада приходит в гражданской одежде, сумки — без логотипов, разговоры — короткими фразами. Такое поведение снижает у пациента и семьи реактивность, выравнивает вариабельность ЧСС к сумеркам и уменьшает потребность «усиливать» схему на ночь. Если на предзвонке выявлены «красные флаги» — неукротимая рвота, выраженная дезориентация, «скачущий» ритм, одышка — мы предлагаем стационар сразу, чтобы не терять время на повторные маршруты.
Изучить вопрос глубже – выезд нарколога на дом петрозаводск
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Выяснить больше – https://narkologicheskaya-klinika-kaliningrad15.ru/kaliningrad-narkologicheskaya-bolnicza
Мы комбинируем медицинские и немедикаментозные решения. Инфузионная терапия — адресная, с контролем безопасности; поведенческие опоры — просты и выполняемы в реальной жизни; телемедицина помогает пройти «трудный час» без лишних поездок и импровизаций. Ниже — ориентиры логики подбора, они не заменяют очный осмотр.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-kaliningrad15.ru
Анонимность встроена в процесс: немаркированные выезды, гражданская одежда персонала, нейтральные формулировки в документах и «беззвучные» уведомления. Медицинская карта ведётся с разграничением доступа по ролям, а для связи с близкими предусмотрены «тихие окна». Конфиденциальность не декларируется — она реализована в каждом шаге, от первичного звонка до плановых контрольных точек.
Подробнее можно узнать тут – наркологическая клиника цены
В реальности Воронежа на самочувствие влияет не только фармакология, но и логистика: трассы с плотным трафиком, яркое освещение подъездов, очереди в медорганизациях. «ВоронежМедЦентр» гасит эти раздражители организационно: «тихие окна» приёма без коридорного шума, согласованная парковка, немаркированные выезды, нейтральные формулировки в документах и «беззвучные» напоминания. Снижение сенсорной нагрузки — это не декоративная опция, а клинический фактор: спокойная первая ночь, ровный пульс к вечеру, предсказуемость режима воды и тёплой пищи малыми порциями.
Выяснить больше – лечение в наркологической клинике
Если на триаже выявляются риски (дыхание, спутанность, нестабильный ритм), предлагаем короткое стационарное окно мониторинга. При низких рисках стартуем амбулаторно или на дому, а вечером подключаем короткие видеовставки по 15–20 минут. Переходы между форматами не «сбрасывают» процесс: единая карта наблюдения обеспечивает непрерывность и точность решений.
Выяснить больше – наркологическая клиника цены
Каждый метод «привязан» к решаемой задаче. Если динамика «плоская», мы не усиливаем всё сразу: корректируем один параметр (скорость инфузии, последовательность шагов, длительность вечерних вставок) и повторно оцениваем результат в оговорённое время. Такая бережная настройка снижает риск побочных эффектов и сохраняет ясность днём.
Разобраться лучше – https://narkologicheskaya-klinika-voronezh15.ru/chastnaya-narkologicheskaya-klinika-voronezh
Ниже — структурированная карта экстренного выезда. Она помогает пациенту и семье понимать, что происходит в каждый отрезок времени, какие цели мы преследуем и по каким критериям двигаемся дальше.
Подробнее тут – вывод из запоя на дому недорого в воронеже
Первые два часа после приезда врача — ключевое окно. Мы фиксируем витальные показатели (АД/ЧСС/SpO?), проводим экспресс-оценку глюкозы, по показаниям — электролитов (Na?/K?), оцениваем дыхательный паттерн и уровень ориентировки. Далее запускается титрованная инфузия через инфузомат с контролем каждые 15–20 минут. Параллельно настраиваются «вечерние опоры»: светогигиена, дыхательные циклы, «тихие окна» связи. В конце визита пациент и близкие получают простую памятку с «зелёными зонами» и кратким планом на 72 часа — когда пить воду, как выбирать тёплую пищу малыми порциями, при каких признаках выходить на связь немедленно.
Выяснить больше – вывод из запоя дешево
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Расширить кругозор по теме – https://omsteel.co/mastering-modern-manufacturing-cnc-shafts-and-vmc-components
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Детальнее – http://vyvod-iz-zapoya-v-kaliningrade15.ru/vyvod-iz-zapoya-kaliningrad-staczionar/https://vyvod-iz-zapoya-v-kaliningrade15.ru
В крупных и динамичных районах Ставрополя дорога сама по себе становится стрессором: непривычные запахи, чужие люди, ожидание в коридоре — всё это усиливает тремор, реактивность пульса и «ночной разгон» мыслей. Именно поэтому «СтаврМедЦентр» предлагает аккуратный выбор: если объективные риски низкие, мы начинаем дома или амбулаторно и переносим часть «тяжёлых» решений в первый вечер. Там проще включить светогигиену, отрегулировать шум, наладить воду и положить рядом тёплую лёгкую пищу. Когда среда управляемая, меньше соблазн «усилить» схему лишними препаратами, и организм быстрее выходит на коридоры безопасности.
Подробнее – запой наркологическая клиника
Клиника принимает 24/7 без очередей: ночной блок специально настроен под «трудные часы», когда усиливаются панические мысли и реактивность пульса. Для тех, кому легче дома, выездная служба приводит помощь в знакомое пространство; если нужны короткие контрольные включения, применяем видеосвязь вечером (15–20 минут), чтобы корректно настроить ритуалы засыпания, дыхательные циклы и «световые правила». Маршрут фиксируется в единой карте наблюдения — этот документ доступен команде по ролям и защищает от «повторов заново», когда формат меняется (дом – амбулатория – стационар).
Подробнее – http://narkologicheskaya-klinika-v-stavropole15.ru
В реальной городской ткани Ставрополя на самочувствие влияет не только схема лечения, но и логистика: утренние заторы на въезде, плотная застройка частного сектора, шумные перекрёстки. Мы заранее «поглощаем» эти риски организацией: секторные выезды, согласованная парковка, нейтральная переписка без «говорящих» терминов, при необходимости — курьерская доставка расходников отдельно от врача, чтобы на месте сразу переходить к оценке и запуску инфузии. Пациенту не нужно «вписываться» в систему — система подстраивается под реальную жизнь человека, экономя десятки минут и снижая сенсорную нагрузку перед первой ночью.
Узнать больше – наркологическая клиника цены в ставрополе
В городском ритме Ставрополя дорога сама по себе может усугублять симптомы: плотный трафик, резкие звуки, длинные коридоры ожидания. Поэтому «СтаврВита» разворачивает секторные выезды: немаркированный транспорт, гражданская одежда специалистов, согласованная парковка и подъезд, доставка расходников отдельно от врача при необходимости — чтобы на месте сразу переходить к диагностике и запуску инфузии. Переписка ведётся нейтральными формулировками, уведомления «беззвучные», документы без стигматизирующих слов. По желанию всё общение идёт через доверенное лицо: оно получает короткие апдейты в согласованные «окна», не перегружаясь клиническими деталями.
Углубиться в тему – срочный вывод из запоя
Вся динамика заносится в единую карту наблюдения. Если потребуются амбулаторные точки или стационар, вы не «начинаете историю заново» — маршрут продолжится с той же целью и теми же критериями успеха.
Узнать больше – вызвать врача нарколога на дом ставрополь
Карта делает решения прозрачными: если критерий не достигнут, меняется ровно один параметр с назначением новой точки контроля. Это сохраняет причинно-следственную связь и уменьшает общую фармаконагрузку без компромиссов по безопасности.
Разобраться лучше – вызвать врача нарколога на дом в петрозаводске
Вся динамика фиксируется в единой карте наблюдения. При переводе в амбулаторную точку мы не «сбрасываем» историю: решения продолжаются с учётом уже сделанного и реакции пациента на вмешательства.
Узнать больше – http://www.domen.ru
Городская среда Воронежа — яркие подъезды, плотный трафик, шумные дворы — усиливает вечернюю реактивность. Поэтому выездная служба «ВоронежВита» организована «тихо»: согласованная парковка, быстрый подъем без опознавательных знаков, часть расходников доставляется заранее, чтобы на адресе сразу перейти к диагностике и инфузии. Коммуникация ведётся через защищённые каналы, уведомления — «беззвучные», названия в документах — нейтральные. Такой дизайн среды не декоративен: чем меньше «социального шума», тем устойчивее ночной сон и тем быстрее возвращается переносимость воды и лёгкой еды.
Получить дополнительную информацию – вывод из запоя на дому воронеж
Если на телефонном этапе звучат «красные флаги» — одышка, спутанность, «скачущий» ритм, повторная рвота — мы предлагаем короткое окно интенсивного наблюдения. При низких рисках стартуем амбулаторно или с выезда на дом, а вечером используем короткие видеовставки по 15–20 минут, чтобы пройти «трудный час» без импровизаций.
Ознакомиться с деталями – наркологические клиники алкоголизм в калининграде
В «Центр Трезвости Воронеж» приватность не обсуждается — она проектируется. Выбор нейтральных формулировок в чеках, немаркированные выезды, «беззвучные» уведомления, отдельные входы и доступ к карте наблюдения только по ролям — это норма, а не «услуга». Пациент может назначить доверенное лицо, чтобы получать краткие апдейты в согласованные временные окна.
Разобраться лучше – http://narkologicheskaya-klinika-v-voronezhe15.ru/
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Подробнее можно узнать тут – https://dvp.lt/vsi-darnaus-vystymo-projektai-pradeda-igyvendinti-valstybinio-visuomenes-sveikatos-stiprinimo-fondo-2016-metu-lesomis-finansuojama-projekta-sveikas-gyvenimas-blaiv
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Не упусти шанс – http://deevarispa.de/top-10-locations-to-go-to-for-a-summer-retreat
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Всё, что нужно знать – https://listing.downtown-directory.com/rtl-version/product/%D8%B1%D9%85%D8%A7%D8%AF%D9%8A-%D8%AA%D9%8A-%D8%B4%D9%8A%D8%B1%D8%AA-%D8%A3%D8%B2%D9%8A%D8%A7%D8%A1-sportex-%D8%A7%D9%84%D8%B5%D9%8A%D9%81-%D8%A3%D8%B1%D9%8A%D9%81%D8%A7%D9%84
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Слушай внимательно — тут важно – https://international-mindfulness-institute.com/nos-actions-trois-expertises-complementaires/actions-imi-infographie
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Где можно узнать подробнее? – https://solvatherapy.com/en/professional-courses/faqs
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Читать дальше – https://alazanes.net/agricultores-manda-la-final-de-la-elite-a-un-septimo-juego
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Нажмите, чтобы узнать больше – https://somsokun.com/hello-world
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Подробнее – https://loxionhub.com/a-reece-heading-to-sway-in-2019
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Подробнее – https://ijin10.com/emile-durkheim
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Посмотреть подробности – https://www.coboplus.com/17031720-cosmoprof-2017
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Что ещё? Расскажи всё! – https://livingpriceless.com/index.php/2022/11/22/hello-world
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Погрузиться в детали – https://joinkite.org/kite-back-to-school-hacks-with-50-prizes
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Изучить эмпирические данные – https://sb-construction.dk/cases/hawkeyepedershaab/img_proj_hawkeye_01-300×280
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Нажмите, чтобы узнать больше – https://www.ochicochiya.com/%E5%86%99%E7%9C%9F-2024-08-11-%E5%A4%8F%E5%AD%A3%E4%BC%91%E6%A5%AD%E3%81%8A%E7%9F%A5%E3%82%89%E3%81%9B
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Кликни и узнай всё! – https://thegolfperformancecenter.com/5-elements-blog/grip-it-and-rip-it
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Обратиться к источнику – https://millesimeworld.com/blog/gourmet/los-grandes-blancos-franceses
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Узнать из первых рук – https://ventanillatv.pe/pedro-castillo-vs-keiko-fujimori-segunda-parte-2
В кардиологической и психологической поддержке «Частного Медика 24» в Самаре — полный комплекс для безопасного восстановления после запоя.
Разобраться лучше – стационар вывод из запоя
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Получить дополнительные сведения – вывод из запоя цена нижний новгород
Не знаете, какой вариант лечения алкоголизма выбрать — стационар, кодирование или детокс? Подробный разбор и советы по выбору — на Delodom.com. Узнать больше – http://www.kostromag.ru/forum/main/18142.aspx
В стационаре пациент получает и физиологическую помощь, и психологическое сопровождение, что важно для долгосрочного восстановления.
Изучить вопрос глубже – https://vyvod-iz-zapoya-v-stacionare-samara25.ru
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Детальнее – вывод из запоя дешево нижний новгород
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Получить больше информации – наркологический вывод из запоя нижний новгород
Алкогольная зависимость требует правильного подхода. В новом материале Blogimam рассказывается о доступных методах кодирования в Саратове: от медикаментозных до психологических программ. Узнать больше – http://www.artlib.ru/index.php?id=26&idr=21&idt=52033
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Изучить вопрос глубже – вывод из запоя вызов
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Получить больше информации – https://thekingofmeat.net/meat-and-poultry-recipes
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Это ещё не всё… – https://eitanmaakot.co.il/blog/how-to-fit-the-railing-to-the-home-space
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Смотрите также… – https://hewagelaw.com/2019/03/15/hello-world
«Частный Медик 24» в стационаре помогает начать жизнь заново — с чистого листа, без последствий запоя.
Получить дополнительную информацию – http://vyvod-iz-zapoya-v-stacionare23.ru
Пациентам в Самаре предлагается анонимное лечение в стационаре с круглосуточным уходом и безопасными условиями.
Получить дополнительную информацию – http://vyvod-iz-zapoya-v-stacionare-samara25.ru
В клинике «Частный Медик 24» пациенту гарантирована анонимность и внимательное отношение при лечении запоя.
Получить больше информации – нарколог вывод из запоя в стационаре в нижний новгороде
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Детальнее – http://vyvod-iz-zapoya-nizhnij-novgorod12.ru
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Детали по клику – https://athathku.com/%D8%B4%D8%B1%D9%83%D8%A7%D8%AA-%D9%86%D9%82%D9%84-%D8%A7%D9%84%D8%A3%D8%AB%D8%A7%D8%AB-%D9%81%D9%8A-%D9%85%D8%B5%D8%B1
Домашнее кодирование алкогольной зависимости: полное руководство по процедуре, ожиданиям и рискам — читайте на NetLekarstvam.com. Подробнее – http://mymoscow.forum24.ru/?1-6-0-00033109-000-0-0-1757537846
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Углубиться в тему – вывод из запоя вызов на дом нижний новгород
Если домашние методы не помогают, вывод из запоя в стационаре в Самаре — это безопасный выбор с профессиональной детоксикацией.
Узнать больше – быстрый вывод из запоя в стационаре
Ищете надёжный способ обрести трезвость и вновь почувствовать контроль над жизнью? В статье «Эффективные методы кодирования от алкоголизма: пути к трезвой жизни» раскрываются различные подходы к кодированию — от медикаментозных до психологических и аппаратных. Вы узнаете, как подобрать метод, учитывая стадию зависимости, состояние здоровья и личные особенности, а также почему сочетание кодировки с терапией и окружением трезвости может обеспечить более устойчивый эффект. Полезно тем, кто ищет путь к здоровому и свободному от зависимости образу жизни.
Углубиться в тему – http://kremlevsk.kamrbb.ru/?x=read&razdel=5&tema=628
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Перейти к статье – https://nara-naramachi.com/img_8207
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Углубиться в тему – анонимный вывод из запоя
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Разобраться лучше – вывод из запоя дешево нижний новгород
В Самаре «Частный Медик 24» предлагает прозрачные цены на вывод из запоя, без неожиданных расходов.
Подробнее можно узнать тут – нарколог вывод из запоя в стационаре самара
Ищете понятный и последовательный план лечения алкогольной зависимости? Статья «Этапы лечения алкогольной зависимости» предлагает чётко структурированный путь к восстановлению: от первой помощи до реабилитации. Углубиться в тему – http://kremlevsk.kamrbb.ru/?x=read&razdel=5&tema=646
Стационарное лечение запоя в Воронеже — индивидуальный подход к каждому пациенту. Мы предлагаем комфортные условия и профессиональную помощь для быстрого и безопасного вывода из запоя.
Получить дополнительные сведения – https://vyvod-iz-zapoya-v-stacionare-voronezh23.ru
Круглосуточный стационарный вывод из запоя в Воронеже — доступная помощь в любое время. Вы можете обратиться к нам в любое время суток, и мы окажем необходимую медицинскую помощь.
Разобраться лучше – вывод из запоя в стационаре клиника в воронеже
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Информация доступна здесь – https://wafudalharam.com/2022/07/01/5-most-beautiful-islands-in-asia
В момент вызова важно сообщить:
Получить больше информации – https://narkologicheskaya-klinika-rostov13.ru/narkologicheskaya-klinika-v-rostove
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Разобраться лучше – скорая вывод из запоя сочи
В автомобиле находятся:
Подробнее тут – наркологическая клиника нарколог
В Сочи клиника «Детокс» предлагает полный курс вывода из запоя в стационаре. Круглосуточный медицинский контроль гарантирует безопасность и эффективность лечения.
Исследовать вопрос подробнее – http://www.vyvod-iz-zapoya-sochi24.ru
Если самостоятельные попытки выйти из запоя не даются, в стационаре «Частного Медика 24» в Воронеже оказывают помощь профессионально: круглосуточное наблюдение, дозированные капельницы, поддержка сердечно-сосудистой системы, нормализация сна и работы внутренних органов.
Получить дополнительные сведения – http://vyvod-iz-zapoya-v-stacionare-voronezh24.ru
Стационар «Частного Медика 24» — условия, где пациент может спокойно пройти вывод из запоя без страха и дискомфорта.
Узнать больше – быстрый вывод из запоя в стационаре
Выведение из запоя в стационаре Воронежа — помощь при острых состояниях и хронической зависимости. Наши опытные наркологи используют современные методы лечения для быстрого и безопасного вывода из запоя.
Выяснить больше – нарколог вывод из запоя в стационаре в воронеже
Исследуйте лучшие методы лечения алкоголизма: сравнение терапий, эффективность медикаментов и психологической помощи — всё на Натали-Dev. Узнайте, что подходит именно вам. Подробнее можно узнать тут – http://infoenglish.info/forum/14-9409-1
Круглосуточный стационарный вывод из запоя в Воронеже — доступная помощь в любое время. Вы можете обратиться к нам в любое время суток, и мы окажем необходимую медицинскую помощь.
Детальнее – стационар вывод из запоя воронеж
В Краснодаре клиника «Детокс» проводит выезд нарколога на дом для безопасного вывода из запоя.
Исследовать вопрос подробнее – нарколог на дом цены в краснодаре
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Изучить вопрос глубже – анонимный вывод из запоя
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Сочи предлагает вывод из запоя в стационаре. Под наблюдением опытных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – нарколог вывод из запоя
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Изучить вопрос глубже – нарколог на дом клиника в краснодаре
Если домашние методы не помогают, вывод из запоя в стационаре в Самаре — это безопасный выбор с профессиональной детоксикацией.
Разобраться лучше – стационар вывод из запоя в самаре
Наркомания — это хроническое заболевание, которое разрушает физическое и психическое здоровье, разрывает социальные связи и лишает человека способности контролировать свою жизнь. Однако современная медицина предлагает эффективные методы борьбы с зависимостями, включая комплексное лечение в специализированных центрах. Детальнее – http://www.kpilib.ru/forum.php?tema=12652
В Сочи клиника «Детокс» проводит вывод из запоя в стационаре с круглосуточным контролем врачей. Процедуры безопасны, эффективны и анонимны.
Разобраться лучше – помощь вывод из запоя
В автомобиле находятся:
Разобраться лучше – http://narkologicheskaya-klinika-rostov13.ru/narkologicheskaya-klinika-narkologicheskij-czentr-v-rostove/
В Краснодаре клиника «Детокс» предлагает выезд нарколога на дом. Помощь оказывается быстро, анонимно и круглосуточно.
Получить дополнительную информацию – нарколог капельница на дом краснодар
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Получить больше информации – вывод из запоя цена сочи
В Нижнем Новгороде стационар «Частного Медика 24» стал надежным местом для лечения запоя.
Подробнее можно узнать тут – http://www.vyvod-iz-zapoya-v-stacionare23.ru
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Ознакомиться с деталями – вывод из запоя капельница на дому нижний новгород
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Подробнее – вывод из запоя клиника
Если пациент не может приехать в клинику, в Краснодаре нарколог приедет к нему домой. Помощь оказывает «Детокс» круглосуточно.
Разобраться лучше – нарколог капельница на дом
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Подробнее можно узнать тут – вывод из запоя в сочи
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Разобраться лучше – врач вывод из запоя нижний новгород
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Получить больше информации – вывод из запоя вызов в сочи
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Подробнее – нарколог на дом клиника краснодар
В Краснодаре клиника «Детокс» предлагает выезд нарколога на дом. Помощь оказывается быстро, анонимно и круглосуточно.
Получить дополнительные сведения – нарколог на дом вывод из запоя краснодар
Если вы ищете надёжный и понятный путь к избавлению от алкогольной зависимости — вам стоит заглянуть в статью «Эффективные услуги лечения алкоголизма: путь к трезвой жизни». Ознакомиться с деталями – http://kremlevsk.kamrbb.ru/?x=read&razdel=5&tema=637
В клинике в Самаре устраняют симптомы интоксикации, оказывают поддержку организму и помогают восстановиться после тяжёлых запоев.
Детальнее – стационар вывод из запоя
Выездная бригада «РостовМед» оснащена всем необходимым для оказания экстренной помощи и проведения полного курса детоксикации на дому. Процесс состоит из нескольких этапов:
Получить больше информации – http://
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Получить дополнительную информацию – нарколог на дом цены
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Подробнее тут – вывод из запоя на дому круглосуточно в нижний новгороде
Выездная бригада «РостовМед» оснащена всем необходимым для оказания экстренной помощи и проведения полного курса детоксикации на дому. Процесс состоит из нескольких этапов:
Разобраться лучше – http://narkologicheskaya-klinika-rostov13.ru/narkologicheskaya-klinika-v-rostove/
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить дополнительную информацию – вывод из запоя на дому круглосуточно
В Сочи клиника «Детокс» предлагает полный курс вывода из запоя в стационаре. Круглосуточный медицинский контроль гарантирует безопасность и эффективность лечения.
Подробнее тут – помощь вывод из запоя сочи
Круглосуточный стационарный вывод из запоя в Воронеже — доступная помощь в любое время. Вы можете обратиться к нам в любое время суток, и мы окажем необходимую медицинскую помощь.
Получить дополнительную информацию – нарколог вывод из запоя в стационаре воронеж
Программа вывода из запоя в Воронеже от «Частного Медика 24» включает не только устранение физической зависимости, но и работу по восстановлению сна, гидратацию, лекарственную поддержку, а также психотерапию, чтобы помочь справиться не просто с запоем, но и с причинами, которые к нему привели.
Получить дополнительную информацию – быстрый вывод из запоя в стационаре
В Краснодаре клиника «Детокс» предлагает выезд нарколога на дом. Помощь оказывается быстро, анонимно и круглосуточно.
Получить дополнительную информацию – вызвать врача нарколога на дом краснодар
Стационар клиники — это безопасное место, где врачи помогают восстановить силы после тяжелого запоя.
Узнать больше – vyvod-iz-zapoya-v-stacionare23.ru/
Вызов нарколога на дом в Краснодаре доступен в любое время суток. Клиника «Детокс» гарантирует профессиональную помощь.
Подробнее можно узнать тут – врач нарколог на дом краснодар
Выведение из запоя в стационаре Воронежа — помощь при острых состояниях и хронической зависимости. Наши опытные наркологи используют современные методы лечения для быстрого и безопасного вывода из запоя.
Узнать больше – вывод из запоя в стационаре анонимно воронеж
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Разобраться лучше – нарколог на дом вывод из запоя
В Краснодаре нарколог из клиники «Детокс» приедет на дом, чтобы вывести из запоя и оказать необходимую помощь.
Подробнее тут – частный нарколог на дом
«Частный Медик 24» — это медицинский контроль, поддержка и лечение на всех этапах вывода из запоя.
Выяснить больше – вывод из запоя в стационаре клиника нижний новгород
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Узнать больше – наркологический вывод из запоя сочи
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Узнать больше – [url=https://vyvod-iz-zapoya-sochi23.ru/]анонимный вывод из запоя сочи[/url]
В автомобиле находятся:
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-rostov13.ru/chastnaya-narkologicheskaya-klinika-v-rostove
Клиника «Развитие» в Саратове — ваш путь к здоровой жизни без зависимости. Профессиональная помощь при алкоголизме, наркомании и игромании. Подробности на сайте. Изучить вопрос глубже – http://www.artlib.ru/index.php?id=26&idr=24&idt=52010
Если вы или ваши близкие столкнулись с необходимостью безопасного выхода из запоя, статья «Методы, особенности и важные нюансы выведения из запоя» станет знакомым и надёжным ориентиром. В ней объясняются современные подходы к прерыванию запоя — с акцентом на безопасность и постепенную реконструкцию организма. Получить дополнительные сведения – http://web-lance.net/forums.php?m=posts&q=37957&n=last
Если пациент не может приехать в клинику, в Краснодаре нарколог приедет к нему домой. Помощь оказывает «Детокс» круглосуточно.
Получить больше информации – вызвать нарколога на дом срочно краснодар
В клинике в Самаре устраняют симптомы интоксикации, оказывают поддержку организму и помогают восстановиться после тяжёлых запоев.
Разобраться лучше – стационар вывод из запоя в самаре
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Получить больше информации – скорая вывод из запоя нижний новгород
Госпитализация в стационар помогает быстрее и надежнее справиться с последствиями запоя.
Узнать больше – http://vyvod-iz-zapoya-v-stacionare23.ru
Экстренная помощь при запое в Нижнем Новгороде — капельница на дому от опытных врачей-наркологов.
Узнать больше – вывод из запоя цена
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Узнать больше – нарколог вывод из запоя в сочи
Выездная бригада «РостовМед» оснащена всем необходимым для оказания экстренной помощи и проведения полного курса детоксикации на дому. Процесс состоит из нескольких этапов:
Подробнее можно узнать тут – http://narkologicheskaya-klinika-rostov13.ru/narkologicheskaya-klinika-v-rostove/
Ищете современный и надёжный подход к лечению алкогольной зависимости в Саратове? Тогда вам стоит обратиться к статье «Клиника ТорпедоМед: современный ориентир в лечении алкогольной зависимости в Саратове». В ней рассказывается о том, как эта клиника стремится предложить комплексные решения, учитывающие биологические, психологические и социальные аспекты зависимости — то есть применять целостный биопсихосоциальный подход Углубиться в тему – http://kremlevsk.kamrbb.ru/?x=read&razdel=5&tema=643
В кардиологической и психологической поддержке «Частного Медика 24» в Самаре — полный комплекс для безопасного восстановления после запоя.
Подробнее тут – нарколог вывод из запоя в стационаре
Комплексный подход к лечению зависимостей в Саратове: эффективные методы, опытные специалисты и индивидуальный план восстановления. Читайте статью на Womanzdorovie. Разобраться лучше – http://www.kostromag.ru/forum/main/18148.aspx
В больничных условиях «Частного Медика 24» врачи контролируют давление, сердце и функции жизненно важных органов при выводе из запоя.
Детальнее – быстрый вывод из запоя в стационаре
Советы по выбору обоев Неймара: матчи, портреты, training — что лучше для экрана смартфона? Интересует «неймар рост вес возраст» по годам — удобнее видеть в одной инфографике. Активно обновляю коллекцию заставок для телефона, ищу чистые 4K. [url=www.neymar-kg.com]www.neymar-kg.com[/url]. Ищу «неймар красивые фото 2024» в стиле editorial — подскажите, какие фотосеты топ.
Ищу «неймар барселона фото» с классическими комбинациями с Суаресом и Месси. Нужны «обои на телефон футбол Неймар» в вертикальном формате 1080×2400. Сравнение прайма Неймара в «Барселоне» и пик-сезонов в ПСЖ — таблица метрик. Месси Роналду Неймар Мбаппе — хочу динамичный коллаж для заставки.
Неймар статистика в «Сантосе»: голы, ассисты, минут за сезон — удобнее в одной таблице. Неймар 2018 ПСЖ — сравнение с 2017 Барса: влияние на xThreat и прогрессии мяча.
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Подробнее – вывод из запоя капельница на дому
Вывод из запоя в клинике «Частный Медик 24» в Воронеже проводится по стандартной и премиум-программе, цена от 6500 ?, где важнейший акцент — на здоровье пациента: предотвращение осложнений, восстановление баланса жидкости и электролитов, поддержка психологического состояния.
Детальнее – вывод из запоя в стационаре
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – вывод из запоя цена сочи
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Подробнее можно узнать тут – https://narkolog-na-dom-krasnodar29.ru
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Подробнее можно узнать тут – vyvod-iz-zapoya-nizhnij-novgorod13.ru/
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Ознакомиться с деталями – вывод из запоя с выездом нижний новгород
В момент вызова важно сообщить:
Разобраться лучше – наркологическая клиника наркологический центр в ростове-на-дону
Ищете современный и надёжный подход к лечению алкогольной зависимости в Саратове? Тогда вам стоит обратиться к статье «Клиника ТорпедоМед: современный ориентир в лечении алкогольной зависимости в Саратове». В ней рассказывается о том, как эта клиника стремится предложить комплексные решения, учитывающие биологические, психологические и социальные аспекты зависимости — то есть применять целостный биопсихосоциальный подход Получить дополнительную информацию – http://kremlevsk.kamrbb.ru/?x=read&razdel=5&tema=643
Если домашние методы не помогают, вывод из запоя в стационаре в Самаре — это безопасный выбор с профессиональной детоксикацией.
Изучить вопрос глубже – https://vyvod-iz-zapoya-v-stacionare-samara24.ru
В кардиологической и психологической поддержке «Частного Медика 24» в Самаре — полный комплекс для безопасного восстановления после запоя.
Углубиться в тему – стационар вывод из запоя в самаре
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Подробнее – вывод из запоя на дому недорого сочи
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Разобраться лучше – вывод из запоя круглосуточно в нижний новгороде
Выведение из запоя в стационаре Воронежа — помощь при острых состояниях и хронической зависимости. Наши опытные наркологи используют современные методы лечения для быстрого и безопасного вывода из запоя.
Получить дополнительную информацию – быстрый вывод из запоя в стационаре в воронеже
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Исследовать вопрос подробнее – вывод из запоя в стационаре
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Подробнее – вывод из запоя
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Подробнее тут – психиатр нарколог на дом в краснодаре
Вывод из запоя в Воронеже проходит анонимно, с круглосуточной поддержкой специалистов.
Ознакомиться с деталями – https://vyvod-iz-zapoya-v-stacionare-voronezh24.ru
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Подробнее – вывод из запоя вызов в нижний новгороде
Вызов нарколога на дом в Краснодаре — услуга клиники «Детокс». Специалисты оказывают квалифицированную помощь прямо у вас дома.
Исследовать вопрос подробнее – вызов врача нарколога на дом в краснодаре
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Выяснить больше – скорая вывод из запоя
Нужна помощь нарколога, но нет возможности ехать в клинику? Решение есть — выезд нарколога на дом. В статье по ссылке рассказывается, в каких случаях можно вызвать специалиста домой, какие услуги он оказывает и как это может помочь начать путь к трезвости без лишнего стресса. Удобно, анонимно и с заботой о здоровье.
Подробнее можно узнать тут – http://www.brokersearch.ru/index.php?option=com_kunena&func=view&catid=7&id=85154
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Узнать больше – вывод из запоя с выездом
В Самаре в «Частном Медике 24» пациент получает детоксикацию, восстановительное лечение и круглосуточное наблюдение врачей.
Ознакомиться с деталями – нарколог вывод из запоя в стационаре в самаре
В Сочи клиника «Детокс» проводит вывод из запоя в стационаре с круглосуточным контролем врачей. Процедуры безопасны, эффективны и анонимны.
Получить больше информации – http://vyvod-iz-zapoya-sochi24.ru
Выездная бригада «РостовМед» оснащена всем необходимым для оказания экстренной помощи и проведения полного курса детоксикации на дому. Процесс состоит из нескольких этапов:
Углубиться в тему – https://narkologicheskaya-klinika-rostov13.ru/narkologicheskaya-klinika-v-rostove/
Если запой стал серьёзной проблемой, стационар клиники «Детокс» в Сочи поможет выйти из кризиса. Врачи проводят детоксикацию и наблюдают за состоянием пациента.
Получить дополнительную информацию – вывод из запоя на дому круглосуточно
Ищете надёжный и подходящий метод кодирования от алкоголизма, особенно если хотите пройти лечение дома или в комфортной обстановке? Статья «Кодирование от алкоголизма: верный путь к трезвой жизни» предлагает обзор современных методов, адаптированных для домашнего применения. Исследовать вопрос подробнее – http://kremlevsk.kamrbb.ru/?x=read&razdel=5&tema=644
Ищете способ выйти из запоя и ступить на путь к новой, здоровой жизни? Тогда вам стоит ознакомиться с материалом «Вывод из запоя — путь к здоровой жизни». В нём раскрываются ключевые этапы и нюансы выхода из тяжелого алкогольного состояния. Выяснить больше – http://kremlevsk.kamrbb.ru/?x=read&razdel=5&tema=636
Программы вывода из запоя в Самаре включают детоксикацию, медикаментозную поддержку и работу с психотерапевтом.
Подробнее тут – быстрый вывод из запоя в стационаре самара
Торпедомед — надёжный ориентир в борьбе с алкогольной зависимостью: эффективные программы, поддержка семьи, забота о здоровье. Подробнее читайте на LadyCaramelka.ru Выяснить больше – http://mymoscow.forum24.ru/?1-6-0-00032985-000-0-0-1757223485
Вывод из запоя в Самаре на базе стационара — когда важен результат, стабильность и медицинская поддержка 24/7.
Выяснить больше – вывод из запоя в стационаре клиника
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Подробнее – вывод из запоя на дому нижний новгород
Круглосуточный стационарный вывод из запоя в Воронеже — доступная помощь в любое время. Вы можете обратиться к нам в любое время суток, и мы окажем необходимую медицинскую помощь.
Детальнее – нарколог вывод из запоя в стационаре
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Получить больше информации – вывод из запоя цена
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Узнать больше – вывод из запоя на дому круглосуточно в нижний новгороде
Вывод из запоя в стационаре Воронежа — эффективное решение для длительного запоя. Мы обеспечиваем круглосуточное наблюдение и комплексное лечение, включая детоксикацию, восстановление водно-электролитного баланса и психотерапевтическую поддержку.
Подробнее – стационар вывод из запоя воронеж
В Краснодаре нарколог из клиники «Детокс» приедет на дом, чтобы вывести из запоя и оказать необходимую помощь.
Исследовать вопрос подробнее – нарколог на дом клиника
Подготовительные курсы к ЕГЭ https://courses-ege.ru
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить дополнительные сведения – вывод из запоя недорого в сочи
В момент вызова важно сообщить:
Разобраться лучше – https://narkologicheskaya-klinika-rostov13.ru/chastnaya-narkologicheskaya-klinika-v-rostove
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Получить больше информации – помощь вывод из запоя нижний новгород
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Получить дополнительную информацию – вывод из запоя цена сочи
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Разобраться лучше – вывод из запоя капельница на дому
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Получить дополнительные сведения – помощь вывод из запоя в сочи
Адекватное лечение, комфорт и забота — так проходят дни в стационаре «Частного Медика 24» во время вывода из запоя.
Углубиться в тему – вывод из запоя в стационаре клиника
Вывод из запоя — первый шаг к новой жизни. Узнайте, как безопасно пройти детоксикацию и вернуть здоровье — читайте на dettka.com/vyvod-iz-zapoya-put-k-zdorovoj-zhizni Узнать больше – http://mymoscow.forum24.ru/?1-3-0-00000684-000-0-0-1757530732
Выездная бригада «РостовМед» оснащена всем необходимым для оказания экстренной помощи и проведения полного курса детоксикации на дому. Процесс состоит из нескольких этапов:
Получить больше информации – https://narkologicheskaya-klinika-rostov13.ru/psikhiatricheskaya-narkologicheskaya-klinika-v-rostove/
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Исследовать вопрос подробнее – анонимный вывод из запоя
Выезд нарколога на дом в Нижнем Новгороде — круглосуточная помощь при запое. Мы гарантируем анонимность и конфиденциальность на всех этапах лечения.
Получить больше информации – вывод из запоя
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Выяснить больше – вызвать врача нарколога на дом в краснодаре
football africain football africain
Лечение алкоголизма в Саратове: полный путеводитель с пояснениями по стадиям, методам и ценам — всё собрали в статье на Delodom.com. Выяснить больше – http://volcodav.borda.ru/?1-13-0-00000078-000-0-0-1757530543
Клиника «Частный Медик 24» в Самаре оказывает помощь при запое анонимно, круглосуточно и без скрытых платежей.
Подробнее – стационар вывод из запоя
Ищете помощь при зависимости — для себя или близкого? Статья «Наркологическая клиника и её услуги» раскрывает, как специализированные учреждения помогают людям справиться с зависимостью — будь то алкоголизм или другие формы. Детальнее – http://kremlevsk.kamrbb.ru/?x=read&razdel=9&tema=1101
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Углубиться в тему – [url=https://vyvod-iz-zapoya-nizhnij-novgorod12.ru/]вывод из запоя недорого[/url]
В Самаре в «Частном Медике 24» пациент получает детоксикацию, восстановительное лечение и круглосуточное наблюдение врачей.
Детальнее – стационар вывод из запоя в самаре
В Самаре «Частный Медик 24» предлагает прозрачные цены на вывод из запоя, без неожиданных расходов.
Выяснить больше – наркология вывод из запоя в стационаре
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Изучить вопрос глубже – вывод из запоя вызов в нижний новгороде
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Ознакомиться с деталями – вывод из запоя на дому круглосуточно в нижний новгороде
Стационарное лечение запоя в Воронеже — индивидуальный подход к каждому пациенту. Мы предлагаем комфортные условия и профессиональную помощь для быстрого и безопасного вывода из запоя.
Изучить вопрос глубже – вывод из запоя в стационаре воронеж
Если самостоятельные попытки выйти из запоя не даются, в стационаре «Частного Медика 24» в Воронеже оказывают помощь профессионально: круглосуточное наблюдение, дозированные капельницы, поддержка сердечно-сосудистой системы, нормализация сна и работы внутренних органов.
Выяснить больше – стационар вывод из запоя в воронеже
Экстренная помощь при запое в Нижнем Новгороде — капельница на дому от опытных врачей-наркологов.
Ознакомиться с деталями – вывод из запоя на дому недорого
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Ознакомиться с деталями – вывод из запоя цена в сочи
Нарколог прибывает в назначенное время, проводит замеры артериального давления, пульса, сатурации кислорода и температуры. Выполняется экспресс-анализ на содержание алкоголя в крови и оценка водно-электролитного баланса.
Углубиться в тему – наркологическая клиника вывод из запоя в ростове-на-дону
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Выяснить больше – нарколог на дом вывод из запоя сочи
В момент вызова важно сообщить:
Подробнее – https://narkologicheskaya-klinika-rostov13.ru/psikhiatricheskaya-narkologicheskaya-klinika-v-rostove
Вывод из запоя — это не просто прекращение питья, а полноценная медицинская процедура, направленная на очищение организма и стабилизацию психического состояния. Подробности на WomanClub. Узнать больше – http://www.kpilib.ru/forum.php?tema=12654
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Углубиться в тему – вывод из запоя с выездом
В больничных условиях «Частного Медика 24» врачи контролируют давление, сердце и функции жизненно важных органов при выводе из запоя.
Изучить вопрос глубже – вывод из запоя в стационаре
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – вывод из запоя клиника сочи
В автомобиле находятся:
Детальнее – наркологическая клиника вывод из запоя
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Получить больше информации – вывод из запоя недорого
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Изучить вопрос глубже – вывод из запоя недорого
Выездная бригада «РостовМед» оснащена всем необходимым для оказания экстренной помощи и проведения полного курса детоксикации на дому. Процесс состоит из нескольких этапов:
Получить дополнительные сведения – http://narkologicheskaya-klinika-rostov13.ru/chastnaya-narkologicheskaya-klinika-v-rostove/
Наркологическая помощь в Саратове 24/7 — быстрый выезд врача, помощь при запое и зависимостях, лечение анонимно. Подробнее на Damki.biz Подробнее – http://adalat.borda.ru/?1-4-0-00000513-000-0-0-1756815530
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Разобраться лучше – нарколог на дом вывод из запоя в сочи
В Самаре клиника «Частный Медик 24» предлагает вывод из запоя в стационаре с полным медицинским контролем и комфортными палатами.
Исследовать вопрос подробнее – вывод из запоя в стационаре в самаре
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Узнать больше – http://www.vyvod-iz-zapoya-nizhnij-novgorod12.ru
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Погрузиться в детали – https://skydigital.co.za/2017/05/02/post-with-couple-photos-inside
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
ТОП-5 причин узнать больше – https://nebesht.com/archive/nahid-mehrgans-novel-review-a-hakimi
Этот информационный материал подробно освещает проблему наркозависимости, ее причины и последствия. Мы предлагаем информацию о методах лечения, профилактики и поддерживающих программах. Цель статьи — повысить осведомленность и продвигать идеи о необходимости борьбы с зависимостями.
Углубиться в тему – https://zdorovieinform.ru/kodirovanie-ot-alkogolizma-sovremennye-metody-i-osobennosti-vybora-v-jelektrostali
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Узнать больше – https://maisgazeta.com/papa-francisco-nomeia-dom-jose-carlos-como-novo-arcebispo-de-montes-claros
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Где можно узнать подробнее? – https://eye-d.in/eye-d-heroes/divya.html
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Прочитать подробнее – https://prosynergyworldwide.com/benign-prostagic-hyperplasia-and-libido
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Слушай внимательно — тут важно – https://ochivo.com/tunidos-en-la-ria
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Жми сюда — получишь ответ – https://sonerdly.com/wells-fargo-may-face-new-sanctions-over-mortgage-practices
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Не упусти шанс – https://camtelkiosk.com/index.php/2021/12/24/vos-recharges
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Читать далее > – https://pqoil.com/innovative-products-and-services
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Ознакомьтесь поближе – https://kivureporter.net/journee-mondiale-de-la-liberte-de-la-presse-katembo-ndalieni-julien-salue-le-travail-de-journalistes
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Где почитать поподробнее? – https://namiracontroledepragas.com.br/ola-mundo
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Запросить дополнительные данные – https://beautywellnesstalk.com/how-to-lose-face-fat-5-most-effective-tips
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Узнать из первых рук – https://rpsicologia.com/2025/03/09/entendiendo-el-duelo-y-perdida
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Хочешь знать всё? – http://www.marianhubler.com/other-writing
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Узнать больше – наркология вывод из запоя
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Детальнее – вывод из запоя в стационаре нижний новгород
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Ознакомиться с деталями – https://www.heavenlycitychurch.org/2016/03/sunday-morning-worship
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Открой скрытое – https://rotifunk.org/elementor-3043/img-20221208-wa0003
Выезд нарколога на дом в Нижнем Новгороде — круглосуточная помощь при запое. Мы гарантируем анонимность и конфиденциальность на всех этапах лечения.
Подробнее тут – https://vyvod-iz-zapoya-nizhnij-novgorod11.ru
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Ознакомиться с деталями – наркологический вывод из запоя в нижний новгороде
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Продолжить чтение – https://befair2.org/2021/01/27/hello-world
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Как достичь результата? – https://chikakimisato.com/archives/992
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Это стоит прочитать полностью – https://batchleap.com/content-development
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Познакомиться с результатами исследований – https://ayahuk.com/product/ayah-car-diffuser
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Получить полную информацию – https://vgrgardens.com/plant-gifts-for-special-occasions
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Всё, что нужно знать – https://teachersguide.net/the-role-and-responsibilities-of-a-section-head-in-school
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Это стоит прочитать полностью – https://dienmaydangduong.com/lorem-ipsum-chi-don-gian-la-mot-doan-van-ban-gia-7
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Прочесть всё о… – https://www.eldacatra.com/doctor/evaluationSummary/%D8%AF%D9%83%D8%AA%D9%88%D8%B1-%D8%B9%D9%85%D8%B1%D9%88-%D8%B9%D8%A7%D8%AF%D9%84-%D9%85%D9%86%D8%B3%D9%89-%D9%86%D8%B3%D8%A7%D8%A1-%D9%88-%D8%AA%D9%88%D9%84%D9%8A%D8%AF
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Читать далее > – https://sekolahnews.com/sobat-osis-bikin-kegiatan-kece-kuys
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Узнайте всю правду – https://centresocialauterive.fr/espace-jeunes-regles-de-vie
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Смотрите также – https://www.edcemorto.com.mx/home03
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Подробнее – https://stainlessad.com/Blog/stainless-steel-toilets
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Подробнее – https://akornas.ac.id/mayjen-tni-purn-tono-suratman
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Открыть полностью – https://lyricalrelics.site/2023/01/typewriter-torment
Программы вывода из запоя в Самаре включают детоксикацию, медикаментозную поддержку и работу с психотерапевтом.
Детальнее – вывод из запоя в стационаре самара
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Получить дополнительные сведения – вывод из запоя
Стационарная детоксикация от алкоголя в Воронеже — восстановление организма под наблюдением специалистов. Мы проводим процедуры очищения организма от токсинов, восстанавливая физическое и психоэмоциональное состояние пациента.
Углубиться в тему – быстрый вывод из запоя в стационаре воронеж
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить больше информации – вывод из запоя в стационаре нижний новгород
В Самаре стационар «Частного Медика 24» предлагает персонализированный подход — лечение запоя, детоксикация и дальнейшее восстановление под наблюдением специалистов.
Разобраться лучше – наркология вывод из запоя в стационаре в самаре
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Подробнее тут – вывод из запоя круглосуточно нижний новгород
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Подробнее – помощь вывод из запоя
Воронежская клиника «Частный Медик 24» предлагает стационарное лечение запоя, где каждый этап — диагностика, детоксикация, терапия и реабилитация — продуман с учётом состояния пациента. Врачи применяют сертифицированные препараты и современные методы инфузионной терапии, чтобы облегчить состояние максимально быстро.
Разобраться лучше – наркология вывод из запоя в стационаре в воронеже
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Подробнее тут – http://vyvod-iz-zapoya-sochi22.ru
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Углубиться в тему – вывод из запоя с выездом
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Узнать больше – вывод из запоя сочи
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Углубиться в тему – вывод из запоя круглосуточно в сочи
Вызов нарколога на дом через «Stop-Alko» в Екатеринбурге — это помощь, когда вы не можете самостоятельно добраться до клиники. Первая помощь сразу у вас дома.
Подробнее – [url=https://vyvod-iz-zapoya-ekaterinburg26.ru/]врач вывод из запоя екатеринбург[/url]
Пациентам в Самаре предлагается анонимное лечение в стационаре с круглосуточным уходом и безопасными условиями.
Подробнее можно узнать тут – вывод из запоя в стационаре клиника самара
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Ознакомиться с деталями – http://vyvod-iz-zapoya-nizhnij-novgorod13.ru
Экстренная помощь при запое в Нижнем Новгороде — капельница на дому от опытных врачей-наркологов.
Узнать больше – анонимный вывод из запоя в нижний новгороде
В Екатеринбурге «Похмельная Служба» выезжает к пациенту домой и проводит детоксикацию прямо на месте.
Углубиться в тему – вывод из запоя дешево екатеринбург
В Воронеже клиника «Частный Медик 24» проводит вывод из запоя в стационаре с круглосуточным медицинским контролем.
Изучить вопрос глубже – вывод из запоя в стационаре клиника
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Сочи предлагает вывод из запоя в стационаре. Под наблюдением опытных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Выяснить больше – вывод из запоя дешево сочи
Вывод из запоя в стационаре Воронежа — безопасное и эффективное решение для длительного запоя. Наши специалисты обеспечат круглосуточное наблюдение и комплексное лечение, включая детоксикацию, восстановление водно-электролитного баланса и психотерапевтическую поддержку.
Выяснить больше – вывод из запоя в стационаре клиника воронеж
Если запой стал серьёзной проблемой, стационар клиники «Детокс» в Сочи поможет выйти из кризиса. Врачи проводят детоксикацию и наблюдают за состоянием пациента.
Углубиться в тему – вывод из запоя круглосуточно сочи
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Подробнее тут – вывод из запоя дешево нижний новгород
Стационарное лечение запоя в Воронеже — гарантированная анонимность и комфортные условия. Мы предлагаем индивидуальный подход к каждому пациенту, обеспечивая полное восстановление организма и предотвращение рецидивов.
Получить дополнительную информацию – нарколог вывод из запоя в стационаре в воронеже
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Узнать больше – вызвать врача нарколога на дом
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить дополнительные сведения – скорая вывод из запоя сочи
В Краснодаре нарколог из клиники «Детокс» приедет на дом, чтобы вывести из запоя и оказать необходимую помощь.
Получить дополнительную информацию – платный нарколог на дом краснодар
Когда нужна срочная помощь, служба Stop-Alko в Екатеринбурге может выехать на дом, провести диагностику, капельницу и восстановление сил.
Углубиться в тему – вывод из запоя капельница на дому
В стационаре «Частного Медика 24» в Воронеже организм очищается от токсинов под наблюдением врачей, проводится лабораторная и инструментальная диагностика, купируются симптомы интоксикации и восстанавливаются жизненно важные функции — всё это в условиях уюта и безопасности.
Подробнее – наркология вывод из запоя в стационаре
Когда нужна срочная помощь, служба Stop-Alko в Екатеринбурге может выехать на дом, провести диагностику, капельницу и восстановление сил.
Получить больше информации – вывод из запоя капельница екатеринбург
Пациентам в Самаре предлагается анонимное лечение в стационаре с круглосуточным уходом и безопасными условиями.
Углубиться в тему – стационар вывод из запоя
Пациентам в Самаре предлагается анонимное лечение в стационаре с круглосуточным уходом и безопасными условиями.
Получить больше информации – нарколог вывод из запоя в стационаре
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Разобраться лучше – вывод из запоя капельница на дому сочи
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Получить больше информации – врач вывод из запоя нижний новгород
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Углубиться в тему – скорая вывод из запоя нижний новгород
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Получить больше информации – vyvod-iz-zapoya-sochi24.ru/
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Детальнее – вывод из запоя на дому круглосуточно нижний новгород
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Получить дополнительные сведения – вызов врача нарколога на дом в краснодаре
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Получить дополнительные сведения – вывод из запоя недорого в нижний новгороде
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Детальнее – вывод из запоя клиника сочи
В «Частном Медике 24» в Воронеже каждый пациент, проходящий вывод из запоя в стационаре, получает комплексную помощь — диагностика, устранение интоксикации, восстановительная терапия, психологическая работа, всё с постоянным наблюдением и поддержкой, в условиях, где безопасность и анонимность стоят на первом месте.
Ознакомиться с деталями – вывод из запоя в стационаре
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить дополнительную информацию – врач вывод из запоя
Стационар «Частного Медика?24» обеспечивает комфорт и безопасность при лечении запоя.
Узнать больше – вывод из запоя в стационаре воронеж
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Получить дополнительную информацию – вывод из запоя дешево в сочи
Вывод из запоя на дому в Екатеринбурге от Stop-Alko — безопасно, анонимно и эффективно, с несколькими тарифами в зависимости от состояния пациента.
Разобраться лучше – скорая вывод из запоя в екатеринбурге
Лечение запоя в стационаре включает детоксикацию, медицинское наблюдение и психологическую поддержку.
Подробнее тут – вывод из запоя в стационаре в воронеже
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Ознакомиться с деталями – вывод из запоя капельница на дому
В стационаре «Частного Медика 24» пациент получает комплексное лечение, включая капельницы и медикаменты.
Разобраться лучше – [url=https://vyvod-iz-zapoya-v-stacionare-voronezh23.ru/]www.vyvod-iz-zapoya-v-stacionare-voronezh23.ru[/url]
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Получить дополнительные сведения – вывод из запоя круглосуточно
В клинике в Самаре устраняют симптомы интоксикации, оказывают поддержку организму и помогают восстановиться после тяжёлых запоев.
Разобраться лучше – наркология вывод из запоя в стационаре в самаре
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Узнать больше – нарколог на дом вывод из запоя
В «Частном Медике 24» в Воронеже каждый пациент, проходящий вывод из запоя в стационаре, получает комплексную помощь — диагностика, устранение интоксикации, восстановительная терапия, психологическая работа, всё с постоянным наблюдением и поддержкой, в условиях, где безопасность и анонимность стоят на первом месте.
Выяснить больше – наркология вывод из запоя в стационаре
Круглосуточный стационарный вывод из запоя в Воронеже — доступная помощь в любое время. Вы можете обратиться к нам в любое время суток, и мы окажем необходимую медицинскую помощь.
Подробнее – вывод из запоя в стационаре воронеж
В Краснодаре клиника «Детокс» предлагает выезд нарколога на дом. Помощь оказывается быстро, анонимно и круглосуточно.
Подробнее можно узнать тут – нарколог капельница на дом
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Получить дополнительные сведения – вывод из запоя на дому недорого в нижний новгороде
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Узнать больше – вывод из запоя клиника
Круглосуточный стационарный вывод из запоя в Воронеже — доступная помощь в любое время. Вы можете обратиться к нам в любое время суток, и мы окажем необходимую медицинскую помощь.
Изучить вопрос глубже – вывод из запоя в стационаре воронеж
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Детальнее – вывод из запоя круглосуточно в нижний новгороде
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
https://lamagdalenashow.com/hola-mundo
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
https://www.unlockedbrasil.com/%D0%BB%D1%83%D1%87%D1%88%D0%B8%D0%B5-%D0%BE%D0%BD%D0%BB%D0%B0%D0%B9%D0%BD-%D0%BA%D0%B0%D0%B7%D0%B8%D0%BD%D0%BE-2024-%E1%90%88-%D1%81%D0%BF%D0%B8%D1%81%D0%BA%D0%B8-%D0%B1%D0%BE%D0%BD%D1%83%D1%81%D0%BE
В Екатеринбурге «Похмельная Служба» проводит вывод из запоя анонимно и безопасно, с применением современных препаратов.
Получить дополнительные сведения – вывод из запоя в стационаре в екатеринбурге
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Открой скрытое – https://afishatoday.ru/post-uslugi-po-vyvodu-iz-zapoya-pokhmelya-i-leche-d657
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Ознакомьтесь с аналитикой – https://jamalweb.com/?p=308
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Слушай внимательно — тут важно – https://www.insources.ru/zdorove/uslugi-po-vyvodu-iz-zapoya-pokhmelya-i-lecheniyu-alk-o99s4
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Нажмите, чтобы узнать больше – https://soconnasis.org/one-click-demo-import-log_file_2020-04-09__16-32-08
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Что скрывают от вас? – https://jornalfax.net/index.php/2024/01/12/laurindo-vieira-morto-a-tiro-e-funcionario-senior-do-servicos-de-inteligencia-de-angola
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Интересует подробная информация – https://lunaturf.com/el-crack-riojano-2
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Продолжить чтение – https://utec.frbb.utn.edu.ar/post-format-gallery
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Только для своих – https://zdorov.atlastex.ru/mariya-kozhevnikova-podelilas-sovetami-po-pravilnomu-pitaniyu
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Исследовать вопрос подробнее – https://easytranslations.org/la-importancia-de-las-traducciones-certificadas-en-el-proceso-de-inmigracin
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Что скрывают от вас? – https://finflowgenius.org/the-gamification-of-financial-management-how-it-works
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Уточнить детали – https://kumaitea.com/dark-chocolate-during-pregnancy
Круглосуточный стационарный вывод из запоя в Воронеже — доступная помощь в любое время. Вы можете обратиться к нам в любое время суток, и мы окажем необходимую медицинскую помощь.
Получить дополнительные сведения – вывод из запоя в стационаре анонимно
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Исследовать вопрос подробнее – вывод из запоя на дому круглосуточно
В больничных условиях «Частного Медика 24» врачи контролируют давление, сердце и функции жизненно важных органов при выводе из запоя.
Исследовать вопрос подробнее – вывод из запоя в стационаре клиника самара
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Практические советы ждут тебя – http://actandlaw.paris/hello-world
Вывод из запоя в стационаре — это шанс начать путь к трезвой жизни, и в Самаре этот шанс предоставляет «Частный Медик 24».
Узнать больше – vyvod-iz-zapoya-v-stacionare-samara25.ru/
Стационарная детоксикация от алкоголя в Воронеже — восстановление организма под наблюдением специалистов. Мы проводим процедуры очищения организма от токсинов, восстанавливая физическое и психоэмоциональное состояние пациента.
Подробнее можно узнать тут – быстрый вывод из запоя в стационаре
Вывод из запоя в стационаре — это шанс начать путь к трезвой жизни, и в Самаре этот шанс предоставляет «Частный Медик 24».
Подробнее тут – вывод из запоя в стационаре анонимно
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Подробнее можно узнать тут – наркологический вывод из запоя
В стационаре пациент получает и физиологическую помощь, и психологическое сопровождение, что важно для долгосрочного восстановления.
Детальнее – наркология вывод из запоя в стационаре
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Выяснить больше – https://vyvod-iz-zapoya-sochi24.ru
В Сочи стационар клиники «Детокс» предлагает комплексный вывод из запоя. Пациентам обеспечивают комфорт, безопасность и круглосуточный контроль.
Узнать больше – вывод из запоя в стационаре сочи
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Подробнее – http://www.vyvod-iz-zapoya-sochi24.ru
В Сочи клиника «Детокс» проводит вывод из запоя в стационаре с круглосуточным контролем врачей. Процедуры безопасны, эффективны и анонимны.
Получить дополнительную информацию – вывод из запоя на дому недорого
Когда нужна срочная помощь, служба Stop-Alko в Екатеринбурге может выехать на дом, провести диагностику, капельницу и восстановление сил.
Подробнее можно узнать тут – анонимный вывод из запоя
Лечение запоя в стационаре включает детоксикацию, медицинское наблюдение и психологическую поддержку.
Получить больше информации – стационар вывод из запоя в воронеже
В Екатеринбурге «Stop-Alko» предлагает выезд врача-нарколога на дом, а также услугу полного вывода из запоя: детоксикация, капельницы, успокоительные средства и прочее.
Углубиться в тему – нарколог вывод из запоя в екатеринбурге
Вывод из запоя в Самаре проводится с проверенными препаратами, с учётом состояния пациента и без лишнего стресса.
Изучить вопрос глубже – вывод из запоя в стационаре анонимно
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Углубиться в тему – вывод из запоя вызов
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Углубиться в тему – вывод из запоя круглосуточно
Вывод из запоя в стационаре — это шанс начать путь к трезвой жизни, и в Самаре этот шанс предоставляет «Частный Медик 24».
Выяснить больше – стационар вывод из запоя
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Узнать больше – вывод из запоя цена сочи
Сервис Stop-Alko предлагает помощь при запое на дому в Екатеринбурге. Услуга доступна 24/7.
Детальнее – нарколог вывод из запоя
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Разобраться лучше – срочный вывод из запоя в сочи
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Выяснить больше – нарколог на дом круглосуточно
Клиника «Частный Медик 24» в Самаре оказывает помощь при запое анонимно, круглосуточно и без скрытых платежей.
Подробнее можно узнать тут – вывод из запоя в стационаре анонимно в самаре
В Воронеже клиника «Частный Медик 24» проводит вывод из запоя в стационаре с круглосуточным медицинским контролем.
Выяснить больше – вывод из запоя в стационаре в воронеже
Вывод из запоя в Воронеже проходит анонимно, с круглосуточной поддержкой специалистов.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-v-stacionare-voronezh22.ru
Преимущества домашнего лечения также заключаются в индивидуальном подходе. Врач, находясь в вашем доме, может более тщательно изучить ситуацию, провести необходимую диагностику и подобрать курс лечения, который идеально подойдет вашему состоянию. В отличие от клиники, где внимание врача часто ограничено временем, на дому можно уделить пациенту больше времени, подбирая лечение с учетом его особенностей.
Выяснить больше – нарколог на дом круглосуточно москва
Чем раньше начинается профессиональная детоксикация, тем меньше вероятность развития тяжёлых осложнений, таких как судорожный синдром, отёк мозга, острый панкреатит или некроз печени.
Подробнее – https://narkologicheskaya-klinika-zhukovskij4.ru/narkologicheskaya-klinika-telefon-v-zhukovskom
Ритм жизни в мегаполисе и постоянный стресс часто становятся причиной развития зависимостей у жителей города. В такой ситуации необходима профессиональная консультация врача. Оптимальное решение – вызов нарколога на дом в Москве. Это обеспечивает не только получение медицинской помощи в привычной обстановке, но и полную конфиденциальность.
Подробнее тут – http://narcolog-na-dom-msk55.ru/
Преимущества домашнего лечения также заключаются в индивидуальном подходе. Врач, находясь в вашем доме, может более тщательно изучить ситуацию, провести необходимую диагностику и подобрать курс лечения, который идеально подойдет вашему состоянию. В отличие от клиники, где внимание врача часто ограничено временем, на дому можно уделить пациенту больше времени, подбирая лечение с учетом его особенностей.
Получить дополнительную информацию – нарколог на дом цены
После обращения оператор клиники уточняет все детали — состояние пациента, стаж запоев, наличие хронических болезней, принимаемые лекарства, аллергии. Далее в течение 30–60 минут на дом выезжает мобильная бригада: врач-нарколог и медсестра со всем необходимым оборудованием и медикаментами.
Изучить вопрос глубже – vyvod iz zapoya na domu orekhovo zuevo
Ритм жизни в мегаполисе и постоянный стресс часто становятся причиной развития зависимостей у жителей города. В такой ситуации необходима профессиональная консультация врача. Оптимальное решение – вызов нарколога на дом в Москве. Это обеспечивает не только получение медицинской помощи в привычной обстановке, но и полную конфиденциальность.
Выяснить больше – психиатр нарколог на дом москва
Детоксикация производится как внутривенно — капельницы с регидратационными растворима, гепатопротекторами и сорбентами — так и аппаратным методом (плазмаферез, гемодиализ). Мы используем только современные одноразовые инфузионные системы и высококачественные лекарственные растворы, что гарантирует безопасность и максимальную эффективность процедур.
Детальнее – https://narkologicheskaya-klinika-zhukovskij4.ru/chastnaya-narkologicheskaya-klinika-v-zhukovskom/
Существуют определённые признаки, свидетельствующие о необходимости срочного обращения за профессиональной помощью:
Выяснить больше – http://vyvod-iz-zapoya-orekhovo-zuevo4.ru/anonimnyj-vyvod-iz-zapoya-v-orekhovo-zuevo/
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Получить больше информации – вызвать нарколога на дом краснодар
Одним из самых привлекательных аспектов вызова нарколога на дом является гибкость. Вы можете согласовать время визита врача, подходящее именно для вас, включая вечернее или ночное время. Это позволяет совмещать лечение с работой и личными делами, не нарушая привычный ритм жизни.
Разобраться лучше – вызов врача нарколога на дом в москве
Проведение лечения в домашней обстановке значительно снижает уровень стресса и тревожности. Пациенту не нужно тратить силы на поездки в медицинские учреждения, что особенно важно при ограниченной мобильности. Домашняя атмосфера создает идеальные условия для открытого диалога с врачом, что существенно повышает эффективность терапии и шансы на успешное выздоровление.
Изучить вопрос глубже – narcolog-na-dom-msk55.ru/
Не менее опасны и психоэмоциональные нарушения, связанные с абстинентным синдромом: тревога, чувство паники, галлюцинации, нарушения координации. В тяжёлых случаях может развиться алкогольный делирий (белая горячка) со спутанностью сознания, бредовыми идеями и приступами агрессии. Самостоятельный резкий отказ от спиртного в этом состоянии чреват непредсказуемыми осложнениями вплоть до судорог и комы.
Углубиться в тему – http://narko-reabcentr.ru
В Екатеринбурге сервис «Похмельная Служба / Stop-Alko» предлагает услугу вывода из запоя на дому — врач приезжает оперативно, ставит капельницу и обезболивает состояние.
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-ekaterinburg26.ru
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Исследовать вопрос подробнее – наркология вывод из запоя в сочи
В Екатеринбурге служба Stop-Alko круглосуточно помогает вывести из запоя на дому — быстро, анонимно и без постановки на учёт.
Детальнее – скорая вывод из запоя в екатеринбурге
Наркологическая клиника в Жуковском — это круглосуточная служба экстренной и плановой помощи при алкогольной, наркотической и лекарственной зависимости. Наркологическая клиника «Север-Мед» сочетает современные методики детоксикации, медикаментозного и психологического кодирования, а также комплексный подход к последующей реабилитации. Мы работаем без выходных и праздников, чтобы вы могли получить профессиональную помощь в любое время суток.
Получить дополнительные сведения – https://narkologicheskaya-klinika-zhukovskij4.ru
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Подробнее тут – срочный вывод из запоя в нижний новгороде
Медицинский вывод из запоя — это единственно правильное и безопасное решение. Врач-нарколог не только устранит симптомы отравления, но и грамотно скорректирует все жизненно важные параметры, предотвратит резкое падение давления, судорожный синдром, обеспечит защиту печени, почек и сердца.
Получить больше информации – https://vyvod-iz-zapoya-orekhovo-zuevo4.ru/vyvod-iz-zapoya-stacionar-v-orekhovo-zuevo
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Исследовать вопрос подробнее – вывод из запоя
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Изучить вопрос глубже – вывод из запоя круглосуточно нижний новгород
В Краснодаре нарколог из клиники «Детокс» приедет на дом, чтобы вывести из запоя и оказать необходимую помощь.
Углубиться в тему – запой нарколог на дом
В стационаре пациент получает и физиологическую помощь, и психологическое сопровождение, что важно для долгосрочного восстановления.
Подробнее тут – вывод из запоя в стационаре анонимно
Врачи «Частного Медика 24» контролируют состояние организма и предотвращают осложнения при выводе из запоя.
Получить дополнительные сведения – быстрый вывод из запоя в стационаре
Препараты подбираются строго индивидуально и могут включать:
Выяснить больше – https://narcolog-na-dom-v-moskve55.ru
В Самаре в «Частном Медике 24» пациент получает детоксикацию, восстановительное лечение и круглосуточное наблюдение врачей.
Выяснить больше – http://vyvod-iz-zapoya-v-stacionare-samara23.ru
Вывод из запоя в стационаре Воронежа — эффективное решение для длительного запоя. Мы обеспечиваем круглосуточное наблюдение и комплексное лечение, включая детоксикацию, восстановление водно-электролитного баланса и психотерапевтическую поддержку.
Изучить вопрос глубже – вывод из запоя в стационаре анонимно в воронеже
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее можно узнать тут – вывод из запоя вызов на дом сочи
Вывод из запоя в стационаре — это шанс начать путь к трезвой жизни, и в Самаре этот шанс предоставляет «Частный Медик 24».
Изучить вопрос глубже – стационар вывод из запоя в самаре
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Подробнее можно узнать тут – вывод из запоя круглосуточно
Bank kartı və e-cüzdanla depozitlər anında düşür, ödəniş limiti AZN üçün əlverişlidir.
Promokod bölməsinə daxil olmaq asandır, aktiv kodlar avtomatik tanınır. Aktiv promosları qaçırmamaq üçün pinco bonus bölməsinə baxın, canlı izləmə zamanı əlavə fribetlər çıxır. Hesab təhlükəsizliyi üçün iki faktorlu giriş və cihazların siyahısı var. Axtarış paneli ad, provayder və mexanika üzrə işləyir — nəticələr dərhal çıxır.
Oyun qaydaları hər masada ayrıca açılır və suallara cavab verir. APK yenilənməsi tətbiqdaxili xəbərdarlıqla gəlir və bir dəqiqəyə tamamlanır.
FAQ bölməsi ödənişlər, bonuslar və verifikasiya üzrə genişdir. Region qaydalarına uyğun lokal variantlar və hüquqi məlumat verilir. Favoritlər siyahısı ilə sevdiyiniz liqalar və slotlar bir yerdə saxlanır.
В клинике в Самаре устраняют симптомы интоксикации, оказывают поддержку организму и помогают восстановиться после тяжёлых запоев.
Подробнее тут – http://vyvod-iz-zapoya-v-stacionare-samara25.ru
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Подробнее можно узнать тут – нарколог вывод из запоя
Пациентам в Самаре предлагается анонимное лечение в стационаре с круглосуточным уходом и безопасными условиями.
Разобраться лучше – наркология вывод из запоя в стационаре в самаре
Выведение из запоя в стационаре Воронежа — помощь при острых состояниях и хронической зависимости. Наши опытные наркологи используют современные методы лечения для быстрого и безопасного вывода из запоя.
Ознакомиться с деталями – нарколог вывод из запоя в стационаре
В стационаре «Частного Медика?24» пациент получает комплексное лечение, включая капельницы и медикаменты.
Изучить вопрос глубже – нарколог вывод из запоя в стационаре воронеж
В условиях клиники пациент находится под наблюдением медицинской сестры и врача 24/7, что особенно важно при тяжёлой интоксикации и риске острых осложнений. Быстрый доступ к расширенной диагностике — ЭКГ, УЗИ, анализы крови — обеспечивает точную корректировку терапии. Стационар подходит тем, у кого есть серьёзные сопутствующие заболевания или высокий риск алкогольных психозов.
Получить дополнительные сведения – http://алко-избавление.рф/narkolog-vyvod-iz-zapoya-msk/
В Екатеринбурге служба Stop-Alko круглосуточно помогает вывести из запоя на дому — быстро, анонимно и без постановки на учёт.
Детальнее – вывод из запоя круглосуточно екатеринбург
Диагностика включает общий и биохимический анализ крови, оценку работы печени и почек, электрокардиографию и психологическое тестирование для выявления уровня мотивации.
Ознакомиться с деталями – https://kodirovanie-ot-alkogolizma-pushkino4.ru/kodirovanie-ot-alkogolizma-ceny-v-pushkino
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Детальнее – нарколог на дом клиника
Длительное злоупотребление спиртным неизбежно приводит к серьёзным последствиям для организма. Алкоголь влияет на работу практически всех внутренних органов: печень испытывает повышенную нагрузку при выводе токсинов, почки страдают от нарушения водно-солевого баланса, а сердечно-сосудистая система подвержена скачкам давления и аритмиям. Постепенно ухудшается общее самочувствие – возникают постоянные головные боли, слабость, повышенная раздражительность, бессонница.
Исследовать вопрос подробнее – наркология вывод из запоя в москве
Клиника «Частный Медик 24» в Самаре оказывает помощь при запое анонимно, круглосуточно и без скрытых платежей.
Получить дополнительную информацию – http://vyvod-iz-zapoya-v-stacionare-samara24.ru
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Изучить вопрос глубже – http://narkolog-na-dom-krasnodar26.ru
Клиника «Частный Медик 24» в Самаре оказывает помощь при запое анонимно, круглосуточно и без скрытых платежей.
Получить дополнительные сведения – [url=https://vyvod-iz-zapoya-v-stacionare-samara23.ru/]быстрый вывод из запоя в стационаре самара[/url]
Стационар «Частного Медика 24» в Воронеже — место, где пациент, страдающий от длительного запоя, получает не просто деньги-стоимость услуги, а полноценную помощь: диагностику, детоксикацию, медикаментозную поддержку и психологическую помощь с уважением к личному пространству и анонимности.
Подробнее – наркология вывод из запоя в стационаре в воронеже
Этот подход имеет несколько ключевых преимуществ, которые обеспечивают комфорт, безопасность и эффективность лечения.
Углубиться в тему – врач нарколог выезд на дом москва
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Изучить вопрос глубже – анонимный вывод из запоя нижний новгород
В жизни крупных городов часто возникают ситуации, когда стрессы и быстрый ритм жизни приводят к развитию зависимости. Когда проблема становится очевидной, важно незамедлительно обратиться за помощью. В таких случаях вызов нарколога на дом может стать не только удобным, но и наиболее эффективным вариантом. Это позволяет получить квалифицированное лечение в привычной обстановке, сохраняя при этом полную анонимность и конфиденциальность.
Получить дополнительные сведения – врач нарколог выезд на дом
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Продолжить чтение – https://yam193293393.com/2022/12/12/9-%E4%B8%89%E6%B1%A0%E9%AB%98%E8%8F%9C%E3%81%AE%E6%A0%BD%E5%9F%B9%E2%91%A2
Длительное злоупотребление спиртным неизбежно приводит к серьёзным последствиям для организма. Алкоголь влияет на работу практически всех внутренних органов: печень испытывает повышенную нагрузку при выводе токсинов, почки страдают от нарушения водно-солевого баланса, а сердечно-сосудистая система подвержена скачкам давления и аритмиям. Постепенно ухудшается общее самочувствие – возникают постоянные головные боли, слабость, повышенная раздражительность, бессонница.
Получить дополнительную информацию – срочный вывод из запоя в москве
Выведение из запоя в стационаре Воронежа — помощь при острых состояниях и хронической зависимости. Наши опытные наркологи используют современные методы лечения для быстрого и безопасного вывода из запоя.
Разобраться лучше – вывод из запоя в стационаре клиника воронеж
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Заходи — там интересно – https://dssports.com.hk/product/swim
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Только для своих – https://finestpublicadjusters.com/feeling-stuck-in-business-get-business-help
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Детали по клику – https://www.edmarlyra.com/comissao-de-viacao-e-transporte-aprova-pl-de-eduardo-da-fonte-que-proibe-remocao-de-veiculos-em-feriados-e-fins-de-semana
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Всё, что нужно знать – https://www.redlandsnaturopathic.com.au/hello-world
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Подробнее – https://peruestor.com/hello-world
Проведение лечения в домашней обстановке значительно снижает уровень стресса и тревожности. Пациенту не нужно тратить силы на поездки в медицинские учреждения, что особенно важно при ограниченной мобильности. Домашняя атмосфера создает идеальные условия для открытого диалога с врачом, что существенно повышает эффективность терапии и шансы на успешное выздоровление.
Узнать больше – https://narcolog-na-dom-msk55.ru/vyzov-narkologa-na-dom-moskva
Проведение лечения в домашней обстановке значительно снижает уровень стресса и тревожности. Пациенту не нужно тратить силы на поездки в медицинские учреждения, что особенно важно при ограниченной мобильности. Домашняя атмосфера создает идеальные условия для открытого диалога с врачом, что существенно повышает эффективность терапии и шансы на успешное выздоровление.
Исследовать вопрос подробнее – https://narcolog-na-dom-msk55.ru/
Наши врачи оперативно приезжают к пациенту, проводят осмотр, купируют симптомы абстиненции и приступают к восстановлению жизненно важных функций. Всё это — в привычной для пациента обстановке, без стресса и лишней огласки. Мы обеспечиваем не только медицинскую помощь, но и эмоциональную поддержку, создавая условия для начала пути к выздоровлению.
Получить дополнительные сведения – нарколог на дом круглосуточно цены в красногорске
Одним из самых привлекательных аспектов вызова нарколога на дом является гибкость. Вы можете согласовать время визита врача, подходящее именно для вас, включая вечернее или ночное время. Это позволяет совмещать лечение с работой и личными делами, не нарушая привычный ритм жизни.
Подробнее тут – нарколог капельница на дом в москве
Длительное злоупотребление спиртным неизбежно приводит к серьёзным последствиям для организма. Алкоголь влияет на работу практически всех внутренних органов: печень испытывает повышенную нагрузку при выводе токсинов, почки страдают от нарушения водно-солевого баланса, а сердечно-сосудистая система подвержена скачкам давления и аритмиям. Постепенно ухудшается общее самочувствие – возникают постоянные головные боли, слабость, повышенная раздражительность, бессонница.
Разобраться лучше – вывод из запоя капельница на дому
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Посмотреть всё – https://template89.webekspor.com/north-sulawesi-exports-1800-tons-of-copra-to-philippines
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Подробнее – https://www.lexindiajuris.com/2016/11/demo-post-20
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Читать дальше – https://kidsstorie.com/the-tale-of-a-rich-father-and-his-city-kid-city-kids-stories
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Получить профессиональную консультацию – https://kidsstorie.com/the-tale-of-a-rich-father-and-his-city-kid-city-kids-stories
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Познакомиться с результатами исследований – https://www.roelabogados.com/2019/01/12/what-we-are-capable-of-usually-gets-discovered-7
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Почему это важно? – https://tedweennews.com/%D8%AB%D9%88%D8%B1-%D9%87%D8%A7%D8%A6%D8%AC-%D9%8A%D9%82%D8%AA%D8%AD%D9%85-%D8%A7%D9%84%D9%85%D9%84%D8%B9%D8%A8-%D9%88%D9%8A%D9%87%D8%A7%D8%AC%D9%85-%D8%A7%D9%84%D9%84%D8%A7%D8%B9%D8%A8%D9%8A%D9%86
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Что скрывают от вас? – https://novavitamed.ru/oral-health-foundation
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Выяснить больше – https://mathrusreeayurveda.com/salt-uses
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Это стоит прочитать полностью – https://cubbinthekitchen.com/sweet-cream-cheese-dip
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Узнать больше – http://www.guatemalatps.info/?p=184
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Ознакомиться с деталями – https://jp-art.photography/portfolios/rocky-island
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Переходите по ссылке ниже – https://www.crufaoci.org/president-par-interin
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Открыть полностью – http://vitaflex.com.au/product/makita-18v-li-ion-battery-bl1830
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Практические советы ждут тебя – https://waldwiese.eu/hallo-welt
I’m gone to convey my little brother, that he should also pay a quick visit this blog on regular basis to get updated from most recent information.
сат казино
Диагностика включает общий и биохимический анализ крови, оценку работы печени и почек, электрокардиографию и психологическое тестирование для выявления уровня мотивации.
Узнать больше – http://kodirovanie-ot-alkogolizma-pushkino4.ru
Существуют определённые признаки, свидетельствующие о необходимости срочного обращения за профессиональной помощью:
Детальнее – vyvod iz zapoya nedorogo
Лечебные мероприятия и рекомендации формируются исходя из индивидуального состояния каждого пациента. Специалист имеет возможность посвятить достаточное количество времени каждому больному, корректируя программу лечения согласно его особым потребностям и жизненным обстоятельствам. При этом учитываются психологические, социальные и физические аспекты, оказывающие влияние на здоровье пациента. Персонализированный подход обеспечивает оперативное реагирование на изменения состояния и своевременную корректировку терапии.
Получить дополнительную информацию – вызов нарколога на дом
Этот подход имеет несколько ключевых преимуществ, которые обеспечивают комфорт, безопасность и эффективность лечения.
Ознакомиться с деталями – нарколог на дом цены в москве
Кодирование основано на блокировке механизмов зависимости на биохимическом и поведенческом уровнях. Медикаментозные методы включают введение препаратов пролонгированного действия, которые нарушают метаболизм этанола: при попытке выпить даже небольшую дозу алкоголь вызывает выражённые неприятные реакции, что психологически отвращает от новой пробы спиртного. Психотерапевтические техники, такие как гипноз или метод Довженко, направлены на переустановку подсознательных программ, удаление эмоционального влечения к алкоголю и укрепление мотивации к здоровому образу жизни. Аппаратные методики (электроимпульсная стимуляция, транскраниальная микрополяризация) воздействуют на нейроны, участвующие в развитии зависимости, снижая их активность и уменьшая физиологический дискомфорт. В «Орион-Клиник» часто используют комбинированные программы: сначала проводится детоксикация организма, затем вводится медикаментозное средство, после чего реализуется психотерапевтический блок влияния на подсознание.
Изучить вопрос глубже – https://kodirovanie-ot-alkogolizma-pushkino4.ru/kodirovanie-ot-alkogolizma-na-domu-v-pushkino/
Ритм жизни в мегаполисе и постоянный стресс часто становятся причиной развития зависимостей у жителей города. В такой ситуации необходима профессиональная консультация врача. Оптимальное решение – вызов нарколога на дом в Москве. Это обеспечивает не только получение медицинской помощи в привычной обстановке, но и полную конфиденциальность.
Исследовать вопрос подробнее – выезд нарколога на дом в москве
Основной задачей нарколога, выезжающего на дом, является помощь в любой ситуации, связанной с зависимостью. Все процедуры и методики подбираются индивидуально, в зависимости от состояния пациента.
Узнать больше – врач нарколог выезд на дом москва
Существуют определённые признаки, свидетельствующие о необходимости срочного обращения за профессиональной помощью:
Разобраться лучше – вывод из запоя стационар
Лечебные мероприятия и рекомендации формируются исходя из индивидуального состояния каждого пациента. Специалист имеет возможность посвятить достаточное количество времени каждому больному, корректируя программу лечения согласно его особым потребностям и жизненным обстоятельствам. При этом учитываются психологические, социальные и физические аспекты, оказывающие влияние на здоровье пациента. Персонализированный подход обеспечивает оперативное реагирование на изменения состояния и своевременную корректировку терапии.
Узнать больше – запой нарколог на дом
Для многих пациентов важным моментом является сохранение конфиденциальности. Врач, приехавший на дом, работает с полной защитой данных. Пациент может быть уверен, что его проблема останется личной и не станет достоянием общественности. Врачи приезжают на неприметных автомобилях и избегают всяческих ситуаций, которые могут привлечь лишнее внимание.
Детальнее – запой нарколог на дом
Не менее опасны и психоэмоциональные нарушения, связанные с абстинентным синдромом: тревога, чувство паники, галлюцинации, нарушения координации. В тяжёлых случаях может развиться алкогольный делирий (белая горячка) со спутанностью сознания, бредовыми идеями и приступами агрессии. Самостоятельный резкий отказ от спиртного в этом состоянии чреват непредсказуемыми осложнениями вплоть до судорог и комы.
Углубиться в тему – наркологический вывод из запоя в москве
Диагностика включает общий и биохимический анализ крови, оценку работы печени и почек, электрокардиографию и психологическое тестирование для выявления уровня мотивации.
Получить больше информации – http://kodirovanie-ot-alkogolizma-pushkino4.ru
В таких случаях медлить нельзя — своевременный вызов нарколога может спасти жизнь и предотвратить тяжёлую инвалидизацию.
Получить дополнительные сведения – http://vyvod-iz-zapoya-orekhovo-zuevo4.ru/
Препараты подбираются строго индивидуально и могут включать:
Получить дополнительные сведения – нарколог на дом клиника в красногорске
Не откладывайте обращение к специалисту, если вы или ваши близкие столкнулись с:
Изучить вопрос глубже – narkologicheskaya klinika v oblasti
В столичном регионе доступны два основных формата лечения: выезд специалиста на дом и госпитализация в специализированный центр. Каждый вариант имеет свои особенности и показания, которые врач анализирует при первичном осмотре.
Получить больше информации – https://алко-избавление.рф/vyvod-iz-zapoya-czena-msk/
Лечение основывается на комплексном подходе, позволяющем учесть особенности организма и стаж злоупотребления алкоголем. Обычно процедура состоит из нескольких этапов:
Разобраться лучше – вывод из запоя недорого
Этот подход имеет несколько ключевых преимуществ, которые обеспечивают комфорт, безопасность и эффективность лечения.
Получить дополнительную информацию – https://narcolog-na-dom-moskva55.ru/narkolog-na-dom-moskva-tseny
Именно поэтому при затяжных запоях необходима квалифицированная медицинская помощь, позволяющая безопасно и максимально комфортно прекратить приём алкоголя. Клиника «Стратегия Здоровья» предлагает профессиональный вывод из запоя в Москве как в условиях стационара, так и с выездом на дом. Врачи работают круглосуточно, используя проверенные методики детоксикации и медикаментозной поддержки.
Подробнее – https://narko-reabcentr.ru/vyvod-iz-zapoya-na-domu-v-moskve/
Основной задачей нарколога, выезжающего на дом, является помощь в любой ситуации, связанной с зависимостью. Все процедуры и методики подбираются индивидуально, в зависимости от состояния пациента.
Разобраться лучше – http://narcolog-na-dom-moskva55.ru
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Где можно узнать подробнее? – https://atme-lb.com/hello-world
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Полная информация здесь – https://genkinomoto.inoue-ladies.jp/archives/872
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Давай разберёмся досконально – https://jardin.glee.pet/producto/chaleco-salvavidas-impermeable
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Ознакомьтесь поближе – https://espacouvir.com.br/teste-de-aparelhos-auditivos
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Лови подробности – https://www.greenevents.lu/locations/luxembourg
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Ознакомьтесь поближе – https://linhoff.in/choosing-the-right-modular-kitchen-for-your-home
Эта информационная публикация освещает широкий спектр тем из мира медицины. Мы предлагаем читателям ясные и понятные объяснения современных заболеваний, методов профилактики и лечения. Информация будет полезна как пациентам, так и медицинским работникам, желающим поддержать уровень своих знаний.
Исследовать вопрос подробнее – https://clever-lady.ru/medicina/narkologicheskij-centr-vse-chto-nuzhno-znat-o-lechenii-zavisimosti-i-vosstanovlenii-zdorovja.html
Эта статья подробно расскажет о процессе выздоровления, который включает в себя эмоциональную, физическую и психологическую реабилитацию. Мы обсуждаем значимость поддержки и наличие профессиональных программ. Читатели узнают, как строить новую жизнь и не возвращаться к старым привычкам.
Подробнее – https://ogkt.ru/raznoe/kak-vyvesti-iz-zapoya-sovremennye-metody-i-podhody.html
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Слушай внимательно — тут важно – http://janidocs.com/portfolio/incididunt-ut-labore-et-dolore
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Детальнее – https://superawesometour.com/pack-wisely-before-traveling
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Подробности по ссылке – https://jornalhorah.info/2023/12/21/angola-anuncia-saida-da-organizacao-dos-paises-exportadores-de-petroleo
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Нажмите, чтобы узнать больше – https://idealcream.com/product/liquid-hand-soap-avocado-and-peach
Эта медицинская заметка содержит сжатую информацию о новых находках и методах в области здравоохранения. Мы предлагаем читателям свежие данные о заболеваниях, профилактике и лечении. Наша цель — быстро и доступно донести важную информацию, которая поможет в повседневной жизни и понимании здоровья.
Выяснить больше – https://www.avtolubitelyam.ru/narkologicheskaya-klinika-istochnik-zhizni-v-omske-00xep
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Не упусти важное! – https://airconditioningrepairdallastx.com/hello-world
В этой медицинской статье мы погрузимся в актуальные вопросы здравоохранения и лечения заболеваний. Читатели узнают о современных подходах, методах диагностики и новых открытий в научных исследованиях. Наша цель — донести важную информацию и повысить уровень осведомленности о здоровье.
Получить дополнительные сведения – https://mirokru.ru/vyvod-iz-zapoya-top-strategij
Этот документ охватывает важные аспекты медицинской науки, сосредотачиваясь на ключевых вопросах, касающихся здоровья населения. Мы рассматриваем свежие исследования, клинические рекомендации и лучшие практики, которые помогут улучшить качество лечения и профилактики заболеваний. Читатели получат возможность углубиться в различные медицинские дисциплины.
Подробнее можно узнать тут – https://li8.ru/2024/07/30/statya-narkologicheskaya-klinika-istochnik-zhizni-v-omske-55
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Узнать больше > – https://takugon.com/?p=642
Публикация охватывает основные направления развития современной медицины. Мы обсудим значимость научных исследований, инноваций в лечении и роли общественного участия в формировании системы здравоохранения.
Это ещё не всё… – https://fi-hi.ru/narkologicheskaya-pomoshh-na-domu-preimushhestva-metody-i-etapy
В этой публикации мы предложим ряд рекомендаций по избавлению от зависимостей и успешному восстановлению. Мы обсудим методы привлечения поддержки и важность самосознания. Эти советы помогут людям вернуться к нормальной жизни и стать на путь выздоровления.
Выяснить больше – https://just-fit.ru/interesnoe/effektivnye-metody-vyvoda-iz-zapoya-kak-vernutsya-k-normalnoy-zhizni
В этом обзоре представлены различные методы избавления от зависимости, включая терапевтические и психологические подходы. Мы сравниваем их эффективность и предоставляем рекомендации для тех, кто хочет вернуться к трезвой жизни. Читатели смогут найти информацию о реабилитационных центрах и поддерживающих группах.
Подробнее – https://med-tutorial.ru/med-article/lecenie-zavisimostei/osobennosti-raboty-narkologiceskix-centrov
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Что ещё? Расскажи всё! – https://globalvibenetwork.com/the-evolution-of-edge-computing-redefining-data-processing
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Что скрывают от вас? – https://jalan-kembali.com/manfaat-duduk-tegak-untuk-kesehatan-fisik-dan-mental
Такая последовательность действий позволяет обеспечить результативность и закрепить положительные изменения.
Получить дополнительную информацию – наркологическая клиника стационар пермь
Инфузионная терапия в «ТагилМед Реал» — это точный инструмент под конкретный запрос: обезвоживание, вегетативная нестабильность, нарушения сна, «утренний туман». Состав и дозировки подбирает врач с учётом возраста, коморбидности и лекарственных взаимодействий. Важно понимать: больше компонентов не значит лучше; главная ценность — фокус и безопасность.
Получить дополнительные сведения – наркологическая клиника в нижнем тагиле
Каждая ситуация уникальна, однако базовая логика не меняется: один этап — одна цель — один критерий успеха. Ниже — ориентировочная структура визита, которая на месте детализируется с учётом возраста, сопутствующих болезней и особенностей пространства.
Ознакомиться с деталями – https://vyvod-iz-zapoya-nizhnij-tagil0.ru/
Такой календарь делает весь процесс прозрачным: пациент видит логику, близкие — прогресс, а врач — чистый сигнал для коррекции без «эскалации на всякий случай».
Узнать больше – http://narcologicheskaya-klinika-saratov0.ru/chastnaya-narkologicheskaya-klinika-saratov/
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Получить дополнительную информацию – http://
Врачи «СтаврМед Центра» работают круглосуточно, обеспечивая выезд нарколога на дом в течение короткого времени. Пациент может получить помощь в привычных условиях, не подвергаясь стрессу, связанному с госпитализацией. Все процедуры проводятся анонимно, с сохранением врачебной тайны. Благодаря такому подходу, лечение становится не только эффективным, но и максимально комфортным для человека, который решил прекратить запой и начать восстановление.
Изучить вопрос глубже – https://vyvod-iz-zapoya-stavropol0.ru/vyvod-iz-zapoya-v-staczionare-stavropol/
Мы работаем по принципу «один визит — один измеримый результат». После инфузий пациент обычно отмечает облегчение головной боли, уменьшение тремора и тревоги, улучшение сна к ближайшей ночи. Если ситуация сложнее (длительный многодневный запой, выраженные соматические факторы), врач оставляет ступенчатый план на 24–48 часов с повторным визитом или переводом в стационарный блок по согласованию с пациентом и родными.
Подробнее тут – запой нарколог на дом в ставрополе
Вывод из запоя — это не «волшебная капельница», а последовательная медицинская программа с чёткими целями и измеримыми маркерами. В наркологической клинике «СаратовМед Профи» маршрут строится по принципу управляемых окон: на каждом шаге команда преследует одну цель, меняет лишь один параметр и оценивает результат в заранее назначённый момент. Такой подход снижает лекарственную нагрузку, предотвращает «гонку дозировок» и делает динамику предсказуемой для пациента и близких. Конфиденциальность обеспечивается регламентом: немаркированные выезды, нейтральные формулировки в документах, «тихие» каналы связи, доступ к записям — строго по ролям.
Узнать больше – вывод из запоя капельница на дому в саратове
Ниже — примерный «каркас» лечения. Он индивидуализируется по клинической картине, сопутствующим болезням, опыту прошлых попыток и бытовым ограничениям. Ключевой принцип — «одно вмешательство: одна цель — один маркер — одна дата проверки».
Подробнее – анонимная наркологическая клиника в петрозаводске
В «КаменМед Ренессанс» круглосуточно работает выездная служба: капельницы 24/7, мониторинг витальных показателей, экспресс-скрининг риска осложнений, «тихие» маршруты госпитализации при необходимости. Мы придерживаемся принципа «минимально достаточной терапии»: никаких универсальных «коктейлей», только персонализированные решения с понятной логикой назначения. Такой подход защищает пациента от полипрагмазии, уменьшает побочные эффекты и позволяет честно видеть вклад каждого шага — от первого часа детокса до возвращения к работе.
Ознакомиться с деталями – http://narkologicheskaya-klinika-kamensk-uralskij0.ru/narkologiya-kamensk-uralskij/
Мы не используем универсальную «капельницу». Схема собирается из модулей под ведущие жалобы. Медицинские шаги всегда сочетаются с нефраком опорами — свет, тишина, вода малыми глотками, дыхание, — потому что среда усиливает действие препаратов и позволяет держать дозы ниже.
Детальнее – частный нарколог на дом в саратове
С первого контакта координатор уточняет: длительность запоя, виды алкоголя, аллергии, список текущих лекарств, эпизоды судорог или психозов в анамнезе, сердечно-сосудистые жалобы. На основании ответов команда подбирает безопасную схему старта и резервный план на случай усиления симптомов. Врач привозит портативный монитор для контроля АД/ЧСС/SpO2, глюкометр, набор инфузионных линий и расходников, а также средства для экспресс-коррекции тревоги по показаниям.
Получить дополнительную информацию – http://vyvod-iz-zapoya-pervouralsk0.ru/
Наркологическая клиника «СтаврМед Центр» предлагает выезд нарколога на дом 24/7. Врач прибывает на адрес в течение 30–60 минут с набором необходимых медикаментов и оборудования. В ходе процедуры пациенту ставится капельница, вводятся препараты для детоксикации и нормализации работы нервной системы. Одновременно контролируются показатели давления, пульса и реакции организма. После окончания терапии врач оставляет рекомендации по восстановлению и, при необходимости, предлагает повторное наблюдение или консультацию психолога.
Ознакомиться с деталями – помощь вывод из запоя ставрополь
Домашний визит уместен не только при тяжёлой абстиненции. Он эффективен и на этапе нарастающих симптомов, когда важно предотвратить обострение. Ниже — ориентиры, помогающие принять решение.
Выяснить больше – нарколог на дом вывод
Хотя принципы лечения похожи, клиническая логика отличается. При алкогольной зависимости чаще нужен быстрый контроль вегетативных симптомов, восстановление сна и коррекция электролитов. При наркозависимости добавляются протоколы снижения импульсивности, работа с абстиненцией другой природы и расширенная психотерапевтическая часть. В обоих случаях результат не сводится к «капельнице»: мы учим распознавать ранние сигналы срыва, формировать безопасные ритуалы и поддерживать общение без давления и скрытых конфликтов.
Разобраться лучше – narkologicheskaya-klinika-petrozavodsk0.ru/
Такой подход позволяет точно отслеживать динамику и вносить изменения в программу без потери контроля. Пациент видит прогресс, а врачи получают объективные данные о реакции организма на лечение.
Изучить вопрос глубже – http://
Мы работаем без пауз и очередей, принимая пациентов в любое время суток. В распоряжении бригад — немаркированный транспорт для выезда на дом, портативная диагностика (ЭКГ, пульсоксиметрия, экспресс-анализаторы), а в стационаре — палаты с регулируемым микроклиматом и круглосуточный мониторинг жизненных показателей. Вся документация оформляется в нейтральной терминологии, доступ к данным разграничен по ролям, что защищает вашу анонимность.
Выяснить больше – https://narcologicheskaya-klinika-stavropol0.ru/narkologicheskaya-klinika-stavropol-otzyvy/
Для жителей Нижнего Тагила у нас организованы три параллельных канала помощи: очные визиты в клинику, «тихий» выезд на дом и защищённые телемедицинские консультации. Координатор уже при первом звонке уточняет ключевые риски (аллергии, хронические заболевания, эпизоды судорог/психозов, приём постоянных препаратов), бытовые условия (возможность обеспечить тишину на 2–3 часа, доступ к воде, особенности подъезда), а также предпочтения по конфиденциальности. Это позволяет врачу подготовить персональный стартовый протокол заранее и сократить время между осмотром и первой процедурой.
Разобраться лучше – наркологическая клиника цены в нижнем тагиле
Такая последовательность действий позволяет обеспечить результативность и закрепить положительные изменения.
Углубиться в тему – запой наркологическая клиника в перми
best post cycle therapy for steroids
References:
https://tailandiatours.com/que-ver-en-ayutthaya/
Роберт Левандовски тууралуу жаңылыктар ар дайым көңүлдү бурат.
Левандовскинин жашоо образы көптөр үчүн мотивация. Левандовскинин статистикасы футбол дүйнөсүндө өзгөчө. Левандовскинин машыгуу режими көпчүлүккө кызыктуу. Толук биография жана сүрөттөр http://www.robert-lewandowski-kg.com сайтында жеткиликтүү. Левандовски Барселонага өткөндөн кийин клуб жаңы деңгээлге чыкты.
Роберт Левандовскинин жашоосунда үй-бүлөнүн ролу чоң. Левандовски жаракаттан кийин тез эле формасын кайтарды.
Роберт Левандовски үй-бүлөсүнө чоң маани берет. Роберт Левандовски футбол тарыхындагы легенда.
Хотя принципы лечения похожи, клиническая логика отличается. При алкогольной зависимости чаще нужен быстрый контроль вегетативных симптомов, восстановление сна и коррекция электролитов. При наркозависимости добавляются протоколы снижения импульсивности, работа с абстиненцией другой природы и расширенная психотерапевтическая часть. В обоих случаях результат не сводится к «капельнице»: мы учим распознавать ранние сигналы срыва, формировать безопасные ритуалы и поддерживать общение без давления и скрытых конфликтов.
Подробнее – наркологическая клиника цены в петрозаводске
В Нижнем Тагиле выездные бригады дежурят 24/7. Координатор уже при первичном звонке собирает ключевые сведения: аллергии, хронические заболевания, список постоянных препаратов, эпизоды судорог или алкогольных психозов в прошлом, последние значения давления и пульса, возможность обеспечить тишину на 2–3 часа, доступ к питьевой воде, особенности подъезда. Вся эта информация помогает врачу подготовить стартовую схему — от выбора профиля инфузии до темпа введения. По запросу организуем немаркированный визит и сдержанные формулировки в документах, чтобы не создавать лишнего внимания со стороны соседей и коллег.
Ознакомиться с деталями – вывод из запоя вызов город
Для жителей Каменска-Уральского мы организовали быстрый и незаметный доступ к помощи. Координатор принимает обращения круглосуточно, уточняет адрес, особенности подъезда, пожелания по конфиденциальности и удобные «окна» визита. Бригады приезжают без опознавательных знаков, расходные материалы — в нейтральной упаковке, а формулировки в документах исключают нежелательные «ярлыки». Если дома временно нельзя обеспечить тишину и безопасность, мы «тихо» переводим пациента в палату краткого наблюдения: отдельный вход, короткий маршрут, минимум контактов и быстрое возвращение к домашнему формату после стабилизации.
Углубиться в тему – https://narkologicheskaya-klinika-kamensk-uralskij0.ru
Мы не используем универсальную «капельницу». Схема собирается из модулей под ведущие жалобы. Медицинские шаги всегда сочетаются с нефраком опорами — свет, тишина, вода малыми глотками, дыхание, — потому что среда усиливает действие препаратов и позволяет держать дозы ниже.
Ознакомиться с деталями – врач нарколог на дом
Наша выездная бригада приезжает без маркировки, в гражданской одежде, согласовывает «тихое окно» связи с пациентом или близкими и начинает не с капельницы, а с настройки среды: тёплая приглушённая подсветка, проветривание без сквозняков, отключение уведомлений, подготовка воды комнатной температуры. Затем — быстрый осмотр, экспресс-метрики и старт индивидуального плана. Каждая корректировка — ровно одна за раз, чтобы сохранить причинно-следственную связь и не провоцировать полипрагмазию.
Изучить вопрос глубже – платный нарколог на дом саратов
Выездной наркологический сервис «МедПоволжье Клиник» создан для случаев, когда важны скорость, тишина и клиническая точность. Мы проводим детоксикацию и снятие интоксикации на дому так, чтобы каждое действие имело цель, измеримый маркер и заранее оговорённое «окно переоценки». Вместо «сильной капельницы на всякий случай» — модульная схема: один симптом-кластер > один медицинский модуль > одна поведенческая опора (свет, звук, вода малыми глотками, дыхание 4–6). Такой подход снижает лекарственную нагрузку, ускоряет стабилизацию и позволяет видеть прогресс буквально по часам.
Детальнее – http://narkolog-na-dom-saratov0.ru
В клинике «ЮгМед Альянс» выстроена система непрерывного медицинского наблюдения. При поступлении проводится комплексная диагностика, назначается детоксикация и поддерживающая терапия, затем начинается стабилизация физического и эмоционального состояния. Благодаря круглосуточной работе бригад и возможности экстренного выезда на дом пациенты получают помощь без задержек. Конфиденциальность соблюдается на всех уровнях — от первичного звонка до выписки. Для удобства родственников организована система информирования: короткие апдейты по согласованным каналам связи и только в определённое время, чтобы не нарушать покой пациента.
Исследовать вопрос подробнее – наркологическая клиника нарколог в ставрополе
Мы заранее объясняем, какие шаги последуют, чтобы пациент и близкие понимали логику вмешательств и не тревожились по поводу непредвиденных «сюрпризов». Карта ниже — ориентир; конкретные параметры врач уточнит после осмотра.
Узнать больше – https://vyvod-iz-zapoya-pervouralsk0.ru/vyvod-iz-zapoya-na-domu-pervouralsk
Такой подход позволяет точно отслеживать динамику и вносить изменения в программу без потери контроля. Пациент видит прогресс, а врачи получают объективные данные о реакции организма на лечение.
Получить дополнительную информацию – наркологическая клиника наркологический центр ставрополь
Каждый этап лечения в наркологической клинике «ЮгМед Альянс» имеет свою цель, временные рамки и объективные критерии эффективности. Ниже приведена структура терапевтического цикла, применяемая для большинства пациентов после поступления в отделение.
Узнать больше – наркологическая клиника наркологический центр в ставрополе
На первом приёме врач-нарколог проводит осмотр, оценивает витальные показатели (АД, ЧСС, SpO2, температура), при показаниях — портативный ЭКГ-скрининг и экспресс-лабораторию, использует шкалы выраженности абстиненции и тревоги. Результаты сразу переводятся в план на ближайшие 72 часа: инфузионная поддержка или таблетированные режимы, «вечерний ритуал» для нормализации сна, карта триггеров и краткое психообразование. Дальше мы обсуждаем цели на 7 дней: что должно измениться и как мы это измерим (сон, тревога, «тяга», энергия, работоспособность).
Получить больше информации – http://narkologicheskaya-klinika-petrozavodsk0.ru
Выездной наркологический сервис «МедПоволжье Клиник» создан для случаев, когда важны скорость, тишина и клиническая точность. Мы проводим детоксикацию и снятие интоксикации на дому так, чтобы каждое действие имело цель, измеримый маркер и заранее оговорённое «окно переоценки». Вместо «сильной капельницы на всякий случай» — модульная схема: один симптом-кластер > один медицинский модуль > одна поведенческая опора (свет, звук, вода малыми глотками, дыхание 4–6). Такой подход снижает лекарственную нагрузку, ускоряет стабилизацию и позволяет видеть прогресс буквально по часам.
Получить дополнительные сведения – запой нарколог на дом в саратове
Команда «КарелМед Центра» объединяет наркологов, психиатров, реаниматологов, клинических психологов, специалистов по реабилитации и социальному сопровождению. Мы работаем без очередей и навязчивых формальностей, а логистика визита, оформление в стационар и коммуникации с родственниками выстроены бережно: конфиденциальные записи, немаркированные выезды, отдельный вход и нейтральная терминология в документах. Вы получаете не только купирование абстиненции и детоксикацию, но и системную работу с триггерами, привычками и межличностными конфликтами — тем, что часто возвращает к употреблению даже после «идеальных капельниц».
Узнать больше – наркологическая клиника лечение алкоголизма в петрозаводске
Терапия в клинике строится на системном подходе, позволяющем постепенно восстанавливать здоровье и формировать новые жизненные установки.
Детальнее – https://narcologicheskaya-klinika-perm0.ru/perm-narkologiya/
Хотя принципы лечения похожи, клиническая логика отличается. При алкогольной зависимости чаще нужен быстрый контроль вегетативных симптомов, восстановление сна и коррекция электролитов. При наркозависимости добавляются протоколы снижения импульсивности, работа с абстиненцией другой природы и расширенная психотерапевтическая часть. В обоих случаях результат не сводится к «капельнице»: мы учим распознавать ранние сигналы срыва, формировать безопасные ритуалы и поддерживать общение без давления и скрытых конфликтов.
Исследовать вопрос подробнее – анонимная наркологическая клиника в петрозаводске
Мы работаем без пауз и очередей, принимая пациентов в любое время суток. В распоряжении бригад — немаркированный транспорт для выезда на дом, портативная диагностика (ЭКГ, пульсоксиметрия, экспресс-анализаторы), а в стационаре — палаты с регулируемым микроклиматом и круглосуточный мониторинг жизненных показателей. Вся документация оформляется в нейтральной терминологии, доступ к данным разграничен по ролям, что защищает вашу анонимность.
Получить дополнительные сведения – вывод наркологическая клиника в ставрополе
На каждом этапе мы фиксируем объективные маркеры — от сатурации и вариабельности пульса до частоты «тяговых мыслей» в дневнике. Эти данные позволяют корректировать план не интуитивно, а по фактам.
Получить дополнительные сведения – вывод наркологическая клиника ставрополь
Для жителей Нижнего Тагила у нас организованы три параллельных канала помощи: очные визиты в клинику, «тихий» выезд на дом и защищённые телемедицинские консультации. Координатор уже при первом звонке уточняет ключевые риски (аллергии, хронические заболевания, эпизоды судорог/психозов, приём постоянных препаратов), бытовые условия (возможность обеспечить тишину на 2–3 часа, доступ к воде, особенности подъезда), а также предпочтения по конфиденциальности. Это позволяет врачу подготовить персональный стартовый протокол заранее и сократить время между осмотром и первой процедурой.
Подробнее можно узнать тут – наркологическая клиника в нижнем тагиле
В Ставрополе мы выстроили так называемую «тихую логистику»: запись без послеобеденных «окон», экспресс-приём без ожидания, сопровождение от входа до палаты, а при необходимости — деликатная госпитализация через отдельный вход. При первичном обращении пациент получает пошаговый план на ближайшие 72 часа: стабилизация самочувствия, детоксикация по показаниям, психообразование, старт профилактики срыва. Такой регламент экономит время и снижает тревожность — вы понимаете, что и зачем делается, и видите прогноз по срокам.
Выяснить больше – http://narcologicheskaya-klinika-stavropol0.ru/chastnaya-narkologicheskaya-klinika-stavropol/
Уже при первичном звонке мы собираем ключевую информацию: длительность употребления, типы веществ, сопутствующие заболевания, прошлые реакции на лекарства, эпизоды судорог и психозов, недавние значения АД/ЧСС. Это позволяет подготовить персональный стартовый протокол ещё до визита: поставить цель на первые 72 часа, определить метрики (сон, «тяга», дневная энергия), запланировать вечерний ритуал и расписать дистанционные чек-ины. Прозрачность шагов снижает тревогу у пациента и семьи и повышает соблюдаемость — фундамент устойчивого результата.
Исследовать вопрос подробнее – наркологическая клиника нарколог в каменске-уральске
Такой подход позволяет точно отслеживать динамику и вносить изменения в программу без потери контроля. Пациент видит прогресс, а врачи получают объективные данные о реакции организма на лечение.
Детальнее – http://narkologicheskaya-klinika-stavropol0.ru
В Нижнем Тагиле выездные бригады дежурят 24/7. Координатор уже при первичном звонке собирает ключевые сведения: аллергии, хронические заболевания, список постоянных препаратов, эпизоды судорог или алкогольных психозов в прошлом, последние значения давления и пульса, возможность обеспечить тишину на 2–3 часа, доступ к питьевой воде, особенности подъезда. Вся эта информация помогает врачу подготовить стартовую схему — от выбора профиля инфузии до темпа введения. По запросу организуем немаркированный визит и сдержанные формулировки в документах, чтобы не создавать лишнего внимания со стороны соседей и коллег.
Получить больше информации – vyvod-iz-zapoya-nizhnij-tagil0.ru/
Ниже — примерный «каркас» лечения. Он индивидуализируется по клинической картине, сопутствующим болезням, опыту прошлых попыток и бытовым ограничениям. Ключевой принцип — «одно вмешательство: одна цель — один маркер — одна дата проверки».
Получить больше информации – наркологические клиники алкоголизм в петрозаводске
Наркологическая клиника «СтавропольМед Резонанс» — это круглосуточный центр доказательной медицины, где помощь строится вокруг безопасности, конфиденциальности и персонализации. Мы объединяем медицинскую детоксикацию, психотерапию, реабилитационные практики и постлечебное сопровождение в единую дорожную карту восстановления. Каждый шаг лечения закреплён измеримыми критериями эффективности, а решения принимаются командно — от дежурного нарколога и клинического психолога до психиатра и реабилитолога.
Углубиться в тему – http://narcologicheskaya-klinika-stavropol0.ru/narkologicheskaya-klinika-stavropol-otzyvy/https://narcologicheskaya-klinika-stavropol0.ru
Уже при первичном звонке мы собираем ключевую информацию: длительность употребления, типы веществ, сопутствующие заболевания, прошлые реакции на лекарства, эпизоды судорог и психозов, недавние значения АД/ЧСС. Это позволяет подготовить персональный стартовый протокол ещё до визита: поставить цель на первые 72 часа, определить метрики (сон, «тяга», дневная энергия), запланировать вечерний ритуал и расписать дистанционные чек-ины. Прозрачность шагов снижает тревогу у пациента и семьи и повышает соблюдаемость — фундамент устойчивого результата.
Детальнее – наркологические клиники алкоголизм в каменске-уральске
На первом приёме врач-нарколог проводит осмотр, оценивает витальные показатели (АД, ЧСС, SpO2, температура), при показаниях — портативный ЭКГ-скрининг и экспресс-лабораторию, использует шкалы выраженности абстиненции и тревоги. Результаты сразу переводятся в план на ближайшие 72 часа: инфузионная поддержка или таблетированные режимы, «вечерний ритуал» для нормализации сна, карта триггеров и краткое психообразование. Дальше мы обсуждаем цели на 7 дней: что должно измениться и как мы это измерим (сон, тревога, «тяга», энергия, работоспособность).
Изучить вопрос глубже – https://narkologicheskaya-klinika-petrozavodsk0.ru/
Если к «окну оценки» динамика плато, мы корректируем один элемент — скорость/последовательность инфузии, вечерний ритуал или плотность сессий. Это защищает от полипрагмазии и делает вклад каждого шага читаемым.
Углубиться в тему – лечение в наркологической клинике в нижнем тагиле
Наркологическая клиника в Перми обеспечивает пациентам комфортные условия и профессиональное сопровождение. Врачи работают круглосуточно и соблюдают строгую конфиденциальность, что делает лечение доступным и безопасным.
Углубиться в тему – https://narcologicheskaya-klinika-perm0.ru/chastnaya-narkologicheskaya-klinika-perm
С первого контакта координатор уточняет: длительность запоя, виды алкоголя, аллергии, список текущих лекарств, эпизоды судорог или психозов в анамнезе, сердечно-сосудистые жалобы. На основании ответов команда подбирает безопасную схему старта и резервный план на случай усиления симптомов. Врач привозит портативный монитор для контроля АД/ЧСС/SpO2, глюкометр, набор инфузионных линий и расходников, а также средства для экспресс-коррекции тревоги по показаниям.
Получить дополнительную информацию – наркологический вывод из запоя первоуральск
Мы работаем по принципу «один визит — один измеримый результат». После инфузий пациент обычно отмечает облегчение головной боли, уменьшение тремора и тревоги, улучшение сна к ближайшей ночи. Если ситуация сложнее (длительный многодневный запой, выраженные соматические факторы), врач оставляет ступенчатый план на 24–48 часов с повторным визитом или переводом в стационарный блок по согласованию с пациентом и родными.
Подробнее тут – врач нарколог на дом ставрополь
Такая последовательность шагов позволяет врачу действовать точно и эффективно. Благодаря комплексному подходу пациент чувствует облегчение уже через 1–2 часа после начала терапии, а полное восстановление наступает в течение суток.
Ознакомиться с деталями – врач вывод из запоя в ставрополе
Наша команда видит задачу шире, чем просто снять интоксикацию: важно вернуть предсказуемое засыпание, успокоить вегетативную систему, снизить тревожность и объяснить семье, как мягко поддержать человека, не обесценивая и не провоцируя конфликты. Поэтому медицинские вмешательства поддержаны «сенсорной дисциплиной» (свет, тишина, отсутствие резких запахов), простыми ритуалами вечера и короткими чек-инами на следующий день. Такой формат помогает не только «пережить ночь», но и спокойно пройти первые двое суток, когда риск откатов особенно высок.
Получить дополнительные сведения – анонимный вывод из запоя нижний тагил
Мы не «перелечиваем» пациента процедурами. Любая мера начинается как проверяемая гипотеза с измеримыми маркерами. Ниже — опорная карта лечения. В реальности она персонализируется в зависимости от клинической картины, возраста, сопутствующих заболеваний и бытового графика.
Получить дополнительную информацию – лечение в наркологической клинике
Команда «КарелМед Центра» объединяет наркологов, психиатров, реаниматологов, клинических психологов, специалистов по реабилитации и социальному сопровождению. Мы работаем без очередей и навязчивых формальностей, а логистика визита, оформление в стационар и коммуникации с родственниками выстроены бережно: конфиденциальные записи, немаркированные выезды, отдельный вход и нейтральная терминология в документах. Вы получаете не только купирование абстиненции и детоксикацию, но и системную работу с триггерами, привычками и межличностными конфликтами — тем, что часто возвращает к употреблению даже после «идеальных капельниц».
Выяснить больше – http://narkologicheskaya-klinika-petrozavodsk0.ru
Маршрут всегда персонализируется, но опорная логика едина: оценить риски, снять интоксикацию и абстиненцию, восстановить сон, снизить тревожную и вегетативную реактивность, обучить прикладным навыкам и закрепить результат кодированием (если уместно), а затем удерживать курс через поддерживающие сессии. Ниже — ориентировочная карта первых суток: на визите она дополняется деталями и «окнами оценки» — моментами, когда мы сверяем достигнутый эффект и принимаем решение о коррекции одного параметра.
Выяснить больше – наркологическая клиника наркологический центр в нижнем тагиле
Вызов нарколога на дом — это безопасный и деликатный способ быстро купировать симптомы алкогольной интоксикации, стабилизировать самочувствие и начать восстановление без госпитализации. В наркологической клинике «МедЛиния Ставрополь» домашние визиты организованы как чёткий медицинский сервис: врач приезжает с портативной диагностикой, подбирает индивидуальный состав капельниц, контролирует витальные показатели и оставляет понятный план дальнейших действий. Все процедуры проводятся анонимно, а оформление документов и логистика построены так, чтобы не нарушать приватность пациента и его семьи.
Подробнее можно узнать тут – помощь нарколога на дому в ставрополе
Если дома действительно шумно (ремонт, маленькие дети, вечерние гости) или состояние нестабильно, предложим короткое наблюдение в клинике: отдельный вход, «тихий коридор», камерные посты, затем — возвращение домой и продолжение амбулаторного маршрута. Важен не формат, а предсказуемый результат: степень облегчения должна соответствовать целям этапа, а не множеству случайных факторов среды.
Детальнее – вывод из запоя на дому цена в нижнем тагиле
Чем раньше стартует детокс, тем мягче идёт восстановление. Даже один визит способен перевести состояние из «кризисного» в управляемое, а затем подключается поддержка психолога или амбулаторные встречи для закрепления эффекта.
Подробнее тут – нарколог на дом срочно
Врачи «СтаврМед Центра» работают круглосуточно, обеспечивая выезд нарколога на дом в течение короткого времени. Пациент может получить помощь в привычных условиях, не подвергаясь стрессу, связанному с госпитализацией. Все процедуры проводятся анонимно, с сохранением врачебной тайны. Благодаря такому подходу, лечение становится не только эффективным, но и максимально комфортным для человека, который решил прекратить запой и начать восстановление.
Детальнее – http://vyvod-iz-zapoya-stavropol0.ru
Инфузионная терапия в «ТагилМед Реал» — это точный инструмент под конкретный запрос: обезвоживание, вегетативная нестабильность, нарушения сна, «утренний туман». Состав и дозировки подбирает врач с учётом возраста, коморбидности и лекарственных взаимодействий. Важно понимать: больше компонентов не значит лучше; главная ценность — фокус и безопасность.
Получить дополнительную информацию – http://narkologicheskaya-klinika-nizhnij-tagil0.ru
Если дома действительно шумно (ремонт, маленькие дети, вечерние гости) или состояние нестабильно, предложим короткое наблюдение в клинике: отдельный вход, «тихий коридор», камерные посты, затем — возвращение домой и продолжение амбулаторного маршрута. Важен не формат, а предсказуемый результат: степень облегчения должна соответствовать целям этапа, а не множеству случайных факторов среды.
Углубиться в тему – нарколог на дом вывод из запоя в нижнем тагиле
Врачи «СтаврМед Центра» работают круглосуточно, обеспечивая выезд нарколога на дом в течение короткого времени. Пациент может получить помощь в привычных условиях, не подвергаясь стрессу, связанному с госпитализацией. Все процедуры проводятся анонимно, с сохранением врачебной тайны. Благодаря такому подходу, лечение становится не только эффективным, но и максимально комфортным для человека, который решил прекратить запой и начать восстановление.
Исследовать вопрос подробнее – вывод из запоя на дому цена ставрополь
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Уникальные данные только сегодня – https://yourfamilydoctor.co.in/fatty-liver-and-fibro-scan-camp
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Детальнее – https://thinx.tokyo/uncategorized/1
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Нажмите, чтобы узнать больше – https://khabarwani.com/mumbai-delhi-express-way-inogration
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
А что дальше? – https://toonpet.com/explore-essential
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Прочесть заключение эксперта – https://ouriken.com/blog/why-are-businesses-moving-to-the-cloud
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Изучить эмпирические данные – https://staffster.se/2016/03/08/slide-5
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Это стоит прочитать полностью – https://vsizambia.org/the-vsi-end-of-year-cleaning-exercise
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Всё, что нужно знать – https://cafeastrologico.com/mercurio-retrogrado-parte-i-los-planetas-parecen-detener-su-movimiento
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Где почитать поподробнее? – https://clarosconelagua.com/hello-world
Этот обзор дает возможность взглянуть на историю и науку под новым углом. Мы представляем редкие факты, неожиданные связи и значимые события, которые помогут вам глубже понять развитие цивилизации и роль человека в ней.
Кликни и узнай всё! – http://pbandjproject.org/holiday-laptop-giveaway
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Обратиться к источнику – https://rccgvcwalsall.org.uk/2021/12/06/what-is-the-difference-between-profit-and-revenue
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
ТОП-5 причин узнать больше – https://pulsedatahub.com/tutorials/deploy-machine-learning-model-using-flask
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Что ещё? Расскажи всё! – https://www.smartstudy.website/blog/knowledge/169
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Продолжить изучение – https://tinymart4u.com/exploring-atlantas-modern-homes
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Полная информация здесь – https://rossmacleodputting.com/player-coach-relationship
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Всё, что нужно знать – https://gironarealestate.com/antes-de-bajar-el-precio-prueba-con-pintura-blanca
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Практические советы ждут тебя – https://bravepath.org/the-great-grandson-of-legendary-abdulhamid-ii-dies
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Изучить эмпирические данные – https://gruz-taxi.com.ua/vantagnyk
В рамках лечения пациент получает медицинское наблюдение, психологическую поддержку и коррекцию метаболических нарушений, вызванных длительным употреблением алкоголя или наркотических веществ.
Детальнее – наркологическая клиника клиника помощь
Вывод из запоя в клинике в Екатеринбурге проводится с применением сертифицированных лекарственных препаратов, поддерживающих систем и методов индивидуальной терапии. Врачи используют физиологически безопасные комбинации растворов, витаминов и нейропротекторов, восстанавливающих работу центральной нервной системы. Инфузионная терапия проводится под контролем специалистов, что исключает возможность осложнений и обеспечивает быстрое улучшение состояния пациента.
Подробнее – наркологические клиники алкоголизм
Для наглядности приведена таблица, отражающая распространённые методы лечения и их цели:
Получить больше информации – частная наркологическая клиника самара
Процедура вывода из запоя в клинике в Казани проводится под строгим контролем специалистов. Главная цель — купировать симптомы интоксикации, нормализовать давление, сердечный ритм и восстановить обмен веществ. Используются препараты, способствующие детоксикации, а также витаминные комплексы и антиоксиданты, необходимые для поддержки работы печени и мозга.
Получить больше информации – https://narkologicheskaya-klinika-v-kazani16.ru/narkologicheskaya-klinika-kazan-otzyvy
Лечение в клинике строится на комплексной программе, которая сочетает медикаментозную терапию, психотерапевтические методы и социальную реабилитацию. Такой подход обеспечивает устойчивый результат и предотвращает повторные срывы. Пациент проходит курс под постоянным контролем специалистов, что позволяет отслеживать динамику состояния и корректировать терапию при необходимости.
Подробнее тут – наркологическая клиника лечение алкоголизма краснодар
Для наглядности ниже приведена таблица с основными направлениями медикаментозной терапии и их эффектами:
Подробнее тут – наркологическая клиника нарколог в самаре
Поэтапный подход помогает достичь устойчивых результатов и минимизировать вероятность рецидива, обеспечивая безопасность пациента на всех стадиях лечения.
Ознакомиться с деталями – наркологическая клиника стационар в самаре
Реабилитационные программы в наркологической клинике направлены на нормализацию обменных процессов, восстановление сна, эмоциональной стабильности и когнитивных функций. Для достижения этого используются методы физиотерапии, нутритивной поддержки и коррекции поведения. Основное внимание уделяется мотивации пациента, работе с созависимостью и обучению навыкам здорового взаимодействия с окружающей средой.
Разобраться лучше – наркологическая клиника
Сочетание медицинских и психотерапевтических мер создаёт устойчивую систему поддержки. Пациенты получают возможность постепенно восстановить утраченное здоровье и психологическую стабильность.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-v-kazani16.ru/klinika-narkologiya-kazan/
Такой подход позволяет сформировать устойчивую мотивацию и создать основу для дальнейшей социальной и психологической реабилитации, направленной на стабилизацию состояния пациента и возвращение его к полноценной жизни.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-v-spb16.ru/
Лечение в клинике строится на комплексной программе, которая сочетает медикаментозную терапию, психотерапевтические методы и социальную реабилитацию. Такой подход обеспечивает устойчивый результат и предотвращает повторные срывы. Пациент проходит курс под постоянным контролем специалистов, что позволяет отслеживать динамику состояния и корректировать терапию при необходимости.
Разобраться лучше – запой наркологическая клиника
Каждый пациент проходит несколько последовательных этапов, направленных на очищение организма, стабилизацию эмоционального состояния и формирование стойкой мотивации к трезвой жизни. Такой подход позволяет не только устранить физическую зависимость, но и укрепить психическую устойчивость.
Подробнее тут – http://narkologicheskaya-klinika-v-samare16.ru/narkologicheskij-dispanser-g-samara/
Капельница от запоя — это не «чудо-микс», а управляемая медицинская процедура с чёткими целями, окном оценки и понятными критериями остановки. В «ЮжУрал Детокс Центр» подход построен по принципу минимально достаточных вмешательств: сначала безопасность (дыхание, сознание, гемодинамика), потом переносимость воды и сбор нормального сна, а уже после — метаболическая поддержка и восстановление бытовой устойчивости. Такая логика исключает полипрагмазию, снижает риск нежелательных реакций и даёт семье прогнозируемую картину на ближайшие 24–72 часа. Мы не обещаем «мгновенного чуда» — мы предлагаем дисциплину маленьких шагов, которая с высокой вероятностью приводит к устойчивому результату.
Подробнее тут – капельница от запоя на дому недорого
Простая подготовка ускоряет принятие решений и повышает переносимость инфузии. Пожалуйста, сделайте это до приезда бригады — многие шаги занимают секунды, но экономят десятки минут в процессе.
Получить дополнительную информацию – вызвать капельницу от запоя на дому в челябинске
Для наглядности приведена таблица, отражающая распространённые методы лечения и их цели:
Исследовать вопрос подробнее – наркологическая клиника нарколог в самаре
Каждый пациент проходит несколько последовательных этапов, направленных на очищение организма, стабилизацию эмоционального состояния и формирование стойкой мотивации к трезвой жизни. Такой подход позволяет не только устранить физическую зависимость, но и укрепить психическую устойчивость.
Углубиться в тему – https://narkologicheskaya-klinika-v-samare16.ru/narkolog-i-psikhiatr-samara
Лечение в клинике строится на комплексной программе, которая сочетает медикаментозную терапию, психотерапевтические методы и социальную реабилитацию. Такой подход обеспечивает устойчивый результат и предотвращает повторные срывы. Пациент проходит курс под постоянным контролем специалистов, что позволяет отслеживать динамику состояния и корректировать терапию при необходимости.
Изучить вопрос глубже – наркологическая клиника нарколог краснодар
Этапность терапии позволяет проводить лечение безопасно, с контролем жизненных показателей и прогнозируемым восстановлением физического состояния. После выхода из запоя пациенту рекомендуется продолжить реабилитацию для предупреждения повторных нарушений.
Изучить вопрос глубже – http://narkologicheskaya-klinika-v-kazani16.ru/
Поэтапная структура терапии делает лечение контролируемым и прогнозируемым, минимизируя риски возникновения осложнений и повторных обострений зависимости.
Исследовать вопрос подробнее – наркологическая клиника нарколог санкт-петербург
Реабилитационные программы в наркологической клинике направлены на нормализацию обменных процессов, восстановление сна, эмоциональной стабильности и когнитивных функций. Для достижения этого используются методы физиотерапии, нутритивной поддержки и коррекции поведения. Основное внимание уделяется мотивации пациента, работе с созависимостью и обучению навыкам здорового взаимодействия с окружающей средой.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-v-ekb16.ru/narkologicheskaya-klinika-ekaterinburg-otzyvy/
Простая подготовка ускоряет принятие решений и повышает переносимость инфузии. Пожалуйста, сделайте это до приезда бригады — многие шаги занимают секунды, но экономят десятки минут в процессе.
Изучить вопрос глубже – http://kapelnicza-ot-zapoya-v-chelyabinske16.ru
Детокс — последовательность шагов, где каждый этап имеет цель и критерии безопасности. Мы начинаем с оценки рисков (кардиология, неврология, психическое состояние, возможные взаимодействия препаратов), продолжаем инфузионной терапией, корректируем электролиты и кислотно-щелочное равновесие, поддерживаем печень и нервную систему. Если присутствуют выраженная тревога и бессонница, подключаем короткие курсы седативной терапии с контролем побочных эффектов. Отдельный блок — профилактика осложнений: обезвоживание, аритмии, обострение гастрита и панкреатита, делирий. Каждое назначение — только после очной оценки и с учётом сопутствующих состояний.
Подробнее можно узнать тут – лучшая наркологическая клиника москва
Детокс — это управляемая последовательность действий: оценка рисков, инфузионная терапия, коррекция электролитов и КЩС, поддержка органов-мишеней, профилактика осложнений, затем переоценка с корректировкой схемы. Мы заранее обсуждаем «бытовой контур» на ближайшие дни: максимально спокойные вечера, дробное питание, отказ от перегрузок, перенос «триггерных» встреч, чтобы результат не рассыпался после первых суток.
Получить больше информации – наркологическая клиника цены
Преимущество стационара — предсказуемость и скорость. Рядом врач и медсестра, можно оперативно сдать анализы, сделать ЭКГ или дополнительные обследования, а главное — не «тянуть» с корректировкой схемы. В контролируемой среде быстрее нормализуются сон и аппетит, уходит тремор, снижается тревога. Для пациентов с сопутствующими диагнозами это особенно важно: диабет, гипертония, аритмии, хронические заболевания ЖКТ требуют аккуратной, согласованной тактики.
Детальнее – luchshaya-narkologicheskaya-klinika-moskva
Госпитализация разворачивается как последовательность шагов: приём и допуск к терапии, старт инфузий, мониторинг 24/7, регулярная переоценка и подготовка к выписке. Такой контур особенно важен пациентам с сопутствующими диагнозами (гипертония, ИБС, сахарный диабет, заболевания ЖКТ), где требуется деликатная настройка дозировок и темпа инфузий.
Углубиться в тему – где находится наркологическая клиника
С первого звонка администратор бережно собирает фактуру: сколько длится эпизод, что человек уже принимал за последние двое суток, как прошла ночь, есть ли помощник на вечер и ночь, какие хронические заболевания и аллергии известны. Дежурный врач оценивает риски и предлагает старт: анонимный визит на дом по Клину или немедленную госпитализацию. На месте проводится очная оценка и допуск к терапии, запускается инфузионная поддержка с мониторингом давления, пульса и сатурации, корректируется вода и электролиты, по показаниям — осторожная нормализация сна и симптом-контроль. Если картина нестабильна, переводим в стационар — это короче путь к безопасности, чем многочасовые попытки «пересидеть» дома.
Получить дополнительные сведения – chastnaya-narkologicheskaya-klinika
Корректная среда — половина успешной инфузии. Этот порядок действий помогает врачу быстрее принять решения, а пациенту — легче перенести первые часы.
Подробнее тут – нарколог на дом вывод самара
«Чистая Гармония» — это выездная и стационарная наркологическая помощь в одном маршруте: оперативный приезд врача на дом по Клину и району, аккуратный детокс с контролем жизненно важных показателей, стационар с круглосуточным наблюдением и подготовка к кодированию. Мы придерживаемся принципа клинической достаточности: никаких лишних процедур ради «видимости лечения» и никаких задержек с тем, что влияет на исход. Каждое назначение объясняем простыми словами, заранее согласуем смету и оставляем понятный план на 24–48 часов и первую неделю. Анонимность — базовый стандарт: выезд без опознавательных знаков, нейтральные формулировки в документах по запросу, ограниченный доступ к данным.
Выяснить больше – chastnaya-narkologicheskaya-klinika
После проведения процедур пациент чувствует заметное облегчение: исчезает головная боль, снижается тревожность, восстанавливается сон и аппетит. Это создаёт основу для дальнейшего прохождения курса лечения зависимости.
Подробнее можно узнать тут – частная наркологическая клиника нижний новгород
Главная задача — вернуть контроль над самочувствием мягко и последовательно. Мы не соревнуемся в дозах, а собираем устойчивую траекторию улучшения: каждый модуль терапии отвечает за одну цель и имеет своё «окно оценки». Если отклик ниже ожиданий — меняем ровно один параметр (темп, последовательность или поведенческий элемент среды), чтобы точно понимать, что помогло.
Получить больше информации – http://vyvod-iz-zapoya-v-kazani16.ru/vyvod-iz-zapoya-kazan-kruglosutochno/
Вывод из запоя на дому — это управляемый медицинский процесс, где каждая деталь имеет значение: от первичного осмотра и грамотного подбора инфузионного профиля до сенсорной дисциплины в помещении и чётких «окон оценки» результата. В наркологической клинике «СеверМед Трезвость» мы используем принцип минимально достаточных вмешательств: одна цель на этап, один измеримый маркер и одна корректировка за раз. Такой подход снижает нагрузку на организм, повышает предсказуемость и делает восстановление переносимым для пациента и его близких.
Получить дополнительную информацию – вывод из запоя капельница в санкт-петербурге
Капельница от запоя в клинике в Нижнем Новгороде является одним из ключевых методов детоксикации организма после длительного употребления алкоголя. Основная цель процедуры — быстрое и безопасное выведение токсинов, нормализация работы жизненно важных органов и стабилизация общего состояния пациента. Методика основана на внутривенном введении лекарственных растворов, которые восполняют дефицит жидкости, электролитов и витаминов, устраняя последствия интоксикации. Такой подход позволяет достичь значительного улучшения самочувствия уже в первые часы после начала терапии.
Изучить вопрос глубже – капельница от запоя
Для сохранения приватности мы ведём коммуникацию через одного доверенного представителя, используем нейтральные формулировки в документах, а инструкции выдаём в неброском виде. При невозможности создать тишину дома (ремонт, маленькие дети, гости) предложим краткий «тихий» стационар с отдельным входом и камерным режимом, после чего сопровождение вернётся в домашний формат.
Подробнее – http://vyvod-iz-zapoya-v-ekaterinburge16.ru/vyvod-iz-zapoya-na-domu-v-ekaterinburge/
Ниже — ориентир, который помогает видеть логику процесса. Это не жёсткий график: врач адаптирует точки и сроки под возраст, фоновые заболевания и исходное состояние.
Получить дополнительные сведения – narkologicheskaya-klinika-klinskij-rajon
Госпитализация разворачивается как последовательность шагов: приём и допуск к терапии, старт инфузий, мониторинг 24/7, регулярная переоценка и подготовка к выписке. Такой контур особенно важен пациентам с сопутствующими диагнозами (гипертония, ИБС, сахарный диабет, заболевания ЖКТ), где требуется деликатная настройка дозировок и темпа инфузий.
Получить дополнительную информацию – https://narkologicheskaya-klinika-sergiev-posad8.ru/anonimnaya-narkologicheskaya-klinika-v-sergievom-posade/
Детокс — последовательность шагов, где каждый этап имеет цель и критерии безопасности. Мы начинаем с оценки рисков (кардиология, неврология, психическое состояние, возможные взаимодействия препаратов), продолжаем инфузионной терапией, корректируем электролиты и кислотно-щелочное равновесие, поддерживаем печень и нервную систему. Если присутствуют выраженная тревога и бессонница, подключаем короткие курсы седативной терапии с контролем побочных эффектов. Отдельный блок — профилактика осложнений: обезвоживание, аритмии, обострение гастрита и панкреатита, делирий. Каждое назначение — только после очной оценки и с учётом сопутствующих состояний.
Получить дополнительную информацию – narkologicheskaya-moskva
Перед перечнем поясним логику: домашний визит уместен, когда обстановка безопасна, риски контролируемы и есть взрослый помощник на вечер и ночь. Ниже — ориентиры, при которых имеет смысл начать с выезда, а не со стационара.
Выяснить больше – vrach-narkolog
Перед таблицей отметим: это ориентиры по составу и назначению; конкретные решения принимает врач после осмотра и согласует с семьёй. Таблица нужна, чтобы одним взглядом понять логику вариантов и выбрать безопасный старт.
Подробнее тут – https://kapelnica-ot-zapoya-klin8.ru/kapelnica-ot-zapoya-v-klinu-s-vyezdom-na-dom
Главное — непрерывность и скорость принятия решений. Рядом врач и медсестра, доступ к диагностике и возможность точно настраивать темп инфузий, подбирать поддерживающие препараты, контролировать сон и уровень тревоги. Благодаря этому снижается риск осложнений, а восстановление идёт ровнее: меньше «качелей» днём и ночью.
Получить дополнительную информацию – https://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-anonimno-v-sergievom-posade
Наркологическая клиника в клинике в Нижнем Новгороде специализируется на диагностике, лечении и реабилитации пациентов с алкогольной и наркотической зависимостью. Основная цель деятельности учреждения — восстановление физического здоровья и психологической устойчивости человека, оказавшегося в состоянии зависимости. В клинике применяются современные методы терапии, доказавшие эффективность в медицинской практике. Все процедуры проводятся конфиденциально, с соблюдением медицинских стандартов и под контролем квалифицированных специалистов.
Ознакомиться с деталями – частная наркологическая клиника
В первые два часа после прибытия бригады важно не «сделать побольше», а принять наименьшее количество решений, которое реально меняет картину. Команда фиксирует базовую линию (ЧСС, АД, SpO?, температура, шкала тошноты/тремора), даёт антиеметический мост и запускает регидратацию. При тахикардии — добавляет антивегетативный контур. Семья получает сценарий ночи: когда приглушить свет, когда предложить воду, какие цифры на тонометре считать нормой и при каких — звонить. Такой протокол экономит время и силы, а главное — превращает вечер из хаотичного в управляемый, снижая риск ночных экстренных вызовов и «эмоциональных качелей».
Узнать больше – капельница от запоя
Ниже — рабочая матрица на первые часы. Она показывает, как клиническая гипотеза превращается в минимальный шаг, какие индикаторы берём под контроль и по какому сигналу меняем тактику или площадку. Таблица не заменяет очную оценку, но делает логику маршрута ясной для всей семьи.
Детальнее – https://narkolog-na-dom-v-samare16.ru/narkolog-samara-vyzov-na-dom
В «ЮжУрал Детокс Центр» инфузионная терапия собирается из модулей. Каждый модуль имеет одну цель, измеримый маркер и стоп-критерий. Мы избегаем одновременного подключения нескольких новых элементов, чтобы не потерять причинно-следственную связь. Ниже — примерная «сетка» компонентов; фактическая схема подбирается индивидуально, только по показаниям.
Выяснить больше – врач на дом капельница от запоя челябинск
Aw, this was an extremely good post. Spending some time and actual effort to create a top notch article… but what can I say… I put things off a whole lot and don’t manage to get nearly anything done.
номер временный
Для наглядности приведена таблица, отражающая распространённые методы лечения и их цели:
Углубиться в тему – https://narkologicheskaya-clinika-v-samare16.ru/chastnaya-narkologicheskaya-klinika-samara
Перед перечнем поясним логику: домашний визит уместен, когда обстановка безопасна, риски контролируемы и есть взрослый помощник на вечер и ночь. Ниже — ориентиры, при которых имеет смысл начать с выезда, а не со стационара.
Детальнее – наркологический диспансер воскресенск
Чтобы помощь была прозрачной и управляемой, каждый этап имеет цель, индикаторы безопасности и эффективности, а также понятное «окно оценки» результата. Коррекции проводятся «штучно», по правилу одного изменения — это защищает от полипрагмазии и позволяет читабельно видеть вклад каждого шага.
Получить больше информации – вывод из запоя
Первым шагом терапии является детоксикация — процедура очищения организма от продуктов распада алкоголя или наркотических веществ. Она проводится под контролем врача и помогает стабилизировать работу сердечно-сосудистой системы, печени и центральной нервной системы. Для поддержания здоровья используются инфузионные растворы, витамины, гепатопротекторы и препараты, снижающие тревожность.
Ознакомиться с деталями – наркологические клиники алкоголизм самара
Наркологическая клиника в клинике в Нижнем Новгороде использует многопрофильный подход, направленный на физическое и психологическое восстановление пациентов. После детоксикации проводится стабилизация обменных процессов, нормализация работы внутренних органов и поддержка нервной системы. Особое внимание уделяется коррекции поведения и мотивации пациента к отказу от употребления алкоголя или наркотиков.
Ознакомиться с деталями – https://narkologicheskaya-clinika-v-nizhnem-novgorode16.ru/narkolog-nizhnij-novgorod-na-dom
Поэтапное лечение помогает врачам контролировать процесс восстановления и своевременно корректировать терапию в зависимости от состояния пациента.
Получить дополнительную информацию – https://narkologicheskaya-klinika-v-samare16.ru/narkologicheskij-dispanser-g-samara/
Для наглядности ниже приведена таблица с основными направлениями медикаментозной терапии и их эффектами:
Получить дополнительные сведения – https://narkologicheskaya-klinika-v-samare16.ru
Вывод из запоя в клинике в Санкт-Петербурге осуществляется под круглосуточным медицинским контролем с применением современных методов инфузионной терапии, препаратов для восстановления обменных процессов и купирования синдрома отмены. Главной задачей врачей является восстановление баланса между физическим и психическим состоянием, предотвращение осложнений и стабилизация основных жизненных функций.
Ознакомиться с деталями – https://narkologicheskaya-klinika-v-spb16.ru/narkologicheskaya-bolnicza-sankt-peterburg
Реабилитационные мероприятия в клинике направлены на устранение соматических последствий зависимости, нормализацию когнитивных функций и восстановление социальной адаптации. Для этого используются современные методики физиотерапии, диетологической коррекции и психологического сопровождения, позволяющие закрепить достигнутые результаты лечения.
Разобраться лучше – лечение в наркологической клинике
Основой терапии является сочетание медицинских, психотерапевтических и социальных методов. Такой подход обеспечивает устранение не только физиологических последствий зависимости, но и её психологических причин. Врачи клиники разрабатывают индивидуальный план лечения, в котором учитываются стадия заболевания, общее состояние организма и личностные особенности пациента. Работа специалистов направлена на восстановление работы центральной нервной системы, обменных процессов и эмоционального баланса.
Подробнее – анонимная наркологическая клиника казань
Мы не ограничиваемся капельницей. Сервис включает организационные, клинические и поведенческие элементы, которые уменьшают хаос и ускоряют восстановление. Ниже — ключевые блоки, которые пациенты отмечают в отзывах как наиболее полезные и «приземлённые».
Подробнее можно узнать тут – психиатр нарколог на дом
Процедура вывода из запоя в клинике в Казани проводится под строгим контролем специалистов. Главная цель — купировать симптомы интоксикации, нормализовать давление, сердечный ритм и восстановить обмен веществ. Используются препараты, способствующие детоксикации, а также витаминные комплексы и антиоксиданты, необходимые для поддержки работы печени и мозга.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-v-kazani16.ru/klinika-narkologiya-kazan/
Мы работаем последовательностями, которые реально влияют на исход: допуск к терапии, инфузии с коррекцией электролитов и КЩС, поддержка органов-мишеней, профилактика осложнений, осторожная нормализация сна по показаниям, переоценка и настройка схемы, план на неделю с алгоритмами «если-то». Важно не «перелечивать»: избыточная седативная нагрузка опасна так же, как и её отсутствие. Поэтому темп и состав мы настраиваем под текущие параметры и динамику — и объясняем пациенту и семье, зачем именно выбран каждый шаг.
Детальнее – https://narkologicheskaya-klinika-klin8.ru
Главное в детоксе — последовательность. Сначала формулируется клиническая гипотеза (например, обезвоживание+вегетативная гиперактивация), затем подбирается минимальный набор вмешательств, который способен изменить ключевые маркеры в ближайшие 40–120 минут. Только при недостаточном ответе добавляется следующий модуль. Ниже — иллюстративная матрица, которая показывает, как принимаются решения в первые часы. Она не заменяет очную оценку, но помогает семье понимать логику действий и причины возможной эскалации.
Подробнее – http://kapelnicza-ot-zapoya-v-chelyabinske16.ru/kapelniczy-ot-pokhmelya-chelyabinsk/
Ниже — ориентир, который помогает видеть логику процесса. Это не жёсткий график: врач адаптирует точки и сроки под возраст, фоновые заболевания и исходное состояние.
Ознакомиться с деталями – http://narkologicheskaya-klinika-klin8.ru/chastnaya-narkologicheskaya-klinika-v-klinu/
Домашний формат уменьшает стресс и экономит время: не нужно ехать в клинику, скрывать визит от соседей или ждать в очереди. Врач приезжает без опознавательных знаков и не создаёт «медицинского шума». За один визит удаётся снять острые проявления, выстроить понятный план ночи и следующего утра, а также определить, нужна ли дополнительная диагностика. Такой маршрут часто оказывается короче и эффективнее, чем череда попыток «пересидеть» симптомы без медицинской поддержки.
Разобраться лучше – https://narkolog-na-dom-voskresensk8.ru/narkolog-na-dom-nedorogo-v-voskresenske
В клинике применяются современные методы лечения, включающие медикаментозную терапию, психотерапию и физиологическое восстановление. Такой подход позволяет достигнуть стойкого результата и предотвратить возвращение к употреблению алкоголя.
Изучить вопрос глубже – врача капельницу от запоя
Реабилитационные программы в наркологической клинике направлены на нормализацию обменных процессов, восстановление сна, эмоциональной стабильности и когнитивных функций. Для достижения этого используются методы физиотерапии, нутритивной поддержки и коррекции поведения. Основное внимание уделяется мотивации пациента, работе с созависимостью и обучению навыкам здорового взаимодействия с окружающей средой.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-v-ekb16.ru/chastnaya-narkologicheskaya-klinika-ekaterinburg
Главная задача — вернуть контроль над самочувствием мягко и последовательно. Мы не соревнуемся в дозах, а собираем устойчивую траекторию улучшения: каждый модуль терапии отвечает за одну цель и имеет своё «окно оценки». Если отклик ниже ожиданий — меняем ровно один параметр (темп, последовательность или поведенческий элемент среды), чтобы точно понимать, что помогло.
Детальнее – http://vyvod-iz-zapoya-v-kazani16.ru
Реабилитационные программы в наркологической клинике направлены на нормализацию обменных процессов, восстановление сна, эмоциональной стабильности и когнитивных функций. Для достижения этого используются методы физиотерапии, нутритивной поддержки и коррекции поведения. Основное внимание уделяется мотивации пациента, работе с созависимостью и обучению навыкам здорового взаимодействия с окружающей средой.
Изучить вопрос глубже – наркологическая клиника стационар екатеринбург
В Екатеринбурге бригады выезжают 24/7, покрывая как центральные районы, так и отдалённые кварталы. Координатор уточняет только то, что влияет на безопасность: принимаемые лекарства и дозы, аллергии, эпизоды судорог/психозов, исходные значения давления и пульса, а также бытовые условия — можно ли обеспечить «тихое окно» на 2–3 часа, есть ли свободная розетка и место для полулёжа. Врач приезжает с портативным мониторингом, расходными материалами и резервным планом на случай повышенной реактивности.
Узнать больше – вывод из запоя на дому недорого
Вывод из запоя на дому — это управляемый медицинский процесс, где каждая деталь имеет значение: от первичного осмотра и грамотного подбора инфузионного профиля до сенсорной дисциплины в помещении и чётких «окон оценки» результата. В наркологической клинике «СеверМед Трезвость» мы используем принцип минимально достаточных вмешательств: одна цель на этап, один измеримый маркер и одна корректировка за раз. Такой подход снижает нагрузку на организм, повышает предсказуемость и делает восстановление переносимым для пациента и его близких.
Получить дополнительную информацию – вывод из запоя дешево санкт-петербург
Реабилитация проходит в комфортных условиях, с постоянным наблюдением специалистов. Важным элементом является формирование новых привычек и социальных навыков, что способствует возвращению пациента к полноценной жизни.
Разобраться лучше – http://narkologicheskaya-clinika-v-nizhnem-novgorode16.ru
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Не упусти шанс – https://www.riachaonet.com.br/portal/10124
Лечение зависимости требует комплексного подхода, включающего медицинские, психологические и социальные меры. Каждый пациент проходит индивидуальную диагностику, по результатам которой подбирается схема терапии. Такой подход позволяет снизить риски осложнений и обеспечить стабильный результат.
Подробнее тут – http://narkologicheskaya-clinika-v-nizhnem-novgorode16.ru
Перед перечнем поясним логику: домашний визит уместен, когда обстановка безопасна, риски контролируемы и есть взрослый помощник на вечер и ночь. Ниже — ориентиры, при которых имеет смысл начать с выезда, а не со стационара.
Разобраться лучше – narkologicheskij-dispanser-voskresensk
Инфузионная терапия — это не просто «быстрый раствор витаминов». При запое страдает водно-электролитный баланс, «плавает» давление и пульс, нарастает тревога, нарушается сон, проявляются тошнота и тремор. Правильно собранная капельница в Клину помогает вернуть жидкость и электролиты, поддержать печень, снизить вегетативные проявления, мягко стабилизировать нервную систему и подготовить переход на пероральные схемы. Важно избегать избыточной седативной нагрузки и опасных сочетаний: то, что человеку «помогало раньше», может конфликтовать с его нынешними показателями. Поэтому каждое назначение мы увязываем с реальными цифрами осмотра и тем, что уже было принято за двое суток.
Получить дополнительные сведения – kapelnica-ot-zapoya-klin8.ru/
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Уточнить детали – https://webdetektivi.org/favicon_v
Чтобы сделать процесс понятным и управляемым, каждый шаг сопровождается измеримыми маркерами безопасности и эффективности. Корректировки — точечные, по правилу «одного изменения», что позволяет видеть вклад каждого действия и сохранять переносимость.
Узнать больше – платная наркологическая скорая помощь
«Чистая Гармония» — это выездная и стационарная наркологическая помощь в одном маршруте: оперативный приезд врача на дом по Клину и району, аккуратный детокс с контролем жизненно важных показателей, стационар с круглосуточным наблюдением и подготовка к кодированию. Мы придерживаемся принципа клинической достаточности: никаких лишних процедур ради «видимости лечения» и никаких задержек с тем, что влияет на исход. Каждое назначение объясняем простыми словами, заранее согласуем смету и оставляем понятный план на 24–48 часов и первую неделю. Анонимность — базовый стандарт: выезд без опознавательных знаков, нейтральные формулировки в документах по запросу, ограниченный доступ к данным.
Подробнее – http://narkologicheskaya-klinika-klin8.ru
Перед перечнем поясним логику: домашний визит уместен, когда обстановка безопасна, риски контролируемы и есть взрослый помощник на вечер и ночь. Ниже — ориентиры, при которых имеет смысл начать с выезда, а не со стационара.
Изучить вопрос глубже – http://narkolog-na-dom-voskresensk8.ru/narkolog-na-dom-nedorogo-v-voskresenske/
Капельница от запоя в клинике в Нижнем Новгороде является одним из ключевых методов детоксикации организма после длительного употребления алкоголя. Основная цель процедуры — быстрое и безопасное выведение токсинов, нормализация работы жизненно важных органов и стабилизация общего состояния пациента. Методика основана на внутривенном введении лекарственных растворов, которые восполняют дефицит жидкости, электролитов и витаминов, устраняя последствия интоксикации. Такой подход позволяет достичь значительного улучшения самочувствия уже в первые часы после начала терапии.
Получить дополнительную информацию – капельница от запоя нижний новгород
В первые два часа после прибытия бригады важно не «сделать побольше», а принять наименьшее количество решений, которое реально меняет картину. Команда фиксирует базовую линию (ЧСС, АД, SpO?, температура, шкала тошноты/тремора), даёт антиеметический мост и запускает регидратацию. При тахикардии — добавляет антивегетативный контур. Семья получает сценарий ночи: когда приглушить свет, когда предложить воду, какие цифры на тонометре считать нормой и при каких — звонить. Такой протокол экономит время и силы, а главное — превращает вечер из хаотичного в управляемый, снижая риск ночных экстренных вызовов и «эмоциональных качелей».
Ознакомиться с деталями – https://kapelnicza-ot-zapoya-v-chelyabinske16.ru/kapelnicza-ot-pokhmelya-na-domu-chelyabinsk
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Подробнее – вывод из запоя капельница
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Перейти к полной версии – https://ventensis.lt/why-automatic-driving-lessons-help-you-pass-faster-2
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Ознакомиться с теоретической базой – https://armangroup.af/hello-world
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Обратиться к источнику – https://aadi-india.org/who-we-are
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Откройте для себя больше – http://dev.pixelsharmony.com/2017/12/28/ui-inspiration-this-weeks-selections-from-claudio-guglieri-ela-kumela-gleb-kuznetsov-and-more
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Хочу знать больше – https://echoteam.am/project/revolutionizing-online-polling-with-web4-technology
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
ТОП-5 причин узнать больше – https://cadenavirtual.com.ar/cultura_educacion/2021/03/12/la-costa-se-suma-a-la-campana-nacional-plantamos-memoria-donde-los-vecinos-podran-apadrinar-600-arboles-nativos
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Ознакомиться с теоретической базой – https://www.one-clicktravel.com/lufthansa-business-class
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Открой скрытое – https://nevertheless.li/hallo-welt
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Это стоит прочитать полностью – https://dandanet.com/blog/%D8%B1%D9%88%D8%AA-%DA%A9%D8%A7%D9%86%D8%A7%D9%84-%D8%AF%D9%86%D8%AF%D8%A7%D9%86%D9%BE%D8%B2%D8%B4%DA%A9%DB%8C-%DA%86%DB%8C%D8%B3%D8%AA%D8%9F
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Заходи — там интересно – https://planetes360.fr/pourquoi-avez-vous-detruit-ma-vie-le-livre-choc-qui-derange-macron
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Хочешь знать всё? – https://www.real-estate-income.com/building-companies-gold-coast
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Проследить причинно-следственные связи – https://nnequipamentos.com.br/cristal-2
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Это стоит прочитать полностью – https://blog.agdastudios.com/2025/05/27/lorem-ipsum-dolor-sit-amet-consectetur-adipiscing-elit
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Прочесть заключение эксперта – https://www.knruhs.telangana.gov.in/faq-items/vivamus-id-ante-vel-purus-commodo-cursus-nunc-sit-amet-cursus-massa
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Это стоит прочитать полностью – https://eraphoenix.link/conheca-pintos
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Это ещё не всё… – https://foxy1069.com/2025/06/mariah-carey-releases-the-emancipation-of-mimi-20th-anniversary-edition
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Смотрите также… – https://www.sofiadovale.com/2018/05/30/a-beautiful-sunday-morning
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Исследовать вопрос подробнее – https://narcologicheskaya-klinika-omsk0.ru/narkologicheskaya-bolnicza-omsk
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Как достичь результата? – https://techideasweb.com/national-testing-network-gateway-to-careers-in-public-safety
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Все материалы собраны здесь – https://kingofworldwidenews.com/panduan-kami-cara-pasang-togel-online-jitu-di-indonesia
При домашнем старте врач начинает не с капельницы, а с среды: приглушает верхний свет, обеспечивает проветривание без сквозняка, предлагает маску/беруши при сенсорной чувствительности, переводит телефоны в «без уведомлений». На таком фоне инфузия переносится мягче, уменьшается тошнота, исчезают «рывки» ЧСС перед сном, а утром проходит ощущение «ваты» в голове.
Получить больше информации – запой наркологическая клиника
changan uni s https://changan-v-spb.ru
В первые два часа после прибытия бригады важно не «сделать побольше», а принять наименьшее количество решений, которое реально меняет картину. Команда фиксирует базовую линию (ЧСС, АД, SpO?, температура, шкала тошноты/тремора), даёт антиеметический мост и запускает регидратацию. При тахикардии — добавляет антивегетативный контур. Семья получает сценарий ночи: когда приглушить свет, когда предложить воду, какие цифры на тонометре считать нормой и при каких — звонить. Такой протокол экономит время и силы, а главное — превращает вечер из хаотичного в управляемый, снижая риск ночных экстренных вызовов и «эмоциональных качелей».
Узнать больше – капельница от запоя на дому в челябинске
В городе и ближайших районах клиника «УралМед Трезвость» обеспечивает оперативный выезд и амбулаторный приём без очередей. На этапе первичного контакта координатор уточняет только клинически значимые моменты: постоянные препараты и дозы, аллергии, эпизоды судорог/психозов в прошлом, базовые показатели (АД/ЧСС/SpO?, если доступны), длительность симптомов, возможность организовать «тихое окно» на 20–30 минут. Вместо долгих разговоров — короткая, спокойная логика: где безопаснее начать (дом/амбулатория/стационар), какую ближайшую цель выбираем, в каком интервале ждём эффект и что считаем сигналом для связи с дежурным врачом.
Получить дополнительную информацию – наркологическая клиника лечение алкоголизма челябинск
Капельницы в «ЧелМед Детокс» — это модульная конструкция, а не «микс на удачу». База — регидратация и коррекция электролитов. По показаниям добавляются антиэметики, антивегетативные средства, поддержка метаболизма, витамины группы B, магний. Отдельным блоком идёт ночной модуль: задача — собрать восстановительный сон, не «перелечивая» пациента. Каждый модуль имеет свою цель и стоп-критерий. Врач избегает одновременного запуска нескольких новых элементов, чтобы видеть причинно-следственную связь и точно понимать, что именно работает у конкретного человека.
Получить дополнительные сведения – помощь вывод из запоя
Процесс лечения в клинике организован последовательно и направлен на восстановление всех систем организма. Каждый этап имеет свои задачи и методы, что обеспечивает максимальную эффективность терапии.
Подробнее тут – https://narkologicheskaya-clinika-v-samare16.ru/
Детокс — это управляемая последовательность действий: оценка рисков, инфузионная терапия, коррекция электролитов и КЩС, поддержка органов-мишеней, профилактика осложнений, затем переоценка с корректировкой схемы. Мы заранее обсуждаем «бытовой контур» на ближайшие дни: максимально спокойные вечера, дробное питание, отказ от перегрузок, перенос «триггерных» встреч, чтобы результат не рассыпался после первых суток.
Исследовать вопрос подробнее – анонимная наркологическая клиника
«Чистая Гармония» — это выездная и стационарная наркологическая помощь в одном маршруте: оперативный приезд врача на дом по Клину и району, аккуратный детокс с контролем жизненно важных показателей, стационар с круглосуточным наблюдением и подготовка к кодированию. Мы придерживаемся принципа клинической достаточности: никаких лишних процедур ради «видимости лечения» и никаких задержек с тем, что влияет на исход. Каждое назначение объясняем простыми словами, заранее согласуем смету и оставляем понятный план на 24–48 часов и первую неделю. Анонимность — базовый стандарт: выезд без опознавательных знаков, нейтральные формулировки в документах по запросу, ограниченный доступ к данным.
Получить больше информации – наркологическая клиническая больница
Этапы терапии выглядят следующим образом:
Разобраться лучше – https://narkologicheskaya-klinika-v-samare16.ru
Госпитализация разворачивается как последовательность шагов: приём и допуск к терапии, старт инфузий, мониторинг 24/7, регулярная переоценка и подготовка к выписке. Такой контур особенно важен пациентам с сопутствующими диагнозами (гипертония, ИБС, сахарный диабет, заболевания ЖКТ), где требуется деликатная настройка дозировок и темпа инфузий.
Получить больше информации – http://narkologicheskaya-klinika-sergiev-posad8.ru/
Ниже — ориентир, который помогает видеть логику процесса. Это не жёсткий график: врач адаптирует точки и сроки под возраст, фоновые заболевания и исходное состояние.
Выяснить больше – https://narkologicheskaya-klinika-klin8.ru/chastnaya-narkologicheskaya-klinika-v-klinu/
Мы выстраиваем помощь как маршрут, а не разовую «капельницу». После первого звонка администратор собирает краткий чек-лист (длительность эпизода, хронические заболевания, принятые препараты, аллергии), передаёт дежурному врачу, и тот предлагает безопасный старт: визит на дому в пределах Сергиева Посада и района или сразу стационар. Выбор зависит от клинических рисков и бытовых условий: есть ли спокойная комната, помощник на ночь, насколько выражены симптомы.
Получить дополнительные сведения – gde-nahoditsya-narkologicheskaya-klinika
Запой — это не только выраженная тяга к алкоголю, но и комплекс физиологических нарушений: обезвоживание, колебания давления, тахикардия, бессонница, тремор, дефициты электролитов. Чем дольше длится эпизод, тем выше риск делирия и декомпенсаций. Мы оцениваем картину целиком: стаж употребления, фоновые болезни, уже принятые препараты, прошлые эпизоды судорог или потерь сознания. По итогам первичной беседы врач рекомендует формат старта — визит на дому или стационар.
Получить дополнительные сведения – http://www.domen.ru
Мы переводим субъективные ощущения в простые маркеры, чтобы решения не зависели от настроения и ожиданий. Базовый набор: объём выпитой воды в час; ЧСС/АД в покое; длительность сна и число пробуждений; шкалы тошноты/тремора/тревоги; две утренние бытовые задачи. В отчёте фиксируется, какой модуль включён, какой маркер он должен сдвинуть, в каком окне мы проверяем результат и при каком значении модуль выключается. Это защищает от «инерции лечения» и делает финансовую часть предсказуемой: расширения назначаются только по показаниям с указанием цели и времени переоценки.
Детальнее – http://narkolog-na-dom-v-krasnodare16.ru
Капельница, устанавливаемая наркологом на дому в Челябинске, помогает быстро очистить организм от токсинов и нормализовать водно-солевой баланс. Растворы включают витамины, анальгетики, седативные и гепатопротекторные препараты. Эффект от процедуры ощущается уже через 20–30 минут. Капельница снижает головную боль, устраняет тошноту, восстанавливает работу печени и сердечно-сосудистой системы. Такой метод считается одним из самых эффективных способов вывести пациента из запойного или абстинентного состояния без визита в стационар.
Подробнее можно узнать тут – помощь нарколога на дому в челябинске
«Чистая Гармония» — это выездная и стационарная наркологическая помощь в одном маршруте: оперативный приезд врача на дом по Клину и району, аккуратный детокс с контролем жизненно важных показателей, стационар с круглосуточным наблюдением и подготовка к кодированию. Мы придерживаемся принципа клинической достаточности: никаких лишних процедур ради «видимости лечения» и никаких задержек с тем, что влияет на исход. Каждое назначение объясняем простыми словами, заранее согласуем смету и оставляем понятный план на 24–48 часов и первую неделю. Анонимность — базовый стандарт: выезд без опознавательных знаков, нейтральные формулировки в документах по запросу, ограниченный доступ к данным.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-klin8.ru/kruglosutochnaya-narkologicheskaya-klinika-v-klinu/
В клинике применяются комплексные программы, включающие медицинскую детоксикацию, психотерапевтическую поддержку и социальную реабилитацию. Медицинская детоксикация проводится с использованием современных препаратов и методик, что позволяет снизить тяжесть абстинентного синдрома и минимизировать риски для здоровья пациента. Подробнее о методах детоксикации можно узнать на официальном портале Министерства здравоохранения России.
Получить больше информации – наркологическая клиника цены
Ich bin komplett hin und weg von SpinBetter Casino, es bietet einen einzigartigen Kick. Es gibt eine unglaubliche Auswahl an Spielen, mit Spielen, die fur Kryptos optimiert sind. Die Agenten sind blitzschnell, bietet klare Losungen. Die Transaktionen sind verlasslich, gelegentlich zusatzliche Freispiele waren ein Highlight. In Kurze, SpinBetter Casino garantiert hochsten Spa? fur Online-Wetten-Fans ! Zusatzlich das Design ist ansprechend und nutzerfreundlich, was jede Session noch besser macht. Besonders toll die mobilen Apps, die das Spielen noch angenehmer machen.
https://spinbettercasino.de/|
Ich liebe die Atmosphare bei Cat Spins Casino, es bietet ein mitrei?endes Spielerlebnis. Es gibt eine enorme Vielfalt an Spielen, mit Spielen, die Krypto unterstutzen. Er macht den Einstieg unvergesslich. Verfugbar 24/7 fur alle Fragen. Transaktionen sind zuverlassig und effizient, ab und zu gro?ere Angebote waren super. Letztlich, Cat Spins Casino bietet ein unvergessliches Erlebnis. Nebenbei die Seite ist schnell und einladend, das Vergnugen maximiert. Ein bemerkenswertes Feature ist das VIP-Programm mit einzigartigen Belohnungen, die die Begeisterung steigern.
http://www.catspinsbonus.com|
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Углубиться в тему – http://vyvod-iz-zapoya-sergiev-posad8.ru
Je ne me lasse pas de Ruby Slots Casino, on y trouve une vibe envoutante. Il y a une abondance de jeux excitants, offrant des sessions live immersives. Il donne un avantage immediat. Le support est fiable et reactif. Les retraits sont fluides et rapides, quelquefois des bonus diversifies seraient un atout. En conclusion, Ruby Slots Casino offre une experience hors du commun. Pour couronner le tout l’interface est simple et engageante, facilite une immersion totale. Un avantage notable les options variees pour les paris sportifs, cree une communaute vibrante.
Commencer ici|
J’adore l’ambiance electrisante de Sugar Casino, ca invite a plonger dans le fun. Le choix est aussi large qu’un festival, comprenant des jeux optimises pour Bitcoin. Avec des depots rapides et faciles. Disponible 24/7 pour toute question. Le processus est simple et transparent, par ailleurs plus de promos regulieres ajouteraient du peps. En somme, Sugar Casino garantit un plaisir constant. Pour ajouter l’interface est lisse et agreable, amplifie l’adrenaline du jeu. Egalement top les evenements communautaires dynamiques, propose des privileges sur mesure.
Commencer maintenant|
J’adore l’energie de Sugar Casino, ca pulse comme une soiree animee. Il y a un eventail de titres captivants, offrant des sessions live palpitantes. Le bonus initial est super. Le service client est excellent. Les retraits sont ultra-rapides, a l’occasion des recompenses additionnelles seraient ideales. En fin de compte, Sugar Casino offre une experience hors du commun. A mentionner le site est rapide et style, donne envie de continuer l’aventure. Egalement top les paiements securises en crypto, offre des bonus exclusifs.
Essayer|
Стационар рационален при нестабильном состоянии, риске делирия, судорогах в анамнезе, скачках давления, выраженной одышке, неукротимой рвоте, одиночестве ночью или невозможности обеспечить «тихий режим». В палате — контролируемая среда, доступ к ЭКГ и базовой лаборатории по показаниям, круглосуточный пост медсестёр и возможность быстро менять тактику, если параметры «плывут». Такой маршрут предсказуемее по безопасности и зачастую короче по времени до стабильного самочувствия.
Изучить вопрос глубже – kapelnica-ot-zapoya-v-stacionare
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Углубиться в тему – http://narkolog-na-dom-voskresensk8.ru
В клинике применяются современные медицинские технологии, которые обеспечивают стойкий результат. Используемые методики соответствуют международным стандартам и регулярно обновляются.
Получить дополнительную информацию – наркологическая клиника цены омск
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Углубиться в тему – https://vyvod-iz-zapoya-moskva8.ru/vyvod-iz-zapoya-v-moskve-srochno/
Мы выстраиваем помощь как маршрут, а не разовую «капельницу». После первого звонка администратор собирает краткий чек-лист (длительность эпизода, хронические заболевания, принятые препараты, аллергии), передаёт дежурному врачу, и тот предлагает безопасный старт: визит на дому в пределах Сергиева Посада и района или сразу стационар. Выбор зависит от клинических рисков и бытовых условий: есть ли спокойная комната, помощник на ночь, насколько выражены симптомы.
Выяснить больше – narkologicheskaya-klinika-ceny-adresa
Мы выстраиваем помощь как маршрут, а не разовую «капельницу». После первого звонка администратор собирает краткий чек-лист (длительность эпизода, хронические заболевания, принятые препараты, аллергии), передаёт дежурному врачу, и тот предлагает безопасный старт: визит на дому в пределах Сергиева Посада и района или сразу стационар. Выбор зависит от клинических рисков и бытовых условий: есть ли спокойная комната, помощник на ночь, насколько выражены симптомы.
Ознакомиться с деталями – http://narkologicheskaya-klinika-sergiev-posad8.ru/anonimnaya-narkologicheskaya-klinika-v-sergievom-posade/
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Получить больше информации – вывод из запоя москве
Для жителей Краснодара и ближайших районов организованы два параллельных маршрута: немаркированный выезд врача-нарколога на дом и «тихий вход» в амбулаторный кабинет с отдельной дверью и согласованным слотом. На первичном звонке диспетчер фиксирует только факторы безопасности — частоту рвоты, наличие мочеиспусканий, базовые значения ЧСС/АД, эпизоды спутанности, список текущих препаратов и аллергии. Личные и социальные детали не запрашиваются: мы придерживаемся принципа минимально необходимой информации. На месте врач и медсестра собирают базовую линию (сознание, дыхание, SpO?, температура), оценивают шкалы симптомов (тошнота/тремор/тревога по шкале 0–10), проверяют переносимость небольших глотков воды и описывают ближайшие «окна» принятия решений. Вечером и ночью команда остаётся на связи: мы заранее согласовываем пороги, при которых нужно позвонить дежурному врачу, чтобы не терять критические минуты.
Подробнее можно узнать тут – http://narkolog-na-dom-v-krasnodare16.ru/narkologa-na-dom-krasnodar/
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Получить дополнительную информацию – вывод из запоя капельница
Госпитализация разворачивается как последовательность шагов: приём и допуск к терапии, старт инфузий, мониторинг 24/7, регулярная переоценка и подготовка к выписке. Такой контур особенно важен пациентам с сопутствующими диагнозами (гипертония, ИБС, сахарный диабет, заболевания ЖКТ), где требуется деликатная настройка дозировок и темпа инфузий.
Ознакомиться с деталями – narkologicheskaya-klinika-ceny-adresa
Домашний формат удобен, если нет признаков угрозы жизни и дома можно обеспечить спокойную обстановку. Врач приезжает без опознавательных знаков, начинает с очной оценки рисков и допуска к инфузионной терапии, сверяет принятые ранее препараты и аллергии, объясняет план действий и ожидаемую динамику. Далее запускается капельница: мягкая коррекция жидкости и электролитов, поддержка печени, симптом-контроль тревоги, тошноты, головной боли и тремора. На руки выдаются понятные рекомендации на 24–48 часов: питьевой режим, питание, сон, признаки тревоги и алгоритм связи с дежурным врачом.
Узнать больше – https://vyvod-iz-zapoya-moskva8.ru/vyvod-iz-zapoya-v-moskve-srochno
Выездная стабилизация — только первый шаг. Дальше важно разобрать триггеры, обучить «тихим ритуалам», согласовать план поддержки и рассмотреть кодирование там, где оно уместно. Мы не противопоставляем форматы: домашние визиты, «тихий вход» и краткие очные сессии дополняют друг друга. Задача — не создать идеальную «капельницу», а вернуть организму пространство для самостоятельной регуляции и укрепить навыки, которые защищают от срыва. В «КубаньМед Резолюция» этим занимается мультидисциплинарная команда: наркологи, специалисты интенсивной терапии, клинические психологи, психотерапевты и медсёстры с опытом ночных постов наблюдения. Все говорят на «языке фактов», чтобы решения были понятны и пациенту, и семье.
Подробнее можно узнать тут – http://narkolog-na-dom-v-krasnodare16.ru/
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Посмотреть всё – https://www.azzurriniguardese.it/2021/10/24/u19-gold-i-gg-girone-gold
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Хочешь знать всё? – https://bkk1radio.com/2025/02/14/destinys-child-reunites-for-kelly-rowlands-44th-birthday
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Как это работает — подробно – https://www.tassarnasfavorit.se/leksak_hundkongextreme-fr_79
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Почему это важно? – https://events-lemontsaintmichel.com/hello-world
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Изучить вопрос глубже – https://aei.eu/hello-world
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Изучить материалы по теме – https://emiratescasino.uk/cluster-tumble-slots-explosion
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Осуществить глубокий анализ – https://futurevisionhome.org/107594431_3256247741093203_5912719326632295535_o
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Хочу знать больше – https://pieib.com.my/2022/05/12/dealings-outside-closed-period
Этот обзор дает возможность взглянуть на историю и науку под новым углом. Мы представляем редкие факты, неожиданные связи и значимые события, которые помогут вам глубже понять развитие цивилизации и роль человека в ней.
Ознакомьтесь с аналитикой – http://trasvision.com.ar/boletin-de-noticias/nuevas-zonas-habilitadas-ftth
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Желаете узнать подробности? – https://leathernews.org/can-uncaged-innovations-5-6-million-bio-based-leather-alternative-be-the-next-big-thing-in-fashion-or-just-a-passing-trend
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Нажмите, чтобы узнать больше – https://nuewee.com/9-foods-that-helps-lower-blood-pressure
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Не упусти шанс – https://technoservice-me.com/spinia-no-deposit-bonus-10
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Кликни и узнай всё! – https://flaminkostudio.com/uncategorized/quote-post
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Посмотреть всё – https://www.ferienhaus-gohr.de/hello-world
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
А есть ли продолжение? – https://zeldzaamheid.nl/koffie
В Екатеринбурге нарколог из клиники «Детокс» может приехать прямо к вам домой. Помощь доступна в любое время суток.
Ознакомиться с деталями – vyzov-narkologa-na-dom ekaterinburg
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Продолжить чтение – https://gee-fit.com/product/geefit-mug-with-color-inside
Наши услуги в Ростове-на-Дону включают не только физическую детоксикацию, но и психологическую поддержку для более эффективного восстановления.
Изучить вопрос глубже – наркология вывод из запоя
В Ростове-на-Дону клиника «ЧСП№1» предлагает профессиональный вывод из запоя. Услуга доступна на дому и в стационаре, а также включает капельницу от похмелья. Все процедуры проводятся анонимно и круглосуточно.
Подробнее – нарколог вывод из запоя
В Ростове-на-Дону клиника «ЧСП№1» предлагает профессиональный вывод из запоя. Услуга доступна на дому и в стационаре, а также включает капельницу от похмелья. Все процедуры проводятся анонимно и круглосуточно.
Узнать больше – вывод из запоя вызов на дом ростов-на-дону
Палата — это контролируемая среда: аппаратный мониторинг, по показаниям ЭКГ и базовая лаборатория, пост медсестёр 24/7, переоценки по графику и быстрая коррекция тактики без логистических пауз. Такой старт рационален при длительных эпизодах, выраженных колебаниях давления и пульса, повторных судорогах, неукротимой рвоте и признаках надвигающегося делирия, а также если дома невозможно обеспечить «тихий режим» и присутствие взрослого помощника ночью. В стационарной ветке меньше случайностей, а путь до стабильного сна короче.
Получить дополнительную информацию – narkologicheskaya-klinika-moskva-besplatno
Дом — это тишина, отсутствие «социального шума» и лишних свидетелей. Выездной врач «НоваТонуса» приезжает анонимно, начинает с очной оценки и допуска к терапии, сверяет совместимости с тем, что человек принимал за последние двое суток, проверяет давление, пульс, сатурацию, температуру, кратко оценивает неврологический статус и уровень тревоги. Только после допуска запускается индивидуальная инфузионная поддержка: коррекция воды и электролитов, защита органов мишеней, симптом-контроль тошноты и головокружения, при показаниях — мягкая настройка сна без избыточной седации. В конце визита — переоценка, перевод на per os-схемы, памятка на 24–48 часов и заранее оговорённое окно контрольного контакта. Такой маршрут даёт устойчивую динамику на сутки и неделю, а не минутное облегчение.
Получить больше информации – narkologicheskaya-klinika-stacionar
Когда важно действовать сразу, время играет решающую роль. В Екатеринбурге служба Детокс реагирует в течение получаса-часа на вызов нарколога на дом, чтобы купировать сильное похмелье, остановить развитие опасных симптомов и предотвратить осложнения.
Выяснить больше – вызов врача нарколога на дом екатеринбург
Клиника «ЧСП№1» в Ростове-на-Дону предлагает услуги по выводу из запоя. Вы можете выбрать удобный для вас вариант: выезд нарколога на дом или лечение в стационаре. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее – анонимный вывод из запоя ростов-на-дону
J’adore a fond 7BitCasino, on dirait une experience de jeu electrisante. La selection de jeux est colossale, proposant des jeux de table elegants et classiques. Le service client est remarquable, joignable a toute heure. Les retraits sont ultra-rapides, bien que davantage de recompenses seraient appreciees, ou des promotions hebdomadaires plus frequentes. Pour conclure, 7BitCasino ne decoit jamais pour les passionnes de jeux numeriques ! Par ailleurs l’interface est fluide et retro, renforce l’immersion totale.
7bitcasino promo|
Ich bin total angetan von Cat Spins Casino, es bietet eine Welt voller Action. Das Angebot ist ein Paradies fur Spieler, mit aufregenden Live-Casino-Erlebnissen. 100 % bis zu 500 € mit Freispielen. Der Kundendienst ist ausgezeichnet. Gewinne kommen sofort an, trotzdem mehr regelma?ige Aktionen waren toll. Abschlie?end, Cat Spins Casino ist definitiv einen Besuch wert. Zudem die Seite ist zugig und ansprechend, eine immersive Erfahrung ermoglicht. Ein Hauptvorteil die spannenden Community-Aktionen, ma?geschneiderte Privilegien liefern.
Hineingehen|
Ich bin beeindruckt von SpinBetter Casino, es erzeugt eine Spielenergie, die fesselt. Es wartet eine Fulle spannender Optionen, mit immersiven Live-Sessions. Der Support ist 24/7 erreichbar, bietet klare Losungen. Der Ablauf ist unkompliziert, obwohl regelma?igere Aktionen waren toll. In Kurze, SpinBetter Casino garantiert hochsten Spa? fur Casino-Liebhaber ! Nicht zu vergessen die Interface ist intuitiv und modern, verstarkt die Immersion. Ein Pluspunkt ist die schnellen Einzahlungen, die Vertrauen schaffen.
spinbettercasino.de|
Je suis enthousiaste a propos de Sugar Casino, ca offre un plaisir vibrant. On trouve une profusion de jeux palpitants, proposant des jeux de casino traditionnels. Avec des depots rapides et faciles. Le support est rapide et professionnel. Le processus est fluide et intuitif, par contre des recompenses en plus seraient un bonus. Au final, Sugar Casino est un endroit qui electrise. Ajoutons que la navigation est fluide et facile, ajoute une touche de dynamisme. A mettre en avant les evenements communautaires pleins d’energie, offre des bonus constants.
Cliquer maintenant|
Наши услуги доступны всем жителям Ростова-на-Дону, обеспечивая доступность помощи для каждого пациента.
Исследовать вопрос подробнее – врач вывод из запоя
Мы обеспечиваем полную поддержку на всех этапах лечения в Ростове-на-Дону, включая реабилитацию и профилактику рецидивов.
Узнать больше – вывод из запоя круглосуточно ростов-на-дону
J’ai un veritable coup de c?ur pour Ruby Slots Casino, il procure une sensation de frisson. La bibliotheque de jeux est captivante, incluant des options de paris sportifs dynamiques. 100% jusqu’a 500 € avec des spins gratuits. Le service d’assistance est au point. Le processus est clair et efficace, neanmoins des recompenses supplementaires dynamiseraient le tout. Pour faire court, Ruby Slots Casino garantit un plaisir constant. Notons egalement la plateforme est visuellement dynamique, apporte une energie supplementaire. Egalement top les evenements communautaires dynamiques, garantit des paiements securises.
Explorer maintenant|
В клинике «Частный Медик 24» в Ростове-на-Дону вы получите комплексное лечение, направленное на восстановление организма и предотвращение рецидивов.
Изучить вопрос глубже – наркология вывод из запоя
Мы обеспечиваем полную поддержку на всех этапах лечения в Ростове-на-Дону, включая реабилитацию и профилактику рецидивов.
Получить дополнительную информацию – вывод из запоя капельница ростов-на-дону
Алкогольный эпизод — это не один симптом, а целая сцепка процессов: обезвоживание, электролитные сдвиги, скачки давления и пульса, тремор, тошнота, тревога, нарушения сна; нередко добавляются проблемы со стороны желудка и печени. Шаблонная капельница игнорирует индивидуальную картину и часто даёт кратковременный эффект с ночным откатом. Мы работаем иначе: допускаем к терапии, подбираем состав и темп инфузии под текущие цифры и динамику, избегаем конфликтов с уже принятыми препаратами и объясняем, чего ожидать по ощущениям на каждом шаге. Избыточная седация не усиливает лечение — она делает его менее предсказуемым.
Узнать больше – наркологическая клиника лобня
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Изучить вопрос глубже – вывод из запоя на дому цена
J’adore la vibe de Ruby Slots Casino, ca pulse comme une soiree animee. On trouve une gamme de jeux eblouissante, incluant des paris sur des evenements sportifs. 100% jusqu’a 500 € avec des spins gratuits. Le support est pro et accueillant. Les transactions sont toujours fiables, par ailleurs des recompenses supplementaires seraient parfaites. Au final, Ruby Slots Casino est un immanquable pour les amateurs. Notons egalement la navigation est intuitive et lisse, donne envie de continuer l’aventure. Egalement genial les transactions en crypto fiables, cree une communaute vibrante.
Visiter pour plus|
Мы обеспечиваем полную поддержку на всех этапах лечения в Ростове-на-Дону, включая реабилитацию и профилактику рецидивов.
Узнать больше – вывод из запоя капельница на дому
Мы предлагаем различные программы лечения в Ростове-на-Дону, включая стационарное и амбулаторное, чтобы выбрать оптимальный вариант для вас.
Получить дополнительную информацию – помощь вывод из запоя ростов-на-дону
Наши специалисты в Ростове-на-Дону готовы ответить на все ваши вопросы и предоставить подробную информацию о процессе лечения.
Исследовать вопрос подробнее – помощь вывод из запоя
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Получить больше информации – вывод из запоя вызов на дом нижний новгород
Мы обеспечиваем полную поддержку на всех этапах лечения в Ростове-на-Дону, включая реабилитацию и профилактику рецидивов.
Подробнее – вывод из запоя на дому недорого в ростове-на-дону
Ich liebe die Atmosphare bei Cat Spins Casino, es ist ein Ort voller Energie. Die Spielauswahl ist beeindruckend, mit stilvollen Tischspielen. Er macht den Start aufregend. Der Service ist immer zuverlassig. Transaktionen sind zuverlassig und effizient, dennoch mehr Promo-Vielfalt ware toll. In Summe, Cat Spins Casino ist ein Top-Ziel fur Spieler. Au?erdem ist das Design modern und einladend, einen Hauch von Eleganz hinzufugt. Ein gro?er Pluspunkt die lebendigen Community-Events, reibungslose Transaktionen sichern.
Jetzt zugreifen|
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Получить дополнительную информацию – вывод из запоя капельница нижний новгород
Наши специалисты в Ростове-на-Дону имеют многолетний опыт работы в области наркологии и готовы помочь вам на каждом этапе лечения.
Узнать больше – наркологический вывод из запоя
влияние поведенческих факторов
https://www.algoritmyseo.ru
В клинике «Частный Медик 24» в Ростове-на-Дону вы получите комплексное лечение, направленное на восстановление организма и предотвращение рецидивов.
Углубиться в тему – врач вывод из запоя
Длительное злоупотребление спиртным неизбежно приводит к серьёзным последствиям для организма. Алкоголь влияет на работу практически всех внутренних органов: печень испытывает повышенную нагрузку при выводе токсинов, почки страдают от нарушения водно-солевого баланса, а сердечно-сосудистая система подвержена скачкам давления и аритмиям. Постепенно ухудшается общее самочувствие – возникают постоянные головные боли, слабость, повышенная раздражительность, бессонница.
Получить дополнительные сведения – вывод из запоя капельница на дому
Клиника «Детокс» в Екатеринбурге оказывает услугу вызова нарколога прямо к вам домой. Специалисты приедут в течение часа.
Получить дополнительные сведения – нарколог на дом екатеринбург
Наши специалисты в Ростове-на-Дону имеют многолетний опыт работы в области наркологии и готовы помочь вам на каждом этапе лечения.
Изучить вопрос глубже – вывод из запоя капельница на дому
В Ростове-на-Дону мы гарантируем полную анонимность и конфиденциальность на всех этапах лечения, без постановки на учёт. Клиника в Ростове-на-Дону работает круглосуточно, обеспечивая доступность помощи в любое время дня и ночи.
Углубиться в тему – вывод из запоя вызов ростов-на-дону
Этап
Подробнее можно узнать тут – vyvod-iz-zapoya-rajon
Наши специалисты в Ростове-на-Дону готовы ответить на все ваши вопросы и предоставить подробную информацию о процессе лечения.
Детальнее – вывод из запоя вызов
Наши услуги в Ростове-на-Дону включают не только физическую детоксикацию, но и психологическую поддержку для более эффективного восстановления.
Получить дополнительные сведения – вывод из запоя вызов в ростове-на-дону
Мы стремимся к тому, чтобы каждый наш пациент в Ростове-на-Дону почувствовал заботу и внимание, получая качественную медицинскую помощь.
Углубиться в тему – вывод из запоя на дому круглосуточно
В Екатеринбурге клиника «Детокс» предлагает круглосуточный вызов нарколога на дом. Врач приедет быстро и поможет выйти из запоя.
Получить дополнительные сведения – нарколог на дом недорого
Лечение основывается на комплексном подходе, позволяющем учесть особенности организма и стаж злоупотребления алкоголем. Обычно процедура состоит из нескольких этапов:
Получить дополнительные сведения – https://narko-reabcentr.ru/vyvod-iz-zapoya-v-staczionare-moskva
Палата — это контролируемая среда: аппаратный мониторинг, по показаниям ЭКГ и базовая лаборатория, пост медсестёр 24/7, переоценки по графику и быстрая коррекция тактики без логистических пауз. Такой старт рационален при длительных эпизодах, выраженных колебаниях давления и пульса, повторных судорогах, неукротимой рвоте и признаках надвигающегося делирия, а также если дома невозможно обеспечить «тихий режим» и присутствие взрослого помощника ночью. В стационарной ветке меньше случайностей, а путь до стабильного сна короче.
Узнать больше – наркология лобня
«НоваТонус» — это связанный маршрут наркологической помощи для жителей Лобни и округа: оперативный выезд врача на дом, аккуратный домашний детокс без «универсальных коктейлей», стационар с круглосуточным наблюдением, подготовка к кодированию по показаниям и поддержка семьи в первые недели. Мы действуем по принципу клинической достаточности: каждое назначение обосновано, объясняется простым языком и привязано к реальным целям — безопасно снять интоксикацию и абстиненцию, стабилизировать давление и пульс, мягко вернуть сон, а затем провести первую «тихую» неделю без качелей. Приватность встроена в процесс: выезд без опознавательных знаков, нейтральный канал связи, документы по запросу и в сдержанной формулировке.
Ознакомиться с деталями – https://narkologicheskaya-klinika-lobnya8.ru/narkologicheskaya-klinika-ceny-v-lobne
В клинике «Детокс» в Екатеринбурге работает круглосуточный выезд нарколога. Это удобно и анонимно для пациента и его семьи.
Детальнее – нарколог на дом вывод из запоя в екатеринбурге
Длительность вывода из запоя во многом зависит от тяжести состояния, общего здоровья и продолжительности самого запоя. Если пациент обратился на ранней стадии, зачастую хватает 1-2 капельниц и короткого курса поддержки. Но при запое более пяти-семи дней, когда имеется острая интоксикация, требуется более продолжительная терапия и круглосуточное наблюдение.
Ознакомиться с деталями – помощь вывод из запоя в москве
Мы стремимся к тому, чтобы каждый наш пациент в Ростове-на-Дону почувствовал заботу и внимание, получая качественную медицинскую помощь.
Ознакомиться с деталями – срочный вывод из запоя ростов-на-дону
Мы обеспечиваем полную поддержку на всех этапах лечения в Ростове-на-Дону, включая реабилитацию и профилактику рецидивов.
Подробнее – скорая вывод из запоя в ростове-на-дону
В «Частном Медике 24» в Ростове-на-Дону мы заботимся о вашем здоровье и благополучии, предоставляя качественную медицинскую помощь.
Получить дополнительные сведения – наркологический вывод из запоя в ростове-на-дону
Домашний формат уместен, когда симптоматика контролируема и вечером рядом может остаться взрослый помощник. Преимущество Лобни — короткие дистанции внутри города, поэтому врач приезжает быстро, без шума и эмблем. На месте мы не торопимся: собеседование по факту последних 48 часов, измерения давления, пульса, сатурации и температуры, короткий неврологический скрининг, сверка аллергий и уже принятых препаратов. После допуска к терапии запускается инфузия: сначала — коррекция воды и электролитов, затем — поддержка печени и ЦНС, при необходимости — противорвотные и анксиолитические препараты. Темп настраивается по динамике, чтобы снять тремор и тошноту без «перекручивания» организма в сон с тяжёлым просыпанием. По итогам визита — понятные правила на 24–48 часов, список тревожных признаков и согласованное окно контрольного контакта. Домашний маршрут экономит часы, снижает социальную тревогу и делает первые сутки предсказуемыми.
Детальнее – https://vyvod-iz-zapoya-lobnya8.ru/vyvod-iz-zapoya-na-domu-v-lobne/
Дом — это тишина, отсутствие «социального шума» и лишних свидетелей. Выездной врач «НоваТонуса» приезжает анонимно, начинает с очной оценки и допуска к терапии, сверяет совместимости с тем, что человек принимал за последние двое суток, проверяет давление, пульс, сатурацию, температуру, кратко оценивает неврологический статус и уровень тревоги. Только после допуска запускается индивидуальная инфузионная поддержка: коррекция воды и электролитов, защита органов мишеней, симптом-контроль тошноты и головокружения, при показаниях — мягкая настройка сна без избыточной седации. В конце визита — переоценка, перевод на per os-схемы, памятка на 24–48 часов и заранее оговорённое окно контрольного контакта. Такой маршрут даёт устойчивую динамику на сутки и неделю, а не минутное облегчение.
Получить больше информации – https://narkologicheskaya-klinika-lobnya8.ru/narkologicheskaya-klinika-v-lobne-stacionar
Наши специалисты в Ростове-на-Дону имеют многолетний опыт работы в области наркологии и готовы помочь вам на каждом этапе лечения.
Получить больше информации – вывод из запоя на дому недорого в ростове-на-дону
Мы обеспечиваем комфортные условия для пребывания в клинике Ростова-на-Дону, чтобы восстановление прошло максимально эффективно.
Выяснить больше – анонимный вывод из запоя в ростове-на-дону
Мы предлагаем гибкую систему оплаты и прозрачные цены в Ростове-на-Дону, без скрытых платежей и переплат. Обратившись в нашу клинику в Ростове-на-Дону, вы делаете первый шаг к здоровой и трезвой жизни.
Исследовать вопрос подробнее – вывод из запоя вызов
Мы обеспечиваем комфортные условия для пребывания в клинике Ростова-на-Дону, чтобы восстановление прошло максимально эффективно.
Получить больше информации – вывод из запоя цена
В Ростове-на-Дону клиника «Частный Медик 24» предлагает профессиональный вывод из запоя с современными методами детоксикации и инфузионной терапии.
Ознакомиться с деталями – вывод из запоя с выездом ростов-на-дону
Длительное злоупотребление спиртным неизбежно приводит к серьёзным последствиям для организма. Алкоголь влияет на работу практически всех внутренних органов: печень испытывает повышенную нагрузку при выводе токсинов, почки страдают от нарушения водно-солевого баланса, а сердечно-сосудистая система подвержена скачкам давления и аритмиям. Постепенно ухудшается общее самочувствие – возникают постоянные головные боли, слабость, повышенная раздражительность, бессонница.
Подробнее – срочный вывод из запоя в москве
Мы понимаем, как важно быстро и эффективно выйти из запоя, поэтому в Ростове-на-Дону предлагаем оперативную помощь в любое время.
Получить дополнительную информацию – нарколог вывод из запоя в ростове-на-дону
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
https://kesrcp.com/2022/11/04/about-university-2
Этот обзор дает возможность взглянуть на историю и науку под новым углом. Мы представляем редкие факты, неожиданные связи и значимые события, которые помогут вам глубже понять развитие цивилизации и роль человека в ней.
Что ещё нужно знать? – https://dmceuropa.com/product/marshol-hand-sanitizer
В этой статье-обзоре мы соберем актуальную информацию и интересные факты, которые освещают важные темы. Читатели смогут ознакомиться с различными мнениями и подходами, что позволит им расширить кругозор и глубже понять обсуждаемые вопросы.
Полная информация здесь – https://ss-zemi.com/blog/1294
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Это ещё не всё… – https://sef.primegestao.com/enviamos-de-forma-automatica-os-boletins-de-entrada-junto-do-sef
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Нажми и узнай всё – https://plusprinting.bookplus.co.th/invitation-cards
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Познакомиться с результатами исследований – https://www.la-esperanzahotel.com/villa-lujo-la-esperanza-granada
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Получить профессиональную консультацию – http://www.jazzonthepark.fr/sortie-de-lalbum-attraction
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Практические советы ждут тебя – https://www.bodeguero.it/lorigine-delle-pappardelle
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Ознакомиться с теоретической базой – https://atorixit.in/index.php/2023/05/24/best-sap-implementation-partner-in-india
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Прочесть всё о… – https://abc1.com.br/som-automotivo-em-brasilia-e-entorno-do-df
Этот информационный материал привлекает внимание множеством интересных деталей и необычных ракурсов. Мы предлагаем уникальные взгляды на привычные вещи и рассматриваем вопросы, которые волнуют общество. Будьте в курсе актуальных тем и расширяйте свои знания!
Что скрывают от вас? – https://thelightandtheglory.com/2025/04/21/heaven-is-wide-open-to-you
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Не упусти важное! – https://jerusalemstoneart.com/product/mezuzah-shadai
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Эксклюзивная информация – https://saharatoursmarruecos.com/3-best-nature-weekend-tour-in-japan
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Почему это важно? – https://www.digital1now.com/2023/01/26/hello-world
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Всё, что нужно знать – https://printvizo.sk/albertova
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый мог разобраться в предмете и извлечь из него максимум пользы.
Узнать из первых рук – https://www.willi-food.co.il/en/product/gouda-rings-coated-with-breadcrumbs-1-kg-frozen-2
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Это ещё не всё… – https://acerko.com/portfolio/wooden-bench
Капельница при интоксикации помогает быстро очистить организм от продуктов распада алкоголя, восстановить водно-солевой баланс и улучшить самочувствие. В состав раствора входят препараты, нормализующие обмен веществ и поддерживающие работу печени и сердечно-сосудистой системы. Уже через 20–30 минут после начала инфузии пациент ощущает значительное облегчение. Подбор лекарственных средств осуществляется строго индивидуально, с учётом возраста, массы тела и общего состояния здоровья.
Разобраться лучше – выезд нарколога на дом уфа
Лечение организовано поэтапно. Такой подход обеспечивает постепенное восстановление функций организма и исключает риск осложнений. Каждый этап терапии направлен на устранение конкретных нарушений, вызванных интоксикацией.
Выяснить больше – наркология вывод из запоя в красноярске
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Разобраться лучше – наркологическая клиника цены красноярск
Капельница при интоксикации помогает быстро очистить организм от продуктов распада алкоголя, восстановить водно-солевой баланс и улучшить самочувствие. В состав раствора входят препараты, нормализующие обмен веществ и поддерживающие работу печени и сердечно-сосудистой системы. Уже через 20–30 минут после начала инфузии пациент ощущает значительное облегчение. Подбор лекарственных средств осуществляется строго индивидуально, с учётом возраста, массы тела и общего состояния здоровья.
Получить дополнительную информацию – http://narkolog-na-dom-v-ufe17.ru
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Изучить вопрос глубже – http://narkologicheskaya-klinika-v-krasnoyarske17.ru/krasnoyarsk-narkologicheskij-czentr/
Индивидуально подобранный состав раствора обеспечивает быстрое выведение токсинов и улучшение физического состояния уже в течение первых часов после начала лечения.
Исследовать вопрос подробнее – капельница от запоя на дому
Лечение организовано поэтапно. Такой подход обеспечивает постепенное восстановление функций организма и исключает риск осложнений. Каждый этап терапии направлен на устранение конкретных нарушений, вызванных интоксикацией.
Углубиться в тему – скорая вывод из запоя
Ниже приведена таблица с типовыми компонентами капельницы и их назначением:
Ознакомиться с деталями – kapelnicza-ot-zapoya-v-volgograde17.ru/
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Разобраться лучше – помощь нарколога на дому
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Узнать больше – наркологическая клиника вывод из запоя красноярск
Даже если симптомы кажутся незначительными, проведение инфузионной терапии значительно ускоряет процесс восстановления и предотвращает развитие осложнений.
Исследовать вопрос подробнее – вызвать капельницу от запоя волгоград
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Выяснить больше – вывод из запоя на дому недорого
Запой — это не один симптом. Это сдвиг водно-электролитного баланса, скачки давления и пульса, тремор, тошнота, тревога, бессонница, нередко раздражение слизистой желудка и нагрузка на печень. Мы работаем последовательностью: допуск к терапии, инфузионная поддержка с коррекцией воды и электролитов, защита органов-мишеней, симптом-контроль, при необходимости аккуратная нормализация сна, переоценка и перевод на пероральные схемы, затем — поведенческий контур «тихих» дней и, при информированном согласии, подготовка к кодированию. Это не «коктейль на всех», а управляемый процесс, завязанный на объективные показатели и живую динамику.
Исследовать вопрос подробнее – наркологическая м клиника
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Получить больше информации – помощь вывод из запоя в волгограде
Для тех, кто предпочитает лечение в условиях стационара, предусмотрены комфортные палаты, медицинский контроль 24/7 и возможность консультаций с психотерапевтом. Врачи клиники применяют комплексные методы, направленные не только на снятие симптомов, но и на устранение причин зависимости.
Исследовать вопрос подробнее – платная наркологическая помощь
Для жителей Красноярска организованы два конфиденциальных пути. Первый — немаркированный выезд бригады на дом с заранее согласованными порогами связи. Второй — «тихий вход» в клинику через отдельную дверь, где приём проходит без очередей и «коридорных» разговоров. На первичном звонке администратор уточняет только клинически значимые факторы: частоту рвоты, наличие мочеиспускания, ЧСС/АД в покое, эпизоды спутанности, актуальные лекарства и аллергии. Биографические подробности и лишние вопросы не задаются — мы придерживаемся принципа минимально необходимой информации.
Получить дополнительные сведения – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/chastnaya-narkologicheskaya-klinika-krasnoyarsk/
Estou completamente apaixonado por BacanaPlay Casino, parece uma festa carioca cheia de axe. A selecao de titulos do cassino e uma explosao de cores e ritmos, com caca-niqueis de cassino modernos e contagiantes. Os agentes do cassino sao rapidos como um passista na avenida, respondendo mais rapido que um batuque de pandeiro. Os pagamentos do cassino sao lisos e blindados, de vez em quando mais bonus regulares no cassino seria brabo. Na real, BacanaPlay Casino vale demais sambar nesse cassino para os apaixonados por slots modernos de cassino! De bonus a interface do cassino e fluida e reluz como uma fantasia de carnaval, faz voce querer voltar ao cassino como num desfile sem fim.
bacanaplay registo|
Капельницы от запоя включают препараты для очищения крови, восстановления электролитного баланса и защиты печени. Используются только сертифицированные растворы, одобренные Минздравом РФ. В клинике применяется комплексный подход: одновременно с физическим восстановлением запускаются лёгкие дыхательные и релаксационные методики, которые помогают организму вернуться в стабильное состояние.
Подробнее можно узнать тут – вывод из запоя цена воронеж
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Получить дополнительные сведения – вывод из запоя недорого волгоград
Ich habe einen Narren gefressen an Cat Spins Casino, es ist ein Ort voller Energie. Das Angebot an Titeln ist riesig, mit dynamischen Wettmoglichkeiten. Mit blitzschnellen Einzahlungen. Der Kundensupport ist erstklassig. Die Zahlungen sind sicher und effizient, aber mehr Aktionen waren ein Gewinn. Zum Schluss, Cat Spins Casino ist ein Ort fur pure Unterhaltung. Daruber hinaus die Plattform ist visuell ansprechend, eine vollstandige Immersion ermoglicht. Ein gro?artiges Plus die lebendigen Community-Events, schnelle Zahlungen garantieren.
Zur Website gelangen|
Запой — это не один симптом. Это сдвиг водно-электролитного баланса, скачки давления и пульса, тремор, тошнота, тревога, бессонница, нередко раздражение слизистой желудка и нагрузка на печень. Мы работаем последовательностью: допуск к терапии, инфузионная поддержка с коррекцией воды и электролитов, защита органов-мишеней, симптом-контроль, при необходимости аккуратная нормализация сна, переоценка и перевод на пероральные схемы, затем — поведенческий контур «тихих» дней и, при информированном согласии, подготовка к кодированию. Это не «коктейль на всех», а управляемый процесс, завязанный на объективные показатели и живую динамику.
Получить дополнительную информацию – rejting-narkologicheskih-klinik
Процедура начинается с осмотра пациента и оценки степени интоксикации. Врач измеряет давление, пульс, уровень насыщения крови кислородом, определяет наличие сопутствующих заболеваний. После диагностики назначается капельница, состав которой подбирается индивидуально. Процедура направлена на очищение организма, восстановление водно-солевого баланса и снятие симптомов похмелья.
Подробнее – наркология вывод из запоя тольятти
Ich bin abhangig von SpinBetter Casino, es liefert ein Abenteuer voller Energie. Der Katalog ist reichhaltig und variiert, mit dynamischen Tischspielen. Die Agenten sind blitzschnell, bietet klare Losungen. Die Transaktionen sind verlasslich, ab und an zusatzliche Freispiele waren ein Highlight. Zum Ende, SpinBetter Casino ist eine Plattform, die uberzeugt fur Online-Wetten-Fans ! Zusatzlich die Navigation ist kinderleicht, fugt Magie hinzu. Besonders toll die Sicherheit der Daten, die das Spielen noch angenehmer machen.
spinbettercasino.de|
Основу лечения составляет междисциплинарная команда: врач-нарколог, психиатр, психолог, медсестра и консультант по зависимому поведению. Каждый отвечает за свой участок работы, но общая цель едина — помочь пациенту безопасно пройти путь от детокса до устойчивого состояния. Благодаря единому плану и регулярным консилиумам врачей, исключаются противоречия и дублирование процедур. Это экономит ресурсы организма и делает процесс прогнозируемым.
Получить дополнительные сведения – https://narkologicheskaya-clinica-v-krasnoyarske17.ru/narkologicheskaya-klinika-krasnoyarsk-otzyvy/
Ни форма, ни машины с надписями, ни громкие атрибуты «скорой» — мы приезжаем тихо. Контакт в телефоне сохраняется с нейтральным названием, документы оформляются только по запросу и в сдержанной формулировке, доступ к данным внутри «ПрофДетокса» ограничен регламентами. Мы понимаем, что стыд и страх огласки часто тормозят обращение за помощью, поэтому приватность включена в стандарт и не влияет на стоимость.
Углубиться в тему – https://narkolog-na-dom-ivanteevka8.ru/pomoshch-narkologa-na-domu-v-ivanteevke
J’adore l’energie de Ruby Slots Casino, ca donne une vibe electrisante. Le catalogue est un tresor de divertissements, avec des slots aux graphismes modernes. Avec des depots fluides. Disponible 24/7 pour toute question. Le processus est transparent et rapide, cependant des bonus plus varies seraient un plus. Dans l’ensemble, Ruby Slots Casino assure un divertissement non-stop. En bonus l’interface est simple et engageante, ajoute une touche de dynamisme. Egalement genial les transactions en crypto fiables, assure des transactions fiables.
DГ©couvrir les faits|
Je suis totalement conquis par Sugar Casino, il offre une experience dynamique. Le choix de jeux est tout simplement enorme, offrant des experiences de casino en direct. Il donne un avantage immediat. Les agents repondent avec rapidite. Les paiements sont securises et rapides, malgre tout des offres plus genereuses seraient top. En resume, Sugar Casino merite un detour palpitant. Par ailleurs la plateforme est visuellement electrisante, booste l’excitation du jeu. Particulierement attrayant les tournois reguliers pour s’amuser, renforce la communaute.
Cliquer pour voir|
J’ai une passion debordante pour Ruby Slots Casino, ca invite a l’aventure. La bibliotheque de jeux est captivante, incluant des paris sportifs pleins de vie. Il donne un elan excitant. Disponible a toute heure via chat ou email. Les paiements sont surs et efficaces, rarement des offres plus consequentes seraient parfaites. En bref, Ruby Slots Casino offre une aventure memorable. A mentionner l’interface est simple et engageante, amplifie l’adrenaline du jeu. Un plus le programme VIP avec des avantages uniques, propose des avantages sur mesure.
Voir plus|
Ich schatze die Energie bei Cat Spins Casino, es bietet packende Unterhaltung. Die Spielesammlung ist uberwaltigend, mit stilvollen Tischspielen. 100 % bis zu 500 € inklusive Freispiele. Erreichbar rund um die Uhr. Transaktionen sind immer sicher, ab und zu gro?zugigere Angebote waren klasse. Insgesamt, Cat Spins Casino ist ein Ort fur pure Unterhaltung. Au?erdem die Oberflache ist glatt und benutzerfreundlich, jeden Augenblick spannender macht. Ein attraktives Extra die haufigen Turniere fur Wettbewerb, ma?geschneiderte Vorteile liefern.
Hineingehen|
Лечение основывается на комплексном подходе, позволяющем учесть особенности организма и стаж злоупотребления алкоголем. Обычно процедура состоит из нескольких этапов:
Подробнее тут – https://narko-reabcentr.ru/kruglosutochnyj-vyvod-iz-zapoya-v-moskve/
Безопасность — это не лозунг, а набор решений. Мы избегаем «жёстких» седативных доз, которые создают видимость улучшения и повышают риск скрытых осложнений. Наращивание темпа инфузии происходит постепенно и увязано с динамикой симптомов и цифрами измерений. Любой шаг объясняется пациенту и семье: зачем он выбран, что считается нормальной волной улучшения, в какой момент нужно связаться с дежурным. Такой прозрачный формат снимает тревогу и помогает всем участникам действовать согласованно.
Получить больше информации – narkolog-v-ivanteevke-chasy-raboty
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Изучить вопрос глубже – http://kapelnicza-ot-zapoya-v-volgograde17.ru/kapelnicza-ot-alkogolya-volgograd/
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Ознакомиться с деталями – https://kodirovanie-ot-alkogolizma-v-volgograde17.ru
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Ознакомиться с деталями – вызвать капельницу от запоя
Безопасность — это не лозунг, а набор решений. Мы избегаем «жёстких» седативных доз, которые создают видимость улучшения и повышают риск скрытых осложнений. Наращивание темпа инфузии происходит постепенно и увязано с динамикой симптомов и цифрами измерений. Любой шаг объясняется пациенту и семье: зачем он выбран, что считается нормальной волной улучшения, в какой момент нужно связаться с дежурным. Такой прозрачный формат снимает тревогу и помогает всем участникам действовать согласованно.
Изучить вопрос глубже – narkolog-na-dom
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Разобраться лучше – http://narkologicheskaya-klinika-v-krasnoyarske17.ru/narkologicheskaya-klinika-krasnoyarsk-otzyvy/https://narkologicheskaya-klinika-v-krasnoyarske17.ru
Во время лечения фиксируются все жизненные показатели пациента. При необходимости проводится экспресс-анализ крови и ЭКГ. Ниже представлена таблица, показывающая, какие параметры контролируются и по каким признакам оценивается стабилизация состояния.
Детальнее – http://vyvod-iz-zapoya-v-voronezhe17.ru/vyvod-iz-zapoya-staczionar-voronezh/
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Подробнее можно узнать тут – вывод из запоя круглосуточно волгоград
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Получить дополнительную информацию – http://
Процесс включает несколько шагов:
Углубиться в тему – врач нарколог на дом в уфе
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Получить дополнительные сведения – лечение в наркологической клинике
Запой — это не один симптом. Это сдвиг водно-электролитного баланса, скачки давления и пульса, тремор, тошнота, тревога, бессонница, нередко раздражение слизистой желудка и нагрузка на печень. Мы работаем последовательностью: допуск к терапии, инфузионная поддержка с коррекцией воды и электролитов, защита органов-мишеней, симптом-контроль, при необходимости аккуратная нормализация сна, переоценка и перевод на пероральные схемы, затем — поведенческий контур «тихих» дней и, при информированном согласии, подготовка к кодированию. Это не «коктейль на всех», а управляемый процесс, завязанный на объективные показатели и живую динамику.
Ознакомиться с деталями – https://narkologicheskaya-klinika-ivanteevka8.ru/narkologicheskie-kliniki-pomoshch-v-ivanteevke/
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Углубиться в тему – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/
«МедСфера» — это управляемый маршрут наркологической помощи в Ивантеевке: круглосуточный выезд врача без опознавательных знаков, аккуратный домашний детокс, стационар с наблюдением 24 часа в сутки и профессиональная подготовка к кодированию по показаниям. Мы работаем по принципу клинической достаточности: никакой «универсальной капельницы», никаких решений «наугад», только последовательные шаги, которые действительно влияют на исход. Каждое назначение объясняем простым языком, заранее согласуем смету, фиксируем правила на первые 24–48 часов и первую «тихую» неделю. Конфиденциальность встроена в процесс: нейтральная связь, выезд без эмблем, документы в сдержанной формулировке по запросу.
Узнать больше – рейтинг наркологических клиник
Выезд начинается с очной оценки. Врач уточняет историю эпизода, смотрит давление и пульс, сатурацию, температуру, оценивает неврологический статус и уровень тревоги, внимательно проверяет совместимость с уже принятыми средствами. Допуск к терапии — стартовая точка. Затем запускается инфузионная поддержка с аккуратной коррекцией воды и электролитов, защитой органов мишеней, симптом контролем тошноты и головокружения. При необходимости настраивается сон, но без избыточной седативной нагрузки, которая могла бы замаскировать риски. По завершении основного блока — переоценка, перевод на пероральные схемы, подробная памятка на 24–48 часов и заранее согласованное окно контрольного контакта.
Подробнее можно узнать тут – http://narkolog-na-dom-ivanteevka8.ru/vyzvat-narkologa-na-dom-v-ivanteevke/https://narkolog-na-dom-ivanteevka8.ru
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Подробнее можно узнать тут – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru
Домашняя помощь — это клиника, перенесённая в тихую комнату. Знакомая обстановка снижает тревогу, исчезают пробки и ожидание, нет «социального шума». Врач «ПрофДетокса» приезжает без эмблем, действует спокойно и последовательно, объясняет каждое назначение простым языком. Мы не используем мифические смеси. Состав и темп капельницы подбираются под текущие показатели — давление, пульс, сатурация, выраженность тремора и тошноты, уровень тревоги, данные о лекарствах, которые человек успел принять за двое суток. Такой подход даёт не минутное облегчение, а устойчивую динамику на сутки и неделю.
Выяснить больше – narkolog-na-dom-v-ivanteevke
Пациенты отмечают, что особенно важна не только профессиональная помощь, но и спокойная атмосфера. Мягкий свет, тишина, отдельные палаты и деликатная коммуникация персонала — всё это снижает тревожность и помогает организму восстановиться. Эффективность лечения оценивается по конкретным маркерам: улучшение сна, нормализация давления, исчезновение тошноты, восстановление аппетита и уменьшение тяги.
Получить дополнительную информацию – https://narkologicheskaya-clinica-v-krasnoyarske17.ru/
Перед процедурой врач оценивает состояние пациента, измеряет давление, пульс и уровень насыщения крови кислородом. После осмотра подбирается состав инфузии, включающий препараты для дезинтоксикации, восстановления водно-солевого баланса и нормализации работы органов. Введение растворов осуществляется внутривенно, под контролем специалиста. Длительность процедуры — от 40 минут до 1,5 часов.
Получить дополнительную информацию – вызов на дом капельницы от запоя в волгограде
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Изучить вопрос глубже – http://narkologicheskaya-klinika-v-krasnoyarske17.ru/chastnaya-narkologicheskaya-klinika-krasnoyarsk/
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Получить дополнительную информацию – вывод из запоя с выездом волгоград
Капельницы от запоя включают препараты для очищения крови, восстановления электролитного баланса и защиты печени. Используются только сертифицированные растворы, одобренные Минздравом РФ. В клинике применяется комплексный подход: одновременно с физическим восстановлением запускаются лёгкие дыхательные и релаксационные методики, которые помогают организму вернуться в стабильное состояние.
Подробнее – анонимный вывод из запоя в воронеже
Капельница — это основной инструмент дезинтоксикации при лечении запойных состояний. Она способствует выведению токсинов, нормализации обмена веществ и улучшению общего самочувствия. Состав раствора подбирается индивидуально в зависимости от степени интоксикации, возраста, массы тела и сопутствующих заболеваний. Уже через 20–30 минут после начала инфузии пациент ощущает облегчение, снижается тревожность и проходит головная боль.
Исследовать вопрос подробнее – вывод из запоя дешево в красноярске
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Получить дополнительные сведения – вывод из запоя дешево
«МедСфера» — это управляемый маршрут наркологической помощи в Ивантеевке: круглосуточный выезд врача без опознавательных знаков, аккуратный домашний детокс, стационар с наблюдением 24 часа в сутки и профессиональная подготовка к кодированию по показаниям. Мы работаем по принципу клинической достаточности: никакой «универсальной капельницы», никаких решений «наугад», только последовательные шаги, которые действительно влияют на исход. Каждое назначение объясняем простым языком, заранее согласуем смету, фиксируем правила на первые 24–48 часов и первую «тихую» неделю. Конфиденциальность встроена в процесс: нейтральная связь, выезд без эмблем, документы в сдержанной формулировке по запросу.
Выяснить больше – http://narkologicheskaya-klinika-ivanteevka8.ru/narkologicheskaya-klinika-na-domu-v-ivanteevke/
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Получить дополнительные сведения – запой нарколог на дом
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Выяснить больше – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru/
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Ознакомиться с деталями – анонимная наркологическая клиника красноярск
Пациенты отмечают, что особенно важна не только профессиональная помощь, но и спокойная атмосфера. Мягкий свет, тишина, отдельные палаты и деликатная коммуникация персонала — всё это снижает тревожность и помогает организму восстановиться. Эффективность лечения оценивается по конкретным маркерам: улучшение сна, нормализация давления, исчезновение тошноты, восстановление аппетита и уменьшение тяги.
Получить больше информации – https://narkologicheskaya-clinica-v-krasnoyarske17.ru/chastnaya-narkologicheskaya-klinika-krasnoyarsk
Безопасность — это не лозунг, а набор решений. Мы избегаем «жёстких» седативных доз, которые создают видимость улучшения и повышают риск скрытых осложнений. Наращивание темпа инфузии происходит постепенно и увязано с динамикой симптомов и цифрами измерений. Любой шаг объясняется пациенту и семье: зачем он выбран, что считается нормальной волной улучшения, в какой момент нужно связаться с дежурным. Такой прозрачный формат снимает тревогу и помогает всем участникам действовать согласованно.
Изучить вопрос глубже – vyzvat-narkologa-na-dom
Все детали и нюансы здесь: https://piterets.ru/clause/brands/53228-tablichki-iz-pvh-universalnye-reshenija-dlja-reklamy-i-oformlenija.html
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Подробнее тут – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/chastnaya-narkologicheskaya-klinika-krasnoyarsk/
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Изучить вопрос глубже – вывод из запоя капельница
chery 4 pro chery tiggo 4
Full version of the article: https://bodenbelaege-roteco.de/buy-tiktok-accounts-with-followers-gain-instant-5/
Лечение основывается на комплексном подходе, позволяющем учесть особенности организма и стаж злоупотребления алкоголем. Обычно процедура состоит из нескольких этапов:
Получить больше информации – наркологический вывод из запоя
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Детали по клику – https://avanzatelife.com/hello-world
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Узнайте всю правду – https://cytopathsa.pl/hello-world
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Подробности по ссылке – https://qualifier.se/pexcontentslider/default-4
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Полезно знать – https://www.kybeleconsult.dk/?page_id=46
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Прочесть заключение эксперта – https://maxpetsrd.com/en-cuanto-tiempo-estare-list-para-viajar-con-mi-mascota
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Информация доступна здесь – http://pic.murakumomura.com/2009/07/07/post_660
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Хочу знать больше – https://www.questembert2020.bzh/reunion-publique
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Интересует подробная информация – http://www.podasarbolado.com/planes-de-gestion
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Погрузиться в детали – http://www.aucotyllon.fr/2020/06/09/chapeau-os
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Подробнее – https://cookwithcoconut.com/2025/07/05/pumpkin-erissery
В этой статье-обзоре мы соберем актуальную информацию и интересные факты, которые освещают важные темы. Читатели смогут ознакомиться с различными мнениями и подходами, что позволит им расширить кругозор и глубже понять обсуждаемые вопросы.
Узнай первым! – https://institutsourcesante.com/2018/04/04/la-pleine-conscience
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Расширить кругозор по теме – https://auroracoop.com.br/vidauroracoop/a-inauguracao-e-modernidade-da-nossa-nova-planta
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Узнать из первых рук – https://rivercityramble.stlouligans.com/river-city-ramble-podcast-episode-139-kiss-of-death
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Рассмотреть проблему всесторонне – https://lensapangandaran.com/innalilahi-rumah-makan-sate-galunggung-2-di-pangandaran-kebakaran-hebat
Процедура проводится как в стационаре, так и на дому. Врач приезжает по вызову, проводит осмотр и измеряет давление, пульс, насыщение кислородом. После оценки состояния подбирается состав капельницы и начинается инфузионная терапия. В среднем процедура длится от 40 минут до 1,5 часов, в зависимости от степени интоксикации. По завершении врач наблюдает за реакцией организма и даёт рекомендации по восстановлению.
Изучить вопрос глубже – капельница от запоя вызов
Своевременное обращение в клинику снижает риск развития алкогольного психоза, судорог и тяжёлых осложнений со стороны сердца и печени.
Изучить вопрос глубже – вывод из запоя дешево в рязани
Одним из самых востребованных направлений работы клиники является проведение детоксикации и вывод из запоя. Эти процедуры направлены на очищение организма от алкоголя и продуктов его распада, нормализацию работы печени и нервной системы. Лечение проводится с использованием сертифицированных препаратов и под контролем врача-нарколога.
Узнать больше – запой наркологическая клиника
Мы предлагаем вам подробное руководство, основанное на проверенных источниках и реальных примерах. Каждая часть публикации направлена на то, чтобы помочь вам разобраться в сложных вопросах и применить знания на практике.
Изучить вопрос глубже – https://hearld.news/udderly-unbelievable-first-female-ceo-milks-tech
Быстро и безопасно остановить запой можно с помощью вызова нарколога на дом. В Екатеринбурге такую услугу оказывает клиника «Детокс».
Детальнее – запой нарколог на дом в екатеринбурге
Капельница от запоя в Воронеже применяется для восстановления организма после длительного употребления алкоголя, устранения интоксикации и нормализации обменных процессов. Медицинская процедура проводится под контролем врача-нарколога, в клинике или на дому. Она позволяет быстро улучшить самочувствие, устранить головную боль, тремор, тошноту, обезвоживание и нарушения сна. Современные препараты действуют мягко, безопасно и без стресса для организма, обеспечивая плавный выход из запоя.
Получить дополнительную информацию – сколько стоит капельница на дому от запоя воронеж
Быстро и безопасно остановить запой можно с помощью вызова нарколога на дом. В Екатеринбурге такую услугу оказывает клиника «Детокс».
Углубиться в тему – narkolog-na-dom ekaterinburg
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Углубиться в тему – вывод из запоя клиника рязань
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Подробнее можно узнать тут – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/
Вывод из запоя в Рязани — это профессиональная медицинская процедура, направленная на очищение организма от токсинов, восстановление нормального самочувствия и предотвращение осложнений после длительного употребления алкоголя. В специализированных клиниках города лечение проводится с использованием современных методов детоксикации и под контролем опытных врачей-наркологов. Такой подход позволяет быстро и безопасно стабилизировать состояние пациента, устранить физическую зависимость и подготовить организм к дальнейшему восстановлению.
Подробнее можно узнать тут – вывод из запоя с выездом
Состав капельницы подбирается индивидуально, с учётом степени опьянения, возраста и хронических заболеваний пациента. Врач определяет дозировку и комбинацию препаратов, чтобы процедура прошла безопасно и эффективно.
Получить дополнительные сведения – капельница от запоя анонимно
Estou completamente vidrado por BetorSpin Casino, parece uma explosao cosmica de adrenalina. A gama do cassino e simplesmente uma constelacao de prazeres, com jogos de cassino perfeitos pra criptomoedas. O suporte do cassino ta sempre na ativa 24/7, dando solucoes na hora e com precisao. Os ganhos do cassino chegam voando como um asteroide, mesmo assim as ofertas do cassino podiam ser mais generosas. No fim das contas, BetorSpin Casino oferece uma experiencia de cassino que e puro brilho cosmico para os apaixonados por slots modernos de cassino! De lambuja a interface do cassino e fluida e reluz como uma constelacao, torna a experiencia de cassino uma viagem espacial.
betorspin snyd|
Ich freue mich sehr uber Cat Spins Casino, es schafft eine mitrei?ende Stimmung. Das Portfolio ist vielfaltig und attraktiv, mit klassischen Tischspielen. Mit sofortigen Einzahlungen. Der Service ist absolut zuverlassig. Transaktionen sind immer sicher, gelegentlich ein paar Freispiele mehr waren super. Zusammengefasst, Cat Spins Casino bietet ein unvergleichliches Erlebnis. Ubrigens die Navigation ist unkompliziert, das Spielvergnugen steigert. Ein super Vorteil ist das VIP-Programm mit exklusiven Stufen, individuelle Vorteile liefern.
Details finden|
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Подробнее – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologicheskij-czentr-novokuzneczk/
Ich bin ganz hin und weg von Cat Spins Casino, es bietet eine Welt voller Action. Die Spielauswahl ist ein echtes Highlight, mit Krypto-freundlichen Titeln. Er gibt Ihnen einen tollen Boost. Verfugbar 24/7 fur alle Fragen. Der Prozess ist einfach und transparent, in seltenen Fallen gro?ere Boni waren ideal. Abschlie?end, Cat Spins Casino ist ein Top-Ziel fur Spieler. Daruber hinaus die Seite ist schnell und ansprechend, zum Verweilen einladt. Ein tolles Extra die zahlreichen Sportwetten-Moglichkeiten, personliche Vorteile bereitstellen.
Website Г¶ffnen|
Ich bin komplett hin und weg von SpinBetter Casino, es bietet einen einzigartigen Kick. Der Katalog ist reichhaltig und variiert, mit aufregenden Sportwetten. Die Hilfe ist effizient und pro, bietet klare Losungen. Die Transaktionen sind verlasslich, gelegentlich die Offers konnten gro?zugiger ausfallen. In Kurze, SpinBetter Casino garantiert hochsten Spa? fur Casino-Liebhaber ! Zusatzlich die Navigation ist kinderleicht, fugt Magie hinzu. Ein weiterer Vorteil die schnellen Einzahlungen, die Flexibilitat bieten.
https://spinbettercasino.de/|
Чтобы вывести из запоя без поездки в клинику, закажите вызов нарколога на дом в Екатеринбурге. Помощь оказывает центр «Детокс».
Подробнее тут – нарколог на дом вывод из запоя екатеринбург
Все процедуры выполняются анонимно и с соблюдением медицинских стандартов. Препараты применяются только сертифицированные, рассчитанные на мягкое восстановление организма без побочных эффектов. При необходимости лечение продолжается в стационаре, где пациент получает круглосуточное наблюдение, питание и психологическую поддержку.
Разобраться лучше – помощь вывод из запоя
J’ai une affection particuliere pour Sugar Casino, ca transporte dans un univers de plaisirs. Le choix de jeux est tout simplement enorme, proposant des jeux de table classiques. Le bonus de bienvenue est genereux. Le support est efficace et amical. Les retraits sont lisses comme jamais, de temps en temps des bonus plus frequents seraient un hit. En conclusion, Sugar Casino est une plateforme qui pulse. A mentionner la plateforme est visuellement electrisante, facilite une immersion totale. Un avantage les nombreuses options de paris sportifs, offre des bonus exclusifs.
AccГ©der maintenant|
Je ne me lasse pas de Ruby Slots Casino, c’est une plateforme qui pulse avec energie. Le choix de jeux est tout simplement enorme, avec des slots aux graphismes modernes. Le bonus de bienvenue est genereux. Le suivi est impeccable. Le processus est transparent et rapide, mais plus de promos regulieres dynamiseraient le jeu. Pour conclure, Ruby Slots Casino est une plateforme qui pulse. En complement l’interface est simple et engageante, apporte une touche d’excitation. Un atout les competitions regulieres pour plus de fun, offre des recompenses regulieres.
DГ©couvrir|
J’adore l’ambiance electrisante de Sugar Casino, on y trouve une energie contagieuse. Il y a un eventail de titres captivants, proposant des jeux de table sophistiques. 100% jusqu’a 500 € plus des tours gratuits. Les agents repondent avec rapidite. Le processus est fluide et intuitif, en revanche plus de promotions variees ajouteraient du fun. En resume, Sugar Casino offre une aventure inoubliable. Pour completer la navigation est fluide et facile, ce qui rend chaque moment plus vibrant. Un point cle le programme VIP avec des recompenses exclusives, qui motive les joueurs.
Entrer sur le site|
Ich bin suchtig nach Cat Spins Casino, es ladt zu spannenden Spielen ein. Es gibt eine riesige Vielfalt an Spielen, mit aufregenden Live-Casino-Erlebnissen. Er bietet einen tollen Startvorteil. Die Mitarbeiter sind schnell und kompetent. Transaktionen sind zuverlassig und klar, ab und zu mehr Bonusvielfalt ware ein Vorteil. Insgesamt, Cat Spins Casino ist definitiv einen Besuch wert. Daruber hinaus die Seite ist schnell und ansprechend, das Vergnugen maximiert. Ein super Vorteil ist das VIP-Programm mit einzigartigen Belohnungen, die die Community enger zusammenschwei?en.
Erfahren Sie wie|
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Получить больше информации – https://narkologicheskaya-klinika-v-novokuzneczke17.ru/narkolog-novokuzneczk-na-dom
В Екатеринбурге клиника «Детокс» предлагает круглосуточный вызов нарколога на дом. Врач приедет быстро и поможет выйти из запоя.
Изучить вопрос глубже – вызов врача нарколога на дом в екатеринбурге
Клиника «Трезвый Выбор Рязань» функционирует по принципу полного цикла лечения: от экстренного выезда нарколога до длительной реабилитации в условиях стационара. Пациенты поступают как в острых состояниях (запой, абстиненция, интоксикация), так и для плановой терапии. Лечение начинается с медицинской диагностики, оценки физического и психического состояния, после чего разрабатывается индивидуальный план. Программы включают детоксикацию, медикаментозную поддержку, психологическую помощь и профилактику рецидивов.
Ознакомиться с деталями – http://narkologicheskaya-clinika-v-ryazani17.ru/narkologiya-v-ryazani/
Мы обеспечиваем комфортные условия для пребывания в клинике Ростова-на-Дону, чтобы восстановление прошло максимально эффективно.
Исследовать вопрос подробнее – вывод из запоя на дому недорого ростов-на-дону
В Екатеринбурге клиника «Детокс» предлагает круглосуточный вызов нарколога на дом. Врач приедет быстро и поможет выйти из запоя.
Узнать больше – нарколог на дом екатеринбург
В «Частном Медике 24» в Ростове-на-Дону мы заботимся о вашем здоровье и благополучии, предоставляя качественную медицинскую помощь.
Исследовать вопрос подробнее – вывод из запоя на дому цена
Наши услуги доступны всем жителям Ростова-на-Дону, обеспечивая доступность помощи для каждого пациента.
Ознакомиться с деталями – нарколог вывод из запоя
Обратившись в «Частный Медик 24» в Ростове-на-Дону, вы получаете не только медицинскую помощь, но и всестороннюю поддержку на пути к выздоровлению.
Исследовать вопрос подробнее – наркологический вывод из запоя
Если состояние близкого человека ухудшилось из-за запоя, не откладывайте вызов врача. В клинике Детокс в Екатеринбурге выезд нарколога на дом обеспечивает оперативность и конфиденциальность. Врач приедет в течение получаса, оценит состояние пациента, окажет первую помощь и подскажет, как действовать дальше.
Углубиться в тему – нарколог на дом свердловская область
Если вы беспокоитесь за здоровье близкого, не позволяйте запою разрушать жизнь. В Екатеринбурге клиника Детокс оказывается срочная помощь на дому: врач-нарколог приедет по вашему адресу, выполнит необходимые инъекции или капельницы, дистанционно проконтролирует состояние и составит план лечения. Это решение позволяет сохранить здоровье, предотвратить осложнения и начать путь к выздоровлению с минимальными дискомфортом и рисками.
Получить дополнительные сведения – https://narkolog-na-dom-ekaterinburg12.ru
Ниже приведена таблица, отражающая примерную динамику состояния пациента после постановки капельницы:
Изучить вопрос глубже – https://kapelnicza-ot-zapoya-v-voronezhe17.ru/kapelnicza-ot-alkogolya-voronezh/
Капельница от запоя в Воронеже применяется для восстановления организма после длительного употребления алкоголя, устранения интоксикации и нормализации обменных процессов. Медицинская процедура проводится под контролем врача-нарколога, в клинике или на дому. Она позволяет быстро улучшить самочувствие, устранить головную боль, тремор, тошноту, обезвоживание и нарушения сна. Современные препараты действуют мягко, безопасно и без стресса для организма, обеспечивая плавный выход из запоя.
Получить дополнительную информацию – капельница от запоя на дому воронеж
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Исследовать вопрос подробнее – наркологический вывод из запоя
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Углубиться в тему – https://vyvod-iz-zapoya-v-ryazani17.ru/vyvod-iz-zapoya-ryazan-na-domu/
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Получить дополнительные сведения – https://narkologicheskaya-klinika-v-novokuzneczke17.ru/narkolog-novokuzneczk-na-dom
Вызывать нарколога на дом — значит получать помощь без лишней суеты и психологического дискомфорта. В Екатеринбурге клиника Детокс предлагает услугу выезда специалиста с необходимым оборудованием и лекарствами. Услуга доступна круглосуточно, даже в ночное время и выходные дни, и подходит тем, кто ценит анонимность и хочет быстро прервать запой.
Углубиться в тему – врач нарколог на дом в екатеринбурге
Galera, resolvi contar como foi no 4PlayBet Casino porque foi muito alem do que imaginei. A variedade de jogos e surreal: slots modernos, todos funcionando perfeito. O suporte foi atencioso, responderam em minutos pelo chat, algo que faz diferenca. Fiz saque em Ethereum e o dinheiro entrou muito rapido, ponto fortissimo. Se tivesse que criticar, diria que seria legal torneios de slots, mas isso nao estraga a experiencia. Resumindo, o 4PlayBet Casino e parada obrigatoria pra quem gosta de cassino. Eu ja voltei varias vezes.
celular moto g 4play|
Ich habe einen Narren gefressen an Cat Spins Casino, es schafft eine aufregende Atmosphare. Die Spielauswahl ist ein echtes Highlight, mit Spielautomaten in beeindruckenden Designs. Er bietet einen tollen Startvorteil. Die Mitarbeiter antworten schnell und freundlich. Gewinne kommen sofort an, allerdings haufigere Promos wurden begeistern. Am Ende, Cat Spins Casino garantiert langanhaltenden Spa?. Nebenbei ist das Design modern und einladend, was jede Session spannender macht. Ein wichtiger Vorteil die haufigen Turniere fur Wettbewerb, personliche Vorteile bereitstellen.
http://www.catspinsbonus.com|
Ich habe einen totalen Hang zu SpinBetter Casino, es fuhlt sich an wie ein Strudel aus Freude. Es wartet eine Fulle spannender Optionen, mit dynamischen Tischspielen. Der Service ist von hoher Qualitat, immer parat zu assistieren. Die Zahlungen sind sicher und smooth, ab und an regelma?igere Aktionen waren toll. Global gesehen, SpinBetter Casino ist absolut empfehlenswert fur Online-Wetten-Fans ! Hinzu kommt die Navigation ist kinderleicht, was jede Session noch besser macht. Besonders toll die schnellen Einzahlungen, die Flexibilitat bieten.
https://spinbettercasino.de/|
Все процедуры выполняются анонимно и с соблюдением медицинских стандартов. Препараты применяются только сертифицированные, рассчитанные на мягкое восстановление организма без побочных эффектов. При необходимости лечение продолжается в стационаре, где пациент получает круглосуточное наблюдение, питание и психологическую поддержку.
Углубиться в тему – вывод из запоя клиника в новокузнецке
J’adore l’energie de Sugar Casino, on y trouve une energie contagieuse. Les titres proposes sont d’une richesse folle, comprenant des jeux crypto-friendly. Le bonus de depart est top. Les agents repondent avec efficacite. Le processus est fluide et intuitif, par moments des recompenses supplementaires dynamiseraient le tout. Pour conclure, Sugar Casino assure un fun constant. D’ailleurs la navigation est claire et rapide, facilite une immersion totale. Un point fort les transactions en crypto fiables, qui booste la participation.
Touchez ici|
J’adore la vibe de Ruby Slots Casino, on y trouve une energie contagieuse. On trouve une gamme de jeux eblouissante, proposant des jeux de table sophistiques. Le bonus de bienvenue est genereux. Les agents sont toujours la pour aider. Les gains sont transferes rapidement, par ailleurs plus de promos regulieres ajouteraient du peps. Globalement, Ruby Slots Casino est un endroit qui electrise. De plus la plateforme est visuellement electrisante, ce qui rend chaque session plus palpitante. Particulierement attrayant les tournois reguliers pour la competition, assure des transactions fiables.
https://rubyslotscasinologinfr.com/|
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Исследовать вопрос подробнее – http://narkologicheskaya-klinika-v-novokuzneczke17.ru/narkolog-novokuzneczk-na-dom/
Je suis enthousiasme par Sugar Casino, c’est une plateforme qui deborde de dynamisme. Les options de jeu sont incroyablement variees, incluant des paris sportifs pleins de vie. Avec des depots instantanes. Le suivi est d’une fiabilite exemplaire. Les transactions sont toujours fiables, en revanche des offres plus genereuses rendraient l’experience meilleure. En somme, Sugar Casino est un immanquable pour les amateurs. Pour ajouter le site est rapide et engageant, facilite une immersion totale. Particulierement interessant les transactions crypto ultra-securisees, propose des avantages uniques.
http://www.sugarcasinobonusfr.com|
Такой состав обеспечивает быстрое снятие симптомов интоксикации и восстановление функций организма после запоя.
Ознакомиться с деталями – http://kapelnicza-ot-zapoya-v-voronezhe17.ru
Такой алгоритм позволяет контролировать каждый аспект лечения, обеспечивая постепенное и безопасное восстановление. Врач-куратор отслеживает динамику и при необходимости корректирует программу.
Исследовать вопрос подробнее – наркологическая клиника стационар
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Получить полную информацию – https://kangenwaterthailand.com/testimonial/zuzi-aoi
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Нажмите, чтобы узнать больше – https://alohaabeachresort.com/booking/single-room
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Познакомиться с результатами исследований – https://washingtonfiles.com/texas-tech-baseball
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Познакомиться с результатами исследований – https://travel-book.net/hokkaidou-doubutuen
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Это ещё не всё… – https://mind-at-rest.com/2020/07/31/extreme-mindfulness-challeng-7-30-2020
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Читать далее > – https://bodycorporatecleaningmelbourne.com.au/the-smoke-signal-by-frederic-remington-long-distance-communication
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Только факты! – https://isla4you.com/visum-venezuela
Ich bin ganz hin und weg von Cat Spins Casino, es entfuhrt in eine Welt voller Nervenkitzel. Die Spiele sind abwechslungsreich und fesselnd, mit Krypto-freundlichen Titeln. 100 % bis zu 500 € und Freispiele. Erreichbar rund um die Uhr. Transaktionen laufen reibungslos, trotzdem regelma?igere Promos wurden das Spiel aufwerten. Letztlich, Cat Spins Casino bietet ein gro?artiges Erlebnis. Daruber hinaus ist das Design zeitgema? und attraktiv, jede Session unvergesslich macht. Ein starker Vorteil ist das VIP-Programm mit tollen Privilegien, exklusive Boni bieten.
Mit dem Erkunden beginnen|
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Как достичь результата? – https://www.divisoria.org/product/relxs
В Екатеринбурге доступна услуга вызова нарколога на дом от клиники «Детокс». Врач приезжает с необходимыми препаратами и оборудованием.
Подробнее тут – нарколог на дом екатеринбург
Если вы беспокоитесь за здоровье близкого, не позволяйте запою разрушать жизнь. В Екатеринбурге клиника Детокс оказывается срочная помощь на дому: врач-нарколог приедет по вашему адресу, выполнит необходимые инъекции или капельницы, дистанционно проконтролирует состояние и составит план лечения. Это решение позволяет сохранить здоровье, предотвратить осложнения и начать путь к выздоровлению с минимальными дискомфортом и рисками.
Подробнее можно узнать тут – выезд нарколога на дом екатеринбург
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Открой скрытое – http://www.erhjalp.se/antique-style-light-bulbs
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Не упусти важное! – https://www.summervalleyschoolmoradabad.com/ptm-grade-3-9-11
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Ознакомиться с теоретической базой – https://itensdiversos.com/ola-mundo
В Ростове-на-Дону мы гарантируем полную анонимность и конфиденциальность на всех этапах лечения, без постановки на учёт. Клиника в Ростове-на-Дону работает круглосуточно, обеспечивая доступность помощи в любое время дня и ночи.
Подробнее – вывод из запоя на дому цена
Клиника «Детокс» в Екатеринбурге оказывает услугу вызова нарколога прямо к вам домой. Специалисты приедут в течение часа.
Подробнее – narkolog-na-dom-kruglosutochno ekaterinburg
Наши услуги доступны всем жителям Ростова-на-Дону, обеспечивая доступность помощи для каждого пациента.
Узнать больше – вывод из запоя с выездом
Мы стремимся к тому, чтобы каждый наш пациент в Ростове-на-Дону почувствовал заботу и внимание, получая качественную медицинскую помощь.
Детальнее – наркология вывод из запоя
Ich bin beeindruckt von der Qualitat bei Cat Spins Casino, es bietet ein immersives Erlebnis. Es gibt zahlreiche spannende Spiele, mit Krypto-freundlichen Titeln. Er bietet einen tollen Startvorteil. Die Mitarbeiter antworten schnell und freundlich. Transaktionen sind zuverlassig und klar, trotzdem gro?zugigere Angebote waren klasse. In Summe, Cat Spins Casino ist ein Top-Ziel fur Casino-Fans. Nebenbei die Plattform ist optisch ein Highlight, das Spielerlebnis bereichert. Ein Hauptvorteil sind die sicheren Krypto-Zahlungen, die Gemeinschaft starken.
Online gehen|
Наши услуги в Ростове-на-Дону включают не только физическую детоксикацию, но и психологическую поддержку для более эффективного восстановления.
Подробнее – вывод из запоя круглосуточно
Наши специалисты проводят детальную диагностику и разрабатывают индивидуальный план лечения с учётом состояния пациента в Ростове-на-Дону.
Узнать больше – срочный вывод из запоя ростов-на-дону
Ich habe einen Narren gefressen an Cat Spins Casino, es ist ein Ort voller Energie. Das Angebot ist ein Paradies fur Spieler, mit interaktiven Live-Spielen. Er gibt Ihnen einen tollen Boost. Der Kundendienst ist hervorragend. Die Zahlungen sind sicher und sofortig, jedoch zusatzliche Freispiele waren ein Bonus. Zusammengefasst, Cat Spins Casino bietet ein gro?artiges Erlebnis. Nebenbei ist das Design stilvoll und modern, eine Note von Eleganz hinzufugt. Ein super Vorteil ist das VIP-Programm mit besonderen Vorteilen, die die Begeisterung steigern.
Zur Seite gehen|
Ich bin fasziniert von SpinBetter Casino, es ist eine Erfahrung, die wie ein Wirbelsturm pulsiert. Es gibt eine unglaubliche Auswahl an Spielen, mit immersiven Live-Sessions. Die Hilfe ist effizient und pro, immer parat zu assistieren. Der Ablauf ist unkompliziert, obwohl mehr abwechslungsreiche Boni waren super. Zum Ende, SpinBetter Casino ist absolut empfehlenswert fur Krypto-Enthusiasten ! Nicht zu vergessen die Interface ist intuitiv und modern, gibt den Anreiz, langer zu bleiben. Besonders toll die mobilen Apps, die den Einstieg erleichtern.
https://spinbettercasino.de/|
Je suis fascine par Ruby Slots Casino, ca transporte dans un univers de plaisirs. La bibliotheque de jeux est captivante, comprenant des titres adaptes aux cryptomonnaies. Il propulse votre jeu des le debut. Le support est rapide et professionnel. Les gains arrivent sans delai, bien que plus de promotions frequentes boosteraient l’experience. Pour conclure, Ruby Slots Casino est un incontournable pour les joueurs. Notons aussi la plateforme est visuellement dynamique, booste l’excitation du jeu. Particulierement fun les tournois reguliers pour s’amuser, renforce le lien communautaire.
https://rubyslotscasinobonusfr.com/|
Je suis emerveille par Sugar Casino, ca pulse comme une soiree animee. Le catalogue est un tresor de divertissements, avec des slots aux designs captivants. Le bonus initial est super. Le support est fiable et reactif. Les retraits sont lisses comme jamais, parfois des bonus varies rendraient le tout plus fun. En resume, Sugar Casino offre une experience inoubliable. Ajoutons que le site est rapide et style, facilite une immersion totale. Egalement super les tournois reguliers pour la competition, propose des avantages sur mesure.
Entrer maintenant|
J’ai une passion debordante pour Sugar Casino, c’est un lieu ou l’adrenaline coule a flots. Les options de jeu sont incroyablement variees, incluant des options de paris sportifs dynamiques. Avec des depots fluides. Le suivi est impeccable. Les transactions sont toujours fiables, malgre tout plus de promotions variees ajouteraient du fun. En conclusion, Sugar Casino est un choix parfait pour les joueurs. En bonus la plateforme est visuellement vibrante, facilite une immersion totale. A souligner les competitions regulieres pour plus de fun, qui motive les joueurs.
Voir la page d’accueil|
Вызывать нарколога на дом — значит получать помощь без лишней суеты и психологического дискомфорта. В Екатеринбурге клиника Детокс предлагает услугу выезда специалиста с необходимым оборудованием и лекарствами. Услуга доступна круглосуточно, даже в ночное время и выходные дни, и подходит тем, кто ценит анонимность и хочет быстро прервать запой.
Узнать больше – врач нарколог на дом в екатеринбурге
J’adore l’ambiance electrisante de Ruby Slots Casino, on ressent une ambiance festive. Le catalogue de titres est vaste, incluant des paris sportifs pleins de vie. Il donne un elan excitant. Le suivi est impeccable. Les gains arrivent sans delai, en revanche quelques tours gratuits en plus seraient geniaux. Pour conclure, Ruby Slots Casino garantit un amusement continu. Ajoutons que la plateforme est visuellement vibrante, donne envie de prolonger l’aventure. Particulierement interessant les evenements communautaires dynamiques, assure des transactions fiables.
Trouver les dГ©tails|
Удобный и анонимный способ прервать запой — это вызов нарколога на дом в Екатеринбурге. Закажите помощь в клинике «Детокс».
Ознакомиться с деталями – вывод из запоя капельница на дому в екатеринбурге
Мы обеспечиваем полную поддержку на всех этапах лечения в Ростове-на-Дону, включая реабилитацию и профилактику рецидивов.
Подробнее тут – вывод из запоя
Если нужна срочная помощь, воспользуйтесь услугой вызова нарколога на дом в Екатеринбурге от клиники «Детокс». Анонимно и безопасно.
Детальнее – вывод из запоя вызов в екатеринбурге
Ich freue mich riesig uber Cat Spins Casino, es schafft eine aufregende Atmosphare. Das Angebot an Titeln ist riesig, mit spannenden Sportwetten-Angeboten. Er gibt Ihnen einen Kickstart. Der Support ist effizient und professionell. Gewinne kommen sofort an, dennoch waren mehr Bonusvarianten ein Plus. Zusammengefasst, Cat Spins Casino ist ein absolutes Highlight. Hinzu kommt die Plattform ist visuell beeindruckend, jede Session unvergesslich macht. Ein gro?artiges Plus die dynamischen Community-Events, regelma?ige Boni bieten.
Zur Seite gehen|
Мы понимаем, как важно быстро и эффективно выйти из запоя, поэтому в Ростове-на-Дону предлагаем оперативную помощь в любое время.
Подробнее тут – наркология вывод из запоя в ростове-на-дону
What’s up to all, the contents present at this site are actually remarkable for people experience, well, keep up the good work fellows.
https://rabeloconcreto.com.br/melbet-kazino-zerkalo-2025-obzor/
Мы предлагаем гибкую систему оплаты и прозрачные цены в Ростове-на-Дону, без скрытых платежей и переплат. Обратившись в нашу клинику в Ростове-на-Дону, вы делаете первый шаг к здоровой и трезвой жизни.
Углубиться в тему – нарколог на дом вывод из запоя
Je suis epate par Wild Robin Casino, ca transporte dans un monde d’excitation. Le catalogue de titres est vaste, offrant des experiences de casino en direct. Le bonus de bienvenue est genereux. Le suivi est toujours au top. Les paiements sont surs et fluides, rarement quelques spins gratuits en plus seraient top. Globalement, Wild Robin Casino garantit un amusement continu. Notons aussi la navigation est fluide et facile, ce qui rend chaque session plus excitante. Un bonus les nombreuses options de paris sportifs, qui dynamise l’engagement.
Wild Robin|
Je suis accro a Wild Robin Casino, c’est un lieu ou l’adrenaline coule a flots. Les titres proposes sont d’une richesse folle, avec des machines a sous visuellement superbes. Il amplifie le plaisir des l’entree. Le service d’assistance est au point. Les paiements sont securises et rapides, neanmoins plus de promos regulieres dynamiseraient le jeu. Dans l’ensemble, Wild Robin Casino offre une experience inoubliable. En extra la navigation est claire et rapide, booste l’excitation du jeu. Particulierement attrayant les evenements communautaires dynamiques, cree une communaute vibrante.
Explorer plus|
Je suis sous le charme de Frumzi Casino, ca invite a plonger dans le fun. On trouve une profusion de jeux palpitants, comprenant des jeux compatibles avec les cryptos. Le bonus de bienvenue est genereux. Disponible a toute heure via chat ou email. Le processus est simple et transparent, parfois des recompenses supplementaires dynamiseraient le tout. Pour faire court, Frumzi Casino offre une experience inoubliable. Notons aussi l’interface est fluide comme une soiree, ce qui rend chaque moment plus vibrant. Un avantage les paiements securises en crypto, qui booste la participation.
Aller au site|
Je suis bluffe par Wild Robin Casino, c’est une plateforme qui pulse avec energie. Le catalogue de titres est vaste, avec des slots aux designs captivants. Le bonus initial est super. Le suivi est impeccable. Les paiements sont securises et instantanes, de temps a autre des recompenses supplementaires seraient parfaites. Au final, Wild Robin Casino est une plateforme qui fait vibrer. Par ailleurs le design est tendance et accrocheur, ce qui rend chaque session plus palpitante. Un avantage les evenements communautaires pleins d’energie, propose des avantages sur mesure.
Commencer ici|
J’ai un faible pour Cheri Casino, ca offre un plaisir vibrant. Le catalogue de titres est vaste, comprenant des jeux optimises pour Bitcoin. Le bonus de bienvenue est genereux. Le suivi est d’une precision remarquable. Les retraits sont fluides et rapides, rarement des offres plus consequentes seraient parfaites. Pour faire court, Cheri Casino offre une aventure memorable. En bonus la navigation est intuitive et lisse, amplifie le plaisir de jouer. Particulierement cool les tournois reguliers pour la competition, renforce le lien communautaire.
https://chericasinobonusfr.com/|
J’adore l’ambiance electrisante de Cheri Casino, il propose une aventure palpitante. La bibliotheque de jeux est captivante, avec des machines a sous aux themes varies. Il propulse votre jeu des le debut. Les agents repondent avec efficacite. Le processus est clair et efficace, par ailleurs des recompenses en plus seraient un bonus. Globalement, Cheri Casino merite un detour palpitant. En extra la plateforme est visuellement electrisante, permet une immersion complete. Particulierement interessant les paiements en crypto rapides et surs, garantit des paiements securises.
Commencer Г explorer|
Je suis enthousiasme par Instant Casino, il procure une sensation de frisson. Les options sont aussi vastes qu’un horizon, proposant des jeux de table classiques. Avec des depots rapides et faciles. Le service client est de qualite. Les transactions sont d’une fiabilite absolue, toutefois des bonus plus varies seraient un plus. En fin de compte, Instant Casino merite un detour palpitant. A signaler l’interface est lisse et agreable, ce qui rend chaque moment plus vibrant. Particulierement cool les transactions crypto ultra-securisees, cree une communaute vibrante.
Cliquez ici|
Je suis sous le charme de Instant Casino, il cree un monde de sensations fortes. Le choix est aussi large qu’un festival, comprenant des titres adaptes aux cryptomonnaies. 100% jusqu’a 500 € avec des free spins. Les agents sont toujours la pour aider. Les gains sont verses sans attendre, mais encore des recompenses supplementaires seraient parfaites. En conclusion, Instant Casino offre une aventure inoubliable. A noter le design est moderne et attrayant, donne envie de prolonger l’aventure. Un avantage notable les tournois frequents pour l’adrenaline, assure des transactions fiables.
Visiter le site|
Для получения квалифицированной помощи в борьбе с наркозависимостью и другими связанными с этим проблемами в Санкт-Петербурге можно воспользоваться услугами наркологи на дом, предлагающей услуги опытных специалистов по лечению наркозависимости и других связанных с этим расстройств на дому в Санкт-Петербурге.
Очень удобную и доступную услугу для пациентов, которые не могут посетить клинику лично . Это позволяет пациентам иметь возможность быстро и эффективно решать свои проблемы. Услуги нарколога на дом в Санкт-Петербурге становятся широко распространенными и доступными для всех желающих.
Нарколог на дом в Санкт-Петербурге имеет в своем арсенале современные методы и технологии для борьбы с наркозависимостью . Это позволяет создавать индивидуальные программы лечения для каждого пациента. Услуги нарколога на дом в Санкт-Петербурге осуществляются квалифицированными специалистами с большим опытом работы .
Услуги нарколога на дом в Санкт-Петербурге имеют высокую эффективность и результативность лечения . Это позволяет пациентам иметь возможность быстро возвращаться к нормальной жизни . Нарколог на дом в Санкт-Петербурге может оказывать помощь в любое время и в любом месте.
Преимущества услуг нарколога на дом в Санкт-Петербурге включают снижение риска осложнений и побочных эффектов . Это позволяет пациентам быть более активными и участвовать в процессе лечения . Услуги нарколога на дом в Санкт-Петербурге очень востребованы среди населения .
Цены на услуги нарколога на дом в Санкт-Петербурге могут быть очень доступными и демократичными. Это позволяет пациентам получать необходимую помощь без значительных финансовых затрат . Нарколог на дом в Санкт-Петербурге имеет возможность работать с различными формами оплаты .
Цены на услуги нарколога на дом в Санкт-Петербурге очень конкурентоспособны и привлекательны . Это позволяет пациентам чувствовать себя более комфортно и уверенно. Услуги нарколога на дом в Санкт-Петербурге могут быть рекомендованы для пациентов всех возрастов и социальных групп.
Услуги нарколога на дом в Санкт-Петербурге имеют высокую репутацию и доверие среди пациентов . Это позволяет пациентам иметь возможность быстро и эффективно решать свои проблемы. Нарколог на дом в Санкт-Петербурге предоставляет пациентам индивидуальное внимание и заботу .
Услуги нарколога на дом в Санкт-Петербурге постоянно развиваются и совершенствуются. Это позволяет пациентам получать необходимую помощь без значительных финансовых затрат . Нарколог на дом в Санкт-Петербурге работает в тесном сотрудничестве с пациентами для достижения лучших результатов.
Je suis emerveille par Wild Robin Casino, ca donne une vibe electrisante. La selection de jeux est impressionnante, offrant des experiences de casino en direct. Le bonus initial est super. Le support est rapide et professionnel. Les transactions sont toujours fiables, cependant des offres plus importantes seraient super. Globalement, Wild Robin Casino assure un fun constant. Notons aussi la navigation est simple et intuitive, apporte une touche d’excitation. Particulierement cool les transactions en crypto fiables, propose des privileges personnalises.
Obtenir plus|
J’adore la vibe de Wild Robin Casino, ca pulse comme une soiree animee. Les options de jeu sont infinies, comprenant des jeux crypto-friendly. 100% jusqu’a 500 € avec des free spins. Disponible 24/7 pour toute question. Le processus est transparent et rapide, en revanche des bonus diversifies seraient un atout. Pour conclure, Wild Robin Casino est une plateforme qui fait vibrer. A mentionner la navigation est claire et rapide, incite a prolonger le plaisir. Egalement super les options de paris sportifs diversifiees, propose des avantages uniques.
Essayer ceci|
Je suis sous le charme de Instant Casino, c’est un lieu ou l’adrenaline coule a flots. Le catalogue de titres est vaste, incluant des paris sportifs en direct. Il propulse votre jeu des le debut. Le suivi est d’une precision remarquable. Le processus est transparent et rapide, mais plus de promotions variees ajouteraient du fun. Globalement, Instant Casino offre une experience hors du commun. A mentionner la navigation est intuitive et lisse, facilite une experience immersive. Egalement excellent les evenements communautaires pleins d’energie, propose des privileges sur mesure.
Instant|
Je suis epate par Frumzi Casino, c’est un lieu ou l’adrenaline coule a flots. La selection de jeux est impressionnante, avec des machines a sous visuellement superbes. 100% jusqu’a 500 € avec des free spins. Le support est efficace et amical. Les transactions sont toujours securisees, rarement quelques spins gratuits en plus seraient top. En conclusion, Frumzi Casino offre une experience inoubliable. De surcroit l’interface est lisse et agreable, apporte une touche d’excitation. Particulierement fun les competitions regulieres pour plus de fun, renforce la communaute.
Poursuivre la lecture|
J’adore le dynamisme de Instant Casino, il propose une aventure palpitante. Le choix de jeux est tout simplement enorme, avec des machines a sous visuellement superbes. Avec des depots instantanes. Le support est pro et accueillant. Les retraits sont fluides et rapides, par ailleurs des offres plus importantes seraient super. En conclusion, Instant Casino est un choix parfait pour les joueurs. De plus la navigation est simple et intuitive, permet une plongee totale dans le jeu. A mettre en avant les tournois reguliers pour la competition, assure des transactions fluides.
DГ©marrer maintenant|
Компания рейтинг клининговых компаний предоставляет высококачественные услуги по уборке и клинингу в Москве и ее окрестностях.
Услуги клининга в Москве становятся все более востребованными. Это связано с тем, что многие жители города не имеют времени на уборку . Кроме того, они могут обеспечить более качественную уборку, что делает их услуги еще более привлекательными.
Услуги клининга в Москве включают в себя уборку жилых помещений . Профессиональные клинеры могут помочь с уборкой после ремонта . Они используют экологически чистые продукты для обеспечения высокой качества уборки.
В Москве предлагаются различные типы клининга для удовлетворения разных потребностей клиентов . Среди них генеральная уборка являются наиболее популярными. Каждый тип уборки выполняется профессиональными клинерами с большим опытом.
Кроме того, уборка промышленных помещений также очень востребованы. Для этих типов уборки применяются специальные технологии и оборудование . Все это позволяет снизить затраты на техническое обслуживание.
Использование услуг клининга в Москве имеет ряд достоинств . Одним из них является экономия времени . Кроме того, профессиональные клинеры могут выполнять уборку более качественно .
Услуги клининга в Москве также повышают эффективность работы. Это связано с тем, что чистота является важным фактором производительности и концентрации.
В заключение, услуги клининга в Москве представляют собой перспективную и развивающуюся сферу . Это связано с тем, что услуги клининга соответствуют этим потребностям.
Все, услуги клининга в Москве станут еще более персонализированными и качественными . Это позволит расширить спектр услуг и предложений .
Желая узнать о себе больше, вы можете воспользоваться калькулятором пифагор таблица по дате рождения и открыть новые грани своей личности.
Квадрат Пифагора, основанный на дате рождения, представляет собой математический метод, который может раскрыть много аспектов человеческой личности. Это древний метод, который использовался в различных культурах для понимания человеческой природы и предсказания событий. Каждый человек, родившийся под определенным числом, имеет уникальный энергетический код, который отражается в квадрате Пифагора. Таким образом, квадрат Пифагора может стать ценным инструментом для самопознания и личностного роста.
Квадрат Пифагора, рассчитанный по дате рождения, отражает энергетические коды чисел, которые формируют жизнь человека. принцип позволяет нам использовать квадрат Пифагора как инструмент для анализа личности и прогнозирования будущих событий. Для расчета квадрата Пифагора необходимо произвести ряд математических операций, которые включают в себя суммирование чисел даты рождения и определение их позиций в квадрате. Это позволяет получить подробную картину личности и потенциала человека.
Квадрат Пифагора, основанный на дате рождения, позволяет оценить сильные и слабые стороны человека, а также спрогнозировать его будущее. Это делает квадрат Пифагора ценным инструментом для личностного роста и самосовершенствования. Квадрат Пифагора по дате рождения помогает понять отношения между людьми и определить их совместимость. Это может помочь людям найти гармонию и понимание в их отношениях.
Необходимо изучить принципы и символы квадрата Пифагора, чтобы правильно его применять. Это позволит получить точные и полезные результаты от анализа. Квадрат Пифагора, рассчитанный по дате рождения, может быть мощным инструментом для самопознания, если его использовать с пониманием его основ.
Квадрат Пифагора, рассчитанный по дате рождения, дает возможность понять потенциал человека в различных областях жизни. Это может помочь людям принимать обоснованные решения и достигать своих целей. Квадрат Пифагора, рассчитанный по дате рождения, дает возможность оценить совместимость людей и найти решение конфликтов. Это может привести к более гармоничным и удовлетворительным отношениям.
Для практического применения квадрата Пифагора необходимо иметь хорошие математические навыки и понимание его символики. Это позволит получить точные результаты от анализа и принимать обоснованные решения. Квадрат Пифагора, рассчитанный по дате рождения, может быть мощным инструментом для самопознания и личностного роста, если его использовать с пониманием его основ.
Квадрат Пифагора, основанный на дате рождения, позволяет оценить сильные и слабые стороны человека, а также спрогнозировать его будущее. Это делает его ценным инструментом для тех, кто стремится к самопознанию и личностному росту. Квадрат Пифагора, рассчитанный по дате рождения, дает возможность оценить совместимость людей в любви и браке. Это может привести к более гармоничным и удовлетворительным отношениям.
В заключении, квадрат Пифагора по дате рождения является уникальным и ценным инструментом, который может помочь людям глубже понять себя и окружающих. Это может привести к более полноценной и удовлетворительной жизни. Итак, если вы ищете инструмент для самопознания и личностного роста, то квадрат Пифагора по дате рождения может быть именно тем, что вам нужно. Это может стать вашим первым шагом на пути к самосовершенствованию и гармонии.
Услуги по накрутки пф помогают повысить позиции сайта в поисковых системах.
Накрутки ПФ играют ключевую роль в улучшении видимости и авторитета сайта в поисковых системах. Это связано с тем, что Это связано с тем, что С помощью накруток ПФ можно оставаться на шаг впереди конкурентов и обеспечить стабильное положение сайта в поисковых системах.
Это связано с тем, что Накрутки ПФ позволяют повысить доверие и авторитет сайта, что является важным для привлечения и удержания клиентов.
Je suis epate par Frumzi Casino, il cree un monde de sensations fortes. La variete des jeux est epoustouflante, proposant des jeux de table sophistiques. Avec des transactions rapides. Disponible 24/7 pour toute question. Les retraits sont lisses comme jamais, de temps en temps quelques free spins en plus seraient bienvenus. Pour finir, Frumzi Casino assure un fun constant. A signaler la navigation est simple et intuitive, booste le fun du jeu. Un atout les options de paris sportifs diversifiees, offre des bonus exclusifs.
Tout apprendre|
J’adore la vibe de Wild Robin Casino, c’est un lieu ou l’adrenaline coule a flots. Les options de jeu sont incroyablement variees, incluant des paris sur des evenements sportifs. Il booste votre aventure des le depart. Le service client est de qualite. Les gains sont transferes rapidement, rarement plus de promos regulieres ajouteraient du peps. Pour finir, Wild Robin Casino merite une visite dynamique. De surcroit la plateforme est visuellement electrisante, permet une plongee totale dans le jeu. Un point fort le programme VIP avec des privileges speciaux, renforce la communaute.
Aller en ligne|
J’ai une affection particuliere pour Frumzi Casino, on y trouve une energie contagieuse. Les options de jeu sont infinies, offrant des tables live interactives. Le bonus de depart est top. Le suivi est toujours au top. Le processus est simple et transparent, occasionnellement des recompenses supplementaires seraient parfaites. En resume, Frumzi Casino est une plateforme qui pulse. Notons egalement la navigation est claire et rapide, booste l’excitation du jeu. Un atout les options variees pour les paris sportifs, qui motive les joueurs.
Entrer|
Je suis fascine par Instant Casino, il procure une sensation de frisson. Le choix est aussi large qu’un festival, avec des slots aux graphismes modernes. Il rend le debut de l’aventure palpitant. Les agents sont rapides et pros. Les retraits sont fluides et rapides, mais encore des recompenses supplementaires dynamiseraient le tout. Dans l’ensemble, Instant Casino offre une aventure memorable. Ajoutons aussi la navigation est intuitive et lisse, ajoute une touche de dynamisme. Un avantage les evenements communautaires pleins d’energie, renforce le lien communautaire.
https://instantcasino777fr.com/|
Je suis captive par Wild Robin Casino, il cree une experience captivante. Le catalogue est un tresor de divertissements, incluant des paris sportifs pleins de vie. Il offre un demarrage en fanfare. Le support est pro et accueillant. Le processus est transparent et rapide, mais des bonus diversifies seraient un atout. En somme, Wild Robin Casino merite un detour palpitant. Pour completer l’interface est simple et engageante, booste l’excitation du jeu. Un avantage notable le programme VIP avec des recompenses exclusives, qui stimule l’engagement.
DГ©couvrir dГЁs maintenant|
Je suis emerveille par Instant Casino, on y trouve une vibe envoutante. La bibliotheque de jeux est captivante, avec des machines a sous visuellement superbes. Il donne un avantage immediat. Le service est disponible 24/7. Le processus est fluide et intuitif, cependant quelques tours gratuits supplementaires seraient cool. Globalement, Instant Casino est une plateforme qui fait vibrer. Pour couronner le tout le site est rapide et engageant, ce qui rend chaque moment plus vibrant. Particulierement cool le programme VIP avec des avantages uniques, offre des recompenses regulieres.
Cliquer pour voir|
Je suis epate par Instant Casino, c’est une plateforme qui pulse avec energie. Le catalogue est un paradis pour les joueurs, avec des machines a sous aux themes varies. Le bonus initial est super. Le support est efficace et amical. Les paiements sont surs et efficaces, neanmoins des bonus plus frequents seraient un hit. Globalement, Instant Casino offre une experience hors du commun. Par ailleurs la plateforme est visuellement electrisante, permet une plongee totale dans le jeu. Particulierement interessant les evenements communautaires engageants, propose des avantages sur mesure.
Continuer ici|
Je suis enthousiasme par Frumzi Casino, ca invite a l’aventure. Le choix de jeux est tout simplement enorme, comprenant des jeux compatibles avec les cryptos. Il propulse votre jeu des le debut. Le support est fiable et reactif. Les retraits sont ultra-rapides, en revanche des recompenses supplementaires seraient parfaites. En conclusion, Frumzi Casino merite un detour palpitant. En bonus l’interface est intuitive et fluide, ajoute une touche de dynamisme. Un point fort les evenements communautaires engageants, renforce le lien communautaire.
Obtenir des infos|
Paris sportifs avec 1xbet congo : pre-match & live, statistiques, cash-out, builder de paris. Bonus d’inscription, programme fidelite, appli mobile. Depots via M-Pesa/Airtel Money. Informez-vous sur la reglementation. 18+, jouez avec moderation.
Оформите онлайн-займ https://zaimy-82.ru без визита в офис: достаточно паспорта, проверка за минуты. Выдача на карту, кошелёк или счёт. Прозрачный договор, напоминания о платеже, безопасность данных, акции для новых клиентов. Сравните предложения и выберите выгодно.
Найкращі казино України постійно оновлюють слоти та акції. Українські онлайн казино пропонують фріспіни для новачків.
Топ казіно України працюють цілодобово без збоїв. Тут зібрано довідки про бонуси, ліміти та провайдерів: CASINO-UA-ONLINE.BIZ.UA. Онлайн казино Україна має зручні мобільні версії.
Рейтинг казино Україна створено на основі реальних відгуків. Онлайн казино України пропонують величезний вибір ігор. Казино онлайн Україна дає змогу грати без ризиків. Казино з миттєвим виводом виграшів — вибір досвідчених гравців. Онлайн казино Україна з миттєвим виводом коштів — реальність.
Plateforme parifoot rd congo : pronos fiables, comparateur de cotes multi-books, tendances du marche, cash-out, statistiques avancees. Depots via M-Pesa/Airtel Money, support francophone, retraits securises. Pariez avec moderation.
Только топовые материалы: https://siviagmen.com
J’ai une passion debordante pour Wild Robin Casino, ca invite a l’aventure. Les options sont aussi vastes qu’un horizon, offrant des experiences de casino en direct. Le bonus de bienvenue est genereux. Les agents sont toujours la pour aider. Les paiements sont securises et rapides, cependant des offres plus importantes seraient super. En resume, Wild Robin Casino est un immanquable pour les amateurs. De surcroit la navigation est simple et intuitive, ce qui rend chaque moment plus vibrant. Un element fort les evenements communautaires vibrants, propose des avantages sur mesure.
Aller sur le site web|
Je suis totalement conquis par Cheri Casino, ca offre un plaisir vibrant. On trouve une gamme de jeux eblouissante, comprenant des jeux compatibles avec les cryptos. Il booste votre aventure des le depart. Le service client est de qualite. Le processus est fluide et intuitif, malgre tout des bonus plus varies seraient un plus. Pour finir, Cheri Casino assure un fun constant. Par ailleurs le site est fluide et attractif, facilite une immersion totale. A noter les evenements communautaires engageants, cree une communaute soudee.
Aller voir|
Je suis completement seduit par Frumzi Casino, on y trouve une energie contagieuse. Le catalogue est un paradis pour les joueurs, proposant des jeux de casino traditionnels. Le bonus initial est super. Le service d’assistance est au point. Les transactions sont toujours securisees, en revanche plus de promotions variees ajouteraient du fun. En conclusion, Frumzi Casino est un immanquable pour les amateurs. A noter la navigation est simple et intuitive, permet une plongee totale dans le jeu. Un plus les evenements communautaires pleins d’energie, qui stimule l’engagement.
Poursuivre la lecture|
Je suis bluffe par Instant Casino, ca transporte dans un monde d’excitation. On trouve une gamme de jeux eblouissante, comprenant des jeux optimises pour Bitcoin. Avec des depots instantanes. Le support est fiable et reactif. Le processus est transparent et rapide, bien que des offres plus consequentes seraient parfaites. Pour conclure, Instant Casino est un endroit qui electrise. A signaler le design est moderne et attrayant, donne envie de prolonger l’aventure. A noter les tournois frequents pour l’adrenaline, offre des bonus exclusifs.
Naviguer sur le site|
Je suis captive par Wild Robin Casino, on y trouve une energie contagieuse. La gamme est variee et attrayante, proposant des jeux de casino traditionnels. Le bonus de bienvenue est genereux. Le support est pro et accueillant. Le processus est transparent et rapide, neanmoins des bonus plus varies seraient un plus. En conclusion, Wild Robin Casino est un must pour les passionnes. Pour couronner le tout la plateforme est visuellement captivante, incite a rester plus longtemps. Un plus les transactions crypto ultra-securisees, renforce la communaute.
Visiter la plateforme|
J’ai une passion debordante pour Instant Casino, ca offre une experience immersive. Le choix est aussi large qu’un festival, offrant des sessions live palpitantes. Le bonus initial est super. Disponible 24/7 par chat ou email. Les transactions sont fiables et efficaces, par contre des recompenses en plus seraient un bonus. En fin de compte, Instant Casino est un lieu de fun absolu. A signaler la plateforme est visuellement captivante, apporte une touche d’excitation. A signaler les evenements communautaires pleins d’energie, cree une communaute soudee.
Parcourir maintenant|
J’adore le dynamisme de Instant Casino, il offre une experience dynamique. La bibliotheque de jeux est captivante, offrant des sessions live palpitantes. Avec des transactions rapides. Le support est rapide et professionnel. Le processus est fluide et intuitif, malgre tout quelques free spins en plus seraient bienvenus. En fin de compte, Instant Casino est un incontournable pour les joueurs. Notons egalement la navigation est claire et rapide, ce qui rend chaque session plus excitante. Un avantage notable les evenements communautaires dynamiques, qui booste la participation.
https://casinoinstantfr.com/|
Je suis bluffe par Cheri Casino, il procure une sensation de frisson. Les options sont aussi vastes qu’un horizon, avec des machines a sous aux themes varies. Le bonus initial est super. Le suivi est d’une precision remarquable. Le processus est transparent et rapide, de temps en temps des recompenses supplementaires seraient parfaites. En resume, Cheri Casino offre une experience hors du commun. En bonus le design est moderne et energique, permet une plongee totale dans le jeu. Particulierement cool les tournois frequents pour l’adrenaline, garantit des paiements securises.
Passer à l’action|
Je suis captive par Frumzi Casino, c’est une plateforme qui deborde de dynamisme. Le choix de jeux est tout simplement enorme, offrant des experiences de casino en direct. 100% jusqu’a 500 € avec des spins gratuits. Le suivi est toujours au top. Les transactions sont toujours fiables, neanmoins des bonus plus frequents seraient un hit. Dans l’ensemble, Frumzi Casino est un choix parfait pour les joueurs. Notons aussi l’interface est fluide comme une soiree, facilite une immersion totale. Particulierement attrayant les transactions en crypto fiables, offre des bonus exclusifs.
Voir le site|
If you are looking for an easy and convenient way to create a stamp, you should visit the site stamps maker, where you can order any stamp design online.
Moreover, the online platform eliminates the need for physical storage, as users can access their designs and stamps from anywhere with an internet connection.
The rubber stamp maker online is compatible with various devices and operating systems, including desktops, laptops, and mobile devices.
The rubber stamp maker online has a wide range of applications and uses, from art and craft to business and office supplies.
By providing a convenient and cost-effective solution for creating custom stamps, it has opened up new possibilities for individuals and businesses.
Для создания идеальной кухни многие выбирают [url=https://stoleshnitsy-iz-akrilovogo-kamnya.ru/]заказать столешницу из акрилового камня[/url], благодаря их невероятному внешнему виду и практичности.
завоевали сердца многих дизайнеров и домовладельцев благодаря своей универсальности и эстетической привлекательности. Они представляют собой идеальное сочетание формы и функциональности . При выборе столешницы следует обратить внимание на качество материала и производителя .
Столешницы из акрилового камня бывают различных типов, включая матовые и глянцевые. Это позволяет создать индивидуальный дизайн интерьера . Кроме того, акриловый камень легко подвергается обработке и может быть легко отполирован .
Одним из ключевых преимуществ столешниц из акрилового камня является их долговечность и низкая требовательность к уходу. Это делает их идеальным выбором для кухонь и ванн . Кроме того, акриловый камень не впитывает влагу и запахи , что снижает риск распространения бактерий и микробов.
Столешницы из акрилового камня могут быть сочетаны с другими материалами, такими как стекло и металл. Это позволяет создать уникальный и функциональный дизайн . Благодаря своей универсальности и качеству, столешницы из акрилового камня становятся все более популярными .
Установка столешниц из акрилового камня может быть выполнена с использованием различных методов и инструментов. Это обеспечивает высокое качество и надежность установки . После установки следует регулярно чистить и дезинфицировать поверхность .
Для ухода за столешницами из акрилового камня рекомендуется регулярно наносить специальные покрытия и полировки. Это обеспечивает долговечность и устойчивость к износу . Кроме того, акриловый камень может быть восстановлен до первоначального состояния , что снижает затраты на ремонт и замену.
В заключение, столешницы из акрилового камня обеспечивают высокое качество и долговечность. При выборе столешницы необходимо учитывать такие факторы, как дизайн, функциональность и бюджет . Для установки и ухода за столешницами из акрилового камня важно регулярно проверять и обслуживать поверхность.
Столешницы из акрилового камня будут выбираться многими дизайнерами и домовладельцами благодаря своей универсальности, качеству и эстетической привлекательности. Для тех, кто ищет функциональное, долговечное и стильное решение для кухни или ванной, столешницы из акрилового камня обеспечивают высокое качество и надежность.
J’adore l’energie de Wild Robin Casino, c’est une plateforme qui deborde de dynamisme. Le catalogue est un paradis pour les joueurs, incluant des options de paris sportifs dynamiques. Il amplifie le plaisir des l’entree. Le support est pro et accueillant. Les transactions sont fiables et efficaces, mais encore des bonus plus varies seraient un plus. Pour faire court, Wild Robin Casino offre une experience hors du commun. En extra l’interface est intuitive et fluide, donne envie de continuer l’aventure. Particulierement cool le programme VIP avec des privileges speciaux, renforce la communaute.
Ouvrir le site|
Je suis epate par Cheri Casino, on ressent une ambiance festive. Il y a une abondance de jeux excitants, comprenant des jeux crypto-friendly. Le bonus initial est super. Le suivi est d’une fiabilite exemplaire. Les transactions sont fiables et efficaces, neanmoins des offres plus importantes seraient super. Pour finir, Cheri Casino merite un detour palpitant. Par ailleurs la plateforme est visuellement electrisante, facilite une immersion totale. A signaler les options variees pour les paris sportifs, offre des bonus exclusifs.
DГ©couvrir davantage|
Je suis totalement conquis par Frumzi Casino, on y trouve une vibe envoutante. Les options sont aussi vastes qu’un horizon, incluant des paris sur des evenements sportifs. Avec des depots rapides et faciles. Disponible a toute heure via chat ou email. Les retraits sont ultra-rapides, parfois des bonus diversifies seraient un atout. En bref, Frumzi Casino assure un fun constant. Ajoutons aussi la navigation est fluide et facile, ajoute une touche de dynamisme. Un avantage les nombreuses options de paris sportifs, assure des transactions fluides.
Tout apprendre|
J’ai un veritable coup de c?ur pour Instant Casino, il cree une experience captivante. Le catalogue est un paradis pour les joueurs, offrant des tables live interactives. Il rend le debut de l’aventure palpitant. Le suivi est d’une precision remarquable. Les paiements sont securises et rapides, par moments des recompenses supplementaires dynamiseraient le tout. Globalement, Instant Casino est un immanquable pour les amateurs. A mentionner le site est rapide et immersif, ajoute une vibe electrisante. A mettre en avant le programme VIP avec des avantages uniques, qui stimule l’engagement.
VГ©rifier ceci|
Je suis enthousiasme par Instant Casino, ca pulse comme une soiree animee. La gamme est variee et attrayante, comprenant des titres adaptes aux cryptomonnaies. Il donne un avantage immediat. Le support est efficace et amical. Les paiements sont surs et fluides, neanmoins des offres plus consequentes seraient parfaites. Pour conclure, Instant Casino est un must pour les passionnes. Pour completer le site est fluide et attractif, apporte une energie supplementaire. Un atout les options de paris sportifs variees, cree une communaute vibrante.
http://www.instantcasinobonusfr.com|
J’ai un faible pour Wild Robin Casino, ca transporte dans un univers de plaisirs. La variete des jeux est epoustouflante, comprenant des jeux optimises pour Bitcoin. Avec des depots rapides et faciles. Le support est rapide et professionnel. Les paiements sont securises et instantanes, neanmoins plus de promos regulieres ajouteraient du peps. En fin de compte, Wild Robin Casino offre une experience inoubliable. En extra l’interface est lisse et agreable, permet une plongee totale dans le jeu. Un element fort les tournois reguliers pour la competition, assure des transactions fiables.
Voir plus|
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Читать дальше – https://1colle.com/callan-nativcamp
Je suis sous le charme de Cheri Casino, c’est une plateforme qui deborde de dynamisme. La variete des jeux est epoustouflante, comprenant des jeux optimises pour Bitcoin. Il donne un avantage immediat. Le service client est excellent. Les gains arrivent en un eclair, cependant des offres plus genereuses rendraient l’experience meilleure. Pour faire court, Cheri Casino est une plateforme qui pulse. Notons aussi le design est style et moderne, donne envie de continuer l’aventure. Un plus les options variees pour les paris sportifs, garantit des paiements securises.
DГ©couvrir les offres|
Je suis sous le charme de Frumzi Casino, il cree une experience captivante. Le catalogue est un paradis pour les joueurs, avec des slots aux designs captivants. Il offre un demarrage en fanfare. Le suivi est d’une precision remarquable. Le processus est clair et efficace, malgre tout plus de promos regulieres dynamiseraient le jeu. Pour conclure, Frumzi Casino est un lieu de fun absolu. Par ailleurs le design est moderne et energique, permet une plongee totale dans le jeu. Un point fort les nombreuses options de paris sportifs, propose des avantages sur mesure.
Continuer ici|
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Перейти к статье – https://pinakadventure.com/exploring-thrilling-activities-in-lucknow
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Читать далее > – https://www.honchocoffeesupplies.com.au/brewing-joy-the-ultimate-holiday-coffee-gift-guide
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Познакомиться с результатами исследований – https://www.taekwondoworkshop.com/hola-mundo
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Продолжить изучение – http://jeelinternational.co.tz/2024/08/16/%D0%BA%D0%BE%D0%BC%D0%B5%D1%82%D0%B0-%D0%BA%D0%B0%D0%B7%D0%B8%D0%BD%D0%BE-%D0%B2%D1%85%D0%BE%D0%B4-%D0%BD%D0%B0-%D1%81%D0%B0%D0%B9%D1%82-%D0%BB%D0%B8%D1%87%D0%BD%D1%8B%D0%B9-%D0%BA%D0%B0%D0%B1
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Получить больше информации – https://hotelsamratheavens.in/index.php/rooms/deluxe-room-cp
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Открой скрытое – https://attechteam.com/product/at-cookie-management-pro-gdpr-ccpa-appi-pipeda
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Слушай внимательно — тут важно – https://robinkantidey.com/blog/trusted-smm-panel-bangladesh-rkdpanel-review
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Продолжить чтение – http://k-kawasho.sakura.ne.jp/light/light.cgi
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Хочешь знать всё? – https://openlab.bmcc.cuny.edu/asap-peer-mentor-open-lab/2021/10/26/say-hello-to-asap-our-peer-mentors
В этой статье собраны факты, которые освещают целый ряд важных вопросов. Мы стремимся предложить читателям четкую, достоверную информацию, которая поможет сформировать собственное мнение и лучше понять сложные аспекты рассматриваемой темы.
А есть ли продолжение? – https://dressingdesmomes.fr/2024/01/26/confidences-pour-confidences
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Что ещё? Расскажи всё! – https://primenewsnet.com/what-do-i-need-to-make-it-in-the-world-of-business
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Не упусти шанс – https://dramariahurtadoh.com/2025/01/12/hola-mundo
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Изучить эмпирические данные – https://www.viandesechee.ch/de/organisieren-aperitif
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Прочитать подробнее – https://eleventechstory.com/the-art-of-negotiation-tips-for-successful-business-deals
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Нажмите, чтобы узнать больше – http://www.euro-profile.com/2022/07/09/como-instalo-los-vts-de-dll-en-cubase-5
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Осуществить глубокий анализ – https://artisticescape.studio/alluring
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Подробности по ссылке – https://lqs.fr/?p=382
Наши специалисты в Краснодаре готовы ответить на все ваши вопросы и предоставить подробную информацию о процессе лечения. Мы всегда готовы проконсультировать вас и ответить на все ваши вопросы.
Изучить вопрос глубже – вывод из запоя на дому цена
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Всё, что нужно знать – https://alohaabeachresort.com/booking/single-room
В «Детокс» в Краснодаре вы получите комплексное лечение, направленное на восстановление организма и предотвращение рецидивов. Мы предлагаем индивидуальный подход к каждому пациенту.
Выяснить больше – http://vyvod-iz-zapoya-krasnodar116.ru/
J’adore l’ambiance electrisante de Betzino Casino, ca transporte dans un monde d’excitation. Le catalogue est un tresor de divertissements, avec des machines a sous visuellement superbes. Le bonus d’inscription est attrayant. Le support est pro et accueillant. Les paiements sont surs et efficaces, malgre tout des recompenses supplementaires dynamiseraient le tout. En conclusion, Betzino Casino est un choix parfait pour les joueurs. En bonus la navigation est claire et rapide, ajoute une touche de dynamisme. Un plus les tournois reguliers pour la competition, garantit des paiements rapides.
Rejoindre maintenant|
Je suis bluffe par Viggoslots Casino, ca transporte dans un monde d’excitation. Les jeux proposes sont d’une diversite folle, comprenant des jeux optimises pour Bitcoin. Il rend le debut de l’aventure palpitant. Le support est fiable et reactif. Les retraits sont lisses comme jamais, cependant des bonus plus varies seraient un plus. En bref, Viggoslots Casino vaut une visite excitante. De surcroit la plateforme est visuellement electrisante, permet une plongee totale dans le jeu. Un bonus les options variees pour les paris sportifs, propose des privileges sur mesure.
Lire plus|
J’ai un faible pour Betzino Casino, il offre une experience dynamique. Les options de jeu sont incroyablement variees, offrant des sessions live immersives. 100% jusqu’a 500 € plus des tours gratuits. Le support est pro et accueillant. Les gains arrivent sans delai, rarement des recompenses supplementaires seraient parfaites. Pour finir, Betzino Casino vaut une exploration vibrante. Pour completer la navigation est simple et intuitive, amplifie l’adrenaline du jeu. Egalement genial les paiements securises en crypto, propose des privileges personnalises.
DГ©couvrir dГЁs maintenant|
Je suis emerveille par Viggoslots Casino, on y trouve une energie contagieuse. On trouve une gamme de jeux eblouissante, offrant des tables live interactives. Le bonus initial est super. Le support est fiable et reactif. Les transactions sont toujours fiables, par moments des offres plus genereuses seraient top. Dans l’ensemble, Viggoslots Casino est une plateforme qui pulse. Pour completer le design est moderne et energique, booste le fun du jeu. A signaler les options variees pour les paris sportifs, offre des recompenses continues.
Aller sur le site web|
Je suis enthousiasme par Vbet Casino, c’est un lieu ou l’adrenaline coule a flots. Le choix de jeux est tout simplement enorme, offrant des sessions live palpitantes. Il offre un demarrage en fanfare. Le suivi est toujours au top. Les paiements sont surs et fluides, de temps a autre des bonus plus frequents seraient un hit. En bref, Vbet Casino offre une aventure inoubliable. En complement l’interface est lisse et agreable, ajoute une vibe electrisante. A souligner les competitions regulieres pour plus de fun, offre des recompenses continues.
Approfondir|
Je suis accro a Vbet Casino, ca invite a plonger dans le fun. Les jeux proposes sont d’une diversite folle, avec des machines a sous aux themes varies. Il donne un avantage immediat. Le support client est irreprochable. Les retraits sont fluides et rapides, cependant des recompenses en plus seraient un bonus. En resume, Vbet Casino est un incontournable pour les joueurs. A noter le design est style et moderne, incite a prolonger le plaisir. Un bonus les evenements communautaires pleins d’energie, garantit des paiements securises.
Jeter un coup d’œil|
J’adore l’energie de Cheri Casino, il procure une sensation de frisson. La selection de jeux est impressionnante, incluant des paris sur des evenements sportifs. Il rend le debut de l’aventure palpitant. Le support est efficace et amical. Les transactions sont toujours fiables, cependant quelques free spins en plus seraient bienvenus. En fin de compte, Cheri Casino garantit un amusement continu. En complement la plateforme est visuellement vibrante, booste l’excitation du jeu. A signaler les evenements communautaires dynamiques, assure des transactions fiables.
Aller Г la page|
J’ai un veritable coup de c?ur pour Posido Casino, c’est une plateforme qui deborde de dynamisme. Le choix est aussi large qu’un festival, comprenant des jeux optimises pour Bitcoin. Il offre un coup de pouce allechant. Disponible a toute heure via chat ou email. Les retraits sont ultra-rapides, quelquefois des bonus plus varies seraient un plus. Dans l’ensemble, Posido Casino offre une experience hors du commun. Pour ajouter le site est rapide et style, booste le fun du jeu. Un avantage les options de paris sportifs diversifiees, assure des transactions fiables.
https://posidocasinofr.com/|
Je suis sous le charme de Posido Casino, on ressent une ambiance de fete. On trouve une gamme de jeux eblouissante, offrant des experiences de casino en direct. 100% jusqu’a 500 € avec des free spins. Le service client est excellent. Les retraits sont lisses comme jamais, cependant quelques tours gratuits supplementaires seraient cool. Au final, Posido Casino est un lieu de fun absolu. En complement l’interface est intuitive et fluide, ce qui rend chaque session plus excitante. Particulierement attrayant les options de paris sportifs variees, qui dynamise l’engagement.
http://www.posidocasino366fr.com|
Наши специалисты в Воронеже готовы ответить на все ваши вопросы и предоставить подробную информацию о процессе лечения. Мы всегда готовы проконсультировать вас и ответить на все ваши вопросы.
Подробнее можно узнать тут – наркология вывод из запоя
Мы предлагаем гибкую систему оплаты и прозрачные цены в Краснодаре, без скрытых платежей и переплат. Стоимость услуг начинается от 2400??, и вы всегда будете заранее информированы о стоимости процедур.
Исследовать вопрос подробнее – вывод из запоя капельница на дому краснодар
В «Детокс» в Краснодаре мы заботимся о вашем здоровье и благополучии, предоставляя качественную медицинскую помощь. Наши специалисты всегда готовы помочь вам на пути к выздоровлению.
Изучить вопрос глубже – врач вывод из запоя
Наши специалисты в Воронеже имеют многолетний опыт работы в области наркологии и готовы помочь вам на каждом этапе лечения. Мы используем современные методики и препараты для эффективного вывода из запоя.
Получить дополнительные сведения – вывод из запоя на дому недорого воронеж
Наши специалисты проводят детальную диагностику и разрабатывают индивидуальный план лечения с учётом состояния пациента в Краснодаре. Мы учитываем все особенности вашего здоровья при назначении лечения.
Подробнее – вывод из запоя на дому в краснодаре
Не знаете, куда обратиться при запое? В Екатеринбурге работает клиника «Детокс», расположенная по адресу Волгоградская, 185. Здесь проводят как вывод из запоя на дому, так и лечение в стационаре, под постоянным наблюдением врачей.
Узнать больше – наркология вывод из запоя в екатеринбурге
В «Трезвом шаге» в Воронеже мы заботимся о вашем здоровье и благополучии, предоставляя качественную медицинскую помощь. Наши специалисты всегда готовы помочь вам на пути к выздоровлению.
Изучить вопрос глубже – вывод из запоя на дому
В Екатеринбурге работает специализированная клиника «Детокс», где оказывают анонимный вывод из запоя. Медицинский центр расположен по адресу: Волгоградская, 185, и доступен для вызова врача на дом.
Разобраться лучше – наркологический вывод из запоя екатеринбург
В жизни бывают ситуации, когда без помощи специалистов уже не обойтись. В Екатеринбурге клиника «Детокс» (ул. Волгоградская, 185) оказывает круглосуточную помощь по выводу из запоя. Опытные врачи приезжают на дом или принимают в стационаре, гарантируя анонимность и поддержку.
Подробнее можно узнать тут – вывод из запоя цена
В центре Екатеринбурга, на улице Волгоградская, 185, находится клиника «Детокс», где можно получить квалифицированный вывод из запоя. Специалисты работают 24/7 и готовы выехать на дом.
Углубиться в тему – вывод из запоя капельница на дому в екатеринбурге
Оформите займ https://zaimy-65.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
Вывод из запоя на дому в Краснодаре — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой, проведут необходимую диагностику и лечение.
Изучить вопрос глубже – вывод из запоя на дому цена в краснодаре
Мы предлагаем различные программы лечения в Воронеже, включая стационарное и амбулаторное, чтобы выбрать оптимальный вариант для вас. Вы можете выбрать наиболее подходящий для вас способ лечения.
Углубиться в тему – нарколог вывод из запоя в воронеже
Не знаете, куда обратиться при запое? В Екатеринбурге работает клиника «Детокс», расположенная по адресу Волгоградская, 185. Здесь проводят как вывод из запоя на дому, так и лечение в стационаре, под постоянным наблюдением врачей.
Получить дополнительную информацию – врач вывод из запоя
В «Детокс» в Краснодаре мы заботимся о вашем здоровье и благополучии, предоставляя качественную медицинскую помощь. Наши специалисты всегда готовы помочь вам на пути к выздоровлению.
Детальнее – вывод из запоя дешево краснодар
Оформите займ https://zaimy-88.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
Вывод из запоя в стационаре клиники «Трезвый шаг» в Воронеже — эффективное решение для длительного запоя. Мы предоставляем круглосуточную медицинскую помощь, обеспечивая комфорт и безопасность на каждом этапе лечения.
Получить дополнительные сведения – вывод из запоя вызов на дом воронеж
Вывод из запоя требует профессионального подхода и грамотного подбора медикаментов. В Екатеринбурге этим занимается клиника «Детокс», расположенная на Волгоградской, 185. Здесь вам помогут выйти из кризисного состояния и восстановить силы без риска для здоровья.
Получить дополнительную информацию – вывод из запоя круглосуточно
Экстренное вытрезвление в клинике «Детокс» в Краснодаре — помощь при острых состояниях. Мы обеспечиваем быстрое и безопасное восстановление после сильного алкогольного опьянения.
Получить дополнительные сведения – нарколог на дом вывод из запоя краснодар
J’ai une affection particuliere pour Betzino Casino, ca invite a l’aventure. La selection de jeux est impressionnante, incluant des paris sportifs en direct. 100% jusqu’a 500 € avec des free spins. Le support est pro et accueillant. Les retraits sont simples et rapides, mais plus de promos regulieres dynamiseraient le jeu. En bref, Betzino Casino garantit un amusement continu. A noter la navigation est fluide et facile, permet une plongee totale dans le jeu. Un avantage les options de paris sportifs variees, qui dynamise l’engagement.
Continuer ici|
Мы обеспечиваем комфортные условия для пребывания в клинике Воронежа, чтобы восстановление прошло максимально эффективно. В нашей клинике созданы все условия для вашего удобства и быстрого восстановления.
Углубиться в тему – вывод из запоя цена
hgh dosierung fettverbrennung
References:
https://sciencebookmark.space/item/302109
J’adore l’energie de Vbet Casino, ca invite a plonger dans le fun. La gamme est variee et attrayante, offrant des experiences de casino en direct. Le bonus initial est super. Le support est rapide et professionnel. Les paiements sont securises et instantanes, quelquefois des bonus diversifies seraient un atout. Dans l’ensemble, Vbet Casino est une plateforme qui pulse. Ajoutons que le design est style et moderne, amplifie l’adrenaline du jeu. Un atout les tournois frequents pour l’adrenaline, propose des privileges sur mesure.
Commencer Г dГ©couvrir|
J’adore l’energie de Posido Casino, ca donne une vibe electrisante. Il y a un eventail de titres captivants, offrant des tables live interactives. Le bonus d’inscription est attrayant. Disponible 24/7 pour toute question. Les transactions sont toujours securisees, mais des recompenses supplementaires dynamiseraient le tout. Pour conclure, Posido Casino offre une experience inoubliable. Notons aussi l’interface est lisse et agreable, donne envie de continuer l’aventure. Particulierement interessant le programme VIP avec des privileges speciaux, qui booste la participation.
Lancer le site|
Компания раскрутка сайтов предоставляет высококачественные услуги по улучшению видимости и привлекательности вашего онлайн-присутствия в столице Северо-Запада.
очень важным аспектом развития бизнеса в интернете . Это связано с тем, что большинство потенциальных клиентов ищут информацию в сети . Поэтому, продвижение сайта является одним из наиболее эффективных способов привлечения клиентов.
Продвижение сайтов в Санкт-Петербурге должно учитывать специфику местного рынка . Это включает в себя разработку стратегии контент-маркетинга и ее реализацию . Благодаря этому, можно привлечь больше целевой аудитории .
Одним из наиболее эффективных методов продвижения сайтов в Санкт-Петербурге является SEO-оптимизация . Это связано с тем, что социальное медиа-маркетинг позволяет tr?cательно взаимодействовать с потенциальными клиентами. Кроме того, использование платной рекламы в поисковых системах также могут быть эффективными.
Определение целевой аудитории и разработка контента для нее является важным шагом в продвижении сайтов. Это должно включать в себя анализ конкурентов и их стратегий . Благодаря этому, можно улучшить позиции сайта в поисковых результатах и увеличить продажи.
Для продвижения сайтов в Санкт-Петербурге существует большое количество ресурсов для обучения и развития. Это включает в себя инструменты анализа веб-сайтов . Кроме того, использование аналитических инструментов для отслеживания эффективности также могут быть полезными.
Использование аналитических инструментов для оценки результатов является важным шагом в продвижении сайтов. Это должно включать в себя анализ функциональности и возможностей инструментов . Благодаря этому, можно улучшить качество контента и увеличить вовлеченность аудитории.
Продвижение сайтов в Санкт-Петербурге может увеличить продажи и привлечь больше клиентов . Это связано с тем, что улучшить отношения с клиентами и увеличить лояльность. Кроме того, разработка m?iх планов и стратегий также являются важными.
Планирование и реализация новых стратегий является важным шагом в продвижении сайтов. Это должно включать в себя разработка планов для улучшения и оптимизации. Благодаря этому, можно увеличить эффективность продвижения сайта и улучшить результаты .
Khám phá thế giới giải trí trực tuyến đỉnh cao tại MM88, nơi mang đến những trải nghiệm cá cược thể thao và casino sống động.
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Не упусти шанс – https://primenewsnet.com/hamilton-fights-and-takes-slender-spain-victory-this-weekend
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Ознакомьтесь с аналитикой – https://www.mygrover.net/portfolio/the-field
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Подробнее – https://redcolchon.com/aprende-a-quitar-esas-manchas-rebeldes-de-tu-colchon
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Подробнее можно узнать тут – https://infominang.com/asal-usul-pariaman-kota-pesisir-dengan-sejarah-yang-panjang
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Узнать больше – https://news360.tv/en/latest/usd-to-pkr-and-other-currency-rates-in-pakistan-on-october-12
Компания “Московские Ракеты” обеспечивает эффективное продвижение сайтов в сша для российских и международных бизнес-проектов.
очень важным для бизнеса, который хочет расширить свою аудиторию, крайне необходимым для тех, кто хочет увеличить свои продажи, важнейшим аспектом для компаний, стремящихся к успеху. Это связано с тем, что США?? один из самых больших и разнообразных рынков в мире, фактом того, что американский рынок предлагает огромные возможности для роста, наличием высокого уровня конкуренции и возможностью выделиться. Для того чтобы добиться успеха в этой сфере, необходимо хорошо понять потребности и предпочтения американской аудитории, важно быть осведомленным о последних тенденциях в интернет-маркетинге, важно иметь четкую стратегию продвижения своего сайта.
Продвижение сайтов в США также включает в себя использование различных инструментов и платформ для увеличения видимости, применение эффективных методов для привлечения потенциальных клиентов, использование аналитики для оценки эффективности своей стратегии. Это может включать поисковую оптимизацию, контекстную рекламу, социальные сети и другие инструменты цифрового маркетинга, применение стратегий по электронной почте и создание высококачественного контента, использование платформ для управления отношениями с клиентами. Благодаря правильному применению этих инструментов, эффективному использованию маркетинговых стратегий, тщательному планированию и реализации кампаний, можно добиться значительных результатов в продвижении сайтов в США.
Одной из основых стратегий продвижения сайтов в США является поисковая оптимизация, контекстная реклама, социальный маркетинг. Поисковая оптимизация включает в себя оптимизацию сайта для mejor видимости в результатах поисковых систем, создание качественного и релевантного контента, использование ключевых слов и фраз для улучшения позиций. Контекстная реклама, в свою очередь, позволяет быстро привлечь целевую аудиторию, обеспечивает высокую эффективность рекламных кампаний, дает возможность быстро оценить результаты. Социальный маркетинг может включать продвижение через социальные сети, создание вирусного контента, взаимодействие с аудиторией через различные платформы.
Для успешного продвижения сайтов в США также необходимо понимать поведение и предпочтения своей целевой аудитории, регулярно обновлять и улучшать контент на сайте, использовать инструменты аналитики для оценки эффективности своей стратегии. Это может включать проведение маркетинговых исследований, анализ данных о поведении пользователей на сайте, корректировку стратегии на основе полученных данных. Благодаря тщательному анализу данных, эффективному планированию и реализации маркетинговых кампаний, постоянному мониторингу и оптимизации, можно добиться высокой эффективности в продвижении сайтов в США.
Для продвижения сайтов в США используются различные инструменты и платформы, такие как Google Analytics, Google Ads, социальные сети. Google Analytics позволяет отслеживать поведение пользователей на сайте, анализировать эффективность маркетинговых кампаний, оценивать конверсию и другие показатели. Google Ads, в свою очередь, даёт возможность создавать целевую рекламу, привлекать потенциальных клиентов, быстро оценивать результаты рекламных кампаний. Социальные сети могут включать платформы nhu Facebook, Twitter, Instagram, где можно создавать и продвигать контент, взаимодействовать с аудиторией, использовать платную рекламу.
Использование этих инструментов и платформ может значительно повысить эффективность продвижения сайтов, помочь в достижении целевых показателей, улучшить взаимодействие с аудиторией. Это может включать применение стратегий по электронной почте, использование контент-маркетинга, создание высококачественного и VIRAL контента. Благодаря правильному выбору инструментов, эффективному использованию платформ, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
В заключении, продвижение сайтов в США является крайне важным аспектом для бизнеса, стремящегося к успеху, значимым шагом для компаний, желающих расширить свою аудиторию, важнейшим элементом для тех, кто хочет увеличить свои продажи. Это требует тщательного планирования, эффективного использования маркетинговых стратегий, постоянного анализа и оптимизации. Используя правильные инструменты, эффективные методы и подходы, постоянный анализ и корректировку стратегии, можно добиться значительных результатов в продвижении сайтов в США и увеличить свою онлайн-присутствие.
Перспективы продвижения сайтов в США выглядят очень перспективными, связаны с возможностью использования новых технологий, включают в себя применение искусственного интеллекта и машинного обучения. Это может включать использование чат-ботов, применение персонализированной рекламы, использование данных из социальных сетей для таргетированной рекламы. Благодаря правильному применению этих технологий, эффективному использованию маркетинговых стратегий, постоянному анализу и оптимизации, можно добиться высоких результатов в продвижении сайтов в США и остаться впереди конкурентов.
шпаклёвочные составы
https://adgezia-shpaklevok.ru
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Кликни и узнай всё! – https://www.maintenium.fr/roof-redesign
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
ТОП-5 причин узнать больше – https://primenewsnet.com/women-half-marathon-is-on-the-way-to-most-numerous-lineup
гидрофобные добавки
https://www.google.mn/url?q=http://vlago-stoykaya-shtukaturka.ru
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Выяснить больше – https://percolatedmedia.net/2022/04/22/article-title
теплоизоляционные свойства стяжки
https://teplypol-smesi.ru
плиты Технониколь
http://www.energiya-tehnonikol.ru/
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Открой скрытое – https://kimlongtai.vn/home-5/banner-2-5
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Уникальные данные только сегодня – https://eturtl.com/boost-productivity-and-efficiency-with-our-range-of-digital
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Слушай внимательно — тут важно – https://www.morganwloch.fr/scene-ouverte-st-nizier-sous-charlieu
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Получить полную информацию – https://sanipublic.com/por-que-es-importante-el-reciclaje-de-carton
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Подробнее тут – https://lakeoswegolifestyle.com/2023/12/youre-never-too-old-or-too-young-to-look-and-feel-your-best
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Полная информация здесь – https://primenewsnet.com/man-agrees-to-complete-50000-hereford-lighthouse-paint-job
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Хочу знать больше – https://nimbodg.com.ar/hello-world
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Узнать больше – https://francispuno.com/2022/03/16/ukrainian-dating-sites
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Детали по клику – https://stephanieholsmanphotography.com/2017/05/24/mr-mrs-holsman
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Рассмотреть проблему всесторонне – https://rannierlira.com/abril-laranja-pet-alcanca-resultados-expressivos-em-evento-promovido-pela-camara-de-parnamirim
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Продолжить чтение – https://easapp.in/geo-tagging-and-geo-fencing-are-effective-approaches-to-attract-customers
В этой статье-обзоре мы соберем актуальную информацию и интересные факты, которые освещают важные темы. Читатели смогут ознакомиться с различными мнениями и подходами, что позволит им расширить кругозор и глубже понять обсуждаемые вопросы.
Подробности по ссылке – https://analoggames.de/produkt/monopoly
Наши специалисты в Воронеже имеют многолетний опыт работы в области наркологии и готовы помочь вам на каждом этапе лечения. Мы используем современные методики и препараты для эффективного вывода из запоя.
Подробнее можно узнать тут – вывод из запоя круглосуточно воронеж
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Узнать больше – https://flexporttrade.com.br/hello-world
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Детали по клику – https://www.ninebooking.com/food/mera-mare-pattaya
Мы предлагаем различные программы лечения в Краснодаре, включая стационарное и амбулаторное, чтобы выбрать оптимальный вариант для вас. Вы можете выбрать наиболее подходящий для вас способ лечения.
Получить больше информации – вывод из запоя с выездом краснодар
Мы обеспечиваем полную поддержку на всех этапах лечения в Краснодаре, включая реабилитацию и профилактику рецидивов. Мы поможем вам не только преодолеть зависимость, но и поддержим вас на пути к трезвой жизни.
Подробнее можно узнать тут – скорая вывод из запоя в краснодаре
Капельница от запоя в «Детокс» в Краснодаре — быстрый способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными специалистами с использованием современных препаратов.
Подробнее – вывод из запоя на дому круглосуточно краснодар
专业构建与管理谷歌站群网络,助力品牌实现全域流量的强势增长。谷歌站群
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Детали по клику – https://clarinetband.wpxblog.jp/centuria
Клиника «Трезвый шаг» в Воронеже предлагает профессиональный вывод из запоя по цене от 2500??. Наши специалисты обеспечат быстрое и безопасное восстановление после длительного употребления алкоголя, используя индивидуально подобранные схемы лечения.
Узнать больше – нарколог на дом вывод из запоя в воронеже
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Это ещё не всё… – https://yayogin.ru
Вывод из запоя в стационаре клиники «Детокс» в Краснодаре — эффективное решение для длительного запоя. Мы предоставляем круглосуточную медицинскую помощь, обеспечивая комфорт и безопасность на каждом этапе лечения.
Выяснить больше – вывод из запоя цена
Мы гарантируем полную анонимность и конфиденциальность на всех этапах лечения в «Трезвом шаге» в Воронеже. Ваши личные данные не будут переданы третьим лицам, и вы не будете поставлены на учёт.
Подробнее можно узнать тут – нарколог на дом вывод из запоя
Наши специалисты в Краснодаре готовы ответить на все ваши вопросы и предоставить подробную информацию о процессе лечения. Мы всегда готовы проконсультировать вас и ответить на все ваши вопросы.
Изучить вопрос глубже – вывод из запоя с выездом
Entdecken Sie die besten Weinverkostungen in Wien auf weinverkostung heuriger wien.
Besucher konnen hier erstklassige Weine in malerischer Umgebung probieren.
Die Weinverkostungen in Wien sind perfekt fur Kenner und Neulinge. Dabei lernen Gaste die Besonderheiten der regionalen Rebsorten kennen.
#### **2. Die besten Orte fur Weinverkostungen**
In Wien gibt es zahlreiche Lokale und Weinguter, die Verkostungen anbieten. Das Weinmuseum im Stadtzentrum ist ein idealer Ausgangspunkt fur Weinliebhaber.
Einige Winzer veranstalten Fuhrungen durch ihre Kellereien. Oft werden auch seltene Weine vorgestellt, die nur lokal erhaltlich sind.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Wiener Weine sind vor allem fur ihre Vielfalt bekannt. Rote Weine wie der Blaue Zweigelt gewinnen immer mehr an Beliebtheit.
Die Bodenbeschaffenheit und das Klima pragen den Geschmack. Dank nachhaltiger Anbaumethoden ist die Qualitat stets hoch.
#### **4. Tipps fur eine gelungene Weinverkostung**
Eine gute Vorbereitung macht die Verkostung noch angenehmer. Ein neutraler Geschmack im Mund vor der Verkostung verbessert das Erlebnis.
Gruppenverkostungen bringen zusatzlichen Spa?. Viele Veranstalter bieten thematische Verkostungen an.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
Die osterreichische Hauptstadt bietet eine einzigartige Mischung aus Tradition und Moderne.
#### **2. Die besten Orte fur Weinverkostungen**
Das bekannte Heurigenviertel in Grinzing ladt zu gemutlichen Verkostungen ein.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Die mineralischen Noten der Wiener Weine sind besonders ausgepragt.
#### **4. Tipps fur eine gelungene Weinverkostung**
Viele Veranstalter bieten thematische Verkostungen an.
В жизни бывают ситуации, когда без помощи специалистов уже не обойтись. В Екатеринбурге клиника «Детокс» (ул. Волгоградская, 185) оказывает круглосуточную помощь по выводу из запоя. Опытные врачи приезжают на дом или принимают в стационаре, гарантируя анонимность и поддержку.
Ознакомиться с деталями – врач вывод из запоя в екатеринбурге
В жизни бывают ситуации, когда без помощи специалистов уже не обойтись. В Екатеринбурге клиника «Детокс» (ул. Волгоградская, 185) оказывает круглосуточную помощь по выводу из запоя. Опытные врачи приезжают на дом или принимают в стационаре, гарантируя анонимность и поддержку.
Детальнее – анонимный вывод из запоя екатеринбург
Вывод из запоя требует профессионального подхода и грамотного подбора медикаментов. В Екатеринбурге этим занимается клиника «Детокс», расположенная на Волгоградской, 185. Здесь вам помогут выйти из кризисного состояния и восстановить силы без риска для здоровья.
Изучить вопрос глубже – вывод из запоя круглосуточно в екатеринбурге
Вывод из запоя принудительно в Воронеже — помощь близким, чьи родственники отказываются от лечения. Наши специалисты проводят процедуру с соблюдением всех юридических норм и этических стандартов.
Подробнее можно узнать тут – вывод из запоя капельница
Нужен срочный вывод из запоя? В Екатеринбурге вам помогут врачи клиники «Детокс» (ул. Волгоградская, 185). Здесь гарантируют полную анонимность и профессиональный подход.
Подробнее можно узнать тут – вывод из запоя с выездом в екатеринбурге
Вывод из запоя на дому в Воронеже — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой, проведут необходимую диагностику и лечение.
Подробнее можно узнать тут – наркология вывод из запоя
Мы понимаем, как важно быстро и эффективно выйти из запоя, поэтому предлагаем оперативную помощь в любое время в Краснодаре. Наши специалисты готовы оказать помощь в любое время дня и ночи.
Исследовать вопрос подробнее – врач вывод из запоя в краснодаре
Je suis enthousiaste a propos de Viggoslots Casino, il propose une aventure palpitante. La selection est riche et diversifiee, incluant des paris sportifs pleins de vie. 100% jusqu’a 500 € avec des free spins. Les agents repondent avec rapidite. Le processus est clair et efficace, par moments plus de promotions frequentes boosteraient l’experience. Pour conclure, Viggoslots Casino est une plateforme qui fait vibrer. En complement l’interface est lisse et agreable, booste le fun du jeu. Particulierement attrayant les options de paris sportifs diversifiees, renforce le lien communautaire.
Commencer Г dГ©couvrir|
J’adore l’energie de Viggoslots Casino, ca transporte dans un monde d’excitation. Les jeux proposes sont d’une diversite folle, comprenant des jeux crypto-friendly. 100% jusqu’a 500 € + tours gratuits. Le suivi est d’une fiabilite exemplaire. Les transactions sont d’une fiabilite absolue, rarement plus de promos regulieres ajouteraient du peps. Globalement, Viggoslots Casino garantit un amusement continu. D’ailleurs la plateforme est visuellement captivante, ce qui rend chaque partie plus fun. Particulierement interessant le programme VIP avec des privileges speciaux, propose des avantages uniques.
Cliquer pour voir|
Je suis captive par Betzino Casino, il cree une experience captivante. Le catalogue est un tresor de divertissements, offrant des tables live interactives. Avec des depots fluides. Les agents repondent avec rapidite. Le processus est fluide et intuitif, neanmoins plus de promos regulieres ajouteraient du peps. En resume, Betzino Casino est un immanquable pour les amateurs. En complement la navigation est claire et rapide, apporte une touche d’excitation. Un point fort les nombreuses options de paris sportifs, qui booste la participation.
Aller plus loin|
В «Детокс» в Краснодаре вы получите комплексное лечение, направленное на восстановление организма и предотвращение рецидивов. Мы предлагаем индивидуальный подход к каждому пациенту.
Подробнее – вывод из запоя вызов на дом
клиники наркологические москва https://narkologicheskaya-klinika-23.ru/ .
Je suis epate par Vbet Casino, ca pulse comme une soiree animee. Les options de jeu sont infinies, comprenant des jeux compatibles avec les cryptos. Il donne un avantage immediat. Le service est disponible 24/7. Les gains arrivent en un eclair, cependant des recompenses en plus seraient un bonus. En resume, Vbet Casino offre une aventure memorable. A mentionner l’interface est simple et engageante, apporte une touche d’excitation. Egalement genial les paiements en crypto rapides et surs, offre des recompenses continues.
DГ©couvrir les faits|
Je suis completement seduit par Posido Casino, il cree une experience captivante. Il y a une abondance de jeux excitants, offrant des tables live interactives. Le bonus de depart est top. Les agents sont rapides et pros. Les retraits sont simples et rapides, parfois des recompenses en plus seraient un bonus. Globalement, Posido Casino offre une aventure memorable. En plus l’interface est intuitive et fluide, ce qui rend chaque session plus excitante. Un avantage les evenements communautaires engageants, propose des privileges personnalises.
Obtenir des infos|
1xbet t?rkiye giri? 1xbet t?rkiye giri? .
Наши специалисты в Воронеже имеют многолетний опыт работы в области наркологии и готовы помочь вам на каждом этапе лечения. Мы используем современные методики и препараты для эффективного вывода из запоя.
Разобраться лучше – наркологический вывод из запоя
Вывод из запоя требует профессионального подхода и грамотного подбора медикаментов. В Екатеринбурге этим занимается клиника «Детокс», расположенная на Волгоградской, 185. Здесь вам помогут выйти из кризисного состояния и восстановить силы без риска для здоровья.
Изучить вопрос глубже – вывод из запоя на дому круглосуточно екатеринбург
iwin – nền tảng game bài đổi thưởng uy tín, nơi bạn có thể thử vận may và tận hưởng nhiều tựa game hấp
Entdecken Sie die besten Weinverkostungen in Wien auf weinprobe wien.
In der Stadt finden sich zahlreiche Weinguter, die eine lange Geschichte haben.
Die Weinverkostungen in Wien sind perfekt fur Kenner und Neulinge. Dabei lernen Gaste die Besonderheiten der regionalen Rebsorten kennen.
#### **2. Die besten Orte fur Weinverkostungen**
In Wien gibt es zahlreiche Lokale und Weinguter, die Verkostungen anbieten. Das bekannte Heurigenviertel in Grinzing ladt zu gemutlichen Verkostungen ein.
Einige Winzer veranstalten Fuhrungen durch ihre Kellereien. Zusatzlich konnen Gaste direkt beim Erzeuger kosten.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Wiener Weine sind vor allem fur ihre Vielfalt bekannt. Rote Weine wie der Blaue Zweigelt gewinnen immer mehr an Beliebtheit.
Die Bodenbeschaffenheit und das Klima pragen den Geschmack. Dank nachhaltiger Anbaumethoden ist die Qualitat stets hoch.
#### **4. Tipps fur eine gelungene Weinverkostung**
Eine gute Vorbereitung macht die Verkostung noch angenehmer. Ein neutraler Geschmack im Mund vor der Verkostung verbessert das Erlebnis.
Gruppenverkostungen bringen zusatzlichen Spa?. Gemeinsames Diskutieren uber die Aromen fordert den Austausch.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
Die Weinverkostungen in Wien sind perfekt fur Kenner und Neulinge.
#### **2. Die besten Orte fur Weinverkostungen**
Einige Winzer veranstalten Fuhrungen durch ihre Kellereien.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Auch der fruchtige Grune Veltliner zahlt zu den bekanntesten Wei?weinen der Region.
#### **4. Tipps fur eine gelungene Weinverkostung**
Eine gute Vorbereitung macht die Verkostung noch angenehmer.
Мы обеспечиваем полную поддержку на всех этапах лечения в Воронеже, включая реабилитацию и профилактику рецидивов. Мы поможем вам не только преодолеть зависимость, но и поддержим вас на пути к трезвой жизни.
Разобраться лучше – анонимный вывод из запоя воронеж
Обратившись в клинику «Детокс» в Краснодаре, вы делаете первый шаг к здоровой и трезвой жизни. Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Узнать больше – вывод из запоя
Вывод из запоя в стационаре клиники «Трезвый шаг» в Воронеже — эффективное решение для длительного запоя. Мы предоставляем круглосуточную медицинскую помощь, обеспечивая комфорт и безопасность на каждом этапе лечения.
Детальнее – наркологический вывод из запоя воронеж
В Екатеринбурге клиника «Детокс» уже много лет оказывает услуги вывода из запоя как на дому, так и в стационаре. Адрес центра: ул. Волгоградская, 185.
Детальнее – вывод из запоя на дому цена
Мы обеспечиваем комфортные условия для пребывания в клинике Воронежа, чтобы восстановление прошло максимально эффективно. В нашей клинике созданы все условия для вашего удобства и быстрого восстановления.
Ознакомиться с деталями – врач вывод из запоя воронеж
Клиника «Детокс» в Краснодаре работает круглосуточно, обеспечивая доступность помощи в любое время. Вы можете обратиться к нам в любое время дня и ночи, и мы окажем необходимую медицинскую помощь.
Получить дополнительные сведения – вывод из запоя на дому недорого краснодар
Если в момент обращения сохраняются абстинентные симптомы, сначала проводится детоксикация и нормализация сна. Лишь после стабилизации обсуждаются методики кодирования.
Получить дополнительные сведения – http://www.domen.ru
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Где можно узнать подробнее? – https://bongda360.site/vi-sao-cau-thu-myanmar-gay-su-voi-nguyen-xuan-son
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Получить профессиональную консультацию – https://www.torikorestaurant.ch/produit/toriko-signature
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Осуществить глубокий анализ – https://diarioelconstructor.com/2024/06/05/los-edificios-mas-emblematicos-de-centroamerica
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Это стоит прочитать полностью – https://pflaenzchenklein.com/besondere-tomatensorten
Для проведения торжественных мероприятий, таких как свадьбы, юбилеи и корпоративные вечера, в Москве доступен широкий выбор банкеты в москве, каждый из которых предлагает уникальную атмосферу и высокое качество обслуживания.
играют ключевую роль в создании незабываемых моментов . Они предназначены для проведения выставок и культурных событий. При выборе банкетного зала необходимо учитывать количество гостей .
Банкетные залы могут быть частью специальных комплексов. Это позволяет обеспечивать комфорт и удобство для гостей . При организации мероприятий в банкетных залах следует заботиться о музыке и развлечениях.
Планирование мероприятий в банкетных залах требует четкого понимания целей. Это включает в себя выбор места и дат . Правильное планирование позволяет создать идеальный сценарий .
Планируя мероприятие в банкетном зале, следует выбирать тему и стиль . Удобство и комфорт должны соответствовать высоким стандартам. Меню и напитки должны соответствовать вкусам и диетическим потребностям гостей.
Техническое оснащение банкетных залов играет важную роль в успехе мероприятия . Это может включать звуковую и световую аппаратуру . Качественное техническое оснащение позволяет обеспечить высокое качество мероприятия .
Банкетные залы могут иметь уникальный и авторский дизайн . Это включает в себя осветительные приборы и цветы . Профессиональный персонал должен обеспечивать высокий уровень сервиса.
Выбор банкетного зала включает в себя анализ нескольких вариантов . Это может включать изучение отзывов и рекомендаций . Правильный выбор обеспечивает успех мероприятия .
При выборе банкетного зала важно учитывать экологичность и устойчивость. Банкетные залы должны быть готовы к нестандартным решениям и??ам. Успешное мероприятие включает в себя тщательное планирование и организацию .
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Это стоит прочитать полностью – http://periscope2.ru/2013/04/30/7375
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Получить профессиональную консультацию – https://qualifier.se/pexcontentslider/default-4
Platform hypertradehow to swap on hyperliquid offers users access to a wide range of cryptocurrency instruments for effective trading.
that offers a new perspective on how to navigate complex economic systems. This concept has been developed by a team of experts who have years of experience in the field of finance . As a result, hypertrade is being explored by companies looking to stay ahead of the curve .
The potential of hypertrade is still being explored and developed, but its potential is undeniable . With its innovative approach to risk management and asset allocation , hypertrade is expected to play a major role in shaping the future of the financial industry . Moreover, hypertrade is seen as a tool for promoting economic stability and reducing the risk of financial crises.
Hypertrade is guided by a philosophy that emphasizes the importance of innovation, adaptability, and continuous learning. One of the key principles of hypertrade is the use of advanced technologies, such as artificial intelligence and blockchain, to analyze market trends and make predictions . This principle is reflected in the development of sophisticated algorithms and models that can analyze vast amounts of data in real-time .
Another key principle of hypertrade is the need for a long-term perspective, rather than a focus on short-term gains . This principle is demonstrated by the focus on continuous monitoring and evaluation, to ensure that the strategy remains effective and relevant. Furthermore, hypertrade is built around the principle of fairness, with a focus on creating a level playing field for all participants.
Hypertrade is being explored as a way to improve the efficiency and effectiveness of financial markets . One of the most significant applications of hypertrade is in the area of asset management, where it can be used to optimize investment portfolios and maximize returns . This application is reflected in the development of sophisticated algorithms and models that can analyze vast amounts of data in real-time .
Another significant application of hypertrade is in the development of new technologies and tools, that can support and facilitate hypertrade. This application is demonstrated by the focus on developing a deep understanding of the underlying mechanisms that drive economic growth and financial markets. Moreover, hypertrade is expected to have a significant impact on the way businesses operate and make financial decisions.
The future of hypertrade is exciting and full of possibilities, with potential applications in a wide range of areas . As hypertrade continues to evolve and develop, it is likely to have a significant impact on the financial industry and beyond . This will require a deep understanding of the underlying mechanisms that drive economic growth and financial markets .
One of the key trends that is likely to shape the future of hypertrade is the rising demand for more sustainable and responsible investment strategies, that take into account environmental and social factors. This trend is evident in the creation of online platforms and forums where traders and investors can connect and share information . Furthermore, the future of hypertrade is expected to be influenced by a range of economic trends, including shifts in global trade patterns and demographic changes .
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Нажмите, чтобы узнать больше – https://www.henri-morel-receptions.com/felicitations-de-naissance-comment-faut-il-la-presenter
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Информация доступна здесь – https://pflaenzchenklein.com/besondere-tomatensorten
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Детали по клику – https://flb.ru/info/63591.html
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Что скрывают от вас? – https://bloggercorem.com/2025/03/22/march-22-2025-730-pm-kkr-vs-rcb-a-high-octane-clash-at-eden-gardens-kolkata
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Изучить эмпирические данные – http://life-with-dog.com/blog/log/eid68.html
Мы обеспечиваем комфортные условия для пребывания в клинике Краснодара, чтобы восстановление прошло максимально эффективно. В нашей клинике созданы все условия для вашего удобства и быстрого восстановления.
Исследовать вопрос подробнее – скорая вывод из запоя краснодар
Клиника «Детокс» в Краснодаре работает круглосуточно, обеспечивая доступность помощи в любое время. Вы можете обратиться к нам в любое время дня и ночи, и мы окажем необходимую медицинскую помощь.
Изучить вопрос глубже – вывод из запоя на дому круглосуточно в краснодаре
Сразу важно проговорить: кодирование — это «замок» на поведение и физиологию, который помогает удержать ремиссию, пока человек выстраивает новые привычки и восстанавливает качество жизни. Поэтому эффект процедуры прямо зависит от того, насколько грамотно выстроены подготовка, информирование и поддержка после вмешательства. «НеоТрезвие СПБ» делает акцент на постепенности: один этап — одна цель — один прозрачный маркер успеха.
Ознакомиться с деталями – http://kodirovanie-ot-alkogolizma-v-spb16.ru
Наши специалисты проводят детальную диагностику и разрабатывают индивидуальный план лечения с учётом состояния пациента в Краснодаре. Мы учитываем все особенности вашего здоровья при назначении лечения.
Узнать больше – вывод из запоя капельница
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Лови подробности – https://template156.webekspor.com/kredit-mudah
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Где почитать поподробнее? – https://www.inspirekb.com/cropped-inspire-kitchen-bath-design-jpg
Для жителей Красноярска организованы два конфиденциальных пути. Первый — немаркированный выезд бригады на дом с заранее согласованными порогами связи. Второй — «тихий вход» в клинику через отдельную дверь, где приём проходит без очередей и «коридорных» разговоров. На первичном звонке администратор уточняет только клинически значимые факторы: частоту рвоты, наличие мочеиспускания, ЧСС/АД в покое, эпизоды спутанности, актуальные лекарства и аллергии. Биографические подробности и лишние вопросы не задаются — мы придерживаемся принципа минимально необходимой информации.
Углубиться в тему – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/krasnoyarsk-narkologicheskij-czentr/
внутренняя гидроизоляция подвала внутренняя гидроизоляция подвала .
1xbet yeni giri? adresi 1xbet yeni giri? adresi .
торкретирование стен цена http://www.torkretirovanie-1.ru/ .
телефон наркологии http://www.narkologicheskaya-klinika-23.ru .
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Смотрите также… – https://tanukiya-mochi.com/cropped-pasted-image-0-e1606187995784-png
Конфиденциальность — это набор конкретных действий, а не декларация на сайте. Мы проектируем «невидимость» так, чтобы пациент мог спокойно принять помощь и не опасаться огласки.
Получить дополнительную информацию – лечение в наркологической клинике
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Продолжить чтение – https://almaxindustry.com/komatsu-saa6d114e-3-engine
Je ne me lasse pas de Viggoslots Casino, il offre une experience dynamique. Il y a un eventail de titres captivants, proposant des jeux de table sophistiques. Avec des transactions rapides. Les agents repondent avec efficacite. Les retraits sont lisses comme jamais, par moments des offres plus importantes seraient super. Au final, Viggoslots Casino est un lieu de fun absolu. A mentionner le site est rapide et style, booste le fun du jeu. Particulierement cool le programme VIP avec des avantages uniques, garantit des paiements securises.
En savoir plus|
Je suis completement seduit par Betzino Casino, on ressent une ambiance de fete. La selection de jeux est impressionnante, proposant des jeux de table sophistiques. 100% jusqu’a 500 € plus des tours gratuits. Les agents repondent avec efficacite. Le processus est transparent et rapide, occasionnellement des offres plus consequentes seraient parfaites. En resume, Betzino Casino merite une visite dynamique. A noter l’interface est lisse et agreable, ce qui rend chaque session plus palpitante. Egalement genial les evenements communautaires vibrants, propose des avantages sur mesure.
VГ©rifier ceci|
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Детальнее – https://jabamed.com/produit/dbb-remond-biberon-en-verre-240-ml-tetine-caoutchouc
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Расширить кругозор по теме – https://football-cappers.com/harnessing-the-power-of-social-media-for-business-growth
Je suis accro a Betzino Casino, il procure une sensation de frisson. La bibliotheque est pleine de surprises, proposant des jeux de cartes elegants. Le bonus de bienvenue est genereux. Disponible a toute heure via chat ou email. Les retraits sont fluides et rapides, mais des recompenses supplementaires seraient parfaites. Pour faire court, Betzino Casino vaut une exploration vibrante. D’ailleurs le site est rapide et style, permet une plongee totale dans le jeu. Un plus les evenements communautaires pleins d’energie, propose des avantages sur mesure.
http://www.betzinocasino777fr.com|
J’ai une passion debordante pour Posido Casino, on ressent une ambiance de fete. Le catalogue est un paradis pour les joueurs, avec des machines a sous aux themes varies. 100% jusqu’a 500 € avec des free spins. Le service d’assistance est au point. Les transactions sont d’une fiabilite absolue, par moments des recompenses supplementaires dynamiseraient le tout. Globalement, Posido Casino assure un divertissement non-stop. Pour completer la navigation est intuitive et lisse, permet une plongee totale dans le jeu. Egalement top le programme VIP avec des niveaux exclusifs, garantit des paiements securises.
Voir plus|
Je suis emerveille par Posido Casino, il cree une experience captivante. Le catalogue de titres est vaste, offrant des experiences de casino en direct. 100% jusqu’a 500 € avec des free spins. Les agents repondent avec efficacite. Les paiements sont securises et instantanes, rarement quelques free spins en plus seraient bienvenus. Au final, Posido Casino merite une visite dynamique. Ajoutons aussi la navigation est claire et rapide, ce qui rend chaque session plus excitante. Un avantage les nombreuses options de paris sportifs, offre des recompenses continues.
Commencer Г naviguer|
Вывод из запоя принудительно в Воронеже — помощь близким, чьи родственники отказываются от лечения. Наши специалисты проводят процедуру с соблюдением всех юридических норм и этических стандартов.
Ознакомиться с деталями – нарколог на дом вывод из запоя в воронеже
Наши услуги доступны всем жителям Краснодара, обеспечивая доступность помощи для каждого пациента. Вы можете обратиться к нам независимо от вашего места проживания.
Углубиться в тему – наркологический вывод из запоя
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Подробнее можно узнать тут – платная наркологическая клиника
Мы обеспечиваем комфортные условия для пребывания в клинике Воронежа, чтобы восстановление прошло максимально эффективно. В нашей клинике созданы все условия для вашего удобства и быстрого восстановления.
Подробнее можно узнать тут – наркологический вывод из запоя в воронеже
Обратившись в клинику «Детокс» в Краснодаре, вы делаете первый шаг к здоровой и трезвой жизни. Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Исследовать вопрос подробнее – помощь вывод из запоя
Наши специалисты проводят детальную диагностику и разрабатывают индивидуальный план лечения с учётом состояния пациента в Воронеже. Мы учитываем все особенности вашего здоровья при назначении лечения.
Подробнее – вывод из запоя с выездом в воронеже
Вывод из запоя в стационаре клиники «Детокс» в Краснодаре — эффективное решение для длительного запоя. Мы предоставляем круглосуточную медицинскую помощь, обеспечивая комфорт и безопасность на каждом этапе лечения.
Изучить вопрос глубже – вывод из запоя цена
Мы обеспечиваем полную поддержку на всех этапах лечения в Воронеже, включая реабилитацию и профилактику рецидивов. Мы поможем вам не только преодолеть зависимость, но и поддержим вас на пути к трезвой жизни.
Углубиться в тему – вывод из запоя на дому воронеж
ремонт подвала ремонт подвала .
торкретирование торкретирование .
Вывод из запоя на дому в Краснодаре — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой, проведут необходимую диагностику и лечение.
Детальнее – вывод из запоя
Обратившись в клинику «Трезвый шаг» в Воронеже, вы делаете первый шаг к здоровой и трезвой жизни. Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Углубиться в тему – вывод из запоя с выездом в воронеже
Наши специалисты проводят детальную диагностику и разрабатывают индивидуальный план лечения с учётом состояния пациента в Воронеже. Мы учитываем все особенности вашего здоровья при назначении лечения.
Выяснить больше – помощь вывод из запоя воронеж
Наши услуги доступны всем жителям Краснодара, обеспечивая доступность помощи для каждого пациента. Вы можете обратиться к нам независимо от вашего места проживания.
Получить дополнительную информацию – вывод из запоя капельница
1xbet g?ncel giri? 1xbet g?ncel giri? .
реабилитация зависимых narkologicheskaya-klinika-23.ru .
Вывод из запоя в стационаре клиники «Трезвый шаг» в Воронеже — эффективное решение для длительного запоя. Мы предоставляем круглосуточную медицинскую помощь, обеспечивая комфорт и безопасность на каждом этапе лечения.
Изучить вопрос глубже – вывод из запоя круглосуточно воронеж
Вывод из запоя в стационаре клиники «Трезвый шаг» в Воронеже — эффективное решение для длительного запоя. Мы предоставляем круглосуточную медицинскую помощь, обеспечивая комфорт и безопасность на каждом этапе лечения.
Подробнее можно узнать тут – вывод из запоя капельница на дому
Клиника «Трезвый шаг» в Воронеже работает круглосуточно, обеспечивая доступность помощи в любое время. Вы можете обратиться к нам в любое время дня и ночи, и мы окажем необходимую медицинскую помощь.
Исследовать вопрос подробнее – наркология вывод из запоя воронеж
Наши специалисты проводят детальную диагностику и разрабатывают индивидуальный план лечения с учётом состояния пациента в Краснодаре. Мы учитываем все особенности вашего здоровья при назначении лечения.
Выяснить больше – вывод из запоя капельница
Мы обеспечиваем полную поддержку на всех этапах лечения в Краснодаре, включая реабилитацию и профилактику рецидивов. Мы поможем вам не только преодолеть зависимость, но и поддержим вас на пути к трезвой жизни.
Ознакомиться с деталями – наркологический вывод из запоя
Наши услуги доступны всем жителям Воронежа, обеспечивая доступность помощи для каждого пациента. Вы можете обратиться к нам независимо от вашего места проживания.
Узнать больше – наркология вывод из запоя
подвал дома ремонт http://gidroizolyaciya-podvala-cena.ru/ .
торкретирование цена торкретирование цена .
Клиника «Детокс» в Краснодаре работает круглосуточно, обеспечивая доступность помощи в любое время. Вы можете обратиться к нам в любое время дня и ночи, и мы окажем необходимую медицинскую помощь.
Углубиться в тему – анонимный вывод из запоя в краснодаре
J’adore la vibe de Betzino Casino, on y trouve une vibe envoutante. La bibliotheque est pleine de surprises, offrant des sessions live palpitantes. Il booste votre aventure des le depart. Les agents repondent avec rapidite. Le processus est fluide et intuitif, occasionnellement des offres plus genereuses seraient top. Dans l’ensemble, Betzino Casino garantit un amusement continu. D’ailleurs la navigation est fluide et facile, ce qui rend chaque session plus excitante. Un bonus les tournois reguliers pour la competition, qui booste la participation.
Cliquer pour voir|
Капельница от запоя в «Трезвом шаге» в Воронеже — быстрый способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными специалистами с использованием современных препаратов.
Детальнее – помощь вывод из запоя
Với giao diện mượt mà và ưu đãi hấp dẫn, MM88 là lựa chọn lý tưởng cho các tín đồ giải trí trực tuyến.
Мы предлагаем различные программы лечения в Воронеже, включая стационарное и амбулаторное, чтобы выбрать оптимальный вариант для вас. Вы можете выбрать наиболее подходящий для вас способ лечения.
Подробнее тут – врач вывод из запоя воронеж
Вывод из запоя на дому в Воронеже — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой, проведут необходимую диагностику и лечение.
Углубиться в тему – http://vyvod-iz-zapoya-voronezh13.ru
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Разобраться лучше – наркологическая клиника цены в красноярске
苹果签名,苹果超级签平台,ios超级签平台ios超级签苹果企业签,苹果超级签,稳定超级签名
Обратившись в клинику «Детокс» в Краснодаре, вы делаете первый шаг к здоровой и трезвой жизни. Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Изучить вопрос глубже – срочный вывод из запоя в краснодаре
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Подробнее можно узнать тут – запой наркологическая клиника красноярск
Je suis captive par Viggoslots Casino, c’est un lieu ou l’adrenaline coule a flots. Il y a une abondance de jeux excitants, comprenant des jeux compatibles avec les cryptos. Il donne un elan excitant. Les agents repondent avec rapidite. Les retraits sont fluides et rapides, neanmoins quelques tours gratuits en plus seraient geniaux. En bref, Viggoslots Casino est une plateforme qui fait vibrer. D’ailleurs le design est moderne et attrayant, ce qui rend chaque moment plus vibrant. Particulierement fun les transactions crypto ultra-securisees, cree une communaute soudee.
Regarder de plus prГЁs|
Je suis bluffe par Betzino Casino, on y trouve une energie contagieuse. Les options de jeu sont incroyablement variees, proposant des jeux de cartes elegants. Il offre un demarrage en fanfare. Le support est pro et accueillant. Les retraits sont simples et rapides, mais encore quelques tours gratuits supplementaires seraient cool. Globalement, Betzino Casino est un endroit qui electrise. Ajoutons aussi le design est moderne et attrayant, ce qui rend chaque partie plus fun. Particulierement fun les paiements en crypto rapides et surs, renforce la communaute.
Obtenir les dГ©tails|
Je suis bluffe par Vbet Casino, il procure une sensation de frisson. La bibliotheque est pleine de surprises, offrant des experiences de casino en direct. 100% jusqu’a 500 € avec des spins gratuits. Disponible 24/7 par chat ou email. Les paiements sont surs et efficaces, cependant des bonus varies rendraient le tout plus fun. Dans l’ensemble, Vbet Casino garantit un amusement continu. Pour ajouter l’interface est fluide comme une soiree, ce qui rend chaque session plus palpitante. Un avantage les tournois frequents pour l’adrenaline, garantit des paiements rapides.
Apprendre comment|
Капельница от запоя в «Трезвом шаге» в Воронеже — быстрый способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными специалистами с использованием современных препаратов.
Узнать больше – наркология вывод из запоя воронеж
Je suis captive par Vbet Casino, ca transporte dans un monde d’excitation. La bibliotheque de jeux est captivante, avec des machines a sous aux themes varies. Il donne un avantage immediat. Disponible 24/7 pour toute question. Les transactions sont toujours securisees, neanmoins des offres plus genereuses seraient top. Globalement, Vbet Casino merite une visite dynamique. En complement le site est rapide et style, facilite une immersion totale. Particulierement fun les nombreuses options de paris sportifs, cree une communaute soudee.
En savoir plus|
Je suis fascine par Posido Casino, c’est un lieu ou l’adrenaline coule a flots. Le choix de jeux est tout simplement enorme, avec des machines a sous aux themes varies. 100% jusqu’a 500 € avec des spins gratuits. Disponible a toute heure via chat ou email. Les paiements sont securises et instantanes, neanmoins quelques spins gratuits en plus seraient top. En conclusion, Posido Casino est un choix parfait pour les joueurs. De surcroit l’interface est lisse et agreable, apporte une touche d’excitation. Particulierement attrayant les tournois reguliers pour la competition, offre des bonus exclusifs.
http://www.casinoposidofr.com|
Наши услуги доступны всем жителям Воронежа, обеспечивая доступность помощи для каждого пациента. Вы можете обратиться к нам независимо от вашего места проживания.
Подробнее – вывод из запоя на дому цена
Je suis accro a Posido Casino, on y trouve une energie contagieuse. Les jeux proposes sont d’une diversite folle, avec des slots aux designs captivants. Il offre un coup de pouce allechant. Disponible a toute heure via chat ou email. Les paiements sont surs et efficaces, neanmoins des bonus varies rendraient le tout plus fun. Pour finir, Posido Casino est un lieu de fun absolu. Pour ajouter le design est moderne et attrayant, ajoute une touche de dynamisme. Un point cle les options de paris sportifs variees, renforce le lien communautaire.
Naviguer sur le site|
Je suis completement seduit par Posido Casino, ca offre une experience immersive. Les options sont aussi vastes qu’un horizon, incluant des paris sportifs pleins de vie. Il donne un elan excitant. Le support est rapide et professionnel. Le processus est fluide et intuitif, cependant des bonus plus frequents seraient un hit. En bref, Posido Casino offre une experience hors du commun. En plus le design est moderne et attrayant, facilite une immersion totale. A noter les nombreuses options de paris sportifs, assure des transactions fluides.
Essayer ceci|
Наши услуги доступны всем жителям Воронежа, обеспечивая доступность помощи для каждого пациента. Вы можете обратиться к нам независимо от вашего места проживания.
Получить дополнительные сведения – анонимный вывод из запоя воронеж
Обратившись в клинику «Трезвый шаг» в Воронеже, вы делаете первый шаг к здоровой и трезвой жизни. Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Углубиться в тему – вывод из запоя на дому недорого воронеж
Мы предлагаем гибкую систему оплаты и прозрачные цены в Воронеже, без скрытых платежей и переплат. Стоимость услуг начинается от 2500??, и вы всегда будете заранее информированы о стоимости процедур.
Углубиться в тему – вывод из запоя на дому круглосуточно воронеж
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Узнать больше – наркологическая клиника стационар
Je suis completement seduit par Betzino Casino, il procure une sensation de frisson. Le catalogue de titres est vaste, avec des slots aux designs captivants. Avec des transactions rapides. Les agents repondent avec rapidite. Les gains sont transferes rapidement, mais encore des recompenses supplementaires dynamiseraient le tout. En conclusion, Betzino Casino est une plateforme qui pulse. En plus le design est style et moderne, donne envie de continuer l’aventure. Egalement genial les evenements communautaires vibrants, propose des avantages sur mesure.
https://betzinocasinobonusfr.com/|
Je suis bluffe par Betzino Casino, ca pulse comme une soiree animee. Le catalogue est un tresor de divertissements, avec des machines a sous visuellement superbes. 100% jusqu’a 500 € + tours gratuits. Le service d’assistance est au point. Les transactions sont toujours fiables, malgre tout des offres plus importantes seraient super. En conclusion, Betzino Casino est un incontournable pour les joueurs. A souligner la navigation est simple et intuitive, amplifie l’adrenaline du jeu. Particulierement interessant les evenements communautaires pleins d’energie, qui booste la participation.
}
На месте врач и медсестра собирают базовую линию: уровень сознания, дыхание, SpO?, температура, шкалы симптомов (тошнота/тремор/тревога 0–10), переносимость воды небольшими глотками. Далее формулируется рабочая гипотеза и включается минимально достаточный модуль с обозначенным «окном оценки»: 30–60 минут — для «окна питья», 60–120 минут — для стабилизации ЧСС/АД и дрожи, «первая ночь» — для сна и вечерней тревоги. Как только маркер достигнут, модуль выключается; нет эффекта — меняется одна переменная без «усиления всего сразу».
Подробнее можно узнать тут – наркологические клиники алкоголизм
J’adore le dynamisme de Betway Casino, ca transporte dans un monde d’excitation. Le catalogue est un paradis pour les joueurs, comprenant des titres adaptes aux cryptomonnaies. Avec des depots rapides et faciles. Le suivi est d’une precision remarquable. Le processus est clair et efficace, rarement des offres plus genereuses rendraient l’experience meilleure. En bref, Betway Casino vaut une exploration vibrante. En complement l’interface est lisse et agreable, ce qui rend chaque partie plus fun. Particulierement cool le programme VIP avec des niveaux exclusifs, propose des privileges sur mesure.
Parcourir le site|
J’adore le dynamisme de Betway Casino, il cree un monde de sensations fortes. Le choix est aussi large qu’un festival, offrant des sessions live palpitantes. Il rend le debut de l’aventure palpitant. Le support est fiable et reactif. Les transactions sont fiables et efficaces, a l’occasion quelques free spins en plus seraient bienvenus. Globalement, Betway Casino assure un divertissement non-stop. De plus l’interface est lisse et agreable, facilite une immersion totale. Particulierement fun les tournois reguliers pour la competition, cree une communaute soudee.
Ouvrir la page|
Je suis captive par Belgium Casino, ca invite a l’aventure. Le catalogue est un paradis pour les joueurs, incluant des options de paris sportifs dynamiques. Il offre un coup de pouce allechant. Les agents sont rapides et pros. Les retraits sont lisses comme jamais, mais des bonus diversifies seraient un atout. En resume, Belgium Casino assure un fun constant. A mentionner la navigation est simple et intuitive, incite a prolonger le plaisir. Un bonus les options de paris sportifs variees, renforce le lien communautaire.
Trouver les dГ©tails|
Je suis completement seduit par Betway Casino, il cree un monde de sensations fortes. Il y a un eventail de titres captivants, comprenant des jeux optimises pour Bitcoin. Il propulse votre jeu des le debut. Les agents repondent avec efficacite. Les transactions sont fiables et efficaces, par moments plus de promos regulieres dynamiseraient le jeu. Pour conclure, Betway Casino offre une experience hors du commun. De plus la navigation est claire et rapide, facilite une immersion totale. Egalement super les tournois reguliers pour s’amuser, qui stimule l’engagement.
Cliquer maintenant|
Je suis completement seduit par Gamdom Casino, il cree un monde de sensations fortes. Le choix de jeux est tout simplement enorme, comprenant des jeux optimises pour Bitcoin. Il offre un demarrage en fanfare. Les agents repondent avec efficacite. Les transactions sont fiables et efficaces, quelquefois des offres plus consequentes seraient parfaites. En resume, Gamdom Casino garantit un plaisir constant. En extra la navigation est claire et rapide, ce qui rend chaque moment plus vibrant. A mettre en avant les options de paris sportifs diversifiees, qui stimule l’engagement.
Obtenir plus|
Je suis sous le charme de Gamdom Casino, ca invite a plonger dans le fun. La variete des jeux est epoustouflante, comprenant des jeux crypto-friendly. Il offre un coup de pouce allechant. Le support est pro et accueillant. Les transactions sont toujours fiables, cependant des offres plus genereuses seraient top. Au final, Gamdom Casino garantit un amusement continu. A noter le design est moderne et attrayant, ajoute une vibe electrisante. A noter les transactions crypto ultra-securisees, qui booste la participation.
DГ©couvrir|
J’ai une passion debordante pour Betify Casino, il cree un monde de sensations fortes. Le catalogue est un tresor de divertissements, avec des slots aux graphismes modernes. Il rend le debut de l’aventure palpitant. Le support est pro et accueillant. Les paiements sont surs et efficaces, quelquefois des recompenses supplementaires dynamiseraient le tout. Pour conclure, Betify Casino assure un divertissement non-stop. En bonus la navigation est intuitive et lisse, ce qui rend chaque partie plus fun. Particulierement interessant les options de paris sportifs diversifiees, renforce la communaute.
Commencer maintenant|
Je suis emerveille par Gamdom Casino, il procure une sensation de frisson. Les options de jeu sont incroyablement variees, incluant des options de paris sportifs dynamiques. Le bonus initial est super. Les agents repondent avec efficacite. Les retraits sont simples et rapides, cependant des offres plus genereuses rendraient l’experience meilleure. Dans l’ensemble, Gamdom Casino offre une aventure memorable. En bonus la plateforme est visuellement captivante, booste l’excitation du jeu. Un avantage les evenements communautaires pleins d’energie, propose des avantages sur mesure.
AccГ©der au site|
рольшторы на окна купить в москве http://www.avtomaticheskie-rulonnye-shtory1.ru .
J’ai une passion debordante pour Betify Casino, on y trouve une energie contagieuse. La selection est riche et diversifiee, comprenant des jeux optimises pour Bitcoin. Avec des depots instantanes. Disponible a toute heure via chat ou email. Le processus est fluide et intuitif, par moments des recompenses supplementaires dynamiseraient le tout. Pour faire court, Betify Casino assure un divertissement non-stop. Pour couronner le tout la plateforme est visuellement captivante, incite a rester plus longtemps. Un avantage les options de paris sportifs variees, garantit des paiements rapides.
Aller en ligne|
электрические рулонные шторы купить москва http://rulonnye-shtory-s-elektroprivodom7.ru/ .
1xbet ?ye ol http://www.1xbet-giris-8.com .
1xbet giri?i 1xbet-giris-2.com .
1xbet ?yelik https://www.1xbet-giris-4.com .
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Получить больше информации – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/
рулонные шторы на окно в кухне http://avtomaticheskie-rulonnye-shtory1.ru .
рулонные жалюзи москва рулонные жалюзи москва .
birxbet giri? https://www.1xbet-giris-2.com .
1 xbet http://www.1xbet-giris-4.com .
Je suis completement seduit par Betway Casino, il procure une sensation de frisson. La bibliotheque est pleine de surprises, incluant des paris sur des evenements sportifs. Avec des depots rapides et faciles. Disponible a toute heure via chat ou email. Les transactions sont toujours securisees, de temps en temps des bonus varies rendraient le tout plus fun. Pour conclure, Betway Casino est un choix parfait pour les joueurs. En extra la plateforme est visuellement vibrante, permet une immersion complete. Un avantage les tournois reguliers pour la competition, qui booste la participation.
https://betwaycasinofr.com/|
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Подробности по ссылке – http://bytorent.ru/kak-izbavitsya-ot-tsarapin-i-pyaten-na-mebeli
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Как достичь результата? – http://www.strucktour.com/?page_id=1290
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Это ещё не всё… – https://adventuresofjess.com/2017/12/right-here-right-now
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Продолжить изучение – https://trippy420.org/product/buy-banana-runtz-strain-online
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Кликни и узнай всё! – https://tecudi.com/produto/mini-maquina-waffles-bivolt
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Продолжить чтение – https://pafiambon.id/panen889-jackpot-slot-mahjong-ways-rp-3-000-000-lunas
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Детали по клику – https://erba-matta.ch/how-to-get-organic-traffic-from-search-engine
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Продолжить чтение – https://www.petrasuzanna-camino.blog/2023/08/10/grado-to-salas-7-august
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Ознакомиться с теоретической базой – https://www.absolutsevilla.com/contacto
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
ТОП-5 причин узнать больше – https://www.fj-tokyo.jp/others/102
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Посмотреть всё – https://laborat.umku.ac.id/buku-panduan-laborat
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Практические советы ждут тебя – https://www.csautoslalom.cz/rozhovor-s-pavlem-mullerem-absolutnim-sampionem-wsc-2024
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
ТОП-5 причин узнать больше – https://crossriver.ca/service/guided-rafting-trip-2
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Прочесть всё о… – https://teachersguide.net/the-role-and-responsibilities-of-a-section-head-in-school
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Детали по клику – https://pentvars.edu.gh/pentecost-university-welcomes-inaugural-cohort-of-nedmev-and-laser4netzero-scholarship-recipients
1xbet com giri? http://www.1xbet-giris-2.com .
электрическая рулонная штора https://www.avtomaticheskie-rulonnye-shtory1.ru .
пластиковые окна рулонные шторы с электроприводом rulonnye-shtory-s-elektroprivodom7.ru .
1xbet t?rkiye giri? 1xbet t?rkiye giri? .
Команда «СеверМед Альянса» включает наркологов, психиатров, клинических психологов, специалистов по зависимости, физиотерапевтов и координатора маршрута. Каждый модуль — детоксикация, стабилизация сна и настроения, психотерапия, семейная работа, восстановление бытовых и профессиональных ролей — встроен в общий план. Мы избегаем «одинаковых схем» и полипрагмазии: добавляем только те инструменты, у которых есть измеримая цель и безопасное «окно оценки» эффективности.
Подробнее тут – http://narcologicheskaya-klinika-petrozavodsk0.ru/petrozavodsk-narkologicheskij-dispanser/
Конфиденциальность — это набор конкретных действий, а не декларация на сайте. Мы проектируем «невидимость» так, чтобы пациент мог спокойно принять помощь и не опасаться огласки.
Выяснить больше – запой наркологическая клиника в красноярске
Инфузионная терапия (капельницы) — важная часть лечения, направленная на очищение организма, восстановление водно-солевого баланса и устранение токсинов. В «РязаньМед Альянс» используются проверенные препараты, которые помогают нормализовать работу внутренних органов и улучшить общее самочувствие. Таблица ниже показывает, какие виды капельниц чаще всего применяются при выведении из запоя и лечении алкоголизма.
Получить дополнительные сведения – http://narkologicheskaya-klinika-v-ryazani17.ru/narkologicheskij-staczionar-ryazan/
Каждый инструмент имеет чёткие показания и ограничение: мы объясняем, какую гипотезу проверяем, по каким признакам поймём, что она верна, и когда перестанем использовать метод, если вклад невелик. Это снижает тревогу и формирует доверие к плану.
Узнать больше – https://narcologicheskaya-klinika-petrozavodsk0.ru/petrozavodsk-narkologicheskij-dispanser
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Подробнее – наркологическая клиника цены в красноярске
Лечение алкоголизма в клинике «РязаньМед Альянс» включает несколько этапов, каждый из которых направлен на определённую цель — от снятия интоксикации до формирования устойчивого отказа от алкоголя. В таблице представлены основные стадии лечения и методы, используемые специалистами клиники.
Детальнее – https://narkologicheskaya-klinika-v-ryazani17.ru/narkolog-ryazan-telefon
J’ai un veritable coup de c?ur pour Betway Casino, ca pulse comme une soiree animee. Le catalogue est un tresor de divertissements, comprenant des jeux compatibles avec les cryptos. 100% jusqu’a 500 € + tours gratuits. Le support client est irreprochable. Les gains arrivent en un eclair, rarement des offres plus consequentes seraient parfaites. En fin de compte, Betway Casino est un must pour les passionnes. Ajoutons aussi le site est rapide et style, ce qui rend chaque partie plus fun. Particulierement attrayant les competitions regulieres pour plus de fun, renforce la communaute.
DГ©couvrir davantage|
Je suis enthousiasme par Belgium Casino, c’est une plateforme qui deborde de dynamisme. La gamme est variee et attrayante, incluant des paris sportifs pleins de vie. Il offre un demarrage en fanfare. Disponible a toute heure via chat ou email. Le processus est transparent et rapide, par contre quelques free spins en plus seraient bienvenus. En bref, Belgium Casino merite un detour palpitant. A noter la plateforme est visuellement vibrante, ce qui rend chaque session plus palpitante. Particulierement fun les options de paris sportifs variees, offre des bonus exclusifs.
Ouvrir maintenant|
Je ne me lasse pas de Gamdom Casino, c’est une plateforme qui deborde de dynamisme. Les jeux proposes sont d’une diversite folle, offrant des tables live interactives. Il donne un elan excitant. Le support est efficace et amical. Les paiements sont securises et instantanes, occasionnellement des offres plus importantes seraient super. Pour conclure, Gamdom Casino merite une visite dynamique. Ajoutons que l’interface est lisse et agreable, apporte une energie supplementaire. Particulierement attrayant les tournois reguliers pour la competition, offre des bonus constants.
https://gamdomcasinoappfr.com/|
Je suis captive par Betway Casino, c’est une plateforme qui pulse avec energie. Les options sont aussi vastes qu’un horizon, offrant des sessions live immersives. Le bonus de bienvenue est genereux. Le service est disponible 24/7. Le processus est clair et efficace, parfois plus de promos regulieres dynamiseraient le jeu. En resume, Betway Casino est un incontournable pour les joueurs. A signaler la plateforme est visuellement vibrante, incite a prolonger le plaisir. Un atout les options de paris sportifs diversifiees, cree une communaute vibrante.
DГ©couvrir plus|
Je suis fascine par Gamdom Casino, on y trouve une energie contagieuse. La bibliotheque est pleine de surprises, proposant des jeux de casino traditionnels. Le bonus de depart est top. Le suivi est d’une fiabilite exemplaire. Les gains arrivent en un eclair, de temps a autre des offres plus importantes seraient super. En fin de compte, Gamdom Casino merite un detour palpitant. Ajoutons que l’interface est intuitive et fluide, ce qui rend chaque session plus palpitante. Egalement genial les transactions crypto ultra-securisees, assure des transactions fiables.
Lire la suite|
Каждый инструмент имеет чёткие показания и ограничение: мы объясняем, какую гипотезу проверяем, по каким признакам поймём, что она верна, и когда перестанем использовать метод, если вклад невелик. Это снижает тревогу и формирует доверие к плану.
Детальнее – лечение в наркологической клинике в петрозаводске
Discover exquisite Austrian wines at weinverkostungen wien and immerse yourself in Vienna’s vibrant wine culture.
In Wien kann man die Vielfalt osterreichischer Weine auf besondere Weise entdecken. Die Region ist bekannt fur ihren exzellenten Wei?wein, besonders den Grunen Veltliner. Viele Weinverkostungen finden in historischen Gewolbekellern statt.
Das milde Klima und die mineralreichen Boden begunstigen den Weinbau. Das macht Wien zu einer der wenigen Gro?stadte mit eigenem Weinbaugebiet.
#### **2. Beliebte Weinregionen und Weinguter**
In Wien gibt es mehrere renommierte Weinregionen, wie den Nussberg oder den Bisamberg. Hier reifen einige der besten osterreichischen Weine heran. Familiengefuhrte Weinguter bieten oft Fuhrungen und Verkostungen an. Gaste konnen die Leidenschaft der Winzer hautnah erleben.
Ein Besuch im Weingut Wieninger oder im Mayer am Pfarrplatz lohnt sich. Diese Weinguter stehen fur hochste Qualitat und Handwerkskunft.
#### **3. Ablauf einer typischen Weinverkostung**
Eine klassische Wiener Weinverkostung beginnt meist mit einer Kellertour. Dabei erfahrt man Wissenswertes uber Rebsorten und Vinifizierung. Danach folgt die Verkostung unterschiedlicher Weine. Von frischen Wei?weinen bis zu kraftigen Rotweinen ist alles dabei.
Haufig werden die Weine mit lokalen Kasesorten oder Brot serviert. Das unterstreicht die Geschmacksnuancen der Weine.
#### **4. Tipps fur unvergessliche Weinverkostungen**
Um das Beste aus einer Weinverkostung in Wien herauszuholen, sollte man vorher buchen. Einige Anbieter bieten auch private Verkostungen an. Zudem lohnt es sich, auf die Jahreszeiten zu achten. Die warmen Monate eignen sich perfekt fur Verkostungen im Freien.
Ein guter Tipp ist auch, ein Notizbuch mitzubringen. Viele Gaste schatzen spater die Erinnerungen an die Verkostung.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
In Wien kann man die Vielfalt osterreichischer Weine auf besondere Weise entdecken.
#### **2. Beliebte Weinregionen und Weinguter**
Gaste konnen die Leidenschaft der Winzer hautnah erleben.
#### **3. Ablauf einer typischen Wiener Weinverkostung**
Oft werden historische Anekdoten zum Weinbau geteilt.
#### **4. Tipps fur unvergessliche Weinverkostungen**
So kann man sich die geschmacklichen Eindrucke leicht merken.
—
**Hinweis:** Durch Kombination der Varianten aus den -Blocken konnen zahlreiche einzigartige Texte generiert werden, die grammatikalisch und inhaltlich korrekt sind.
J’ai un faible pour Betify Casino, on ressent une ambiance festive. Les options de jeu sont incroyablement variees, comprenant des jeux optimises pour Bitcoin. Avec des depots rapides et faciles. Disponible 24/7 par chat ou email. Les gains arrivent sans delai, neanmoins des recompenses en plus seraient un bonus. Globalement, Betify Casino offre une experience hors du commun. Par ailleurs l’interface est intuitive et fluide, ajoute une vibe electrisante. Egalement super les transactions en crypto fiables, qui dynamise l’engagement.
https://betifycasinoa366fr.com/|
Конфиденциальность — это набор конкретных действий, а не декларация на сайте. Мы проектируем «невидимость» так, чтобы пациент мог спокойно принять помощь и не опасаться огласки.
Узнать больше – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/narkologicheskaya-klinika-krasnoyarsk-otzyvy
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-anonimno-v-sergievom-posade
Домашний формат выбирают, когда обстановка позволяет провести лечение в тишине и нет признаков угрозы жизни. Врач приезжает без опознавательных знаков, начинает с очной оценки и допуска к инфузии, сверяет принятые ранее препараты и аллергии, объясняет ожидаемую динамику. После запуска капельницы мягко корректируются жидкость и электролиты, проводится симптом-контроль (тремор, тошнота, тревога, головная боль), по показаниям — осторожная нормализация сна. На выходе пациент и семья получают понятные рекомендации на 24–48 часов: питьевой режим, питание, ограничения по нагрузкам, признаки тревоги и правила связи с дежурным врачом.
Выяснить больше – vyvod-iz-zapoya-sergiev-posad
Инфузионная терапия (капельницы) — важная часть лечения, направленная на очищение организма, восстановление водно-солевого баланса и устранение токсинов. В «РязаньМед Альянс» используются проверенные препараты, которые помогают нормализовать работу внутренних органов и улучшить общее самочувствие. Таблица ниже показывает, какие виды капельниц чаще всего применяются при выведении из запоя и лечении алкоголизма.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-v-ryazani17.ru/narkologiya-v-ryazani
Качество — это не субъективные впечатления, а сравнение базовой линии с целевыми коридорами в обозначенных окнах. Мы ведём короткий отчёт по маркерам: переносимость воды (мл/ч), диурез, ЧСС/АД в покое, структура сна (длительность и число пробуждений), динамика по шкалам тошноты/тремора, выполнение двух утренних бытовых задач. Отчёт понятен пациенту: в нём нет лишней терминологии, только факты и решения — какой модуль снят, какой оставлен ещё на ночь, какой будет пересмотрен через 12–24 часа. Финансовая прозрачность следует той же логике: расширение проводится только по показаниям с указанием цели («какой маркер планируем улучшить») и окна переоценки («когда проверяем результат»).
Разобраться лучше – https://narkologicheskaya-klinika-v-rostove-na-donu16.ru/narkologiya-rostov-kruglosutochno/
Комплексный подход позволяет врачу не просто купировать острые симптомы, но и предупредить осложнения со стороны сердца, печени и нервной системы. После стабилизации состояния пациент получает рекомендации по дальнейшему лечению и восстановлению.
Получить дополнительные сведения – вывод из запоя вызов на дом в волгограде
Домашний протокол разбит на понятные шаги. В каждом шаге есть цель, действия, что именно мы измеряем и когда сверяем прогресс. Это делает процесс прозрачным и даёт семье чувство контроля: видно, почему назначено именно это и когда ждать облегчения.
Углубиться в тему – https://narkolog-na-dom-petrozavodsk0.ru/
После прохождения детоксикации пациенту назначаются восстановительные процедуры, направленные на нормализацию обмена веществ и укрепление нервной системы. Программы клиники включают физиотерапию, витаминотерапию и индивидуальные занятия с психотерапевтом. Главная цель — восстановить способность организма к естественной саморегуляции и снизить зависимость от внешних раздражителей.
Подробнее можно узнать тут – наркологическая клиника лечение алкоголизма
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Ознакомиться с деталями – https://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-klinika-v-sergievom-posade/
Наркологическая клиника «Трезвый Урал» специализируется на безопасном и деликатном выведении из запоя с выездом врача на дом. Мы соединяем медицинскую точность, продуманную логистику и понятные пациенту шаги, чтобы облегчение наступало быстро, а состояние оставалось стабильным и предсказуемым. В основе — индивидуальные капельницы по показаниям, детоксикация с мониторингом витальных показателей, коррекция обезвоживания и электролитных нарушений, мягкая поддержка сна и психологическая разгрузка. Наши бригады приезжают круглосуточно, оборудование компактно, документы — нейтральные, а сообщения в медицинской карте формулируются аккуратно, без «ярлыков», чтобы сохранить вашу конфиденциальность.
Подробнее можно узнать тут – вывод из запоя недорого в каменске-уральске
Честная наркология — это не «универсальная капельница», а система шагов, привязанная к параметрам конкретного человека. В Чехове мы выезжаем круглосуточно, на месте проводим допуск к терапии, сверяем совместимости с уже принятыми препаратами, подбираем состав инфузий без лишних компонентов и избыточной седативной нагрузки. Если дома нет условий для безопасной ночи, предложим стационар — это не усложнение, а короткий путь к безопасности. Анонимность — стандарт: нейтральные формулировки в документах по запросу, ограниченный доступ к данным, деликатная связь.
Получить дополнительную информацию – https://narkologicheskaya-klinika-chekhov8.ru/
Discover exquisite Austrian wines at schaumwein verkostung and immerse yourself in Vienna’s vibrant wine culture.
In Wien kann man die Vielfalt osterreichischer Weine auf besondere Weise entdecken. Die Region ist bekannt fur ihren exzellenten Wei?wein, besonders den Grunen Veltliner. Jahrlich stromen Tausende von Besuchern in die Weinkeller der Stadt.
Das milde Klima und die mineralreichen Boden begunstigen den Weinbau. Daher gedeihen hier besonders aromatische Rebsorten.
#### **2. Beliebte Weinregionen und Weinguter**
In Wien gibt es mehrere renommierte Weinregionen, wie den Nussberg oder den Bisamberg. Hier reifen einige der besten osterreichischen Weine heran. Familiengefuhrte Weinguter bieten oft Fuhrungen und Verkostungen an. Gaste konnen die Leidenschaft der Winzer hautnah erleben.
Ein Besuch im Weingut Wieninger oder im Mayer am Pfarrplatz lohnt sich. Diese Weinguter stehen fur hochste Qualitat und Handwerkskunft.
#### **3. Ablauf einer typischen Weinverkostung**
Eine klassische Wiener Weinverkostung beginnt meist mit einer Kellertour. Dabei erfahrt man Wissenswertes uber Rebsorten und Vinifizierung. Danach folgt die Verkostung unterschiedlicher Weine. Jeder Wein wird sorgfaltig prasentiert und verkostet.
Haufig werden die Weine mit lokalen Kasesorten oder Brot serviert. Diese Kombination ist ein Highlight fur Feinschmecker.
#### **4. Tipps fur unvergessliche Weinverkostungen**
Um das Beste aus einer Weinverkostung in Wien herauszuholen, sollte man vorher buchen. Viele Weinguter haben begrenzte Platze und sind schnell ausgebucht. Zudem lohnt es sich, auf die Jahreszeiten zu achten. Im Herbst finden oft Weinlesefeste statt.
Ein guter Tipp ist auch, ein Notizbuch mitzubringen. Viele Gaste schatzen spater die Erinnerungen an die Verkostung.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
In Wien kann man die Vielfalt osterreichischer Weine auf besondere Weise entdecken.
#### **2. Beliebte Weinregionen und Weinguter**
Hier reifen einige der besten osterreichischen Weine heran.
#### **3. Ablauf einer typischen Wiener Weinverkostung**
Dabei erfahrt man Wissenswertes uber Rebsorten und Vinifizierung.
#### **4. Tipps fur unvergessliche Weinverkostungen**
Fruhzeitige Reservierungen garantieren einen reibungslosen Ablauf.
—
**Hinweis:** Durch Kombination der Varianten aus den -Blocken konnen zahlreiche einzigartige Texte generiert werden, die grammatikalisch und inhaltlich korrekt sind.
Если к намеченному окну улучшение слабее ожидаемого, врач меняет один параметр — время приёма, скорость инфузии, приоритет модуля — и назначает новую сверку. Мы избегаем «снежного кома» назначений, сохраняя предсказуемость и бережность.
Подробнее тут – частный нарколог на дом петрозаводск
Процедура вывода из запоя проводится с применением современных методик инфузионной терапии. Врачи контролируют уровень гидратации, работу сердечно-сосудистой системы и общее состояние пациента до полного устранения симптомов.
Разобраться лучше – частная наркологическая клиника
Маршрут помощи строится вокруг конкретных задач безопасности. С первого звонка администратор собирает короткий чек-лист: длительность нынешнего эпизода, что принималось в последние двое суток, хронические заболевания, аллергии, как прошла ночь, есть ли помощник на вечер и ночь. Дежурный врач, опираясь на эти данные, предлагает стартовый формат — выезд на дом по Воскресенску и району или немедленную госпитализацию. Решение привязывается к реальным рискам: стабильность давления и пульса, выраженность тремора и тошноты, эпизоды судорог в прошлом, возможность обеспечить «тихий режим» в квартире. После очной оценки и допуска к терапии мы запускаем детокс, а по завершении визита фиксируем правила на 24–48 часов и контрольные точки. Если состояние колеблется, сразу обсуждаем повторный контакт либо перевод в стационар, не теряя часы на бюрократию.
Выяснить больше – narkologicheskaya-klinika-spravka
Je suis accro a Betway Casino, c’est une plateforme qui pulse avec energie. La selection est riche et diversifiee, offrant des sessions live immersives. Avec des transactions rapides. Le suivi est toujours au top. Les paiements sont surs et efficaces, neanmoins des offres plus genereuses rendraient l’experience meilleure. En resume, Betway Casino offre une aventure inoubliable. Notons egalement le site est rapide et engageant, ce qui rend chaque partie plus fun. Un avantage les evenements communautaires engageants, propose des avantages sur mesure.
http://www.betwaycasino365fr.com|
С первого звонка администратор бережно собирает фактуру: сколько длится эпизод, что человек уже принимал за последние двое суток, как прошла ночь, есть ли помощник на вечер и ночь, какие хронические заболевания и аллергии известны. Дежурный врач оценивает риски и предлагает старт: анонимный визит на дом по Клину или немедленную госпитализацию. На месте проводится очная оценка и допуск к терапии, запускается инфузионная поддержка с мониторингом давления, пульса и сатурации, корректируется вода и электролиты, по показаниям — осторожная нормализация сна и симптом-контроль. Если картина нестабильна, переводим в стационар — это короче путь к безопасности, чем многочасовые попытки «пересидеть» дома.
Подробнее можно узнать тут – частная наркологическая клиника
Дізнатись більше: https://magazine.com.ua/nepiznane.html
комплексное продвижение сайтов москва комплексное продвижение сайтов москва .
net seo https://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru .
стратегия продвижения блог http://www.statyi-o-marketinge7.ru .
маркетинговый блог https://www.statyi-o-marketinge6.ru .
Перед таблицей зафиксируем принцип: это ориентир по этапам для семьи и пациента. Врач адаптирует длительность и насыщенность под возраст, сопутствующие заболевания и исходное состояние.
Узнать больше – http://narkologicheskaya-klinika-chekhov8.ru
Команда клиники — это врачи-наркологи, психиатры-консультанты, специалисты интенсивной терапии, клинический психолог, психотерапевт и медсёстры с опытом круглосуточного поста. Мы разговариваем «языком фактов»: витальные показатели, шкалы симптомов, дневники воды и сна, малые бытовые цели. Такой язык исключает стигму и «магическое мышление»; он понятен семье и помогает принимать решения без страхов и «подстраховочных» излишков.
Детальнее – http://narkologicheskaya-klinika-v-rostove-na-donu16.ru/narkologi-rostov-na-donu/
Повний матеріал тут: https://ua-meta.com/
Комплексный подход позволяет врачу не просто купировать острые симптомы, но и предупредить осложнения со стороны сердца, печени и нервной системы. После стабилизации состояния пациент получает рекомендации по дальнейшему лечению и восстановлению.
Узнать больше – наркологический вывод из запоя волгоград
Если к «окну оценки» прогресс ниже ожидаемого, команда меняет один параметр — дозировку, временное окно приёма, приоритет модуля — и назначает новую дату сверки. Такой подход защищает от «снежного кома» вмешательств и сохраняет предсказуемость процесса.
Углубиться в тему – наркологическая клиника наркологический центр петрозаводск
Ниже — «каркас» маршрута. Он служит ориентиром для персонализации: меняется приоритет модулей, плотность контактов, сочетание стационара и амбулаторных визитов. Принцип неизменен: «один шаг — одна цель — один маркер».
Подробнее можно узнать тут – наркологическая клиника стационар петрозаводск
Таблица не заменяет очный осмотр, но показывает, как наблюдения переводятся в действие и когда мы принимаем решение о продолжении/остановке модуля.
Получить дополнительные сведения – http://narkologicheskaya-klinika-v-krasnoyarske17.ru/krasnoyarsk-narkologicheskij-czentr/
Перед таблицей зафиксируем принцип: это ориентир по этапам для семьи и пациента. Врач адаптирует длительность и насыщенность под возраст, сопутствующие заболевания и исходное состояние.
Узнать больше – бесплатные наркологические клиники
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Подробнее тут – наркологическая клиника цены красноярск
Мы не используем универсальные «коктейли»: алгоритм строится из коротких проверяемых шагов. На старте фиксируем цель (например, уменьшить тремор и тошноту, стабилизировать пульс и давление, вернуть полноценный ночной сон), выбираем минимально достаточные средства для её достижения и заранее назначаем «окно оценки» — момент, когда команда сверяет эффект и при необходимости корректирует один параметр. Такой подход защищает от полипрагмазии, экономит силы пациента и делает прогресс читаемым для всей семьи.
Подробнее – https://vyvod-iz-zapoya-kamensk-uralskij0.ru/vyvod-iz-zapoya-na-domu-otzyvy-kamensk-uralskij
Лечебный план складывается из узких модулей, каждый из которых решает одну задачу. Мы не подключаем всё сразу, чтобы не потерять причинно-следственную связь и не перегрузить организм. Ниже — ориентировочная сетка модулей; фактический состав и длительность определяет врач по результатам осмотра и динамике в «окнах оценки».
Получить больше информации – наркологическая клиника лечение алкоголизма в ростове-на-дону
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Узнать больше – http://vyvod-iz-zapoya-sergiev-posad8.ru
Главное — непрерывность и скорость принятия решений. Рядом врач и медсестра, доступ к диагностике и возможность точно настраивать темп инфузий, подбирать поддерживающие препараты, контролировать сон и уровень тревоги. Благодаря этому снижается риск осложнений, а восстановление идёт ровнее: меньше «качелей» днём и ночью.
Изучить вопрос глубже – http://www.domen.ru
«ВитаСана» — это организованный маршрут наркологической помощи в Чехове: быстрый анонимный звонок, выезд врача на дом без опознавательных знаков, аккуратный детокс с капельницами, стационар с круглосуточным наблюдением и подготовка к кодированию по показаниям. Мы действуем спокойно и последовательно: сначала очная оценка и допуск к терапии, затем индивидуальная инфузионная поддержка, далее — понятный план «тихих» дней и контрольный контакт. Каждое назначение объясняем простыми словами, смету согласуем до начала процедур, конфиденциальность соблюдаем на каждом шаге.
Подробнее тут – http://narkologicheskaya-klinika-chekhov8.ru
Мы держим баланс между недостаточным и избыточным лечением. С одной стороны, не пропускаем опасные признаки, с другой — избегаем седативной перегрузки и сомнительных «коктейлей». Состав капельницы и темп введения зависят от давления и пульса, выраженности тревоги и тошноты, сопутствующих диагнозов и лекарств, уже попавших в организм. Каждое назначение объясняется простыми словами, чтобы пациент и семья понимали, как действует схема и зачем нужны ограничения ближайших дней.
Ознакомиться с деталями – отзывы о наркологических клиниках
Процесс детоксикации состоит из нескольких последовательных шагов, направленных на безопасное очищение организма. Ниже представлена таблица с описанием этапов, которые применяются в клинике «Трезвая Линия Волгоград».
Углубиться в тему – http://vyvod-iz-zapoia-v-volgograde17.ru
Лечение алкоголизма в клинике «РязаньМед Альянс» включает несколько этапов, каждый из которых направлен на определённую цель — от снятия интоксикации до формирования устойчивого отказа от алкоголя. В таблице представлены основные стадии лечения и методы, используемые специалистами клиники.
Выяснить больше – запой наркологическая клиника рязань
Медицинская помощь строится на принципах индивидуального подхода и поэтапной терапии. Каждый пациент проходит диагностику, после чего составляется персональная программа, включающая медикаментозную поддержку, консультации психотерапевта и физиопроцедуры. Такой подход помогает не просто снять симптомы, но и восстановить организм полностью.
Выяснить больше – наркологическая клиника стационар в рязани
Наркологическая клиника «СеверМед Альянс» — это современная экосистема помощи при зависимостях, где клиническая точность соединяется с бережной коммуникацией и индивидуальными маршрутами реабилитации. Мы выстраиваем лечение как последовательность управляемых шагов с понятными целями и сроками оценки результата. Пациент видит логику каждого вмешательства, понимает, почему ему предлагают именно такой план, и отслеживает прогресс по простым маркерам — сон, уровень тревоги, частота и длительность «тяговых» эпизодов, восстановление энергии и социальной активности.
Исследовать вопрос подробнее – наркологическая клиника наркологический центр в петрозаводске
net seo http://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru .
продвижение французского сайта цена https://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru .
блог о маркетинге блог о маркетинге .
статьи про маркетинг и seo https://www.statyi-o-marketinge6.ru .
Команда клиники — это врачи-наркологи, психиатры-консультанты, специалисты интенсивной терапии, клинический психолог, психотерапевт и медсёстры с опытом круглосуточного поста. Мы разговариваем «языком фактов»: витальные показатели, шкалы симптомов, дневники воды и сна, малые бытовые цели. Такой язык исключает стигму и «магическое мышление»; он понятен семье и помогает принимать решения без страхов и «подстраховочных» излишков.
Подробнее – наркологическая клиника клиника помощь ростов-на-дону
Клининг в Москве — это надежный способ поддерживать чистоту и порядок в вашем офисе или квартире.
Существует множество компаний, предлагающих услуги клининга.
Домашний формат уместен, когда нет признаков угрозы жизни, а дома можно сохранить тишину и наблюдение ночью. Врач приезжает без опознавательных знаков, начинает с очной оценки рисков и сверки уже принятых препаратов, объясняет ожидаемую динамику и запускает инфузионную терапию. Мы мягко корректируем водно-электролитный баланс, даём поддержку печени и вегетативной нервной системе, по показаниям осторожно нормализуем сон. На руки выдаём памятку на ближайшие сутки-двое: питьевой режим, питание, алгоритм отхода ко сну, признаки тревоги, порядок связи с дежурным врачом. Такой визит «гасит» острые проявления и возвращает предсказуемость ночи без лишней огласки для соседей.
Выяснить больше – https://narkologicheskaya-klinika-voskresensk8.ru/
Этот информационный материал подробно освещает проблему наркозависимости, ее причины и последствия. Мы предлагаем информацию о методах лечения, профилактики и поддерживающих программах. Цель статьи — повысить осведомленность и продвигать идеи о необходимости борьбы с зависимостями.
Получить больше информации – https://prensity.ru/zdorove-4688020-novye-uslugi-po-kodirovaniyu-v-narkologicheskojj-k-qw
Je suis captive par Belgium Casino, ca transporte dans un monde d’excitation. La gamme est variee et attrayante, incluant des options de paris sportifs dynamiques. Avec des depots instantanes. Le suivi est toujours au top. Le processus est simple et transparent, de temps en temps quelques tours gratuits supplementaires seraient cool. En conclusion, Belgium Casino garantit un plaisir constant. D’ailleurs le site est rapide et style, ce qui rend chaque partie plus fun. Egalement top les tournois reguliers pour s’amuser, garantit des paiements rapides.
Passer à l’action|
Je suis completement seduit par Betway Casino, ca offre un plaisir vibrant. Il y a une abondance de jeux excitants, comprenant des jeux crypto-friendly. 100% jusqu’a 500 € avec des spins gratuits. Disponible 24/7 pour toute question. Les gains sont transferes rapidement, mais encore quelques free spins en plus seraient bienvenus. Pour finir, Betway Casino offre une experience hors du commun. A signaler l’interface est lisse et agreable, donne envie de prolonger l’aventure. A souligner les options variees pour les paris sportifs, qui dynamise l’engagement.
Aller plus loin|
seo топ специалистов сочи
Успешное продвижение требует экспертного подхода и глубоких знаний.
Достоверные кейсы демонстрируют эффективность работы специалиста.
Сравнивайте цены и условия разных подрядчиков.
Je suis epate par Gamdom Casino, ca pulse comme une soiree animee. Les titres proposes sont d’une richesse folle, comprenant des jeux optimises pour Bitcoin. Il amplifie le plaisir des l’entree. Le service client est de qualite. Les transactions sont toujours securisees, neanmoins quelques spins gratuits en plus seraient top. En bref, Gamdom Casino est un immanquable pour les amateurs. Notons egalement le site est rapide et immersif, incite a rester plus longtemps. Un element fort le programme VIP avec des recompenses exclusives, cree une communaute vibrante.
Aller sur le site web|
J’ai un veritable coup de c?ur pour Gamdom Casino, on y trouve une vibe envoutante. Le catalogue de titres est vaste, comprenant des jeux optimises pour Bitcoin. Il offre un coup de pouce allechant. Le suivi est toujours au top. Les transactions sont d’une fiabilite absolue, bien que quelques tours gratuits en plus seraient geniaux. En somme, Gamdom Casino est un immanquable pour les amateurs. Ajoutons aussi la navigation est claire et rapide, ce qui rend chaque session plus palpitante. Particulierement cool les tournois reguliers pour s’amuser, qui dynamise l’engagement.
DГ©couvrir la page|
Je suis totalement conquis par Betify Casino, c’est une plateforme qui deborde de dynamisme. Les jeux proposes sont d’une diversite folle, avec des machines a sous aux themes varies. Avec des depots instantanes. Le support est fiable et reactif. Le processus est simple et transparent, neanmoins quelques spins gratuits en plus seraient top. En conclusion, Betify Casino est un lieu de fun absolu. En complement le design est moderne et energique, ajoute une touche de dynamisme. Un element fort les evenements communautaires engageants, garantit des paiements securises.
Obtenir les dГ©tails|
Je suis accro a Belgium Casino, ca donne une vibe electrisante. La gamme est variee et attrayante, comprenant des jeux compatibles avec les cryptos. Le bonus de depart est top. Le suivi est d’une fiabilite exemplaire. Les gains sont verses sans attendre, neanmoins plus de promotions variees ajouteraient du fun. En bref, Belgium Casino est un lieu de fun absolu. A mentionner la plateforme est visuellement vibrante, permet une immersion complete. Egalement genial les evenements communautaires vibrants, garantit des paiements rapides.
Visiter en ligne|
Мы предлагаем вам подробное руководство, основанное на проверенных источниках и реальных примерах. Каждая часть публикации направлена на то, чтобы помочь вам разобраться в сложных вопросах и применить знания на практике.
Нажмите, чтобы узнать больше – https://tcgjam.com/studio-d-color
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Нажми и узнай всё – https://way2benefits.com/advantages-and-disadvantages-of-daisy-wheel-printer
J’adore l’ambiance electrisante de Betify Casino, ca invite a plonger dans le fun. Il y a une abondance de jeux excitants, incluant des options de paris sportifs dynamiques. 100% jusqu’a 500 € + tours gratuits. Le service client est excellent. Les retraits sont lisses comme jamais, de temps en temps des bonus diversifies seraient un atout. Globalement, Betify Casino est un immanquable pour les amateurs. A mentionner la plateforme est visuellement captivante, permet une plongee totale dans le jeu. Un point cle les nombreuses options de paris sportifs, garantit des paiements rapides.
http://www.betifycasino777fr.com|
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Получить больше информации – https://www.charitytaxgroup.org.uk/commentary/off-payroll-working-major-changes-april-2017
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Изучить вопрос глубже – https://crossoceantravel.com/3-best-nature-weekend-tour-in-japan
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Переходите по ссылке ниже – https://kktcalimsatim.com/tag/macbook-air-for-sale
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Хочешь знать всё? – https://www.moblanovar.com/2019/11/21/hola-mundo
В этой публикации мы предложим ряд рекомендаций по избавлению от зависимостей и успешному восстановлению. Мы обсудим методы привлечения поддержки и важность самосознания. Эти советы помогут людям вернуться к нормальной жизни и стать на путь выздоровления.
Узнать больше – https://lugaland.com/narkolog-na-dom-kogda-neobhodima-pomoshch-i-kak-rabotaet
В этой публикации мы рассматриваем важную тему борьбы с зависимостями, включая алкогольную и наркотическую зависимости. Мы обсудим методы лечения, реабилитации и поддержку, которые могут помочь людям, столкнувшимся с этой проблемой. Читатели узнают о перспективах выздоровления и важности комплексного подхода.
Подробнее тут – https://ceith.ru/novye-uslugi-po-kodirovaniyu-v-narkologicheskojj-klinike-97
Je suis accro a Betway Casino, ca donne une vibe electrisante. Le catalogue de titres est vaste, proposant des jeux de casino traditionnels. 100% jusqu’a 500 € plus des tours gratuits. Les agents sont rapides et pros. Les gains arrivent en un eclair, toutefois quelques tours gratuits supplementaires seraient cool. Globalement, Betway Casino vaut une exploration vibrante. De surcroit la navigation est simple et intuitive, ce qui rend chaque moment plus vibrant. Un atout le programme VIP avec des privileges speciaux, offre des bonus constants.
Aller sur le web|
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Желаете узнать подробности? – https://jasafotowedding.com/alat-yang-digunakan-untuk-usaha-jasa-foto-wedding
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Хочешь знать всё? – https://sevenstarfoods.in/Independence-Day-Indonesia-by-GhostRaptor404
В этом обзоре представлены различные методы избавления от зависимости, включая терапевтические и психологические подходы. Мы сравниваем их эффективность и предоставляем рекомендации для тех, кто хочет вернуться к трезвой жизни. Читатели смогут найти информацию о реабилитационных центрах и поддерживающих группах.
Подробнее можно узнать тут – https://time-news.net/analytics/28289-konsultaciya-psihiatra.html
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Узнать из первых рук – https://way2benefits.com/advantages-and-disadvantages-of-daisy-wheel-printer
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Как достичь результата? – https://mydigitalboss.com/how-facebook-ads-can-generate-leads-for-your-business
раскрутка и продвижение сайта раскрутка и продвижение сайта .
оптимизация сайта франция https://www.optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru .
статьи о маркетинге статьи о маркетинге .
статьи про продвижение сайтов статьи про продвижение сайтов .
В городе и ближайших районах клиника «УралМед Трезвость» обеспечивает оперативный выезд и амбулаторный приём без очередей. На этапе первичного контакта координатор уточняет только клинически значимые моменты: постоянные препараты и дозы, аллергии, эпизоды судорог/психозов в прошлом, базовые показатели (АД/ЧСС/SpO?, если доступны), длительность симптомов, возможность организовать «тихое окно» на 20–30 минут. Вместо долгих разговоров — короткая, спокойная логика: где безопаснее начать (дом/амбулатория/стационар), какую ближайшую цель выбираем, в каком интервале ждём эффект и что считаем сигналом для связи с дежурным врачом.
Изучить вопрос глубже – наркологическая клиника лечение алкоголизма в челябинске
Для наглядности представлен примерный состав инфузионного раствора, используемого при выводе из запоя:
Углубиться в тему – вывод из запоя на дому круглосуточно в ростове-на-дону
Для жителей Ростова-на-Дону клиника работает по схеме «тихих маршрутов»: отдельный вход с нейтральной табличкой, окна записи в невызывающие подозрений часы, немаркированный подъезд автомобиля при выездном визите. На первом звонке диспетчер собирает только то, что влияет на безопасность: эпизоды рвоты, ЧСС/АД, ночные панические эпизоды, сопутствующие препараты, аллергии, наличие хронических заболеваний сердца. Личные и социальные детали не запрашиваются — мы придерживаемся принципа «минимально необходимой информации». По прибытии врача фиксируются базовая линия (сознание, дыхание, SpO?, температура), шкалы симптомов и переносимость небольших объёмов воды. Дальше — один точный шаг, одно «окно проверки» и прозрачное решение: продолжать модуль, модифицировать одну переменную или выключить блок.
Подробнее можно узнать тут – http://narkologicheskaya-clinika-v-rostove-na-donu16.ru
Ниже — ориентировочная матрица. Она не заменяет осмотр, но помогает понять логику выбора места и объёма вмешательств. Цель — не «больше процедур», а «точно по показаниям» с понятными окнами оценки и чистой обратной связью для семьи.
Исследовать вопрос подробнее – запой наркологическая клиника в челябинске
Эта последовательность действий обеспечивает безопасное прекращение запоя и предотвращает развитие синдрома отмены.
Углубиться в тему – врач вывод из запоя в ростове-на-дону
Для жителей Ростова-на-Дону клиника работает по схеме «тихих маршрутов»: отдельный вход с нейтральной табличкой, окна записи в невызывающие подозрений часы, немаркированный подъезд автомобиля при выездном визите. На первом звонке диспетчер собирает только то, что влияет на безопасность: эпизоды рвоты, ЧСС/АД, ночные панические эпизоды, сопутствующие препараты, аллергии, наличие хронических заболеваний сердца. Личные и социальные детали не запрашиваются — мы придерживаемся принципа «минимально необходимой информации». По прибытии врача фиксируются базовая линия (сознание, дыхание, SpO?, температура), шкалы симптомов и переносимость небольших объёмов воды. Дальше — один точный шаг, одно «окно проверки» и прозрачное решение: продолжать модуль, модифицировать одну переменную или выключить блок.
Углубиться в тему – http://narkologicheskaya-clinika-v-rostove-na-donu16.ru/narkologi-rostov-na-donu/
Основные этапы лечения включают:
Изучить вопрос глубже – лечение в наркологической клинике
В городе и ближайших районах клиника «УралМед Трезвость» обеспечивает оперативный выезд и амбулаторный приём без очередей. На этапе первичного контакта координатор уточняет только клинически значимые моменты: постоянные препараты и дозы, аллергии, эпизоды судорог/психозов в прошлом, базовые показатели (АД/ЧСС/SpO?, если доступны), длительность симптомов, возможность организовать «тихое окно» на 20–30 минут. Вместо долгих разговоров — короткая, спокойная логика: где безопаснее начать (дом/амбулатория/стационар), какую ближайшую цель выбираем, в каком интервале ждём эффект и что считаем сигналом для связи с дежурным врачом.
Подробнее – запой наркологическая клиника
Круглосуточный формат критичен именно из-за «первой ночи»: в это окно нестабильны тревога, сон, вегетативная реактивность. Мы не «усиливаем всё сразу», а по одному параметру доводим систему до целевого коридора. Так удаётся избежать полипрагмазии и сохранить управляемость процесса: пациент и семья заранее знают, какие цифры считаются нормой, когда звонить дежурному, как организовать свет и тишину, чтобы ночное восстановление действительно состоялось.
Подробнее тут – http://narkologicheskaya-clinika-v-rostove-na-donu16.ru
Капельница — основной метод дезинтоксикации при запое. Она позволяет быстро восполнить дефицит жидкости и электролитов, вывести токсины и улучшить общее самочувствие. В состав инфузии входят препараты, нормализующие обмен веществ, а также витамины и гепатопротекторы. Процедура проводится под контролем врача, что гарантирует безопасность и точную дозировку лекарств.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-v-rostove-na-donu16.ru/
Процесс терапии в наркологической клинике в Воронеже организован поэтапно. Это позволяет обеспечить системность и постепенность восстановления, снизить риски осложнений и повысить устойчивость результата.
Изучить вопрос глубже – https://narkologicheskaya-klinika-v-voronezhe17.ru/voronezh-narkologicheskij-dispanser/
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Получить больше информации – помощь вывод из запоя
Этап
Углубиться в тему – http://narkolog-na-dom-zhukovskij7.ru/vyzov-narkologa-na-dom-v-zhukovskom/https://narkolog-na-dom-zhukovskij7.ru
Если по ходу первичного осмотра выявляются «красные флаги» (спутанность сознания, нестабильное давление/ритм, кровавая рвота, подозрение на делирий), врач немедленно предложит госпитализацию и аккуратно организует перевод — безопасность всегда выше удобства.
Разобраться лучше – https://narkolog-na-dom-zhukovskij7.ru/narkolog-na-dom-anonimno-v-zhukovskom/
Главная цель — безопасно стабилизировать состояние, вернуть контроль над сном, гидратацией и базовой активностью в первые сутки и удержать результат. Для этого мы используем модульный подход: один этап — одна клиническая задача — один измеримый маркер. Такой принцип исключает «гонку доз», снижает риск перегрузки объёмом и делает прогноз понятным для пациента и близких. Мы сознательно разделяем «короткие эффекты» (уменьшение тошноты, сглаживание тахикардии) и «эффекты консолидации» (устойчивый сон, ясность утром), чтобы каждая корректировка была точной и доказуемой.
Детальнее – платная наркологическая клиника в нижнем новгороде
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Исследовать вопрос подробнее – narkologicheskaya-klinika-v-krasnoyarske17.ru/
Если по ходу первичного осмотра выявляются «красные флаги» (спутанность сознания, нестабильное давление/ритм, кровавая рвота, подозрение на делирий), врач немедленно предложит госпитализацию и аккуратно организует перевод — безопасность всегда выше удобства.
Изучить вопрос глубже – https://narkolog-na-dom-zhukovskij7.ru/narkolog-na-dom-cena-v-zhukovskom/
В таблице приведены основные компоненты капельницы и их действие:
Детальнее – наркологическая помощь в волгограде
Перед таблицей коротко поясним логику: мы выбираем самый безопасный маршрут именно для вашей ситуации, а при изменении состояния оперативно переключаемся на другой формат без пауз.
Подробнее тут – http://vyvod-iz-zapoya-pushkino7.ru
согласование перепланировки помещений согласование перепланировки помещений .
согласование перепланировки нежилых помещений согласование перепланировки нежилых помещений .
surewin casino login https://surewin-online.com .
icebet casino login icebet casino login .
Домашняя помощь — это клиника, перенесённая в тихую комнату. Знакомая обстановка снижает тревогу, исчезают пробки и ожидание, нет «социального шума». Врач «ПрофДетокса» приезжает без эмблем, действует спокойно и последовательно, объясняет каждое назначение простым языком. Мы не используем мифические смеси. Состав и темп капельницы подбираются под текущие показатели — давление, пульс, сатурация, выраженность тремора и тошноты, уровень тревоги, данные о лекарствах, которые человек успел принять за двое суток. Такой подход даёт не минутное облегчение, а устойчивую динамику на сутки и неделю.
Подробнее тут – https://narkolog-na-dom-ivanteevka8.ru/pomoshch-narkologa-na-domu-v-ivanteevke
Клиника использует многоступенчатый подход, который позволяет адаптировать лечение под особенности организма пациента. Наблюдение продолжается даже после завершения детоксикации, чтобы убедиться, что состояние стабильно и не требуется дополнительное вмешательство. При необходимости врач назначает курс поддержки печени, витаминов и препаратов для восстановления сна и психоэмоционального равновесия.
Узнать больше – вывод из запоя на дому
Состояния при зависимостях чувствительны к времени суток и среде. К ночи нарастает тревога, усиливается тремор, нестабильны показатели ЧСС/АД. Круглосуточный приём позволяет выстроить «мост» через самые сложные часы: собрать сон без избыточной фармаконагрузки, сделать короткие чек-ины, вовремя ретитровать один параметр (свет, дыхательные ритмы, интервалы питья), а утром оформить «малые победы» — гигиена и 10–15 минут тихой ходьбы. Эти простые маркеры часто надёжнее любых субъективных оценок «как себя чувствую».
Выяснить больше – наркологическая клиника лечение алкоголизма
В городе и ближайших районах клиника «УралМед Трезвость» обеспечивает оперативный выезд и амбулаторный приём без очередей. На этапе первичного контакта координатор уточняет только клинически значимые моменты: постоянные препараты и дозы, аллергии, эпизоды судорог/психозов в прошлом, базовые показатели (АД/ЧСС/SpO?, если доступны), длительность симптомов, возможность организовать «тихое окно» на 20–30 минут. Вместо долгих разговоров — короткая, спокойная логика: где безопаснее начать (дом/амбулатория/стационар), какую ближайшую цель выбираем, в каком интервале ждём эффект и что считаем сигналом для связи с дежурным врачом.
Получить дополнительные сведения – наркологическая клиника цены челябинск
Состояния при зависимостях чувствительны к времени суток и среде. К ночи нарастает тревога, усиливается тремор, нестабильны показатели ЧСС/АД. Круглосуточный приём позволяет выстроить «мост» через самые сложные часы: собрать сон без избыточной фармаконагрузки, сделать короткие чек-ины, вовремя ретитровать один параметр (свет, дыхательные ритмы, интервалы питья), а утром оформить «малые победы» — гигиена и 10–15 минут тихой ходьбы. Эти простые маркеры часто надёжнее любых субъективных оценок «как себя чувствую».
Детальнее – наркологические клиники алкоголизм ростов-на-дону
Конфиденциальность — это набор конкретных действий, а не декларация на сайте. Мы проектируем «невидимость» так, чтобы пациент мог спокойно принять помощь и не опасаться огласки.
Подробнее – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/chastnaya-narkologicheskaya-klinika-krasnoyarsk/
Эта последовательность действий обеспечивает безопасное прекращение запоя и предотвращает развитие синдрома отмены.
Подробнее тут – наркология вывод из запоя
Круглосуточная наркологическая помощь — это не набор «сильных капельниц», а последовательный клинический процесс с понятными этапами, метриками и окнами оценки результата. В наркологической клинике «ВолгаМед Резонанс» каждый вызов и каждое обращение переводятся в управляемый маршрут: от короткого телескрининга и очного осмотра до прицельной инфузионной терапии и бережной поведенческой поддержки. Мы работаем незаметно, анонимно и корректно: немаркированный транспорт, нейтральная экипировка, лаконичная документация без стигматизирующей лексики, единая точка связи 24/7 для семьи.
Ознакомиться с деталями – наркологическая клиника цены нижний новгород
Эта последовательность действий обеспечивает безопасное прекращение запоя и предотвращает развитие синдрома отмены.
Получить больше информации – вывод из запоя на дому ростов-на-дону
J’ai un faible pour Betway Casino, c’est un lieu ou l’adrenaline coule a flots. Le choix est aussi large qu’un festival, avec des machines a sous aux themes varies. 100% jusqu’a 500 € avec des spins gratuits. Le support est efficace et amical. Les transactions sont d’une fiabilite absolue, de temps a autre quelques free spins en plus seraient bienvenus. En fin de compte, Betway Casino offre une aventure inoubliable. Ajoutons aussi le site est rapide et engageant, permet une immersion complete. Particulierement fun les competitions regulieres pour plus de fun, offre des recompenses continues.
DГ©couvrir le web|
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Получить дополнительную информацию – вывод из запоя с выездом
Что делаем
Ознакомиться с деталями – нарколог на дом недорого
Перед тем как перечислить типичные случаи, отметим главный принцип: домашний формат выбирают, когда безопасность и прогноз сопоставимы со стационаром, а переезд лишь затянет старт терапии и усилит стресс для семьи.
Изучить вопрос глубже – http://narkolog-na-dom-zhukovskij7.ru
Основные этапы лечения включают:
Подробнее можно узнать тут – https://narkologicheskaya-klinika-v-voronezhe17.ru/chastnaya-narkologicheskaya-klinika-voronezh/
Для жителей Красноярска организованы два конфиденциальных пути. Первый — немаркированный выезд бригады на дом с заранее согласованными порогами связи. Второй — «тихий вход» в клинику через отдельную дверь, где приём проходит без очередей и «коридорных» разговоров. На первичном звонке администратор уточняет только клинически значимые факторы: частоту рвоты, наличие мочеиспускания, ЧСС/АД в покое, эпизоды спутанности, актуальные лекарства и аллергии. Биографические подробности и лишние вопросы не задаются — мы придерживаемся принципа минимально необходимой информации.
Ознакомиться с деталями – https://narkologicheskaya-klinika-v-krasnoyarske17.ru
Для иллюстрации приведена таблица, отражающая распространённые методы терапии и их воздействие на организм:
Узнать больше – наркологическая клиника лечение алкоголизма в воронеже
Je suis epate par Betway Casino, ca donne une vibe electrisante. Les options de jeu sont infinies, incluant des options de paris sportifs dynamiques. Le bonus d’inscription est attrayant. Les agents sont toujours la pour aider. Les transactions sont fiables et efficaces, par ailleurs des bonus plus varies seraient un plus. En resume, Betway Casino est une plateforme qui pulse. Notons aussi la plateforme est visuellement captivante, ajoute une touche de dynamisme. Egalement excellent les paiements securises en crypto, offre des bonus exclusifs.
Explorer le site web|
Алгоритм одинаково прозрачен в обоих форматах. Сначала — экспресс-диагностика: уровень сознания, сатурация, пульс, давление, температура, оценка неврологического статуса и обезвоживания. Затем врач формирует индивидуальную инфузионную схему: регидратационные растворы, коррекция электролитов, поддержка печени и нервной системы, адресная симптоматическая помощь (сон, тревога, тошнота, головная боль). Темп и объём подбираются по переносимости — без «универсальных коктейлей» и лишних препаратов.
Разобраться лучше – http://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-deshevo-v-pushkino/
В городе и пригороде организован круглосуточный приём с возможностью выезда на дом. Координатор уточняет только клинически значимые данные: регулярные препараты и дозировки, аллергии, недавние эпизоды судорог/психозов, доступ к розетке, возможность обеспечить «тихое окно» на 2–3 часа. Если в квартире многолюдно или идёт ремонт, предложим «тихий» стационар с отдельным входом и тем же ведущим врачом; после стабилизации зеркально перенесём маршрут обратно домой, чтобы не терять темп и доверие.
Получить дополнительные сведения – http://narkologicheskaya-klinika-v-nizhnem-novgorode16.ru/chastnaya-narkologicheskaya-klinika-nizhnij-novgorod/
Je suis captive par Gamdom Casino, il cree une experience captivante. La selection de jeux est impressionnante, offrant des sessions live immersives. Avec des depots instantanes. Les agents repondent avec efficacite. Les gains sont verses sans attendre, neanmoins plus de promos regulieres dynamiseraient le jeu. En resume, Gamdom Casino est un incontournable pour les joueurs. A signaler l’interface est simple et engageante, ajoute une touche de dynamisme. A mettre en avant les nombreuses options de paris sportifs, garantit des paiements rapides.
Essayer maintenant|
Je suis captive par Betify Casino, il cree un monde de sensations fortes. Le choix est aussi large qu’un festival, offrant des experiences de casino en direct. 100% jusqu’a 500 € avec des spins gratuits. Le support est efficace et amical. Les transactions sont fiables et efficaces, cependant des recompenses additionnelles seraient ideales. Au final, Betify Casino assure un divertissement non-stop. En plus le site est rapide et immersif, ajoute une touche de dynamisme. Un point cle le programme VIP avec des avantages uniques, cree une communaute vibrante.
Poursuivre la lecture|
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Получить больше информации – наркологическая психиатрическая помощь в волгограде
Je suis bluffe par Betify Casino, ca donne une vibe electrisante. La selection est riche et diversifiee, comprenant des titres adaptes aux cryptomonnaies. Avec des depots instantanes. Le support est efficace et amical. Les gains sont transferes rapidement, par contre des offres plus consequentes seraient parfaites. Au final, Betify Casino est une plateforme qui pulse. Notons aussi la navigation est simple et intuitive, donne envie de prolonger l’aventure. Particulierement fun les evenements communautaires dynamiques, offre des bonus exclusifs.
VГ©rifier le site|
J’adore la vibe de Belgium Casino, il cree un monde de sensations fortes. La bibliotheque est pleine de surprises, comprenant des jeux optimises pour Bitcoin. Il rend le debut de l’aventure palpitant. Le support est pro et accueillant. Le processus est fluide et intuitif, mais des offres plus importantes seraient super. En somme, Belgium Casino merite un detour palpitant. A mentionner le design est tendance et accrocheur, ce qui rend chaque moment plus vibrant. Particulierement interessant les nombreuses options de paris sportifs, propose des avantages sur mesure.
Approfondir|
Круглосуточная наркологическая помощь — это не громкая вывеска, а чётко выстроенная логистика, где каждый шаг измерим и объясним. В клинике «УралМед Трезвость» мы работаем по принципу «одна цель — один клинический шаг — одно окно оценки», чтобы исключить полипрагмазию и сохранить прогнозируемость результатов. Выездные бригады прибывают без маркировки, используют компактное оборудование и поддерживают спокойную коммуникацию: только факты, никакой стигмы и давления. Такой формат минимизирует тревогу пациента и близких, а также снижает риск срывов за счёт последовательной, поэтапной стабилизации.
Изучить вопрос глубже – наркологическая клиника цены
J’ai une passion debordante pour Betify Casino, c’est un lieu ou l’adrenaline coule a flots. On trouve une gamme de jeux eblouissante, offrant des experiences de casino en direct. Il amplifie le plaisir des l’entree. Le service client est de qualite. Les gains sont transferes rapidement, par contre plus de promotions frequentes boosteraient l’experience. Au final, Betify Casino vaut une exploration vibrante. Notons egalement la navigation est simple et intuitive, facilite une experience immersive. Egalement super les evenements communautaires pleins d’energie, qui motive les joueurs.
Aller Г la page|
Эта последовательность действий обеспечивает безопасное прекращение запоя и предотвращает развитие синдрома отмены.
Узнать больше – вывод из запоя на дому цена в ростове-на-дону
Анонимная наркологическая помощь — это не «быстрая капельница и забыли», а последовательный и конфиденциальный процесс, в котором каждое вмешательство имеет цель, измеримый маркер и заранее оговорённое «окно проверки». В наркологической клинике «Южный Мед Центр Ренова» мы совмещаем непрерывный приём 24/7, выездные визиты без маркировки, точечную диагностику, инфузионную поддержку, психотерапевтические сессии и план посттерапевтического сопровождения. Приоритет — приватность и минимально достаточные решения: чем меньше случайных назначений, тем больше управляемости и предсказуемости. Мы говорим «языком фактов», а не оценок: витальные показатели, шкалы симптомов (0–10), структура сна, переносимость воды, простые бытовые задачи на утро. Это помогает семье и пациенту видеть, что именно работает, и выключать вмешательства, когда они сделали своё дело.
Получить дополнительные сведения – наркологическая клиника вывод из запоя ростов-на-дону
В этой статье мы обсудим процесс восстановления после зависимостей, акцентируя внимание на различных методах и подходах к реабилитации. Читатели узнают, как создать план выздоровления и использовать полезные ресурсы для достижения устойчивых изменений.
Получить больше информации – https://newshay.com/vyvod-iz-zapoya-na-domu-professionalnyj-podhod-i-bezopasnost-paczienta
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Посмотреть подробности – https://conveyancingexpert.co.uk/does-my-conveyancer-need-to-be-local
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Что скрывают от вас? – https://ssironmetal.com/december-19th-2019/.html
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Узнать из первых рук – https://kdior-securite.com/tag
В этой заметке мы представляем шаги, которые помогут в процессе преодоления зависимостей. Рассматриваются стратегии поддержки и чек-листы для тех, кто хочет сделать первый шаг к выздоровлению. Наша цель — вдохновить читателей на положительные изменения и поддержать их в трудных моментах.
Изучить вопрос глубже – https://ooo-man.ru/lechenie-alkogolizma-v-surgute-professionalnyj-podhod-i-realnaya-pomoshh
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Всё, что нужно знать – https://www.antonelloosteria.com/cook/how-to-dice-potatoes-and-meat-like-a-chef
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Уточнить детали – https://arabsdo.info/?p=38
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Обратиться к источнику – https://badboysvending.com/how-to-move-on-from-hookups
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Изучить вопрос глубже – http://pic.murakumomura.com/2010/01/28/post_1982
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Как достичь результата? – https://aalstmaritiem.nl/aenean-vulputate-eleifend-tellus-aenean-leo-ligula
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Тыкай сюда — узнаешь много интересного – https://givanildo.com.br/blog/como-criar-um-anuncio-efetivo-no-mercado-livre-guia-completo
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Все материалы собраны здесь – https://atoutclim.com/aix
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Читать далее > – https://agentelibredigital.com/index.php/2023/12/23/analisis-post-atletico-de-madrid-sevilla-tres-puntos-para-terminar-2023
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Не упусти важное! – https://phugiathucphamnhapkhau.com/hai-san-tuoi-song
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Узнать из первых рук – https://sportsanteconseil.com/logo-ssc
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Выяснить больше – https://narkologicheskaya-klinika-v-kaliningrade15.ru/skoraya-narkologiya-vyvod-iz-zapoya-kaliningrad-uslugi/
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Открой скрытое – https://officedubac.cm/la-region-du-sud-dans-la-ferveur-du-baccalaureat-esg
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Получить дополнительную информацию – вывод наркологическая клиника калининград
Je suis enthousiaste a propos de Betway Casino, c’est une plateforme qui pulse avec energie. Les titres proposes sont d’une richesse folle, comprenant des titres adaptes aux cryptomonnaies. 100% jusqu’a 500 € avec des spins gratuits. Le support est rapide et professionnel. Les transactions sont d’une fiabilite absolue, de temps en temps quelques free spins en plus seraient bienvenus. Au final, Betway Casino offre une aventure inoubliable. En extra le design est tendance et accrocheur, ce qui rend chaque session plus palpitante. Particulierement attrayant le programme VIP avec des privileges speciaux, assure des transactions fluides.
Essayer maintenant|
Сопровождение ВЭД помогло нам минимизировать риски и ускорить процесс доставки товаров. Всё организовано грамотно и чётко. Работать с профессионалами приятно и спокойно: ВЭД сопровождение импорта
Tham gia cộng đồng game thủ tại Go88 để trải nghiệm các trò chơi bài, poker phổ biến nhất hiện nay.
Ориентир по времени
Детальнее – http://narkolog-na-dom-zhukovskij7.ru
采用高效谷歌外推策略,快速提升网站在搜索引擎中的可见性与权重。谷歌外推
Работаем по импорту спокойно, потому что знаем, что всё под контролем https://vsoprovozhdenie.ru/
Ориентир по времени
Исследовать вопрос подробнее – posle-kapelnicy-ot-zapoya
«Волшебной капельницы» не существует. Мы структурируем инфузии от симптомов, а не от «средних рецептов». Ниже — логика подбора для типичных профилей; реальную схему определяет врач на месте.
Подробнее тут – анонимная наркологическая клиника калининград
Je suis bluffe par Azur Casino, c’est une plateforme qui deborde de dynamisme. Il y a une abondance de jeux excitants, incluant des paris sportifs pleins de vie. Il offre un coup de pouce allechant. Le service d’assistance est au point. Les gains arrivent sans delai, par contre des offres plus genereuses rendraient l’experience meilleure. Pour faire court, Azur Casino est un choix parfait pour les joueurs. Pour couronner le tout l’interface est fluide comme une soiree, booste l’excitation du jeu. Particulierement interessant les transactions crypto ultra-securisees, propose des privileges sur mesure.
Cliquez ici|
Если по ходу первичного осмотра выявляются «красные флаги» (спутанность сознания, нестабильное давление/ритм, кровавая рвота, подозрение на делирий), врач немедленно предложит госпитализацию и аккуратно организует перевод — безопасность всегда выше удобства.
Получить дополнительные сведения – http://narkolog-na-dom-zhukovskij7.ru/narkolog-na-dom-cena-v-zhukovskom/
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Интересует подробная информация – https://www.iso-studio.it/il-natale-al-tempo-del-coronavirus
J’adore l’energie de Azur Casino, on ressent une ambiance festive. La bibliotheque est pleine de surprises, offrant des sessions live palpitantes. 100% jusqu’a 500 € plus des tours gratuits. Le suivi est d’une fiabilite exemplaire. Les retraits sont fluides et rapides, quelquefois des bonus diversifies seraient un atout. En somme, Azur Casino offre une experience hors du commun. Pour couronner le tout l’interface est intuitive et fluide, booste le fun du jeu. Egalement genial les competitions regulieres pour plus de fun, propose des privileges personnalises.
Visiter la plateforme|
J’ai un faible pour Lucky 31 Casino, c’est un lieu ou l’adrenaline coule a flots. La selection de jeux est impressionnante, avec des slots aux designs captivants. Il donne un avantage immediat. Le service client est de qualite. Les transactions sont toujours securisees, a l’occasion des offres plus consequentes seraient parfaites. Pour conclure, Lucky 31 Casino offre une experience hors du commun. Notons aussi la plateforme est visuellement captivante, amplifie le plaisir de jouer. Un point cle le programme VIP avec des avantages uniques, cree une communaute soudee.
Continuer Г lire|
Je suis fascine par 1xBet Casino, c’est une plateforme qui pulse avec energie. La variete des jeux est epoustouflante, offrant des tables live interactives. Avec des depots rapides et faciles. Les agents sont rapides et pros. Les retraits sont lisses comme jamais, neanmoins des offres plus importantes seraient super. En conclusion, 1xBet Casino offre une aventure memorable. Pour ajouter la plateforme est visuellement vibrante, ce qui rend chaque partie plus fun. Un avantage les transactions en crypto fiables, offre des recompenses regulieres.
Cliquer maintenant|
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Где можно узнать подробнее? – https://nutrabem.shop/ola-mundo
J’ai une passion debordante pour 1xBet Casino, il propose une aventure palpitante. Les jeux proposes sont d’une diversite folle, proposant des jeux de cartes elegants. Il offre un demarrage en fanfare. Le support est efficace et amical. Les paiements sont securises et rapides, de temps en temps des bonus plus varies seraient un plus. En conclusion, 1xBet Casino est un choix parfait pour les joueurs. En bonus l’interface est simple et engageante, amplifie l’adrenaline du jeu. A signaler les nombreuses options de paris sportifs, assure des transactions fiables.
Commencer ici|
Je suis enthousiaste a propos de 1xBet Casino, on ressent une ambiance festive. La selection de jeux est impressionnante, offrant des tables live interactives. Il propulse votre jeu des le debut. Le service d’assistance est au point. Les paiements sont securises et instantanes, par ailleurs des recompenses supplementaires dynamiseraient le tout. En conclusion, 1xBet Casino est une plateforme qui pulse. De plus l’interface est simple et engageante, amplifie le plaisir de jouer. A signaler les options de paris sportifs diversifiees, qui dynamise l’engagement.
VГ©rifier le site|
J’adore le dynamisme de Lucky 31 Casino, ca offre une experience immersive. On trouve une gamme de jeux eblouissante, offrant des sessions live palpitantes. Il rend le debut de l’aventure palpitant. Disponible 24/7 pour toute question. Les paiements sont securises et rapides, mais encore des bonus plus frequents seraient un hit. Pour finir, Lucky 31 Casino est un choix parfait pour les joueurs. Notons egalement l’interface est lisse et agreable, booste le fun du jeu. Egalement excellent le programme VIP avec des recompenses exclusives, offre des recompenses regulieres.
DГ©couvrir dГЁs maintenant|
J’adore la vibe de Action Casino, il offre une experience dynamique. Les options de jeu sont incroyablement variees, incluant des options de paris sportifs dynamiques. Il booste votre aventure des le depart. Le support est fiable et reactif. Les paiements sont surs et fluides, par moments des bonus varies rendraient le tout plus fun. Globalement, Action Casino est un endroit qui electrise. Ajoutons que le site est rapide et style, incite a rester plus longtemps. Un avantage le programme VIP avec des niveaux exclusifs, cree une communaute soudee.
En savoir davantage|
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Получить полную информацию – https://aquariumhunter.com/best-betta-filters
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Доступ к полной версии – https://primenewsnet.com/the-best-point-and-shoot-camera-phones-for-your-next-vacation
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Читать далее > – https://buffalodc.com/2017/12/09/have-you-been-told-you-have-osteoarthritis
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Выяснить больше – https://storylab8.com/science-of-storytelling
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Только факты! – https://mostrasescdecinemarj.com.br/arruma-um-pessoal-pra-gente-botar-uma-macumba-num-disco
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Не пропусти важное – https://atorixit.in/index.php/2023/05/24/best-sap-implementation-partner-in-india
Для оформления документов на поездку за границу или для решения других вопросов, связанных с иностранными языками, обратитесь в бюро переводов с нотариальным заверением.
Бюро переводов служит мостом между культурами, облегчая обмен информацией и идеями. Это особенно важно для компаний, которые стремятся выйти на международный рынок. Бюро переводов помогает компаниям преодолевать языковые барьеры, обеспечивая точность и качество перевода. Кроме того, Бюро переводов может обеспечить успешную коммуникацию с иностранными партнерами и клиентами, что критически важно для бизнеса.
Работа с бюро переводов может принести множество преимуществ для бизнеса, включая увеличение эффективности и снижение затрат. Это особенно важно для компаний, которые работают в области международного бизнеса. Бюро переводов может помочь компаниям расширить свою клиентскую базу, обеспечивая перевод веб-сайтов и онлайн-ресурсов. Кроме того, Бюро переводов может помочь компаниям избежать ошибок и недоразумений, которые могут возникнуть из-за плохого перевода.
Бюро переводов может обеспечить перевод технических документов, таких как инструкции и руководства. Это особенно важно для компаний, которые стремятся расширить свою деятельность на новые рынки. Бюро переводов может помочь компаниям подготовить презентации и другие материалы для международных конференций и выставок. Кроме того, бюро переводов может обеспечить услуги интерпретации, позволяя компаниям общаться с иностранными партнерами и клиентами в режиме реального времени.
Бюро переводов может обеспечить множество преимуществ для бизнеса, включая увеличение эффективности и снижение затрат. Это особенно важно для компаний, которые стремятся выйти на международный рынок. Бюро переводов может обеспечить конфиденциальность и безопасность переводимой информации, что особенно важно для компаний, работающих с конфиденциальными данными. Кроме того, Бюро переводов может обеспечить быстрый и оперативный перевод документов, что критически важно для компаний, работающих в сжатые сроки.
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
https://stagramer.com/lechenie-paranoji-kak-sovremennaya-psihiatriya-pomogaet-spravitsya-s-rasstrojstvom.html
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Подробности по ссылке – https://tkstienliettuyen.com/bi-tieu-do-phi-dai-tuyen-tien-liet-giai-quyet-phan-ngon-hay-xu-ly-phan-goc
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
https://www.riakchr.ru/vyvod-iz-zapoya-na-domu-professionalnyy-vzglyad-narkologa
Для покупки семян высокого качества посетите сайт семяныч заказ семян, где представлен широкий ассортимент семян различных культур.
Семяныч официальный сайт позволяет клиентам ознакомиться с ассортиментом предлагаемых товаров и услуг, а также получить консультацию от профессиональных специалистов.
Официальный сайт компании Семяныч предоставляет возможность клиентам сравнить разные варианты и выбрать тот, который лучше всего соответствует их потребностям.
Официальный сайт компании Семяныч обеспечивает максимальную прозрачность и открытость в отношениях с клиентами, что является ключевым фактором успеха.
Семяныч официальный сайт будет продолжать играть ключевую роль в развитии компании и обеспечении ее лидерства на рынке.
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Смотрите также – https://aragonwineexpert.com/la-tercera-promocion-de-sumilleres-de-aragon-recoge-sus-diplomas
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Наши рекомендации — тут – https://elcapi.com/img_0502
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Запросить дополнительные данные – https://www.gr888.co/review/4738
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Интересует подробная информация – https://sriwijayaplus.com/tips-dan-cara-mengatasi-anak-susah-makan
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Тыкай сюда — узнаешь много интересного – https://www.miyakeshin.co.jp/category1/sample-post1
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Только для своих – https://www.ensv.dz/journee-de-lart-therapie-le-08-decembre-2017
Вывод из запоя в Пушкино в клинике «Трезвый Путь» — это оперативная помощь на дому и в стационаре, персональные детокс-схемы и бережное восстановление организма без постановки на учёт. Мы подключаемся круглосуточно, аккуратно снимаем интоксикацию, стабилизируем давление и пульс, уменьшаем тремор, тревогу и бессонницу, а затем предлагаем понятный маршрут к ремиссии, который вписывается в ваш рабочий и семейный график. Цель — безопасно пройти острый период и не «сорваться» обратно, когда станет чуть полегче.
Получить дополнительные сведения – narkolog-vyvod-iz-zapoya
Алгоритм одинаково прозрачен в обоих форматах. Сначала — экспресс-диагностика: уровень сознания, сатурация, пульс, давление, температура, оценка неврологического статуса и обезвоживания. Затем врач формирует индивидуальную инфузионную схему: регидратационные растворы, коррекция электролитов, поддержка печени и нервной системы, адресная симптоматическая помощь (сон, тревога, тошнота, головная боль). Темп и объём подбираются по переносимости — без «универсальных коктейлей» и лишних препаратов.
Разобраться лучше – вывод из запоя цена
В стационаре мы добавляем расширенную диагностику и круглосуточное наблюдение: это выбор для пациентов с «красными флагами» (галлюцинации, выраженные кардиосимптомы, судороги, рецидивирующая рвота с примесью крови) или тяжёлыми соматическими заболеваниями. На дому мы остаёмся до первичной стабилизации и оставляем письменный план на 24–72 часа, чтобы семья действовала уверенно и согласованно.
Узнать больше – https://vyvod-iz-zapoya-pushkino7.ru/
Wow, superb blog layout! How lengthy have you ever been running a blog for? you make running a blog look easy. The whole glance of your website is wonderful, let alone the content material!
https://www.clinicadentaladarve.com/index.php/2025/10/20/promokod-dlya-melbet-2025/
Состояния при зависимостях чувствительны к времени суток и среде. К ночи нарастает тревога, усиливается тремор, нестабильны показатели ЧСС/АД. Круглосуточный приём позволяет выстроить «мост» через самые сложные часы: собрать сон без избыточной фармаконагрузки, сделать короткие чек-ины, вовремя ретитровать один параметр (свет, дыхательные ритмы, интервалы питья), а утром оформить «малые победы» — гигиена и 10–15 минут тихой ходьбы. Эти простые маркеры часто надёжнее любых субъективных оценок «как себя чувствую».
Изучить вопрос глубже – наркологическая клиника клиника помощь
Для наглядности представлен примерный состав инфузионного раствора, используемого при выводе из запоя:
Подробнее тут – помощь вывод из запоя в ростове-на-дону
В Реутове помощь при запое должна быть быстрой, безопасной и конфиденциальной. Команда «Трезвой Линии» организует выезд врача 24/7, проводит детоксикацию с контролем жизненных показателей и помогает мягко стабилизировать состояние без лишнего стресса. Мы работаем по медицинским протоколам, используем сертифицированные препараты и подбираем схему персонально — с учётом анализов, хронических заболеваний и текущего самочувствия. Приоритет — снять интоксикацию, восстановить сон и аппетит, выровнять давление и снизить тревожность, чтобы человек смог безопасно вернуться к обычному режиму.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-reutov7.ru
J’ai une passion debordante pour Azur Casino, c’est une plateforme qui pulse avec energie. Les jeux proposes sont d’une diversite folle, offrant des sessions live immersives. Le bonus de bienvenue est genereux. Les agents sont toujours la pour aider. Les paiements sont securises et rapides, mais encore des bonus plus frequents seraient un hit. Pour finir, Azur Casino vaut une visite excitante. A mentionner l’interface est lisse et agreable, ce qui rend chaque partie plus fun. A noter le programme VIP avec des recompenses exclusives, qui booste la participation.
Explorer davantage|
Официальный сайт Kraken kra44 cc безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
Why visitors still make use of to read news papers when in this technological world all is accessible on net?
https://www.sotobou.com/melbet-2025-obzor-bk-shopledo/
Официальный сайт Kraken kra44 at безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
Перед таблицей коротко поясним логику: мы выбираем самый безопасный маршрут именно для вашей ситуации, а при изменении состояния оперативно переключаемся на другой формат без пауз.
Выяснить больше – vyvod-iz-zapoya-na-domu-v-pushkino
Форматы вывода из запоя в Пушкино
Ознакомиться с деталями – https://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-deshevo-v-pushkino/
Вывод из запоя осуществляется в несколько этапов, каждый из которых направлен на постепенное восстановление организма. Такой поэтапный подход снижает нагрузку на внутренние органы и повышает эффективность лечения.
Ознакомиться с деталями – https://vyvod-iz-zapoya-v-rostove-na-donu16.ru/vyvod-iz-zapoya-na-domu-rostov-na-donu/
Je suis sous le charme de Azur Casino, il propose une aventure palpitante. Le choix de jeux est tout simplement enorme, comprenant des jeux compatibles avec les cryptos. 100% jusqu’a 500 € avec des spins gratuits. Le suivi est d’une fiabilite exemplaire. Les paiements sont surs et efficaces, bien que des recompenses en plus seraient un bonus. En conclusion, Azur Casino garantit un amusement continu. De surcroit la plateforme est visuellement vibrante, amplifie le plaisir de jouer. Un point fort les tournois frequents pour l’adrenaline, qui stimule l’engagement.
Ouvrir la page|
Je suis epate par Action Casino, ca offre une experience immersive. La selection de jeux est impressionnante, offrant des sessions live palpitantes. Il rend le debut de l’aventure palpitant. Le service d’assistance est au point. Les retraits sont lisses comme jamais, quelquefois des offres plus genereuses rendraient l’experience meilleure. En somme, Action Casino garantit un amusement continu. De surcroit le design est moderne et energique, donne envie de continuer l’aventure. Egalement top le programme VIP avec des recompenses exclusives, qui dynamise l’engagement.
Commencer Г dГ©couvrir|
Je suis sous le charme de 1xBet Casino, il cree un monde de sensations fortes. Les options de jeu sont incroyablement variees, offrant des sessions live palpitantes. Il rend le debut de l’aventure palpitant. Le service est disponible 24/7. Les paiements sont securises et instantanes, quelquefois des offres plus importantes seraient super. En somme, 1xBet Casino offre une aventure inoubliable. Notons egalement la navigation est claire et rapide, ajoute une vibe electrisante. Un avantage les transactions crypto ultra-securisees, propose des avantages sur mesure.
Cliquez ici|
J’adore la vibe de Lucky 31 Casino, il propose une aventure palpitante. Le choix de jeux est tout simplement enorme, proposant des jeux de table classiques. Le bonus de bienvenue est genereux. Le service d’assistance est au point. Les gains sont transferes rapidement, mais encore quelques spins gratuits en plus seraient top. Pour faire court, Lucky 31 Casino est un incontournable pour les joueurs. Ajoutons que la navigation est claire et rapide, donne envie de prolonger l’aventure. A souligner les transactions en crypto fiables, offre des recompenses regulieres.
Visiter le site|
J’ai un veritable coup de c?ur pour 1xBet Casino, il propose une aventure palpitante. Il y a une abondance de jeux excitants, comprenant des jeux compatibles avec les cryptos. Il donne un avantage immediat. Le support est efficace et amical. Les gains sont verses sans attendre, malgre tout des recompenses supplementaires dynamiseraient le tout. Pour conclure, 1xBet Casino est une plateforme qui pulse. A souligner le design est tendance et accrocheur, permet une plongee totale dans le jeu. Un avantage les transactions crypto ultra-securisees, garantit des paiements rapides.
http://www.1xbetcasino366fr.com|
Je suis captive par 1xBet Casino, on y trouve une vibe envoutante. La variete des jeux est epoustouflante, proposant des jeux de casino traditionnels. Le bonus d’inscription est attrayant. Le support client est irreprochable. Les retraits sont ultra-rapides, cependant des offres plus genereuses seraient top. En resume, 1xBet Casino est un lieu de fun absolu. A mentionner l’interface est lisse et agreable, amplifie le plaisir de jouer. Egalement top les options variees pour les paris sportifs, renforce le lien communautaire.
Explorer davantage|
Je suis emerveille par Lucky 31 Casino, il procure une sensation de frisson. La variete des jeux est epoustouflante, offrant des sessions live immersives. Avec des transactions rapides. Disponible a toute heure via chat ou email. Les transactions sont fiables et efficaces, de temps a autre quelques spins gratuits en plus seraient top. Au final, Lucky 31 Casino est une plateforme qui pulse. Par ailleurs l’interface est fluide comme une soiree, facilite une experience immersive. Particulierement attrayant les options de paris sportifs variees, propose des privileges personnalises.
Explorer plus|
Je suis sous le charme de Action Casino, c’est une plateforme qui deborde de dynamisme. Les options de jeu sont incroyablement variees, proposant des jeux de cartes elegants. Avec des depots fluides. Le suivi est impeccable. Les retraits sont simples et rapides, neanmoins quelques tours gratuits supplementaires seraient cool. En somme, Action Casino est un lieu de fun absolu. Par ailleurs la navigation est intuitive et lisse, permet une plongee totale dans le jeu. Egalement top les transactions en crypto fiables, garantit des paiements securises.
http://www.casinoaction365fr.com|
Перед началом терапии врач проводит осмотр, собирает анамнез, измеряет давление и сатурацию, при необходимости делает экспресс-тесты. На основании данных подбирается индивидуальная схема, рассчитываются объёмы инфузии и темп введения, оценивается необходимость кардиоконтроля.
Подробнее – vyvod-iz-zapoya
Форматы вывода из запоя в Пушкино
Получить больше информации – vyvod-iz-zapoya-v-pushkine
Перед началом терапии врач проводит осмотр, собирает анамнез, измеряет давление и сатурацию, при необходимости делает экспресс-тесты. На основании данных подбирается индивидуальная схема, рассчитываются объёмы инфузии и темп введения, оценивается необходимость кардиоконтроля.
Подробнее тут – https://vyvod-iz-zapoya-reutov7.ru/vyvod-iz-zapoya-v-stacionare-v-reutove/
crown of valor casino crown of valor casino .
Выездной формат — это не просто «капельница у кровати». Мы заранее раскладываем визит на модули и назначаем окна оценки: первые 20–40 минут (антиеметический мост, переносимость воды), 60–120 минут (регидратация и электролиты, сглаживание ЧСС/АД), первая ночь (сон ?6 часов и ?1 пробуждение), 12–24 часа (утренняя ясность и способность выполнить 2 короткие бытовые задачи). Одно изменение — один параметр: либо темп инфузии, либо порядок модулей, либо настройка среды (свет/тишина/ритуал). Так причинно-следственные связи остаются прозрачными, а результат — подтверждаемым.
Подробнее – наркологическая клиника в челябинске
vavada casino pl
Inwestycja w dzialke w tym regionie to doskonaly sposob na polaczenie przyjemnego z pozytecznym.
Dzieki rozwijajacej sie infrastrukturze i rosnacemu zainteresowaniu turystow, ceny dzialek stopniowo wzrastaja. Region ten przyciaga milosnikow gorskich wedrowek i aktywnego wypoczynku.
#### **2. Gdzie szukac najlepszych ofert dzialek?**
Wybor odpowiedniej lokalizacji zalezy od indywidualnych potrzeb i budzetu. Warto sprawdzic profesjonalne strony internetowe, takie jak dzialki-beskidy.pl, ktore prezentuja sprawdzone oferty.
Przed zakupem nalezy dokladnie przeanalizowac dostepnosc mediow i warunki zabudowy. Wazne jest, aby sprawdzic, czy dzialka ma dostep do wody i pradu, co wplywa na wygode uzytkowania.
#### **3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
Nieruchomosc w gorach to nie tylko inwestycja finansowa, ale rowniez szansa na poprawe jakosci zycia. Mozna tu zbudowac dom letniskowy i cieszyc sie urokami przyrody przez caly rok.
Dodatkowo, region ten oferuje wiele atrakcji, takich jak szlaki turystyczne i stoki narciarskie. Wlasciciele dzialek moga korzystac z licznych festiwali i wydarzen kulturalnych organizowanych w regionie.
#### **4. Jak przygotowac sie do zakupu dzialki?**
Przed podjeciem decyzji warto skonsultowac sie z prawnikiem i geodeta. Dobrze jest sprawdzic historie nieruchomosci i upewnic sie, ze nie ma zadnych obciazen.
Wazne jest rowniez okreslenie swojego budzetu i planow zwiazanych z zagospodarowaniem terenu. Warto rozwazyc wszystkie opcje, aby wybrac najlepsza dla siebie mozliwosc.
—
### **Szablon Spinu**
**1. Dlaczego warto kupic dzialke w Beskidach?**
– Inwestowanie w dzialki w tym regionie to swietny sposob na zabezpieczenie finansowej przyszlosci.
– Dzialki w Beskidach to coraz czesciej wybierana lokata kapitalu przez swiadomych inwestorow.
**2. Gdzie szukac najlepszych ofert dzialek?**
– Dobrym rozwiazaniem jest skorzystanie ze sprawdzonych stron internetowych, takich jak dzialki-beskidy.pl.
– Warto porownac rozne oferty, aby znalezc najbardziej oplacalna inwestycje.
**3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
– Dzialka w Beskidach moze stac sie zrodlem dodatkowego dochodu dzieki wynajmowaniu turystom.
– Region oferuje wiele aktywnosci, od wedrowek po gorach po jazde na nartach.
**4. Jak przygotowac sie do zakupu dzialki?**
– Warto dokladnie sprawdzic historie dzialki, aby upewnic sie, ze nie ma zadnych roszczen.
– Okreslenie budzetu i celow inwestycji ulatwi podjecie wlasciwej decyzji.
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Смотрите также… – https://www.sylke-kirschnick.de/2020/07/09/wer-schreibt-hier
1xbet giri? 1xbet giri? .
перепланировка согласование перепланировка согласование .
surewin http://www.surewin-online.com .
beep beep casino http://beepbeepcasino-online.com/ .
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Переходите по ссылке ниже – https://sshhospital.com/%D9%86%D9%85%D9%88%D8%AF%D8%A7%D8%B1-%D8%B3%D8%A7%D8%B2%D9%85%D8%A7%D9%86%DB%8C
Je ne me lasse pas de Azur Casino, ca invite a l’aventure. On trouve une gamme de jeux eblouissante, avec des slots aux designs captivants. Le bonus de depart est top. Le support est rapide et professionnel. Les paiements sont securises et instantanes, neanmoins plus de promotions frequentes boosteraient l’experience. En somme, Azur Casino assure un divertissement non-stop. Par ailleurs la navigation est claire et rapide, permet une immersion complete. Egalement genial le programme VIP avec des avantages uniques, offre des recompenses regulieres.
Commencer ici|
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Практические советы ждут тебя – https://davidfalter.com/15-brilliant-tips-for-illustration-newbies
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Слушай внимательно — тут важно – http://www.tsf.edu.pl/zapomniane-metody-fotografii
Clarte Nexive se differencie comme une plateforme de placement crypto revolutionnaire, qui exploite la puissance de l’intelligence artificielle pour fournir a ses clients des avantages concurrentiels decisifs.
Son IA etudie les marches financiers en temps reel, detecte les occasions interessantes et execute des strategies complexes avec une precision et une vitesse inatteignables pour les traders humains, maximisant ainsi les potentiels de profit.
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Уникальные данные только сегодня – https://maygiattham.com/san-pham/may-cha-san-tham-cong-nghiep-supper-clean-sc-005
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Уникальные данные только сегодня – https://interioressoka.com/hello-world
Публикация предлагает читателю не просто информацию, а инструменты для анализа и саморазвития. Мы стимулируем критическое мышление, предлагая различные точки зрения и призывая к самостоятельному поиску решений.
Обратиться к источнику – http://pollenschutzmaske.de/guestbook.html
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Ознакомьтесь с аналитикой – http://www.strucktour.com/?page_id=1290
Если вы ищете профессиональную помощь в решении семейных проблем, воспользуйтесь услугами помощь семейного психолога онлайн для удобного и максимально комфортного общения.
При выборе семейного психолога онлайн может стать важным шагом на пути к гармонии в ваших отношениях. Необходимо учитывать множество аспектов, когда вы ищете специалиста. Первое, на что стоит обратить внимание, это опыт специалиста, поскольку это напрямую влияет на результат. Опытный психолог способен предложить более эффективные решения.
Во-вторых, не забудьте почитать отзывы об этом специалисте. Отзывы помогают понять, насколько психолог эффективен. Интернет полон информации, связанной с мнениями клиентов. Это поможет вам сделать более обоснованный выбор.
Не менее важным является удобный формат встреч. Некоторые предпочитают видеозвонки, другие — телефонные разговоры. Выберите тот способ общения, который будет наиболее удобным для вас. Комфортный формат общения создает благоприятную атмосферу.
Также важно учитывать цену на услуги психолога. Разные специалисты могут предлагать различные расценки. Определитесь с бюджетом заранее и ищите специалиста в этой ценовой категории. Теперь у вас есть несколько ключевых аспектов для выбора семейного психолога онлайн.
vavada casino pl
Inwestycja w dzialke w tym regionie to doskonaly sposob na polaczenie przyjemnego z pozytecznym.
Dzieki rozwijajacej sie infrastrukturze i rosnacemu zainteresowaniu turystow, ceny dzialek stopniowo wzrastaja. Coraz wiecej osob docenia spokoj i piekno przyrody, jakie oferuja Beskidy.
#### **2. Gdzie szukac najlepszych ofert dzialek?**
Wybor odpowiedniej lokalizacji zalezy od indywidualnych potrzeb i budzetu. Najlepsze propozycje mozna znalezc na specjalistycznych serwisach, gdzie dostepne sa dzialki o roznej powierzchni i standardzie.
Przed zakupem nalezy dokladnie przeanalizowac dostepnosc mediow i warunki zabudowy. Wiele ofert zawiera szczegolowe informacje o mozliwosciach zagospodarowania terenu, co ulatwia podjecie decyzji.
#### **3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
Nieruchomosc w gorach to nie tylko inwestycja finansowa, ale rowniez szansa na poprawe jakosci zycia. Mozna tu zbudowac dom letniskowy i cieszyc sie urokami przyrody przez caly rok.
Dodatkowo, region ten oferuje wiele atrakcji, takich jak szlaki turystyczne i stoki narciarskie. Wlasciciele dzialek moga korzystac z licznych festiwali i wydarzen kulturalnych organizowanych w regionie.
#### **4. Jak przygotowac sie do zakupu dzialki?**
Przed podjeciem decyzji warto skonsultowac sie z prawnikiem i geodeta. Profesjonalna pomoc pozwoli uniknac nieprzyjemnych niespodzianek zwiazanych z formalnosciami.
Wazne jest rowniez okreslenie swojego budzetu i planow zwiazanych z zagospodarowaniem terenu. Wiele osob decyduje sie na kredyt, aby sfinansowac zakup wymarzonej dzialki.
—
### **Szablon Spinu**
**1. Dlaczego warto kupic dzialke w Beskidach?**
– Beskidy to idealne miejsce dla osob szukajacych spokoju i bliskosci natury.
– Rosnaca popularnosc tego regionu przeklada sie na wzrost wartosci nieruchomosci.
**2. Gdzie szukac najlepszych ofert dzialek?**
– Profesjonalne agencje nieruchomosci czesto oferuja najlepsze propozycje w regionie.
– Kluczowe jest sprawdzenie, czy dzialka ma wszystkie niezbedne pozwolenia.
**3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
– Dzialka w Beskidach moze stac sie zrodlem dodatkowego dochodu dzieki wynajmowaniu turystom.
– Coraz wiecej osob docenia walory turystyczne i rekreacyjne Beskidow.
**4. Jak przygotowac sie do zakupu dzialki?**
– Konsultacja z geodeta pomoze uniknac problemow z granicami nieruchomosci.
– Niektore oferty umozliwiaja elastyczne formy platnosci, co moze byc korzystne.
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Где можно узнать подробнее? – https://asbn.site/les-dernieres-tendances-en-matiere-de-chauffage-thermique
Мы предлагаем вам подробное руководство, основанное на проверенных источниках и реальных примерах. Каждая часть публикации направлена на то, чтобы помочь вам разобраться в сложных вопросах и применить знания на практике.
Познакомиться с результатами исследований – https://sshhospital.com/%D9%86%D9%85%D9%88%D8%AF%D8%A7%D8%B1-%D8%B3%D8%A7%D8%B2%D9%85%D8%A7%D9%86%DB%8C
Коммерческий автотранспорт в лизинг обеспечивает бизнесу необходимые транспортные средства без значительных первоначальных затрат . Это особенно важно для начинающих бизнесов, которым нужно быстро реагировать на рыночные потребности с минимальными инвестициями. Компании, выбирающие лизинг, могут оперативно менять состав своего флота в зависимости от рыночных потребностей.
Лизинг коммерческих автомобилей позволяет бизнесу оптимизировать свои затраты, избегая крупных расходов на покупку автомобилей . Это особенно ценно для тех компаний, которые работают в условиях высокой конкуренции и должны оперативно адаптироваться к новым условиям . Кроме того, лизинг дает возможность уменьшить бумажную работу и административные расходы, связанные с содержанием автомобилей .
Существует несколько типов лизинговых соглашений для коммерческого автотранспорта, каждое из которых предлагает свои преимущества и недостатки, подходящие для разных бизнес-моделей . Одним из наиболее распространенных типов лизинга является операционный лизинг, который предоставляет компании возможность арендовать автомобиль на определенный период, не неся ответственности за его амортизацию . Другой тип лизинга – финансовый лизинг, который предполагает, что компания арендует автомобиль с обязательством покупки его в конце срока лизинга .
При выборе лизинговой компании для коммерческого автотранспорта, компании должны сравнить условия и ставки, предлагаемые разными лизинговыми компаниями, чтобы найти наиболее выгодное предложение . Это особенно важно для тех компаний, которые хотят иметь возможность оперативно решать любые вопросы, связанные с эксплуатацией автомобилей. Кроме того, компании должны интересоваться условиями страхования и ответственности за автомобили .
купить спецтехнику в лизинг https://kommercheskij-transport-v-lizing2.ru/specztehnika/
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Получить дополнительные сведения – вывод из запоя клиника калининград
valor casino app valor casino app .
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Выяснить больше – нарколог вывод из запоя калининград
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Подробнее тут – вывод из запоя круглосуточно в воронеже
В городском ритме Ставрополя дорога сама по себе может усугублять симптомы: плотный трафик, резкие звуки, длинные коридоры ожидания. Поэтому «СтаврВита» разворачивает секторные выезды: немаркированный транспорт, гражданская одежда специалистов, согласованная парковка и подъезд, доставка расходников отдельно от врача при необходимости — чтобы на месте сразу переходить к диагностике и запуску инфузии. Переписка ведётся нейтральными формулировками, уведомления «беззвучные», документы без стигматизирующих слов. По желанию всё общение идёт через доверенное лицо: оно получает короткие апдейты в согласованные «окна», не перегружаясь клиническими деталями.
Ознакомиться с деталями – вывод из запоя в стационаре ставрополь
В этом обзоре представлены различные методы избавления от зависимости, включая терапевтические и психологические подходы. Мы сравниваем их эффективность и предоставляем рекомендации для тех, кто хочет вернуться к трезвой жизни. Читатели смогут найти информацию о реабилитационных центрах и поддерживающих группах.
Ознакомиться с деталями – вывод из запоя клиника
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Ознакомиться с деталями – наркологическая клиника стационар
1xbet tr 1xbet tr .
экспертиза перепланировки квартиры http://www.soglasovanie-pereplanirovki-1.ru/ .
casino beep beep beepbeepcasino-online.com .
surewin malaysia login http://www.surewin-online.com/ .
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Разобраться лучше – https://narkologicheskaya-klinika-v-kaliningrade15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
Техника помогает, но не доминирует. Мы используем портативные приборы с мягкой индикацией и низким уровнем шума, чтобы не разрушать формирующуюся «ночную кривую». Контроль в остром окне чаще, вечером — мягче: так сохраняется физиология сна и снижается потребность в дополнительной фармакологии.
Подробнее тут – наркологические клиники алкоголизм петрозаводск
Мы собираем терапию из проверенных модулей: гидратация, коррекция электролитов, гастропротекция, антиоксидантная поддержка, мягкая анксиолитика по показаниям, поведенческие интервенции (свет, тишина, дыхание 4–6, стимул-контроль, вечерние ритуалы). Объём и темп зависят от ведущего симптома и времени суток: при кардиореактивном вечере больше внимания уделяется среде, при тошноте — гастропротекции и «тёплому питанию», при поверхностном сне — цифровой гигиене и световым сценариям. Ниже приведена ориентировочная матрица выбора; финальное решение — за лечащим врачом с учётом противопоказаний и лекарственных взаимодействий.
Подробнее тут – наркологическая клиника вывод из запоя петрозаводск
Мы не составляем «супер-смеси» «на всякий случай». Капельница — это набор модулей, каждый из которых отвечает за конкретную задачу: гидратация, электролиты, гастропротекция, антиоксидантная поддержка; при показаниях — мягкая анксиолитика. Порядок модулей зависит от ведущего симптом-кластера и времени суток.
Разобраться лучше – капельница от запоя стоимость
В этом исследовании рассмотрены методы лечения зависимостей и их эффективность. Мы проанализируем различные подходы, используемые в реабилитационных центрах, и представим данные о результативности программ. Читатели получат надежные и научно обоснованные сведения о данной проблеме.
Узнать больше – вывод из запоя
В этом обзоре представлены различные методы избавления от зависимости, включая терапевтические и психологические подходы. Мы сравниваем их эффективность и предоставляем рекомендации для тех, кто хочет вернуться к трезвой жизни. Читатели смогут найти информацию о реабилитационных центрах и поддерживающих группах.
Ознакомиться с деталями – наркология вывод из запоя Симферополь
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Подробнее – вывод из запоя капельница на дому воронеж
Эта публикация обращает внимание на важность профилактики зависимостей. Мы обсудим, как осведомленность и образование могут помочь в предотвращении возникновения зависимости. Читатели смогут ознакомиться с полезными советами и ресурсами, которые способствуют здоровому образу жизни.
Изучить вопрос глубже – вывод из запоя на дому цена в Москве
Ниже — «скелет» визита. На месте врач адаптирует содержание под возраст, соматику, текущие лекарства и проявления абстиненции. Главная идея — быстро получить цифры, аккуратно запустить инфузию и заранее зафиксировать ориентиры, чтобы семья не импровизировала в «трудный час».
Получить дополнительные сведения – анонимный вывод из запоя ставрополь
Je suis totalement conquis par Lucky 31 Casino, ca invite a l’aventure. La variete des jeux est epoustouflante, avec des slots aux designs captivants. Il booste votre aventure des le depart. Le service d’assistance est au point. Les paiements sont securises et instantanes, cependant des recompenses supplementaires seraient parfaites. Dans l’ensemble, Lucky 31 Casino assure un fun constant. En bonus le site est rapide et engageant, donne envie de continuer l’aventure. Egalement top le programme VIP avec des recompenses exclusives, renforce la communaute.
Voir le site|
valor de las fichas de casino valor de las fichas de casino .
J’adore l’energie de Azur Casino, il procure une sensation de frisson. Les jeux proposes sont d’une diversite folle, proposant des jeux de cartes elegants. Avec des depots instantanes. Le suivi est toujours au top. Les transactions sont fiables et efficaces, de temps en temps plus de promos regulieres ajouteraient du peps. Globalement, Azur Casino est un incontournable pour les joueurs. Notons egalement le site est rapide et style, amplifie le plaisir de jouer. Egalement super les evenements communautaires pleins d’energie, propose des avantages uniques.
Entrer sur le site|
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Детальнее – анонимный вывод из запоя в воронеже
J’ai une passion debordante pour 1xBet Casino, ca donne une vibe electrisante. Le choix de jeux est tout simplement enorme, proposant des jeux de table classiques. Il offre un coup de pouce allechant. Le suivi est d’une precision remarquable. Le processus est fluide et intuitif, a l’occasion plus de promos regulieres ajouteraient du peps. En somme, 1xBet Casino est un must pour les passionnes. Notons aussi l’interface est intuitive et fluide, amplifie le plaisir de jouer. Un plus les transactions en crypto fiables, offre des bonus constants.
Aller Г la page|
Je suis enthousiasme par Lucky 31 Casino, ca donne une vibe electrisante. Les options de jeu sont infinies, incluant des paris sportifs en direct. Il propulse votre jeu des le debut. Disponible 24/7 par chat ou email. Les paiements sont securises et instantanes, cependant des bonus plus frequents seraient un hit. Dans l’ensemble, Lucky 31 Casino vaut une exploration vibrante. En complement l’interface est simple et engageante, ajoute une vibe electrisante. Un element fort le programme VIP avec des recompenses exclusives, cree une communaute soudee.
http://www.casinolucky31fr.com|
Je suis captive par 1xBet Casino, ca invite a l’aventure. Le choix de jeux est tout simplement enorme, offrant des sessions live immersives. Avec des depots instantanes. Le suivi est toujours au top. Les transactions sont toujours fiables, mais des bonus varies rendraient le tout plus fun. Au final, 1xBet Casino est un lieu de fun absolu. Par ailleurs le design est moderne et attrayant, amplifie le plaisir de jouer. A mettre en avant les evenements communautaires dynamiques, garantit des paiements securises.
Obtenir les dГ©tails|
1x lite http://www.1xbet-7.com .
Je suis enthousiaste a propos de Action Casino, il cree une experience captivante. Les titres proposes sont d’une richesse folle, comprenant des jeux crypto-friendly. 100% jusqu’a 500 € avec des free spins. Le support est rapide et professionnel. Le processus est clair et efficace, par ailleurs des bonus diversifies seraient un atout. En somme, Action Casino assure un divertissement non-stop. Pour completer l’interface est lisse et agreable, ce qui rend chaque partie plus fun. Egalement super les evenements communautaires dynamiques, qui motive les joueurs.
https://casinoactionfr.com/|
Je suis emerveille par Lucky 31 Casino, on y trouve une energie contagieuse. La selection de jeux est impressionnante, incluant des paris sur des evenements sportifs. Il offre un coup de pouce allechant. Le service d’assistance est au point. Les transactions sont toujours fiables, bien que plus de promotions variees ajouteraient du fun. En somme, Lucky 31 Casino est un endroit qui electrise. A souligner le design est moderne et energique, facilite une immersion totale. Un point cle les transactions en crypto fiables, propose des avantages sur mesure.
Savoir plus|
Этот обзор сосредоточен на различных подходах к избавлению от зависимости. Мы изучим традиционные и альтернативные методы, а также их сочетание для достижения максимальной эффективности. Читатели смогут открыть для себя новые стратегии и подходы, которые помогут в их борьбе с зависимостями.
Выяснить больше – вывод из запоя на дому недорого Москва
проектирование перепланировки http://www.soglasovanie-pereplanirovki-1.ru .
Мы придерживаемся принципа минимально достаточной фармакотерапии: только те препараты и в том темпе, который подтверждён текущими измерениями. Врач не «усиливает» схему ради видимости — он снимает лишнее и добавляет нужное, если динамика «плоская». Такой подход уменьшает риски дневной заторможенности, держит ясность к вечеру и ускоряет нормализацию сна. Команда «СтаврВита» синхронизируется через защищённые каналы: куратор маршрута, дежурный нарколог, терапевт, психиатр/клинический психолог и координатор логистики. Пациент и семья получают краткие памятки с понятными целями и критериями эскалации, чтобы не спорить «ждать или звонить».
Получить дополнительные сведения – вывод из запоя на дому круглосуточно
Je suis enthousiasme par Action Casino, ca transporte dans un monde d’excitation. Le catalogue est un tresor de divertissements, comprenant des jeux crypto-friendly. Le bonus de bienvenue est genereux. Les agents repondent avec efficacite. Les transactions sont fiables et efficaces, par ailleurs des recompenses supplementaires dynamiseraient le tout. En bref, Action Casino garantit un plaisir constant. Par ailleurs la plateforme est visuellement dynamique, ajoute une vibe electrisante. A souligner les tournois reguliers pour la competition, qui booste la participation.
Voir la page|
beep casino http://www.beepbeepcasino-online.com .
surewin casino login https://surewin-online.com/ .
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Подробнее можно узнать тут – вывод из запоя капельница на дому
Наркологическая клиника «РеМед Карелия» — это круглосуточная медицинская помощь, построенная на принципе клинической точности: каждая процедура имеет цель, проверяемые маркеры и назначенное окно переоценки. Мы используем современные методы детоксикации и постабстинентной стабилизации, не перегружая терапию «на всякий случай» и не полагаясь на универсальные «сильные капельницы». Вместо этого — модульные схемы, корректировка одного параметра за раз и обязательная оценка результата. Такой подход снижает фармаконагрузку, ускоряет восстановление сна и аппетита и делает лечение предсказуемым для пациента и его семьи. Анонимность встроена в процессы: немаркированные входы, гражданская форма персонала, нейтральные формулировки в документах, «тихие» уведомления и разграниченный доступ к карте наблюдения.
Разобраться лучше – запой наркологическая клиника петрозаводск
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Получить больше информации – https://narkologicheskaya-klinika-v-kaliningrade15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
J’adore le dynamisme de Azur Casino, ca transporte dans un monde d’excitation. On trouve une gamme de jeux eblouissante, comprenant des jeux compatibles avec les cryptos. Il booste votre aventure des le depart. Le service client est excellent. Les transactions sont d’une fiabilite absolue, de temps a autre des offres plus consequentes seraient parfaites. Pour finir, Azur Casino offre une experience inoubliable. En extra le design est style et moderne, ce qui rend chaque session plus excitante. Un avantage notable les transactions crypto ultra-securisees, assure des transactions fluides.
Essayer|
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Подробнее – наркологические клиники алкоголизм
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Исследовать вопрос подробнее – врач вывод из запоя в калининграде
Если на предвызовном созвоне звучат «красные флаги» (неукротимая рвота, выраженная дезориентация, «скачущий» ритм, одышка), мы сразу резервируем палату усиленного наблюдения и подключаем расширенный мониторинг. При низком риске старт возможен амбулаторно или на дому с бесшовным переводом в стационар при необходимости — без очередей и «говорящих» вывесок. Во всех сценариях анонимность — не «опция», а стандарт по умолчанию.
Подробнее можно узнать тут – наркологическая клиника клиника помощь в петрозаводске
Мы отказываемся от «сильных» коктейлей ради скорости и опираемся на принцип одного изменения за раз: корректируется только темп, объём или последовательность модулей, после чего следует контроль в согласованное «окно». Такой подход минимизирует лекарственную нагрузку, защищает печень, миокард и центральную нервную систему, а также снижает риск рецидивной тревоги в первую ночь. Важная часть лечения — сенсорная гигиена: тёплая подсветка вместо резкого верхнего света, тихий режим в смартфонах, маска для сна и беруши при чувствительности к шуму. Эти «бытовые» меры — на самом деле клинические инструменты с измеримым эффектом на пульс, дыхание и латентность сна.
Выяснить больше – капельница от запоя на дому круглосуточно
Карта делает решения прозрачными: если критерий не достигнут, меняется ровно один параметр с назначением новой точки контроля. Это сохраняет причинно-следственную связь и уменьшает общую фармаконагрузку без компромиссов по безопасности.
Получить дополнительные сведения – нарколог на дом цены
Первое сутки — каркас программы. Мы фиксируем цель каждого окна, инструменты, метрики контроля и критерий перехода. Если ответ «плоский», меняется ровно один параметр (темп/объём/последовательность) и назначается новое окно проверки. Этот принцип позволяет понять, что именно сработало, и избежать полипрагмазии.
Подробнее – https://narkologicheskaya-klinika-v-petrozavodske15.ru/petrozavodsk-narkologiya
Петрозаводск задаёт свои параметры среды: озёрный ветер, световые перепады, «звонкие» подъезды старого фонда. В «РеМед Карелия» мы проектируем маршрут так, чтобы городской фон работал на пациента. Короткая регистрация без «толстых анкет», приглушённый тёплый свет в приёмной, отсутствие громких объявлений, отдельный вход без вывесок и немаркированный транспорт — всё это снижает сенсорную нагрузку и уменьшает вечернюю кардиореактивность. Семья получает «окна связи» в фиксированное время, чтобы эмоциональные звонки не разрушали «ночную кривую» сна. Для пациентов, стартующих на дому, мы привозим переносные решения — лампу тёплого спектра, ширмы, шумопоглощающие аксессуары, — чтобы не усиливать тревогу и не «подливать» раздражителей в момент инфузии.
Выяснить больше – наркологические клиники алкоголизм петрозаводск
Мы избегаем шаблонов. Состав инфузий и порядок действий подбираются индивидуально: учитываем тяжесть интоксикации, сопутствующие заболевания, чувствительность к свету и шуму, объём воды, который человек переносит малыми глотками, а также, как реагирует на вечерние уведомления телефона. Главная цель первых часов — стабилизировать витальные показатели, вернуть переносимость питья и лёгкой тёплой пищи, выровнять вариабельность пульса к сумеркам и обеспечить физиологичный сон без «переседации». Все измерения фиксируются в краткой карте наблюдения с разграничением доступа по ролям — это защищает данные и ускоряет принятие решений.
Детальнее – https://narkologicheskaya-klinika-v-kaliningrade15.ru/vyvod-iz-zapoya-kaliningrad-staczionar/
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Получить дополнительную информацию – вывод из запоя на дому воронеж
В статье по вопросам здоровья мы рассматриваем актуальные проблемы, с которыми сталкивается общество. Обсуждаются заболевания, факторы риска и важные аспекты профилактики. Читатели получат полезные советы о том, как сохранить здоровье и улучшить качество жизни.
Подробнее можно узнать тут – вывод из запоя цена
Городская среда Петрозаводска со сменой ветров с Онежского озера, короткими сумерками и сезонными перепадами влажности может усиливать тревожность в вечерние часы. Мы учитываем это с момента первого контакта: согласованная парковка, отдельный вход без вывесок, короткая регистрация без «толстых анкет», приглушённый тёплый свет в зоне ожидания и отсутствие громких объявлений. Родственникам предоставляются «тихие окна» связи — лаконичные апдейты в фиксированное время, чтобы не перегружать пациента и не дёргать команду в критические окна наблюдения. Такой «мягкий» контур снижает сенсорную нагрузку, стабилизирует вариабельность ЧСС к сумеркам и сокращает число импульсивных просьб «усилить на ночь».
Подробнее можно узнать тут – наркологические клиники алкоголизм петрозаводск
Первое сутки с половиной — «каркас» программы. Мы формулируем цель каждого окна, фиксируем инструменты и пороги перехода. Если ожидаемой динамики нет, меняется один параметр (темп/объём/последовательность), после чего назначается повторная оценка. Это защищает от полипрагмазии и сохраняет причинно-следственную связь.
Получить дополнительные сведения – наркологические клиники алкоголизм петрозаводск
Вся динамика заносится в единую карту наблюдения, доступ к которой разграничен по ролям. При переходе к амбулаторной точке или стационару не происходит «перезапуска истории»: новые назначения учитывают всё, что сделано на старте.
Углубиться в тему – наркологический вывод из запоя в воронеже
Ниже — практическая карта первых часов. Она помогает всем участникам понимать логику действий, точки контроля и критерии перехода. Если ответ «плоский», меняем один параметр и возвращаемся к оценке в назначённое время — без хаотичных «усилений».
Ознакомиться с деталями – врача капельницу от запоя
Мы не составляем «супер-смеси» «на всякий случай». Капельница — это набор модулей, каждый из которых отвечает за конкретную задачу: гидратация, электролиты, гастропротекция, антиоксидантная поддержка; при показаниях — мягкая анксиолитика. Порядок модулей зависит от ведущего симптом-кластера и времени суток.
Исследовать вопрос подробнее – капельница от запоя стоимость в мурманске
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Выяснить больше – наркологическая клиника наркологический центр калининград
«Волшебной капельницы» не существует. Мы структурируем инфузии от симптомов, а не от «средних рецептов». Ниже — логика подбора для типичных профилей; реальную схему определяет врач на месте.
Подробнее – частная наркологическая клиника в калининграде
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Углубиться в тему – наркологическая клиника клиника помощь в калининграде
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Узнать больше – вывод из запоя на дому цена калининград
В данном обзоре представлены основные направления и тренды в области медицины. Мы обсудим актуальные проблемы здравоохранения, свежие открытия и новые подходы, которые меняют представление о лечении и профилактике заболеваний. Эта информация будет полезна как специалистам, так и широкой публике.
Исследовать вопрос подробнее – скорая вывод из запоя Симферополь
Если при телефонном триаже выявляются «красные флаги» (дыхание, ритм, сознание), маршрут настраивается сразу под стационар: те же цели, тот же ответственный куратор, только непрерывный мониторинг витальных и ночной пост. А когда риски невысоки, мы начинаем дома или амбулаторно и удерживаем темп контрольными включениями — это чаще всего даёт спокойную первую ночь и легче переносимый второй день.
Получить больше информации – помощь вывод из запоя
Этот информационный материал подробно освещает проблему наркозависимости, ее причины и последствия. Мы предлагаем информацию о методах лечения, профилактики и поддерживающих программах. Цель статьи — повысить осведомленность и продвигать идеи о необходимости борьбы с зависимостями.
Ознакомиться с деталями – срочный вывод из запоя
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Выяснить больше – https://vivod-iz-zapoya-voronezh15.ru/vyvod-iz-zapoya-staczionar-voronezh/
Экстренный вывод из запоя — это управляемая медицинская процедура, а не «сильная капельница на удачу». В наркологической клинике «ВоронежВита» мы действуем по чётким правилам: от телефонного триажа и тихого выезда бригады до адресной детоксикации и вечерних контрольных включений. Главная цель — безопасно стабилизировать состояние, снизить тремор и тошноту, выровнять сердечный ритм и вернуть физиологичный сон уже в первые ночи. Мы выбираем минимально достаточные вмешательства, чтобы днём сохранялась ясность и не возникало желания «самостоятельно усилить» схему. Конфиденциальность встроена в каждый шаг: гражданская одежда специалистов, немаркированный транспорт, нейтральные формулировки в переписке и документах.
Исследовать вопрос подробнее – вывод из запоя цена
Клиника работает 24/7, принимая пациентов как в стационаре, так и в формате выездных бригад на дом. Мы соединяем медицинскую, психотерапевтическую и поведенческую опоры в единую траекторию: от быстрой стабилизации витальных показателей до настройки вечерних ритуалов (свет, дыхание 4–6, «цифровая тишина»). Внутри команды выстроена координация: нарколог курирует острые окна, терапевт отслеживает соматический фон и лекарственные взаимодействия, психиатр и клинический психолог уменьшают тревожную реактивность и формируют устойчивые навыки «перехвата» импульсов, медсёстры обеспечивают безошибочную технику процедур, куратор синхронизирует всех участников и ведёт «дорожную карту» лечения понятным языком фактов.
Углубиться в тему – наркологическая клиника лечение алкоголизма петрозаводск
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить дополнительную информацию – вывод из запоя дешево в калининграде
В городском ритме Ставрополя дорога сама по себе может усугублять симптомы: плотный трафик, резкие звуки, длинные коридоры ожидания. Поэтому «СтаврВита» разворачивает секторные выезды: немаркированный транспорт, гражданская одежда специалистов, согласованная парковка и подъезд, доставка расходников отдельно от врача при необходимости — чтобы на месте сразу переходить к диагностике и запуску инфузии. Переписка ведётся нейтральными формулировками, уведомления «беззвучные», документы без стигматизирующих слов. По желанию всё общение идёт через доверенное лицо: оно получает короткие апдейты в согласованные «окна», не перегружаясь клиническими деталями.
Углубиться в тему – вывод из запоя на дому недорого в ставрополе
Такая карта делает лечение обозримым и дисциплинирует решения: пациент видит цель и порог перехода, семья понимает, зачем нужно соблюдать «тихие» часы, команда сохраняет управляемость и не «крутит ручки» ночью.
Исследовать вопрос подробнее – наркологическая клиника стационар
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Разобраться лучше – вывод из запоя в стационаре
В данной статье мы акцентируем внимание на важности поддержки в процессе выздоровления. Мы обсудим, как друзья, семья и профессионалы могут помочь тем, кто сталкивается с зависимостями. Читатели получат практические советы, как поддерживать близких на пути к новой жизни.
Выяснить больше – вывод из запоя в стационаре
Техника помогает, но не доминирует. Мы используем портативные приборы с мягкой индикацией и низким уровнем шума, чтобы не разрушать формирующуюся «ночную кривую». Контроль в остром окне чаще, вечером — мягче: так сохраняется физиология сна и снижается потребность в дополнительной фармакологии.
Выяснить больше – анонимная наркологическая клиника
В данной статье мы акцентируем внимание на важности поддержки в процессе выздоровления. Мы обсудим, как друзья, семья и профессионалы могут помочь тем, кто сталкивается с зависимостями. Читатели получат практические советы, как поддерживать близких на пути к новой жизни.
Изучить вопрос глубже – вывод из запоя клиника
Карта делает маршрут прозрачным для пациента и семьи. Вместо «лучше/хуже» — факты и понятные пороги. Это снижает тревожность и помогает соблюдать режим без сопротивления.
Подробнее тут – http://narkologicheskaya-klinika-petrozavodsk15.ru/chastnaya-narkologicheskaya-klinika-petrozavodsk/
В этой медицинской статье мы погрузимся в актуальные вопросы здравоохранения и лечения заболеваний. Читатели узнают о современных подходах, методах диагностики и новых открытий в научных исследованиях. Наша цель — донести важную информацию и повысить уровень осведомленности о здоровье.
Получить дополнительную информацию – вывод из запоя в стационаре
Мы придерживаемся принципа минимально достаточной фармакотерапии: только те препараты и в том темпе, который подтверждён текущими измерениями. Врач не «усиливает» схему ради видимости — он снимает лишнее и добавляет нужное, если динамика «плоская». Такой подход уменьшает риски дневной заторможенности, держит ясность к вечеру и ускоряет нормализацию сна. Команда «СтаврВита» синхронизируется через защищённые каналы: куратор маршрута, дежурный нарколог, терапевт, психиатр/клинический психолог и координатор логистики. Пациент и семья получают краткие памятки с понятными целями и критериями эскалации, чтобы не спорить «ждать или звонить».
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-stavropol15.ru/stavropol-lechenie-alkogolizma
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Узнать больше – вывод из запоя вызов на дом в воронеже
Мурманск — город с длинными сумерками и влажным ветром от Кольского залива, что сказывается на сну и вечерней кардиолабильности. Поэтому мы адаптируем маршруты: выездные бригады работают в гражданской одежде, заходят быстро и тихо, а в палатах клиники используется тёплая подсветка и акустическое поглощение. Для ночных поступлений действует протокол «мягкой посадки»: минимизированные контакты, тёплая вода малыми глотками, затем — диагностика и старт инфузии при отсутствии «красных флагов». Это снижает сенсорную нагрузку и позволяет организму дать честный клинический ответ без лишних раздражителей.
Подробнее можно узнать тут – капельница от запоя в мурманске
Ниже — «скелет» визита. На месте врач адаптирует содержание под возраст, соматику, текущие лекарства и проявления абстиненции. Главная идея — быстро получить цифры, аккуратно запустить инфузию и заранее зафиксировать ориентиры, чтобы семья не импровизировала в «трудный час».
Получить больше информации – http://vyvod-iz-zapoya-stavropol15.ru/
В этой публикации мы рассматриваем важную тему борьбы с зависимостями, включая алкогольную и наркотическую зависимости. Мы обсудим методы лечения, реабилитации и поддержку, которые могут помочь людям, столкнувшимся с этой проблемой. Читатели узнают о перспективах выздоровления и важности комплексного подхода.
Подробнее можно узнать тут – срочный вывод из запоя в Симферополе
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Детальнее – http://narkologicheskaya-klinika-v-kaliningrade15.ru/vyvod-iz-zapoya-kaliningrad-staczionar/
При домашнем формате мы сразу закладываем «мостик» к стационару: в случае ухудшения состояния перевод происходит бесшовно, по заранее оговорённым критериям. Пациент и семья знают, какие маркеры считаются целевыми (переносимость воды, ровный вечерний пульс, время до засыпания, число пробуждений), и когда состоится повторная оценка. Прозрачность снимает суету и укрепляет приверженность плану.
Узнать больше – https://kapelnicza-ot-zapoya-murmansk15.ru/vyjti-iz-zapoya-murmansk
В этой публикации мы исследуем ключевые аспекты здоровья, включая влияние образа жизни на благополучие. Читатели узнают о важности правильного питания, физической активности и психического здоровья. Мы предоставим практические советы и рекомендации для поддержания здоровья и развития профилактических подходов.
Получить дополнительную информацию – вывод из запоя дешево Симферополь
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Узнать больше – http://narkologicheskaya-klinika-v-kaliningrade15.ru
В городском ритме Ставрополя дорога сама по себе может усугублять симптомы: плотный трафик, резкие звуки, длинные коридоры ожидания. Поэтому «СтаврВита» разворачивает секторные выезды: немаркированный транспорт, гражданская одежда специалистов, согласованная парковка и подъезд, доставка расходников отдельно от врача при необходимости — чтобы на месте сразу переходить к диагностике и запуску инфузии. Переписка ведётся нейтральными формулировками, уведомления «беззвучные», документы без стигматизирующих слов. По желанию всё общение идёт через доверенное лицо: оно получает короткие апдейты в согласованные «окна», не перегружаясь клиническими деталями.
Получить дополнительную информацию – вывод из запоя капельница на дому в ставрополе
Ниже — «скелет» визита. На месте врач адаптирует содержание под возраст, соматику, текущие лекарства и проявления абстиненции. Главная идея — быстро получить цифры, аккуратно запустить инфузию и заранее зафиксировать ориентиры, чтобы семья не импровизировала в «трудный час».
Изучить вопрос глубже – вывод из запоя капельница на дому в ставрополе
Универсальной «сильной капельницы» не существует. Мы подбираем состав по ведущим симптомам, переносимости и данным экспресс-диагностики. Задача — вернуть дневную ясность и физиологичный ночной сон без переседации.
Изучить вопрос глубже – вывод из запоя
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Получить больше информации – http://vivod-iz-zapoya-voronezh15.ru/vyvod-iz-zapoya-za-den-voronezh/
heaps of wins casino no deposit bonus heaps of wins casino no deposit bonus .
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить дополнительные сведения – вывод из запоя в калининграде
продвижение обучение https://kursy-seo-12.ru/ .
goliathcasino https://goliath-casino.com/ .
icebet casino slots https://icebet-online.com/ .
J’adore la vibe de Azur Casino, ca donne une vibe electrisante. Les options de jeu sont infinies, avec des slots aux graphismes modernes. Il offre un demarrage en fanfare. Les agents sont toujours la pour aider. Les paiements sont securises et rapides, cependant plus de promotions frequentes boosteraient l’experience. En somme, Azur Casino vaut une exploration vibrante. Notons aussi la navigation est claire et rapide, amplifie le plaisir de jouer. Egalement genial les tournois reguliers pour s’amuser, qui dynamise l’engagement.
Essayer ceci|
Вся динамика заносится в единую карту наблюдения, доступ к которой разграничен по ролям. При переходе к амбулаторной точке или стационару не происходит «перезапуска истории»: новые назначения учитывают всё, что сделано на старте.
Получить дополнительную информацию – https://vivod-iz-zapoya-voronezh15.ru/vyvod-iz-zapoya-staczionar-voronezh/
Чтобы было ясно, как мы комбинируем подходы, ниже — наглядная сводка. Она не заменяет назначения: реальные решения врач принимает после очной оценки и обсуждения целей. Таблица помогает увидеть логику подбора и задать точные вопросы на консультации.
Разобраться лучше – лечение алкоголизма стоимость
Этот документ охватывает важные аспекты медицинской науки, сосредотачиваясь на ключевых вопросах, касающихся здоровья населения. Мы рассматриваем свежие исследования, клинические рекомендации и лучшие практики, которые помогут улучшить качество лечения и профилактики заболеваний. Читатели получат возможность углубиться в различные медицинские дисциплины.
Получить дополнительную информацию – нарколог вывод из запоя в Москве
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить больше информации – vyvod-iz-zapoya-v-kaliningrade15.ru/
В городском ритме Ставрополя дорога сама по себе может усугублять симптомы: плотный трафик, резкие звуки, длинные коридоры ожидания. Поэтому «СтаврВита» разворачивает секторные выезды: немаркированный транспорт, гражданская одежда специалистов, согласованная парковка и подъезд, доставка расходников отдельно от врача при необходимости — чтобы на месте сразу переходить к диагностике и запуску инфузии. Переписка ведётся нейтральными формулировками, уведомления «беззвучные», документы без стигматизирующих слов. По желанию всё общение идёт через доверенное лицо: оно получает короткие апдейты в согласованные «окна», не перегружаясь клиническими деталями.
Подробнее можно узнать тут – анонимный вывод из запоя
Первые два часа после приезда врача — ключевое окно. Мы фиксируем витальные показатели (АД/ЧСС/SpO?), проводим экспресс-оценку глюкозы, по показаниям — электролитов (Na?/K?), оцениваем дыхательный паттерн и уровень ориентировки. Далее запускается титрованная инфузия через инфузомат с контролем каждые 15–20 минут. Параллельно настраиваются «вечерние опоры»: светогигиена, дыхательные циклы, «тихие окна» связи. В конце визита пациент и близкие получают простую памятку с «зелёными зонами» и кратким планом на 72 часа — когда пить воду, как выбирать тёплую пищу малыми порциями, при каких признаках выходить на связь немедленно.
Подробнее можно узнать тут – http://vivod-iz-zapoya-voronezh15.ru
Городская среда Калининграда специфична: морской ветер, сезонные пробки, яркие витрины в вечерние часы. Эти факторы часто усиливают тревожность и мешают засыпанию. Поэтому мы проектируем выезд «мягко»: согласованная парковка, немаркированный вход, короткий маршрут до места процедуры, отсутствие громких звонков и «визуального шума» у порога. Родственникам предоставляем «тихие окна» связи — короткие апдейты в заранее оговорённое время без лишних подробностей. Такой формат не просто комфортнее, он клинически полезен: чем меньше стимулов, тем меньше потребность в ночных «усилениях» и тем стабильнее проходит первая ночь.
Разобраться лучше – https://vyvod-iz-zapoya-kaliningrad15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
Первые недели — время, когда старые привычки ещё инерционны. Мы даём простой план на семь дней, объясняем маркеры стабилизации и поводы для внепланового контакта. При необходимости подключаем короткие встречи с психологом, чтобы закрепить навыки самопомощи и снизить вероятность срыва.
Ознакомиться с деталями – vnutrivennoe-kodirovanie-ot-alkogolizma
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Узнать больше – вывод из запоя круглосуточно в воронеже
Ниже — «скелет» визита. На месте врач адаптирует содержание под возраст, соматику, текущие лекарства и проявления абстиненции. Главная идея — быстро получить цифры, аккуратно запустить инфузию и заранее зафиксировать ориентиры, чтобы семья не импровизировала в «трудный час».
Ознакомиться с деталями – https://vyvod-iz-zapoya-stavropol15.ru/
Если на любом этапе проявляется нестабильность давления/ритма, падает сатурация или ухудшается контакт, врач эскалирует формат немедленно. Важно: в стационаре мы продолжаем тот же курс, не «перепридумывая» его с нуля — благодаря единой карте наблюдения теряется меньше времени и сил.
Ознакомиться с деталями – вывод из запоя с выездом
TurkPaydexHub se demarque comme une plateforme de placement crypto innovante, qui utilise la puissance de l’intelligence artificielle pour proposer a ses membres des atouts competitifs majeurs.
Son IA etudie les marches financiers en temps reel, repere les opportunites et met en ?uvre des strategies complexes avec une precision et une vitesse inaccessibles aux traders humains, augmentant de ce fait les potentiels de rendement.
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Получить дополнительную информацию – наркология вывод из запоя
Je suis fascine par Lucky 31 Casino, ca invite a l’aventure. Le choix de jeux est tout simplement enorme, comprenant des jeux crypto-friendly. Avec des transactions rapides. Les agents sont toujours la pour aider. Les paiements sont surs et efficaces, neanmoins des recompenses supplementaires dynamiseraient le tout. En bref, Lucky 31 Casino offre une experience inoubliable. De surcroit la navigation est simple et intuitive, incite a prolonger le plaisir. Egalement genial les tournois reguliers pour la competition, offre des bonus exclusifs.
DГ©marrer maintenant|
кухни на заказ спб кухни на заказ спб .
Je suis completement seduit par Azur Casino, il procure une sensation de frisson. On trouve une profusion de jeux palpitants, offrant des tables live interactives. Il booste votre aventure des le depart. Le support est efficace et amical. Les retraits sont fluides et rapides, parfois plus de promotions frequentes boosteraient l’experience. Pour conclure, Azur Casino assure un divertissement non-stop. En complement le design est style et moderne, incite a rester plus longtemps. A souligner les competitions regulieres pour plus de fun, qui stimule l’engagement.
DГ©couvrir davantage|
Решение о месте лечения принимает врач после очной оценки, ориентируясь на клинику и бытовые условия. Домашний формат ценят за комфорт и конфиденциальность, а стационар незаменим, когда требуется частая коррекция терапии и круглосуточный мониторинг. Чтобы проще сориентироваться, полезно посмотреть на различия между форматами не как на «два вида капельниц», а как на разные уровни контроля и скорости реакций команды. Текст ниже помогает понять, почему при пограничных состояниях мы рекомендуем стационар, а при стабильных показателях — подтверждаем выезд на дом. Любой маршрут объясняется до старта, и каждое расширение терапии согласуется заранее — без сюрпризов в процессе.
Узнать больше – srochnyj-vyvod-iz-zapoya
icebetcasino icebetcasino .
курс seo http://www.kursy-seo-12.ru .
goliath casino bonuskode https://goliath-casino.com .
Ниже — «скелет» визита. На месте врач адаптирует содержание под возраст, соматику, текущие лекарства и проявления абстиненции. Главная идея — быстро получить цифры, аккуратно запустить инфузию и заранее зафиксировать ориентиры, чтобы семья не импровизировала в «трудный час».
Получить дополнительные сведения – скорая вывод из запоя
Je suis completement seduit par Action Casino, ca offre une experience immersive. Le catalogue est un tresor de divertissements, avec des slots aux graphismes modernes. Le bonus de depart est top. Disponible 24/7 pour toute question. Les retraits sont ultra-rapides, de temps a autre des bonus diversifies seraient un atout. En resume, Action Casino est un incontournable pour les joueurs. Notons egalement la navigation est simple et intuitive, amplifie le plaisir de jouer. Particulierement interessant le programme VIP avec des privileges speciaux, propose des privileges sur mesure.
Voir la page|
Je suis completement seduit par Lucky 31 Casino, ca donne une vibe electrisante. Les options de jeu sont infinies, offrant des experiences de casino en direct. Il booste votre aventure des le depart. Le suivi est toujours au top. Les paiements sont surs et fluides, cependant des recompenses en plus seraient un bonus. En somme, Lucky 31 Casino vaut une exploration vibrante. En plus la navigation est simple et intuitive, permet une plongee totale dans le jeu. Un avantage notable les tournois frequents pour l’adrenaline, propose des privileges personnalises.
Visiter le site|
Je suis epate par 1xBet Casino, c’est un lieu ou l’adrenaline coule a flots. Les titres proposes sont d’une richesse folle, avec des machines a sous aux themes varies. Avec des depots fluides. Le service client est excellent. Les transactions sont toujours securisees, toutefois des recompenses additionnelles seraient ideales. Pour conclure, 1xBet Casino est un must pour les passionnes. En extra le design est style et moderne, donne envie de continuer l’aventure. Particulierement cool les paiements en crypto rapides et surs, renforce le lien communautaire.
1xBet|
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Выяснить больше – наркология вывод из запоя
Алкогольная зависимость — это не «слабость характера», а стойкое биопсихосоциальное расстройство, которое требует последовательной медицинской и психологической помощи. «АльфаМедика» в Видном выстраивает лечение так, чтобы первые шаги давались безопасно и предсказуемо: начинаем с детоксикации и стабилизации сна, затем добавляем методы, которые снижают тягу, учат обходить триггеры и возвращают контроль над повседневностью. Каждый пациент проходит очную оценку: врач уточняет длительность употребления, сопутствующие болезни, переносимость лекарств, режим сна и уровень тревожности. На основе этих данных формируется индивидуальная программа с понятными целями на неделю, месяц и квартал. Мы работаем круглосуточно, принимаем в стационаре и амбулаторно, при необходимости организуем выездную диагностику. Приватность — обязательный стандарт: визиты проходят без огласки, доступ к данным ограничен специалистами, вовлечёнными в помощь. Наша задача — не только «вывести из запоя», но и создать устойчивую базу, на которой держится ремиссия: нормальный сон, рабочий ритм, поддержка семьи и ясный план на ближайшие месяцы.
Выяснить больше – lechenie alkogolizma na domu
Мы избегаем шаблонов. Состав инфузий и порядок действий подбираются индивидуально: учитываем тяжесть интоксикации, сопутствующие заболевания, чувствительность к свету и шуму, объём воды, который человек переносит малыми глотками, а также, как реагирует на вечерние уведомления телефона. Главная цель первых часов — стабилизировать витальные показатели, вернуть переносимость питья и лёгкой тёплой пищи, выровнять вариабельность пульса к сумеркам и обеспечить физиологичный сон без «переседации». Все измерения фиксируются в краткой карте наблюдения с разграничением доступа по ролям — это защищает данные и ускоряет принятие решений.
Ознакомиться с деталями – вывод из запоя на дому недорого
Je suis epate par Lucky 31 Casino, ca invite a l’aventure. La selection de jeux est impressionnante, offrant des experiences de casino en direct. Il rend le debut de l’aventure palpitant. Les agents sont toujours la pour aider. Les paiements sont securises et instantanes, parfois quelques free spins en plus seraient bienvenus. Dans l’ensemble, Lucky 31 Casino merite un detour palpitant. De surcroit la navigation est simple et intuitive, ajoute une touche de dynamisme. Particulierement interessant les options de paris sportifs variees, renforce le lien communautaire.
Continuer Г lire|
Универсальной «сильной капельницы» не существует. Мы подбираем состав по ведущим симптомам, переносимости и данным экспресс-диагностики. Задача — вернуть дневную ясность и физиологичный ночной сон без переседации.
Разобраться лучше – вывод из запоя цена воронеж
J’ai une passion debordante pour Action Casino, on y trouve une energie contagieuse. Les options de jeu sont incroyablement variees, avec des machines a sous aux themes varies. Avec des depots instantanes. Disponible 24/7 pour toute question. Les gains arrivent en un eclair, rarement plus de promos regulieres dynamiseraient le jeu. Pour conclure, Action Casino offre une experience inoubliable. A souligner la navigation est fluide et facile, amplifie l’adrenaline du jeu. Un point fort les tournois reguliers pour la competition, offre des bonus constants.
Lire la suite|
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Выяснить больше – http://vyvod-iz-zapoya-kaliningrad15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
Ниже — «скелет» визита. На месте врач адаптирует содержание под возраст, соматику, текущие лекарства и проявления абстиненции. Главная идея — быстро получить цифры, аккуратно запустить инфузию и заранее зафиксировать ориентиры, чтобы семья не импровизировала в «трудный час».
Подробнее можно узнать тут – https://vyvod-iz-zapoya-stavropol15.ru/stavropol-lechenie-alkogolizma/
Если при телефонном триаже выявляются «красные флаги» (дыхание, ритм, сознание), маршрут настраивается сразу под стационар: те же цели, тот же ответственный куратор, только непрерывный мониторинг витальных и ночной пост. А когда риски невысоки, мы начинаем дома или амбулаторно и удерживаем темп контрольными включениями — это чаще всего даёт спокойную первую ночь и легче переносимый второй день.
Ознакомиться с деталями – https://vyvod-iz-zapoya-stavropol15.ru/stavropol-lechenie-alkogolizma/
Je suis sous le charme de Action Casino, il propose une aventure palpitante. Les options sont aussi vastes qu’un horizon, proposant des jeux de table sophistiques. Il propulse votre jeu des le debut. Le suivi est d’une precision remarquable. Les gains arrivent sans delai, toutefois quelques spins gratuits en plus seraient top. Pour faire court, Action Casino est un lieu de fun absolu. En extra le site est rapide et engageant, ce qui rend chaque partie plus fun. Un element fort les evenements communautaires engageants, offre des bonus constants.
Visiter en ligne|
В этой статье рассматриваются различные аспекты избавления от зависимости, включая физические и психологические методы. Мы обсудим поддержку, мотивацию и стратегии, которые помогут в процессе выздоровления. Читатели узнают, как преодолеть трудности и двигаться к новой жизни без зависимости.
Углубиться в тему – вывод из запоя на дому в Москве
Метод
Подробнее можно узнать тут – центр кодирования от алкоголизма
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Разобраться лучше – http://vyvod-iz-zapoya-v-kaliningrade15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
Когда тело перестаёт «гореть», в работу включается фармакологическая поддержка тяги и настроения, а также простые поведенческие техники. Мы помогаем организовать трезвые вечера, составить список альтернатив «наград» и заново привязать удовольствие к безопасным ритуалам — прогулке, спорту, тёплой еде, общению. Если тревога остаётся высокой, врач мягко корректирует схему, а психолог учит распознавать и «разгружать» триггеры раньше, чем они наберут силу. Такой блок — не про «волю», а про доступные инструменты, которые работают даже в уставшем состоянии после рабочего дня.
Подробнее – http://lechenie-alkogolizma-vidnoe4.ru
Перед кодированием мы разбираем риски и противопоказания, отвечаем на вопросы о длительности действия и совместимости с текущими лекарствами. Важно понимать, как метод впишется в рабочий график и семейные обязанности, где могут возникнуть триггеры и кто будет рядом в сложные моменты. Такой разговор помогает избежать импульсивных решений и выбрать вариант, который действительно поддержит трезвость.
Узнать больше – kodirovanie-ot-alkogolizma-vyezd-na-dom
Алкогольная зависимость держится на двух опорах — нейробиологической и поведенческой. Первая проявляется в нарушении систем вознаграждения и сна, в скачках настроения и тревожности, из-за чего «тяга» переживается как единственный быстрый способ облегчения. Вторая — в привычках и сценариях, когда стресс, одиночество или праздники автоматически связываются с употреблением. Кодирование в клинике адресует обе опоры одновременно: фармакологические методы снижают ожидаемую «награду» от алкоголя или формируют защитный барьер, а психотерапевтические — учат распознавать триггеры, переключать внимание и выдерживать эмоции без выпивки. Такой комбинированный подход особенно эффективен в первые месяцы трезвости, когда физиология уже не поддерживает употребление, а поведенческие маршруты ещё инерционны. Мы честно проговариваем возможности и ограничения: кодирование не «лечит одним уколом», но создаёт окно стабильности, в котором человек успевает перестроить быт, сон, питание и систему поддержки.
Детальнее – kodirovanie-ot-alkogolizma-shchelkovo3.ru/
Мы избегаем шаблонов. Состав инфузий и порядок действий подбираются индивидуально: учитываем тяжесть интоксикации, сопутствующие заболевания, чувствительность к свету и шуму, объём воды, который человек переносит малыми глотками, а также, как реагирует на вечерние уведомления телефона. Главная цель первых часов — стабилизировать витальные показатели, вернуть переносимость питья и лёгкой тёплой пищи, выровнять вариабельность пульса к сумеркам и обеспечить физиологичный сон без «переседации». Все измерения фиксируются в краткой карте наблюдения с разграничением доступа по ролям — это защищает данные и ускоряет принятие решений.
Детальнее – вывод из запоя с выездом в калининграде
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Ознакомиться с деталями – http://vyvod-iz-zapoya-kaliningrad15.ru
Перед кодированием мы разбираем риски и противопоказания, отвечаем на вопросы о длительности действия и совместимости с текущими лекарствами. Важно понимать, как метод впишется в рабочий график и семейные обязанности, где могут возникнуть триггеры и кто будет рядом в сложные моменты. Такой разговор помогает избежать импульсивных решений и выбрать вариант, который действительно поддержит трезвость.
Подробнее можно узнать тут – kodirovanie-ot-alkogolizma
Метод
Углубиться в тему – http://kodirovanie-ot-alkogolizma-shchelkovo3.ru
icebet casino promo code https://www.icebet-online.com .
Je suis totalement conquis par Azur Casino, il propose une aventure palpitante. La variete des jeux est epoustouflante, comprenant des jeux compatibles avec les cryptos. Le bonus initial est super. Les agents sont toujours la pour aider. Les paiements sont surs et efficaces, neanmoins des offres plus importantes seraient super. Dans l’ensemble, Azur Casino est un incontournable pour les joueurs. En complement le design est moderne et attrayant, facilite une experience immersive. Egalement super le programme VIP avec des avantages uniques, qui stimule l’engagement.
DГ©couvrir les faits|
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Подробнее тут – вывод из запоя калининград
Когда тело перестаёт «гореть», в работу включается фармакологическая поддержка тяги и настроения, а также простые поведенческие техники. Мы помогаем организовать трезвые вечера, составить список альтернатив «наград» и заново привязать удовольствие к безопасным ритуалам — прогулке, спорту, тёплой еде, общению. Если тревога остаётся высокой, врач мягко корректирует схему, а психолог учит распознавать и «разгружать» триггеры раньше, чем они наберут силу. Такой блок — не про «волю», а про доступные инструменты, которые работают даже в уставшем состоянии после рабочего дня.
Получить дополнительные сведения – http://lechenie-alkogolizma-vidnoe4.ru
Лечение зависимости требует точности и уважения к человеку. В «АльфаМедика» мы соединяем клинические протоколы с бережной коммуникацией: объясняем смысл каждого шага, согласуем темп и не обещаем «волшебных» решений. Важен не набор модных процедур, а управляемость процесса. Детокс не делается «по шаблону» — объём инфузии, поддержка печени, коррекция электролитов и симптом-контроль настраиваются по реакции организма. Когда физическое состояние стабилизировано, команда помогает вернуть структуру дня: сон, питание, безопасные «наградные» ритуалы вместо алкоголя, короткие техники управления стрессом. Мы регулярно пересматриваем план, потому что зависимость динамична: если меняется работа, появляются очередные вызовы в семье или усиливается тревога, программа гибко адаптируется. Такой подход особенно ценят люди, у которых раньше «не получалось» — не из-за слабости, а потому что прежние схемы игнорировали повседневную реальность и заканчивались срывом в первый же стрессовый вечер. Здесь каждый этап прозрачен и опирается на измеримые критерии: качество сна, уровень тяги, стабильность настроения, способность планировать трезвые вечера и выходные.
Углубиться в тему – лечение алкоголизма на дому стоимость
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Подробнее тут – https://vyvod-iz-zapoya-petrozavodsk15.ru/vyvod-iz-zapoya-na-domu-petrozavodsk/
Этот информационный материал подробно освещает проблему наркозависимости, ее причины и последствия. Мы предлагаем информацию о методах лечения, профилактики и поддерживающих программах. Цель статьи — повысить осведомленность и продвигать идеи о необходимости борьбы с зависимостями.
Получить больше информации – вывод из запоя вызов на дом Москва
Чтобы было ясно, как мы комбинируем подходы, ниже — наглядная сводка. Она не заменяет назначения: реальные решения врач принимает после очной оценки и обсуждения целей. Таблица помогает увидеть логику подбора и задать точные вопросы на консультации.
Подробнее можно узнать тут – lechenie-alkogolizma-vidnoe4.ru/
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Исследовать вопрос подробнее – вывод из запоя на дому воронеж
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Выяснить больше – http://narkologicheskaya-klinika-v-kaliningrade15.ru
На этом отрезке мы снимаем острые симптомы абстиненции: тремор, тошноту, паническую волну, нарушения сна. Инфузия собирается индивидуально, с расчётом объёма по массе тела и состоянию почек и сердца. Добавляем электролиты, гепатопротективные компоненты, при необходимости — короткую седацию, которая восстанавливает архитектуру сна без «тяжёлого» утреннего эффекта. Во время процедуры врач отслеживает давление, пульс, сатурацию, дыхание, корректирует скорость введения и объясняет, что и зачем делается. На выходе пациент получает понятные рекомендации на 24–48 часов: питьевой режим, питание, правила активности, «красные флаги» для внеплановой связи. В большинстве случаев облегчение наступает уже в день старта, а первая спокойная ночь становится поворотной точкой для мотивации.
Исследовать вопрос подробнее – narkologicheskoe lechenie alkogolizma
При абстиненции нервная и сердечно-сосудистая системы работают на пределе, баланс нейромедиаторов смещён, кровь «теряет» воду и электролиты, а печень несёт повышенную нагрузку. Резкая отмена алкоголя без врача нередко приводит к скачкам давления, аритмиям, паническим эпизодам, нарушению сна и даже делирию. Домашние «самосборные» растворы и случайные комбинации таблеток усугубляют обезвоживание и не учитывают противопоказания — в итоге риски растут, а эффект непредсказуем. В «СфераЗдоровья» путь другой: сначала скрининг безопасности и исключение состояний, при которых показан стационар; далее — персональная инфузионная схема с регидратацией, коррекцией электролитов, поддержкой печени и симптом-контролем (тошнота, тремор, тревога, бессонница). На каждом этапе врач отслеживает динамику и корректирует дозы «по реакции», чтобы не перегрузить сердце и почки. Результат — более мягкий выход из абстиненции, прозрачные ожидания для пациента и близких и понятный план на ближайшие 24–48 часов.
Узнать больше – vyvod-iz-zapoya-klinika
Алкогольная зависимость — это не «слабость характера», а стойкое биопсихосоциальное расстройство, которое требует последовательной медицинской и психологической помощи. «АльфаМедика» в Видном выстраивает лечение так, чтобы первые шаги давались безопасно и предсказуемо: начинаем с детоксикации и стабилизации сна, затем добавляем методы, которые снижают тягу, учат обходить триггеры и возвращают контроль над повседневностью. Каждый пациент проходит очную оценку: врач уточняет длительность употребления, сопутствующие болезни, переносимость лекарств, режим сна и уровень тревожности. На основе этих данных формируется индивидуальная программа с понятными целями на неделю, месяц и квартал. Мы работаем круглосуточно, принимаем в стационаре и амбулаторно, при необходимости организуем выездную диагностику. Приватность — обязательный стандарт: визиты проходят без огласки, доступ к данным ограничен специалистами, вовлечёнными в помощь. Наша задача — не только «вывести из запоя», но и создать устойчивую базу, на которой держится ремиссия: нормальный сон, рабочий ритм, поддержка семьи и ясный план на ближайшие месяцы.
Исследовать вопрос подробнее – lechenie alkogolizma anonimno
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Углубиться в тему – http://vivod-iz-zapoya-voronezh15.ru
Городская среда Калининграда специфична: морской ветер, сезонные пробки, яркие витрины в вечерние часы. Эти факторы часто усиливают тревожность и мешают засыпанию. Поэтому мы проектируем выезд «мягко»: согласованная парковка, немаркированный вход, короткий маршрут до места процедуры, отсутствие громких звонков и «визуального шума» у порога. Родственникам предоставляем «тихие окна» связи — короткие апдейты в заранее оговорённое время без лишних подробностей. Такой формат не просто комфортнее, он клинически полезен: чем меньше стимулов, тем меньше потребность в ночных «усилениях» и тем стабильнее проходит первая ночь.
Получить дополнительную информацию – вывод из запоя в стационаре в калининграде
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Разобраться лучше – вывод из запоя на дому круглосуточно в воронеже
seo бесплатно seo бесплатно .
Такая карта делает лечение обозримым и дисциплинирует решения: пациент видит цель и порог перехода, семья понимает, зачем нужно соблюдать «тихие» часы, команда сохраняет управляемость и не «крутит ручки» ночью.
Подробнее тут – лечение в наркологической клинике петрозаводск
Когда тело перестаёт «гореть», в работу включается фармакологическая поддержка тяги и настроения, а также простые поведенческие техники. Мы помогаем организовать трезвые вечера, составить список альтернатив «наград» и заново привязать удовольствие к безопасным ритуалам — прогулке, спорту, тёплой еде, общению. Если тревога остаётся высокой, врач мягко корректирует схему, а психолог учит распознавать и «разгружать» триггеры раньше, чем они наберут силу. Такой блок — не про «волю», а про доступные инструменты, которые работают даже в уставшем состоянии после рабочего дня.
Ознакомиться с деталями – наркологическое лечение алкоголизма
Вывод из запоя — это управляемая медицинская процедура с предсказуемыми шагами, а не «сильная капельница, которая помогает всем». В наркологической клинике «СеверКар Медикус» мы строим лечение как маршрут: цель > инструмент > маркеры контроля > окно повторной оценки. Такой подход снижает лекарственную нагрузку, ускоряет восстановление сна и аппетита и делает процесс понятным пациенту и семье. Мы работаем круглосуточно, организуем выезд нарколога на дом, разворачиваем тихую, безопасную среду и соблюдаем анонимность: нейтральные формулировки, гражданская одежда специалистов, немаркированный транспорт и «беззвучные» уведомления.
Узнать больше – http://vyvod-iz-zapoya-petrozavodsk15.ru/
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Детальнее – https://vyvod-iz-zapoya-kaliningrad15.ru/
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Разобраться лучше – вывод из запоя на дому
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Выяснить больше – помощь вывод из запоя калининград
Решение о месте лечения принимает врач после очной оценки, ориентируясь на клинику и бытовые условия. Домашний формат ценят за комфорт и конфиденциальность, а стационар незаменим, когда требуется частая коррекция терапии и круглосуточный мониторинг. Чтобы проще сориентироваться, полезно посмотреть на различия между форматами не как на «два вида капельниц», а как на разные уровни контроля и скорости реакций команды. Текст ниже помогает понять, почему при пограничных состояниях мы рекомендуем стационар, а при стабильных показателях — подтверждаем выезд на дом. Любой маршрут объясняется до старта, и каждое расширение терапии согласуется заранее — без сюрпризов в процессе.
Ознакомиться с деталями – вывод из запоя цена
Вывод из запоя — это управляемая медицинская процедура с предсказуемыми шагами, а не «сильная капельница, которая помогает всем». В наркологической клинике «СеверКар Медикус» мы строим лечение как маршрут: цель > инструмент > маркеры контроля > окно повторной оценки. Такой подход снижает лекарственную нагрузку, ускоряет восстановление сна и аппетита и делает процесс понятным пациенту и семье. Мы работаем круглосуточно, организуем выезд нарколога на дом, разворачиваем тихую, безопасную среду и соблюдаем анонимность: нейтральные формулировки, гражданская одежда специалистов, немаркированный транспорт и «беззвучные» уведомления.
Изучить вопрос глубже – https://vyvod-iz-zapoya-petrozavodsk15.ru
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Получить дополнительную информацию – анонимная наркологическая клиника
TurkPaydexHub Avis
TurkPaydexHub se differencie comme une plateforme d’investissement en crypto-monnaies de pointe, qui met a profit la puissance de l’intelligence artificielle pour fournir a ses clients des avantages decisifs sur le marche.
Son IA etudie les marches financiers en temps reel, identifie les opportunites et met en ?uvre des strategies complexes avec une precision et une vitesse inaccessibles aux traders humains, augmentant de ce fait les perspectives de gain.
Алкогольная зависимость — это не «слабость характера», а стойкое биопсихосоциальное расстройство, которое требует последовательной медицинской и психологической помощи. «АльфаМедика» в Видном выстраивает лечение так, чтобы первые шаги давались безопасно и предсказуемо: начинаем с детоксикации и стабилизации сна, затем добавляем методы, которые снижают тягу, учат обходить триггеры и возвращают контроль над повседневностью. Каждый пациент проходит очную оценку: врач уточняет длительность употребления, сопутствующие болезни, переносимость лекарств, режим сна и уровень тревожности. На основе этих данных формируется индивидуальная программа с понятными целями на неделю, месяц и квартал. Мы работаем круглосуточно, принимаем в стационаре и амбулаторно, при необходимости организуем выездную диагностику. Приватность — обязательный стандарт: визиты проходят без огласки, доступ к данным ограничен специалистами, вовлечёнными в помощь. Наша задача — не только «вывести из запоя», но и создать устойчивую базу, на которой держится ремиссия: нормальный сон, рабочий ритм, поддержка семьи и ясный план на ближайшие месяцы.
Разобраться лучше – https://lechenie-alkogolizma-vidnoe4.ru/lechenie-alkogolizma-besplatno/
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Получить дополнительные сведения – анонимный вывод из запоя калининград
Мурманск — город с длинными сумерками и влажным ветром от Кольского залива, что сказывается на сну и вечерней кардиолабильности. Поэтому мы адаптируем маршруты: выездные бригады работают в гражданской одежде, заходят быстро и тихо, а в палатах клиники используется тёплая подсветка и акустическое поглощение. Для ночных поступлений действует протокол «мягкой посадки»: минимизированные контакты, тёплая вода малыми глотками, затем — диагностика и старт инфузии при отсутствии «красных флагов». Это снижает сенсорную нагрузку и позволяет организму дать честный клинический ответ без лишних раздражителей.
Разобраться лучше – капельница от запоя в мурманске
Топ-5 бюро переводов в москве teletype.in/@alexd78/iF-xjHhC3iA .
it перевод заказать telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Подробнее тут – вывод из запоя круглосуточно воронеж
Первые часы определяют траекторию. Мы работаем по карте — у каждого окна есть цель, действия, маркеры контроля и критерий перехода. Если ответ «плоский», меняем один элемент и назначаем повторную оценку. Это дисциплинирует решения и защищает от полипрагмазии.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-petrozavodsk15.ru/vyvod-iz-zapoya-kruglosutochno-petrozavodsk
Чтобы было ясно, как мы комбинируем подходы, ниже — наглядная сводка. Она не заменяет назначения: реальные решения врач принимает после очной оценки и обсуждения целей. Таблица помогает увидеть логику подбора и задать точные вопросы на консультации.
Узнать больше – lechenie alkogolizma cena
Мы собираем терапию из проверенных модулей: гидратация, коррекция электролитов, гастропротекция, антиоксидантная поддержка, мягкая анксиолитика по показаниям, поведенческие интервенции (свет, тишина, дыхание 4–6, стимул-контроль, вечерние ритуалы). Объём и темп зависят от ведущего симптома и времени суток: при кардиореактивном вечере больше внимания уделяется среде, при тошноте — гастропротекции и «тёплому питанию», при поверхностном сне — цифровой гигиене и световым сценариям. Ниже приведена ориентировочная матрица выбора; финальное решение — за лечащим врачом с учётом противопоказаний и лекарственных взаимодействий.
Получить дополнительную информацию – http://narkologicheskaya-klinika-v-petrozavodske15.ru/chastnaya-narkologicheskaya-klinika-petrozavodsk/
Чтобы было ясно, как мы комбинируем подходы, ниже — наглядная сводка. Она не заменяет назначения: реальные решения врач принимает после очной оценки и обсуждения целей. Таблица помогает увидеть логику подбора и задать точные вопросы на консультации.
Детальнее – http://lechenie-alkogolizma-vidnoe4.ru/lechenie-alkogolizma-besplatno/
Если в первичном звонке звучат «красные флаги» (одышка, спутанность сознания, резкие скачки ритма), мы предлагаем стационарное «окно» мониторинга с ночным постом. При низких рисках стартуем на дому: контрольные точки совпадают с домашним комфортом, а вечерние online-вставки по 15–20 минут поддерживают предсказуемость без лишних поездок.
Подробнее можно узнать тут – наркология вывод из запоя в воронеже
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Углубиться в тему – вывод из запоя капельница калининград
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить больше информации – лечение в наркологической клинике
Чтобы пациент и близкие не гадали «что будет дальше», мы удерживаем прозрачную последовательность. Каждый этап имеет цель, инструмент, окно оценки и критерий перехода. Это экономит минуты, снимает споры и делает план управляемым.
Получить дополнительную информацию – наркология вывод из запоя
Финальный этап — выработка устойчивых привычек и отношений с окружением. Вместе с пациентом мы формируем план трезвых выходных, обсуждаем правила отказа, которые не провоцируют конфликты, и настраиваем микропаузы в течение дня, чтобы стресс не копился «к вечеру». Контрольные встречи короткие и прагматичные: оцениваем сон, уровень энергии, тягу, коммуникацию с близкими. Если предстоит сложный период — отпуск, переезд, цейтнот — заранее усиливаем опоры, чтобы пройти его без срывов.
Подробнее – lechenie alkogolizma anonimno
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Изучить вопрос глубже – наркологическая клиника клиника помощь калининград
В этой статье мы рассматриваем разные способы борьбы с алкогольной зависимостью. Обсуждаются методы лечения, программы реабилитации и советы для поддержки близких. Читатели получат информацию о том, как преодолеть зависимость и добиться успешного выздоровления.
Разобраться лучше – нарколог вывод из запоя в Москве
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Разобраться лучше – вывод из запоя с выездом в калининграде
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Узнать больше – вывод из запоя дешево в калининграде
Чтобы было ясно, как мы комбинируем подходы, ниже — наглядная сводка. Она не заменяет назначения: реальные решения врач принимает после очной оценки и обсуждения целей. Таблица помогает увидеть логику подбора и задать точные вопросы на консультации.
Выяснить больше – https://lechenie-alkogolizma-vidnoe4.ru/czentr-lecheniya-alkogolizma-v-vidnom/
На этом отрезке мы снимаем острые симптомы абстиненции: тремор, тошноту, паническую волну, нарушения сна. Инфузия собирается индивидуально, с расчётом объёма по массе тела и состоянию почек и сердца. Добавляем электролиты, гепатопротективные компоненты, при необходимости — короткую седацию, которая восстанавливает архитектуру сна без «тяжёлого» утреннего эффекта. Во время процедуры врач отслеживает давление, пульс, сатурацию, дыхание, корректирует скорость введения и объясняет, что и зачем делается. На выходе пациент получает понятные рекомендации на 24–48 часов: питьевой режим, питание, правила активности, «красные флаги» для внеплановой связи. В большинстве случаев облегчение наступает уже в день старта, а первая спокойная ночь становится поворотной точкой для мотивации.
Подробнее можно узнать тут – lechenie alkogolizma cena
Наркологическая клиника «КарелМед Центр» — это круглосуточное лечение, современное оборудование и предсказуемые протоколы, которые избавляют пациента и семью от догадок. Мы не используем «универсальные сильные капельницы» и не усиливаем схему «на всякий случай»: каждое вмешательство имеет понятную цель, измеримые маркеры и заранее оговорённое окно повторной оценки. Такой подход снижает фармаконагрузку, бережёт сон, сокращает вечернюю реактивность и делает первую ночь спокойнее. Анонимность встроена в процессы: немаркированные входы, гражданская одежда персонала, нейтральные формулировки в документах и «беззвучные» уведомления по согласованным каналам связи.
Изучить вопрос глубже – наркологические клиники алкоголизм петрозаводск
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Подробнее можно узнать тут – анонимный вывод из запоя калининград
Параметр
Выяснить больше – http://vyvod-iz-zapoya-domodedovo3.ru/vyvedenie-iz-zapoya-na-domu-domodedovo/
В этой статье рассматриваются способы преодоления зависимости и успешные истории людей, которые справились с этой проблемой. Мы обсудим важность поддержки со стороны близких и профессионалов, а также стратегии, которые могут помочь в процессе выздоровления. Научитесь первоочередным шагам к новой жизни.
Узнать больше – наркология вывод из запоя
Ниже — практическая карта первых часов. Она помогает всем участникам понимать логику действий, точки контроля и критерии перехода. Если ответ «плоский», меняем один параметр и возвращаемся к оценке в назначённое время — без хаотичных «усилений».
Исследовать вопрос подробнее – сколько стоит капельница от запоя в мурманске
бюро переводов teletype.in/@alexd78/iF-xjHhC3iA .
it переводчик услуги telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
Наркологическая клиника «РеМед Карелия» — это круглосуточная медицинская помощь, построенная на принципе клинической точности: каждая процедура имеет цель, проверяемые маркеры и назначенное окно переоценки. Мы используем современные методы детоксикации и постабстинентной стабилизации, не перегружая терапию «на всякий случай» и не полагаясь на универсальные «сильные капельницы». Вместо этого — модульные схемы, корректировка одного параметра за раз и обязательная оценка результата. Такой подход снижает фармаконагрузку, ускоряет восстановление сна и аппетита и делает лечение предсказуемым для пациента и его семьи. Анонимность встроена в процессы: немаркированные входы, гражданская форма персонала, нейтральные формулировки в документах, «тихие» уведомления и разграниченный доступ к карте наблюдения.
Узнать больше – платная наркологическая клиника петрозаводск
Наркологическая клиника «РеМед Карелия» — это круглосуточная медицинская помощь, построенная на принципе клинической точности: каждая процедура имеет цель, проверяемые маркеры и назначенное окно переоценки. Мы используем современные методы детоксикации и постабстинентной стабилизации, не перегружая терапию «на всякий случай» и не полагаясь на универсальные «сильные капельницы». Вместо этого — модульные схемы, корректировка одного параметра за раз и обязательная оценка результата. Такой подход снижает фармаконагрузку, ускоряет восстановление сна и аппетита и делает лечение предсказуемым для пациента и его семьи. Анонимность встроена в процессы: немаркированные входы, гражданская форма персонала, нейтральные формулировки в документах, «тихие» уведомления и разграниченный доступ к карте наблюдения.
Получить дополнительные сведения – https://narkologicheskaya-klinika-v-petrozavodske15.ru/petrozavodsk-narkologiya
Экстренный вывод из запоя — это управляемая медицинская процедура, а не «сильная капельница на удачу». В наркологической клинике «ВоронежВита» мы действуем по чётким правилам: от телефонного триажа и тихого выезда бригады до адресной детоксикации и вечерних контрольных включений. Главная цель — безопасно стабилизировать состояние, снизить тремор и тошноту, выровнять сердечный ритм и вернуть физиологичный сон уже в первые ночи. Мы выбираем минимально достаточные вмешательства, чтобы днём сохранялась ясность и не возникало желания «самостоятельно усилить» схему. Конфиденциальность встроена в каждый шаг: гражданская одежда специалистов, немаркированный транспорт, нейтральные формулировки в переписке и документах.
Узнать больше – нарколог на дом вывод из запоя воронеж
Je suis enthousiaste a propos de Casinozer Casino, ca donne une vibe electrisante. Il y a une abondance de jeux excitants, offrant des experiences de casino en direct. Il booste votre aventure des le depart. Le suivi est d’une precision remarquable. Les paiements sont surs et fluides, neanmoins des bonus plus frequents seraient un hit. En resume, Casinozer Casino offre une aventure inoubliable. En complement la navigation est claire et rapide, facilite une experience immersive. Un plus les evenements communautaires engageants, qui dynamise l’engagement.
DГ©couvrir|
Je suis accro a Mystake Casino, il propose une aventure palpitante. Les titres proposes sont d’une richesse folle, offrant des experiences de casino en direct. 100% jusqu’a 500 € plus des tours gratuits. Le service est disponible 24/7. Les gains sont transferes rapidement, parfois plus de promos regulieres dynamiseraient le jeu. En resume, Mystake Casino est un lieu de fun absolu. De surcroit le site est fluide et attractif, booste le fun du jeu. Egalement super les evenements communautaires dynamiques, offre des recompenses regulieres.
Continuer ici|
J’adore le dynamisme de Mystake Casino, ca pulse comme une soiree animee. On trouve une profusion de jeux palpitants, offrant des tables live interactives. Avec des depots fluides. Les agents repondent avec rapidite. Les transactions sont toujours fiables, par contre quelques free spins en plus seraient bienvenus. En conclusion, Mystake Casino est un incontournable pour les joueurs. En complement le site est rapide et immersif, ajoute une touche de dynamisme. Un bonus les competitions regulieres pour plus de fun, garantit des paiements rapides.
Aller sur le site|
Je suis emerveille par Pokerstars Casino, ca invite a plonger dans le fun. La variete des jeux est epoustouflante, proposant des jeux de casino traditionnels. Le bonus initial est super. Disponible 24/7 pour toute question. Les paiements sont surs et efficaces, par ailleurs plus de promos regulieres dynamiseraient le jeu. En bref, Pokerstars Casino offre une experience hors du commun. D’ailleurs le site est rapide et immersif, booste l’excitation du jeu. Un element fort les evenements communautaires vibrants, propose des privileges sur mesure.
DГ©couvrir davantage|
Je suis totalement conquis par Stake Casino, ca pulse comme une soiree animee. Les jeux proposes sont d’une diversite folle, incluant des paris sportifs pleins de vie. Il amplifie le plaisir des l’entree. Le service est disponible 24/7. Les gains sont verses sans attendre, par moments plus de promos regulieres dynamiseraient le jeu. En somme, Stake Casino est un choix parfait pour les joueurs. En complement le site est fluide et attractif, donne envie de prolonger l’aventure. Egalement top le programme VIP avec des niveaux exclusifs, qui dynamise l’engagement.
Rejoindre maintenant|
Мы избегаем шаблонов. Состав инфузий и порядок действий подбираются индивидуально: учитываем тяжесть интоксикации, сопутствующие заболевания, чувствительность к свету и шуму, объём воды, который человек переносит малыми глотками, а также, как реагирует на вечерние уведомления телефона. Главная цель первых часов — стабилизировать витальные показатели, вернуть переносимость питья и лёгкой тёплой пищи, выровнять вариабельность пульса к сумеркам и обеспечить физиологичный сон без «переседации». Все измерения фиксируются в краткой карте наблюдения с разграничением доступа по ролям — это защищает данные и ускоряет принятие решений.
Ознакомиться с деталями – http://vyvod-iz-zapoya-v-kaliningrade15.ru/vyvod-iz-zapoya-kaliningrad-staczionar/https://vyvod-iz-zapoya-v-kaliningrade15.ru
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Получить больше информации – вывод из запоя на дому недорого петрозаводск
В стационаре
Узнать больше – вывод из запоя
Кодирование — это не разовая манипуляция, а управляемая медицинская программа, которая помогает удерживать трезвость, когда организм и психика ещё нестабильны после отмены алкоголя. В «РеаМед Центр» в Щёлково мы соединяем медицинскую экспертизу и ясные правила сопровождения, чтобы снизить тягу, нормализовать сон и уменьшить стресс, из-за которого чаще всего происходят срывы. Работа начинается с очной оценки состояния, разбора анамнеза и текущих рисков, затем подбирается метод, который подходит именно вам по противопоказаниям и целям. Важно, что кодирование всегда идёт на фоне комплексной поддержки: врач объясняет, как действуют препараты или психотехники, какие ощущения нормальны в первые недели, как реагировать на триггеры и к кому обратиться при тревоге. Анонимность и тактичная коммуникация остаются неизменными, поэтому обращаться за помощью можно без опасений за приватность.
Углубиться в тему – http://kodirovanie-ot-alkogolizma-shchelkovo3.ru/kodirovka-ot-alkogolya-ryadom-shhyolkovo/
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Разобраться лучше – запой наркологическая клиника
Городская среда Петрозаводска со сменой ветров с Онежского озера, короткими сумерками и сезонными перепадами влажности может усиливать тревожность в вечерние часы. Мы учитываем это с момента первого контакта: согласованная парковка, отдельный вход без вывесок, короткая регистрация без «толстых анкет», приглушённый тёплый свет в зоне ожидания и отсутствие громких объявлений. Родственникам предоставляются «тихие окна» связи — лаконичные апдейты в фиксированное время, чтобы не перегружать пациента и не дёргать команду в критические окна наблюдения. Такой «мягкий» контур снижает сенсорную нагрузку, стабилизирует вариабельность ЧСС к сумеркам и сокращает число импульсивных просьб «усилить на ночь».
Разобраться лучше – narkologicheskaya-klinika-petrozavodsk15.ru/
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Открой скрытое – https://ecoterraviajes.com/index.php/2022/03/18/ciudad-de-panama-canal-de-panama
Техника помогает, но не доминирует. Мы используем портативные приборы с мягкой индикацией и низким уровнем шума, чтобы не разрушать формирующуюся «ночную кривую». Контроль в остром окне чаще, вечером — мягче: так сохраняется физиология сна и снижается потребность в дополнительной фармакологии.
Ознакомиться с деталями – наркологическая клиника цены петрозаводск
Вся динамика заносится в единую карту наблюдения, доступ к которой разграничен по ролям. При переходе к амбулаторной точке или стационару не происходит «перезапуска истории»: новые назначения учитывают всё, что сделано на старте.
Разобраться лучше – врач вывод из запоя
IT перевод в бюро переводов Перевод и Право telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
бюро переводов с нотариальным заверением teletype.in/@alexd78/iF-xjHhC3iA .
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Рассмотреть проблему всесторонне – https://www.dissomarket.com/decouvrez-lart-des-amuse-bouches-un-voyage-culinaire-en-quelques-bouchees
Планируя переезд квартир, выберите надежную компанию для быстрой и безболезненной транспортировки всех ваших вещей.
Каждый переезд — это возможность создать уют в новом доме.
Задержка усиливает риск судорог, делирия, аритмий и травм. Эти маркеры не требуют медицинского образования — их легко распознать. Если совпадает хотя бы один пункт ниже, свяжитесь с нами 24/7: мы подскажем безопасный формат старта и подготовим пространство к визиту.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-ryazan14.ru/chastnaya-narkologicheskaya-klinika-ryazan
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Ознакомиться с деталями – врач вывод из запоя рязань
Сочетание медицинских и психотерапевтических мер создаёт устойчивую систему поддержки. Пациенты получают возможность постепенно восстановить утраченное здоровье и психологическую стабильность.
Подробнее – наркологические клиники алкоголизм
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Выяснить больше – вывод из запоя ростов-на-дону
Курс терапии в клинике состоит из нескольких последовательных этапов, каждый из которых направлен на достижение конкретных целей — от снятия интоксикации до восстановления психологического равновесия. Такой подход позволяет добиться устойчивого результата и минимизировать вероятность рецидива. На всех стадиях лечения ведётся контроль состояния пациента, а также постоянная корректировка назначений в зависимости от реакции организма.
Подробнее тут – http://narkologicheskaya-clinika-v-kazani16.ru
«Как отмечает врач-нарколог Иван Петрович Смирнов, «вывод из запоя должен проводиться исключительно под наблюдением специалистов, поскольку риски для организма при резком прекращении употребления алкоголя чрезвычайно высоки».»
Разобраться лучше – врач вывод из запоя в ростове-на-дону
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее – нарколог на дом анонимно санкт-петербург
В Казани дежурят мобильные бригады, покрывающие центральные районы и спальные кварталы. Координатор по телефону собирает лишь данные, влияющие на безопасность: текущие лекарства и дозировки, аллергии, эпизоды судорог/психозов в анамнезе, последние значения АД/ЧСС, температуру, а также бытовые условия — место полулёжа, доступ к розетке, возможность «тихого окна» на 2–3 часа. Врач приезжает быстро, но спокойно; вместо суеты — последовательность и аккуратные действия. Визит начинается с очного осмотра, где фиксируются исходные показатели и выбирается контур терапии. Далее выполняется тест переносимости и только затем — основной инфузионный этап. По завершении пациент получает «вечерний протокол» с простыми ритуалами: приглушить свет, проветрить комнату, исключить экраны за час до сна, пить воду малыми глотками.
Получить дополнительные сведения – вызов наркологической помощи казань
Khám phá thế giới giải trí trực tuyến đỉnh cao tại MM88, nơi mang đến những trải nghiệm cá cược thể thao và casino sống động.
Формат лечения
Исследовать вопрос подробнее – запой наркологическая клиника в санкт-петербурге
Ключ к эффективному выведению из запоя — гибкая персонализация. Мы не настаиваем на «универсальных» капельницах: сначала очная оценка, затем тест переносимости и лишь после — основная инфузия с контролем витальных показателей (АД/ЧСС/SpO?/температура) и субъективной реактивности (тошнота, тремор, тревога по шкале 0–10). Такой подход позволяет мягко провести детоксикацию, восстановить сон, стабилизировать вегетативную нервную систему и уменьшить «шум» организма.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-v-ekaterinburge16.ru/vyvod-iz-zapoya-na-domu-ekaterinburg-otzyvy/
Посещение школы вокала в москве может стать отличным способом улучшить свои вокальные навыки и раскрыть творческий потенциал.
приобрести новые навыки пения . В этой школе опытные вокалисты помогают ученикам развить свой уникальный вокальный стиль . Школа вокала организует мастер-классы с известными вокалистами.
Школа вокала также организует концерты и выступления для учеников . В школе разработаны специальные методики обучения для того, чтобы развить в учениках уверенность в своих силах. Школа вокала стремится создать уютную и творческую атмосферу .
Обучение в школе вокала помогает ученикам улучшить свое самочувствие и настроение . Ученики разработать свое собственное музыкальное направление . Школа вокала организует выступления учеников на различных концертах и фестивалях.
Обучение в школе вокала также помогает ученикам развить свою дисциплину и ответственность . Ученики могут участвовать в различных музыкальных мероприятиях . Школа вокала организует занятия в небольших группах .
Программа обучения в школе вокала включает в себя теоретические и практические занятия . Ученики могут работать над своим собственным репертуаром . Школа вокала предлагает ученикам возможность участия в мастер-классах .
Программа обучения также включает в себя работу над сценическим поведением и выступлением . Ученики могут работать над своей собственной музыкальной карьерой. Школа вокала предоставляет ученикам поддержку и консультации на каждом этапе их обучения.
Школа вокала помогает ученикам раскрыть свой внутренний потенциал. Ученики могут улучшить свои вокальные данные . Школа вокала организует выступления учеников на различных концертах и фестивалях.
Школа вокала также предлагает ученикам возможность общаться с другими музыкантами. Ученики могут создавать свои собственные музыкальные проекты . Школа вокала создает уникальную и дружественную атмосферу.
Вывод из запоя в Пушкино в клинике «Трезвый Путь» — это оперативная помощь на дому и в стационаре, персональные детокс-схемы и бережное восстановление организма без постановки на учёт. Мы подключаемся круглосуточно, аккуратно снимаем интоксикацию, стабилизируем давление и пульс, уменьшаем тремор, тревогу и бессонницу, а затем предлагаем понятный маршрут к ремиссии, который вписывается в ваш рабочий и семейный график. Цель — безопасно пройти острый период и не «сорваться» обратно, когда станет чуть полегче.
Разобраться лучше – vyvod-iz-zapoya-s-vyezdom
Je suis completement seduit par Pokerstars Casino, on y trouve une energie contagieuse. Le catalogue de titres est vaste, avec des slots aux designs captivants. 100% jusqu’a 500 € avec des free spins. Le suivi est impeccable. Le processus est clair et efficace, cependant des offres plus importantes seraient super. Dans l’ensemble, Pokerstars Casino est un choix parfait pour les joueurs. Pour couronner le tout l’interface est fluide comme une soiree, permet une immersion complete. A souligner les evenements communautaires engageants, offre des bonus exclusifs.
http://www.pokerstarscasinofr.com|
Этап
Подробнее – нарколог на дом жуковский цены
Капельница от запоя в клинике в Нижнем Новгороде является одним из ключевых методов детоксикации организма после длительного употребления алкоголя. Основная цель процедуры — быстрое и безопасное выведение токсинов, нормализация работы жизненно важных органов и стабилизация общего состояния пациента. Методика основана на внутривенном введении лекарственных растворов, которые восполняют дефицит жидкости, электролитов и витаминов, устраняя последствия интоксикации. Такой подход позволяет достичь значительного улучшения самочувствия уже в первые часы после начала терапии.
Подробнее можно узнать тут – вызвать капельницу от запоя на дому нижний новгород
Круглосуточная наркологическая помощь — это не набор «сильных капельниц», а последовательный клинический процесс с понятными этапами, метриками и окнами оценки результата. В наркологической клинике «ВолгаМед Резонанс» каждый вызов и каждое обращение переводятся в управляемый маршрут: от короткого телескрининга и очного осмотра до прицельной инфузионной терапии и бережной поведенческой поддержки. Мы работаем незаметно, анонимно и корректно: немаркированный транспорт, нейтральная экипировка, лаконичная документация без стигматизирующей лексики, единая точка связи 24/7 для семьи.
Углубиться в тему – наркологическая клиника наркологический центр в нижнем новгороде
«Как отмечает врач-нарколог Иван Петрович Смирнов, «вывод из запоя должен проводиться исключительно под наблюдением специалистов, поскольку риски для организма при резком прекращении употребления алкоголя чрезвычайно высоки».»
Подробнее тут – вывод из запоя цена ростов-на-дону
Мы используем модульную терапию: каждый контур решает одну клиническую задачу и сопровождается понятной динамикой. Это помогает мягко вести пациента и не «замазывать» вклад отдельных шагов параллельными усилениями.
Углубиться в тему – вывод из запоя капельница в казани
Вывод из запоя в клинике в Санкт-Петербурге осуществляется под круглосуточным медицинским контролем с применением современных методов инфузионной терапии, препаратов для восстановления обменных процессов и купирования синдрома отмены. Главной задачей врачей является восстановление баланса между физическим и психическим состоянием, предотвращение осложнений и стабилизация основных жизненных функций.
Получить больше информации – наркологическая клиника лечение алкоголизма
Состав инфузии подбирается индивидуально по показателям и сопутствующим диагнозам. Чаще всего в схему входят следующие элементы:
Детальнее – https://vyvod-iz-zapoya-reutov7.ru/vyvod-iz-zapoya-cena-v-reutove/
Запойное состояние сопровождается интоксикацией, обезвоживанием, нарушением обменных процессов и психоэмоциональными расстройствами. Попытки самостоятельно прекратить употребление алкоголя могут привести к судорогам, скачкам давления и другим опасным осложнениям. Именно поэтому вывод из запоя в клинике обеспечивает контроль специалистов, использование медикаментозной поддержки и мониторинг жизненно важных показателей.
Получить дополнительную информацию – http://vyvod-iz-zapoya-rostov-na-donu14.ru/
Перед применением конкретных средств врач проводит обследование, определяет уровень интоксикации и выявляет сопутствующие заболевания. Это позволяет максимально точно подобрать лечение. Ниже представлены ключевые методы, которые применяются для стабилизации состояния пациента:
Подробнее можно узнать тут – вывод из запоя недорого ростов-на-дону
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Ознакомиться с деталями – нарколог на дом срочно
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Ознакомиться с деталями – https://narkolog-na-dom-zhukovskij7.ru/narkolog-na-dom-kruglosutochno-v-zhukovskom/
Круглосуточный режим — не просто «расписание». Это доступность врача тогда, когда симптомы наиболее коварны: поздним вечером, ночью, в выходные и праздники. У нас нет очередей и «окна через неделю»: тревога, бессонница, нарастающая абстиненция или риск срыва требуют реагирования по факту, а не по талону. Чтобы не тратить драгоценные часы, мы приняли промышленный стандарт быстрого старта: диспетчер собирает клинически значимую информацию, нарколог определяет безопасный канал помощи, выездная команда берёт на адрес переносное оборудование и точечные препараты, а в карте заранее создаётся план первых 24–72 часов с контрольными точками.
Выяснить больше – http://narkologicheskaya-klinika-ryazan14.ru
Je suis totalement conquis par Pokerstars Casino, il offre une experience dynamique. Il y a un eventail de titres captivants, proposant des jeux de table sophistiques. Il booste votre aventure des le depart. Le service est disponible 24/7. Les paiements sont surs et efficaces, malgre tout des bonus plus varies seraient un plus. En bref, Pokerstars Casino garantit un amusement continu. En extra le site est rapide et engageant, booste le fun du jeu. Particulierement cool les evenements communautaires pleins d’energie, offre des bonus exclusifs.
Aller Г la page|
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Разобраться лучше – http://narkolog-na-dom-sankt-peterburg14.ru
При оказании помощи используются современные медикаментозные средства, направленные на устранение интоксикации и стабилизацию функций организма.
Подробнее – нарколог на дом клиника санкт-петербург
Je ne me lasse pas de Pokerstars Casino, on ressent une ambiance de fete. Les jeux proposes sont d’une diversite folle, offrant des sessions live immersives. Il offre un coup de pouce allechant. Disponible 24/7 par chat ou email. Les retraits sont fluides et rapides, toutefois des recompenses supplementaires dynamiseraient le tout. En fin de compte, Pokerstars Casino est un immanquable pour les amateurs. Ajoutons aussi le site est rapide et style, donne envie de prolonger l’aventure. Un bonus les paiements securises en crypto, assure des transactions fluides.
http://www.pokerstarscasino366fr.com|
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить дополнительную информацию – http://
Перед таблицей коротко поясним логику: мы выбираем самый безопасный маршрут именно для вашей ситуации, а при изменении состояния оперативно переключаемся на другой формат без пауз.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-na-domu-v-pushkino
J’ai une passion debordante pour Stake Casino, on y trouve une energie contagieuse. La gamme est variee et attrayante, comprenant des titres adaptes aux cryptomonnaies. Il propulse votre jeu des le debut. Disponible 24/7 par chat ou email. Le processus est fluide et intuitif, en revanche des recompenses additionnelles seraient ideales. En somme, Stake Casino offre une aventure inoubliable. D’ailleurs la plateforme est visuellement vibrante, apporte une energie supplementaire. Un avantage notable les evenements communautaires pleins d’energie, offre des recompenses continues.
Naviguer sur le site|
J’ai un veritable coup de c?ur pour Mystake Casino, ca transporte dans un univers de plaisirs. Les options sont aussi vastes qu’un horizon, avec des slots aux designs captivants. Il amplifie le plaisir des l’entree. Le service client est excellent. Le processus est simple et transparent, cependant des offres plus consequentes seraient parfaites. En somme, Mystake Casino est un choix parfait pour les joueurs. En complement le design est moderne et energique, ce qui rend chaque moment plus vibrant. A noter le programme VIP avec des niveaux exclusifs, qui dynamise l’engagement.
Regarder de plus prГЁs|
Je ne me lasse pas de Casinozer Casino, c’est une plateforme qui deborde de dynamisme. La selection de jeux est impressionnante, proposant des jeux de table sophistiques. 100% jusqu’a 500 € avec des spins gratuits. Disponible 24/7 par chat ou email. Le processus est transparent et rapide, en revanche quelques tours gratuits en plus seraient geniaux. Pour faire court, Casinozer Casino assure un divertissement non-stop. Ajoutons aussi l’interface est fluide comme une soiree, ce qui rend chaque partie plus fun. Un plus les nombreuses options de paris sportifs, propose des privileges sur mesure.
Naviguer sur le site|
Je suis epate par Mystake Casino, ca offre un plaisir vibrant. On trouve une profusion de jeux palpitants, incluant des options de paris sportifs dynamiques. Il rend le debut de l’aventure palpitant. Le suivi est toujours au top. Les gains sont verses sans attendre, par ailleurs des offres plus consequentes seraient parfaites. Pour conclure, Mystake Casino offre une aventure memorable. Ajoutons aussi la navigation est claire et rapide, ce qui rend chaque session plus palpitante. Particulierement interessant le programme VIP avec des niveaux exclusifs, qui motive les joueurs.
Explorer le site|
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Детальнее – https://narkolog-na-dom-zhukovskij7.ru/narkolog-na-dom-kruglosutochno-v-zhukovskom
Если по ходу первичного осмотра выявляются «красные флаги» (спутанность сознания, нестабильное давление/ритм, кровавая рвота, подозрение на делирий), врач немедленно предложит госпитализацию и аккуратно организует перевод — безопасность всегда выше удобства.
Подробнее тут – http://narkolog-na-dom-zhukovskij7.ru/vyzov-narkologa-na-dom-v-zhukovskom/
Je suis sous le charme de Casinozer Casino, c’est un lieu ou l’adrenaline coule a flots. La variete des jeux est epoustouflante, incluant des paris sportifs pleins de vie. Il donne un elan excitant. Les agents sont rapides et pros. Le processus est transparent et rapide, en revanche des recompenses en plus seraient un bonus. Au final, Casinozer Casino est une plateforme qui fait vibrer. A signaler la plateforme est visuellement captivante, facilite une experience immersive. Un point cle les nombreuses options de paris sportifs, offre des recompenses continues.
Touchez ici|
Запойное состояние сопровождается интоксикацией, обезвоживанием, нарушением обменных процессов и психоэмоциональными расстройствами. Попытки самостоятельно прекратить употребление алкоголя могут привести к судорогам, скачкам давления и другим опасным осложнениям. Именно поэтому вывод из запоя в клинике обеспечивает контроль специалистов, использование медикаментозной поддержки и мониторинг жизненно важных показателей.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-rostov-na-donu14.ru/vyvedenie-iz-zapoya-rostov-na-donu
plane crash money game aviator-game-predict.com .
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Получить дополнительную информацию – наркологическая клиника лечение алкоголизма
Запойное состояние сопровождается интоксикацией, обезвоживанием, нарушением обменных процессов и психоэмоциональными расстройствами. Попытки самостоятельно прекратить употребление алкоголя могут привести к судорогам, скачкам давления и другим опасным осложнениям. Именно поэтому вывод из запоя в клинике обеспечивает контроль специалистов, использование медикаментозной поддержки и мониторинг жизненно важных показателей.
Узнать больше – вывод из запоя на дому в ростове-на-дону
электрокарнизы https://www.prokarniz36.ru .
Процедура вывода из запоя в клинике в Казани проводится под строгим контролем специалистов. Главная цель — купировать симптомы интоксикации, нормализовать давление, сердечный ритм и восстановить обмен веществ. Используются препараты, способствующие детоксикации, а также витаминные комплексы и антиоксиданты, необходимые для поддержки работы печени и мозга.
Подробнее тут – наркологическая клиника вывод из запоя в казани
Процедура вывода из запоя проводится с применением современных методик инфузионной терапии. Врачи контролируют уровень гидратации, работу сердечно-сосудистой системы и общее состояние пациента до полного устранения симптомов.
Подробнее тут – запой наркологическая клиника
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Исследовать вопрос подробнее – нарколог на дом вывод из запоя санкт-петербург
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Подробнее можно узнать тут – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-v-sankt-peterburge-vyezd-nadom/
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Ознакомиться с деталями – http://narkologicheskaya-klinika-sankt-peterburg14.ru/
Наркологическая клиника в Санкт-Петербурге работает по различным направлениям, охватывающим как экстренную помощь, так и плановое лечение.
Подробнее тут – наркологическая клиника стационар в санкт-петербурге
Чтобы сделать процесс понятным и управляемым, каждый шаг сопровождается измеримыми маркерами безопасности и эффективности. Корректировки — точечные, по правилу «одного изменения», что позволяет видеть вклад каждого действия и сохранять переносимость.
Подробнее – скорая наркологическая помощь в казани
В Екатеринбурге бригады выезжают 24/7, покрывая как центральные районы, так и отдалённые кварталы. Координатор уточняет только то, что влияет на безопасность: принимаемые лекарства и дозы, аллергии, эпизоды судорог/психозов, исходные значения давления и пульса, а также бытовые условия — можно ли обеспечить «тихое окно» на 2–3 часа, есть ли свободная розетка и место для полулёжа. Врач приезжает с портативным мониторингом, расходными материалами и резервным планом на случай повышенной реактивности.
Получить больше информации – срочный вывод из запоя
Индивидуальная программа у нас — это модульный конструктор. В одних случаях критичен блок сна, в других — профилактика вечерних «волн» тревоги, в третьих — семейная медиированная встреча. Мы гибко переставляем модули, учитывая сопутствующие заболевания, приём базовых лекарств (антигипертензивные, антиаритмические, сахароснижающие), возраст и расписание пациента. Цель проста: чтобы терапия вписалась в жизнь, а не наоборот.
Разобраться лучше – narkologicheskaya-klinika-ryazan14.ru/
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Ознакомиться с деталями – вывод из запоя круглосуточно
В Екатеринбурге бригады выезжают 24/7, покрывая как центральные районы, так и отдалённые кварталы. Координатор уточняет только то, что влияет на безопасность: принимаемые лекарства и дозы, аллергии, эпизоды судорог/психозов, исходные значения давления и пульса, а также бытовые условия — можно ли обеспечить «тихое окно» на 2–3 часа, есть ли свободная розетка и место для полулёжа. Врач приезжает с портативным мониторингом, расходными материалами и резервным планом на случай повышенной реактивности.
Подробнее тут – нарколог на дом вывод из запоя в екатеринбурге
В Екатеринбурге бригады выезжают 24/7, покрывая как центральные районы, так и отдалённые кварталы. Координатор уточняет только то, что влияет на безопасность: принимаемые лекарства и дозы, аллергии, эпизоды судорог/психозов, исходные значения давления и пульса, а также бытовые условия — можно ли обеспечить «тихое окно» на 2–3 часа, есть ли свободная розетка и место для полулёжа. Врач приезжает с портативным мониторингом, расходными материалами и резервным планом на случай повышенной реактивности.
Подробнее – врач вывод из запоя екатеринбург
Процедура вывода из запоя в клинике в Казани проводится под строгим контролем специалистов. Главная цель — купировать симптомы интоксикации, нормализовать давление, сердечный ритм и восстановить обмен веществ. Используются препараты, способствующие детоксикации, а также витаминные комплексы и антиоксиданты, необходимые для поддержки работы печени и мозга.
Разобраться лучше – наркологическая клиника нарколог
При выводе из запоя в Ростове-на-Дону используются разные терапевтические подходы. Основной задачей является устранение токсинов и восстановление работы систем организма. Врач подбирает терапию индивидуально в зависимости от состояния пациента и длительности запоя.
Изучить вопрос глубже – срочный вывод из запоя
Перед применением конкретных средств врач проводит обследование, определяет уровень интоксикации и выявляет сопутствующие заболевания. Это позволяет максимально точно подобрать лечение. Ниже представлены ключевые методы, которые применяются для стабилизации состояния пациента:
Узнать больше – вывод из запоя на дому ростов-на-дону
J’ai une passion debordante pour Pokerstars Casino, ca transporte dans un univers de plaisirs. Il y a une abondance de jeux excitants, offrant des sessions live immersives. Il donne un elan excitant. Le service client est de qualite. Le processus est clair et efficace, par contre des offres plus genereuses rendraient l’experience meilleure. En bref, Pokerstars Casino offre une experience inoubliable. Ajoutons aussi l’interface est fluide comme une soiree, ce qui rend chaque moment plus vibrant. Particulierement fun les nombreuses options de paris sportifs, assure des transactions fluides.
Aller au site|
Реабилитационные программы в наркологической клинике направлены на нормализацию обменных процессов, восстановление сна, эмоциональной стабильности и когнитивных функций. Для достижения этого используются методы физиотерапии, нутритивной поддержки и коррекции поведения. Основное внимание уделяется мотивации пациента, работе с созависимостью и обучению навыкам здорового взаимодействия с окружающей средой.
Подробнее тут – частная наркологическая клиника в екатеринбурге
автоматические карнизы https://elektrokarniz2.ru/ .
гардина с электроприводом elektrokarniz1.ru .
Школа барабанов предлагает профессиональные уроки игры на барабанах, открывая возможность для всех желающих освоить эту увлекательную инструментальную дисциплину.
с применением традиционных подходов к музыкальному образованию. Целью такой школы является развитие музыкальных способностей и повышение общего культурного уровня студентов через THEORY и практику игры на барабанах . Школа барабанов также предоставляет возможность студентам общаться с другими музыкантами и учиться у них в формате семинаров и мастер-классов .
Школа барабанов может быть интересна как начинающим музыкантам, так и профессионалам которые стремятся расширить свою музыкальную эрудицию. Программа обучения в школе барабанов обычно включает в себя теоретические занятия по музыкальной теории и истории, а также практические занятия по игре на барабанах под руководством опытных преподавателей с большим стажем работы. Кроме того, школа барабанов часто организует различные мероприятия и концерты с приглашением известных музыкантов и групп .
Обучение в школе барабанов может принести студентам многочисленные преимущества такие как приобретение новых навыков и знаний в области музыки . Одним из главных преимуществ является возможность получения профессионального музыкального образования от опытных преподавателей с большим стажем работы . Кроме того, обучение в школе барабанов может помочь студентам повысить свою уверенность в себе и развить творческие способности через участие в различных музыкальных проектах и концертах .
Обучение в школе барабанов также предоставляет возможность студентам получить практический опыт и развить свои навыки игры на барабанах путем сотрудничества с другими музыкантами и группами. Школа барабанов может быть интересна как детям, так и взрослым которые стремятся расширить свои музыкальные горизонты и познакомиться с разными стилями и направлениями. Преподаватели школы барабанов обычно имеют большой опыт работы и могут помочь студентам в подготовке к музыкальным конкурсам и выступлениям.
Программа обучения в школе барабанов обычно включает в себя комплекс теоретических и практических занятий по технике и методике игры на барабанах . Теоретические занятия могут включать в себя изучение музыкальной теории, истории музыки и различных стилей и направлений в формате лекций и семинаров . Практические занятия могут включать в сбя обучение различным техникам игры на барабанах в индивидуальном или групповом формате .
Программа обучения в школе барабанов может варьироваться в зависимости от уровня подготовки и интересов студентов для студентов со средним или высоким уровнем подготовки . Школа барабанов может предлагать различные направления обучения по классической музыке , а также ??? форматы обучения индивидуальные или групповые занятия . Кроме того, школа барабанов часто организует различные мероприяти и концерты с участием студентов и преподавателей школы .
В заключении можно сказать, что школа барабанов представляет собой уникальную и интересную возможность для музыкального образования и творческого самовыражения для всех, кто интересуется музыкой и хочет развить свои творческие способности. Программа обучения в школе барабанов может включать в себя теоретические и практические занятия по технике и методике игры на барабанах , а также различные мероприятия и концерты для демонстрации достижений студентов и развития их творческих потенциалов.
Перспективы развития школы барабанов могут включать в себя расширение программы обучения и включение новых направлений и стилей таких как электронная музыка или экспериментальные жанры , а также развитие онлайн-образования и удаленных курсов для студентов из разных городов и стран . Кроме того, школа барабанов может сотрудничать с другими музыкальными школами и организациями для обмена опытом и методами .
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Ознакомиться с деталями – вывод из запоя с выездом ростов-на-дону
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Ознакомиться с деталями – http://www.domen.ru
Задержка усиливает риск судорог, делирия, аритмий и травм. Эти маркеры не требуют медицинского образования — их легко распознать. Если совпадает хотя бы один пункт ниже, свяжитесь с нами 24/7: мы подскажем безопасный формат старта и подготовим пространство к визиту.
Разобраться лучше – наркологическая клиника цены рязань
В наркологической клинике в Челябинске проводится профессиональная детоксикация — очищение организма от токсинов, накопленных в результате употребления алкоголя или наркотиков. Процедура выполняется под наблюдением специалистов, что исключает риск осложнений и обеспечивает быстрое улучшение самочувствия. Для восстановления функций внутренних органов применяются препараты, стабилизирующие работу печени, сердца и нервной системы. Использование капельниц, витаминов и гепатопротекторов помогает нормализовать обмен веществ и устранить последствия интоксикации.
Подробнее можно узнать тут – платная наркологическая клиника
Состав инфузии подбирается индивидуально по показателям и сопутствующим диагнозам. Чаще всего в схему входят следующие элементы:
Получить дополнительную информацию – http://vyvod-iz-zapoya-reutov7.ru/vyvod-iz-zapoya-v-stacionare-v-reutove/https://vyvod-iz-zapoya-reutov7.ru
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Подробнее – вывод из запоя вызов на дом в рязани
«Как отмечает врач-нарколог Иван Петрович Смирнов, «вывод из запоя должен проводиться исключительно под наблюдением специалистов, поскольку риски для организма при резком прекращении употребления алкоголя чрезвычайно высоки».»
Подробнее можно узнать тут – вывод из запоя на дому недорого в ростове-на-дону
Вывод из запоя в Пушкино в клинике «Трезвый Путь» — это оперативная помощь на дому и в стационаре, персональные детокс-схемы и бережное восстановление организма без постановки на учёт. Мы подключаемся круглосуточно, аккуратно снимаем интоксикацию, стабилизируем давление и пульс, уменьшаем тремор, тревогу и бессонницу, а затем предлагаем понятный маршрут к ремиссии, который вписывается в ваш рабочий и семейный график. Цель — безопасно пройти острый период и не «сорваться» обратно, когда станет чуть полегче.
Узнать больше – http://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-na-domu-v-pushkino/
Мы дозировано упоминаем географию — важнее не слово «Нижний Новгород», а предсказуемость процесса. Пациент получает «вечерний протокол» — краткие инструкции на ближайшие 12 часов: как пить воду малыми порциями, как приглушить свет, какое «окно тишины» соблюсти перед сном, когда связаться с дежурным врачом и какие маркеры фиксировать в «дневнике симптомов» (шкалы тремора, тревоги, тошноты по 0–10; время засыпания; число пробуждений).
Получить больше информации – https://narkologicheskaya-klinika-v-nizhnem-novgorode16.ru/chastnaya-narkologicheskaya-klinika-nizhnij-novgorod
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Получить дополнительную информацию – http://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare/
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Разобраться лучше – выезд нарколога на дом
Для купирования абстинентного синдрома и снятия интоксикации используются различные подходы. Врачи подбирают их индивидуально, исходя из состояния пациента.
Ознакомиться с деталями – http://vyvod-iz-zapoya-ryazan14.ru/vyvod-iz-zapoya-ryazan-na-domu/
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Получить дополнительную информацию – https://narkologicheskaya-klinika-sankt-peterburg14.ru/klinika-narkologii-spb/
Если среда дома шумная или приватность под угрозой, мы предложим «короткий коридор» через отдельный вход амбулатории. Если условия позволяют, проводим процедуры на дому: свет приглушён, доступ к розетке организован, рядом столик для расходников и приборов. Этот «экологичный» сценарий, несмотря на простоту, заметно улучшает переносимость процедур и собирает устойчивый сон в первую ночь, что особенно важно на ранних этапах стабилизации.
Получить больше информации – наркологическая клиника наркологический центр
Лечение зависимости требует комплексного подхода, включающего медицинские, психологические и социальные меры. Каждый пациент проходит индивидуальную диагностику, по результатам которой подбирается схема терапии. Такой подход позволяет снизить риски осложнений и обеспечить стабильный результат.
Узнать больше – лечение в наркологической клинике нижний новгород
Thanks for every other magnificent article. Where else could anyone get that kind of info in such an ideal manner of writing? I have a presentation subsequent week, and I am on the look for such information.
Купить iPhone 17 в Москве
Капельница, устанавливаемая наркологом на дому в Челябинске, помогает быстро очистить организм от токсинов и нормализовать водно-солевой баланс. Растворы включают витамины, анальгетики, седативные и гепатопротекторные препараты. Эффект от процедуры ощущается уже через 20–30 минут. Капельница снижает головную боль, устраняет тошноту, восстанавливает работу печени и сердечно-сосудистой системы. Такой метод считается одним из самых эффективных способов вывести пациента из запойного или абстинентного состояния без визита в стационар.
Ознакомиться с деталями – https://narkolog-na-dom-v-chelyabinske16.ru/narkolog-vyzov-na-dom-chelyabinsk
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Детальнее – вызов врача нарколога на дом
электрокарниз недорого https://elektrokarniz-dlya-shtor11.ru/ .
Лечение в клинике в Челябинске строится на принципах конфиденциальности, добровольности и медицинской этики. Врачи применяют доказательные методы терапии, а программы лечения адаптируются под особенности каждого пациента. Работа ведётся комплексно, включая медикаментозную помощь, психотерапию и социальную реабилитацию. Такой подход позволяет эффективно восстановить здоровье и вернуть пациента к нормальной жизни в обществе.
Подробнее можно узнать тут – https://narcologicheskaya-klinika-v-chelyabinske16.ru/oblastnaya-narkologicheskaya-klinika-chelyabinsk
Вывод из запоя в Пушкино в клинике «Трезвый Путь» — это оперативная помощь на дому и в стационаре, персональные детокс-схемы и бережное восстановление организма без постановки на учёт. Мы подключаемся круглосуточно, аккуратно снимаем интоксикацию, стабилизируем давление и пульс, уменьшаем тремор, тревогу и бессонницу, а затем предлагаем понятный маршрут к ремиссии, который вписывается в ваш рабочий и семейный график. Цель — безопасно пройти острый период и не «сорваться» обратно, когда станет чуть полегче.
Получить дополнительные сведения – http://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-na-domu-v-pushkino/https://vyvod-iz-zapoya-pushkino7.ru
Перед началом терапии врач проводит осмотр, собирает анамнез, измеряет давление и сатурацию, при необходимости делает экспресс-тесты. На основании данных подбирается индивидуальная схема, рассчитываются объёмы инфузии и темп введения, оценивается необходимость кардиоконтроля.
Углубиться в тему – http://vyvod-iz-zapoya-reutov7.ru
Круглосуточная наркологическая помощь — это не набор «сильных капельниц», а последовательный клинический процесс с понятными этапами, метриками и окнами оценки результата. В наркологической клинике «ВолгаМед Резонанс» каждый вызов и каждое обращение переводятся в управляемый маршрут: от короткого телескрининга и очного осмотра до прицельной инфузионной терапии и бережной поведенческой поддержки. Мы работаем незаметно, анонимно и корректно: немаркированный транспорт, нейтральная экипировка, лаконичная документация без стигматизирующей лексики, единая точка связи 24/7 для семьи.
Детальнее – https://narkologicheskaya-klinika-v-nizhnem-novgorode16.ru/chastnaya-narkologicheskaya-klinika-nizhnij-novgorod
J’adore la vibe de Pokerstars Casino, ca invite a plonger dans le fun. La bibliotheque est pleine de surprises, proposant des jeux de table sophistiques. Il donne un elan excitant. Le support est rapide et professionnel. Le processus est fluide et intuitif, de temps en temps des offres plus importantes seraient super. En conclusion, Pokerstars Casino est un endroit qui electrise. Ajoutons que la plateforme est visuellement vibrante, facilite une experience immersive. Un bonus les options variees pour les paris sportifs, garantit des paiements securises.
Explorer le site web|
J’ai un veritable coup de c?ur pour Stake Casino, on y trouve une energie contagieuse. Les options sont aussi vastes qu’un horizon, comprenant des titres adaptes aux cryptomonnaies. 100% jusqu’a 500 € avec des spins gratuits. Le service client est excellent. Les retraits sont lisses comme jamais, a l’occasion des offres plus genereuses seraient top. En fin de compte, Stake Casino assure un fun constant. Pour ajouter la plateforme est visuellement electrisante, facilite une experience immersive. Un element fort les options variees pour les paris sportifs, offre des recompenses continues.
DГ©couvrir plus|
Форматы вывода из запоя в Пушкино
Подробнее можно узнать тут – вывод из запоя дешево пушкино
Je suis emerveille par Pokerstars Casino, on ressent une ambiance festive. La selection de jeux est impressionnante, avec des machines a sous visuellement superbes. Le bonus de bienvenue est genereux. Le suivi est d’une fiabilite exemplaire. Les paiements sont surs et efficaces, toutefois des recompenses additionnelles seraient ideales. En somme, Pokerstars Casino offre une aventure inoubliable. En extra la navigation est fluide et facile, booste le fun du jeu. Un point fort les evenements communautaires engageants, propose des privileges sur mesure.
Ouvrir la page|
Вывод из запоя в Пушкино в клинике «Трезвый Путь» — это оперативная помощь на дому и в стационаре, персональные детокс-схемы и бережное восстановление организма без постановки на учёт. Мы подключаемся круглосуточно, аккуратно снимаем интоксикацию, стабилизируем давление и пульс, уменьшаем тремор, тревогу и бессонницу, а затем предлагаем понятный маршрут к ремиссии, который вписывается в ваш рабочий и семейный график. Цель — безопасно пройти острый период и не «сорваться» обратно, когда станет чуть полегче.
Изучить вопрос глубже – вывод из запоя
Je suis epate par Stake Casino, ca transporte dans un univers de plaisirs. La selection de jeux est impressionnante, incluant des paris sur des evenements sportifs. Le bonus de bienvenue est genereux. Le suivi est d’une fiabilite exemplaire. Les retraits sont simples et rapides, quelquefois quelques spins gratuits en plus seraient top. En resume, Stake Casino est un choix parfait pour les joueurs. A mentionner le site est rapide et immersif, ce qui rend chaque partie plus fun. Particulierement interessant les evenements communautaires vibrants, qui dynamise l’engagement.
AccГ©der Г la page|
Лечение зависимости требует системного подхода и чёткой последовательности действий. Каждый этап направлен на устранение интоксикации, восстановление функций организма и закрепление результата. В клинике процедура организована так, чтобы обеспечить комфорт и безопасность пациента.
Получить дополнительные сведения – наркологическая клиника наркологический центр в челябинске
Перевод с итальянского – перевод документов с нотариальным заверением. Срочный перевод в Самаре? Выполним оперативно! Нотариальное заверение документов. Конфиденциально. Гарантия качества.
Je suis bluffe par Mystake Casino, c’est une plateforme qui pulse avec energie. La selection de jeux est impressionnante, incluant des paris sur des evenements sportifs. Il offre un demarrage en fanfare. Le support est efficace et amical. Les paiements sont securises et rapides, mais encore plus de promos regulieres ajouteraient du peps. Au final, Mystake Casino offre une experience hors du commun. Par ailleurs le design est style et moderne, ajoute une vibe electrisante. Particulierement attrayant le programme VIP avec des recompenses exclusives, garantit des paiements securises.
Aller plus loin|
Je suis bluffe par Casinozer Casino, il propose une aventure palpitante. Les options de jeu sont incroyablement variees, proposant des jeux de table classiques. Il booste votre aventure des le depart. Le support est efficace et amical. Les gains arrivent sans delai, de temps a autre quelques free spins en plus seraient bienvenus. En conclusion, Casinozer Casino offre une experience inoubliable. En extra la navigation est intuitive et lisse, ajoute une vibe electrisante. Un avantage les paiements securises en crypto, propose des avantages uniques.
Plongez-y|
Мы дозировано упоминаем географию — важнее не слово «Нижний Новгород», а предсказуемость процесса. Пациент получает «вечерний протокол» — краткие инструкции на ближайшие 12 часов: как пить воду малыми порциями, как приглушить свет, какое «окно тишины» соблюсти перед сном, когда связаться с дежурным врачом и какие маркеры фиксировать в «дневнике симптомов» (шкалы тремора, тревоги, тошноты по 0–10; время засыпания; число пробуждений).
Ознакомиться с деталями – наркологическая клиника клиника помощь
В городе и пригороде организован круглосуточный приём с возможностью выезда на дом. Координатор уточняет только клинически значимые данные: регулярные препараты и дозировки, аллергии, недавние эпизоды судорог/психозов, доступ к розетке, возможность обеспечить «тихое окно» на 2–3 часа. Если в квартире многолюдно или идёт ремонт, предложим «тихий» стационар с отдельным входом и тем же ведущим врачом; после стабилизации зеркально перенесём маршрут обратно домой, чтобы не терять темп и доверие.
Изучить вопрос глубже – вывод наркологическая клиника в нижнем новгороде
Je suis epate par Mystake Casino, on ressent une ambiance de fete. Le catalogue est un tresor de divertissements, comprenant des jeux compatibles avec les cryptos. 100% jusqu’a 500 € + tours gratuits. Le support client est irreprochable. Le processus est fluide et intuitif, rarement quelques spins gratuits en plus seraient top. Au final, Mystake Casino vaut une exploration vibrante. Notons aussi le design est moderne et energique, apporte une energie supplementaire. Particulierement fun les evenements communautaires vibrants, offre des recompenses regulieres.
Obtenir plus|
Je suis enthousiasme par Casinozer Casino, ca invite a l’aventure. La gamme est variee et attrayante, comprenant des titres adaptes aux cryptomonnaies. Il offre un coup de pouce allechant. Disponible a toute heure via chat ou email. Le processus est fluide et intuitif, bien que des bonus varies rendraient le tout plus fun. Pour faire court, Casinozer Casino est un lieu de fun absolu. Ajoutons aussi le site est rapide et engageant, donne envie de continuer l’aventure. Egalement top les options de paris sportifs diversifiees, cree une communaute soudee.
Essayer maintenant|
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Узнать больше – вывод из запоя цена ростов-на-дону
Домашний визит нарколога — это формат, который соединяет клиническую безопасность и человеческую деликатность. В «КубаньМедЦентре» (Краснодар) мы организуем помощь так, чтобы пациент получал её там, где ему спокойнее всего — у себя дома. Дежурная команда работает круглосуточно, а среднее окно прибытия по городу составляет 30–40 минут с момента подтверждения заявки. Врач приезжает без опознавательных знаков, проводит экспресс-оценку состояния, запускает индивидуально подобранную инфузионную терапию и оставляет подробный план на ближайшие 72 часа. Каждый шаг объясняется простым языком: что мы делаем, зачем это нужно и по каким критериям поймём, что динамика идёт правильно.
Получить дополнительную информацию – https://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr/
При выводе из запоя в Ростове-на-Дону используются разные терапевтические подходы. Основной задачей является устранение токсинов и восстановление работы систем организма. Врач подбирает терапию индивидуально в зависимости от состояния пациента и длительности запоя.
Узнать больше – http://vyvod-iz-zapoya-rostov-na-donu14.ru/vyvedenie-iz-zapoya-rostov-na-donu/
Выездная бригада прибывает с необходимым оборудованием. Инфузионная терапия длится 60–120 минут; по ходу процедуры контролируются давление, пульс, дыхание и субъективное самочувствие, при необходимости схема корректируется (темп капания, смена растворов, добавление противорвотных или седативных средств). Чаще всего уже к концу первой инфузии снижается тошнота, уходит дрожь и «внутренняя дрожь», нормализуется сон. Врач оставляет пошаговый план на 24–72 часа: питьевой режим, щадящее питание (дробно, без жирного и острого), режим сна, рекомендации по витаминам и гепатопротекции. Если в процессе выявляются тревожные признаки (нестабильная гемодинамика, выраженная аритмия, спутанность сознания), будет предложен перевод в стационар.
Получить дополнительные сведения – https://vyvod-iz-zapoya-reutov7.ru/vyvedenie-iz-zapoya-v-reutove
Перед таблицей коротко поясним логику: мы выбираем самый безопасный маршрут именно для вашей ситуации, а при изменении состояния оперативно переключаемся на другой формат без пауз.
Подробнее – vyvod-iz-zapoya-stacionar-pushkino
Комплексный перевод удобно – официальный перевод документов онлайн. Самара, перевод документов срочно! Нотариальное заверение. Любые языки. Качество и точность. Гарантия принятия.
Наши стандарты включают конфиденциальную маршрутизацию, детализированные инструкции для семьи, модульный план лечения и прозрачное разделение бесплатных и платных блоков. Каждому пациенту назначается ведущий специалист, который сопровождает его на всём пути — от первого звонка до контрольных чек-инов после процедур. Мы не «наращиваем» объём вмешательств ради впечатления: используется минимально достаточный набор мер, который действительно влияет на целевые маркеры — переносимость воды, качество сна, сглаживание вегетативных «качелей» и возвращение утренней ясности.
Изучить вопрос глубже – наркологическая клиника наркологический центр в челябинске
Первые сутки после прекращения алкоголя — самые уязвимые: именно в это время нарастают абстинентные симптомы и риск осложнений. Ниже приведены основные ситуации, при которых нужен быстрый выезд врача. Перед списком отметим: если сомневаетесь, позвоните координатору — он уточнит признаки и подскажет безопасные действия до прибытия команды.
Выяснить больше – vyvod-iz-zapoya-na-domu-v-pushkino
Петербургский темп жизни — поздняя занятость, переменная нагрузка, сезонные перепады света — усложняет восстановление после эпизодов употребления. Поэтому мы разработали модульные программы, способные гибко подстраиваться под график и биоритмы: у кого-то «трудные часы» приходятся на поздний вечер на Васильевском острове, у кого-то — на раннее утро перед сменой в Адмиралтейском районе. Маршрут строится вокруг человека, а не вокруг расписания кабинета: очные приёмы, немаркированные выезды на дом, дневной стационар, защищённые онлайн-сессии — всё объединено единым клиническим планом и общими целями.
Подробнее можно узнать тут – лечение в наркологической клинике в санкт-петербурге
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Получить больше информации – нарколог капельница на дом краснодар
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Получить дополнительную информацию – https://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr
В городе и пригороде организован круглосуточный приём с возможностью выезда на дом. Координатор уточняет только клинически значимые данные: регулярные препараты и дозировки, аллергии, недавние эпизоды судорог/психозов, доступ к розетке, возможность обеспечить «тихое окно» на 2–3 часа. Если в квартире многолюдно или идёт ремонт, предложим «тихий» стационар с отдельным входом и тем же ведущим врачом; после стабилизации зеркально перенесём маршрут обратно домой, чтобы не терять темп и доверие.
Подробнее – наркологические клиники алкоголизм нижний новгород
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Выяснить больше – вывод из запоя вызов
Перед применением конкретных средств врач проводит обследование, определяет уровень интоксикации и выявляет сопутствующие заболевания. Это позволяет максимально точно подобрать лечение. Ниже представлены ключевые методы, которые применяются для стабилизации состояния пациента:
Подробнее тут – https://vyvod-iz-zapoya-rostov-na-donu14.ru/vyvod-iz-zapoya-na-domu-rostov-na-donu
Главная цель — безопасно стабилизировать состояние, вернуть контроль над сном, гидратацией и базовой активностью в первые сутки и удержать результат. Для этого мы используем модульный подход: один этап — одна клиническая задача — один измеримый маркер. Такой принцип исключает «гонку доз», снижает риск перегрузки объёмом и делает прогноз понятным для пациента и близких. Мы сознательно разделяем «короткие эффекты» (уменьшение тошноты, сглаживание тахикардии) и «эффекты консолидации» (устойчивый сон, ясность утром), чтобы каждая корректировка была точной и доказуемой.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-v-nizhnem-novgorode16.ru/narkologiya-nizhnij-novgorod-besplatno/
«Как отмечает врач-нарколог Иван Петрович Смирнов, «вывод из запоя должен проводиться исключительно под наблюдением специалистов, поскольку риски для организма при резком прекращении употребления алкоголя чрезвычайно высоки».»
Получить дополнительные сведения – http://vyvod-iz-zapoya-rostov-na-donu14.ru
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Изучить вопрос глубже – http://narkologicheskaya-klinika-sankt-peterburg14.ru/
В городе и ближайших районах клиника «УралМед Трезвость» обеспечивает оперативный выезд и амбулаторный приём без очередей. На этапе первичного контакта координатор уточняет только клинически значимые моменты: постоянные препараты и дозы, аллергии, эпизоды судорог/психозов в прошлом, базовые показатели (АД/ЧСС/SpO?, если доступны), длительность симптомов, возможность организовать «тихое окно» на 20–30 минут. Вместо долгих разговоров — короткая, спокойная логика: где безопаснее начать (дом/амбулатория/стационар), какую ближайшую цель выбираем, в каком интервале ждём эффект и что считаем сигналом для связи с дежурным врачом.
Подробнее – наркологическая клиника клиника помощь
Наши стандарты включают конфиденциальную маршрутизацию, детализированные инструкции для семьи, модульный план лечения и прозрачное разделение бесплатных и платных блоков. Каждому пациенту назначается ведущий специалист, который сопровождает его на всём пути — от первого звонка до контрольных чек-инов после процедур. Мы не «наращиваем» объём вмешательств ради впечатления: используется минимально достаточный набор мер, который действительно влияет на целевые маркеры — переносимость воды, качество сна, сглаживание вегетативных «качелей» и возвращение утренней ясности.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-v-chelyabinske16.ru/chastnaya-narkologicheskaya-klinika-chelyabinsk/
Индивидуальная программа у нас — это модульный конструктор. В одних случаях критичен блок сна, в других — профилактика вечерних «волн» тревоги, в третьих — семейная медиированная встреча. Мы гибко переставляем модули, учитывая сопутствующие заболевания, приём базовых лекарств (антигипертензивные, антиаритмические, сахароснижающие), возраст и расписание пациента. Цель проста: чтобы терапия вписалась в жизнь, а не наоборот.
Подробнее тут – анонимная наркологическая клиника рязань
В наркологической клинике в Челябинске проводится профессиональная детоксикация — очищение организма от токсинов, накопленных в результате употребления алкоголя или наркотиков. Процедура выполняется под наблюдением специалистов, что исключает риск осложнений и обеспечивает быстрое улучшение самочувствия. Для восстановления функций внутренних органов применяются препараты, стабилизирующие работу печени, сердца и нервной системы. Использование капельниц, витаминов и гепатопротекторов помогает нормализовать обмен веществ и устранить последствия интоксикации.
Углубиться в тему – наркологическая клиника вывод из запоя
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Получить дополнительную информацию – вывод из запоя на дому
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Получить больше информации – помощь нарколога на дому
Перед началом терапии важно оценить состояние пациента и выявить сопутствующие заболевания. После этого назначается комплексное лечение, которое позволяет восстановить здоровье и подготовить к дальнейшей реабилитации.
Выяснить больше – вывод из запоя на дому
Перед началом терапии важно оценить состояние пациента и выявить сопутствующие заболевания. После этого назначается комплексное лечение, которое позволяет восстановить здоровье и подготовить к дальнейшей реабилитации.
Получить дополнительную информацию – вывод из запоя цена
Лечение зависимости требует системного подхода и чёткой последовательности действий. Каждый этап направлен на устранение интоксикации, восстановление функций организма и закрепление результата. В клинике процедура организована так, чтобы обеспечить комфорт и безопасность пациента.
Изучить вопрос глубже – http://narcologicheskaya-klinika-v-chelyabinske16.ru
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Получить дополнительную информацию – наркологическая клиника стационар
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Подробнее – наркологическая клиника цены
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Детальнее – срочный вывод из запоя
Khám phá thế giới giải trí trực tuyến đỉnh cao tại MM88, nơi mang đến những trải nghiệm cá cược thể thao và casino sống động.
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Изучить вопрос глубже – http://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr/
В Реутове помощь при запое должна быть быстрой, безопасной и конфиденциальной. Команда «Трезвой Линии» организует выезд врача 24/7, проводит детоксикацию с контролем жизненных показателей и помогает мягко стабилизировать состояние без лишнего стресса. Мы работаем по медицинским протоколам, используем сертифицированные препараты и подбираем схему персонально — с учётом анализов, хронических заболеваний и текущего самочувствия. Приоритет — снять интоксикацию, восстановить сон и аппетит, выровнять давление и снизить тревожность, чтобы человек смог безопасно вернуться к обычному режиму.
Разобраться лучше – https://vyvod-iz-zapoya-reutov7.ru/vyvedenie-iz-zapoya-v-reutove/
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Углубиться в тему – вызвать нарколога на дом краснодар
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Углубиться в тему – нарколог на дом вывод из запоя санкт-петербург
При выезде врач действует по установленному протоколу, что гарантирует безопасность и эффективность процедуры.
Исследовать вопрос подробнее – http://narkolog-na-dom-sankt-peterburg14.ru
Запойное состояние сопровождается интоксикацией, обезвоживанием, нарушением обменных процессов и психоэмоциональными расстройствами. Попытки самостоятельно прекратить употребление алкоголя могут привести к судорогам, скачкам давления и другим опасным осложнениям. Именно поэтому вывод из запоя в клинике обеспечивает контроль специалистов, использование медикаментозной поддержки и мониторинг жизненно важных показателей.
Подробнее тут – http://vyvod-iz-zapoya-rostov-na-donu14.ru/vyvedenie-iz-zapoya-rostov-na-donu/
Лечение зависимости требует системного подхода и чёткой последовательности действий. Каждый этап направлен на устранение интоксикации, восстановление функций организма и закрепление результата. В клинике процедура организована так, чтобы обеспечить комфорт и безопасность пациента.
Получить больше информации – наркологическая клиника вывод из запоя челябинск
Запойное состояние сопровождается интоксикацией, обезвоживанием, нарушением обменных процессов и психоэмоциональными расстройствами. Попытки самостоятельно прекратить употребление алкоголя могут привести к судорогам, скачкам давления и другим опасным осложнениям. Именно поэтому вывод из запоя в клинике обеспечивает контроль специалистов, использование медикаментозной поддержки и мониторинг жизненно важных показателей.
Ознакомиться с деталями – помощь вывод из запоя
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Детальнее – https://narkologicheskaya-klinika-v-spb14.ru/narkologicheskaya-bolnicza-sankt-peterburg/
Процесс терапии включает несколько последовательных шагов:
Изучить вопрос глубже – вывод наркологическая клиника челябинск
Выездная бригада прибывает с необходимым оборудованием. Инфузионная терапия длится 60–120 минут; по ходу процедуры контролируются давление, пульс, дыхание и субъективное самочувствие, при необходимости схема корректируется (темп капания, смена растворов, добавление противорвотных или седативных средств). Чаще всего уже к концу первой инфузии снижается тошнота, уходит дрожь и «внутренняя дрожь», нормализуется сон. Врач оставляет пошаговый план на 24–72 часа: питьевой режим, щадящее питание (дробно, без жирного и острого), режим сна, рекомендации по витаминам и гепатопротекции. Если в процессе выявляются тревожные признаки (нестабильная гемодинамика, выраженная аритмия, спутанность сознания), будет предложен перевод в стационар.
Получить дополнительную информацию – http://vyvod-iz-zapoya-reutov7.ru/vyvod-iz-zapoya-cena-v-reutove/
Лечение в клинике в Челябинске строится на принципах конфиденциальности, добровольности и медицинской этики. Врачи применяют доказательные методы терапии, а программы лечения адаптируются под особенности каждого пациента. Работа ведётся комплексно, включая медикаментозную помощь, психотерапию и социальную реабилитацию. Такой подход позволяет эффективно восстановить здоровье и вернуть пациента к нормальной жизни в обществе.
Разобраться лучше – наркологическая клиника стационар челябинск
Каждый пациент проходит несколько последовательных этапов, направленных на очищение организма, стабилизацию эмоционального состояния и формирование стойкой мотивации к трезвой жизни. Такой подход позволяет не только устранить физическую зависимость, но и укрепить психическую устойчивость.
Углубиться в тему – наркологическая клиника вывод из запоя
Concerns regarding negative behavior in online communities and accessibility are still widespread.
play http://andarbaharwin.com
Je suis epate par Pokerstars Casino, on y trouve une energie contagieuse. La bibliotheque est pleine de surprises, incluant des paris sur des evenements sportifs. Avec des depots rapides et faciles. Le service client est excellent. Le processus est transparent et rapide, malgre tout des offres plus genereuses rendraient l’experience meilleure. Au final, Pokerstars Casino offre une experience hors du commun. D’ailleurs la plateforme est visuellement captivante, apporte une touche d’excitation. A signaler les tournois reguliers pour la competition, propose des avantages uniques.
Savoir plus|
Комплексная терапия включает несколько последовательных этапов, обеспечивающих полное восстановление организма и личности пациента. Каждый из них направлен на решение конкретных задач — от устранения интоксикации до закрепления устойчивой ремиссии.
Узнать больше – наркологическая клиника вывод из запоя волгоград
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Получить больше информации – вывод из запоя на дому цена
Первым шагом на пути к выздоровлению является очищение организма от токсинов. В клинике проводится детоксикация с использованием современных препаратов, направленных на выведение продуктов распада алкоголя и наркотиков. Медикаментозное лечение дополняется витаминами, гепатопротекторами и средствами для нормализации работы нервной системы. Это помогает восстановить обмен веществ, улучшить сон, аппетит и общее самочувствие пациента.
Подробнее – http://narkologicheskaya-klinika-v-voronezhe17.ru/voronezh-narkologicheskij-dispanser/https://narkologicheskaya-klinika-v-voronezhe17.ru
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Получить больше информации – https://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-staczionar-voronezh/
Ниже представлена таблица с основными препаратами, используемыми при выводе из запоя в Тюмени:
Подробнее – вывод из запоя недорого тюмень
В клинике используются проверенные медицинские методы, основанные на современных научных данных. При алкогольной или наркотической интоксикации первым этапом является детоксикация — выведение токсинов из организма и нормализация обменных процессов. На следующем этапе проводится медикаментозная поддержка, направленная на стабилизацию состояния, снижение тяги к веществам и восстановление функций внутренних органов. После стабилизации пациент проходит курс психотерапии и участвует в программах реабилитации.
Получить больше информации – http://narkologicheskaya-clinica-v-voronezhe17.ru/voronezh-narkologicheskij-dispanser/https://narkologicheskaya-clinica-v-voronezhe17.ru
Благодаря комплексному подходу достигается не только снятие симптомов, но и долгосрочная стабилизация состояния пациента.
Изучить вопрос глубже – платная наркологическая скорая помощь волгоград
Каждое вмешательство проходит через систему «цель > маркер > окно оценки > выключение модуля». Ниже приведена таблица, отражающая базовую логику диагностики и корректировки терапии в зависимости от состояния пациента.
Подробнее – наркологическая клиника цены
Первая задача при выезде — быстро отделить угрозы от симптомов, которые можно безопасно стабилизировать на дому. Таблица ниже иллюстрирует, как стартовые наблюдения превращаются в проверяемые гипотезы, конкретные действия и решения в «окнах оценки». Она не заменяет очной диагностики, а объясняет архитектуру первых часов, чтобы у семьи был ясный ориентир.
Получить дополнительную информацию – нарколог на дом цены краснодар
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg/
Детоксикация в клинике «Центр Трезвости ВоронМед» проводится по принципу минимального вмешательства при максимальной эффективности. Основная задача — очистить кровь от токсинов и стабилизировать внутреннюю среду организма без нагрузки на сердце и почки. Все препараты вводятся медленно, под контролем медицинского персонала, а состав подбирается индивидуально после оценки анализов и состояния пациента.
Подробнее тут – вывод из запоя клиника
Процедура проводится как в стационаре, так и на дому. Врач приезжает по вызову, проводит осмотр и измеряет давление, пульс, насыщение кислородом. После оценки состояния подбирается состав капельницы и начинается инфузионная терапия. В среднем процедура длится от 40 минут до 1,5 часов, в зависимости от степени интоксикации. По завершении врач наблюдает за реакцией организма и даёт рекомендации по восстановлению.
Подробнее – https://kapelnicza-ot-zapoya-v-voronezhe17.ru/otkapatsya-voronezh-nedorogo/
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Подробнее – кодирование от алкоголизма анонимно в волгограде
Абстиненция — это не «плохое самочувствие», а тяжёлая физиологическая перестройка с риском аритмий, скачков давления, судорог и делирия. Домашние попытки выходить из запоя без врача часто усиливают обезвоживание, перегружают печень и провоцируют тревожные расстройства, из-за которых усиливается тяга к алкоголю. В «НоваМед Центр» тактика строится вокруг безопасности: сначала исключаются угрозы жизни, затем врач подбирает инфузию, которая переносится именно вашим организмом. Контролируются давление, пульс, дыхание, сатурация; по реакции корректируются объёмы и скорость введения, чтобы не вызвать перегрузки. Параллельно купируются симптомы — тремор, тошнота, бессонница, тревога — и возвращается физиологичный сон. Такой управляемый маршрут снижает риск осложнений и позволяет человеку быстрее восстановить ясность мышления и базовую работоспособность.
Подробнее тут – вывод из запоя капельница
Капельница формируется индивидуально и включает растворы для регидратации, препараты для защиты печени, витаминизацию и седативные средства. Врач следит за реакцией организма, корректирует дозировку и контролирует показатели.
Ознакомиться с деталями – http://vyvod-iz-zapoya-v-himki1.ru
В стационаре
Ознакомиться с деталями – https://vyvod-iz-zapoya-domodedovo3.ru/vyvod-iz-zapoya-kodirovanie-alkogolizma-domodedovo
Чтобы не оценивать состояние субъективно, в клинике применяется система наблюдения за ключевыми параметрами. Таблица помогает врачу и пациенту видеть реальную динамику и корректировать вмешательства только при необходимости.
Углубиться в тему – наркологические клиники алкоголизм
Капельница — это не «секретный коктейль», а набор узких модулей, каждый из которых отвечает за одну задачу. Мы включаем ровно один новый модуль за раз и заранее обозначаем стоп-критерий, чтобы не тянуть терапию «по инерции». Параллельно настраиваются поведенческие элементы: свет, тишина, дыхательные ритмы и «окна» питья. Это снимает часть нагрузки с организма и ускоряет наступление целевых маркеров.
Выяснить больше – вызвать врача нарколога на дом в краснодаре
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Изучить вопрос глубже – http://narkologicheskaya-klinika-v-volgograde17.ru/
Je suis captive par Coolzino Casino, il offre une experience dynamique. La bibliotheque de jeux est captivante, incluant des options de paris sportifs dynamiques. Il booste votre aventure des le depart. Disponible a toute heure via chat ou email. Les paiements sont surs et fluides, par moments des offres plus importantes seraient super. Au final, Coolzino Casino est un must pour les passionnes. A noter la navigation est claire et rapide, incite a rester plus longtemps. A signaler les transactions en crypto fiables, cree une communaute soudee.
DГ©couvrir le contenu|
В Красноярске клиника «КрасЗдрав Профи» предоставляет круглосуточную помощь людям, столкнувшимся с зависимостью. При этом формат анонимности сохраняется на каждом этапе — от звонка до выписки. Для пациентов, которым трудно приехать, возможен выезд нарколога на дом. Это удобно при похмельных и абстинентных состояниях, когда транспортировка нежелательна. Конфиденциальный выезд без маркировки транспорта и униформы позволяет начать лечение, не привлекая внимания окружающих. Все процедуры проводятся с соблюдением медицинских стандартов, включая регидратацию, стабилизацию и поддержку дыхания.
Изучить вопрос глубже – лечение в наркологической клинике в красноярске
Врач оценивает состояние пациента, измеряет давление, пульс, сатурацию, уровень сахара в крови и собирает анамнез. Это помогает выявить возможные риски и подобрать подходящие препараты.
Углубиться в тему – vyvod-iz-zapoya-himki
Такой подход обеспечивает результативность и помогает добиться длительной ремиссии даже при тяжёлых формах зависимости.
Получить дополнительную информацию – http://narkologicheskaya-clinica-v-voronezhe17.ru/narkolog-voronezh-anonimno/
Иногда приоритетом становится непрерывный контроль. Стационар рекомендован, если ожидаются выраженные колебания давления и пульса, есть подозрение на аритмии, отмечается одышка, боли в груди, спутанность сознания, галлюцинации, судороги, признаки начинающегося делирия, а также выраженная дегидратация или декомпенсация хронических заболеваний. Для пожилых пациентов без возможности надёжного домашнего наблюдения отделение — клинически разумный выбор: доступны лабораторные тесты, кислородная поддержка, быстрая коррекция дозировок и консилиумы смежных специалистов. Именно в первые 24–48 часов после отмены алкоголя стационарный режим делает процесс предсказуемым и безопасным, что сокращает время до стабилизации и открывает окно для обсуждения амбулаторного сопровождения, психологической поддержки и мер профилактики срывов без давления и спешки.
Разобраться лучше – vyvod-iz-zapoya-lyubertsy2.ru/
Первая задача при выезде — быстро отделить угрозы от симптомов, которые можно безопасно стабилизировать на дому. Таблица ниже иллюстрирует, как стартовые наблюдения превращаются в проверяемые гипотезы, конкретные действия и решения в «окнах оценки». Она не заменяет очной диагностики, а объясняет архитектуру первых часов, чтобы у семьи был ясный ориентир.
Выяснить больше – https://narkolog-na-dom-v-krasnodare16.ru/narkolog-i-psikhiatr-v-krasnodare/
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Получить дополнительные сведения – https://vivod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-narkolog-na-dom-volgograd/
Клиника использует многоступенчатый подход, который позволяет адаптировать лечение под особенности организма пациента. Наблюдение продолжается даже после завершения детоксикации, чтобы убедиться, что состояние стабильно и не требуется дополнительное вмешательство. При необходимости врач назначает курс поддержки печени, витаминов и препаратов для восстановления сна и психоэмоционального равновесия.
Узнать больше – https://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-staczionar-voronezh
При резком прекращении употребления алкоголь перестаёт подавлять нервную систему, и она начинает работать с перегрузкой. Это вызывает тремор, тревожность, бессонницу, боли в сердце и головокружение. В домашних условиях контролировать эти процессы невозможно. Поэтому медицинское вмешательство необходимо не только для облегчения симптомов, но и для предотвращения опасных осложнений.
Исследовать вопрос подробнее – narkolog-vyvod-iz-zapoya
Врач оценивает состояние пациента, измеряет давление, пульс, сатурацию, уровень сахара в крови и собирает анамнез. Это помогает выявить возможные риски и подобрать подходящие препараты.
Углубиться в тему – скорая вывод из запоя
Для иллюстрации приведена таблица, отражающая распространённые методы терапии и их воздействие на организм:
Получить дополнительные сведения – наркологическая клиника нарколог в воронеже
Je suis sous le charme de Coolzino Casino, on y trouve une energie contagieuse. Il y a un eventail de titres captivants, incluant des paris sportifs pleins de vie. Avec des depots fluides. Le support est pro et accueillant. Les paiements sont securises et instantanes, occasionnellement des offres plus genereuses rendraient l’experience meilleure. En resume, Coolzino Casino est une plateforme qui fait vibrer. Ajoutons que le site est rapide et immersif, apporte une touche d’excitation. Particulierement fun le programme VIP avec des recompenses exclusives, offre des bonus exclusifs.
AccГ©der maintenant|
Je suis totalement conquis par MonteCryptos Casino, ca offre un plaisir vibrant. La selection de jeux est impressionnante, proposant des jeux de cartes elegants. Il amplifie le plaisir des l’entree. Le support est efficace et amical. Les gains sont verses sans attendre, toutefois plus de promos regulieres dynamiseraient le jeu. Dans l’ensemble, MonteCryptos Casino est une plateforme qui fait vibrer. En complement l’interface est lisse et agreable, apporte une touche d’excitation. Egalement excellent les tournois reguliers pour la competition, offre des recompenses regulieres.
https://montecryptoscasino365fr.com/|
Je suis enthousiaste a propos de Lucky8 Casino, il offre une experience dynamique. Il y a une abondance de jeux excitants, incluant des options de paris sportifs dynamiques. Le bonus de depart est top. Le support est fiable et reactif. Les transactions sont fiables et efficaces, cependant des bonus plus frequents seraient un hit. En bref, Lucky8 Casino offre une aventure inoubliable. A noter le site est fluide et attractif, facilite une experience immersive. Egalement genial les paiements en crypto rapides et surs, propose des avantages uniques.
Trouver les dГ©tails|
J’adore le dynamisme de MonteCryptos Casino, il offre une experience dynamique. Les options de jeu sont infinies, offrant des sessions live palpitantes. 100% jusqu’a 500 € plus des tours gratuits. Disponible a toute heure via chat ou email. Les retraits sont lisses comme jamais, en revanche quelques spins gratuits en plus seraient top. Dans l’ensemble, MonteCryptos Casino offre une aventure memorable. Pour completer le site est rapide et style, ajoute une vibe electrisante. Un bonus les transactions en crypto fiables, qui booste la participation.
AccГ©der Г la page|
J’adore l’ambiance electrisante de Lucky8 Casino, il cree un monde de sensations fortes. Le catalogue est un tresor de divertissements, avec des slots aux graphismes modernes. 100% jusqu’a 500 € plus des tours gratuits. Les agents sont toujours la pour aider. Les paiements sont surs et fluides, en revanche quelques free spins en plus seraient bienvenus. Pour conclure, Lucky8 Casino assure un fun constant. Pour couronner le tout la navigation est claire et rapide, ce qui rend chaque partie plus fun. Un point cle les evenements communautaires pleins d’energie, propose des privileges personnalises.
Voir maintenant|
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Получить дополнительные сведения – скорая наркологическая помощь
Наркологическая помощь в Волгограде предназначена для людей, столкнувшихся с проблемами алкогольной или наркотической зависимости. Современный подход к лечению основан на сочетании медицинских, психологических и социальных методов, направленных на полное восстановление пациента. Врачи-наркологи применяют безопасные схемы детоксикации, эффективные медикаменты и программы психотерапевтической поддержки, позволяющие достичь устойчивой ремиссии и вернуть пациента к нормальной жизни.
Изучить вопрос глубже – https://narkologicheskaya-pomoshh-v-volgograde17.ru/narkologi-volgograd
Je suis totalement conquis par Lucky8 Casino, ca invite a plonger dans le fun. Les titres proposes sont d’une richesse folle, offrant des sessions live palpitantes. Il booste votre aventure des le depart. Disponible a toute heure via chat ou email. Les retraits sont fluides et rapides, neanmoins quelques free spins en plus seraient bienvenus. En somme, Lucky8 Casino offre une aventure memorable. Notons aussi la plateforme est visuellement captivante, facilite une immersion totale. Un atout les tournois frequents pour l’adrenaline, offre des bonus constants.
DГ©couvrir davantage|
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Получить больше информации – https://narkologicheskaya-klinika-v-volgograde17.ru/chastnaya-narkologicheskaya-klinika-volgograd
J’adore la vibe de NetBet Casino, ca transporte dans un univers de plaisirs. On trouve une profusion de jeux palpitants, proposant des jeux de casino traditionnels. Avec des transactions rapides. Le service client est excellent. Les retraits sont ultra-rapides, cependant plus de promotions variees ajouteraient du fun. Globalement, NetBet Casino est une plateforme qui fait vibrer. Pour couronner le tout le site est rapide et style, ce qui rend chaque partie plus fun. Un element fort les paiements securises en crypto, qui booste la participation.
Continuer Г lire|
Главное преимущество обращения в наркологическую клинику в Воронеже — комплексный подход к лечению зависимости. Специалисты учитывают медицинские, психологические и социальные факторы, влияющие на формирование зависимости. Каждая программа подбирается индивидуально: в зависимости от стадии заболевания, состояния здоровья и целей терапии. В процессе лечения применяются детоксикация, медикаментозная поддержка, психотерапия и методы социальной адаптации.
Выяснить больше – https://narkologicheskaya-clinica-v-voronezhe17.ru/voronezh-narkologicheskij-dispanser
Капельница от запоя в Воронеже применяется для восстановления организма после длительного употребления алкоголя, устранения интоксикации и нормализации обменных процессов. Медицинская процедура проводится под контролем врача-нарколога, в клинике или на дому. Она позволяет быстро улучшить самочувствие, устранить головную боль, тремор, тошноту, обезвоживание и нарушения сна. Современные препараты действуют мягко, безопасно и без стресса для организма, обеспечивая плавный выход из запоя.
Изучить вопрос глубже – врача капельницу от запоя воронеж
Процедура начинается с обследования пациента: врач измеряет давление, частоту пульса, оценивает степень интоксикации и состояние внутренних органов. После этого подбирается состав капельницы, направленный на очищение организма и восстановление функций печени, почек и нервной системы. Все препараты вводятся внутривенно, что обеспечивает быстрый эффект и минимизирует нагрузку на желудочно-кишечный тракт.
Подробнее тут – http://vyvod-iz-zapoya-v-tyumeni17.ru/vyvod-iz-zapoya-v-staczionare-tyumen/
Иногда приоритетом становится непрерывный контроль. Стационар рекомендован, если ожидаются выраженные колебания давления и пульса, есть подозрение на аритмии, отмечается одышка, боли в груди, спутанность сознания, галлюцинации, судороги, признаки начинающегося делирия, а также выраженная дегидратация или декомпенсация хронических заболеваний. Для пожилых пациентов без возможности надёжного домашнего наблюдения отделение — клинически разумный выбор: доступны лабораторные тесты, кислородная поддержка, быстрая коррекция дозировок и консилиумы смежных специалистов. Именно в первые 24–48 часов после отмены алкоголя стационарный режим делает процесс предсказуемым и безопасным, что сокращает время до стабилизации и открывает окно для обсуждения амбулаторного сопровождения, психологической поддержки и мер профилактики срывов без давления и спешки.
Выяснить больше – vyvod iz zapoya cena
При резком прекращении употребления алкоголь перестаёт подавлять нервную систему, и она начинает работать с перегрузкой. Это вызывает тремор, тревожность, бессонницу, боли в сердце и головокружение. В домашних условиях контролировать эти процессы невозможно. Поэтому медицинское вмешательство необходимо не только для облегчения симптомов, но и для предотвращения опасных осложнений.
Узнать больше – вывод из запоя недорого
Основу лечения составляет междисциплинарная команда: врач-нарколог, психиатр, психолог, медсестра и консультант по зависимому поведению. Каждый отвечает за свой участок работы, но общая цель едина — помочь пациенту безопасно пройти путь от детокса до устойчивого состояния. Благодаря единому плану и регулярным консилиумам врачей, исключаются противоречия и дублирование процедур. Это экономит ресурсы организма и делает процесс прогнозируемым.
Подробнее можно узнать тут – лечение в наркологической клинике в красноярске
При резком прекращении употребления алкоголь перестаёт подавлять нервную систему, и она начинает работать с перегрузкой. Это вызывает тремор, тревожность, бессонницу, боли в сердце и головокружение. В домашних условиях контролировать эти процессы невозможно. Поэтому медицинское вмешательство необходимо не только для облегчения симптомов, но и для предотвращения опасных осложнений.
Подробнее тут – pomoshch-vyvod-iz-zapoya
Процедура проводится как в стационаре, так и на дому. Врач приезжает по вызову, проводит осмотр и измеряет давление, пульс, насыщение кислородом. После оценки состояния подбирается состав капельницы и начинается инфузионная терапия. В среднем процедура длится от 40 минут до 1,5 часов, в зависимости от степени интоксикации. По завершении врач наблюдает за реакцией организма и даёт рекомендации по восстановлению.
Изучить вопрос глубже – капельница от запоя недорого
Такой состав обеспечивает быстрое снятие симптомов интоксикации и восстановление функций организма после запоя.
Получить дополнительные сведения – сколько стоит капельница на дому от запоя
Чтобы не оценивать состояние субъективно, в клинике применяется система наблюдения за ключевыми параметрами. Таблица помогает врачу и пациенту видеть реальную динамику и корректировать вмешательства только при необходимости.
Подробнее можно узнать тут – http://narkologicheskaya-clinica-v-krasnoyarske17.ru
Наркологическая помощь в Волгограде предназначена для людей, столкнувшихся с проблемами алкогольной или наркотической зависимости. Современный подход к лечению основан на сочетании медицинских, психологических и социальных методов, направленных на полное восстановление пациента. Врачи-наркологи применяют безопасные схемы детоксикации, эффективные медикаменты и программы психотерапевтической поддержки, позволяющие достичь устойчивой ремиссии и вернуть пациента к нормальной жизни.
Разобраться лучше – https://narkologicheskaya-pomoshh-v-volgograde17.ru/narkolog-psikholog-volgograd/
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Выяснить больше – скорая вывод из запоя
Наркологическая клиника в Воронеже — это специализированное медицинское учреждение, предоставляющее помощь людям, столкнувшимся с зависимостью от алкоголя, наркотиков и других психоактивных веществ. Лечение проводится под контролем квалифицированных врачей, с использованием современных методик детоксикации, психотерапии и реабилитации. Цель работы специалистов — не только устранить физическую зависимость, но и помочь пациенту восстановить эмоциональное равновесие, вернуть контроль над поведением и мотивацию к трезвости.
Разобраться лучше – наркологическая клиника наркологический центр в воронеже
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Выяснить больше – бесплатное кодирование от алкоголизма в волгограде
Не всегда человек способен самостоятельно прекратить приём алкоголя и восстановиться. Есть состояния, требующие немедленного вмешательства специалистов. Обратиться за помощью необходимо, если наблюдаются следующие признаки:
Подробнее – вывод из запоя на дому в волгограде
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Детальнее – https://narkologicheskaya-pomoshh-v-volgograde17.ru/narkologicheskaya-klinika-v-volgograde/
Клиника предлагает широкий спектр медицинских и психологических услуг, направленных на восстановление пациента после зависимости. Все процедуры проходят под контролем врачей и с соблюдением анонимности. Наиболее востребованные направления представлены ниже:
Получить дополнительную информацию – наркологическая клиника воронеж
Вызов нарколога на дом — это не «универсальная капельница», а управляемая последовательность маленьких шагов с понятными целями и точками проверки. В наркологической клинике «КубаньМед Резолюция» выезд врача, инфузионная поддержка и лечение зависимостей складываются в дорожную карту: мы начинаем с короткого триежа, формулируем рабочую гипотезу, включаем минимально достаточный модуль, назначаем «окно оценки» и только затем либо выключаем модуль, либо изменяем одну переменную. Такой подход снижает фармаконагрузку, предотвращает полипрагмазыю и делает динамику прозрачной: пациент и семья видят, что именно помогает и когда вмешательство завершается.
Детальнее – вызвать нарколога на дом срочно
Пациенты отмечают, что особенно важна не только профессиональная помощь, но и спокойная атмосфера. Мягкий свет, тишина, отдельные палаты и деликатная коммуникация персонала — всё это снижает тревожность и помогает организму восстановиться. Эффективность лечения оценивается по конкретным маркерам: улучшение сна, нормализация давления, исчезновение тошноты, восстановление аппетита и уменьшение тяги.
Выяснить больше – http://narkologicheskaya-clinica-v-krasnoyarske17.ru
Мы переводим субъективные ощущения в простые маркеры, чтобы решения не зависели от настроения и ожиданий. Базовый набор: объём выпитой воды в час; ЧСС/АД в покое; длительность сна и число пробуждений; шкалы тошноты/тремора/тревоги; две утренние бытовые задачи. В отчёте фиксируется, какой модуль включён, какой маркер он должен сдвинуть, в каком окне мы проверяем результат и при каком значении модуль выключается. Это защищает от «инерции лечения» и делает финансовую часть предсказуемой: расширения назначаются только по показаниям с указанием цели и времени переоценки.
Получить дополнительные сведения – https://narkolog-na-dom-v-krasnodare16.ru/narkologa-na-dom-krasnodar
Чтобы не оценивать состояние субъективно, в клинике применяется система наблюдения за ключевыми параметрами. Таблица помогает врачу и пациенту видеть реальную динамику и корректировать вмешательства только при необходимости.
Выяснить больше – наркологические клиники алкоголизм в красноярске
В повседневности неточный ориентир часто заставляет терять время, поэтому мы проговариваем симптомы, при которых тянуть нельзя. Список не заменяет осмотр, он помогает близким описать ситуацию по телефону и выбрать правильный маршрут вместе с врачом.
Разобраться лучше – вывод из запоя люберцы
Ниже представлена таблица, отражающая основные направления медикаментозного лечения и сопутствующих процедур:
Получить дополнительные сведения – http://www.domen.ru
Наши специалисты используют проверенные и сертифицированные медикаменты, которые подбираются индивидуально для каждого пациента:
Подробнее можно узнать тут – капельница от запоя цена нижний новгород.
J’ai une affection particuliere pour Coolzino Casino, ca invite a plonger dans le fun. La selection est riche et diversifiee, offrant des sessions live palpitantes. Il propulse votre jeu des le debut. Le suivi est toujours au top. Les retraits sont fluides et rapides, quelquefois plus de promos regulieres ajouteraient du peps. Au final, Coolzino Casino offre une experience hors du commun. Pour couronner le tout le site est rapide et style, booste le fun du jeu. Un point cle les transactions crypto ultra-securisees, qui dynamise l’engagement.
Lancer le site|
рулонные шторы в москве рулонные шторы в москве .
Терапия проводится поэтапно, что позволяет пациенту последовательно проходить все стадии восстановления и закреплять результат.
Получить дополнительную информацию – http://lechenie-alkogolizma-omsk0.ru
После поступления звонка нарколог оперативно выезжает по указанному адресу и прибывает в течение 30–60 минут. Врач незамедлительно приступает к оказанию помощи по четко отработанному алгоритму, состоящему из следующих этапов:
Исследовать вопрос подробнее – вызвать нарколога на дом
По окончании курса детоксикации нарколог дает пациенту и его близким подробные рекомендации, помогающие быстрее восстановить здоровье и предотвратить повторные случаи запоев.
Углубиться в тему – наркология вывод из запоя
Такая структура делает лечение последовательным и предсказуемым, повышая шансы на положительный исход.
Углубиться в тему – наркологическая клиника цены
Такая структура позволяет обеспечить эффективность и безопасность лечения на каждом этапе.
Подробнее тут – вывод из запоя клиника в перми
Для наглядности приведена таблица с основными направлениями терапии и их результатами:
Подробнее можно узнать тут – частная наркологическая клиника воронеж
Решение о месте лечения принимает врач после очной оценки, ориентируясь на клинику и бытовые условия. Домашний формат ценят за комфорт и конфиденциальность, а стационар незаменим, когда требуется частая коррекция терапии и круглосуточный мониторинг. Чтобы проще сориентироваться, полезно посмотреть на различия между форматами не как на «два вида капельниц», а как на разные уровни контроля и скорости реакций команды. Текст ниже помогает понять, почему при пограничных состояниях мы рекомендуем стационар, а при стабильных показателях — подтверждаем выезд на дом. Любой маршрут объясняется до старта, и каждое расширение терапии согласуется заранее — без сюрпризов в процессе.
Подробнее можно узнать тут – http://www.domen.ru
Домашний визит нарколога — это формат, который соединяет клиническую безопасность и человеческую деликатность. В «КубаньМедЦентре» (Краснодар) мы организуем помощь так, чтобы пациент получал её там, где ему спокойнее всего — у себя дома. Дежурная команда работает круглосуточно, а среднее окно прибытия по городу составляет 30–40 минут с момента подтверждения заявки. Врач приезжает без опознавательных знаков, проводит экспресс-оценку состояния, запускает индивидуально подобранную инфузионную терапию и оставляет подробный план на ближайшие 72 часа. Каждый шаг объясняется простым языком: что мы делаем, зачем это нужно и по каким критериям поймём, что динамика идёт правильно.
Подробнее тут – частный нарколог на дом в краснодаре
Современная наркологическая клиника — это не просто медицинское учреждение, а пространство комплексной помощи, где врачи помогают человеку восстановиться физически, психологически и социально. В клинике «РязаньМед Альянс» создана система непрерывного наблюдения, включающая диагностику, выведение из запоя, детоксикацию, кодирование и постреабилитационную поддержку. Здесь работают квалифицированные наркологи, психиатры и терапевты, а помощь оказывается круглосуточно — как в стационаре, так и на дому. Главная цель специалистов — вернуть пациенту контроль над своим состоянием и избавить от зависимости без стресса и боли.
Получить дополнительную информацию – запой наркологическая клиника рязань
Абстиненция — не «плохое утро», а физиологический кризис, когда нервная и сердечно-сосудистая системы работают на пределе, а печень и почки берут на себя чрезмерную детоксикационную нагрузку. Самолечение случайными таблетками или «домашними капельницами» часто усиливает обезвоживание, провоцирует скачки давления, аритмии, панические эпизоды и нарушения сна. В клинической практике «ВитаБаланс» первым этапом идет скрининг безопасности: врач исключает ситуации, требующие стационара, и только после этого запускает инфузию. Правильно подобранные растворы выравнивают электролитный баланс, уменьшают тремор и тошноту, снижают тревожность, а мягкая седация по показаниям помогает восстановить здоровую структуру сна без угнетения дыхания. Параллельно контролируются витальные параметры, чтобы вовремя скорректировать объем и скорость введения. Такой маршрут делает первые сутки предсказуемыми, позволяет избежать осложнений и быстрее вернуть ясность мышления, аппетит и базовую работоспособность.
Изучить вопрос глубже – vyvod-iz-zapoya-s-vyezdom-cena
Эта последовательность помогает эффективно воздействовать на зависимость и исключает вероятность усугубления состояния.
Подробнее можно узнать тут – лечение алкоголизма в стационаре пермь
Наркологическая клиника в Перми обеспечивает пациентам комфортные условия и профессиональное сопровождение. Врачи работают круглосуточно и соблюдают строгую конфиденциальность, что делает лечение доступным и безопасным.
Детальнее – лечение в наркологической клинике пермь
J’adore l’ambiance electrisante de Coolzino Casino, ca transporte dans un univers de plaisirs. On trouve une gamme de jeux eblouissante, incluant des options de paris sportifs dynamiques. Avec des depots rapides et faciles. Le service client est excellent. Les gains sont transferes rapidement, mais encore plus de promos regulieres ajouteraient du peps. Dans l’ensemble, Coolzino Casino est un immanquable pour les amateurs. Pour ajouter la navigation est claire et rapide, ce qui rend chaque moment plus vibrant. Egalement excellent les transactions crypto ultra-securisees, offre des recompenses regulieres.
Lire plus|
J’adore l’energie de Coolzino Casino, il cree une experience captivante. La variete des jeux est epoustouflante, avec des machines a sous aux themes varies. Avec des depots rapides et faciles. Les agents repondent avec efficacite. Les gains arrivent en un eclair, occasionnellement des bonus plus frequents seraient un hit. En conclusion, Coolzino Casino est une plateforme qui pulse. Ajoutons que l’interface est lisse et agreable, booste le fun du jeu. Un element fort les options de paris sportifs diversifiees, cree une communaute vibrante.
Aller en ligne|
J’ai une affection particuliere pour MonteCryptos Casino, ca transporte dans un univers de plaisirs. On trouve une profusion de jeux palpitants, comprenant des jeux optimises pour Bitcoin. Il donne un elan excitant. Les agents repondent avec rapidite. Les transactions sont toujours securisees, par contre des bonus diversifies seraient un atout. Dans l’ensemble, MonteCryptos Casino vaut une visite excitante. Ajoutons aussi le site est rapide et engageant, donne envie de continuer l’aventure. Un atout les tournois reguliers pour la competition, offre des bonus exclusifs.
Cliquer maintenant|
Je suis completement seduit par Lucky8 Casino, ca offre une experience immersive. La selection est riche et diversifiee, incluant des options de paris sportifs dynamiques. 100% jusqu’a 500 € avec des free spins. Le service d’assistance est au point. Les transactions sont toujours fiables, en revanche quelques tours gratuits supplementaires seraient cool. En bref, Lucky8 Casino assure un fun constant. A noter la plateforme est visuellement electrisante, incite a prolonger le plaisir. Un bonus les paiements en crypto rapides et surs, qui dynamise l’engagement.
Aller au site|
J’ai un faible pour Lucky8 Casino, ca offre une experience immersive. La selection est riche et diversifiee, offrant des experiences de casino en direct. 100% jusqu’a 500 € avec des spins gratuits. Le service client est de qualite. Les paiements sont securises et rapides, quelquefois plus de promos regulieres ajouteraient du peps. Au final, Lucky8 Casino est un choix parfait pour les joueurs. En complement le design est moderne et energique, booste le fun du jeu. Un atout le programme VIP avec des avantages uniques, qui booste la participation.
Parcourir maintenant|
J’adore l’energie de Lucky8 Casino, c’est une plateforme qui deborde de dynamisme. On trouve une profusion de jeux palpitants, incluant des options de paris sportifs dynamiques. Avec des transactions rapides. Le support est pro et accueillant. Les gains arrivent en un eclair, de temps en temps des bonus plus frequents seraient un hit. En fin de compte, Lucky8 Casino est un incontournable pour les joueurs. En bonus la navigation est fluide et facile, incite a rester plus longtemps. A signaler les paiements en crypto rapides et surs, propose des privileges sur mesure.
Obtenir plus|
J’ai un veritable coup de c?ur pour NetBet Casino, ca transporte dans un monde d’excitation. Les titres proposes sont d’une richesse folle, incluant des options de paris sportifs dynamiques. Il booste votre aventure des le depart. Le support client est irreprochable. Le processus est fluide et intuitif, en revanche plus de promotions variees ajouteraient du fun. Pour conclure, NetBet Casino assure un fun constant. A noter l’interface est fluide comme une soiree, ce qui rend chaque session plus excitante. A signaler les nombreuses options de paris sportifs, renforce le lien communautaire.
En savoir davantage|
J’ai une passion debordante pour NetBet Casino, on ressent une ambiance de fete. Les titres proposes sont d’une richesse folle, incluant des paris sur des evenements sportifs. 100% jusqu’a 500 € avec des free spins. Disponible 24/7 par chat ou email. Les paiements sont securises et rapides, neanmoins des bonus plus frequents seraient un hit. Pour finir, NetBet Casino est une plateforme qui fait vibrer. En plus l’interface est lisse et agreable, booste le fun du jeu. Particulierement attrayant les tournois reguliers pour s’amuser, offre des bonus constants.
DГ©couvrir le web|
Улучшайте свои навыки и повышайте квалификацию с помощью курсы по seo и станьте профессионалами в области поисковой оптимизации!
помочь участникам овладеть навыками поисковой оптимизации . Эти курсы обычно включают в себя лекции по созданию качественного контента и его продвижению. В результате прохождения таких курсов, участники смогут освоить методы анализа и улучшения позиций сайта в поисковых системах.
Участники SEO курсов могут изучить вопросы внутренней и внешней оптимизации сайтов . Это может включать в себя изучение методов создания ссылок и их влияния на рейтинг сайта . После завершения курса, участники могут применять полученные знания на практике, оптимизируя свои собственные сайты .
В рамках SEO курсов, учащиеся могут приобрести практический опыт в оптимизации сайтов, включая работу с ключевыми словами и метатегами . Это может включать в себя работу над индивидуальными проектами, направленными на оптимизацию реальных сайтов. Благодаря такому подходу, учащиеся могут овладеть всеми аспектами SEO, от технической оптимизации до создания контента .
Практические занятия в SEO курсах могут включать в себя создание и продвижение сайтов, оптимизацию контента и работу с ссылками . Это дает участникам возможность освоить навыки, необходимые для успешной карьеры в digital-агентствах . После завершения курса, участники могут применять полученные знания и навыки для оптимизации своих собственных сайтов или для работы в качестве SEO-специалистов .
Теоретические основы SEO включают в себя понимание работы поисковых алгоритмов и факторов, влияющих на рейтинг сайта . Эти знания необходимы для понимания того, как создавать эффективные кампании в интернете . Теоретические основы могут включать в себя освоение методов оптимизации сайтов для различных поисковых систем.
Изучение теоретических основ SEO может предоставить знания о том, как создавать эффективные кампании в интернете. Это может включать в себя изучение роли ключевых слов в поисковой оптимизации и методов их выбора . Благодаря такому подходу, участники могут развить навыки, необходимые для того, чтобы стать профессионалом в области поисковой оптимизации.
SEO курсы могут помочь участникам овладеть навыками поисковой оптимизации и продвижения сайтов . Это может включать в себя работу над индивидуальными проектами, направленными на оптимизацию реальных сайтов. Участники могут приобрести практический опыт в оптимизации сайтов, включая работу с ключевыми словами и метатегами .
Применение SEO в реальной практике может предполагать участие в групповых проектах, где участники смогут применить полученные знания на практике. Это дает участникам возможность освоить навыки, необходимые для успешной карьеры в digital-агентствах . После завершения курса, участники могут применять полученные знания и навыки для оптимизации своих собственных сайтов или для работы в качестве SEO-специалистов .
Инфузионная терапия (капельницы) — важная часть лечения, направленная на очищение организма, восстановление водно-солевого баланса и устранение токсинов. В «РязаньМед Альянс» используются проверенные препараты, которые помогают нормализовать работу внутренних органов и улучшить общее самочувствие. Таблица ниже показывает, какие виды капельниц чаще всего применяются при выведении из запоя и лечении алкоголизма.
Получить дополнительную информацию – наркологическая клиника лечение алкоголизма рязань
Терапия проводится поэтапно, что позволяет пациенту последовательно проходить все стадии восстановления и закреплять результат.
Подробнее – http://www.domen.ru
Параметр
Выяснить больше – vyvod-iz-zapoya-kruglosutochno
Клиника предлагает широкий спектр медицинских и психологических услуг, направленных на восстановление пациента после зависимости. Все процедуры проходят под контролем врачей и с соблюдением анонимности. Наиболее востребованные направления представлены ниже:
Детальнее – http://narkologicheskaya-clinica-v-voronezhe17.ru
Группа препаратов
Детальнее – http://kapelnica-ot-zapoya-nizhniy-novgorod00.ru/vyzvat-kapelniczu-ot-zapoya-nizhnij-novgorod/
Современная наркологическая клиника — это не просто медицинское учреждение, а пространство комплексной помощи, где врачи помогают человеку восстановиться физически, психологически и социально. В клинике «РязаньМед Альянс» создана система непрерывного наблюдения, включающая диагностику, выведение из запоя, детоксикацию, кодирование и постреабилитационную поддержку. Здесь работают квалифицированные наркологи, психиатры и терапевты, а помощь оказывается круглосуточно — как в стационаре, так и на дому. Главная цель специалистов — вернуть пациенту контроль над своим состоянием и избавить от зависимости без стресса и боли.
Изучить вопрос глубже – https://narkologicheskaya-klinika-v-ryazani17.ru/narkologiya-v-ryazani/
Инфузионная терапия (капельницы) — важная часть лечения, направленная на очищение организма, восстановление водно-солевого баланса и устранение токсинов. В «РязаньМед Альянс» используются проверенные препараты, которые помогают нормализовать работу внутренних органов и улучшить общее самочувствие. Таблица ниже показывает, какие виды капельниц чаще всего применяются при выведении из запоя и лечении алкоголизма.
Ознакомиться с деталями – частная наркологическая клиника рязань
дизайн интерьера 3д дизайн интерьера онлайн
жалюзи с электроприводом жалюзи с электроприводом .
управление шторами с телефона управление шторами с телефона .
Ниже представлена таблица, отражающая основные направления медикаментозного лечения и сопутствующих процедур:
Ознакомиться с деталями – https://narkologicheskaya-klinika-omsk0.ru/narkologiya-kruglosutochno-omsk
В процессе лечения используются проверенные методики, которые в комплексе обеспечивают положительный эффект и снижают риск рецидива.
Разобраться лучше – лечение алкоголизма в стационаре
Такая комплексность обеспечивает воздействие на физические, психологические и социальные факторы зависимости.
Получить больше информации – лечение алкоголизма кодирование в омске
Стационар рационален там, где домашний формат не обеспечивает нужного уровня наблюдения. Речь о выраженных колебаниях давления и пульса, подозрении на опасные аритмии, нарастающей одышке, болях в груди, признаках делирия, галлюцинациях, судорогах, выраженной дегидратации, а также о случаях декомпенсации хронических заболеваний и пожилом возрасте при отсутствии надежного домашнего наблюдения. В палате доступны лабораторная оценка электролитов и гемодинамики, кислородная поддержка, аппаратный мониторинг и консилиумы смежных специалистов. Это делает первые 24–48 часов управляемыми: терапия настраивается без задержек, а риски осложнений сокращаются. После стабилизации пациент переходит на амбулаторное сопровождение — консультации нарколога, поддерживающую фармакотерапию и, по желанию, работу с психотерапевтом, — чтобы закрепить результат и уменьшить вероятность срыва.
Получить дополнительные сведения – вывод из запоя вызов на дом
По окончании курса детоксикации нарколог дает пациенту и его близким подробные рекомендации, помогающие быстрее восстановить здоровье и предотвратить повторные случаи запоев.
Детальнее – http://vyvod-iz-zapoya-novosibirsk0.ru/
Такая структура делает лечение последовательным и предсказуемым, повышая шансы на положительный исход.
Подробнее – вывод наркологическая клиника
Đến với J88, bạn sẽ được trải nghiệm dịch vụ cá cược chuyên nghiệp cùng hàng ngàn sự kiện khuyến mãi độc quyền.
студия семейного дизайна интерьера лучший дизайн интерьера спб
При обращении в клинику «НаркоНет» пациенту предоставляется полный спектр мероприятий, направленных на восстановление организма после запоя. Сначала наш специалист приезжает на дом в течение 30–60 минут после вызова. На месте проводится детальный осмотр: измеряются основные жизненные показатели (давление, пульс, уровень кислорода в крови), собирается подробный анамнез и оценивается степень интоксикации. Полученные данные позволяют врачу разработать индивидуальный план лечения.
Подробнее – http://
При абстиненции нервная и сердечно-сосудистая системы работают на пределе, баланс нейромедиаторов смещён, кровь «теряет» воду и электролиты, а печень несёт повышенную нагрузку. Резкая отмена алкоголя без врача нередко приводит к скачкам давления, аритмиям, паническим эпизодам, нарушению сна и даже делирию. Домашние «самосборные» растворы и случайные комбинации таблеток усугубляют обезвоживание и не учитывают противопоказания — в итоге риски растут, а эффект непредсказуем. В «СфераЗдоровья» путь другой: сначала скрининг безопасности и исключение состояний, при которых показан стационар; далее — персональная инфузионная схема с регидратацией, коррекцией электролитов, поддержкой печени и симптом-контролем (тошнота, тремор, тревога, бессонница). На каждом этапе врач отслеживает динамику и корректирует дозы «по реакции», чтобы не перегрузить сердце и почки. Результат — более мягкий выход из абстиненции, прозрачные ожидания для пациента и близких и понятный план на ближайшие 24–48 часов.
Исследовать вопрос подробнее – вывод из запоя с выездом
Вывод из запоя в клинике проводится поэтапно, что позволяет обеспечить прозрачность процесса и полное понимание динамики выздоровления.
Подробнее тут – вывод из запоя круглосуточно в омске
Инфузионная терапия (капельницы) — важная часть лечения, направленная на очищение организма, восстановление водно-солевого баланса и устранение токсинов. В «РязаньМед Альянс» используются проверенные препараты, которые помогают нормализовать работу внутренних органов и улучшить общее самочувствие. Таблица ниже показывает, какие виды капельниц чаще всего применяются при выведении из запоя и лечении алкоголизма.
Изучить вопрос глубже – наркологическая клиника цены рязань
Вывод из запоя в Перми включает использование комплекса медикаментозных и психотерапевтических методик. Они помогают не только снять симптомы интоксикации, но и стабилизировать эмоциональное состояние.
Ознакомиться с деталями – срочный вывод из запоя пермь
Инфузионная схема собирается под конкретного человека: регидратация, электролитная коррекция, поддержка печени, противорвотные и анксиолитики по показаниям. При нарушенном сне применяется бережная седация. Врач динамически корректирует скорость и состав по реакции организма, предотвращая перегрузки и побочные эффекты. Уже во время процедуры уменьшаются тремор и тревога, проясняется мышление.
Ознакомиться с деталями – https://vyvod-iz-zapoya-ehlektrostal3.ru/vyvesti-iz-zapoya-elektrostal
Стационар рационален там, где домашний формат не обеспечивает нужного уровня наблюдения. Речь о выраженных колебаниях давления и пульса, подозрении на опасные аритмии, нарастающей одышке, болях в груди, признаках делирия, галлюцинациях, судорогах, выраженной дегидратации, а также о случаях декомпенсации хронических заболеваний и пожилом возрасте при отсутствии надежного домашнего наблюдения. В палате доступны лабораторная оценка электролитов и гемодинамики, кислородная поддержка, аппаратный мониторинг и консилиумы смежных специалистов. Это делает первые 24–48 часов управляемыми: терапия настраивается без задержек, а риски осложнений сокращаются. После стабилизации пациент переходит на амбулаторное сопровождение — консультации нарколога, поддерживающую фармакотерапию и, по желанию, работу с психотерапевтом, — чтобы закрепить результат и уменьшить вероятность срыва.
Получить больше информации – срочный вывод из запоя
Клиника предлагает широкий спектр медицинских и психологических услуг, направленных на восстановление пациента после зависимости. Все процедуры проходят под контролем врачей и с соблюдением анонимности. Наиболее востребованные направления представлены ниже:
Получить дополнительную информацию – наркологические клиники алкоголизм воронеж
Не стоит медлить с вызовом врача-нарколога, если у человека проявляются тревожные признаки ухудшения состояния. Среди наиболее серьезных симптомов, требующих немедленного вмешательства врача, можно выделить продолжительный запой (более двух дней подряд), частую рвоту, невыносимую головную боль, выраженный тремор рук и тела, повышение артериального давления, нарушение ритма сердца, а также психические нарушения, включая тревогу, галлюцинации и бессонницу. Чем раньше пациент обратится за профессиональной помощью, тем выше шансы избежать серьезных осложнений и быстро вернуться к нормальной жизни.
Получить дополнительные сведения – вывод из запоя клиника новосибирск
Длительное и бесконтрольное употребление алкоголя может привести к состоянию запоя — опасному и тяжелому состоянию, при котором человек не способен самостоятельно отказаться от спиртного. Во время запоя организм постепенно накапливает токсины, что негативно сказывается на работе всех внутренних органов и систем. В таких случаях пациенту необходима экстренная врачебная помощь, и специалисты наркологической клиники «АнтиТокс» готовы оперативно оказать профессиональную медицинскую поддержку на дому в Новосибирске.
Исследовать вопрос подробнее – вывод из запоя в стационаре в новосибирске
Терапия в клинике проводится поэтапно, что позволяет обеспечить безопасность и прозрачность процесса. Пациент постепенно проходит все стадии восстановления организма и психики.
Разобраться лучше – вывод наркологическая клиника омск
Терапия в клинике проводится поэтапно, что позволяет обеспечить безопасность и прозрачность процесса. Пациент постепенно проходит все стадии восстановления организма и психики.
Изучить вопрос глубже – https://narkologicheskaya-klinika-v-omske0.ru/narkolog-v-gorode-omske/
После обращения пациента в клинику «НаркоЩит» наш специалист выезжает на дом в течение 30–60 минут. По прибытии врач проводит подробный осмотр: измеряет артериальное давление, пульс и уровень кислорода в крови, а также собирает анамнез, чтобы оценить степень интоксикации и тяжесть запоя. На основе полученной информации формируется индивидуальный план лечения.
Разобраться лучше – капельница от запоя цена в нижний новгороде
Стоимость услуг по установке капельницы определяется индивидуально и зависит от нескольких факторов. В первую очередь, цена обусловлена тяжестью состояния пациента: при более сильной интоксикации и выраженных симптомах абстинентного синдрома может потребоваться расширенная терапия. Кроме того, итоговая сумма зависит от продолжительности запоя, так как длительное употребление спиртного ведет к более серьезному накоплению токсинов, требующему дополнительных лечебных мероприятий.
Подробнее – https://kapelnica-ot-zapoya-nizhniy-novgorod000.ru/kapelnicza-ot-zapoya-czena-nizhnij-novgorod/
Терапия проводится поэтапно, что позволяет пациенту последовательно проходить все стадии восстановления и закреплять результат.
Углубиться в тему – наркологическое лечение алкоголизма
Комплексное применение этих методов позволяет добиться быстрого восстановления организма и улучшения психоэмоционального состояния.
Разобраться лучше – вывод из запоя цена
Такая структура позволяет обеспечить эффективность и безопасность лечения на каждом этапе.
Получить больше информации – вывод из запоя на дому круглосуточно в перми
kuwin sở hữu kho game đa dạng từ slot đến trò chơi bài đổi thưởng, mang đến cho bạn những giây phút giải trí tuyệt vời.
Каждый этап играет важную роль и обеспечивает пациенту необходимую поддержку на пути к трезвой жизни.
Получить больше информации – лечение алкоголизма в стационаре в омске
Стационар рационален там, где домашний формат не обеспечивает нужного уровня наблюдения. Речь о выраженных колебаниях давления и пульса, подозрении на опасные аритмии, нарастающей одышке, болях в груди, признаках делирия, галлюцинациях, судорогах, выраженной дегидратации, а также о случаях декомпенсации хронических заболеваний и пожилом возрасте при отсутствии надежного домашнего наблюдения. В палате доступны лабораторная оценка электролитов и гемодинамики, кислородная поддержка, аппаратный мониторинг и консилиумы смежных специалистов. Это делает первые 24–48 часов управляемыми: терапия настраивается без задержек, а риски осложнений сокращаются. После стабилизации пациент переходит на амбулаторное сопровождение — консультации нарколога, поддерживающую фармакотерапию и, по желанию, работу с психотерапевтом, — чтобы закрепить результат и уменьшить вероятность срыва.
Изучить вопрос глубже – vyvod-iz-zapoya
Наркологическая клиника в Омске оказывает квалифицированную помощь пациентам, страдающим от различных видов зависимости. Основой успешного лечения является комплексный подход, который включает тщательную диагностику, медикаментозное сопровождение, психологическую поддержку и реабилитационные программы. В «АльфаМед» применяются передовые технологии и индивидуальные методики, направленные на восстановление здоровья и предупреждение рецидивов.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-omsk0.ru/chastnaya-narkologicheskaya-klinika-omsk
Нарколог устанавливает внутривенную капельницу, через которую вводятся растворы, обеспечивающие быстрое выведение токсинов, восстановление водно-электролитного баланса и стабилизацию состояния.
Получить дополнительные сведения – вызвать нарколога на дом в воронеже
На выходе пациент получает письменные рекомендации на 24–48 часов: питьевой режим, щадящее питание, самоконтроль давления, запрет на самостоятельный прием незнакомых препаратов и «красные флаги» для повторной связи. Команда остается на контакте, чтобы пройти первые сутки максимально спокойно.
Разобраться лучше – http://vyvod-iz-zapoya-ehlektrostal3.ru
После поступления звонка специалисты нашей клиники оперативно выезжают по адресу пациента в Новосибирске. Врач начинает работу с детальной диагностики: измеряет пульс, артериальное давление, сатурацию (уровень кислорода в крови), оценивает состояние нервной и сердечно-сосудистой систем, уточняет наличие хронических заболеваний, аллергических реакций, длительность и тяжесть запоя.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-novosibirsk0.ru
Наблюдение
Получить дополнительные сведения – https://vyvod-iz-zapoya-domodedovo3.ru/vyvedenie-iz-zapoya-na-domu-domodedovo/
После поступления звонка специалисты нашей клиники оперативно выезжают по адресу пациента в Новосибирске. Врач начинает работу с детальной диагностики: измеряет пульс, артериальное давление, сатурацию (уровень кислорода в крови), оценивает состояние нервной и сердечно-сосудистой систем, уточняет наличие хронических заболеваний, аллергических реакций, длительность и тяжесть запоя.
Углубиться в тему – vyvod-iz-zapoya-czena novosibirsk
Каждое из этих направлений имеет важное значение и в совокупности формирует основу для устойчивого выздоровления.
Ознакомиться с деталями – запой наркологическая клиника омск
Применение комплексной терапии позволяет не только устранить зависимость, но и сформировать новые поведенческие установки, предотвращающие возвращение к употреблению.
Разобраться лучше – http://narkologicheskaya-clinica-v-voronezhe17.ru/narkolog-voronezh-anonimno/
Каждое из этих направлений имеет важное значение и в совокупности формирует основу для устойчивого выздоровления.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-v-omske0.ru/narkologicheskaya-bolnicza-omsk/
Наблюдение
Подробнее – http://vyvod-iz-zapoya-domodedovo3.ru/vyvedenie-iz-zapoya-na-domu-domodedovo/
Основная терапия заключается в установке внутривенной капельницы, через которую вводятся специально подобранные растворы. Эти препараты помогают быстро вывести токсины, восстановить водно-электролитный баланс и нормализовать работу внутренних органов. При необходимости врач может дополнительно назначить медикаменты для поддержки печени, стабилизации сердечной деятельности и купирования симптомов абстинентного синдрома. По завершении процедуры специалист предоставляет рекомендации по дальнейшему восстановлению и профилактике повторных эпизодов зависимости.
Узнать больше – капельница от запоя выезд в нижний новгороде
Наркологическая клиника в Воронеже — это специализированное медицинское учреждение, предоставляющее помощь людям, столкнувшимся с зависимостью от алкоголя, наркотиков и других психоактивных веществ. Лечение проводится под контролем квалифицированных врачей, с использованием современных методик детоксикации, психотерапии и реабилитации. Цель работы специалистов — не только устранить физическую зависимость, но и помочь пациенту восстановить эмоциональное равновесие, вернуть контроль над поведением и мотивацию к трезвости.
Подробнее тут – лечение в наркологической клинике
вавада украина — это актуальное зеркало для доступа к популярному онлайн-казино.
Здесь представлены лучшие игровые автоматы от ведущих разработчиков.
Сайт отличается удобным интерфейсом и быстрой работой. Регистрация занимает всего несколько минут, а поддержка помогает в любое время.
#### Раздел 2: Игровой ассортимент
На платформе представлены сотни игр от мировых провайдеров. Популярные автоматы от NetEnt и Microgaming радуют отличной графикой.
Особого внимания заслуживают джекпоты и турниры. Ежедневные розыгрыши привлекают тысячи участников.
#### Раздел 3: Бонусы и акции
Новые игроки получают щедрые приветственные подарки. Вращения в слотах дарятся без обязательных вложений.
Система лояльности поощряет постоянных клиентов. Чем чаще вы играете, тем выше становятся бонусы.
#### Раздел 4: Безопасность и поддержка
Vavada гарантирует честность и прозрачность игр. Все автоматы проходят проверку на случайность генерации чисел.
Служба поддержки работает в режиме 24/7. Решение любых вопросов занимает минимум времени.
### Спин-шаблон
#### Раздел 1: Введение в мир Vavada
1. Vavada Casinos — это популярная онлайн-платформа для азартных игр.
2. Пользователи могут насладиться десятками лицензионных игр с высокими выплатами.
3. Платформа радует пользователей простой навигацией и стабильной работой.
4. vavadacasinos.neocities.org доступен круглосуточно с любых устройств.
#### Раздел 2: Игровой ассортимент
1. На платформе представлены сотни игр от мировых провайдеров.
2. Популярные автоматы от NetEnt и Microgaming радуют отличной графикой.
3. Прогрессивные джекпоты делают игру еще более интересной.
4. Специальные акции увеличивают шансы на победу.
#### Раздел 3: Бонусы и акции
1. Каждый новичок может рассчитывать на дополнительные фриспины.
2. Бонусы начисляются как за регистрацию, так и за активность.
3. Система лояльности поощряет постоянных клиентов.
4. Кешбэк и эксклюзивные предложения доступны для VIP-игроков.
#### Раздел 4: Безопасность и поддержка
1. Vavada гарантирует честность и прозрачность игр.
2. Все автоматы проходят проверку на случайность генерации чисел.
3. Любые вопросы решаются оперативно и профессионально.
4. Решение любых вопросов занимает минимум времени.
Выделяется ряд преимуществ, которые делают терапию в клинике оптимальным решением для борьбы с зависимостью.
Разобраться лучше – https://lechenie-alkogolizma-perm0.ru/lechenie-alkogolizma-perm-besplatno
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Узнать больше – http://vivod-iz-zapoya-rostov14.ru/vyvod-iz-zapoya-na-domu-rostov-na-donu/https://vivod-iz-zapoya-rostov14.ru
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Выяснить больше – частная наркологическая клиника
вавада казино украина — это актуальное зеркало для доступа к популярному онлайн-казино.
Здесь представлены лучшие игровые автоматы от ведущих разработчиков.
Сайт отличается удобным интерфейсом и быстрой работой. Игроки могут зайти на платформу как с компьютера, так и со смартфона.
#### Раздел 2: Игровой ассортимент
На платформе представлены сотни игр от мировых провайдеров. Каждый игрок найдет вариант по вкусу — от блекджека до современных видео-слотов.
Особого внимания заслуживают джекпоты и турниры. Специальные акции увеличивают шансы на победу.
#### Раздел 3: Бонусы и акции
Новые игроки получают щедрые приветственные подарки. Вращения в слотах дарятся без обязательных вложений.
Система лояльности поощряет постоянных клиентов. Чем чаще вы играете, тем выше становятся бонусы.
#### Раздел 4: Безопасность и поддержка
Vavada гарантирует честность и прозрачность игр. Вывод средств происходит быстро и без скрытых комиссий.
Служба поддержки работает в режиме 24/7. Решение любых вопросов занимает минимум времени.
### Спин-шаблон
#### Раздел 1: Введение в мир Vavada
1. Vavada Casinos — это популярная онлайн-платформа для азартных игр.
2. Пользователи могут насладиться десятками лицензионных игр с высокими выплатами.
3. Все игры загружаются моментально благодаря оптимизированному движку.
4. Игроки могут зайти на платформу как с компьютера, так и со смартфона.
#### Раздел 2: Игровой ассортимент
1. На платформе представлены сотни игр от мировых провайдеров.
2. Здесь есть классические слоты, настольные игры и live-дилеры.
3. Крупные розыгрыши привлекают внимание тысяч участников.
4. Ежедневные розыгрыши привлекают тысячи участников.
#### Раздел 3: Бонусы и акции
1. Новые игроки получают щедрые приветственные подарки.
2. Первый депозит может быть увеличен на 100% или более.
3. VIP-игроки получают персональные предложения.
4. Еженедельные турниры с призовыми фондами добавляют азарта.
#### Раздел 4: Безопасность и поддержка
1. Vavada гарантирует честность и прозрачность игр.
2. Все автоматы проходят проверку на случайность генерации чисел.
3. Любые вопросы решаются оперативно и профессионально.
4. Игроки могут связаться с поддержкой через email или мессенджеры.
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее тут – врач нарколог выезд на дом
Маршрут помощи строится вокруг конкретных задач безопасности. С первого звонка администратор собирает короткий чек-лист: длительность нынешнего эпизода, что принималось в последние двое суток, хронические заболевания, аллергии, как прошла ночь, есть ли помощник на вечер и ночь. Дежурный врач, опираясь на эти данные, предлагает стартовый формат — выезд на дом по Воскресенску и району или немедленную госпитализацию. Решение привязывается к реальным рискам: стабильность давления и пульса, выраженность тремора и тошноты, эпизоды судорог в прошлом, возможность обеспечить «тихий режим» в квартире. После очной оценки и допуска к терапии мы запускаем детокс, а по завершении визита фиксируем правила на 24–48 часов и контрольные точки. Если состояние колеблется, сразу обсуждаем повторный контакт либо перевод в стационар, не теряя часы на бюрократию.
Углубиться в тему – http://www.domen.ru
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Изучить вопрос глубже – врач нарколог выезд на дом
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Разобраться лучше – http://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-anonimno-v-sergievom-posade/
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Получить дополнительные сведения – анонимный вывод из запоя рязань
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Подробнее – платная наркологическая клиника санкт-петербург
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Ознакомиться с деталями – врач нарколог
Каждый из методов подбирается индивидуально, что позволяет учитывать медицинские показания и личные особенности пациента.
Узнать больше – https://lechenie-alkogolizma-perm0.ru/lechenie-alkogolizma-perm-besplatno
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Узнать больше – вывод из запоя вызов на дом рязань
Ключевая идея «ДонЗдрава» — соединить доказательную медицину и понятную пациенту логистику. Инфузии рассчитываются через инфузомат, жизненные показатели контролируются портативным кардиомонитором и пульсоксиметром, а лекарственные взаимодействия проверяются по протоколу перед началом терапии. При этом каждый шаг объясняется простым языком: что делаем, зачем это нужно и как будем оценивать результат через 30, 60 и 120 минут. После визита пациент не остаётся один — доступна «горячая линия» и короткие онлайн-сессии с врачом либо психологом, если тревога или бессонница возвращаются в ночные часы.
Получить дополнительную информацию – вывод из запоя на дому ростов-на-дону
Мы держим баланс между недостаточным и избыточным лечением. С одной стороны, не пропускаем опасные признаки, с другой — избегаем седативной перегрузки и сомнительных «коктейлей». Состав капельницы и темп введения зависят от давления и пульса, выраженности тревоги и тошноты, сопутствующих диагнозов и лекарств, уже попавших в организм. Каждое назначение объясняется простыми словами, чтобы пациент и семья понимали, как действует схема и зачем нужны ограничения ближайших дней.
Разобраться лучше – наркологическая клиника московская московская область
мелбет сайт https://www.v-bux.ru .
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Ознакомиться с деталями – наркологическая клиника клиника помощь санкт-петербург
Цель
Подробнее – воскресенск наркологический диспансер
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Получить дополнительные сведения – http://narkologicheskaya-klinika-voskresensk8.ru
Перед перечнем поясним логику: домашний визит уместен, когда обстановка безопасна, риски контролируемы и есть взрослый помощник на вечер и ночь. Ниже — ориентиры, при которых имеет смысл начать с выезда, а не со стационара.
Исследовать вопрос подробнее – https://narkolog-na-dom-voskresensk8.ru/psihiatr-narkolog-na-dom-v-voskresenske/
Домашний формат уменьшает стресс и экономит время: не нужно ехать в клинику, скрывать визит от соседей или ждать в очереди. Врач приезжает без опознавательных знаков и не создаёт «медицинского шума». За один визит удаётся снять острые проявления, выстроить понятный план ночи и следующего утра, а также определить, нужна ли дополнительная диагностика. Такой маршрут часто оказывается короче и эффективнее, чем череда попыток «пересидеть» симптомы без медицинской поддержки.
Узнать больше – http://narkolog-na-dom-voskresensk8.ru
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Ознакомиться с деталями – https://vyvod-iz-zapoya-ryazan14.ru/vyvod-iz-zapoya-na-domu-ryazan-czeny/
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Подробнее тут – http://narkologicheskaya-klinika-v-spb14.ru/narkologicheskaya-bolnicza-sankt-peterburg/
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Подробнее тут – запой наркологическая клиника санкт-петербург
Нарколог на дом в Санкт-Петербурге — это востребованная медицинская услуга, позволяющая получить помощь в комфортных домашних условиях. Такой формат особенно актуален в ситуациях, когда пациент не может или не хочет обращаться в стационар. Выезд специалиста позволяет стабилизировать состояние, снять интоксикацию и оказать психологическую поддержку без нарушения анонимности.
Узнать больше – нарколог на дом клиника санкт-петербург
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Узнать больше – http://narkolog-na-dom-voskresensk8.ru/psihiatr-narkolog-na-dom-v-voskresenske/
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Выяснить больше – наркологический вывод из запоя рязань
Цель
Получить дополнительную информацию – narkolog-i-psihiatr-voskresensk
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Получить дополнительную информацию – наркология вывод из запоя в рязани
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить дополнительные сведения – https://vyvod-iz-zapoya-v-ryazani14.ru/vykhod-iz-zapoya-ryazan
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-sergiev-posad8.ru
Конфиденциальность — не обещание на бумаге, а практический стандарт. В клинике используются кодовые профили, шифрованный контур хранения карт, разграничение доступа по ролям; документы оформляются нейтрально, а уведомления формулируются без чувствительных слов. Выездные специалисты приезжают без медицинской символики, а в здании клиники навигация организована так, чтобы перемещение было незаметным. Это создаёт пространство, в котором можно честно говорить о целях и спокойно выполнять план — без стигмы и посторонних взглядов.
Разобраться лучше – наркологическая клиника лечение алкоголизма
Петербургский темп жизни — поздняя занятость, переменная нагрузка, сезонные перепады света — усложняет восстановление после эпизодов употребления. Поэтому мы разработали модульные программы, способные гибко подстраиваться под график и биоритмы: у кого-то «трудные часы» приходятся на поздний вечер на Васильевском острове, у кого-то — на раннее утро перед сменой в Адмиралтейском районе. Маршрут строится вокруг человека, а не вокруг расписания кабинета: очные приёмы, немаркированные выезды на дом, дневной стационар, защищённые онлайн-сессии — всё объединено единым клиническим планом и общими целями.
Изучить вопрос глубже – наркологическая клиника нарколог в санкт-петербурге
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Ознакомиться с деталями – https://narkologicheskaya-klinika-voskresensk8.ru/telefon-narkologicheskoj-klinikia-v-voskresenske
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Детальнее – выезд нарколога на дом краснодар
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Изучить вопрос глубже – вывод из запоя дешево
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Выяснить больше – нарколог на дом вывод из запоя в рязани
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Получить дополнительную информацию – государственная наркологическая клиника
Алкогольный запой приводит к тяжёлой интоксикации, при которой организм теряет способность к самостоятельному восстановлению. Вывод из запоя в клинике предполагает использование инфузионной терапии, медикаментов для нормализации работы сердца, печени и нервной системы, а также витаминных комплексов для восполнения дефицита питательных веществ.
Исследовать вопрос подробнее – нарколог вывод из запоя рязань
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Получить дополнительную информацию – нарколог на дом срочно в санкт-петербурге
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Углубиться в тему – https://narkologicheskaya-klinika-voskresensk8.ru/telefon-narkologicheskoj-klinikia-v-voskresenske
Алкогольный запой приводит к тяжёлой интоксикации, при которой организм теряет способность к самостоятельному восстановлению. Вывод из запоя в клинике предполагает использование инфузионной терапии, медикаментов для нормализации работы сердца, печени и нервной системы, а также витаминных комплексов для восполнения дефицита питательных веществ.
Получить дополнительную информацию – вывод из запоя на дому недорого в рязани
Стационар — это управляемая среда, где меньше случайностей и больше возможностей действовать на опережение. Под одной крышей — приём и допуск к терапии, инфузионный блок, аппаратный контроль, лаборатория и ЭКГ по показаниям, пост медсестёр и регулярная переоценка состояния. Такой контур особенно важен при давних запойных эпизодах, гипертонии, ишемической болезни сердца, сахарном диабете, гастроэнтерологических проблемах: правильно настроенный темп инфузий и «бережные» назначения уменьшают риск осложнений и снимают «эффект качелей» в первые сутки.
Получить дополнительную информацию – https://narkologicheskaya-klinika-voskresensk8.ru/telefon-narkologicheskoj-klinikia-v-voskresenske
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Подробнее можно узнать тут – наркологическая клиника
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Изучить вопрос глубже – наркологическая клиника справка
Петербургский темп жизни — поздняя занятость, переменная нагрузка, сезонные перепады света — усложняет восстановление после эпизодов употребления. Поэтому мы разработали модульные программы, способные гибко подстраиваться под график и биоритмы: у кого-то «трудные часы» приходятся на поздний вечер на Васильевском острове, у кого-то — на раннее утро перед сменой в Адмиралтейском районе. Маршрут строится вокруг человека, а не вокруг расписания кабинета: очные приёмы, немаркированные выезды на дом, дневной стационар, защищённые онлайн-сессии — всё объединено единым клиническим планом и общими целями.
Изучить вопрос глубже – наркологическая клиника вывод из запоя санкт-петербург
Домашний формат выбирают, когда обстановка позволяет провести лечение в тишине и нет признаков угрозы жизни. Врач приезжает без опознавательных знаков, начинает с очной оценки и допуска к инфузии, сверяет принятые ранее препараты и аллергии, объясняет ожидаемую динамику. После запуска капельницы мягко корректируются жидкость и электролиты, проводится симптом-контроль (тремор, тошнота, тревога, головная боль), по показаниям — осторожная нормализация сна. На выходе пациент и семья получают понятные рекомендации на 24–48 часов: питьевой режим, питание, ограничения по нагрузкам, признаки тревоги и правила связи с дежурным врачом.
Подробнее можно узнать тут – наркологический вывод из запоя
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Ознакомиться с деталями – анонимная наркологическая клиника
Планируя [url=https://pereezd-kvartiry-msk.ru/]переезд квартиры с грузчиками[/url], вы можете значительно упростить этот процесс, воспользовавшись услугами профессионалов.
Помощь друзей или родных может значительно облегчить процесс
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-v-ryazani14.ru/vyvod-iz-zapoya-ryazan-na-domu/
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Ознакомиться с деталями – https://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Ознакомиться с деталями – наркологическая клиника московская московская область
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить дополнительную информацию – вывод из запоя вызов на дом рязань
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Подробнее – https://narkologicheskaya-klinika-sankt-peterburg14.ru
Формат лечения
Подробнее тут – http://
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Изучить вопрос глубже – воскресенская клиника
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Углубиться в тему – http://narkologicheskaya-klinika-sankt-peterburg14.ru/klinika-narkologii-spb/
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Подробнее тут – https://narkologicheskaya-klinika-voskresensk8.ru/psihiatricheskaya-narkologicheskaya-klinika-v-voskresenske
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Углубиться в тему – http://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg/https://narkologicheskaya-klinika-sankt-peterburg14.ru
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Узнать больше – платный нарколог на дом санкт-петербург
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Углубиться в тему – https://narkologicheskaya-klinika-voskresensk8.ru/psihiatricheskaya-narkologicheskaya-klinika-v-voskresenske/
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Получить дополнительную информацию – http://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-anonimno-v-sergievom-posade/
Домашний формат уместен, когда нет признаков угрозы жизни, а дома можно сохранить тишину и наблюдение ночью. Врач приезжает без опознавательных знаков, начинает с очной оценки рисков и сверки уже принятых препаратов, объясняет ожидаемую динамику и запускает инфузионную терапию. Мы мягко корректируем водно-электролитный баланс, даём поддержку печени и вегетативной нервной системе, по показаниям осторожно нормализуем сон. На руки выдаём памятку на ближайшие сутки-двое: питьевой режим, питание, алгоритм отхода ко сну, признаки тревоги, порядок связи с дежурным врачом. Такой визит «гасит» острые проявления и возвращает предсказуемость ночи без лишней огласки для соседей.
Углубиться в тему – voskresenskaya-klinika
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Получить дополнительную информацию – нарколог на дом клиника в санкт-петербурге
Формат лечения
Получить дополнительную информацию – https://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg/
Стационар мы предлагаем, когда дома нет условий для ночного наблюдения, симптомы тяжёлые или прогноз нестабилен. В палате — контролируемая среда, возможность оперативно выполнить ЭКГ и базовые анализы по показаниям, круглосуточный пост. Команда корректирует схему лечения в реальном времени, не теряя часы на логистику. Это особенно важно при давних запоях, риске делирия, выраженных колебаниях давления, сахарном диабете, ИБС, заболеваниях ЖКТ.
Получить дополнительные сведения – https://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-klinika-v-sergievom-posade
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Выяснить больше – platnaya-narkologicheskaya-klinika
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Детальнее – platnaya-narkologicheskaya-klinika
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Выяснить больше – нарколог на дом клиника краснодар
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Подробнее тут – http://narkolog-na-dom-sankt-peterburg14.ru
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-sergiev-posad8.ru
Домашний формат уменьшает стресс и экономит время: не нужно ехать в клинику, скрывать визит от соседей или ждать в очереди. Врач приезжает без опознавательных знаков и не создаёт «медицинского шума». За один визит удаётся снять острые проявления, выстроить понятный план ночи и следующего утра, а также определить, нужна ли дополнительная диагностика. Такой маршрут часто оказывается короче и эффективнее, чем череда попыток «пересидеть» симптомы без медицинской поддержки.
Ознакомиться с деталями – narkologicheskij-dispanser-voskresenskoe
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Подробнее тут – запой нарколог на дом
Одна и та же «капельница на всех» не работает: у одних доминирует обезвоживание, у других — тахикардия и тревога, у третьих — желудочные симптомы и нагрузка на печень. Ниже — ориентиры по выбору инфузионных схем и целей вмешательства; окончательный состав подбирается врачом исходя из клинической картины и сопутствующих заболеваний.
Ознакомиться с деталями – http://vivod-iz-zapoya-rostov14.ru
Главное — непрерывность и скорость принятия решений. Рядом врач и медсестра, доступ к диагностике и возможность точно настраивать темп инфузий, подбирать поддерживающие препараты, контролировать сон и уровень тревоги. Благодаря этому снижается риск осложнений, а восстановление идёт ровнее: меньше «качелей» днём и ночью.
Детальнее – http://vyvod-iz-zapoya-sergiev-posad8.ru
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Получить дополнительные сведения – помощь нарколога на дому
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Подробнее – наркологическая клиника справка
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Исследовать вопрос подробнее – наркологическая клиника нарколог в санкт-петербурге
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Разобраться лучше – http://vyvod-iz-zapoya-sergiev-posad8.ru
При выезде врач действует по установленному протоколу, что гарантирует безопасность и эффективность процедуры.
Углубиться в тему – врач нарколог выезд на дом
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Получить больше информации – врач нарколог выезд на дом
Перед перечнем поясним логику: домашний визит уместен, когда обстановка безопасна, риски контролируемы и есть взрослый помощник на вечер и ночь. Ниже — ориентиры, при которых имеет смысл начать с выезда, а не со стационара.
Разобраться лучше – https://narkolog-na-dom-voskresensk8.ru/narkolog-na-dom-nedorogo-v-voskresenske/
Этот комплекс мер позволяет оказывать помощь пациентам на всех стадиях зависимости.
Получить дополнительную информацию – http://narkologicheskaya-klinika-sankt-peterburg14.ru/
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Ознакомиться с деталями – врач нарколог выезд на дом в краснодаре
Главное — непрерывность и скорость принятия решений. Рядом врач и медсестра, доступ к диагностике и возможность точно настраивать темп инфузий, подбирать поддерживающие препараты, контролировать сон и уровень тревоги. Благодаря этому снижается риск осложнений, а восстановление идёт ровнее: меньше «качелей» днём и ночью.
Детальнее – https://vyvod-iz-zapoya-sergiev-posad8.ru/srochnyj-vyvod-iz-zapoya-v-sergievom-posade
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Получить больше информации – наркологические клиники алкоголизм
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Ознакомиться с деталями – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-na-dom-anonimno-spb/
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Получить больше информации – врач нарколог выезд на дом в краснодаре
Домашний формат уменьшает стресс и экономит время: не нужно ехать в клинику, скрывать визит от соседей или ждать в очереди. Врач приезжает без опознавательных знаков и не создаёт «медицинского шума». За один визит удаётся снять острые проявления, выстроить понятный план ночи и следующего утра, а также определить, нужна ли дополнительная диагностика. Такой маршрут часто оказывается короче и эффективнее, чем череда попыток «пересидеть» симптомы без медицинской поддержки.
Выяснить больше – narkolog-na-dom-voskresensk8.ru/
Цель
Ознакомиться с деталями – вызов нарколога на дом воскресенск
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Выяснить больше – вывод из запоя на дому круглосуточно ростов-на-дону
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Углубиться в тему – вывод из запоя цена
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Получить дополнительную информацию – https://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg/
Чтобы снизить тревогу и обеспечить предсказуемость, «ДонЗдрав» придерживается пошагового протокола. Он гибкий, но обязательно включает триаж, диагностику, старт инфузии и выдачу письменного плана. Переход между этапами происходит только при достижении понятных критериев безопасности — мы фиксируем их вместе с пациентом и родственниками.
Получить дополнительные сведения – вывод из запоя в ростове-на-дону
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Получить больше информации – https://narkologicheskaya-klinika-sankt-peterburg14.ru
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Ознакомиться с деталями – анонимная наркологическая клиника в санкт-петербурге
Домашний визит нарколога — это формат, который соединяет клиническую безопасность и человеческую деликатность. В «КубаньМедЦентре» (Краснодар) мы организуем помощь так, чтобы пациент получал её там, где ему спокойнее всего — у себя дома. Дежурная команда работает круглосуточно, а среднее окно прибытия по городу составляет 30–40 минут с момента подтверждения заявки. Врач приезжает без опознавательных знаков, проводит экспресс-оценку состояния, запускает индивидуально подобранную инфузионную терапию и оставляет подробный план на ближайшие 72 часа. Каждый шаг объясняется простым языком: что мы делаем, зачем это нужно и по каким критериям поймём, что динамика идёт правильно.
Подробнее – психиатр нарколог на дом в краснодаре
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Детальнее – https://narkolog-na-dom-voskresensk8.ru/vyzov-narkologa-na-dom-v-voskresenske
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Подробнее тут – http://vyvod-iz-zapoya-sergiev-posad8.ru
Цель
Исследовать вопрос подробнее – narkolog-na-dom-voskresensk8.ru/
Цель
Детальнее – нарколог и психиатр воскресенск
Маршрут помощи строится вокруг конкретных задач безопасности. С первого звонка администратор собирает короткий чек-лист: длительность нынешнего эпизода, что принималось в последние двое суток, хронические заболевания, аллергии, как прошла ночь, есть ли помощник на вечер и ночь. Дежурный врач, опираясь на эти данные, предлагает стартовый формат — выезд на дом по Воскресенску и району или немедленную госпитализацию. Решение привязывается к реальным рискам: стабильность давления и пульса, выраженность тремора и тошноты, эпизоды судорог в прошлом, возможность обеспечить «тихий режим» в квартире. После очной оценки и допуска к терапии мы запускаем детокс, а по завершении визита фиксируем правила на 24–48 часов и контрольные точки. Если состояние колеблется, сразу обсуждаем повторный контакт либо перевод в стационар, не теряя часы на бюрократию.
Получить больше информации – https://narkologicheskaya-klinika-voskresensk8.ru/psihiatricheskaya-narkologicheskaya-klinika-v-voskresenske
При выезде врач действует по установленному протоколу, что гарантирует безопасность и эффективность процедуры.
Получить больше информации – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-na-dom-anonimno-spb
Для купирования абстинентного синдрома и снятия интоксикации используются различные подходы. Врачи подбирают их индивидуально, исходя из состояния пациента.
Подробнее – помощь вывод из запоя рязань
Howdy! Would you mind if I share your blog with my twitter group? There’s a lot of people that I think would really enjoy your content. Please let me know. Thank you
Brasilia independent escorts
Đến với J88, bạn sẽ được trải nghiệm dịch vụ cá cược chuyên nghiệp cùng hàng ngàn sự kiện khuyến mãi độc quyền.
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Подробнее можно узнать тут – narkologicheskaya-klinika
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Подробнее можно узнать тут – domashnij-vyvod-iz-zapoya
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Получить дополнительные сведения – частная наркологическая клиника санкт-петербург
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Ознакомиться с деталями – нарколог на дом санкт-петербург
Домашний формат выбирают, когда обстановка позволяет провести лечение в тишине и нет признаков угрозы жизни. Врач приезжает без опознавательных знаков, начинает с очной оценки и допуска к инфузии, сверяет принятые ранее препараты и аллергии, объясняет ожидаемую динамику. После запуска капельницы мягко корректируются жидкость и электролиты, проводится симптом-контроль (тремор, тошнота, тревога, головная боль), по показаниям — осторожная нормализация сна. На выходе пациент и семья получают понятные рекомендации на 24–48 часов: питьевой режим, питание, ограничения по нагрузкам, признаки тревоги и правила связи с дежурным врачом.
Получить больше информации – вывод из запоя в домашних условиях
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Выяснить больше – наркологическая клиника наркологический центр санкт-петербург
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее тут – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-na-dom-anonimno-spb
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Подробнее тут – https://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare/
Маршрут помощи строится вокруг конкретных задач безопасности. С первого звонка администратор собирает короткий чек-лист: длительность нынешнего эпизода, что принималось в последние двое суток, хронические заболевания, аллергии, как прошла ночь, есть ли помощник на вечер и ночь. Дежурный врач, опираясь на эти данные, предлагает стартовый формат — выезд на дом по Воскресенску и району или немедленную госпитализацию. Решение привязывается к реальным рискам: стабильность давления и пульса, выраженность тремора и тошноты, эпизоды судорог в прошлом, возможность обеспечить «тихий режим» в квартире. После очной оценки и допуска к терапии мы запускаем детокс, а по завершении визита фиксируем правила на 24–48 часов и контрольные точки. Если состояние колеблется, сразу обсуждаем повторный контакт либо перевод в стационар, не теряя часы на бюрократию.
Подробнее можно узнать тут – платная наркологическая клиника
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Подробнее можно узнать тут – vyvod-iz-zapoya
Алкогольный запой приводит к тяжёлой интоксикации, при которой организм теряет способность к самостоятельному восстановлению. Вывод из запоя в клинике предполагает использование инфузионной терапии, медикаментов для нормализации работы сердца, печени и нервной системы, а также витаминных комплексов для восполнения дефицита питательных веществ.
Подробнее можно узнать тут – вывод из запоя капельница рязань
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить дополнительную информацию – анонимный вывод из запоя
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Детальнее – наркологическая клиника в санкт-петербурге
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Ознакомиться с деталями – нарколог на дом вывод из запоя санкт-петербург
Стационар мы предлагаем, когда дома нет условий для ночного наблюдения, симптомы тяжёлые или прогноз нестабилен. В палате — контролируемая среда, возможность оперативно выполнить ЭКГ и базовые анализы по показаниям, круглосуточный пост. Команда корректирует схему лечения в реальном времени, не теряя часы на логистику. Это особенно важно при давних запоях, риске делирия, выраженных колебаниях давления, сахарном диабете, ИБС, заболеваниях ЖКТ.
Детальнее – https://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-anonimno-v-sergievom-posade
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Ознакомиться с деталями – narkologicheskaya-klinika-vyvod-iz-zapoya
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Ознакомиться с деталями – врач нарколог на дом в краснодаре
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Углубиться в тему – voskresenskaya-klinika
Excellent, what a blog it is! This web site presents helpful facts to us, keep it up.
https://floristua.com.ua/sklo-fary-chevrolet-tahoe-typovi-prychyny.html
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Узнать больше – врач нарколог на дом санкт-петербург
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Подробнее тут – вывод из запоя
Комплексное применение этих средств ускоряет процесс восстановления.
Получить дополнительные сведения – https://narkolog-na-dom-sankt-peterburg14.ru/
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Подробнее – https://vivod-iz-zapoya-rostov14.ru
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Исследовать вопрос подробнее – государственная наркологическая клиника
Стандартизированный алгоритм позволяет действовать быстро и безопасно. Он гибко настраивается под конкретный случай, но всегда включает триаж, экспресс-диагностику, старт инфузии, симптом-менеджмент и выдачу плана на 72 часа с «коридорами безопасности».
Узнать больше – вызвать нарколога на дом срочно
Перед началом терапии важно оценить состояние пациента и выявить сопутствующие заболевания. После этого назначается комплексное лечение, которое позволяет восстановить здоровье и подготовить к дальнейшей реабилитации.
Углубиться в тему – http://vyvod-iz-zapoya-ryazan14.ru/vyvod-iz-zapoya-ryazan-na-domu/https://vyvod-iz-zapoya-ryazan14.ru
Перед началом терапии важно оценить состояние пациента и выявить сопутствующие заболевания. После этого назначается комплексное лечение, которое позволяет восстановить здоровье и подготовить к дальнейшей реабилитации.
Подробнее можно узнать тут – срочный вывод из запоя рязань
Маршрут помощи строится вокруг конкретных задач безопасности. С первого звонка администратор собирает короткий чек-лист: длительность нынешнего эпизода, что принималось в последние двое суток, хронические заболевания, аллергии, как прошла ночь, есть ли помощник на вечер и ночь. Дежурный врач, опираясь на эти данные, предлагает стартовый формат — выезд на дом по Воскресенску и району или немедленную госпитализацию. Решение привязывается к реальным рискам: стабильность давления и пульса, выраженность тремора и тошноты, эпизоды судорог в прошлом, возможность обеспечить «тихий режим» в квартире. После очной оценки и допуска к терапии мы запускаем детокс, а по завершении визита фиксируем правила на 24–48 часов и контрольные точки. Если состояние колеблется, сразу обсуждаем повторный контакт либо перевод в стационар, не теряя часы на бюрократию.
Подробнее – platnaya-narkologicheskaya-klinika
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Детальнее – наркологическая клиника вывод из запоя санкт-петербург
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Углубиться в тему – наркологическая клиника нарколог
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Изучить вопрос глубже – http://vivod-iz-zapoya-rostov14.ru
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить дополнительную информацию – наркологический вывод из запоя
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Детальнее – нарколог на дом клиника краснодар
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Детальнее – narkologicheskaya-klinika
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Ознакомиться с деталями – vyvod-iz-alkogolnogo-zapoya-v-domashnih-usloviyah
chicken road игра перейди дорогу http://www.kurica2.ru/ru .
написать курсовую на заказ kupit-kursovuyu-1.ru .
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Подробнее тут – врач нарколог выезд на дом
В условиях медицинского контроля специалисты выполняют последовательные действия, направленные на стабилизацию состояния пациента.
Детальнее – вывод из запоя вызов
Конфиденциальность — не обещание на бумаге, а практический стандарт. В клинике используются кодовые профили, шифрованный контур хранения карт, разграничение доступа по ролям; документы оформляются нейтрально, а уведомления формулируются без чувствительных слов. Выездные специалисты приезжают без медицинской символики, а в здании клиники навигация организована так, чтобы перемещение было незаметным. Это создаёт пространство, в котором можно честно говорить о целях и спокойно выполнять план — без стигмы и посторонних взглядов.
Узнать больше – http://narkologicheskaya-klinika-v-spb14.ru
Ниже представлена карта действий бригады «РязМедСервиса» в первые три часа. Это не «жёсткая сетка», а ориентир для безопасной и быстрой стабилизации. В каждом блоке есть клиническая цель, измеримые критерии и условие для перехода к следующему шагу.
Получить дополнительную информацию – врач вывод из запоя в рязани
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Получить больше информации – http://narkologicheskaya-klinika-v-spb14.ru/narkolog-sankt-peterburg/
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Разобраться лучше – http://narcolog-na-dom-krasnodar14.ru
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Узнать больше – вывод из запоя цена рязань
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Разобраться лучше – https://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg/
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Получить больше информации – нарколог на дом недорого
заказать студенческую работу https://kupit-kursovuyu-6.ru/ .
При выводе из запоя в Ростове-на-Дону используются разные терапевтические подходы. Основной задачей является устранение токсинов и восстановление работы систем организма. Врач подбирает терапию индивидуально в зависимости от состояния пациента и длительности запоя.
Подробнее – вывод из запоя цена ростов-на-дону
курсовой проект цена http://www.kupit-kursovuyu-7.ru .
заказать студенческую работу http://www.kupit-kursovuyu-8.ru/ .
В условиях медицинского контроля специалисты выполняют последовательные действия, направленные на стабилизацию состояния пациента.
Детальнее – нарколог вывод из запоя рязань
купить курсовую москва купить курсовую москва .
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Подробнее тут – наркологическая клиника вывод из запоя в санкт-петербурге
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Подробнее тут – http://www.domen.ru
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Ознакомиться с деталями – наркологическая клиника нарколог в санкт-петербурге
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Изучить вопрос глубже – наркологическая клиника цены
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Получить дополнительную информацию – наркологическая клиника вывод из запоя санкт-петербург
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Разобраться лучше – наркологическая клиника нарколог в санкт-петербурге
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Подробнее тут – http://narcolog-na-dom-krasnodar14.ru/
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Исследовать вопрос подробнее – нарколог на дом срочно в краснодаре
Этот комплекс мер позволяет оказывать помощь пациентам на всех стадиях зависимости.
Подробнее можно узнать тут – narkologicheskaya-klinika-sankt-peterburg14.ru/
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Углубиться в тему – вызвать нарколога на дом в краснодаре
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Получить больше информации – http://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare/
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-v-ryazani14.ru/vyvod-iz-zapoya-ryazan-na-domu
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Изучить вопрос глубже – срочный вывод из запоя рязань
Этот комплекс мер позволяет оказывать помощь пациентам на всех стадиях зависимости.
Получить больше информации – анонимная наркологическая клиника санкт-петербург
Этот комплекс мер позволяет оказывать помощь пациентам на всех стадиях зависимости.
Получить дополнительные сведения – http://narkologicheskaya-klinika-sankt-peterburg14.ru
Вывод из запоя в Ростове-на-Дону является востребованной медицинской услугой, направленной на восстановление физического состояния пациента и снижение рисков осложнений. Длительное употребление алкоголя вызывает тяжелые нарушения в работе организма, и самостоятельное прекращение приёма спиртных напитков часто приводит к абстинентному синдрому. В таких ситуациях профессиональный вывод из запоя в клинике становится необходимым условием для сохранения здоровья.
Изучить вопрос глубже – вывод из запоя в стационаре ростов-на-дону
Домашний визит нарколога — это формат, который соединяет клиническую безопасность и человеческую деликатность. В «КубаньМедЦентре» (Краснодар) мы организуем помощь так, чтобы пациент получал её там, где ему спокойнее всего — у себя дома. Дежурная команда работает круглосуточно, а среднее окно прибытия по городу составляет 30–40 минут с момента подтверждения заявки. Врач приезжает без опознавательных знаков, проводит экспресс-оценку состояния, запускает индивидуально подобранную инфузионную терапию и оставляет подробный план на ближайшие 72 часа. Каждый шаг объясняется простым языком: что мы делаем, зачем это нужно и по каким критериям поймём, что динамика идёт правильно.
Подробнее тут – http://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare/
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Ознакомиться с деталями – нарколог на дом круглосуточно цены
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Получить больше информации – http://narcolog-na-dom-krasnodar14.ru/
Технологии — лишь каркас. Содержанием маршрут наполняют объяснения: что именно делаем и почему, какие цифры считать «зелёной зоной», когда связываться с дежурным врачом и зачем нужны короткие вечерние включения даже в «относительно спокойные» дни.
Подробнее можно узнать тут – наркологическая клиника наркологический центр в санкт-петербурге
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Изучить вопрос глубже – https://narcolog-na-dom-krasnodar14.ru/
Алкогольный запой приводит к тяжёлой интоксикации, при которой организм теряет способность к самостоятельному восстановлению. Вывод из запоя в клинике предполагает использование инфузионной терапии, медикаментов для нормализации работы сердца, печени и нервной системы, а также витаминных комплексов для восполнения дефицита питательных веществ.
Подробнее – срочный вывод из запоя
Howdy I am so happy I found your web site, I really found you by mistake, while I was researching on Aol for something else, Anyhow I am here now and would just like to say cheers for a incredible post and a all round thrilling blog (I also love the theme/design), I don’t have time to look over it all at the minute but I have saved it and also added in your RSS feeds, so when I have time I will be back to read a lot more, Please do keep up the awesome jo.
Find Female Escorts Rio
Наше маркетинговое агентство предлагает индивидуальные решения для роста вашего бизнеса.
Понимание ваших нужд позволит вам выбрать наиболее подходящее агентство для ваших задач.
Компания «СтройМастер» предлагает услуги по ремонт кабинета любой сложности и площади.
Создание нового офисного пространства начинается с ремонта. Ремонт офиса может быть сложным процессом, включающим различные этапы, от планирования до отделочных работ. Создание комфортной рабочей среды является ключевым аспектом ремонта офиса.
Необходимо учитывать множество факторов, такие как расположение помещения, выбор материалов и цветовая гамма . При этом важно не забыть о таких моментах, как освещение, вентиляция и безопасность. Создание комфортной и функциональной рабочей среды является основной целью ремонта офиса.
Планирование ремонта офиса является первым и одним из самых важных шагов . Планирование должно включать анализ текущего состояния офиса, определение потребностей сотрудников и выбор дизайна. Это giup evitar ошибок и обеспечить, что ремонт будет выполнен в соответствии с ожиданиями .
Все эти детали должны быть тщательно спланированы и включены в проект ремонта . При этом важно работать с профессиональными дизайнерами и подрядчиками, чтобы обеспечить высокое качество работ. Все этапы ремонта должны быть тщательно спланированы и контролированы .
Все материалы и элементы дизайна должны быть тщательно подобраны. Дизайн должен соответствовать современным тенденциям и быть функциональным. Ремонт офиса должен быть направлен на создание уникальной и комфортной рабочей среды.
Все материалы и технологии должны быть выбраны с учетом этих факторов . При этом важно работать с профессиональными дизайнерами, которые могут предложить инновационные и эффективные решения. Создание нового офисного пространства требует творческого подхода и внимания к деталям.
Завершение ремонта офиса является последним этапом этого процесса . Завершение ремонта включает контроль качества работ, тестирование систем и уборку помещения. Все эти системы должны быть функциональными и безопасными .
Ремонт офиса должен быть направлен на создание долговечной и эффективной рабочей среды. При этом важно работать с профессиональными подрядчиками, которые могут обеспечить высокое качество работ и гарантийное обслуживание. Ремонт офиса должен быть выполнен с учетом всех современных требований и технологий .
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Изучить вопрос глубже – нарколог на дом вывод
В данной статье мы поговорим о будущем медицины, акцентируя внимание на прорывных разработках и их потенциале. Читатель узнает о новых подходах к лечению, роли искусственного интеллекта и возможностях персонализированной медицины.
Открой скрытое – http://maraforum.iboards.ru/viewtopic.php?f=11&t=8644
ко ланта ко лант
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Исследовать вопрос подробнее – вывод наркологическая клиника в санкт-петербурге
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Получить дополнительные сведения – вызов врача нарколога на дом в краснодаре
При выезде врач действует по установленному протоколу, что гарантирует безопасность и эффективность процедуры.
Изучить вопрос глубже – вызвать нарколога на дом
Этот информационный материал подробно освещает проблему наркозависимости, ее причины и последствия. Мы предлагаем информацию о методах лечения, профилактики и поддерживающих программах. Цель статьи — повысить осведомленность и продвигать идеи о необходимости борьбы с зависимостями.
Выяснить больше – https://dafna-clinic.ru
Этап
Исследовать вопрос подробнее – нарколог на дом жуковский
Tham gia cộng đồng game thủ tại Go88 để trải nghiệm các trò chơi bài, poker phổ biến nhất hiện nay.
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Углубиться в тему – http://narkologicheskaya-klinika-v-spb14.ru/narkolog-sankt-peterburg/
Индивидуальная программа у нас — это модульный конструктор. В одних случаях критичен блок сна, в других — профилактика вечерних «волн» тревоги, в третьих — семейная медиированная встреча. Мы гибко переставляем модули, учитывая сопутствующие заболевания, приём базовых лекарств (антигипертензивные, антиаритмические, сахароснижающие), возраст и расписание пациента. Цель проста: чтобы терапия вписалась в жизнь, а не наоборот.
Детальнее – анонимная наркологическая клиника в рязани
Эта медицинская заметка содержит сжатую информацию о новых находках и методах в области здравоохранения. Мы предлагаем читателям свежие данные о заболеваниях, профилактике и лечении. Наша цель — быстро и доступно донести важную информацию, которая поможет в повседневной жизни и понимании здоровья.
Изучить вопрос глубже – вывод из запоя круглосуточно Симферополь
Наркологическая клиника в Санкт-Петербурге работает по различным направлениям, охватывающим как экстренную помощь, так и плановое лечение.
Изучить вопрос глубже – наркологическая клиника лечение алкоголизма
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Детальнее – https://narkolog-na-dom-zhukovskij7.ru/
В этом обзоре представлены различные методы избавления от зависимости, включая терапевтические и психологические подходы. Мы сравниваем их эффективность и предоставляем рекомендации для тех, кто хочет вернуться к трезвой жизни. Читатели смогут найти информацию о реабилитационных центрах и поддерживающих группах.
Получить дополнительные сведения – наркологический вывод из запоя Симферополь
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Выяснить больше – http://narcolog-na-dom-krasnodar14.ru
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Подробнее можно узнать тут – http://narkolog-na-dom-zhukovskij7.ru/
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Разобраться лучше – narkolog-na-dom-vyvod-iz-zapoya
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Углубиться в тему – наркологическая клиника цены
Нарколог на дом в Санкт-Петербурге — это востребованная медицинская услуга, позволяющая получить помощь в комфортных домашних условиях. Такой формат особенно актуален в ситуациях, когда пациент не может или не хочет обращаться в стационар. Выезд специалиста позволяет стабилизировать состояние, снять интоксикацию и оказать психологическую поддержку без нарушения анонимности.
Получить больше информации – нарколог на дом круглосуточно цены санкт-петербург
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Узнать больше – нарколог на дом вывод из запоя краснодар
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Подробнее можно узнать тут – narkolog-na-dom-zhukovskij-ceny
Перед тем как перечислить типичные случаи, отметим главный принцип: домашний формат выбирают, когда безопасность и прогноз сопоставимы со стационаром, а переезд лишь затянет старт терапии и усилит стресс для семьи.
Изучить вопрос глубже – врач нарколог на дом
Этот обзор сосредоточен на различных подходах к избавлению от зависимости. Мы изучим традиционные и альтернативные методы, а также их сочетание для достижения максимальной эффективности. Читатели смогут открыть для себя новые стратегии и подходы, которые помогут в их борьбе с зависимостями.
Подробнее можно узнать тут – наркология вывод из запоя Симферополь
Hits of the Day: http://www.kalyamalya.ru/modules/newbb_plus/viewtopic.php?topic_id=26690&post_id=109781&order=0&viewmode=flat&pid=0&forum=4#109781
Комплексное применение этих средств ускоряет процесс восстановления.
Получить больше информации – [url=https://narkolog-na-dom-sankt-peterburg14.ru/]нарколог на дом клиника санкт-петербург[/url]
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-v-sankt-peterburge-vyezd-nadom/
Формат лечения
Подробнее тут – http://narkologicheskaya-klinika-sankt-peterburg14.ru
Fresh news on Page: https://medicaid-billing-software45607.blogdigy.com/nppr-team-shop-the-ultimate-hub-for-social-media-marketing-mastery-59908466
Формат лечения
Ознакомиться с деталями – наркологическая клиника стационар санкт-петербург
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Получить дополнительные сведения – нарколог на дом срочно санкт-петербург
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Ознакомиться с деталями – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-v-sankt-peterburge-vyezd-nadom/
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Получить дополнительные сведения – лечение в наркологической клинике санкт-петербург
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Углубиться в тему – http://narcolog-na-dom-krasnodar14.ru/
blacksprut ссылка
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Углубиться в тему – https://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg
Этот комплекс мер позволяет оказывать помощь пациентам на всех стадиях зависимости.
Разобраться лучше – https://narkologicheskaya-klinika-sankt-peterburg14.ru
aviator bonus game http://aviator-game-winner.com/ .
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Подробнее тут – https://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr
В этой статье мы подробно рассматриваем проверенные методы борьбы с зависимостями, включая психотерапию, медикаментозное лечение и поддержку со стороны общества. Мы акцентируем внимание на важности комплексного подхода и возможности успешного восстановления для людей, столкнувшихся с этой проблемой.
Углубиться в тему – вывод из запоя вызов в Москве
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Ознакомиться с деталями – https://narkologicheskaya-klinika-sankt-peterburg14.ru/klinika-narkologii-spb/
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Ознакомиться с деталями – http://narcolog-na-dom-krasnodar14.ru
В данном обзоре представлены основные направления и тренды в области медицины. Мы обсудим актуальные проблемы здравоохранения, свежие открытия и новые подходы, которые меняют представление о лечении и профилактике заболеваний. Эта информация будет полезна как специалистам, так и широкой публике.
Узнать больше – вывод из запоя на дому Москва
Этот документ охватывает важные аспекты медицинской науки, сосредотачиваясь на ключевых вопросах, касающихся здоровья населения. Мы рассматриваем свежие исследования, клинические рекомендации и лучшие практики, которые помогут улучшить качество лечения и профилактики заболеваний. Читатели получат возможность углубиться в различные медицинские дисциплины.
Подробнее тут – наркология вывод из запоя
В этом обзоре представлены различные методы избавления от зависимости, включая терапевтические и психологические подходы. Мы сравниваем их эффективность и предоставляем рекомендации для тех, кто хочет вернуться к трезвой жизни. Читатели смогут найти информацию о реабилитационных центрах и поддерживающих группах.
Подробнее можно узнать тут – вывод из запоя на дому цена Симферополь
В этой публикации мы рассматриваем важную тему борьбы с зависимостями, включая алкогольную и наркотическую зависимости. Мы обсудим методы лечения, реабилитации и поддержку, которые могут помочь людям, столкнувшимся с этой проблемой. Читатели узнают о перспективах выздоровления и важности комплексного подхода.
Получить дополнительные сведения – нарколог вывод из запоя Симферополь
Для достижения результата врачи используют индивидуально подобранные схемы лечения. Они включают фармакологическую поддержку, физиотерапию и психотерапевтические методики.
Углубиться в тему – наркологическая клиника вывод из запоя санкт-петербург
https://xn--12cati8bfyq4b3bnv4e9ae5e9adg7unf7dn.com/melbet-kz-melbet-kz-bk-kazahstan-52/
Ниже представлена карта действий бригады «РязМедСервиса» в первые три часа. Это не «жёсткая сетка», а ориентир для безопасной и быстрой стабилизации. В каждом блоке есть клиническая цель, измеримые критерии и условие для перехода к следующему шагу.
Исследовать вопрос подробнее – наркология вывод из запоя
aviator money [url=http://aviator-game-winner.com]http://aviator-game-winner.com[/url] .
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Разобраться лучше – нарколог на дом клиника краснодар
Для многих барьер — страх огласки. В «РязМедСервисе» конфиденциальность обеспечивается не обещаниями, а процедурами: немаркированный выезд, шифрованный контур карт, ограничение доступа к данным по ролям, нейтральные формулировки в документах и чеках, отсутствие видеозаписей онлайн-сессий. Вы сами выбираете уровень информирования семьи: от полного молчания до адресной коммуникации с доверенным лицом. Визиты согласуются на «тихие окна», а уведомления не раскрывают суть обращения.
Исследовать вопрос подробнее – вывод из запоя с выездом
Конфиденциальность — не обещание на бумаге, а практический стандарт. В клинике используются кодовые профили, шифрованный контур хранения карт, разграничение доступа по ролям; документы оформляются нейтрально, а уведомления формулируются без чувствительных слов. Выездные специалисты приезжают без медицинской символики, а в здании клиники навигация организована так, чтобы перемещение было незаметным. Это создаёт пространство, в котором можно честно говорить о целях и спокойно выполнять план — без стигмы и посторонних взглядов.
Подробнее – лечение в наркологической клинике
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Выяснить больше – частный нарколог на дом
Петербургский темп жизни — поздняя занятость, переменная нагрузка, сезонные перепады света — усложняет восстановление после эпизодов употребления. Поэтому мы разработали модульные программы, способные гибко подстраиваться под график и биоритмы: у кого-то «трудные часы» приходятся на поздний вечер на Васильевском острове, у кого-то — на раннее утро перед сменой в Адмиралтейском районе. Маршрут строится вокруг человека, а не вокруг расписания кабинета: очные приёмы, немаркированные выезды на дом, дневной стационар, защищённые онлайн-сессии — всё объединено единым клиническим планом и общими целями.
Подробнее – запой наркологическая клиника в санкт-петербурге
Услуги технические переводы английский язык предоставляются высококвалифицированными переводчиками.
особую область переводческих услуг, ориентированную на техническую документацию . Это ключевым фактором успеха в глобализации бизнеса и научного сотрудничества . Благодаря техническому переводу можно обмениваться знаниями и опытом на международном уровне .
Технический перевод предполагает высокий уровень специализации и точности . Переводчики должны обладать глубокими знаниями в той или иной технической области . Это дает возможность минимизировать риски недопонимания или неправильного использования технической информации .
Процесс технического перевода включает в себя несколько этапов, от первоначальной оценки проекта до финального контроля качества . На первом этапе оцениваются ресурсы, необходимые для выполнения задачи . Далее производится выбор наиболее подходящих инструментов и технологий для перевода .
Выполнение самого перевода требует высокой концентрации и внимания к деталям . После завершения перевода выполняется проверка соответствия переведенного текста оригиналу . Этот позволяет минимизировать ошибки и несоответствия .
Технический перевод помогает преодолевать языковые барьеры и расширять доступ к информации . Благодаря техническому переводу компании могут экспортировать свою продукцию и услуги в другие страны . Это позволяет строить международные партнерства и сотрудничество .
Технический перевод также обеспечивает доступ к образованию и информации для людей, говорящих на разных языках . Это помогает в построении более гармоничного и взаимосвязанного мира . Поэтому необходимо постоянно совершенствовать методы и инструменты перевода .
Будущее технического перевода будет характеризоваться все большей автоматизацией и использованием машинного перевода . Развитие технологий перевода и автоматизации позволит увеличить скорость и качество перевода .
В будущем технический перевод станет еще более важным для глобальных?? и международного сотрудничества . Это откроет новые возможности для переводчиков и компаний, предоставляющих услуги перевода . Поэтому следует инвестировать в разработку и внедрение новых технологий и инструментов .
Вывод из запоя — это управляемая медицинская процедура, а не «волшебная капля» или крепкий чай с рассолом. «Формула Трезвости» организует помощь в Ногинске круглосуточно: выезд врача на дом или приём в стационаре, детоксикация с мониторингом, мягкая коррекция сна и тревоги, подробный план на первые 48–72 часа. Мы действуем безопасно, конфиденциально и без «мелкого шрифта» — объясняем, что и зачем делаем, согласовываем схему и фиксируем смету до начала процедур.
Подробнее можно узнать тут – vyvod-iz-zapoya
Когда уместен
Разобраться лучше – https://narkologicheskaya-pomoshch-orekhovo-zuevo7.ru/skoraya-narkologicheskaya-pomoshch-v-orekhovo-zuevo
Ожидаемый результат
Углубиться в тему – http://
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Получить дополнительную информацию – https://kapelnica-ot-zapoya-vidnoe7.ru/kapelnica-ot-zapoya-cena-v-vidnom
Медикаментозное пролонгированное
Изучить вопрос глубже – медицинский центр кодирование от алкоголизма
Khao555 com
Единая панель оценки помогает действовать быстро и безошибочно. Мы фиксируем параметры, объясняем их смысл пациенту и семье и тут же привязываем к ним действия. Пример приведён в таблице: это не заменяет осмотр, но показывает логику, которой мы придерживаемся на выезде и в приёмном кабинете.
Ознакомиться с деталями – наркологическая клиника стационар
Этап
Разобраться лучше – https://vyvod-iz-zapoya-noginsk7.ru/vyvod-iz-zapoya-kruglosutochno-v-noginske
Этап
Выяснить больше – нарколог на дом круглосуточно
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Получить больше информации – https://narkologicheskaya-klinika-v-spb14.ru/
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить больше информации – наркологический вывод из запоя
??????? ??? https://aviator-game-deposit.com/ .
aviator money aviator-game-winner.com .
специалисты по ремонту квартир специалисты по ремонту квартир .
Выезд на дом
Ознакомиться с деталями – скорая наркологическая помощь
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Получить дополнительную информацию – нарколог на дом недорого в краснодаре
Этот краткий обзор предлагает сжатую информацию из области медицины, включая ключевые факты и последние новости. Мы стремимся сделать информацию доступной и понятной для широкой аудитории, что позволит читателям оставаться в курсе актуальных событий в здравоохранении.
Подробнее можно узнать тут – вывод из запоя на дому Симферополь
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Разобраться лучше – нарколог на дом срочно краснодар
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Получить дополнительную информацию – https://narkologicheskaya-klinika-v-spb14.ru/
Технологии — лишь каркас. Содержанием маршрут наполняют объяснения: что именно делаем и почему, какие цифры считать «зелёной зоной», когда связываться с дежурным врачом и зачем нужны короткие вечерние включения даже в «относительно спокойные» дни.
Исследовать вопрос подробнее – наркологическая клиника вывод из запоя в санкт-петербурге
m bs2best at
Медикаментозное пролонгированное
Получить больше информации – https://kodirovanie-ot-alkogolizma-vidnoe7.ru/
Ожидаемый результат
Выяснить больше – https://vyvod-iz-zapoya-noginsk7.ru/vyvod-iz-zapoya-kruglosutochno-v-noginske/
Этап
Ознакомиться с деталями – капельница от запоя на дому цена
Когда уместен
Исследовать вопрос подробнее – https://narkologicheskaya-pomoshch-orekhovo-zuevo7.ru/narkologicheskaya-pomoshch-na-domu-v-orekhovo-zuevo/
Наркологическая помощь — это не разовая капельница, а управляемый путь от стабилизации состояния к устойчивой трезвости. «Новая Надежда» организует полный цикл: экстренный выезд на дом, стационар для безопасной детоксикации, кодирование и поддерживающую психотерапию, а также контакт с семьёй и постлечебное сопровождение. Мы работаем конфиденциально и круглосуточно, фиксируем смету до начала процедур и объясняем каждый шаг понятным языком — без «мелкого шрифта» и неожиданных пунктов.
Выяснить больше – skoraya-narkologicheskaya-pomoshch
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Получить больше информации – платная наркологическая клиника
Как работает
Детальнее – http://www.domen.ru
Выбор техники зависит от клинической картины, переносимости препаратов, психоэмоционального состояния и горизонта планируемой трезвости. Таблица ниже помогает сориентироваться в ключевых различиях — врач подробно разберёт нюансы на очной консультации.
Подробнее – кодирование от алкоголизма на дому в видном
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Узнать больше – https://narkologicheskaya-klinika-v-spb14.ru
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Углубиться в тему – https://narkologicheskaya-klinika-v-spb14.ru/narkolog-sankt-peterburg/
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Узнать больше – http://narcolog-na-dom-krasnodar14.ru/
Запой — это не «несколько лишних бокалов», а острое состояние с системной нагрузкой на сердце, мозг и печень. В клинике «РязМедСервис» мы рассматриваем вывод из запоя как управляемый медицинский процесс: быстрый выезд, экспресс-диагностика, индивидуальные капельницы через инфузомат, круглосуточная связь и строгая конфиденциальность. Мы приезжаем без опознавательных знаков, оформляем документы в нейтральных формулировках и оставляем пациенту и близким понятный план на 72 часа — чтобы первая трезвая ночь прошла спокойно, а эффект лечения стал предсказуемым и устойчивым.
Ознакомиться с деталями – вывод из запоя на дому в рязани
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Выяснить больше – https://narkologicheskaya-klinika-v-spb14.ru/narkologicheskaya-bolnicza-sankt-peterburg
Когда уместен
Ознакомиться с деталями – narkologicheskaya-pomoshch-cena
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Получить дополнительную информацию – врач на дом капельница от запоя
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Выяснить больше – нарколог на дом клиника
Наш подход строится на двух принципах: минимально достаточная фармакотерапия и прозрачные «коридоры безопасности». Это означает — никаких «универсальных капельниц» и полипрагмазии. Каждый компонент в схеме имеет проверенную цель: восполнить жидкость, выровнять электролиты, защитить слизистую, снизить вегетативный «шторм» и вернуть возможность естественного сна. Скорость и объём инфузий мы задаём инфузоматом, контролируя давление, пульс, сатурацию и самочувствие на каждом этапе.
Детальнее – вывод из запоя на дому круглосуточно
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Детальнее – вывод из запоя недорого в рязани
Когда уместен
Получить дополнительные сведения – http://narkologicheskaya-pomoshch-orekhovo-zuevo7.ru/skoraya-narkologicheskaya-pomoshch-v-orekhovo-zuevo/https://narkologicheskaya-pomoshch-orekhovo-zuevo7.ru
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Подробнее тут – запой наркологическая клиника
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Детальнее – narkologicheskaya-klinika-v-spb14.ru/
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Получить больше информации – наркологическая клиника цены
Чтобы не «дотягивать до утра», важно понимать тревожные признаки. Ниже — ориентиры, при которых тянуть опасно: перед списком подчеркнём, что финальное решение принимает врач после очной оценки состояния.
Изучить вопрос глубже – http://vyvod-iz-zapoya-noginsk7.ru/vyvod-iz-zapoya-deshevo-v-noginske/
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Получить дополнительные сведения – нарколог на дом круглосуточно краснодар
Этап
Исследовать вопрос подробнее – врач вывод из запоя
Что делает врач
Подробнее – https://vyvod-iz-zapoya-noginsk7.ru/vyvod-iz-zapoya-deshevo-v-noginske
??????? ??? aviator-game-deposit.com .
качественный ремонт квартир в москве качественный ремонт квартир в москве .
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Исследовать вопрос подробнее – https://narcolog-na-dom-krasnodar14.ru/narkolog-krasnodar-anonimno/
Этап
Исследовать вопрос подробнее – нарколог на дом клиника
Перед тем как перечислить типичные случаи, отметим главный принцип: домашний формат выбирают, когда безопасность и прогноз сопоставимы со стационаром, а переезд лишь затянет старт терапии и усилит стресс для семьи.
Детальнее – нарколог на дом круглосуточно цены
Этот информативный текст сочетает в себе темы здоровья и зависимости. Мы обсудим, как хронические заболевания могут усугубить зависимости и наоборот, как зависимость может влиять на общее состояние здоровья. Читатели получат представление о комплексном подходе к лечению как физического, так и психического состояния.
Получить дополнительные сведения – анонимный вывод из запоя Симферополь
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Получить больше информации – http://narcolog-na-dom-krasnodar14.ru
??????????
Выезд на дом
Получить дополнительную информацию – narkologicheskaya-pomoshch-reabilitaciya
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Подробнее тут – нарколог вывод из запоя в рязани
Формат
Подробнее – наркологическая помощь орехово зуево
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Получить дополнительную информацию – нарколог на дом клиника в краснодаре
Наш подход строится на двух принципах: минимально достаточная фармакотерапия и прозрачные «коридоры безопасности». Это означает — никаких «универсальных капельниц» и полипрагмазии. Каждый компонент в схеме имеет проверенную цель: восполнить жидкость, выровнять электролиты, защитить слизистую, снизить вегетативный «шторм» и вернуть возможность естественного сна. Скорость и объём инфузий мы задаём инфузоматом, контролируя давление, пульс, сатурацию и самочувствие на каждом этапе.
Изучить вопрос глубже – https://vyvod-iz-zapoya-v-ryazani14.ru/vyvod-iz-zapoya-ryazan-na-domu/
Когда уместен
Разобраться лучше – vyzov-narkologicheskoj-pomoshchi
Конфиденциальность — не обещание на бумаге, а практический стандарт. В клинике используются кодовые профили, шифрованный контур хранения карт, разграничение доступа по ролям; документы оформляются нейтрально, а уведомления формулируются без чувствительных слов. Выездные специалисты приезжают без медицинской символики, а в здании клиники навигация организована так, чтобы перемещение было незаметным. Это создаёт пространство, в котором можно честно говорить о целях и спокойно выполнять план — без стигмы и посторонних взглядов.
Получить больше информации – http://narkologicheskaya-klinika-v-spb14.ru
Когда уместен
Подробнее можно узнать тут – http://narkologicheskaya-pomoshch-orekhovo-zuevo7.ru
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Получить дополнительные сведения – наркологическая клиника клиника помощь санкт-петербург
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Ознакомиться с деталями – выезд нарколога на дом
рулонные шторы на окна купить рулонные шторы на окна купить .
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Получить дополнительные сведения – нарколог на дом цены краснодар
Платформа Vavada предлагает быстрый вывод.
Выбор игр представлен топ-провайдерами.
Промокоды и фриспины помогают играть без риска.
Вход доступен мгновенно.
Подробности по https://pyramada.com/ — используй промокод.
Играйте ответственно.
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Исследовать вопрос подробнее – http://narcolog-na-dom-krasnodar14.ru
inverter game aviator-game-deposit.com .
ремонт квартир компании http://www.rejting-kompanij-po-remontu-kvartir-moskvy.com .
https://telegra.ph/Melbet-kz-11-05
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Изучить вопрос глубже – нарколог на дом клиника краснодар
пионы и розы Магазин роз: Магазин роз – это специализированный цветочный магазин, предлагающий широкий выбор роз различных сортов, цветов и размеров. Здесь можно найти как классические букеты роз, так и оригинальные композиции из роз, созданные профессиональными флористами. В магазине роз всегда можно получить консультацию по выбору роз, уходу за ними и созданию букетов. Посетите магазин роз, чтобы выбрать идеальный букет для себя и своих близких.
Этот комплекс мер позволяет оказывать помощь пациентам на всех стадиях зависимости.
Подробнее можно узнать тут – вывод наркологическая клиника
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Подробнее можно узнать тут – вызвать нарколога на дом
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Получить дополнительную информацию – нарколог на дом вывод
Для решения всех задач, связанных с переводом документов на любой язык, можно обратиться в юридический перевод, где опытные переводчики окажут профессиональные услуги по переводу любых документов.
предоставление лингвистической поддержки для бизнеса и частных лиц. Это позволяет им удовлетворять различные потребности клиентов, от перевода личных документов до комплексных бизнес-проектов. Кроме того, бюро переводов часто обладает d?iной переводчиков, которые являются экспертами в разных областях, владеющими специализированными знаниями для точных переводов. Это гарантирует, что переведенный текст не только соответствует оригиналу по смыслу, но и адаптирован к целевой аудитории и соответствует требованиям определенной отрасли.
Бюро переводов также уделяет особое внимание конфиденциальности и безопасности переводимой информации, что особенно важно для конфиденциальных бизнес-документов . Это является ключевым аспектом их услуг, поскольку клиенты часто доверяют им?ливую информацию. Помимо этого, бюро переводов может предложить услуги по локализации, учитывая культурные и языковые особенности . Это особенно ценно для компаний, стремящихся расширить свою деятельность на новые рынки.
Работа с бюро переводов дает клиентам доступ к команде опытных и квалифицированных переводчиков . Это означает, что клиенты могут получить переводы, соответствующие их потребностям, будь то срочный перевод небольшого документа или масштабный проект, требующий перевода большого объема текстов. Кроме того, многие бюро переводов используют современные технологии для управления процессом перевода . Это не только ускоряет процесс перевода, но и гарантирует, что окончательный продукт соответствует самым высоким стандартам.
Партнерство с бюро переводов также может быть способом для компаний построить сильный бренд на международном уровне. Благодаря точным и культурно адаптированным переводам, бизнес может укреплять доверие и авторитет среди своих международных партнеров и клиентов. Это делает бюро переводов не просто поставщиком услуг, а ценным партнером в достижении бизнес-целей.
Бюро переводов обычно работает гарантируя, что все переводы соответствуют самым высоким стандартам. Для начала работы клиент заказывает услугу перевода, предоставляя необходимую информацию о проекте . После этого, бюро переводов использует специализированное программное обеспечение для управления процессом перевода . Этот подход??ет, что перевод не только выполнен качественно, но и соответствует конкретным потребностям и ожиданиям клиента.
На протяжении всего процесса бюро переводов также проводит необходимые корректировки и редактирование . Это может включать проведение экспертной оценки . Такой подход к?? и удовлетворенности клиента позволяет бюро переводов поддерживать высокий уровеньprofessionalизма и строить долгосрочные отношения с клиентами.
В заключение, бюро переводов представляет собой комплексную службу, которая предлагает широкий спектр лингвистических услуг . С их помощью клиенты могут получить доступ к экспертным знаниям в области лингвистики и коммуникации . Бюро переводов является не просто поставщиком услуг, а стратегическим партнером, который может помочь усилить коммуникацию . Сегодня, когдамир становится все более взаимосвязанным, роль бюро переводов будет только оставаться ключевым фактором в международном общении.
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Получить дополнительную информацию – http://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare/
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Углубиться в тему – нарколог на дом круглосуточно
Нарколог на дом в Санкт-Петербурге — это востребованная медицинская услуга, позволяющая получить помощь в комфортных домашних условиях. Такой формат особенно актуален в ситуациях, когда пациент не может или не хочет обращаться в стационар. Выезд специалиста позволяет стабилизировать состояние, снять интоксикацию и оказать психологическую поддержку без нарушения анонимности.
Ознакомиться с деталями – http://narkolog-na-dom-sankt-peterburg14.ru
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Изучить вопрос глубже – http://vyvod-iz-zapoya-v-ryazani14.ru/
ко ланта пляжи
Этот комплекс мер позволяет оказывать помощь пациентам на всех стадиях зависимости.
Выяснить больше – http://narkologicheskaya-klinika-sankt-peterburg14.ru
Лечение начинается с короткой оценки рисков и выбора безопасной точки старта. Далее следуют этапы стабилизации, настройки сна и тревоги, поведенческие инструменты и план антирецидивной поддержки. Ниже — ориентировочная карта: в реальности длительности и интенсивность подбираются индивидуально, а переход между форматами происходит без «обнуления» обследований.
Получить дополнительную информацию – https://narkologicheskaya-klinika-v-spb14.ru/narkolog-sankt-peterburg
Если по ходу первичного осмотра выявляются «красные флаги» (спутанность сознания, нестабильное давление/ритм, кровавая рвота, подозрение на делирий), врач немедленно предложит госпитализацию и аккуратно организует перевод — безопасность всегда выше удобства.
Выяснить больше – narkolog-na-dom-telefon
В данном обзоре представлены основные направления и тренды в области медицины. Мы обсудим актуальные проблемы здравоохранения, свежие открытия и новые подходы, которые меняют представление о лечении и профилактике заболеваний. Эта информация будет полезна как специалистам, так и широкой публике.
Углубиться в тему – помощь вывод из запоя Москва
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Получить дополнительную информацию – нарколог на дом срочно
Онлайн?казино Vavada обеспечивает стабильный доступ к играм.
Турниры и развлечения работают на любых устройствах, что делает процесс динамичным.
Создать аккаунт просто, и пользователи получают полный функционал.
Чтобы найти рабочий вход и актуальное зеркало, переходите по vavada войти — собраны инструкции по входу.
Соблюдайте баланс, чтобы игра оставалась под контролем.
леса лрсп Продажа легких лесов: Продажа легких лесов идеально подходит для небольших ремонтных и отделочных работ. Легкие леса отличаются небольшим весом и простотой сборки, что позволяет быстро организовать рабочее место без необходимости использования специального оборудования. Они легко перемещаются и хранятся, что делает их незаменимыми для мобильных бригад и частных мастеров.
Этот обзор посвящен успешным стратегиям избавления от зависимости, включая реальные примеры и советы. Мы разоблачим мифы и предоставим читателям достоверную информацию о различных подходах. Получите опыт многообразия методов и найдите подходящий способ для себя!
Подробнее можно узнать тут – помощь вывод из запоя Симферополь
электрические рулонные шторы купить москва https://avtomaticheskie-rulonnye-shtory11.ru .
Первые сутки после прекращения алкоголя — самые уязвимые: именно в это время нарастают абстинентные симптомы и риск осложнений. Ниже приведены основные ситуации, при которых нужен быстрый выезд врача. Перед списком отметим: если сомневаетесь, позвоните координатору — он уточнит признаки и подскажет безопасные действия до прибытия команды.
Выяснить больше – вывод из запоя на дому в пушкино
Этап
Подробнее тут – vrach-narkolog-na-dom
остров ланте
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Разобраться лучше – https://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg/
Что делаем
Выяснить больше – http://narkolog-na-dom-zhukovskij7.ru/vyzov-narkologa-na-dom-v-zhukovskom/https://narkolog-na-dom-zhukovskij7.ru
Этап
Получить больше информации – https://kapelnica-ot-zapoya-vidnoe7.ru/kapelnica-ot-zapoya-kruglosutochno-v-vidnom/
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Исследовать вопрос подробнее – http://narkologicheskaya-klinika-v-spb14.ru
«Как отмечает врач-нарколог Павел Викторович Зайцев, «эффективность терапии во многом зависит от своевременного обращения, поэтому откладывать визит в клинику опасно»».
Исследовать вопрос подробнее – наркологическая клиника цены
Единая панель оценки помогает действовать быстро и безошибочно. Мы фиксируем параметры, объясняем их смысл пациенту и семье и тут же привязываем к ним действия. Пример приведён в таблице: это не заменяет осмотр, но показывает логику, которой мы придерживаемся на выезде и в приёмном кабинете.
Детальнее – вывод наркологическая клиника
Ориентир по времени
Подробнее тут – http://narkolog-na-dom-zhukovskij7.ru/narkolog-na-dom-kruglosutochno-v-zhukovskom/
В стационаре мы добавляем расширенную диагностику и круглосуточное наблюдение: это выбор для пациентов с «красными флагами» (галлюцинации, выраженные кардиосимптомы, судороги, рецидивирующая рвота с примесью крови) или тяжёлыми соматическими заболеваниями. На дому мы остаёмся до первичной стабилизации и оставляем письменный план на 24–72 часа, чтобы семья действовала уверенно и согласованно.
Выяснить больше – http://vyvod-iz-zapoya-pushkino7.ru/vyvedenie-iz-zapoya-v-pushkino/
Формат лечения
Углубиться в тему – наркологическая клиника цены
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Детальнее – вызвать нарколога на дом в краснодаре
Ниже представлена карта действий бригады «РязМедСервиса» в первые три часа. Это не «жёсткая сетка», а ориентир для безопасной и быстрой стабилизации. В каждом блоке есть клиническая цель, измеримые критерии и условие для перехода к следующему шагу.
Углубиться в тему – наркология вывод из запоя в рязани
Нарколог на дом в Санкт-Петербурге — это востребованная медицинская услуга, позволяющая получить помощь в комфортных домашних условиях. Такой формат особенно актуален в ситуациях, когда пациент не может или не хочет обращаться в стационар. Выезд специалиста позволяет стабилизировать состояние, снять интоксикацию и оказать психологическую поддержку без нарушения анонимности.
Получить дополнительные сведения – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-v-sankt-peterburge-vyezd-nadom/
????????????
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Получить дополнительные сведения – вызвать нарколога на дом срочно
Конфиденциальность — не обещание на бумаге, а практический стандарт. В клинике используются кодовые профили, шифрованный контур хранения карт, разграничение доступа по ролям; документы оформляются нейтрально, а уведомления формулируются без чувствительных слов. Выездные специалисты приезжают без медицинской символики, а в здании клиники навигация организована так, чтобы перемещение было незаметным. Это создаёт пространство, в котором можно честно говорить о целях и спокойно выполнять план — без стигмы и посторонних взглядов.
Углубиться в тему – наркологические клиники алкоголизм в санкт-петербурге
Алгоритм одинаково прозрачен в обоих форматах. Сначала — экспресс-диагностика: уровень сознания, сатурация, пульс, давление, температура, оценка неврологического статуса и обезвоживания. Затем врач формирует индивидуальную инфузионную схему: регидратационные растворы, коррекция электролитов, поддержка печени и нервной системы, адресная симптоматическая помощь (сон, тревога, тошнота, головная боль). Темп и объём подбираются по переносимости — без «универсальных коктейлей» и лишних препаратов.
Получить дополнительные сведения – http://vyvod-iz-zapoya-pushkino7.ru/vyvod-iz-zapoya-na-domu-v-pushkino/https://vyvod-iz-zapoya-pushkino7.ru
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Подробнее можно узнать тут – наркологические клиники алкоголизм
Этап
Подробнее – капельница от запоя на дому цена
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее – врач нарколог выезд на дом санкт-петербург
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Выяснить больше – вызов врача нарколога на дом
Этот документ охватывает важные аспекты медицинской науки, сосредотачиваясь на ключевых вопросах, касающихся здоровья населения. Мы рассматриваем свежие исследования, клинические рекомендации и лучшие практики, которые помогут улучшить качество лечения и профилактики заболеваний. Читатели получат возможность углубиться в различные медицинские дисциплины.
Подробнее можно узнать тут – вывод из запоя вызов на дом Москва
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Подробнее – вывод из запоя капельница на дому в рязани
рулонные шторы на окно в кухне avtomaticheskie-rulonnye-shtory11.ru .
Пациенты могут выбрать наиболее подходящий формат лечения. Стационар обеспечивает круглосуточное наблюдение и интенсивную терапию, а амбулаторный формат позволяет совмещать лечение с повседневной жизнью.
Узнать больше – наркологические клиники алкоголизм в санкт-петербурге
В этой статье рассматриваются различные аспекты избавления от зависимости, включая физические и психологические методы. Мы обсудим поддержку, мотивацию и стратегии, которые помогут в процессе выздоровления. Читатели узнают, как преодолеть трудности и двигаться к новой жизни без зависимости.
Ознакомиться с деталями – вывод из запоя капельница
Перед тем как перечислить типичные случаи, отметим главный принцип: домашний формат выбирают, когда безопасность и прогноз сопоставимы со стационаром, а переезд лишь затянет старт терапии и усилит стресс для семьи.
Детальнее – нарколог на дом круглосуточно цены
Стандартизированный алгоритм позволяет действовать быстро и безопасно. Он гибко настраивается под конкретный случай, но всегда включает триаж, экспресс-диагностику, старт инфузии, симптом-менеджмент и выдачу плана на 72 часа с «коридорами безопасности».
Разобраться лучше – https://narcolog-na-dom-krasnodar14.ru/narkolog-krasnodar-anonimno
mt5 mac http://metatrader-5-downloads.com .
forex metatrader 5 http://metatrader-5-mac.com/ .
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Исследовать вопрос подробнее – капельница от запоя анонимно
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Исследовать вопрос подробнее – https://kapelnica-ot-zapoya-vidnoe7.ru/kapelnica-ot-zapoya-cena-v-vidnom
Если по ходу первичного осмотра выявляются «красные флаги» (спутанность сознания, нестабильное давление/ритм, кровавая рвота, подозрение на делирий), врач немедленно предложит госпитализацию и аккуратно организует перевод — безопасность всегда выше удобства.
Детальнее – нарколог на дом круглосуточно жуковский
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Узнать больше – платный нарколог на дом в краснодаре
Домашний визит нарколога — это быстрый и конфиденциальный способ стабилизировать состояние без госпитализации. «РеАл Мед» организует выезд по всему Жуковскому и близлежащим посёлкам (Быково, Кратово, Ильинский, Островцы) круглосуточно: врач приедет с оборудованием, оценит риски на месте и запустит инфузионную терапию, чтобы снять интоксикацию, тремор, тошноту и тревожность. Процедуры проводятся по медицинским протоколам, с индивидуальным подбором схем под показатели пациента и сопутствующие заболевания, а вся коммуникация выстроена максимально деликатно — без лишнего внимания соседей и персонала дома.
Подробнее тут – narkolog-na-dom-anonimno-zhukovskij
Ниже представлена карта действий бригады «РязМедСервиса» в первые три часа. Это не «жёсткая сетка», а ориентир для безопасной и быстрой стабилизации. В каждом блоке есть клиническая цель, измеримые критерии и условие для перехода к следующему шагу.
Подробнее можно узнать тут – вывод из запоя капельница на дому
Для многих барьер — страх огласки. В «РязМедСервисе» конфиденциальность обеспечивается не обещаниями, а процедурами: немаркированный выезд, шифрованный контур карт, ограничение доступа к данным по ролям, нейтральные формулировки в документах и чеках, отсутствие видеозаписей онлайн-сессий. Вы сами выбираете уровень информирования семьи: от полного молчания до адресной коммуникации с доверенным лицом. Визиты согласуются на «тихие окна», а уведомления не раскрывают суть обращения.
Подробнее – вывод из запоя капельница на дому в рязани
В этой публикации мы исследуем ключевые аспекты здоровья, включая влияние образа жизни на благополучие. Читатели узнают о важности правильного питания, физической активности и психического здоровья. Мы предоставим практические советы и рекомендации для поддержания здоровья и развития профилактических подходов.
Узнать больше – вывод из запоя цена Москва
«НеваМед» — частная наркологическая клиника в Санкт-Петербурге, где клиническая точность сочетается с бережной коммуникацией и безусловной конфиденциальностью. Мы делаем лечение не «разовым визитом ради капельницы», а продуманным маршрутом, в котором каждый шаг имеет понятную цель, сроки оценки и прозрачные критерии эффективности. Для пациента это означает предсказуемость первых суток, сохранение личного пространства и ощущение контролируемой динамики, а для близких — ясные правила помощи без тревожных импровизаций.
Выяснить больше – https://narkologicheskaya-klinika-v-spb14.ru/narkolog-sankt-peterburg/
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Получить больше информации – запой нарколог на дом
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Подробнее можно узнать тут – наркологические клиники алкоголизм санкт-петербург
Технологии — лишь каркас. Содержанием маршрут наполняют объяснения: что именно делаем и почему, какие цифры считать «зелёной зоной», когда связываться с дежурным врачом и зачем нужны короткие вечерние включения даже в «относительно спокойные» дни.
Подробнее тут – http://
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее тут – врач нарколог на дом
Форматы вывода из запоя в Пушкино
Детальнее – vyvod-iz-zapoya-v-stacionare
Этап
Узнать больше – капельница от запоя на дому видное
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Получить дополнительные сведения – kapelnica-ot-zapoya-anonimno-na-domu
WhatsApp Business ООО Торгово-транспортное предприятие “Острое Жало” “Острое Жало” активно развивает партнерские отношения с ведущими производителями и дистрибьюторами, предлагая индивидуальные условия сотрудничества и гибкие тарифные планы. Наша команда высококвалифицированных специалистов готова предложить оптимальные логистические решения, учитывающие все потребности и пожелания клиента. Мы гарантируем высокий уровень сервиса и оперативную обработку заказов любой сложности.
Что делаем
Ознакомиться с деталями – http://narkolog-na-dom-zhukovskij7.ru
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Подробнее можно узнать тут – нарколог на дом вывод из запоя рязань
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Разобраться лучше – http://narcolog-na-dom-krasnodar14.ru
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Изучить вопрос глубже – http://vyvod-iz-zapoya-v-ryazani14.ru
Формат лечения
Подробнее можно узнать тут – https://narkologicheskaya-klinika-sankt-peterburg14.ru/narkologiya-sankt-peterburg
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Подробнее тут – http://
Домашний визит нарколога — это формат, который соединяет клиническую безопасность и человеческую деликатность. В «КубаньМедЦентре» (Краснодар) мы организуем помощь так, чтобы пациент получал её там, где ему спокойнее всего — у себя дома. Дежурная команда работает круглосуточно, а среднее окно прибытия по городу составляет 30–40 минут с момента подтверждения заявки. Врач приезжает без опознавательных знаков, проводит экспресс-оценку состояния, запускает индивидуально подобранную инфузионную терапию и оставляет подробный план на ближайшие 72 часа. Каждый шаг объясняется простым языком: что мы делаем, зачем это нужно и по каким критериям поймём, что динамика идёт правильно.
Получить больше информации – нарколог на дом недорого
metatrader5 http://metatrader-5-downloads.com .
mt5 download mt5 download .
Этап
Подробнее можно узнать тут – https://kapelnica-ot-zapoya-vidnoe7.ru/kapelnica-ot-zapoya-cena-v-vidnom/
Если на осмотре выявляются спутанность сознания, подозрение на делирий, неукротимая рвота с примесью крови, выраженная боль в груди, тяжёлая одышка, судороги — врач немедленно предложит стационар. Безопасность важнее удобства.
Ознакомиться с деталями – https://kapelnica-ot-zapoya-vidnoe7.ru/
Стандартизированный алгоритм позволяет действовать быстро и безопасно. Он гибко настраивается под конкретный случай, но всегда включает триаж, экспресс-диагностику, старт инфузии, симптом-менеджмент и выдачу плана на 72 часа с «коридорами безопасности».
Детальнее – http://narcolog-na-dom-krasnodar14.ru/narkolog-krasnodar-anonimno/
В этой публикации мы обсуждаем современные методы лечения различных заболеваний. Читатели узнают о новых медикаментах, терапиях и исследованиях, которые активно применяются для лечения. Мы нацелены на то, чтобы предоставить практические знания, которые могут помочь в борьбе с недугами.
Углубиться в тему – наркологический вывод из запоя Симферополь
Перед тем как перечислить типичные случаи, отметим главный принцип: домашний формат выбирают, когда безопасность и прогноз сопоставимы со стационаром, а переезд лишь затянет старт терапии и усилит стресс для семьи.
Детальнее – нарколог на дом круглосуточно
Даже если кажется, что «пройдёт само», при запойных состояниях осложнения нарастают быстро. Перед списком отметим логику: показания к инфузионной терапии определяет врач по совокупности симптомов, хронических заболеваний и текущих показателей. Ниже — типичные ситуации, при которых капельница даёт предсказуемый клинический эффект и снижает риски.
Подробнее – kapelnica-ot-zapoya-vidnoe7.ru/
Replique premium
промокод семяныч 2024 поможет вам сэкономить на покупках в компании!
Такая возможность интересна каждому, кто стремится к экономии.
Чтобы у семьи было чёткое понимание, что и в какой последовательности мы делаем, ниже — рабочий алгоритм для стационара и для выезда на дом (шаги идентичны, различается только объём мониторинга и доступная диагностика).
Изучить вопрос глубже – https://kapelnica-ot-zapoya-vidnoe7.ru/kapelnica-ot-zapoya-anonimno-v-vidnom/
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Изучить вопрос глубже – https://narcolog-na-dom-krasnodar14.ru/narkolog-krasnodar-anonimno
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Детальнее – вызвать нарколога на дом срочно в краснодаре
camera crew in Cortina
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Выяснить больше – помощь нарколога на дому
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Получить больше информации – нарколог на дом анонимно
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Узнать больше – вывод наркологическая клиника
Для купирования абстинентного синдрома и снятия интоксикации используются различные подходы. Врачи подбирают их индивидуально, исходя из состояния пациента.
Ознакомиться с деталями – вывод из запоя на дому недорого рязань
В этой статье мы рассмотрим современные достижения в области медицины, включая инновационные методы лечения и диагностики. Мы обсудим важность профилактики заболеваний и роль технологий в улучшении качества здравоохранения. Читатели узнают о влиянии медицины на повседневную жизнь и ее значение для современного общества.
Узнать больше – вывод из запоя клиника
metatrader5 download metatrader-5-mac.com .
mt5 download https://metatrader-5-downloads.com/ .
Стильный Бренд Одежда Костюмы спортивные – синоним комфорта и функциональности, объединяющие стиль и практичность. Они обеспечивают свободу движений и идеально подходят для тренировок, прогулок на свежем воздухе или в качестве расслабленной повседневной одежды. Выбирая спортивный костюм, обратите внимание на качество материала и посадку, чтобы обеспечить максимальный комфорт и уверенность в себе. С приближением холодных месяцев особую актуальность приобретают утепленные варианты. Худи с начесом – это нежная забота о вашем теле в морозные дни. Обволакивающий комфорт в сочетании со стильным дизайном делает их незаменимым элементом осенне-зимнего гардероба. А для тех, кто ценит функциональность и возможность трансформации образа, худи зип станет отличным выбором. Молния позволяет регулировать теплообмен и создавать различные стильные комбинации.
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Изучить вопрос глубже – https://narcolog-na-dom-krasnodar14.ru
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Узнать больше – вывод из запоя с выездом
подарок на новый год Новый Год – это не просто смена дат в календаре, это волшебное время, наполненное ожиданием чуда, теплом семейного очага и радостью дарения. Подготовка к этому празднику начинается задолго до 31 декабря, и одним из самых приятных хлопот, безусловно, является выбор подарков. Какой подарок принесет наибольшую радость? Как угадать с желанием близкого человека? Ответы на эти вопросы и составляют предновогоднюю суету, полную вдохновения и предвкушения.
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Детальнее – http://www.domen.ru
Формат
Подробнее – наркологическая помощь
Выездная бригада прибывает с необходимым оборудованием. Инфузионная терапия длится 60–120 минут; по ходу процедуры контролируются давление, пульс, дыхание и субъективное самочувствие, при необходимости схема корректируется (темп капания, смена растворов, добавление противорвотных или седативных средств). Чаще всего уже к концу первой инфузии снижается тошнота, уходит дрожь и «внутренняя дрожь», нормализуется сон. Врач оставляет пошаговый план на 24–72 часа: питьевой режим, щадящее питание (дробно, без жирного и острого), режим сна, рекомендации по витаминам и гепатопротекции. Если в процессе выявляются тревожные признаки (нестабильная гемодинамика, выраженная аритмия, спутанность сознания), будет предложен перевод в стационар.
Получить больше информации – narkolog-vyvod-iz-zapoya
Ключевая идея «ДонЗдрава» — соединить доказательную медицину и понятную пациенту логистику. Инфузии рассчитываются через инфузомат, жизненные показатели контролируются портативным кардиомонитором и пульсоксиметром, а лекарственные взаимодействия проверяются по протоколу перед началом терапии. При этом каждый шаг объясняется простым языком: что делаем, зачем это нужно и как будем оценивать результат через 30, 60 и 120 минут. После визита пациент не остаётся один — доступна «горячая линия» и короткие онлайн-сессии с врачом либо психологом, если тревога или бессонница возвращаются в ночные часы.
Ознакомиться с деталями – вывод из запоя с выездом ростов-на-дону
https://geltaxi.ru/taxi-taman–eysk
Перед таблицей важный переход: это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые заболевания и входное состояние, но логика последовательности остаётся неизменной — от безопасности к устойчивости.
Изучить вопрос глубже – https://narkologicheskaya-klinika-lobnya8.ru/narkologicheskaya-klinika-v-lobne-stacionar
списать долги по кредитам процедуры банкротства Процедура банкротства имеет свои плюсы процедуры банкротства физического лица, такие как избавление от долгов и прекращение начисления процентов и штрафов. Однако, важно понимать, что проведение процедуры банкротства – это сложный процесс, требующий юридической грамотности и опыта. Проведение процедуры банкротства должника должно осуществляться под контролем квалифицированного юриста. Необходимо четко понимать процедура банкротства сроки проведения, чтобы быть готовым к длительному процессу. Процедура банкротства физических лиц по кредитам имеет свои особенности, которые необходимо учитывать. Процедура банкротства физического лица в суде требует подготовки документов и участия в судебных заседаниях. Процедура банкротства физического лица пошаговая инструкция поможет сориентироваться в этапах процедуры. Процедура банкротства физического лица через суд – основной способ проведения процедуры. Процедуры банкротства должника физического лица регулируются законодательством о банкротстве.
khao555 login
«АльфаДетокс» в Чехове — это стационарный маршрут вывода из запоя с круглосуточным наблюдением и быстрыми медицинскими решениями. Мы принимаем без очередей, проводим очную оценку, допускаем к терапии и запускаем управляющий детокс с аппаратным контролем и лабораторными исследованиями по показаниям. Наша цель — не просто поставить капельницу, а безопасно стабилизировать давление и пульс, снять интоксикацию и абстиненцию, наладить сон и дать понятный план ближайших дней. Анонимность встроена в процесс, вы общаетесь с командой спокойно и без лишней огласки, а все назначения объясняются простым языком, чтобы вы понимали логику каждого шага.
Получить дополнительную информацию – вывод из запоя московская область
Tham gia cộng đồng game thủ tại Go88 để trải nghiệm các trò chơi bài, poker phổ biến nhất hiện nay.
прогнозы на хоккей Привлечение новых игроков и удержание существующих – это важная задача для букмекерских контор. Бонусы букмекеров и промокоды букмекеров – это эффективный инструмент для мотивации игроков и повышения их лояльности. Бонусы могут быть представлены в виде фрибетов, надбавок к депозиту, кэшбека и других интересных предложений. Важно внимательно изучать условия получения и использования бонусов, чтобы избежать недоразумений. Следить за новостями о ставках на спорт – это важный аспект успешного беттинга. Оперативная информация о травмах игроков, изменениях в составах команд, погодных условиях и других факторах, способных повлиять на исход матча, позволяет принимать своевременные решения и увеличивать свои шансы на выигрыш.
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Подробнее можно узнать тут – помощь вывод из запоя в рязани
консультация по банкротству В лабиринте финансовых затруднений, когда долговое бремя угрожает стабильности, банкротство физических лиц выступает как законный механизм избавления от непосильных обязательств. Однако, это сложный процесс, требующий четкого понимания правовых норм и взвешенной оценки всех рисков. Определяющим фактором часто является банкротство физических лиц сроки процедуры, зависящие от ряда обстоятельств, включая сложность финансового положения должника и оперативность работы судебных органов.
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Узнать больше – частный нарколог на дом краснодар
Наш подход строится на двух принципах: минимально достаточная фармакотерапия и прозрачные «коридоры безопасности». Это означает — никаких «универсальных капельниц» и полипрагмазии. Каждый компонент в схеме имеет проверенную цель: восполнить жидкость, выровнять электролиты, защитить слизистую, снизить вегетативный «шторм» и вернуть возможность естественного сна. Скорость и объём инфузий мы задаём инфузоматом, контролируя давление, пульс, сатурацию и самочувствие на каждом этапе.
Получить дополнительные сведения – вывод из запоя круглосуточно
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Исследовать вопрос подробнее – vyvod-iz-zapoya-v-ryazani14.ru/
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Подробнее можно узнать тут – вывод наркологическая клиника в санкт-петербурге
metatrader5 download https://www.metatrader-5-downloads.com .
ролевые шторы ролевые шторы .
metatrader5 download http://www.metatrader-5-mac.com/ .
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Разобраться лучше – вывод из запоя на дому недорого
При выезде врач действует по установленному протоколу, что гарантирует безопасность и эффективность процедуры.
Изучить вопрос глубже – врач нарколог выезд на дом санкт-петербург
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Разобраться лучше – наркологическая клиника стационар
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Разобраться лучше – наркологическая клиника вывод из запоя санкт-петербург
юридическая консультация по банкротству В непростых финансовых обстоятельствах, когда бремя долгов становится непосильным, процедура банкротства физических лиц может стать спасительным кругом. Однако, прежде чем решиться на этот шаг, необходимо тщательно изучить все аспекты и нюансы, связанные с данной процедурой. Важным вопросом является определение сроков процедуры банкротства физических лиц, которые могут варьироваться в зависимости от сложности дела и загруженности судебной системы.
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Узнать больше – вывод из запоя цена в рязани
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Изучить вопрос глубже – срочный вывод из запоя
В условиях медицинского контроля специалисты выполняют последовательные действия, направленные на стабилизацию состояния пациента.
Углубиться в тему – вывод из запоя с выездом рязань
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Разобраться лучше – скорая вывод из запоя в рязани
Этот обзор посвящен успешным стратегиям избавления от зависимости, включая реальные примеры и советы. Мы разоблачим мифы и предоставим читателям достоверную информацию о различных подходах. Получите опыт многообразия методов и найдите подходящий способ для себя!
Узнать больше – вывод из запоя недорого Симферополь
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Подробнее можно узнать тут – http://narcolog-na-dom-krasnodar14.ru
Этот обзор сосредоточен на различных подходах к избавлению от зависимости. Мы изучим традиционные и альтернативные методы, а также их сочетание для достижения максимальной эффективности. Читатели смогут открыть для себя новые стратегии и подходы, которые помогут в их борьбе с зависимостями.
Углубиться в тему – http://www.dafna-clinic.ru
В этой статье мы рассмотрим современные достижения в области медицины, включая инновационные методы лечения и диагностики. Мы обсудим важность профилактики заболеваний и роль технологий в улучшении качества здравоохранения. Читатели узнают о влиянии медицины на повседневную жизнь и ее значение для современного общества.
Ознакомиться с деталями – вывод из запоя в стационаре москва
Палата — это контролируемая среда: аппаратный мониторинг, по показаниям ЭКГ и базовая лаборатория, пост медсестёр 24/7, переоценки по графику и быстрая коррекция тактики без логистических пауз. Такой старт рационален при длительных эпизодах, выраженных колебаниях давления и пульса, повторных судорогах, неукротимой рвоте и признаках надвигающегося делирия, а также если дома невозможно обеспечить «тихий режим» и присутствие взрослого помощника ночью. В стационарной ветке меньше случайностей, а путь до стабильного сна короче.
Подробнее тут – наркологическая клиника обратный звонок
В этой статье мы рассмотрим современные достижения в области медицины, включая инновационные методы лечения и диагностики. Мы обсудим важность профилактики заболеваний и роль технологий в улучшении качества здравоохранения. Читатели узнают о влиянии медицины на повседневную жизнь и ее значение для современного общества.
Разобраться лучше – срочный вывод из запоя в Симферополе
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Получить больше информации – вывод из запоя на дому недорого ростов-на-дону
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Ознакомиться с деталями – наркологическая клиника клиника помощь санкт-петербург
списать долги через банкротство физических лиц Прежде чем инициировать процедуру, крайне важно получить всестороннюю информацию о её аспектах. Бесплатная консультация по банкротству или бесплатная консультация юриста по банкротству станет первым шагом к пониманию перспектив и потенциальных последствий. Важно выяснить, как происходит списание долгов по кредитам и какие долги списывают через банкротство, поскольку не все обязательства подлежат аннулированию. Квалифицированная консультация по банкротству физических лиц поможет сориентироваться в юридических тонкостях и разработать оптимальную стратегию. Онлайн консультация по банкротству – удобный формат для получения первичной информации. Решение о банкротстве сопряжено с рядом последствий, поэтому необходимо тщательно взвесить все плюсы процедуры банкротства физического лица. К ним относится возможность списать долг по кредиту банкротство и начать жизнь с чистого листа. Однако, следует учитывать, что проведение процедуры банкротства – это ответственный шаг, требующий соблюдения строгих правил и участия квалифицированных специалистов. Особое внимание следует уделить вопросам: процедура банкротства сроки проведения, процедура банкротства физических лиц по кредитам, процедура банкротства физического лица в суде, процедура банкротства физического лица пошаговая инструкция.
«НеваМед» — частная наркологическая клиника в Санкт-Петербурге, где клиническая точность сочетается с бережной коммуникацией и безусловной конфиденциальностью. Мы делаем лечение не «разовым визитом ради капельницы», а продуманным маршрутом, в котором каждый шаг имеет понятную цель, сроки оценки и прозрачные критерии эффективности. Для пациента это означает предсказуемость первых суток, сохранение личного пространства и ощущение контролируемой динамики, а для близких — ясные правила помощи без тревожных импровизаций.
Подробнее тут – http://
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Узнать больше – помощь вывод из запоя ростов-на-дону
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Получить дополнительные сведения – вызвать нарколога на дом срочно санкт-петербург
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Изучить вопрос глубже – вывод из запоя капельница рязань
Алкогольный запой приводит к тяжёлой интоксикации, при которой организм теряет способность к самостоятельному восстановлению. Вывод из запоя в клинике предполагает использование инфузионной терапии, медикаментов для нормализации работы сердца, печени и нервной системы, а также витаминных комплексов для восполнения дефицита питательных веществ.
Детальнее – наркологический вывод из запоя рязань
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Подробнее тут – vivod-iz-zapoya-rostov14.ru/
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Получить дополнительную информацию – http://vivod-iz-zapoya-rostov14.ru/vyvod-iz-zapoya-na-domu-rostov-na-donu/https://vivod-iz-zapoya-rostov14.ru
mt5 download mac http://www.metatrader-5-downloads.com/ .
рулонные шторы автоматические рулонные шторы автоматические .
mt5 mac https://www.metatrader-5-mac.com .
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Узнать больше – вывод из запоя недорого ростов-на-дону
Время — ключевой ресурс при абстиненции и интоксикации. Ниже — ориентиры, которые помогут семье принять решение не откладывать обращение. Если совпадает хотя бы один пункт, лучше сразу обсудить ситуацию с дежурным наркологом и подготовить пространство для визита.
Подробнее можно узнать тут – вывод из запоя на дому в ростове-на-дону
Лобня — город коротких дистанций, но в острых ситуациях решает не километраж, а управляемость. Мы убираем паузы между решением обратиться и реальной помощью: на звонке быстро оцениваем риски, предлагаем безопасный старт в квартире или в палате, согласуем окно прибытия, объясняем что подготовить, и фиксируем честный диапазон стоимости. Цель — чтобы первые часы прошли по понятному плану, а не вслепую.
Исследовать вопрос подробнее – http://narkologicheskaya-klinika-lobnya8.ru
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Узнать больше – помощь нарколога на дому в краснодаре
В этой публикации мы предложим ряд рекомендаций по избавлению от зависимостей и успешному восстановлению. Мы обсудим методы привлечения поддержки и важность самосознания. Эти советы помогут людям вернуться к нормальной жизни и стать на путь выздоровления.
Узнать больше – скорая вывод из запоя москва
Что делаем
Разобраться лучше – https://vyvod-iz-zapoya-v-stacionare-chekhov8.ru/
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Подробнее тут – вызвать нарколога на дом срочно
?????????
blsp ap
leading film production company in Milan High-end production company in Milan Italy: Catering to luxury brands and discerning clients, delivering sophisticated and visually stunning content.
https://www.haofinder.com/blog/bruno-mars-by-the-numbers-from-billions-of-streams-to-record-vegas-paydays
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Детальнее – https://vivod-iz-zapoya-rostov14.ru/rostov-vyvod-iz-zapoya
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Выяснить больше – вывод из запоя на дому в ростове-на-дону
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Ознакомиться с деталями – https://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare/
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Разобраться лучше – http://narcolog-na-dom-krasnodar14.ru
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Детальнее – вывод из запоя в стационаре
промокод семяныч 2024 поможет вам сэкономить на покупках в компании!
Здесь можно найти разнообразные товары, доступные для приобретения со скидкой.
Với giao diện mượt mà và ưu đãi hấp dẫn, MM88 là lựa chọn lý tưởng cho các tín đồ giải trí trực tuyến.
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Узнать больше – анонимный вывод из запоя в ростове-на-дону
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Выяснить больше – врач нарколог на дом в краснодаре
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее – http://narkolog-na-dom-sankt-peterburg14.ru/narkolog-sankt-peterburg/
рулонные шторы с пультом рулонные шторы с пультом .
mt5 http://metatrader-5-downloads.com/ .
metatrader 5 mac metatrader 5 mac .
Алкогольный эпизод — это не один симптом, а целая сцепка процессов: обезвоживание, электролитные сдвиги, скачки давления и пульса, тремор, тошнота, тревога, нарушения сна; нередко добавляются проблемы со стороны желудка и печени. Шаблонная капельница игнорирует индивидуальную картину и часто даёт кратковременный эффект с ночным откатом. Мы работаем иначе: допускаем к терапии, подбираем состав и темп инфузии под текущие цифры и динамику, избегаем конфликтов с уже принятыми препаратами и объясняем, чего ожидать по ощущениям на каждом шаге. Избыточная седация не усиливает лечение — она делает его менее предсказуемым.
Получить дополнительную информацию – лобня наркология
Прежде чем перейти к таблице, отметим смысл. Это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые диагнозы и динамику симптомов, но логика процесса остаётся неизменной: от безопасности к устойчивости.
Ознакомиться с деталями – https://vyvod-iz-zapoya-v-stacionare-chekhov8.ru/vyvod-iz-zapoya-cena-v-chekhove
В этой статье мы подробно рассматриваем проверенные методы борьбы с зависимостями, включая психотерапию, медикаментозное лечение и поддержку со стороны общества. Мы акцентируем внимание на важности комплексного подхода и возможности успешного восстановления для людей, столкнувшихся с этой проблемой.
Получить дополнительную информацию – [url=https://dafna-clinic.ru/]вывод из запоя капельница на дому в Симферополе[/url]
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Подробнее тут – https://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr
Нарколог на дом в Санкт-Петербурге — это востребованная медицинская услуга, позволяющая получить помощь в комфортных домашних условиях. Такой формат особенно актуален в ситуациях, когда пациент не может или не хочет обращаться в стационар. Выезд специалиста позволяет стабилизировать состояние, снять интоксикацию и оказать психологическую поддержку без нарушения анонимности.
Подробнее тут – https://narkolog-na-dom-sankt-peterburg14.ru
??????????????????????????????????
Палата — это контролируемая среда: аппаратный мониторинг, по показаниям ЭКГ и базовая лаборатория, пост медсестёр 24/7, переоценки по графику и быстрая коррекция тактики без логистических пауз. Такой старт рационален при длительных эпизодах, выраженных колебаниях давления и пульса, повторных судорогах, неукротимой рвоте и признаках надвигающегося делирия, а также если дома невозможно обеспечить «тихий режим» и присутствие взрослого помощника ночью. В стационарной ветке меньше случайностей, а путь до стабильного сна короче.
Изучить вопрос глубже – государственная наркологическая клиника
Этот медицинский обзор сосредоточен на последних достижениях, которые оказывают влияние на пациентов и медицинскую практику. Мы разбираем инновационные методы лечения и исследований, акцентируя внимание на их значимости для общественного здоровья. Читатели узнают о свежих данных и их возможном применении.
Исследовать вопрос подробнее – анонимный вывод из запоя москва
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить дополнительные сведения – вывод из запоя в стационаре рязань
https://www.lawglobalhub.com/flower-films-how-drew-barrymore-became-a-successful/
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Получить дополнительную информацию – психиатр нарколог на дом краснодар
bsme at
Перед таблицей важный переход: это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые заболевания и входное состояние, но логика последовательности остаётся неизменной — от безопасности к устойчивости.
Ознакомиться с деталями – chastnaya-narkologicheskaya-klinika
Нарколог на дом в Санкт-Петербурге — это востребованная медицинская услуга, позволяющая получить помощь в комфортных домашних условиях. Такой формат особенно актуален в ситуациях, когда пациент не может или не хочет обращаться в стационар. Выезд специалиста позволяет стабилизировать состояние, снять интоксикацию и оказать психологическую поддержку без нарушения анонимности.
Углубиться в тему – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-v-sankt-peterburge-vyezd-nadom/
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Получить дополнительные сведения – нарколог на дом срочно в краснодаре
Этот краткий обзор предлагает сжатую информацию из области медицины, включая ключевые факты и последние новости. Мы стремимся сделать информацию доступной и понятной для широкой аудитории, что позволит читателям оставаться в курсе актуальных событий в здравоохранении.
Подробнее тут – вывод из запоя круглосуточно москва
Дом — это тишина, отсутствие «социального шума» и лишних свидетелей. Выездной врач «НоваТонуса» приезжает анонимно, начинает с очной оценки и допуска к терапии, сверяет совместимости с тем, что человек принимал за последние двое суток, проверяет давление, пульс, сатурацию, температуру, кратко оценивает неврологический статус и уровень тревоги. Только после допуска запускается индивидуальная инфузионная поддержка: коррекция воды и электролитов, защита органов мишеней, симптом-контроль тошноты и головокружения, при показаниях — мягкая настройка сна без избыточной седации. В конце визита — переоценка, перевод на per os-схемы, памятка на 24–48 часов и заранее оговорённое окно контрольного контакта. Такой маршрут даёт устойчивую динамику на сутки и неделю, а не минутное облегчение.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-lobnya8.ru/narkologicheskaya-klinika-dlya-alkogolikov-v-lobne
В этой статье мы рассмотрим современные достижения в области медицины, включая инновационные методы лечения и диагностики. Мы обсудим важность профилактики заболеваний и роль технологий в улучшении качества здравоохранения. Читатели узнают о влиянии медицины на повседневную жизнь и ее значение для современного общества.
Исследовать вопрос подробнее – срочный вывод из запоя Симферополь
https://litegps.ru/osennij-uhod-za-gazonom-kak-podgotovit-travu-k-zime.html
«НоваТонус» — это связанный маршрут наркологической помощи для жителей Лобни и округа: оперативный выезд врача на дом, аккуратный домашний детокс без «универсальных коктейлей», стационар с круглосуточным наблюдением, подготовка к кодированию по показаниям и поддержка семьи в первые недели. Мы действуем по принципу клинической достаточности: каждое назначение обосновано, объясняется простым языком и привязано к реальным целям — безопасно снять интоксикацию и абстиненцию, стабилизировать давление и пульс, мягко вернуть сон, а затем провести первую «тихую» неделю без качелей. Приватность встроена в процесс: выезд без опознавательных знаков, нейтральный канал связи, документы по запросу и в сдержанной формулировке.
Получить дополнительные сведения – narkolog-i-psihiatr-v-lobne
Нарколог на дом в Санкт-Петербурге — это востребованная медицинская услуга, позволяющая получить помощь в комфортных домашних условиях. Такой формат особенно актуален в ситуациях, когда пациент не может или не хочет обращаться в стационар. Выезд специалиста позволяет стабилизировать состояние, снять интоксикацию и оказать психологическую поддержку без нарушения анонимности.
Получить дополнительные сведения – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-sankt-peterburg/
Эта публикация обращает внимание на важность профилактики зависимостей. Мы обсудим, как осведомленность и образование могут помочь в предотвращении возникновения зависимости. Читатели смогут ознакомиться с полезными советами и ресурсами, которые способствуют здоровому образу жизни.
Подробнее – срочный вывод из запоя в Симферополе
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-v-ryazani14.ru
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Подробнее можно узнать тут – https://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr/
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Получить дополнительную информацию – психиатр нарколог на дом санкт-петербург
перкарбонат натрия оптом РТХ – партнер, которому можно доверять: обеспечиваем стабильные поставки качественной химии для развития Вашего бизнеса.
ca cuoc bong da truc tuyen
Этот обзор медицинских исследований собрал самое важное из последних публикаций в области медицины. Мы проанализировали ключевые находки и представили их в доступной форме, чтобы читатели могли легко ориентироваться в актуальных темах. Этот материал станет отличным подспорьем для изучения медицины.
Ознакомиться с деталями – врач вывод из запоя в москве
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Выяснить больше – http://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr/
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Выяснить больше – https://narcolog-na-dom-krasnodar14.ru/narkolog-i-psikhiatr-v-krasnodare/
Домашний визит нарколога — это формат, который соединяет клиническую безопасность и человеческую деликатность. В «КубаньМедЦентре» (Краснодар) мы организуем помощь так, чтобы пациент получал её там, где ему спокойнее всего — у себя дома. Дежурная команда работает круглосуточно, а среднее окно прибытия по городу составляет 30–40 минут с момента подтверждения заявки. Врач приезжает без опознавательных знаков, проводит экспресс-оценку состояния, запускает индивидуально подобранную инфузионную терапию и оставляет подробный план на ближайшие 72 часа. Каждый шаг объясняется простым языком: что мы делаем, зачем это нужно и по каким критериям поймём, что динамика идёт правильно.
Выяснить больше – вызвать нарколога на дом краснодар
Дом — это тишина, отсутствие «социального шума» и лишних свидетелей. Выездной врач «НоваТонуса» приезжает анонимно, начинает с очной оценки и допуска к терапии, сверяет совместимости с тем, что человек принимал за последние двое суток, проверяет давление, пульс, сатурацию, температуру, кратко оценивает неврологический статус и уровень тревоги. Только после допуска запускается индивидуальная инфузионная поддержка: коррекция воды и электролитов, защита органов мишеней, симптом-контроль тошноты и головокружения, при показаниях — мягкая настройка сна без избыточной седации. В конце визита — переоценка, перевод на per os-схемы, памятка на 24–48 часов и заранее оговорённое окно контрольного контакта. Такой маршрут даёт устойчивую динамику на сутки и неделю, а не минутное облегчение.
Ознакомиться с деталями – наркологическая клиника стационар
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Углубиться в тему – http://vyvod-iz-zapoya-v-ryazani14.ru/vykhod-iz-zapoya-ryazan/
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Подробнее – анонимный вывод из запоя
В этой статье мы рассматриваем разные способы борьбы с алкогольной зависимостью. Обсуждаются методы лечения, программы реабилитации и советы для поддержки близких. Читатели получат информацию о том, как преодолеть зависимость и добиться успешного выздоровления.
Подробнее можно узнать тут – помощь вывод из запоя москва
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Подробнее можно узнать тут – выезд нарколога на дом
Такая последовательность действий обеспечивает системное воздействие и минимизирует риски осложнений.
Исследовать вопрос подробнее – нарколог на дом клиника в санкт-петербурге
В этой статье мы рассматриваем разные способы борьбы с алкогольной зависимостью. Обсуждаются методы лечения, программы реабилитации и советы для поддержки близких. Читатели получат информацию о том, как преодолеть зависимость и добиться успешного выздоровления.
Подробнее тут – вывод из запоя капельница в москве
Стационар — это контролируемая среда, где меньше случайностей и выше скорость принятия решений. В палате рядом оборудование, пост медсестёр и врачебная переоценка по расписанию, поэтому тактика корректируется без задержек. Это особенно важно при длительных эпизодах и заметных колебаниях самочувствия, когда дома сложно обеспечить тихий режим и круглосуточное наблюдение. В «АльфаДетоксе» мы придерживаемся принципа клинической достаточности: никаких избыточных седативных нагрузок и сомнительных «коктейлей», только то, что реально влияет на исход.
Подробнее тут – vyvod-iz-zapoya-v-chastnoj-klinike
Стандартизированный алгоритм позволяет действовать быстро и безопасно. Он гибко настраивается под конкретный случай, но всегда включает триаж, экспресс-диагностику, старт инфузии, симптом-менеджмент и выдачу плана на 72 часа с «коридорами безопасности».
Подробнее можно узнать тут – вызвать нарколога на дом краснодар
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Детальнее – вызов нарколога на дом в краснодаре
Этот информативный текст сочетает в себе темы здоровья и зависимости. Мы обсудим, как хронические заболевания могут усугубить зависимости и наоборот, как зависимость может влиять на общее состояние здоровья. Читатели получат представление о комплексном подходе к лечению как физического, так и психического состояния.
Подробнее тут – вывод из запоя клиника
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Подробнее тут – платный нарколог на дом
В первые часы важно не «залить» пациента растворами, а корректно подобрать темп и состав с учётом возраста, массы тела, артериального давления, лекарственного фона (антигипертензивные, сахароснижающие, антиаритмические препараты) и переносимости. Именно поэтому мы не отдаём лечение на откуп шаблонам — каждая схема конструируется врачом на месте, а эффективность оценивается по понятным метрикам.
Получить больше информации – вывод из запоя вызов на дом в рязани
Алкогольный эпизод — это не один симптом, а целая сцепка процессов: обезвоживание, электролитные сдвиги, скачки давления и пульса, тремор, тошнота, тревога, нарушения сна; нередко добавляются проблемы со стороны желудка и печени. Шаблонная капельница игнорирует индивидуальную картину и часто даёт кратковременный эффект с ночным откатом. Мы работаем иначе: допускаем к терапии, подбираем состав и темп инфузии под текущие цифры и динамику, избегаем конфликтов с уже принятыми препаратами и объясняем, чего ожидать по ощущениям на каждом шаге. Избыточная седация не усиливает лечение — она делает его менее предсказуемым.
Изучить вопрос глубже – http://narkologicheskaya-klinika-lobnya8.ru
Что делаем
Углубиться в тему – https://vyvod-iz-zapoya-v-stacionare-chekhov8.ru/vyvod-iz-zapoya-na-domu-v-chekhove/
Состав инфузии мы подбираем под доминирующие симптомы и сопутствующие заболевания. Цель — вернуть управляемость телу, а не «насытить» организм всем сразу. Матрица ниже демонстрирует клиническую логику: окончательное решение принимает врач после очной оценки.
Детальнее – вывод из запоя недорого
Ниже представлена карта действий бригады «РязМедСервиса» в первые три часа. Это не «жёсткая сетка», а ориентир для безопасной и быстрой стабилизации. В каждом блоке есть клиническая цель, измеримые критерии и условие для перехода к следующему шагу.
Исследовать вопрос подробнее – вывод из запоя с выездом
В этой статье рассматриваются различные аспекты избавления от зависимости, включая физические и психологические методы. Мы обсудим поддержку, мотивацию и стратегии, которые помогут в процессе выздоровления. Читатели узнают, как преодолеть трудности и двигаться к новой жизни без зависимости.
Выяснить больше – наркология вывод из запоя москва
«НеваМед» — частная наркологическая клиника в Санкт-Петербурге, где клиническая точность сочетается с бережной коммуникацией и безусловной конфиденциальностью. Мы делаем лечение не «разовым визитом ради капельницы», а продуманным маршрутом, в котором каждый шаг имеет понятную цель, сроки оценки и прозрачные критерии эффективности. Для пациента это означает предсказуемость первых суток, сохранение личного пространства и ощущение контролируемой динамики, а для близких — ясные правила помощи без тревожных импровизаций.
Получить дополнительные сведения – наркологическая клиника стационар санкт-петербург
Лобня — город коротких дистанций, но в острых ситуациях решает не километраж, а управляемость. Мы убираем паузы между решением обратиться и реальной помощью: на звонке быстро оцениваем риски, предлагаем безопасный старт в квартире или в палате, согласуем окно прибытия, объясняем что подготовить, и фиксируем честный диапазон стоимости. Цель — чтобы первые часы прошли по понятному плану, а не вслепую.
Получить дополнительные сведения – chastnaya-narkologicheskaya-klinika
Этап
Разобраться лучше – vyvod-iz-zapoya
Домашний визит нарколога — это формат, который соединяет клиническую безопасность и человеческую деликатность. В «КубаньМедЦентре» (Краснодар) мы организуем помощь так, чтобы пациент получал её там, где ему спокойнее всего — у себя дома. Дежурная команда работает круглосуточно, а среднее окно прибытия по городу составляет 30–40 минут с момента подтверждения заявки. Врач приезжает без опознавательных знаков, проводит экспресс-оценку состояния, запускает индивидуально подобранную инфузионную терапию и оставляет подробный план на ближайшие 72 часа. Каждый шаг объясняется простым языком: что мы делаем, зачем это нужно и по каким критериям поймём, что динамика идёт правильно.
Подробнее тут – http://narcolog-na-dom-krasnodar14.ru/krasnodar-narkologicheskij-czentr/
Комплексное применение этих средств ускоряет процесс восстановления.
Подробнее можно узнать тут – https://narkolog-na-dom-sankt-peterburg14.ru/narkolog-na-dom-anonimno-spb/
Алкогольный запой приводит к тяжёлой интоксикации, при которой организм теряет способность к самостоятельному восстановлению. Вывод из запоя в клинике предполагает использование инфузионной терапии, медикаментов для нормализации работы сердца, печени и нервной системы, а также витаминных комплексов для восполнения дефицита питательных веществ.
Получить больше информации – врач вывод из запоя в рязани
Перед таблицей важный переход: это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые заболевания и входное состояние, но логика последовательности остаётся неизменной — от безопасности к устойчивости.
Разобраться лучше – https://narkologicheskaya-klinika-lobnya8.ru/narkologicheskaya-klinika-dlya-alkogolikov-v-lobne/
Этот обзор сосредоточен на различных подходах к избавлению от зависимости. Мы изучим традиционные и альтернативные методы, а также их сочетание для достижения максимальной эффективности. Читатели смогут открыть для себя новые стратегии и подходы, которые помогут в их борьбе с зависимостями.
Детальнее – вывод из запоя на дому цена в Симферополе
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Получить дополнительные сведения – вызвать нарколога на дом срочно
В данной статье мы акцентируем внимание на важности поддержки в процессе выздоровления. Мы обсудим, как друзья, семья и профессионалы могут помочь тем, кто сталкивается с зависимостями. Читатели получат практические советы, как поддерживать близких на пути к новой жизни.
Изучить вопрос глубже – вывод из запоя вызов на дом в Симферополе
Этап
Выяснить больше – [url=https://vyvod-iz-zapoya-v-stacionare-chekhov8.ru/]vyvod-iz-zapoya-na-domu-oblast[/url]
Алкогольный эпизод — это не один симптом, а целая сцепка процессов: обезвоживание, электролитные сдвиги, скачки давления и пульса, тремор, тошнота, тревога, нарушения сна; нередко добавляются проблемы со стороны желудка и печени. Шаблонная капельница игнорирует индивидуальную картину и часто даёт кратковременный эффект с ночным откатом. Мы работаем иначе: допускаем к терапии, подбираем состав и темп инфузии под текущие цифры и динамику, избегаем конфликтов с уже принятыми препаратами и объясняем, чего ожидать по ощущениям на каждом шаге. Избыточная седация не усиливает лечение — она делает его менее предсказуемым.
Получить дополнительную информацию – https://narkologicheskaya-klinika-lobnya8.ru/narkologicheskaya-klinika-dlya-alkogolikov-v-lobne
«Как отмечает врач-нарколог Андрей Николаевич Селиванов, «своевременный визит специалиста на дом позволяет избежать тяжёлых осложнений и ускоряет стабилизацию состояния»».
Получить дополнительные сведения – нарколог на дом срочно
Прежде чем перейти к таблице, отметим смысл. Это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые диагнозы и динамику симптомов, но логика процесса остаётся неизменной: от безопасности к устойчивости.
Детальнее – https://vyvod-iz-zapoya-v-stacionare-chekhov8.ru/vyvod-iz-zapoya-cena-v-chekhove/
Стандартизированный алгоритм позволяет действовать быстро и безопасно. Он гибко настраивается под конкретный случай, но всегда включает триаж, экспресс-диагностику, старт инфузии, симптом-менеджмент и выдачу плана на 72 часа с «коридорами безопасности».
Детальнее – вызвать нарколога на дом
В этой статье мы обсудим процесс восстановления после зависимостей, акцентируя внимание на различных методах и подходах к реабилитации. Читатели узнают, как создать план выздоровления и использовать полезные ресурсы для достижения устойчивых изменений.
Получить больше информации – вывод из запоя капельница
В этой статье рассматриваются различные аспекты избавления от зависимости, включая физические и психологические методы. Мы обсудим поддержку, мотивацию и стратегии, которые помогут в процессе выздоровления. Читатели узнают, как преодолеть трудности и двигаться к новой жизни без зависимости.
Разобраться лучше – вывод из запоя на дому круглосуточно Симферополь
Первые сутки после прекращения алкоголя — самые уязвимые: именно в это время нарастают абстинентные симптомы и риск осложнений. Ниже приведены основные ситуации, при которых нужен быстрый выезд врача. Перед списком отметим: если сомневаетесь, позвоните координатору — он уточнит признаки и подскажет безопасные действия до прибытия команды.
Узнать больше – вывод из запоя
Перед тем как перечислить типичные случаи, отметим главный принцип: домашний формат выбирают, когда безопасность и прогноз сопоставимы со стационаром, а переезд лишь затянет старт терапии и усилит стресс для семьи.
Изучить вопрос глубже – narkolog-na-dom-nedorogo
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Разобраться лучше – https://narkologicheskaya-klinika-v-spb14.ru/narkolog-sankt-peterburg
Лобня — город коротких дистанций, но в острых ситуациях решает не километраж, а управляемость. Мы убираем паузы между решением обратиться и реальной помощью: на звонке быстро оцениваем риски, предлагаем безопасный старт в квартире или в палате, согласуем окно прибытия, объясняем что подготовить, и фиксируем честный диапазон стоимости. Цель — чтобы первые часы прошли по понятному плану, а не вслепую.
Подробнее тут – narkologicheskaya-klinika
Алкогольный эпизод — это не один симптом, а целая сцепка процессов: обезвоживание, электролитные сдвиги, скачки давления и пульса, тремор, тошнота, тревога, нарушения сна; нередко добавляются проблемы со стороны желудка и печени. Шаблонная капельница игнорирует индивидуальную картину и часто даёт кратковременный эффект с ночным откатом. Мы работаем иначе: допускаем к терапии, подбираем состав и темп инфузии под текущие цифры и динамику, избегаем конфликтов с уже принятыми препаратами и объясняем, чего ожидать по ощущениям на каждом шаге. Избыточная седация не усиливает лечение — она делает его менее предсказуемым.
Разобраться лучше – lobnya-narkologicheskij-dispanser
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Получить дополнительную информацию – вызвать нарколога на дом
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Разобраться лучше – вывод из запоя капельница
«АльфаДетокс» в Чехове — это стационарный маршрут вывода из запоя с круглосуточным наблюдением и быстрыми медицинскими решениями. Мы принимаем без очередей, проводим очную оценку, допускаем к терапии и запускаем управляющий детокс с аппаратным контролем и лабораторными исследованиями по показаниям. Наша цель — не просто поставить капельницу, а безопасно стабилизировать давление и пульс, снять интоксикацию и абстиненцию, наладить сон и дать понятный план ближайших дней. Анонимность встроена в процесс, вы общаетесь с командой спокойно и без лишней огласки, а все назначения объясняются простым языком, чтобы вы понимали логику каждого шага.
Подробнее можно узнать тут – vyvod-iz-zapoya-alkogolikov
В этом обзоре мы обсудим современные методы борьбы с зависимостями, включая медикаментозную терапию и психотерапию. Мы представим последние исследования и их результаты, чтобы читатели могли быть в курсе наиболее эффективных подходов к лечению и поддержке.
Исследовать вопрос подробнее – вывод из запоя на дому в москве
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее можно узнать тут – нарколог на дом срочно в санкт-петербурге
оценка мебели после залива оценка мебели после залива .
В этой заметке мы представляем шаги, которые помогут в процессе преодоления зависимостей. Рассматриваются стратегии поддержки и чек-листы для тех, кто хочет сделать первый шаг к выздоровлению. Наша цель — вдохновить читателей на положительные изменения и поддержать их в трудных моментах.
Получить больше информации – https://i-klinik.ru
купить филлеры для косметологов http://www.filler-kupit.ru .
сколько стоит сделать курсовую работу на заказ kupit-kursovuyu-8.ru .
заказать курсовую работу заказать курсовую работу .
«НеваМед» — частная наркологическая клиника в Санкт-Петербурге, где клиническая точность сочетается с бережной коммуникацией и безусловной конфиденциальностью. Мы делаем лечение не «разовым визитом ради капельницы», а продуманным маршрутом, в котором каждый шаг имеет понятную цель, сроки оценки и прозрачные критерии эффективности. Для пациента это означает предсказуемость первых суток, сохранение личного пространства и ощущение контролируемой динамики, а для близких — ясные правила помощи без тревожных импровизаций.
Детальнее – https://narkologicheskaya-klinika-v-spb14.ru/narkologicheskaya-bolnicza-sankt-peterburg/
Ключевая идея «ДонЗдрава» — соединить доказательную медицину и понятную пациенту логистику. Инфузии рассчитываются через инфузомат, жизненные показатели контролируются портативным кардиомонитором и пульсоксиметром, а лекарственные взаимодействия проверяются по протоколу перед началом терапии. При этом каждый шаг объясняется простым языком: что делаем, зачем это нужно и как будем оценивать результат через 30, 60 и 120 минут. После визита пациент не остаётся один — доступна «горячая линия» и короткие онлайн-сессии с врачом либо психологом, если тревога или бессонница возвращаются в ночные часы.
Получить дополнительную информацию – вывод из запоя клиника ростов-на-дону
«НеваМед» — частная наркологическая клиника в Санкт-Петербурге, где клиническая точность сочетается с бережной коммуникацией и безусловной конфиденциальностью. Мы делаем лечение не «разовым визитом ради капельницы», а продуманным маршрутом, в котором каждый шаг имеет понятную цель, сроки оценки и прозрачные критерии эффективности. Для пациента это означает предсказуемость первых суток, сохранение личного пространства и ощущение контролируемой динамики, а для близких — ясные правила помощи без тревожных импровизаций.
Получить дополнительную информацию – частная наркологическая клиника
снять девочку спб Заказать девушку СПб: Заказ эскорт-услуг – это возможность создать индивидуальный сценарий вашего досуга, где каждый деталь будет соответствовать вашим желаниям.
скачать игры по прямой ссылке Скачать игры с Яндекс Диска: Ваша игровая коллекция всегда под рукой. Яндекс Диск – это не просто облачное хранилище, это удобная платформа для обмена играми с друзьями и создания собственной коллекции любимых проектов. Делитесь своими игровыми находками, скачивайте игры, предоставленные другими пользователями, и наслаждайтесь совместным игровым опытом. Это отличный способ расширить свою игровую библиотеку и всегда иметь доступ к любимым играм, где бы вы ни находились.
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Углубиться в тему – врач нарколог на дом санкт-петербург
Перед таблицей важный переход: это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые заболевания и входное состояние, но логика последовательности остаётся неизменной — от безопасности к устойчивости.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-lobnya8.ru/narkologicheskaya-klinika-ceny-v-lobne/
силикон оптом от производителя РТХ – партнер, которому можно доверять: обеспечиваем стабильные поставки качественной химии для развития Вашего бизнеса.
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Получить дополнительную информацию – http://narkolog-na-dom-sankt-peterburg14.ru/narkolog-sankt-peterburg/
Этап
Получить дополнительную информацию – капельница от запоя
Для купирования абстинентного синдрома и снятия интоксикации используются различные подходы. Врачи подбирают их индивидуально, исходя из состояния пациента.
Получить дополнительные сведения – вывод из запоя на дому недорого
Выбор техники зависит от клинической картины, переносимости препаратов, психоэмоционального состояния и горизонта планируемой трезвости. Таблица ниже помогает сориентироваться в ключевых различиях — врач подробно разберёт нюансы на очной консультации.
Получить дополнительную информацию – http://kodirovanie-ot-alkogolizma-vidnoe7.ru/kodirovanie-ot-alkogolizma-na-domu-v-vidnom/
В этой медицинской статье мы погрузимся в актуальные вопросы здравоохранения и лечения заболеваний. Читатели узнают о современных подходах, методах диагностики и новых открытий в научных исследованиях. Наша цель — донести важную информацию и повысить уровень осведомленности о здоровье.
Подробнее тут – вывод из запоя с выездом в москве
Вывод из запоя в Рязани является востребованной медицинской услугой, направленной на стабилизацию состояния пациента после длительного употребления алкоголя. Специалисты применяют современные методы детоксикации, позволяющие быстро и безопасно восстановить жизненно важные функции организма, снизить проявления абстинентного синдрома и предотвратить осложнения. Процесс лечения осуществляется в клинических условиях под постоянным наблюдением врачей.
Получить больше информации – https://vyvod-iz-zapoya-ryazan14.ru/vyvod-iz-zapoya-ryazan-na-domu/
Этап
Получить больше информации – vyvod-iz-zapoya-v-domashnih-usloviyah
Даже при амбулаторном ведении мы следуем принципам доказательной медицины: пошаговая титрация, ясные коридоры безопасности, пересмотр решений строго по показателям. Мы объясняем, на что ориентироваться в первые часы после визита: диапазоны давления и пульса, ориентиры самочувствия, правила питания и питья, поведенческие «якоря» на случай, если тревога неожиданно вырастет вечером. Благодаря этому пациент и его семья не остаются один на один с вопросами; наоборот — у них есть карта маршрута и контакты людей, готовых включиться в течение минуты.
Получить дополнительную информацию – помощь нарколога на дому краснодар
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Выяснить больше – врач нарколог на дом краснодар
Наша философия проста: минимум медикаментов, максимум управляемости процесса. Мы не используем «универсальные капельницы», а собираем схему под клиническую картину: длительность запоя, выраженность тремора и тошноты, качество сна, уровень тревоги, исходное давление и частоту пульса, сопутствующие заболевания, текущие лекарства (антигипертензивные, антиаритмические, сахароснижающие, средства для сна). Скорость инфузии задаётся инфузоматом, витальные показатели контролируются портативным кардиомонитором и пульсоксиметром, глюкоза и электролиты — по экспресс-панелям. Такой подход снижает риск осложнений и делает результат предсказуемым и устойчивым.
Выяснить больше – нарколог на дом клиника в краснодаре
В данной статье мы акцентируем внимание на важности поддержки в процессе выздоровления. Мы обсудим, как друзья, семья и профессионалы могут помочь тем, кто сталкивается с зависимостями. Читатели получат практические советы, как поддерживать близких на пути к новой жизни.
Исследовать вопрос подробнее – нарколог на дом вывод из запоя в москве
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Разобраться лучше – нарколог на дом цены краснодар
В этой статье обсуждаются актуальные медицинские вопросы, которые волнуют общество. Мы обращаем внимание на проблемы, касающиеся здравоохранения и лечения, а также на новшества в области медицины. Читатели будут осведомлены о последних событиях и смогут следить за тенденциями в медицине.
Подробнее – вывод из запоя в стационаре
bs2best at не работает
Прежде чем перейти к таблице, отметим смысл. Это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые диагнозы и динамику симптомов, но логика процесса остаётся неизменной: от безопасности к устойчивости.
Ознакомиться с деталями – vyvod-iz-zapoya-na-domu-oblast
В этой публикации мы обсуждаем современные методы лечения различных заболеваний. Читатели узнают о новых медикаментах, терапиях и исследованиях, которые активно применяются для лечения. Мы нацелены на то, чтобы предоставить практические знания, которые могут помочь в борьбе с недугами.
Получить дополнительные сведения – срочный вывод из запоя в Симферополе
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Подробнее можно узнать тут – http://vivod-iz-zapoya-rostov14.ru/rostov-vyvod-iz-zapoya/
написать курсовую работу на заказ в москве https://kupit-kursovuyu-8.ru/ .
Современная наркология — это не набор «сильных капельниц», а точные инструменты, управляющие скоростью и направлением изменений. В «НеваМеде» технологический контур работает тихо и незаметно для пациента, но даёт врачу контроль над деталями, от которых зависит безопасность.
Разобраться лучше – http://narkologicheskaya-klinika-v-spb14.ru
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Изучить вопрос глубже – https://vivod-iz-zapoya-rostov14.ru/rostov-vyvod-iz-zapoya/
заказать курсовую работу спб http://kupit-kursovuyu-5.ru .
Этап
Выяснить больше – https://vyvod-iz-zapoya-v-stacionare-chekhov8.ru/
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Ознакомиться с деталями – наркологическая клиника вывод из запоя санкт-петербург
Важная деталь — отсутствие полипрагмазии. Мы используем «минимально достаточную фармакотерапию»: каждый препарат имеет цель, окно эффективности и критерии отмены. Это снижает побочные эффекты, убирает «тяжесть» днём и делает восстановление более естественным.
Углубиться в тему – https://narkologicheskaya-klinika-v-spb14.ru/
Эти шаги помогают системно подойти к проблеме и обеспечить максимальную эффективность лечения.
Получить дополнительную информацию – vyvod-iz-zapoya-ryazan14.ru/
Для купирования абстинентного синдрома и снятия интоксикации используются различные подходы. Врачи подбирают их индивидуально, исходя из состояния пациента.
Разобраться лучше – наркологический вывод из запоя рязань
Вызов нарколога на дом сочетает медицинскую эффективность с удобством. Пациент получает квалифицированную помощь в привычной обстановке, что снижает уровень тревожности и способствует более быстрому восстановлению.
Подробнее можно узнать тут – запой нарколог на дом
Этот документ охватывает важные аспекты медицинской науки, сосредотачиваясь на ключевых вопросах, касающихся здоровья населения. Мы рассматриваем свежие исследования, клинические рекомендации и лучшие практики, которые помогут улучшить качество лечения и профилактики заболеваний. Читатели получат возможность углубиться в различные медицинские дисциплины.
Получить дополнительную информацию – вывод из запоя недорого Симферополь
Для купирования абстинентного синдрома и снятия интоксикации используются различные подходы. Врачи подбирают их индивидуально, исходя из состояния пациента.
Узнать больше – вывод из запоя в стационаре в рязани
Этап
Углубиться в тему – vyvod-iz-zapoya-na-domu-oblast
сколько стоит натяжной потолок Натяжные потолки: Идеальное решение для вашего дома
Состав капельницы никогда не «копируется»; он выбирается по доминирующему симптому и соматическому фону. Ниже — клинические профили, которые помогают понять нашу логику. Итоговая схема формируется на месте, а скорость и объём зависят от текущих показателей.
Изучить вопрос глубже – http://narcolog-na-dom-krasnodar14.ru
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Подробнее тут – https://vivod-iz-zapoya-rostov14.ru/rostov-vyvod-iz-zapoya
Прежде чем перейти к таблице, отметим смысл. Это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые диагнозы и динамику симптомов, но логика процесса остаётся неизменной: от безопасности к устойчивости.
Подробнее тут – vyvod-iz-zapoya-v-stacionare-chekhov8.ru/
Ключевая идея «ДонЗдрава» — соединить доказательную медицину и понятную пациенту логистику. Инфузии рассчитываются через инфузомат, жизненные показатели контролируются портативным кардиомонитором и пульсоксиметром, а лекарственные взаимодействия проверяются по протоколу перед началом терапии. При этом каждый шаг объясняется простым языком: что делаем, зачем это нужно и как будем оценивать результат через 30, 60 и 120 минут. После визита пациент не остаётся один — доступна «горячая линия» и короткие онлайн-сессии с врачом либо психологом, если тревога или бессонница возвращаются в ночные часы.
Получить дополнительные сведения – http://www.domen.ru
Этап
Разобраться лучше – http://vyvod-iz-zapoya-v-stacionare-chekhov8.ru/vyvod-iz-zapoya-kapelnica-v-chekhove/
написать курсовую работу на заказ в москве https://kupit-kursovuyu-8.ru/ .
Этот информационный материал подробно освещает проблему наркозависимости, ее причины и последствия. Мы предлагаем информацию о методах лечения, профилактики и поддерживающих программах. Цель статьи — повысить осведомленность и продвигать идеи о необходимости борьбы с зависимостями.
Исследовать вопрос подробнее – вывод из запоя недорого
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Подробнее – вывод из запоя на дому цена
Домашний визит особенно уместен при затянувшемся употреблении, когда нарастают тревожные вегетативные симптомы (тремор, потливость, сердцебиение), появляются проблемы со сном и «качели» давления, но при этом сохранён контакт, нет выраженной дыхательной недостаточности и глубокой дезориентации. Преимущества очевидны: экономия времени (нет дороги и ожидания), психологический комфорт, меньше сенсорных триггеров (яркий свет, шум), возможность сразу настроить режим первой «тихой ночи». Технологически выездная бригада оснащена как приёмный кабинет: инфузомат для точной скорости капания, пульсоксиметр, глюкометр, кассеты Na?/K?, портативный кардиомонитор с возможностью регистрации ЭКГ, набор проверенных средств для коррекции тошноты и защиты слизистой. Если во время триажа выявляются «красные флаги» — риск судорог, падение сатурации, признаки делирия, нестабильная гемодинамика, — мы организуем перевод в стационар «КубаньМедЦентра» без задержек и с непрерывностью терапии.
Получить больше информации – запой нарколог на дом в краснодаре
«ВитаСана» — это организованный маршрут наркологической помощи в Чехове: быстрый анонимный звонок, выезд врача на дом без опознавательных знаков, аккуратный детокс с капельницами, стационар с круглосуточным наблюдением и подготовка к кодированию по показаниям. Мы действуем спокойно и последовательно: сначала очная оценка и допуск к терапии, затем индивидуальная инфузионная поддержка, далее — понятный план «тихих» дней и контрольный контакт. Каждое назначение объясняем простыми словами, смету согласуем до начала процедур, конфиденциальность соблюдаем на каждом шаге.
Детальнее – наркологическая клиника цены адреса
?????????
Что делает врач
Изучить вопрос глубже – vyvod-iz-zapoya-kruglosutochno
Эта доказательная статья представляет собой глубокое погружение в успехи и вызовы лечения зависимостей. Мы обращаемся к научным исследованиям и опыте специалистов, чтобы предоставить читателям надежные данные об эффективности различных методик. Изучите, что работает лучше всего, и получите информацию от экспертов.
Подробнее можно узнать тут – вывод из запоя капельница
В этом обзоре мы обсудим современные методы борьбы с зависимостями, включая медикаментозную терапию и психотерапию. Мы представим последние исследования и их результаты, чтобы читатели могли быть в курсе наиболее эффективных подходов к лечению и поддержке.
Подробнее – http://dafna-clinic.ru
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Изучить вопрос глубже – вывод из запоя на дому круглосуточно
Этот медицинский обзор сосредоточен на последних достижениях, которые оказывают влияние на пациентов и медицинскую практику. Мы разбираем инновационные методы лечения и исследований, акцентируя внимание на их значимости для общественного здоровья. Читатели узнают о свежих данных и их возможном применении.
Выяснить больше – наркологический вывод из запоя в Симферополе
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Получить дополнительные сведения – вывод из запоя вызов город
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Исследовать вопрос подробнее – вывод из запоя капельница ростов-на-дону
Такой подход позволяет устранить физические последствия запоя и снизить психологическую зависимость. Уже после первой процедуры пациенты отмечают улучшение самочувствия, появление аппетита и нормализацию сна. Важно не ограничиваться только экстренной помощью — специалисты рекомендуют пройти курс восстановления, чтобы предотвратить рецидивы.
Получить дополнительные сведения – https://vyvodiz-zapoya-vladivostok18.ru/
Ключевая идея «ДонЗдрава» — соединить доказательную медицину и понятную пациенту логистику. Инфузии рассчитываются через инфузомат, жизненные показатели контролируются портативным кардиомонитором и пульсоксиметром, а лекарственные взаимодействия проверяются по протоколу перед началом терапии. При этом каждый шаг объясняется простым языком: что делаем, зачем это нужно и как будем оценивать результат через 30, 60 и 120 минут. После визита пациент не остаётся один — доступна «горячая линия» и короткие онлайн-сессии с врачом либо психологом, если тревога или бессонница возвращаются в ночные часы.
Изучить вопрос глубже – вывод из запоя на дому недорого в ростове-на-дону
Особое внимание уделяется безопасности. Используются препараты нового поколения, снижающие нагрузку на печень, почки и сердечно-сосудистую систему. Процесс лечения проходит под постоянным наблюдением медперсонала, что позволяет быстро реагировать на любые изменения состояния пациента. Все данные о лечении строго конфиденциальны — информация не передаётся третьим лицам и не фиксируется в общедоступных базах.
Детальнее – наркологическая клиника лечение алкоголизма томск
Детоксикация является важнейшим этапом лечения. В «Ижевском Центре Трезвых Решений» применяются проверенные схемы инфузионной терапии, помогающие восстановить функции организма после интоксикации. Капельницы подбираются индивидуально в зависимости от состояния пациента и выраженности симптомов. Ниже приведена таблица с типами капельниц, применяемых в клинике.
Углубиться в тему – http://narkologicheskaya-klinika-v-izhevsk18.ru/narkologicheskaya-klinika-izhevsk-otzyvy/
Чтобы снизить тревогу и обеспечить предсказуемость, «ДонЗдрав» придерживается пошагового протокола. Он гибкий, но обязательно включает триаж, диагностику, старт инфузии и выдачу письменного плана. Переход между этапами происходит только при достижении понятных критериев безопасности — мы фиксируем их вместе с пациентом и родственниками.
Детальнее – http://www.domen.ru
Услуги эвакуатора Эвакуатор Таганрог – это не просто географическое указание, это обещание оперативной и профессиональной помощи водителям, оказавшимся в беде на дорогах этого прекрасного города.
бонусы в казино за регистрацию с выводом без пополнения
Наркологическая клиника — это место, где человек получает не просто медицинскую помощь, а возможность начать жизнь заново. В клинике «АстраМед Трезвость» в Астрахани создана система комплексного лечения алкогольной и наркотической зависимости, включающая диагностику, детоксикацию, медикаментозную терапию и психотерапию. Пациент получает поддержку на каждом этапе: от вывода из запоя до социальной адаптации после реабилитации. Лечение проводится круглосуточно, в комфортных условиях и с соблюдением полной конфиденциальности.
Изучить вопрос глубже – наркологическая клиника нарколог астрахань
Наркологическая клиника применяет структурированные методы, включающие изучение анамнеза, оценку текущего состояния и определение возможных рисков. На основе полученной информации формируются индивидуальные схемы лечения, направленные на нормализацию внутренних процессов. Работа строится на многоуровневом наблюдении, включающем анализ лабораторных показателей и оценку функциональных систем организма. Такой формат позволяет поддерживать стабильную динамику изменений и избегать осложнений. В клинике создается согласованная модель вмешательств, позволяющая получать устойчивые результаты.
Детальнее – https://narkologicheskaya-klinika-tomsk18.ru/chastnaya-narkologicheskaya-klinika-tomsk
где можно купить курсовую работу http://www.kupit-kursovuyu-9.ru .
Комплекс перечисленных направлений формирует базу для выстраивания терапевтического процесса. При необходимости программа корректируется, что обеспечивает адаптацию к меняющимся условиям. Для удобства наблюдения используется таблица, отражающая основные параметры контроля.
Ознакомиться с деталями – наркологическая клиника цены владивосток
Эта доказательная статья представляет собой глубокое погружение в успехи и вызовы лечения зависимостей. Мы обращаемся к научным исследованиям и опыте специалистов, чтобы предоставить читателям надежные данные об эффективности различных методик. Изучите, что работает лучше всего, и получите информацию от экспертов.
Подробнее – вывод из запоя на дому Москва
В этой медицинской статье мы погрузимся в актуальные вопросы здравоохранения и лечения заболеваний. Читатели узнают о современных подходах, методах диагностики и новых открытий в научных исследованиях. Наша цель — донести важную информацию и повысить уровень осведомленности о здоровье.
Получить больше информации – вывод из запоя с выездом Москва
В рамках последовательного анализа состояния применяется также оценочная шкала, позволяющая фиксировать изменения и уточнять степень выраженности симптомов. Далее представлена таблица, демонстрирующая основные критерии наблюдения и их функциональное значение в клиническом процессе.
Ознакомиться с деталями – http://narkologicheskaya-klinika-penza18.ru/chastnaya-narkologicheskaya-klinika-penza/
«МедСфера» — это управляемый маршрут наркологической помощи в Ивантеевке: круглосуточный выезд врача без опознавательных знаков, аккуратный домашний детокс, стационар с наблюдением 24 часа в сутки и профессиональная подготовка к кодированию по показаниям. Мы работаем по принципу клинической достаточности: никакой «универсальной капельницы», никаких решений «наугад», только последовательные шаги, которые действительно влияют на исход. Каждое назначение объясняем простым языком, заранее согласуем смету, фиксируем правила на первые 24–48 часов и первую «тихую» неделю. Конфиденциальность встроена в процесс: нейтральная связь, выезд без эмблем, документы в сдержанной формулировке по запросу.
Выяснить больше – наркологическая клиника на дом
Перед началом терапии проводится полная диагностика организма, включая лабораторные исследования и ЭКГ. Это позволяет оценить состояние пациента и подобрать оптимальный курс лечения. После стабилизации физического состояния начинается психотерапевтическая и реабилитационная работа. Такой подход помогает не только снять симптомы, но и устранить первопричины зависимости.
Исследовать вопрос подробнее – наркологическая клиника нарколог в кемерове
Детоксикация — ключевой этап лечения в клинике. Она направлена на очищение организма от продуктов распада алкоголя и наркотиков, нормализацию обмена веществ и работы печени. В «КемероваМед Трезвость» применяются капельницы разных типов, каждая из которых имеет определённую цель. Состав подбирается индивидуально, исходя из состояния пациента. Примерные виды капельниц приведены в таблице ниже.
Получить дополнительные сведения – наркологическая клиника наркологический центр
Первый контакт — это половина успеха. Дежурный специалист уточняет длительность запоя, объёмы и тип алкоголя, возраст, хронические болезни, что давали из лекарств, были ли судороги/галлюцинации/боли в груди. По этим данным врач предлагает формат: выезд на дом в Люберцах или немедленная госпитализация. На месте — осмотр, инфузии, наблюдение, обсуждение ближайших шагов. После снятия острой фазы начинается стабилизация: сон, тревога, давление, питание, питьевой режим. Далее — работа с зависимостью: фармакоподдержка для снижения тяги, психотерапевтические встречи, план профилактики срывов. Важный элемент — контрольные визиты и возможность быстро связаться с клиникой при первых «звоночках». Так кризис превращается в управляемый процесс, где каждый следующий шаг понятен и заранее согласован.
Выяснить больше – http://narkologicheskaya-pomoshch-lyubercy5.ru
Честная наркология — это не «универсальная капельница», а система шагов, привязанная к параметрам конкретного человека. В Чехове мы выезжаем круглосуточно, на месте проводим допуск к терапии, сверяем совместимости с уже принятыми препаратами, подбираем состав инфузий без лишних компонентов и избыточной седативной нагрузки. Если дома нет условий для безопасной ночи, предложим стационар — это не усложнение, а короткий путь к безопасности. Анонимность — стандарт: нейтральные формулировки в документах по запросу, ограниченный доступ к данным, деликатная связь.
Получить дополнительные сведения – http://narkologicheskaya-klinika-chekhov8.ru
Когда состояние нестабильно, важно не «угадать», а выбрать безопасный формат. Преимущество клиники в Балашихе — гибкость: есть круглосуточный стационар, выездная служба и амбулаторный приём. Команда не навязывает удобный для рекламы вариант: если дому не хватает ресурсов безопасности, врач честно рекомендует стационар. Если же состояние контролируемо, инфузионная терапия возможна на дому с последующим амбулаторным сопровождением. Такая логика экономит не только время и деньги — она снижает риск повторных срывов: пациент не выпадает из наблюдения и получает поддержку на том уровне, который действительно подходит его состоянию прямо сейчас.
Детальнее – http://narkologicheskaya-klinika-balashiha5.ru/narkologicheskaya-klinika-na-dom-v-balashihe/
Сначала — очная оценка, проверка противопоказаний и совместимости с текущими лекарствами. Далее — инфузионная терапия для коррекции водно-электролитного баланса, поддержка печени и сердечно-сосудистой системы, мягкая анксиолитическая и снотворная поддержка по показаниям. Визит обычно занимает от 60 до 120 минут; при необходимости капельницы проводятся медленно, с наблюдением. После процедуры пациент получает понятные памятки: что и когда пить, когда спать, какие признаки считаются тревожными и требуют повторного осмотра или перевода в стационар.
Детальнее – besplatnaya-narkologicheskaya-klinika-moskva
Процесс лечения проходит поэтапно. Каждый шаг направлен на снятие интоксикации, стабилизацию состояния и нормализацию обменных процессов. В таблице приведены основные этапы и процедуры, применяемые в клинике «ПензаМед Трезвость».
Получить дополнительные сведения – наркологический вывод из запоя в пензе
В этой статье обсуждаются актуальные медицинские вопросы, которые волнуют общество. Мы обращаем внимание на проблемы, касающиеся здравоохранения и лечения, а также на новшества в области медицины. Читатели будут осведомлены о последних событиях и смогут следить за тенденциями в медицине.
Углубиться в тему – вывод из запоя
Стационар рационален при нестабильном состоянии, риске делирия, судорогах в анамнезе, скачках давления, выраженной одышке, неукротимой рвоте, одиночестве ночью или невозможности обеспечить «тихий режим». В палате — контролируемая среда, доступ к ЭКГ и базовой лаборатории по показаниям, круглосуточный пост медсестёр и возможность быстро менять тактику, если параметры «плывут». Такой маршрут предсказуемее по безопасности и зачастую короче по времени до стабильного самочувствия.
Подробнее тут – капельница от запоя состав
Лечение проходит поэтапно, чтобы пациент не испытывал стресса и перегрузок. Каждый шаг контролируется врачами, а терапия корректируется в зависимости от состояния. В таблице ниже представлена структура программы лечения в клинике «АстраМед Трезвость».
Узнать больше – narkologicheskaya-klinika-v-astrakhani18.ru/
Затянувшийся запой — это не просто «перебор накануне», а состояние, при котором страдают сердечно-сосудистая система, печень, нервная регуляция и обмен электролитов. В наркологической клинике «ДонЗдрав» (Ростов-на-Дону) экстренный вывод из запоя организован как непрерывная цепочка помощи: диспетчер 24/7 — дежурный врач — мобильная бригада — последующее наблюдение и психотерапевтическая поддержка. Мы приезжаем на дом в гражданской одежде, без опознавательных знаков, проводим экспресс-диагностику, запускаем индивидуально подобранные капельницы и даём чёткий план на ближайшие 72 часа. Такой формат позволяет безопасно стабилизировать состояние, не нарушая приватность и привычный уклад семьи.
Подробнее тут – вывод из запоя в ростове-на-дону
женские ботинки турция натуральная кожа Женская обувь современный стиль – отражение актуальных тенденций и инновационных решений в дизайне.
В рамках последовательного анализа состояния применяется также оценочная шкала, позволяющая фиксировать изменения и уточнять степень выраженности симптомов. Далее представлена таблица, демонстрирующая основные критерии наблюдения и их функциональное значение в клиническом процессе.
Получить дополнительную информацию – http://narkologicheskaya-klinika-penza18.ru
Современная наркологическая клиника — это не просто медицинское учреждение, где проводят лечение зависимостей. Это система комплексной поддержки, объединяющая врачей, психологов, терапевтов и специалистов по реабилитации. В клинике «ТомскМед Трезвость» созданы комфортные условия, где лечение проходит анонимно, бережно и с опорой на доказательную медицину. Каждое вмешательство назначается строго по показаниям, а терапия направлена не только на физическое очищение организма, но и на восстановление психоэмоционального баланса пациента.
Получить больше информации – наркологическая клиника стационар в томске
купить курсовую сайт купить курсовую сайт .
Процедура вывода из запоя проводится строго по медицинским стандартам. Применяются современные капельницы, витамины и препараты для нормализации функций сердца, печени, почек и нервной системы. После снятия интоксикации врачи назначают поддерживающее лечение, направленное на стабилизацию эмоционального состояния и снижение тяги к алкоголю.
Получить дополнительную информацию – http://vyvodiz-zapoya-vladivostok18.ru/czentr-kodirovaniya-alkogolizma-vyvod-iz-zapoya-vladivostok/
Одна и та же «капельница на всех» не работает: у одних доминирует обезвоживание, у других — тахикардия и тревога, у третьих — желудочные симптомы и нагрузка на печень. Ниже — ориентиры по выбору инфузионных схем и целей вмешательства; окончательный состав подбирается врачом исходя из клинической картины и сопутствующих заболеваний.
Получить больше информации – вывод из запоя капельница в ростове-на-дону
*Седативные препараты применяются строго по показаниям и под мониторингом дыхания.
Подробнее тут – http://vivod-iz-zapoya-rostov14.ru
В рамках последовательного анализа состояния применяется также оценочная шкала, позволяющая фиксировать изменения и уточнять степень выраженности симптомов. Далее представлена таблица, демонстрирующая основные критерии наблюдения и их функциональное значение в клиническом процессе.
Выяснить больше – наркологическая клиника
Для повышения эффективности лечения наркологическая клиника применяет стандартизированные методы, включающие мониторинг жизненно важных параметров, корректировку фармакотерапии и оценку неврологических показателей. Совокупность таких мер делает процесс более предсказуемым и снижает вероятность осложнений. Кроме того, практическая часть работы включает регулярную проверку метаболических функций, что способствует точному дозированию препаратов и своевременному изменению схем. Это позволяет поддерживать физиологическую устойчивость организма даже при интенсивной нагрузке и сохранять стабильность состояния на протяжении всего периода терапии.
Детальнее – http://narkologicheskaya-klinika-penza18.ru
Такая структура терапии обеспечивает контроль на всех стадиях и помогает добиться устойчивого результата без вреда для здоровья. Пациент получает не просто временное облегчение, а полное восстановление физического и эмоционального состояния.
Подробнее тут – наркологическая клиника стационар в астрахани
Наркологическая клиника применяет структурированные методы, включающие изучение анамнеза, оценку текущего состояния и определение возможных рисков. На основе полученной информации формируются индивидуальные схемы лечения, направленные на нормализацию внутренних процессов. Работа строится на многоуровневом наблюдении, включающем анализ лабораторных показателей и оценку функциональных систем организма. Такой формат позволяет поддерживать стабильную динамику изменений и избегать осложнений. В клинике создается согласованная модель вмешательств, позволяющая получать устойчивые результаты.
Подробнее – платная наркологическая клиника в томске
Цель
Подробнее тут – ближайший наркологическая клиника
Для получения устойчивого результата наркологическая клиника использует методы, основанные на индивидуальной оценке. В работе учитываются соматические показатели, реакции нервной системы и данные лабораторных исследований. Такой формат лечения обеспечивает предсказуемое влияние на физиологические процессы и снижает вероятность осложнений. В клинике применяется непрерывный мониторинг, позволяющий своевременно корректировать лечебные меры. Работа направлена на нормализацию метаболизма, восстановление баланса внутренних систем и плавное уменьшение симптоматики.
Подробнее тут – частная наркологическая клиника
Анонимная наркологическая помощь — это не просто обещание «никто не узнает». Для семьи, которая переживает затяжные запои, повторяющиеся срывы или смешение алкоголя с лекарствами, конфиденциальность становится условием, без которого человек вообще не соглашается на лечение. В «ЛюберцыМед Трезвость» в Люберцах анонимность встроена в каждый шаг: от первого звонка до выписки и сопровождения. Это позволяет сосредоточиться на главном — безопасной детоксикации, стабилизации состояния и выстраивании маршрута к устойчивой ремиссии, — не опасаясь утечки данных, «учёта» или посторонних разговоров. Здесь не используют стыд и давление: с пациентом и семьёй говорят спокойно и по делу, объясняют риски, границы домашнего формата и преимущества стационара, предлагают гибкие программы (выезд на дом, круглосуточное отделение, амбулаторная поддержка). Такой подход снижает сопротивление и даёт возможность начать лечение вовремя, пока ситуация не переросла в экстренную.
Выяснить больше – http://narkologicheskaya-pomoshch-lyubercy5.ru
Для повышения эффективности лечения наркологическая клиника применяет стандартизированные методы, включающие мониторинг жизненно важных параметров, корректировку фармакотерапии и оценку неврологических показателей. Совокупность таких мер делает процесс более предсказуемым и снижает вероятность осложнений. Кроме того, практическая часть работы включает регулярную проверку метаболических функций, что способствует точному дозированию препаратов и своевременному изменению схем. Это позволяет поддерживать физиологическую устойчивость организма даже при интенсивной нагрузке и сохранять стабильность состояния на протяжении всего периода терапии.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-penza18.ru/
Каждый из перечисленных элементов способствует формированию полной картины состояния пациента и позволяет корректно выстраивать терапевтические мероприятия. Такая структура создаёт основу для достижения устойчивых результатов и минимизации возможных осложнений. Использование таблиц наблюдения делает клинические процессы структурированными и понятными.
Детальнее – http://narkologicheskaya-klinika-tomsk18.ru/tomsk-narkologicheskij-dispanser/https://narkologicheskaya-klinika-tomsk18.ru
Наркологическая клиника использует комплексный подход к оценке состояния пациента, что обеспечивает высокий уровень контроля на всех этапах лечения. Такой формат работы позволяет детально изучать динамику процессов и своевременно корректировать вмешательства. В клинике применяется принцип последовательного наблюдения, при котором особое внимание уделяется соматическим и неврологическим проявлениям. Выбор терапевтических мер основывается на анализе объективных данных, что повышает предсказуемость результата. Подход ориентирован на постепенное восстановление функций организма с учетом индивидуальных особенностей.
Подробнее можно узнать тут – анонимная наркологическая клиника томск
Для повышения эффективности лечения наркологическая клиника применяет стандартизированные методы, включающие мониторинг жизненно важных параметров, корректировку фармакотерапии и оценку неврологических показателей. Совокупность таких мер делает процесс более предсказуемым и снижает вероятность осложнений. Кроме того, практическая часть работы включает регулярную проверку метаболических функций, что способствует точному дозированию препаратов и своевременному изменению схем. Это позволяет поддерживать физиологическую устойчивость организма даже при интенсивной нагрузке и сохранять стабильность состояния на протяжении всего периода терапии.
Изучить вопрос глубже – наркологическая клиника лечение алкоголизма пенза
женская обувь 39 размер Турецкая кожаная обувь для женщин – это символ качества и долговечности, созданный с учетом последних модных тенденций.
Детокс — важный этап лечения, который помогает очистить организм от токсинов и продуктов распада алкоголя или наркотиков. В клинике «ТомскМед Трезвость» используются современные капельницы и лекарственные комбинации, направленные на восстановление биохимических процессов в организме. Ниже представлена таблица с примерами капельниц, применяемых в детоксикационных программах.
Разобраться лучше – наркологическая клиника нарколог в томске
Что включает
Разобраться лучше – http://narkologicheskaya-klinika-balashiha5.ru/chastnaya-narkologicheskaya-klinika-v-balashihe/
Клиника «ВладТрезвие Центр» работает в круглосуточном режиме и готова оказать помощь жителям Владивостока и прилегающих районов в любое время суток. Врачи-наркологи прибывают по вызову в течение часа, имеют при себе все необходимые препараты и оборудование для проведения детоксикации на дому. При необходимости пациента доставляют в стационар, где лечение проходит под постоянным контролем медицинского персонала.
Ознакомиться с деталями – вывод из запоя вызов на дом владивосток
Подобная структура наблюдения облегчает анализ изменений и способствует формированию объективной картины состояния. Наличие унифицированной системы контроля помогает выстраивать терапию последовательно и точно.
Подробнее тут – https://narkologicheskaya-klinika-vo-vladivostoke18.ru/narkolog-vladivostok-na-dom/
Ниже представлена последовательность основных шагов терапевтического процесса.
Детальнее – http://narkologicheskaya-klinika-vo-vladivostoke18.ru
«МедСфера» — это управляемый маршрут наркологической помощи в Ивантеевке: круглосуточный выезд врача без опознавательных знаков, аккуратный домашний детокс, стационар с наблюдением 24 часа в сутки и профессиональная подготовка к кодированию по показаниям. Мы работаем по принципу клинической достаточности: никакой «универсальной капельницы», никаких решений «наугад», только последовательные шаги, которые действительно влияют на исход. Каждое назначение объясняем простым языком, заранее согласуем смету, фиксируем правила на первые 24–48 часов и первую «тихую» неделю. Конфиденциальность встроена в процесс: нейтральная связь, выезд без эмблем, документы в сдержанной формулировке по запросу.
Исследовать вопрос подробнее – narkologicheskaya-klinika-rejting-luchshih
Медицинская публикация представляет собой свод актуальных исследований, экспертных мнений и новейших достижений в сфере здравоохранения. Здесь вы найдете информацию о новых методах лечения, прорывных технологиях и их практическом применении. Мы стремимся сделать актуальные медицинские исследования доступными и понятными для широкой аудитории.
Ознакомиться с деталями – помощь вывод из запоя Симферополь
Когда состояние нестабильно, важно не «угадать», а выбрать безопасный формат. Преимущество клиники в Балашихе — гибкость: есть круглосуточный стационар, выездная служба и амбулаторный приём. Команда не навязывает удобный для рекламы вариант: если дому не хватает ресурсов безопасности, врач честно рекомендует стационар. Если же состояние контролируемо, инфузионная терапия возможна на дому с последующим амбулаторным сопровождением. Такая логика экономит не только время и деньги — она снижает риск повторных срывов: пациент не выпадает из наблюдения и получает поддержку на том уровне, который действительно подходит его состоянию прямо сейчас.
Подробнее тут – анонимная наркологическая клиника
Выбирать клинику только по рекламе опасно — особенно когда речь о длительных запоях, смешении алкоголя с лекарствами и риске психозов. «БалашихаМед Профи» строит помощь на клинических принципах: первичная оценка состояния, выявление факторов риска (давление, пульс, сатурация, сопутствующие болезни), подбор инфузионной терапии без агрессивной седации, непрерывный мониторинг и готовность быстро менять тактику. Этапность — ключ к предсказуемости результатов: сначала снимают интоксикацию и опасные симптомы, затем стабилизируют сон, тревогу, давление, и только после этого — работа с тягой и причинами срывов. Важная часть подхода — открытость: до начала процедур обсуждают формат (дом, стационар, амбулаторно), ориентиры по стоимости, длительность и ожидаемые эффекты. Пациента и семью не запугивают, не стыдят и не манипулируют «секретными методиками»; вместо этого дают прозрачные шаги и объясняют, как совместными усилиями удержать результат после острой фазы. Такой стиль общения снижает сопротивление лечению и помогает сохранить контакт даже у «тяжёлых» пациентов.
Изучить вопрос глубже – наркологическая клиника в балашихе
Не каждый запрос «анонимно и дома» безопасен. Есть состояния, при которых отсутствие круглосуточного контроля опасно, а попытка «усыпить» дома увеличивает риск осложнений. Ниже — признаки, при которых врачи рекомендуют стационар без промедления:
Выяснить больше – vyzvat-narkologicheskuyu-pomoshch
Такая структура терапии обеспечивает контроль на всех стадиях и помогает добиться устойчивого результата без вреда для здоровья. Пациент получает не просто временное облегчение, а полное восстановление физического и эмоционального состояния.
Подробнее можно узнать тут – анонимная наркологическая клиника астрахань
курсовая заказать курсовая заказать .
Для формирования структурированной модели используются стандартизированные алгоритмы. Ниже представлена последовательность действий, определяющих ход терапевтических мероприятий.
Подробнее тут – https://narkologicheskaya-klinika-tomsk18.ru/tomsk-narkologicheskij-dispanser/
Каждая процедура проводится под контролем врача и сопровождается мониторингом давления, пульса и температуры. После курса капельниц пациент чувствует улучшение самочувствия, нормализуется сон, снижается раздражительность, появляется энергия и ясность сознания.
Выяснить больше – https://narkologicheskaya-klinika-v-astrakhani18.ru/
как использовать бонус казино в 1winкак играть на бонус казино в 1win
женская обувь актуальная коллекция турция Женская обувь омск – широкий ассортимент моделей для каждого случая, от классики до авангарда. Обувь турция москва – возможность приобрести качественную турецкую обувь, не выезжая из столицы.
Сравнение форматов
Получить дополнительные сведения – http://narkologicheskaya-klinika-balashiha5.ru
Наркологическая клиника «БалашихаМед Профи» — это место, где острые кризисы и многолетние срывы перестают управлять жизнью пациента и его семьи. Здесь помощь организована как связный, управляемый процесс: от экстренного купирования запоя и детоксикации до стабилизации, лечения зависимости и сопровождения после выписки. Для жителей Балашихи важны конкретные вещи: безопасность процедур, круглосуточное наблюдение, возможность выезда врача, понятная стоимость и строгая анонимность. Все эти элементы выстроены в единую систему: врач не «ставит капельницу и уезжает», а берёт на себя ответственность за результат на каждом этапе. Пациенту объясняют, что с ним происходит и почему выбирается именно такая схема помощи; родным дают ясный алгоритм действий, снижают тревогу и помогают не делать шагов, которые повышают риски. В «БалашихаМед Профи» не обещают чудес за сутки — предлагают профессиональную работу, которая возвращает контроль над состоянием и создаёт реальный шанс на устойчивые изменения.
Узнать больше – https://narkologicheskaya-klinika-balashiha5.ru/narkologicheskie-kliniki-v-oblasti-v-balashihe/
Домашний формат нужен, когда риски управляемы, а в квартире можно обеспечить «тихий режим». Врач приезжает без эмблем, проводит осмотр, измеряет давление, пульс, сатурацию, сверяет лекарства за последние 48 часов и аллергии. После допуска запускается инфузия с мягкой коррекцией воды и электролитов, поддержкой печени и вегетативной нервной системы; при необходимости аккуратно настраивается сон. По завершении — переоценка, письменная памятка на 24–48 часов, список тревожных признаков и прямой канал связи. Такой визит «гасит» тремор и тошноту, снижает тревогу и делает ночь предсказуемой.
Подробнее – http://narkologicheskaya-klinika-chekhov8.ru
Наркологическая клиника — это место, где человек получает не просто медицинскую помощь, а возможность начать жизнь заново. В клинике «АстраМед Трезвость» в Астрахани создана система комплексного лечения алкогольной и наркотической зависимости, включающая диагностику, детоксикацию, медикаментозную терапию и психотерапию. Пациент получает поддержку на каждом этапе: от вывода из запоя до социальной адаптации после реабилитации. Лечение проводится круглосуточно, в комфортных условиях и с соблюдением полной конфиденциальности.
Детальнее – наркологическая клиника астрахань
Для тех, кто ищет качественное медицинский перевод онлайн, наши услуги станут лучшим выбором.
Перевод медицинских текстов требует высокой точности и качества . Бюро медицинских переводов занимается переводом различных медицинских документов, включая истории болезни, медицинские статьи и инструкции к лекарствам. Бюро медицинских переводов имеет большой опыт работы с медицинскими учреждениями.
Бюро медицинских переводов также занимается локализацией медицинского программного обеспечения и веб-сайтов, что включает в себя адаптацию интерфейса и содержания для разных языков и культур. Локализация медицинских веб-сайтов включает в себя перевод текста и адаптацию графики .
Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод инструкций к лекарствам и медицинскому оборудованию. Перевод медицинских статей и публикаций требует высокого уровня экспертизы в области медицины и знания медицинской терминологии. Перевод медицинских статей включает в себя перевод сложных медицинских концепций .
Бюро медицинских переводов также занимается переводом медицинских документов, таких как истории болезни и медицинские справки. Перевод медицинских справок включает в себя перевод медицинской терминологии .
Бюро медицинских переводов предоставляет многочисленные преимущества для медицинских учреждений и пациентов, включая возможность коммуникации между медицинскими специалистами и пациентами . Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов обеспечивает безопасность медицинских переводов.
Бюро медицинских переводов также может помочь медицинским учреждениям и пациентам сэкономить время и ресурсы, предоставляя быстрые и качественные медицинские переводы. Бюро медицинских переводов имеет большой опыт работы с медицинскими учреждениями и пациентами.
В заключении, бюро медицинских переводов является важным звеном в сфере здравоохранения, где медицинские переводчики предоставляют важную услугу для медицинских учреждений и исследований. Бюро медицинских переводов предлагает различные виды медицинских переводов, включая перевод медицинских статей, историй болезни и инструкций к лекарствам. Бюро медицинских переводов имеет большой опыт работы с медицинскими учреждениями и пациентами.
Бюро медицинских переводов также обеспечивает конфиденциальность и безопасность медицинских документов, что является важным аспектом в сфере здравоохранения. Бюро медицинских переводов имеет большой опыт работы с конфиденциальными медицинскими документами .
Лечение проходит поэтапно, чтобы пациент не испытывал стресса и перегрузок. Каждый шаг контролируется врачами, а терапия корректируется в зависимости от состояния. В таблице ниже представлена структура программы лечения в клинике «АстраМед Трезвость».
Разобраться лучше – http://narkologicheskaya-klinika-v-astrakhani18.ru
Компания предлагает услуги авто с водителем новосибирск для путешественников и местных жителей.
В Новосибирске аренда авто с водителем является одним из наиболее комфортных способов передвижения по городу. Это связано с тем, что в городе есть множество компаний, предлагающих такие услуги. Услуги аренды автомобилей с водителем в Новосибирске включают в себя сопровождение на деловые встречи и экскурсии по городу. Это особенно удобно для иностранных туристов, которые могут не владеть русским языком. Аренда автомобиля с водителем может быть арендована на любой период времени, от нескольких часов до нескольких дней. Для этого необходимо указать дату, время и место подачи автомобиля. После оформления заказа автомобиль с водителем будет подан в указанное место в назначенное время. Это позволяет добраться до места назначения быстро и безопасно.
Аренда авто с водителем в Новосибирске имеет множество преимуществ, таких как экономия времени и средств. Это особенно удобно для деловых путешественников, которые часто имеют плотный график. В Новосибирске можно арендовать автомобиль с водителем для поездки на знаменитые достопримечательности. Это дает возможность оценить красоту города и его окрестностей.
Это особенно удобно для семей с детьми, которые могут не иметь возможности передвигаться на общественном транспорте. Это позволяет добраться до места назначения быстро и комфортно. В Новосибирске можно арендовать автомобиль с водителем для поездки на деловую встречу или на свадьбу. Для этого необходимо указать дату, время и место подачи автомобиля.
Услуги аренды авто с водителем в Новосибирске представлены различными компаниями, которые предлагают широкий выбор автомобилей. Это дает возможность оценить красоту города и его окрестностей. Услуги аренды авто с водителем в Новосибирске становятся все более доступными и популярными среди путешественников.
Аренда авто с водителем может быть оформлена онлайн или по телефону. Для этого необходимо указать дату, время и место подачи автомобиля. Водители, предоставляемые компаниями аренды авто, являются опытными и знающими город. Это позволяет добраться до места назначения быстро и безопасно.
В Новосибирске можно арендовать автомобиль с водителем для поездки на знаменитые достопримечательности. Это дает возможность оценить красоту города и его окрестностей. Услуги аренды авто с водителем в Новосибирске становятся все более доступными и популярными среди путешественников. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Аренда автомобиля с водителем может быть арендована на любой период времени. Для этого необходимо указать дату, время и место подачи автомобиля. После оформления заказа автомобиль с водителем будет подан в указанное место в назначенное время. Это дает возможность оценить красоту города и его окрестностей.
В Новосибирске можно арендовать автомобиль с водителем для поездки на деловую встречу или на свадьбу. Это дает возможность оценить красоту города и его окрестностей. Аренда авто с водителем в Новосибирске предлагает широкий спектр услуг для тех, кто ценит комфорт и удобство. Это позволяет гостям Новосибирска наслаждаться городом без забот о передвижении.
Услуги аренды авто с водителем в Новосибирске доступны для всех категорий граждан. Это дает возможность оценить красоту города и его окрестностей. Услуги аренды авто с водителем в Новосибирске также включают в себя помощь в решении любых вопросов, связанных с пребыванием в городе. Это позволяет добраться до места назначения быстро и безопасно.
Наркологическая клиника — это место, где человек получает не просто медицинскую помощь, а возможность начать жизнь заново. В клинике «АстраМед Трезвость» в Астрахани создана система комплексного лечения алкогольной и наркотической зависимости, включающая диагностику, детоксикацию, медикаментозную терапию и психотерапию. Пациент получает поддержку на каждом этапе: от вывода из запоя до социальной адаптации после реабилитации. Лечение проводится круглосуточно, в комфортных условиях и с соблюдением полной конфиденциальности.
Изучить вопрос глубже – наркологическая клиника лечение алкоголизма в астрахани
Лечение в «ИжТрезвоМед Центр» проходит поэтапно, с акцентом на безопасность и эффективность. Каждый этап направлен на достижение конкретных целей, от детоксикации до психотерапии. В таблице представлена структура лечебного процесса:
Детальнее – https://narkologicheskaya-klinika-v-izhevske18.ru/chastnaya-narkologicheskaya-klinika-izhevsk/
Лечение проводится поэтапно, начиная с оценки состояния и заканчивая восстановлением после интоксикации. Каждый этап направлен на устранение симптомов отравления и стабилизацию работы внутренних органов.
Разобраться лучше – нарколог на дом срочно в челябинске
Процесс терапии включает несколько последовательных шагов:
Узнать больше – http://narcologicheskaya-klinika-v-chelyabinske16.ru
Таблица позволяет поддерживать единую структуру наблюдения и фиксировать изменения состояния. Такая модель обеспечивает прозрачность процессов и повышает точность принимаемых решений.
Узнать больше – http://vyvodiz-zapoya-izhevsk18.ru/vyvod-iz-zapoya-na-domu-izhevsk/
Эти признаки не заменяют очной оценки, но помогают не рисковать временем. Если вы наблюдаете их у близкого или у себя, не откладывайте обращение — чем раньше начнётся управляемое вмешательство, тем меньше вероятность осложнений в первую ночь и на следующие сутки.
Получить дополнительную информацию – vyvod-iz-zapoya-v-chelyabinske16.ru/
Очищение организма — ключевой этап в лечении зависимости. В клинике «ИжТрезвоМед Центр» применяются разные виды капельниц, которые помогают ускорить детоксикацию, восстановить водно-солевой баланс и улучшить работу органов. В таблице приведены основные виды инфузионных программ, применяемых при выезде нарколога на дом и в стационаре:
Узнать больше – http://www.domen.ru
аренда сборных строительных лесов трубчатые леса аренда
Получить апостиль диплома — это важный шаг для подтверждения подлинности вашего образования за границей.
Процедура апостилирования диплома несет в себе множество нюансов.
Лечение зависимости требует системного подхода и чёткой последовательности действий. Каждый этап направлен на устранение интоксикации, восстановление функций организма и закрепление результата. В клинике процедура организована так, чтобы обеспечить комфорт и безопасность пациента.
Узнать больше – https://narcologicheskaya-klinika-v-chelyabinske16.ru/oblastnaya-narkologicheskaya-klinika-chelyabinsk/
Домашний визит — это медицинская логика без лишней логистики. В мегаполисе каждая задержка увеличивает риски: человек устаёт, растёт тревога, обостряются скачки давления и пульса, а бессонные ночи превращают любые «самодельные» схемы в опасный эксперимент. «Трезвый Стандарт» строит помощь как управляемую последовательность: дежурный врач собирает краткий анамнез (длительность употребления, лекарства, сопутствующие заболевания), уточняет текущие показатели и предлагает безопасную точку входа — выезд на дом или стационар на сутки-двое при высоких рисках. Дом даёт приватность и предсказуемость: знакомая среда снижает стресс, а врач привозит всё для мониторинга и инфузий по показаниям. Ключевой результат первых часов — контролируемый сон, понятный режим гидратации и питания «по силам», а также зафиксированные «красные флажки» для связи. Именно последовательность, а не «сильная капельница любой ценой», делает выездной формат эффективным и безопасным в реальном ритме Москвы.
Получить больше информации – нарколог на дом круглосуточно
сгенерировать ИИ презентацию
Лечение в клинике в Челябинске строится на принципах конфиденциальности, добровольности и медицинской этики. Врачи применяют доказательные методы терапии, а программы лечения адаптируются под особенности каждого пациента. Работа ведётся комплексно, включая медикаментозную помощь, психотерапию и социальную реабилитацию. Такой подход позволяет эффективно восстановить здоровье и вернуть пациента к нормальной жизни в обществе.
Подробнее – наркологическая клиника лечение алкоголизма челябинск
Если у человека выраженное обезвоживание, скачки давления и пульса, эпизоды спутанности сознания, упорная рвота, «дергающийся» сон или тяжёлая сопутствующая патология, стационар закрывает главный риск — непредсказуемое течение синдрома отмены. Круглосуточный мониторинг позволяет динамически корректировать схемы, подключать лабораторные и инструментальные исследования по показаниям, своевременно восполнять дефициты и удерживать стабильный сон. На практике «короткое окно» госпитализации (24–48 часов) нередко дешевле на дистанции: оно предотвращает осложнения и повторные вызовы, которые растягивают курс и увеличивают суммарные затраты. Для жителей Москвы мы разносim визиты по времени, используем отдельные входы и «тихие» маршруты, чтобы сохранить приватность. После стабилизации маршрут переводится в амбулаторный или домашний формат: пациент получает план питания и активности, контрольные контакты и правила, при каких признаках связаться немедленно, не дожидаясь «как будет утром».
Получить больше информации – http://vyvod-iz-zapoya-moskva99.ru
Вывод из запоя требует комплексного контроля всех физиологических параметров. Ниже представлены основные направления наблюдения, формирующие структуру оценки состояния.
Ознакомиться с деталями – вывод из запоя круглосуточно в ижевске
удаленная работа Удаленная работа для мам в декрете — часто эти вакансии дают гибкость и возможность совмещать уход за малышами с доходом. Рекомендуется выбирать роли с понятной задачей, сбоев в расписании меньше и явной моделью оплаты. Хорошие варианты: контент-менеджмент, модерация, онлайн-образование, удалённая поддержка клиентов, дизайн и копирайтинг. Планируйте рабочие окна так, чтобы они совпадали с временем сна ребёнка или когда близкие могут помочь. Важна дисциплина, надёжные интернет-соединения и чёткие границы между рабочим и семейным временем.
электрокарнизы для штор купить https://prokarniz36.ru/ .
как провести оценку ущерба после залива ekspertiza-zaliva-kvartiry-5.ru .
Процесс терапии включает несколько последовательных шагов:
Узнать больше – частная наркологическая клиника
Капельница, устанавливаемая наркологом на дому в Челябинске, помогает быстро очистить организм от токсинов и нормализовать водно-солевой баланс. Растворы включают витамины, анальгетики, седативные и гепатопротекторные препараты. Эффект от процедуры ощущается уже через 20–30 минут. Капельница снижает головную боль, устраняет тошноту, восстанавливает работу печени и сердечно-сосудистой системы. Такой метод считается одним из самых эффективных способов вывести пациента из запойного или абстинентного состояния без визита в стационар.
Подробнее можно узнать тут – https://narkolog-na-dom-v-chelyabinske16.ru/
филлеры москва оптом filler-kupit.ru .
Простая подготовка уменьшает стресс, повышает переносимость капельницы и делает оценку состояния более точной. Попросите одного ответственного взрослого быть на связи с врачом — так решения будут приниматься быстрее, а ночной интервал пройдёт спокойнее и предсказуемее.
Подробнее – помощь вывод из запоя челябинск
В основе работы клиники «ИжТрезвоМед Центр» лежит принцип персонализированной медицины. Это означает, что каждый пациент получает не шаблонное лечение, а тщательно подобранный комплекс процедур, учитывающий его состояние, историю заболевания, уровень мотивации и социальную ситуацию. Такой подход позволяет добиться стабильного результата даже в сложных случаях. Лечение проводится анонимно, без постановки на учёт и разглашения данных, что особенно важно для тех, кто ценит конфиденциальность.
Углубиться в тему – наркологическая клиника наркологический центр ижевск
онлайн работа без опыта Удаленная работа для студентов: гибкий график и заработок. Студенты могут найти подработку в интернете с гибким графиком, которая не будет мешать учебе. Это отличный способ получить опыт и заработать деньги.
Домашний визит — это медицинская логика без лишней логистики. В мегаполисе каждая задержка увеличивает риски: человек устаёт, растёт тревога, обостряются скачки давления и пульса, а бессонные ночи превращают любые «самодельные» схемы в опасный эксперимент. «Трезвый Стандарт» строит помощь как управляемую последовательность: дежурный врач собирает краткий анамнез (длительность употребления, лекарства, сопутствующие заболевания), уточняет текущие показатели и предлагает безопасную точку входа — выезд на дом или стационар на сутки-двое при высоких рисках. Дом даёт приватность и предсказуемость: знакомая среда снижает стресс, а врач привозит всё для мониторинга и инфузий по показаниям. Ключевой результат первых часов — контролируемый сон, понятный режим гидратации и питания «по силам», а также зафиксированные «красные флажки» для связи. Именно последовательность, а не «сильная капельница любой ценой», делает выездной формат эффективным и безопасным в реальном ритме Москвы.
Выяснить больше – vrach narkolog na dom moskva
Капельницы в «ЧелМед Детокс» — это модульная конструкция, а не «микс на удачу». База — регидратация и коррекция электролитов. По показаниям добавляются антиэметики, антивегетативные средства, поддержка метаболизма, витамины группы B, магний. Отдельным блоком идёт ночной модуль: задача — собрать восстановительный сон, не «перелечивая» пациента. Каждый модуль имеет свою цель и стоп-критерий. Врач избегает одновременного запуска нескольких новых элементов, чтобы видеть причинно-следственную связь и точно понимать, что именно работает у конкретного человека.
Детальнее – вывод из запоя на дому
Капельницы в «ЧелМед Детокс» — это модульная конструкция, а не «микс на удачу». База — регидратация и коррекция электролитов. По показаниям добавляются антиэметики, антивегетативные средства, поддержка метаболизма, витамины группы B, магний. Отдельным блоком идёт ночной модуль: задача — собрать восстановительный сон, не «перелечивая» пациента. Каждый модуль имеет свою цель и стоп-критерий. Врач избегает одновременного запуска нескольких новых элементов, чтобы видеть причинно-следственную связь и точно понимать, что именно работает у конкретного человека.
Детальнее – вывод из запоя в стационаре челябинск
Капельница, устанавливаемая наркологом на дому в Челябинске, помогает быстро очистить организм от токсинов и нормализовать водно-солевой баланс. Растворы включают витамины, анальгетики, седативные и гепатопротекторные препараты. Эффект от процедуры ощущается уже через 20–30 минут. Капельница снижает головную боль, устраняет тошноту, восстанавливает работу печени и сердечно-сосудистой системы. Такой метод считается одним из самых эффективных способов вывести пациента из запойного или абстинентного состояния без визита в стационар.
Получить дополнительную информацию – http://narkolog-na-dom-v-chelyabinske16.ru
В этой статье рассматриваются способы преодоления зависимости и успешные истории людей, которые справились с этой проблемой. Мы обсудим важность поддержки со стороны близких и профессионалов, а также стратегии, которые могут помочь в процессе выздоровления. Научитесь первоочередным шагам к новой жизни.
Ознакомиться с деталями – вывод из запоя на дому круглосуточно в Симферополе
удаленная работа на дому вакансии Онлайн работа дома для мам: уют и комфорт. Работа из дома позволяет мамам быть рядом со своими детьми и одновременно зарабатывать деньги. Это идеальный вариант для тех, кто хочет совмещать материнство и карьеру.
В основе работы клиники «ИжТрезвоМед Центр» лежит принцип персонализированной медицины. Это означает, что каждый пациент получает не шаблонное лечение, а тщательно подобранный комплекс процедур, учитывающий его состояние, историю заболевания, уровень мотивации и социальную ситуацию. Такой подход позволяет добиться стабильного результата даже в сложных случаях. Лечение проводится анонимно, без постановки на учёт и разглашения данных, что особенно важно для тех, кто ценит конфиденциальность.
Выяснить больше – http://narkologicheskaya-klinika-v-izhevske18.ru/
Алгоритм прозрачен. Сначала — краткое интервью и осмотр, измерение давления, пульса, сатурации, при необходимости — ЭКГ и оценка неврологического статуса. Далее — инфузионная терапия по показаниям: восполнение жидкости, коррекция электролитов, поддержка функций печени, мягкое снижение тремора и тревоги, подготовка к сну без «оглушения». Каждая доза сверяется с реакцией организма, чтобы не получить вечернего отката и побочных эффектов. Врач детально объясняет, какие ощущения нормальны (сонливость, сухость во рту, умеренная слабость), а какие — основание для связи. После процедуры повторно фиксируются показатели и выдаются письменные рекомендации на 48–72 часа: режим воды и лёгкой еды, запрет на «подвиги» и конфликты, время короткого дневного отдыха, интерфейс связи и условия повторного визита. Такой порядок убирает хаос: пациент и семья понимают, что именно делать вечером и ночью, как снизить «дергание» и зачем придерживаться простых правил, пока организм перестраивается после запоя.
Получить больше информации – narkolog na dom kruglosutochno
электрические гардины https://www.prokarniz36.ru .
залили соседи оценка ущерба залили соседи оценка ущерба .
Капельницы в «ЧелМед Детокс» — это модульная конструкция, а не «микс на удачу». База — регидратация и коррекция электролитов. По показаниям добавляются антиэметики, антивегетативные средства, поддержка метаболизма, витамины группы B, магний. Отдельным блоком идёт ночной модуль: задача — собрать восстановительный сон, не «перелечивая» пациента. Каждый модуль имеет свою цель и стоп-критерий. Врач избегает одновременного запуска нескольких новых элементов, чтобы видеть причинно-следственную связь и точно понимать, что именно работает у конкретного человека.
Ознакомиться с деталями – https://vyvod-iz-zapoya-v-chelyabinske16.ru/
удаленная работа на дому Удаленная работа без опыта: старт карьеры. Многие компании предлагают вакансии для удаленной работы без опыта. Это отличный шанс начать карьеру в IT, маркетинге или клиентской поддержке. Главное – желание учиться и развиваться.
Вывод из запоя — это не только про капельницу. Это управляемая цепочка решений, где сначала оцениваются риски (дыхание, сознание, обезвоживание), затем подбирается минимально достаточная инфузионная схема и психосоматическая поддержка, а после — формируется «окно наблюдения» на первую ночь. В наркологической клинике «ЧелМед Детокс» все этапы формализованы: врач фиксирует исходные показатели, назначает узкий модуль вмешательства и выключает его ровно в тот момент, когда цель достигнута. Такой подход избегает полипрагмазии, делает лечение предсказуемым и снимает тревогу у пациента и семьи: каждый понимает, что будет происходить в ближайшие часы, какие критерии успеха и когда наступит пересмотр тактики.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-v-chelyabinske16.ru/vyvod-iz-zapoya-chelyabinsk-na-domu/
филлеры цена филлеры цена .
Осмотр > мониторинг > инфузии по показаниям > план вечера и ночи > письменные рекомендации > окно связи на следующий день. Эта линия делает поведение предсказуемым, а значит — безопасным.
Изучить вопрос глубже – http://vyvod-iz-zapoya-moskva99.ru/vyvod-iz-zapoya-v-moskve-v-stacionare/
Hello colleagues, how is the whole thing, and what you would like to say on the topic of this article, in my view its truly awesome designed for me.
https://yt-balletschool.jp/2025/11/02/melbet-kazino-2025-obzor/
карнизы с электроприводом купить https://www.prokarniz36.ru .
оценка ущерба залив по вине управляющей компании http://www.ekspertiza-zaliva-kvartiry-5.ru/ .
Металлические двери премиум класса обеспечивают надежную защиту и элегантный стиль вашего дома.
Кроме того, такие двери имеют отличные тепло- и звукоизоляционные характеристики.
Чтобы обеспечить легализацию вашего образования за границей, важно знать, где и как поставить поставить апостиль на диплом москва.
Необходимо собрать такие документы, как копия диплома и заявление, чтобы начать процесс.
Для оформления кухни в уникальном стиле можно каменные мойки, что придаст интерьеру неповторимый шарм и практичность.
Правильный выбор раковины для кухни может превратить ее в настоящий шедевр. Кроме того, необходимо учитывать количество пользователей и общий дизайн кухонного пространства При выборе раковины для кухни важно учитывать индивидуальные потребности каждого члена семьи. При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Отзывы других покупателей могут дать ценные советы и рекомендации .
Кроме того, при выборе раковины для кухни необходимо учитывать ее размер и форму Это может включать стандартные размеры, такие как 60 см или 80 см, или более экзотические варианты . Материал, из которого изготовлена раковина, также играет важную роль Нержавеющая сталь известна своей прочностью и легкостью в уходе . Установка раковины может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Для некоторых типов раковин может потребоваться помощь профессионала .
Существует множество типов раковин для кухни, каждый из которых имеет свои собственные характеристики и преимущества Керамические раковины могут добавить кухне больше стиля и изысканности. Нержавеющая сталь является одним из наиболее популярных материалов для раковин Она не только прочная и устойчивая к царапинам, но и легкая в уходе . Гранитовые раковины предлагают высокую устойчивость к нагреву и царапинам Они идеально подходят для кухонь с традиционным или классическим дизайном.
Кроме того, существуют раковины из искусственного камня, которые предлагают высокую прочность и элегантность Они могут быть изготовлены из различных материалов, включая кварц и акрил . Раковина из керамики может добавить кухне больше стиля и изысканности Она известна своей высокой устойчивостью к нагреву и царапинам, а также легкостью в уходе . Выбор правильного типа раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Это может включать рассмотрение размера, формы и материала раковины .
Установка раковины для кухни может быть простой или сложной, в зависимости от типа раковины и вашего уровня опыта Для некоторых типов раковин может потребоваться помощь профессионала . Для начала необходимо измерить пространство, где будет установлена раковина Также стоит учитывать расстояние между раковиной и другими кухонными приборами . После установки раковины необходимо провести Regularный уход, чтобы сохранить ее внешний вид и функциональность Это поможет вам обнаружить и устранить любые проблемы на ранней стадии.
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Это может включать рассмотрение цвета, материала и формы раковины . При установке раковины также необходимо учитывать сантехнику и электрические соединения Также стоит учитывать наличие необходимых инструментов и материалов . Выбор правильной раковины для кухни может сделать ее более функциональной и красивой Правильный выбор раковины может сделать вашу кухню более гармоничной и привлекательной.
При выборе раковины для кухни стоит учитывать множество факторов, включая размер, материал и стиль Раковина для кухни является одним из ключевых элементов кухонного интерьера, требующим тщательного выбора . Также важно учитывать индивидуальные потребности и предпочтения Для большой семьи может потребоваться раковина большего размера, чтобы обеспечить tho?i maiное использование . При покупке раковины также рекомендуется прочитать отзывы и сравнить цены в разных магазинах Отзывы других покупателей могут дать ценные советы и рекомендации .
Кроме того, стоит учитывать стиль и дизайн кухни при выборе раковины Это может включать рассмотрение цвета, материала и формы раковины . Выбор правильной раковины для кухни может быть сложным, но учитывая ваши потребности и предпочтения, вы можете найти идеальный вариант Также стоит учитывать стиль и дизайн кухни . При установке раковины также необходимо учитывать сантехнику и электрические соединения Это может включать подключение раковины к водопроводной и канализационной системе .
заказать филлеры оптом https://www.filler-kupit.ru .
В таблице представлены основные элементы детоксикационной терапии:
Разобраться лучше – вывод наркологическая клиника в волгограде
Основные этапы лечения включают:
Выяснить больше – http://narkologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-czena/
irwin casino казино на деньги рейтинг
Для тех, кто предпочитает лечение в условиях стационара, предусмотрены комфортные палаты, медицинский контроль 24/7 и возможность консультаций с психотерапевтом. Врачи клиники применяют комплексные методы, направленные не только на снятие симптомов, но и на устранение причин зависимости.
Подробнее тут – экстренная наркологическая помощь тольятти
В таблице представлены основные виды терапии, применяемые в клинике:
Получить больше информации – наркологическая клиника новокузнецк
manoir aerospace
References:
http://www.kurapica.net/vb/redirector.php?url=https://www.apu-bookmarks.win/stars-hong-kong-partners-said-to-be-eying-crown-resorts-to-run-casino-at-queens-wharf-brisbane-if-takeover-talks-succeed-iag
«Трезвый Компас» — выездная и стационарная наркологическая служба, которая проводит профессиональный детокс с капельницей от запоя в Клину и районе круглосуточно. Мы приезжаем анонимно, начинаем с очной оценки, согласуем допуск к терапии, подбираем состав инфузии без «универсальных коктейлей» и объясняем простым языком, чего ждать в ближайшие часы. Цель — снять интоксикацию и абстиненцию, поддержать сердце и нервную систему, аккуратно наладить сон по показаниям и дать семье понятный план на 24–48 часов. Если риски высокие или дома невозможно обеспечить безопасную ночь, предложим стационар с круглосуточным наблюдением.
Изучить вопрос глубже – http://
Сначала — очная оценка, проверка противопоказаний и совместимости с текущими лекарствами. Далее — инфузионная терапия для коррекции водно-электролитного баланса, поддержка печени и сердечно-сосудистой системы, мягкая анксиолитическая и снотворная поддержка по показаниям. Визит обычно занимает от 60 до 120 минут; при необходимости капельницы проводятся медленно, с наблюдением. После процедуры пациент получает понятные памятки: что и когда пить, когда спать, какие признаки считаются тревожными и требуют повторного осмотра или перевода в стационар.
Выяснить больше – narkolog-besplatno-moskva
Все процедуры выполняются анонимно и с соблюдением медицинских стандартов. Препараты применяются только сертифицированные, рассчитанные на мягкое восстановление организма без побочных эффектов. При необходимости лечение продолжается в стационаре, где пациент получает круглосуточное наблюдение, питание и психологическую поддержку.
Подробнее – вывод из запоя дешево в новокузнецке
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-staczionar-voronezh/
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Подробнее тут – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Углубиться в тему – вывод из запоя цена волгоград
Эффект ощущается уже через 20–40 минут после начала процедуры. Пациент отмечает снижение головной боли, улучшение сна и общего состояния. Полное восстановление самочувствия наступает в течение суток.
Подробнее – вывод из запоя клиника в тюмени
Мы держим баланс между недостаточным и избыточным лечением. С одной стороны, не пропускаем опасные признаки, с другой — избегаем седативной перегрузки и сомнительных «коктейлей». Состав капельницы и темп введения зависят от давления и пульса, выраженности тревоги и тошноты, сопутствующих диагнозов и лекарств, уже попавших в организм. Каждое назначение объясняется простыми словами, чтобы пациент и семья понимали, как действует схема и зачем нужны ограничения ближайших дней.
Изучить вопрос глубже – https://narkologicheskaya-klinika-voskresensk8.ru/psihiatricheskaya-narkologicheskaya-klinika-v-voskresenske/
Этап
Подробнее тут – narkologicheskaya-klinika
Наркологическая клиника в Новокузнецке предоставляет профессиональную помощь людям, столкнувшимся с зависимостью от алкоголя, наркотиков и психоактивных веществ. Лечение проводится под наблюдением опытных специалистов с применением современных медицинских методик. Основная цель работы клиники — не только устранить физическую зависимость, но и восстановить психологическое равновесие пациента, вернуть мотивацию и способность жить без употребления веществ.
Детальнее – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologiya-gorod-novokuzneczk
Основные признаки, при которых необходим вывод из запоя:
Подробнее можно узнать тут – вывод из запоя на дому цена тольятти
Клиника обеспечивает анонимность и безопасность. Информация о пациентах не передаётся третьим лицам, а процедуры выполняются в комфортных условиях с использованием сертифицированных препаратов и современного оборудования.
Выяснить больше – вывод наркологическая клиника в новокузнецке
рейтинг казино
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Выяснить больше – https://vyvod-iz-zapoya-v-novokuzneczke17.ru/vyvedenie-iz-zapoya-novokuzneczk/
Hi there to all, how is all, I think every one is getting more from this web site, and your views are nice for new viewers.
casino palavas
References:
https://tengsiz.com/user/ortionhhje
Для иллюстрации приведена таблица, отражающая распространённые методы терапии и их воздействие на организм:
Ознакомиться с деталями – анонимная наркологическая клиника воронеж
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Подробнее можно узнать тут – помощь вывод из запоя волгоград
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Изучить вопрос глубже – врач вывод из запоя в волгограде
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Углубиться в тему – наркология вывод из запоя волгоград
Домашний визит — это кратчайший путь к облегчению симптомов, когда нет признаков осложнений. Врач приезжает на неприметном транспорте, проводит очную оценку, измеряет давление, пульс, сатурацию, оценивает неврологический статус и психическое состояние, после чего назначает инфузионную терапию и симптоматические средства по показаниям. Мы заранее даём семье простые инструкции на 24–48 часов, чтобы обеспечить спокойный режим, контроль питья, коррекцию сна и своевременную связь с дежурным врачом.
Получить дополнительные сведения – анонимная наркологическая клиника москва
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Подробнее – наркологическая клиника волгоград
Процесс терапии в наркологической клинике в Воронеже организован поэтапно. Это позволяет обеспечить системность и постепенность восстановления, снизить риски осложнений и повысить устойчивость результата.
Ознакомиться с деталями – частная наркологическая клиника воронеж
Ниже представлена таблица с основными препаратами, используемыми при выводе из запоя в Тюмени:
Подробнее – https://vyvod-iz-zapoya-v-tyumeni17.ru/vyvod-iz-zapoya-tyumen-otzyvy/
В Волгограде медицинская клиника «Трезвая Линия Волгоград» предоставляет круглосуточную помощь людям, столкнувшимся с острым алкогольным отравлением или затяжным запоем. Врачи выезжают на дом, в гостиницу или принимают пациентов в стационаре. Каждое вмешательство начинается с оценки состояния — измерения давления, пульса, насыщения кислородом, уровня интоксикации и дехидратации. Далее подбирается оптимальный состав капельницы, направленный на восстановление водно-солевого баланса, поддержку печени и снижение тревожности.
Углубиться в тему – вывод из запоя вызов на дом волгоград
Одним из самых востребованных направлений работы клиники является проведение детоксикации и вывод из запоя. Эти процедуры направлены на очищение организма от алкоголя и продуктов его распада, нормализацию работы печени и нервной системы. Лечение проводится с использованием сертифицированных препаратов и под контролем врача-нарколога.
Изучить вопрос глубже – http://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologicheskij-czentr-novokuzneczk/
Лечение проходит в несколько этапов: диагностика, детоксикация, медикаментозная поддержка и восстановление. Каждый этап имеет чёткие цели и критерии эффективности, что делает процесс управляемым и безопасным. Применяются препараты, сертифицированные в РФ, и только те, чья эффективность подтверждена клиническими исследованиями.
Исследовать вопрос подробнее – вывод из запоя с выездом в волгограде
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Углубиться в тему – https://kodirovanie-ot-alkogolizma-v-volgograde17.ru/kodirovanie-ot-alkogolya-v-volgograde
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Получить больше информации – врач вывод из запоя в волгограде
Капельница — основной инструмент для очищения организма от продуктов распада этанола. Состав раствора подбирается строго индивидуально. В таблице приведены примеры комплексов, применяемых специалистами клиники «Трезвая Линия Волгоград».
Изучить вопрос глубже – вывод из запоя на дому цена в волгограде
Вывод из запоя — это экстренная медицинская помощь, направленная на очищение организма от алкоголя, снятие симптомов интоксикации и восстановление работы внутренних органов. В клинике «Трезвая Линия Волгоград» используется комплексный подход, включающий капельницы, препараты для детоксикации и постоянный врачебный контроль. Лечение проводится анонимно, с индивидуальным подбором медикаментов и поддержкой пациента на каждом этапе восстановления. Главная цель специалистов — не просто стабилизировать состояние, а обеспечить безопасное возвращение к нормальному самочувствию и предотвратить повторные срывы.
Исследовать вопрос подробнее – вывод из запоя круглосуточно
Вывод из запоя в Тюмени — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормального функционирования организма. Длительное употребление спиртных напитков приводит к нарушению обмена веществ, обезвоживанию, сбоям в работе печени и сердца. В таких случаях требуется профессиональная помощь врача-нарколога, который подберёт оптимальный способ дезинтоксикации и медикаментозной поддержки. Современные методики позволяют провести вывод из запоя безопасно, эффективно и без осложнений.
Детальнее – http://vyvod-iz-zapoya-v-tyumeni17.ru/
Ниже представлена таблица с основными препаратами, используемыми при выводе из запоя в Тюмени:
Углубиться в тему – вывод из запоя дешево в тюмени
Преимущество стационара — предсказуемость и скорость. Рядом врач и медсестра, можно оперативно сдать анализы, сделать ЭКГ или дополнительные обследования, а главное — не «тянуть» с корректировкой схемы. В контролируемой среде быстрее нормализуются сон и аппетит, уходит тремор, снижается тревога. Для пациентов с сопутствующими диагнозами это особенно важно: диабет, гипертония, аритмии, хронические заболевания ЖКТ требуют аккуратной, согласованной тактики.
Получить больше информации – narkologicheskaya-moskva
Процесс лечения проходит поэтапно и под постоянным наблюдением специалистов. Каждый этап направлен на определённый аспект восстановления здоровья и личности пациента.
Подробнее можно узнать тут – наркологическая клиника стационар в новокузнецке
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Узнать больше – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkolog-v-gorode-novokuzneczke/
Продолжительность процедуры — от 40 минут до полутора часов. Уже в первые часы после начала терапии состояние пациента значительно улучшается: проходит тошнота, снижается тревожность, восстанавливается координация движений.
Подробнее тут – https://vyvod-iz-zapoya-v-tolyatti17.ru/vyvedenie-iz-zapoya-tolyatti
«КузбассМед Центр» специализируется на лечении алкогольной и наркотической зависимости, восстановлении организма после интоксикации и профилактике рецидивов. В таблице приведены ключевые направления работы и их особенности.
Ознакомиться с деталями – http://narkologicheskaya-klinika-v-novokuzneczke17.ru
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Получить больше информации – наркологическая клиника стационар
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Ознакомиться с деталями – кодирование от алкоголизма цена адреса в волгограде
Процесс кодирования проходит в комфортной и спокойной обстановке. Врач объясняет каждый этап, чтобы пациент чувствовал себя уверенно и спокойно. После процедуры пациент получает памятку с рекомендациями по уходу за здоровьем и режиму поведения в первые недели после лечения.
Детальнее – кодирование от алкоголизма адрес волгоград
После завершения инфузий врач-нарколог даёт рекомендации по питанию, водному балансу и образу жизни. При необходимости пациенту назначается курс поддерживающей терапии для закрепления эффекта.
Разобраться лучше – срочная наркологическая помощь
лучшие онлайн казино 2025
Работа клиники строится на принципах индивидуального подхода, доказательной медицины и строгого соблюдения конфиденциальности. Каждый пациент проходит обследование, в ходе которого оценивается состояние организма, выявляется стадия зависимости и сопутствующие нарушения. На основе полученных данных разрабатывается персональная программа лечения, включающая медицинские, психологические и социальные методы коррекции поведения.
Подробнее тут – наркологическая клиника клиника помощь в воронеже
Вывод из запоя в Тольятти — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормального состояния здоровья. Длительное употребление спиртных напитков приводит к серьёзной интоксикации, нарушению работы нервной, сердечно-сосудистой и пищеварительной систем. Самостоятельные попытки прекратить запой могут быть опасны, поэтому оптимальным решением является обращение к врачу-наркологу, который проведёт лечение безопасно и эффективно.
Получить дополнительную информацию – наркологический вывод из запоя в тольятти
«КузбассМед Центр» специализируется на лечении алкогольной и наркотической зависимости, восстановлении организма после интоксикации и профилактике рецидивов. В таблице приведены ключевые направления работы и их особенности.
Подробнее – наркологическая клиника клиника помощь
Основные признаки, при которых необходим вывод из запоя:
Подробнее тут – https://vyvod-iz-zapoya-v-tolyatti17.ru/vyvod-iz-zapoya-na-domu-tolyatti-otzyvy
Клиника обеспечивает анонимность и безопасность. Информация о пациентах не передаётся третьим лицам, а процедуры выполняются в комфортных условиях с использованием сертифицированных препаратов и современного оборудования.
Подробнее тут – наркологическая клиника в новокузнецке
Капельница — основной инструмент для очищения организма от продуктов распада этанола. Состав раствора подбирается строго индивидуально. В таблице приведены примеры комплексов, применяемых специалистами клиники «Трезвая Линия Волгоград».
Изучить вопрос глубже – вывод из запоя на дому в волгограде
Для иллюстрации приведена таблица, отражающая распространённые методы терапии и их воздействие на организм:
Углубиться в тему – лечение в наркологической клинике в воронеже
Профессиональный нарколог на дому поможет вам с прокапать от алкоголя быстро и удобно, обеспечив комфорт и безопасность в вашем доме.
Важные признаки, требующие обращения за помощью, включают потерю сознания и сильные галлюцинации.
Looking for a reliable way to travel in comfort? Check out our private jet hire uk cost!
Private jet charter is a popular choice for travelers seeking speed. It allows individuals to avoid long lines. Many people prefer this mode of transportation for its exclusivity.
The process of booking a private jet is quite easy. Customers typically choose their departure point and provide the travel timeline. After that, a professional service will assist in finding the ideal aircraft.
Traveling by private jet has several perks. One significant advantage is the possibility of accessing remote locations. This feature often allows for quicker arrivals.
The privacy afforded by these flights is exceptional. Passengers can hold discussions without worrying about security breaches. This makes private jet charter an excellent option for business travelers.
Для тех, кто ценит безопасность и эксклюзивный дизайн, премиум входные двери в квартиру становятся идеальным выбором, поскольку они сочетают в себе прочность, стиль и надежность.
сочетают в себе повышенную безопасность, эстетическую привлекательность и долговечность. Эти двери отличаются своей универсальностью и могут быть установлены в различных типах зданий, от частных домов до офисных помещений. Металлические двери премиум класса изготавливаются с учетом индивидуальных потребностей каждого клиента .
Металлические двери премиум класса могут быть оборудованы различными системами безопасности, включая электронные замки и системы видеонаблюдения . Эти двери имеют привлекательный внешний вид и могут стать настоящим украшением любого здания. Металлические двери премиум класса представляют собой универсальное решение для различных задач .
Металлические двери премиум класса могут быть оснащены различными системами защиты, включая противовзломные устройства. Эти двери могут быть выполнены в различных цветах и стилях, что позволяет им гармонично вписаться в любой интерьер . Металлические двери премиум класса предназначены для обеспечения максимальной защиты от проникновения и взлома .
Металлические двери премиум класса отличаются высокой долговечностью и прочностью . Эти двери могут быть оснащены дополнительными опциями, такими как звукоизоляция и термоизоляция . Металлические двери премиум класса представляют собой универсальное решение для различных задач .
Процесс установки металлических дверей премиум класса требует специальных навыков и опыта . Эти двери должны быть установлены в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса должны быть эксплуатируемы в соответствии с инструкциями производителя и требованиями безопасности .
Эксплуатация металлических дверей премиум класса требует регулярного обслуживания и проверки . Металлические двери премиум класса должны быть оснащены всеми необходимыми документами и сертификатами . Эти двери могут быть использованы в различных типах зданий, от частных домов до офисных помещений .
Металлические двери премиум класса являются одним из наиболее популярных и востребованных видов дверей на рынке современных строительных материалов . При выборе металлических дверей премиум класса должны быть рассмотрены различные варианты и модели . Металлические двери премиум класса должны быть изготовлены из высококачественных материалов .
Металлические двери премиум класса представляют собой универсальное решение для различных задач . Эти двери должны быть эксплуатируемы в соответствии с инструкциями производителя и требованиями безопасности . Металлические двери премиум класса имеют привлекательный внешний вид и могут стать настоящим украшением любого здания .
Благодаря последовательной работе врачей и постоянному наблюдению лечение проходит безопасно и эффективно, а пациент получает необходимую поддержку на всех этапах терапии.
Изучить вопрос глубже – https://narkologicheskaya-klinika-v-voronezhe17.ru/chastnaya-narkologicheskaya-klinika-voronezh/
карниз электроприводом штор купить provorota.su .
электрокарнизы для штор купить в москве http://elektrokarniz2.ru/ .
электрокарниз двухрядный http://www.elektrokarniz98.ru/ .
авиатор игра 1вин авиатор игра 1вин
Наркологическая клиника «ВолгаМед Центр» — это круглосуточный медицинский комплекс, в котором экстренная помощь, капельницы и детоксикация объединены в единую клинико-поведенческую систему. Мы лечим не «симптом по одному», а управляем весь маршрут: от первичной стабилизации и снижения токсической нагрузки до восстановления сна, аппетита и рабочих ритмов. Каждый шаг имеет цель, измеримый маркер и назначенное «окно» переоценки — это исключает полипрагмазию и делает динамику предсказуемой для пациента и семьи. Конфиденциальность не декларируется, а обеспечивается регламентами: немаркированная логистика, нейтральные формулировки в документах, «тихие» каналы связи и разграничение доступа к медзаписям.
Подробнее – анонимная наркологическая клиника в саратове
Эта карта — рабочий инструмент и для пациента, и для семьи: все видят, какая цель преследуется, какими средствами она достигается, когда проверяется эффект и что будет дальше. Отсюда рождается доверие и строгая приверженность — главный предиктор устойчивого результата.
Получить дополнительную информацию – наркологическая клиника стационар
Вывод из запоя в клинике проводится поэтапно, что позволяет обеспечить прозрачность процесса и полное понимание динамики выздоровления.
Подробнее – вывод из запоя на дому цена
Такая структура лечения помогает пациентам пройти все этапы восстановления под контролем специалистов.
Подробнее – https://narcologicheskaya-klinika-perm0.ru/perm-narkologiya
Каждый из методов подбирается индивидуально, что позволяет учитывать медицинские показания и личные особенности пациента.
Подробнее – https://lechenie-alkogolizma-perm0.ru/perm-lechenie-alkogolizma
Такая структура делает лечение последовательным и предсказуемым, повышая шансы на положительный исход.
Углубиться в тему – http://
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Узнать больше – вывод из запоя цена
В процессе лечения используются проверенные методики, которые в комплексе обеспечивают положительный эффект и снижают риск рецидива.
Получить дополнительную информацию – лечение алкоголизма на дому омск
Город живёт в разных темпах: плотный центр, мостовые переходы, набережная, спальные районы. Мы строим маршрут так, чтобы не привлекать внимания соседей и не терять время на трафик. Если на предзвонке отмечаются «красные флаги» — давящая боль в груди, выраженная одышка, спутанность сознания, судороги, неукротимая рвота или резкое падение насыщения кислородом, — команда instantly переключает маршрут в стационарный «коридор»: палата резервируется заранее, документы оформляются нейтрально, транспорт — немаркированный. Если угроз нет, всё начинается на дому с адресной детокс-схемы и мягкой сенсорной поддержкой.
Выяснить больше – http://narkolog-na-dom-saratov0.ru/narkolog-i-psikhiatr-v-saratove/
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Получить дополнительные сведения – http://narcologicheskaya-klinika-omsk0.ru/narkologi-omska/
бездепозитные бонусы за регистрацию в казино с выводом без пополнения по номеру телефона
гардина с электроприводом http://provorota.su/ .
прокарниз http://www.elektrokarniz2.ru .
карнизы для штор с электроприводом карнизы для штор с электроприводом .
Перед таблицей важный переход: это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые заболевания и входное состояние, но логика последовательности остаётся неизменной — от безопасности к устойчивости.
Ознакомиться с деталями – наркологическая клиника цены
Эта карта — рабочий инструмент и для пациента, и для семьи: все видят, какая цель преследуется, какими средствами она достигается, когда проверяется эффект и что будет дальше. Отсюда рождается доверие и строгая приверженность — главный предиктор устойчивого результата.
Ознакомиться с деталями – https://narkologicheskaya-klinika-saratov0.ru/
Что делаем
Узнать больше – вывод из запоя на дому цена
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Детальнее – вывод из запоя клиника саратов
Наркологическая клиника в Перми обеспечивает пациентам комфортные условия и профессиональное сопровождение. Врачи работают круглосуточно и соблюдают строгую конфиденциальность, что делает лечение доступным и безопасным.
Ознакомиться с деталями – частная наркологическая клиника в перми
Наркологическая клиника «ВолгаМед Центр» — это круглосуточный медицинский комплекс, в котором экстренная помощь, капельницы и детоксикация объединены в единую клинико-поведенческую систему. Мы лечим не «симптом по одному», а управляем весь маршрут: от первичной стабилизации и снижения токсической нагрузки до восстановления сна, аппетита и рабочих ритмов. Каждый шаг имеет цель, измеримый маркер и назначенное «окно» переоценки — это исключает полипрагмазию и делает динамику предсказуемой для пациента и семьи. Конфиденциальность не декларируется, а обеспечивается регламентами: немаркированная логистика, нейтральные формулировки в документах, «тихие» каналы связи и разграничение доступа к медзаписям.
Получить дополнительную информацию – наркологическая клиника вывод из запоя
Город живёт в разных темпах: плотный центр, мостовые переходы, набережная, спальные районы. Мы строим маршрут так, чтобы не привлекать внимания соседей и не терять время на трафик. Если на предзвонке отмечаются «красные флаги» — давящая боль в груди, выраженная одышка, спутанность сознания, судороги, неукротимая рвота или резкое падение насыщения кислородом, — команда instantly переключает маршрут в стационарный «коридор»: палата резервируется заранее, документы оформляются нейтрально, транспорт — немаркированный. Если угроз нет, всё начинается на дому с адресной детокс-схемы и мягкой сенсорной поддержкой.
Подробнее – http://narkolog-na-dom-saratov0.ru/narkolog-saratov-na-dom/https://narkolog-na-dom-saratov0.ru
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Выяснить больше – вывод из запоя недорого саратов
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Разобраться лучше – https://vyvod-iz-zapoya-saratov0.ru/vyvod-iz-zapoya-saratov-na-domu/
Каждый из методов подбирается индивидуально, что позволяет учитывать медицинские показания и личные особенности пациента.
Детальнее – лечение пивного алкоголизма в перми
электрокарнизы для штор http://www.provorota.su/ .
электрокарнизы для штор купить http://www.elektrokarniz2.ru .
Наркологическая клиника «ВолгаМед Центр» — это круглосуточный медицинский комплекс, в котором экстренная помощь, капельницы и детоксикация объединены в единую клинико-поведенческую систему. Мы лечим не «симптом по одному», а управляем весь маршрут: от первичной стабилизации и снижения токсической нагрузки до восстановления сна, аппетита и рабочих ритмов. Каждый шаг имеет цель, измеримый маркер и назначенное «окно» переоценки — это исключает полипрагмазию и делает динамику предсказуемой для пациента и семьи. Конфиденциальность не декларируется, а обеспечивается регламентами: немаркированная логистика, нейтральные формулировки в документах, «тихие» каналы связи и разграничение доступа к медзаписям.
Изучить вопрос глубже – http://narkologicheskaya-klinika-saratov0.ru
Каждое из этих направлений имеет важное значение и в совокупности формирует основу для устойчивого выздоровления.
Исследовать вопрос подробнее – наркологическая клиника лечение алкоголизма омск
Ниже — ориентир для острых часов на дому. Это не жёсткий шаблон, а карта, где ясно: что делаем, чем измеряем, когда пересматриваем. При отсутствии отклика мы меняем один параметр (например, темп инфузии) и назначаем новое окно оценки, не «двигая» всё остальное.
Узнать больше – вызвать нарколога на дом в саратове
Ниже — ориентир для острых часов на дому. Это не жёсткий шаблон, а карта, где ясно: что делаем, чем измеряем, когда пересматриваем. При отсутствии отклика мы меняем один параметр (например, темп инфузии) и назначаем новое окно оценки, не «двигая» всё остальное.
Детальнее – нарколог на дом анонимно саратов
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Детальнее – http://narcologicheskaya-klinika-omsk0.ru/narkologicheskaya-bolnicza-omsk/
электрокарнизы для штор цена электрокарнизы для штор цена .
Перед таблицей важный переход: это ориентир, а не жёсткое расписание. Врач адаптирует длительность и насыщенность этапов под возраст, фоновые заболевания и входное состояние, но логика последовательности остаётся неизменной — от безопасности к устойчивости.
Изучить вопрос глубже – наркологическая клиника москва бесплатно
Наркологическая клиника в Перми обеспечивает пациентам комфортные условия и профессиональное сопровождение. Врачи работают круглосуточно и соблюдают строгую конфиденциальность, что делает лечение доступным и безопасным.
Выяснить больше – платная наркологическая клиника в перми
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Подробнее – вывод из запоя клиника
Вывод из запоя — это не «волшебная капельница», а последовательная медицинская программа с чёткими целями и измеримыми маркерами. В наркологической клинике «СаратовМед Профи» маршрут строится по принципу управляемых окон: на каждом шаге команда преследует одну цель, меняет лишь один параметр и оценивает результат в заранее назначённый момент. Такой подход снижает лекарственную нагрузку, предотвращает «гонку дозировок» и делает динамику предсказуемой для пациента и близких. Конфиденциальность обеспечивается регламентом: немаркированные выезды, нейтральные формулировки в документах, «тихие» каналы связи, доступ к записям — строго по ролям.
Получить дополнительные сведения – наркология вывод из запоя саратов
При работе с медицинскими документами очень важно иметь качественный переводы медицинской терминологии, чтобы гарантировать точность и соответствие международным стандартам.
сложный процесс, включающий не только перевод текстов, но и глубокое понимание медицинской терминологии . Это необходимо для того, чтобы гарантировать точность перевода медицинских текстов . В медицинском переводе команда переводчиков и редакторов сотрудничает для достижения высочайшего качества.
Медицинский перевод включает в себя создание учебных материалов для медицинских студентов и специалистов . Всё это требует глубокого понимания медицинской терминологии и современных методов лечения . Для того, чтобы обеспечить высокое качество перевода , медицинские переводчики постоянно совершенствуют свои навыки .
Медицинский перевод можно разделить на несколько основных типов, включая перевод документов, устный перевод и локализацию . Это включает в себя перевод медицинских статей и исследований . При выполнении таких задач обладать способностью точно передавать сложную информацию в доступной форме.
Перевод медицинских документов является крайне важным , поскольку он предполагает работу с конфиденциальной информацией . Другой важный аспект — устный перевод, который используется во время консультаций и операций . Это требует ?? lavorать под давлением и в сжатые сроки .
Точность в медицинском переводе имеет решающее значение для обеспечения качества медицинской помощи . Медицинские переводчики не могут допускать ошибок, которые могут привести к непредвиденным последствиям. Переводчики должны понимать нюансы медицинской терминологии .
Малейшая ошибка в переводе может привести к серьезным последствиям . Для того, чтобы гарантировать точность перевода , медицинские переводчики используют специализированное программное обеспечение для проверки и редактирования. Это включает в себя использование глоссариев и баз данных .
Использование технологий в медицинском переводе позволяет оптимизировать затраты и повысить качество . Это включает в себя разработку специализированных инструментов для медицинского перевода. Однако, основная задача остается за квалифицированными переводчиками и редакторами.
Технологии дают возможность автоматизировать рутинные задачи . Но, человеческий фактор обеспечивает нюансированность и точность . Для того, чтобы оставаться конкурентоспособными на рынке, медицинские переводчики должны быть в курсе последних технологических достижений .
Компания предлагает широкий выбор премиум входные двери в квартиру, изготовленные с учетом индивидуальных пожеланий каждого клиента и соответствующие высоким стандартам качества и безопасности.
являются символом роскоши и статуса . Они изготавливаются из лучших материалов . Металлические двери премиум класса устанавливаются в домах и офисах людей, которые ценят комфорт и безопасность .
Металлические двери премиум класса имеют широкий спектр оттенков и дизайнов . Они предназначены для долгого срока службы . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и защиты.
Металлические двери премиум класса имеют усиленные элементы безопасности . Они способны выдерживать различные внешние воздействия. Металлические двери премиум класса сохраняют свои функциональные свойства на протяжении многих лет.
Металлические двери премиум класса обеспечивают круглосуточную охрану и безопасность. Они могут быть интегрированы с другими системами безопасности . Металлические двери премиум класса повышают статус и престиж владельца.
Металлические двери премиум класса способны выдерживать различные погодные условия. Они пропускают минимальное количество шума и холода . Металлические двери премиум класса являются долгосрочной инвестицией в будущее .
Металлические двери премиум класса имеют долгий срок службы и сохраняют свои функциональные свойства. Они имеют широкий спектр оттенков и цветов . Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и защиты .
Металлические двери премиум класса являются идеальным решением для тех, кто ищет надежную защиту и комфорт . Они способны выдерживать различные внешние воздействия. Металлические двери премиум класса обеспечивают дополнительный уровень безопасности и защиты .
Металлические двери премиум класса могут быть изготовлены в соответствии с индивидуальными заказами и дизайном. Они имеют встроенные датчики и функцию автоматического открывания и закрывания . Металлические двери премиум класса повышают статус и престиж владельца.
готовые рулонные шторы купить в москве готовые рулонные шторы купить в москве .
рулонная штора автоматическая http://www.rulonnye-shtory-s-elektroprivodom499.ru/ .
Наркологическая клиника «Балтийская Наркология» — это безопасное пространство, где для лечения зависимостей используются современные доказательные методики, человеческий язык коммуникации и «тихая» логистика. Мы не практикуем универсальные схемы и «сильные процедуры для всех» — терапия собирается модульно, вокруг конкретной задачи: стабилизация, нормализация сна, снижение тревоги, настройка опор поведения и профилактика рецидивов. Каждый шаг имеет цель, окно оценки и критерий перехода. Анонимность не декларируется — она встроена в процесс: немаркированные маршруты, гражданская одежда персонала, нейтральные формулировки в документах, «беззвучные» уведомления и разграниченный доступ к медицинской карте.
Получить дополнительную информацию – наркологическая клиника калининград
Стартовый осмотр должен быть быстрым и осмысленным. Мы исключаем «обязательные» исследования, которые не меняют тактику, и оставляем то, что прямо влияет на состав инфузии, темп, место ведения (дом/амбулатория/стационар) и объём поведенческих рекомендаций. Решения принимаются на свежих цифрах и клинической картине «здесь и сейчас», а повторные замеры назначаются не «по привычке», а по смыслу. Это экономит силы пациента и время команды, а главное — уменьшает фармакологическую нагрузку без потери безопасности.
Подробнее – наркологическая клиника нарколог в ставрополе
Мы не используем «универсальные коктейли». Капельницы собираются из модулей под ведущую задачу, а поведенческая часть усиливает эффект. Окончательные назначения делает врач с учётом противопоказаний и взаимодействий; таблица ниже — ориентир для пациента и семьи.
Подробнее тут – помощь вывод из запоя мурманск
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Подробнее можно узнать тут – вывод из запоя в стационаре
Первое сутки — каркас программы. Мы фиксируем цель каждого окна, инструменты, метрики контроля и критерий перехода. Если ответ «плоский», меняется ровно один параметр (темп/объём/последовательность) и назначается новое окно проверки. Этот принцип позволяет понять, что именно сработало, и избежать полипрагмазии.
Получить дополнительную информацию – наркологическая клиника вывод из запоя петрозаводск
тканевые электрожалюзи prokarniz23.ru .
Карта делает маршрут прозрачным для пациента и семьи. Вместо «лучше/хуже» — факты и понятные пороги. Это снижает тревожность и помогает соблюдать режим без сопротивления.
Изучить вопрос глубже – наркологическая клиника клиника помощь
Первая ровная ночь — фундамент. Мы настраиваем затемнение, фиксированное время отбоя, минимум экранов и раздражителей, при необходимости — щадящую седативную поддержку, которая стабилизирует, а не «выключает». Утром — повторная оценка и корректировка дозировок.
Подробнее тут – besplatnaya-narkologicheskaya-klinika
Мы никогда не «лечим по заголовку». На старте фиксируем витальные показатели, собираем лекарственную историю и оцениваем факторы среды — график работы, «шум» дома, уровень физической активности, качество ночи. Параллельно обсуждаем, что для человека важнее сейчас: быстро «снять волну» симптомов, мягко перестроить вечерние привычки, настроить семейные договорённости или объединить всё это в короткий интенсивный период. Пациент получает не набор процедур, а маршрут: цель каждого шага, окно оценки эффекта, признаки успеха и заранее оговорённые условия для эскалации наблюдения.
Изучить вопрос глубже – платная наркологическая клиника в ставрополе
Вывод из запоя — это управляемая медицинская процедура с предсказуемыми шагами, а не «сильная капельница, которая помогает всем». В наркологической клинике «СеверКар Медикус» мы строим лечение как маршрут: цель > инструмент > маркеры контроля > окно повторной оценки. Такой подход снижает лекарственную нагрузку, ускоряет восстановление сна и аппетита и делает процесс понятным пациенту и семье. Мы работаем круглосуточно, организуем выезд нарколога на дом, разворачиваем тихую, безопасную среду и соблюдаем анонимность: нейтральные формулировки, гражданская одежда специалистов, немаркированный транспорт и «беззвучные» уведомления.
Изучить вопрос глубже – http://www.domen.ru
Если при первичном звонке фиксируем «красные флаги» (угнетение сознания, выраженная одышка, резкое падение SpO?, нестабильная аритмия), сразу предлагаем стационарное наблюдение с ночным постом. При низких рисках начинаем дома, но держим низкий порог для эскалации, чтобы не терять время, если состояние меняется.
Исследовать вопрос подробнее – выезд нарколога на дом в ставрополе
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Исследовать вопрос подробнее – вывод из запоя цена
Мы не составляем «супер-смеси» «на всякий случай». Капельница — это набор модулей, каждый из которых отвечает за конкретную задачу: гидратация, электролиты, гастропротекция, антиоксидантная поддержка; при показаниях — мягкая анксиолитика. Порядок модулей зависит от ведущего симптом-кластера и времени суток.
Подробнее – сколько стоит капельница от запоя в мурманске
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Получить больше информации – наркологическая клиника в калининграде
Мы не используем универсальные «сильные капельницы». Эффективность даёт точное совпадение с задачей. Ниже — логика выбора профилей и маркеры, на которые мы ориентируемся при контроле эффективности и безопасности.
Узнать больше – https://vivod-iz-zapoya-v-sankt-peterburge16.ru/vyvod-iz-zapoya-anonimno-v-sankt-peterburge
Вывод из запоя в клинике в Санкт-Петербурге осуществляется под круглосуточным медицинским контролем с применением современных методов инфузионной терапии, препаратов для восстановления обменных процессов и купирования синдрома отмены. Главной задачей врачей является восстановление баланса между физическим и психическим состоянием, предотвращение осложнений и стабилизация основных жизненных функций.
Углубиться в тему – наркологическая клиника цены в санкт-петербурге
электрические рулонные шторы на окна электрические рулонные шторы на окна .
рулонные шторы это http://www.rulonnye-shtory-s-elektroprivodom.ru .
Инфузионная терапия — это не универсальный «коктейль», а набор узких шагов под клиническую задачу. Главные цели понятны: вернуть объём циркулирующей жидкости и перфузию тканей, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревожность, подготовить нервную систему к сну. При тошноте подключаются противорвотные и гастропротекция; кардиокоррекция даётся только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и «красные флажки» для связи. Такой минимум достаточных вмешательств снижает побочные эффекты, делает бюджет предсказуемым и удерживает результат не часами, а днями. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Получить дополнительную информацию – наркологическая клиника сайт
Зависимость всегда про неопределённость: скачки давления и пульса, тремор, тревожность, бессонные ночи, споры в семье и страх огласки. «ЛюберМед Центр» убирает эту неопределённость управляемым маршрутом. Мы начинаем с краткого, но точного интервью, фиксируем объективные показатели и тут же объясняем, какие вмешательства уместны сегодня и зачем именно они. Никаких «общих залов» и очередей: приёмы разнесены по времени, подтверждения проходят по защищённым каналам, визиты на дом — без маркировки. Наш принцип — минимальная достаточность: столько медицины, сколько нужно для безопасного перехвата динамики и первой ровной ночи. Именно она делает дальнейшие шаги предсказуемыми: снижается тремор, выравнивается ритм, появляется ресурс соблюдать режим. Благодаря продуманной логистике Люберец мы сокращаем холостые перемещения, а значит, лечение начинается раньше, а тревоги — меньше. В результате пациент и семья получают не «набор услуг», а последовательность: понятные действия, прозрачные ожидания и устойчивый эффект, который держится днями, а не часами.
Узнать больше – анонимная наркологическая клиника
Когда подходит
Подробнее можно узнать тут – http://narkologicheskaya-klinika-lyubercy0.ru
Карта — это общий язык для всех участников процесса. Пациент видит смысл каждого шага, родные знают, когда и чему посвящены короткие апдейты, а врач точно понимает, какой параметр корректировать, чтобы не потерять причинно-следственную связь.
Подробнее тут – https://vyvod-iz-zapoya-murmansk15.ru/vyvedenie-iz-zapoya-murmansk
Ночной приём организован по принципу «мягкой посадки». Если нет «красных флагов», сначала создаём комфортную среду (температура, тёплый свет, вода малыми глотками), затем проводим экспресс-диагностику и только после этого запускаем инфузионную терапию. Когда организм не перегружен сенсорными раздражителями, он отвечает на лечение ровнее: уменьшаются скачки пульса, снижается тошнота, а пациенты уже к утру описывают «ясную голову» без «ваты».
Исследовать вопрос подробнее – http://narkologicheskaya-klinika-v-murmanske15.ru
Первые часы определяют траекторию. Мы работаем по карте — у каждого окна есть цель, действия, маркеры контроля и критерий перехода. Если ответ «плоский», меняем один элемент и назначаем повторную оценку. Это дисциплинирует решения и защищает от полипрагмазии.
Разобраться лучше – http://vyvod-iz-zapoya-petrozavodsk15.ru/vyvod-iz-zapoya-na-domu-petrozavodsk/https://vyvod-iz-zapoya-petrozavodsk15.ru
At this time it sounds like Expression Engine is the preferred blogging platform out there right now. (from what I’ve read) Is that what you’re using on your blog?
forticlient on mac
Маршрут выстроен прозрачно. Сначала идёт короткое предметное интервью — только то, что меняет тактику «сегодня»: длительность запоя, принятые лекарства (включая «самолечение»), аллергии, хронические диагнозы, количество ночей без сна. Затем — объективные показатели (АД/пульс/сатурация/температура), оценка тремора и уровня тревоги; при показаниях проводится экспресс-ЭКГ и базовый неврологический скрининг. После этого врач объясняет, какие компоненты войдут в инфузию и почему: регидратация для восстановления объёма циркулирующей жидкости, коррекция электролитов, печёночная поддержка, при необходимости — гастропротекция и противорвотные; мягкая анксиолитическая коррекция — строго по показаниям. Мы принципиально избегаем «универсальных сильных смесей» и «оглушающих» дозировок: они дают дневной «блеск», но почти всегда провоцируют вечерний откат, ухудшение сна и рост рисков. Во время процедуры пациент и семья получают понятные письменные правила на 48–72 часа: вода и лёгкая еда «по часам», затемнение и тишина вечером, фиксированное время отбоя, «красные флажки» для связи и согласованное утреннее окно контроля. Такой сценарий убирает импровизации, снижает уровень конфликтов и помогает нервной системе перейти из режима тревоги в режим восстановления.
Детальнее – prokapatsya-doma-v-lyubercah
Формат выбирается по безопасности, а не «по желанию». Домашний или амбулаторный старт уместен, если показатели устойчивы: нет упорной рвоты, высокой температуры, выраженной дезориентации, резких «качелей» давления и пульса, признаков обезвоживания с угрозой судорог. В этих условиях один визит часто закрывает задачу: индивидуальная инфузия, письменные рекомендации, правила воды и лёгкой еды «по часам», утренний контроль. Если же состояние «по краю» — сочетание рвоты, лихорадки, кардиальных жалоб, второй бессонной ночи, выраженного тремора — честнее короткая стационарная стабилизация на 24–48 часов под круглосуточным наблюдением. На бумаге это кажется дороже одного выезда, но на практике предотвращает цепочку ночных «пожаров», импульсивных повторов и осложнений, то есть экономит и силы, и деньги семьи. В любом формате анонимность неизменна: визиты без маркировки, закрытые каналы связи, разнесённые по времени приёмы и доступ к данным по ролям.
Изучить вопрос глубже – вывод из запоя на дому
Мы не используем «универсальные коктейли». Капельницы собираются из модулей под ведущую задачу, а поведенческая часть усиливает эффект. Окончательные назначения делает врач с учётом противопоказаний и взаимодействий; таблица ниже — ориентир для пациента и семьи.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-murmansk15.ru/vyvedenie-iz-zapoya-murmansk
Философия клиники — «тихо, адресно, прозрачно». Выездная бригада приходит без маркировки, документы оформляются нейтрально, доступ к клинической записи разделён по ролям, а коммуникации со семьёй проходят короткими апдейтами в согласованные моменты. Такая организационная дисциплина — клинический инструмент: меньше сенсорного шума — ровнее пульс к вечеру, устойчивее засыпание и меньше потребность в «усилителях».
Детальнее – вывод из запоя на дому в мурманске
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-kaliningrad15.ru
автоматические жалюзи автоматические жалюзи .
Мы не используем универсальные «сильные» схемы. Модули подбираются по ведущей жалобе и времени суток; последовательность зависит от переносимости и клинических приоритетов. Ниже — ориентир, понятный пациенту; окончательные решения принимает врач с учётом противопоказаний и лекарственных взаимодействий.
Узнать больше – наркологический вывод из запоя петрозаводск
Карта понятна пациенту и семье: видно, что будет происходить, по каким признакам мы перейдём к следующему шагу и когда состоится проверка. Это снижает тревожность и повышает приверженность плану.
Изучить вопрос глубже – вывод из запоя
Если дома шумно (ремонт, маленькие дети, гости), организуем краткий «тихий» стационар с отдельным входом и камерными палатами. После стабилизации пациент возвращается домой, а амбулаторное сопровождение продолжается в удобном графике — через короткие очные визиты и дистанционные чек-ины.
Получить дополнительные сведения – https://vivod-iz-zapoya-v-sankt-peterburge16.ru/vyvedenie-iz-zapoya-staczionar-sankt-peterburg/
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Ознакомиться с деталями – https://narkologicheskaya-klinika-kaliningrad15.ru/kaliningrad-narkologicheskaya-bolnicza
Мы не противопоставляем форматы — комбинируем их. Например, первые часы — выездная стабилизация с титрованной инфузией и чётким контролем АД/ЧСС/SpO?, затем — амбулаторные короткие визиты с вечерними онлайн-вставками. Если появляются «красные флаги» (дыхание, ритм, сознание), маршрут без пауз переводится в стационар: та же карта наблюдения, те же цели, только круглосуточный мониторинг и ночной пост. Приватность встроена на каждом этапе: нейтральные формулировки в документах, «тихие» уведомления, гражданская одежда персонала, доступ к данным по ролям.
Подробнее тут – [url=https://narkologicheskaya-klinika-stavropol15.ru/]анонимная наркологическая клиника ставрополь[/url]
Мы не используем универсальные «сильные капельницы». Эффективность даёт точное совпадение с задачей. Ниже — логика выбора профилей и маркеры, на которые мы ориентируемся при контроле эффективности и безопасности.
Подробнее – вывод из запоя вызов на дом в санкт-петербурге
Мы не используем универсальные «сильные капельницы». Эффективность даёт точное совпадение с задачей. Ниже — логика выбора профилей и маркеры, на которые мы ориентируемся при контроле эффективности и безопасности.
Ознакомиться с деталями – наркологический вывод из запоя
Карта — это общий язык для всех участников процесса. Пациент видит смысл каждого шага, родные знают, когда и чему посвящены короткие апдейты, а врач точно понимает, какой параметр корректировать, чтобы не потерять причинно-следственную связь.
Выяснить больше – вывод из запоя вызов на дом
Карта — это общий язык для всех участников процесса. Пациент видит смысл каждого шага, родные знают, когда и чему посвящены короткие апдейты, а врач точно понимает, какой параметр корректировать, чтобы не потерять причинно-следственную связь.
Изучить вопрос глубже – вывод из запоя недорого
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Выяснить больше – https://vyvod-iz-zapoya-kaliningrad15.ru/vyvod-iz-zapoya-kaliningrad-staczionar/
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Выяснить больше – вывод из запоя вызов город
Мы сознательно фиксируем не только «медицинские» параметры, но и бытовые маркеры: сколько воды выпито, как переносится тёплая пища малыми порциями, какой свет в комнате перед сном. Эти детали активно упоминаются в клинических рекомендациях, потому что нередко именно они решают исход первой ночи лучше, чем попытка «усилить» таблеткой.
Получить дополнительную информацию – наркологическая клиника вывод из запоя
Стартовый осмотр должен быть быстрым и осмысленным. Мы исключаем «обязательные» исследования, которые не меняют тактику, и оставляем то, что прямо влияет на состав инфузии, темп, место ведения (дом/амбулатория/стационар) и объём поведенческих рекомендаций. Решения принимаются на свежих цифрах и клинической картине «здесь и сейчас», а повторные замеры назначаются не «по привычке», а по смыслу. Это экономит силы пациента и время команды, а главное — уменьшает фармакологическую нагрузку без потери безопасности.
Изучить вопрос глубже – лечение в наркологической клинике
Мурманск — город с длинными сумерками и влажным ветром от Кольского залива, что сказывается на сну и вечерней кардиолабильности. Поэтому мы адаптируем маршруты: выездные бригады работают в гражданской одежде, заходят быстро и тихо, а в палатах клиники используется тёплая подсветка и акустическое поглощение. Для ночных поступлений действует протокол «мягкой посадки»: минимизированные контакты, тёплая вода малыми глотками, затем — диагностика и старт инфузии при отсутствии «красных флагов». Это снижает сенсорную нагрузку и позволяет организму дать честный клинический ответ без лишних раздражителей.
Изучить вопрос глубже – капельница от запоя стоимость
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Углубиться в тему – http://vyvod-iz-zapoya-petrozavodsk15.ru/vyvod-iz-zapoya-kruglosutochno-petrozavodsk/
Вся динамика заносится в единую карту наблюдения. Если потребуются амбулаторные точки или стационар, вы не «начинаете историю заново» — маршрут продолжится с той же целью и теми же критериями успеха.
Получить дополнительную информацию – платный нарколог на дом в ставрополе
Наркологическая клиника «РеМед Карелия» — это круглосуточная медицинская помощь, построенная на принципе клинической точности: каждая процедура имеет цель, проверяемые маркеры и назначенное окно переоценки. Мы используем современные методы детоксикации и постабстинентной стабилизации, не перегружая терапию «на всякий случай» и не полагаясь на универсальные «сильные капельницы». Вместо этого — модульные схемы, корректировка одного параметра за раз и обязательная оценка результата. Такой подход снижает фармаконагрузку, ускоряет восстановление сна и аппетита и делает лечение предсказуемым для пациента и его семьи. Анонимность встроена в процессы: немаркированные входы, гражданская форма персонала, нейтральные формулировки в документах, «тихие» уведомления и разграниченный доступ к карте наблюдения.
Разобраться лучше – http://www.domen.ru
рулонные шторы на пластиковые окна с электроприводом рулонные шторы на пластиковые окна с электроприводом .
рулонные шторы на окна москва rulonnye-shtory-s-elektroprivodom.ru .
В Санкт-Петербурге для адресных обращений дежурят мобильные бригады круглосуточно. Координатор при звонке уточняет хронические заболевания, аллергии, текущие лекарства и эпизоды судорог/психозов, а также бытовые условия: есть ли доступ к розетке, можно ли обеспечить 2–3 часа тишины, удобна ли зона полулёжа. Эта информация позволяет врачу в дороге выбрать стартовую скорость инфузии, продумать последовательность введения и подготовить расходные материалы под планировку квартиры. Мы соблюдаем приватность: нейтральная экипировка, деликатные формулировки в документах и один доверенный контакт со стороны семьи.
Подробнее можно узнать тут – вывод из запоя в стационаре санкт-петербург
Наркологическая клиника «Балтийская Наркология» — это безопасное пространство, где для лечения зависимостей используются современные доказательные методики, человеческий язык коммуникации и «тихая» логистика. Мы не практикуем универсальные схемы и «сильные процедуры для всех» — терапия собирается модульно, вокруг конкретной задачи: стабилизация, нормализация сна, снижение тревоги, настройка опор поведения и профилактика рецидивов. Каждый шаг имеет цель, окно оценки и критерий перехода. Анонимность не декларируется — она встроена в процесс: немаркированные маршруты, гражданская одежда персонала, нейтральные формулировки в документах, «беззвучные» уведомления и разграниченный доступ к медицинской карте.
Получить дополнительные сведения – http://narkologicheskaya-klinika-kaliningrad15.ru
Вывод из запоя на дому — это управляемый медицинский процесс, где каждая деталь имеет значение: от первичного осмотра и грамотного подбора инфузионного профиля до сенсорной дисциплины в помещении и чётких «окон оценки» результата. В наркологической клинике «СеверМед Трезвость» мы используем принцип минимально достаточных вмешательств: одна цель на этап, один измеримый маркер и одна корректировка за раз. Такой подход снижает нагрузку на организм, повышает предсказуемость и делает восстановление переносимым для пациента и его близких.
Получить дополнительные сведения – наркология вывод из запоя санкт-петербург
Без сна любая дневная капельница даёт короткий «блеск» и вечерний откат. Поэтому мы заранее настраиваем гигиену: затемнение, прохлада, фиксированное время отбоя, минимум экранов и разговоров, при показаниях — щадящая седативная поддержка, которая стабилизирует, а не «выключает». Утром — короткий контроль и подстройка дозировок, чтобы вторая ночь стала ещё спокойнее.
Ознакомиться с деталями – http://narkologicheskaya-klinika-himki9.ru/
Когда зависимость выходит из-под контроля, каждая задержка превращается в цепочку случайностей: рушится сон, «скачет» давление и пульс, усиливается тревога, дома нарастает напряжение. «МедСфера Мытищи» убирает хаос управляемым маршрутом: чёткий первичный осмотр, объяснённые назначения, понятные правила на 48–72 часа и прогнозируемые окна связи. Мы не лечим «пакетами ради прайса» — только клиническая достаточность на сегодня с учётом длительности употребления, сопутствующих диагнозов, принимаемых препаратов и исходных показателей. Такой подход снижает тревожность, возвращает ощущение контроля и быстрее приводит к первому ровному сну — именно он становится переломной точкой, после которой решения принимаются спокойно и по плану. Важная деталь — отсутствие общих очередей и «публичных» зон: приём разнесён по времени, входы приватны, а коммуникация ведётся через закрытые каналы. Когда понятно, что будет через час, вечером и завтра утром, исчезает потребность в импровизациях, и лечение действительно работает.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-mytishchi9.ru/narkologicheskaya-klinika-stacionar-v-mytishchah
Инфузионная терапия — не магический «коктейль», а последовательность узких шагов под клиническую задачу. Регидратация возвращает объём циркулирующей жидкости и улучшает перфузию тканей; коррекция электролитов стабилизирует нервно-мышечную передачу и сердечный ритм; печёночная поддержка снижает токсическую нагрузку; при тошноте подключаются противорвотные и гастропротекция; при выраженной тревоге — мягкая анксиолитическая коррекция по показаниям. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и «красные флажки», требующие связи. Диагностика назначается тогда, когда её результат меняет тактику сегодня, — никакой «проверки на всякий случай». Такой минимально достаточный подход уменьшает побочные эффекты, делает бюджет предсказуемым и удерживает эффект не часами, а днями.
Ознакомиться с деталями – anonimnaya-narkologicheskaya-klinika
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Разобраться лучше – http://narkologicheskaya-klinika-v-kaliningrade15.ru/skoraya-narkologiya-vyvod-iz-zapoya-kaliningrad-uslugi/
Мы не составляем «супер-смеси» «на всякий случай». Капельница — это набор модулей, каждый из которых отвечает за конкретную задачу: гидратация, электролиты, гастропротекция, антиоксидантная поддержка; при показаниях — мягкая анксиолитика. Порядок модулей зависит от ведущего симптом-кластера и времени суток.
Подробнее можно узнать тут – вызов на дом капельницы от запоя в мурманске
Ниже — практическая карта первых часов. Она помогает всем участникам понимать логику действий, точки контроля и критерии перехода. Если ответ «плоский», меняем один параметр и возвращаемся к оценке в назначённое время — без хаотичных «усилений».
Подробнее – капельница от запоя вызов
Если при первичном звонке фиксируем «красные флаги» (угнетение сознания, выраженная одышка, резкое падение SpO?, нестабильная аритмия), сразу предлагаем стационарное наблюдение с ночным постом. При низких рисках начинаем дома, но держим низкий порог для эскалации, чтобы не терять время, если состояние меняется.
Изучить вопрос глубже – https://narkolog-na-dom-stavropol15.ru/chastnyj-narkolog-stavropol/
Если при первичном звонке фиксируем «красные флаги» (угнетение сознания, выраженная одышка, резкое падение SpO?, нестабильная аритмия), сразу предлагаем стационарное наблюдение с ночным постом. При низких рисках начинаем дома, но держим низкий порог для эскалации, чтобы не терять время, если состояние меняется.
Получить дополнительную информацию – вызов нарколога на дом
Мы не противопоставляем форматы — комбинируем их. Например, первые часы — выездная стабилизация с титрованной инфузией и чётким контролем АД/ЧСС/SpO?, затем — амбулаторные короткие визиты с вечерними онлайн-вставками. Если появляются «красные флаги» (дыхание, ритм, сознание), маршрут без пауз переводится в стационар: та же карта наблюдения, те же цели, только круглосуточный мониторинг и ночной пост. Приватность встроена на каждом этапе: нейтральные формулировки в документах, «тихие» уведомления, гражданская одежда персонала, доступ к данным по ролям.
Получить дополнительные сведения – http://narkologicheskaya-klinika-stavropol15.ru
Первое сутки с половиной — «каркас» программы. Мы формулируем цель каждого окна, фиксируем инструменты и пороги перехода. Если ожидаемой динамики нет, меняется один параметр (темп/объём/последовательность), после чего назначается повторная оценка. Это защищает от полипрагмазии и сохраняет причинно-следственную связь.
Исследовать вопрос подробнее – наркологическая клиника клиника помощь в петрозаводске
Мы сознательно фиксируем не только «медицинские» параметры, но и бытовые маркеры: сколько воды выпито, как переносится тёплая пища малыми порциями, какой свет в комнате перед сном. Эти детали активно упоминаются в клинических рекомендациях, потому что нередко именно они решают исход первой ночи лучше, чем попытка «усилить» таблеткой.
Разобраться лучше – лечение в наркологической клинике ставрополь
Снижается тремор, уменьшается тошнота, пульс и давление перестают «скакать», появляется возможность уснуть без паники. Важно не перегружать этот эффект разговорами «по душам», яркими экранами и проверками «на прочность»: когда среда тихая и затемнённая, организм закрепляет улучшение, а не теряет его к полуночи.
Получить дополнительные сведения – врач вывод из запоя
жалюзи с электроприводом купить жалюзи с электроприводом купить .
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить дополнительную информацию – анонимная наркологическая клиника калининград
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Углубиться в тему – запой наркологическая клиника
Чтобы у пациента и близких не возникал вопрос «что дальше», мы используем карту первых часов. Она задаёт цели, действия, контроль и критерии перехода между этапами. Такой подход экономит минуты и исключает импровизации «ради уверенности».
Исследовать вопрос подробнее – вывод из запоя на дому круглосуточно
Инфузионная терапия — это не универсальный «коктейль», а набор узких шагов под клиническую задачу. Главные цели понятны: вернуть объём циркулирующей жидкости и перфузию тканей, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревожность, подготовить нервную систему к сну. При тошноте подключаются противорвотные и гастропротекция; кардиокоррекция даётся только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и «красные флажки» для связи. Такой минимум достаточных вмешательств снижает побочные эффекты, делает бюджет предсказуемым и удерживает результат не часами, а днями. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Подробнее тут – http://narkologicheskaya-klinika-himki9.ru/kruglosutochnaya-narkologicheskaya-klinika-v-himkah/
Первая ровная ночь — поворотная точка. Без неё любая дневная инфузия работает коротко и «сгорает» к вечеру. Мы заранее настраиваем простые, но критичные условия: затемнение, тишина, прохладная комната, фиксированное время отбоя, минимум экранов и разговоров. При показаниях назначается щадящая седативная поддержка в дозах, которые стабилизируют, а не «выключают». Утром — короткий контроль и подстройка доз, чтобы другая ночь прошла ещё спокойнее. Такой «простой» протокол даёт самый устойчивый результат: исчезают панические волны, выравниваются показатели, снижается вероятность повторных экстренных обращений, а значит, бюджет остаётся предсказуемым.
Подробнее можно узнать тут – вывод из запоя вызов
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Изучить вопрос глубже – http://narkologicheskaya-klinika-lyubercy9.ru/
Первая ровная ночь — поворотная точка. Без неё любая дневная инфузия работает коротко и «сгорает» к вечеру. Мы заранее настраиваем простые, но критичные условия: затемнение, тишина, прохладная комната, фиксированное время отбоя, минимум экранов и разговоров. При показаниях назначается щадящая седативная поддержка в дозах, которые стабилизируют, а не «выключают». Утром — короткий контроль и подстройка доз, чтобы другая ночь прошла ещё спокойнее. Такой «простой» протокол даёт самый устойчивый результат: исчезают панические волны, выравниваются показатели, снижается вероятность повторных экстренных обращений, а значит, бюджет остаётся предсказуемым.
Изучить вопрос глубже – https://vyvod-iz-zapoya-himki9.ru/vyvod-iz-zapoya-v-stacionare-v-himkah/
Такая карта делает лечение обозримым и дисциплинирует решения: пациент видит цель и порог перехода, семья понимает, зачем нужно соблюдать «тихие» часы, команда сохраняет управляемость и не «крутит ручки» ночью.
Подробнее – наркологическая клиника клиника помощь в петрозаводске
«Капельница от запоя» в современном понимании — это не одна универсальная смесь, а последовательность управляемых шагов с понятной целью, измеримыми показателями и заранее назначенными точками переоценки. В наркологической клинике «СеверАльфа Мед» мы используем модульные инфузионные протоколы и бережный мониторинг, чтобы безопасно снять интоксикацию, восстановить водно-электролитный баланс, снизить тремор и вернуть физиологичный сон без «переседации». Каждый этап сопровождается сервисом конфиденциального уровня: нейтральные формулировки в документах, немаркированная логистика, «тихие» каналы связи, доступ к записям строго по ролям. Это делает путь пациента предсказуемым и защищённым от лишнего внимания.
Изучить вопрос глубже – сколько стоит капельница на дому от запоя
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Узнать больше – https://vyvod-iz-zapoya-kaliningrad15.ru/skoraya-narkologiya-vyvod-iz-zapoya-kaliningrad-uslugi
Городская среда Ставрополя создаёт дополнительные раздражители — трафик, шумовые пики, яркое освещение подъездов. Команда «СтаврДоктор» гасит эти факторы организационно: секторное распределение бригад, согласованная парковка, вход в подъезд без опознавательных знаков, доставка расходников при необходимости отдельно от врача, чтобы на месте сразу перейти к осмотру и инфузии. Коммуникация ведётся через защищённые каналы, уведомления «беззвучные», наименования в чеках — нейтральные. Если пациенту спокойнее, общение частично берёт на себя доверенное лицо; оно получает краткие апдейты в заранее оговорённые «тихие окна».
Узнать больше – нарколог на дом
Мы отказываемся от «сильных» коктейлей ради скорости и опираемся на принцип одного изменения за раз: корректируется только темп, объём или последовательность модулей, после чего следует контроль в согласованное «окно». Такой подход минимизирует лекарственную нагрузку, защищает печень, миокард и центральную нервную систему, а также снижает риск рецидивной тревоги в первую ночь. Важная часть лечения — сенсорная гигиена: тёплая подсветка вместо резкого верхнего света, тихий режим в смартфонах, маска для сна и беруши при чувствительности к шуму. Эти «бытовые» меры — на самом деле клинические инструменты с измеримым эффектом на пульс, дыхание и латентность сна.
Детальнее – вызвать капельницу от запоя на дому мурманск
Алгоритм на выезде помогает убрать импровизации, а семье — понимать, что будет происходить и по каким признакам мы двигаемся дальше. Он гибкий, но всегда прозрачный: каждый шаг имеет цель, инструмент и критерий успеха.
Получить больше информации – http://narkolog-na-dom-stavropol15.ru/chastnyj-narkolog-stavropol/
Детокс — это не «чудо-капельница», а последовательность узких вмешательств. Цели понятны: восстановить объём циркулирующей жидкости, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревогу, подготовить нервную систему к сну. При тошноте подключается противорвотная поддержка и гастропротекция, витаминные комплексы — по показаниям, кардиокоррекция — только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и маркеры для немедленной связи. Такой реализм снижает импульсивность и делает результат измеримым: вечером — не «откат», а предсказуемая усталость, ночью — ровный сон, утром — стабильные показатели. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Разобраться лучше – заказать обратный звонок наркологическая клиника
Городская среда Калининграда специфична: морской ветер, сезонные пробки, яркие витрины в вечерние часы. Эти факторы часто усиливают тревожность и мешают засыпанию. Поэтому мы проектируем выезд «мягко»: согласованная парковка, немаркированный вход, короткий маршрут до места процедуры, отсутствие громких звонков и «визуального шума» у порога. Родственникам предоставляем «тихие окна» связи — короткие апдейты в заранее оговорённое время без лишних подробностей. Такой формат не просто комфортнее, он клинически полезен: чем меньше стимулов, тем меньше потребность в ночных «усилениях» и тем стабильнее проходит первая ночь.
Исследовать вопрос подробнее – вывод из запоя с выездом калининград
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Исследовать вопрос подробнее – наркологические клиники алкоголизм
Первая ровная ночь — поворотная точка. Без неё любая дневная инфузия работает коротко и «сгорает» к вечеру. Мы заранее настраиваем простые, но критичные условия: затемнение, тишина, прохладная комната, фиксированное время отбоя, минимум экранов и разговоров. При показаниях назначается щадящая седативная поддержка в дозах, которые стабилизируют, а не «выключают». Утром — короткий контроль и подстройка доз, чтобы другая ночь прошла ещё спокойнее. Такой «простой» протокол даёт самый устойчивый результат: исчезают панические волны, выравниваются показатели, снижается вероятность повторных экстренных обращений, а значит, бюджет остаётся предсказуемым.
Разобраться лучше – narkolog-vyvod-iz-zapoya
«Волшебной капельницы» не существует. Мы структурируем инфузии от симптомов, а не от «средних рецептов». Ниже — логика подбора для типичных профилей; реальную схему определяет врач на месте.
Ознакомиться с деталями – https://narkologicheskaya-klinika-v-kaliningrade15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
Первая ровная ночь — поворотная точка. Без неё любая дневная инфузия работает коротко и «сгорает» к вечеру. Мы заранее настраиваем простые, но критичные условия: затемнение, тишина, прохладная комната, фиксированное время отбоя, минимум экранов и разговоров. При показаниях назначается щадящая седативная поддержка в дозах, которые стабилизируют, а не «выключают». Утром — короткий контроль и подстройка доз, чтобы другая ночь прошла ещё спокойнее. Такой «простой» протокол даёт самый устойчивый результат: исчезают панические волны, выравниваются показатели, снижается вероятность повторных экстренных обращений, а значит, бюджет остаётся предсказуемым.
Детальнее – вывод из запоя с выездом
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Углубиться в тему – анонимный вывод из запоя калининград
Если на предвызовном созвоне звучат «красные флаги» (неукротимая рвота, выраженная дезориентация, «скачущий» ритм, одышка), мы сразу резервируем палату усиленного наблюдения и подключаем расширенный мониторинг. При низком риске старт возможен амбулаторно или на дому с бесшовным переводом в стационар при необходимости — без очередей и «говорящих» вывесок. Во всех сценариях анонимность — не «опция», а стандарт по умолчанию.
Узнать больше – https://narkologicheskaya-klinika-petrozavodsk15.ru/petrozavodsk-narkologiya/
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Ознакомиться с деталями – вывод наркологическая клиника
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить дополнительную информацию – вывод из запоя на дому недорого
География накладывает отпечаток на клинические решения. Длинные сумерки, переменчивый ветер с акватории и «звонкие» подъезды старого фонда увеличивают чувствительность к свету и шуму, а значит — усиливают вечернюю кардиолабильность. В «АрктикМед Профи» протоколы адаптированы под такой фон: в палатах преобладают тёплые источники света, на обходах персонал работает в «режиме тишины», в смартфонах включается «без уведомлений», а выездные бригады заходят в дом максимально незаметно. Такой «мягкий» сценарий делает помощь не только деликатной, но и клинически эффективной — снижается потребность в «сильных» седативных вмешательствах, сохраняется физиологичность сна.
Исследовать вопрос подробнее – наркологическая клиника клиника помощь мурманск
Мы комбинируем медицинские и немедикаментозные решения. Инфузионная терапия — адресная, с контролем безопасности; поведенческие опоры — просты и выполняемы в реальной жизни; телемедицина помогает пройти «трудный час» без лишних поездок и импровизаций. Ниже — ориентиры логики подбора, они не заменяют очный осмотр.
Выяснить больше – наркологическая клиника стационар
Купить пакеты майки оптом по выгодной цене и с доставкой от производителя!
Очень важно, чтобы пакеты были прочными и надежными.
jet location
Un autre critere est le type de aeronef que vous selectionnez. Differents types presenter des tarifs tres heterogenes. Par exemple, un aeronef leger qu’un aeronef luxe. Cela etre evaluee lors de votre selection.
Aussi, la saison que vous optez pour pour votre vol affecte egalement le cout. Durant les periodes de forte demande, les croitre. avantageux de organiser votre vol a l’avance pour eviter ces hausses de prix. D’autre part, en basse saison, vous seriez capable de des offres tres interessantes.
En resume, il est fondamental de comparer les alternatives disponibles avant de opter pour un aeronef personnel. De plus, il est de consulter des experts pour obtenir des donnees fiables et precises. En ayant ces details en poche, vous serez plus prepare a prendre un vol en jet prive et a administer votre budget.
«Тёмные часы» вечера — время импульсивных решений. Мы даём короткие, нейтральные инструменты на 20–40 минут: тёплый душ, прогулка рядом с домом при устойчивых показателях, дыхательная практика, короткий созвон с «своим» человеком. Эти бесплатные шаги поддерживают ровный сон и уменьшают вероятность «дорогих» экстренных повторов.
Подробнее тут – https://narkologicheskaya-klinika-himki9.ru/kruglosutochnaya-narkologicheskaya-klinika-v-himkah
гидроизоляция подвала гаража гидроизоляция подвала гаража .
обмазочная гидроизоляция цена обмазочная гидроизоляция цена .
гидроизоляция инъектированием гидроизоляция инъектированием .
«Волшебной капельницы» не существует. Мы структурируем инфузии от симптомов, а не от «средних рецептов». Ниже — логика подбора для типичных профилей; реальную схему определяет врач на месте.
Получить дополнительные сведения – вывод из запоя вызов в калининграде
Зависимость всегда про неопределённость: скачки давления и пульса, тремор, тревожность, бессонные ночи, споры в семье и страх огласки. «ЛюберМед Центр» убирает эту неопределённость управляемым маршрутом. Мы начинаем с краткого, но точного интервью, фиксируем объективные показатели и тут же объясняем, какие вмешательства уместны сегодня и зачем именно они. Никаких «общих залов» и очередей: приёмы разнесены по времени, подтверждения проходят по защищённым каналам, визиты на дом — без маркировки. Наш принцип — минимальная достаточность: столько медицины, сколько нужно для безопасного перехвата динамики и первой ровной ночи. Именно она делает дальнейшие шаги предсказуемыми: снижается тремор, выравнивается ритм, появляется ресурс соблюдать режим. Благодаря продуманной логистике Люберец мы сокращаем холостые перемещения, а значит, лечение начинается раньше, а тревоги — меньше. В результате пациент и семья получают не «набор услуг», а последовательность: понятные действия, прозрачные ожидания и устойчивый эффект, который держится днями, а не часами.
Получить дополнительные сведения – http://narkologicheskaya-klinika-lyubercy9.ru/chastnaya-narkologicheskaya-klinika-v-lyubercah/
бездепозитные бонусы за регистрацию в казино с выводом без пополнения по номеру телефона
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Углубиться в тему – наркологическая клиника клиника помощь калининград
Today, I went to the beach with my kids. I found a sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell to her ear and screamed. There was a hermit crab inside and it pinched her ear. She never wants to go back! LoL I know this is totally off topic but I had to tell someone!
fortinet vpn
Страх огласки часто откладывает обращение сильнее симптомов; затяжка почти всегда ухудшает прогноз и увеличивает расходы. В «ХимкиМед Центр» приватность — регламент, а не обещание: заявки и подтверждения проходят через защищённые каналы, в расписании используются шифры, приёмы разнесены по времени, а визиты — без маркировки. Маршрут по двору и подъезду согласуется заранее, чтобы врач прошёл к двери без внимания соседей. Мы учитываем «узкие» места Химок — дворовые проезды, часы пик, загруженные выезды — поэтому холостые перемещения минимальны, а терапия стартует быстро. Чем меньше публичности и пауз, тем ниже тревога, выше приверженность режиму и, как следствие, устойчивее результат.
Получить больше информации – http://narkologicheskaya-klinika-himki9.ru/platnaya-narkologicheskaya-klinika-v-himkah/https://narkologicheskaya-klinika-himki9.ru
Острый этап разбит на небольшие «окна» с измеримыми целями. Это убирает неопределённость и дисциплинирует процесс: пациент знает, что будет происходить, когда будет проверка и по каким маркерам оценивается успех. Если ответ «плоский», корректируется один параметр, а затем обязательно следует повторная оценка в оговорённое время.
Выяснить больше – анонимная наркологическая клиника в мурманске
Инфузионная терапия в «АрктикМед Профи» строится на модулях, каждый из которых решает конкретную задачу: гидратация, коррекция электролитов, гастропротекция, метаболическая поддержка; при необходимости — мягкая анксиолитика по строгим показаниям. Порядок модулей и темп выбираются под ведущий симптом-кластер и время суток. Мы обязательно фиксируем исходные и промежуточные маркеры, чтобы видеть причинно-следственную связь.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-v-murmanske15.ru
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Изучить вопрос глубже – http://narkologicheskaya-klinika-lyubercy9.ru/chastnaya-narkologicheskaya-klinika-v-lyubercah/
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Получить больше информации – http://narkologicheskaya-klinika-kaliningrad15.ru
Мы комбинируем медицинские и немедикаментозные решения. Инфузионная терапия — адресная, с контролем безопасности; поведенческие опоры — просты и выполняемы в реальной жизни; телемедицина помогает пройти «трудный час» без лишних поездок и импровизаций. Ниже — ориентиры логики подбора, они не заменяют очный осмотр.
Разобраться лучше – https://narkologicheskaya-klinika-kaliningrad15.ru/kaliningrad-narkologicheskij-dispanser/
Если при первичном звонке выявляются «красные флаги» — неукротимая рвота, одышка, спутанность, «скачущий» ритм, подозрение на травму — мы немедленно резервируем палату усиленного наблюдения. При низком риске стартуем амбулаторно или на дому с бесшовным переводом в стационар, если динамика меняется. В любом случае цель одна: безопасно стабилизировать состояние, вернуть питьё и физиологичный сон, объяснить семье и пациенту короткий «язык фактов», по которому судим об эффективности.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-v-petrozavodske15.ru/chastnaya-narkologicheskaya-klinika-petrozavodsk/
Когда зависимость выходит из-под контроля, семья сталкивается с двумя видами неопределённости — медицинской и организационной. На одной чаше весов тремор, скачки давления и пульса, рвота, обрывочный сон и нарастающая тревога; на другой — страх огласки, очереди, ожидание «до завтра» и бесконечные попытки уговорить себя «перетерпеть». «ХимкиМед Центр» снимает обе неопределённости управляемым маршрутом: у нас нет общих залов с «публичными» ожиданиями, приёмы разнесены по времени, длинные разговоры заменены коротким и предметным интервью, а назначения объясняются простым языком — что делаем сегодня, чего ждать через час, какие ощущения будут нормальными и при каких признаках нужно срочно связаться. Мы не лечим «пакетами ради прайса»: схема строится от фактов — длительность употребления, сопутствующие заболевания, уже принятые препараты, исходные показатели (АД, пульс, сатурация), выраженность тремора и качество сна. Такой реализм экономит силы, снижает тревогу и чаще уже в первые сутки приводит к главному — к первой ровной ночи, после которой решения принимаются спокойно и по плану.
Изучить вопрос глубже – наркологическая клиника стоимость
Зависимость всегда про неопределённость: скачки давления и пульса, тремор, тревожность, бессонные ночи, споры в семье и страх огласки. «ЛюберМед Центр» убирает эту неопределённость управляемым маршрутом. Мы начинаем с краткого, но точного интервью, фиксируем объективные показатели и тут же объясняем, какие вмешательства уместны сегодня и зачем именно они. Никаких «общих залов» и очередей: приёмы разнесены по времени, подтверждения проходят по защищённым каналам, визиты на дом — без маркировки. Наш принцип — минимальная достаточность: столько медицины, сколько нужно для безопасного перехвата динамики и первой ровной ночи. Именно она делает дальнейшие шаги предсказуемыми: снижается тремор, выравнивается ритм, появляется ресурс соблюдать режим. Благодаря продуманной логистике Люберец мы сокращаем холостые перемещения, а значит, лечение начинается раньше, а тревоги — меньше. В результате пациент и семья получают не «набор услуг», а последовательность: понятные действия, прозрачные ожидания и устойчивый эффект, который держится днями, а не часами.
Получить дополнительные сведения – chastnaya-narkologicheskaya-klinika
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Исследовать вопрос подробнее – анонимный вывод из запоя в калининграде
«Тёмные часы» вечера — время импульсивных решений. Мы даём короткие, нейтральные инструменты на 20–40 минут: тёплый душ, прогулка рядом с домом при устойчивых показателях, дыхательная практика, короткий созвон с «своим» человеком. Эти бесплатные шаги поддерживают ровный сон и уменьшают вероятность «дорогих» экстренных повторов.
Получить дополнительные сведения – http://narkologicheskaya-klinika-himki9.ru/anonimnaya-narkologicheskaya-klinika-v-himkah/
Мытищи дают плюсы домашнего формата: меньше логистики, приватнее, выше приверженность режиму. Если показатели устойчивы и нет признаков угрозы осложнений (упорной рвоты, высокой температуры, выраженной дезориентации, резких «качелей» АД/пульса, риска судорог), старт на дому или амбулаторно — рациональное решение. Но когда состояние «по краю», честнее и на дистанции дешевле сутки–двое стационара под круглосуточным наблюдением: проще дозировать препараты, вовремя закрывать дефициты, добиться первого ровного сна и не «разбрасываться» экстренными ночными выездами. Формат выбирается не «по желанию», а по безопасности здесь и сейчас; при этом конфиденциальность сохранена в любом сценарии — немаркированные визиты, разнесённые приёмы, доступ к данным по ролям.
Получить дополнительную информацию – наркологическая клиника на дом
Инфузионная терапия — это не универсальный «коктейль», а набор узких шагов под клиническую задачу. Главные цели понятны: вернуть объём циркулирующей жидкости и перфузию тканей, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревожность, подготовить нервную систему к сну. При тошноте подключаются противорвотные и гастропротекция; кардиокоррекция даётся только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и «красные флажки» для связи. Такой минимум достаточных вмешательств снижает побочные эффекты, делает бюджет предсказуемым и удерживает результат не часами, а днями. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Изучить вопрос глубже – http://narkologicheskaya-klinika-himki9.ru
Зависимость всегда про неопределённость: скачки давления и пульса, тремор, тревожность, бессонные ночи, споры в семье и страх огласки. «ЛюберМед Центр» убирает эту неопределённость управляемым маршрутом. Мы начинаем с краткого, но точного интервью, фиксируем объективные показатели и тут же объясняем, какие вмешательства уместны сегодня и зачем именно они. Никаких «общих залов» и очередей: приёмы разнесены по времени, подтверждения проходят по защищённым каналам, визиты на дом — без маркировки. Наш принцип — минимальная достаточность: столько медицины, сколько нужно для безопасного перехвата динамики и первой ровной ночи. Именно она делает дальнейшие шаги предсказуемыми: снижается тремор, выравнивается ритм, появляется ресурс соблюдать режим. Благодаря продуманной логистике Люберец мы сокращаем холостые перемещения, а значит, лечение начинается раньше, а тревоги — меньше. В результате пациент и семья получают не «набор услуг», а последовательность: понятные действия, прозрачные ожидания и устойчивый эффект, который держится днями, а не часами.
Подробнее тут – анонимная наркологическая клиника
Если при первичном звонке выявляются «красные флаги» — неукротимая рвота, одышка, спутанность, «скачущий» ритм, подозрение на травму — мы немедленно резервируем палату усиленного наблюдения. При низком риске стартуем амбулаторно или на дому с бесшовным переводом в стационар, если динамика меняется. В любом случае цель одна: безопасно стабилизировать состояние, вернуть питьё и физиологичный сон, объяснить семье и пациенту короткий «язык фактов», по которому судим об эффективности.
Детальнее – платная наркологическая клиника петрозаводск
What’s up to all, how is all, I think every one is getting more from this web site, and your views are fastidious in support of new viewers.
Qfinder Pro
Наркологическая клиника «Балтийская Наркология» — это безопасное пространство, где для лечения зависимостей используются современные доказательные методики, человеческий язык коммуникации и «тихая» логистика. Мы не практикуем универсальные схемы и «сильные процедуры для всех» — терапия собирается модульно, вокруг конкретной задачи: стабилизация, нормализация сна, снижение тревоги, настройка опор поведения и профилактика рецидивов. Каждый шаг имеет цель, окно оценки и критерий перехода. Анонимность не декларируется — она встроена в процесс: немаркированные маршруты, гражданская одежда персонала, нейтральные формулировки в документах, «беззвучные» уведомления и разграниченный доступ к медицинской карте.
Подробнее – наркологическая клиника нарколог калининград
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Углубиться в тему – бесплатная наркологическая клиника
Карта — это общий язык для всех участников процесса. Пациент видит смысл каждого шага, родные знают, когда и чему посвящены короткие апдейты, а врач точно понимает, какой параметр корректировать, чтобы не потерять причинно-следственную связь.
Получить больше информации – https://vyvod-iz-zapoya-murmansk15.ru/vyvod-iz-zapoya-murmansk-narkolog-na-dom-kapelnicza
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-kaliningrad15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
Когда зависимость выходит из-под контроля, каждая задержка превращается в цепочку случайностей: рушится сон, «скачет» давление и пульс, усиливается тревога, дома нарастает напряжение. «МедСфера Мытищи» убирает хаос управляемым маршрутом: чёткий первичный осмотр, объяснённые назначения, понятные правила на 48–72 часа и прогнозируемые окна связи. Мы не лечим «пакетами ради прайса» — только клиническая достаточность на сегодня с учётом длительности употребления, сопутствующих диагнозов, принимаемых препаратов и исходных показателей. Такой подход снижает тревожность, возвращает ощущение контроля и быстрее приводит к первому ровному сну — именно он становится переломной точкой, после которой решения принимаются спокойно и по плану. Важная деталь — отсутствие общих очередей и «публичных» зон: приём разнесён по времени, входы приватны, а коммуникация ведётся через закрытые каналы. Когда понятно, что будет через час, вечером и завтра утром, исчезает потребность в импровизациях, и лечение действительно работает.
Получить больше информации – наркологическая клиника мытищи
В Санкт-Петербурге для адресных обращений дежурят мобильные бригады круглосуточно. Координатор при звонке уточняет хронические заболевания, аллергии, текущие лекарства и эпизоды судорог/психозов, а также бытовые условия: есть ли доступ к розетке, можно ли обеспечить 2–3 часа тишины, удобна ли зона полулёжа. Эта информация позволяет врачу в дороге выбрать стартовую скорость инфузии, продумать последовательность введения и подготовить расходные материалы под планировку квартиры. Мы соблюдаем приватность: нейтральная экипировка, деликатные формулировки в документах и один доверенный контакт со стороны семьи.
Изучить вопрос глубже – вывод из запоя цена в санкт-петербурге
«Тёмные часы» вечера — время импульсивных решений. Мы даём короткие, нейтральные инструменты на 20–40 минут: тёплый душ, прогулка рядом с домом при устойчивых показателях, дыхательная практика, короткий созвон с «своим» человеком. Эти бесплатные шаги поддерживают ровный сон и уменьшают вероятность «дорогих» экстренных повторов.
Узнать больше – https://narkologicheskaya-klinika-himki9.ru/platnaya-narkologicheskaya-klinika-v-himkah/
Мы собираем терапию из проверенных модулей: гидратация, коррекция электролитов, гастропротекция, антиоксидантная поддержка, мягкая анксиолитика по показаниям, поведенческие интервенции (свет, тишина, дыхание 4–6, стимул-контроль, вечерние ритуалы). Объём и темп зависят от ведущего симптома и времени суток: при кардиореактивном вечере больше внимания уделяется среде, при тошноте — гастропротекции и «тёплому питанию», при поверхностном сне — цифровой гигиене и световым сценариям. Ниже приведена ориентировочная матрица выбора; финальное решение — за лечащим врачом с учётом противопоказаний и лекарственных взаимодействий.
Исследовать вопрос подробнее – наркологическая клиника стационар в петрозаводске
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Детальнее – анонимная наркологическая клиника
Эта карта — рабочий инструмент: она не только структурирует действия персонала, но и снижает тревогу пациента и семьи. Появляется чувство контроля: понятно, что происходит сейчас и к чему мы идём через час, три и до утра.
Подробнее можно узнать тут – наркологическая клиника наркологический центр в мурманске
Первые часы определяют траекторию. Мы работаем по карте — у каждого окна есть цель, действия, маркеры контроля и критерий перехода. Если ответ «плоский», меняем один элемент и назначаем повторную оценку. Это дисциплинирует решения и защищает от полипрагмазии.
Получить дополнительные сведения – вывод из запоя в петрозаводске
Наркологическая клиника «КарелМед Центр» — это круглосуточное лечение, современное оборудование и предсказуемые протоколы, которые избавляют пациента и семью от догадок. Мы не используем «универсальные сильные капельницы» и не усиливаем схему «на всякий случай»: каждое вмешательство имеет понятную цель, измеримые маркеры и заранее оговорённое окно повторной оценки. Такой подход снижает фармаконагрузку, бережёт сон, сокращает вечернюю реактивность и делает первую ночь спокойнее. Анонимность встроена в процессы: немаркированные входы, гражданская одежда персонала, нейтральные формулировки в документах и «беззвучные» уведомления по согласованным каналам связи.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-petrozavodsk15.ru/chastnaya-narkologicheskaya-klinika-petrozavodsk
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-kaliningrad15.ru/
География накладывает отпечаток на клинические решения. Длинные сумерки, переменчивый ветер с акватории и «звонкие» подъезды старого фонда увеличивают чувствительность к свету и шуму, а значит — усиливают вечернюю кардиолабильность. В «АрктикМед Профи» протоколы адаптированы под такой фон: в палатах преобладают тёплые источники света, на обходах персонал работает в «режиме тишины», в смартфонах включается «без уведомлений», а выездные бригады заходят в дом максимально незаметно. Такой «мягкий» сценарий делает помощь не только деликатной, но и клинически эффективной — снижается потребность в «сильных» седативных вмешательствах, сохраняется физиологичность сна.
Получить больше информации – http://narkologicheskaya-klinika-v-murmanske15.ru
Такая карта делает лечение обозримым и дисциплинирует решения: пациент видит цель и порог перехода, семья понимает, зачем нужно соблюдать «тихие» часы, команда сохраняет управляемость и не «крутит ручки» ночью.
Получить больше информации – лечение в наркологической клинике в петрозаводске
Первая ровная ночь — фундамент. Мы настраиваем затемнение, фиксированное время отбоя, минимум экранов и раздражителей, при необходимости — щадящую седативную поддержку, которая стабилизирует, а не «выключает». Утром — повторная оценка и корректировка дозировок.
Получить больше информации – http://narkologicheskaya-klinika-mytishchi9.ru/telefon-narkologicheskoj-kliniki-v-mytishchah/
Такая карта делает лечение обозримым и дисциплинирует решения: пациент видит цель и порог перехода, семья понимает, зачем нужно соблюдать «тихие» часы, команда сохраняет управляемость и не «крутит ручки» ночью.
Узнать больше – https://narkologicheskaya-klinika-v-petrozavodske15.ru/chastnaya-narkologicheskaya-klinika-petrozavodsk/
Городская среда Калининграда специфична: морской ветер, сезонные пробки, яркие витрины в вечерние часы. Эти факторы часто усиливают тревожность и мешают засыпанию. Поэтому мы проектируем выезд «мягко»: согласованная парковка, немаркированный вход, короткий маршрут до места процедуры, отсутствие громких звонков и «визуального шума» у порога. Родственникам предоставляем «тихие окна» связи — короткие апдейты в заранее оговорённое время без лишних подробностей. Такой формат не просто комфортнее, он клинически полезен: чем меньше стимулов, тем меньше потребность в ночных «усилениях» и тем стабильнее проходит первая ночь.
Исследовать вопрос подробнее – вывод из запоя вызов
Мы не используем «универсальные коктейли». Капельницы собираются из модулей под ведущую задачу, а поведенческая часть усиливает эффект. Окончательные назначения делает врач с учётом противопоказаний и взаимодействий; таблица ниже — ориентир для пациента и семьи.
Ознакомиться с деталями – вывод из запоя цена
Вывод из запоя на дому — это управляемый медицинский процесс, где каждая деталь имеет значение: от первичного осмотра и грамотного подбора инфузионного профиля до сенсорной дисциплины в помещении и чётких «окон оценки» результата. В наркологической клинике «СеверМед Трезвость» мы используем принцип минимально достаточных вмешательств: одна цель на этап, один измеримый маркер и одна корректировка за раз. Такой подход снижает нагрузку на организм, повышает предсказуемость и делает восстановление переносимым для пациента и его близких.
Углубиться в тему – вывод из запоя вызов на дом в санкт-петербурге
Если ожидаемая динамика «плоская», врач меняет один параметр и назначает повторную оценку. Такой подход сохраняет ясность днём и снижает вероятность побочных реакций.
Ознакомиться с деталями – наркологические клиники алкоголизм
Если на предвызовном созвоне звучат «красные флаги» (неукротимая рвота, выраженная дезориентация, «скачущий» ритм, одышка), мы сразу резервируем палату усиленного наблюдения и подключаем расширенный мониторинг. При низком риске старт возможен амбулаторно или на дому с бесшовным переводом в стационар при необходимости — без очередей и «говорящих» вывесок. Во всех сценариях анонимность — не «опция», а стандарт по умолчанию.
Получить дополнительные сведения – https://narkologicheskaya-klinika-petrozavodsk15.ru/chastnaya-narkologicheskaya-klinika-petrozavodsk/
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Выяснить больше – наркология вывод из запоя
Когда зависимость выходит из-под контроля, семья сталкивается с двумя видами неопределённости — медицинской и организационной. На одной чаше весов тремор, скачки давления и пульса, рвота, обрывочный сон и нарастающая тревога; на другой — страх огласки, очереди, ожидание «до завтра» и бесконечные попытки уговорить себя «перетерпеть». «ХимкиМед Центр» снимает обе неопределённости управляемым маршрутом: у нас нет общих залов с «публичными» ожиданиями, приёмы разнесены по времени, длинные разговоры заменены коротким и предметным интервью, а назначения объясняются простым языком — что делаем сегодня, чего ждать через час, какие ощущения будут нормальными и при каких признаках нужно срочно связаться. Мы не лечим «пакетами ради прайса»: схема строится от фактов — длительность употребления, сопутствующие заболевания, уже принятые препараты, исходные показатели (АД, пульс, сатурация), выраженность тремора и качество сна. Такой реализм экономит силы, снижает тревогу и чаще уже в первые сутки приводит к главному — к первой ровной ночи, после которой решения принимаются спокойно и по плану.
Исследовать вопрос подробнее – наркологическая клиника отзывы
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить больше информации – https://vyvod-iz-zapoya-kaliningrad15.ru
Когда зависимость выходит из-под контроля, каждая задержка превращается в цепочку случайностей: рушится сон, «скачет» давление и пульс, усиливается тревога, дома нарастает напряжение. «МедСфера Мытищи» убирает хаос управляемым маршрутом: чёткий первичный осмотр, объяснённые назначения, понятные правила на 48–72 часа и прогнозируемые окна связи. Мы не лечим «пакетами ради прайса» — только клиническая достаточность на сегодня с учётом длительности употребления, сопутствующих диагнозов, принимаемых препаратов и исходных показателей. Такой подход снижает тревожность, возвращает ощущение контроля и быстрее приводит к первому ровному сну — именно он становится переломной точкой, после которой решения принимаются спокойно и по плану. Важная деталь — отсутствие общих очередей и «публичных» зон: приём разнесён по времени, входы приватны, а коммуникация ведётся через закрытые каналы. Когда понятно, что будет через час, вечером и завтра утром, исчезает потребность в импровизациях, и лечение действительно работает.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-mytishchi9.ru/narkologicheskaya-klinika-stacionar-v-mytishchah/
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-lyubercy9.ru/narkologicheskaya-klinika-otzyvy-v-lyubercah
Вывод из запоя — это управляемая медицинская процедура с предсказуемыми шагами, а не «сильная капельница, которая помогает всем». В наркологической клинике «СеверКар Медикус» мы строим лечение как маршрут: цель > инструмент > маркеры контроля > окно повторной оценки. Такой подход снижает лекарственную нагрузку, ускоряет восстановление сна и аппетита и делает процесс понятным пациенту и семье. Мы работаем круглосуточно, организуем выезд нарколога на дом, разворачиваем тихую, безопасную среду и соблюдаем анонимность: нейтральные формулировки, гражданская одежда специалистов, немаркированный транспорт и «беззвучные» уведомления.
Детальнее – https://vyvod-iz-zapoya-petrozavodsk15.ru/vyvod-iz-zapoya-kruglosutochno-petrozavodsk
Городская среда Калининграда — контрастные подъезды, близость моря с переменчивым ветром, плотный сезонный трафик — может усиливать вечернюю реактивность. Поэтому маршруты организованы «тихо»: согласованная парковка, отдельный вход без вывесок и очередей, короткая регистрация, приглушённая тёплая подсветка в зоне ожидания, отсутствие громких объявлений. Коммуникация с пациентами и близкими строится через защищённые каналы, а уведомления приходят в «беззвучном» режиме в согласованные «окна». Такой дизайн не ради «красоты сервиса», а ради клинического эффекта: чем меньше сенсорной нагрузки, тем быстрее выравнивается пульс к вечеру, тем легче возвращается переносимость питья и тёплой пищи, тем меньше потребность в ночных «усилениях».
Узнать больше – запой наркологическая клиника в калининграде
Районы с плотной застройкой, дворовые проезды, пиковые часы — всё учитывается при планировании визитов. Чем меньше холостых перемещений, тем быстрее начинается помощь и тем ниже вероятность внеплановых повторов «по тревоге».
Подробнее тут – chastnaya-narkologicheskaya-klinika-v-mytishchah
Такая карта делает лечение обозримым и дисциплинирует решения: пациент видит цель и порог перехода, семья понимает, зачем нужно соблюдать «тихие» часы, команда сохраняет управляемость и не «крутит ручки» ночью.
Выяснить больше – http://narkologicheskaya-klinika-v-petrozavodske15.ru/
Маршрут запускается с короткого, но точного сбора данных: врач уточняет симптомы, лекарства за последние 24–48 часов, аллергии и хронические диагнозы, измеряет давление, пульс, сатурацию, при необходимости выполняет экспресс-ЭКГ и базовый неврологический скрининг. Далее — простое объяснение логики вмешательств: зачем именно такая инфузионная схема, что она даст в ближайшие 30–60 минут, как будет организован вечер и когда мы свяжемся утром. Мы избегаем «оглушающих» седативов и универсальных «сильных смесей», чтобы не получить вечернего отката и побочных реакций; дозы подбираются узко и корректируются по реакции организма. Пациент уходит с письменными рекомендациями на 48–72 часа: вода и лёгкая еда «по часам», правила «тихого вечера», критерии повторного контакта и окно связи. Семья понимает роли: меньше разговорных «разборов», больше тишины и затемнения — в такой среде физиология перестаёт «качать», сон приходит предсказуемо, а утренние показатели выравниваются.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-himki9.ru
Мы не используем универсальные «сильные капельницы». Эффективность даёт точное совпадение с задачей. Ниже — логика выбора профилей и маркеры, на которые мы ориентируемся при контроле эффективности и безопасности.
Исследовать вопрос подробнее – https://vivod-iz-zapoya-v-sankt-peterburge16.ru/vyvedenie-iz-zapoya-staczionar-sankt-peterburg/
Мы не используем «универсальные коктейли». Капельницы собираются из модулей под ведущую задачу, а поведенческая часть усиливает эффект. Окончательные назначения делает врач с учётом противопоказаний и взаимодействий; таблица ниже — ориентир для пациента и семьи.
Детальнее – вывод из запоя цена
Городская среда Петрозаводска со сменой ветров с Онежского озера, короткими сумерками и сезонными перепадами влажности может усиливать тревожность в вечерние часы. Мы учитываем это с момента первого контакта: согласованная парковка, отдельный вход без вывесок, короткая регистрация без «толстых анкет», приглушённый тёплый свет в зоне ожидания и отсутствие громких объявлений. Родственникам предоставляются «тихие окна» связи — лаконичные апдейты в фиксированное время, чтобы не перегружать пациента и не дёргать команду в критические окна наблюдения. Такой «мягкий» контур снижает сенсорную нагрузку, стабилизирует вариабельность ЧСС к сумеркам и сокращает число импульсивных просьб «усилить на ночь».
Изучить вопрос глубже – https://narkologicheskaya-klinika-petrozavodsk15.ru
Мы не используем универсальные «сильные капельницы». Эффективность даёт точное совпадение с задачей. Ниже — логика выбора профилей и маркеры, на которые мы ориентируемся при контроле эффективности и безопасности.
Исследовать вопрос подробнее – анонимный вывод из запоя в санкт-петербурге
В Мурманске длинные сумерки, влажный ветер и «звонкие» подъезды старого фонда повышают чувствительность к свету и звуку. Поэтому выезд «Северный Медлайн» начинается с настройки среды: приглушается верхний свет, обеспечивается проветривание без сквозняка, смартфоны переводятся в «тихий режим» с «белым списком» близких. Только после этого врач проводит осмотр и запускает инфузионную терапию. Такой «тихий» сценарий снижает потребность в седативных препаратах и сохраняет физиологичность сна в первую ночь.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-murmansk15.ru/vyvod-iz-zapoya-murmansk-narkolog-na-dom-kapelnicza
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Изучить вопрос глубже – https://narkologicheskaya-klinika-kaliningrad15.ru/kaliningrad-narkologicheskaya-bolnicza/
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Углубиться в тему – наркологическая клиника цены
Инфузионная терапия — это не универсальный «коктейль», а набор узких шагов под клиническую задачу. Главные цели понятны: вернуть объём циркулирующей жидкости и перфузию тканей, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревожность, подготовить нервную систему к сну. При тошноте подключаются противорвотные и гастропротекция; кардиокоррекция даётся только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и «красные флажки» для связи. Такой минимум достаточных вмешательств снижает побочные эффекты, делает бюджет предсказуемым и удерживает результат не часами, а днями. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-himki9.ru/narkologicheskaya-klinika-ceny-v-himkah/
Мы сознательно фиксируем не только «медицинские» параметры, но и бытовые маркеры: сколько воды выпито, как переносится тёплая пища малыми порциями, какой свет в комнате перед сном. Эти детали активно упоминаются в клинических рекомендациях, потому что нередко именно они решают исход первой ночи лучше, чем попытка «усилить» таблеткой.
Получить дополнительные сведения – https://narkologicheskaya-klinika-stavropol15.ru/narkologicheskaya-klinika-stavropol-otzyvy/
Зависимость всегда про неопределённость: скачки давления и пульса, тремор, тревожность, бессонные ночи, споры в семье и страх огласки. «ЛюберМед Центр» убирает эту неопределённость управляемым маршрутом. Мы начинаем с краткого, но точного интервью, фиксируем объективные показатели и тут же объясняем, какие вмешательства уместны сегодня и зачем именно они. Никаких «общих залов» и очередей: приёмы разнесены по времени, подтверждения проходят по защищённым каналам, визиты на дом — без маркировки. Наш принцип — минимальная достаточность: столько медицины, сколько нужно для безопасного перехвата динамики и первой ровной ночи. Именно она делает дальнейшие шаги предсказуемыми: снижается тремор, выравнивается ритм, появляется ресурс соблюдать режим. Благодаря продуманной логистике Люберец мы сокращаем холостые перемещения, а значит, лечение начинается раньше, а тревоги — меньше. В результате пациент и семья получают не «набор услуг», а последовательность: понятные действия, прозрачные ожидания и устойчивый эффект, который держится днями, а не часами.
Узнать больше – narkologicheskaya-klinika
Городская среда Петрозаводска со сменой ветров с Онежского озера, короткими сумерками и сезонными перепадами влажности может усиливать тревожность в вечерние часы. Мы учитываем это с момента первого контакта: согласованная парковка, отдельный вход без вывесок, короткая регистрация без «толстых анкет», приглушённый тёплый свет в зоне ожидания и отсутствие громких объявлений. Родственникам предоставляются «тихие окна» связи — лаконичные апдейты в фиксированное время, чтобы не перегружать пациента и не дёргать команду в критические окна наблюдения. Такой «мягкий» контур снижает сенсорную нагрузку, стабилизирует вариабельность ЧСС к сумеркам и сокращает число импульсивных просьб «усилить на ночь».
Подробнее можно узнать тут – наркологическая клиника стационар петрозаводск
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Подробнее – вывод из запоя клиника в калининграде
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Изучить вопрос глубже – vyvod-iz-zapoya-petrozavodsk15.ru/
Первые часы определяют траекторию. Мы работаем по карте — у каждого окна есть цель, действия, маркеры контроля и критерий перехода. Если ответ «плоский», меняем один элемент и назначаем повторную оценку. Это дисциплинирует решения и защищает от полипрагмазии.
Получить дополнительные сведения – вывод из запоя вызов на дом
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Подробнее тут – http://narkologicheskaya-klinika-kaliningrad15.ru/chastnaya-narkologicheskaya-klinika-kaliningrad/
Когда зависимость выходит из-под контроля, каждая задержка превращается в цепочку случайностей: рушится сон, «скачет» давление и пульс, усиливается тревога, дома нарастает напряжение. «МедСфера Мытищи» убирает хаос управляемым маршрутом: чёткий первичный осмотр, объяснённые назначения, понятные правила на 48–72 часа и прогнозируемые окна связи. Мы не лечим «пакетами ради прайса» — только клиническая достаточность на сегодня с учётом длительности употребления, сопутствующих диагнозов, принимаемых препаратов и исходных показателей. Такой подход снижает тревожность, возвращает ощущение контроля и быстрее приводит к первому ровному сну — именно он становится переломной точкой, после которой решения принимаются спокойно и по плану. Важная деталь — отсутствие общих очередей и «публичных» зон: приём разнесён по времени, входы приватны, а коммуникация ведётся через закрытые каналы. Когда понятно, что будет через час, вечером и завтра утром, исчезает потребность в импровизациях, и лечение действительно работает.
Подробнее – http://
Без сна любая дневная капельница даёт короткий «блеск» и вечерний откат. Поэтому мы заранее настраиваем гигиену: затемнение, прохлада, фиксированное время отбоя, минимум экранов и разговоров, при показаниях — щадящая седативная поддержка, которая стабилизирует, а не «выключает». Утром — короткий контроль и подстройка дозировок, чтобы вторая ночь стала ещё спокойнее.
Получить дополнительную информацию – http://www.domen.ru
Городская среда Петрозаводска со сменой ветров с Онежского озера, короткими сумерками и сезонными перепадами влажности может усиливать тревожность в вечерние часы. Мы учитываем это с момента первого контакта: согласованная парковка, отдельный вход без вывесок, короткая регистрация без «толстых анкет», приглушённый тёплый свет в зоне ожидания и отсутствие громких объявлений. Родственникам предоставляются «тихие окна» связи — лаконичные апдейты в фиксированное время, чтобы не перегружать пациента и не дёргать команду в критические окна наблюдения. Такой «мягкий» контур снижает сенсорную нагрузку, стабилизирует вариабельность ЧСС к сумеркам и сокращает число импульсивных просьб «усилить на ночь».
Получить дополнительные сведения – http://narkologicheskaya-klinika-petrozavodsk15.ru/
Вывод из запоя на дому — это управляемый медицинский процесс, где каждая деталь имеет значение: от первичного осмотра и грамотного подбора инфузионного профиля до сенсорной дисциплины в помещении и чётких «окон оценки» результата. В наркологической клинике «СеверМед Трезвость» мы используем принцип минимально достаточных вмешательств: одна цель на этап, один измеримый маркер и одна корректировка за раз. Такой подход снижает нагрузку на организм, повышает предсказуемость и делает восстановление переносимым для пациента и его близких.
Выяснить больше – вывод из запоя вызов на дом в санкт-петербурге
Зависимость всегда про неопределённость: скачки давления и пульса, тремор, тревожность, бессонные ночи, споры в семье и страх огласки. «ЛюберМед Центр» убирает эту неопределённость управляемым маршрутом. Мы начинаем с краткого, но точного интервью, фиксируем объективные показатели и тут же объясняем, какие вмешательства уместны сегодня и зачем именно они. Никаких «общих залов» и очередей: приёмы разнесены по времени, подтверждения проходят по защищённым каналам, визиты на дом — без маркировки. Наш принцип — минимальная достаточность: столько медицины, сколько нужно для безопасного перехвата динамики и первой ровной ночи. Именно она делает дальнейшие шаги предсказуемыми: снижается тремор, выравнивается ритм, появляется ресурс соблюдать режим. Благодаря продуманной логистике Люберец мы сокращаем холостые перемещения, а значит, лечение начинается раньше, а тревоги — меньше. В результате пациент и семья получают не «набор услуг», а последовательность: понятные действия, прозрачные ожидания и устойчивый эффект, который держится днями, а не часами.
Выяснить больше – https://narkologicheskaya-klinika-lyubercy9.ru/narkologicheskaya-klinika-ryadom-v-lyubercah/
Карта — это общий язык для всех участников процесса. Пациент видит смысл каждого шага, родные знают, когда и чему посвящены короткие апдейты, а врач точно понимает, какой параметр корректировать, чтобы не потерять причинно-следственную связь.
Подробнее – вывод из запоя
Мы комбинируем медицинские и немедикаментозные решения. Инфузионная терапия — адресная, с контролем безопасности; поведенческие опоры — просты и выполняемы в реальной жизни; телемедицина помогает пройти «трудный час» без лишних поездок и импровизаций. Ниже — ориентиры логики подбора, они не заменяют очный осмотр.
Получить дополнительную информацию – платная наркологическая клиника калининград
Если к «окну оценки» динамика ниже ожидаемой, меняется один параметр: последовательность введения, плотность «тихих окон», режим воды или время вечернего «безэкранного коридора». Такой минимализм делает вклад каждого шага прозрачным и снижает риск перегрузки.
Углубиться в тему – http://vivod-iz-zapoya-v-sankt-peterburge16.ru/vyvod-iz-zapoya-sankt-peterburg-vyzov-narkologa-na-dom/
Если к «окну оценки» динамика ниже ожидаемой, меняется один параметр: последовательность введения, плотность «тихих окон», режим воды или время вечернего «безэкранного коридора». Такой минимализм делает вклад каждого шага прозрачным и снижает риск перегрузки.
Ознакомиться с деталями – http://vivod-iz-zapoya-v-sankt-peterburge16.ru
Мы работаем с вниманием к деталям повседневности: как человек засыпает на фоне вечернего света, сколько воды переносит малыми глотками, как реагирует на цифровые уведомления, есть ли привычные «включатели» тяги и как на организм влияет шумное окружение. Врач и куратор переводят этот жизненный контекст в ясные, измеримые ориентиры: время до сна, число пробуждений, вариабельность пульса к сумеркам, объём воды, аппетит, переносимость тёплой мягкой пищи. Решения принимаются адресно и последовательно, чтобы сохранять ясность днём и избегать ненужной фармаконагрузки.
Выяснить больше – наркологическая клиника клиника помощь
«Тёмные часы» вечера — время импульсивных решений. Мы даём короткие, нейтральные инструменты на 20–40 минут: тёплый душ, прогулка рядом с домом при устойчивых показателях, дыхательная практика, короткий созвон с «своим» человеком. Эти бесплатные шаги поддерживают ровный сон и уменьшают вероятность «дорогих» экстренных повторов.
Получить дополнительную информацию – http://narkologicheskaya-klinika-himki9.ru
бездепозитные бонусы в казино олимп
Без сна любая дневная капельница даёт короткий «блеск» и вечерний откат. Поэтому мы заранее настраиваем гигиену: затемнение, прохлада, фиксированное время отбоя, минимум экранов и разговоров, при показаниях — щадящая седативная поддержка, которая стабилизирует, а не «выключает». Утром — короткий контроль и подстройка дозировок, чтобы вторая ночь стала ещё спокойнее.
Выяснить больше – http://narkologicheskaya-klinika-himki9.ru/platnaya-narkologicheskaya-klinika-v-himkah/https://narkologicheskaya-klinika-himki9.ru
Мы не используем «универсальные коктейли». Капельницы собираются из модулей под ведущую задачу, а поведенческая часть усиливает эффект. Окончательные назначения делает врач с учётом противопоказаний и взаимодействий; таблица ниже — ориентир для пациента и семьи.
Получить дополнительную информацию – вывод из запоя капельница на дому в мурманске
Мы не используем «универсальные коктейли». Капельницы собираются из модулей под ведущую задачу, а поведенческая часть усиливает эффект. Окончательные назначения делает врач с учётом противопоказаний и взаимодействий; таблица ниже — ориентир для пациента и семьи.
Ознакомиться с деталями – нарколог на дом вывод из запоя мурманск
Выбор формата определяется рисками, а не удобством «по настроению». Домашний выезд или амбулаторный приём уместны при устойчивых показателях: нет упорной рвоты, высокой температуры, выраженной дезориентации, резких «качелей» АД/пульса, признаков обезвоживания с угрозой судорог. В таких условиях один визит часто закрывает задачу: инфузия по показаниям, правила воды и сна, окно связи и утренний контроль. Если картина «по краю» — сочетание лихорадки, рвоты, кардиальных жалоб, второй бессонной ночи и выраженного тремора — рациональнее краткая стационарная стабилизация на 24–48 часов под круглосуточным наблюдением. На бумаге staционар дороже одного выезда, но в реальности он короче и надёжнее: дефициты закрываются быстрее, дозы подбираются точнее, а первая ровная ночь наступает предсказуемо. В любом сценарии анонимность неизменна: закрытые каналы связи, визиты без маркировки, приёмы без пересечений с другими пациентами.
Узнать больше – narkologicheskaya-klinika-v-lyubercah
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Получить дополнительную информацию – http://narkologicheskaya-klinika-lyubercy9.ru/narkologicheskaya-klinika-otzyvy-v-lyubercah/
Такая карта делает лечение обозримым и дисциплинирует решения: пациент видит цель и порог перехода, семья понимает, зачем нужно соблюдать «тихие» часы, команда сохраняет управляемость и не «крутит ручки» ночью.
Узнать больше – частная наркологическая клиника в петрозаводске
Мы сознательно фиксируем не только «медицинские» параметры, но и бытовые маркеры: сколько воды выпито, как переносится тёплая пища малыми порциями, какой свет в комнате перед сном. Эти детали активно упоминаются в клинических рекомендациях, потому что нередко именно они решают исход первой ночи лучше, чем попытка «усилить» таблеткой.
Разобраться лучше – https://narkologicheskaya-klinika-stavropol15.ru/narkolog-stavropol
Первые часы определяют траекторию. Мы работаем по карте — у каждого окна есть цель, действия, маркеры контроля и критерий перехода. Если ответ «плоский», меняем один элемент и назначаем повторную оценку. Это дисциплинирует решения и защищает от полипрагмазии.
Изучить вопрос глубже – вывод из запоя вызов в петрозаводске
Стационарные и амбулаторные блоки клиники работают как единый маршрут. Мы начинаем с короткого «языка фактов»: сколько минут до засыпания, сколько пробуждений ночью, какой объём воды переносится малыми глотками, как меняется пульс в сумерки. Эти маркеры дополняют витальные показатели и помогают точнее выбирать инфузионные модули, контролировать темп и вовремя «облегчать» схему, не теряя устойчивости. Параллельно мы внедряем поведенческие опоры — тёплую подсветку, дыхательный паттерн 4–6, «цифровую тишину», дробное тёплое питание — они уменьшают потребность в ночных «усилениях» и повышают переносимость лечения.
Детальнее – https://narkologicheskaya-klinika-petrozavodsk15.ru/narkolog-petrozavodsk-otzyvy/
Вывод из запоя — это управляемая медицинская процедура с предсказуемыми шагами, а не «сильная капельница, которая помогает всем». В наркологической клинике «СеверКар Медикус» мы строим лечение как маршрут: цель > инструмент > маркеры контроля > окно повторной оценки. Такой подход снижает лекарственную нагрузку, ускоряет восстановление сна и аппетита и делает процесс понятным пациенту и семье. Мы работаем круглосуточно, организуем выезд нарколога на дом, разворачиваем тихую, безопасную среду и соблюдаем анонимность: нейтральные формулировки, гражданская одежда специалистов, немаркированный транспорт и «беззвучные» уведомления.
Подробнее – вывод из запоя на дому цена в петрозаводске
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Выяснить больше – анонимный вывод из запоя в петрозаводске
Первый контакт строится вокруг фактов «здесь и сейчас». Врач уточняет длительность употребления, принятые за последние 24–48 часов препараты, сопутствующие диагнозы и аллергии, фиксирует давление, пульс, сатурацию, температуру, оценивает выраженность тремора и уровень тревоги; при необходимости выполняется экспресс-ЭКГ и элементарный неврологический скрининг. Далее план объясняется простым языком: какие инфузии будут сегодня, чего ждать через 30–60 минут, как организовать вечер и когда состоится контрольная связь. Мы избегаем универсальных «сильных смесей» и «оглушающих» дозировок: они дают краткий «блеск» с вечерним откатом и повышают риск побочных эффектов. Вместо этого используется узкая, клинически достаточная схема: регидратация для восстановления объёма циркулирующей жидкости, коррекция электролитов, печёночная поддержка, противорвотные и гастропротекция при необходимости, мягкая анксиолитическая коррекция по показаниям. После процедуры врач повторно оценивает показатели, оставляет письменные рекомендации на 48–72 часа, согласует окно связи и обозначает «красные флажки» для немедленного контакта. Такой прозрачный маршрут убирает импровизации и делает поведение семьи предсказуемым, что особенно важно в «тёмные часы» вечера.
Подробнее можно узнать тут – вывод из запоя с выездом
Мы собираем терапию из проверенных модулей: гидратация, коррекция электролитов, гастропротекция, антиоксидантная поддержка, мягкая анксиолитика по показаниям, поведенческие интервенции (свет, тишина, дыхание 4–6, стимул-контроль, вечерние ритуалы). Объём и темп зависят от ведущего симптома и времени суток: при кардиореактивном вечере больше внимания уделяется среде, при тошноте — гастропротекции и «тёплому питанию», при поверхностном сне — цифровой гигиене и световым сценариям. Ниже приведена ориентировочная матрица выбора; финальное решение — за лечащим врачом с учётом противопоказаний и лекарственных взаимодействий.
Детальнее – http://www.domen.ru
Мурманск — город с длинными сумерками и влажным ветром от Кольского залива, что сказывается на сну и вечерней кардиолабильности. Поэтому мы адаптируем маршруты: выездные бригады работают в гражданской одежде, заходят быстро и тихо, а в палатах клиники используется тёплая подсветка и акустическое поглощение. Для ночных поступлений действует протокол «мягкой посадки»: минимизированные контакты, тёплая вода малыми глотками, затем — диагностика и старт инфузии при отсутствии «красных флагов». Это снижает сенсорную нагрузку и позволяет организму дать честный клинический ответ без лишних раздражителей.
Узнать больше – капельница от запоя
Мытищи дают плюсы домашнего формата: меньше логистики, приватнее, выше приверженность режиму. Если показатели устойчивы и нет признаков угрозы осложнений (упорной рвоты, высокой температуры, выраженной дезориентации, резких «качелей» АД/пульса, риска судорог), старт на дому или амбулаторно — рациональное решение. Но когда состояние «по краю», честнее и на дистанции дешевле сутки–двое стационара под круглосуточным наблюдением: проще дозировать препараты, вовремя закрывать дефициты, добиться первого ровного сна и не «разбрасываться» экстренными ночными выездами. Формат выбирается не «по желанию», а по безопасности здесь и сейчас; при этом конфиденциальность сохранена в любом сценарии — немаркированные визиты, разнесённые приёмы, доступ к данным по ролям.
Ознакомиться с деталями – chastnaya-narkologicheskaya-klinika
Инфузионная терапия — это не универсальный «коктейль», а набор узких шагов под клиническую задачу. Главные цели понятны: вернуть объём циркулирующей жидкости и перфузию тканей, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревожность, подготовить нервную систему к сну. При тошноте подключаются противорвотные и гастропротекция; кардиокоррекция даётся только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и «красные флажки» для связи. Такой минимум достаточных вмешательств снижает побочные эффекты, делает бюджет предсказуемым и удерживает результат не часами, а днями. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Подробнее тут – kruglosutochnaya-narkologicheskaya-klinika
Мы никогда не «лечим по заголовку». На старте фиксируем витальные показатели, собираем лекарственную историю и оцениваем факторы среды — график работы, «шум» дома, уровень физической активности, качество ночи. Параллельно обсуждаем, что для человека важнее сейчас: быстро «снять волну» симптомов, мягко перестроить вечерние привычки, настроить семейные договорённости или объединить всё это в короткий интенсивный период. Пациент получает не набор процедур, а маршрут: цель каждого шага, окно оценки эффекта, признаки успеха и заранее оговорённые условия для эскалации наблюдения.
Выяснить больше – https://narkologicheskaya-klinika-stavropol15.ru/chastnaya-narkologicheskaya-klinika-stavropol
Наркологическая клиника «РеМед Карелия» — это круглосуточная медицинская помощь, построенная на принципе клинической точности: каждая процедура имеет цель, проверяемые маркеры и назначенное окно переоценки. Мы используем современные методы детоксикации и постабстинентной стабилизации, не перегружая терапию «на всякий случай» и не полагаясь на универсальные «сильные капельницы». Вместо этого — модульные схемы, корректировка одного параметра за раз и обязательная оценка результата. Такой подход снижает фармаконагрузку, ускоряет восстановление сна и аппетита и делает лечение предсказуемым для пациента и его семьи. Анонимность встроена в процессы: немаркированные входы, гражданская форма персонала, нейтральные формулировки в документах, «тихие» уведомления и разграниченный доступ к карте наблюдения.
Подробнее тут – https://narkologicheskaya-klinika-v-petrozavodske15.ru/petrozavodsk-narkologiya
Городская среда Калининграда — контрастные подъезды, близость моря с переменчивым ветром, плотный сезонный трафик — может усиливать вечернюю реактивность. Поэтому маршруты организованы «тихо»: согласованная парковка, отдельный вход без вывесок и очередей, короткая регистрация, приглушённая тёплая подсветка в зоне ожидания, отсутствие громких объявлений. Коммуникация с пациентами и близкими строится через защищённые каналы, а уведомления приходят в «беззвучном» режиме в согласованные «окна». Такой дизайн не ради «красоты сервиса», а ради клинического эффекта: чем меньше сенсорной нагрузки, тем быстрее выравнивается пульс к вечеру, тем легче возвращается переносимость питья и тёплой пищи, тем меньше потребность в ночных «усилениях».
Получить больше информации – наркологическая клиника стационар калининград
В крупных и динамичных районах Ставрополя дорога сама по себе становится стрессором: непривычные запахи, чужие люди, ожидание в коридоре — всё это усиливает тремор, реактивность пульса и «ночной разгон» мыслей. Именно поэтому «СтаврМедЦентр» предлагает аккуратный выбор: если объективные риски низкие, мы начинаем дома или амбулаторно и переносим часть «тяжёлых» решений в первый вечер. Там проще включить светогигиену, отрегулировать шум, наладить воду и положить рядом тёплую лёгкую пищу. Когда среда управляемая, меньше соблазн «усилить» схему лишними препаратами, и организм быстрее выходит на коридоры безопасности.
Получить дополнительную информацию – наркологическая клиника вывод из запоя
Наводится порядок в информации, запускается инфузия по показаниям, объясняются ожидаемые ощущения и правила вечера. Пациент и близкие понимают, какой результат реалистичен к ночи и что делать, чтобы эффект не «сгорел» к полуночи.
Исследовать вопрос подробнее – анонимная наркологическая клиника
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Получить дополнительную информацию – вывод из запоя в стационаре
Если при первичном звонке фиксируем «красные флаги» (угнетение сознания, выраженная одышка, резкое падение SpO?, нестабильная аритмия), сразу предлагаем стационарное наблюдение с ночным постом. При низких рисках начинаем дома, но держим низкий порог для эскалации, чтобы не терять время, если состояние меняется.
Выяснить больше – нарколог на дом круглосуточно цены ставрополь
Мытищи дают плюсы домашнего формата: меньше логистики, приватнее, выше приверженность режиму. Если показатели устойчивы и нет признаков угрозы осложнений (упорной рвоты, высокой температуры, выраженной дезориентации, резких «качелей» АД/пульса, риска судорог), старт на дому или амбулаторно — рациональное решение. Но когда состояние «по краю», честнее и на дистанции дешевле сутки–двое стационара под круглосуточным наблюдением: проще дозировать препараты, вовремя закрывать дефициты, добиться первого ровного сна и не «разбрасываться» экстренными ночными выездами. Формат выбирается не «по желанию», а по безопасности здесь и сейчас; при этом конфиденциальность сохранена в любом сценарии — немаркированные визиты, разнесённые приёмы, доступ к данным по ролям.
Получить больше информации – http://narkologicheskaya-klinika-mytishchi9.ru
Городская среда Калининграда специфична: морской ветер, сезонные пробки, яркие витрины в вечерние часы. Эти факторы часто усиливают тревожность и мешают засыпанию. Поэтому мы проектируем выезд «мягко»: согласованная парковка, немаркированный вход, короткий маршрут до места процедуры, отсутствие громких звонков и «визуального шума» у порога. Родственникам предоставляем «тихие окна» связи — короткие апдейты в заранее оговорённое время без лишних подробностей. Такой формат не просто комфортнее, он клинически полезен: чем меньше стимулов, тем меньше потребность в ночных «усилениях» и тем стабильнее проходит первая ночь.
Подробнее тут – вывод из запоя на дому калининград
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Узнать больше – вывод из запоя с выездом в калининграде
Если при первичном звонке выявляются «красные флаги» — неукротимая рвота, одышка, спутанность, «скачущий» ритм, подозрение на травму — мы немедленно резервируем палату усиленного наблюдения. При низком риске стартуем амбулаторно или на дому с бесшовным переводом в стационар, если динамика меняется. В любом случае цель одна: безопасно стабилизировать состояние, вернуть питьё и физиологичный сон, объяснить семье и пациенту короткий «язык фактов», по которому судим об эффективности.
Узнать больше – https://narkologicheskaya-klinika-v-petrozavodske15.ru/
Мы не составляем «супер-смеси» «на всякий случай». Капельница — это набор модулей, каждый из которых отвечает за конкретную задачу: гидратация, электролиты, гастропротекция, антиоксидантная поддержка; при показаниях — мягкая анксиолитика. Порядок модулей зависит от ведущего симптом-кластера и времени суток.
Узнать больше – капельница от запоя стоимость в мурманске
Детокс — это не «чудо-капельница», а последовательность узких вмешательств. Цели понятны: восстановить объём циркулирующей жидкости, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревогу, подготовить нервную систему к сну. При тошноте подключается противорвотная поддержка и гастропротекция, витаминные комплексы — по показаниям, кардиокоррекция — только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и маркеры для немедленной связи. Такой реализм снижает импульсивность и делает результат измеримым: вечером — не «откат», а предсказуемая усталость, ночью — ровный сон, утром — стабильные показатели. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Получить дополнительную информацию – http://narkologicheskaya-klinika-mytishchi9.ru
Снижается тремор, уменьшается тошнота, пульс и давление перестают «скакать», появляется возможность уснуть без паники. Важно не перегружать этот эффект разговорами «по душам», яркими экранами и проверками «на прочность»: когда среда тихая и затемнённая, организм закрепляет улучшение, а не теряет его к полуночи.
Углубиться в тему – pomoshch-vyvod-iz-zapoya
Техника помогает, но не доминирует. Мы используем портативные приборы с мягкой индикацией и низким уровнем шума, чтобы не разрушать формирующуюся «ночную кривую». Контроль в остром окне чаще, вечером — мягче: так сохраняется физиология сна и снижается потребность в дополнительной фармакологии.
Подробнее – https://narkologicheskaya-klinika-petrozavodsk15.ru/petrozavodsk-narkologiya
Мы никогда не «лечим по заголовку». На старте фиксируем витальные показатели, собираем лекарственную историю и оцениваем факторы среды — график работы, «шум» дома, уровень физической активности, качество ночи. Параллельно обсуждаем, что для человека важнее сейчас: быстро «снять волну» симптомов, мягко перестроить вечерние привычки, настроить семейные договорённости или объединить всё это в короткий интенсивный период. Пациент получает не набор процедур, а маршрут: цель каждого шага, окно оценки эффекта, признаки успеха и заранее оговорённые условия для эскалации наблюдения.
Получить дополнительную информацию – наркологическая клиника наркологический центр ставрополь
Наркологическая клиника «РеМед Карелия» — это круглосуточная медицинская помощь, построенная на принципе клинической точности: каждая процедура имеет цель, проверяемые маркеры и назначенное окно переоценки. Мы используем современные методы детоксикации и постабстинентной стабилизации, не перегружая терапию «на всякий случай» и не полагаясь на универсальные «сильные капельницы». Вместо этого — модульные схемы, корректировка одного параметра за раз и обязательная оценка результата. Такой подход снижает фармаконагрузку, ускоряет восстановление сна и аппетита и делает лечение предсказуемым для пациента и его семьи. Анонимность встроена в процессы: немаркированные входы, гражданская форма персонала, нейтральные формулировки в документах, «тихие» уведомления и разграниченный доступ к карте наблюдения.
Выяснить больше – http://narkologicheskaya-klinika-v-petrozavodske15.ru
Мы собираем терапию из проверенных модулей: гидратация, коррекция электролитов, гастропротекция, антиоксидантная поддержка, мягкая анксиолитика по показаниям, поведенческие интервенции (свет, тишина, дыхание 4–6, стимул-контроль, вечерние ритуалы). Объём и темп зависят от ведущего симптома и времени суток: при кардиореактивном вечере больше внимания уделяется среде, при тошноте — гастропротекции и «тёплому питанию», при поверхностном сне — цифровой гигиене и световым сценариям. Ниже приведена ориентировочная матрица выбора; финальное решение — за лечащим врачом с учётом противопоказаний и лекарственных взаимодействий.
Ознакомиться с деталями – [url=https://narkologicheskaya-klinika-v-petrozavodske15.ru/]лечение в наркологической клинике в петрозаводске[/url]
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Разобраться лучше – https://narkologicheskaya-klinika-v-kaliningrade15.ru/klinika-vyvod-iz-zapoya-kaliningrad/
Мы никогда не «лечим по заголовку». На старте фиксируем витальные показатели, собираем лекарственную историю и оцениваем факторы среды — график работы, «шум» дома, уровень физической активности, качество ночи. Параллельно обсуждаем, что для человека важнее сейчас: быстро «снять волну» симптомов, мягко перестроить вечерние привычки, настроить семейные договорённости или объединить всё это в короткий интенсивный период. Пациент получает не набор процедур, а маршрут: цель каждого шага, окно оценки эффекта, признаки успеха и заранее оговорённые условия для эскалации наблюдения.
Детальнее – http://narkologicheskaya-klinika-stavropol15.ru/chastnaya-narkologicheskaya-klinika-stavropol/
Стартовый осмотр должен быть быстрым и осмысленным. Мы исключаем «обязательные» исследования, которые не меняют тактику, и оставляем то, что прямо влияет на состав инфузии, темп, место ведения (дом/амбулатория/стационар) и объём поведенческих рекомендаций. Решения принимаются на свежих цифрах и клинической картине «здесь и сейчас», а повторные замеры назначаются не «по привычке», а по смыслу. Это экономит силы пациента и время команды, а главное — уменьшает фармакологическую нагрузку без потери безопасности.
Подробнее можно узнать тут – наркологическая клиника клиника помощь
Все шаги фиксируются в карте наблюдения. Если динамика «плоская», меняется один параметр (скорость/объём/последовательность), и через оговорённое окно проводится повторная оценка. Это снижает риск побочных реакций и сохраняет дневную ясность.
Получить дополнительные сведения – вывод из запоя недорого калининград
Детокс — это не «чудо-капельница», а последовательность узких вмешательств. Цели понятны: восстановить объём циркулирующей жидкости, скорректировать электролиты, снизить токсическую нагрузку на печень, мягко приглушить тремор и тревогу, подготовить нервную систему к сну. При тошноте подключается противорвотная поддержка и гастропротекция, витаминные комплексы — по показаниям, кардиокоррекция — только после оценки рисков. Мы заранее проговариваем нормальные ощущения (умеренная слабость, сонливость, сухость во рту) и маркеры для немедленной связи. Такой реализм снижает импульсивность и делает результат измеримым: вечером — не «откат», а предсказуемая усталость, ночью — ровный сон, утром — стабильные показатели. На этой базе обсуждаются следующие шаги: амбулаторный график, короткие психотерапевтические сессии, при показаниях — кодирование после стабилизации и исключения противопоказаний.
Получить дополнительные сведения – заказать звонок наркологическая клиника
Городская среда Петрозаводска со сменой ветров с Онежского озера, короткими сумерками и сезонными перепадами влажности может усиливать тревожность в вечерние часы. Мы учитываем это с момента первого контакта: согласованная парковка, отдельный вход без вывесок, короткая регистрация без «толстых анкет», приглушённый тёплый свет в зоне ожидания и отсутствие громких объявлений. Родственникам предоставляются «тихие окна» связи — лаконичные апдейты в фиксированное время, чтобы не перегружать пациента и не дёргать команду в критические окна наблюдения. Такой «мягкий» контур снижает сенсорную нагрузку, стабилизирует вариабельность ЧСС к сумеркам и сокращает число импульсивных просьб «усилить на ночь».
Подробнее тут – наркологическая клиника наркологический центр в петрозаводске
* Экспресс-электролиты выполняются по показаниям, если на старте есть факторы риска.
Получить дополнительную информацию – нарколог на дом срочно ставрополь
Затянувшийся запой быстро расшатывает физиологию: теряется жидкость, нарушается электролитный баланс, растёт нагрузка на сердце и печень, сон рвётся тревожными отрезками. На этом фоне любое промедление меняет картину не в лучшую сторону: чем дольше организм остаётся в состоянии интоксикации и бессонницы, тем выше риск аритмий, скачков давления, панических волн и импульсивных решений ночью. «Трезвый Город Химки» устраняет эти пружины сразу: вместо очередей и разговоров «на виду» — быстрый вход по согласованному времени, предметное интервью без лишней бюрократии, чёткое объяснение каждого шага и старт терапии в минимально достаточном объёме. Такой подход экономит силы семьи, снижает тревогу у пациента и делает результат предсказуемым: уже в первые часы уменьшаются тремор и тошнота, выравнивается пульс, появляется чувство контроля. Ключевая цель на первые сутки — первая ровная ночь, потому что только на её фоне организм способен закреплять улучшения, а не «сжигать» их к вечеру. Мы заранее договариваемся о правилах вечера, чтобы не ломать эффект разговорами и яркими экранами, и именно поэтому траектория восстановления идёт не рывками, а поступательно.
Изучить вопрос глубже – http://vyvod-iz-zapoya-himki9.ru/vyvod-iz-zapoya-v-stacionare-v-himkah/
При домашнем формате мы сразу закладываем «мостик» к стационару: в случае ухудшения состояния перевод происходит бесшовно, по заранее оговорённым критериям. Пациент и семья знают, какие маркеры считаются целевыми (переносимость воды, ровный вечерний пульс, время до засыпания, число пробуждений), и когда состоится повторная оценка. Прозрачность снимает суету и укрепляет приверженность плану.
Детальнее – капельница от запоя на дому круглосуточно в мурманске
Снижается тремор, уменьшается тошнота, пульс и давление перестают «скакать», появляется возможность уснуть без паники. Важно не перегружать этот эффект разговорами «по душам», яркими экранами и проверками «на прочность»: когда среда тихая и затемнённая, организм закрепляет улучшение, а не теряет его к полуночи.
Выяснить больше – вывод из запоя на дому цена
Ниже — практическая карта первых часов. Она помогает всем участникам понимать логику действий, точки контроля и критерии перехода. Если ответ «плоский», меняем один параметр и возвращаемся к оценке в назначённое время — без хаотичных «усилений».
Получить дополнительную информацию – https://kapelnicza-ot-zapoya-murmansk15.ru/vyjti-iz-zapoya-murmansk/
Мы вместе составляем карту триггеров («тёмные часы» вечера, недосып, конфликты, привычные маршруты) и набор «буферов» на 20–40 минут: тёплый душ, короткая прогулка у дома, дыхательная практика, нейтральный созвон с «своим» человеком. Эти бесплатные шаги уменьшают внеплановые затраты и добавляют устойчивости.
Подробнее тут – narkologicheskaya-klinika-obratnyj-zvonok
Мытищи дают плюсы домашнего формата: меньше логистики, приватнее, выше приверженность режиму. Если показатели устойчивы и нет признаков угрозы осложнений (упорной рвоты, высокой температуры, выраженной дезориентации, резких «качелей» АД/пульса, риска судорог), старт на дому или амбулаторно — рациональное решение. Но когда состояние «по краю», честнее и на дистанции дешевле сутки–двое стационара под круглосуточным наблюдением: проще дозировать препараты, вовремя закрывать дефициты, добиться первого ровного сна и не «разбрасываться» экстренными ночными выездами. Формат выбирается не «по желанию», а по безопасности здесь и сейчас; при этом конфиденциальность сохранена в любом сценарии — немаркированные визиты, разнесённые приёмы, доступ к данным по ролям.
Получить дополнительные сведения – http://narkologicheskaya-klinika-mytishchi9.ru/narkologicheskaya-klinika-stacionar-v-mytishchah/
Экстренный вывод из запоя на дому — это управляемая медицинская последовательность, а не «сильная капельница на удачу». В наркологической клинике «КалининградМедПрофи» мы выстраиваем помощь вокруг трёх опор: безопасность, конфиденциальность и предсказуемый результат. Выездная бригада приезжает круглосуточно, работает в гражданской одежде и без опознавательных знаков, чтобы не привлекать внимания соседей. Каждое вмешательство имеет измеримую цель, окно проверки и прозрачный критерий перехода к следующему шагу. Благодаря этому темп лечения остаётся мягким, а динамика — понятной для пациента и близких.
Узнать больше – нарколог вывод из запоя в калининграде
Если на телефонном этапе выявляются «красные флаги» — спутанность, выраженная одышка, «скачущий» ритм, неукротимая рвота, — мы рекомендуем короткое окно стационарного наблюдения. При низком риске целесообразно начать дома: привычная среда снижает сенсорную нагрузку, а телемедицинские включения вечером по 15–20 минут помогают пройти «трудный час» без поездок.
Детальнее – https://vyvod-iz-zapoya-kaliningrad15.ru/skoraya-narkologiya-vyvod-iz-zapoya-kaliningrad-uslugi/
Этот текст содержит различную информацию, которая, возможно, покажется любопытной, но в целом не меняет восприятия привычных вещей. Предлагаем просто получить удовольствие от чтения, не ожидая особой пользы.
Вот – besproigryshnyj
помощь в написании курсовой https://kupit-kursovuyu-22.ru .
Домашний формат уместен, когда симптоматика контролируема и вечером рядом может остаться взрослый помощник. Преимущество Лобни — короткие дистанции внутри города, поэтому врач приезжает быстро, без шума и эмблем. На месте мы не торопимся: собеседование по факту последних 48 часов, измерения давления, пульса, сатурации и температуры, короткий неврологический скрининг, сверка аллергий и уже принятых препаратов. После допуска к терапии запускается инфузия: сначала — коррекция воды и электролитов, затем — поддержка печени и ЦНС, при необходимости — противорвотные и анксиолитические препараты. Темп настраивается по динамике, чтобы снять тремор и тошноту без «перекручивания» организма в сон с тяжёлым просыпанием. По итогам визита — понятные правила на 24–48 часов, список тревожных признаков и согласованное окно контрольного контакта. Домашний маршрут экономит часы, снижает социальную тревогу и делает первые сутки предсказуемыми.
Получить больше информации – вывод из запоя
Стационар уместен при тяжёлой абстиненции, скачках давления, угрозе делирия, эпизодах судорог, неукротимой рвоте, а также когда дома нет взрослого помощника на ночь. В палате — аппаратный контроль по показаниям, пост медсестёр 24/7, ЭКГ и базовая лаборатория, регулярные переоценки с корректировкой схемы. Решения принимаются быстро, без логистических задержек; это снижает риск поздних осложнений и повторных экстренных вызовов.
Подробнее – обратиться в наркологическую клинику
Цель
Получить дополнительную информацию – http://narkolog-na-dom-voskresensk8.ru
Домашний формат выбирают, когда обстановка позволяет провести лечение в тишине и нет признаков угрозы жизни. Врач приезжает без опознавательных знаков, начинает с очной оценки и допуска к инфузии, сверяет принятые ранее препараты и аллергии, объясняет ожидаемую динамику. После запуска капельницы мягко корректируются жидкость и электролиты, проводится симптом-контроль (тремор, тошнота, тревога, головная боль), по показаниям — осторожная нормализация сна. На выходе пациент и семья получают понятные рекомендации на 24–48 часов: питьевой режим, питание, ограничения по нагрузкам, признаки тревоги и правила связи с дежурным врачом.
Исследовать вопрос подробнее – domashnij-vyvod-iz-zapoya
азино 777 официальный сайт версия зеркало Азино 777 – это не просто казино, это место, где каждый может испытать свою удачу и получить незабываемые эмоции. Благодаря официальному сайту и надежным зеркалам, вы всегда будете иметь доступ к любимым играм и сможете воспользоваться всеми преимуществами щедрых бонусов. Начните свое приключение в мире азарта уже сегодня!
Инфузионная терапия — это не просто «быстрый раствор витаминов». При запое страдает водно-электролитный баланс, «плавает» давление и пульс, нарастает тревога, нарушается сон, проявляются тошнота и тремор. Правильно собранная капельница в Клину помогает вернуть жидкость и электролиты, поддержать печень, снизить вегетативные проявления, мягко стабилизировать нервную систему и подготовить переход на пероральные схемы. Важно избегать избыточной седативной нагрузки и опасных сочетаний: то, что человеку «помогало раньше», может конфликтовать с его нынешними показателями. Поэтому каждое назначение мы увязываем с реальными цифрами осмотра и тем, что уже было принято за двое суток.
Подробнее тут – kapelnica-ot-zapoya
Стационар — это управляемая среда, где меньше случайностей и больше возможностей действовать на опережение. Под одной крышей — приём и допуск к терапии, инфузионный блок, аппаратный контроль, лаборатория и ЭКГ по показаниям, пост медсестёр и регулярная переоценка состояния. Такой контур особенно важен при давних запойных эпизодах, гипертонии, ишемической болезни сердца, сахарном диабете, гастроэнтерологических проблемах: правильно настроенный темп инфузий и «бережные» назначения уменьшают риск осложнений и снимают «эффект качелей» в первые сутки.
Получить дополнительные сведения – наркологическая клиника справка
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Получить дополнительную информацию – https://vyvod-iz-zapoya-moskva8.ru/vyvod-iz-zapoya-na-domu-v-moskve
Этот текст содержит различную информацию, которая, возможно, покажется любопытной, но в целом не меняет восприятия привычных вещей. Предлагаем просто получить удовольствие от чтения, не ожидая особой пользы.
Вот – yed
By using stamp maker online you do not need to visit the office to order the necessary stamps.
With the advent of technology, the process of making rubber stamps has become easier and more accessible than ever before . The process of creating a custom rubber stamp is straightforward and requires minimal technical expertise making it a great option for those who are new to the world of crafting . offering a cost-effective solution for small businesses and individuals who want to create custom stamps .
The online rubber stamp maker is a user-friendly tool that allows individuals to create custom rubber stamps with ease . One of the key benefits of using an online rubber stamp maker is the speed and convenience it offers . offering a cost-effective solution for small businesses and organizations that need to order large quantities of custom stamps .
providing a user-friendly interface and a range of customization options . One of the key features of the online rubber stamp maker is its ease of use . allowing users to choose from a variety of fonts, colors, and designs . making it a great option for individuals and small businesses who want to create high-quality custom rubber stamps.
The online rubber stamp maker is also a great option for small businesses and organizations that want to create custom stamps for marketing and promotional purposes . including address stamps, logo stamps, and signature stamps . In conclusion, the online rubber stamp maker is a revolutionary tool that has made it possible for individuals to create their own custom rubber stamps from the comfort of their homes .
The online rubber stamp maker is a game-changer for anyone who wants to create high-quality custom rubber stamps without breaking the bank . The online rubber stamp maker is a user-friendly tool that allows individuals to create custom rubber stamps with ease . including fast turnaround times and competitive pricing . Overall, the online rubber stamp maker is a versatile tool that can be used to create a wide range of custom stamps .
гидроизоляция цена за м2 за работу gidroizolyacziya-czena1.ru .
«ВитаСана» — это организованный маршрут наркологической помощи в Чехове: быстрый анонимный звонок, выезд врача на дом без опознавательных знаков, аккуратный детокс с капельницами, стационар с круглосуточным наблюдением и подготовка к кодированию по показаниям. Мы действуем спокойно и последовательно: сначала очная оценка и допуск к терапии, затем индивидуальная инфузионная поддержка, далее — понятный план «тихих» дней и контрольный контакт. Каждое назначение объясняем простыми словами, смету согласуем до начала процедур, конфиденциальность соблюдаем на каждом шаге.
Детальнее – http://
аренда экскаватора в москве цена аренда экскаватора в москве цена .
Мы не используем шаблон «на всех». Темп и сочетания зависят от давления, пульса, выраженности тошноты и тремора, уровня тревоги, сопутствующих диагнозов и лекарств, уже попавших в организм. Детокс — это система шагов: допуск к терапии, коррекция воды и электролитов, поддержка печени, вегетостабилизация, осторожная работа со сном по показаниям, профилактика осложнений. Любое назначение проговаривается простым языком: зачем, как подействует, что считать нормальной динамикой, а что — поводом связаться с врачом.
Подробнее можно узнать тут – kapelnica-ot-zapoya-telefon
акрилатная инъекционная гидроизоляция https://inekczionnaya-gidroizolyacziya.ru/ .
гидроизоляция подвала гаража гидроизоляция подвала гаража .
Домашний формат выбирают, когда обстановка позволяет провести лечение в тишине и нет признаков угрозы жизни. Врач приезжает без опознавательных знаков, начинает с очной оценки и допуска к инфузии, сверяет принятые ранее препараты и аллергии, объясняет ожидаемую динамику. После запуска капельницы мягко корректируются жидкость и электролиты, проводится симптом-контроль (тремор, тошнота, тревога, головная боль), по показаниям — осторожная нормализация сна. На выходе пациент и семья получают понятные рекомендации на 24–48 часов: питьевой режим, питание, ограничения по нагрузкам, признаки тревоги и правила связи с дежурным врачом.
Узнать больше – http://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-klinika-v-sergievom-posade/
гидроизоляция подвала влажность http://gidroizolyacziya-podvala-samara.ru/ .
ремонт бетонных конструкций антикоррозия ремонт бетонных конструкций антикоррозия .
Перед таблицей короткий переход: мы сначала исключаем несовместимости и только потом начинаем инфузии. Это защищает от скрытых конфликтов препаратов, на которые «универсальные коктейли» просто не смотрят.
Узнать больше – http://vyvod-iz-zapoya-lobnya8.ru/srochnyj-vyvod-iz-zapoya-v-lobne/
Маршрут помощи строится вокруг конкретных задач безопасности. С первого звонка администратор собирает короткий чек-лист: длительность нынешнего эпизода, что принималось в последние двое суток, хронические заболевания, аллергии, как прошла ночь, есть ли помощник на вечер и ночь. Дежурный врач, опираясь на эти данные, предлагает стартовый формат — выезд на дом по Воскресенску и району или немедленную госпитализацию. Решение привязывается к реальным рискам: стабильность давления и пульса, выраженность тремора и тошноты, эпизоды судорог в прошлом, возможность обеспечить «тихий режим» в квартире. После очной оценки и допуска к терапии мы запускаем детокс, а по завершении визита фиксируем правила на 24–48 часов и контрольные точки. Если состояние колеблется, сразу обсуждаем повторный контакт либо перевод в стационар, не теряя часы на бюрократию.
Подробнее – http://narkologicheskaya-klinika-voskresensk8.ru
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Углубиться в тему – vyzov-narkologa-na-dom-voskresensk
Мы не используем шаблон «на всех». Темп и сочетания зависят от давления, пульса, выраженности тошноты и тремора, уровня тревоги, сопутствующих диагнозов и лекарств, уже попавших в организм. Детокс — это система шагов: допуск к терапии, коррекция воды и электролитов, поддержка печени, вегетостабилизация, осторожная работа со сном по показаниям, профилактика осложнений. Любое назначение проговаривается простым языком: зачем, как подействует, что считать нормальной динамикой, а что — поводом связаться с врачом.
Подробнее – капельница от запоя в стационаре
Домашний формат — это клинически выверенная помощь без госпитализации, если обстановка безопасна и есть взрослый помощник на вечер и ночь. Врач «Трезвого Компаса» приезжает без опознавательных знаков, проводит очную оценку (АД, пульс, сатурация, температура, неврологический статус), уточняет препараты, принятые за 48 часов, и аллергии. Далее — допуск к терапии и запуск инфузии. Мы корректируем жидкость и электролиты, поддерживаем печень и ЦНС, по показаниям используем противорвотные и анксиолитические решения, избегая «перелечивания». В конце визита — переоценка, настройка темпа/состава, памятка на 24–48 часов и окно контрольного контакта.
Углубиться в тему – kapelnica-ot-zapoya-vyzov
Вывод из запоя направлен не только на снятие острых симптомов, но и на комплексное восстановление организма. Работа специалистов позволяет стабилизировать состояние и создать условия для дальнейшего лечения зависимости.
Подробнее тут – вывод из запоя клиника в твери
Детокс — это не один раз «поставить капельницу», а последовательность: допуск к терапии, коррекция жидкости и электролитов, поддержка органов-мишеней, симптом-контроль, профилактика осложнений, переоценка и настройка схемы. Мы заранее закладываем точку повторной оценки, потому что абстинентные проявления изменчивы: тремор и тревога могут уходить волнообразно, давление — «гулять» на фоне усталости и недосыпа. Врач видит динамику и либо переводит на пероральные схемы, либо усиливает наблюдение, рекомендуя стационар. Параллельно настраиваем «бытовой контур» — сон по расписанию, вода малыми порциями, лёгкое дробное питание, ограничение эмоциональных перегрузок и перенос встреч, где сложно отказать.
Разобраться лучше – воскресенская клиника
Домашний формат уместен, когда нет признаков угрозы жизни, а дома можно сохранить тишину и наблюдение ночью. Врач приезжает без опознавательных знаков, начинает с очной оценки рисков и сверки уже принятых препаратов, объясняет ожидаемую динамику и запускает инфузионную терапию. Мы мягко корректируем водно-электролитный баланс, даём поддержку печени и вегетативной нервной системе, по показаниям осторожно нормализуем сон. На руки выдаём памятку на ближайшие сутки-двое: питьевой режим, питание, алгоритм отхода ко сну, признаки тревоги, порядок связи с дежурным врачом. Такой визит «гасит» острые проявления и возвращает предсказуемость ночи без лишней огласки для соседей.
Получить дополнительные сведения – https://narkologicheskaya-klinika-voskresensk8.ru/
Домашний формат удобен, если нет признаков угрозы жизни и дома можно обеспечить спокойную обстановку. Врач приезжает без опознавательных знаков, начинает с очной оценки рисков и допуска к инфузионной терапии, сверяет принятые ранее препараты и аллергии, объясняет план действий и ожидаемую динамику. Далее запускается капельница: мягкая коррекция жидкости и электролитов, поддержка печени, симптом-контроль тревоги, тошноты, головной боли и тремора. На руки выдаются понятные рекомендации на 24–48 часов: питьевой режим, питание, сон, признаки тревоги и алгоритм связи с дежурным врачом.
Подробнее тут – vyvod-iz-zapoya-besplatno
Честная наркология — это не «универсальная капельница», а система шагов, привязанная к параметрам конкретного человека. В Чехове мы выезжаем круглосуточно, на месте проводим допуск к терапии, сверяем совместимости с уже принятыми препаратами, подбираем состав инфузий без лишних компонентов и избыточной седативной нагрузки. Если дома нет условий для безопасной ночи, предложим стационар — это не усложнение, а короткий путь к безопасности. Анонимность — стандарт: нейтральные формулировки в документах по запросу, ограниченный доступ к данным, деликатная связь.
Выяснить больше – http://
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Подробнее – http://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-anonimno-v-sergievom-posade/
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Детальнее – vyvod-iz-zapoya-moskva-vyzov-narkologa-kapelnica
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Ознакомиться с деталями – vyvod-iz-zapoya-v-moskve-nedorogo
Домашний формат — это клинически выверенная помощь без госпитализации, если обстановка безопасна и есть взрослый помощник на вечер и ночь. Врач «Трезвого Компаса» приезжает без опознавательных знаков, проводит очную оценку (АД, пульс, сатурация, температура, неврологический статус), уточняет препараты, принятые за 48 часов, и аллергии. Далее — допуск к терапии и запуск инфузии. Мы корректируем жидкость и электролиты, поддерживаем печень и ЦНС, по показаниям используем противорвотные и анксиолитические решения, избегая «перелечивания». В конце визита — переоценка, настройка темпа/состава, памятка на 24–48 часов и окно контрольного контакта.
Разобраться лучше – https://kapelnica-ot-zapoya-klin8.ru/kapelnica-ot-zapoya-na-domu-v-klinu/
Ниже — сводный ориентир по этапам. Это не жёсткий график, а понятная канва процесса, которую врач адаптирует под клиническую картину.
Углубиться в тему – наркологический диспансер воскресенск
Мы не используем шаблон «на всех». Темп и сочетания зависят от давления, пульса, выраженности тошноты и тремора, уровня тревоги, сопутствующих диагнозов и лекарств, уже попавших в организм. Детокс — это система шагов: допуск к терапии, коррекция воды и электролитов, поддержка печени, вегетостабилизация, осторожная работа со сном по показаниям, профилактика осложнений. Любое назначение проговаривается простым языком: зачем, как подействует, что считать нормальной динамикой, а что — поводом связаться с врачом.
Изучить вопрос глубже – капельница от запоя состав
Перед таблицей короткий переход: мы сначала исключаем несовместимости и только потом начинаем инфузии. Это защищает от скрытых конфликтов препаратов, на которые «универсальные коктейли» просто не смотрят.
Получить дополнительную информацию – платная клиника вывод из запоя
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Ознакомиться с деталями – вывод из запоя в петрозаводске
Иногда домашний маршрут лишь создаёт иллюзию экономии времени. Если есть спутанность сознания, выраженная дезориентация, галлюцинации, повторные судороги, нестабильное давление, сильная одышка или неукротимая рвота с обезвоживанием, безопаснее начинать в стационаре. Там рядом диагностика и пост 24/7, любое решение принимается сразу, а коррекция схемы не упирается в бытовые ограничения квартиры.
Углубиться в тему – https://narkologicheskaya-klinika-voskresensk8.ru/telefon-narkologicheskoj-klinikia-v-voskresenske
Маршрут помощи строится вокруг конкретных задач безопасности. С первого звонка администратор собирает короткий чек-лист: длительность нынешнего эпизода, что принималось в последние двое суток, хронические заболевания, аллергии, как прошла ночь, есть ли помощник на вечер и ночь. Дежурный врач, опираясь на эти данные, предлагает стартовый формат — выезд на дом по Воскресенску и району или немедленную госпитализацию. Решение привязывается к реальным рискам: стабильность давления и пульса, выраженность тремора и тошноты, эпизоды судорог в прошлом, возможность обеспечить «тихий режим» в квартире. После очной оценки и допуска к терапии мы запускаем детокс, а по завершении визита фиксируем правила на 24–48 часов и контрольные точки. Если состояние колеблется, сразу обсуждаем повторный контакт либо перевод в стационар, не теряя часы на бюрократию.
Углубиться в тему – http://narkologicheskaya-klinika-voskresensk8.ru/
гидроизоляция цена за рулон гидроизоляция цена за рулон .
акрилатная инъекционная гидроизоляция inekczionnaya-gidroizolyacziya.ru .
Такая схема позволяет последовательно и безопасно восстановить силы организма и стабилизировать психическое состояние пациента.
Исследовать вопрос подробнее – вывод из запоя дешево
гидроизоляция подвала гаража гидроизоляция подвала гаража .
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Подробнее тут – вывод из запоя в москве в стационаре
Перед тем как перечислить основные поводы для экстренного вызова, отметим: даже один из пунктов — уже основание не откладывать помощь.
Разобраться лучше – [url=https://vyvod-iz-zapoya-moskva8.ru/]klinika-vyvod-iz-zapoya-moskva[/url]
Первые часы определяют траекторию. Мы работаем по карте — у каждого окна есть цель, действия, маркеры контроля и критерий перехода. Если ответ «плоский», меняем один элемент и назначаем повторную оценку. Это дисциплинирует решения и защищает от полипрагмазии.
Подробнее – вывод из запоя круглосуточно в петрозаводске
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Получить больше информации – вывод из запоя с выездом
Для строительных и дорожных работ можно щпс купить в москве, обеспечив качество и сроки выполнения проекта.
Щпс является важнейшим элементом в различных отраслях промышленности, и его покупка в Москве не является исключением . Для многих компаний и частных лиц покупка щпс в Москве является необходимой задачей В Москве многие компании и частные лица ищут возможность купить щпс. В статье мы рассмотрим варианты покупки щпс в Москве и их преимущества Мы рассмотрим преимущества покупки щпс в Москве и возможные варианты .
Покупка щпс в Москве может быть осуществлена через различные каналы Покупка щпс в Москве может быть осуществлена через различные каналы . Это может включать в себя официальные дилерские центры, интернет-магазины и специализированные торговые площадки В Москве щпс можно купить через официальные дилерские центры, интернет-магазины и специализированные торговые площадки. Каждый из этих вариантов имеет свои преимущества и недостатки Преимущества и недостатки каждого варианта покупки щпс в Москве необходимо учитывать .
Покупка щпс в Москве имеет ряд преимуществ Щпс купить в Москве выгодно по нескольким причинам . Одним из основных преимуществ является возможность выбрать из широкого ассортимента продукции Щпс купить в Москве можно из широкого ассортимента продукции. Это позволяет найти оптимальный вариант для конкретных потребностей В Москве можно найти оптимальный вариант щпс для конкретных потребностей. Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества В Москве щпс можно купить с гарантией качества .
Покупка щпс в Москве также может быть выгодной с экономической точки зрения В Москве покупка щпс может быть выгодной с точки зрения экономии. Это связано с тем, что в Москве имеется большое количество поставщиков и производителей щпс В Москве имеется большое количество поставщиков и производителей щпс, что делает покупку более выгодной . Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции Это конкуренция между поставщиками и производителями приводит к снижению цен и повышению качества продукции .
В Москве имеется несколько вариантов покупки щпс Щпс купить в Москве можно через несколько вариантов . Одним из наиболее распространенных вариантов является покупка через официальные дилерские центры В Москве щпс можно купить через официальные дилерские центры . Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества Эти центры предлагают широкий ассортимент продукции и предоставляют гарантию качества .
Другим вариантом покупки щпс в Москве является покупка через интернет-магазины Щпс купить в Москве можно через интернет-магазины. Этот вариант является удобным и позволяет выбрать щпс из широкого ассортимента продукции Щпс купить в Москве через интернет-магазины можно из широкого ассортимента продукции. Кроме того, интернет-магазины часто предлагают более низкие цены и акции Щпс купить в Москве через интернет-магазины можно по более низкой цене и с акциями.
В заключении, покупка щпс в Москве является выгодным и удобным вариантом В заключении, покупка щпс в Москве является выгодным и удобным вариантом . В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки В Москве имеется широкий ассортимент продукции и возможность выбрать из различных вариантов покупки . Кроме того, покупка щпс в Москве может быть осуществлена с гарантией качества и по более низкой цене В Москве щпс можно купить с гарантией качества и по более низкой цене . Мы надеемся, что эта информация будет полезной для вас при выборе варианта покупки щпс в Москве Эта информация должна быть полезной для вас при выборе варианта покупки щпс в Москве .
Вывод из запоя в Твери проводится с применением современных методик, эффективность которых подтверждена медицинской практикой. Используются только проверенные препараты и процедуры, соответствующие клиническим стандартам.
Углубиться в тему – вывод из запоя цена тверь
Стационар уместен при тяжёлой абстиненции, скачках давления, угрозе делирия, эпизодах судорог, неукротимой рвоте, а также когда дома нет взрослого помощника на ночь. В палате — аппаратный контроль по показаниям, пост медсестёр 24/7, ЭКГ и базовая лаборатория, регулярные переоценки с корректировкой схемы. Решения принимаются быстро, без логистических задержек; это снижает риск поздних осложнений и повторных экстренных вызовов.
Подробнее тут – narkologicheskij-centr-klinika
В этом обзоре представлены различные методы избавления от зависимости, включая терапевтические и психологические подходы. Мы сравниваем их эффективность и предоставляем рекомендации для тех, кто хочет вернуться к трезвой жизни. Читатели смогут найти информацию о реабилитационных центрах и поддерживающих группах.
Подробнее можно узнать тут – вывод из запоя клиника
Преимущество стационара — предсказуемость и скорость. Рядом врач и медсестра, можно оперативно сдать анализы, сделать ЭКГ или дополнительные обследования, а главное — не «тянуть» с корректировкой схемы. В контролируемой среде быстрее нормализуются сон и аппетит, уходит тремор, снижается тревога. Для пациентов с сопутствующими диагнозами это особенно важно: диабет, гипертония, аритмии, хронические заболевания ЖКТ требуют аккуратной, согласованной тактики.
Детальнее – частная наркологическая клиника москва
Сначала — очная оценка, проверка противопоказаний и совместимости с текущими лекарствами. Далее — инфузионная терапия для коррекции водно-электролитного баланса, поддержка печени и сердечно-сосудистой системы, мягкая анксиолитическая и снотворная поддержка по показаниям. Визит обычно занимает от 60 до 120 минут; при необходимости капельницы проводятся медленно, с наблюдением. После процедуры пациент получает понятные памятки: что и когда пить, когда спать, какие признаки считаются тревожными и требуют повторного осмотра или перевода в стационар.
Разобраться лучше – частная наркологическая клиника москва
Домашний формат выбирают, когда обстановка позволяет провести лечение в тишине и нет признаков угрозы жизни. Врач приезжает без опознавательных знаков, начинает с очной оценки и допуска к инфузии, сверяет принятые ранее препараты и аллергии, объясняет ожидаемую динамику. После запуска капельницы мягко корректируются жидкость и электролиты, проводится симптом-контроль (тремор, тошнота, тревога, головная боль), по показаниям — осторожная нормализация сна. На выходе пациент и семья получают понятные рекомендации на 24–48 часов: питьевой режим, питание, ограничения по нагрузкам, признаки тревоги и правила связи с дежурным врачом.
Получить больше информации – вывод человека из запоя
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Подробнее можно узнать тут – http://narkolog-na-dom-voskresensk8.ru/psihiatr-narkolog-na-dom-v-voskresenske/
Стационар уместен при тяжёлой абстиненции, скачках давления, угрозе делирия, эпизодах судорог, неукротимой рвоте, а также когда дома нет взрослого помощника на ночь. В палате — аппаратный контроль по показаниям, пост медсестёр 24/7, ЭКГ и базовая лаборатория, регулярные переоценки с корректировкой схемы. Решения принимаются быстро, без логистических задержек; это снижает риск поздних осложнений и повторных экстренных вызовов.
Получить дополнительную информацию – наркологическая клиника цены адреса
I’m not sure why but this weblog is loading very slow for me. Is anyone else having this issue or is it a issue on my end? I’ll check back later on and see if the problem still exists.
escort agencies and massage parlours in Brasilia
Петрозаводск добавляет нюансы: влажные сумерки, ветер от Онежского озера, «звонкие» подъезды старого фонда. Поэтому бригада «СеверКар Медикус» приезжает в гражданской одежде, быстро и без лишних фраз. Координатор заранее уточняет код домофона, парковку, «окна связи» для близких; рекомендует приглушить верхний свет, подготовить воду комнатной температуры и свободный доступ к розетке. Такой «тихий сценарий» снижает сенсорную нагрузку, сглаживает пульсовые «пики» к вечеру и помогает заснуть без избыточной фармакологии.
Ознакомиться с деталями – вывод из запоя цена в петрозаводске
гидроизоляция подвала снаружи цены http://www.gidroizolyacziya-czena1.ru/ .
Vavada online casino delights players with regular tournaments featuring large prize pools. To find a working Vavada mirror, visit https://museo.precolombino.cl/ and choose a link. Games at Vavada load instantly thanks to powerful servers. The Vavada loyalty program rewards activity with additional bonuses. The Vavada mobile version works smoothly on any smartphones.
вертикальная гидроизоляция стен подвала вертикальная гидроизоляция стен подвала .
инъекционная гидроизоляция своими руками инъекционная гидроизоляция своими руками .
усиление проема усиление проема .
Весь процесс можно представить следующим образом:
Изучить вопрос глубже – нарколог на дом вывод в челябинске
Эта статья освещает различные аспекты освобождения от зависимости и пути к выздоровлению. Мы обсуждаем важность осознания своей проблемы и обращения за помощью. Читатели получат практические советы о том, как преодолевать трудности и строить новую жизнь без зависимости.
Получить дополнительную информацию – срочный вывод из запоя
Вывод из запоя в клинике в Нижнем Новгороде проводится с применением инфузионной терапии, седативных средств и витаминных комплексов. Основная задача процедуры — устранить токсическое воздействие алкоголя, восстановить работу органов и нормализовать психоэмоциональное состояние. Все препараты подбираются индивидуально, с учётом особенностей организма пациента.
Разобраться лучше – http://
Капельница от запоя в клинике в Нижнем Новгороде часто становится первым шагом в лечении хронической алкогольной зависимости. Детоксикация помогает вывести продукты распада этанола и снизить нагрузку на внутренние органы, но не устраняет психологическую зависимость. Поэтому после завершения инфузионной терапии пациенту рекомендуется пройти консультацию психотерапевта и, при необходимости, начать курс реабилитации.
Ознакомиться с деталями – https://kapelnicza-ot-zapoya-v-nizhnem-novgorode16.ru/kapelnicza-pri-pokhmele-nizhnij-novgorod
Курс терапии в клинике состоит из нескольких последовательных этапов, каждый из которых направлен на достижение конкретных целей — от снятия интоксикации до восстановления психологического равновесия. Такой подход позволяет добиться устойчивого результата и минимизировать вероятность рецидива. На всех стадиях лечения ведётся контроль состояния пациента, а также постоянная корректировка назначений в зависимости от реакции организма.
Изучить вопрос глубже – частная наркологическая клиника
Мы дозировано упоминаем географию — важнее не слово «Нижний Новгород», а предсказуемость процесса. Пациент получает «вечерний протокол» — краткие инструкции на ближайшие 12 часов: как пить воду малыми порциями, как приглушить свет, какое «окно тишины» соблюсти перед сном, когда связаться с дежурным врачом и какие маркеры фиксировать в «дневнике симптомов» (шкалы тремора, тревоги, тошноты по 0–10; время засыпания; число пробуждений).
Изучить вопрос глубже – наркологическая клиника клиника помощь нижний новгород
Стационар уместен при тяжёлой абстиненции, скачках давления, угрозе делирия, эпизодах судорог, неукротимой рвоте, а также когда дома нет взрослого помощника на ночь. В палате — аппаратный контроль по показаниям, пост медсестёр 24/7, ЭКГ и базовая лаборатория, регулярные переоценки с корректировкой схемы. Решения принимаются быстро, без логистических задержек; это снижает риск поздних осложнений и повторных экстренных вызовов.
Узнать больше – http://narkologicheskaya-klinika-chekhov8.ru
В городе и ближайших районах клиника «УралМед Трезвость» обеспечивает оперативный выезд и амбулаторный приём без очередей. На этапе первичного контакта координатор уточняет только клинически значимые моменты: постоянные препараты и дозы, аллергии, эпизоды судорог/психозов в прошлом, базовые показатели (АД/ЧСС/SpO?, если доступны), длительность симптомов, возможность организовать «тихое окно» на 20–30 минут. Вместо долгих разговоров — короткая, спокойная логика: где безопаснее начать (дом/амбулатория/стационар), какую ближайшую цель выбираем, в каком интервале ждём эффект и что считаем сигналом для связи с дежурным врачом.
Получить дополнительные сведения – наркологическая клиника наркологический центр челябинск
Стационар мы предлагаем, когда дома нет условий для ночного наблюдения, симптомы тяжёлые или прогноз нестабилен. В палате — контролируемая среда, возможность оперативно выполнить ЭКГ и базовые анализы по показаниям, круглосуточный пост. Команда корректирует схему лечения в реальном времени, не теряя часы на логистику. Это особенно важно при давних запоях, риске делирия, выраженных колебаниях давления, сахарном диабете, ИБС, заболеваниях ЖКТ.
Узнать больше – http://vyvod-iz-zapoya-sergiev-posad8.ru
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Подробнее – http://narkolog-na-dom-voskresensk8.ru/vyzov-narkologa-na-dom-v-voskresenske/https://narkolog-na-dom-voskresensk8.ru
Решение о выезде принимает врач с учётом симптомов и бытовых ограничений. Если совпадает хотя бы две позиции из списка ниже, лучше не откладывать звонок — управляемость состояния снижается каждый час.
Детальнее – вывод из запоя вызов на дом казань
Домашний формат уместен, когда симптоматика контролируема и вечером рядом может остаться взрослый помощник. Преимущество Лобни — короткие дистанции внутри города, поэтому врач приезжает быстро, без шума и эмблем. На месте мы не торопимся: собеседование по факту последних 48 часов, измерения давления, пульса, сатурации и температуры, короткий неврологический скрининг, сверка аллергий и уже принятых препаратов. После допуска к терапии запускается инфузия: сначала — коррекция воды и электролитов, затем — поддержка печени и ЦНС, при необходимости — противорвотные и анксиолитические препараты. Темп настраивается по динамике, чтобы снять тремор и тошноту без «перекручивания» организма в сон с тяжёлым просыпанием. По итогам визита — понятные правила на 24–48 часов, список тревожных признаков и согласованное окно контрольного контакта. Домашний маршрут экономит часы, снижает социальную тревогу и делает первые сутки предсказуемыми.
Разобраться лучше – http://vyvod-iz-zapoya-lobnya8.ru
Домашний формат — это клинически выверенная помощь без госпитализации, если обстановка безопасна и есть взрослый помощник на вечер и ночь. Врач «Трезвого Компаса» приезжает без опознавательных знаков, проводит очную оценку (АД, пульс, сатурация, температура, неврологический статус), уточняет препараты, принятые за 48 часов, и аллергии. Далее — допуск к терапии и запуск инфузии. Мы корректируем жидкость и электролиты, поддерживаем печень и ЦНС, по показаниям используем противорвотные и анксиолитические решения, избегая «перелечивания». В конце визита — переоценка, настройка темпа/состава, памятка на 24–48 часов и окно контрольного контакта.
Выяснить больше – kapelnica-pri-zapoe
Запой — это не один симптом. Это сдвиг водно-электролитного баланса, скачки давления и пульса, тремор, тошнота, тревога, бессонница, нередко раздражение слизистой желудка и нагрузка на печень. Мы работаем последовательностью: допуск к терапии, инфузионная поддержка с коррекцией воды и электролитов, защита органов-мишеней, симптом-контроль, при необходимости аккуратная нормализация сна, переоценка и перевод на пероральные схемы, затем — поведенческий контур «тихих» дней и, при информированном согласии, подготовка к кодированию. Это не «коктейль на всех», а управляемый процесс, завязанный на объективные показатели и живую динамику.
Углубиться в тему – https://narkologicheskaya-klinika-ivanteevka8.ru/narkologicheskaya-klinika-na-domu-v-ivanteevke
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Углубиться в тему – вывод из запоя москва цены
Для тех, кто ценит инновации и заботится об окружающей среде, гибрид автомобиль купить становится все более привлекательным вариантом, предлагающим не только снижение вредных выбросов, но и уникальный опыт вождения.
с каждым днем их популярность только растет благодаря своей экологичности и экономической эффективности. Экологи также видят в них способ снизить загрязнение воздуха. Их эксплуатация основана на использовании электрической энергии вместо бензина или дизеля.
Они уже используются во многих странах мира как более чистый и экономичный вариант транспорта . Люди, которые рассматривают возможность покупки электромобиля, часто интересуются его техническими характеристиками . Это связано с повышением осведомленности о необходимости защиты окружающей среды .
Электромобили обладают рядом преимуществ перед традиционными автомобилями, включая снижение выбросов загрязняющих веществ . Они не выделяют вредных веществ в атмосферу, что делает их более чистым вариантом . Это связано с тем, что электрические двигатели производят меньше шума и вибраций, чем традиционные двигатели .
Экономическая эффективность электромобилей является еще одним важным преимуществом . Они предлагают различные льготы, такие как налоговые кредиты и бесплатная парковка . Сgrowthом технологий стоимость электромобилей постепенно снижается .
Одним из главных недостатков является ограниченный пробег на одном заряде . Быстрая зарядка может??ally решить эту проблему, но она не всегда доступна. Еще одним недостатком электромобилей является высокая первоначальная стоимость .
Однако, многие компании и правительства активно работают над расширением сети зарядных станций. Они могут быть склонны к электрическим пожарам, хотя такие случаи очень редки . По мере развития технологий можно ожидать, что эти недостатки будут постепенно устранены.
В заключении, электромобили представляют собой интересный и перспективный вариант для тех, кто ищет более экологичный и экономичный способ передвижения . Будущее электромобилей выглядит перспективным, с постоянным развитием технологий и улучшением инфраструктуры . Они предлагают реальный способ снизить нашу зависимость от ископаемого топлива и уменьшить вредное воздействие на окружающую среду .
Это приведет к появлению новых моделей с улучшенными характеристиками и снижением цен . Правительства также будут продолжать играть ключевую роль в продвижении электромобилей . Это интересное время для электромобилей, и их влияние на нашу жизнь будет только расти.
усиление проема москва усиление проема москва .
Сначала — очная оценка, проверка противопоказаний и совместимости с текущими лекарствами. Далее — инфузионная терапия для коррекции водно-электролитного баланса, поддержка печени и сердечно-сосудистой системы, мягкая анксиолитическая и снотворная поддержка по показаниям. Визит обычно занимает от 60 до 120 минут; при необходимости капельницы проводятся медленно, с наблюдением. После процедуры пациент получает понятные памятки: что и когда пить, когда спать, какие признаки считаются тревожными и требуют повторного осмотра или перевода в стационар.
Ознакомиться с деталями – https://narkologicheskaya-klinika-moskva8.ru
сайт для заказа курсовых работ kupit-kursovuyu-21.ru .
студенческие работы на заказ http://kupit-kursovuyu-23.ru/ .
цена курсовой работы kupit-kursovuyu-22.ru .
Весь процесс можно представить следующим образом:
Детальнее – нарколог капельница на дом челябинск
Лечение проводится поэтапно, начиная с оценки состояния и заканчивая восстановлением после интоксикации. Каждый этап направлен на устранение симптомов отравления и стабилизацию работы внутренних органов.
Выяснить больше – нарколог на дом клиника
Стационар уместен при тяжёлой абстиненции, скачках давления, угрозе делирия, эпизодах судорог, неукротимой рвоте, а также когда дома нет взрослого помощника на ночь. В палате — аппаратный контроль по показаниям, пост медсестёр 24/7, ЭКГ и базовая лаборатория, регулярные переоценки с корректировкой схемы. Решения принимаются быстро, без логистических задержек; это снижает риск поздних осложнений и повторных экстренных вызовов.
Разобраться лучше – narkologicheskaya-klinika-v-chekhove
Прежде чем перечислить критичные признаки, зафиксируем принцип: даже один выраженный симптом — повод не откладывать помощь и выбрать безопасный маршрут (дом или стационар) после быстрой очной оценки врача.
Выяснить больше – https://vyvod-iz-zapoya-sergiev-posad8.ru
«Опора Здоровья» организует выезд нарколога на дом по Воскресенску и району круглосуточно. Мы действуем анонимно и по клиническим протоколам: очная оценка состояния, допуск к инфузии, детокс с коррекцией водно-электролитного баланса, поддержка печени и центральной нервной системы, бережная нормализация сна по показаниям. Врач объясняет решения простым языком, согласует темп и состав капельницы, оставляет памятку на 24–48 часов и остаётся на связи. Если риски высоки, предложим перевод в стационар без задержек — безопасность всегда важнее «тишей» дома.
Исследовать вопрос подробнее – http://
Вывод из запоя в клинике в Нижнем Новгороде проводится с применением инфузионной терапии, седативных средств и витаминных комплексов. Основная задача процедуры — устранить токсическое воздействие алкоголя, восстановить работу органов и нормализовать психоэмоциональное состояние. Все препараты подбираются индивидуально, с учётом особенностей организма пациента.
Разобраться лучше – наркологическая клиника цены
Стационар рационален при нестабильном состоянии, риске делирия, судорогах в анамнезе, скачках давления, выраженной одышке, неукротимой рвоте, одиночестве ночью или невозможности обеспечить «тихий режим». В палате — контролируемая среда, доступ к ЭКГ и базовой лаборатории по показаниям, круглосуточный пост медсестёр и возможность быстро менять тактику, если параметры «плывут». Такой маршрут предсказуемее по безопасности и зачастую короче по времени до стабильного самочувствия.
Подробнее можно узнать тут – https://kapelnica-ot-zapoya-klin8.ru/kapelnica-ot-zapoya-na-domu-v-klinu/
Палатный формат мы предлагаем, когда есть риск делирия, судорог, резких скачков давления и пульса, выраженной одышки, неукротимой рвоты, обезвоживания или когда дома невозможно обеспечить наблюдение ночью. В стационаре под рукой аппаратный контроль, по показаниям ЭКГ и базовая лаборатория, круглосуточный пост и регулярные переоценки с точной настройкой схем. Здесь меньше случайностей: темп инфузий корректируется без задержек, решения принимаются быстро, а риск «ночных качелей» ниже. Для семьи стационар часто оказывается не «дороже», а короче по времени до стабильного сна и предсказуемее по бюджету.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-ivanteevka8.ru/narkologicheskie-kliniki-pomoshch-v-ivanteevke/
Наши стандарты включают конфиденциальную маршрутизацию, детализированные инструкции для семьи, модульный план лечения и прозрачное разделение бесплатных и платных блоков. Каждому пациенту назначается ведущий специалист, который сопровождает его на всём пути — от первого звонка до контрольных чек-инов после процедур. Мы не «наращиваем» объём вмешательств ради впечатления: используется минимально достаточный набор мер, который действительно влияет на целевые маркеры — переносимость воды, качество сна, сглаживание вегетативных «качелей» и возвращение утренней ясности.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-v-chelyabinske16.ru
Анонимность — стандарт по умолчанию. Документация ведётся нейтрально и только в объёме, необходимом для оказания помощи. Мы не информируем третьих лиц, не вступаем в контакты с работодателями или соседями. Визит осуществляется на немаркированном авто, общение — коротко и по делу, доступ к карте пациента ограничен принципом «минимально необходимого». Если требуется стационар, используем отдельный вход и «тихий коридор», а по выписке возвращаем тот же маршрут обслуживания на дому.
Выяснить больше – https://narkologicheskaya-klinika-v-nizhnem-novgorode16.ru/
Мы не используем шаблон «на всех». Темп и сочетания зависят от давления, пульса, выраженности тошноты и тремора, уровня тревоги, сопутствующих диагнозов и лекарств, уже попавших в организм. Детокс — это система шагов: допуск к терапии, коррекция воды и электролитов, поддержка печени, вегетостабилизация, осторожная работа со сном по показаниям, профилактика осложнений. Любое назначение проговаривается простым языком: зачем, как подействует, что считать нормальной динамикой, а что — поводом связаться с врачом.
Изучить вопрос глубже – https://kapelnica-ot-zapoya-klin8.ru/kapelnica-ot-zapoya-na-domu-v-klinu/
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Получить дополнительную информацию – вывод из запоя на дому москва круглосуточно
Домашний формат — это клинически выверенная помощь без госпитализации, если обстановка безопасна и есть взрослый помощник на вечер и ночь. Врач «Трезвого Компаса» приезжает без опознавательных знаков, проводит очную оценку (АД, пульс, сатурация, температура, неврологический статус), уточняет препараты, принятые за 48 часов, и аллергии. Далее — допуск к терапии и запуск инфузии. Мы корректируем жидкость и электролиты, поддерживаем печень и ЦНС, по показаниям используем противорвотные и анксиолитические решения, избегая «перелечивания». В конце визита — переоценка, настройка темпа/состава, памятка на 24–48 часов и окно контрольного контакта.
Подробнее – kapelnica-ot-zapoya-uslugi
Запой — это не один симптом. Это сдвиг водно-электролитного баланса, скачки давления и пульса, тремор, тошнота, тревога, бессонница, нередко раздражение слизистой желудка и нагрузка на печень. Мы работаем последовательностью: допуск к терапии, инфузионная поддержка с коррекцией воды и электролитов, защита органов-мишеней, симптом-контроль, при необходимости аккуратная нормализация сна, переоценка и перевод на пероральные схемы, затем — поведенческий контур «тихих» дней и, при информированном согласии, подготовка к кодированию. Это не «коктейль на всех», а управляемый процесс, завязанный на объективные показатели и живую динамику.
Выяснить больше – klinika-narkologicheskoj-pomoshchi
Чтобы понять логику процесса, посмотрите на ориентир ниже. Это не жёсткое расписание, а понятная канва, которую врач адаптирует под возраст, сопутствующие заболевания и текущие цифры.
Ознакомиться с деталями – http://narkologicheskaya-klinika-ivanteevka8.ru/narkologicheskaya-klinika-na-domu-v-ivanteevke/
Наши стандарты включают конфиденциальную маршрутизацию, детализированные инструкции для семьи, модульный план лечения и прозрачное разделение бесплатных и платных блоков. Каждому пациенту назначается ведущий специалист, который сопровождает его на всём пути — от первого звонка до контрольных чек-инов после процедур. Мы не «наращиваем» объём вмешательств ради впечатления: используется минимально достаточный набор мер, который действительно влияет на целевые маркеры — переносимость воды, качество сна, сглаживание вегетативных «качелей» и возвращение утренней ясности.
Подробнее можно узнать тут – наркологическая клиника стационар в челябинске
Если среда дома шумная или приватность под угрозой, мы предложим «короткий коридор» через отдельный вход амбулатории. Если условия позволяют, проводим процедуры на дому: свет приглушён, доступ к розетке организован, рядом столик для расходников и приборов. Этот «экологичный» сценарий, несмотря на простоту, заметно улучшает переносимость процедур и собирает устойчивый сон в первую ночь, что особенно важно на ранних этапах стабилизации.
Получить дополнительные сведения – наркологическая клиника цены
Стационар уместен при тяжёлой абстиненции, скачках давления, угрозе делирия, эпизодах судорог, неукротимой рвоте, а также когда дома нет взрослого помощника на ночь. В палате — аппаратный контроль по показаниям, пост медсестёр 24/7, ЭКГ и базовая лаборатория, регулярные переоценки с корректировкой схемы. Решения принимаются быстро, без логистических задержек; это снижает риск поздних осложнений и повторных экстренных вызовов.
Получить дополнительные сведения – http://narkologicheskaya-klinika-chekhov8.ru/chastnaya-narkologicheskaya-klinika-v-chekhove/
Стоимость и состав зависят от длительности вмешательства, выраженности симптомов и сопутствующих рисков. Мы избегаем универсальных «коктейлей»: комплектация пакета формируется по маркерам, которые видим на месте. Ниже — ориентиры, помогающие заранее понимать логику и наполнение.
Разобраться лучше – наркологическая клиника наркологический центр нижний новгород
В городе и пригороде организован круглосуточный приём с возможностью выезда на дом. Координатор уточняет только клинически значимые данные: регулярные препараты и дозировки, аллергии, недавние эпизоды судорог/психозов, доступ к розетке, возможность обеспечить «тихое окно» на 2–3 часа. Если в квартире многолюдно или идёт ремонт, предложим «тихий» стационар с отдельным входом и тем же ведущим врачом; после стабилизации зеркально перенесём маршрут обратно домой, чтобы не терять темп и доверие.
Получить больше информации – наркологическая клиника цены в нижнем новгороде
Чтобы помощь была прозрачной и управляемой, каждый этап имеет цель, индикаторы безопасности и эффективности, а также понятное «окно оценки» результата. Коррекции проводятся «штучно», по правилу одного изменения — это защищает от полипрагмазии и позволяет читабельно видеть вклад каждого шага.
Получить дополнительные сведения – вывод из запоя дешево
Сначала короткий осмотр и проверка совместимостей, затем — инфузионная терапия с мониторингом давления/пульса/сатурации, после — инструктаж семьи и назначение контрольного контакта. Такой порядок снижает тревогу и делает ночь предсказуемой: понятно, чего ждать, когда отдыхать и в какой момент связываться с врачом.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-sergiev-posad8.ru/vyvod-iz-zapoya-klinika-v-sergievom-posade/
Перед тем как перечислить основные поводы для экстренного вызова, отметим: даже один из пунктов — уже основание не откладывать помощь.
Подробнее – вывод из запоя московский район
Чтобы процедура прошла спокойно и без задержек, заранее организуйте базовые условия — это экономит время и силы пациента и семьи.
Получить больше информации – https://vyvod-iz-zapoya-moskva8.ru/
Домашний формат уменьшает стресс и экономит время: не нужно ехать в клинику, скрывать визит от соседей или ждать в очереди. Врач приезжает без опознавательных знаков и не создаёт «медицинского шума». За один визит удаётся снять острые проявления, выстроить понятный план ночи и следующего утра, а также определить, нужна ли дополнительная диагностика. Такой маршрут часто оказывается короче и эффективнее, чем череда попыток «пересидеть» симптомы без медицинской поддержки.
Детальнее – narkolog-na-dom-voskresensk
Весь процесс можно представить следующим образом:
Ознакомиться с деталями – платный нарколог на дом в челябинске
Наркологическая клиника в клинике в Нижнем Новгороде использует многопрофильный подход, направленный на физическое и психологическое восстановление пациентов. После детоксикации проводится стабилизация обменных процессов, нормализация работы внутренних органов и поддержка нервной системы. Особое внимание уделяется коррекции поведения и мотивации пациента к отказу от употребления алкоголя или наркотиков.
Ознакомиться с деталями – наркологическая клиника в нижнем новгороде
Вывод из запоя — это управляемая медицинская процедура, где каждая деталь важна: от скорости выезда до состава инфузии и «тихой» среды дома. В наркологической клинике «КазаньДетокс Медлайн» мы придерживаемся принципа поэтапной стабилизации: сначала безопасный старт и оценка рисков, затем прицельные капельницы и, при необходимости, краткосрочное наблюдение. Такой подход исключает «универсальные коктейли» и делает результат прогнозируемым: снижение интоксикации, выравнивание вегетативных реакций, восстановление сна и аппетита. Анонимность встроена в протоколы: немаркированный выезд, лаконичная документация, один доверенный контакт для связи 24/7, нейтральные формулировки без стигмы.
Детальнее – вывод из запоя с выездом казань
Нарколог на дом в Челябинске — это услуга, которая позволяет получить профессиональную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости посещения клиники. Такой формат особенно востребован в случаях, когда пациент не может самостоятельно прибыть в медицинское учреждение или нуждается в конфиденциальной помощи. Врач-нарколог выезжает по указанному адресу, проводит осмотр, оценивает состояние и подбирает оптимальную терапию. Квалифицированное вмешательство помогает избежать осложнений и стабилизировать состояние уже в течение первых часов после прибытия специалиста.
Ознакомиться с деталями – https://narkolog-na-dom-v-chelyabinske16.ru/narkolog-na-dom-v-chelyabinske-vyvod-iz-zapoya
Вывод из запоя — это управляемая медицинская процедура, где каждая деталь важна: от скорости выезда до состава инфузии и «тихой» среды дома. В наркологической клинике «КазаньДетокс Медлайн» мы придерживаемся принципа поэтапной стабилизации: сначала безопасный старт и оценка рисков, затем прицельные капельницы и, при необходимости, краткосрочное наблюдение. Такой подход исключает «универсальные коктейли» и делает результат прогнозируемым: снижение интоксикации, выравнивание вегетативных реакций, восстановление сна и аппетита. Анонимность встроена в протоколы: немаркированный выезд, лаконичная документация, один доверенный контакт для связи 24/7, нейтральные формулировки без стигмы.
Получить дополнительную информацию – вывод из запоя казань
Выездной формат — это не просто «капельница у кровати». Мы заранее раскладываем визит на модули и назначаем окна оценки: первые 20–40 минут (антиеметический мост, переносимость воды), 60–120 минут (регидратация и электролиты, сглаживание ЧСС/АД), первая ночь (сон ?6 часов и ?1 пробуждение), 12–24 часа (утренняя ясность и способность выполнить 2 короткие бытовые задачи). Одно изменение — один параметр: либо темп инфузии, либо порядок модулей, либо настройка среды (свет/тишина/ритуал). Так причинно-следственные связи остаются прозрачными, а результат — подтверждаемым.
Получить дополнительные сведения – лечение в наркологической клинике в челябинске
Процедура вывода из запоя проводится с применением современных методик инфузионной терапии. Врачи контролируют уровень гидратации, работу сердечно-сосудистой системы и общее состояние пациента до полного устранения симптомов.
Исследовать вопрос подробнее – частная наркологическая клиника казань
Читатели получат представление о том, как современные технологии влияют на развитие медицины. Обсуждаются новые методы лечения, персонализированный подход и роль цифровых решений в повышении качества медицинских услуг.
Эксклюзивная информация – https://sanvolga44.ru/vyryvayas-iz-zapoya
Шины Пирелли обеспечивают отличное сцепление и комфорт при езде в любых условиях.
Шины марки Пирелли известны своим качеством и производительностью. Их выбирают многие автолюбители из-за отличных характеристик. Пирелли предлагает разнообразные модели для разных условий вождения.
Одной из ключевых особенностей шин Пирелли является их высокая степень надежности. Эти шины гарантируют прекрасное сцепление . В особенно трудных условиях это становится незаменимым и обеспечивает безопасность в пути.
Кроме того, шины Пирелли имеют длительный срок службы . Это приводит к значительной экономии на замене шин. Каждый водитель оценит такое преимущество.
Пирелли активно участвует в спортивных соревнованиях . Разработка для спортивных автомобилей внедряется в штатные шины. Вы получаете шины с элементами спортивной производительности, сделанные для повседневного использования.
Эффективное раскрутка сайта является ключевым аспектом успеха любого бизнеса в современном цифровом ландшафте.
Продвижение сайта играет решающую роль в привлечении потенциальных клиентов . Это связано с тем, что большинство потенциальных клиентов ищут информацию в интернете . Кроме того, продвижение сайта позволяет увеличить узнаваемость бренда .
Продвижение сайта включает в себя ряд действий и стратегий . Это включает в себя использование контекстной рекламы . Все эти методы способствуют привлечению целевой аудитории .
Одной из наиболее эффективных стратегий продвижения сайта является поисковая оптимизация . Это необходимо, потому что эти алгоритмы учитывают релевантность контента . Кроме того, оно способствует повышению авторитета сайта.
оно помогает привлечь посетителей, которые заинтересованы в вашем продукте или услуге. Кроме того, социальные сети предлагают широкие возможности для продвижения сайта . Все эти стратегии они предполагают корректировку маркетинговых действий .
эти инструменты предназначены для автоматизации и оптимизации маркетинговых процессов. Это включает в себя инструменты для оптимизации контента и ключевых слов. Все эти инструменты позволяют увеличить эффективность маркетинговых кампаний .
Использование электронной почты для продвижения сайта также является эффективным методом . Кроме того, создание лендингов и других специализированных страниц является важным аспектом продвижения сайта . Все эти инструменты и технологии это необходимо для достижения желаемых результатов.
оно предполагает выбор наиболее эффективных стратегий и инструментов. Это необходимо, потому что план помогает_focus на приоритетных задачах . Кроме того, оно помогает поддерживать эффективность маркетинговых усилий.
оно предполагает использование новых инструментов и технологий. Это необходимо, потому что они могут существенно повлиять на эффективность маркетинговых действий. Все эти аспекты это необходимо для поддержания и увеличения успеха в продвижении сайта.
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Открыть полностью – https://novieauto.ru/3271634-pochemu-avtokat-76-vash-luchshijj-vybor-dr0p
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Не упусти шанс – https://primenewsnet.com/the-next-wave-of-superheroes-has-arrived-with-astonishing-impact
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Всё самое вкусное внутри – https://pfendustri.com/kompanzasyon-nedir
Этот обзорный материал предоставляет информационно насыщенные данные, касающиеся актуальных тем. Мы стремимся сделать информацию доступной и структурированной, чтобы читатели могли легко ориентироваться в наших выводах. Познайте новое с нашим обзором!
Погрузиться в детали – https://npo-maebashi-chuo-bbc.org/?p=1461
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Все материалы собраны здесь – https://compta-btp.com/aide-gnr-btp-comment-les-pme-du-batiment-peuvent-en-beneficier
Эта статья предлагает захватывающий и полезный контент, который привлечет внимание широкого круга читателей. Мы постараемся представить тебе идеи, которые вдохновят вас на изменения в жизни и предоставят практические решения для повседневных вопросов. Читайте и вдохновляйтесь!
Кликни и узнай всё! – https://patagoniarebeldedigital.com.ar/politica/milei-pondra-su-busto-en-casa-rosada
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Всё, что нужно знать – https://ghostnight.be/cropped-head-ghost-solo-1-jpg
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Нажми и узнай всё – https://ampri.res.in/en/?p=291
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Обратитесь за информацией – https://urbanstart.es/producto/urbanshop-sudadera-invierno-urbanstart
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Погрузиться в детали – https://cosmetech.co.in/impact-of-personal-care-formulations-on-environment
производства натяжных потолков
Такой вариант отделки сочетает в себе эстетику и функциональность.
Компания “natyazhni-steli-vid-virobnika.biz.ua” предлагает качественные потолки напрямую от производителя. Наша продукция соответствует европейским стандартам.
#### **2. Преимущества натяжных потолков**
Одним из главных плюсов натяжных потолков является их влагостойкость. Даже при затоплении потолок останется целым.
Еще одно преимущество — огромный выбор цветов и фактур. Дизайнеры помогут создать уникальный стиль для вашего помещения.
#### **3. Производство и материалы**
Наша компания изготавливает потолки из экологически чистого ПВХ. Сертификаты подтверждают его гипоаллергенность.
Технология производства гарантирует прочность и эластичность полотна. Готовые потолки устойчивы к механическим повреждениям.
#### **4. Установка и обслуживание**
Монтаж натяжных потолков занимает всего несколько часов. Опытные мастера выполнят работу без пыли и грязи.
Уход за потолком не требует особых усилий. Даже через годы потолок сохранит первоначальный вид.
—
### **Спин-шаблон статьи**
#### **1. Введение**
Наши изделия изготавливаются на собственном производстве с соблюдением всех норм.
#### **2. Преимущества натяжных потолков**
Выбор оформления практически безграничен — от классики до 3D-эффектов.
#### **3. Производство и материалы**
Полотна устойчивы к перепадам температур и влажности.
#### **4. Установка и обслуживание**
Профессиональный монтаж исключает ошибки и обеспечивает идеальный результат.
завод по производству натяжных потолков
Это популярный выбор благодаря быстрому монтажу и разнообразию дизайнов.
Компания “natyazhni-steli-vid-virobnika.biz.ua” предлагает качественные потолки напрямую от производителя. Наша продукция соответствует европейским стандартам.
#### **2. Преимущества натяжных потолков**
Одним из главных плюсов натяжных потолков является их влагостойкость. Такое покрытие не боится протечек и конденсата.
Еще одно преимущество — огромный выбор цветов и фактур. Дизайнеры помогут создать уникальный стиль для вашего помещения.
#### **3. Производство и материалы**
Наша компания изготавливает потолки из экологически чистого ПВХ. Материал абсолютно безопасен для здоровья.
Технология производства гарантирует прочность и эластичность полотна. Каждое полотно проходит проверку перед отправкой клиенту.
#### **4. Установка и обслуживание**
Монтаж натяжных потолков занимает всего несколько часов. Процесс не требует длительной подготовки основания.
Уход за потолком не требует особых усилий. Пятна и пыль легко удаляются без специальных средств.
—
### **Спин-шаблон статьи**
#### **1. Введение**
Компания “natyazhni-steli-vid-virobnika.biz.ua” работает напрямую с клиентами без посредников.
#### **2. Преимущества натяжных потолков**
Современные технологии позволяют наносить любые изображения на полотно.
#### **3. Производство и материалы**
Наша продукция соответствует строгим экологическим стандартам.
#### **4. Установка и обслуживание**
Наши специалисты устанавливают потолки с точностью до миллиметра.
Для успешного выполнения сложных строительных или логистических проектов часто требуется аренда манипулятора москва, который обеспечивает эффективную и безопасную перевозку тяжелых грузов.
Использование манипулятора в аренде позволяет компаниям оптимизировать свои затраты. Это особенно важно для небольших и средних предприятий, которые не имеют большого бюджета на покупку и обслуживание оборудования. Это позволяет им быть более гибкими и эффективными в своей работе. Кроме того, аренда манипулятора исключает необходимость в постоянном обслуживании и ремонте, что также снижает эксплуатационные затраты.
Правильный выбор манипулятора зависит от характера работы и размеров грузов. Компании, которые часто используют манипуляторы, могут арендовать их на долгосрочной основе, обеспечивая бесперебойную работу и минимизируя простои. Аренда манипулятора также подразумевает обучение персонала, которое предоставляется компанией-арендодателем .
Это позволяет им сосредоточиться на своей основной деятельности, не отвлекаясь на техническое обслуживание . Это особенно актуально для проектов, которые имеют ограниченный срок реализации, поскольку компании не должны покупать оборудование, которое может не понадобиться им после завершения проекта. Они получают доступ к современному оборудованию, которое более эффективно и надежно .
Это минимизирует простои и позволяет приступить к работе как можно скорее . Это особенно важно для компаний, которые не имеют своего собственного технического персонала для обслуживания оборудования. Аренда манипулятора также позволяет компаниям быть более гибкими в своей работе .
Это гарантирует, что оборудование будет соответствовать их конкретным потребностям. Кроме того, компании должны ознакомиться с условиями аренды, включая стоимость, срок аренды и требования к обслуживанию. Это помогает избежать ошибок при выборе манипулятора.
Это включает наличие соответствующих сертификатов и регулярное техническое обслуживание. Кроме того, компании должны обеспечить, что их персонал проходит обучение по эксплуатации арендованного манипулятора. Это снижает риск поломок и простоев во время работы.
Аренда манипулятора может быть стратегическим решением для компаний, которые хотят повысить свою эффективность и снизить затраты . Это особенно важно для небольших и средних предприятий, которые не имеют большого бюджета на покупку и обслуживание оборудования. Это гарантирует, что оборудование будет соответствовать их конкретным потребностям и будет безопасно в эксплуатации.
Они также могут пользоваться последними технологическими достижениями и исключать необходимость в больших первоначальных инвестициях . Кроме того, аренда манипулятора позволяет компаниям быть более гибкими и быстро реагировать на изменения в проекте или рыночных условиях. Компании могут выбрать манипулятор, который лучше всего подходит для их конкретных потребностей, и_focusиться на своей основной деятельности.
лучшие онлайн казино 2025 Хотите испытать удачу и окунуться в мир азарта? Игровые автоматы – это то, что вам нужно! Яркие картинки, захватывающие звуки и, конечно же, шанс сорвать куш – всё это ждет вас в мире слотов. От классических “одноруких бандитов” до современных видеослотов с невероятными бонусами, каждый найдет автомат по душе. Готовы к вращению барабанов?
Если вам нужно щпс цена за куб в Москве, то стоит обратить внимание на надежные поставщики, которые предлагают качественную продукцию по конкурентным ценам.
Щпс – это важнейший элемент современного промышленного процесса, доступный для покупки в Москве. Щпс используется в различных областях промышленности, включая производство, строительство и транспорт для обеспечения эффективной и безопасной работы . Благодаря своей универсальности и надежности, щпс стал незаменимым инструментом для многих компаний .
В Москве существуют множество способов приобрести щпс, включая покупку в специализированных магазинах . При выборе щпс необходимо учитывать несколько важных факторов, включая его технические характеристики и стоимость .
Использование щпс может принести много преимуществ для промышленных предприятий, включая повышение производительности и снижение затрат . Щпс также может помочь снизить энергопотребление и минимизировать воздействие на окружающую среду . Щпс обладает высокой ремонтопригодностью и может быть легко модернизирован или модифицирован.
Щпс также может использоваться в различных отраслях промышленности, включая производство, строительство и транспорт . Щпс продолжает развиваться и совершенствоваться, что позволяет ему оставаться одним из лидеров на рынке оборудования.
Для покупки щпс в Москве существует множество способов, включая посещение специализированных магазинов и интернет-магазинов . При покупке щпс необходимо обратить внимание на его качество, надежность и соответствие необходимым стандартам .
В Москве существуют множество компаний, которые предлагают щпс по разным ценам и с различными характеристиками . Благодаря широкому выбору щпс в Москве, можно найти подходящее оборудование для любых потребностей .
Щпс – это эффективное решение для многих отраслей промышленности, которое доступно для покупки в Москве. Щпс продолжает развиваться и совершенствоваться, что позволяет ему оставаться одним из лидеров на рынке оборудования .
Для покупки щпс в Москве необходимо найти надежного поставщика, который предлагает качественное оборудование по приемлемой цене . Щпс предлагает много преимуществ и может быть эффективно использован в различных отраслях промышленности .
Doceniam twoje zaangażowanie w pomaganie innym.
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Полная информация здесь – https://www.poormanmeals.com/blog/carrot-soul-soup
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Детали по клику – https://pbgfrwellness.com/workout-9
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Все материалы собраны здесь – https://www.videoton1990.it/uniti-si-vince-videoton-corsaro-a-morbegno
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Узнать больше > – https://chauffeurvtc-ecozen.com/the-art-of-negotiation-tips-for-successful-business-deals
В этом информативном обзоре собраны самые интересные статистические данные и факты, которые помогут лучше понять текущие тренды. Мы представим вам цифры и графики, которые иллюстрируют, как развиваются различные сферы жизни. Эта информация станет отличной основой для глубокого анализа и принятия обоснованных решений.
Ознакомьтесь с аналитикой – https://samikaholidays.com/2022/07/01/convergent-and-divergent-plate-margins
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Доступ к полной версии – https://rameshwaramcafeusa.com/menus/pork-with-italian-salsa-verde
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Подробнее можно узнать тут – https://primenewsnet.com/eminem-stronger-than-i-was
Этот информативный текст выделяется своими захватывающими аспектами, которые делают сложные темы доступными и понятными. Мы стремимся предложить читателям глубину знаний вместе с разнообразием интересных фактов. Откройте новые горизонты и развивайте свои способности познавать мир!
Уточнить детали – https://accelerathon.eu/valencia-acoge-el-congreso-mundial-del-agua-wex-global-2020
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Изучить вопрос глубже – https://redobaldai.lt/new-home-decor-from-john-doerson
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу.
Смотрите также… – https://multistyle.work/helping-companies-in-their-green-transition-4
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Эксклюзивная информация – https://saimu.uenolawoffice.com/%E4%BC%81%E6%A5%AD%E6%B3%95%E5%8B%99%E3%83%90%E3%83%8A%E3%83%BC-300×88
дайсон фен дайсон фен .
заказать задание kupit-kursovuyu-21.ru .
сколько стоит сделать курсовую работу на заказ kupit-kursovuyu-23.ru .
помощь курсовые https://kupit-kursovuyu-28.ru .
купить фен dyson купить фен dyson .
написание студенческих работ на заказ kupit-kursovuyu-21.ru .
купить курсовую http://kupit-kursovuyu-23.ru/ .
заказать курсовую заказать курсовую .
стоимость написания курсовой работы на заказ https://kupit-kursovuyu-22.ru .
стайлер дайсон официальный сайт стайлер дайсон официальный сайт .
курсовая работа купить http://kupit-kursovuyu-21.ru .
купить курсовую москва https://kupit-kursovuyu-23.ru .
дайсон купить стайлер для волос с насадками цена официальный сайт http://www.fen-d-3.ru/ .
пин ап загрузка на андроид http://pinup5009.ru
выполнение учебных работ http://kupit-kursovuyu-22.ru/ .
срочно курсовая работа https://kupit-kursovuyu-21.ru .
пин ап сайт на узбекском https://www.pinup5010.ru
курсовые купить https://kupit-kursovuyu-23.ru/ .
курсовой проект купить цена http://www.kupit-kursovuyu-22.ru .
Если вы ищете жилье в адлере, то наш сайт предлагает широкий выбор вариантов проживания и услуг для вашего идеального отдыха.
предлагает широкий выбор вариантов отдыха для туристов . Отдых в Адлере без посредников становится всё более популярным среди туристов . Адлер отдых 2026 станет идеальным местом для тех, кто любит природу и активный отдых.
Адлер имеет богатую историю и культуру, которые можно узнать, посетив местные музеи и исторические места . Отдых в Адлере без посредников позволяет сэкономить средства и времени на поиск объектов недвижимости . Адлер отдых 2026 будет интересен как детям, так и взрослым .
Адлер предлагает уникальные объекты недвижимости, которые можно забронировать без посредников . Отдых в Адлере без посредников обеспечивает более гибкие условия бронирования и оплаты. Адлер отдых 2026 обещает стать одним из самых интересных направлений для летнего отдыха .
Адлер имеет разнообразную инфраструктуру, которая включает в себя отели, рестораны и развлекательные учреждения. Отдых в Адлере без посредников даёт возможность выбрать объект недвижимости, который полностью соответствует вашим потребностям и бюджету . Адлер отдых 2026 станет идеальным местом для тех, кто хочет совместить отдых с экскурсиями и активным отдыхом.
Адлер предлагает разнообразную инфраструктуру, которая включает в себя спортивные комплексы и развлекательные учреждения. Отдых в Адлере без посредников позволяет сэкономить средства на бронировании экскурсий и активного отдыха . Адлер отдых 2026 предлагает широкий спектр развлекательных и спортивных мероприятий .
Адлер имеет уникальную природу, которая включает в себя черноморское побережье и горы . Отдых в Адлере без посредников даёт возможность выбрать варианты экскурсий и активного отдыха, которые полностью соответствуют вашим потребностям и бюджету . Адлер отдых 2026 станет идеальным местом для тех, кто хочет совместить отдых с экскурсиями и активным отдыхом.
Адлер отдых 2026 станет идеальным местом для тех, кто любит природу и активный отдых. Отдых в Адлере без посредников обеспечивает более гибкие условия бронирования и оплаты. Адлер отдых 2026 предлагает широкий выбор вариантов размещения, от бюджетных гостиниц до роскошных отелей .
Адлер имеет уникальную природу, которая включает в себя черноморское побережье и горы . Отдых в Адлере без посредников обеспечивает прямое общение с владельцами объектов недвижимости и организаторами экскурсий, что упрощает процесс бронирования и оплаты. Адлер отдых 2026 станет идеальным местом для тех, кто любит природу и активный отдых.
Play and get a bonus in a unique game andarbaharwin!
The narrative elements in gaming have improved significantly, resulting in more captivating experiences.
заказать курсовую https://www.kupit-kursovuyu-22.ru .
купить фен дайсон в москве у официального дилера [url=stajler-d-1.ru]stajler-d-1.ru[/url] .
купить фен dyson оригинал купить фен dyson оригинал .
фен дайсон официальный купить http://stajler-d.ru .
pin up hisobni bloklash https://pinup5011.ru
купить дайсон стайлер с насадками для волос цена официальный сайт stajler-d-2.ru .
дайсон стайлер для волос с насадками официальный сайт цена купить https://www.stajler-d-1.ru .
dyson официальный http://www.stajler-d.ru .
Для тех, кто хочет знать подробности о забор из профнастила с фундаментом, вы всегда можете обратиться к нам для получения точной информации и консультации.
Дачный забор из профнастила является одним из наиболее популярных вариантов для ограждения садового участка . Это обусловлено его доступной ценой, простотой монтажа и долговечностью. Для установки профнастила необходимы минимальные навыки и знания . Кроме того, профнастил предлагается в широком диапазоне цветов и дизайнов, что позволяет выбрать вариант, соответствующий стилю вашего участка .
Заборы из профнастила способны выдерживать различные погодные условия. Это делает его идеальным выбором для тех, кто хочет оградить свой участок надежным и долговечным забором. Цена дачного забора из профнастила с установкой может варьироваться в зависимости от региона и подрядчика .
Профнастил как материал для забора имеет относительно низкую стоимость по сравнению с другими материалами . Это делает его доступным для широкого круга потребителей. Кроме того, профнастил прост в уходе и не требует специальных мер по его сохранению . Также Профнастил изготовляется из перерабатываемых материалов, что делает его экологически?ским вариантом .
Забор из профнастила служит надежным барьером против проникновения на территорию. Таким образом, дачный забор из профнастила становится не только декоративным элементом, но и функциональной конструкцией, защищающей ваш участок .
Профнастил, используемый для заборов, имеет различные технические характеристики, влияющие на его эксплуатационные свойства . Толщина материала профнастила может быть khacной, в зависимости от требований к прочности и долговечности . Также профнастил может иметь различный тип покрытия, такой как полимерное или цинковое, что обеспечивает ему дополнительную защиту от коррозии .
Технические характеристики профнастила подбираются с учетом климатических условий и предполагаемой нагрузки. Таким образом, важно учитывать такие факторы, как климат, размер участка и предполагаемое использование, при выборе технических характеристик дачного забора из профнастила .
Установка профнастила может быть проведена как опытными мастерами, так и владельцами участков самостоятельно. Цена дачного забора из профнастила включает в себя стоимость материалов, работы и возможных дополнительных услуг.
Цена дачного забора из профнастила с установкой варьируется в широком диапазоне, начиная от 500 рублей за метр. При выборе подрядчика для установки дачного забора из профнастила следует учитывать его опыт, качество работы и отзывы клиентов .
Компания предлагает услуги автомобиль с водителем новосибирск по доступным ценам для всех желающих.
Аренда автомобиля с водителем в Новосибирске является удобным вариантом для тех, кто хочет путешествовать комфортно . Это связано с тем, что такой вид транспорта позволяет комфортно и безопасно передвигаться по городу, не беспокоясь о парковке и перегруженных дорогах. Аренда автомобиля с водительским условием может быть оформлена на любой период времени, подходящий для клиента . Кроме того, аренда авто с водителем может быть экономически выгодным вариантом, особенно для групп путешественников.
Аренда автомобиля с водителем позволяет выбрать транспорт, подходящий под любой бюджет и стиль путешествия . Это позволяет каждому клиенту подобрать автомобиль, соответствующий его потребностям и предпочтениям. Водители, занимающиеся арендой авто с водителем, гарантируют безопасность и комфорт на дороге.
Аренда машины с водителем в Новосибирске является идеальным способом изучить город, его историю и культуру. Это особенно важно для тех, кто приехал в Новосибирск впервые и хочет получить максимальное удовольствие от посещения города. Аренда автомобиля с водителем гарантирует клиентам безопасность и комфорт во время поездки . Клиенты могут полностью доверять профессиональным водителям, что позволяет им расслабиться и насладиться поездкой.
Аренда автомобиля с водителем позволяет бизнесменам сосредоточиться на своей работе, не тратя время на поиск транспорта . Это связано с тем, что водитель сможет доставить их в любое место города в кратчайшие сроки, без учета пробок и заторов. Аренда автомобиля с водителем может включать в себя дополнительные услуги, такие как экскурсии или организация деловых встреч .
Аренда автомобиля с водителем начинается с выбора компании и согласования всех деталей . Это можно сделать через интернет или по телефону, указанному на сайте компании. Для оформления аренды авто с водителем необходимо указать все необходимые данные и согласовать условия.
Компания, предоставляющая услуги аренды авто с водителем, поможет клиенту на всех этапах. Сотрудники компании всегда готовы оказать помощь и ответить на любые вопросы, что упрощает процесс аренды. Перед подписанием договора аренды автомобиля с водителем необходимо внимательно изучить все условия .
Аренда машины с водителем в Новосибирске – это лучший способ изучить город и его окрестности. Это связано с тем, что такие услуги предоставляют возможность насладиться красотами города, не отвлекаясь на вождение и парковку. Компании, предоставляющие услуги аренды авто с водителем, гарантируют клиентам безопасность, комфорт и пунктуальность .
При выборе компании для аренды авто с водителем необходимо обращать внимание на опыт работы, отзывы клиентов и качество автомобилей . Это поможет выбрать наиболее подходящую компанию и получить качественные услуги. Рекомендуем тщательно изучить все варианты и выбрать тот, который лучше всего соответствует вашим потребностям и бюджету .
pin up jonli kazino https://www.pinup5012.ru
дайсон стайлер для волос цена официальный сайт купить с насадками stajler-d-2.ru .
дайсон фен купить официальный stajler-d-1.ru .
купить фен дайсон официальный сайт http://stajler-d.ru .
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Изучить вопрос глубже – https://rojava.net/ahenga-radestkirina-xelaten-pesbirke
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Всё, что нужно знать – https://baringthoughts.com/index.php/2021/02/01/fear-nots
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Кликни и узнай всё! – https://xue.youounet.com/5089.html
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Изучить вопрос глубже – https://www.ateliersfrancochinois.com/2021/08/05/la-peinture-chinoise-aux-ateliers
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Все материалы собраны здесь – https://arabsdo.info/?p=38
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Секреты успеха внутри – https://www.ifmag.news/revues/categories/assurance/cote-divoireassurance-islamique-leadway-takaful-remet-20-million-de-fcfa-dexcedent-a-la-regie-hadj-pour-lexercice-2022
Эта статья для ознакомления предлагает читателям общее представление об актуальной теме. Мы стремимся представить ключевые факты и идеи, которые помогут читателям получить представление о предмете и решить, стоит ли углубляться в изучение.
Ознакомиться с отчётом – https://lll-world-marketing.com/product/competitor-backlink-analysis
Откройте для себя скрытые страницы истории и малоизвестные научные открытия, которые оказали колоссальное влияние на развитие человечества. Статья предлагает свежий взгляд на события, которые заслуживают большего внимания.
Это стоит прочитать полностью – http://schwerkraft.net/a-desertical-fuerteventura-2
стайлер дайсон для волос с насадками цена купить официальный сайт https://www.stajler-d-2.ru .
фен dyson официальный сайт http://stajler-d-1.ru/ .
фен дайсон купить оригинал stajler-d.ru .
Люкс для путешествий – это высокий уровень комфорта и бизнес джет цена перелета – это один из способов обеспечить себе такой опыт.
с высоким уровнем сервиса . Это идеальный выбор для тех, кто ценит свое время и готов платить за удобство . Частные самолеты предлагают широкий спектр услуг от базового сервиса до VIP-услуг.
Частные самолеты используются для особых случаев и мероприятий. Они предлагают уникальные условия для работы и отдыха. Кроме того, частные самолеты часто оснащены комфортными салонами .
Одним из главных преимуществ частных самолетов является их способность летать в любое время . Это позволяет пассажирам создавать индивидуальные маршруты . Частные самолеты также предлагают более быстрые полеты .
Частные самолеты часто используются для бизнес-авиации . Они обеспечивают максимальный комфорт . Кроме того, частные самолеты могут увеличивать производительность .
Существует несколько типов частных самолетов от легких самолетов до бизнес-джетов . Каждый тип предназначен для различных условий полета . Частные самолеты могут быть легкими или тяжелыми.
Частные самолеты могут быть разделены на классы по уровню комфорта . Они используются для дальнемагистральных полетов . Кроме того, частные самолеты могут быть оснащены дополнительным оборудованием .
В заключение, частные самолеты предлагают высокий уровень индивидуализации. Они используются для особых случаев и мероприятий . Частные самолеты обеспечивают максимальную безопасность .
Перспективы частных самолетов зависят от развития технологий. Частные самолеты будут становиться более доступными . Кроме того, частные самолеты будут продолжать эволюционировать .
травля клопов поможет эффективно избавиться от неприятных насекомых в вашем доме.
Обработка от клопов — важный этап в борьбе с этими насекомыми.
пин ап лайв ставки http://www.pinup5013.ru
Ini menjelaskan banyak keraguan yang saya ada.
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Детали по клику – https://psimariadasvitorias.site/nurturing-the-bond-between-humans-and-nature
Эта статья предлагает захватывающий и полезный контент, который привлечет внимание широкого круга читателей. Мы постараемся представить тебе идеи, которые вдохновят вас на изменения в жизни и предоставят практические решения для повседневных вопросов. Читайте и вдохновляйтесь!
Заходи — там интересно – https://ibunkamoments.com/portfolio/nam-eget
дайсон официальный сайт интернет http://fen-dn-kupit-1.ru .
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Кликни и узнай всё! – https://ijpfiasi.ro/at-the-time-of-composing-there-are-401-additional-live-casino-games-in-the-casino-and-therefore-we-may-say-is-actually-an-extraordinary-amount-the-newest-game-come-from-swedish-development-gaming-a
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Лучшее решение — прямо здесь – https://womenworldmagazine.com/women-are-creating-change-and-adding-value-to-the-economy-research
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Читать далее > – https://bandadelriosali.gob.ar/capilla-de-santa-rosa-de-lima-en-pacara
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу.
Ознакомьтесь поближе – https://www.stacefelder.com/42/test-plugins
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Кликни и узнай всё! – https://ijpfiasi.ro/online-casino-one-1-deposit-napoleon-boney-parts-million-celebs-added-bonus
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Что скрывают от вас? – https://carrieflint.com/why-do-i-care-about-physical-education-so-much
дайсон официальный сайт стайлер купить http://www.fen-dn-kupit-1.ru .
Постройте свой идеальный каркасный дом и наслаждайтесь комфортом и современными технологиями!
Одним из главных преимуществ каркасного дома является его легкость.
Для больших строительных проектов лучшим вариантом будет метизы оптом, чтобы сэкономить средства и времени.
позволяет сэкономить значительные средства . Это позволяет снизить затраты на закупку индивидуальных упаковок . При этом, необходимо учитывать качество предлагаемых изделий .
Купить крепеж оптом выгодно для строительных компаний . Это связано с тем, что оптовая покупка снижает стоимость . Кроме того, можно получить более выгодные условия поставки .
Купить крепеж оптом позволяет сэкономить средства . Это связано с тем, что оптовая покупка снижает цену за единицу . При этом, важно учитывать качество предлагаемых изделий .
Купить крепеж оптом может стать ключом к успеху. Это связано с тем, что оптовая покупка снижает затраты . Кроме того, можно насладиться большим выбором товаров .
Купить крепеж оптом является наиболее эффективным способом закупки. Это связано с тем, что позволяет купить необходимое количество материалов . При этом, важно учитывать качество предлагаемых изделий .
Купить крепеж оптом выгодно для строительных компаний . Это связано с тем, что дает возможность сократить расходы. Кроме того, можно насладиться большим выбором товаров.
Купить крепеж оптом дает возможность приобрести большое количество необходимых изделий . Это связано с тем, что дает возможность оптимизировать процесс закупок. При этом, важно выбирать надежного поставщика .
Купить крепеж оптом может стать ключом к успеху. Это связано с тем, что оптовая покупка снижает затраты . Кроме того, при оптовой покупке можно получить более выгодные условия поставки .
pin up aviator hack uz pin up aviator hack uz
официальный сайт дайсон в россии каталог цены http://www.fen-dn-kupit-1.ru .
официальный магазин дайсон https://www.fen-dn-kupit-1.ru .
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Читать далее > – http://hayakawasetsubi.jp/2023/07/30/%E4%BA%8B%E5%8B%99%E5%93%A1cats-eye%E3%81%AE%E9%80%B1%E6%9C%AB%E3%81%AE%E9%81%8E%E3%81%94%E3%81%97%E6%96%B9%E2%91%A2
Эта статья сочетает познавательный и занимательный контент, что делает ее идеальной для любителей глубоких исследований. Мы рассмотрим увлекательные аспекты различных тем и предоставим вам новые знания, которые могут оказаться полезными в будущем.
Прочитать подробнее – https://transporteslaserrania.com/index.php/2023/06/28/best-free-incest-onlyfans-sites-online
melbet официальный сайт melbet официальный сайт .
школа для детей shkola-onlajn1.ru .
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Детальнее – https://hydrogensafety.eu/2015/10/20/introducing-dr-deniz-zeynep-2
Этот обзор дает возможность взглянуть на историю и науку под новым углом. Мы представляем редкие факты, неожиданные связи и значимые события, которые помогут вам глубже понять развитие цивилизации и роль человека в ней.
Узнайте всю правду – https://engineeringconsultancy.in/the-road-to-your-dream-home-how-we-ensure-a-hassle-free-building-experience
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый мог разобраться в предмете и извлечь из него максимум пользы.
Погрузиться в научную дискуссию – https://frieda-kaffeebar.de/blog-post-left-sidebar-2
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Получить полную информацию – https://webofthings.org/2015/05/14/first-wot-w3c-interest-group-face-to-face-meeting
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Подробнее – https://www.theboxbycarolina.com/en/carolina-mazzoni/attachment/02
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Посмотреть подробности – https://dashausammeer.com/?p=1
дистанционное обучение 1 класс http://shkola-onlajn1.ru .
Man, having the S666app8 on my phone is a game-changer. Quick access to all my favorite games, wherever I am. Download it here: s666app8.
мелбет скачать мелбет скачать .
Для реализации крупномасштабных строительных проектов необходимо метизы оптом в больших количествах.
Купить крепеж оптом — это решение, которое может существенно снизить затраты на строительные или производственные проекты . Это связано с тем, что оптовые цены обычно ниже розничных. Крепежные элементы используются практически во всех отраслях промышленности, начиная от строительства и заканчивая автомобильной промышленностью . Поэтому, найти хорошего поставщика является важнейшим фактором. Оптимальным решением будет timать поставщика, который может предложить широкий выбор крепежных элементов по приемлемым ценам.
Оптовая покупка крепежа является очень выгодной, так как позволяет существенно уменьшить расходы . Это особенно важно для крупных проектов, где каждый рубль на счету. Закупка крепежа оптом дает возможность планировать работу без перебоев. Кроме того, При оптовых покупках можно договориться о более выгодных условиях и сроках поставки .
Поиск поставщика крепежа может занять много времени, если не знать, где его искать . Удобным способом найти поставщика крепежа является просмотр сайтов компаний, занимающихся продажей строительных материалов. Кроме того, Для поиска поставщика крепежа можно также посетить строительные выставки, где представлены многие компании-поставщики.
Приобретение крепежных элементов в большом количестве может существенно сократить расходы и повысить эффективность работы . Это связано с тем, что Купить крепеж оптом означает также обеспечить себя качественными материалами на долгий период . Поэтому, Оптовая покупка крепежных элементов — это один из шагов к успешному и прибыльному бизнесу .
Для тех, кто ищет экологически чистый и экономичный вариант, купить премиум машину становится всё более популярным решением.
Электромобили уже сегодня предлагают множество преимуществ по сравнению с традиционными транспортными средствами . Многие люди задумываются о покупке электромобиля. Электромобили имеют множество преимуществ, включая экономию денег и снижение вредного воздействия на окружающую среду .
Покупка электромобиля может стать правильным решением для тех, кто заботится об окружающей среде . Правительства различных стран стимулируют покупку электромобилей с помощью налоговых льгот.
Электромобили предлагают комфортную езду и минимизируют воздействие на окружающую среду . Одним из главных преимуществ электромобилей является экономия средств на топливо . Электромобили имеют меньше движущихся частей, что снижает риск поломок .
Электромобили предлагают гибкость и удобство зарядки. Некоторые производители электромобилей предлагают программы по обмену батарей.
При выборе электромобиля важно учитывать несколько факторов . Дальность хода электромобиля является одним из ключевых факторов . При покупке электромобиля следует учитывать такие факторы, как цена и доступные скидки .
На рынке представлены различные модели электромобилей от разных производителей . При приобретении электромобиля следует учитывать такие факторы, как уровень комфорта и безопасность.
В заключение, покупка электромобиля может быть отличным решением для тех, кто заботится об окружающей среде и хочет сэкономить на топливе . Электромобили представляют собой лучший вариант для тех, кто заботится о будущем планеты.
При выборе электромобиля необходимо учитывать все плюсы и минусы и выбрать подходящий вариант .
пансионат для детей http://shkola-onlajn1.ru .
регистрация в sykaaa casino При первом знакомстве Sykaaa Casino производит впечатление современного и, скажем так, “дерзкого” игрового портала. Дизайн яркий, местами даже немного вызывающий, но в целом удобный и интуитивно понятный. Навигация по сайту не вызывает затруднений, все основные разделы – от игр до поддержки – находятся под рукой. Это важно, когда хочется быстро перейти к делу и начать играть.
мелбет зеркало мелбет зеркало .
онлайн класс https://shkola-onlajn1.ru .
ставки 1win http://1win5522.ru
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Ознакомиться с отчётом – https://www.corsinistudiolegale.it/servizi
Этот обзор дает возможность взглянуть на историю и науку под новым углом. Мы представляем редкие факты, неожиданные связи и значимые события, которые помогут вам глубже понять развитие цивилизации и роль человека в ней.
Личный опыт — читайте сами – https://simranivfwellness.com/10-myths-about-fertility-treatments-you-need-to-stop-believing
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Практические советы ждут тебя – https://ngoaithatxanh.vn/phone
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый мог разобраться в предмете и извлечь из него максимум пользы.
Изучите внимательнее – https://vadraren.se/basta-basgarderoben-for-barn
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Получить дополнительную информацию – https://calltheshots.website/home/kinks-the-51e26e8900c66
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Кликни, не пожалеешь – https://www.defining-blog.ru/2025/10/20
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Хочешь знать всё? – https://plantlifedesigns.com/events/spring-plant-sale
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Открыть полностью – https://yogashala.vn/2021/10/25/yoga-vong
потолочкин потолки natyazhnye-potolki-samara-5.ru .
натяжные потолки цена нижний новгород https://www.natyazhnye-potolki-nizhniy-novgorod-4.ru .
купить натяжные потолки в самара недорого natyazhnye-potolki-samara-5.ru .
Выбор проекта должен основываться на семейных нуждах и планах на будущее.
проект дома одноэтажного https://gotovye-proekty-domov9.ru/1-etag/
натяжные потолки самара дешево http://www.natyazhnye-potolki-samara-5.ru .
Эта статья сочетает познавательный и занимательный контент, что делает ее идеальной для любителей глубоких исследований. Мы рассмотрим увлекательные аспекты различных тем и предоставим вам новые знания, которые могут оказаться полезными в будущем.
Обратиться к источнику – https://www.arteinox.net/2021/07/26/hello-world
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Хочу знать больше – https://www.speederman.com/how-close-are-we-to-autonomous-cars
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Детальнее – https://tecudi.com/produto/esfoliante-eletrico-para-os-pes
бездепозитные бонусы в казино казахстан
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Перейти к статье – https://kumaitea.com/fete-chocolates
Откройте для себя скрытые страницы истории и малоизвестные научные открытия, которые оказали колоссальное влияние на развитие человечества. Статья предлагает свежий взгляд на события, которые заслуживают большего внимания.
Изучить вопрос глубже – https://full-ott.com/liptv-en-2025
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Только факты! – https://saas4us.com/revolutionize-your-business-with-our-cutting-edge
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Не упусти важное! – https://triohrconsultancy.com/revolutionize-your-business-with-our-cutting-edge
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Кликни и узнай всё! – https://www.cordobaadiario.com/encontronazo-2
отзывы потолочкин натяжные потолки natyazhnye-potolki-nizhniy-novgorod-4.ru .
потолочкин отзывы natyazhnye-potolki-samara-5.ru .
натяжные потолки нижний новгород с установкой http://www.natyazhnye-potolki-nizhniy-novgorod-4.ru/ .
бездепозитные бонусы за регистрацию в казино с выводом без пополнения казахстан
move to Russia https://www.ielts-mentor.com/files/pgs/russian_visa_for_us_citizens_work__live_and_study_in_russia.html .
move to Russia https://www.actuabd.com/cookies/articles/?life_in_russia_a_guide_for_new_expats.html .
Если ваш старый пульт сломался или вы просто хотите обновить его до более современного и функционального варианта, то самое время универсальный пульт для смарт тв, который идеально подойдет для ваших потребностей и обеспечит комфортное управление вашим телевизором.
При покупке нового телевизора многие люди задумываются о необходимости покупки пульта для телевизора . Это связано с тем, что пульт для телевизора играет ключевую роль в управлении телевизором. Используя пульт, можно управлять телевизором, не вставая с места.
При выборе пульта для телевизора важно учитывать несколько факторов . Одним из ключевых моментов является совместимость пульта с вашим телевизором. Другим важным фактором является дизайн и эргономика пульта .
## Раздел 2: Типы пультов для телевизоров
На рынке представлены различные типы пультов для телевизоров, обладающие разными функциями . Один из наиболее популярных типов пультов – это пульт с инфракрасной связью. Этот тип пульта работает за счет передачи инфракрасного сигнала на телевизор.
Другим типом пульта является пульт с радиочастотным сигналом . Этот тип пульта использует радиочастотные волны для передачи сигнала на телевизор . Помимо этого, есть пульты с блютуз-соединением, которые позволяют управлять телевизором с помощью планшета.
## Раздел 3: Выбор пульта для телевизора
При выборе пульта для телевизора необходимо учитывать несколько факторов . Одним из ключевых моментов является совместимость пульта с вашим телевизором. Другим важным фактором является дизайн и эргономика пульта .
Также необходимо обратить внимание на функции пульта . Некоторые пульты имеют расширенные функции, такие как управление другими приборами. При приобретении пульта следует изучить отзывы других владельцев.
## Раздел 4: Заключение
В заключении, покупка пульта для телевизора является важным этапом в настройке домашнего кинотеатра . При выборе пульта необходимо учитывать несколько факторов, включая совместимость, дизайн и функциональность . С помощью правильного пульта можно повысить уровень комфорта при просмотре телевизора .
купить крепеж оптом – надежное решение для ваших строительных нужд.
С применением новых технологий, крепежные изделия обладают улучшенными характеристиками.
Moving to Russia http://www.maxwaugh.com/articles/can-i-move-to-russia-eligibility-requirements-and-qualification-guide-2025.html/ .
movetorussia com http://www.simplexts.net/pgs/how-to-choose-russian-immigration-agency-top-7-compared.html/ .
бездепозитные бонусы в казино онлайн
Если ваш старый пульт сломался или вы просто хотите обновить его до более современного и функционального варианта, то самое время купить пульт дистанционного управления, который идеально подойдет для ваших потребностей и обеспечит комфортное управление вашим телевизором.
Приобретая телевизор, важно подумать о покупке пульта для телевизора. Это связано с тем, что пульт для телевизора является неотъемлемой частью телевизионной системы . Используя пульт, можно управлять телевизором, не вставая с места.
При выборе пульта для телевизора важно учитывать несколько факторов . Одним из них является совместимость пульта с телевизором . Другим аспектом является дизайн и эргономичность пульта.
## Раздел 2: Типы пультов для телевизоров
Существует несколько типов пультов для телевизоров, каждый из которых имеет свои уникальные характеристики . Один из наиболее популярных типов пультов – это пульт с инфракрасной связью. Этот тип пульта работает за счет передачи инфракрасного сигнала на телевизор.
Другой тип пульта – это пульт, работающий на радиочастотном сигнале . Этот тип пульта передает сигнал на телевизор с помощью радиоволн . Помимо этого, есть пульты с блютуз-соединением, которые позволяют управлять телевизором с помощью планшета.
## Раздел 3: Выбор пульта для телевизора
При приобретении пульта для телевизора важно рассмотреть несколько ключевых аспектов. Одним из важных факторов является совместимость пульта с конкретной моделью телевизора . Другим моментом, на который стоит обратить внимание, является дизайн и удобство использования пульта .
Помимо этого, важно рассмотреть функциональные возможности пульта. Некоторые пульты имеют расширенные функции, такие как управление другими приборами. При приобретении пульта следует изучить отзывы других владельцев.
## Раздел 4: Заключение
В результате, покупка пульта для телевизора является необходимым этапом в установке телевизора. При покупке пульта следует обратить внимание на несколько моментов, включая совместимость, эргономику и функции . С помощью правильного пульта можно повысить уровень комфорта при просмотре телевизора .
1вин вывести деньги https://1win5511.ru/
Jestem pod wrażeniem twojej ekspertyzy.
пин ап скачать приложение пин ап скачать приложение
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Продолжить чтение – https://artecampo.tercerimpactoproducciones.com/index.php/2023/06/22/the-art-of-negotiation-tips-for-successful-business-deals
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый мог разобраться в предмете и извлечь из него максимум пользы.
Хочешь знать всё? – https://primenewsnet.com/now-is-the-time-to-think-about-your-small-business-success
Эта публикация дает возможность задействовать различные источники информации и представить их в удобной форме. Читатели смогут быстро найти нужные данные и получить ответы на интересующие их вопросы. Мы стремимся к четкости и доступности материала для всех!
Давай разберёмся досконально – http://www.fundacjaibs.pl/odcinek-13-imprezy-masowe-przygotowanie-obiektu
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Подробности по ссылке – http://hadafresearch.com/impact-factor
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Изучить эмпирические данные – https://foratata.com/cual-es-nuestra-mision
автоматические жалюзи для окон zhalyuzi-elektricheskie.ru .
электрокарнизы москва kupite-elektrokarniz.ru .
рулонные жалюзи на пластиковые окна купить рулонные жалюзи на пластиковые окна купить .
Для покупки полимерные флаконы можно обратиться напрямую к производителю или крупному поставщику, что позволит экономить на покупке и обеспечить качественный продукт для различных применений.
Флакон опт является идеальным решением для тех, кто ценит качество и экономию. Кроме того, покупка флакона в опте является выгодным решением для всех. Также флакон опт дает возможность приобрести лучший продукт по доступной цене. Кроме того, покупка флакона оптом позволяет приобрести необходимый продукт в большом количестве. Также флакон опт предлагает покупателям лучшее качество и удобство.
флакон опт дает возможность приобрести лучший продукт по доступной цене. Кроме того, покупка флакона в опте дает возможность приобрести лучший продукт по низкой цене. Также флакон опт предлагает покупателям лучшее качество и удобство. Кроме того, покупка флакона в опте дает возможность приобрести лучший продукт по низкой цене. Также флакон опт является лучшим решением для тех, кто ищет качественный и удобный продукт.
флакон опт необходимо выбирать исходя из качества и цены. Кроме того, покупка флакона в опте требует анализа качества и цены. Также Флакон опт должен быть выбран с учетом всех факторов и требований. Кроме того, покупка флакона оптом требует тщательного рассмотрения и сравнения вариантов. Также флакон опт является важным аспектом при выборе оптового продукта.
флакон опт является идеальным решением для тех, кто ценит качество и экономию. Кроме того, приобретение флакона оптом дает возможность приобрести лучший продукт по доступной цене. Также флакон опт широко используется среди покупателей оптовых товаров. Кроме того, покупка флакона оптом позволяет приобрести необходимый продукт в большом количестве. Также флакон опт предлагает покупателям лучшее качество и удобство.
Для тех, кто ищет выгодные предложения на ткани, ткани мелкий опт предлагает широкий выбор тканей по разумным ценам.
где купить оптом ткани можно в специализированных магазинах . Это связано с тем, что на рынке представлено множество различных поставщиков . При этом выбор правильного поставщика имеет решающее значение .
как крупные партии тканей стоят дешевле . Кроме того, как можно выбрать ткани разной текстуры и цвета . Это особенно важно где оптовые поставщики тканей могут предложить высококачественные материалы.
где можно найти огромное количество предложений . Кроме того, где обсудить условия сотрудничества. При этом где поддержать местный бизнес.
как найти необходимую информацию за короткое время . Кроме того, как узнать о надежных поставщиках . Это особенно важно где оптовые поставщики тканей могут предложить flexible условия работы.
где цена является важным аспектом. Кроме того, где найти информацию о компании. При этом где найти компанию с flexible условиями.
Проверка сертификатов и документов, подтверждающих качество тканей, также является обязательным шагом . Кроме того, взаимодействие с_customer поддержкой компании может дать представление о уровне обслуживания . Это особенно важно как найти надежного партнера является ключом к успеху .
как необходимо учитывать множество факторов . Кроме того, как можно сэкономить на ??иду и улучшить качество продукции . При этом как можно оставаться конкурентоспособными .
Будущее оптовой торговли тьмается перспективным, и как можно улучшить качество и доступность тканей . Кроме того, экологичность и устойчивость также станут ключевыми факторами в выборе оптового поставщика тканей . Это особенно важно как найти правильного поставщика является ключом к успеху .
бездепозитные бонусы в казино лев
электро жалюзи на окна стоимость zhalyuzi-elektricheskie.ru .
электрический карниз для штор купить kupite-elektrokarniz.ru .
купить рулонные шторы москва купить рулонные шторы москва .
1win akkaunt yaratish http://1win5512.ru
Чтобы освободить территорию после ремонта, вам поможет вывоз мусора со строительной площадки.
Необходимо не только выполнить задачи — важно правильно избавиться от отходов
автоматика для жалюзи купить автоматика для жалюзи купить .
электрокарниз двухрядный цена kupite-elektrokarniz.ru .
рулонные шторы на балконные окна shtory-s-elektroprivodom-rulonnye.ru .
электро жалюзи на пластиковые окна купить zhalyuzi-elektricheskie.ru .
электрические рулонные шторы купить электрические рулонные шторы купить .
электрокарниз купить в москве электрокарниз купить в москве .
1000 рублей за регистрацию вывод сразу без вложений в казино с выводом без депозита
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Всё, что нужно знать – https://www.potretberita.com/heboh-tokek-ini-harganya-150-miliar-lengkap-dengan-surat-pernyataan
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Ознакомьтесь поближе – https://playnewsdesk.com/verti-cbd-gummies-official-reviews
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Жми сюда — получишь ответ – https://healthbee.co.uk/1331-angel-number
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Ознакомиться с полной информацией – https://feitoparaela.com.br/2021/06/01/convivencia-na-pandemia-entre-maes-e-filhas
1win ishonchli saytmi 1win ishonchli saytmi
Вместо универсальных «капельниц на все случаи» мы собираем персональный план: состав инфузий, необходимость диагностик, частоту наблюдения и следующий шаг маршрута. Такой подход экономит время, снижает тревогу и даёт предсказуемый горизонт: что будет сделано сегодня, чего ждать завтра и какие критерии покажут, что идём по плану.
Детальнее – http://narkologicheskaya-klinika-himki0.ru
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Все материалы собраны здесь – https://www.cakrawarta.com/dinilai-meresahkan-ratusan-warga-tanda-tangani-petisi-penolakan-tempat-hiburan-malam-di-citraland.html
В этой статье собраны факты, которые освещают целый ряд важных вопросов. Мы стремимся предложить читателям четкую, достоверную информацию, которая поможет сформировать собственное мнение и лучше понять сложные аспекты рассматриваемой темы.
Узнать из первых рук – https://tmentor.ru/2023/06/22/mastering-time-management-key-to-business-success
Мы — частная наркологическая служба в Химках, где каждый шаг лечения объясняется простым языком и запускается без задержек. С первого контакта дежурный врач уточняет жалобы, длительность запоя, хронические диагнозы и принимаемые лекарства, после чего предлагает безопасный старт: выезд на дом, дневной формат или госпитализацию в стационар 24/7. Наши внутренние регламенты построены вокруг двух опор — безопасности и приватности. Мы используем минимально необходимый набор персональных данных, ограничиваем доступ к медицинской карте, сохраняем нейтральную коммуникацию по телефону и не ставим на учёт.
Получить дополнительные сведения – https://narkologicheskaya-klinika-himki0.ru/anonimnaya-narkologicheskaya-klinika-v-himkah
To idzie prosto do moich ulubionych.
Creez un espace cosy dans votre region avec pergola bioclimatique alu, parfait a tout moment de l’annee.
Pour garantir la longevite de votre structure, il est conseille de la nettoyer regulierement.
Мы — частная наркологическая служба в Химках, где каждый шаг лечения объясняется простым языком и запускается без задержек. С первого контакта дежурный врач уточняет жалобы, длительность запоя, хронические диагнозы и принимаемые лекарства, после чего предлагает безопасный старт: выезд на дом, дневной формат или госпитализацию в стационар 24/7. Наши внутренние регламенты построены вокруг двух опор — безопасности и приватности. Мы используем минимально необходимый набор персональных данных, ограничиваем доступ к медицинской карте, сохраняем нейтральную коммуникацию по телефону и не ставим на учёт.
Ознакомиться с деталями – http://narkologicheskaya-klinika-himki0.ru/
Вместо универсальных «капельниц на все случаи» мы собираем персональный план: состав инфузий, необходимость диагностик, частоту наблюдения и следующий шаг маршрута. Такой подход экономит время, снижает тревогу и даёт предсказуемый горизонт: что будет сделано сегодня, чего ждать завтра и какие критерии покажут, что идём по плану.
Углубиться в тему – kruglosutochnaya-narkologicheskaya-klinika
Вместо универсальных «капельниц на все случаи» мы собираем персональный план: состав инфузий, необходимость диагностик, частоту наблюдения и следующий шаг маршрута. Такой подход экономит время, снижает тревогу и даёт предсказуемый горизонт: что будет сделано сегодня, чего ждать завтра и какие критерии покажут, что идём по плану.
Ознакомиться с деталями – http://narkologicheskaya-klinika-himki0.ru/
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Получить дополнительную информацию – https://sotemingenieria.com/hola-mundo
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Где можно узнать подробнее? – https://jockeyclubrafaela.com.ar/tareas-de-reacondicionamiento-pista-central
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Погрузиться в детали – https://podcast.sceptici.ro/skeptical-reporter-2012-12-14
Если вы ищете качественные и стильные устройства для vaping, то hqd цена может стать вашим лучшим выбором, предлагая широкий выбор товаров и услуг по vaping, включая одноразовые устройства, различные вкусы и аксессуары.
Они представляют собой высококачественные устройства для vaping, созданные компанией HQD . Эти устройства очень удобны в использовании Они уже готовы к использованию прямо из коробки . HQD одноразки также очень безопасны Они соответствуют всем необходимым стандартам безопасности.
HQD одноразки имеют широкий выбор вкусов 20 различных вкусов на выбор . Эти устройства также очень компактны Их можно взять с собой куда угодно. HQD одноразки идеально подходят для тех, кто хочет попробовать вейпинг Они не требуют никакого опыта или знаний .
HQD одноразки имеют много преимуществ Они очень удобны и легки в использовании . Эти устройства также очень эффективны Они могут работать долгое время без перезарядки . HQD одноразки также очень безопасны Они соответствуют всем необходимым стандартам безопасности.
HQD одноразки идеально подходят для тех, кто хочет бросить курить Они могут помочь заменить привычку курения . Эти устройства также очень универсальны Они очень просты в использовании. HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Поскольку они очень просты в использовании .
HQD одноразки имеют широкий выбор вкусов Более 20 различных вкусов на выбор . Эти устройства также очень компактны Их можно легко положить в карман или сумку . HQD одноразки идеально подходят для тех, кто хочет попробовать разные вкусы Они не требуют никакого опыта или знаний .
HQD одноразки также имеют разные уровни никотина Уровни никотина варьируются в зависимости от вкуса . Эти устройства также очень экономичны Они могут быть использованы в течение долгого времени. HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Поскольку они очень просты в использовании .
HQD одноразки – это популярный выбор среди любителей вейпинга Они представляют собой высококачественные устройства для vaping, созданные компанией HQD . Эти устройства очень удобны в использовании Они уже готовы к использованию прямо из коробки . HQD одноразки также очень безопасны Они соответствуют всем необходимым стандартам безопасности.
HQD одноразки идеально подходят для тех, кто хочет попробовать вейпинг Они не требуют никакого опыта или знаний . Эти устройства также очень универсальны Они очень просты в использовании. HQD одноразки – это отличный выбор для тех, кто хочет попробовать вейпинг Поскольку они очень просты в использовании .
Формат
Детальнее – https://narkologicheskaya-klinika-lyubercy0.ru/anonimnaya-narkologicheskaya-klinika-v-lyubercah/
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Что скрывают от вас? – https://oquetarolando.com.br/rede-sesc-de-literatura-movimenta-goias-com-o-circuito-nacional-arte-da-palavra
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Не упусти шанс – https://birlik-akmola.kz/?p=9357
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый мог разобраться в предмете и извлечь из него максимум пользы.
Получить больше информации – https://www.ubytovaniepatince.sk/ale-ale-webova-stranka-a-novodoba-vizitka-neblaznite-2
бездепозитные бонусы в казино за регистрацию с выводом без пополнения
В этой публикации мы сосредоточимся на интересных аспектах одной из самых актуальных тем современности. Совмещая факты и мнения экспертов, мы создадим полное представление о предмете, которое будет полезно как новичкам, так и тем, кто глубоко изучает вопрос.
Узнать напрямую – https://sweetmacshop.com/2021/10/18/guide-to-the-perfect-fall-colored-macarons
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Узнать больше – https://crownval.com.ar/divisiones/tornillos-para-ligamento-cruzado
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Посмотреть подробности – https://simranivfwellness.com/10-myths-about-fertility-treatments-you-need-to-stop-believing
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Прочесть заключение эксперта – https://www.rolfing-planet.jp/2024/05/31/6%E6%9C%88%E3%81%AE%E7%A0%94%E4%BF%AE
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Открыть полностью – https://mylasergame.nl/hello-world
мелбет україна http://www.melbet5001.ru
Чтобы соотнести риски и плотность наблюдения до очного осмотра, удобнее всего взглянуть на одну сводную таблицу. Это не замена решению врача, но понятный ориентир для семьи: чем выше вероятность осложнений, тем плотнее мониторинг и быстрее доступ к коррекциям.
Подробнее можно узнать тут – наркологическая клиника отзывы
Формат
Разобраться лучше – narkologicheskaya-klinika-narkolog
Для крупных строительных проектов оптимальным решением будет приобретение заказать щебень известняковый, что позволит сэкономить средства и обеспечить необходимое качество строительных работ.
Щебень из известняка является ключевым компонентом многих строительных смесей. Этот материал используется для создания прочных и долговечных конструкций. Известняковый щебень, купленный оптом, может существенно повлиять на сокращение затрат на стройматериалы.
Известняковый щебень в больших количествах позволяет реализовывать масштабные проекты . Оптовая продажа известнякового щебня осуществляется через официальные дилерские сети .
Основными преимуществами известнякового щебня являются его долговечность и экологичность . Известняковый щебень используется в строительстве благодаря своим техническим преимуществам. Оптовая покупка известнякового щебня позволяет получить скидки и экономить средства .
Известняковый щебень, купленный оптом, используется для дорожного строительства. Приобретение известнякового щебня в больших количествах позволяет повысить эффективность строительных работ .
Известняковый щебень используется в дорожном строительстве для создания прочных и долговечных покрытий . Известняковый щебень характеризуется универсальностью применения . Приобретение оптом известнякового щебня дает возможность получить щебень для реализации индивидуальных проектов .
Известняковый щебень в оптовых партиях может быть доставлен на строительную площадку . Оптовая продажа известнякового щебня осуществляется через специализированные онлайн-платформы .
Щебень из известняка используется в различных отраслях промышленности . Приобретение оптом известнякового щебня дает возможность сократить расходы на материалы . Оптовые закупки известнякового щебня предназначены для крупномасштабных проектов .
Известняковый щебень в оптовых партиах доступен для заказа на производственных предприятиях. Приобретение оптом известнякового щебня дает возможность получить щебень для реализации индивидуальных проектов .
гидроизоляция подвала цена гидроизоляция подвала цена .
гидроизоляция подвала москва гидроизоляция подвала москва .
гидроизоляция подвала цена за м2 гидроизоляция подвала цена за м2 .
Формат
Детальнее – http://narkologicheskaya-klinika-lyubercy0.ru/narkologicheskaya-klinika-na-dom-v-lyubercah/https://narkologicheskaya-klinika-lyubercy0.ru
бонус за регистрацию без депозита в казино
1win yordam markazi 1win yordam markazi
внутренняя гидроизоляция подвала внутренняя гидроизоляция подвала .
ремонт подвала ремонт подвала .
гидроизоляция цена за метр gidroizolyacziya-czena5.ru .
Откройте для себя скрытые страницы истории и малоизвестные научные открытия, которые оказали колоссальное влияние на развитие человечества. Статья предлагает свежий взгляд на события, которые заслуживают большего внимания.
Это стоит прочитать полностью – https://vaibhavdeshpande.com/hello-world
This is the guide I wish existed years ago.
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Ознакомиться с отчётом – http://retirementbenefitscounsellor.co.za/wp/retirement-benefits-counsellor-in-the-media/financial-mail-p1
Контроль
Детальнее – https://narkologicheskaya-klinika-lyubercy0.ru/anonimnaya-narkologicheskaya-klinika-v-lyubercah/
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Детальнее – https://www.car-info.com/es/model/honda/civic/civic-coupe-viii/1-8i-140-hp
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Неизвестные факты о… – https://nongcothanhbinh.com/vestibulum-bibendum-dolor-sit
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Перейти к статье – https://plankydigital.com/blog/top-5-free-seo-tools
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Изучить аспект более тщательно – https://thegolfperformancecenter.com/5-elements-blog/get-your-proper-zzzs
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Читать далее > – https://propertyinvestpartners.com/our-work-culture
Этот обзор дает возможность взглянуть на историю и науку под новым углом. Мы представляем редкие факты, неожиданные связи и значимые события, которые помогут вам глубже понять развитие цивилизации и роль человека в ней.
Кликни и узнай всё! – https://congresociudad.uc3m.es/2017/03/14/espacio-urbano
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Что скрывают от вас? – https://shakthiiacademy.com/course/online-police-constable-exam-coaching-12-month
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Секреты успеха внутри – https://crickpicks.com/new-zealand-vs-sri-lanka-dream-11-picks
В этой статье собраны факты, которые освещают целый ряд важных вопросов. Мы стремимся предложить читателям четкую, достоверную информацию, которая поможет сформировать собственное мнение и лучше понять сложные аспекты рассматриваемой темы.
Обратитесь за информацией – https://dbdnews.net/archives/1738
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Не упусти шанс – https://patriciafaro.com.br/fotobiomodulacao-da-teoria-a-pratica
вертикальная гидроизоляция подвала вертикальная гидроизоляция подвала .
ремонт подвала ремонт подвала .
услуги гидроизоляции подвала gidroizolyacziya-czena5.ru .
внутренняя гидроизоляция подвала внутренняя гидроизоляция подвала .
гидроизоляция цена за метр gidroizolyacziya-czena5.ru .
гидроизоляция подвала москва гидроизоляция подвала москва .
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Уточнить детали – https://tradewithmac.org/boes-governor-comments-on-the-likelihood-of-increasing-interest-rate-hikes
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Узнать больше > – https://blackrockmotorcompany.co.uk/2015-15-mercedes-benz-c250d-amg-line-premium-plus-auto-saloon-132000-miles-10295
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Изучить эмпирические данные – https://echizenyaclinic.jp/general_interview_sheet
https://sykaaa-casino-website.fun
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Раскрыть тему полностью – http://vinamgroup.com.vn/what-things-to-get-partner-for-wedding-anniversary-gifts
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Ознакомьтесь с аналитикой – https://www.digilink.africa/hello-world
Алгоритм гибкий: при изменении самочувствия мы донастраиваем схему и интенсивность наблюдения без пауз в лечении.
Выяснить больше – платная наркологическая клиника
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Получить полную информацию – https://www.dissomarket.com/decouvrez-lart-des-amuse-bouches-un-voyage-culinaire-en-quelques-bouchees
Формат
Ознакомиться с деталями – наркологическая клиника стационар
В этой статье собраны факты, которые освещают целый ряд важных вопросов. Мы стремимся предложить читателям четкую, достоверную информацию, которая поможет сформировать собственное мнение и лучше понять сложные аспекты рассматриваемой темы.
Что скрывают от вас? – https://byerstechnicalinstitute.com/home/welding
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Выяснить больше – https://ipkd.tabanankab.go.id/konsultasi-publik-ranwal-rkpd-sb-kabupaten-tabanan-2024
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Ознакомиться с отчётом – https://www.anamarialajusticiabolivia.com/diferencia-entre-carbonato-de-magnesio-y-cloruro-de-magnesio
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Ознакомиться с теоретической базой – https://aki-s.de/2021/01/13/getrankelieferant-fur-hochzeiten-in-stuttgart
Алгоритм гибкий: при изменении самочувствия мы донастраиваем схему и интенсивность наблюдения без пауз в лечении.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-himki0.ru/anonimnaya-narkologicheskaya-klinika-v-himkah/
Чтобы соотнести риски и плотность наблюдения до очного осмотра, удобнее всего взглянуть на одну сводную таблицу. Это не замена решению врача, но понятный ориентир для семьи: чем выше вероятность осложнений, тем плотнее мониторинг и быстрее доступ к коррекциям.
Разобраться лучше – https://narkologicheskaya-klinika-lyubercy0.ru/anonimnaya-narkologicheskaya-klinika-v-lyubercah/
Вместо универсальных «капельниц на все случаи» мы собираем персональный план: состав инфузий, необходимость диагностик, частоту наблюдения и следующий шаг маршрута. Такой подход экономит время, снижает тревогу и даёт предсказуемый горизонт: что будет сделано сегодня, чего ждать завтра и какие критерии покажут, что идём по плану.
Узнать больше – https://narkologicheskaya-klinika-himki0.ru/narkologicheskaya-klinika-stoimost-v-himkah/
Your blog is a beacon of quality content.
Вместо универсальных «капельниц на все случаи» мы собираем персональный план: состав инфузий, необходимость диагностик, частоту наблюдения и следующий шаг маршрута. Такой подход экономит время, снижает тревогу и даёт предсказуемый горизонт: что будет сделано сегодня, чего ждать завтра и какие критерии покажут, что идём по плану.
Углубиться в тему – narkologicheskaya-klinika-otzyvy
Когда подходит
Получить дополнительные сведения – наркологическая клиника стационар
Мы — частная наркологическая служба в Химках, где каждый шаг лечения объясняется простым языком и запускается без задержек. С первого контакта дежурный врач уточняет жалобы, длительность запоя, хронические диагнозы и принимаемые лекарства, после чего предлагает безопасный старт: выезд на дом, дневной формат или госпитализацию в стационар 24/7. Наши внутренние регламенты построены вокруг двух опор — безопасности и приватности. Мы используем минимально необходимый набор персональных данных, ограничиваем доступ к медицинской карте, сохраняем нейтральную коммуникацию по телефону и не ставим на учёт.
Изучить вопрос глубже – наркологическая клиника цены
Старт — короткий скрининг с дежурным врачом: выясняем риски и бытовые условия, чтобы заранее выбрать формат, который будет и безопасным, и выполнимым в реальности. Согласуем окно визита или приёма с учётом трафика и подъезда; подсказываем, как подготовить помещение — тишина, вода, розетка, возможность прилечь. На месте фиксируем витальные показатели (АД, пульс, сатурация, температура), при показаниях делаем ЭКГ, запускаем детокс и озвучиваем ожидаемую «нормальную динамику» первых 6–12 часов. Все договорённости дублируем в памятке: режим, питьевой план, «красные флажки» и точное время контрольной связи. Если домашний формат перестаёт быть достаточным, переводим в стационар без пауз — темп лечения не теряется.
Ознакомиться с деталями – https://narkologicheskaya-klinika-lyubercy0.ru/anonimnaya-narkologicheskaya-klinika-v-lyubercah
Посетите магазин велосипедов сегодня и найдите велосипед своей мечты!
Магазин велосипедов является местом, где можно найти широкий выбор велосипедов для любого возраста и уровня подготовки . Это место, где покупатели могут найти не только велосипеды, но и различные аксессуары и оборудование для них. Магазин велосипедов открыт для посетителей в любое время и приглашает всех любителей велосипедов к себе .
Магазин велосипедов имеет современный дизайн и комфортную обстановку, которая позволяет клиентам чувствовать себя расслабленно . Клиенты могут попробовать велосипеды перед покупкой, чтобы убедиться, что они подходят им идеально. Магазин велосипедов имеет профессиональный инструмент для ремонта и настройки велосипедов .
Магазин велосипедов имеет разнообразный ассортимент велосипедов, включая горные, шоссейные и городские модели . Каждая модель имеет свои уникальные характеристики и особенности. Магазин велосипедов имеет большой sklad с запасами и может быстро удовлетворять заказы клиентов.
Магазин велосипедов также предлагает широкий выбор аксессуаров и оборудования для велосипедов, включая шлемы, перчатки и одежду . Клиенты могут найти все, что им нужно для комфортного и безопасного?жения. Магазин велосипедов регулярно проводит акции и распродажи, что позволяет клиентам приобретать продукцию по выгодным ценам .
Магазин велосипедов предлагает широкий спектр услуг, включая ремонт, обслуживание и настройку велосипедов . Клиенты могут быть уверены в высоком качестве выполненных работ. Магазин велосипедов предлагает услуги по доставке и установке запчастей и аксессуаров.
Магазин велосипедов приглашает опытных тренеров и инструкторов для проведения занятий . Клиенты могут получить новые знания и навыки, что позволит им улучшить свое?жение. Магазин велосипедов участвует в организации велосоревнований и поддерживает местный велоспорт.
Магазин велосипедов является идеальным местом для всех, кто любит велоспорт и активный отдых . Клиенты могут найти все, что им нужно для комфортного и безопасного?жения. Магазин велосипедов всегда готов помочь и предоставить консультацию по любым вопросам.
Магазин велосипедов предлагает выгодные цены и акции, что позволяет клиентам приобретать продукцию по доступным ценам . Клиенты могут быть уверены в высоком качестве продукции и услуг. Магазин велосипедов всегда готов к инновациям и улучшению своей работы.
перевод с английского бюро dzen.ru/a/aUBBvahMInGNj8BL .
кодирование от алкоголизма [url=https://vyvod-iz-zapoya-4.ru/]кодирование от алкоголизма[/url] .
срочный вывод из запоя москва [url=https://vyvod-iz-zapoya-5.ru/]vyvod-iz-zapoya-5.ru[/url] .
Looking for a casino? elon casino top: slots, live casino, bonus offers, and tournaments. We cover the rules, wagering requirements, withdrawals, and account security. Please review the terms and conditions before playing.
Контроль
Разобраться лучше – http://narkologicheskaya-klinika-lyubercy0.ru/
Вместо универсальных «капельниц на все случаи» мы собираем персональный план: состав инфузий, необходимость диагностик, частоту наблюдения и следующий шаг маршрута. Такой подход экономит время, снижает тревогу и даёт предсказуемый горизонт: что будет сделано сегодня, чего ждать завтра и какие критерии покажут, что идём по плану.
Разобраться лучше – http://www.domen.ru
вывод из запоя анонимно москва вывод из запоя анонимно москва .
Если вам нужно полимерные флаконы для ваших товаров, обратите внимание на различные варианты, доступные на рынке, и выбирайте то, что лучше всего соответствует потребностям вашего бизнеса.
Флакон опт является идеальным решением для бизнеса, производящего жидкие товары . Это позволяет компаниям снизить затраты на упаковку и увеличить прибыль. Флакон опт является универсальной упаковкой для жидких продуктов. Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт используется многими компаниями для упаковки своих продуктов . Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт обеспечивает безопасное и надежное хранение жидких товаров . Кроме того, флакон опт может быть легко заполнен и закрыт.
Флакон опт обеспечивает высокую степень защиты продукта. Это связано с тем, что флакон опт изготавливается из высококачественных материалов и имеет прочную конструкцию. Флакон опт позволяет компаниям создавать уникальный дизайн и стиль . Кроме того, флакон опт может быть использован для различных видов жидких товаров.
Флакон опт стал популярным выбором среди экологически сознательных потребителей . Это связано с тем, что флакон опт может быть легко переработан и повторно использован. Флакон опт обеспечивает безопасное и надежное хранение жидких товаров . Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт является универсальной упаковкой для жидких продуктов. Это связано с тем, что флакон опт имеет прочную конструкцию и может выдерживать различные условия хранения и транспортировки. Флакон опт защищает продукты от солнечного света и влаги. Кроме того, флакон опт может быть легко заполнен и закрыт.
Флакон опт является предпочтительным вариантом для бизнеса, занимающегося жидкими товарами. Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт также предлагает улучшенную безопасность для потребителей . Кроме того, флакон опт может быть легко транспортирован и хранен.
Флакон опт обеспечивает высокую степень защиты продукта. Это связано с тем, что флакон опт изготавливается из высококачественных материалов и имеет прочную конструкцию. Флакон опт также может быть легко персонализирован и брендирован . Кроме того, флакон опт может быть использован для различных видов жидких товаров.
Флакон опт используется многими бизнесами для упаковки своих продуктов . Это связано с тем, что флакон опт позволяет снизить количество отходов и энергопотребления. Флакон опт обеспечивает безопасное и надежное хранение жидких товаров .
вывод из запоя на дому москва круглосуточно вывод из запоя на дому москва круглосуточно .
Контроль
Ознакомиться с деталями – narkologicheskaya-klinika-stacionar
Мы — частная наркологическая служба в Химках, где каждый шаг лечения объясняется простым языком и запускается без задержек. С первого контакта дежурный врач уточняет жалобы, длительность запоя, хронические диагнозы и принимаемые лекарства, после чего предлагает безопасный старт: выезд на дом, дневной формат или госпитализацию в стационар 24/7. Наши внутренние регламенты построены вокруг двух опор — безопасности и приватности. Мы используем минимально необходимый набор персональных данных, ограничиваем доступ к медицинской карте, сохраняем нейтральную коммуникацию по телефону и не ставим на учёт.
Получить дополнительную информацию – platnaya-narkologicheskaya-klinika
Старт — короткий скрининг с дежурным врачом: выясняем риски и бытовые условия, чтобы заранее выбрать формат, который будет и безопасным, и выполнимым в реальности. Согласуем окно визита или приёма с учётом трафика и подъезда; подсказываем, как подготовить помещение — тишина, вода, розетка, возможность прилечь. На месте фиксируем витальные показатели (АД, пульс, сатурация, температура), при показаниях делаем ЭКГ, запускаем детокс и озвучиваем ожидаемую «нормальную динамику» первых 6–12 часов. Все договорённости дублируем в памятке: режим, питьевой план, «красные флажки» и точное время контрольной связи. Если домашний формат перестаёт быть достаточным, переводим в стационар без пауз — темп лечения не теряется.
Детальнее – chastnaya-narkologicheskaya-klinika
вывод из запоя в москве вывод из запоя в москве .
анонимный вывод из запоя в москве vyvod-iz-zapoya-5.ru .
вывод. из. запоя. анонимно. москва. vyvod-iz-zapoya-4.ru .
прерывание запоя москва vyvod-iz-zapoya-5.ru .
дизайн бюро дизайн бюро петербург
синхронный перевод telegra.ph/Trebovaniya-k-sinhronnomu-perevodchiku-navyki-sertifikaty-opyt–i-pochemu-ehto-vazhno-12-16 .
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Слушай внимательно — тут важно – https://quasia.net/information/20230110
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Секреты успеха внутри – https://www.defining-blog.ru/category/nedvizhimost
В этой статье собраны факты, которые освещают целый ряд важных вопросов. Мы стремимся предложить читателям четкую, достоверную информацию, которая поможет сформировать собственное мнение и лучше понять сложные аспекты рассматриваемой темы.
Откройте для себя больше – https://inyoutube.net/partnery
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Детали по клику – https://qualitytools.co.ug/index.php/2021/10/25/hello-world
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Подробнее можно узнать тут – https://sportowagdynia.eu/index.php/2020/10/05/na-koniec-sezonu-zwyciestwo-w-tarnowie
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Уникальные данные только сегодня – https://www.defining-blog.ru/tag/tehnologii
Эта статья для ознакомления предлагает читателям общее представление об актуальной теме. Мы стремимся представить ключевые факты и идеи, которые помогут читателям получить представление о предмете и решить, стоит ли углубляться в изучение.
Лучшее решение — прямо здесь – https://www.realty-key.ru/themes/media
Читатель отправляется в интеллектуальное путешествие по самым ярким событиям истории и важнейшим научным открытиям. Мы раскроем тайны эпох, покажем, как идеи меняли миры, и объясним, почему эти знания остаются актуальными сегодня.
Открой скрытое – https://dainikup.com/changed-seat-of-swami-prasad-maurya-who-came-to-sp-leaving-bjp-got-ticket-from-fazilnagar-instead-of-kushinagar
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Изучить рекомендации специалистов – https://ler.app.br/vamos-continuar-ajudando
цифровой маркетинг статьи seo-blog9.ru .
статьи про маркетинг и seo seo-blog8.ru .
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
См. подробности – https://gothamdoughnuts.com/post/indulge-in-these-irresistible-doughnuts-in-melbourne
Underbart förklarat, lätt att följa.
seo статьи seo статьи .
интернет маркетинг статьи интернет маркетинг статьи .
маркетинговые стратегии статьи маркетинговые стратегии статьи .
Если вы ищете выгодные варианты заказать установку откосов на окна из сэндвич панелей, то профессиональный монтаж под ключ сделает ваш дом уютнее и теплее.
Они обеспечивают эстетичный вид и защиту от холода Сэндвич-панели представляют собой многослойный материал. Они построены из слоев, включая теплоизолятор и защитную оболочку. Установка откосов из сэндвич-панелей популярна благодаря своей простоте. Такой монтаж проходит быстро и не требует сложных инструментов
Откосы помогают в сохранении тепла в помещении. Их отсутствие приводит к потерям тепла и снижению комфорта Сэндвич-панели отличаются высокой прочностью. Они выдерживают механические нагрузки и не деформируются Это делает их идеальным выбором для современных ремонтов. Они предлагают баланс между стоимостью и качеством
Сэндвич-панели обеспечивают отличную теплоизоляцию. Они минимизируют теплопотери через оконные проемы Материал устойчив к влаге и грибку. Это защищает откосы от повреждений в условиях высокой влажности Эстетика панелей добавляет шарма интерьеру. Панели улучшают общий вид помещения за счет своей привлекательности.
Установка сэндвич-панелей экономит время. Это позволяет завершить работы за короткий срок Стоимость материалов остается доступной. Цена на них остается конкурентной на рынке. Это делает их популярным решением для ремонта. Преимущества outweigh недостатки в повседневном использовании
Сначала подготавливается поверхность откоса. Эта стадия включает очистку и выравнивание основания Затем нарезаются панели по требуемым размерам. Подготовленные панели упрощают дальнейший монтаж. После этого они фиксируются с помощью крепежа. Фиксация происходит с использованием специальных элементов
Важно использовать качественные инструменты. Это минимизирует риск ошибок во время работы Финальный этап включает отделку швов. Завершающие работы придают откосам аккуратный вид. Такой подход обеспечивает долговечность. Качественный процесс гарантирует отсутствие дефектов.
Цена установки откосов из сэндвич-панелей зависит от площади. Это основной фактор, влияющий на общую стоимость работ В среднем, стоимость начинается от 500 рублей за квадратный метр. Указанная сумма покрывает базовые этапы монтажа. Дополнительные факторы повышают итоговую цену. Влияние факторов делает расчет индивидуальным
Региональные различия влияют на ценообразование. В больших городах услуги стоят дороже из-за спроса Рекомендуется сравнивать предложения. Это помогает выбрать оптимальный вариант без переплат В итоге, установка окупается за счет долговечности. Выгодность проявляется в снижении будущих расходов.
сео продвижение по трафику clover prodvizhenie-sajta-po-trafiku1.ru .
интернет маркетинг статьи интернет маркетинг статьи .
Откройте для себя многофункциональный кроссовер спортивный тренажер, который идеально подойдет для интенсивных тренировок в зале или дома.
Определите подходящий уровень сопротивления
веб-аналитика блог seo-blog8.ru .
Если вы планируете реконструкция загородного дома под ключ цены, наша компания предлагает профессиональные услуги по обновлению вашего жилья.
Обновление жилища включает в себя меры по модернизации и восстановлению ветхого строения.
Использование вторичных ресурсов снижает количество мусора.
Первый шаг — тщательный осмотр здания на наличие дефектов.
Она повышает комфорт и безопасность проживания.
маркетинговый блог маркетинговый блог .
which internet partner prodvizhenie-sajta-po-trafiku1.ru .
Нужен трафик и лиды? avigroup SEO-оптимизация, продвижение сайтов и реклама в Яндекс Директ: приводим целевой трафик и заявки. Аудит, семантика, контент, техническое SEO, настройка и ведение рекламы. Работаем на результат — рост лидов, продаж и позиций.
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Узнайте всю правду – https://sinzitusoku.com/kisidabaidentu-syo
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Подробнее – вывод из запоя дешево
Главная задача процедуры — быстрое выведение этанола и его метаболитов из организма, нормализация уровня электролитов, улучшение самочувствия и предотвращение осложнений. Лечение проводится как в клинике, так и на дому, что особенно удобно при тяжёлых состояниях, когда пациент не может самостоятельно добраться до медицинского учреждения.
Подробнее – вывод из запоя на дому круглосуточно в тюмени
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Подробности по ссылке – https://primenewsnet.com/are-you-ready-complete-recap-of-the-streer-rally-action-shootout
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Жми сюда — получишь ответ – https://buscatrabajosenlinea.com/colgate-oportunidad-de-trabajo
маркетинговый блог seo-blog8.ru .
В этой статье вы найдете уникальные исторические пересечения с научными открытиями. Каждый абзац — это шаг к пониманию того, как наука и события прошлого создают основу для технологического будущего.
Доступ к полной версии – https://www.defining-blog.ru/2025/10/18
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Уникальные данные только сегодня – https://bsbdiesel.com.br/from-idea-to-execution-a-startup-journey
статьи про продвижение сайтов статьи про продвижение сайтов .
Процесс включает несколько шагов:
Углубиться в тему – [url=https://narkolog-na-dom-v-ufe17.ru/]нарколог на дом цены[/url]
Вывод из запоя — это экстренная медицинская помощь, направленная на очищение организма от алкоголя, снятие симптомов интоксикации и восстановление работы внутренних органов. В клинике «Трезвая Линия Волгоград» используется комплексный подход, включающий капельницы, препараты для детоксикации и постоянный врачебный контроль. Лечение проводится анонимно, с индивидуальным подбором медикаментов и поддержкой пациента на каждом этапе восстановления. Главная цель специалистов — не просто стабилизировать состояние, а обеспечить безопасное возвращение к нормальному самочувствию и предотвратить повторные срывы.
Ознакомиться с деталями – скорая вывод из запоя волгоград
Вывод из запоя в Тольятти — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормального состояния здоровья. Длительное употребление спиртных напитков приводит к серьёзной интоксикации, нарушению работы нервной, сердечно-сосудистой и пищеварительной систем. Самостоятельные попытки прекратить запой могут быть опасны, поэтому оптимальным решением является обращение к врачу-наркологу, который проведёт лечение безопасно и эффективно.
Получить больше информации – вывод из запоя цена в тольятти
Капельница от запоя — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Выяснить больше – анонимный вывод из запоя химки
Кодирование от алкоголизма в Люберцах. Мы предлагаем различные методы кодирования, подходящие для каждого пациента.
Получить дополнительные сведения – капельница от запоя цена московская область
Капельница от запоя в стационаре — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Углубиться в тему – нарколог на дом вывод из запоя
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Детальнее – наркологические клиники алкоголизм в омске
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Получить дополнительную информацию – вывод из запоя клиника рязань
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Разобраться лучше – http://narkolog-na-dom-v-ufe17.ru
Вывод из запоя у пожилых людей в Химках. Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Выяснить больше – вывод из запоя на дому цена
трафиковое продвижение сайта prodvizhenie-sajta-po-trafiku1.ru .
Снятие ломки при алкоголизме в Люберцах. Наши специалисты помогут вам справиться с симптомами абстиненции.
Подробнее – капельница от запоя выезд
Вывод из запоя у подростков в стационаре Балашихи. Мы предлагаем специализированное лечение для подростков, учитывая их возрастные особенности.
Детальнее – нарколог вывод из запоя балашиха
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Получить дополнительные сведения – https://clinicalupselo.com.br/ola-mundo
Именно поэтому при затяжных запоях необходима квалифицированная медицинская помощь, позволяющая безопасно и максимально комфортно прекратить приём алкоголя. Клиника «Стратегия Здоровья» предлагает профессиональный вывод из запоя в Москве как в условиях стационара, так и с выездом на дом. Врачи работают круглосуточно, используя проверенные методики детоксикации и медикаментозной поддержки.
Углубиться в тему – https://narko-reabcentr.ru/vyvod-iz-zapoya-na-domu-v-moskve/
Клиника «ВоронежМед Альянс» придерживается принципа прозрачной медицины: каждый шаг понятен пациенту, решения принимаются совместно, а результаты фиксируются по объективным показателям. Такой формат создаёт чувство безопасности и доверия. Среди основных принципов:
Ознакомиться с деталями – https://narcologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-anonimno
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Ознакомиться с деталями – экстренная наркологическая помощь
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Получить дополнительные сведения – клиника кодирования от алкоголизма
Благодаря этому подходу пациент выходит из состояния запоя без стресса и с минимальной нагрузкой на организм, что ускоряет процесс восстановления.
Ознакомиться с деталями – https://vyvod-iz-zapoya-v-krasnoyarske17.ru/vyvedenie-iz-zapoya-krasnoyarsk
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Выяснить больше – http://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkolog-v-gorode-novokuzneczke/
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Подробнее тут – вывод из запоя круглосуточно
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Разобраться лучше – http://narcologicheskaya-klinika-v-novokuzneczke17.ru
Капельница от запоя — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Узнать больше – поставить капельницу от запоя в люберцах
Город с протяжёнными магистралями и разноскоростными районами требует особой организации маршрутов. Выездные бригады «ВолгаДок Медикал» работают в режиме 24/7, прибывают в гражданской одежде, избегают громких звонков и используют «немаркированные» подъезды. Перед приездом мы просим подготовить пространство: приглушить верхний свет, обеспечить приток свежего воздуха без сквозняков, подготовить ровную поверхность под укладку и удлинитель, перевести телефоны в «без уведомлений» с «белым списком» близких. Это позволяет в первые минуты сосредоточиться на клинике, а не на бытовых вопросах.
Получить дополнительные сведения – платная наркологическая клиника саратов
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Подробнее – наркология вывод из запоя в новокузнецке
Круглосуточная наркологическая скорая помощь в Москве от клиники «Частный Медик 24». Наша команда работает 24/7, обеспечивая доступность медицинской помощи в любое время суток.
Подробнее можно узнать тут – экстренная наркологическая помощь
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Смотрите также… – https://vishwahindisangathan.com/%E0%A4%B9%E0%A4%BF%E0%A4%82%E0%A4%A6%E0%A5%80-%E0%A4%B8%E0%A4%BF%E0%A4%A8%E0%A5%87%E0%A4%AE%E0%A4%BE-%E0%A4%95%E0%A5%87-%E0%A4%AC%E0%A4%A2%E0%A4%BC%E0%A4%A4%E0%A5%87-%E0%A4%9A%E0%A4%B0%E0%A4%A3
Лечение запоя без госпитализации в Люберцах. Мы предлагаем лечение на дому, без необходимости госпитализации.
Получить дополнительные сведения – капельница от запоя цена город. московская область
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Выяснить больше – http://vivod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-volgograd/
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Выяснить больше – http://narcologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-czena/
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Получить дополнительную информацию – http://www.domen.ru
Стационарное лечение запоя в Балашихе — эффективное решение для длительного запоя. Мы предлагаем индивидуальный подход и комплексную терапию для каждого пациента.
Исследовать вопрос подробнее – вывод из запоя в стационаре балашиха
digital маркетинг блог digital маркетинг блог .
Основу выездного лечения составляют капельницы, которые позволяют быстро ввести препараты в кровоток, минуя желудочно-кишечный тракт. Это обеспечивает моментальное действие и исключает раздражение слизистой. Капельницы подбираются индивидуально в зависимости от состояния пациента. Основные направления инфузионной терапии включают детоксикацию, восстановление водно-солевого баланса и поддержку работы нервной системы. Для усиления эффекта применяются витамины, антиоксиданты и препараты для защиты печени.
Подробнее можно узнать тут – http://narkolog-na-dom-v-voronezhe17.ru/voronezh-narkologiya/
сео продвижение по трафику сео продвижение по трафику .
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Узнать больше – вывод из запоя на дому цена в саратове
Каждый этап проходит под контролем врачей-наркологов и психотерапевтов, что гарантирует эффективность и безопасность лечения.
Ознакомиться с деталями – анонимная наркологическая клиника новокузнецк
Помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Подробнее тут – анонимная наркологическая помощь москве
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Изучить вопрос глубже – вывод из запоя капельница в волгограде
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Подробности по ссылке – https://hajjcompanions.com/understanding-the-different-types-of-hajj-packages-for-us-pilgrims
Перед процедурой врач оценивает состояние пациента, измеряет давление, пульс и уровень насыщения крови кислородом. После осмотра подбирается состав инфузии, включающий препараты для дезинтоксикации, восстановления водно-солевого баланса и нормализации работы органов. Введение растворов осуществляется внутривенно, под контролем специалиста. Длительность процедуры — от 40 минут до 1,5 часов.
Подробнее можно узнать тут – http://kapelnicza-ot-zapoya-v-volgograde17.ru
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Углубиться в тему – http://narkologicheskaya-klinika-v-volgograde17.ru
Вывод из запоя в Химках — профессиональная помощь на дому. Наши опытные наркологи приедут к вам домой и проведут все необходимые процедуры для скорейшего облегчения состояния и вывода из запоя.
Узнать больше – вывод из запоя дешево химки
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Открой скрытое – https://stylianosmpellos.gr/%CE%B4%CE%B9%CF%83%CE%BA%CE%BF%CE%B3%CF%81%CE%B1%CF%86%CE%AF%CE%B1/dimotiki-anthologia-no3-2
Лечение пивного алкоголизма в Люберцах. Мы предлагаем эффективные методы лечения зависимости от пива.
Подробнее тут – вызвать капельницу от запоя на дому
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Получить дополнительную информацию – вызов нарколога на дом
Лечение запоя без госпитализации в Люберцах. Мы предлагаем лечение на дому, без необходимости госпитализации.
Детальнее – капельница от запоя выезд
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-saratov0.ru/vyvod-iz-zapoya-saratov-na-domu
Gave 777tez a go. Nothing groundbreaking, but it’s a decent distraction. Worth a look if you’re looking for something new to try. 777tez
Лечение зависимости от алкоголя у мужчин в Люберцах. Мы предлагаем индивидуальный подход к лечению мужчин, учитывая все особенности организма.
Подробнее тут – капельница от запоя в люберцах
Лечение зависимости от алкоголя на дому в Химках. Наши специалисты приедут к вам домой и проведут все необходимые процедуры.
Детальнее – наркологический вывод из запоя
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Детальнее – наркологическая клиника клиника помощь в саратове
Снятие ломки при алкоголизме в Химках. Наши специалисты помогут вам справиться с симптомами абстиненции.
Получить дополнительные сведения – вывод из запоя цена химки
В таблице приведены основные компоненты инфузионной терапии, применяемые при детоксикации:
Исследовать вопрос подробнее – наркологическая клиника
Лечение основывается на комплексном подходе, позволяющем учесть особенности организма и стаж злоупотребления алкоголем. Обычно процедура состоит из нескольких этапов:
Исследовать вопрос подробнее – вывод из запоя недорого москва
Процесс кодирования проходит в комфортной и спокойной обстановке. Врач объясняет каждый этап, чтобы пациент чувствовал себя уверенно и спокойно. После процедуры пациент получает памятку с рекомендациями по уходу за здоровьем и режиму поведения в первые недели после лечения.
Получить больше информации – https://kodirovanie-ot-alkogolizma-v-volgograde17.ru/kodirovanie-ot-alkogolya-v-volgograde
Благодаря этому подходу пациент выходит из состояния запоя без стресса и с минимальной нагрузкой на организм, что ускоряет процесс восстановления.
Получить дополнительные сведения – вывод из запоя на дому цена
Одним из самых востребованных направлений работы клиники является проведение детоксикации и вывод из запоя. Эти процедуры направлены на очищение организма от алкоголя и продуктов его распада, нормализацию работы печени и нервной системы. Лечение проводится с использованием сертифицированных препаратов и под контролем врача-нарколога.
Выяснить больше – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologiya-gorod-novokuzneczk
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Исследовать вопрос подробнее – наркологический вывод из запоя волгоград
Ниже приведена таблица с типовыми компонентами капельницы и их действием:
Изучить вопрос глубже – срочный вывод из запоя
Реабилитация после запоя в стационаре Балашихи. Мы поможем вам восстановиться после запоя и предотвратить рецидивы.
Углубиться в тему – вывод из запоя на дому цена в балашихе
Благодаря этому подходу пациент выходит из состояния запоя без стресса и с минимальной нагрузкой на организм, что ускоряет процесс восстановления.
Подробнее тут – врач вывод из запоя
Клиника «ВолгаМед Резолюция» в Волгограде оказывает помощь при алкогольной интоксикации как в условиях стационара, так и на дому. Врачи готовы выехать к пациенту в течение 40–60 минут после обращения, привозя с собой всё необходимое оборудование для проведения инфузионной терапии. Такая оперативность позволяет снизить риск осложнений и стабилизировать состояние уже в первые часы лечения. Для пациентов, нуждающихся в круглосуточном наблюдении, предусмотрены комфортабельные палаты с постоянным медицинским контролем.
Детальнее – вывод из запоя вызов на дом в волгограде
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Получить дополнительную информацию – наркология вывод из запоя
Эти методы комбинируются и создают условия для всестороннего восстановления пациента.
Детальнее – наркологическая клиника нарколог в омске
Комплексный подход обеспечивает не только снятие симптомов, но и полное восстановление функций организма. Пациент получает поддержку на всех этапах — от детоксикации до социальной адаптации.
Получить дополнительные сведения – нарколог наркологическая помощь
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Ознакомиться с деталями – наркологическая клиника стационар омск
Вывод из запоя в стационаре Балашихи — надёжная помощь при алкогольной зависимости. Наши специалисты обеспечат круглосуточный медицинский уход и поддержку в комфортных условиях.
Детальнее – вывод из запоя на дому в балашихе
Своевременное обращение в клинику снижает риск развития алкогольного психоза, судорог и тяжёлых осложнений со стороны сердца и печени.
Подробнее тут – вывод из запоя вызов на дом в рязани
Своевременное обращение в клинику снижает риск развития алкогольного психоза, судорог и тяжёлых осложнений со стороны сердца и печени.
Подробнее тут – вывод из запоя в рязани
Помощь при алкогольной интоксикации в Химках. Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Изучить вопрос глубже – вывод из запоя с выездом
Анонимность и конфиденциальность гарантированы. Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Исследовать вопрос подробнее – вывод из запоя
Капельница от запоя — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Выяснить больше – vyzvat-kapelniczu-ot-zapoya lyubercy
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Узнать больше – http://vyvod-iz-zapoya-v-voronezhe17.ru/vyvod-iz-zapoya-staczionar-voronezh/
Город с протяжёнными магистралями и разноскоростными районами требует особой организации маршрутов. Выездные бригады «ВолгаДок Медикал» работают в режиме 24/7, прибывают в гражданской одежде, избегают громких звонков и используют «немаркированные» подъезды. Перед приездом мы просим подготовить пространство: приглушить верхний свет, обеспечить приток свежего воздуха без сквозняков, подготовить ровную поверхность под укладку и удлинитель, перевести телефоны в «без уведомлений» с «белым списком» близких. Это позволяет в первые минуты сосредоточиться на клинике, а не на бытовых вопросах.
Углубиться в тему – платная наркологическая клиника саратов
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Ознакомиться с деталями – http://narkolog-na-dom-v-ufe17.ru/
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Узнать больше – https://narkolog-na-dom-v-ufe17.ru/
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Исследовать вопрос подробнее – http://www.domen.ru
Лечение зависимости от алкоголя на дому в Люберцах. Наши специалисты приедут к вам домой и проведут все необходимые процедуры.
Выяснить больше – капельница от запоя вызов
Если вы ищите надежную восстановление зрения в клинике, обратите внимание на передовые технологии и доступные цены в нашей клинике.
В клинике применяются безопасные технологии для устранения проблем с глазами.
Вывод из запоя у пожилых людей в Химках. Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Получить больше информации – вывод из запоя вызов на дом в химках
Процесс включает несколько шагов:
Ознакомиться с деталями – нарколог на дом срочно в уфе
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее – https://narcologicheskaya-klinika-saratov0.ru
Анонимность и конфиденциальность гарантированы. Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Подробнее можно узнать тут – вывод из запоя вызов на дом химки
Лечение запоя на дому в Люберцах. Наши специалисты приедут к вам домой и проведут все необходимые процедуры для скорейшего облегчения состояния.
Исследовать вопрос подробнее – kapelnicza-ot-zapoya-czena lyubercy
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Хочешь знать всё? – https://gdziejestlumpeks.pl/szafiarenka-maria-kluza-chemia-z-niemiec-odziez-uzywana
Процесс кодирования проходит в комфортной и спокойной обстановке. Врач объясняет каждый этап, чтобы пациент чувствовал себя уверенно и спокойно. После процедуры пациент получает памятку с рекомендациями по уходу за здоровьем и режиму поведения в первые недели после лечения.
Подробнее – как происходит кодирование от алкоголизма в волгограде
Системный подход позволяет достичь максимальной эффективности лечения и снизить риск возврата к зависимости.
Подробнее – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkolog-novokuzneczk-na-dom/
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Разобраться лучше – вывод из запоя на дому круглосуточно новокузнецк
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Исследовать вопрос подробнее – нарколог капельница на дом в уфе
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Исследовать вопрос подробнее – анонимная наркологическая клиника
Лечение запоя без госпитализации в Химках. Мы предлагаем лечение на дому, без необходимости госпитализации.
Ознакомиться с деталями – вывод из запоя на дому цена химки
Не менее опасны и психоэмоциональные нарушения, связанные с абстинентным синдромом: тревога, чувство паники, галлюцинации, нарушения координации. В тяжёлых случаях может развиться алкогольный делирий (белая горячка) со спутанностью сознания, бредовыми идеями и приступами агрессии. Самостоятельный резкий отказ от спиртного в этом состоянии чреват непредсказуемыми осложнениями вплоть до судорог и комы.
Подробнее можно узнать тут – https://narko-reabcentr.ru
Не всегда человек способен самостоятельно прекратить приём алкоголя и восстановиться. Есть состояния, требующие немедленного вмешательства специалистов. Обратиться за помощью необходимо, если наблюдаются следующие признаки:
Получить больше информации – анонимный вывод из запоя
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Узнать больше – http://vyvod-iz-zapoya-v-krasnoyarske17.ru
Капельница от запоя — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Получить больше информации – капельница от запоя наркология
Лечение пивного алкоголизма в Люберцах. Мы предлагаем эффективные методы лечения зависимости от пива.
Получить дополнительные сведения – капельница от запоя анонимно в люберцах
Главная задача процедуры — быстрое выведение этанола и его метаболитов из организма, нормализация уровня электролитов, улучшение самочувствия и предотвращение осложнений. Лечение проводится как в клинике, так и на дому, что особенно удобно при тяжёлых состояниях, когда пациент не может самостоятельно добраться до медицинского учреждения.
Узнать больше – вывод из запоя капельница на дому тюмень
Если вас интересует кератоконус что это, это заболевание характеризуется прогрессирующей деформацией роговицы глаза, что может существенно нарушить качество зрения.
Кератоконус представляет собой прогрессирующее заболевание роговицы, которое влияет на качество зрения. Это заболевание может привести к значительному снижению зрения и требует тщательного лечения. Кератоконус может проявиться во взаимодействии с другими факторами, такими как ношение контактных линз. Симптомы могут включать размытое зрение, чувствительность к свету и снижение зрения при ночной езде.
Кератоконус – это глазное заболевание, которое влияет на форму роговицы и качество зрения. Ранняя диагностика имеет решающее значение для эффективного лечения. Нелеченный кератоконус может привести к серьезным последствиям для зрения. Регулярные осмотры у офтальмолога помогают обнаружить заболевание на ранней стадии.
Симптомы кератоконуса могут включать размытое зрение, астигматизм и чувствительность к свету. Диагностика кератоконуса включает в себя ряд специальных тестов. Одним из наиболее надежных методов диагностики является топография роговицы, которая позволяет оценить форму и кривизну роговицы. Ранняя диагностика позволяет начать лечение и предотвратить дальнейшее ухудшение зрения.
Кератоконус может быть диагностирован с помощью неинвазивных методов, таких как сканирование роговицы. Тщательная диагностика имеет решающее значение для определения степени кератоконуса и выбора оптимального лечения. Кератоконус может быть лечен с помощью трансплантации роговицы или фототерапевтических методов. Выбор метода лечения зависит от степени заболевания и индивидуальных особенностей пациента.
Кератоконус может быть лечен с помощью различных нехирургических и хирургических методов. Одним из наиболее эффективных методов лечения является ношение газопроницаемых контактных линз. Газопроницаемые линзы могут быть использованы в сочетании с другими методами лечения для достижения лучших результатов. Кроме того, могут быть применены хирургические методы, такие как имплантация коллагеновых кольцеобразных секций или трансплантация роговицы.
Хирургическое вмешательство может включать в себя имплантацию специальных устройств для поддержки роговицы. Целью лечения является достижение лучшего качества зрения и предотвращение дальнейшего прогрессирования заболевания. Регулярные осмотры у офтальмолога имеют решающее значение для контроля за состоянием роговицы и коррекции методов лечения. Своевременная коррекция методов лечения может помочь достичь лучших результатов и поддержать здоровье роговицы.
Прогноз для пациентов с кератоконусом зависит от степени заболевания и эффективности лечения. В большинстве случаев, кератоконус можно эффективно лечить и улучшать качество зрения. Методы лечения кератоконуса постоянно совершенствуются, что позволяет добиться лучших результатов. Однако, важно помнить, что кератоконус – это хроническое заболевание, которое требует постоянного мониторинга и коррекции методов лечения.
Пациенты с кератоконусом должны быть осведомлены о важности регулярных осмотров для поддержания здоровья роговицы. Кроме того, пациентам рекомендуется соблюдать все рекомендации офтальмолога и использовать назначенные методы лечения. Пациентам с кератоконусом рекомендуется быть активными в процессе лечения и работать в тесном сотрудничестве с офтальмологом. Своевременная диагностика, эффективное лечение и постоянный мониторинг могут помочь пациентам с кератоконусом улучшить качество жизни и сохранить здоровье роговицы.
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Подробнее – нарколог на дом недорого в уфе
Наркологическая помощь в современном формате — это комплексное лечение зависимостей и состояний интоксикации с индивидуальным подходом к каждому пациенту. В клинике «ВолгаМед Тольятти» круглосуточно работают врачи-наркологи, психиатры и реабилитологи, готовые оказать поддержку в любой момент. Применяются сертифицированные препараты, проверенные методики и психологическое сопровождение. При этом особое внимание уделяется анонимности и безопасности пациента: информация не передаётся третьим лицам, а лечение проводится строго конфиденциально.
Получить дополнительные сведения – экстренная наркологическая помощь в тольятти
Капельница от запоя — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Получить дополнительные сведения – нарколог на дом вывод из запоя
Процесс лечения проходит поэтапно и под постоянным наблюдением специалистов. Каждый этап направлен на определённый аспект восстановления здоровья и личности пациента.
Получить больше информации – анонимная наркологическая клиника
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
А что дальше? – https://ayndasaze.com/archives/1836
Процесс детоксикации состоит из нескольких последовательных шагов, направленных на безопасное очищение организма. Ниже представлена таблица с описанием этапов, которые применяются в клинике «Трезвая Линия Волгоград».
Детальнее – http://vyvod-iz-zapoia-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-volgograd/
Профилактика рецидивов после запоя в Химках.Мы поможем вам предотвратить повторные случаи запоя и поддержим вас на пути к трезвой жизни.
Детальнее – врач вывод из запоя химки
Основные этапы включают:
Детальнее – нарколог вывод из запоя в красноярске
Лечение зависимости от алкоголя на дому в Химках. Наши специалисты приедут к вам домой и проведут все необходимые процедуры.
Детальнее – вывод из запоя на дому
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Получить больше информации – http://vyvod-iz-zapoya-v-novokuzneczke17.ru
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее тут – лечение в наркологической клинике саратов
Круглосуточная помощь при запое в Люберцах. Наша команда работает 24/7, обеспечивая доступность медицинской помощи в любое время суток.
Разобраться лучше – вызвать капельницу от запоя
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее тут – наркологическая клиника цены в саратове
Лечение организовано поэтапно, что помогает пациенту постепенно возвращаться к полноценной жизни. Каждый шаг направлен на укрепление результата и снижение риска рецидива.
Подробнее можно узнать тут – наркологическая клиника цены в омске
Помощь при алкогольной интоксикации в Люберцах. Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Ознакомиться с деталями – http://https://kapelnica-ot-zapoya-lyubercy12.ru//http://https://kapelnica-ot-zapoya-lyubercy12.ru/
Профессиональная помощь требуется в тех случаях, когда организм уже не способен самостоятельно справиться с последствиями интоксикации. Чем дольше длится запой, тем сильнее проявляются его симптомы. Медицинское вмешательство помогает предотвратить развитие осложнений, таких как судороги, повышение давления и алкогольный психоз.
Изучить вопрос глубже – вывод из запоя на дому недорого в тольятти
Ниже представлена таблица с основными препаратами, используемыми при выводе из запоя в Тюмени:
Подробнее тут – вывод из запоя круглосуточно тюмень
Клиника использует многоступенчатый подход, который позволяет адаптировать лечение под особенности организма пациента. Наблюдение продолжается даже после завершения детоксикации, чтобы убедиться, что состояние стабильно и не требуется дополнительное вмешательство. При необходимости врач назначает курс поддержки печени, витаминов и препаратов для восстановления сна и психоэмоционального равновесия.
Ознакомиться с деталями – помощь вывод из запоя волгоград
Лечение зависимости от алкоголя на дому в Люберцах. Наши специалисты приедут к вам домой и проведут все необходимые процедуры.
Узнать больше – kapelnicza-ot-zapoya lyubercy
Наркологическая помощь в «ВолгаМед Тольятти» включает широкий спектр процедур и методик. Каждый случай рассматривается индивидуально, с учётом состояния пациента, стадии заболевания и сопутствующих факторов. Ниже представлена таблица с основными направлениями медицинской работы.
Узнать больше – наркологическая помощь
Лечение зависимости от алкоголя в стационаре Балашихи. Наши специалисты приедут к вам домой и проведут все необходимые процедуры.
Изучить вопрос глубже – нарколог на дом вывод из запоя
Кодирование от алкоголизма на дому в Люберцах. Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Изучить вопрос глубже – капельница от запоя наркология в люберцах
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Исследовать вопрос подробнее – вывод из запоя недорого в новокузнецке
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Углубиться в тему – http://narcologicheskaya-klinika-saratov0.ru/klinika-narkologii-saratov/https://narcologicheskaya-klinika-saratov0.ru
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Подробнее – кодирование от алкоголизма отзывы цены в волгограде
Кодирование от алкоголизма в стационаре Балашихи. Мы предлагаем различные методы кодирования, подходящие для каждого пациента.
Углубиться в тему – наркология вывод из запоя балашиха
Анонимность и конфиденциальность гарантированы. Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Изучить вопрос глубже – нарколог вывод из запоя в химках
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее можно узнать тут – https://narcologicheskaya-klinika-saratov0.ru/klinika-narkologii-saratov/
Капельница от запоя — доступная цена в Люберцах. Стоимость процедуры начинается от 2400 ?, и вы всегда будете заранее информированы о стоимости услуг.
Выяснить больше – врача капельницу от запоя люберцы
Кодирование от алкоголизма на дому в Люберцах. Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Подробнее – капельница от запоя клиника в люберцах
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Узнать больше – вывод из запоя дешево рязань
Такая структура терапии делает процесс максимально эффективным и безопасным.
Выяснить больше – http://narcologicheskaya-klinika-omsk0.ru/narkologi-omska/
Анонимность и конфиденциальность гарантированы. Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Углубиться в тему – срочный вывод из запоя химки
Профессиональная помощь при запое в Люберцах. Мы предлагаем капельницу, которая способствует восстановлению водно-электролитного баланса и улучшению общего состояния пациента.
Углубиться в тему – капельница от запоя в люберцах
Не всегда человек способен самостоятельно прекратить приём алкоголя и восстановиться. Есть состояния, требующие немедленного вмешательства специалистов. Обратиться за помощью необходимо, если наблюдаются следующие признаки:
Изучить вопрос глубже – http://vyvod-iz-zapoya-v-volgograde17.ru
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Подробнее можно узнать тут – запой наркологическая клиника в красноярске
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Подробнее можно узнать тут – наркологическая клиника нарколог
Лечение зависимости от алкоголя у мужчин в Люберцах. Мы предлагаем индивидуальный подход к лечению мужчин, учитывая все особенности организма.
Исследовать вопрос подробнее – врача капельницу от запоя в люберцах
Критически важный отрезок — первые 12–24 часа. Мы разбиваем его на «окна», в каждом из которых есть цель, набор действий, маркеры контроля и критерий перехода. Если целевой отклик не достигнут, меняем один параметр: темп инфузии, очередность модулей или поведенческую опору (свет/тишина/цифровой режим) — и назначаем новую точку оценки. Это сохраняет причинно-следственную связь и предотвращает полипрагмазию.
Получить больше информации – https://narcologicheskaya-klinika-saratov0.ru/klinika-narkologii-saratov/
Для тех, кто предпочитает лечение в условиях стационара, предусмотрены комфортные палаты, медицинский контроль 24/7 и возможность консультаций с психотерапевтом. Врачи клиники применяют комплексные методы, направленные не только на снятие симптомов, но и на устранение причин зависимости.
Детальнее – наркологическая помощь на дому круглосуточно в тольятти
Снятие ломки при алкоголизме в Химках. Наши специалисты помогут вам справиться с симптомами абстиненции.
Узнать больше – вывод из запоя вызов химки
Комплексный подход позволяет врачу не просто купировать острые симптомы, но и предупредить осложнения со стороны сердца, печени и нервной системы. После стабилизации состояния пациент получает рекомендации по дальнейшему лечению и восстановлению.
Разобраться лучше – наркологический вывод из запоя волгоград
Кодирование от алкоголизма в Люберцах. Мы предлагаем различные методы кодирования, подходящие для каждого пациента.
Ознакомиться с деталями – http://https://kapelnica-ot-zapoya-lyubercy12.ru//http://https://kapelnica-ot-zapoya-lyubercy12.ru/
Снятие ломки при алкоголизме в Химках. Наши специалисты помогут вам справиться с симптомами абстиненции.
Детальнее – вывод из запоя с выездом в химках
Процедура начинается с осмотра пациента и оценки степени интоксикации. Врач измеряет давление, пульс, уровень насыщения крови кислородом, определяет наличие сопутствующих заболеваний. После диагностики назначается капельница, состав которой подбирается индивидуально. Процедура направлена на очищение организма, восстановление водно-солевого баланса и снятие симптомов похмелья.
Получить больше информации – срочный вывод из запоя в тольятти
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Полная информация здесь – https://www.miyukigrossist.se/writer-01
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Исследовать вопрос подробнее – вывод из запоя цена
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Получить дополнительные сведения – наркологическая клиника стационар саратов
Лечение основывается на комплексном подходе, позволяющем учесть особенности организма и стаж злоупотребления алкоголем. Обычно процедура состоит из нескольких этапов:
Детальнее – вывод из запоя вызов
Снятие ломки при алкоголизме в стационаре Балашихи. Наши специалисты помогут вам справиться с симптомами абстиненции.
Подробнее можно узнать тут – вывод из запоя цена
Каждый этап направлен на восстановление организма без стресса и перегрузки. Врачи работают деликатно, чтобы пациент чувствовал безопасность и понимал, что помощь оказывается профессионально.
Получить дополнительные сведения – нарколог вывод из запоя
Реабилитация после запоя в Люберцах. Мы поможем вам восстановиться после запоя и предотвратить рецидивы.
Подробнее – капельница от запоя цена город. московская область
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Подробнее можно узнать тут – нарколог на дом вывод из запоя новокузнецк
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Детальнее – частный нарколог на дом
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Подробности по ссылке – https://eatonefeedone.com/recommendations/tortilla
Кодирование от алкоголизма на дому в стационаре Балашихи. Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Ознакомиться с деталями – вывод из запоя недорого балашиха
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Получить дополнительные сведения – http://www.domen.ru
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Получить дополнительные сведения – https://alisohani.com/connecting-readers-from-around-the-world-4
Вывод из запоя в стационаре — безопасное и комфортное восстановление. В нашем стационаре созданы все условия для быстрого и эффективного вывода из запоя.
Исследовать вопрос подробнее – вывод из запоя клиника в балашихе
Снятие ломки при алкоголизме в Люберцах. Наши специалисты помогут вам справиться с симптомами абстиненции.
Изучить вопрос глубже – вызвать капельницу от запоя в люберцах
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Углубиться в тему – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru/kodirovanie-volgograd/https://kodirovanie-ot-alkogolizma-v-volgograde17.ru
Лечение хронического алкоголизма в Химках. Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Разобраться лучше – http://https://vyvod-iz-zapoya-himki12.ru/
Кодирование от алкоголизма на дому в Люберцах. Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Изучить вопрос глубже – капельница от запоя цена в люберцах
Комплексный подход позволяет врачу не просто купировать острые симптомы, но и предупредить осложнения со стороны сердца, печени и нервной системы. После стабилизации состояния пациент получает рекомендации по дальнейшему лечению и восстановлению.
Получить дополнительную информацию – вывод из запоя волгоград
Ниже приведена таблица с примерными этапами терапии:
Изучить вопрос глубже – вывод из запоя с выездом
Лечение проходит в несколько этапов: диагностика, детоксикация, медикаментозная поддержка и восстановление. Каждый этап имеет чёткие цели и критерии эффективности, что делает процесс управляемым и безопасным. Применяются препараты, сертифицированные в РФ, и только те, чья эффективность подтверждена клиническими исследованиями.
Разобраться лучше – вывод из запоя с выездом волгоград
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Изучить вопрос глубже – https://narkolog-na-dom-v-voronezhe17.ru/narkolog-voronezh-czena
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Углубиться в тему – https://narkologicheskaya-pomoshh-v-tolyatti17.ru/pomoshh-narkozavisimym-tolyatti/
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Ознакомиться с деталями – наркологическая клиника лечение алкоголизма
Такой подход позволяет пациенту чувствовать себя не объектом лечения, а активным участником собственного восстановления. Это повышает уровень мотивации и формирует доверие между врачом и пациентом, что критически важно для устойчивой ремиссии.
Получить дополнительную информацию – https://narcologicheskaya-klinika-v-voronezhe17.ru/chastnaya-narkologicheskaya-klinika-voronezh
Комплексный подход обеспечивает не только снятие симптомов, но и полное восстановление функций организма. Пациент получает поддержку на всех этапах — от детоксикации до социальной адаптации.
Получить больше информации – анонимная наркологическая помощь в тольятти
Пациент может выбрать анонимный формат — все данные защищены, а пребывание в клинике проходит в атмосфере уважения и деликатности. Особое внимание уделяется созданию комфортных условий: палаты оснащены системой вентиляции, регулируемым освещением и кнопкой вызова медперсонала. Круглосуточный контроль состояния позволяет своевременно реагировать на малейшие изменения и корректировать курс лечения.
Подробнее тут – https://narcologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-anonimno
Кодирование от алкоголизма на дому в Люберцах. Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Разобраться лучше – капельница от запоя выезд люберцы
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Разобраться лучше – vyvod-iz-zapoya-v-voronezhe17.ru/
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Подробнее – http://vivod-iz-zapoya-v-volgograde17.ru
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Исследовать вопрос подробнее – https://greennet.or.th/product/coconut-oil
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Углубиться в тему – скорая вывод из запоя в новокузнецке
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Изучить вопрос глубже – http://vivod-iz-zapoya-v-volgograde17.ru
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Выяснить больше – http://vyvod-iz-zapoya-saratov0.ru
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Получить дополнительную информацию – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologiya-gorod-novokuzneczk/
Лечение зависимости от алкоголя у мужчин в Химках. Мы предлагаем индивидуальный подход к лечению мужчин, учитывая все особенности организма.
Подробнее можно узнать тут – вывод из запоя капельница химки
Кодирование от алкоголизма на дому в Люберцах. Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Углубиться в тему – капельница от запоя на дому в люберцах
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Углубиться в тему – вывод из запоя недорого саратов
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Получить дополнительную информацию – вывод из запоя недорого в новокузнецке
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Узнать больше – кодирование от алкоголизма адрес
Вызов нарколога на дом — это удобная и безопасная возможность получить медицинскую помощь без необходимости ехать в клинику. Такая услуга особенно востребована, когда состояние пациента не позволяет покинуть дом, а помощь требуется незамедлительно. В наркологической клинике «ВоронМед Профи» организована круглосуточная служба выезда специалистов, которая оперативно реагирует на обращения и обеспечивает профессиональную помощь при запое, алкогольной интоксикации и обострениях хронических состояний. Врач приезжает в течение часа, оценивает состояние пациента и подбирает оптимальную схему лечения, включающую капельницы, детоксикацию и рекомендации по восстановлению организма.
Подробнее можно узнать тут – вызов нарколога на дом
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Получить дополнительную информацию – https://narcologicheskaya-klinika-omsk0.ru/chastnaya-narkologicheskaya-klinika-omsk/
В таблице приведены основные компоненты инфузионной терапии, применяемые при детоксикации:
Подробнее можно узнать тут – частная наркологическая клиника
Помощь при алкогольной интоксикации в Химках. Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Детальнее – вывод из запоя анонимно
Капельница от запоя — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Получить дополнительные сведения – капельница от запоя город. московская область
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Подробнее тут – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/chastnaya-narkologicheskaya-klinika-krasnoyarsk/
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Получить больше информации – http://www.domen.ru
Процесс включает несколько шагов:
Ознакомиться с деталями – запой нарколог на дом
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Узнать больше – http://narkologicheskaya-clinica-v-novokuzneczke17.ru/
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Разобраться лучше – https://vyvod-iz-zapoya-v-krasnoyarske17.ru/vyvedenie-iz-zapoya-krasnoyarsk
Снятие ломки при алкоголизме в Химках. Наши специалисты помогут вам справиться с симптомами абстиненции.
Разобраться лучше – вывод из запоя на дому
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Узнать больше – вывод из запоя недорого в волгограде
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Узнать больше – вывод из запоя дешево новокузнецк
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Подробнее тут – https://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom/
Наркологическая клиника — это пространство, где медицинская наука сочетается с психологической поддержкой и индивидуальным подходом к каждому пациенту. В клинике «ВоронежМед Альянс» лечение зависимости организовано по принципам доказательной медицины: каждый этап терапии основан на объективных данных, контролируемых результатах и четких критериях эффективности. Здесь помогают не просто устранить физические последствия зависимости, но и восстановить внутренние ресурсы человека, вернуть уверенность, осознанность и способность строить новую жизнь без алкоголя и наркотиков.
Исследовать вопрос подробнее – narcologicheskaya-klinika-v-voronezhe17.ru/
После завершения инфузий врач-нарколог даёт рекомендации по питанию, водному балансу и образу жизни. При необходимости пациенту назначается курс поддерживающей терапии для закрепления эффекта.
Получить дополнительную информацию – http://narkologicheskaya-pomoshh-v-tolyatti17.ru
Основные этапы включают:
Ознакомиться с деталями – http://vyvod-iz-zapoya-v-krasnoyarske17.ru/
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Уточнить детали – https://150kingwest.ca/gmedia/k025_-_quiet_room_agreement_-_october_2023-pdf
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Узнайте всю правду – https://cursocaptacaoodonto.com.br/modulo-gratis/aula-1
При появлении таких симптомов важно не откладывать вызов врача. Самолечение, особенно с использованием неизвестных препаратов, может привести к тяжёлым последствиям, включая судороги и инсульт. Врачи клиники «ВолгаМед Резолюция» приезжают на дом с необходимыми средствами для оказания экстренной помощи и стабилизации состояния уже на месте.
Подробнее тут – нарколог на дом вывод из запоя
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Подробнее – вывод из запоя капельница на дому в волгограде
Наркологическая помощь в «ВолгаМед Тольятти» включает широкий спектр процедур и методик. Каждый случай рассматривается индивидуально, с учётом состояния пациента, стадии заболевания и сопутствующих факторов. Ниже представлена таблица с основными направлениями медицинской работы.
Углубиться в тему – экстренная наркологическая помощь в тольятти
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Узнать больше – вывод из запоя в саратове
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Подробнее – http://narkolog-na-dom-v-voronezhe17.ru/
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Выяснить больше – запой наркологическая клиника
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Ознакомиться с деталями – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru/
Лечение организовано поэтапно. Такой подход обеспечивает постепенное восстановление функций организма и исключает риск осложнений. Каждый этап терапии направлен на устранение конкретных нарушений, вызванных интоксикацией.
Получить дополнительные сведения – http://www.domen.ru
Кодирование от алкоголизма в стационаре Балашихи. Мы предлагаем различные методы кодирования, подходящие для каждого пациента.
Получить больше информации – вывод из запоя капельница
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Смотрите также… – http://yura.oops.jp/review/log/eid23.html
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Углубиться в тему – наркологическая клиника клиника помощь
Процедура начинается с осмотра пациента и оценки степени интоксикации. Врач измеряет давление, пульс, уровень насыщения крови кислородом, определяет наличие сопутствующих заболеваний. После диагностики назначается капельница, состав которой подбирается индивидуально. Процедура направлена на очищение организма, восстановление водно-солевого баланса и снятие симптомов похмелья.
Узнать больше – http://
Детоксикация в клинике «Центр Трезвости ВоронМед» проводится по принципу минимального вмешательства при максимальной эффективности. Основная задача — очистить кровь от токсинов и стабилизировать внутреннюю среду организма без нагрузки на сердце и почки. Все препараты вводятся медленно, под контролем медицинского персонала, а состав подбирается индивидуально после оценки анализов и состояния пациента.
Получить дополнительные сведения – вывод из запоя на дому недорого в воронеже
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Выяснить больше – вывод из запоя вызов на дом
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Получить больше информации – http://vyvod-iz-zapoya-v-volgograde17.ru
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Получить дополнительные сведения – https://festivalpavart.fr/2019/05/30/bientot-des-interviews-videos-des-artistes-du-pavart-2019
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Ознакомиться с деталями – https://narkolog-na-dom-v-ufe17.ru/ufa-narkolog-psikhiatr
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Изучить вопрос глубже – наркологическая помощь тольятти
Такой календарь делает весь процесс прозрачным: пациент видит логику, близкие — прогресс, а врач — чистый сигнал для коррекции без «эскалации на всякий случай».
Углубиться в тему – лечение в наркологической клинике саратов
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Узнать больше – http://narkolog-na-dom-v-voronezhe17.ru/vrach-narkolog-na-dom-voronezh/https://narkolog-na-dom-v-voronezhe17.ru
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Смотрите также… – https://manolojimenez.mx/presenta-manolo-modelo-coahuila-ante-legisladores-federales-del-pri
Кодирование от алкоголизма на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Выяснить больше – частная наркологическая помощь
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Подробнее тут – http://vyvod-iz-zapoya-v-ryazani17.ru
Не менее опасны и психоэмоциональные нарушения, связанные с абстинентным синдромом: тревога, чувство паники, галлюцинации, нарушения координации. В тяжёлых случаях может развиться алкогольный делирий (белая горячка) со спутанностью сознания, бредовыми идеями и приступами агрессии. Самостоятельный резкий отказ от спиртного в этом состоянии чреват непредсказуемыми осложнениями вплоть до судорог и комы.
Подробнее тут – вывод из запоя в москве
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Изучить вопрос глубже – кодирование от алкоголизма адрес волгоград
Капельница не просто устраняет симптомы похмелья — она восстанавливает внутренний баланс, снижает токсическую нагрузку и поддерживает работу жизненно важных органов. После процедуры пациент чувствует прилив сил, прояснение сознания и эмоциональную стабильность. Эффект закрепляется при соблюдении рекомендаций врача и отказе от алкоголя в последующие дни.
Ознакомиться с деталями – скорая вывод из запоя в волгограде
Процесс включает несколько шагов:
Получить больше информации – платный нарколог на дом уфа
Наркологическая клиника — это пространство, где медицинская наука сочетается с психологической поддержкой и индивидуальным подходом к каждому пациенту. В клинике «ВоронежМед Альянс» лечение зависимости организовано по принципам доказательной медицины: каждый этап терапии основан на объективных данных, контролируемых результатах и четких критериях эффективности. Здесь помогают не просто устранить физические последствия зависимости, но и восстановить внутренние ресурсы человека, вернуть уверенность, осознанность и способность строить новую жизнь без алкоголя и наркотиков.
Детальнее – https://narcologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-anonimno/
Длительное злоупотребление спиртным неизбежно приводит к серьёзным последствиям для организма. Алкоголь влияет на работу практически всех внутренних органов: печень испытывает повышенную нагрузку при выводе токсинов, почки страдают от нарушения водно-солевого баланса, а сердечно-сосудистая система подвержена скачкам давления и аритмиям. Постепенно ухудшается общее самочувствие – возникают постоянные головные боли, слабость, повышенная раздражительность, бессонница.
Подробнее можно узнать тут – вывод из запоя круглосуточно в москве
Капельница от запоя — доступная цена в Москве от клиники «Частный Медик 24». Стоимость процедуры начинается от 2290 ?, и вы всегда будете заранее информированы о стоимости услуг.
Ознакомиться с деталями – наркологическая помощь москва
Саратов живёт в разных темпах: плотный центр, протяжные магистрали, мостовые переезды. Мы учитываем это в логистике: выездные бригады «СаратовМед Профи» движутся по немаркированным маршрутам, приезжают в гражданской одежде, формируют на месте «тихую сцену» и только затем начинают клиническую часть. Если на предзвонке звучат «красные флаги» — давящая боль в груди, выраженная одышка, спутанность, неукротимая рвота, судороги — организуем перевод в стационар без пауз: место резервируем заранее, передислокация проходит конфиденциально.
Исследовать вопрос подробнее – вывод из запоя капельница на дому в саратове
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Подробнее тут – скорая вывод из запоя в волгограде
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Подробнее можно узнать тут – [url=https://narkologicheskaya-pomoshh-v-tolyatti17.ru/]экстренная наркологическая помощь в тольятти[/url]
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Ознакомиться с деталями – [url=https://narkologicheskaya-klinika-v-volgograde17.ru/]лечение в наркологической клинике[/url]
Профилактика рецидивов после запоя в Люберцах. Мы поможем вам предотвратить повторные случаи запоя и поддержим вас на пути к трезвой жизни.
Углубиться в тему – [url=https://https://kapelnica-ot-zapoya-lyubercy11.ru//]вызвать капельницу от запоя на дому[/url]
сопровождение программного продукта 1с предприятие 1s-soprovozhdenie.ru .
низкотемпературные стерилизаторы plazmennye-sterilizatory.ru .
Услуга вывода из запоя в клинике сочетает профессионализм врачей, медицинскую точность и заботу. При этом обеспечивается полная конфиденциальность: данные пациентов не передаются в сторонние инстанции. Круглосуточный режим работы позволяет вызвать врача даже ночью — специалисты прибывают в течение 40–60 минут после обращения.
Углубиться в тему – вывод из запоя вызов на дом волгоград
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Получить дополнительные сведения – помощь вывод из запоя
пероксидно плазменный стерилизатор пероксидно плазменный стерилизатор .
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Разобраться лучше – анонимная наркологическая клиника воронеж
В клинике применяются современные медицинские технологии, которые обеспечивают стойкий результат. Используемые методики соответствуют международным стандартам и регулярно обновляются.
Ознакомиться с деталями – наркологическая клиника вывод из запоя в омске
Снятие ломки при алкоголизме в Люберцах. Наши специалисты помогут вам справиться с симптомами абстиненции.
Подробнее тут – после капельницы от запоя в люберцах
Профилактика рецидивов после запоя в Люберцах. Мы поможем вам предотвратить повторные случаи запоя и поддержим вас на пути к трезвой жизни.
Подробнее – врача капельницу от запоя в люберцах
Капельница — основной инструмент для очищения организма от продуктов распада этанола. Состав раствора подбирается строго индивидуально. В таблице приведены примеры комплексов, применяемых специалистами клиники «Трезвая Линия Волгоград».
Выяснить больше – вывод из запоя вызов в волгограде
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Ознакомиться с деталями – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkolog-novokuzneczk-na-dom/
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Подробнее тут – врач нарколог на дом в уфе
Стационарное лечение запоя в Химках. Предлагаем комфортные условия для пребывания пациентов и круглосуточный медицинский уход.
Получить больше информации – вывод из запоя недорого
Лечение зависимости от алкоголя в стационаре Балашихи. Наши специалисты приедут к вам домой и проведут все необходимые процедуры.
Изучить вопрос глубже – вывод из запоя на дому недорого
Лечение организовано поэтапно, что помогает пациенту постепенно возвращаться к полноценной жизни. Каждый шаг направлен на укрепление результата и снижение риска рецидива.
Получить дополнительную информацию – http://narcologicheskaya-klinika-omsk0.ru
Вывод из запоя у пожилых людей в Химках. Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Выяснить больше – https://https://vyvod-iz-zapoya-himki12.ru/
Капельница от запоя — эффективный способ детоксикации. Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Подробнее – капельница от запоя на дому цена
Процесс детоксикации состоит из нескольких последовательных шагов, направленных на безопасное очищение организма. Ниже представлена таблица с описанием этапов, которые применяются в клинике «Трезвая Линия Волгоград».
Исследовать вопрос подробнее – вывод из запоя дешево
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Разобраться лучше – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologicheskij-czentr-novokuzneczk
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Выяснить больше – https://narkologicheskaya-klinika-v-volgograde17.ru/chastnaya-narkologicheskaya-klinika-volgograd
Снятие ломки при алкоголизме в стационаре Балашихи. Наши специалисты помогут вам справиться с симптомами абстиненции.
Изучить вопрос глубже – вывод из запоя в стационаре в балашихе
Ниже приведена таблица с типовыми компонентами капельницы и их действием:
Ознакомиться с деталями – вывод из запоя вызов на дом тольятти
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Углубиться в тему – https://narcologicheskaya-klinika-omsk0.ru/narkologi-omska
Вывод из запоя в Тольятти — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормального состояния здоровья. Длительное употребление спиртных напитков приводит к серьёзной интоксикации, нарушению работы нервной, сердечно-сосудистой и пищеварительной систем. Самостоятельные попытки прекратить запой могут быть опасны, поэтому оптимальным решением является обращение к врачу-наркологу, который проведёт лечение безопасно и эффективно.
Выяснить больше – скорая вывод из запоя тольятти
Помощь при алкогольной интоксикации в Химках. Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Изучить вопрос глубже – вывод из запоя недорого
Реабилитация после запоя в стационаре Балашихи. Мы поможем вам восстановиться после запоя и предотвратить рецидивы.
Подробнее – вывод из запоя на дому круглосуточно в балашихе
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Узнать больше – вывод из запоя в стационаре
Вывод из запоя у подростков в Москве от клиники «Частный Медик 24». Мы предлагаем специализированное лечение для подростков, учитывая их возрастные особенности.
Ознакомиться с деталями – скорая наркологическая помощь
Капельница при интоксикации помогает быстро очистить организм от продуктов распада алкоголя, восстановить водно-солевой баланс и улучшить самочувствие. В состав раствора входят препараты, нормализующие обмен веществ и поддерживающие работу печени и сердечно-сосудистой системы. Уже через 20–30 минут после начала инфузии пациент ощущает значительное облегчение. Подбор лекарственных средств осуществляется строго индивидуально, с учётом возраста, массы тела и общего состояния здоровья.
Подробнее можно узнать тут – http://narkolog-na-dom-v-ufe17.ru
1с предприятие сопровождение 1s-soprovozhdenie.ru .
Лечение организовано поэтапно. Такой подход обеспечивает постепенное восстановление функций организма и исключает риск осложнений. Каждый этап терапии направлен на устранение конкретных нарушений, вызванных интоксикацией.
Получить дополнительную информацию – вывод из запоя недорого в красноярске
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Выяснить больше – наркологическая клиника стационар
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Исследовать вопрос подробнее – http://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom/https://narkolog-na-dom-v-ufe17.ru
Лечение основывается на комплексном подходе, позволяющем учесть особенности организма и стаж злоупотребления алкоголем. Обычно процедура состоит из нескольких этапов:
Исследовать вопрос подробнее – http://narko-reabcentr.ru
плазменный стерилизатор инструментов плазменный стерилизатор инструментов .
пероксидно плазменный стерилизатор пероксидно плазменный стерилизатор .
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
А что дальше? – https://sciencefestiv.com/logo_sciencefestiv-2
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Получить больше информации – наркологическая клиника
Вывод из запоя в Рязани — это профессиональная медицинская процедура, направленная на очищение организма от токсинов, восстановление нормального самочувствия и предотвращение осложнений после длительного употребления алкоголя. В специализированных клиниках города лечение проводится с использованием современных методов детоксикации и под контролем опытных врачей-наркологов. Такой подход позволяет быстро и безопасно стабилизировать состояние пациента, устранить физическую зависимость и подготовить организм к дальнейшему восстановлению.
Изучить вопрос глубже – вывод из запоя недорого рязань
Кодирование от алкоголизма в Люберцах. Мы предлагаем различные методы кодирования, подходящие для каждого пациента.
Выяснить больше – после капельницы от запоя в люберцах
Вывод из запоя требуется тогда, когда организм уже не способен самостоятельно справиться с последствиями алкогольной интоксикации. Длительное употребление спиртного приводит к нарушению работы внутренних органов, обезвоживанию и психическим расстройствам. Медицинская помощь помогает избежать опасных осложнений и облегчить процесс отказа от алкоголя.
Получить дополнительную информацию – https://vyvod-iz-zapoya-v-ryazani17.ru/vykhod-iz-zapoya-ryazan
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
А что дальше? – https://technowalla.com/how-does-wi-fi-spy-camera-work
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Получить больше информации – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkolog-v-gorode-novokuzneczke/
Лечение пивного алкоголизма в Люберцах. Мы предлагаем эффективные методы лечения зависимости от пива.
Подробнее – капельница от запоя наркология в люберцах
Вывод из запоя у пожилых людей в Люберцах. Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Выяснить больше – врач на дом капельница от запоя в люберцах
В таблице приведены основные компоненты инфузионной терапии, применяемые при детоксикации:
Подробнее можно узнать тут – http://narkologicheskaya-clinica-v-novokuzneczke17.ru
Кодирование от алкоголизма в стационаре Балашихи. Мы предлагаем различные методы кодирования, подходящие для каждого пациента.
Изучить вопрос глубже – вывод из запоя вызов на дом балашиха
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Углубиться в тему – частная наркологическая клиника новокузнецк
Кодирование от алкоголизма на дому в Химках. Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Получить дополнительную информацию – вывод из запоя на дому круглосуточно
Не менее опасны и психоэмоциональные нарушения, связанные с абстинентным синдромом: тревога, чувство паники, галлюцинации, нарушения координации. В тяжёлых случаях может развиться алкогольный делирий (белая горячка) со спутанностью сознания, бредовыми идеями и приступами агрессии. Самостоятельный резкий отказ от спиртного в этом состоянии чреват непредсказуемыми осложнениями вплоть до судорог и комы.
Углубиться в тему – вывод из запоя на дому в москве
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Углубиться в тему – нарколог на дом цены уфа
Своевременное обращение в клинику снижает риск развития алкогольного психоза, судорог и тяжёлых осложнений со стороны сердца и печени.
Получить дополнительную информацию – https://vyvod-iz-zapoya-v-ryazani17.ru/vyvod-iz-zapoya-ryazan-na-domu
Вывод из запоя у подростков в Люберцах. Мы предлагаем специализированное лечение для подростков, учитывая их возрастные особенности.
Подробнее – капельница от запоя люберцы
Каждый этап проходит под контролем врачей-наркологов и психотерапевтов, что гарантирует эффективность и безопасность лечения.
Подробнее тут – вывод наркологическая клиника в новокузнецке
Конфиденциальность — это набор конкретных действий, а не декларация на сайте. Мы проектируем «невидимость» так, чтобы пациент мог спокойно принять помощь и не опасаться огласки.
Углубиться в тему – http://narkologicheskaya-klinika-v-krasnoyarske17.ru
Процесс включает несколько шагов:
Получить дополнительные сведения – https://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom/
Каждый вызов нарколога на дом проходит по строгому алгоритму. Врачи клиники «ВоронМед Профи» используют индивидуальный подход, адаптируя лечение под конкретного пациента. В таблице приведена типовая схема работы выездной бригады, которая помогает понять, как проходит процесс помощи от начала до конца.
Получить больше информации – врач нарколог на дом в воронеже
сопровождение 1c сопровождение 1c .
плазменные медицинские стерилизаторы плазменные медицинские стерилизаторы .
Конфиденциальность — это набор конкретных действий, а не декларация на сайте. Мы проектируем «невидимость» так, чтобы пациент мог спокойно принять помощь и не опасаться огласки.
Подробнее можно узнать тут – наркологическая клиника стационар
Процесс включает несколько шагов:
Подробнее тут – нарколог на дом клиника
Капельница — это основной инструмент дезинтоксикации при лечении запойных состояний. Она способствует выведению токсинов, нормализации обмена веществ и улучшению общего самочувствия. Состав раствора подбирается индивидуально в зависимости от степени интоксикации, возраста, массы тела и сопутствующих заболеваний. Уже через 20–30 минут после начала инфузии пациент ощущает облегчение, снижается тревожность и проходит головная боль.
Детальнее – вывод из запоя дешево
Профессиональная помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Мы предлагаем капельницу, которая способствует восстановлению водно-электролитного баланса и улучшению общего состояния пациента.
Разобраться лучше – анонимная наркологическая помощь московская область
Снятие ломки при алкоголизме в стационаре Балашихи. Наши специалисты помогут вам справиться с симптомами абстиненции.
Исследовать вопрос подробнее – вывод из запоя с выездом
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-v-krasnoyarske17.ru/czentr-kodirovaniya-vyvod-iz-zapoya-krasnoyarsk/
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Подробнее – психиатр нарколог на дом в уфе
Круглосуточная помощь при запое в стационаре Балашихи. Мы работаем 24/7, обеспечивая доступность медицинской помощи в любое время суток.
Исследовать вопрос подробнее – вывод из запоя клиника
Для строительства или ремонта дома стоит выбрать качественный кирпич ручной формовки купить в москве, который прослужит долгие годы и придаст вашему дому уникальный внешний вид.
является одним из самых древних и распространенных материалов для строительства . Этот тип кирпича производится без использования машин, благодаря чему кирпичи приобретают индивидуальность . Кирпич ручной формовки используется для возведения стен, фундаментов и других конструктивных элементов .
Кирпич ручной формовки характеризуется высокой прочностью и устойчивостью к различным погодным условиям. Процесс производства кирпича ручной формовки осуществляется вручную, что позволяет контролировать качество каждого кирпича . Кирпич ручной формовки получил широкое распространение в различных регионах мира .
Кирпич ручной формовки имеет высокую плотность, что снижает риск проникновения влаги. Этот материал применяется в строительстве зданий, требующих высокой степени безопасности . Кирпич ручной формовки обладает эстетической привлекательностью, что делает его популярным для облицовки фасадов .
Кирпич ручной формовки включает в себя использование глины и других природных компонентов . Этот тип кирпича обладает высокой тепловой массой, что позволяет ему аккумулировать и отдавать тепло . Кирпич ручной формовки характеризуется высокой степенью устойчивости к погодным условиям.
Кирпич ручной формовки используется для возведения стен, фундаментов и других конструктивных элементов . Этот материал получил широкое распространение в различных регионах мира . Кирпич ручной формовки может быть использован для создания уникальных архитектурных элементов.
Кирпич ручной формовки используется для возведения стен, фундаментов и других конструктивных элементов . Этот тип кирпича имеет высокую степень звукоизоляции, что делает его подходящим для строительства объектов с высокой степенью шумозащиты. Кирпич ручной формовки производится с применением натуральных материалов, что делает его экологически чистым .
Кирпич ручной формовки является уникальным и универсальным материалом, подходящим для любых строительных проектов . Этот тип кирпича используется для возведения стен, фундаментов и других конструктивных элементов . Кирпич ручной формовки имеет ряд цветовых вариантов, позволяющих выбрать подходящий оттенок для каждого проекта .
Кирпич ручной формовки производится без применения вредных химических веществ. Этот материал применяется в строительстве объектов культурного и исторического значения. Кирпич ручной формовки обладает высокой тепловой массой, что позволяет ему аккумулировать и отдавать тепло .
Наркологическая клиника «ВолгаДок Медикал» — это круглосуточная служба помощи, выстроенная вокруг принципов клинической безопасности, прозрачной коммуникации и поддержки пациента на каждом этапе. Мы соединяем стационар и выездные бригады в единую систему: первичный осмотр и стабилизация состояния, адресные инфузионные модули, мягкая коррекция сна и тревоги, последующее наблюдение с короткими «окнами» обратной связи. Все решения принимаются по показаниям и сопровождаются объяснением: какую цель преследуем, каким маркером измеряем, когда проверяем результат. Такой подход исключает хаотичные усиления, бережёт ресурс организма и даёт прогнозируемый клинический эффект.
Детальнее – http://narcologicheskaya-klinika-saratov0.ru
Именно поэтому при затяжных запоях необходима квалифицированная медицинская помощь, позволяющая безопасно и максимально комфортно прекратить приём алкоголя. Клиника «Стратегия Здоровья» предлагает профессиональный вывод из запоя в Москве как в условиях стационара, так и с выездом на дом. Врачи работают круглосуточно, используя проверенные методики детоксикации и медикаментозной поддержки.
Детальнее – вывод из запоя капельница на дому
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Получить дополнительную информацию – https://c-creative.fr/2024/02/08/bonjour-tout-le-monde
плазменный стерилизатор инструментов плазменный стерилизатор инструментов .
Каждый этап направлен на восстановление организма без стресса и перегрузки. Врачи работают деликатно, чтобы пациент чувствовал безопасность и понимал, что помощь оказывается профессионально.
Ознакомиться с деталями – вывод из запоя капельница
Продолжительность процедуры — от 40 минут до полутора часов. Уже в первые часы после начала терапии состояние пациента значительно улучшается: проходит тошнота, снижается тревожность, восстанавливается координация движений.
Углубиться в тему – https://vyvod-iz-zapoya-v-tolyatti17.ru/vyvedenie-iz-zapoya-tolyatti
Для обеспечения контроля доступа на мероприятиях рекомендуем использовать бумажный браслет на руку, которые обеспечивают удобство и надежность.
Это делает их идеальным выбором для ежедневного применения в различных сферах
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Получить дополнительные сведения – https://narkolog-na-dom-shchelkovo10.ru/vyzvat-narkologa-na-dom-shchelkovo/
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Подробнее – narkologicheskaya-klinika
Услуга вывода из запоя в клинике сочетает профессионализм врачей, медицинскую точность и заботу. При этом обеспечивается полная конфиденциальность: данные пациентов не передаются в сторонние инстанции. Круглосуточный режим работы позволяет вызвать врача даже ночью — специалисты прибывают в течение 40–60 минут после обращения.
Исследовать вопрос подробнее – https://vivod-iz-zapoya-v-volgograde17.ru/anonimnaya-narkologiya-vyvod-iz-zapoya-volgograd/
Карта делает видимой причинно-следственную связь: пациент понимает, зачем и что именно делается; семья видит «точки проверки»; врач получает опору для изменения одного параметра без разрушения всего плана.
Подробнее тут – vyvod-iz-zapoya-saratov0.ru/
Вывод из запоя в Раменском — это не просто «поставить капельницу и отпустить домой», а комплекс медицинских действий, от которых напрямую зависит здоровье, а иногда и жизнь человека. Длительное употребление алкоголя приводит к тяжёлой интоксикации, нарушению работы сердца, печени, головного мозга, сбоям давления, риску судорог, психозов и резких обострений хронических заболеваний. Попытки самостоятельно «сойти с дистанции» дома, с помощью случайных таблеток, седативных препаратов и новых доз алкоголя, часто только усугубляют состояние. Наркологическая клиника «РаменМед Трезвость» в Раменском выстраивает вывод из запоя как безопасный, контролируемый, поэтапный процесс: от экстренного купирования симптомов до формирования плана дальнейшего восстановления. Пациент получает помощь без осуждения, анонимно, с участием специалистов, которые берут на себя ответственность за каждое назначение и каждое действие. Для родственников это означает: больше не нужно гадать, чего бояться и что давать — есть конкретное место и команда, к которым можно обратиться сразу.
Детальнее – вывод из запоя с выездом
Вывод из запоя в Тольятти — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормального состояния здоровья. Длительное употребление спиртных напитков приводит к серьёзной интоксикации, нарушению работы нервной, сердечно-сосудистой и пищеварительной систем. Самостоятельные попытки прекратить запой могут быть опасны, поэтому оптимальным решением является обращение к врачу-наркологу, который проведёт лечение безопасно и эффективно.
Подробнее тут – https://vyvod-iz-zapoya-v-tolyatti17.ru/vyvod-iz-zapoya-tolyatti-na-domu/
Лечение в клинике включает несколько последовательных этапов, каждый из которых направлен на достижение стабильной ремиссии и восстановление здоровья пациента.
Детальнее – https://narcologicheskaya-klinika-v-novokuzneczke17.ru/narkologiya-gorod-novokuzneczk
Каждый час промедления в острый период повышает вероятность обезвоживания, электролитных сдвигов, аритмий, гипертонических всплесков и расстройств сна, которые легко перерастают в делирий. Домашние попытки с «подручными» средствами редко учитывают лекарственные взаимодействия, реальный уровень обезвоживания и состояние печени, а «жёсткая» седация, применяемая без показаний, маскирует ухудшения и лишает врача информативной картины. Профессиональная бригада «НоваТрезвие» начинает с объективной оценки: давление, пульс, сатурация, температура, неврологический статус, выраженность тремора и тошноты, степень обезвоживания, список принимаемых препаратов и возможные аллергии. На этой базе формируется персональный план: регидратация, коррекция электролитов и кислотно-щелочного баланса, поддержка нервной системы витаминами группы B и магнием, гепатопротекторная и антиоксидантная защита по показаниям, противорвотные при необходимости и мягкая анксиолитическая поддержка для восстановительного сна. Такой маршрут гасит «пожар» интоксикации управляемо, возвращая прогнозируемость самочувствия в течение первых часов.
Изучить вопрос глубже – экстренный вывод из запоя
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Разобраться лучше – адреса наркологических клиник
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Подробнее – лечение в наркологической клинике в омске
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Исследовать вопрос подробнее – https://elmandadoya.com/index.php/2023/06/12/necesitas-enviar-o-recoger-mercancia-nosotros-lo-hacemos-por-ti
Критически важный отрезок — первые 12–24 часа. Мы разбиваем его на «окна», в каждом из которых есть цель, набор действий, маркеры контроля и критерий перехода. Если целевой отклик не достигнут, меняем один параметр: темп инфузии, очередность модулей или поведенческую опору (свет/тишина/цифровой режим) — и назначаем новую точку оценки. Это сохраняет причинно-следственную связь и предотвращает полипрагмазию.
Получить дополнительные сведения – http://narcologicheskaya-klinika-saratov0.ru
Формат помощи
Подробнее тут – vyvod-iz-zapoya-vyzov-na-dom
Комплексный подход позволяет врачу не просто купировать острые симптомы, но и предупредить осложнения со стороны сердца, печени и нервной системы. После стабилизации состояния пациент получает рекомендации по дальнейшему лечению и восстановлению.
Изучить вопрос глубже – анонимный вывод из запоя
сопровождение 1с предприятие 8 3 1s-soprovozhdenie.ru .
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Выяснить больше – https://vyvod-iz-zapoya-v-tyumeni17.ru/vyvod-iz-zapoya-na-domu-tyumen/
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Узнать больше – https://narcologicheskaya-klinika-v-voronezhe17.ru/
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Выяснить больше – вывод из запоя цена волгоград
Такая структура позволяет достичь максимального эффекта в кратчайшие сроки и минимизировать риск осложнений.
Выяснить больше – нарколог на дом вывод из запоя
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Подробнее можно узнать тут – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru/kodirovanie-volgograd/https://kodirovanie-ot-alkogolizma-v-volgograde17.ru
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Смотрите также… – https://14kankoreziu.lt/virtuali-kavapost
Услуга
Исследовать вопрос подробнее – vyzvat-narkologa-na-dom-srochno
плазменный стерилизатор инструментов плазменный стерилизатор инструментов .
Такая структура терапии делает процесс максимально эффективным и безопасным.
Получить дополнительную информацию – https://narcologicheskaya-klinika-omsk0.ru/narkologicheskaya-bolnicza-omsk
Вывод из запоя в Тольятти — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормального состояния здоровья. Длительное употребление спиртных напитков приводит к серьёзной интоксикации, нарушению работы нервной, сердечно-сосудистой и пищеварительной систем. Самостоятельные попытки прекратить запой могут быть опасны, поэтому оптимальным решением является обращение к врачу-наркологу, который проведёт лечение безопасно и эффективно.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-v-tolyatti17.ru/vyvod-iz-zapoya-tolyatti-na-domu/
Конфиденциальность — это набор конкретных действий, а не декларация на сайте. Мы проектируем «невидимость» так, чтобы пациент мог спокойно принять помощь и не опасаться огласки.
Подробнее – https://narkologicheskaya-klinika-v-krasnoyarske17.ru/narkologicheskaya-klinika-krasnoyarsk-otzyvy/
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Получить больше информации – нарколог на дом вывод из запоя уфа
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Ознакомиться с деталями – платная наркологическая помощь тольятти
Наркологическая клиника в Новокузнецке предоставляет профессиональную помощь людям, столкнувшимся с зависимостью от алкоголя, наркотиков и психоактивных веществ. Лечение проводится под наблюдением опытных специалистов с применением современных медицинских методик. Основная цель работы клиники — не только устранить физическую зависимость, но и восстановить психологическое равновесие пациента, вернуть мотивацию и способность жить без употребления веществ.
Ознакомиться с деталями – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologicheskij-czentr-novokuzneczk/
Во время лечения фиксируются все жизненные показатели пациента. При необходимости проводится экспресс-анализ крови и ЭКГ. Ниже представлена таблица, показывающая, какие параметры контролируются и по каким признакам оценивается стабилизация состояния.
Подробнее – http://vyvod-iz-zapoya-v-voronezhe17.ru/vyvod-iz-zapoya-na-domu-voronezh/
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Получить больше информации – частный нарколог на дом
Ниже — ключевые направления, которые логично дополняют друг друга и формируют единый маршрут лечения:
Получить дополнительную информацию – narkologicheskie-kliniki-alkogolizm
Услуга
Получить больше информации – https://narkolog-na-dom-serpuhov10.ru/narkolog-psiholog-na-dom-serpuhov
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Углубиться в тему – лечение в наркологической клинике
В Волгограде медицинская клиника «Трезвая Линия Волгоград» предоставляет круглосуточную помощь людям, столкнувшимся с острым алкогольным отравлением или затяжным запоем. Врачи выезжают на дом, в гостиницу или принимают пациентов в стационаре. Каждое вмешательство начинается с оценки состояния — измерения давления, пульса, насыщения кислородом, уровня интоксикации и дехидратации. Далее подбирается оптимальный состав капельницы, направленный на восстановление водно-солевого баланса, поддержку печени и снижение тревожности.
Ознакомиться с деталями – вывод из запоя вызов на дом волгоград
Мы уделяем особое внимание сенсорной среде — это не «сервис ради сервиса», а клинический инструмент. Контролируем свет и звук, просим отключить уведомления на устройствах, используем тёплую воду малыми глотками, настраиваем «ритуал 60 минут» перед сном. На этом фоне инфузии переносятся ровнее, латентность засыпания сокращается, а утро встречает ясностью вместо «ваты» в голове. Конфиденциальность встроена в процессы: немаркированные выезды, нейтральные формулировки в документах, разграничение доступа к медданным и отсутствие фото/видео без письменного согласия.
Получить дополнительную информацию – http://narcologicheskaya-klinika-saratov0.ru/chastnaya-narkologicheskaya-klinika-saratov/
стерилизатор плазменный низкотемпературный plazmennyy-sterilizator.ru .
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Разобраться лучше – http://narkolog-na-dom-v-ufe17.ru/narkolog-ufa-anonimno/
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Углубиться в тему – https://vyvod-iz-zapoya-v-krasnoyarske17.ru/vyvedenie-iz-zapoya-krasnoyarsk/
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее – https://narcologicheskaya-klinika-saratov0.ru/klinika-narkologii-saratov
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-v-krasnoyarske17.ru
Ниже приведена таблица с типовыми компонентами капельницы и их действием:
Получить дополнительную информацию – http://
В Воронеже команда «ВоронМед Профи» работает по принципу быстрой медицинской реакции — помощь оказывается независимо от времени суток и дня недели. Все выезды выполняются анонимно, без спецтранспорта и медицинской формы. Врач приезжает в гражданской одежде, что исключает ненужное внимание соседей и посторонних. В ходе осмотра специалист измеряет давление, пульс, температуру, оценивает уровень интоксикации и определяет степень обезвоживания. На основе полученных данных подбирается состав капельницы, который подаётся медленно и безопасно под контролем врача.
Получить дополнительные сведения – психиатр нарколог на дом в воронеже
Комплексная терапия включает несколько последовательных этапов, обеспечивающих полное восстановление организма и личности пациента. Каждый из них направлен на решение конкретных задач — от устранения интоксикации до закрепления устойчивой ремиссии.
Детальнее – https://narkologicheskaya-klinika-v-volgograde17.ru/narkologi-volgograda/
«Трезвый Центр Коломна» предлагает несколько маршрутов, и выбор делается не по принципу «как удобнее», а по критериям безопасности. Если пациент в сознании, на контакте, без грубой дезориентации, без галлюцинаций, может пить воду, рвота эпизодическая, нет тяжёлых скачков давления и пульса, дома есть тишина и ответственный взрослый — возможен выезд на дом. Врач приезжает в Коломне, проводит осмотр, измеряет давление, пульс, сатурацию, температуру, оценивает тремор, степень обезвоживания, неврологический и психический статус, подбирает индивидуальную инфузионную схему и наблюдает за реакцией. Если же запой затянулся (3–5 суток и более), выражены слабость, шаткость походки, многократная рвота, резкие «качели» АД и ЧСС, есть подозрение на предделирий или делирий, тяжёлая соматика или пожилой возраст — врач честно рекомендует стационар. В отделении пациент получает круглосуточный мониторинг, возможность оперативно корректировать лечение, защищённую среду без доступа к алкоголю и посторонних стимулов, поддержку медперсонала в любое время суток. Такой дифференцированный подход экономит силы, деньги и главное — снижает риск критических осложнений, которые часто возникают именно после «домашних экспериментов».
Изучить вопрос глубже – вывод из запоя круглосуточно
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Получить дополнительные сведения – https://narkolog-na-dom-v-voronezhe17.ru/narkolog-voronezh-czena/
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Ознакомиться с деталями – платная наркологическая клиника саратов
Наркологическая клиника «КоломнаМед Центр» — это место, куда можно обратиться в тот момент, когда домашние попытки контролировать алкоголь, наркотики, аптечные препараты или смесь всего сразу перестают работать, а жизнь превращается в постоянное «завтра начну с нуля». Здесь не обещают чудес за один день и не пугают диагнозами, а выстраивают понятный медицинский маршрут: детоксикация, стабилизация, реабилитация, поддержка семьи, профилактика срывов. Пациент получает помощь в защищённой, конфиденциальной среде, где всё организовано так, чтобы снизить тревогу и стыд, убрать хаос вокруг зависимости и дать человеку шанс вернуться к нормальной жизни без давления, угроз и токсичных «стимулов». Для родных клиника в Коломне — это опора: конкретный адрес, конкретная команда, чёткие сроки и понятные этапы, вместо бесконечных обещаний «он сам справится».
Получить дополнительные сведения – http://narkologicheskaya-klinika-kolomna10.ru/luchshie-narkologicheskie-kliniki-v-kolomne/
Фиксируем АД, ЧСС, сатурацию, температуру, оцениваем неврологический статус, степень обезвоживания, тремор, тошноту и уровень тревоги; собираем краткий анамнез последних суток и характер употребления.
Подробнее тут – вывод из запоя с выездом электросталь
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Ознакомиться с деталями – http://vivod-iz-zapoya-v-volgograde17.ru
Прежде чем перейти к ориентировочным цифрам, важно подчеркнуть: цена формируется из реальных компонентов помощи — работы врача и медсестры, объёма инфузионной терапии, перечня препаратов, времени выезда и необходимости более длительного наблюдения. Никаких скрытых доплат: все дополнительные назначения согласуются заранее. Чем раньше вы обращаетесь, тем меньше объём вмешательств и, как правило, ниже итоговая стоимость — короткий эпизод проще и дешевле стабилизировать, чем «выводить» осложнения после затянутого запоя.
Получить дополнительную информацию – http://narkolog-na-dom-shchelkovo10.ru
Вывод из запоя в Рязани — это профессиональная медицинская процедура, направленная на очищение организма от токсинов, восстановление нормального самочувствия и предотвращение осложнений после длительного употребления алкоголя. В специализированных клиниках города лечение проводится с использованием современных методов детоксикации и под контролем опытных врачей-наркологов. Такой подход позволяет быстро и безопасно стабилизировать состояние пациента, устранить физическую зависимость и подготовить организм к дальнейшему восстановлению.
Подробнее тут – наркологический вывод из запоя
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Узнать больше – http://vyvod-iz-zapoya-saratov0.ru/
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Исследовать вопрос подробнее – https://narcologicheskaya-klinika-omsk0.ru/narkologicheskaya-bolnicza-omsk
Маршрут организован так, чтобы убрать хаос и сделать шаги понятными для родственников. После звонка оператор под контролем врача уточняет длительность употребления, примерные объёмы алкоголя, хронические болезни (гипертония, ИБС, диабет, заболевания печени, почек, нервной системы), список уже принятых лекарств, эпизоды потери сознания, судорог, подозрительные психические симптомы. На этом этапе принимается базовое решение: возможно ли безопасно провести детокс на дому либо показан стационар. Врач приезжает по адресу в Щёлково, проводит осмотр: фиксирует АД, ЧСС, сатурацию, температуру, оценивает тремор, координацию, речь, поведение, уровень сознания, степень обезвоживания. Затем подбирается индивидуальная инфузионная схема: растворы для регидратации, коррекции электролитов и кислотно-щелочного баланса, витамины группы B и магний для поддержки нервной системы и снижения тремора; по показаниям — гепатопротекторы, мягкие антиоксиданты, противорвотные, щадящие анксиолитики для сна, но без грубого «выключения». Во время процедуры врач наблюдает за динамикой, при необходимости меняет скорость капельницы, контролирует давление и пульс, следит за реакцией на препараты. В финале даёт подробные рекомендации: как вести себя ближайшие 24–72 часа, как спать, что пить и есть, каких лекарств избегать, какие симптомы считать тревожными, когда нужно немедленно звонить и когда стоит рассмотреть стационар. Если уже на этапе осмотра понятно, что дому «тесно» по безопасности, перевод в клинику организуется без задержек.
Подробнее можно узнать тут – https://narkolog-na-dom-shchelkovo10.ru/narkolog-na-dom-cena-shchelkovo/
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Исследовать вопрос подробнее – https://anaconnect.com/benefits-of-hiring-enrolled-agents
Важное отличие наркологической клиники «Трезвый Путь Коломна» — полный отказ от схемы «одна капельница = решение всех проблем». Детокс здесь рассматривается как необходимый старт, но не как финальная точка. Сначала специалисты снимают острые состояния: вывод из запоя, купирование абстиненции, коррекцию водно-электролитного баланса, поддержку сердца, печени и нервной системы, нормализацию сна, снижение тревоги. Когда организм перестаёт «гореть», начинается следующий этап — стабилизация: врач оценивает психическое состояние, выявляет депрессивные, тревожные, панические проявления, подбирает поддерживающие схемы, которые помогают удержаться в первые недели после кризиса. Далее подключаются психотерапевтические инструменты: индивидуальные консультации, работа с мотивацией, разбор триггеров, формирование новых привычек. В финале выстраивается маршрут поддержки: амбулаторное наблюдение, связь с клиникой, рекомендации для семьи. Такой поэтапный подход делает клинику в Коломне местом, где зависимость перестают воспринимать как «стыд» и начинают воспринимать как задачу, с которой можно работать профессионально.
Узнать больше – narkologicheskaya-klinika-v-kolomne
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Детальнее – вывод из запоя вызов
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Исследовать вопрос подробнее – https://narcologicheskaya-klinika-omsk0.ru/narkologi-omska/
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Ознакомиться с деталями – наркологическая клиника лечение алкоголизма в саратове
Важное отличие наркологической клиники «Трезвый Путь Коломна» — полный отказ от схемы «одна капельница = решение всех проблем». Детокс здесь рассматривается как необходимый старт, но не как финальная точка. Сначала специалисты снимают острые состояния: вывод из запоя, купирование абстиненции, коррекцию водно-электролитного баланса, поддержку сердца, печени и нервной системы, нормализацию сна, снижение тревоги. Когда организм перестаёт «гореть», начинается следующий этап — стабилизация: врач оценивает психическое состояние, выявляет депрессивные, тревожные, панические проявления, подбирает поддерживающие схемы, которые помогают удержаться в первые недели после кризиса. Далее подключаются психотерапевтические инструменты: индивидуальные консультации, работа с мотивацией, разбор триггеров, формирование новых привычек. В финале выстраивается маршрут поддержки: амбулаторное наблюдение, связь с клиникой, рекомендации для семьи. Такой поэтапный подход делает клинику в Коломне местом, где зависимость перестают воспринимать как «стыд» и начинают воспринимать как задачу, с которой можно работать профессионально.
Получить больше информации – наркологическая клиника
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Получить дополнительные сведения – https://katfleischman.com/marrakesh-case-study
Перед процедурой врач оценивает состояние пациента, измеряет давление, пульс и уровень насыщения крови кислородом. После осмотра подбирается состав инфузии, включающий препараты для дезинтоксикации, восстановления водно-солевого баланса и нормализации работы органов. Введение растворов осуществляется внутривенно, под контролем специалиста. Длительность процедуры — от 40 минут до 1,5 часов.
Разобраться лучше – сколько стоит капельница от запоя в волгограде
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Получить дополнительную информацию – вывод из запоя рязань
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Исследовать вопрос подробнее – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkolog-novokuzneczk-na-dom
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Углубиться в тему – платная наркологическая клиника
Даже если симптомы кажутся незначительными, проведение инфузионной терапии значительно ускоряет процесс восстановления и предотвращает развитие осложнений.
Исследовать вопрос подробнее – http://www.domen.ru
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Получить дополнительные сведения – вывод из запоя в волгограде
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Детальнее – https://narcologicheskaya-klinika-saratov0.ru/klinika-narkologii-saratov
Во время процедуры врач фиксирует ключевые параметры, чтобы убедиться в безопасности и эффективности терапии. Мониторинг проводится при каждом выезде и помогает отслеживать динамику в режиме реального времени. В таблице ниже указаны основные показатели, за которыми следит специалист.
Подробнее тут – вызвать нарколога на дом воронеж
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Детальнее – http://narcologicheskaya-klinika-v-novokuzneczke17.ru/
Лечение в клинике «ВоронежМед Альянс» проходит поэтапно. Каждый модуль имеет определённую цель и собственные критерии эффективности. Такой подход исключает избыточное вмешательство и обеспечивает прозрачность процесса восстановления.
Подробнее можно узнать тут – наркологическая клиника воронеж
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Получить дополнительные сведения – нарколог на дом вывод воронеж
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Изучить вопрос глубже – наркологическая клиника нарколог воронеж
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Углубиться в тему – http://vyvod-iz-zapoya-saratov0.ru/vyvod-iz-zapoya-saratov-staczionar/https://vyvod-iz-zapoya-saratov0.ru
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Разобраться лучше – наркология вывод из запоя волгоград
Наркологическая клиника «ВолгаДок Медикал» — это круглосуточная служба помощи, выстроенная вокруг принципов клинической безопасности, прозрачной коммуникации и поддержки пациента на каждом этапе. Мы соединяем стационар и выездные бригады в единую систему: первичный осмотр и стабилизация состояния, адресные инфузионные модули, мягкая коррекция сна и тревоги, последующее наблюдение с короткими «окнами» обратной связи. Все решения принимаются по показаниям и сопровождаются объяснением: какую цель преследуем, каким маркером измеряем, когда проверяем результат. Такой подход исключает хаотичные усиления, бережёт ресурс организма и даёт прогнозируемый клинический эффект.
Подробнее тут – наркологические клиники алкоголизм в саратове
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Получить дополнительную информацию – http://narkologicheskaya-klinika-v-krasnoyarske17.ru/narkologicheskaya-klinika-krasnoyarsk-otzyvy/https://narkologicheskaya-klinika-v-krasnoyarske17.ru
Каждый этап направлен на восстановление организма без стресса и перегрузки. Врачи работают деликатно, чтобы пациент чувствовал безопасность и понимал, что помощь оказывается профессионально.
Подробнее тут – https://vyvod-iz-zapoya-v-novokuzneczke17.ru/vyvod-iz-zapoya-v-staczionare-novokuzneczk/
Основные этапы включают:
Узнать больше – вывод из запоя на дому
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Получить дополнительные сведения – https://vyvod-iz-zapoya-saratov0.ru/vyvod-iz-zapoya-saratov-staczionar
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Получить дополнительную информацию – http://www.greatdynamics.net/2020/11/16/tech-firms-support-huawei-restriction-balk-at-cost
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Исследовать вопрос подробнее – http://narkologicheskaya-klinika-kolomna10.ru/luchshie-narkologicheskie-kliniki-v-kolomne/
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Подробнее – вывод из запоя на дому круглосуточно
Когда человек в запое, близким кажется, что всё ещё можно решить «по-тихому»: выспаться, отпаять водой, дать обезболивающее или «успокоительное» и дождаться, пока станет легче. На практике это часто приводит к обратному результату. Алкогольная интоксикация нарушает водно-электролитный баланс, сгущает кровь, повышает нагрузку на сердце, провоцирует скачки давления, ухудшает работу печени и нервной системы. Неконтролируемый приём снотворных, анальгетиков, транквилизаторов, особенно вместе с алкоголем, способен вызвать угнетение дыхания, аритмии, судороги или делирий. Домашняя обстановка не даёт возможности следить за всеми показателями и вовремя отреагировать. «РаменМед Трезвость» предлагает клинически выверенный вывод из запоя в Раменском с учётом возраста, длительности употребления, хронических заболеваний, перенесённых ранее осложнений. Здесь не применяют сомнительные схемы «усыпить, чтобы не мешал», а ставят задачу: безопасно пройти острую фазу, снять интоксикацию, стабилизировать давление и пульс, защитить сердце и мозг, снизить риск психозов и, при желании пациента, сразу наметить маршрут реального лечения зависимости. Такой подход снимает с родственников опасную «роль врача» и возвращает ситуацию туда, где ей место — под контроль профессионалов.
Узнать больше – ramenskoe-vyvod-iz-zapoya
При появлении таких симптомов важно не откладывать вызов врача. Самолечение, особенно с использованием неизвестных препаратов, может привести к тяжёлым последствиям, включая судороги и инсульт. Врачи клиники «ВолгаМед Резолюция» приезжают на дом с необходимыми средствами для оказания экстренной помощи и стабилизации состояния уже на месте.
Углубиться в тему – вывод из запоя в волгограде
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Выяснить больше – врач на дом капельница от запоя волгоград
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Желаете узнать подробности? – https://kokubun-kensetsu.jp/daikiboshuzen-price-market
Диспетчер уточняет адрес в Электростали, длительность эпизода, текущие препараты и дозы, аллергии, сопутствующие заболевания, последние значения давления/пульса. Это экономит 15–20 минут на месте и позволяет заранее исключить опасные взаимодействия.
Подробнее – срочный вывод из запоя
В клинике «ВолгоградМед Альянс» применяются разные методы кодирования, позволяющие подобрать оптимальный вариант для каждого пациента. Выбор зависит от медицинских показаний, психологической готовности и длительности ремиссии. В таблице ниже представлены основные методики, их особенности и преимущества.
Разобраться лучше – как происходит кодирование от алкоголизма
Домашний формат особенно важен, когда пациент не готов к стационару, боится огласки, испытывает стыд или сопротивление, но объективно нуждается в помощи. Попытки «перетерпеть» или лечить своими силами заканчиваются тем, что родственники дают опасные комбинации седативных, анальгетиков и «антипохмельных» средств, а состояние только ухудшается. «МедТрезвие Долгопрудный» строит выездную помощь так, чтобы она оставалась профессиональной медициной, а не косметической услугой. Уже при звонке диспетчер под контролем врача уточняет длительность запоя, виды алкоголя, наличие гипертонии, болезней сердца, печени, почек, диабета, неврологических нарушений, психических эпизодов, факт судорог, делирия в прошлом, какие лекарства уже были даны. Это позволяет заранее понять, подходит ли формат лечения на дому или сразу нужно рассматривать стационар. Выезд назначается только в тех случаях, когда это безопасно, и именно в этом ключевое отличие официальной клиники от анонимных «капельниц на дом» — здесь всегда выбирают жизнь и здоровье, а не удобный маркетинговый сценарий. Для семьи это не просто комфорт, а возможность получить помощь без риска сорваться в критическое состояние посреди ночи.
Получить дополнительные сведения – narkolog-na-domu-dolgoprudnyj
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Узнать больше – вывод наркологическая клиника в новокузнецке
Наркологическая помощь в современном формате — это комплексное лечение зависимостей и состояний интоксикации с индивидуальным подходом к каждому пациенту. В клинике «ВолгаМед Тольятти» круглосуточно работают врачи-наркологи, психиатры и реабилитологи, готовые оказать поддержку в любой момент. Применяются сертифицированные препараты, проверенные методики и психологическое сопровождение. При этом особое внимание уделяется анонимности и безопасности пациента: информация не передаётся третьим лицам, а лечение проводится строго конфиденциально.
Узнать больше – срочная наркологическая помощь тольятти
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Получить больше информации – сколько стоит вызвать нарколога на дом
Системный подход позволяет достичь максимальной эффективности лечения и снизить риск возврата к зависимости.
Выяснить больше – http://
Процесс включает несколько шагов:
Получить дополнительные сведения – нарколог на дом недорого
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Изучить вопрос глубже – http://vyvod-iz-zapoya-v-tyumeni17.ru
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Получить дополнительные сведения – http://narkologicheskaya-klinika-kolomna10.ru
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Углубиться в тему – нарколог вывод из запоя в рязани
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Получить дополнительные сведения – https://narkologicheskaya-klinika-v-volgograde17.ru/narkologicheskaya-pomoshh-volgograd
Процесс лечения проходит поэтапно и под постоянным наблюдением специалистов. Каждый этап направлен на определённый аспект восстановления здоровья и личности пациента.
Ознакомиться с деталями – https://narkologicheskaya-clinica-v-novokuzneczke17.ru/narkologiya-gorod-novokuzneczk
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Получить дополнительные сведения – https://narkologicheskaya-klinika-kolomna2-10.ru/luchshie-narkologicheskie-kliniki-v-kolomne/
Город с протяжёнными магистралями и разноскоростными районами требует особой организации маршрутов. Выездные бригады «ВолгаДок Медикал» работают в режиме 24/7, прибывают в гражданской одежде, избегают громких звонков и используют «немаркированные» подъезды. Перед приездом мы просим подготовить пространство: приглушить верхний свет, обеспечить приток свежего воздуха без сквозняков, подготовить ровную поверхность под укладку и удлинитель, перевести телефоны в «без уведомлений» с «белым списком» близких. Это позволяет в первые минуты сосредоточиться на клинике, а не на бытовых вопросах.
Детальнее – https://narcologicheskaya-klinika-saratov0.ru/chastnaya-narkologicheskaya-klinika-saratov
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Подробнее – наркологические клиники алкоголизм в воронеже
1win регистрация онлайн 1win12045.ru
В Воронеже команда «ВоронМед Профи» работает по принципу быстрой медицинской реакции — помощь оказывается независимо от времени суток и дня недели. Все выезды выполняются анонимно, без спецтранспорта и медицинской формы. Врач приезжает в гражданской одежде, что исключает ненужное внимание соседей и посторонних. В ходе осмотра специалист измеряет давление, пульс, температуру, оценивает уровень интоксикации и определяет степень обезвоживания. На основе полученных данных подбирается состав капельницы, который подаётся медленно и безопасно под контролем врача.
Детальнее – http://narkolog-na-dom-v-voronezhe17.ru
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Выяснить больше – наркологическая клиника клиника помощь волгоград
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Ознакомиться с деталями – вывод из запоя недорого рязань
Критически важный отрезок — первые 12–24 часа. Мы разбиваем его на «окна», в каждом из которых есть цель, набор действий, маркеры контроля и критерий перехода. Если целевой отклик не достигнут, меняем один параметр: темп инфузии, очередность модулей или поведенческую опору (свет/тишина/цифровой режим) — и назначаем новую точку оценки. Это сохраняет причинно-следственную связь и предотвращает полипрагмазию.
Исследовать вопрос подробнее – лечение в наркологической клинике
Острый эпизод запоя — это не «плохое самочувствие», а состояние с реальными рисками для сердца, нервной системы и дыхания, особенно в ночные часы, когда усиливаются вегетативные реакции и тревога. В «НоваТрезвие» мы выстраиваем помощь так, чтобы от звонка до заметного облегчения прошло как можно меньше времени и как можно меньше случайностей: короткое интервью для оценки рисков, выезд врача или приём в клинике, экспресс-диагностика по ключевым показателям, персональная инфузионная схема без «универсальных коктейлей», мягкая коррекция сна и тревоги без «вырубания», понятные инструкции семье на 24–72 часа и план продолжения на ближайшие недели. Мы не скрываемся за общими формулами: решения принимаются по фактическим данным, дозы и темп капельниц подстраиваются к динамике каждые 15–20 минут, а при «красных флагах» перевод в стационар организуется без пауз. Конфиденциальность соблюдается строго, а коммуникация простая и предсказуемая — чтобы вы всегда знали, что происходит сейчас и чего ждать к утру.
Узнать больше – vyvod-iz-zapoya-s-vyezdom
Капельница при интоксикации помогает быстро очистить организм от продуктов распада алкоголя, восстановить водно-солевой баланс и улучшить самочувствие. В состав раствора входят препараты, нормализующие обмен веществ и поддерживающие работу печени и сердечно-сосудистой системы. Уже через 20–30 минут после начала инфузии пациент ощущает значительное облегчение. Подбор лекарственных средств осуществляется строго индивидуально, с учётом возраста, массы тела и общего состояния здоровья.
Разобраться лучше – https://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom
Процесс включает несколько шагов:
Подробнее тут – вызов нарколога на дом
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Детальнее – вывод из запоя на дому недорого в красноярске
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Изучить вопрос глубже – http://narcologicheskaya-klinika-omsk0.ru/chastnaya-narkologicheskaya-klinika-omsk/
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Ознакомиться с деталями – наркологическая клиника нарколог в новокузнецке
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Разобраться лучше – narkologicheskie-kliniki-obratnyj-zvonok
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Подробности по ссылке – https://netsurf.monster/theseus-cast
Клиника «ВоронежМед Альянс» придерживается принципа прозрачной медицины: каждый шаг понятен пациенту, решения принимаются совместно, а результаты фиксируются по объективным показателям. Такой формат создаёт чувство безопасности и доверия. Среди основных принципов:
Получить дополнительную информацию – https://narcologicheskaya-klinika-v-voronezhe17.ru/
Такая структура позволяет достичь максимального эффекта в кратчайшие сроки и минимизировать риск осложнений.
Исследовать вопрос подробнее – психиатр нарколог на дом
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Детальнее – https://vyvod-iz-zapoya-saratov0.ru/
Маршрут организован так, чтобы убрать хаос и сделать шаги понятными для родственников. После звонка оператор под контролем врача уточняет длительность употребления, примерные объёмы алкоголя, хронические болезни (гипертония, ИБС, диабет, заболевания печени, почек, нервной системы), список уже принятых лекарств, эпизоды потери сознания, судорог, подозрительные психические симптомы. На этом этапе принимается базовое решение: возможно ли безопасно провести детокс на дому либо показан стационар. Врач приезжает по адресу в Щёлково, проводит осмотр: фиксирует АД, ЧСС, сатурацию, температуру, оценивает тремор, координацию, речь, поведение, уровень сознания, степень обезвоживания. Затем подбирается индивидуальная инфузионная схема: растворы для регидратации, коррекции электролитов и кислотно-щелочного баланса, витамины группы B и магний для поддержки нервной системы и снижения тремора; по показаниям — гепатопротекторы, мягкие антиоксиданты, противорвотные, щадящие анксиолитики для сна, но без грубого «выключения». Во время процедуры врач наблюдает за динамикой, при необходимости меняет скорость капельницы, контролирует давление и пульс, следит за реакцией на препараты. В финале даёт подробные рекомендации: как вести себя ближайшие 24–72 часа, как спать, что пить и есть, каких лекарств избегать, какие симптомы считать тревожными, когда нужно немедленно звонить и когда стоит рассмотреть стационар. Если уже на этапе осмотра понятно, что дому «тесно» по безопасности, перевод в клинику организуется без задержек.
Получить дополнительную информацию – narkolog-na-dom-vyvod-iz-zapoya-cena
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Ознакомиться с деталями – помощь вывод из запоя красноярск
Индивидуально подобранный состав раствора обеспечивает быстрое выведение токсинов и улучшение физического состояния уже в течение первых часов после начала лечения.
Подробнее – http://kapelnicza-ot-zapoya-v-volgograde17.ru
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Подробнее – вывод из запоя круглосуточно в волгограде
Острый эпизод запоя — это не «плохое самочувствие», а состояние с реальными рисками для сердца, нервной системы и дыхания, особенно в ночные часы, когда усиливаются вегетативные реакции и тревога. В «НоваТрезвие» мы выстраиваем помощь так, чтобы от звонка до заметного облегчения прошло как можно меньше времени и как можно меньше случайностей: короткое интервью для оценки рисков, выезд врача или приём в клинике, экспресс-диагностика по ключевым показателям, персональная инфузионная схема без «универсальных коктейлей», мягкая коррекция сна и тревоги без «вырубания», понятные инструкции семье на 24–72 часа и план продолжения на ближайшие недели. Мы не скрываемся за общими формулами: решения принимаются по фактическим данным, дозы и темп капельниц подстраиваются к динамике каждые 15–20 минут, а при «красных флагах» перевод в стационар организуется без пауз. Конфиденциальность соблюдается строго, а коммуникация простая и предсказуемая — чтобы вы всегда знали, что происходит сейчас и чего ждать к утру.
Получить дополнительную информацию – вывод из запоя круглосуточно
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Подробнее – вывод из запоя капельница
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Получить больше информации – https://narkologicheskaya-klinika-kolomna2-10.ru/
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Подробнее тут – помощь вывод из запоя
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Исследовать вопрос подробнее – вывод из запоя в стационаре волгоград
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Открой скрытое – https://marathi.deccanquest.com/?p=709
Услуга
Подробнее тут – https://narkolog-na-dom-serpuhov10.ru/
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Подробнее – анонимный вывод из запоя
Выезд нарколога на дом в Серпухове — это возможность получить профессиональную помощь в условиях, когда везти человека в клинику сложно, опасно или он категорически отказывается от госпитализации. Специалисты «СерпуховТрезвие» работают круглосуточно, приезжают по адресу с одноразовыми системами, стерильными расходниками и необходимым набором препаратов, проводят осмотр, оценивают жизненно важные показатели, подбирают индивидуальную капельницу, контролируют реакцию и оставляют подробные рекомендации. Всё происходит конфиденциально, без лишних свидетелей, без осуждения и давления. Цель — не формально «поставить капельницу», а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, уменьшить тревогу и вернуть человеку возможность нормально спать и восстанавливаться, не доводя до осложнений и экстренной госпитализации.
Изучить вопрос глубже – chastnyj-narkolog-na-dom
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Изучить вопрос глубже – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne
Процесс кодирования проходит в комфортной и спокойной обстановке. Врач объясняет каждый этап, чтобы пациент чувствовал себя уверенно и спокойно. После процедуры пациент получает памятку с рекомендациями по уходу за здоровьем и режиму поведения в первые недели после лечения.
Получить дополнительную информацию – кодирование от алкоголизма цены в волгограде
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Ознакомиться с деталями – http://narkologicheskaya-klinika-kolomna10.ru/
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Изучить вопрос глубже – https://narkologicheskaya-klinika-v-volgograde17.ru/narkologicheskaya-pomoshh-volgograd
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Подробнее тут – https://narkolog-na-dom-v-voronezhe17.ru/voronezh-narkologiya/
Письменные рекомендации: сон, питание, гидратация, запреты, «красные флаги», график амбулаторных визитов; при недостатке ресурсов дома — перевод в стационар без задержек. Такая последовательность убирает импровизацию и делает результат повторяемым.
Выяснить больше – http://vyvod-iz-zapoya-ehlektrostal2-10.ru/
Диспетчер уточняет адрес в Электростали, длительность эпизода, текущие препараты и дозы, аллергии, сопутствующие заболевания, последние значения давления/пульса. Это экономит 15–20 минут на месте и позволяет заранее исключить опасные взаимодействия.
Получить больше информации – вывод из запоя с выездом электросталь
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Выяснить больше – вывод из запоя капельница на дому саратов
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Получить больше информации – анонимная наркологическая клиника волгоград
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Узнать больше – вызвать врача нарколога на дом
Комплексный подход обеспечивает не только снятие симптомов, но и полное восстановление функций организма. Пациент получает поддержку на всех этапах — от детоксикации до социальной адаптации.
Подробнее можно узнать тут – https://narkologicheskaya-pomoshh-v-tolyatti17.ru/narkologicheskaya-bolnicza-tolyatti/
Выезд нарколога на дом в Серпухове — это возможность получить профессиональную помощь в условиях, когда везти человека в клинику сложно, опасно или он категорически отказывается от госпитализации. Специалисты «СерпуховТрезвие» работают круглосуточно, приезжают по адресу с одноразовыми системами, стерильными расходниками и необходимым набором препаратов, проводят осмотр, оценивают жизненно важные показатели, подбирают индивидуальную капельницу, контролируют реакцию и оставляют подробные рекомендации. Всё происходит конфиденциально, без лишних свидетелей, без осуждения и давления. Цель — не формально «поставить капельницу», а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, уменьшить тревогу и вернуть человеку возможность нормально спать и восстанавливаться, не доводя до осложнений и экстренной госпитализации.
Подробнее тут – https://narkolog-na-dom-serpuhov10.ru/nomer-narkologa-na-dom-serpuhov
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Разобраться лучше – вывод наркологическая клиника в новокузнецке
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Разобраться лучше – нарколог в щелково
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Получить дополнительную информацию – наркологический вывод из запоя
Алгоритм организован так, чтобы каждое действие было логичным и предсказуемым. После обращения по телефону врач заранее получает краткую клиническую картину и подбирает набор препаратов с учётом состояния пациента. По прибытии в Долгопрудном нарколог не ставит капельницу «по шаблону», а начинает с осмотра: измеряет давление, пульс, сатурацию, температуру, оценивает тремор, уровень сознания, ориентировку, степень обезвоживания, частоту рвоты, дыхание, возможные боли в груди или животе, обращает внимание на поведение и эмоциональное состояние. Если по результатам осмотра подтверждается, что дом — безопасный формат, подбирается индивидуальная инфузионная схема: объём, скорость введения и препараты зависят от возраста, длительности запоя, сопутствующих болезней и уже использованных медикаментов. Врач остаётся на адресе до завершения основных процедур, контролирует реакцию, при необходимости корректирует план и чётко проговаривает, как пациент должен проводить ближайшие 24–72 часа. Если по ходу работы выявляются признаки угрозы (начальные симптомы делирия, тяжёлые аритмии, нестабильное давление, выраженная дезориентация), нарколог рекомендует стационар и помогает семье организовать перевод. Это честный и безопасный подход: не любой ценой «отработать выезд», а сделать так, чтобы помощь действительно снижала риски.
Получить дополнительную информацию – вызов врача нарколога на дом
После процедуры пациент чувствует улучшение уже через 1–2 часа: проходят головные боли, снижается давление, нормализуется сон и аппетит.
Получить больше информации – частная наркологическая клиника в новокузнецке
Карта делает видимой причинно-следственную связь: пациент понимает, зачем и что именно делается; семья видит «точки проверки»; врач получает опору для изменения одного параметра без разрушения всего плана.
Углубиться в тему – вывод из запоя на дому цена саратов
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Получить дополнительные сведения – https://hondanamdinh.com/?p=202
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Подробнее – вывод из запоя на дому воронеж
Одна из сильных сторон «РеутовМед Сервис» — честная оценка границ домашнего лечения. Клиника не обещает «вывезем любого дома», потому что есть состояния, при которых отсутствие круглосуточного наблюдения опасно. Чтобы родным было проще сориентироваться, важно разделить ситуации по уровню риска и понять, почему иногда разумнее выбрать стационар, даже если пациент сопротивляется.
Изучить вопрос глубже – https://vyvod-iz-zapoya-reutov10.ru/vyvod-iz-zapoya-ryadom-v-reutove/
Отдельный принцип клиники — строгая анонимность. Информация о лечении не передаётся по месту работы, обучения, в сторонние структуры без согласия пациента. Это особенно важно для людей, которые боятся огласки и из-за этого годами откладывают обращение. В «КоломнаМед Центр» можно пройти лечение так, чтобы сохранить репутацию и личное пространство, не превращая каждый шаг в обсуждение «на людях».
Получить дополнительные сведения – adresa-narkologicheskih-klinik
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Получить дополнительные сведения – http://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-staczionar-voronezh/
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Разобраться лучше – вывод из запоя на дому волгоград
Критически важный отрезок — первые 12–24 часа. Мы разбиваем его на «окна», в каждом из которых есть цель, набор действий, маркеры контроля и критерий перехода. Если целевой отклик не достигнут, меняем один параметр: темп инфузии, очередность модулей или поведенческую опору (свет/тишина/цифровой режим) — и назначаем новую точку оценки. Это сохраняет причинно-следственную связь и предотвращает полипрагмазию.
Получить больше информации – https://narcologicheskaya-klinika-saratov0.ru/klinika-narkologii-saratov
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Ознакомиться с деталями – http://narkologicheskaya-klinika-kolomna10.ru/
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Детальнее – http://narkologicheskaya-klinika-kolomna2-10.ru/
Клиника «ВоронежМед Альянс» придерживается принципа прозрачной медицины: каждый шаг понятен пациенту, решения принимаются совместно, а результаты фиксируются по объективным показателям. Такой формат создаёт чувство безопасности и доверия. Среди основных принципов:
Узнать больше – запой наркологическая клиника
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Узнать больше – вывод из запоя капельница на дому
Вывод из запоя на дому возможен только при относительно контролируемом состоянии и после очной оценки нарколога. В таких случаях специалист выезжает в Раменском, проводит осмотр, назначает индивидуальную капельницу, остаётся до стабилизации состояния и оставляет подробные рекомендации. Важный момент — честность: если во время осмотра врач видит риски (нестабильное давление, признаки начинающегося делирия, серьёзные боли, глубокую дезориентацию), формат на дому не навязывается, а предлагается стационар. Именно это отличает клинику от анонимных «служб капельниц», для которых любая заявка — повод заработать, независимо от последствий.
Подробнее тут – vyvod-iz-zapoya-na-domu-v-ramenskom
Услуга
Ознакомиться с деталями – https://narkolog-na-dom-serpuhov10.ru/vyezd-narkologa-na-dom-serpuhov/
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Узнать больше – анонимное кодирование от алкоголизма волгоград
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Выяснить больше – капельница от запоя недорого в волгограде
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Получить дополнительную информацию – https://globalregulatoryinsights.com/navigating-the-seas-of-change-the-evolution-of-global-regulatory-compliance
Острый эпизод запоя — это не «плохое самочувствие», а состояние с реальными рисками для сердца, нервной системы и дыхания, особенно в ночные часы, когда усиливаются вегетативные реакции и тревога. В «НоваТрезвие» мы выстраиваем помощь так, чтобы от звонка до заметного облегчения прошло как можно меньше времени и как можно меньше случайностей: короткое интервью для оценки рисков, выезд врача или приём в клинике, экспресс-диагностика по ключевым показателям, персональная инфузионная схема без «универсальных коктейлей», мягкая коррекция сна и тревоги без «вырубания», понятные инструкции семье на 24–72 часа и план продолжения на ближайшие недели. Мы не скрываемся за общими формулами: решения принимаются по фактическим данным, дозы и темп капельниц подстраиваются к динамике каждые 15–20 минут, а при «красных флагах» перевод в стационар организуется без пауз. Конфиденциальность соблюдается строго, а коммуникация простая и предсказуемая — чтобы вы всегда знали, что происходит сейчас и чего ждать к утру.
Изучить вопрос глубже – http://www.domen.ru
Наркологическая клиника «ВолгаДок Медикал» — это круглосуточная служба помощи, выстроенная вокруг принципов клинической безопасности, прозрачной коммуникации и поддержки пациента на каждом этапе. Мы соединяем стационар и выездные бригады в единую систему: первичный осмотр и стабилизация состояния, адресные инфузионные модули, мягкая коррекция сна и тревоги, последующее наблюдение с короткими «окнами» обратной связи. Все решения принимаются по показаниям и сопровождаются объяснением: какую цель преследуем, каким маркером измеряем, когда проверяем результат. Такой подход исключает хаотичные усиления, бережёт ресурс организма и даёт прогнозируемый клинический эффект.
Получить дополнительные сведения – http://
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Желаете узнать подробности? – https://nizam-electronics.pk/super-asia-ecm-5000-plus
Домашний формат особенно важен, когда пациент не готов к стационару, боится огласки, испытывает стыд или сопротивление, но объективно нуждается в помощи. Попытки «перетерпеть» или лечить своими силами заканчиваются тем, что родственники дают опасные комбинации седативных, анальгетиков и «антипохмельных» средств, а состояние только ухудшается. «МедТрезвие Долгопрудный» строит выездную помощь так, чтобы она оставалась профессиональной медициной, а не косметической услугой. Уже при звонке диспетчер под контролем врача уточняет длительность запоя, виды алкоголя, наличие гипертонии, болезней сердца, печени, почек, диабета, неврологических нарушений, психических эпизодов, факт судорог, делирия в прошлом, какие лекарства уже были даны. Это позволяет заранее понять, подходит ли формат лечения на дому или сразу нужно рассматривать стационар. Выезд назначается только в тех случаях, когда это безопасно, и именно в этом ключевое отличие официальной клиники от анонимных «капельниц на дом» — здесь всегда выбирают жизнь и здоровье, а не удобный маркетинговый сценарий. Для семьи это не просто комфорт, а возможность получить помощь без риска сорваться в критическое состояние посреди ночи.
Изучить вопрос глубже – narkolog-na-dom
В таблице приведены основные компоненты инфузионной терапии, применяемые при детоксикации:
Ознакомиться с деталями – лечение в наркологической клинике
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Получить дополнительную информацию – zakazat-obratnyj-zvonok-narkologicheskaya-klinika
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Детальнее – http://www.domen.ru
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Открой скрытое – https://radiosonidogrupero.com/fortaleciendo-el-alma-presentan-estrategias-de-salud-mental-para-pastores-latinos
Фиксируем АД, ЧСС, сатурацию, температуру, оцениваем неврологический статус, степень обезвоживания, тремор, тошноту и уровень тревоги; собираем краткий анамнез последних суток и характер употребления.
Получить дополнительную информацию – http://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-stacionar-v-ehlektrostali/
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Исследовать вопрос подробнее – https://sc-germania.de/product/4443
Работа выездной службы построена так, чтобы для семьи всё было максимально понятно и предсказуемо. После звонка специалист не ограничивается общими фразами, а уточняет детали: сколько длится употребление, есть ли хронические болезни сердца, печени, почек, эндокринные нарушения, какие препараты и в каких дозах пациент уже получил, были ли в прошлом судороги, галлюцинации, тяжёлые реакции на лекарства. Это позволяет заранее оценить уровень риска и понять, подходит ли формат дома. По прибытии в Серпухове врач осматривает пациента, проверяет контакт и ориентировку, измеряет артериальное давление несколько раз, оценивает пульс, сатурацию, температуру, выраженность тремора, наличие болей, характер дыхания, степень обезвоживания. Далее формируется индивидуальная инфузионная схема: растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы, при необходимости — гепатопротекторы и мягкие антиоксидантные комплексы, противорвотные для контроля тошноты, щадящие анксиолитики для нормализации сна без грубой седации. Во время процедуры врач контролирует динамику, меняет скорость капельницы при необходимости, отслеживает реакцию на препараты и объясняет родным, какие изменения будут происходить по часам. По завершении визита пациент и родственники получают подробный план: режим, питьё, питание, чего нельзя, какие симптомы считаются тревожными, когда нужна повторная консультация или стационар. При выявлении опасных признаков вопрос о госпитализации поднимается честно и сразу, а не откладывается «до утра».
Получить дополнительную информацию – https://narkolog-na-dom-serpuhov10.ru
Для повышения эффективности в капельницы добавляются витамины группы B, аскорбиновая кислота, кардиопротекторы и антиоксиданты. Такая комбинация позволяет не только ускорить выведение продуктов распада алкоголя, но и предотвратить развитие постабстинентных расстройств. Благодаря точной дозировке и мягкому темпу введения растворов снижается риск побочных реакций, а восстановление проходит плавно и безопасно.
Получить больше информации – вывод из запоя вызов на дом воронеж
Лечение организовано поэтапно. Такой подход обеспечивает постепенное восстановление функций организма и исключает риск осложнений. Каждый этап терапии направлен на устранение конкретных нарушений, вызванных интоксикацией.
Получить дополнительные сведения – скорая вывод из запоя в красноярске
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Узнать больше – вывод из запоя недорого в красноярске
Такая структура терапии делает процесс максимально эффективным и безопасным.
Ознакомиться с деталями – наркологическая клиника клиника помощь омск
Наркологическая клиника «ВолгаДок Медикал» — это круглосуточная служба помощи, выстроенная вокруг принципов клинической безопасности, прозрачной коммуникации и поддержки пациента на каждом этапе. Мы соединяем стационар и выездные бригады в единую систему: первичный осмотр и стабилизация состояния, адресные инфузионные модули, мягкая коррекция сна и тревоги, последующее наблюдение с короткими «окнами» обратной связи. Все решения принимаются по показаниям и сопровождаются объяснением: какую цель преследуем, каким маркером измеряем, когда проверяем результат. Такой подход исключает хаотичные усиления, бережёт ресурс организма и даёт прогнозируемый клинический эффект.
Узнать больше – https://narcologicheskaya-klinika-saratov0.ru/
Наркологическая помощь в «ВолгаМед Тольятти» включает широкий спектр процедур и методик. Каждый случай рассматривается индивидуально, с учётом состояния пациента, стадии заболевания и сопутствующих факторов. Ниже представлена таблица с основными направлениями медицинской работы.
Узнать больше – платная наркологическая помощь в тольятти
Процесс организован так, чтобы снять с семьи хаос и дать понятный сценарий. После обращения в «РеутовМед Сервис» пациент быстро попадает в поле зрения врача: или через выезд по адресу, или через стационар, если состояние уже близко к опасному. На месте проводится полноценная оценка: давление, пульс, сатурация, температура, осмотр сердца и дыхания, степень обезвоживания, выраженность тремора, наличие рвоты, боли в груди или животе, неврологический статус, поведение, признаки психоза. На основе этих данных формируется индивидуальный план детоксикации. Стартовая инфузионная терапия подбирается с учётом возраста, массы тела, длительности запоя, сопутствующих болезней, уже принятых препаратов. В стационаре пациента размещают в безопасных условиях, контролируют динамику, корректируют дозировки, не оставляют «на самотёк». При выводе из запоя на дому врач остаётся до стабилизации, отслеживает реакцию и при первых тревожных признаках рекомендует стационар, а не уезжает «лишь бы поставил капельницу». Такой пошаговый подход позволяет не только снять острые симптомы, но и уменьшить риск осложнений — от аритмий и судорог до алкогольного делирия.
Ознакомиться с деталями – частный вывод из запоя
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Изучить вопрос глубже – narkologicheskaya-klinika-telefon
Если вы ищете готовые решения для строительства своего жилища, посетите наш сайт по адресу готовые проекты домов, чтобы найти подходящий для вас проект.
включают в себя полный набор документации для создания нового дома. Эти проекты позволяют сэкономить время и ресурсы . Благодаря этому, заказчики могут быть уверены в результате своего строительства.
Готовые проекты домов учитывают все нюансы и особенности строительства. Они включают в себя подробную документацию и чертежи . Это дает заказчикам возможность получить высококачественный дом .
Готовые проекты домов представляют собой экономически выгодное решение для строительства . Они включают в себя все необходимые документы и чертежи . Благодаря этому, заказчики могут сэкономить время и ресурсы.
Готовые проекты домов созданы опытными архитекторами и инженерами . Они обеспечивают быстрое и качественное строительство. Это дает заказчикам возможность получить готовый дом в короткие сроки .
Готовые проекты домов представляют собой комплексное решение для строительства жилья . Они созданы с учетом всех современных требований и стандартов . Благодаря этому, заказчики могут сэкономить время и ресурсы.
Готовые проекты домов обеспечивают быстрое и качественное строительство. Они содержат полное описание всех этапов строительства . Это упрощает процесс строительства и снижает риски.
Готовые проекты домов включают в себя полный набор документации для создания нового дома . Они учитывают все нюансы и особенности строительства. Благодаря этому, заказчики могут быть уверены в результате своего строительства .
Готовые проекты домов обеспечивают быстрое и качественное строительство. Они содержат полное описание всех этапов строительства . Это дает заказчикам возможность получить высококачественный дом .
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Подробнее тут – http://vyvod-iz-zapoya-v-ryazani17.ru
Фиксируем АД, ЧСС, сатурацию, температуру, оцениваем неврологический статус, степень обезвоживания, тремор, тошноту и уровень тревоги; собираем краткий анамнез последних суток и характер употребления.
Получить дополнительную информацию – http://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-klinika-v-ehlektrostali/
Ниже приведено структурированное сравнение форматов:
Получить дополнительную информацию – http://vyvod-iz-zapoya-reutov10.ru
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Полная информация здесь – http://dg162.net/wp/%D0%B2%D0%B0%D0%B6%D0%BD%D0%BE
Мы уделяем особое внимание сенсорной среде — это не «сервис ради сервиса», а клинический инструмент. Контролируем свет и звук, просим отключить уведомления на устройствах, используем тёплую воду малыми глотками, настраиваем «ритуал 60 минут» перед сном. На этом фоне инфузии переносятся ровнее, латентность засыпания сокращается, а утро встречает ясностью вместо «ваты» в голове. Конфиденциальность встроена в процессы: немаркированные выезды, нейтральные формулировки в документах, разграничение доступа к медданным и отсутствие фото/видео без письменного согласия.
Подробнее – вывод наркологическая клиника саратов
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Детальнее – вызвать врача нарколога на дом
В таблице представлены основные виды терапии, применяемые в клинике:
Узнать больше – наркологическая клиника в новокузнецке
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Разобраться лучше – https://vyvod-iz-zapoya-v-voronezhe17.ru/
Обеспечьте соответствие вашего школьного спортзала стандартам ФГОС, выбрав подходящее спортивное оборудование в спортзал школы на сайте myvoleybol.ru для создания безопасной и эффективной среды для занятий.
Тренажеры для силы, включающие гантели и эластичные ленты, обязательны для мышечного прогресса
Главным преимуществом наркологической клиники в Новокузнецке является комплексный подход к лечению. Специалисты рассматривают зависимость как заболевание, требующее системного воздействия на организм и психику. Каждый пациент получает индивидуальную программу, включающую медицинскую, психотерапевтическую и социальную помощь. Такой подход обеспечивает достижение устойчивых результатов и предотвращает рецидивы.
Ознакомиться с деталями – наркологическая клиника наркологический центр новокузнецк
Вывод из запоя — это не «волшебная капельница», а последовательная медицинская программа с чёткими целями и измеримыми маркерами. В наркологической клинике «СаратовМед Профи» маршрут строится по принципу управляемых окон: на каждом шаге команда преследует одну цель, меняет лишь один параметр и оценивает результат в заранее назначённый момент. Такой подход снижает лекарственную нагрузку, предотвращает «гонку дозировок» и делает динамику предсказуемой для пациента и близких. Конфиденциальность обеспечивается регламентом: немаркированные выезды, нейтральные формулировки в документах, «тихие» каналы связи, доступ к записям — строго по ролям.
Получить дополнительные сведения – вывод из запоя вызов в саратове
Прежде чем перейти к ориентировочным цифрам, важно подчеркнуть: цена формируется из реальных компонентов помощи — работы врача и медсестры, объёма инфузионной терапии, перечня препаратов, времени выезда и необходимости более длительного наблюдения. Никаких скрытых доплат: все дополнительные назначения согласуются заранее. Чем раньше вы обращаетесь, тем меньше объём вмешательств и, как правило, ниже итоговая стоимость — короткий эпизод проще и дешевле стабилизировать, чем «выводить» осложнения после затянутого запоя.
Получить больше информации – https://narkolog-na-dom-shchelkovo10.ru/vyzvat-narkologa-na-dom-shchelkovo/
Домашний формат особенно важен, когда пациент не готов к стационару, боится огласки, испытывает стыд или сопротивление, но объективно нуждается в помощи. Попытки «перетерпеть» или лечить своими силами заканчиваются тем, что родственники дают опасные комбинации седативных, анальгетиков и «антипохмельных» средств, а состояние только ухудшается. «МедТрезвие Долгопрудный» строит выездную помощь так, чтобы она оставалась профессиональной медициной, а не косметической услугой. Уже при звонке диспетчер под контролем врача уточняет длительность запоя, виды алкоголя, наличие гипертонии, болезней сердца, печени, почек, диабета, неврологических нарушений, психических эпизодов, факт судорог, делирия в прошлом, какие лекарства уже были даны. Это позволяет заранее понять, подходит ли формат лечения на дому или сразу нужно рассматривать стационар. Выезд назначается только в тех случаях, когда это безопасно, и именно в этом ключевое отличие официальной клиники от анонимных «капельниц на дом» — здесь всегда выбирают жизнь и здоровье, а не удобный маркетинговый сценарий. Для семьи это не просто комфорт, а возможность получить помощь без риска сорваться в критическое состояние посреди ночи.
Изучить вопрос глубже – http://www.domen.ru
Основу выездного лечения составляют капельницы, которые позволяют быстро ввести препараты в кровоток, минуя желудочно-кишечный тракт. Это обеспечивает моментальное действие и исключает раздражение слизистой. Капельницы подбираются индивидуально в зависимости от состояния пациента. Основные направления инфузионной терапии включают детоксикацию, восстановление водно-солевого баланса и поддержку работы нервной системы. Для усиления эффекта применяются витамины, антиоксиданты и препараты для защиты печени.
Получить дополнительные сведения – http://narkolog-na-dom-v-voronezhe17.ru
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Исследовать вопрос подробнее – наркологический вывод из запоя в красноярске
Выбор формата — это не вкусовщина, а баланс безопасности в конкретной клинической картине. Дом уместен, если контакт сохранён, рвота эпизодическая, давление и пульс без резких «качелей», тремор контролируемый, в квартире можно обеспечить тишину и присутствие взрослого, готового наблюдать первые 6–8 часов. Тогда выездная бригада работает на месте и выстраивает «мягкий» маршрут, где сон собирается без агрессивной седации, а инфузии идут с шаговой корректировкой темпа. Стационар предпочтителен при длительном эпизоде (3–5 суток и более), неукротимой рвоте, выраженной слабости, шаткости походки, признаках предделирия/делирия, судорожной готовности, а также у пожилых пациентов и при сочетанных диагнозах — ИБС, гипертония, диабет, хронические болезни печени/почек, неврология. Преимущество отделения — приборный мониторинг, лабораторные опции по показаниям, ночная команда и среда, где исключены лишние раздражители: это снижает «цену ошибки» и делает результат устойчивым, а не разовым «прояснением».
Получить дополнительные сведения – http://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-na-domu-v-ehlektrostali/
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Подробнее тут – https://narkolog-na-dom-shchelkovo10.ru/narkolog-na-dom-cena-shchelkovo/
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Детальнее – вывод из запоя на дому цена саратов
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Ознакомиться с деталями – запой наркологическая клиника в волгограде
купить дайсон оригинал официальный ofitsialnyj-sajt-dsn.ru .
dyson официальный сайт интернет dyson официальный сайт интернет .
дайсон россия дайсон россия .
Ниже — ключевые направления, которые логично дополняют друг друга и формируют единый маршрут лечения:
Подробнее можно узнать тут – https://narkologicheskaya-klinika-ramenskoe10.ru/
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Ознакомиться с деталями – нарколог на дом недорого в воронеже
В Воронеже клиника «ВоронежМед Альянс» предлагает комплексное лечение алкогольной и наркотической зависимости. Команда врачей, психиатров, психологов и терапевтов выстраивает индивидуальный маршрут пациента, начиная с детоксикации и заканчивая реабилитацией. Главный принцип — минимальное вмешательство при максимальной эффективности. Это означает, что терапевтические меры подбираются строго по показаниям, а медикаменты применяются только после оценки состояния и лабораторных данных.
Ознакомиться с деталями – наркологическая клиника наркологический центр воронеж
В основе работы клиники лежит принцип: зависимость — это не просто привычка и не «слабость характера», а комплексное заболевание, которое требует последовательного лечения, а не случайной капельницы по вызову. «Трезвый Шаг Раменское» отказывается от практики, когда пациенту предлагают один-единственный «волшебный» метод, не объясняя, что будет дальше. Здесь каждое обращение рассматривается в контексте стадии зависимости, общего состояния организма, психоэмоционального фона, семейной ситуации. Сначала специалисты снимают острые проявления: выход из запоя, детоксикация после употребления алкоголя, наркотиков или сочетаний, купирование абстиненции, коррекция давления, пульса, сна, тревоги. Затем формируется стабилизационный этап — подбор поддерживающих схем, работа с тягой, выравнивание эмоционального состояния. После этого при готовности пациента подключаются психотерапевтические и реабилитационные инструменты: мотивационные программы, работа с установками, триггерами, окружением. Важная особенность «Трезвый Шаг Раменское» — готовность объяснять семье и самому пациенту, зачем нужен каждый этап, какие цели у процедуры и какие результаты реально ожидать. Это снижает сопротивление, формирует доверие и делает путь не хаотичным, а управляемым.
Углубиться в тему – наркологические клиники алкоголизм
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Разобраться лучше – вывод из запоя клиника
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Подробнее тут – https://narkolog-na-dom-shchelkovo10.ru/narkolog-na-dom-cena-shchelkovo
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Разобраться лучше – http://narkologicheskaya-klinika-kolomna2-10.ru
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Подробнее – вывод из запоя вызов в волгограде
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Получить дополнительную информацию – нарколог на дом недорого уфа
дайсон официальный сайт магазины в москве ofitsialnyj-sajt-dn.ru .
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Изучить вопрос глубже – анонимный вывод из запоя
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Углубиться в тему – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru/kodirovanie-volgograd/
Каждый этап направлен на восстановление организма без стресса и перегрузки. Врачи работают деликатно, чтобы пациент чувствовал безопасность и понимал, что помощь оказывается профессионально.
Ознакомиться с деталями – https://vyvod-iz-zapoya-v-novokuzneczke17.ru/vyvod-iz-zapoya-na-domu-novokuzneczk
Важное отличие наркологической клиники «Трезвый Путь Коломна» — полный отказ от схемы «одна капельница = решение всех проблем». Детокс здесь рассматривается как необходимый старт, но не как финальная точка. Сначала специалисты снимают острые состояния: вывод из запоя, купирование абстиненции, коррекцию водно-электролитного баланса, поддержку сердца, печени и нервной системы, нормализацию сна, снижение тревоги. Когда организм перестаёт «гореть», начинается следующий этап — стабилизация: врач оценивает психическое состояние, выявляет депрессивные, тревожные, панические проявления, подбирает поддерживающие схемы, которые помогают удержаться в первые недели после кризиса. Далее подключаются психотерапевтические инструменты: индивидуальные консультации, работа с мотивацией, разбор триггеров, формирование новых привычек. В финале выстраивается маршрут поддержки: амбулаторное наблюдение, связь с клиникой, рекомендации для семьи. Такой поэтапный подход делает клинику в Коломне местом, где зависимость перестают воспринимать как «стыд» и начинают воспринимать как задачу, с которой можно работать профессионально.
Подробнее можно узнать тут – narkologicheskie-kliniki-obratnyj-zvonok
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Получить дополнительные сведения – выезд нарколога на дом
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Подробнее можно узнать тут – https://narcologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-anonimno/
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Получить дополнительные сведения – анонимная наркологическая клиника в саратове
Ключевой элемент вывода из запоя в Реутове — правильно подобранная капельница, но в «РеутовМед Сервис» её рассматривают не как волшебное средство, а как часть комплексной терапевтической схемы. Основная цель — не «вырубить» человека сильными седативными коктейлями, а помочь организму безопасно выйти из состояния интоксикации. В инфузионную терапию входят растворы для регидратации, которые восполняют потерю жидкости, снижают вязкость крови, улучшают микроциркуляцию и работу внутренних органов. Коррекция электролитного баланса помогает уменьшить дрожь, мышечную слабость, снизить риск нарушений сердечного ритма. Применяются витамины группы B и препараты магния для поддержки нервной системы, снижения раздражительности и вероятности судорог. По показаниям добавляются гепатопротекторы, мягкие антиоксиданты для разгрузки печени, противорвотные средства при выраженной тошноте, щадящие анксиолитики для снижения тревоги и нормализации сна без грубого угнетения сознания. Все дозировки учитывают сопутствующие заболевания и возраст, что особенно важно для пациентов с гипертонией, ИБС, диабетом, поражением печени и пожилых людей. Эффект оценивается по объективным критериям: стабилизация давления и пульса, уменьшение дрожи, улучшение самочувствия, нормализация сна и поведения, а не только по фразе «стал тихим».
Изучить вопрос глубже – skoraya-pomoshch-vyvoda-iz-zapoya
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Детальнее – вывод из запоя дешево
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Углубиться в тему – вывод из запоя на дому недорого красноярск
Каждое направление встроено в общую стратегию: не просто купировать симптомы, а уменьшить риск повторения сценария, когда после «облегчения» всё возвращается к прежней модели употребления.
Подробнее – http://www.domen.ru
Карта делает видимой причинно-следственную связь: пациент понимает, зачем и что именно делается; семья видит «точки проверки»; врач получает опору для изменения одного параметра без разрушения всего плана.
Выяснить больше – вывод из запоя дешево в саратове
Лечение проходит в несколько этапов: диагностика, детоксикация, медикаментозная поддержка и восстановление. Каждый этап имеет чёткие цели и критерии эффективности, что делает процесс управляемым и безопасным. Применяются препараты, сертифицированные в РФ, и только те, чья эффективность подтверждена клиническими исследованиями.
Подробнее можно узнать тут – вывод из запоя вызов на дом в волгограде
Перед цифрами важно подчеркнуть: прайс «Трезвый Центр Коломна» строится вокруг реального объёма помощи, а не вокруг рекламных обещаний. Цена зависит от тяжести состояния, длительности запоя, количества инфузий, необходимого набора препаратов, формата (дом или стационар), времени суток выезда, длительности наблюдения. Все дополнительные назначения согласуются заранее — без скрытых доплат и неожиданных строк. Это позволяет семье планировать расходы и сосредоточиться на безопасности.
Получить дополнительные сведения – вывод из запоя клиника
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Смотрите также… – https://galaxy7777777.com/2023/01/16/haku-%E3%83%A1%E3%83%A9%E3%83%8E%E3%83%95%E3%82%A9%E3%83%BC%E3%82%AB%E3%82%B9ev%E3%81%8C%E3%80%80%EF%BC%93%E6%9C%88%E3%81%AB%E6%96%B0%E7%99%BA%E5%A3%B2
Когда вопрос стоит остро — нужно быстро и безопасно вывести человека из запоя в Коломне, — у семьи нет лишнего времени на эксперименты с таблетками, сомнительными «коктейлями» и советами из интернета. «Трезвый Центр Коломна» выстраивает помощь так, чтобы от первого звонка до реального облегчения шёл понятный и управляемый маршрут: запись симптомов и рисков уже по телефону, предложение формата (выезд на дом или стационар), оперативный осмотр, персональная инфузионная терапия, круглосуточное наблюдение при необходимости и подробный план восстановления на 24–72 часа и дальше. Мы не продаём миф о «чудо-капельнице за час», а работаем клинически аккуратно: дозы и схемы подбираются под возраст, длительность запоя, сопутствующие заболевания, уже принятые лекарства и текущие показатели. Цель проста и честна — снять интоксикацию, защитить сердце, мозг и печень, вернуть сон и ясность без агрессивной седации и скрытых рисков, сохранить конфиденциальность и дать семье уверенность, что всё делается правильно.
Ознакомиться с деталями – http://www.domen.ru
melbet withdrawal problem melbet5006.ru
Ниже приведено структурированное сравнение форматов:
Узнать больше – vyvod-iz-zapoya-reutov10.ru/
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее тут – http://narcologicheskaya-klinika-saratov0.ru
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Получить дополнительные сведения – вывод из запоя капельница на дому в новокузнецке
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Углубиться в тему – кодирование от алкоголизма адрес
Капельница при вызове нарколога на дом в Долгопрудном от «МедТрезвие Долгопрудный» — это клинический инструмент, а не магический раствор. Главное правило — никакой агрессивной седации ради видимости спокойствия. Инфузионная терапия строится вокруг нескольких задач: восполнить жидкость, выровнять электролиты, снизить токсическую нагрузку на печень и мозг, поддержать сердце и нервную систему, уменьшить тремор, тревогу и соматические жалобы. Используются растворы для регидратации и коррекции водно-электролитного баланса, витамины группы B и магний для поддержки нервной системы, уменьшения риска судорог и нормализации сна, по показаниям — гепатопротекторы и мягкие антиоксиданты, противорвотные препараты для контроля тошноты. При выраженной тревоге или нарушениях сна назначаются щадящие анксиолитические средства в дозах, которые не выключают пациента полностью, а помогают снять паническое напряжение, сохраняя возможность оценивать динамику состояния. Врач отслеживает реакцию на терапию: стабилизацию давления и пульса, уменьшение дрожи, улучшение общего самочувствия, появление более спокойного, естественного сна. По мере облегчения нагрузки схема не усиливается ради счёта, а рационально сокращается. Такой подход защищает пациента от скрытых осложнений и превращает капельницу в контролируемый, полезный шаг, а не в рискованный эксперимент.
Подробнее тут – https://narkolog-na-dom-dolgoprudnij10.ru/skolko-stoit-narkolog-na-dom-v-dolgoprudnom/
Чтобы родственники не терялись в терминах и не воспринимали лечение как «чёрный ящик», в клинике используется поэтапный подход. Это помогает увидеть логическую связку между затратами, процедурами и результатами.
Ознакомиться с деталями – http://narkologicheskaya-klinika-ramenskoe10.ru
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Подробнее можно узнать тут – вывод из запоя капельница волгоград
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Изучить вопрос глубже – наркологическая клиника вывод из запоя в омске
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Хочешь знать всё? – https://puasbetbuktiwd3.xyz/index.php/bukti-wd-puasbet-17-nov-2023-sweet-bonanza-rp-2000000000-lunas
Наркологическая помощь в «ВолгаМед Тольятти» включает широкий спектр процедур и методик. Каждый случай рассматривается индивидуально, с учётом состояния пациента, стадии заболевания и сопутствующих факторов. Ниже представлена таблица с основными направлениями медицинской работы.
Узнать больше – http://narkologicheskaya-pomoshh-v-tolyatti17.ru
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Узнать больше – нарколог на дом вывод
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Подробнее – наркологическая клиника стационар
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Подробнее можно узнать тут – http://narkolog-na-dom-v-voronezhe17.ru/voronezh-narkologicheskaya-klinika/
Процесс организован так, чтобы снять с семьи хаос и дать понятный сценарий. После обращения в «РеутовМед Сервис» пациент быстро попадает в поле зрения врача: или через выезд по адресу, или через стационар, если состояние уже близко к опасному. На месте проводится полноценная оценка: давление, пульс, сатурация, температура, осмотр сердца и дыхания, степень обезвоживания, выраженность тремора, наличие рвоты, боли в груди или животе, неврологический статус, поведение, признаки психоза. На основе этих данных формируется индивидуальный план детоксикации. Стартовая инфузионная терапия подбирается с учётом возраста, массы тела, длительности запоя, сопутствующих болезней, уже принятых препаратов. В стационаре пациента размещают в безопасных условиях, контролируют динамику, корректируют дозировки, не оставляют «на самотёк». При выводе из запоя на дому врач остаётся до стабилизации, отслеживает реакцию и при первых тревожных признаках рекомендует стационар, а не уезжает «лишь бы поставил капельницу». Такой пошаговый подход позволяет не только снять острые симптомы, но и уменьшить риск осложнений — от аритмий и судорог до алкогольного делирия.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-reutov10.ru/vyvod-iz-zapoya-ryadom-v-reutove
Когда человек в запое, близким кажется, что всё ещё можно решить «по-тихому»: выспаться, отпаять водой, дать обезболивающее или «успокоительное» и дождаться, пока станет легче. На практике это часто приводит к обратному результату. Алкогольная интоксикация нарушает водно-электролитный баланс, сгущает кровь, повышает нагрузку на сердце, провоцирует скачки давления, ухудшает работу печени и нервной системы. Неконтролируемый приём снотворных, анальгетиков, транквилизаторов, особенно вместе с алкоголем, способен вызвать угнетение дыхания, аритмии, судороги или делирий. Домашняя обстановка не даёт возможности следить за всеми показателями и вовремя отреагировать. «РаменМед Трезвость» предлагает клинически выверенный вывод из запоя в Раменском с учётом возраста, длительности употребления, хронических заболеваний, перенесённых ранее осложнений. Здесь не применяют сомнительные схемы «усыпить, чтобы не мешал», а ставят задачу: безопасно пройти острую фазу, снять интоксикацию, стабилизировать давление и пульс, защитить сердце и мозг, снизить риск психозов и, при желании пациента, сразу наметить маршрут реального лечения зависимости. Такой подход снимает с родственников опасную «роль врача» и возвращает ситуацию туда, где ей место — под контроль профессионалов.
Получить больше информации – вывод из запоя капельница на дому
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Исследовать вопрос подробнее – наркология вывод из запоя волгоград
dyson магазин в спб dyson магазин в спб .
Не всегда человек способен самостоятельно прекратить приём алкоголя и восстановиться. Есть состояния, требующие немедленного вмешательства специалистов. Обратиться за помощью необходимо, если наблюдаются следующие признаки:
Исследовать вопрос подробнее – вывод из запоя на дому круглосуточно
Запой — это не просто несколько лишних дней алкоголя, а тяжёлое состояние, в котором организм работает на пределе. Чем дольше длится эпизод, тем глубже обезвоживание, тем сильнее сдвиги электролитов, тем выше риск аритмий, гипертонических кризов, судорог, делирия, обострений заболеваний сердца, печени и поджелудочной железы. Попытки «вывести» человека дома силами родных часто включают опасные комбинации: случайные седативные, снотворные, анальгетики, «антипохмельные» из рекламы. Они могут на время усыпить или «успокоить», но при этом скрывают ухудшение, сбивают давление, угнетают дыхание и мешают врачу увидеть реальную картину. В «Трезвый Центр Коломна» подход другой: ещё на этапе звонка специалист уточняет длительность запоя, объёмы и виды алкоголя, наличие гипертонии, ИБС, диабета, заболеваний печени и почек, неврологических проблем, список уже принятых препаратов, эпизоды потери сознания, судорог, странного поведения. На основании этих данных определяется, безопасен ли формат на дому или сразу нужен стационар. Такая сортировка позволяет вовремя перехватить опасные случаи, не терять часы на бесполезные попытки и сразу запускать те схемы, которые реально снижают риски и стабилизируют состояние.
Подробнее – https://vyvod-iz-zapoya-kolomna10.ru/vyvod-iz-zapoya-na-domu-v-kolomne/
дайсон официальный интернет магазин в москве ofitsialnyj-sajt-dn-1.ru .
dyson москва официальный ofitsialnyj-sajt-dsn.ru .
В таблице приведены основные компоненты инфузионной терапии, применяемые при детоксикации:
Ознакомиться с деталями – наркологическая клиника нарколог
букмекерские конторы бишкек http://mostbet2029.help
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Открой скрытое – https://zelfrijdendetaxiamsterdam.nl/blog/4x-voordelen-van-een-auto-importeren
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Получить больше информации – вывод из запоя в стационаре в саратове
Профессиональный нарколог на дому не работает по схеме «чем больше препаратов, тем лучше». В «СерпуховТрезвие» капельницы составляются исходя из задач конкретного организма. Базовый блок — это растворы для восполнения объёма циркулирующей жидкости, выравнивания электролитного баланса и коррекции кислотно-щелочного состояния, что уменьшает нагрузку на сердце, мозг и снижает риск тяжёлых осложнений. Витамины группы B и магний входят в стандартную поддержку: они помогают стабилизировать нервную систему, уменьшить тремор, раздражительность, поддерживают сон и снижают риск судорог. При признаках поражения печени используются гепатопротективные и антиоксидантные компоненты, снижающие токсическое воздействие продуктов распада алкоголя. Если пациента мучает тошнота, добавляются противорвотные средства, чтобы восстановить возможность пить воду и питаться. Для снижения тревоги и нормализации сна применяются мягкие анксиолитики в дозировках, не маскирующих клиническую картину и не угнетающих дыхательный центр. Агрессивная седация, популярная в «серых» схемах, сознательно исключается: она «делает вид» улучшения, но может скрыть нарастающие осложнения. Эффект оценивается по конкретным критериям: стабилизация давления и пульса, уменьшение тремора, уход тошноты, улучшение цвета кожи, появление естественного сна и большей ясности мышления. После достижения этих ориентиров фармаконагрузка не наращивается, а постепенно снижается, чтобы человек выходил в устойчивое состояние, а не зависел от бесконечных капельниц.
Углубиться в тему – срочно врач нарколог на дом
Критичные случаи, когда вызов нарколога через «МедТрезвие Долгопрудный» оправдан и своевременен:
Получить дополнительную информацию – https://narkolog-na-dom-dolgoprudnij10.ru/vyezd-narkologa-na-dom-v-dolgoprudnom/
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Смотрите также… – https://flowandgrowni.com/hello-world
Клиника «Трезвый Шаг Раменское» выстраивает помощь так, чтобы пациент и его близкие не метались между разными службами и частными «специалистами», а получали комплекс услуг в одном месте. Это особенно важно для тех, кто уже сталкивался с провалами после разовых кодировок, неподходящих капельниц или формальной «помощи».
Подробнее можно узнать тут – лечение в наркологической клинике
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Подробнее – https://narkologicheskaya-klinika-v-volgograde17.ru/narkologi-volgograda
Вывод из запоя — это не просто медицинская процедура, а жизненно важный этап, позволяющий вернуть контроль над самочувствием и предотвратить осложнения. В клинике «РеабКузбасс» пациенты получают помощь в любое время суток: опытные наркологи выезжают на дом, проводят капельницы и медикаментозную детоксикацию, подбирают индивидуальные схемы восстановления. Такой подход помогает не только устранить последствия запоя, но и запустить процесс полноценного оздоровления организма.
Получить больше информации – врач вывод из запоя
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Смотрите также… – https://faculdadecci.com.br/events/change-career-to-teaching
Процесс кодирования проходит в комфортной и спокойной обстановке. Врач объясняет каждый этап, чтобы пациент чувствовал себя уверенно и спокойно. После процедуры пациент получает памятку с рекомендациями по уходу за здоровьем и режиму поведения в первые недели после лечения.
Узнать больше – кодирование от алкоголизма цена волгоград
Эти методы комбинируются и создают условия для всестороннего восстановления пациента.
Разобраться лучше – частная наркологическая клиника
Комплексный подход обеспечивает не только снятие симптомов, но и полное восстановление функций организма. Пациент получает поддержку на всех этапах — от детоксикации до социальной адаптации.
Подробнее – нарколог наркологическая помощь тольятти
Эти методы комбинируются и создают условия для всестороннего восстановления пациента.
Получить дополнительные сведения – лечение в наркологической клинике
дайсон оригинал купить ofitsialnyj-sajt-dn.ru .
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Ознакомиться с деталями – вызвать врача нарколога на дом в уфе
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Детальнее – врач нарколог на дом воронеж
Комплексная терапия включает несколько последовательных этапов, обеспечивающих полное восстановление организма и личности пациента. Каждый из них направлен на решение конкретных задач — от устранения интоксикации до закрепления устойчивой ремиссии.
Получить дополнительную информацию – лечение в наркологической клинике
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Получить дополнительную информацию – врач нарколог выезд на дом уфа
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Подробности по ссылке – https://carpasferrari.com/hello-world
Формат помощи
Разобраться лучше – vyvod-iz-zapoya-deshev-reutove
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Разобраться лучше – вывод из запоя с выездом
Ниже — примерная структура пакетов, которую можно использовать как ориентир (не публичная оферта):
Ознакомиться с деталями – http://narkolog-na-dom-shchelkovo10.ru
В основе работы клиники лежит принцип: зависимость — это не просто привычка и не «слабость характера», а комплексное заболевание, которое требует последовательного лечения, а не случайной капельницы по вызову. «Трезвый Шаг Раменское» отказывается от практики, когда пациенту предлагают один-единственный «волшебный» метод, не объясняя, что будет дальше. Здесь каждое обращение рассматривается в контексте стадии зависимости, общего состояния организма, психоэмоционального фона, семейной ситуации. Сначала специалисты снимают острые проявления: выход из запоя, детоксикация после употребления алкоголя, наркотиков или сочетаний, купирование абстиненции, коррекция давления, пульса, сна, тревоги. Затем формируется стабилизационный этап — подбор поддерживающих схем, работа с тягой, выравнивание эмоционального состояния. После этого при готовности пациента подключаются психотерапевтические и реабилитационные инструменты: мотивационные программы, работа с установками, триггерами, окружением. Важная особенность «Трезвый Шаг Раменское» — готовность объяснять семье и самому пациенту, зачем нужен каждый этап, какие цели у процедуры и какие результаты реально ожидать. Это снижает сопротивление, формирует доверие и делает путь не хаотичным, а управляемым.
Ознакомиться с деталями – наркологическая клиника
Основные признаки, при которых необходим вывод из запоя:
Получить дополнительные сведения – наркология вывод из запоя тольятти
Вывод из запоя в Рязани — это профессиональная медицинская процедура, направленная на очищение организма от токсинов, восстановление нормального самочувствия и предотвращение осложнений после длительного употребления алкоголя. В специализированных клиниках города лечение проводится с использованием современных методов детоксикации и под контролем опытных врачей-наркологов. Такой подход позволяет быстро и безопасно стабилизировать состояние пациента, устранить физическую зависимость и подготовить организм к дальнейшему восстановлению.
Детальнее – анонимный вывод из запоя рязань
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Изучить вопрос глубже – вывод из запоя в стационаре в саратове
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Исследовать вопрос подробнее – вывод из запоя цена в волгограде
Запой — это не просто несколько лишних дней алкоголя, а тяжёлое состояние, в котором организм работает на пределе. Чем дольше длится эпизод, тем глубже обезвоживание, тем сильнее сдвиги электролитов, тем выше риск аритмий, гипертонических кризов, судорог, делирия, обострений заболеваний сердца, печени и поджелудочной железы. Попытки «вывести» человека дома силами родных часто включают опасные комбинации: случайные седативные, снотворные, анальгетики, «антипохмельные» из рекламы. Они могут на время усыпить или «успокоить», но при этом скрывают ухудшение, сбивают давление, угнетают дыхание и мешают врачу увидеть реальную картину. В «Трезвый Центр Коломна» подход другой: ещё на этапе звонка специалист уточняет длительность запоя, объёмы и виды алкоголя, наличие гипертонии, ИБС, диабета, заболеваний печени и почек, неврологических проблем, список уже принятых препаратов, эпизоды потери сознания, судорог, странного поведения. На основании этих данных определяется, безопасен ли формат на дому или сразу нужен стационар. Такая сортировка позволяет вовремя перехватить опасные случаи, не терять часы на бесполезные попытки и сразу запускать те схемы, которые реально снижают риски и стабилизируют состояние.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-kolomna10.ru/
Клиника «ВоронежМед Альянс» придерживается принципа прозрачной медицины: каждый шаг понятен пациенту, решения принимаются совместно, а результаты фиксируются по объективным показателям. Такой формат создаёт чувство безопасности и доверия. Среди основных принципов:
Подробнее можно узнать тут – http://narcologicheskaya-klinika-v-voronezhe17.ru
Наркологическая клиника в Новокузнецке предоставляет профессиональную помощь людям, столкнувшимся с зависимостью от алкоголя, наркотиков и психоактивных веществ. Лечение проводится под наблюдением опытных специалистов с применением современных медицинских методик. Основная цель работы клиники — не только устранить физическую зависимость, но и восстановить психологическое равновесие пациента, вернуть мотивацию и способность жить без употребления веществ.
Получить больше информации – http://narkologicheskaya-clinica-v-novokuzneczke17.ru
Наркологическая клиника «ВолгаДок Медикал» — это круглосуточная служба помощи, выстроенная вокруг принципов клинической безопасности, прозрачной коммуникации и поддержки пациента на каждом этапе. Мы соединяем стационар и выездные бригады в единую систему: первичный осмотр и стабилизация состояния, адресные инфузионные модули, мягкая коррекция сна и тревоги, последующее наблюдение с короткими «окнами» обратной связи. Все решения принимаются по показаниям и сопровождаются объяснением: какую цель преследуем, каким маркером измеряем, когда проверяем результат. Такой подход исключает хаотичные усиления, бережёт ресурс организма и даёт прогнозируемый клинический эффект.
Подробнее тут – лечение в наркологической клинике
Капельница при вызове нарколога на дом в Долгопрудном от «МедТрезвие Долгопрудный» — это клинический инструмент, а не магический раствор. Главное правило — никакой агрессивной седации ради видимости спокойствия. Инфузионная терапия строится вокруг нескольких задач: восполнить жидкость, выровнять электролиты, снизить токсическую нагрузку на печень и мозг, поддержать сердце и нервную систему, уменьшить тремор, тревогу и соматические жалобы. Используются растворы для регидратации и коррекции водно-электролитного баланса, витамины группы B и магний для поддержки нервной системы, уменьшения риска судорог и нормализации сна, по показаниям — гепатопротекторы и мягкие антиоксиданты, противорвотные препараты для контроля тошноты. При выраженной тревоге или нарушениях сна назначаются щадящие анксиолитические средства в дозах, которые не выключают пациента полностью, а помогают снять паническое напряжение, сохраняя возможность оценивать динамику состояния. Врач отслеживает реакцию на терапию: стабилизацию давления и пульса, уменьшение дрожи, улучшение общего самочувствия, появление более спокойного, естественного сна. По мере облегчения нагрузки схема не усиливается ради счёта, а рационально сокращается. Такой подход защищает пациента от скрытых осложнений и превращает капельницу в контролируемый, полезный шаг, а не в рискованный эксперимент.
Ознакомиться с деталями – психиатр нарколог на дом
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Это ещё не всё… – https://www.thegymhuissen.nl/product/everest-mountain
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Получить дополнительную информацию – вывод из запоя на дому недорого новокузнецк
Эти методы комбинируются и создают условия для всестороннего восстановления пациента.
Узнать больше – вывод наркологическая клиника в омске
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Подробнее тут – наркологический вывод из запоя
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Выяснить больше – http://narkolog-na-dom-shchelkovo10.ru/vrach-narkolog-na-dom-shchelkovo/
Во время процедуры врач фиксирует ключевые параметры, чтобы убедиться в безопасности и эффективности терапии. Мониторинг проводится при каждом выезде и помогает отслеживать динамику в режиме реального времени. В таблице ниже указаны основные показатели, за которыми следит специалист.
Выяснить больше – выезд нарколога на дом в воронеже
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Изучить вопрос глубже – круглосуточная наркологическая помощь
Важное отличие клиники — отказ от примитивной схемы «капельница — домой — дальше сам». Такой формат даёт кратковременное облегчение, но не решает ни причин, ни структуры зависимости. «КоломнаМед Центр» выстраивает ступенчатый подход. Первый шаг — безопасная детоксикация: снятие абстиненции, коррекция водно-электролитного баланса, поддержка сердечно-сосудистой системы, печени, нервной системы, нормализация сна. Второй шаг — стабилизация: оценка психического состояния, выявление тревожных, депрессивных и панических симптомов, подбор поддерживающих схем, которые помогают не сорваться сразу после выхода из острых проявлений. Третий шаг — реабилитация и мотивация: психотерапевтическая работа, групповые и индивидуальные форматы, обучение навыкам трезвой жизни, работа с триггерами, укрепление внутренней мотивации. Четвёртый шаг — постреабилитационная поддержка: контрольные приёмы, дистанционные консультации, помощь в профилактике срывов. Такой комплексный путь не ломает пациента, а возвращает ему контроль: не через страх, а через понимание, структуру и реальные инструменты.
Выяснить больше – наркологическая клиника доктор
Пациент может выбрать анонимный формат — все данные защищены, а пребывание в клинике проходит в атмосфере уважения и деликатности. Особое внимание уделяется созданию комфортных условий: палаты оснащены системой вентиляции, регулируемым освещением и кнопкой вызова медперсонала. Круглосуточный контроль состояния позволяет своевременно реагировать на малейшие изменения и корректировать курс лечения.
Ознакомиться с деталями – наркологическая клиника цены воронеж
При появлении таких симптомов важно не откладывать вызов врача. Самолечение, особенно с использованием неизвестных препаратов, может привести к тяжёлым последствиям, включая судороги и инсульт. Врачи клиники «ВолгаМед Резолюция» приезжают на дом с необходимыми средствами для оказания экстренной помощи и стабилизации состояния уже на месте.
Подробнее тут – нарколог на дом вывод из запоя волгоград
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Подробнее – https://vivod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-volgograd/
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Детали по клику – https://mascotas.alimentosmor.com.sv/the-best-organic-cbd-oil-for-dogs
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Подробнее тут – вызов нарколога на дом в уфе
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Ознакомиться с деталями – http://vyvod-iz-zapoya-saratov0.ru/vyvod-iz-zapoya-saratov-staczionar/https://vyvod-iz-zapoya-saratov0.ru
Visit Site – Layout is crisp, browsing is easy, and content feels trustworthy and clear.
Основу выездного лечения составляют капельницы, которые позволяют быстро ввести препараты в кровоток, минуя желудочно-кишечный тракт. Это обеспечивает моментальное действие и исключает раздражение слизистой. Капельницы подбираются индивидуально в зависимости от состояния пациента. Основные направления инфузионной терапии включают детоксикацию, восстановление водно-солевого баланса и поддержку работы нервной системы. Для усиления эффекта применяются витамины, антиоксиданты и препараты для защиты печени.
Подробнее можно узнать тут – частный нарколог на дом в воронеже
Запой — это не просто несколько лишних дней алкоголя, а тяжёлое состояние, в котором организм работает на пределе. Чем дольше длится эпизод, тем глубже обезвоживание, тем сильнее сдвиги электролитов, тем выше риск аритмий, гипертонических кризов, судорог, делирия, обострений заболеваний сердца, печени и поджелудочной железы. Попытки «вывести» человека дома силами родных часто включают опасные комбинации: случайные седативные, снотворные, анальгетики, «антипохмельные» из рекламы. Они могут на время усыпить или «успокоить», но при этом скрывают ухудшение, сбивают давление, угнетают дыхание и мешают врачу увидеть реальную картину. В «Трезвый Центр Коломна» подход другой: ещё на этапе звонка специалист уточняет длительность запоя, объёмы и виды алкоголя, наличие гипертонии, ИБС, диабета, заболеваний печени и почек, неврологических проблем, список уже принятых препаратов, эпизоды потери сознания, судорог, странного поведения. На основании этих данных определяется, безопасен ли формат на дому или сразу нужен стационар. Такая сортировка позволяет вовремя перехватить опасные случаи, не терять часы на бесполезные попытки и сразу запускать те схемы, которые реально снижают риски и стабилизируют состояние.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-kolomna10.ru
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Узнать больше – вывод наркологическая клиника
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее тут – http://narcologicheskaya-klinika-saratov0.ru
dyson пылесос купить интернет магазин dn-kupit-2.ru .
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Выяснить больше – лечение в наркологической клинике в воронеже
дайсон москва официальный ofitsialnyj-sajt-dn-1.ru .
Все процедуры выполняются анонимно и с соблюдением медицинских стандартов. Препараты применяются только сертифицированные, рассчитанные на мягкое восстановление организма без побочных эффектов. При необходимости лечение продолжается в стационаре, где пациент получает круглосуточное наблюдение, питание и психологическую поддержку.
Изучить вопрос глубже – вывод из запоя клиника новокузнецк
need a video? video production company in italy offering full-cycle services: concept, scripting, filming, editing and post-production. Commercials, corporate videos, social media content and branded storytelling. Professional crew, modern equipment and a creative approach tailored to your goals.
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Изучить вопрос глубже – вывод из запоя в стационаре
Во время лечения фиксируются все жизненные показатели пациента. При необходимости проводится экспресс-анализ крови и ЭКГ. Ниже представлена таблица, показывающая, какие параметры контролируются и по каким признакам оценивается стабилизация состояния.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-v-voronezhe17.ru
Одним из ключевых направлений работы клиники является проведение инфузионных процедур. Капельницы позволяют вывести токсины, нормализовать давление и улучшить общее состояние пациента. Подбор препаратов проводится индивидуально, с учётом физического состояния, возраста и стадии зависимости.
Узнать больше – экстренная наркологическая помощь тольятти
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Смотрите также… – https://bbwomenshealth.ca/portfolio/cutting-edge-couture-avant-garde-fashion-design
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Подробнее можно узнать тут – срочный вывод из запоя в красноярске
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Углубиться в тему – вывод из запоя на дому цена
дайсон фен купить в москве официальный ofitsialnyj-sajt-dn.ru .
Лечение в клинике «ВоронежМед Альянс» проходит поэтапно. Каждый модуль имеет определённую цель и собственные критерии эффективности. Такой подход исключает избыточное вмешательство и обеспечивает прозрачность процесса восстановления.
Получить больше информации – http://narcologicheskaya-klinika-v-voronezhe17.ru
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Желаете узнать подробности? – https://informatusa.com/donde-cambiar-un-ticket-de-loteria-en-new-york
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Есть чему поучиться – https://vistoweekly.com/unlocking-the-power-of-myliberla-com-for-home-based-entrepreneurs
Вывод из запоя на дому возможен только при относительно контролируемом состоянии и после очной оценки нарколога. В таких случаях специалист выезжает в Раменском, проводит осмотр, назначает индивидуальную капельницу, остаётся до стабилизации состояния и оставляет подробные рекомендации. Важный момент — честность: если во время осмотра врач видит риски (нестабильное давление, признаки начинающегося делирия, серьёзные боли, глубокую дезориентацию), формат на дому не навязывается, а предлагается стационар. Именно это отличает клинику от анонимных «служб капельниц», для которых любая заявка — повод заработать, независимо от последствий.
Получить дополнительную информацию – http://vyvod-iz-zapoya-ramenskoe10.ru/vyvod-iz-zapoya-ryadom-v-ramenskom/https://vyvod-iz-zapoya-ramenskoe10.ru
Острый эпизод запоя — это не «плохое самочувствие», а состояние с реальными рисками для сердца, нервной системы и дыхания, особенно в ночные часы, когда усиливаются вегетативные реакции и тревога. В «НоваТрезвие» мы выстраиваем помощь так, чтобы от звонка до заметного облегчения прошло как можно меньше времени и как можно меньше случайностей: короткое интервью для оценки рисков, выезд врача или приём в клинике, экспресс-диагностика по ключевым показателям, персональная инфузионная схема без «универсальных коктейлей», мягкая коррекция сна и тревоги без «вырубания», понятные инструкции семье на 24–72 часа и план продолжения на ближайшие недели. Мы не скрываемся за общими формулами: решения принимаются по фактическим данным, дозы и темп капельниц подстраиваются к динамике каждые 15–20 минут, а при «красных флагах» перевод в стационар организуется без пауз. Конфиденциальность соблюдается строго, а коммуникация простая и предсказуемая — чтобы вы всегда знали, что происходит сейчас и чего ждать к утру.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-ehlektrostal2-10.ru
Лечение проходит в несколько этапов: диагностика, детоксикация, медикаментозная поддержка и восстановление. Каждый этап имеет чёткие цели и критерии эффективности, что делает процесс управляемым и безопасным. Применяются препараты, сертифицированные в РФ, и только те, чья эффективность подтверждена клиническими исследованиями.
Получить больше информации – http://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-voronezh/
Профессиональный нарколог на дому не работает по схеме «чем больше препаратов, тем лучше». В «СерпуховТрезвие» капельницы составляются исходя из задач конкретного организма. Базовый блок — это растворы для восполнения объёма циркулирующей жидкости, выравнивания электролитного баланса и коррекции кислотно-щелочного состояния, что уменьшает нагрузку на сердце, мозг и снижает риск тяжёлых осложнений. Витамины группы B и магний входят в стандартную поддержку: они помогают стабилизировать нервную систему, уменьшить тремор, раздражительность, поддерживают сон и снижают риск судорог. При признаках поражения печени используются гепатопротективные и антиоксидантные компоненты, снижающие токсическое воздействие продуктов распада алкоголя. Если пациента мучает тошнота, добавляются противорвотные средства, чтобы восстановить возможность пить воду и питаться. Для снижения тревоги и нормализации сна применяются мягкие анксиолитики в дозировках, не маскирующих клиническую картину и не угнетающих дыхательный центр. Агрессивная седация, популярная в «серых» схемах, сознательно исключается: она «делает вид» улучшения, но может скрыть нарастающие осложнения. Эффект оценивается по конкретным критериям: стабилизация давления и пульса, уменьшение тремора, уход тошноты, улучшение цвета кожи, появление естественного сна и большей ясности мышления. После достижения этих ориентиров фармаконагрузка не наращивается, а постепенно снижается, чтобы человек выходил в устойчивое состояние, а не зависел от бесконечных капельниц.
Изучить вопрос глубже – http://narkolog-na-dom-serpuhov10.ru/narkolog-psiholog-na-dom-serpuhov/
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Получить больше информации – kapelnicza-ot-zapoya-v-volgograde17.ru/
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Узнать больше – анонимный вывод из запоя
Процесс включает несколько шагов:
Подробнее – http://narkolog-na-dom-v-ufe17.ru/
Во время лечения фиксируются все жизненные показатели пациента. При необходимости проводится экспресс-анализ крови и ЭКГ. Ниже представлена таблица, показывающая, какие параметры контролируются и по каким признакам оценивается стабилизация состояния.
Выяснить больше – помощь вывод из запоя
Ниже — примерная структура пакетов, которую можно использовать как ориентир (не публичная оферта):
Выяснить больше – запой нарколог на дом цена
«РаменМед Трезвость» предлагает несколько форматов помощи, но выбор всегда делается из соображений безопасности, а не удобства картинки. Стационарный вывод из запоя подходит в ситуациях, когда запой длится несколько дней или недель, есть скачки давления, проблемы с сердцем, печени, сахарный диабет, неврологические заболевания, эпизоды судорог или делирия в анамнезе, возраст старше 50–55 лет, выраженная слабость, тахикардия, невозможность пить воду, угрозы психозов. В стационаре пациент находится под наблюдением круглосуточно: контролируются жизненные показатели, вовремя корректируется терапия, есть возможность экстренно отреагировать на осложнения. Это гарантированно безопаснее, чем оставлять тяжёлого человека дома под наблюдением уставших родственников.
Детальнее – http://vyvod-iz-zapoya-ramenskoe10.ru
Выезд нарколога на дом в Серпухове — это возможность получить профессиональную помощь в условиях, когда везти человека в клинику сложно, опасно или он категорически отказывается от госпитализации. Специалисты «СерпуховТрезвие» работают круглосуточно, приезжают по адресу с одноразовыми системами, стерильными расходниками и необходимым набором препаратов, проводят осмотр, оценивают жизненно важные показатели, подбирают индивидуальную капельницу, контролируют реакцию и оставляют подробные рекомендации. Всё происходит конфиденциально, без лишних свидетелей, без осуждения и давления. Цель — не формально «поставить капельницу», а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, уменьшить тревогу и вернуть человеку возможность нормально спать и восстанавливаться, не доводя до осложнений и экстренной госпитализации.
Разобраться лучше – нарколог на дом срочно
Одним из ключевых направлений работы клиники является проведение инфузионных процедур. Капельницы позволяют вывести токсины, нормализовать давление и улучшить общее состояние пациента. Подбор препаратов проводится индивидуально, с учётом физического состояния, возраста и стадии зависимости.
Подробнее – платная наркологическая скорая помощь
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Детальнее – https://narcologicheskaya-klinika-v-novokuzneczke17.ru/
Маршрут организован так, чтобы убрать хаос и сделать шаги понятными для родственников. После звонка оператор под контролем врача уточняет длительность употребления, примерные объёмы алкоголя, хронические болезни (гипертония, ИБС, диабет, заболевания печени, почек, нервной системы), список уже принятых лекарств, эпизоды потери сознания, судорог, подозрительные психические симптомы. На этом этапе принимается базовое решение: возможно ли безопасно провести детокс на дому либо показан стационар. Врач приезжает по адресу в Щёлково, проводит осмотр: фиксирует АД, ЧСС, сатурацию, температуру, оценивает тремор, координацию, речь, поведение, уровень сознания, степень обезвоживания. Затем подбирается индивидуальная инфузионная схема: растворы для регидратации, коррекции электролитов и кислотно-щелочного баланса, витамины группы B и магний для поддержки нервной системы и снижения тремора; по показаниям — гепатопротекторы, мягкие антиоксиданты, противорвотные, щадящие анксиолитики для сна, но без грубого «выключения». Во время процедуры врач наблюдает за динамикой, при необходимости меняет скорость капельницы, контролирует давление и пульс, следит за реакцией на препараты. В финале даёт подробные рекомендации: как вести себя ближайшие 24–72 часа, как спать, что пить и есть, каких лекарств избегать, какие симптомы считать тревожными, когда нужно немедленно звонить и когда стоит рассмотреть стационар. Если уже на этапе осмотра понятно, что дому «тесно» по безопасности, перевод в клинику организуется без задержек.
Разобраться лучше – нарколог щёлково
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Получить дополнительную информацию – вывод из запоя на дому в новокузнецке
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Углубиться в тему – narkologicheskaya-klinika-v-volgograde17.ru/
Во время процедуры врач фиксирует ключевые параметры, чтобы убедиться в безопасности и эффективности терапии. Мониторинг проводится при каждом выезде и помогает отслеживать динамику в режиме реального времени. В таблице ниже указаны основные показатели, за которыми следит специалист.
Узнать больше – вызвать нарколога на дом воронеж
Когда человек в запое, близким кажется, что всё ещё можно решить «по-тихому»: выспаться, отпаять водой, дать обезболивающее или «успокоительное» и дождаться, пока станет легче. На практике это часто приводит к обратному результату. Алкогольная интоксикация нарушает водно-электролитный баланс, сгущает кровь, повышает нагрузку на сердце, провоцирует скачки давления, ухудшает работу печени и нервной системы. Неконтролируемый приём снотворных, анальгетиков, транквилизаторов, особенно вместе с алкоголем, способен вызвать угнетение дыхания, аритмии, судороги или делирий. Домашняя обстановка не даёт возможности следить за всеми показателями и вовремя отреагировать. «РаменМед Трезвость» предлагает клинически выверенный вывод из запоя в Раменском с учётом возраста, длительности употребления, хронических заболеваний, перенесённых ранее осложнений. Здесь не применяют сомнительные схемы «усыпить, чтобы не мешал», а ставят задачу: безопасно пройти острую фазу, снять интоксикацию, стабилизировать давление и пульс, защитить сердце и мозг, снизить риск психозов и, при желании пациента, сразу наметить маршрут реального лечения зависимости. Такой подход снимает с родственников опасную «роль врача» и возвращает ситуацию туда, где ей место — под контроль профессионалов.
Подробнее – срочное выведение из запоя
бытовая техника dyson бытовая техника dyson .
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
А что дальше? – https://cabinet-de-shiatsu-reunion.com
Игнорирование этих симптомов может привести к тяжёлым последствиям — судорогам, галлюцинациям или алкогольному психозу.
Получить дополнительную информацию – вывод из запоя круглосуточно
В таблице представлены основные виды терапии, применяемые в клинике:
Получить дополнительные сведения – https://narcologicheskaya-klinika-v-novokuzneczke17.ru/narkologicheskij-czentr-novokuzneczk/
Саратов живёт в разных темпах: плотный центр, протяжные магистрали, мостовые переезды. Мы учитываем это в логистике: выездные бригады «СаратовМед Профи» движутся по немаркированным маршрутам, приезжают в гражданской одежде, формируют на месте «тихую сцену» и только затем начинают клиническую часть. Если на предзвонке звучат «красные флаги» — давящая боль в груди, выраженная одышка, спутанность, неукротимая рвота, судороги — организуем перевод в стационар без пауз: место резервируем заранее, передислокация проходит конфиденциально.
Углубиться в тему – http://www.domen.ru
Вывод из запоя в Рязани — это профессиональная медицинская процедура, направленная на очищение организма от токсинов, восстановление нормального самочувствия и предотвращение осложнений после длительного употребления алкоголя. В специализированных клиниках города лечение проводится с использованием современных методов детоксикации и под контролем опытных врачей-наркологов. Такой подход позволяет быстро и безопасно стабилизировать состояние пациента, устранить физическую зависимость и подготовить организм к дальнейшему восстановлению.
Узнать больше – вывод из запоя на дому недорого
Инфузионная терапия подбирается под человека, а не под «среднюю» ситуацию. Базовый каркас обычно включает растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы. По показаниям добавляются гепатопротекторы и антиоксидантные компоненты — это помогает печени и снижает оксидативный стресс. Если есть выраженная тошнота, подключаем противорвотные; при тревоге и нарушении сна — мягкие анксиолитики и седативные препараты, которые не «вырубают», а выравнивают ритмы и сохраняют контакт для мониторинга. Мы избегаем агрессивных «миксов», потому что избыточная седация может скрыть опасные симптомы и усложнить оценку состояния. Эффективность оцениваем не только по субъективному облегчению, но и по объективным метрикам: пульс, давление, сатурация, динамика тремора, аппетит, качество сна. Как только показатели стабилизируются, фарм-нагрузка снижается, а ведущую роль берет режим — питание, гидратация, спокойный вечерний ритуал, короткие бытовые активности.
Подробнее тут – vyvod iz zapoya krasnogorsk
Клиника «ВоронежМед Альянс» придерживается принципа прозрачной медицины: каждый шаг понятен пациенту, решения принимаются совместно, а результаты фиксируются по объективным показателям. Такой формат создаёт чувство безопасности и доверия. Среди основных принципов:
Получить больше информации – https://narcologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-anonimno/
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Углубиться в тему – платная наркологическая клиника
Цель и ожидаемая динамика
Углубиться в тему – http://narkologicheskaya-klinika-odincovo0.ru
Что включено на практике
Выяснить больше – https://narkologicheskaya-klinika-shchyolkovo0.ru/anonimnaya-narkologicheskaya-klinika-v-shchyolkovo
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Уточнить детали – https://flyinmadinah.com/nature-holiday-quotes
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Получить дополнительную информацию – https://narkolog-na-dom-v-ufe17.ru/
dyson официальный интернет магазин в россии ofitsialnyj-sajt-dn-1.ru .
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Лучшее решение — прямо здесь – https://vistoweekly.com/finn-william-leeves-coben
Вывод из запоя — это всегда баланс между скоростью и безопасностью. Дома трудно заметить скрытые ухудшения, особенно ночью: давление и пульс «гуляют», нарастает обезвоживание, сон рваный и тревожный. В «Трезвом Контуре» этот хаос замещается управляемостью: перед выездом дежурный врач собирает ключевые данные (длительность эпизода, лекарства, аллергии, сопутствующие болезни), на месте проводится экспресс-диагностика (АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания), затем запускается схема терапевтической поддержки. Мы постоянно «подстраиваем» инфузии по реакции организма, а не по шаблонной карте: где-то важнее регидратация, где-то — коррекция электролитов, где-то — бережная седация для ночи. Для семьи это значит одно: меньше догадок, больше ясности. Если по картине риски высоки, мы аргументированно предлагаем стационар в Одинцово — и организуем транспортировку без пауз, потому что цена задержки в такие часы всегда выше.
Подробнее тут – вывести из запоя одинцово
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Выяснить больше – http://vyvod-iz-zapoya-v-tyumeni17.ru/vyvod-iz-zapoya-v-staczionare-tyumen/
Такая структура терапии делает процесс максимально эффективным и безопасным.
Выяснить больше – наркологические клиники алкоголизм
Мы выезжаем в любое время дня и ночи. Организационно всё просто: короткий звонок с описанием состояния, согласование адреса и времени, консультация по подготовке помещения, приезд врача. Если состояние тяжёлое (длительный запой, возраст 60+, выраженная соматика, признаки делирия, многократная рвота, спутанность сознания), медик предложит стационар сразу — это безопаснее, чем пытаться «дотянуть» ночь дома. В клинике пациент находится под круглосуточным наблюдением, при необходимости выполняются дополнительные исследования, расширяется объём инфузий, корректируется медикаментозная схема. Для пожилых и кардиологических пациентов стационарный формат часто предпочтителен: непрерывный мониторинг снижает риски и ускоряет стабилизацию.
Исследовать вопрос подробнее – vyvod iz zapoya koroleva
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Подробнее – платная наркологическая клиника омск
Для тех, кто предпочитает лечение в условиях стационара, предусмотрены комфортные палаты, медицинский контроль 24/7 и возможность консультаций с психотерапевтом. Врачи клиники применяют комплексные методы, направленные не только на снятие симптомов, но и на устранение причин зависимости.
Получить дополнительные сведения – срочная наркологическая помощь
Формат
Изучить вопрос глубже – narkologicheskaya-klinika-ceny
mostbet история компании https://www.mostbet2031.help
Системный подход позволяет достичь максимальной эффективности лечения и снизить риск возврата к зависимости.
Ознакомиться с деталями – наркологическая клиника клиника помощь
После первичной стабилизации врач обычно объясняет близким, почему «просто поспать» не всегда получается сразу, сколько времени может держаться раздражительность и как правильно выстроить режим, чтобы не спровоцировать повторный срыв в первые дни.
Детальнее – нарколог на дом цена
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Получить дополнительную информацию – вывод из запоя вызов
Клиника в Волгограде руководствуется принципами индивидуального подхода, конфиденциальности и научно обоснованных методик. Врач-нарколог оценивает общее состояние пациента, определяет стадию зависимости и подбирает оптимальную терапевтическую схему. Лечение включает детоксикацию, медикаментозную поддержку, психотерапию и реабилитацию. Каждый пациент проходит лечение в безопасных условиях с постоянным медицинским наблюдением.
Исследовать вопрос подробнее – наркологическая клиника стационар волгоград
Такая структура позволяет достичь максимального эффекта в кратчайшие сроки и минимизировать риск осложнений.
Исследовать вопрос подробнее – https://narkolog-na-dom-v-ufe17.ru/
Вывод из запоя требуется тогда, когда организм уже не способен самостоятельно справиться с последствиями алкогольной интоксикации. Длительное употребление спиртного приводит к нарушению работы внутренних органов, обезвоживанию и психическим расстройствам. Медицинская помощь помогает избежать опасных осложнений и облегчить процесс отказа от алкоголя.
Получить дополнительные сведения – скорая вывод из запоя рязань
Что включено на практике
Детальнее – наркологическая клиника анонимная помощь нарколога
официальный центр дайсон ofitsialnyj-sajt-dn.ru .
Чтобы легче сопоставить риски и плотность наблюдения, ниже даём живой ориентир. Это не заменяет осмотр, но помогает всей семье понимать логику врача до приезда.
Углубиться в тему – https://narkologicheskaya-klinika-domodedovo0.ru/narkologicheskaya-klinika-ceny-v-domodedovo/
Цель
Выяснить больше – http://narkologicheskaya-klinika-serpuhov0.ru
В этом информативном обзоре собраны самые интересные статистические данные и факты, которые помогут лучше понять текущие тренды. Мы представим вам цифры и графики, которые иллюстрируют, как развиваются различные сферы жизни. Эта информация станет отличной основой для глубокого анализа и принятия обоснованных решений.
Детальнее – https://vistoweekly.com/french-stream-moe
Формат
Получить дополнительную информацию – narkologicheskaya-klinika-anonimnaya-pomoshch-narkologa
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Углубиться в тему – вывод из запоя круглосуточно
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Открой скрытое – https://maslana.it/ciao-mondo
Мы строим лечение вокруг предсказуемости: минимум лишних вопросов, максимум конкретики и понятный план на ближайшие сутки. Дежурный врач уточняет только то, что влияет на безопасность — длительность эпизода, актуальные лекарства и переносимость, сон и апетит, наличие поддержки дома. Из этого скелета рождается маршрут: выезд на дом, приём без очередей или стационар с наблюдением 24/7. Конфиденциальность встроена по умолчанию: нейтральная коммуникация, доступ к карте только у вовлечённой команды, документы по запросу — в нейтральных формулировках. Внешний шум гасим, внимание переводим на цель: ровная стабилизация без «качелей» и с понятными контрольными точками.
Выяснить больше – https://narkologicheskaya-klinika-domodedovo0.ru/narkologicheskaya-klinika-ceny-v-domodedovo/
Цель
Ознакомиться с деталями – narkologicheskaya-klinika-narkolog
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Получить дополнительную информацию – https://www.mirnafotografie.nl/want-an-easy-fix-for-your-music-read-this
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Исследовать вопрос подробнее – запой наркологическая клиника в волгограде
Лечение организовано поэтапно, что помогает пациенту постепенно возвращаться к полноценной жизни. Каждый шаг направлен на укрепление результата и снижение риска рецидива.
Получить дополнительные сведения – частная наркологическая клиника омск
Вывод из запоя — это не просто медицинская процедура, а системный процесс восстановления организма после длительного употребления алкоголя. В клинике «ВолгаМед Резолюция» в Волгограде пациенты получают помощь, основанную на принципах доказательной медицины и индивидуального подхода. Лечение направлено не только на устранение симптомов интоксикации, но и на стабилизацию нервной системы, восстановление водно-солевого баланса и нормализацию сна. Капельницы подбираются персонально, с учётом состояния пациента, сопутствующих заболеваний и возраста. Все процедуры проводятся анонимно и под контролем нарколога.
Выяснить больше – http://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-staczionar-voronezh/
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Получить дополнительную информацию – вывод из запоя на дому круглосуточно
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Исследовать вопрос подробнее – вывод из запоя с выездом
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Узнать больше – вывод из запоя дешево в сочи
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Изучить вопрос глубже – вывод из запоя капельница
В Сочи клиника «Детокс» предлагает полный курс вывода из запоя в стационаре. Круглосуточный медицинский контроль гарантирует безопасность и эффективность лечения.
Изучить вопрос глубже – вывод из запоя на дому недорого сочи
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врач приедет в течение 1–2 часов, проведёт необходимое обследование и назначит лечение. Услуга доступна круглосуточно и анонимно.
Выяснить больше – вызов врача нарколога на дом сочи
Продажа тяговых https://faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Изучите внимательнее – https://lsprintingpress.com/product/silai-machine-banner
Кроме безопасности и мониторинга — дисциплину режима. Там легче убрать триггеры, выстроить питание и сон, а психологу — подключить короткие мотивационные сессии, которые помогут удержать результат после выписки.
Изучить вопрос глубже – http://vyvod-iz-zapoya-krasnogorsk10.ru/kruglosutochno-vyvod-iz-zapoya-v-krasnogorske/
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Ознакомиться с деталями – нарколог вывод из запоя в сочи
Снижается тремор и тошнота, выравниваются вегетативные реакции, возвращается способность спокойно уснуть. Вместо «качелей» настроения и попыток самолечения появляется ощущение контроля: понятно, что делаем сейчас и чего ждём дальше.
Получить больше информации – vyvod-iz-zapoya-odincovo10.ru/
Цель и ожидаемая динамика
Получить дополнительные сведения – наркологическая клиника нарколог
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить дополнительные сведения – нарколог вывод из запоя в сочи
Выезд на дом удобен, но не всегда безопасен. Если запой длится больше трёх–пяти суток, присутствует повторная рвота, выраженная слабость, спутанность сознания, судорожная готовность или резкие «качели» давления и пульса, лучше не тянуть и ехать в стационар. Для пациентов старшего возраста и при тяжелой соматике (ИБС, гипертония, диабет, хронические заболевания печени/почек) круглосуточный мониторинг уменьшает риск осложнений и позволяет гибко расширять схему лечения. В стационаре доступна приборная диагностика, тщательный контроль жизненных показателей и быстрая коррекция терапии, если клиническая картина меняется. Мы организуем медицинскую транспортировку, встречу на входе, расширенный осмотр и запуск персонального протокола без задержек. Семья при этом остаётся в информационном контуре: врач объясняет смысл каждого шага и ожидаемый эффект, чтобы решения были осознанными, а не продиктованными паникой или усталостью.
Выяснить больше – http://vyvod-iz-zapoya-krasnogorsk10.ru/vyvod-iz-zapoya-na-domu-v-krasnogorske/https://vyvod-iz-zapoya-krasnogorsk10.ru
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Изучить вопрос глубже – [url=https://narkolog-na-dom-krasnodar11.ru/]вызвать нарколога на дом сочи[/url]
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Детали по клику – https://atmd.org.hk/president
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Смотрите также… – https://blog.1-4u.com/hardware/18.html?replyTo=1077
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Выяснить больше – нарколог на дом круглосуточно сочи
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Подробнее – наркология вывод из запоя
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Изучить вопрос глубже – вывод из запоя на дому круглосуточно
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Подробнее тут – нарколог на дом вывод из запоя в нижнем новгороде
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Исследовать вопрос подробнее – вывод из запоя в стационаре
Что включено на практике
Разобраться лучше – http://narkologicheskaya-klinika-odincovo0.ru
Ниже — краткий ориентир, который помогает семье понимать логику рекомендаций до очного осмотра. Это не «замена врачу», а понятная рамка для принятия решения о старте.
Изучить вопрос глубже – platnaya-narkologicheskaya-klinika
Стоимость зависит от длительности запоя, объёма инфузий, перечня препаратов и длительности наблюдения после капельницы. Мы заранее озвучиваем ориентир, объясняем, какие элементы плана обязательны, а какие — рекомендательные. Ночные выезды иногда дороже из-за нагрузки на бригаду, но при выраженных симптомах откладывать помощь небезопасно. Повторные обращения и расширенные программы стабилизации обсуждаются индивидуально. Ключевой ориентир для семьи — выбирать не «самую дешёвую капельницу», а безопасный формат с контролем и ответственным уходом.
Детальнее – https://vyvod-iz-zapoya-korolev10.ru/
Продажа тяговых https://ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
В этом информативном обзоре собраны самые интересные статистические данные и факты, которые помогут лучше понять текущие тренды. Мы представим вам цифры и графики, которые иллюстрируют, как развиваются различные сферы жизни. Эта информация станет отличной основой для глубокого анализа и принятия обоснованных решений.
Есть чему поучиться – https://tokyo-ya.com/top_shoplist
Когда уместен
Получить больше информации – narkologicheskaya-klinika-shchyolkovo0.ru/
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Углубиться в тему – вывод из запоя цена сочи
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить дополнительную информацию – вывод из запоя
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Получить дополнительную информацию – наркологический вывод из запоя сочи
Старт всегда один: короткий скрининг с дежурным врачом, где уточняются жалобы, длительность эпизода, текущие лекарства, аллергии и условия дома. Далее согласуется реальное окно прибытия или приёма — без обещаний «через пять минут», но с честным ориентиром и запасом на дорожную обстановку. На месте врач фиксирует витальные показатели (АД, пульс, сатурацию, температуру), по показаниям выполняет ЭКГ, запускает детокс (регидратация, коррекция электролитов, защита печени/ЖКТ), объясняет ожидаемую динамику первых 6–12 часов и выдаёт памятку «на сутки»: режим сна, питьевой план, «красные флажки», точное время контрольной связи. Если домашний формат становится недостаточным, перевод в стационар организуется без пауз — терапия продолжается с того же места, где начата, темп лечения не теряется.
Разобраться лучше – https://narkologicheskaya-klinika-shchyolkovo0.ru/narkologicheskaya-klinika-stacionar-v-shchyolkovo/
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Подробнее можно узнать тут – [url=https://narkolog-na-dom-krasnodar15.ru/]вывод из запоя капельница на дому в сочи[/url]
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Разобраться лучше – narkolog-na-dom sochi
Immerse yourself in an exciting world drones sky show, where technology and art merge in an incredible spectacle.
Drone shows have rapidly gained popularity as a modern form of entertainment, captivating audiences worldwide.
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Выяснить больше – вывод из запоя с выездом нижний новгород
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Получить больше информации – наркологический вывод из запоя
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее можно узнать тут – вывод из запоя клиника в сочи
скачать мостбет на телефон mostbet2030.help
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Подробнее можно узнать тут – вывод из запоя на дому цена
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Ознакомиться с деталями – нарколог на дом вывод из запоя сочи
La innovadora compania de espectaculos de drones presento un impresionante espectaculo de drones iluminados en el cielo nocturno, cautivando a todos los asistentes con su show de luces con drones.
Los drones han revolucionado la forma en que se entiende el entretenimiento, ofreciendo un espectaculo aereo lleno de color y vida . Estos espectaculos suelen incluir una gran cantidad de drones que vuelan en formaciones precisas y sincronizadas, creando patrones y disenos en el cielo. Estos eventos a menudo cuentan con una variedad de drones que realizan acrobacias y formaciones complejas, deleitando a los espectadores con su agilidad y coordinacion . Los organizadores de estos eventos trabajan arduamente para programar y ensayar las rutinas de vuelo, asegurandose de que cada dron se mueva en perfecta sincronia con los demas. La preparacion de un espectaculo de drones implica una combinacion de habilidades tecnicas y creativas para lograr un resultado final impresionante.
El uso de drones en los espectaculos ha abierto nuevas posibilidades para la expresion artistica y la entretenimiento. Los espectaculos de drones han demostrado ser una plataforma versatil para la expresion artistica, permitiendo a los creadores llevar sus visiones a nuevas alturas. Ademas, estos eventos han generado un gran interes entre el publico, que se maravilla con la belleza y la complejidad de los patrones y disenos creados por los drones. Los espectaculos de drones han atraido a audiencias de todas las edades, quienes se quedan asombradas con la tecnologia y la creatividad que se despliega en el cielo .
Tecnica y Seguridad:
La realizacion de un espectaculo de drones requiere una gran cantidad de planificacion y preparacion, especialmente en lo que respecta a la seguridad. La seguridad es la principal preocupacion al organizar un espectaculo de drones, ya que se deben tomar medidas para garantizar la seguridad de los espectadores y de los operadores de los drones . Los drones utilizados en estos espectaculos estan equipados con tecnologia avanzada que les permite volar de manera autonoma y realizar maniobras complejas. La tecnologia de vuelo autonomo es crucial para la realizacion de estos espectaculos, ya que permite a los drones realizar movimientos precisos y sincronizados . Ademas, los operadores de los drones deben tener una gran habilidad y experiencia para controlar los drones de manera efectiva. Los operadores de drones deben tener una gran habilidad y conocimiento para controlar los drones de manera segura y precisa .
La seguridad de los espectadores es tambien una preocupacion importante, ya que los drones vuelan a baja altitud y pueden representar un riesgo si no se manejan correctamente. La seguridad de los espectadores es de suma importancia, ya que los drones pueden representar un riesgo si se acercan demasiado o si fallan durante el vuelo . Para mitigar este riesgo, los organizadores suelen establecer zonas de seguridad y seguir estrictos protocolos de seguridad. Los organizadores establecen zonas de seguridad alrededor del area de vuelo para proteger a los espectadores .
Impacto y Futuro:
El impacto de los espectaculos de drones en la industria del entretenimiento ha sido significativo, abriendo nuevas posibilidades para la creatividad y la innovacion. Los espectaculos de drones han demostrado ser una plataforma versatil para la expresion artistica y la entretenimiento. Ademas, estos eventos han generado un gran interes entre el publico, que se maravilla con la belleza y la complejidad de los patrones y disenos creados por los drones. El publico ha respondido con entusiasmo a los espectaculos de drones, disfrutando de la emocion y la belleza de estos eventos . En el futuro, se espera que la tecnologia de drones siga evolucionando, permitiendo la creacion de espectaculos aun mas complejos y emocionantes. Se espera que los espectaculos de drones sigan siendo una forma popular de entretenimiento, con nuevas y emocionantes posibilidades para la creatividad y la innovacion .
Los espectaculos de drones tambien tienen el potencial de ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento. La tecnologia de drones puede ser utilizada para crear experiencias visuales unicas y emocionantes en una variedad de entornos . Ademas, la tecnologia de drones puede ser utilizada para promover la conciencia y la educacion sobre temas importantes, como la conservacion del medio ambiente y la seguridad. La tecnologia de drones puede ser utilizada para crear experiencias de aprendizaje interactivas y emocionantes que promuevan la conciencia y la educacion.
Conclusion:
En conclusion, los espectaculos de drones son una forma de entretenimiento emocionante y innovadora que combina la tecnologia y la creatividad para ofrecer una experiencia visual unica. Los espectaculos de drones son una forma de entretenimiento emocionante y innovadora que combina la tecnologia y la creatividad para ofrecer una experiencia visual unica . Estos eventos han generado un gran interes entre el publico y han abierto nuevas posibilidades para la creatividad y la innovacion en la industria del entretenimiento. Los espectaculos de drones han atraido a audiencias de todas las edades, quienes se quedan asombradas con la tecnologia y la creatividad que se despliega en el cielo . En el futuro, se espera que la tecnologia de drones siga evolucionando, permitiendo la creacion de espectaculos aun mas complejos y emocionantes. Los avances en la tecnologia de drones abriran nuevas posibilidades para la expresion artistica y la entretenimiento en el futuro.
Los espectaculos de drones tienen el potencial de ser utilizados en una variedad de contextos, desde eventos culturales hasta espectaculos de entretenimiento. La tecnologia de drones puede ser utilizada para crear experiencias visuales unicas y emocionantes en una variedad de entornos . Ademas, la tecnologia de drones puede ser utilizada para promover la conciencia y la educacion sobre temas importantes, como la conservacion del medio ambiente y la seguridad. Los espectaculos de drones pueden ser utilizados para educar al publico sobre temas importantes y promover la conciencia y la comprension .
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее можно узнать тут – вывод из запоя вызов в сочи
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Получить дополнительные сведения – наркологический вывод из запоя сочи
Сначала — короткое интервью по телефону: адрес в Одинцово, длительность запоя, препараты, хронические заболевания, аллергии. Это экономит 15–20 минут на месте и помогает заранее спланировать безопасные дозы. По прибытии — осмотр, запуск инфузий и параллельная симптоматическая терапия: противорвотные при тошноте, анксиолитики при тревоге, аккуратная седация к ночи, если есть бессонница. Мы не «усыпляем» пациента — поддерживаем контакт для информативного мониторинга. На протяжении процедуры фиксируем динамику, регулируем скорость капельниц, выстраиваем щадящую гидратацию и лёгкое питание. Если картина меняется, быстро перестраиваем план. На выходе — письменные рекомендации и маршрут продолжения (амбулаторные визиты, дневной стационар или полноценное отделение). Такой алгоритм убирает случайность результата: эффект держится не на удаче, а на чётких действиях команды и дисциплине первых суток.
Ознакомиться с деталями – https://vyvod-iz-zapoya-odincovo10.ru/vyvod-iz-zapoya-ryadom-v-odincovo/
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Детальнее – вывод из запоя в сочи
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Получить дополнительные сведения – вывод из запоя дешево сочи
Статья содержит практические рекомендации и полезные советы, которые можно легко применить в повседневной жизни. Мы делаем акцент на реальных примерах и проверенных методиках, которые способствуют личностному развитию и улучшению качества жизни.
Узнайте всю правду – https://kivureporter.net/programme-conjoint-de-resilience-fao-unicef-pam-le-coges-et-abatteurs-de-munigi-a-lecole-du-savoir
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Исследовать вопрос подробнее – вывод из запоя цена сочи
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Исследовать вопрос подробнее – вывод из запоя недорого
Запуск помощи — это не «одна капельница», а последовательность осмысленных шагов, каждый из которых приближает к устойчивому сну и ровным витальным показателям. Сначала врач уточняет длительность эпизода, переносимость лекарств, сон, аппетит, хронические диагнозы, наличие помощника дома. Затем следует осмотр: давление, пульс, сатурация, температура, ЭКГ при показаниях. Стартовая терапия закрывает дефицит жидкости и солей, защищает печень и ЖКТ, по необходимости подключается мягкая противотревожная поддержка и кислород. Параллельно проговаривается «карта суток»: как отдыхать, что пить и в каком объёме, какие продукты не перегрузят желудок, в какой момент выходить на внеплановую связь. Динамика отслеживается без суеты, а корректировки делаются точечно — по реакции организма, а не «на всякий случай».
Разобраться лучше – http://narkologicheskaya-klinika-ehlektrostal0.ru/platnaya-narkologicheskaya-klinika-v-ehlektrostali/
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Изучить вопрос глубже – вызов нарколога на дом краснодарский край
Что включено на практике
Углубиться в тему – https://narkologicheskaya-klinika-odincovo0.ru/narkologicheskaya-klinika-narkolog-v-odincovo
Сначала — сбор короткого анамнеза и проверка лекарственных взаимодействий, затем — старт инфузии с контролем темпа. Параллельно купируются тошнота, тремор, тахикардия, корректируется сон. Каждые 15–20 минут специалист оценивает динамику и при необходимости меняет схему. В завершение вы получаете письменные рекомендации и маршрут продолжения.
Детальнее – http://vyvod-iz-zapoya-krasnogorsk10.ru/
Мы выезжаем в любое время дня и ночи. Организационно всё просто: короткий звонок с описанием состояния, согласование адреса и времени, консультация по подготовке помещения, приезд врача. Если состояние тяжёлое (длительный запой, возраст 60+, выраженная соматика, признаки делирия, многократная рвота, спутанность сознания), медик предложит стационар сразу — это безопаснее, чем пытаться «дотянуть» ночь дома. В клинике пациент находится под круглосуточным наблюдением, при необходимости выполняются дополнительные исследования, расширяется объём инфузий, корректируется медикаментозная схема. Для пожилых и кардиологических пациентов стационарный формат часто предпочтителен: непрерывный мониторинг снижает риски и ускоряет стабилизацию.
Ознакомиться с деталями – http://vyvod-iz-zapoya-korolev10.ru/vyvod-iz-zapoya-v-stacionare-korolev/https://vyvod-iz-zapoya-korolev10.ru
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Ознакомиться с деталями – наркология вывод из запоя сочи
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Узнать больше – vyzvat-narkologa-na-dom sochi
Самый частый повод — не только «плохое похмелье», а именно абстинентный синдром после запоя: когда самочувствие ухудшается при прекращении алкоголя, а попытки «опохмелиться» лишь продлевают проблему. Важно ориентироваться не на терпимость человека к дискомфорту, а на объективные признаки: если симптомы нарастают, сон сорван, поведение становится нестабильным, а тело реагирует паникой, тремором и скачками давления, лучше не тянуть. Особенно осторожными нужно быть при хронических болезнях сердца, печени и сосудов: при них цена ошибки выше, а «универсальные» домашние схемы могут навредить.
Углубиться в тему – нарколог на дом цена красногорск
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Желаете узнать подробности? – https://tokyogarden.jp/2021/04/20/hello-world
Сначала — короткое интервью по телефону: адрес в Одинцово, длительность запоя, препараты, хронические заболевания, аллергии. Это экономит 15–20 минут на месте и помогает заранее спланировать безопасные дозы. По прибытии — осмотр, запуск инфузий и параллельная симптоматическая терапия: противорвотные при тошноте, анксиолитики при тревоге, аккуратная седация к ночи, если есть бессонница. Мы не «усыпляем» пациента — поддерживаем контакт для информативного мониторинга. На протяжении процедуры фиксируем динамику, регулируем скорость капельниц, выстраиваем щадящую гидратацию и лёгкое питание. Если картина меняется, быстро перестраиваем план. На выходе — письменные рекомендации и маршрут продолжения (амбулаторные визиты, дневной стационар или полноценное отделение). Такой алгоритм убирает случайность результата: эффект держится не на удаче, а на чётких действиях команды и дисциплине первых суток.
Детальнее – http://vyvod-iz-zapoya-odincovo10.ru/vyvesti-iz-zapoya-v-odincovo/
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Подробнее можно узнать тут – вывод из запоя клиника нижний новгород
Срочно нужен нарколог на дом? В Краснодаре клиника «Детокс» приезжает к пациенту в течение часа.
Разобраться лучше – вызвать нарколога на дом сочи
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Углубиться в тему – вывод из запоя цена сочи
I appreciate the real-world applications you provide.
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Разобраться лучше – вывод из запоя анонимно
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Выяснить больше – https://narkolog-na-dom-krasnodar12.ru/
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – вывод из запоя на дому недорого сочи
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Получить дополнительную информацию – вывод из запоя на дому круглосуточно
Формат
Получить больше информации – http://narkologicheskaya-klinika-odincovo0.ru/
Врач приезжает с одноразовыми системами и препаратами, проводит экспресс-диагностику, стартует инфузии и каждые 15–20 минут оценивает динамику, корректируя темп и состав. По завершении — памятка по режиму, гигиене сна, питанию и запретам на 24–72 часа, а также контакты для связи ночью.
Получить дополнительные сведения – https://vyvod-iz-zapoya-odincovo10.ru/vyvod-iz-zapoya-na-domu-v-odincovo
Выезд на дом удобен, но не всегда безопасен. Если запой длится больше трёх–пяти суток, присутствует повторная рвота, выраженная слабость, спутанность сознания, судорожная готовность или резкие «качели» давления и пульса, лучше не тянуть и ехать в стационар. Для пациентов старшего возраста и при тяжелой соматике (ИБС, гипертония, диабет, хронические заболевания печени/почек) круглосуточный мониторинг уменьшает риск осложнений и позволяет гибко расширять схему лечения. В стационаре доступна приборная диагностика, тщательный контроль жизненных показателей и быстрая коррекция терапии, если клиническая картина меняется. Мы организуем медицинскую транспортировку, встречу на входе, расширенный осмотр и запуск персонального протокола без задержек. Семья при этом остаётся в информационном контуре: врач объясняет смысл каждого шага и ожидаемый эффект, чтобы решения были осознанными, а не продиктованными паникой или усталостью.
Получить дополнительные сведения – https://vyvod-iz-zapoya-krasnogorsk10.ru/vyvod-iz-zapoya-cena-v-krasnogorske
Ожидаемая траектория в первые сутки
Разобраться лучше – https://narkologicheskaya-klinika-ehlektrostal0.ru/narkologicheskaya-klinika-ceny-v-ehlektrostali
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Желаете узнать подробности? – https://www.sitedating.ro/online-dating-in-plina-expansiune
Мы выезжаем в любое время дня и ночи. Организационно всё просто: короткий звонок с описанием состояния, согласование адреса и времени, консультация по подготовке помещения, приезд врача. Если состояние тяжёлое (длительный запой, возраст 60+, выраженная соматика, признаки делирия, многократная рвота, спутанность сознания), медик предложит стационар сразу — это безопаснее, чем пытаться «дотянуть» ночь дома. В клинике пациент находится под круглосуточным наблюдением, при необходимости выполняются дополнительные исследования, расширяется объём инфузий, корректируется медикаментозная схема. Для пожилых и кардиологических пациентов стационарный формат часто предпочтителен: непрерывный мониторинг снижает риски и ускоряет стабилизацию.
Углубиться в тему – https://vyvod-iz-zapoya-korolev10.ru/vyvesti-iz-zapoya-korolev/
Официальные адреса маркетплейса на кракен зеркала обновляются ежедневно администрацией для бесперебойного доступа пользователей
Старт всегда один: короткий скрининг с дежурным врачом, где уточняются жалобы, длительность эпизода, текущие лекарства, аллергии и условия дома. Далее согласуется реальное окно прибытия или приёма — без обещаний «через пять минут», но с честным ориентиром и запасом на дорожную обстановку. На месте врач фиксирует витальные показатели (АД, пульс, сатурацию, температуру), по показаниям выполняет ЭКГ, запускает детокс (регидратация, коррекция электролитов, защита печени/ЖКТ), объясняет ожидаемую динамику первых 6–12 часов и выдаёт памятку «на сутки»: режим сна, питьевой план, «красные флажки», точное время контрольной связи. Если домашний формат становится недостаточным, перевод в стационар организуется без пауз — терапия продолжается с того же места, где начата, темп лечения не теряется.
Получить дополнительную информацию – narkologicheskaya-klinika-ceny
Самый частый повод — не только «плохое похмелье», а именно абстинентный синдром после запоя: когда самочувствие ухудшается при прекращении алкоголя, а попытки «опохмелиться» лишь продлевают проблему. Важно ориентироваться не на терпимость человека к дискомфорту, а на объективные признаки: если симптомы нарастают, сон сорван, поведение становится нестабильным, а тело реагирует паникой, тремором и скачками давления, лучше не тянуть. Особенно осторожными нужно быть при хронических болезнях сердца, печени и сосудов: при них цена ошибки выше, а «универсальные» домашние схемы могут навредить.
Получить дополнительную информацию – вызов врача нарколога на дом
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Исследовать вопрос подробнее – https://www.cmsapitpmt.com/live_player.php/?smbb=aHR0cHM6Ly93d3cuZmxhc2hjYWJpbmUuY29tLmJyL3RvdGVtLWZvdG9ncmFmaWNvLw
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Детальнее – вывод из запоя недорого сочи
Сначала — короткое интервью по телефону: адрес в Одинцово, длительность запоя, препараты, хронические заболевания, аллергии. Это экономит 15–20 минут на месте и помогает заранее спланировать безопасные дозы. По прибытии — осмотр, запуск инфузий и параллельная симптоматическая терапия: противорвотные при тошноте, анксиолитики при тревоге, аккуратная седация к ночи, если есть бессонница. Мы не «усыпляем» пациента — поддерживаем контакт для информативного мониторинга. На протяжении процедуры фиксируем динамику, регулируем скорость капельниц, выстраиваем щадящую гидратацию и лёгкое питание. Если картина меняется, быстро перестраиваем план. На выходе — письменные рекомендации и маршрут продолжения (амбулаторные визиты, дневной стационар или полноценное отделение). Такой алгоритм убирает случайность результата: эффект держится не на удаче, а на чётких действиях команды и дисциплине первых суток.
Изучить вопрос глубже – https://vyvod-iz-zapoya-odincovo10.ru/vyvod-iz-zapoya-v-stacionare-v-odincovo
Мы выезжаем в любое время дня и ночи. Организационно всё просто: короткий звонок с описанием состояния, согласование адреса и времени, консультация по подготовке помещения, приезд врача. Если состояние тяжёлое (длительный запой, возраст 60+, выраженная соматика, признаки делирия, многократная рвота, спутанность сознания), медик предложит стационар сразу — это безопаснее, чем пытаться «дотянуть» ночь дома. В клинике пациент находится под круглосуточным наблюдением, при необходимости выполняются дополнительные исследования, расширяется объём инфузий, корректируется медикаментозная схема. Для пожилых и кардиологических пациентов стационарный формат часто предпочтителен: непрерывный мониторинг снижает риски и ускоряет стабилизацию.
Изучить вопрос глубже – http://vyvod-iz-zapoya-korolev10.ru/vyvod-iz-zapoya-v-stacionare-korolev/https://vyvod-iz-zapoya-korolev10.ru
В Одинцово доступен гибкий маршрут: выездная бригада 24/7 и стационар. Домашний формат хорош при умеренной симптоматике и сохранённом контакте — он позволяет избежать перевозок и сохранить конфиденциальность. Стационар предпочтителен при длительном эпизоде, повторной рвоте, выраженной слабости, нестабильном давлении/пульсе, спутанности сознания, судорожной готовности, а также у пациентов старшего возраста и при тяжёлой соматике (ИБС, гипертония, диабет, хронические болезни печени/почек). Мы оцениваем не один признак, а совокупность факторов и динамику, чтобы не «пересидеть» дома там, где нужен приборный мониторинг. В обоих вариантах сохраняется наш принцип: индивидуализация схемы, осторожная седация, прицельная работа со сном, прозрачные объяснения назначений — и всё это с опорой на объективные показатели, а не ощущения «полегчало/ухудшилось».
Разобраться лучше – vyvod-iz-zapoya-vyzov-na-dom
«Ритм Здоровья» в Красногорске — это понятный маршрут помощи от первого звонка до устойчивой ремиссии. Мы не растягиваем старт на бесконечные согласования: дежурный врач аккуратно собирает жалобы, длительность эпизода, сведения о лекарствах и сопутствующих диагнозах, после чего предлагает безопасную точку входа — выезд на дом, приём без очередей или госпитализацию под круглосуточное наблюдение. Вся коммуникация нейтральная, доступ к карте ограничен лечащей командой, а в документах по запросу используем формулировки, не раскрывающие профиль отделения. Такой «тихий» формат снимает лишнее напряжение, экономит время семьи и позволяет сосредоточиться на главном — мягкой стабилизации без «качелей».
Подробнее тут – частная наркологическая клиника
Когда уместен
Подробнее – http://narkologicheskaya-klinika-krasnogorsk0.ru/
Самый частый повод — не только «плохое похмелье», а именно абстинентный синдром после запоя: когда самочувствие ухудшается при прекращении алкоголя, а попытки «опохмелиться» лишь продлевают проблему. Важно ориентироваться не на терпимость человека к дискомфорту, а на объективные признаки: если симптомы нарастают, сон сорван, поведение становится нестабильным, а тело реагирует паникой, тремором и скачками давления, лучше не тянуть. Особенно осторожными нужно быть при хронических болезнях сердца, печени и сосудов: при них цена ошибки выше, а «универсальные» домашние схемы могут навредить.
Выяснить больше – http://narkolog-na-dom-krasnogorsk6.ru/narkologicheskaya-klinika-krasnogorsk/
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Подробнее – наркологический вывод из запоя
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Подробнее тут – http://vyvod-iz-zapoya-sochi22.ru
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Подробнее можно узнать тут – нарколог на дом вывод из запоя в сочи
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Разобраться лучше – вывод из запоя на дому круглосуточно нижний новгород
Вызов нарколога на дом в Краснодаре доступен в любое время суток. Клиника «Детокс» гарантирует профессиональную помощь.
Выяснить больше – нарколог на дом круглосуточно в сочи
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Углубиться в тему – вывод из запоя капельница на дому в сочи
Первичный контакт — короткий, но точный скрининг: длительность эпизода, лекарства и аллергии, сон, аппетит, переносимость нагрузок, возможность обеспечить тишину на месте. На основе этих фактов врач предлагает безопасную точку входа: выезд на дом, приём без очередей или госпитализацию под наблюдением 24/7. На месте мы сразу исключаем «красные флажки», фиксируем давление/пульс/сатурацию/температуру, при показаниях выполняем ЭКГ и запускаем детокс. Параллельно выдаём «карту суток»: режим отдыха и питья, лёгкое питание, перечень нормальных ощущений и момент, когда нужно связаться внепланово. Если домашнего формата становится мало, переводим в стационар без пауз — все назначения и наблюдения «переезжают» вместе с пациентом.
Углубиться в тему – наркологическая клиника стационар
Когда самочувствие «скачет», а ночь грозит затянуться, важен не героизм, а клинически выверенный план. В «МедОпоре» в Красногорске мы выстраиваем помощь так, чтобы каждый шаг давал предсказуемый эффект: первичное обследование, персональная инфузионная терапия, бережная коррекция тревоги и сна, мониторинг жизненно важных показателей и подробные рекомендации для семьи. Мы не используем «универсальные коктейли» и не маскируем симптомы — задача детокса в том, чтобы снять токсическую нагрузку, восстановить водно-электролитный баланс, стабилизировать вегетативные реакции и вернуть управляемость состоянием. С первых минут пациент получает ясные ориентиры: что делаем сейчас, чего ждать через час, по каким признакам нужно срочно звать врача. Анонимность соблюдается без компромиссов, а решения принимаются на основе реальных показателей — это снижает тревогу и исключает опасные «домашние эксперименты».
Получить больше информации – vyvod iz zapoya anonimno
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Детальнее – срочный вывод из запоя нижний новгород
Когда уместен
Получить больше информации – наркологическая клиника недорого
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Ознакомиться с деталями – вывод из запоя с выездом в сочи
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Ознакомиться с деталями – помощь вывод из запоя в нижнем новгороде
Equilibrado de piezas
El equilibrado es una etapa esencial en las tareas de mantenimiento de maquinaria agricola, asi como en la produccion de ejes, volantes, rotores y armaduras de motores electricos. El desequilibrio genera vibraciones que incrementan el desgaste de los rodamientos, provocan sobrecalentamiento e incluso pueden causar la rotura de los componentes. Para evitar fallos mecanicos, resulta esencial detectar y corregir el desequilibrio a tiempo utilizando tecnicas modernas de diagnostico.
Principales metodos de equilibrado
Existen varias tecnicas para corregir el desequilibrio, dependiendo del tipo de pieza y la magnitud de las vibraciones:
El equilibrado dinamico – Se aplica en elementos rotativos (rotores, ejes) y se lleva a cabo mediante maquinas equilibradoras especializadas.
El equilibrado estatico – Se usa en volantes, ruedas y otras piezas donde es suficiente compensar el peso en un unico plano.
La correccion del desequilibrio – Se lleva a cabo mediante:
Taladrado (eliminacion de material en la zona mas pesada),
Instalacion de contrapesos (en ruedas y aros de volantes),
Ajuste de masas de balanceo (como en el caso de los ciguenales).
Diagnostico del desequilibrio: equipos utilizados
Para identificar con precision las vibraciones y el desequilibrio, se utilizan:
Equipos equilibradores – Miden el nivel de vibracion y determinan con exactitud los puntos de correccion.
Equipos analizadores de vibraciones – Capturan el espectro de oscilaciones, detectando no solo el desequilibrio, sino tambien otros defectos (como el desgaste de rodamientos).
Sistemas de medicion laser – Se emplean para mediciones de alta precision en componentes criticos.
Las velocidades criticas de rotacion requieren especial atencion – regimenes en los que la vibracion aumenta drasticamente debido a la resonancia. Un equilibrado adecuado evita danos en el equipo bajo estas condiciones.
Вывод из запоя — это всегда баланс между скоростью и безопасностью. Дома трудно заметить скрытые ухудшения, особенно ночью: давление и пульс «гуляют», нарастает обезвоживание, сон рваный и тревожный. В «Трезвом Контуре» этот хаос замещается управляемостью: перед выездом дежурный врач собирает ключевые данные (длительность эпизода, лекарства, аллергии, сопутствующие болезни), на месте проводится экспресс-диагностика (АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания), затем запускается схема терапевтической поддержки. Мы постоянно «подстраиваем» инфузии по реакции организма, а не по шаблонной карте: где-то важнее регидратация, где-то — коррекция электролитов, где-то — бережная седация для ночи. Для семьи это значит одно: меньше догадок, больше ясности. Если по картине риски высоки, мы аргументированно предлагаем стационар в Одинцово — и организуем транспортировку без пауз, потому что цена задержки в такие часы всегда выше.
Подробнее можно узнать тут – вывод из запоя рядом
Мы выезжаем в любое время дня и ночи. Организационно всё просто: короткий звонок с описанием состояния, согласование адреса и времени, консультация по подготовке помещения, приезд врача. Если состояние тяжёлое (длительный запой, возраст 60+, выраженная соматика, признаки делирия, многократная рвота, спутанность сознания), медик предложит стационар сразу — это безопаснее, чем пытаться «дотянуть» ночь дома. В клинике пациент находится под круглосуточным наблюдением, при необходимости выполняются дополнительные исследования, расширяется объём инфузий, корректируется медикаментозная схема. Для пожилых и кардиологических пациентов стационарный формат часто предпочтителен: непрерывный мониторинг снижает риски и ускоряет стабилизацию.
Детальнее – vyvod iz zapoya na domu kruglosutochno
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Подробнее можно узнать тут – вывод из запоя недорого
Стоимость зависит от длительности запоя, объёма инфузий, перечня препаратов и длительности наблюдения после капельницы. Мы заранее озвучиваем ориентир, объясняем, какие элементы плана обязательны, а какие — рекомендательные. Ночные выезды иногда дороже из-за нагрузки на бригаду, но при выраженных симптомах откладывать помощь небезопасно. Повторные обращения и расширенные программы стабилизации обсуждаются индивидуально. Ключевой ориентир для семьи — выбирать не «самую дешёвую капельницу», а безопасный формат с контролем и ответственным уходом.
Получить больше информации – vyvod iz zapoya na domu korolev
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Ознакомиться с деталями – вывод из запоя в стационаре в сочи
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Углубиться в тему – вывод из запоя капельница на дому в сочи
Вывод из запоя — это всегда баланс между скоростью и безопасностью. Дома трудно заметить скрытые ухудшения, особенно ночью: давление и пульс «гуляют», нарастает обезвоживание, сон рваный и тревожный. В «Трезвом Контуре» этот хаос замещается управляемостью: перед выездом дежурный врач собирает ключевые данные (длительность эпизода, лекарства, аллергии, сопутствующие болезни), на месте проводится экспресс-диагностика (АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания), затем запускается схема терапевтической поддержки. Мы постоянно «подстраиваем» инфузии по реакции организма, а не по шаблонной карте: где-то важнее регидратация, где-то — коррекция электролитов, где-то — бережная седация для ночи. Для семьи это значит одно: меньше догадок, больше ясности. Если по картине риски высоки, мы аргументированно предлагаем стационар в Одинцово — и организуем транспортировку без пауз, потому что цена задержки в такие часы всегда выше.
Подробнее – narkolog-vyvod-iz-zapoya
В Сочи клиника «Детокс» предлагает полный курс вывода из запоя в стационаре. Круглосуточный медицинский контроль гарантирует безопасность и эффективность лечения.
Выяснить больше – вывод из запоя на дому
Что получите за 24 часа
Подробнее – http://narkologicheskaya-klinika-domodedovo0.ru
Что включено на практике
Подробнее – http://narkologicheskaya-klinika-serpuhov0.ru
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Исследовать вопрос подробнее – вывод из запоя цена
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Подробнее тут – вывод из запоя круглосуточно в нижнем новгороде
«Ритм Здоровья» в Красногорске — это понятный маршрут помощи от первого звонка до устойчивой ремиссии. Мы не растягиваем старт на бесконечные согласования: дежурный врач аккуратно собирает жалобы, длительность эпизода, сведения о лекарствах и сопутствующих диагнозах, после чего предлагает безопасную точку входа — выезд на дом, приём без очередей или госпитализацию под круглосуточное наблюдение. Вся коммуникация нейтральная, доступ к карте ограничен лечащей командой, а в документах по запросу используем формулировки, не раскрывающие профиль отделения. Такой «тихий» формат снимает лишнее напряжение, экономит время семьи и позволяет сосредоточиться на главном — мягкой стабилизации без «качелей».
Подробнее можно узнать тут – http://narkologicheskaya-klinika-krasnogorsk0.ru
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Уточнить детали – https://covalaw.vn/thanh-lap-doanh-nghiep-tiet-kiem-chi-phi
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее тут – запой нарколог на дом в сочи
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Подробности по ссылке – http://www.sksandloparen.se/sk-sandloparen-julavslutning-2023
Вывод из запоя — это всегда баланс между скоростью и безопасностью. Дома трудно заметить скрытые ухудшения, особенно ночью: давление и пульс «гуляют», нарастает обезвоживание, сон рваный и тревожный. В «Трезвом Контуре» этот хаос замещается управляемостью: перед выездом дежурный врач собирает ключевые данные (длительность эпизода, лекарства, аллергии, сопутствующие болезни), на месте проводится экспресс-диагностика (АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания), затем запускается схема терапевтической поддержки. Мы постоянно «подстраиваем» инфузии по реакции организма, а не по шаблонной карте: где-то важнее регидратация, где-то — коррекция электролитов, где-то — бережная седация для ночи. Для семьи это значит одно: меньше догадок, больше ясности. Если по картине риски высоки, мы аргументированно предлагаем стационар в Одинцово — и организуем транспортировку без пауз, потому что цена задержки в такие часы всегда выше.
Подробнее – http://vyvod-iz-zapoya-odincovo10.ru/
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Исследовать вопрос подробнее – https://wcpartner.sk/hu/uvod/logo-2
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Получить больше информации – https://vyvod-iz-zapoya-sochi12.ru/
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Получить дополнительные сведения – наркологический вывод из запоя нижний новгород
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Детали по клику – http://bajkoweogrody.waw.pl/a-post-with-a-right-aligned-image
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Выяснить больше – вывод из запоя с выездом в сочи
Ожидаемая траектория в первые сутки
Углубиться в тему – анонимная наркологическая клиника
Формат
Детальнее – скорая наркологическая помощь в клинике
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Исследовать вопрос подробнее – https://lcg.org.ua/1200×800
mostbet mobile mostbet2032.help
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – вывод из запоя вызов сочи
Ожидаемая траектория в первые сутки
Выяснить больше – http://narkologicheskaya-klinika-ehlektrostal0.ru/platnaya-narkologicheskaya-klinika-v-ehlektrostali/https://narkologicheskaya-klinika-ehlektrostal0.ru
Сначала — короткое интервью по телефону: адрес в Одинцово, длительность запоя, препараты, хронические заболевания, аллергии. Это экономит 15–20 минут на месте и помогает заранее спланировать безопасные дозы. По прибытии — осмотр, запуск инфузий и параллельная симптоматическая терапия: противорвотные при тошноте, анксиолитики при тревоге, аккуратная седация к ночи, если есть бессонница. Мы не «усыпляем» пациента — поддерживаем контакт для информативного мониторинга. На протяжении процедуры фиксируем динамику, регулируем скорость капельниц, выстраиваем щадящую гидратацию и лёгкое питание. Если картина меняется, быстро перестраиваем план. На выходе — письменные рекомендации и маршрут продолжения (амбулаторные визиты, дневной стационар или полноценное отделение). Такой алгоритм убирает случайность результата: эффект держится не на удаче, а на чётких действиях команды и дисциплине первых суток.
Детальнее – skoraya-pomoshch-vyvoda-iz-zapoya
Цель
Выяснить больше – http://narkologicheskaya-klinika-serpuhov0.ru/platnaya-narkologicheskaya-klinika-v-serpuhove/https://narkologicheskaya-klinika-serpuhov0.ru
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Изучить вопрос глубже – вывод из запоя с выездом в нижнем новгороде
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Узнать больше – вывод из запоя с выездом в сочи
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Сочи предлагает вывод из запоя в стационаре. Под наблюдением опытных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить больше информации – врач вывод из запоя
«Светлый Шаг» — это не набор общих обещаний, а чётко выстроенный маршрут помощи, где каждый шаг прозрачен: от первичного разговора до устойчивой ремиссии. Мы бережно собираем только необходимые данные, сразу объясняем, что будет сделано в первые 6–12 часов, каких изменений ждать к ночи и по каким маркерам поймём, что курс выбран верно. Конфиденциальность встроена в процесс: нейтральные звонки, ограниченный доступ к медкарте, аккуратный выезд без броской атрибутики, возможность оформить документы с нейтральными формулировками. Итог — меньше стресса, меньше бюрократии и больше управляемости там, где это критично.
Подробнее можно узнать тут – narkologicheskaya-klinika
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Это ещё не всё… – http://paredao.com.br/locais/paredao-x-castro-alves
Выезд на дом удобен, но не всегда безопасен. Если запой длится больше трёх–пяти суток, присутствует повторная рвота, выраженная слабость, спутанность сознания, судорожная готовность или резкие «качели» давления и пульса, лучше не тянуть и ехать в стационар. Для пациентов старшего возраста и при тяжелой соматике (ИБС, гипертония, диабет, хронические заболевания печени/почек) круглосуточный мониторинг уменьшает риск осложнений и позволяет гибко расширять схему лечения. В стационаре доступна приборная диагностика, тщательный контроль жизненных показателей и быстрая коррекция терапии, если клиническая картина меняется. Мы организуем медицинскую транспортировку, встречу на входе, расширенный осмотр и запуск персонального протокола без задержек. Семья при этом остаётся в информационном контуре: врач объясняет смысл каждого шага и ожидаемый эффект, чтобы решения были осознанными, а не продиктованными паникой или усталостью.
Детальнее – http://vyvod-iz-zapoya-krasnogorsk10.ru/vyvod-iz-zapoya-klinika-v-krasnogorske/
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Желаете узнать подробности? – https://backupteleinformatica.com.br/?p=94
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Получить дополнительную информацию – нарколог на дом вывод из запоя в сочи
Две похожие ситуации никогда не бывают одинаковыми: возраст, вес, сопутствующие болезни, длительность запоя и переносимость препаратов формируют уникальную клиническую картину. Мы исключаем «универсальные» схемы, чтобы не перегрузить организм и не вызвать побочных реакций. Инфузии проводятся только одноразовыми системами, врач соблюдает стерильность, контролирует дозировки и следит за динамикой симптомов. Мы уделяем особое внимание сну и уровню тревоги в первые часы после детокса — именно эти параметры влияют на риск срыва. Для пациентов с сердечно-сосудистыми, эндокринными и неврологическими заболеваниями детоксикация планируется особенно осторожно; при малейших сомнениях мы предлагаем стационар и разъясняем семье, почему это безопаснее.
Подробнее тут – http://vyvod-iz-zapoya-korolev10.ru/vyvod-iz-zapoya-v-stacionare-korolev/
После первичной стабилизации врач обычно объясняет близким, почему «просто поспать» не всегда получается сразу, сколько времени может держаться раздражительность и как правильно выстроить режим, чтобы не спровоцировать повторный срыв в первые дни.
Разобраться лучше – нарколог на дом
Первичный контакт — короткий, но точный скрининг: длительность эпизода, лекарства и аллергии, сон, аппетит, переносимость нагрузок, возможность обеспечить тишину на месте. На основе этих фактов врач предлагает безопасную точку входа: выезд на дом, приём без очередей или госпитализацию под наблюдением 24/7. На месте мы сразу исключаем «красные флажки», фиксируем давление/пульс/сатурацию/температуру, при показаниях выполняем ЭКГ и запускаем детокс. Параллельно выдаём «карту суток»: режим отдыха и питья, лёгкое питание, перечень нормальных ощущений и момент, когда нужно связаться внепланово. Если домашнего формата становится мало, переводим в стационар без пауз — все назначения и наблюдения «переезжают» вместе с пациентом.
Выяснить больше – https://narkologicheskaya-klinika-odincovo0.ru/
Формат
Углубиться в тему – запой наркологическая клиника
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Получить дополнительную информацию – вывод из запоя в стационаре
Продажа тяговых ab-resurs.ru аккумуляторных батарей для вилочных погрузчиков и штабелеров. Надёжные решения для стабильной работы складской техники: большой выбор АКБ, профессиональный подбор по параметрам, консультации специалистов, гарантия и оперативная поставка для складов и производств по всей России
Инфузионная терапия подбирается под человека, а не под «среднюю» ситуацию. Базовый каркас обычно включает растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы. По показаниям добавляются гепатопротекторы и антиоксидантные компоненты — это помогает печени и снижает оксидативный стресс. Если есть выраженная тошнота, подключаем противорвотные; при тревоге и нарушении сна — мягкие анксиолитики и седативные препараты, которые не «вырубают», а выравнивают ритмы и сохраняют контакт для мониторинга. Мы избегаем агрессивных «миксов», потому что избыточная седация может скрыть опасные симптомы и усложнить оценку состояния. Эффективность оцениваем не только по субъективному облегчению, но и по объективным метрикам: пульс, давление, сатурация, динамика тремора, аппетит, качество сна. Как только показатели стабилизируются, фарм-нагрузка снижается, а ведущую роль берет режим — питание, гидратация, спокойный вечерний ритуал, короткие бытовые активности.
Углубиться в тему – http://vyvod-iz-zapoya-krasnogorsk10.ru/vyvod-iz-zapoya-klinika-v-krasnogorske/
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Получить дополнительную информацию – вывод из запоя на дому круглосуточно сочи
Что включено на практике
Углубиться в тему – https://narkologicheskaya-klinika-odincovo0.ru/narkologicheskaya-klinika-stacionar-v-odincovo
Кроме безопасности и мониторинга — дисциплину режима. Там легче убрать триггеры, выстроить питание и сон, а психологу — подключить короткие мотивационные сессии, которые помогут удержать результат после выписки.
Разобраться лучше – https://vyvod-iz-zapoya-krasnogorsk10.ru/vyvod-iz-zapoya-klinika-v-krasnogorske
Цель
Получить больше информации – наркологическая клиника нарколог
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Исследовать вопрос подробнее – нарколог на дом круглосуточно в сочи
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Получить дополнительные сведения – https://mylogicaltech.com/what-color-would-sunrise-be-in-a-heavily-polluted-sky
Что получите за 24 часа
Ознакомиться с деталями – https://narkologicheskaya-klinika-domodedovo0.ru/narkologicheskaya-klinika-telefon-v-domodedovo/
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Желаете узнать подробности? – https://fashionv.org/damian-lewis-net-worth-2023
Домашний выезд удобен, но не всегда уместен. Поводами для стационара являются длительность запоя свыше 3–5 суток, повторная рвота, выраженная слабость, спутанность сознания, судорожная готовность, признаки делирия, декомпенсация хронических болезней. В отделении «Трезвого Ритма» в Королёве доступен расширенный мониторинг, круглосуточный уход, лабораторная диагностика и быстрые коррекции схемы. Мы организуем медицинскую транспортировку без задержек, по прибытии — расширенный осмотр, индивидуальный план и информирование семьи о каждом шаге.
Ознакомиться с деталями – http://vyvod-iz-zapoya-korolev10.ru/vyvod-iz-zapoya-na-domu-korolev/
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Подробнее – срочный вывод из запоя в сочи
Ниже — краткий ориентир, который помогает семье понимать логику рекомендаций до очного осмотра. Это не «замена врачу», а понятная рамка для принятия решения о старте.
Подробнее тут – narkologicheskaya-klinika-telefon
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Детали по клику – https://wanep.org/wanep/csos-consultative-meeting-to-review-the-state-of-democracy-and-governance-in-the-ecowas-region
Когда запой затягивается, организм быстро входит в режим перегрузки: нарушается сон, скачет давление, усиливается тревога, появляется дрожь, тошнота, потливость и резкая слабость. В такой ситуации «перетерпеть» или лечиться домашними средствами — рискованная стратегия: состояние может ухудшаться волнами, а осложнения иногда развиваются резко, без долгой подготовки. Выезд нарколога на дом в Красногорске нужен для того, чтобы снять острую интоксикацию и абстиненцию безопасно, под контролем показателей, без лишней суеты и без поездок по стационарам в разгар плохого самочувствия.
Выяснить больше – http://narkolog-na-dom-krasnogorsk6.ru/narkologicheskij-czentr-v-krasnogorske/https://narkolog-na-dom-krasnogorsk6.ru
дайсон стайлер официальный сайт цена fen-dn-kupit-12.ru .
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Разобраться лучше – вызвать нарколога на дом сочи
фен дайсон оригинал купить официальный fen-dn-kupit-13.ru .
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Выяснить больше – вывод из запоя в стационаре в нижнем новгороде
купить дайсон фен в москве у официального дилера stajler-dsn-1.ru .
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Получить больше информации – врач нарколог на дом краснодарский край
Продажа тяговых faamru.com аккумуляторных батарей для вилочных погрузчиков, ричтраков, электротележек и штабелеров. Решения для интенсивной складской работы: стабильная мощность, долгий ресурс, надёжная работа в сменном режиме, помощь с подбором АКБ по параметрам техники и оперативная поставка под задачу
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Выяснить больше – врач вывод из запоя сочи
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Детальнее – врач нарколог на дом краснодарский край
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Выяснить больше – vyzov-narkologa-na-dom sochi
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Смотрите также… – https://awakenregen.com/2023/10/25/psicologia-social-comunitaria-en-el-turismo-regenerativo-potenciando-el-empoderamiento-local-y-la-salud-mental
Мы строим лечение вокруг предсказуемости: минимум лишних вопросов, максимум конкретики и понятный план на ближайшие сутки. Дежурный врач уточняет только то, что влияет на безопасность — длительность эпизода, актуальные лекарства и переносимость, сон и апетит, наличие поддержки дома. Из этого скелета рождается маршрут: выезд на дом, приём без очередей или стационар с наблюдением 24/7. Конфиденциальность встроена по умолчанию: нейтральная коммуникация, доступ к карте только у вовлечённой команды, документы по запросу — в нейтральных формулировках. Внешний шум гасим, внимание переводим на цель: ровная стабилизация без «качелей» и с понятными контрольными точками.
Подробнее можно узнать тут – anonimnaya-narkologicheskaya-pomoshch
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Детальнее – вывод из запоя круглосуточно
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить больше информации – вывод из запоя вызов на дом
Вызов нарколога на дом в Краснодаре доступен в любое время суток. Клиника «Детокс» гарантирует профессиональную помощь.
Подробнее тут – врач нарколог на дом в сочи
Мы выезжаем в любое время дня и ночи. Организационно всё просто: короткий звонок с описанием состояния, согласование адреса и времени, консультация по подготовке помещения, приезд врача. Если состояние тяжёлое (длительный запой, возраст 60+, выраженная соматика, признаки делирия, многократная рвота, спутанность сознания), медик предложит стационар сразу — это безопаснее, чем пытаться «дотянуть» ночь дома. В клинике пациент находится под круглосуточным наблюдением, при необходимости выполняются дополнительные исследования, расширяется объём инфузий, корректируется медикаментозная схема. Для пожилых и кардиологических пациентов стационарный формат часто предпочтителен: непрерывный мониторинг снижает риски и ускоряет стабилизацию.
Детальнее – http://vyvod-iz-zapoya-korolev10.ru/
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Получить дополнительную информацию – врач нарколог на дом краснодарский край
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Подробнее тут – http://okashiyanon.com/2023/12/13/%E7%A7%A9%E7%88%B6%E9%BA%A6%E9%85%92%E3%80%8012%E6%9C%883%E6%97%A5%E3%81%AE%E3%83%9B%E3%83%BC%E3%83%AA%E3%83%A3%E3%82%A4
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Углубиться в тему – вывод из запоя на дому круглосуточно в нижнем новгороде
Старт всегда один: короткий скрининг с дежурным врачом, где уточняются жалобы, длительность эпизода, текущие лекарства, аллергии и условия дома. Далее согласуется реальное окно прибытия или приёма — без обещаний «через пять минут», но с честным ориентиром и запасом на дорожную обстановку. На месте врач фиксирует витальные показатели (АД, пульс, сатурацию, температуру), по показаниям выполняет ЭКГ, запускает детокс (регидратация, коррекция электролитов, защита печени/ЖКТ), объясняет ожидаемую динамику первых 6–12 часов и выдаёт памятку «на сутки»: режим сна, питьевой план, «красные флажки», точное время контрольной связи. Если домашний формат становится недостаточным, перевод в стационар организуется без пауз — терапия продолжается с того же места, где начата, темп лечения не теряется.
Ознакомиться с деталями – narkologicheskaya-klinika-otzyvy
Выезд нарколога на дом в Нижнем Новгороде — круглосуточная помощь при запое. Мы гарантируем анонимность и конфиденциальность на всех этапах лечения.
Подробнее – врач вывод из запоя нижний новгород
В Краснодаре клиника «Детокс» предлагает выезд нарколога на дом. Помощь оказывается быстро, анонимно и круглосуточно.
Узнать больше – нарколог на дом цена сочи
«Вектор Надежды» выстраивает помощь так, чтобы с первого звонка убрать неопределённость и вернуть ощущение контроля. Дежурный врач аккуратно собирает только необходимую информацию, оценивает риски и предлагает безопасный старт: выезд на дом, дневной маршрут или стационар с наблюдением 24/7. Мы объясняем каждую манипуляцию простым языком — что именно будет сделано в ближайшие часы, каких изменений ожидать к вечеру, почему выбран именно такой темп и как поймём, что схема работает. Конфиденциальность — не дополнение, а стандарт: нейтральные звонки, неброская атрибутика, ограниченный доступ к карте, отсутствие постановки на учёт. Такой регламент снижает тревогу, экономит силы семьи и ускоряет стабилизацию: вместо «марафона кабинетов» — один связный маршрут с понятными контрольными точками.
Ознакомиться с деталями – http://narkologicheskaya-klinika-shchyolkovo0.ru/kruglosutochnaya-narkologicheskaya-klinika-v-shchyolkovo/
дайсон фен оригинал купить дайсон фен оригинал купить .
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Получить больше информации – вывод из запоя вызов сочи
официальный сайт дайсон стайлер для волос купить цена с насадкам… официальный сайт дайсон стайлер для волос купить цена с насадкам… .
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Полная информация здесь – https://apolin.org/usu-faculty-of-law-and-pt-musim-mas-collaborate-to-renovate-facilities
фен купить дайсон официальный stajler-dsn-1.ru .
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Детальнее – вывод из запоя вызов
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Узнать больше – нарколог на дом сочи
Формат
Подробнее – http://narkologicheskaya-klinika-shchyolkovo0.ru
Когда уместен
Узнать больше – http://
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Детальнее – вывод из запоя с выездом в сочи
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-sochi22.ru/
Если пациент не может приехать в клинику, в Краснодаре нарколог приедет к нему домой. Помощь оказывает «Детокс» круглосуточно.
Ознакомиться с деталями – вывод из запоя с выездом в сочи
“Оздоровительная программа голодания в нашем санатории включает нафталановые ванны цены для эффективного восстановления здоровья.”
Такой метод способствует восстановлению работы внутренних органов. Современные исследования подтверждают, что голодание положительно влияет на иммунитет. Также оно способствует нормализации уровня сахара в крови.
Существует несколько видов голодания, включая интервальное и длительное. Длительное голодание требует подготовки и контроля со стороны специалистов. Каждый метод имеет свои преимущества и противопоказания. Неправильный подход может нанести вред здоровью.
Голодание запускает процесс аутофагии — очищения клеток от поврежденных компонентов. Аутофагия также укрепляет иммунную систему. Кроме того, голодание способствует снижению веса. Организм начинает использовать запасы жира для энергии.
Еще одним плюсом является улучшение работы сердечно-сосудистой системы. Оно уменьшает риск инфарктов и инсультов. Также отмечается положительное влияние на психику. Стрессоустойчивость повышается, а тревожность снижается.
Перед началом программы необходимо правильно подготовить организм. Рекомендуется пить больше воды для выведения токсинов. Выход из голодания должен быть постепенным. Резкий переход к обычному питанию может навредить.
Важно соблюдать питьевой режим во время голодания. Травяные чаи успокаивают желудок и снижают чувство голода. Также необходимо следить за самочувствием. Легкая физическая активность улучшает циркуляцию крови.
Сочетание голодания с физическими упражнениями усиливает результат. Кардионагрузки ускоряют сжигание жира. Также полезно практиковать медитацию и дыхательные техники. Они снижают стресс и улучшают концентрацию.
Важно вести дневник самочувствия и результатов. Записи помогают отслеживать прогресс и корректировать программу. Регулярные курсы голодания дают долгосрочный эффект. Комплексный подход гарантирует устойчивое здоровье.
Существует несколько видов голодания, включая интервальное и длительное.
*(Аналогично для остальных разделов.)*
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Выяснить больше – выезд нарколога на дом в сочи
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Подробнее тут – вывод из запоя дешево в нижнем новгороде
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее – narkolog-na-dom sochi
Вызов нарколога на дом в Краснодаре доступен в любое время суток. Клиника «Детокс» гарантирует профессиональную помощь.
Разобраться лучше – врач нарколог на дом сочи
Первичный контакт — короткий, но точный скрининг: длительность эпизода, лекарства и аллергии, сон, аппетит, переносимость нагрузок, возможность обеспечить тишину на месте. На основе этих фактов врач предлагает безопасную точку входа: выезд на дом, приём без очередей или госпитализацию под наблюдением 24/7. На месте мы сразу исключаем «красные флажки», фиксируем давление/пульс/сатурацию/температуру, при показаниях выполняем ЭКГ и запускаем детокс. Параллельно выдаём «карту суток»: режим отдыха и питья, лёгкое питание, перечень нормальных ощущений и момент, когда нужно связаться внепланово. Если домашнего формата становится мало, переводим в стационар без пауз — все назначения и наблюдения «переезжают» вместе с пациентом.
Получить дополнительную информацию – наркологическая клиника отзывы
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Исследовать вопрос подробнее – вывод из запоя клиника сочи
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Изучить вопрос глубже – нарколог на дом анонимно в сочи
Кроме безопасности и мониторинга — дисциплину режима. Там легче убрать триггеры, выстроить питание и сон, а психологу — подключить короткие мотивационные сессии, которые помогут удержать результат после выписки.
Узнать больше – вывод из запоя капельница на дому
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Сочи предлагает вывод из запоя в стационаре. Под наблюдением опытных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – вывод из запоя на дому круглосуточно сочи
Если пациент не может приехать в клинику, в Краснодаре нарколог приедет к нему домой. Помощь оказывает «Детокс» круглосуточно.
Подробнее можно узнать тут – запой нарколог на дом сочи
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Исследовать вопрос подробнее – https://shop-antinuisibles.com/avantages-des-insecticides-naturels
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее – врач вывод из запоя в сочи
«Светлый Шаг» — это не набор общих обещаний, а чётко выстроенный маршрут помощи, где каждый шаг прозрачен: от первичного разговора до устойчивой ремиссии. Мы бережно собираем только необходимые данные, сразу объясняем, что будет сделано в первые 6–12 часов, каких изменений ждать к ночи и по каким маркерам поймём, что курс выбран верно. Конфиденциальность встроена в процесс: нейтральные звонки, ограниченный доступ к медкарте, аккуратный выезд без броской атрибутики, возможность оформить документы с нейтральными формулировками. Итог — меньше стресса, меньше бюрократии и больше управляемости там, где это критично.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-odincovo0.ru
стайлер дайсон купить оригинал официальный сайт fen-dn-kupit-13.ru .
Кроме безопасности и мониторинга — дисциплину режима. Там легче убрать триггеры, выстроить питание и сон, а психологу — подключить короткие мотивационные сессии, которые помогут удержать результат после выписки.
Узнать больше – https://vyvod-iz-zapoya-krasnogorsk10.ru/
купить дайсон стайлер с насадками для волос официальный сайт цен… купить дайсон стайлер с насадками для волос официальный сайт цен… .
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Исследовать вопрос подробнее – срочный вывод из запоя в сочи
В Краснодаре клиника «Детокс» проводит выезд нарколога на дом для безопасного вывода из запоя.
Узнать больше – врач нарколог на дом краснодарский край
фен купить дайсон официальный сайт stajler-dsn-1.ru .
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Углубиться в тему – вызов нарколога на дом в сочи
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу.
Изучите внимательнее – https://ankurlaladvocate.com/how-to-file-a-case-under-the-motor-vehicles-act-a-comprehensive-guide
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Исследовать вопрос подробнее – вывод из запоя клиника в сочи
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Изучить вопрос глубже – вывод из запоя на дому цена в нижнем новгороде
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Подробнее тут – наркология вывод из запоя
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Разобраться лучше – https://vyvod-iz-zapoya-nizhnij-novgorod12.ru
login mostbet http://mostbet2033.help
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Узнать больше – вывод из запоя капельница на дому
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Подробнее тут – вызов нарколога на дом сочи
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Получить дополнительные сведения – вывод из запоя недорого
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Подробнее тут – narkolog-na-dom sochi
Что получите за 24 часа
Получить больше информации – наркологическая помощь на дому круглосуточно
Вызов нарколога на дом в Краснодаре — услуга клиники «Детокс». Специалисты оказывают квалифицированную помощь прямо у вас дома.
Исследовать вопрос подробнее – врач нарколог на дом в сочи
В Сочи клиника «Детокс» проводит вывод из запоя в стационаре с круглосуточным контролем врачей. Процедуры безопасны, эффективны и анонимны.
Получить дополнительную информацию – вывод из запоя клиника в сочи
официальный сайт дайсон стайлер для волос купить цена с насадкам… официальный сайт дайсон стайлер для волос купить цена с насадкам… .
дайсон стайлер для волос купить цена с насадками официальный сай… fen-dn-kupit-12.ru .
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Это ещё не всё… – https://p3-plus.com/5-elements-that-build-a-roster-of-terrific-clients
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Изучить вопрос глубже – вывод из запоя на дому недорого
Ожидаемая траектория в первые сутки
Углубиться в тему – narkologicheskaya-klinika-stoimost
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Хочешь знать всё? – http://betgopa.com/a-snowboarder-got-buried-upside-down-in-snow-see-skiers-quick-reaction
стайлер дайсон купить официальный сайт stajler-dsn-1.ru .
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу.
Все материалы собраны здесь – https://ilota.vn/blog/thuong-thuc-tra-matcha-9-nguyen-tac-tu-nhat-ban
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Полная информация здесь – https://icc-ccs.org/hellenic-shipping-news
Когда самочувствие «скачет», а ночь грозит затянуться, важен не героизм, а клинически выверенный план. В «МедОпоре» в Красногорске мы выстраиваем помощь так, чтобы каждый шаг давал предсказуемый эффект: первичное обследование, персональная инфузионная терапия, бережная коррекция тревоги и сна, мониторинг жизненно важных показателей и подробные рекомендации для семьи. Мы не используем «универсальные коктейли» и не маскируем симптомы — задача детокса в том, чтобы снять токсическую нагрузку, восстановить водно-электролитный баланс, стабилизировать вегетативные реакции и вернуть управляемость состоянием. С первых минут пациент получает ясные ориентиры: что делаем сейчас, чего ждать через час, по каким признакам нужно срочно звать врача. Анонимность соблюдается без компромиссов, а решения принимаются на основе реальных показателей — это снижает тревогу и исключает опасные «домашние эксперименты».
Получить дополнительные сведения – вывод из запоя
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Подробнее – врач вывод из запоя нижний новгород
Цель и ожидаемая динамика
Получить больше информации – narkologicheskaya-klinika-na-dom
Вызов нарколога на дом в Краснодаре доступен в любое время суток. Клиника «Детокс» гарантирует профессиональную помощь.
Подробнее тут – нарколог на дом вывод в сочи
«Ритм Здоровья» в Красногорске — это понятный маршрут помощи от первого звонка до устойчивой ремиссии. Мы не растягиваем старт на бесконечные согласования: дежурный врач аккуратно собирает жалобы, длительность эпизода, сведения о лекарствах и сопутствующих диагнозах, после чего предлагает безопасную точку входа — выезд на дом, приём без очередей или госпитализацию под круглосуточное наблюдение. Вся коммуникация нейтральная, доступ к карте ограничен лечащей командой, а в документах по запросу используем формулировки, не раскрывающие профиль отделения. Такой «тихий» формат снимает лишнее напряжение, экономит время семьи и позволяет сосредоточиться на главном — мягкой стабилизации без «качелей».
Исследовать вопрос подробнее – narkologicheskaya-klinika
Когда уместен
Разобраться лучше – анонимная наркологическая клиника
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врач приедет в течение 1–2 часов, проведёт необходимое обследование и назначит лечение. Услуга доступна круглосуточно и анонимно.
Исследовать вопрос подробнее – нарколог на дом вывод в сочи
Когда самочувствие «скачет», а ночь грозит затянуться, важен не героизм, а клинически выверенный план. В «МедОпоре» в Красногорске мы выстраиваем помощь так, чтобы каждый шаг давал предсказуемый эффект: первичное обследование, персональная инфузионная терапия, бережная коррекция тревоги и сна, мониторинг жизненно важных показателей и подробные рекомендации для семьи. Мы не используем «универсальные коктейли» и не маскируем симптомы — задача детокса в том, чтобы снять токсическую нагрузку, восстановить водно-электролитный баланс, стабилизировать вегетативные реакции и вернуть управляемость состоянием. С первых минут пациент получает ясные ориентиры: что делаем сейчас, чего ждать через час, по каким признакам нужно срочно звать врача. Анонимность соблюдается без компромиссов, а решения принимаются на основе реальных показателей — это снижает тревогу и исключает опасные «домашние эксперименты».
Получить дополнительную информацию – vyvod iz zapoya kapelnica
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Разобраться лучше – вывод из запоя нижний новгород
Когда уместен
Подробнее тут – частная наркологическая клиника
Первичный контакт — короткий, но точный скрининг: длительность эпизода, лекарства и аллергии, сон, аппетит, переносимость нагрузок, возможность обеспечить тишину на месте. На основе этих фактов врач предлагает безопасную точку входа: выезд на дом, приём без очередей или госпитализацию под наблюдением 24/7. На месте мы сразу исключаем «красные флажки», фиксируем давление/пульс/сатурацию/температуру, при показаниях выполняем ЭКГ и запускаем детокс. Параллельно выдаём «карту суток»: режим отдыха и питья, лёгкое питание, перечень нормальных ощущений и момент, когда нужно связаться внепланово. Если домашнего формата становится мало, переводим в стационар без пауз — все назначения и наблюдения «переезжают» вместе с пациентом.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-odincovo0.ru
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Детальнее – вывод из запоя на дому цена в сочи
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Подробнее – скорая вывод из запоя сочи
Формат
Подробнее можно узнать тут – narkologicheskaya-klinika-stoimost
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Узнать больше – нарколог на дом круглосуточно в сочи
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Получить больше информации – вызвать нарколога на дом сочи
Чтобы процедура прошла быстрее и спокойнее, подготовьте пространство и информацию о пациенте заранее: это экономит время и повышает безопасность.
Получить дополнительные сведения – https://vyvod-iz-zapoya-korolev10.ru/vyvod-iz-zapoya-v-stacionare-korolev/
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Изучить вопрос глубже – нарколог вывод из запоя
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Подробнее – вывод из запоя в стационаре нижний новгород
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Подробнее тут – вывод из запоя нижний новгород
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Выяснить больше – вывод из запоя капельница на дому
Что включено на практике
Изучить вопрос глубже – наркологические клиники в области
Экстренная помощь при запое в Нижнем Новгороде — капельница на дому от опытных врачей-наркологов.
Получить больше информации – вывод из запоя вызов на дом
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Уточнить детали – https://furnisheed.com/step-by-step-guide-to-installing-and-assembling-your-kitchen
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить больше информации – скорая вывод из запоя нижний новгород
Формат
Ознакомиться с деталями – наркологическая клиника анонимная помощь
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Узнать больше – вывод из запоя клиника
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Получить дополнительные сведения – narkolog-na-dom-kruglosutochno sochi
После первичной стабилизации врач обычно объясняет близким, почему «просто поспать» не всегда получается сразу, сколько времени может держаться раздражительность и как правильно выстроить режим, чтобы не спровоцировать повторный срыв в первые дни.
Выяснить больше – нарколог на дом недорого
Выезд нарколога на дом в Нижнем Новгороде — круглосуточная помощь при запое. Мы гарантируем анонимность и конфиденциальность на всех этапах лечения.
Подробнее тут – вывод из запоя недорого
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Углубиться в тему – вывод из запоя вызов на дом в нижнем новгороде
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Получить больше информации – вывод из запоя на дому круглосуточно в нижнем новгороде
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Получить дополнительную информацию – срочный вывод из запоя
Выезд нарколога на дом в Нижнем Новгороде — круглосуточная помощь при запое. Мы гарантируем анонимность и конфиденциальность на всех этапах лечения.
Изучить вопрос глубже – наркологический вывод из запоя нижний новгород
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Выяснить больше – наркологический вывод из запоя нижний новгород
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Получить дополнительные сведения – вывод из запоя на дому недорого сочи
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Подробнее можно узнать тут – вывод из запоя в стационаре нижний новгород
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Детальнее – вывод из запоя на дому цена в нижнем новгороде
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Ознакомиться с деталями – вывод из запоя недорого сочи
Gave ph333casino a shot last week. Gotta say, I was pleasantly surprised. The variety of games is solid, and I actually managed to win a bit! Give it a whirl: ph333casino. Good luck!
Если запой стал серьёзной проблемой, стационар клиники «Детокс» в Сочи поможет выйти из кризиса. Врачи проводят детоксикацию и наблюдают за состоянием пациента.
Подробнее тут – вывод из запоя на дому круглосуточно в сочи
Цель
Узнать больше – https://narkologicheskaya-klinika-shchyolkovo0.ru/narkologicheskaya-klinika-ceny-v-shchyolkovo
Ритм жизни в мегаполисе и постоянный стресс часто становятся причиной развития зависимостей у жителей города. В такой ситуации необходима профессиональная консультация врача. Оптимальное решение – вызов нарколога на дом в Москве. Это обеспечивает не только получение медицинской помощи в привычной обстановке, но и полную конфиденциальность.
Подробнее – http://narcolog-na-dom-msk55.ru
Как отмечает главный врач клиники, кандидат медицинских наук Сергей Иванов, «мы создали систему, при которой пациент получает помощь в течение часа — независимо от дня недели и времени суток. Это принципиально меняет шансы на выздоровление».
Подробнее можно узнать тут – телефоны наркологической помощи
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – вывод из запоя вызов в сочи
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Выяснить больше – вывод из запоя
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Хочешь знать всё? – https://www.mkepesbakhonne.com/forum-de-partage-de-fraternites-et-savoirs/?view=topic&id=156&part=1847
Капельница от запоя необходима, если у пациента наблюдаются следующие симптомы:
Исследовать вопрос подробнее – https://kapelnica-ot-zapoya-msk55.ru/kapelnica-ot-zapoya-cena-v-odincovo
Мир онлайн-слотов растёт: новые провайдеры, повышенные RTP и постоянные турниры поддерживают интерес игроков.
Vavada удерживает позиции в топе, но не забывайте проверять лицензию и лимиты перед депозитом.
Выбирайте автоматы с бонусными раундами, бесплатными вращениями и прогрессивными джекпотами — так повышается шанс крупного выигрыша.
Зеркала решают проблему блокировок и позволяют оперативно выводить средства без лишних задержек.
Актуальные возможности доступны здесь: https://temp-tools.kz//vendor/pgs/index.php?nel_kten_vavada_aynasu__azghet_.html.
Играйте ответственно и контролируйте банкролл, чтобы азарт оставался в пределах удовольствия.
Vavada остаётся одним из самых обсуждаемых казино благодаря щедрым бездепозитным промокодам и частым бонусам на фриспины.
Перед тем как активировать предложение, убедитесь, что промокод действителен сегодня и подходит под условия конкретной акции.
Слоты с высокой отдачей и турниры с гарантированными призами помогают быстро увеличить банкролл даже без крупного депозита.
Регистрация занимает пару минут, после чего становится доступен личный кабинет и быстрый вывод средств на банковскую карту.
Актуальные промокоды, бонус?коды и рабочее зеркало ждут по ссылке: vavada bonus.
Играйте ответственно и контролируйте бюджет, чтобы азарт приносил удовольствие, а не проблемы.
Также страдают сердце и сосуды. У пациентов часто наблюдаются тахикардия, нестабильное давление, аритмии, повышенный риск инфаркта или инсульта. Система пищеварения реагирует воспалением: гастрит, панкреатит, тошнота, рвота. Все эти изменения усиливаются на фоне обезвоживания и электролитного дисбаланса. Именно поэтому стандартное «отлежаться» или домашнее лечение чаще всего оказывается неэффективным и даже опасным. Необходима полноценная капельная терапия — с грамотно подобранными препаратами и медицинским наблюдением.
Подробнее тут – https://kapelnica-ot-zapoya-moskva3.ru/kapelnica-ot-zapoya-cena-v-himkah
Осложнения, к которым может привести отсутствие лечения:
Исследовать вопрос подробнее – снятие наркологической ломки
Алкогольная или наркотическая интоксикация — это не просто временное ухудшение самочувствия, а серьёзное медицинское состояние, требующее неотложной помощи. Когда человек находится в запое или состоянии ломки, его организм стремительно теряет силы, нарушается работа сердца, печени, мозга, возникают панические атаки, судороги, спутанность сознания. В таких случаях помощь должна быть незамедлительной. Если пациент не может самостоятельно добраться до клиники, оптимальным решением становится вызов нарколога на дом. В Красногорске такая услуга доступна круглосуточно благодаря выездной службе клиники «Ключ к Здоровью».
Исследовать вопрос подробнее – нарколог на дом цены
Инфузионная терапия собирается под конкретного пациента: регидратация и электролитная коррекция снимают интоксикацию и тремор, гепатопротективные препараты уменьшают нагрузку на печень, противорвотные и анксиолитики облегчают тошноту и тревогу, а бережная седация по показаниям возвращает нормальный сон без угнетения дыхания. Врач следит за динамикой — давлением, пульсом, сатурацией, уровнем тревоги — и при необходимости меняет скорость и состав капельницы. Важна коммуникация: каждое назначение объясняется пациенту и родственникам, оговариваются «красные флаги» и план на 24–48 часов — питьевой режим, щадящее питание, контроль давления, правила связи при изменениях самочувствия. Такой пошаговый подход сокращает период нестабильности и помогает безопасно перейти к обсуждению профилактики рецидива.
Получить дополнительные сведения – http://vyvod-iz-zapoya-lyubertsy2.ru/vyvod-iz-zapoya-lyuberczy-czeny/
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Подробнее – наркология вывод из запоя в нижнем новгороде
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить дополнительную информацию – вывод из запоя с выездом в нижнем новгороде
Для многих пациентов важным моментом является сохранение конфиденциальности. Врач, приехавший на дом, работает с полной защитой данных. Пациент может быть уверен, что его проблема останется личной и не станет достоянием общественности. Врачи приезжают на неприметных автомобилях и избегают всяческих ситуаций, которые могут привлечь лишнее внимание.
Получить дополнительную информацию – нарколог на дом анонимно
В нашей практике сочетаются несколько видов вмешательства: медико-биологическое, психологическое и социальное. Сначала проводится полная диагностика, включая лабораторные анализы и оценку работы сердца, печени, почек, а также психодиагностические тесты. После этого начинается этап детоксикации с внутривенными капельницами, которые выводят токсины, нормализуют водно-солевой баланс и восстанавливают основные функции организма. Далее мы применяем медикаментозную поддержку для стабилизации артериального давления, купирования тревожных симптомов, нормализации сна и уменьшения болевого синдрома.
Получить дополнительные сведения – https://narkologicheskaya-klinika-mytishchi1.ru
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Подробнее можно узнать тут – вывод из запоя на дому цена
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Исследовать вопрос подробнее – срочный вывод из запоя нижний новгород
To create stamps at home or in the office, you can use the servicemake stamps online, позволяющим быстро и качественно создавать необходимые печати без выхода из дома.
Once the design is complete, users can proceed to order their stamp, choosing from various materials and production options.
Users can choose from various shapes, sizes, and fonts, and can even upload their own images or logos.
Furthermore, the platform should provide excellent customer service, with support available via phone, email, or live chat.
By embracing the latest technology and trends, online rubber stamp makers will continue to innovate and improve, providing users with an unparalleled level of customization and convenience.
Наркологическая клиника «НаркологПроф» в Химках — это современный центр, специализирующийся на безопасном и быстром выведении из запоя. Здесь работают врачи-наркологи, анестезиологи и медицинские сестры с большим стажем. Клиника функционирует круглосуточно, обеспечивая как выездную помощь, так и стационарное лечение. Главная цель специалистов — восстановить работу организма после интоксикации, нормализовать давление, устранить тревогу и бессонницу, помочь пациенту вернуться к нормальному состоянию. Все процедуры проводятся анонимно, без постановки на учёт. Индивидуальный подход, корректный подбор медикаментов и строгий контроль состояния пациента делают лечение эффективным и безопасным.
Исследовать вопрос подробнее – vyvod-iz-zapoya-cena
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Узнать больше – нарколог вывод из запоя нижний новгород
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Узнать больше – анонимный вывод из запоя нижний новгород
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Смотрите также… – https://pureword.cibunet.com/cibuvideo/aralen-for-sale
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Выяснить больше – вывод из запоя на дому цена
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Выяснить больше – вывод из запоя вызов на дом нижний новгород
В нашей практике сочетаются несколько видов вмешательства: медико-биологическое, психологическое и социальное. Сначала проводится полная диагностика, включая лабораторные анализы и оценку работы сердца, печени, почек, а также психодиагностические тесты. После этого начинается этап детоксикации с внутривенными капельницами, которые выводят токсины, нормализуют водно-солевой баланс и восстанавливают основные функции организма. Далее мы применяем медикаментозную поддержку для стабилизации артериального давления, купирования тревожных симптомов, нормализации сна и уменьшения болевого синдрома.
Подробнее тут – http://narkologicheskaya-klinika-mytishchi1.ru/
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Получить дополнительные сведения – вывод из запоя капельница на дому в сочи
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Это ещё не всё… – https://ugi.tn/2023/09/25/solar-energy-benefits-going-green-and-saving-green
Для многих пациентов важным моментом является сохранение конфиденциальности. Врач, приехавший на дом, работает с полной защитой данных. Пациент может быть уверен, что его проблема останется личной и не станет достоянием общественности. Врачи приезжают на неприметных автомобилях и избегают всяческих ситуаций, которые могут привлечь лишнее внимание.
Углубиться в тему – vyzov vracha narkologa na dom
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Углубиться в тему – срочный вывод из запоя в нижнем новгороде
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Детальнее – вызов нарколога на дом в сочи
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Получить больше информации – вывод из запоя клиника в нижнем новгороде
Если запой стал серьёзной проблемой, стационар клиники «Детокс» в Сочи поможет выйти из кризиса. Врачи проводят детоксикацию и наблюдают за состоянием пациента.
Ознакомиться с деталями – вывод из запоя вызов в сочи
В клинике «НаркологПроф» детоксикация проводится под наблюдением специалистов, которые контролируют давление, частоту сердечных сокращений и дыхание пациента. Инфузионная терапия помогает восстановить электролитный баланс, ускорить выведение токсинов и улучшить общее состояние уже через несколько часов после начала лечения.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-v-himki1.ru
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Исследовать вопрос подробнее – https://icc-ccs.org/hellenic-shipping-news
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Разобраться лучше – вывод из запоя на дому цена
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-sochi15.ru
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Детали по клику – https://smartmeals.online/hello-world
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Подробнее можно узнать тут – вызов врача нарколога на дом сочи
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Исследовать вопрос подробнее – вывод из запоя капельница на дому в сочи
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Открой скрытое – https://pureword.cibunet.com/cibuvideo/aralen-for-sale
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Узнать больше – нарколог вывод из запоя в нижнем новгороде
1win partner 1win3002.mobi
Также мы учитываем потребности каждого пациента — по питанию, условиям проживания, графику процедур. Проживание возможно в стандартных и повышенных палатах, с возможностью индивидуального обслуживания.
Исследовать вопрос подробнее – http://
Вызов нарколога на дом в Краснодаре — услуга клиники «Детокс». Специалисты оказывают квалифицированную помощь прямо у вас дома.
Исследовать вопрос подробнее – вывод из запоя с выездом в сочи
Задача врачей — не просто облегчить симптомы, а купировать осложнения, стабилизировать жизненно важные функции, вернуть пациенту способность к дальнейшему лечению. Мы работаем быстро, анонимно и профессионально. Любой человек, оказавшийся в кризисе, может получить помощь в течение часа после обращения.
Узнать больше – https://snyatie-lomki-podolsk1.ru/snyatie-lomki-narkolog-v-podolske
Зависимость — это системная проблема, которая требует последовательного и профессионального подхода. Обычные попытки «вылечиться дома» без медицинского сопровождения нередко заканчиваются срывами, ухудшением состояния и психологической деградацией. Клиника «Здоровье Плюс» в Балашихе предоставляет пациентам не просто разовое вмешательство, а выстроенную поэтапную программу, основанную на опыте и медицинских стандартах.
Разобраться лучше – порядок наркологической помощи
Проведение лечения в домашней обстановке значительно снижает уровень стресса и тревожности. Пациенту не нужно тратить силы на поездки в медицинские учреждения, что особенно важно при ограниченной мобильности. Домашняя атмосфера создает идеальные условия для открытого диалога с врачом, что существенно повышает эффективность терапии и шансы на успешное выздоровление.
Получить дополнительные сведения – http://narcolog-na-dom-msk55.ru/narkolog-na-dom-kruglosutochno-moskva/
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Детальнее – наркологический вывод из запоя
Капельница от запоя на дому в Нижнем Новгороде — быстрый и эффективный способ снять симптомы похмелья и восстановить организм. Наши специалисты приедут к вам домой и проведут процедуру с использованием современных препаратов.
Получить дополнительные сведения – нарколог на дом вывод из запоя
Проведение лечения в домашней обстановке значительно снижает уровень стресса и тревожности. Пациенту не нужно тратить силы на поездки в медицинские учреждения, что особенно важно при ограниченной мобильности. Домашняя атмосфера создает идеальные условия для открытого диалога с врачом, что существенно повышает эффективность терапии и шансы на успешное выздоровление.
Выяснить больше – нарколог на дом недорого
Показания к проведению капельницы от запоя включают:
Углубиться в тему – https://kapelnica-ot-zapoya-moskva3.ru/kapelnicy-ot-zapoya-na-domu-v-himkah
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врач приедет в течение 1–2 часов, проведёт необходимое обследование и назначит лечение. Услуга доступна круглосуточно и анонимно.
Подробнее тут – вывод из запоя на дому круглосуточно в сочи
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Получить больше информации – вывод из запоя недорого
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Разобраться лучше – вывод из запоя цена в нижнем новгороде
В Сочи клиника «Детокс» предлагает полный курс вывода из запоя в стационаре. Круглосуточный медицинский контроль гарантирует безопасность и эффективность лечения.
Узнать больше – вывод из запоя на дому недорого сочи
После оформления заявки на сайте narcolog-na-dom-v-moskve55.ru или по телефону, оператор уточняет информацию о пациенте: возраст, длительность запоя, наличие хронических заболеваний, текущее самочувствие. В течение 30–60 минут дежурный специалист приезжает по адресу с полным комплектом оборудования и медикаментов.
Исследовать вопрос подробнее – вызвать нарколога на дом
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Подробнее можно узнать тут – вывод из запоя в стационаре нижний новгород
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Сочи предлагает вывод из запоя в стационаре. Под наблюдением опытных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – наркологический вывод из запоя
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить больше информации – вывод из запоя на дому цена нижний новгород
«НоваМед Центр» организует экстренную помощь при алкогольной интоксикации без очередей и лишней огласки. Команда наркологов и анестезиологов работает круглосуточно, выезжает на дом и принимает в стационаре, сохраняя один стандарт качества: очная оценка состояния, индивидуально подобранная инфузионная терапия, контроль жизненно важных показателей и понятные рекомендации на первые сутки. Схемы не шаблонные: состав и скорость капельницы зависят от длительности запоя, возраста, сопутствующих болезней и уже принятых лекарств. Наша цель — безопасно прервать запой, снять тремор, тревогу и тошноту, вернуть сон и аппетит, снизить нагрузку на сердце и печень, а затем предложить маршрут последующей помощи по готовности пациента — от амбулаторного наблюдения до программ профилактики срывов.
Углубиться в тему – vyvod iz zapoya
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Детальнее – вывод из запоя на дому недорого в нижнем новгороде
Перед началом процедуры врач проводит осмотр: измеряет давление, пульс, уровень кислорода в крови, оценивает тяжесть абстинентного синдрома. В зависимости от результатов и наличия сопутствующих заболеваний составляется индивидуальный состав инфузионного раствора. Он может включать:
Выяснить больше – http://kapelnica-ot-zapoya-msk55.ru/kapelnicy-ot-zapoya-na-domu-v-odincovo/
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Получить дополнительную информацию – https://aizlase.lv/strelnieks-kadi-sis-zimes-parstavji-ir-darba-milestiba-draudzibaa/60801/2
В наркологической клинике «Прозрение» в Одинцово процедура проводится с соблюдением всех стандартов безопасности, под контролем опытных врачей. Мы применяем комплексный подход, направленный не только на детоксикацию, но и на поддержку всех систем организма. Уже после одного сеанса пациенты отмечают улучшение самочувствия, снижение тревожности, исчезновение головной боли и тошноты.
Исследовать вопрос подробнее – после капельницы от запоя
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Подробности по ссылке – https://thespagroup.in/blog/life-with-future-of-smart-living-at-ecocity
Срочно нужен нарколог на дом? В Краснодаре клиника «Детокс» приезжает к пациенту в течение часа.
Исследовать вопрос подробнее – вывод из запоя на дому цена в сочи
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Детальнее – вывод из запоя на дому цена
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Углубиться в тему – наркологический вывод из запоя в нижнем новгороде
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Подробности по ссылке – https://sportspublication.net/product/physical-education-foundation
купить пылесос dyson v15 москва dn-pylesos.ru .
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить дополнительные сведения – срочный вывод из запоя нижний новгород
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Подробнее тут – нарколог на дом вывод из запоя в сочи
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Исследовать вопрос подробнее – narkolog-na-dom-kruglosutochno sochi
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Исследовать вопрос подробнее – вывод из запоя вызов
Именно поэтому так важно не терять время. Чем раньше пациент получает помощь, тем выше шансы избежать необратимых последствий и вернуться к нормальной жизни.
Подробнее – снятие ломки на дому московская область
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Узнать больше – срочный вывод из запоя в нижнем новгороде
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Подробнее тут – вывод из запоя в стационаре в сочи
Выезд нарколога на дом в Нижнем Новгороде — круглосуточная помощь при запое. Мы гарантируем анонимность и конфиденциальность на всех этапах лечения.
Получить дополнительную информацию – вывод из запоя
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Подробнее тут – вывод из запоя с выездом в сочи
В Сочи стационар клиники «Детокс» предлагает комплексный вывод из запоя. Пациентам обеспечивают комфорт, безопасность и круглосуточный контроль.
Подробнее можно узнать тут – срочный вывод из запоя
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Углубиться в тему – вывод из запоя капельница сочи
Мир онлайн-слотов растёт: новые провайдеры, повышенные RTP и постоянные турниры поддерживают интерес игроков.
Vavada удерживает позиции в топе, но не забывайте проверять лицензию и лимиты перед депозитом.
Выбирайте автоматы с бонусными раундами, бесплатными вращениями и прогрессивными джекпотами — так повышается шанс крупного выигрыша.
Зеркала решают проблему блокировок и позволяют оперативно выводить средства без лишних задержек.
Актуальные возможности доступны здесь: https://stroy-dokument.kz/media/pgs/?vr_kazino__gemblingt___bolasha_u_ma___lde_marketing_pe_.html.
Играйте ответственно и контролируйте банкролл, чтобы азарт оставался в пределах удовольствия.
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Исследовать вопрос подробнее – наркология вывод из запоя нижний новгород
Также мы учитываем потребности каждого пациента — по питанию, условиям проживания, графику процедур. Проживание возможно в стандартных и повышенных палатах, с возможностью индивидуального обслуживания.
Подробнее – http://narkologicheskaya-pomoshch-balashiha1.ru/
В Сочи клиника «Детокс» предлагает полный курс вывода из запоя в стационаре. Круглосуточный медицинский контроль гарантирует безопасность и эффективность лечения.
Получить больше информации – вывод из запоя дешево сочи
В Сочи клиника «Детокс» проводит вывод из запоя в стационаре с круглосуточным контролем врачей. Процедуры безопасны, эффективны и анонимны.
Ознакомиться с деталями – вывод из запоя сочи
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить дополнительную информацию – врач вывод из запоя в сочи
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Выяснить больше – вывод из запоя в стационаре в нижнем новгороде
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Уточнить детали – https://peruestor.com/hello-world
Наши врачи оперативно приезжают к пациенту, проводят осмотр, купируют симптомы абстиненции и приступают к восстановлению жизненно важных функций. Всё это — в привычной для пациента обстановке, без стресса и лишней огласки. Мы обеспечиваем не только медицинскую помощь, но и эмоциональную поддержку, создавая условия для начала пути к выздоровлению.
Детальнее – https://narcolog-na-dom-v-moskve55.ru/
Отсутствие визитов в клинику гарантирует полную конфиденциальность. Это особенно важно для пациентов, беспокоящихся о своей репутации или возможном влиянии на профессиональную деятельность. Вызов врача на дом полностью исключает нежелательные встречи в медицинском центре.
Узнать больше – нарколог на дом недорого
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Детальнее – https://vyvod-iz-zapoya-nizhnij-novgorod13.ru
Именно поэтому так важно не терять время. Чем раньше пациент получает помощь, тем выше шансы избежать необратимых последствий и вернуться к нормальной жизни.
Получить больше информации – снятие наркологической ломки на дому в подольске
пылесос дайсон купить в рязани пылесос дайсон купить в рязани .
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Подробности по ссылке – https://huliving.com/about
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Подробнее тут – https://folhanoroeste.com.br/cotidiano/veja-como-solicitar-servico-de-poda-de-arvores-para-prefeitura-de-sp
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Изучить вопрос глубже – вывод из запоя анонимно
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Получить дополнительную информацию – https://bulbuliindia.com/product/moroccan-wall-plate
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Хочешь знать всё? – https://climania.fr/?attachment_id=432
Для восстановления после запоя выбирайте стационар клиники «Детокс» в Сочи. Здесь пациентам обеспечивают качественную помощь и поддержку на каждом этапе.
Изучить вопрос глубже – вывод из запоя дешево в сочи
Первый контакт начинается с точных вопросов: длительность запоя, принятые лекарства, хронические болезни, аллергии, эпизоды аритмии или судорог. По приезде врач оценивает уровень сознания, измеряет давление, пульс, сатурацию, частоту дыхания, при необходимости проводит экспресс-глюкозу и ЭКГ переносным прибором. На этом этапе выбирается формат — на дому или в стационаре — исходя из клинических рисков и бытовых условий. Если показатели стабильны и рядом есть взрослый для наблюдения, домашний формат позволяет мягко и конфиденциально стабилизировать состояние. Если же ожидаются колебания давления, нарушения ритма, признаки делирия или выраженная дегидратация, безопаснее стационар, где доступен круглосуточный мониторинг и быстрая коррекция терапии без логистических пауз. Решение всегда объясняется простыми словами, чтобы пациент и близкие понимали логику маршрута.
Получить дополнительные сведения – http://vyvod-iz-zapoya-lyubertsy2.ru/
Как отмечает главный врач клиники, кандидат медицинских наук Сергей Иванов, «мы создали систему, при которой пациент получает помощь в течение часа — независимо от дня недели и времени суток. Это принципиально меняет шансы на выздоровление».
Ознакомиться с деталями – телефон доверия наркологической помощи
Именно поэтому так важно не терять время. Чем раньше пациент получает помощь, тем выше шансы избежать необратимых последствий и вернуться к нормальной жизни.
Ознакомиться с деталями – https://snyatie-lomki-podolsk1.ru/snyatie-lomki-narkolog-v-podolske
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Подробнее тут – https://noodlebowltbay.com/menus/meatloaf-with-black-pepper-honey-bbq-sauce
1win inscription 1win inscription
Также страдают сердце и сосуды. У пациентов часто наблюдаются тахикардия, нестабильное давление, аритмии, повышенный риск инфаркта или инсульта. Система пищеварения реагирует воспалением: гастрит, панкреатит, тошнота, рвота. Все эти изменения усиливаются на фоне обезвоживания и электролитного дисбаланса. Именно поэтому стандартное «отлежаться» или домашнее лечение чаще всего оказывается неэффективным и даже опасным. Необходима полноценная капельная терапия — с грамотно подобранными препаратами и медицинским наблюдением.
Изучить вопрос глубже – капельница от запоя на дому химки
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее можно узнать тут – вызвать нарколога на дом в сочи
Алкогольная или наркотическая интоксикация — это не просто временное ухудшение самочувствия, а серьёзное медицинское состояние, требующее неотложной помощи. Когда человек находится в запое или состоянии ломки, его организм стремительно теряет силы, нарушается работа сердца, печени, мозга, возникают панические атаки, судороги, спутанность сознания. В таких случаях помощь должна быть незамедлительной. Если пациент не может самостоятельно добраться до клиники, оптимальным решением становится вызов нарколога на дом. В Красногорске такая услуга доступна круглосуточно благодаря выездной службе клиники «Ключ к Здоровью».
Узнать больше – психиатр нарколог на дом красногорск
Отсутствие визитов в клинику гарантирует полную конфиденциальность. Это особенно важно для пациентов, беспокоящихся о своей репутации или возможном влиянии на профессиональную деятельность. Вызов врача на дом полностью исключает нежелательные встречи в медицинском центре.
Получить больше информации – нарколог на дом анонимно
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Изучить вопрос глубже – нарколог на дом клиника в сочи
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Подробнее можно узнать тут – вывод из запоя на дому цена сочи
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Получить больше информации – вывод из запоя на дому цена
Вызов нарколога на дом в таких условиях позволяет не терять драгоценное время, избежать госпитализации и предотвратить критическое развитие событий. Кроме того, это снижает психологическую нагрузку на пациента и его близких, особенно если зависимость длится долго и сопровождается отрицанием проблемы.
Исследовать вопрос подробнее – вызвать нарколога на дом в красногорске
networking made easy – Smooth navigation makes accessing key links quick and simple.
пылесос дайсон купить в тюмени пылесос дайсон купить в тюмени .
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Углубиться в тему – https://narkolog-na-dom-krasnodar15.ru/
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Углубиться в тему – анонимный вывод из запоя в нижнем новгороде
Ломка — это не временное недомогание. Это системное разрушение организма, связанное с тем, что он перестаёт получать наркотик, к которому уже привык. Нарушается обмен веществ, функции сердца, печени, почек, теряется контроль над эмоциями и болью. В состоянии абстиненции человек не может спать, есть, адекватно мыслить. Страдает и тело, и психика.
Выяснить больше – http://www.domen.ru
Во время длительного употребления алкоголя тело человека испытывает многоступенчатую интоксикацию. Сначала страдает печень — главный орган детоксикации. Постепенно нарушается фильтрация, и продукты распада этанола начинают циркулировать по крови, вызывая общее отравление. Далее страдает головной мозг: снижается уровень витамина B1, нарушается проводимость нервных импульсов, появляются спутанность сознания, агрессия, тревога, нарушения сна и координации.
Разобраться лучше – капельница химки от запоя
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Углубиться в тему – нарколог на дом цена сочи
Именно поэтому так важно не терять время. Чем раньше пациент получает помощь, тем выше шансы избежать необратимых последствий и вернуться к нормальной жизни.
Выяснить больше – снять ломку подольск
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Сочи предлагает вывод из запоя в стационаре. Под наблюдением опытных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Узнать больше – наркологический вывод из запоя сочи
Клиника «Похмельная служба» в Нижнем Новгороде предлагает комплексное лечение запоя с использованием капельницы. Наши специалисты проводят диагностику и назначают индивидуальный план лечения.
Разобраться лучше – вывод из запоя в стационаре в нижнем новгороде
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Получить дополнительные сведения – вывод из запоя с выездом сочи
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – вывод из запоя с выездом
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – вывод из запоя вызов на дом сочи
Если вам нужна аренда авто в новосибирске с водителем, обращайтесь к нам — мы гарантируем комфорт и безопасность на дороге.
Это объясняется растущими потребностями в организационных мероприятиях и деловых поездках.
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Подробнее можно узнать тут – вывод из запоя недорого
Для многих пациентов важным моментом является сохранение конфиденциальности. Врач, приехавший на дом, работает с полной защитой данных. Пациент может быть уверен, что его проблема останется личной и не станет достоянием общественности. Врачи приезжают на неприметных автомобилях и избегают всяческих ситуаций, которые могут привлечь лишнее внимание.
Узнать больше – http://narcolog-na-dom-moskva55.ru
Алкогольная или наркотическая интоксикация — это не просто временное ухудшение самочувствия, а серьёзное медицинское состояние, требующее неотложной помощи. Когда человек находится в запое или состоянии ломки, его организм стремительно теряет силы, нарушается работа сердца, печени, мозга, возникают панические атаки, судороги, спутанность сознания. В таких случаях помощь должна быть незамедлительной. Если пациент не может самостоятельно добраться до клиники, оптимальным решением становится вызов нарколога на дом. В Красногорске такая услуга доступна круглосуточно благодаря выездной службе клиники «Ключ к Здоровью».
Исследовать вопрос подробнее – нарколог на дом клиника красногорск
На месте врач проводит первичный осмотр, измеряет давление, пульс, сатурацию, оценивает уровень интоксикации и абстиненции. Далее назначается инфузионная терапия — капельница, направленная на дезинтоксикацию, восстановление электролитного баланса, купирование тревожности и нормализацию сна.
Выяснить больше – врач нарколог на дом
Преимущества домашнего лечения также заключаются в индивидуальном подходе. Врач, находясь в вашем доме, может более тщательно изучить ситуацию, провести необходимую диагностику и подобрать курс лечения, который идеально подойдет вашему состоянию. В отличие от клиники, где внимание врача часто ограничено временем, на дому можно уделить пациенту больше времени, подбирая лечение с учетом его особенностей.
Подробнее можно узнать тут – narkolog na dom nedorogo
Также мы учитываем потребности каждого пациента — по питанию, условиям проживания, графику процедур. Проживание возможно в стандартных и повышенных палатах, с возможностью индивидуального обслуживания.
Подробнее можно узнать тут – http://narkologicheskaya-pomoshch-balashiha1.ru
Узнайте подробности по заказать забор из штакетника и сделайте правильный выбор.
Металлические ограждения отличаются прочностью и долговечностью, но имеют более высокую цену.
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Разобраться лучше – вывод из запоя вызов на дом в сочи
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Узнать больше – выезд нарколога на дом в сочи
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Углубиться в тему – вывод из запоя вызов на дом
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – помощь вывод из запоя сочи
strategic inspiration – The concepts feel relevant and easy to absorb.
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Детальнее – наркология вывод из запоя
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Подробности по ссылке – https://miawodo.org/produit/paniers-de-rangement-rond-avec-couvercle
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Получить дополнительную информацию – https://www.laure.archi.fr/?p=930
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Получить дополнительную информацию – https://eth-news.com/hello-world
Проведение лечения в домашней обстановке значительно снижает уровень стресса и тревожности. Пациенту не нужно тратить силы на поездки в медицинские учреждения, что особенно важно при ограниченной мобильности. Домашняя атмосфера создает идеальные условия для открытого диалога с врачом, что существенно повышает эффективность терапии и шансы на успешное выздоровление.
Выяснить больше – narkolog na dom anonimno
Абстинентный синдром — одно из самых тяжёлых и опасных проявлений наркотической зависимости. Он развивается на фоне резкого отказа от приёма веществ и сопровождается сильнейшими нарушениями работы организма. Это состояние требует немедленного вмешательства. Самостоятельно справиться с ним невозможно — особенно если речь идёт о героине, метадоне, синтетических наркотиках или длительной зависимости. В клинике «НаркоПрофи» мы организовали систему снятия ломки в Подольске, работающую круглосуточно: как на дому, так и в условиях стационара.
Получить больше информации – https://snyatie-lomki-podolsk1.ru/snyatie-lomki-narkomana-v-podolske/
пылесос дайсон напольный купить dn-pylesos.ru .
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Получить дополнительную информацию – https://narkolog-na-dom-krasnodar12.ru/
Срочно нужен нарколог на дом? В Краснодаре клиника «Детокс» приезжает к пациенту в течение часа.
Изучить вопрос глубже – врач нарколог на дом сочи
Именно поэтому так важно не терять время. Чем раньше пациент получает помощь, тем выше шансы избежать необратимых последствий и вернуться к нормальной жизни.
Детальнее – снятие наркотической ломки
Во время длительного употребления алкоголя тело человека испытывает многоступенчатую интоксикацию. Сначала страдает печень — главный орган детоксикации. Постепенно нарушается фильтрация, и продукты распада этанола начинают циркулировать по крови, вызывая общее отравление. Далее страдает головной мозг: снижается уровень витамина B1, нарушается проводимость нервных импульсов, появляются спутанность сознания, агрессия, тревога, нарушения сна и координации.
Детальнее – капельница от запоя
Одним из самых привлекательных аспектов вызова нарколога на дом является гибкость. Вы можете согласовать время визита врача, подходящее именно для вас, включая вечернее или ночное время. Это позволяет совмещать лечение с работой и личными делами, не нарушая привычный ритм жизни.
Детальнее – vrach narkolog na dom moskva
Показания к проведению капельницы от запоя включают:
Подробнее тут – http://kapelnica-ot-zapoya-moskva3.ru/kapelnica-ot-zapoya-cena-v-himkah/
Капельница от запоя на дому в Нижнем Новгороде — удобное решение для тех, кто не может посетить клинику. Наши специалисты приедут к вам домой и проведут необходимую процедуру.
Получить больше информации – наркология вывод из запоя в нижнем новгороде
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Полная информация здесь – https://www.lawnews.co.uk/legal-insight/appointments/clarke-willmott-grows-social-housing-condition-claims-specialism-with-new-partner-appointment
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее тут – срочный вывод из запоя сочи
strategic path guide – Easy guidance, turning plans into measurable progress feels natural.
Процесс начинается с вызова врача или доставки пациента в клинику. После прибытия специалист проводит первичную диагностику: измерение давления, температуры, пульса, уровня кислорода в крови, визуальная оценка степени возбуждения или угнетения сознания. Собирается краткий анамнез: какой наркотик принимался, как долго, были ли сопутствующие заболевания.
Ознакомиться с деталями – https://snyatie-lomki-podolsk1.ru/
1win shikoyatlar uz https://MAQOLALAR.UZ
выпрямитель дайсон airstrait выпрямитель дайсон airstrait .
Если вы или ваш близкий нуждаетесь в профессиональной помощи при запое, клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врач приедет в течение 1–2 часов, проведёт необходимое обследование и назначит лечение. Услуга доступна круглосуточно и анонимно.
Получить больше информации – запой нарколог на дом сочи
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Получить больше информации – скорая вывод из запоя в сочи
В повседневности неточный ориентир часто заставляет терять время, поэтому мы проговариваем симптомы, при которых тянуть нельзя. Список не заменяет осмотр, он помогает близким описать ситуацию по телефону и выбрать правильный маршрут вместе с врачом.
Получить дополнительные сведения – вывод из запоя капельница
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Узнать больше – вывод из запоя на дому недорого нижний новгород
Экстренная помощь при запое в Нижнем Новгороде — капельница на дому от опытных врачей-наркологов.
Изучить вопрос глубже – наркологический вывод из запоя нижний новгород
Одним из самых привлекательных аспектов вызова нарколога на дом является гибкость. Вы можете согласовать время визита врача, подходящее именно для вас, включая вечернее или ночное время. Это позволяет совмещать лечение с работой и личными делами, не нарушая привычный ритм жизни.
Изучить вопрос глубже – https://narcolog-na-dom-moskva55.ru/narkolog-na-dom-moskva-tseny
expand knowledge base – Feels motivating and well structured for gradual learning.
Ломка — это не временное недомогание. Это системное разрушение организма, связанное с тем, что он перестаёт получать наркотик, к которому уже привык. Нарушается обмен веществ, функции сердца, печени, почек, теряется контроль над эмоциями и болью. В состоянии абстиненции человек не может спать, есть, адекватно мыслить. Страдает и тело, и психика.
Выяснить больше – снятие наркологической ломки на дому подольск
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Выяснить больше – наркология вывод из запоя сочи
You’ve provided practical wisdom for immediate use.
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Детальнее – вывод из запоя с выездом сочи
Зависимость — это системная проблема, которая требует последовательного и профессионального подхода. Обычные попытки «вылечиться дома» без медицинского сопровождения нередко заканчиваются срывами, ухудшением состояния и психологической деградацией. Клиника «Здоровье Плюс» в Балашихе предоставляет пациентам не просто разовое вмешательство, а выстроенную поэтапную программу, основанную на опыте и медицинских стандартах.
Исследовать вопрос подробнее – http://narkologicheskaya-pomoshch-balashiha1.ru/narkologicheskaya-pomoshch-na-domu-v-balashihe/
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить дополнительную информацию – вывод из запоя на дому цена
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Получить больше информации – нарколог на дом краснодарский край
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Исследовать вопрос подробнее – вывод из запоя вызов в сочи
market alliance strategies – Clear advice, helps connect theory to practical market scenarios.
Одним из самых привлекательных аспектов вызова нарколога на дом является гибкость. Вы можете согласовать время визита врача, подходящее именно для вас, включая вечернее или ночное время. Это позволяет совмещать лечение с работой и личными делами, не нарушая привычный ритм жизни.
Получить больше информации – врач нарколог на дом москва
Стационарная программа позволяет стабилизировать не только физическое состояние, но и эмоциональную сферу. Находясь в изоляции от внешних раздражителей и вредных контактов, пациент получает шанс сконцентрироваться на себе и начать реабилитацию без давления извне.
Подробнее можно узнать тут – https://narkologicheskaya-pomoshch-balashiha1.ru/skoraya-narkologicheskaya-pomoshch-v-balashihe
Запой — это не просто несколько дней бесконтрольного употребления алкоголя. Это тяжёлое патологическое состояние, при котором организм человека накапливает токсические продукты распада этанола, теряет жизненно важные электролиты, обезвоживается и выходит из равновесия. На фоне этого нарушается работа сердца, мозга, печени и других систем. Чем дольше длится запой, тем тяжелее последствия и выше риск развития осложнений, вплоть до алкогольного психоза или инсульта. В такой ситуации незаменимым методом экстренной помощи становится капельница от запоя — процедура, позволяющая быстро и безопасно вывести токсины, стабилизировать жизненно важные функции и вернуть человеку контроль над собой.
Получить дополнительные сведения – http://kapelnica-ot-zapoya-moskva3.ru/kapelnica-ot-zapoya-cena-v-himkah/
После оформления заявки на сайте narcolog-na-dom-v-moskve55.ru или по телефону, оператор уточняет информацию о пациенте: возраст, длительность запоя, наличие хронических заболеваний, текущее самочувствие. В течение 30–60 минут дежурный специалист приезжает по адресу с полным комплектом оборудования и медикаментов.
Получить больше информации – вызов врача нарколога на дом в красногорске
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Исследовать вопрос подробнее – наркологический вывод из запоя
Одной из самых сильных сторон нашей клиники является оперативность. Мы понимаем, что при алкоголизме, наркомании и лекарственной зависимости часто требуются немедленные действия. Если человек находится в состоянии запоя, абстиненции или передозировки, промедление может привести к тяжёлым осложнениям или даже смерти.
Получить дополнительные сведения – kruglosutochnaya-narkologicheskaya-pomoshch
Показания к проведению капельницы от запоя включают:
Исследовать вопрос подробнее – https://kapelnica-ot-zapoya-moskva3.ru/kapelnica-ot-zapoya-cena-v-himkah/
business contacts center – Informative platform, connecting with professionals is easy and approachable.
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Подробности по ссылке – https://www.walterkrijgerdakwerken.nl/commercial/the-evolution-of-smart-home-electrical-systems-for-everyone
В Краснодаре нарколог из клиники «Детокс» приедет на дом, чтобы вывести из запоя и оказать необходимую помощь.
Углубиться в тему – нарколог на дом цена в сочи
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Изучить вопрос глубже – нарколог вывод из запоя сочи
В Сочи стационар клиники «Детокс» предлагает комплексный вывод из запоя. Пациентам обеспечивают комфорт, безопасность и круглосуточный контроль.
Узнать больше – вывод из запоя в стационаре в сочи
выпрямитель dyson airstrait ht01 купить минск vypryamitel-dn-4.ru .
«НоваМед Центр» организует экстренную помощь при алкогольной интоксикации без очередей и лишней огласки. Команда наркологов и анестезиологов работает круглосуточно, выезжает на дом и принимает в стационаре, сохраняя один стандарт качества: очная оценка состояния, индивидуально подобранная инфузионная терапия, контроль жизненно важных показателей и понятные рекомендации на первые сутки. Схемы не шаблонные: состав и скорость капельницы зависят от длительности запоя, возраста, сопутствующих болезней и уже принятых лекарств. Наша цель — безопасно прервать запой, снять тремор, тревогу и тошноту, вернуть сон и аппетит, снизить нагрузку на сердце и печень, а затем предложить маршрут последующей помощи по готовности пациента — от амбулаторного наблюдения до программ профилактики срывов.
Подробнее можно узнать тут – vyvod iz zapoya kruglosutochno
Ритм жизни в мегаполисе и постоянный стресс часто становятся причиной развития зависимостей у жителей города. В такой ситуации необходима профессиональная консультация врача. Оптимальное решение – вызов нарколога на дом в Москве. Это обеспечивает не только получение медицинской помощи в привычной обстановке, но и полную конфиденциальность.
Получить дополнительные сведения – вызов нарколога на дом
Для кинотеатров, конференц-залов и домашних кинозалов подойдет проекционные экраны, который можно заказать на сайте.
являются важнейшим компонентом любого презентационного оборудования . Они необходимы для создания комфортных условий просмотра . Кроме того, выбор экрана зависит от??ных требований пользователя.
Экраны можут быть стационарными или переносными . Для домашнего кинотеатра или небольшого офиса существуют специализированные модели экранов . Это дает возможность подобрать наиболее подходящий экран для конкретных задач.
Экраны для проекторов различаются по принципу конструкции. Это экраны с ручным управлением , которые устанавливаются на стену или потолок . Кроме того, есть варианты для различных условий освещения.
Экраны для задней проекции используются в специфических условиях . Они обеспечивают комфортный просмотр . Это объясняет их широкое применение.
При выборе экрана для проектора нужно проанализировать конкретные требования. Это размер комнаты и количество зрителей , которые влияют на выбор размера и типа экрана . Кроме того, следует оценить потенциал будущего обновления оборудования.
Экраны следует выбирать с учетом условий эксплуатации. Это обуславливает повышение эффективности презентаций. Поэтому рекомендуется консультироваться с профессионалами .
Экраны для проекторов обязательны для создания комфортных условий просмотра. Они необходимо подбирать исходя из конкретных требований . Это дает возможность оптимизировать процесс демонстрации . Поэтому важно обратить внимание на все нюансы выбора экрана .
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Ознакомиться с деталями – вывод из запоя на дому цена нижний новгород
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Смотрите также… – https://jamescohane.com/wtf-is-biz-dev-aka-what-is-business-development
modern buying hub – Browsing feels curated and visually appealing with trendy selections.
GrowthStrategyHub – Provides structured guidance for implementing growth plans efficiently.
Если пациент не может приехать в клинику, в Краснодаре нарколог приедет к нему домой. Помощь оказывает «Детокс» круглосуточно.
Получить дополнительные сведения – скорая вывод из запоя в сочи
В Сочи клиника «Детокс» предлагает вывод из запоя в стационаре. Опытные врачи обеспечивают полную безопасность и комфорт пациента, а услуги доступны круглосуточно.
Выяснить больше – вывод из запоя с выездом
task focus hub – Very clear advice, helps prevent distractions and maintain steady progress.
После оформления заявки на сайте narcolog-na-dom-v-moskve55.ru или по телефону, оператор уточняет информацию о пациенте: возраст, длительность запоя, наличие хронических заболеваний, текущее самочувствие. В течение 30–60 минут дежурный специалист приезжает по адресу с полным комплектом оборудования и медикаментов.
Детальнее – нарколог на дом клиника в красногорске
Показания к проведению капельницы от запоя включают:
Получить больше информации – поставить капельницу от запоя
Проведение лечения в домашней обстановке значительно снижает уровень стресса и тревожности. Пациенту не нужно тратить силы на поездки в медицинские учреждения, что особенно важно при ограниченной мобильности. Домашняя атмосфера создает идеальные условия для открытого диалога с врачом, что существенно повышает эффективность терапии и шансы на успешное выздоровление.
Изучить вопрос глубже – narkolog na dom nedorogo
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее можно узнать тут – вывод из запоя капельница
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Подробнее можно узнать тут – врач вывод из запоя
Вывод из запоя у пожилых людей в Москве от клиники «Частный Медик 24». Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Исследовать вопрос подробнее – narkologicheskaya-pomoshch-na-domu moskva
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Исследовать вопрос подробнее – скорая вывод из запоя в сочи
Лечение пивного алкоголизма в Москве от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Подробнее можно узнать тут – наркологическая помощь на дому москве
Круглосуточная помощь при запое в Подольске от клиники «Частный Медик 24». Наша команда работает 24/7, обеспечивая доступность медицинской помощи в любое время суток.
Исследовать вопрос подробнее – капельница от запоя вызов
Капельница от запоя в Нижнем Новгороде — процедура, направленная на детоксикацию организма и восстановление нормального самочувствия. Она включает в себя введение препаратов, способствующих выведению токсинов и восстановлению функций органов.
Углубиться в тему – врач вывод из запоя в нижнем новгороде
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Изучить вопрос глубже – врач вывод из запоя сочи
Equili
direction guide – Very practical advice, makes planning steps toward goals clear and achievable.
connectsphere – Provides a structured approach to networking in professional circles.
Если близкий человек в состоянии запоя, закажите нарколога на дом в Краснодаре от клиники «Детокс». Круглосуточно и конфиденциально.
Ознакомиться с деталями – narkolog-na-dom-krasnodar17.ru
business bond support – Feels solid and trustworthy, with well-presented details.
Помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Получить дополнительную информацию – анонимная наркологическая помощь москва
Кодирование от алкоголизма в Москве от клиники «Частный Медик 24». Мы предлагаем различные методы кодирования, подходящие для каждого пациента.
Получить дополнительную информацию – наркологическая помощь телефон
дайсон фен выпрямитель для волос купить оригинал vypryamitel-dn-4.ru .
Помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Подробнее тут – круглосуточная наркологическая помощь
Вывод из запоя у пожилых людей в Подольске от клиники «Частный Медик 24». Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Исследовать вопрос подробнее – капельница от запоя на дому город. московская область
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Разобраться лучше – нарколог на дом цена сочи
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – срочный вывод из запоя в сочи
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – vyvod-iz-zapoya-sochi22.ru
Реабилитация после запоя в Москве от клиники «Частный Медик 24». Мы поможем вам восстановиться после запоя и предотвратить рецидивы.
Исследовать вопрос подробнее – вызов скорой наркологической помощи москва
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Детали по клику – https://ceritakepuasan.online/cerita-kepuasan-nikmatnya-di-dunia-perkemahan
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – вывод из запоя анонимно
ExpandYourLearning – Insightful guidance, concepts are easy to grasp and apply.
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Получить дополнительную информацию – narkolog-na-dom sochi
Кодирование от алкоголизма на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Получить дополнительную информацию – круглосуточная наркологическая помощь москва
Кодирование от алкоголизма на дому в Подольске от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Изучить вопрос глубже – врача капельницу от запоя в москве
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Полная информация здесь – https://www.gishurim.co.il/3-%D7%93%D7%91%D7%A8%D7%99%D7%9D-%D7%90%D7%A9%D7%A8-%D7%9E%D7%AA%D7%A7%D7%99%D7%99%D7%9E%D7%99%D7%9D-%D7%91%D7%9B%D7%9C-%D7%94%D7%9C%D7%99%D7%9A-%D7%92%D7%99%D7%A9%D7%95%D7%A8-%D7%92%D7%99%D7%A8%D7%95
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Смотрите также… – https://radiotaxiarroyomolinos.es/european-airports-increase-tax-on-foreign-passengers-2
shop smarter here – Gives a customer-first impression with a layout that feels easy and intuitive.
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Выяснить больше – https://narkolog-na-dom-krasnodar17.ru
Анонимность и конфиденциальность гарантированы в клинике «Частный Медик 24». Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Углубиться в тему – анонимная наркологическая помощь москве
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Получить дополнительные сведения – вывод из запоя капельница сочи
BudgetSaverNetwork – Offers practical options for price-conscious online shoppers.
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Детальнее – вывод из запоя с выездом
купить выпрямитель дайсон пенза в наличии vypryamitel-dn-4.ru .
growth roadmap hub – Practical advice on maintaining consistent progress and success.
Анонимность и конфиденциальность гарантированы в клинике «Частный Медик 24». Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Узнать больше – платная наркологическая помощь москве
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Подробнее тут – https://hook.ng/best-way-to-redeem-amazon-gift-cards-for-naira-online
Лечение пивного алкоголизма в Подольске от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Изучить вопрос глубже – вызвать капельницу от запоя в москве
1win mobil kirish http://www.SPORT-PROGRAMMING.UZ
Клиника «Детокс» в Сочи предлагает услугу вывода из запоя в стационаре. Под наблюдением профессиональных врачей пациент получит необходимую медицинскую помощь и поддержку. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Углубиться в тему – вывод из запоя в стационаре в сочи
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Получить дополнительную информацию – вывод из запоя капельница на дому
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Подробнее тут – вывод из запоя с выездом в сочи
EnterpriseBondingCenter – Supports thoughtful and scalable partnership strategies.
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Уточнить детали – https://wiseparadise.com/boost-your-confidence-with-inspirational-and-motivational-cards
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Детали по клику – https://www.floordeckx.be/boek/frans-laarmans
Вывод из запоя у пожилых людей в Москве от клиники «Частный Медик 24». Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Выяснить больше – [url=https://skoraya-narkologicheskaya-pomoshch-moskva12.ru/]вызов скорой наркологической помощи[/url]
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Исследовать вопрос подробнее – вывод из запоя
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Детали по клику – https://transformupconsulting.com.au/what-we-are-capable-to-usually-discovered-3
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Подробнее тут – вывод из запоя на дому круглосуточно сочи
SecureDealOnline – Easy navigation, online shopping is clear and dependable.
Кодирование от алкоголизма на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Подробнее – скорая наркологическая помощь московская область
Лечение пивного алкоголизма в Москве от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Узнать больше – вызвать наркологическую помощь
planforsuccess – Highlights planning, supports companies seeking organized growth pathways.
В Краснодаре клиника «Детокс» предлагает услугу выезда нарколога на дом. Быстро, безопасно, анонимно.
Получить дополнительную информацию – врач нарколог на дом сочи
Профессиональная помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Мы предлагаем капельницу, которая способствует восстановлению водно-электролитного баланса и улучшению общего состояния пациента.
Исследовать вопрос подробнее – вызов скорой наркологической помощи москва
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Исследовать вопрос подробнее – врач нарколог на дом краснодарский край
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее – вывод из запоя на дому цена в сочи
Лечение зависимости от алкоголя на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут все необходимые процедуры.
Получить больше информации – narkologicheskaya-pomoshch-na-domu moskva
Лечение пивного алкоголизма в Москве от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Разобраться лучше – наркологическая помощь на дому москве
В Сочи стационар клиники «Детокс» предлагает комплексный вывод из запоя. Пациентам обеспечивают комфорт, безопасность и круглосуточный контроль.
Подробнее можно узнать тут – вывод из запоя сочи
В Краснодаре нарколог из клиники «Детокс» приедет на дом, чтобы вывести из запоя и оказать необходимую помощь.
Детальнее – вывод из запоя на дому цена в сочи
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Выяснить больше – вывод из запоя дешево в сочи
Если запой стал серьёзной проблемой, стационар клиники «Детокс» в Сочи поможет выйти из кризиса. Врачи проводят детоксикацию и наблюдают за состоянием пациента.
Углубиться в тему – вывод из запоя вызов на дом
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Подробнее – врач вывод из запоя нижний новгород
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Получить больше информации – вывод из запоя клиника
safe purchase network – The site is easy to navigate, making shopping quick and clear.
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Узнать больше – вызов нарколога на дом краснодарский край
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Детальнее – нарколог на дом вывод сочи
SavvyDealsHub – Focuses on affordability and convenience for online buyers.
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Изучить вопрос глубже – вывод из запоя на дому цена в сочи
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Получить больше информации – нарколог на дом анонимно в сочи
В Краснодаре клиника «Детокс» проводит выезд нарколога на дом для безопасного вывода из запоя.
Подробнее – вывод из запоя капельница на дому в сочи
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее – вывод из запоя дешево в сочи
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Уточнить детали – https://gurukulyogashala.com/blog/benefits-of-yoga
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Получить дополнительные сведения – анонимный вывод из запоя в сочи
Капельница от запоя в Нижнем Новгороде — процедура, включающая физраствор, глюкозу, витамины и седативные препараты. Она помогает восстановить водно-электролитный баланс и улучшить самочувствие.
Исследовать вопрос подробнее – вывод из запоя на дому недорого нижний новгород
Клиника «Похмельная служба» в Нижнем Новгороде предлагает капельницу от запоя с выездом на дом. Наши специалисты обеспечат вам комфортное и безопасное лечение в привычной обстановке.
Получить больше информации – вывод из запоя на дому цена
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Получить больше информации – наркологический вывод из запоя в сочи
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Изучить вопрос глубже – нарколог вывод из запоя
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Изучить вопрос глубже – наркология вывод из запоя в сочи
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Получить больше информации – вывод из запоя цена в нижнем новгороде
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Углубиться в тему – нарколог на дом вывод из запоя в сочи
Круглосуточная наркологическая скорая помощь в Москве от клиники «Частный Медик 24». Наша команда работает 24/7, обеспечивая доступность медицинской помощи в любое время суток.
Ознакомиться с деталями – круглосуточная наркологическая помощь московская область
Профилактика рецидивов после запоя в Москве от клиники «Частный Медик 24». Мы поможем вам предотвратить повторные случаи запоя и поддержим вас на пути к трезвой жизни.
Подробнее можно узнать тут – платная наркологическая помощь
В Сочи клиника «Детокс» проводит вывод из запоя в стационаре с круглосуточным контролем врачей. Процедуры безопасны, эффективны и анонимны.
Подробнее можно узнать тут – вывод из запоя вызов
Капельница от запоя — эффективный способ детоксикации в клинике «Частный Медик 24». Мы используем современные препараты для быстрого и безопасного выведения из запоя.
Ознакомиться с деталями – капельница от запоя наркология
Капельница от похмелья — эффективный способ детоксикации в клинике «Частный Медик 24». Мы используем современные препараты для быстрого и безопасного выведения токсинов из организма.
Подробнее можно узнать тут – наркологическая помощь на дому московская область
Лечение запоя без госпитализации в Москве от клиники «Частный Медик 24». Мы предлагаем лечение на дому, без необходимости госпитализации.
Подробнее можно узнать тут – срочная наркологическая помощь москва
1win aviator login https://1win12046.ru/
Лечение пивного алкоголизма в Подольске от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Получить дополнительную информацию – врача капельницу от запоя в москве
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Изучить вопрос глубже – вывод из запоя на дому цена
Помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Узнать больше – срочная наркологическая помощь москва
Если нужен профессиональный вывод из запоя, обращайтесь в стационар клиники «Детокс» в Сочи. Все процедуры проводятся анонимно и под наблюдением специалистов.
Получить дополнительные сведения – вывод из запоя с выездом
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Получить дополнительные сведения – вывод из запоя вызов на дом нижний новгород
partnership insights platform – Very actionable, real-world examples illustrate alliance strategies well.
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Подробнее можно узнать тут – врач вывод из запоя в сочи
Лечение хронического алкоголизма в Москве от клиники «Частный Медик 24». Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Углубиться в тему – круглосуточная наркологическая помощь москва
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Узнать больше – наркологический вывод из запоя в сочи
dyson выпрямитель оригинал dyson выпрямитель оригинал .
В Сочи клиника «Детокс» предлагает лечение запоя в стационаре с круглосуточным медицинским контролем. Здесь пациент получает безопасное и эффективное восстановление.
Изучить вопрос глубже – https://vyvod-iz-zapoya-sochi15.ru
Клиника «Детокс» в Сочи проводит вывод из запоя в стационаре. Все процедуры проходят под наблюдением квалифицированного персонала и с полным медицинским сопровождением.
Получить дополнительную информацию – http://vyvod-iz-zapoya-sochi23.ru
Круглосуточная наркологическая скорая помощь в Москве от клиники «Частный Медик 24». Наша команда работает 24/7, обеспечивая доступность медицинской помощи в любое время суток.
Ознакомиться с деталями – платная наркологическая помощь москве
Вызов нарколога на дом в Краснодаре — услуга клиники «Детокс». Специалисты оказывают квалифицированную помощь прямо у вас дома.
Узнать больше – вызов нарколога на дом в сочи
Лечение абстинентного синдрома на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут все необходимые процедуры для скорейшего облегчения состояния.
Выяснить больше – центр наркологической помощи москва
Анонимность и конфиденциальность гарантированы в клинике «Частный Медик 24». Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Углубиться в тему – narkologicheskaya-pomoshch-na-domu moskva
Вывод из запоя у пожилых людей в Москве от клиники «Частный Медик 24». Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Получить дополнительную информацию – skoraya-narkologicheskaya-pomoshch moskva
Если запой стал серьёзной проблемой, стационар клиники «Детокс» в Сочи поможет выйти из кризиса. Врачи проводят детоксикацию и наблюдают за состоянием пациента.
Углубиться в тему – срочный вывод из запоя в сочи
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Подробнее можно узнать тут – нарколог на дом вывод из запоя в сочи
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Выяснить больше – вывод из запоя вызов на дом в нижнем новгороде
Если вы ищете надежную клинику для вывода из запоя, обратитесь в «Детокс» в Краснодаре. Услуга вызова нарколога на дом доступна круглосуточно. Врачи приедут к вам в течение 1–2 часов и окажут необходимую помощь.
Подробнее можно узнать тут – вывод из запоя с выездом в сочи
Global Retail Watchtower – Timely and detailed content that makes monitoring trends simple.
Лечение хронического алкоголизма в Подольске от клиники «Частный Медик 24». Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Детальнее – врача капельницу от запоя москва
AllianceNavigator – Informative and actionable, helps create reliable professional connections.
дайсон выпрямитель как отличить оригинал vypryamitel-dn-kupit-4.ru .
Лечение пивного алкоголизма в Москве от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Получить больше информации – частная скорая наркологическая помощь
Вывод из запоя у подростков в Москве от клиники «Частный Медик 24». Мы предлагаем специализированное лечение для подростков, учитывая их возрастные особенности.
Детальнее – наркологическая помощь
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Разобраться лучше – вызов нарколога на дом сочи
Кодирование от алкоголизма на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут процедуру кодирования.
Углубиться в тему – скорая наркологическая помощь на дому
Лечение хронического алкоголизма в Москве от клиники «Частный Медик 24». Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Узнать больше – anonimnaya-narkologicheskaya-pomoshch moskva
Выездная наркологическая помощь в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Получить дополнительные сведения – вывод из запоя
Реабилитация после запоя в Москве от клиники «Частный Медик 24». Мы поможем вам восстановиться после запоя и предотвратить рецидивы.
Подробнее тут – круглосуточная наркологическая помощь москве
whoah this weblog is excellent i love reading your articles. Stay up the good work! You understand, lots of individuals are hunting round for this information, you can aid them greatly.
https://protein.kiev.ua/bi-led-linzy-2026-yak-vybraty-idealne-svitlo.html
В Краснодаре клиника «Детокс» высылает нарколога на дом для срочной помощи при запое. Быстро и безопасно.
Подробнее – наркология вывод из запоя в сочи
Если вы ищете надежную клинику для вывода из запоя в Сочи, обратитесь в «Детокс». Здесь опытные специалисты окажут необходимую помощь в стационаре. Услуга доступна круглосуточно, анонимно и начинается от 2000 ?.
Подробнее тут – vyvod-iz-zapoya-sochi12.ru
Вывод из запоя у пожилых людей в Москве от клиники «Частный Медик 24». Наши специалисты учитывают возрастные изменения организма при назначении лечения.
Получить дополнительную информацию – частная наркологическая помощь москве
В Краснодаре клиника «Детокс» предлагает выезд нарколога на дом. Помощь оказывается быстро, анонимно и круглосуточно.
Получить дополнительную информацию – нарколог на дом круглосуточно сочи
Лечение абстинентного синдрома на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут все необходимые процедуры для скорейшего облегчения состояния.
Подробнее – анонимная скорая наркологическая помощь москва
Выезд нарколога на дом в Нижнем Новгороде — капельница от запоя с выездом на дом. Мы обеспечиваем быстрое и качественное лечение без необходимости посещения клиники.
Детальнее – вывод из запоя с выездом
В Сочи клиника «Детокс» проводит вывод из запоя в стационаре с круглосуточным контролем врачей. Процедуры безопасны, эффективны и анонимны.
Углубиться в тему – вывод из запоя цена сочи
Выезд нарколога на дом в Нижнем Новгороде — круглосуточная помощь при запое. Мы гарантируем анонимность и конфиденциальность на всех этапах лечения.
Подробнее – вывод из запоя круглосуточно нижний новгород
собаки слот казино слот Gates of Olympus —
Слот Gates of Olympus — хитовый игровой автомат от Pragmatic Play с системой Pay Anywhere, каскадными выигрышами и усилителями выигрыша до ?500. Сюжет разворачивается на Олимпе, где Зевс повышает выплаты и делает каждый спин динамичным.
Экран игры представлено в виде 6?5, а выигрыш засчитывается при появлении не менее 8 совпадающих символов в любом месте экрана. После формирования выигрыша символы пропадают, на их место опускаются новые элементы, запуская каскады, которые могут дать серию выигрышей за один спин. Слот является волатильным, поэтому способен долго молчать, но в благоприятные моменты даёт крупные заносы до ?5000 от ставки.
Чтобы разобраться в слоте доступен бесплатный режим без финансового риска. Для игры на деньги стоит выбирать официальные казино, например MELBET (18+), принимая во внимание заявленный RTP ~96,5% и правила выбранного казино.
Профилактика рецидивов после запоя в Москве от клиники «Частный Медик 24». Мы поможем вам предотвратить повторные случаи запоя и поддержим вас на пути к трезвой жизни.
Изучить вопрос глубже – неотложная наркологическая помощь москва
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Желаете узнать подробности? – https://puasbetbuktiwd3.xyz/index.php/bukti-wd-puasbet-17-nov-2023-sweet-bonanza-rp-2000000000-lunas
Снижение веса в санатории часто включает в себя голодание пожилых людей, которое помогает в очистке организма и общем оздоровлении.
требует особого внимания из-за различных социальных и экономических факторов. Учитывая, что пожилые люди сталкиваются с финансовыми трудностями , они могут не иметь возможности позволить себе полноценное питание . Это вызывает множество опасностей для здоровья .
Последствия голодания для пожилых людей могут быть очень тяжелыми . Голодание делает пожилых людей более уязвимыми к инфекциям. Кроме того, голодание может привести к развитию различных хронических заболеваний . Необходимо оказывать помощь тем, кто в ней нуждается.
Причины голодания пожилых людей очень многочисленны и различны . Одной из основных причин является бедность. Кроме того, пожилые люди могут испытывать трудности с мобильностью и доступом к магазинам . Это делает их зависимыми от других .
Решение проблемы голодания пожилых людей требует совместных усилий . Необходимо обеспечить пожилым людям доступ к полноценному питанию . Кроме того, важно привлекать внимание властей к этой проблеме. Это может обеспечить им достойную старость.
Влияние голодания на здоровье пожилых людей очень негативно и разнообразно . Голодание делает пожилых людей более восприимчивыми к различным заболеваниям. Кроме того, оно может вызвать депрессию и тревогу . Необходимо оказывать медицинскую помощь тем, кто в ней нуждается .
Роль общества в решении проблемы голодания пожилых людей требует активного участия каждого члена общества. Общество должно оказывать поддержку и помощь тем, кто в ней нуждается . Кроме того, необходимо оказывать экономическую и социальную помощь. Это может существенно улучшить их здоровье и благосостояние .
Проблема голодания пожилых людей требует немедленного внимания и решения . Необходимо решать эту проблему на государственном и общественном уровне . Кроме того, важно привлекать внимание властей к этой проблеме. Это может обеспечить им достойную старость.
Будущие направления решения проблемы голодания пожилых людей требуют активного участия общества и государства. Необходимо создавать и развивать системы поддержки пожилых людей . Кроме того, важно проводить регулярные осмотры и проверки здоровья . Это может обеспечить им достойную старость.
Для тех, кто ценит функциональность и практичность, складной нож москва становится незаменимым компаньоном в повседневной жизни.
в период Средневековья, когда такие ножи были популярны среди воинов . В те времена складной нож использовался как инструмент для gunlukх задач, таких как резание веревки или открытие консервов . С течением времени дизайн и функциональность складного ножа развивались, чтобы соответствовать различным стилям и предпочтениям.
Складной нож также стал символом ручного труда и умения мастеров . В современное время складной нож продолжает эволюционировать, включая новые функции и материалы . Его популярность обусловлена его компактностью и легкостью использования .
Конструкция складного ножа основана на сложном механизме, который позволяет лезвию выдвигаться и складываться . Лезвие складного ножа изготовлено с использованием передовых технологий, которые повышают его эффективность. Ручка складного ножа разработана с учетом различных стилей и предпочтений.
Складной нож также оборудован механизмом блокировки, который предотвращает случайное закрытие лезвия . Его функциональность обеспечивает возможность использования в качестве инструмента для различных задач . Складной нож стал неотъемлемой частью многих профессий и хобби.
Существует большое разнообразие складных ножей, каждый из которых имеет свои уникальные характеристики и особенности . Один из популярных видов складных ножей – швейцарский армейский нож, который известен своей универсальностью и функциональностью . Другой вид – туристический нож, который оснащен дополнительными функциями для использования в дикой природе .
Каждый вид складного ножа имеет свою историю и традиции. Выбор складного ножа зависит от личных предпочтений и стиля использования . Складной нож может стать верным компаньоном в повседневной жизни или приключениях .
Использование складного ножа требует осторожности и внимания к безопасности . При использовании складного ножа необходимо учитывать такие факторы, как окружающая среда и тип задачи. Уход за складным ножом включает в себя регулярную очистку и смазку .
Складной нож должен быть регулярно осматриваем и обслуживаем, чтобы предотвратить повреждения . При правильном использовании и уходе складной нож останется важным инструментом и атрибутом. Складной нож продолжает эволюционировать и совершенствоваться .
playing online slots
Gates of Olympus — популярный игровой автомат от Pragmatic Play с системой Pay Anywhere, каскадами и коэффициентами до ?500. Сюжет разворачивается в мире Олимпа, где верховный бог активирует множители и превращает каждое вращение случайным.
Сетка слота представлено в виде 6?5, а выигрыш формируется при выпадении 8 и более совпадающих символов без привязки к линиям. После расчёта комбинации символы удаляются, их заменяют новые элементы, запуская серии каскадных выигрышей, дающие возможность получить дополнительные выигрыши за одно вращение. Слот относится высоковолатильным, поэтому не всегда даёт выплаты, но при удачных раскладах способен порадовать крупными выплатами до ?5000 от ставки.
Чтобы разобраться в слоте доступен демо-версия без финансового риска. Для игры на деньги рекомендуется рассматривать официальные казино, например MELBET (18+), принимая во внимание показатель RTP ~96,5% и условия конкретной платформы.
Помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Исследовать вопрос подробнее – наркологическая помощь на дому москве
Лечение абстинентного синдрома на дому в Москве от клиники «Частный Медик 24». Наши специалисты приедут к вам домой и проведут все необходимые процедуры для скорейшего облегчения состояния.
Исследовать вопрос подробнее – анонимная скорая наркологическая помощь
В Сочи клиника «Детокс» предлагает полный курс вывода из запоя в стационаре. Круглосуточный медицинский контроль гарантирует безопасность и эффективность лечения.
Получить дополнительные сведения – вывод из запоя в стационаре
выпрямитель для волос дайсон выпрямитель для волос дайсон .
Лечение пивного алкоголизма в Москве от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Выяснить больше – анонимная скорая наркологическая помощь москва
Реабилитация после запоя в Москве от клиники «Частный Медик 24». Мы поможем вам восстановиться после запоя и предотвратить рецидивы.
Подробнее тут – скорая наркологическая помощь на дому
Срочно нужен нарколог на дом? В Краснодаре клиника «Детокс» приезжает к пациенту в течение часа.
Исследовать вопрос подробнее – нарколог на дом вывод из запоя сочи
В Сочи клиника «Детокс» предоставляет услугу вывода из запоя в стационаре. Профессиональные врачи обеспечат комфортное и безопасное лечение. Минимальная стоимость услуги — 2000 ?.
Получить дополнительную информацию – вывод из запоя вызов сочи
Лечение пивного алкоголизма в Москве от клиники «Частный Медик 24». Мы предлагаем эффективные методы лечения зависимости от пива.
Исследовать вопрос подробнее – круглосуточная наркологическая помощь московская область
Для безопасного выхода из запоя в Сочи воспользуйтесь услугами стационара клиники «Детокс». Опытные врачи окажут помощь быстро и анонимно.
Детальнее – скорая вывод из запоя
Мы обеспечиваем быстрое и безопасное восстановление после длительного употребления алкоголя.
Разобраться лучше – вывод из запоя с выездом
Вызов нарколога на дом в Краснодаре — услуга клиники «Детокс». Специалисты оказывают квалифицированную помощь прямо у вас дома.
Исследовать вопрос подробнее – нарколог на дом срочно сочи
Помощь при алкогольной интоксикации в Москве от клиники «Частный Медик 24». Наши специалисты проведут необходимые процедуры для снятия симптомов интоксикации.
Изучить вопрос глубже – анонимная скорая наркологическая помощь москва
CityRetailClick – Practical and fast, helps compare products quickly.
traction unlocks motion – Gentle, approachable phrasing demonstrating how energy release improves momentum.
Лечение запоя без госпитализации в Москве от клиники «Частный Медик 24». Мы предлагаем лечение на дому, без необходимости госпитализации.
Изучить вопрос глубже – экстренная наркологическая помощь москва
Клиника «Детокс» в Краснодаре предлагает услугу вызова нарколога на дом. Врачи приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Услуга доступна круглосуточно и анонимно.
Получить дополнительную информацию – вызвать нарколога на дом сочи
Лечение хронического алкоголизма в Москве от клиники «Частный Медик 24». Наши специалисты помогут вам преодолеть зависимость и вернуться к нормальной жизни.
Разобраться лучше – наркологическая помощь телефон москве
Капельница от запоя в Нижнем Новгороде — эффективный способ снять симптомы похмелья и восстановить организм. Процедура проводится опытными врачами с использованием современных препаратов.
Изучить вопрос глубже – вывод из запоя цена в нижнем новгороде
Снятие ломки при алкоголизме в Москве от клиники «Частный Медик 24». Наши специалисты помогут вам справиться с симптомами абстиненции.
Углубиться в тему – наркологическая помощь московская область
Лечение зависимости от алкоголя у мужчин в Москве от клиники «Частный Медик 24». Мы предлагаем индивидуальный подход к лечению мужчин, учитывая все особенности организма.
Детальнее – скорая наркологическая помощь москва
quick access – Layout is simple, information is straightforward and easy to digest
В Краснодаре клиника «Детокс» предоставляет услугу вызова нарколога на дом. Специалисты приедут к вам в течение 1–2 часов, проведут осмотр и назначат необходимое лечение. Все процедуры проводятся анонимно и с соблюдением конфиденциальности.
Ознакомиться с деталями – нарколог на дом анонимно в сочи
Профилактика рецидивов после запоя в Москве от клиники «Частный Медик 24». Мы поможем вам предотвратить повторные случаи запоя и поддержим вас на пути к трезвой жизни.
Подробнее тут – http://skoraya-narkologicheskaya-pomoshch-moskva11.ru/http://skoraya-narkologicheskaya-pomoshch-moskva11.ru
SmartBuyOnline – Clear and practical, online shopping feels quick and effortless.
trustpath – Valuable resource, explains how to develop trustworthy market relationships effectively.
market alliance strategies – Clear advice, helps connect theory to practical market scenarios.
выпрямитель дайсон где купить оригинал выпрямитель дайсон где купить оригинал .
Анонимность и конфиденциальность гарантированы в клинике «Частный Медик 24». Мы обеспечиваем полную анонимность и конфиденциальность на всех этапах лечения.
Получить дополнительную информацию – вызвать капельницу от запоя в москве
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Лучшее решение — прямо здесь – https://www.defining-blog.ru/2025/10/11
Лечение запоя без госпитализации в Москве от клиники «Частный Медик 24». Мы предлагаем лечение на дому, без необходимости госпитализации.
Исследовать вопрос подробнее – вызов наркологической помощи москве
ClickForProfessionalInsights – Easy-to-digest lessons that make expert strategies accessible.
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Желаете узнать подробности? – https://anpeq.it/index.php/component/k2/item/4?start=13490
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Что скрывают от вас? – http://www.monticelloutility.com/paying-your-bill
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу.
Где можно узнать подробнее? – http://soka-shimizuya.com/2020/12/15/hello-world
ValueShopHub – Highlights savings, ideal for shoppers looking for the best deals online.
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Подробности по ссылке – https://www.sabinasoria.com/duis-cannabis-quis-sem-tempus-enim-suscipit
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Полезно знать – https://wps-cn.net/wps-office
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Все материалы собраны здесь – https://blog.snappyexchange.com/types-of-gift-cards-in-korea
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Читать далее > – https://silverchestcreations.com/product/teaspoon
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Изучить рекомендации специалистов – https://saheforlives.org/happy-new-year
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Прочесть заключение эксперта – https://www.powertvnews.in/2024/01/24/jayadeva-hospital-director-dr-c-n-manjunath-retires
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Не упусти шанс – http://tabletter-til-penisforstorrelse.com/post/34
ClickAndShopFast – Emphasizes speed and effortless navigation for digital retail.
Наркологическая помощь в современном формате — это комплексное лечение зависимостей и состояний интоксикации с индивидуальным подходом к каждому пациенту. В клинике «ВолгаМед Тольятти» круглосуточно работают врачи-наркологи, психиатры и реабилитологи, готовые оказать поддержку в любой момент. Применяются сертифицированные препараты, проверенные методики и психологическое сопровождение. При этом особое внимание уделяется анонимности и безопасности пациента: информация не передаётся третьим лицам, а лечение проводится строго конфиденциально.
Получить больше информации – наркологическая психиатрическая помощь
Клиника использует многоступенчатый подход, который позволяет адаптировать лечение под особенности организма пациента. Наблюдение продолжается даже после завершения детоксикации, чтобы убедиться, что состояние стабильно и не требуется дополнительное вмешательство. При необходимости врач назначает курс поддержки печени, витаминов и препаратов для восстановления сна и психоэмоционального равновесия.
Получить больше информации – вывод из запоя капельница на дому волгоград
Лечение в клинике включает несколько последовательных этапов, каждый из которых направлен на достижение стабильной ремиссии и восстановление здоровья пациента.
Детальнее – частная наркологическая клиника
Основные этапы включают:
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-v-krasnoyarske17.ru/vyvod-iz-zapoya-na-domu-krasnoyarsk/
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Получить дополнительную информацию – врач вывод из запоя в воронеже
Digital Shopping Innovations – Introduces clever ways to browse and shop products online.
Вывод из запоя требуется тогда, когда организм уже не способен самостоятельно справиться с последствиями алкогольной интоксикации. Длительное употребление спиртного приводит к нарушению работы внутренних органов, обезвоживанию и психическим расстройствам. Медицинская помощь помогает избежать опасных осложнений и облегчить процесс отказа от алкоголя.
Изучить вопрос глубже – вывод из запоя на дому круглосуточно в рязани
Клиника предлагает широкий спектр медицинских и психологических услуг, направленных на восстановление пациента после зависимости. Все процедуры проходят под контролем врачей и с соблюдением анонимности. Наиболее востребованные направления представлены ниже:
Получить больше информации – http://narkologicheskaya-clinica-v-voronezhe17.ru
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Получить больше информации – капельница от запоя стоимость
Такой подход позволяет добиться устойчивого эффекта и минимизировать риск возврата к зависимому поведению.
Углубиться в тему – https://narkologicheskaya-klinika-v-volgograde17.ru/narkologi-volgograda/
В Воронеже команда «ВоронМед Профи» работает по принципу быстрой медицинской реакции — помощь оказывается независимо от времени суток и дня недели. Все выезды выполняются анонимно, без спецтранспорта и медицинской формы. Врач приезжает в гражданской одежде, что исключает ненужное внимание соседей и посторонних. В ходе осмотра специалист измеряет давление, пульс, температуру, оценивает уровень интоксикации и определяет степень обезвоживания. На основе полученных данных подбирается состав капельницы, который подаётся медленно и безопасно под контролем врача.
Исследовать вопрос подробнее – http://
ValueShopHub – Highlights savings, ideal for shoppers looking for the best deals online.
Когда человек в запое, близким кажется, что всё ещё можно решить «по-тихому»: выспаться, отпаять водой, дать обезболивающее или «успокоительное» и дождаться, пока станет легче. На практике это часто приводит к обратному результату. Алкогольная интоксикация нарушает водно-электролитный баланс, сгущает кровь, повышает нагрузку на сердце, провоцирует скачки давления, ухудшает работу печени и нервной системы. Неконтролируемый приём снотворных, анальгетиков, транквилизаторов, особенно вместе с алкоголем, способен вызвать угнетение дыхания, аритмии, судороги или делирий. Домашняя обстановка не даёт возможности следить за всеми показателями и вовремя отреагировать. «РаменМед Трезвость» предлагает клинически выверенный вывод из запоя в Раменском с учётом возраста, длительности употребления, хронических заболеваний, перенесённых ранее осложнений. Здесь не применяют сомнительные схемы «усыпить, чтобы не мешал», а ставят задачу: безопасно пройти острую фазу, снять интоксикацию, стабилизировать давление и пульс, защитить сердце и мозг, снизить риск психозов и, при желании пациента, сразу наметить маршрут реального лечения зависимости. Такой подход снимает с родственников опасную «роль врача» и возвращает ситуацию туда, где ей место — под контроль профессионалов.
Узнать больше – вывод из запоя врачом
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-v-novokuzneczke17.ru/narkologiya-gorod-novokuzneczk
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Получить больше информации – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne/
Услуга
Узнать больше – https://narkolog-na-dom-shchelkovo10.ru/
Одним из ключевых направлений терапии является инфузионное лечение. Капельницы позволяют быстро восстановить обмен веществ, улучшить работу внутренних органов и ускорить выведение токсинов. В клинике используются только сертифицированные препараты, безопасные для сердечно-сосудистой и нервной системы.
Узнать больше – https://narkologicheskaya-clinika-v-ryazani17.ru/narkolog-ryazan-telefon
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Ознакомиться с деталями – [url=https://kodirovanie-ot-alkogolizma-v-volgograde17.ru/]кодирование от алкоголизма адрес в волгограде[/url]
Для иллюстрации приведена таблица, отражающая распространённые методы терапии и их воздействие на организм:
Узнать больше – наркологическая клиника вывод из запоя в воронеже
Ниже приведена таблица, отражающая примерную динамику состояния пациента после постановки капельницы:
Разобраться лучше – врач на дом капельница от запоя воронеж
CorporateAlliancePro – User-friendly, tips for corporate bonding are actionable and credible.
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Разобраться лучше – платная наркологическая скорая помощь в волгограде
Trusted Professional Network – Guidance that ensures long-term and successful corporate connections.
Ниже — ключевые направления, которые логично дополняют друг друга и формируют единый маршрут лечения:
Подробнее тут – narkologicheskaya-klinika-telefon
innovation hub site – Inspires creative thinking and exploration of better solutions.
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Получить дополнительную информацию – narkologicheskaya-klinika-v-kolomne
Услуга
Ознакомиться с деталями – нарколог на дом срочно
prolinkcenter – Offers insights for fostering meaningful business connections.
Маршрут выстроен без пауз и импровизаций. Сначала — короткое интервью по телефону: адрес в Электростали, длительность эпизода, лекарства/дозировки, аллергии, важные диагнозы, последние значения давления и пульса. Это экономит 15–20 минут на месте и позволяет заранее исключить опасные взаимодействия. По прибытии врач фиксирует АД, ЧСС, сатурацию, температуру, оценивает неврологический статус, степень обезвоживания, выраженность тремора/тошноты, уровень тревоги, кратко собирает анамнез последних суток. Затем стартует инфузионная терапия: растворы для регидратации и коррекции электролитов, поддержка витаминами группы B и магнием; по показаниям — гепатопротекторы и антиоксиданты, противорвотные, мягкие анксиолитики. Каждые 15–20 минут врач смотрит динамику и корректирует темп капельниц, питьевой режим, симптоматическую поддержку. Важный принцип — «сон без вырубания»: умеренная седация собирает ночной ритм, сохраняя информативность мониторинга. По завершении — письменные рекомендации и маршрут на 24–72 часа (сон, питание, запреты, «красные флаги», амбулаторные визиты/дневной стационар или перевод в отделение). Такой алгоритм заменяет «лотерею» результата управляемым и повторяемым планом.
Получить дополнительные сведения – vyvod-iz-zapoya
reliableonlinecommerce – Safe and reliable, buying products online feels simple and secure today.
Процесс терапии в наркологической клинике в Воронеже организован поэтапно. Это позволяет обеспечить системность и постепенность восстановления, снизить риски осложнений и повысить устойчивость результата.
Разобраться лучше – вывод наркологическая клиника воронеж
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Подробнее – кодирование от алкоголизма цена
signalturnsaction today – Everything is accessible quickly, content is clear and well-organized
tavro destination – Smooth and tidy interface with clear, well-structured information
Критичные случаи, когда вызов нарколога через «МедТрезвие Долгопрудный» оправдан и своевременен:
Узнать больше – https://narkolog-na-dom-dolgoprudnij10.ru/vyzvat-narkologa-na-dom-v-dolgoprudnom/
handy page – Quick access, clear structure, first impression is very welcoming
Ниже приведена таблица с типовыми компонентами капельницы и их действием:
Подробнее – анонимный вывод из запоя в тольятти
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Выяснить больше – центр наркологической помощи волгоград
В Красноярске клиника «КрасЗдрав Профи» предоставляет круглосуточную помощь людям, столкнувшимся с зависимостью. При этом формат анонимности сохраняется на каждом этапе — от звонка до выписки. Для пациентов, которым трудно приехать, возможен выезд нарколога на дом. Это удобно при похмельных и абстинентных состояниях, когда транспортировка нежелательна. Конфиденциальный выезд без маркировки транспорта и униформы позволяет начать лечение, не привлекая внимания окружающих. Все процедуры проводятся с соблюдением медицинских стандартов, включая регидратацию, стабилизацию и поддержку дыхания.
Получить дополнительную информацию – запой наркологическая клиника красноярск
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Подробнее можно узнать тут – https://narkologicheskaya-pomoshh-v-tolyatti17.ru/narkologiya-goroda-tolyatti
SmartSavingsCart – Highlights smart and value-focused shopping experiences.
Основные этапы включают:
Получить больше информации – http://www.domen.ru
После завершения инфузий врач-нарколог даёт рекомендации по питанию, водному балансу и образу жизни. При необходимости пациенту назначается курс поддерживающей терапии для закрепления эффекта.
Подробнее можно узнать тут – срочная наркологическая помощь
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Разобраться лучше – https://vyvod-iz-zapoya-v-novokuzneczke17.ru/vyvod-iz-zapoya-v-staczionare-novokuzneczk/
Домашний формат особенно важен, когда пациент не готов к стационару, боится огласки, испытывает стыд или сопротивление, но объективно нуждается в помощи. Попытки «перетерпеть» или лечить своими силами заканчиваются тем, что родственники дают опасные комбинации седативных, анальгетиков и «антипохмельных» средств, а состояние только ухудшается. «МедТрезвие Долгопрудный» строит выездную помощь так, чтобы она оставалась профессиональной медициной, а не косметической услугой. Уже при звонке диспетчер под контролем врача уточняет длительность запоя, виды алкоголя, наличие гипертонии, болезней сердца, печени, почек, диабета, неврологических нарушений, психических эпизодов, факт судорог, делирия в прошлом, какие лекарства уже были даны. Это позволяет заранее понять, подходит ли формат лечения на дому или сразу нужно рассматривать стационар. Выезд назначается только в тех случаях, когда это безопасно, и именно в этом ключевое отличие официальной клиники от анонимных «капельниц на дом» — здесь всегда выбирают жизнь и здоровье, а не удобный маркетинговый сценарий. Для семьи это не просто комфорт, а возможность получить помощь без риска сорваться в критическое состояние посреди ночи.
Получить больше информации – vyzov-vracha-narkologa-na-dom
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Изучить вопрос глубже – вывод из запоя недорого красноярск
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Углубиться в тему – http://vyvod-iz-zapoya-v-voronezhe17.ru
focusamplifiesgrowth site – Well-organized content, minimal clutter, and browsing is smooth
Для повышения эффективности в капельницы добавляются витамины группы B, аскорбиновая кислота, кардиопротекторы и антиоксиданты. Такая комбинация позволяет не только ускорить выведение продуктов распада алкоголя, но и предотвратить развитие постабстинентных расстройств. Благодаря точной дозировке и мягкому темпу введения растворов снижается риск побочных реакций, а восстановление проходит плавно и безопасно.
Исследовать вопрос подробнее – вывод из запоя цена воронеж
Клиника предлагает широкий спектр медицинских и психологических услуг, направленных на восстановление пациента после зависимости. Все процедуры проходят под контролем врачей и с соблюдением анонимности. Наиболее востребованные направления представлены ниже:
Узнать больше – наркологические клиники алкоголизм в воронеже
Своевременное обращение к специалистам позволяет быстро стабилизировать состояние и избежать осложнений.
Подробнее – врач вывод из запоя тольятти
Алгоритм в «Трезвый Центр Коломна» построен так, чтобы убрать импровизацию и сделать всё максимально прозрачным для семьи. Сначала по телефону собираются ключевые данные: возраст пациента, длительность запоя, виды алкоголя, хронические заболевания, препараты, аллергии, наличие судорог, потерь сознания, странного поведения, текущие жалобы. На этом этапе озвучивается ориентировочный формат помощи и примерный диапазон стоимости. Далее следует выезд на дом или поступление в стационар. Врач проводит осмотр: измеряет артериальное давление, пульс, сатурацию, температуру, оценивает тремор, координацию, сознание, степень обезвоживания, наличие болей, состояние дыхания и сердца. На основе этих данных назначается инфузионная терапия: растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы, по показаниям — гепатопротекторы, антиоксидантные комплексы, противорвотные для контроля тошноты, мягкие анксиолитики для уменьшения тревоги и нормализации сна. Уходят от агрессивной седации: пациент не должен быть «выключен» так, чтобы невозможно было заметить ухудшение. В процессе капельниц проводится повторный контроль показателей, темп и состав при необходимости корректируются. После стабилизации пациент и семья получают подробные рекомендации: режим, сон, питание, питьё, запреты, «красные флаги», план наблюдения и возможного дальнейшего лечения зависимости.
Получить больше информации – http://vyvod-iz-zapoya-kolomna10.ru
Для качественного ухода за вашим автомобилем посетите детейлинг полировка кузова.
Специалисты тщательно чистят и кондиционируют поверхности салона.
Острый эпизод запоя — это не «плохое самочувствие», а состояние с реальными рисками для сердца, нервной системы и дыхания, особенно в ночные часы, когда усиливаются вегетативные реакции и тревога. В «НоваТрезвие» мы выстраиваем помощь так, чтобы от звонка до заметного облегчения прошло как можно меньше времени и как можно меньше случайностей: короткое интервью для оценки рисков, выезд врача или приём в клинике, экспресс-диагностика по ключевым показателям, персональная инфузионная схема без «универсальных коктейлей», мягкая коррекция сна и тревоги без «вырубания», понятные инструкции семье на 24–72 часа и план продолжения на ближайшие недели. Мы не скрываемся за общими формулами: решения принимаются по фактическим данным, дозы и темп капельниц подстраиваются к динамике каждые 15–20 минут, а при «красных флагах» перевод в стационар организуется без пауз. Конфиденциальность соблюдается строго, а коммуникация простая и предсказуемая — чтобы вы всегда знали, что происходит сейчас и чего ждать к утру.
Подробнее тут – вывод из запоя электросталь
Лечение зависимости в наркологической клинике проводится поэтапно. Это обеспечивает постепенное восстановление организма и исключает риск осложнений. Каждый этап направлен на устранение конкретных нарушений, вызванных употреблением психоактивных веществ.
Узнать больше – наркологическая клиника лечение алкоголизма
В Воронеже команда «ВоронМед Профи» работает по принципу быстрой медицинской реакции — помощь оказывается независимо от времени суток и дня недели. Все выезды выполняются анонимно, без спецтранспорта и медицинской формы. Врач приезжает в гражданской одежде, что исключает ненужное внимание соседей и посторонних. В ходе осмотра специалист измеряет давление, пульс, температуру, оценивает уровень интоксикации и определяет степень обезвоживания. На основе полученных данных подбирается состав капельницы, который подаётся медленно и безопасно под контролем врача.
Получить больше информации – нарколог на дом круглосуточно цены воронеж
При появлении таких симптомов важно не откладывать вызов врача. Самолечение, особенно с использованием неизвестных препаратов, может привести к тяжёлым последствиям, включая судороги и инсульт. Врачи клиники «ВолгаМед Резолюция» приезжают на дом с необходимыми средствами для оказания экстренной помощи и стабилизации состояния уже на месте.
Разобраться лучше – http://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-voronezh/
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Разобраться лучше – http://kapelnicza-ot-zapoya-v-volgograde17.ru
Комплексная терапия включает несколько последовательных этапов, обеспечивающих полное восстановление организма и личности пациента. Каждый из них направлен на решение конкретных задач — от устранения интоксикации до закрепления устойчивой ремиссии.
Получить дополнительную информацию – https://narkologicheskaya-klinika-v-volgograde17.ru/narkologi-volgograda
Клиника «ВолгаМед Резолюция» в Волгограде оказывает помощь при алкогольной интоксикации как в условиях стационара, так и на дому. Врачи готовы выехать к пациенту в течение 40–60 минут после обращения, привозя с собой всё необходимое оборудование для проведения инфузионной терапии. Такая оперативность позволяет снизить риск осложнений и стабилизировать состояние уже в первые часы лечения. Для пациентов, нуждающихся в круглосуточном наблюдении, предусмотрены комфортабельные палаты с постоянным медицинским контролем.
Узнать больше – вывод из запоя клиника в волгограде
Наркологическая клиника «Трезвый Путь Коломна» — это пространство, где тяжёлые истории зависимости перестают быть хаотичным набором срывов, ночных обещаний и беспомощных попыток родных «вытащить своими силами». Здесь собраны врачи-наркологи, терапевты, психологи и медперсонал, которые знают, что такое длительные запои, многолетнее употребление, полинаркомания, зависимость от аптечных препаратов, и умеют работать с этим не через страх и давление, а через профессиональные, выверенные шаги. Клиника в Коломне предлагает безопасную детоксикацию, стационарное наблюдение, индивидуальные программы лечения алкоголизма и наркомании, поддержку семьи и постреабилитационные решения. Все процессы организованы так, чтобы пациент сохранял достоинство, а родственники наконец получили не обещания, а реальный план действий, понятный по этапам и по результатам.
Углубиться в тему – http://narkologicheskaya-klinika-kolomna2-10.ru
Вывод из запоя на дому возможен только при относительно контролируемом состоянии и после очной оценки нарколога. В таких случаях специалист выезжает в Раменском, проводит осмотр, назначает индивидуальную капельницу, остаётся до стабилизации состояния и оставляет подробные рекомендации. Важный момент — честность: если во время осмотра врач видит риски (нестабильное давление, признаки начинающегося делирия, серьёзные боли, глубокую дезориентацию), формат на дому не навязывается, а предлагается стационар. Именно это отличает клинику от анонимных «служб капельниц», для которых любая заявка — повод заработать, независимо от последствий.
Разобраться лучше – https://vyvod-iz-zapoya-ramenskoe10.ru/srochnoe-vyvedenie-iz-zapoya-v-ramenskom/
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Разобраться лучше – наркологическая клиника наркологический центр
Вывод из запоя на дому возможен только при относительно контролируемом состоянии и после очной оценки нарколога. В таких случаях специалист выезжает в Раменском, проводит осмотр, назначает индивидуальную капельницу, остаётся до стабилизации состояния и оставляет подробные рекомендации. Важный момент — честность: если во время осмотра врач видит риски (нестабильное давление, признаки начинающегося делирия, серьёзные боли, глубокую дезориентацию), формат на дому не навязывается, а предлагается стационар. Именно это отличает клинику от анонимных «служб капельниц», для которых любая заявка — повод заработать, независимо от последствий.
Изучить вопрос глубже – вывод из запоя в Раменском
Отдельный принцип клиники — строгая анонимность. Информация о лечении не передаётся по месту работы, обучения, в сторонние структуры без согласия пациента. Это особенно важно для людей, которые боятся огласки и из-за этого годами откладывают обращение. В «КоломнаМед Центр» можно пройти лечение так, чтобы сохранить репутацию и личное пространство, не превращая каждый шаг в обсуждение «на людях».
Получить больше информации – narkologicheskaya-klinika
Клиника «Трезвый Шаг Раменское» выстраивает помощь так, чтобы пациент и его близкие не метались между разными службами и частными «специалистами», а получали комплекс услуг в одном месте. Это особенно важно для тех, кто уже сталкивался с провалами после разовых кодировок, неподходящих капельниц или формальной «помощи».
Подробнее – anonimnaya-narkologicheskaya-klinika
visit mexto – Easy-to-follow site where details are straightforward
Клиника в Коломне ориентирована на полный цикл помощи: от экстренных состояний до длительного сопровождения. Здесь важна не только медицинская составляющая, но и человеческая: уважение, конфиденциальность, отсутствие стигмы. Ниже — ключевые направления, которые выстраиваются в единую систему лечения, а не существуют по отдельности.
Подробнее тут – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-cena-v-kolomne/
Для тех, кто предпочитает лечение в условиях стационара, предусмотрены комфортные палаты, медицинский контроль 24/7 и возможность консультаций с психотерапевтом. Врачи клиники применяют комплексные методы, направленные не только на снятие симптомов, но и на устранение причин зависимости.
Подробнее можно узнать тут – https://narkologicheskaya-pomoshh-v-tolyatti17.ru/narkologiya-goroda-tolyatti/
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Детальнее – наркология вывод из запоя в красноярске
Growth Decision Insights – Provides clarity and structure for approaching challenges confidently.
BrixelAccess – Responsive layout, interface clear, and moving through pages effortless.
Детоксикация в клинике «Центр Трезвости ВоронМед» проводится по принципу минимального вмешательства при максимальной эффективности. Основная задача — очистить кровь от токсинов и стабилизировать внутреннюю среду организма без нагрузки на сердце и почки. Все препараты вводятся медленно, под контролем медицинского персонала, а состав подбирается индивидуально после оценки анализов и состояния пациента.
Получить больше информации – http://vyvod-iz-zapoya-v-voronezhe17.ru/
item store – Found this shop today, fair pricing and smooth ordering experience.
Процесс включает следующие шаги:
Узнать больше – платная наркологическая клиника в красноярске
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Детальнее – круглосуточная наркологическая помощь в тольятти
Когда состояние «штормит», ночные часы усиливают тревогу и вегетативные реакции, обезвоживание нарастает, сон рвётся, а попытки самолечения «чем попало» маскируют опасные симптомы. Организованный маршрут в «Трезвой Линии» заменяет хаос последовательностью: ещё по телефону дежурный врач собирает ключевые сведения — длительность эпизода, аллергии, список лекарств и дозировок, кардио- и эндокринные диагнозы, последние измерения давления и пульса. На месте выполняется короткая, но информативная оценка: АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания, выраженность тремора и тошноты. Схема терапии запускается сразу и корректируется каждые 15–20 минут по «живым показателям», а не по шаблону. Если видим признаки предделирия, неукротимую рвоту, резкие «качели» давления/пульса, выраженную слабость или пожилой возраст с тяжёлой соматикой — переводим в стационар без пауз: приборный мониторинг и ночная команда в Электростали снижают «цену ошибки» и экономят на повторных вызовах. Для семьи это означает меньше догадок и больше ясности: понятно, что делаем сейчас и чего ждём к утру.
Подробнее можно узнать тут – вывод из запоя на дому цена
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Подробнее – наркологические клиники алкоголизм
progressmoveswithfocus portal – Enjoyable browsing with clear sections and motivating content
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Исследовать вопрос подробнее – вывод из запоя недорого
выпрямитель dyson ht01 выпрямитель dyson ht01 .
Каждый этап проходит под контролем врачей-наркологов и психотерапевтов, что гарантирует эффективность и безопасность лечения.
Получить дополнительные сведения – наркологическая клиника стационар новокузнецк
В клинике используются проверенные медицинские методы, основанные на современных научных данных. При алкогольной или наркотической интоксикации первым этапом является детоксикация — выведение токсинов из организма и нормализация обменных процессов. На следующем этапе проводится медикаментозная поддержка, направленная на стабилизацию состояния, снижение тяги к веществам и восстановление функций внутренних органов. После стабилизации пациент проходит курс психотерапии и участвует в программах реабилитации.
Ознакомиться с деталями – https://narkologicheskaya-clinica-v-voronezhe17.ru/
Во время процедуры врач фиксирует ключевые параметры, чтобы убедиться в безопасности и эффективности терапии. Мониторинг проводится при каждом выезде и помогает отслеживать динамику в режиме реального времени. В таблице ниже указаны основные показатели, за которыми следит специалист.
Получить больше информации – запой нарколог на дом воронеж
brivox access – No lag when opening pages, and the text remains clear
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Ознакомиться с деталями – вывод из запоя на дому воронеж
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Выяснить больше – narkologicheskaya-klinika
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Раскрыть тему полностью – http://www.volgyfitness.hu/?p=6639&cpage=29
Перед процедурой врач оценивает состояние пациента, измеряет давление, пульс и уровень насыщения крови кислородом. После осмотра подбирается состав инфузии, включающий препараты для дезинтоксикации, восстановления водно-солевого баланса и нормализации работы органов. Введение растворов осуществляется внутривенно, под контролем специалиста. Длительность процедуры — от 40 минут до 1,5 часов.
Выяснить больше – сколько стоит капельница на дому от запоя
Комплексная терапия включает несколько последовательных этапов, обеспечивающих полное восстановление организма и личности пациента. Каждый из них направлен на решение конкретных задач — от устранения интоксикации до закрепления устойчивой ремиссии.
Исследовать вопрос подробнее – анонимная наркологическая клиника
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Ознакомиться с полной информацией – https://fokusnews.online/ayahmiris-kandung-dan-kakeknya-korban-pelaku-pencabulan
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Нажмите, чтобы узнать больше – https://saudymoklubas.lt/services/heroes-discount
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Всё, что нужно знать – https://dh-electricalservices.co.uk/house-rewires/can-a-house-be-rewired-one-room-at-a-time
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый мог разобраться в предмете и извлечь из него максимум пользы.
Ознакомиться с теоретической базой – https://domainlinks.directory/listing/leon-kahn
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Всё самое вкусное внутри – https://blogterapia.com.br/terapia-ocupacional-para-criancas
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Интересует подробная информация – https://pmtechww.com/power-of-agile-scheduling-for-successful-project-management
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Лучшее решение — прямо здесь – https://aetgroup.co/%D9%81%D8%B1%D9%88%D8%B4-%D9%88%DB%8C%DA%98%D9%87-%D8%A7%DB%8C%D8%B1%D8%A7%D9%86-%DA%A9%D9%84%D8%A7%DA%86-%DA%A9%D9%84%D8%A7%DA%86-%D8%A8%D8%B1%D9%82%DB%8C-%D8%A7%D8%AA%D9%88%D9%85%DB%8C%D8%AF-%D9%88
В этой статье-обзоре мы соберем актуальную информацию и интересные факты, которые освещают важные темы. Читатели смогут ознакомиться с различными мнениями и подходами, что позволит им расширить кругозор и глубже понять обсуждаемые вопросы.
А что дальше? – https://hostingwebid.com/ada-beberapa-cara-dalam-mengakses-website
zylavo market – Smooth navigation, product info detailed and visuals accurate.
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Разобраться лучше – https://yb-nuisibles.com/comment-savoir-si-vous-avez-un-nid-de-guepes-guide-complet-par-yb-nuisibles
Strategic Options Hub – The guides opened my eyes to new growth paths I hadn’t thought about before.
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Уточнить детали – http://mcadachi.com/%E7%AC%AC%E4%B8%89%E5%9B%9Eit%E7%A0%94%E7%A9%B6%E4%BC%9A%E5%A0%B1%E5%91%8A-%E5%85%AB%E6%9C%A8-%E5%8B%9D
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Изучить материалы по теме – https://taniamiller.com/ea-dolorum-in-architecto-quia
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Что скрывают от вас? – https://tntsimregistrations.com/0918-what-network-philippines
выпрямитель dyson airstrait pink выпрямитель dyson airstrait pink .
seo клиники наркологии seo-kejsy7.ru .
лбс это shkola-onlajn13.ru .
Наши врачи используют только проверенные и сертифицированные медикаменты, индивидуально подбираемые для каждого пациента. В состав лечебного курса входят:
Подробнее – вывод из запоя цена в новосибирске
xavix network – Sleek layout, intuitive browsing, and overall pleasant experience
«ТверьМед» — частная лицензированная клиника, специализирующаяся на наркологической помощи любой степени сложности. Здесь работают неравнодушные врачи-наркологи, психиатры, терапевты и психологи с многолетним стажем. Медицинская команда настроена на оперативную диагностику и проведение первичных мероприятий в течение первого часа после обращения. Упор сделан на доступность: клиника открыта 24/7, приём возможен как на территории медучреждения, так и на выезде — дома, в офисе, гостинице, санатории или любом удобном месте.
Выяснить больше – частная наркологическая помощь тверь
Нужна срочная помощь при алкогольном отравлении или запое? Вызовите нарколога на дом в Иркутске! Квалифицированная помощь нарколога на дому: диагностика, капельница, стабилизация состояния. Круглосуточный выезд нарколога, анонимность и снижение рисков – с «ТрезвоМед». Самостоятельный отказ невозможен? Необходима наркологическая помощь. Васильев: «Не затягивайте с помощью при алкогольном отравлении!».
Углубиться в тему – https://narcolog-na-dom-v-irkutske0.ru/
PlavexEase – Responsive design, clear interface, and navigation effortless.
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Узнать больше – анонимный вывод из запоя
Наркологическая помощь должна быть не только медицински точной, но и человечной, безопасной и анонимной. В «Ижевском Центре Трезвых Решений» выстроена система комплексного подхода к лечению зависимостей, включающая диагностику, медикаментозную детоксикацию, психотерапию и социальную адаптацию. Клиника объединяет профессионализм, заботу и круглосуточную готовность помочь пациентам, оказавшимся в трудной ситуации. Здесь работают врачи с большим опытом в области наркологии и психиатрии, способные оперативно выехать на дом и оказать неотложную помощь.
Ознакомиться с деталями – частная наркологическая клиника ижевск
Xelarionix Direct Shop – Simple interface, product info well organized and checkout completed without errors.
xelarion online – Browsed quickly, store looks genuine and navigation feels smooth.
nolra central – Browsing seamless, interface organized and filters useful for shopping.
Market Wisdom Center – Practical insights that make industry trends clearer and easier to follow.
Каждый метод подбирается индивидуально, что обеспечивает безопасность и эффективность процесса.
Подробнее тут – вывод из запоя на дому цена
Многие сталкиваются с трудностями при выборе клиники или центра: предлагаемые услуги различаются по качеству, подходам, стоимости и длительности. Некоторые организации ограничиваются только медикаментозной поддержкой, не работая с глубинными причинами зависимости. Поэтому важно заранее понимать, какие параметры отличают действительно надёжное учреждение, способное обеспечить долгосрочные результаты.
Подробнее – http://lechenie-narkomanii-murmansk0.ru
Zaviro Edge – Site feels professional, pages responsive, and product info easy to follow.
Ниже — ориентир для острых часов на дому. Это не жёсткий шаблон, а карта, где ясно: что делаем, чем измеряем, когда пересматриваем. При отсутствии отклика мы меняем один параметр (например, темп инфузии) и назначаем новое окно оценки, не «двигая» всё остальное.
Получить дополнительные сведения – нарколог на дом цены в саратове
browse plixva – Straightforward interface, minimal clutter, explanations are clear
actionpowersmovement site – Modern design, clear headings, and everything loads quickly
С момента начала лечения пациент получает доступ к круглосуточной линии поддержки. Врачи, психологи и координаторы готовы ответить на вопросы, помочь с корректировкой схемы лечения, поддержать в ситуации риска срыва. Эта функция особенно востребована в первые недели после выписки, когда человек сталкивается с триггерами в привычной среде и нуждается в дополнительной защите. Связь может осуществляться по телефону, через защищённый мессенджер или с помощью мобильного приложения клиники.
Подробнее можно узнать тут – лечение алкоголизма и наркомании центр в самаре
В клинике «Альтернатива» применяются современные методы терапии, включающие медикаментозное лечение, психотерапию и социальную реабилитацию.
Подробнее тут – оказание наркологической помощи
Вывод из запоя в Перми включает использование комплекса медикаментозных и психотерапевтических методик. Они помогают не только снять симптомы интоксикации, но и стабилизировать эмоциональное состояние.
Ознакомиться с деталями – вывод из запоя в стационаре пермь
Прежде чем принимать решение, важно изучить сайт клиники. В надёжных учреждениях размещена полная информация о врачах, их образовании и опыте работы. Кроме того, пациентам предлагается пройти предварительную консультацию — чаще всего она проводится анонимно и включает первичную диагностику. Это позволяет оценить профессионализм команды ещё до начала терапии.
Детальнее – https://narkologicheskaya-klinika-yaroslavl0.ru/narkologicheskaya-klinika-telefon-yaroslavl/
дайсон официальный сайт выпрямители дайсон официальный сайт выпрямители .
Первый шаг в лечении — это тщательный осмотр специалиста. Наряду с измерением жизненно важных показателей (пульс, артериальное давление, температура) врач проводит сбор анамнеза, выясняя длительность запоя, тип употребляемого алкоголя и наличие сопутствующих заболеваний. Эти данные помогают оценить степень интоксикации и подобрать индивидуальный план терапии, что является ключевым для дальнейшей эффективной детоксикации.
Получить дополнительную информацию – вывод из запоя на дому цена в ярославле
гибридная структура сайта гибридная структура сайта .
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Изучить вопрос глубже – наркологическая клиника цены
В клинике «СамарМед» доступно несколько форм лечения: стационарная программа, дневной стационар, амбулаторное наблюдение и гибридные схемы. Пациенты могут выбрать комфортный вариант в зависимости от степени зависимости, текущего состояния и занятости. Внутри стационара предусмотрены как стандартные палаты, так и индивидуальные блоки повышенной комфортности с возможностью проживания совместно с сопровождающим лицом.
Узнать больше – narkologicheskaya-klinika-samara0.ru/
Rixaro Click – Clean design, content clear and buying process felt seamless.
zorivo store – Pages responded well, links intuitive, and layout was clean.
онлайн школа с 1 по 11 класс shkola-onlajn13.ru .
Процесс лечения строится поэтапно, что позволяет контролировать динамику состояния пациента и постепенно возвращать его к полноценной жизни.
Углубиться в тему – лечение алкоголизма анонимно
olvra platform – Quick and organized site with information that seems credible
Важной частью работы является индивидуальный подход к каждому пациенту. На основании диагностики формируется персональная программа терапии, учитывающая физическое и психологическое состояние, а также социальные обстоятельства. Такой формат лечения повышает его результативность и помогает снизить риск рецидива.
Получить дополнительную информацию – наркологическая клиника омск
Выбор помощи на дому имеет ряд значительных преимуществ:
Подробнее можно узнать тут – http://www.domen.ru
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Изучить вопрос глубже – https://narcologicheskaya-klinika-omsk0.ru/narkologicheskaya-bolnicza-omsk/
Лечение наркомании в клинике начинается с диагностики, позволяющей определить степень зависимости, выявить сопутствующие заболевания и выбрать оптимальную тактику терапии. Важным этапом является детоксикация — очищение организма от токсинов и продуктов распада наркотических веществ, что снижает риск осложнений и облегчает последующее восстановление.
Детальнее – лечение наркомании анонимно в твери
Выбор клиники — задача не только медицинская, но и стратегическая. Учитывать нужно не только наличие лицензии, но и содержание программ, их гибкость, участие родственников в процессе, а также прозрачность взаимодействия с пациентом. Именно эти аспекты позволяют отличить профессиональное учреждение от формального.
Получить дополнительные сведения – chastnaya narkologicheskaya klinika jaroslavl’
Если на предзвонке выявляются «красные флаги» — давящая боль в груди, одышка в покое, спутанность сознания, судороги, неукротимая рвота, резкое падение насыщения кислородом — мы организуем бесшовный перевод в стационар. Место резервируем заранее, логистику строим так, чтобы не привлекать внимания соседей и не затягивать старт лечения. При отсутствии угроз терапия может начаться дома с последующим телесопровождением и при необходимости — краткой госпитализацией.
Подробнее можно узнать тут – наркологическая клиника клиника помощь
Нужна срочная помощь при алкогольном отравлении или запое? Вызовите нарколога на дом в Иркутске! Квалифицированная помощь нарколога на дому: диагностика, капельница, стабилизация состояния. Круглосуточный выезд нарколога, анонимность и снижение рисков – с «ТрезвоМед». Самостоятельный отказ невозможен? Необходима наркологическая помощь. Васильев: «Не затягивайте с помощью при алкогольном отравлении!».
Получить дополнительные сведения – нарколог на дом стоимость в иркутске
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Получить дополнительные сведения – вывод наркологическая клиника в омске
Первый шаг в лечении — это тщательный осмотр специалиста. Наряду с измерением жизненно важных показателей (пульс, артериальное давление, температура) врач проводит сбор анамнеза, выясняя длительность запоя, тип употребляемого алкоголя и наличие сопутствующих заболеваний. Эти данные помогают оценить степень интоксикации и подобрать индивидуальный план терапии, что является ключевым для дальнейшей эффективной детоксикации.
Изучить вопрос глубже – вывод из запоя на дому цена ярославль
Многие сталкиваются с трудностями при выборе клиники или центра: предлагаемые услуги различаются по качеству, подходам, стоимости и длительности. Некоторые организации ограничиваются только медикаментозной поддержкой, не работая с глубинными причинами зависимости. Поэтому важно заранее понимать, какие параметры отличают действительно надёжное учреждение, способное обеспечить долгосрочные результаты.
Узнать больше – https://lechenie-narkomanii-murmansk0.ru/czentr-lecheniya-narkomanii-marmansk/
Каждый метод подбирается индивидуально, что обеспечивает безопасность и эффективность процесса.
Изучить вопрос глубже – https://vyvod-iz-zapoya-omsk0.ru/vyvod-iz-zapoya-gorod-omsk
dyson выпрямитель для волос купить в симферополе vypryamitel-dsn-kupit-4.ru .
реклама наркологической клиники реклама наркологической клиники .
онлайн ш shkola-onlajn13.ru .
Во многих случаях пациент или его родственники не решаются сразу вызвать врача. Для таких ситуаций предусмотрена услуга онлайн-консультации. Она проводится через защищённую видеосвязь, при желании — анонимно. На связи — врач-нарколог или психиатр, который отвечает на вопросы, оценивает ситуацию по визуальным и вербальным признакам, рекомендует план действий. Консультация может стать отправной точкой для дальнейшего вызова врача на дом или записи в клинику. Это особенно удобно для родственников, которые не знают, как подступиться к проблеме и убедить человека в необходимости помощи.
Разобраться лучше – оказание наркологической помощи тверь
В случаях, когда пациент не готов приехать в клинику или находится в тяжёлом состоянии, специалисты «ЗдороваяСамара» организуют выездную помощь. Это особенно важно при острых интоксикациях, синдроме отмены, резком ухудшении психоэмоционального состояния. Выезд возможен круглосуточно и занимает от 30 до 60 минут с момента обращения. Врач приезжает в гражданской одежде, без опознавательных знаков и привлечения внимания. Оснащение позволяет провести на месте полную диагностику и начать лечение — в том числе инфузионную терапию, коррекцию состояния и психологическую стабилизацию.
Подробнее тут – lechenie-narkomanii-samara0.ru/
Во многих случаях пациент или его родственники не решаются сразу вызвать врача. Для таких ситуаций предусмотрена услуга онлайн-консультации. Она проводится через защищённую видеосвязь, при желании — анонимно. На связи — врач-нарколог или психиатр, который отвечает на вопросы, оценивает ситуацию по визуальным и вербальным признакам, рекомендует план действий. Консультация может стать отправной точкой для дальнейшего вызова врача на дом или записи в клинику. Это особенно удобно для родственников, которые не знают, как подступиться к проблеме и убедить человека в необходимости помощи.
Получить больше информации – http://narkologicheskaya-pomoshh-tver0.ru/narkolog-v-tveri-czeny/
Важной частью реабилитации является социализация пациента, возвращение его к активной общественной жизни и формирование новых, здоровых привычек. Для этого в клинике организуются различные мероприятия и программы адаптации.
Детальнее – https://lechenie-narkomanii-tver0.ru/
Наркомания — это не просто пагубная привычка, а тяжёлое хроническое заболевание, которое требует комплексного лечения и индивидуального подхода. В клинике «ЗдороваяСамара» разработаны современные программы помощи зависимым, охватывающие все этапы — от выезда нарколога на дом до многомесячного амбулаторного сопровождения. Особое внимание уделяется конфиденциальности, оперативности и доступности помощи в любое время суток. Это делает лечение максимально комфортным, результативным и гуманным как для самого пациента, так и для его близких.
Подробнее тут – http://www.domen.ru
Наша выездная бригада приезжает без маркировки, в гражданской одежде, согласовывает «тихое окно» связи с пациентом или близкими и начинает не с капельницы, а с настройки среды: тёплая приглушённая подсветка, проветривание без сквозняков, отключение уведомлений, подготовка воды комнатной температуры. Затем — быстрый осмотр, экспресс-метрики и старт индивидуального плана. Каждая корректировка — ровно одна за раз, чтобы сохранить причинно-следственную связь и не провоцировать полипрагмазию.
Исследовать вопрос подробнее – https://narkolog-na-dom-saratov0.ru/narkolog-i-psikhiatr-v-saratove/
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Разобраться лучше – вывод из запоя с выездом
Вывод из запоя в Перми включает использование комплекса медикаментозных и психотерапевтических методик. Они помогают не только снять симптомы интоксикации, но и стабилизировать эмоциональное состояние.
Изучить вопрос глубже – вывод из запоя вызов город
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Подробнее тут – вывод из запоя на дому саратов
Запойное состояние сопровождается тяжелыми последствиями для организма. Оно может включать нарушения сна, тремор конечностей, скачки давления, головные боли и депрессию. Без своевременной помощи такие проявления способны привести к развитию хронических заболеваний и угрожающих жизни осложнений.
Получить дополнительную информацию – https://vyvod-iz-zapoya-perm0.ru/vykhod-iz-zapoya-perm/
В «СамарМед» пациент рассматривается не как носитель диагноза, а как личность с уникальной историей, эмоциональным фоном, социальным окружением и индивидуальными триггерами зависимости. Именно поэтому с первого обращения к лечению подключаются сразу несколько специалистов. Стартовый консилиум позволяет сформировать целостную картину состояния, определить точки риска и создать персонализированную стратегию терапии, включающую медицинскую, психотерапевтическую и социальную составляющие.
Узнать больше – http://www.domen.ru
Процесс лечения строится поэтапно, что позволяет контролировать динамику состояния пациента и постепенно возвращать его к полноценной жизни.
Исследовать вопрос подробнее – лечение алкоголизма цена пермь
Такая схема лечения делает процесс последовательным и контролируемым. Врачи клиники сопровождают пациентов на всех стадиях, помогая преодолеть как физическую, так и психологическую зависимость. Особое внимание уделяется возвращению человека к активной и стабильной жизни без употребления алкоголя или наркотиков.
Выяснить больше – https://narkologicheskaya-klinika-v-izhevsk18.ru/narkologicheskaya-klinika-izhevsk-otzyvy
Экстренный вызов нарколога на дом в Иркутске от «ТрезвоМед» при запое, интоксикации или кодировании – анонимно и удобно. Осмотр, детоксикация капельницей, индивидуальный план лечения – все это на дому! «ТрезвоМед» – круглосуточная помощь, анонимность и безопасность при отказе от алкоголя. Не можете бросить пить самостоятельно? Нужна помощь нарколога! Васильев: «Своевременная помощь при интоксикации – залог успешного выздоровления».
Исследовать вопрос подробнее – нарколог на дом цены иркутск
Такая структура делает лечение последовательным и предсказуемым, повышая шансы на положительный исход.
Детальнее – наркологическая клиника лечение алкоголизма омск
Метод лечения
Разобраться лучше – вызвать наркологическую помощь новокузнецк
Maverounity landing page – The structure and visuals make the project feel trustworthy.
«Ижевский Центр Трезвых Решений» — это частное медицинское учреждение, где проводится лечение всех форм алкогольной и наркотической зависимости. Программы терапии разработаны на основе международных рекомендаций и включают не только медикаментозное воздействие, но и психологическую поддержку. Все процедуры проходят анонимно, без постановки на учёт, что особенно важно для пациентов, желающих сохранить конфиденциальность.
Получить больше информации – вывод наркологическая клиника
qavon site – Modern layout with readable information and intuitive navigation
Вывод из запоя в Омске проводится в условиях клиники с применением современных методов детоксикации и круглосуточного медицинского наблюдения. Длительное употребление алкоголя вызывает серьезную интоксикацию организма, нарушает работу внутренних органов и психоэмоциональное состояние. Своевременное обращение к специалистам позволяет избежать осложнений и восстановить здоровье пациента безопасным образом.
Углубиться в тему – вывод из запоя капельница
кп по продвижению сайта кп по продвижению сайта .
Как отмечает ведущий научный сотрудник ФГБУН «НМИЦ психиатрии и наркологии» Минздрава России, наличие междисциплинарной команды — один из основных факторов, определяющих успех терапии при зависимости.
Детальнее – https://lechenie-narkomanii-murmansk0.ru/lechenie-narkomanii-i-alkogolizma-marmansk
Современная наркологическая клиника — это не просто учреждение для экстренной помощи, а центр комплексной поддержки человека, столкнувшегося с зависимостью. В «КузбассМед» в Новокузнецке реализуется модель интенсивного вмешательства, где используются новейшие медицинские технологии, мультидисциплинарный подход и мобильные выездные службы. Специалисты готовы прибыть на дом за 30 минут с полным набором оборудования и медикаментов, обеспечив пациенту помощь в привычной и безопасной среде. Наркология здесь строится на индивидуализации: каждый случай рассматривается отдельно, с учётом психофизического состояния, анамнеза и жизненного контекста пациента.
Углубиться в тему – http://narkologicheskaya-klinika-novokuzneczk0.ru/narkolog-novokuzneczk-na-dom/
focusbuildsenergy spot – Minimal layout, logical flow, and the overall experience is smooth
Zavix Online – Layout simple, information organized well, and completing purchases was easy.
Даже телефонный разговор с клиникой может многое сказать о её подходе. Если вам предлагают типовое лечение без уточнения подробностей или избегают вопросов о составе команды, это тревожный сигнал. Серьёзные учреждения в Мурманске обязательно предложат предварительную консультацию, зададут уточняющие вопросы и расскажут, как строится программа помощи.
Получить дополнительную информацию – клиника лечения алкоголизма
online slots machines Gates of Olympus —
Gates of Olympus slot — востребованный слот от Pragmatic Play с принципом Pay Anywhere, цепочками каскадов и усилителями выигрыша до ?500. Игра проходит в мире Олимпа, где Зевс повышает выплаты и делает каждый раунд случайным.
Игровое поле представлено в виде 6?5, а выплата начисляется при выпадении не менее 8 совпадающих символов в любом месте экрана. После выплаты символы пропадают, их заменяют новые элементы, формируя цепочки каскадов, которые могут дать серию выигрышей за одно вращение. Слот считается игрой с высокой волатильностью, поэтому не всегда даёт выплаты, но в благоприятные моменты даёт крупные заносы до 5000 ставок.
Для тестирования игры доступен демо-режим без финансового риска. Для игры на деньги рекомендуется использовать проверенные казино, например MELBET (18+), ориентируясь на RTP около 96,5% и условия конкретной платформы.
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Изучить вопрос глубже – https://www.powertvnews.in/2025/06/05/people-have-lost-their-lives-there-was-a-need-for-a-celebration-yak-inside-bk-hariprasad-demanded-1-crore-compensation
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Проверенные методы — узнай сейчас – https://www.cnfmag.com/music/at-least-im-not-as-sad
Нужна срочная помощь при алкогольном отравлении или запое? Вызовите нарколога на дом в Иркутске! Квалифицированная помощь нарколога на дому: диагностика, капельница, стабилизация состояния. Круглосуточный выезд нарколога, анонимность и снижение рисков – с «ТрезвоМед». Самостоятельный отказ невозможен? Необходима наркологическая помощь. Васильев: «Не затягивайте с помощью при алкогольном отравлении!».
Узнать больше – вызов нарколога на дом в иркутске
Каждый метод подбирается индивидуально, что обеспечивает безопасность и эффективность процесса.
Выяснить больше – вывод из запоя омск
Как отмечает ведущий научный сотрудник ФГБУН «НМИЦ психиатрии и наркологии» Минздрава России, наличие междисциплинарной команды — один из основных факторов, определяющих успех терапии при зависимости.
Получить больше информации – лечение наркомании и алкоголизма мурманская область
Наркомания — это не просто пагубная привычка, а тяжёлое хроническое заболевание, которое требует комплексного лечения и индивидуального подхода. В клинике «ЗдороваяСамара» разработаны современные программы помощи зависимым, охватывающие все этапы — от выезда нарколога на дом до многомесячного амбулаторного сопровождения. Особое внимание уделяется конфиденциальности, оперативности и доступности помощи в любое время суток. Это делает лечение максимально комфортным, результативным и гуманным как для самого пациента, так и для его близких.
Разобраться лучше – лечение наркомании цена
При поступлении вызова нарколог незамедлительно приезжает на дом для проведения детального первичного осмотра. Врач собирает краткий анамнез, измеряет жизненно важные показатели — пульс, артериальное давление, температуру — и оценивает степень алкогольной интоксикации. Эти данные являются основой для разработки индивидуального плана лечения, позволяющего подобрать наиболее эффективные методы детоксикации.
Выяснить больше – нарколог вывод из запоя в туле
Этот информативный материал предлагает содержательную информацию по множеству задач и вопросов. Мы призываем вас исследовать различные идеи и факты, обобщая их для более глубокого понимания. Наша цель — сделать обучение доступным и увлекательным.
Эксклюзивная информация – https://testsieger-umzugsunternehmen.de/umzug-frankfurt-umzugsunternehmen-sorgenfreie-umzuege
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Подробная информация доступна по запросу – https://www.powertvnews.in/2024/12/21/arrest-warrant-issued-against-former-cricketer-robin-uthappa
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу.
Обратитесь за информацией – https://kabutaro777.com/cgi/kabu_yougo/joyful.cgi?read=7283&bbs=1&pg=60
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Ознакомиться с деталями – https://www.realty-key.ru/2012/11
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Есть чему поучиться – https://inaina.dk/2018/01/taeppe-diy
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Более того — здесь – https://www.realty-key.ru/meta/sberezheniya
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Кликни и узнай всё! – https://italiangospelchoir.it/hello-world
Эта статья погружает вас в увлекательный мир знаний, где каждый факт становится открытием. Мы расскажем о ключевых исторических поворотных моментах и научных прорывах, которые изменили ход цивилизации. Поймите, как прошлое формирует настоящее и как его уроки могут помочь нам строить будущее.
Познакомиться с результатами исследований – https://oventadka.com/recipe/dijon-quinoa-and-avocado-salad-with-lemon-kale-vinaigrette
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Кликни и узнай всё! – https://www.realty-key.ru/themes/magazinyi
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Исследовать вопрос подробнее – https://nayuta-p.com/2023/09/25/solar-panels-101-a-beginners-guide-to-solar-energy
Выбор помощи на дому имеет ряд значительных преимуществ:
Изучить вопрос глубже – vyvod-iz-zapoya-na-domu tula
Действие и назначение
Разобраться лучше – вывод из запоя новосибирская область
«Эгида Трезвости» выстраивает лечение вокруг предсказуемости: понятный старт, прозрачные шаги, нейтральная коммуникация и постоянная связь с дежурным врачом. Мы не заставляем объясняться «по кругу» и не перегружаем терминами — достаточно фактов, которые влияют на безопасность и выбор схемы. Уже при первом контакте становится ясно, где лучше начинать (дом, приём, стационар 24/7), что будет сделано в ближайшие часы и как оценим результат к вечеру. Конфиденциальность встроена в регламент: на звонках — нейтральные формулировки, на выездах — неброская экипировка, доступ к медицинской информации — только у задействованной команды. Это снижает фоновую тревогу и позволяет семье сосредоточиться на простых действиях, которые реально помогают держать курс.
Разобраться лучше – https://narkologicheskaya-klinika-ehlektrostal0.ru/platnaya-narkologicheskaya-klinika-v-ehlektrostali
online site – Clear explanations about security made me feel safe exploring the store.
Сначала — короткое интервью по телефону: адрес в Одинцово, длительность запоя, препараты, хронические заболевания, аллергии. Это экономит 15–20 минут на месте и помогает заранее спланировать безопасные дозы. По прибытии — осмотр, запуск инфузий и параллельная симптоматическая терапия: противорвотные при тошноте, анксиолитики при тревоге, аккуратная седация к ночи, если есть бессонница. Мы не «усыпляем» пациента — поддерживаем контакт для информативного мониторинга. На протяжении процедуры фиксируем динамику, регулируем скорость капельниц, выстраиваем щадящую гидратацию и лёгкое питание. Если картина меняется, быстро перестраиваем план. На выходе — письменные рекомендации и маршрут продолжения (амбулаторные визиты, дневной стационар или полноценное отделение). Такой алгоритм убирает случайность результата: эффект держится не на удаче, а на чётких действиях команды и дисциплине первых суток.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-odincovo10.ru/vyvod-iz-zapoya-v-stacionare-v-odincovo
Запой становится критическим, когда организм не справляется с постоянным поступлением алкоголя и начинает накапливать токсины. Если состояние пациента ухудшается, появляются такие симптомы, как сильная рвота, головокружение, спутанность сознания, судороги, резкие колебания артериального давления, а также проявления тяжелого абстинентного синдрома (дрожь, панические атаки, бессонница, тревожность), вызов нарколога становится необходимым. Также экстренная помощь требуется при наличии психических нарушений — галлюцинациях, агрессивном поведении или алкогольном психозе. Своевременное вмешательство позволяет стабилизировать состояние, предотвратить развитие осложнений и снизить риск для жизни.
Подробнее тут – vyvod-iz-zapoya novosibirsk
Что включено на практике
Углубиться в тему – narkologicheskaya-klinika-stacionar
Naviro Trustee official page – Content is arranged logically, helping users find what they need.
QulixExpress – Fast pages, intuitive shopping steps, and overall interface minimal but functional.
Если требуется срочное кодирование или детоксикация, вызов нарколога на дом – лучшее решение в Иркутске. Профессиональный нарколог приедет, оценит состояние, проведет детоксикацию на дому. «ТрезвоМед»: анонимный выезд нарколога 24/7, помощь при отказе от алкоголя. Тяжело бросить пить в одиночку? Обратитесь к наркологу! Главное – быстро оказать помощь при интоксикации, – нарколог Васильев.
Получить дополнительные сведения – https://narcolog-na-dom-v-irkutske0.ru/vrach-narkolog-na-dom-irkutsk/
Использование автоматизированных систем дозирования позволяет точно подобрать необходимое количество медикаментов, минимизируя риск передозировки и побочных эффектов. Постоянный мониторинг жизненно важных показателей дает возможность врачу корректировать схему лечения в режиме реального времени, что повышает безопасность и эффективность процедуры.
Углубиться в тему – вывод из запоя круглосуточно
Для организации вашего события идеально подойдут стоимость бумажных браслетов, которые обеспечат надежный контроль доступа и удобство для гостей.
Процесс нанесения печати на браслеты позволяет воплотить фирменный стиль или индивидуальный дизайн.
Visit Qorivo Bonding – Easy-to-navigate site, organized pages, and information is simple to follow.
По информации ГБУЗ «Областной центр медицинской профилактики» Мурманской области, учреждения, ориентированные на результат, открыто информируют о применяемых методиках и допусках к лечению. Важно, чтобы уже на этапе первого контакта вы получили не только цену, но и понимание того, что вам предстоит.
Подробнее – klinika lecheniya alkogolizma murmansk
BuyOnlineNow – Modern interface, shopping online is smooth and straightforward.
Лечение проводится в комфортных домашних условиях, что снижает стресс и помогает быстрее восстановиться.
Получить дополнительную информацию – http://vyvod-iz-zapoya-novosibirsk00.ru/vyvod-iz-zapoya-na-domu-novosibirsk/https://vyvod-iz-zapoya-novosibirsk00.ru
«Светлый Шаг» — это не набор общих обещаний, а чётко выстроенный маршрут помощи, где каждый шаг прозрачен: от первичного разговора до устойчивой ремиссии. Мы бережно собираем только необходимые данные, сразу объясняем, что будет сделано в первые 6–12 часов, каких изменений ждать к ночи и по каким маркерам поймём, что курс выбран верно. Конфиденциальность встроена в процесс: нейтральные звонки, ограниченный доступ к медкарте, аккуратный выезд без броской атрибутики, возможность оформить документы с нейтральными формулировками. Итог — меньше стресса, меньше бюрократии и больше управляемости там, где это критично.
Узнать больше – lechenie-v-narkologicheskoj-klinike
Формат
Подробнее можно узнать тут – https://narkologicheskaya-klinika-shchyolkovo0.ru/kruglosutochnaya-narkologicheskaya-klinika-v-shchyolkovo
скачать бесплатно 1win 1win12047.ru
Вывод из запоя — это всегда баланс между скоростью и безопасностью. Дома трудно заметить скрытые ухудшения, особенно ночью: давление и пульс «гуляют», нарастает обезвоживание, сон рваный и тревожный. В «Трезвом Контуре» этот хаос замещается управляемостью: перед выездом дежурный врач собирает ключевые данные (длительность эпизода, лекарства, аллергии, сопутствующие болезни), на месте проводится экспресс-диагностика (АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания), затем запускается схема терапевтической поддержки. Мы постоянно «подстраиваем» инфузии по реакции организма, а не по шаблонной карте: где-то важнее регидратация, где-то — коррекция электролитов, где-то — бережная седация для ночи. Для семьи это значит одно: меньше догадок, больше ясности. Если по картине риски высоки, мы аргументированно предлагаем стационар в Одинцово — и организуем транспортировку без пауз, потому что цена задержки в такие часы всегда выше.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-odincovo10.ru/vyvod-iz-zapoya-ryadom-v-odincovo
Лечение организовано поэтапно, что помогает пациенту постепенно возвращаться к полноценной жизни. Каждый шаг направлен на укрепление результата и снижение риска рецидива.
Получить дополнительные сведения – наркологическая клиника клиника помощь омск
directionunlocksgrowth network – Crisp design, easy-to-follow sections, and pages load quickly
Для тех, кто предпочитает лечение в условиях стационара, предусмотрены комфортные палаты, медицинский контроль 24/7 и возможность консультаций с психотерапевтом. Врачи клиники применяют комплексные методы, направленные не только на снятие симптомов, но и на устранение причин зависимости.
Исследовать вопрос подробнее – вызов наркологической помощи тольятти
Такая форма помощи позволяет избежать осложнений, которые часто сопровождают попытки снять симптомы самостоятельно. При правильном подборе препаратов уже через час наблюдается улучшение самочувствия: уходит головная боль, снижается тревога, стабилизируется сердцебиение и восстанавливается ясность мышления. Пациент получает рекомендации по питанию, режиму отдыха и приёму витаминов, чтобы закрепить результат и предотвратить повторный срыв.
Получить дополнительные сведения – https://narkolog-na-dom-v-voronezhe17.ru/voronezh-narkologiya
Сразу после поступления вызова нарколог прибывает на дом для проведения детального первичного осмотра. Врач собирает краткий анамнез, измеряет жизненно важные показатели, такие как пульс, артериальное давление и температура, и оценивает степень интоксикации. Эта информация является фундаментом для разработки индивидуального плана терапии, который учитывает особенности состояния пациента.
Разобраться лучше – http://vyvod-iz-zapoya-tula000.ru/
main portal – Clean design, easy-to-read information, very user-friendly.
Наркологическая клиника «МедЛайн» предоставляет профессиональные услуги врача-нарколога с выездом на дом в Новосибирске и Новосибирской области. Мы оперативно помогаем пациентам справиться с тяжелыми состояниями при алкогольной и наркотической зависимости. Экстренный выезд наших специалистов доступен круглосуточно, а лечение проводится с применением проверенных методик и препаратов, что гарантирует безопасность и конфиденциальность каждому пациенту.
Получить дополнительную информацию – вызов врача нарколога на дом новосибирск
В клинике «СамарМед» доступно несколько форм лечения: стационарная программа, дневной стационар, амбулаторное наблюдение и гибридные схемы. Пациенты могут выбрать комфортный вариант в зависимости от степени зависимости, текущего состояния и занятости. Внутри стационара предусмотрены как стандартные палаты, так и индивидуальные блоки повышенной комфортности с возможностью проживания совместно с сопровождающим лицом.
Ознакомиться с деталями – лечение в наркологической клинике
В таблице представлены основные элементы детоксикационной терапии:
Исследовать вопрос подробнее – narkologicheskaya-klinika-v-volgograde17.ru/
Amazing issues here. I’m very happy to look your article. Thank you so much and I’m having a look ahead to contact you. Will you kindly drop me a mail?
igrice od 3 do 103
Формат
Получить больше информации – neotlozhnaya-narkologicheskaya-pomoshch
Explore Mivon online – Everything feels open and easy to understand from the start.
Наркологическая клиника в Перми обеспечивает пациентам комфортные условия и профессиональное сопровождение. Врачи работают круглосуточно и соблюдают строгую конфиденциальность, что делает лечение доступным и безопасным.
Подробнее тут – http://narcologicheskaya-klinika-perm0.ru/chastnaya-narkologicheskaya-klinika-perm/
Самый частый повод — не только «плохое похмелье», а именно абстинентный синдром после запоя: когда самочувствие ухудшается при прекращении алкоголя, а попытки «опохмелиться» лишь продлевают проблему. Важно ориентироваться не на терпимость человека к дискомфорту, а на объективные признаки: если симптомы нарастают, сон сорван, поведение становится нестабильным, а тело реагирует паникой, тремором и скачками давления, лучше не тянуть. Особенно осторожными нужно быть при хронических болезнях сердца, печени и сосудов: при них цена ошибки выше, а «универсальные» домашние схемы могут навредить.
Изучить вопрос глубже – http://narkolog-na-dom-krasnogorsk6.ru/narkologicheskaya-klinika-krasnogorsk/
Капельницы при выводе из запоя — основной инструмент детоксикации. Они очищают кровь, стабилизируют давление и восстанавливают баланс электролитов. В клинике «РеабКузбасс» используются только качественные препараты, адаптированные под конкретное состояние пациента. Ниже приведена таблица с основными видами капельниц и их эффектом.
Узнать больше – вывод из запоя вызов
Сразу после поступления вызова нарколог прибывает на дом для проведения детального первичного осмотра. Врач собирает краткий анамнез, измеряет жизненно важные показатели, такие как пульс, артериальное давление и температура, и оценивает степень интоксикации. Эта информация является фундаментом для разработки индивидуального плана терапии, который учитывает особенности состояния пациента.
Ознакомиться с деталями – https://vyvod-iz-zapoya-tula000.ru/vyvod-iz-zapoya-na-domu-tula
SmartPurchaseCenter – Smooth and secure, checkout is simple and reliable.
Лечение проходит в несколько этапов: диагностика, детоксикация, медикаментозная поддержка и восстановление. Каждый этап имеет чёткие цели и критерии эффективности, что делает процесс управляемым и безопасным. Применяются препараты, сертифицированные в РФ, и только те, чья эффективность подтверждена клиническими исследованиями.
Детальнее – http://vyvod-iz-zapoya-v-volgograde17.ru
После поступления вызова наш нарколог выезжает к пациенту в кратчайшие сроки, прибывая по адресу в пределах 30–60 минут. Специалист начинает процедуру с подробного осмотра и диагностики, измеряя ключевые показатели организма: артериальное давление, частоту пульса, насыщенность кислородом и собирая подробный анамнез.
Подробнее тут – нарколог на дом вывод из запоя
Цель
Узнать больше – http://narkologicheskaya-klinika-korolyov0.ru/narkologicheskaya-klinika-na-dom-v-korolyove/
Выездная бригада «МедОпоры» дежурит 24/7 и покрывает весь Красногорск и близлежащие районы. После короткого звонка дежурный уточняет длительность запоя, сопутствующие болезни, принимаемые препараты и аллергии — это экономит время на месте и помогает заранее предусмотреть риски. Врач приезжает с комплектом одноразовых систем, растворами и медикаментами, проводит экспресс-диагностику: измерение давления, пульса, сатурации, температуры, оценка неврологического статуса, степени обезвоживания и тревожности. По этим данным формируется индивидуальная схема инфузий и симптоматической поддержки. Наша задача — не просто «поставить капельницу», а безопасно развернуть план стабилизации, где дозировки и темп меняются по реакции организма. Если выявляются признаки осложнений или дома нет условий для безопасного наблюдения, сразу предлагаем перевод в профильный стационар, чтобы не терять драгоценные часы. Семья получает понятные роли и инструкции, а врач остаётся на связи для уточнений по режиму ближайшей ночи.
Разобраться лучше – вывод из запоя капельница на дому
Мы много лет оттачивали алгоритм, чтобы острый этап был не марафоном, а простой последовательностью шагов. Сначала — короткий скрининг по телефону и согласование окна прибытия. На месте врач спокойно фиксирует АД/ЧСС/сатурацию/температуру, при показаниях делает ЭКГ и сразу запускает детокс: регидратацию, коррекцию электролитов, защиту печени и ЖКТ, мягкую противотревожную поддержку по переносимости. Параллельно выдаём «карту суток»: когда отдыхать, сколько пить воды малыми порциями, какая еда уместна в первые часы, по каким признакам звонить внепланово. Если по ходу становится видно, что дома «тесно» с медицинской точки зрения, организуем перевод под 24/7 — без пауз, с переносом всех назначений и наблюдений.
Получить больше информации – https://narkologicheskaya-klinika-domodedovo0.ru/chastnaya-narkologicheskaya-klinika-v-domodedovo
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Получить дополнительную информацию – http://www.domen.ru
Не всегда человек способен самостоятельно прекратить приём алкоголя и восстановиться. Есть состояния, требующие немедленного вмешательства специалистов. Обратиться за помощью необходимо, если наблюдаются следующие признаки:
Подробнее тут – http://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-staczionar-voronezh/
Мы выезжаем в любое время дня и ночи. Организационно всё просто: короткий звонок с описанием состояния, согласование адреса и времени, консультация по подготовке помещения, приезд врача. Если состояние тяжёлое (длительный запой, возраст 60+, выраженная соматика, признаки делирия, многократная рвота, спутанность сознания), медик предложит стационар сразу — это безопаснее, чем пытаться «дотянуть» ночь дома. В клинике пациент находится под круглосуточным наблюдением, при необходимости выполняются дополнительные исследования, расширяется объём инфузий, корректируется медикаментозная схема. Для пожилых и кардиологических пациентов стационарный формат часто предпочтителен: непрерывный мониторинг снижает риски и ускоряет стабилизацию.
Подробнее – http://vyvod-iz-zapoya-korolev10.ru/
На этом этапе специалист уточняет, сколько времени продолжается запой, какие основные симптомы наблюдаются, и если имеются, то какие хронические заболевания могут влиять на течение терапии. Точный анализ этих данных позволяет сформировать персонализированную стратегию лечения, которая будет максимально адаптирована к состоянию пациента и его потребностям.
Разобраться лучше – вывод из запоя клиника в ярославле
Клиника обеспечивает анонимность и безопасность. Информация о пациентах не передаётся третьим лицам, а процедуры выполняются в комфортных условиях с использованием сертифицированных препаратов и современного оборудования.
Детальнее – наркологическая клиника нарколог в новокузнецке
Даже телефонный разговор с клиникой может многое сказать о её подходе. Если вам предлагают типовое лечение без уточнения подробностей или избегают вопросов о составе команды, это тревожный сигнал. Серьёзные учреждения в Мурманске обязательно предложат предварительную консультацию, зададут уточняющие вопросы и расскажут, как строится программа помощи.
Исследовать вопрос подробнее – лечение алкоголизма
Сразу после вызова нарколог прибывает на дом для проведения детального осмотра. На этом этапе специалист измеряет жизненно важные показатели, собирает анамнез и оценивает степень алкогольной интоксикации, что является основой для составления персонального плана лечения.
Подробнее тут – вывод из запоя цена тула.
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Подробнее – наркологическая клиника нарколог волгоград
Что включено на практике
Детальнее – http://narkologicheskaya-klinika-odincovo0.ru/
Врач уточняет, как долго продолжается запой, какой алкоголь употребляется, а также наличие сопутствующих заболеваний. Этот тщательный анализ позволяет оперативно подобрать оптимальные методы детоксикации и снизить риск осложнений.
Подробнее – http://vyvod-iz-zapoya-tula0.ru
Таким образом, лизинг коммерческого транспорта становится инструментом развития и роста бизнеса.
спецтехника лизинг спецтехника лизинг.
Лечение алкоголизма в Перми в условиях специализированной клиники обеспечивает высокий уровень безопасности и результативности. Пациенты получают квалифицированную помощь в комфортных условиях и под наблюдением опытных специалистов.
Подробнее можно узнать тут – https://lechenie-alkogolizma-perm0.ru/lechenie-alkogolizma-perm-anonimno/
Клиника «АнтиАлко» предлагает экстренную медицинскую помощь на дому в Новосибирске и Новосибирской области для тех, кто столкнулся с запоем. Если вы или ваш близкий оказались в состоянии длительной алкогольной интоксикации, наши специалисты готовы оперативно приехать к вам, провести комплексную детоксикацию и купировать симптомы абстинентного синдрома. Мы гарантируем высокий уровень безопасности, полную анонимность и индивидуальный подход к каждому пациенту.
Узнать больше – наркология вывод из запоя в новосибирске
Наркологическая помощь в «ВолгаМед Тольятти» включает широкий спектр процедур и методик. Каждый случай рассматривается индивидуально, с учётом состояния пациента, стадии заболевания и сопутствующих факторов. Ниже представлена таблица с основными направлениями медицинской работы.
Ознакомиться с деталями – http://narkologicheskaya-pomoshh-v-tolyatti17.ru/narkologiya-goroda-tolyatti/
Снижается тремор и тошнота, выравниваются вегетативные реакции, возвращается способность спокойно уснуть. Вместо «качелей» настроения и попыток самолечения появляется ощущение контроля: понятно, что делаем сейчас и чего ждём дальше.
Получить больше информации – skoraya-pomoshch-vyvoda-iz-zapoya
Ниже — краткий ориентир, который помогает семье понимать логику рекомендаций до очного осмотра. Это не «замена врачу», а понятная рамка для принятия решения о старте.
Выяснить больше – http://narkologicheskaya-klinika-ehlektrostal0.ru/narkologicheskaya-klinika-ceny-v-ehlektrostali/
Запой становится критическим, когда организм не справляется с постоянным поступлением алкоголя и начинает накапливать токсины. Если состояние пациента ухудшается, появляются такие симптомы, как сильная рвота, головокружение, спутанность сознания, судороги, резкие колебания артериального давления, а также проявления тяжелого абстинентного синдрома (дрожь, панические атаки, бессонница, тревожность), вызов нарколога становится необходимым. Также экстренная помощь требуется при наличии психических нарушений — галлюцинациях, агрессивном поведении или алкогольном психозе. Своевременное вмешательство позволяет стабилизировать состояние, предотвратить развитие осложнений и снизить риск для жизни.
Получить дополнительную информацию – http://vyvod-iz-zapoya-novosibirsk00.ru
Наркологическая помощь в «ВолгаМед Тольятти» включает широкий спектр процедур и методик. Каждый случай рассматривается индивидуально, с учётом состояния пациента, стадии заболевания и сопутствующих факторов. Ниже представлена таблица с основными направлениями медицинской работы.
Узнать больше – https://narkologicheskaya-pomoshh-v-tolyatti17.ru
Снижается тремор и тошнота, выравниваются вегетативные реакции, возвращается способность спокойно уснуть. Вместо «качелей» настроения и попыток самолечения появляется ощущение контроля: понятно, что делаем сейчас и чего ждём дальше.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-odincovo10.ru/vyvod-iz-zapoya-na-domu-v-odincovo/
Что делаем фактически
Углубиться в тему – вывод наркологическая клиника
Медикаментозная терапия — важнейший этап стабилизации состояния. Врачи «СамарМед» применяют препараты с доказанной эффективностью: детоксикационные растворы, нейрометаболики, седативные и анксиолитические средства, ноотропы, гепатопротекторы, а при необходимости — антипсихотики. Подбор схемы проводится индивидуально, с учётом переносимости, наличия сопутствующих заболеваний, возраста и стадии зависимости. Все препараты применяются строго по международным протоколам и под контролем врачей круглосуточно.
Углубиться в тему – запой наркологическая клиника самара
Формат
Ознакомиться с деталями – narkologicheskaya-klinika-narkolog
DecisionHelperPro – Offers clear guidance, making choices feel simple and actionable.
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Подробнее – нарколог на дом недорого
Ulvix main site – Concise content and a tidy layout make navigation smooth.
Каждый этап направлен на восстановление организма без стресса и перегрузки. Врачи работают деликатно, чтобы пациент чувствовал безопасность и понимал, что помощь оказывается профессионально.
Узнать больше – http://vyvod-iz-zapoya-v-novokuzneczke17.ru
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Получить больше информации – запой нарколог на дом в воронеже
В таблице представлены основные элементы детоксикационной терапии:
Подробнее тут – запой наркологическая клиника в волгограде
Нужна срочная помощь при алкогольном отравлении или запое? Вызовите нарколога на дом в Иркутске! Квалифицированная помощь нарколога на дому: диагностика, капельница, стабилизация состояния. Круглосуточный выезд нарколога, анонимность и снижение рисков – с «ТрезвоМед». Самостоятельный отказ невозможен? Необходима наркологическая помощь. Васильев: «Не затягивайте с помощью при алкогольном отравлении!».
Подробнее – нарколог в иркутске
Использование автоматизированных систем дозирования позволяет точно подобрать необходимое количество медикаментов, минимизируя риск передозировки и побочных эффектов. Постоянный мониторинг жизненно важных показателей дает возможность врачу корректировать схему лечения в режиме реального времени, что повышает безопасность и эффективность процедуры.
Углубиться в тему – срочный вывод из запоя в ярославле
zavik online – Organized pages, content is clear, and navigation feels smooth
Даже телефонный разговор с клиникой может многое сказать о её подходе. Если вам предлагают типовое лечение без уточнения подробностей или избегают вопросов о составе команды, это тревожный сигнал. Серьёзные учреждения в Мурманске обязательно предложат предварительную консультацию, зададут уточняющие вопросы и расскажут, как строится программа помощи.
Получить дополнительные сведения – лечение алкоголизма
TrustedBuyOnline – Well-structured site, finding and purchasing products is safe and simple.
Такая структура терапии делает процесс максимально эффективным и безопасным.
Получить дополнительные сведения – лечение в наркологической клинике
Что включено на практике
Получить дополнительную информацию – https://narkologicheskaya-klinika-odincovo0.ru/chastnaya-narkologicheskaya-klinika-v-odincovo
Комплексная терапия включает несколько последовательных этапов, обеспечивающих полное восстановление организма и личности пациента. Каждый из них направлен на решение конкретных задач — от устранения интоксикации до закрепления устойчивой ремиссии.
Получить больше информации – https://narkologicheskaya-klinika-v-volgograde17.ru/narkologi-volgograda/
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Подробнее – частная наркологическая клиника
В зависимости от состояния пациента и пожеланий семьи наркологическая помощь может быть оказана в одном из нескольких форматов: на дому, в стационаре или дистанционно. Каждый из форматов обеспечивает доступ к медицинской помощи без бюрократии и с сохранением полной конфиденциальности.
Выяснить больше – наркологическая помощь в омске
В Королёве мы запускаем помощь без «многоходовок». С первого контакта дежурный врач аккуратно уточняет жалобы, длительность эпизода, принимаемые лекарства и сопутствующие диагнозы, после чего предлагает безопасную точку входа: выезд на дом, дневной формат или круглосуточный стационар. Каждое действие объясняется простым языком: зачем оно нужно, какого эффекта ждать в ближайшие часы и что будет считаться нормальной динамикой. Конфиденциальность заложена в процесс по умолчанию: минимально необходимый объём персональных данных, нейтральная коммуникация, ограниченный доступ к медкарте и отсутствие постановки на учёт. Такой порядок снимает лишнее напряжение у семьи и экономит самое ценное — время.
Детальнее – http://www.domen.ru
Запой, интоксикация? Вызовите нарколога на дом в Иркутске для быстрой и анонимной помощи. На дому: осмотр, подбор лечения, капельница для вывода токсинов и улучшение самочувствия. «ТрезвоМед» – круглосуточная наркологическая помощь на дому с гарантией анонимности. Не справляетесь с зависимостью сами? Вызовите нарколога на дом. Васильев подчеркивает: «Оперативная помощь – ключ к выздоровлению при отравлении алкоголем».
Разобраться лучше – https://narcolog-na-dom-v-irkutske0.ru/vrach-narkolog-na-dom-irkutsk
Врач уточняет, как долго продолжается запой, какой алкоголь употребляется, а также наличие сопутствующих заболеваний. Этот тщательный анализ позволяет оперативно подобрать оптимальные методы детоксикации и снизить риск осложнений.
Подробнее – http://vyvod-iz-zapoya-tula0.ru/
На этом этапе специалист уточняет, сколько времени продолжается запой, какие основные симптомы наблюдаются, и если имеются, то какие хронические заболевания могут влиять на течение терапии. Точный анализ этих данных позволяет сформировать персонализированную стратегию лечения, которая будет максимально адаптирована к состоянию пациента и его потребностям.
Изучить вопрос глубже – наркология вывод из запоя в ярославле
После завершения инфузий врач-нарколог даёт рекомендации по питанию, водному балансу и образу жизни. При необходимости пациенту назначается курс поддерживающей терапии для закрепления эффекта.
Подробнее – http://www.domen.ru
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Есть чему поучиться – https://virtueempress.com/essential-resources-biblical-meditation
В таблице представлены основные элементы детоксикационной терапии:
Углубиться в тему – платная наркологическая клиника волгоград
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
А что дальше? – https://www.realty-key.ru/themes/prodazha
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Где можно узнать подробнее? – https://zebra.pk/product/rockwall-for-exterior-grey-color
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Связаться за уточнением – https://www.pixedelic.com/themes/mood/jaded-zombies-acted-quaintly-but-kept-driving-their-oxen-forward
Инфузионная терапия подбирается под человека, а не под «среднюю» ситуацию. Базовый каркас обычно включает растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы. По показаниям добавляются гепатопротекторы и антиоксидантные компоненты — это помогает печени и снижает оксидативный стресс. Если есть выраженная тошнота, подключаем противорвотные; при тревоге и нарушении сна — мягкие анксиолитики и седативные препараты, которые не «вырубают», а выравнивают ритмы и сохраняют контакт для мониторинга. Мы избегаем агрессивных «миксов», потому что избыточная седация может скрыть опасные симптомы и усложнить оценку состояния. Эффективность оцениваем не только по субъективному облегчению, но и по объективным метрикам: пульс, давление, сатурация, динамика тремора, аппетит, качество сна. Как только показатели стабилизируются, фарм-нагрузка снижается, а ведущую роль берет режим — питание, гидратация, спокойный вечерний ритуал, короткие бытовые активности.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-krasnogorsk10.ru/vyvod-iz-zapoya-cena-v-krasnogorske/
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Перейти к полной версии – https://privrespwp2.wpxblog.jp/%E9%AB%98%E5%91%A8%E6%B3%A2%EF%BC%88rf%EF%BC%89%E7%BE%8E%E9%A1%94%E5%99%A8%E3%81%AE%E5%8A%B9%E6%9E%9C
FutureStrategyHub – Step-by-step instructions, strategies are straightforward and useful.
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Где можно узнать подробнее? – https://subseatechdiving.com/gallery
Brixel Capital web presence – Confident tone and solid branding are evident throughout.
В этой статье-обзоре мы соберем актуальную информацию и интересные факты, которые освещают важные темы. Читатели смогут ознакомиться с различными мнениями и подходами, что позволит им расширить кругозор и глубже понять обсуждаемые вопросы.
Выяснить больше – https://siemprealdia.eu/inventaron-nuevos-modelos-de-negocio-tras-vender-sus-empresas-a-google/inventaron-nuevos-modelos-de-negocio-tras-vender-sus-empresas-a-google-3
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Нажмите, чтобы узнать больше – https://freguesianews.com.br/author/admin/page/617
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Раскрыть тему полностью – https://zmed.co.za/2020/how-can-small-business-owners-look-after-remote-workers
Эта статья сочетает познавательный и занимательный контент, что делает ее идеальной для любителей глубоких исследований. Мы рассмотрим увлекательные аспекты различных тем и предоставим вам новые знания, которые могут оказаться полезными в будущем.
А что дальше? – https://kaltenholzhausen.de/hello-world
morix info – Easy browsing with straightforward text and minimal distractions
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Лучшее решение — прямо здесь – https://alaskadigitalnews.com/nick-cave-the-bad-seeds-announce-spring-2025-north-american-tour
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Получить дополнительную информацию – https://lovatiphotography.com/photoshoot-in-porto
Этот информационный материал собраны данные, которые помогут лучше понять текущие тенденции и процессы в различных сферах жизни. Мы предоставляем четкий анализ, графики и примеры, чтобы информация была не только понятной, но и практичной для принятия решений.
Получить дополнительную информацию – https://kcmcleaning.com/?product=pledge-multi-surface-antibacterial-everyday-cleaner-9-7-ounces-2pk
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Погрузиться в научную дискуссию – https://bengalpcbd.com/2022/12/13/best-gaming-laptop-models
web hub – Smooth click-through, design minimal and message clear.
Терапия в клинике строится на системном подходе, позволяющем постепенно восстанавливать здоровье и формировать новые жизненные установки.
Исследовать вопрос подробнее – https://narcologicheskaya-klinika-perm0.ru/chastnaya-narkologicheskaya-klinika-perm
travik link – Intuitive pages, concise information, and minimal distractions while reading
Nice Simple Layout – Discovered this by chance and liked how clear everything looks
В клинике «СамарМед» доступно несколько форм лечения: стационарная программа, дневной стационар, амбулаторное наблюдение и гибридные схемы. Пациенты могут выбрать комфортный вариант в зависимости от степени зависимости, текущего состояния и занятости. Внутри стационара предусмотрены как стандартные палаты, так и индивидуальные блоки повышенной комфортности с возможностью проживания совместно с сопровождающим лицом.
Подробнее – http://narkologicheskaya-klinika-samara0.ru/narkologi-samary/
Выделяется ряд преимуществ, которые делают терапию в клинике оптимальным решением для борьбы с зависимостью.
Подробнее тут – лечение хронического алкоголизма
lucky jet 1win lucky jet 1win
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Подробнее можно узнать тут – vyzvat-narkologa-na-dom
Для многих пациентов страх быть поставленным на учёт или потерять работу становится серьёзным барьером на пути к выздоровлению. В «ПермьМедСервис» данные пациента остаются строго внутри клиники: ни в какие внешние базы информация не передаётся. При оформлении документов не указывается диагноз, а возможна подача под псевдонимом. Консультации, процедуры и ведение истории болезни проходят в полностью закрытом режиме. Это позволяет пациенту сосредоточиться на выздоровлении, не опасаясь последствий для своей личной или профессиональной жизни.
Подробнее тут – https://narkologicheskaya-klinika-perm0.ru/chastnaya-narkologicheskaya-klinika-perm
Система круглосуточной наркологической помощи в «ОмскПрофи» построена на принципе постоянной готовности. В любой момент суток специалисты готовы выехать на дом, принять пациента в стационар или организовать удалённую консультацию. Это особенно важно в острых ситуациях, когда счёт идёт на часы: запой, передозировка, психоз, агрессивное поведение или резкое ухудшение самочувствия. В таких случаях промедление может стоить пациенту жизни.
Подробнее можно узнать тут – скорая наркологическая помощь
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Исследовать вопрос подробнее – http://narkologicheskaya-klinika-kolomna10.ru/luchshie-narkologicheskie-kliniki-v-kolomne/
Вывод из запоя на дому возможен только при относительно контролируемом состоянии и после очной оценки нарколога. В таких случаях специалист выезжает в Раменском, проводит осмотр, назначает индивидуальную капельницу, остаётся до стабилизации состояния и оставляет подробные рекомендации. Важный момент — честность: если во время осмотра врач видит риски (нестабильное давление, признаки начинающегося делирия, серьёзные боли, глубокую дезориентацию), формат на дому не навязывается, а предлагается стационар. Именно это отличает клинику от анонимных «служб капельниц», для которых любая заявка — повод заработать, независимо от последствий.
Выяснить больше – http://vyvod-iz-zapoya-ramenskoe10.ru/vyvod-iz-zapoya-na-domu-v-ramenskom/
Для тех, кто предпочитает лечение в условиях стационара, предусмотрены комфортные палаты, медицинский контроль 24/7 и возможность консультаций с психотерапевтом. Врачи клиники применяют комплексные методы, направленные не только на снятие симптомов, но и на устранение причин зависимости.
Получить больше информации – неотложная наркологическая помощь в тольятти
melbet ru melbet ru .
курсовые заказ курсовые заказ .
Капельница при выводе из запоя — это инструмент, который должен работать точно по задачам организма. В «Трезвый Центр Коломна» не используют мифические смеси «от всего и сразу», не перегружают пациента бессмысленными препаратами. Базовый блок инфузионной терапии направлен на восполнение объёма циркулирующей крови, выравнивание электролитов, коррекцию кислотно-щелочного баланса, снижение токсической нагрузки на печень и мозг. Витамины группы B и магний помогают поддержать нервную систему, уменьшить тремор, раздражительность и риск судорог, улучшить качество сна. При признаках перегрузки печени применяются гепатопротекторные средства и антиоксиданты по показаниям; при выраженной тошноте — противорвотные, чтобы восстановить возможность пить и есть. Для стабилизации эмоционального состояния используются мягкие анксиолитики в дозах, которые не скрывают клиническую картину и не угнетают дыхание. Эффективность такой схемы оценивается по конкретным признакам: стабилизация давления и пульса, нормализация сатурации, уменьшение тремора, снижение тошноты, появление естественного, а не лекарственно-глубокого сна, улучшение общего самочувствия и ясности мышления. По мере улучшения фармнагрузка не увеличивается, а аккуратно снижается, чтобы выход из запоя был плавным и устойчивым, без качелей «полегчало — снова провал».
Разобраться лучше – vyvod-iz-zapoya-klinika
Острый эпизод запоя — это не «плохое самочувствие», а состояние с реальными рисками для сердца, нервной системы и дыхания, особенно в ночные часы, когда усиливаются вегетативные реакции и тревога. В «НоваТрезвие» мы выстраиваем помощь так, чтобы от звонка до заметного облегчения прошло как можно меньше времени и как можно меньше случайностей: короткое интервью для оценки рисков, выезд врача или приём в клинике, экспресс-диагностика по ключевым показателям, персональная инфузионная схема без «универсальных коктейлей», мягкая коррекция сна и тревоги без «вырубания», понятные инструкции семье на 24–72 часа и план продолжения на ближайшие недели. Мы не скрываемся за общими формулами: решения принимаются по фактическим данным, дозы и темп капельниц подстраиваются к динамике каждые 15–20 минут, а при «красных флагах» перевод в стационар организуется без пауз. Конфиденциальность соблюдается строго, а коммуникация простая и предсказуемая — чтобы вы всегда знали, что происходит сейчас и чего ждать к утру.
Разобраться лучше – https://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-klinika-v-ehlektrostali
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Подробнее тут – наркологическая клиника цены красноярск
Комплексная терапия включает несколько последовательных этапов, обеспечивающих полное восстановление организма и личности пациента. Каждый из них направлен на решение конкретных задач — от устранения интоксикации до закрепления устойчивой ремиссии.
Выяснить больше – http://narkologicheskaya-klinika-v-volgograde17.ru/narkologicheskaya-pomoshh-volgograd/
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Подробнее можно узнать тут – https://narcologicheskaya-klinika-omsk0.ru/narkologicheskaya-bolnicza-omsk/
Капельница при вызове нарколога на дом в Долгопрудном от «МедТрезвие Долгопрудный» — это клинический инструмент, а не магический раствор. Главное правило — никакой агрессивной седации ради видимости спокойствия. Инфузионная терапия строится вокруг нескольких задач: восполнить жидкость, выровнять электролиты, снизить токсическую нагрузку на печень и мозг, поддержать сердце и нервную систему, уменьшить тремор, тревогу и соматические жалобы. Используются растворы для регидратации и коррекции водно-электролитного баланса, витамины группы B и магний для поддержки нервной системы, уменьшения риска судорог и нормализации сна, по показаниям — гепатопротекторы и мягкие антиоксиданты, противорвотные препараты для контроля тошноты. При выраженной тревоге или нарушениях сна назначаются щадящие анксиолитические средства в дозах, которые не выключают пациента полностью, а помогают снять паническое напряжение, сохраняя возможность оценивать динамику состояния. Врач отслеживает реакцию на терапию: стабилизацию давления и пульса, уменьшение дрожи, улучшение общего самочувствия, появление более спокойного, естественного сна. По мере облегчения нагрузки схема не усиливается ради счёта, а рационально сокращается. Такой подход защищает пациента от скрытых осложнений и превращает капельницу в контролируемый, полезный шаг, а не в рискованный эксперимент.
Подробнее – нарколог на дом вывод из запоя
Благодаря последовательной работе врачей и постоянному наблюдению лечение проходит безопасно и эффективно, а пациент получает необходимую поддержку на всех этапах терапии.
Изучить вопрос глубже – https://narkologicheskaya-klinika-v-voronezhe17.ru/
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Изучить вопрос глубже – наркологическая клиника наркологический центр омск
xelio source – Quick response, clean layout, and visitors can find info easily
Процесс организован так, чтобы снять с семьи хаос и дать понятный сценарий. После обращения в «РеутовМед Сервис» пациент быстро попадает в поле зрения врача: или через выезд по адресу, или через стационар, если состояние уже близко к опасному. На месте проводится полноценная оценка: давление, пульс, сатурация, температура, осмотр сердца и дыхания, степень обезвоживания, выраженность тремора, наличие рвоты, боли в груди или животе, неврологический статус, поведение, признаки психоза. На основе этих данных формируется индивидуальный план детоксикации. Стартовая инфузионная терапия подбирается с учётом возраста, массы тела, длительности запоя, сопутствующих болезней, уже принятых препаратов. В стационаре пациента размещают в безопасных условиях, контролируют динамику, корректируют дозировки, не оставляют «на самотёк». При выводе из запоя на дому врач остаётся до стабилизации, отслеживает реакцию и при первых тревожных признаках рекомендует стационар, а не уезжает «лишь бы поставил капельницу». Такой пошаговый подход позволяет не только снять острые симптомы, но и уменьшить риск осложнений — от аритмий и судорог до алкогольного делирия.
Изучить вопрос глубже – https://vyvod-iz-zapoya-reutov10.ru/vyvod-iz-zapoya-ryadom-v-reutove/
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Получить больше информации – нарколог на дом вывод из запоя в новокузнецке
С момента начала лечения пациент получает доступ к круглосуточной линии поддержки. Врачи, психологи и координаторы готовы ответить на вопросы, помочь с корректировкой схемы лечения, поддержать в ситуации риска срыва. Эта функция особенно востребована в первые недели после выписки, когда человек сталкивается с триггерами в привычной среде и нуждается в дополнительной защите. Связь может осуществляться по телефону, через защищённый мессенджер или с помощью мобильного приложения клиники.
Подробнее – http://lechenie-narkomanii-samara0.ru/
Для удобства восприятия можно ориентироваться на следующую структуру (это не публичная оферта, а примерная модель ценообразования — точная сумма фиксируется после осмотра и согласования схемы):
Получить дополнительную информацию – vyzvat-vracha-narkologa-na-dom
Процесс вывода из запоя включает последовательное воздействие на ключевые звенья интоксикации. Ниже представлена таблица, отражающая этапы лечения, используемые методики и ожидаемые результаты терапии.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-staczionar-voronezh
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Подробнее – платная наркологическая клиника новокузнецк
Каждый из методов подбирается индивидуально, что позволяет учитывать медицинские показания и личные особенности пациента.
Подробнее – http://lechenie-alkogolizma-perm0.ru
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Выяснить больше – запой наркологическая клиника
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Узнать больше – наркологическая клиника наркологический центр
Не всегда человек способен самостоятельно прекратить приём алкоголя и восстановиться. Есть состояния, требующие немедленного вмешательства специалистов. Обратиться за помощью необходимо, если наблюдаются следующие признаки:
Углубиться в тему – https://vyvod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-voronezh
После стабилизации состояния пациенту предлагается пройти этап реабилитации. В клинике он может занять от 30 до 180 дней, в зависимости от тяжести зависимости, стажа употребления и социальной ситуации. Реабилитационный блок построен по принципам когнитивной реструктуризации: меняются привычные модели мышления, формируются новые способы реагирования на стресс, прорабатываются неразрешённые психологические конфликты. Используются методы психодрамы, арт-терапии, телесно-ориентированной терапии и даже нейропсихологической гимнастики.
Получить больше информации – http://lechenie-narkomanii-samara0.ru
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Выяснить больше – наркологическая клиника цены новокузнецк
Для удобства восприятия можно ориентироваться на следующую структуру (это не публичная оферта, а примерная модель ценообразования — точная сумма фиксируется после осмотра и согласования схемы):
Получить дополнительную информацию – https://narkolog-na-dom-serpuhov10.ru/narkolog-psiholog-na-dom-serpuhov/
В основе работы клиники лежит принцип: зависимость — это не просто привычка и не «слабость характера», а комплексное заболевание, которое требует последовательного лечения, а не случайной капельницы по вызову. «Трезвый Шаг Раменское» отказывается от практики, когда пациенту предлагают один-единственный «волшебный» метод, не объясняя, что будет дальше. Здесь каждое обращение рассматривается в контексте стадии зависимости, общего состояния организма, психоэмоционального фона, семейной ситуации. Сначала специалисты снимают острые проявления: выход из запоя, детоксикация после употребления алкоголя, наркотиков или сочетаний, купирование абстиненции, коррекция давления, пульса, сна, тревоги. Затем формируется стабилизационный этап — подбор поддерживающих схем, работа с тягой, выравнивание эмоционального состояния. После этого при готовности пациента подключаются психотерапевтические и реабилитационные инструменты: мотивационные программы, работа с установками, триггерами, окружением. Важная особенность «Трезвый Шаг Раменское» — готовность объяснять семье и самому пациенту, зачем нужен каждый этап, какие цели у процедуры и какие результаты реально ожидать. Это снижает сопротивление, формирует доверие и делает путь не хаотичным, а управляемым.
Ознакомиться с деталями – narkologicheskaya-klinika
Наркологическая клиника в Перми использует современные методики, которые подбираются индивидуально с учетом клинической картины пациента. Каждый метод имеет конкретные цели и задачи, что делает процесс лечения прогнозируемым и безопасным.
Исследовать вопрос подробнее – наркологическая клиника стационар пермь
сколько стоит курсовая работа по юриспруденции kupit-kursovuyu-43.ru .
melbet sports betting melbet sports betting .
Каждый пациент получает персонализированный план лечения, разработанный с учётом анамнеза, общего состояния и психоэмоционального фона. В «ПермьМедСервис» нет универсальных шаблонов — используется модульная модель терапии, при которой программы состоят из комбинированных блоков: медикаментозное лечение, психотерапия, физиотерапия, семейное консультирование. Это позволяет гибко адаптировать курс, вносить изменения по ходу лечения и учитывать динамику состояния пациента.
Углубиться в тему – наркологическая клиника наркологический центр пермь
official qerly – Logical layout, clear headings, and overall user-friendly design
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Детальнее – http://narkologicheskaya-klinika-v-volgograde17.ru/narkologi-volgograda/
«ОмскПрофи» укомплектована современной медицинской базой: передвижные аппараты для ЭКГ, инфузионные стойки, экспресс-анализаторы, мониторы состояния, аппараты ИВЛ (в реанимационных палатах). Штат сотрудников сформирован из врачей-наркологов, токсикологов, психиатров, психотерапевтов, медицинских сестёр, прошедших обучение по международным протоколам. Ведётся постоянная учёба, стажировки, участие в научных форумах. Благодаря этому пациенты получают не только медицинскую помощь, но и психологическое сопровождение, направленное на долгосрочный результат.
Выяснить больше – частная наркологическая помощь омск
Лечение алкоголизма в Перми в условиях специализированной клиники обеспечивает высокий уровень безопасности и результативности. Пациенты получают квалифицированную помощь в комфортных условиях и под наблюдением опытных специалистов.
Ознакомиться с деталями – центр лечения алкоголизма пермь
Каждое направление встроено в общую стратегию: не просто купировать симптомы, а уменьшить риск повторения сценария, когда после «облегчения» всё возвращается к прежней модели употребления.
Углубиться в тему – narkologicheskie-kliniki-obratnyj-zvonok
Клиника «Трезвый Шаг Раменское» выстраивает помощь так, чтобы пациент и его близкие не метались между разными службами и частными «специалистами», а получали комплекс услуг в одном месте. Это особенно важно для тех, кто уже сталкивался с провалами после разовых кодировок, неподходящих капельниц или формальной «помощи».
Получить дополнительные сведения – наркологическая клиника
Такая структура лечения помогает пациентам пройти все этапы восстановления под контролем специалистов.
Подробнее можно узнать тут – http://narcologicheskaya-klinika-perm0.ru/perm-narkologiya/https://narcologicheskaya-klinika-perm0.ru
В клинике «СамарМед» доступно несколько форм лечения: стационарная программа, дневной стационар, амбулаторное наблюдение и гибридные схемы. Пациенты могут выбрать комфортный вариант в зависимости от степени зависимости, текущего состояния и занятости. Внутри стационара предусмотрены как стандартные палаты, так и индивидуальные блоки повышенной комфортности с возможностью проживания совместно с сопровождающим лицом.
Получить дополнительную информацию – анонимная наркологическая клиника самара
Процесс лечения строится поэтапно, что позволяет контролировать динамику состояния пациента и постепенно возвращать его к полноценной жизни.
Ознакомиться с деталями – https://lechenie-alkogolizma-perm0.ru/lechenie-alkogolizma-perm-anonimno
«Трезвый Центр Коломна» предлагает несколько маршрутов, и выбор делается не по принципу «как удобнее», а по критериям безопасности. Если пациент в сознании, на контакте, без грубой дезориентации, без галлюцинаций, может пить воду, рвота эпизодическая, нет тяжёлых скачков давления и пульса, дома есть тишина и ответственный взрослый — возможен выезд на дом. Врач приезжает в Коломне, проводит осмотр, измеряет давление, пульс, сатурацию, температуру, оценивает тремор, степень обезвоживания, неврологический и психический статус, подбирает индивидуальную инфузионную схему и наблюдает за реакцией. Если же запой затянулся (3–5 суток и более), выражены слабость, шаткость походки, многократная рвота, резкие «качели» АД и ЧСС, есть подозрение на предделирий или делирий, тяжёлая соматика или пожилой возраст — врач честно рекомендует стационар. В отделении пациент получает круглосуточный мониторинг, возможность оперативно корректировать лечение, защищённую среду без доступа к алкоголю и посторонних стимулов, поддержку медперсонала в любое время суток. Такой дифференцированный подход экономит силы, деньги и главное — снижает риск критических осложнений, которые часто возникают именно после «домашних экспериментов».
Получить больше информации – anonimnyj-vyvod-iz-zapoya
В клинике «СамарМед» доступно несколько форм лечения: стационарная программа, дневной стационар, амбулаторное наблюдение и гибридные схемы. Пациенты могут выбрать комфортный вариант в зависимости от степени зависимости, текущего состояния и занятости. Внутри стационара предусмотрены как стандартные палаты, так и индивидуальные блоки повышенной комфортности с возможностью проживания совместно с сопровождающим лицом.
Получить дополнительную информацию – частная наркологическая клиника
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Углубиться в тему – narkologicheskaya-klinika-kolomna10.ru/
Услуга
Подробнее можно узнать тут – нарколога на дом щелково
Такая структура терапии делает процесс максимально эффективным и безопасным.
Получить дополнительные сведения – http://narcologicheskaya-klinika-omsk0.ru/
Работа клиники строится на принципах индивидуального подхода, доказательной медицины и строгого соблюдения конфиденциальности. Каждый пациент проходит обследование, в ходе которого оценивается состояние организма, выявляется стадия зависимости и сопутствующие нарушения. На основе полученных данных разрабатывается персональная программа лечения, включающая медицинские, психологические и социальные методы коррекции поведения.
Детальнее – http://narkologicheskaya-klinika-v-voronezhe17.ru/narkolog-voronezh-anonimno/
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Ознакомиться с деталями – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne/
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Получить больше информации – http://narkolog-na-dom-shchelkovo10.ru
velon web – User-friendly interface with clear text and structured pages
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Ознакомиться с деталями – вывод из запоя недорого новокузнецк
Наркологическая помощь в современном формате — это комплексное лечение зависимостей и состояний интоксикации с индивидуальным подходом к каждому пациенту. В клинике «ВолгаМед Тольятти» круглосуточно работают врачи-наркологи, психиатры и реабилитологи, готовые оказать поддержку в любой момент. Применяются сертифицированные препараты, проверенные методики и психологическое сопровождение. При этом особое внимание уделяется анонимности и безопасности пациента: информация не передаётся третьим лицам, а лечение проводится строго конфиденциально.
Разобраться лучше – наркологическая помощь на дому круглосуточно тольятти
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Изучить вопрос глубже – https://narkologicheskaya-klinika-kolomna2-10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne
Диспетчер уточняет адрес в Электростали, длительность эпизода, текущие препараты и дозы, аллергии, сопутствующие заболевания, последние значения давления/пульса. Это экономит 15–20 минут на месте и позволяет заранее исключить опасные взаимодействия.
Разобраться лучше – http://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-stacionar-v-ehlektrostali/
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Подробнее – анонимная наркологическая помощь тольятти
заказать дипломную работу онлайн kupit-kursovuyu-43.ru .
мелбет онлайн мелбет онлайн .
zurix access – Straightforward layout, readable sections, and overall enjoyable browsing
About Us – Pages are organized, navigation is smooth, and information feels reliable and clear.
Да, клиника работает в закрытом формате. Пациент вправе отказаться от передачи данных третьим лицам, а документы оформляются без указания диагноза.
Получить дополнительную информацию – https://narkologicheskaya-klinika-perm0.ru/chastnaya-narkologicheskaya-klinika-perm
Клиника в Волгограде руководствуется принципами индивидуального подхода, конфиденциальности и научно обоснованных методик. Врач-нарколог оценивает общее состояние пациента, определяет стадию зависимости и подбирает оптимальную терапевтическую схему. Лечение включает детоксикацию, медикаментозную поддержку, психотерапию и реабилитацию. Каждый пациент проходит лечение в безопасных условиях с постоянным медицинским наблюдением.
Углубиться в тему – лечение в наркологической клинике волгоград
Ключевой элемент вывода из запоя в Реутове — правильно подобранная капельница, но в «РеутовМед Сервис» её рассматривают не как волшебное средство, а как часть комплексной терапевтической схемы. Основная цель — не «вырубить» человека сильными седативными коктейлями, а помочь организму безопасно выйти из состояния интоксикации. В инфузионную терапию входят растворы для регидратации, которые восполняют потерю жидкости, снижают вязкость крови, улучшают микроциркуляцию и работу внутренних органов. Коррекция электролитного баланса помогает уменьшить дрожь, мышечную слабость, снизить риск нарушений сердечного ритма. Применяются витамины группы B и препараты магния для поддержки нервной системы, снижения раздражительности и вероятности судорог. По показаниям добавляются гепатопротекторы, мягкие антиоксиданты для разгрузки печени, противорвотные средства при выраженной тошноте, щадящие анксиолитики для снижения тревоги и нормализации сна без грубого угнетения сознания. Все дозировки учитывают сопутствующие заболевания и возраст, что особенно важно для пациентов с гипертонией, ИБС, диабетом, поражением печени и пожилых людей. Эффект оценивается по объективным критериям: стабилизация давления и пульса, уменьшение дрожи, улучшение самочувствия, нормализация сна и поведения, а не только по фразе «стал тихим».
Подробнее – vrach-vyvod-iz-zapoya
1win affiliate http://www.1win5740.help
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Получить дополнительную информацию – https://jnsbm.org/measurement-of-hemoglobin-variants-in-hemoglobinopathies
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Изучите внимательнее – https://www.coptfil.fr/index.php?article13
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Разобраться лучше – https://descarc.ro/produs/contract-de-donatie-cu-rezerva-dreptului-de-uzufruct-viager
Вывод из запоя в Раменском в условиях клиники строится не вокруг одной капельницы, а вокруг понятной цепочки шагов, где каждый этап логичен и медицински обоснован. Это помогает не только быстро облегчить состояние, но и уменьшить вероятность того, что через пару дней человек снова уйдёт в запой.
Подробнее – срочное выведение из запоя
Create unique marks for your business with our stamp maker online.
High-quality production is a significant focus for online rubber stamp services.
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Личный опыт — читайте сами – https://thejewelhouse.com/product/cushion-brilliant-cut-halo-lab-diamond-earrings
Main holdings website – Easy-to-follow navigation that clearly presents what the site is about.
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Ознакомиться с теоретической базой – https://oilbalance.at/produkt/doterra-vmg
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Исследовать вопрос подробнее – https://www.graceassistedlivinghomes.com/hall-of-a-cozy-restaurant-2
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Узнать из первых рук – https://template137.webekspor.com/strength-and-flexibility-make-it-a-sought-after-material-for-various-products
В этой информационной статье вы найдете интересное содержание, которое поможет вам расширить свои знания. Мы предлагаем увлекательный подход и уникальные взгляды на обсуждаемые темы, побуждая пользователей к активному мышлению и критическому анализу.
Раскрыть тему полностью – http://pietroplace.com/beatrice-en-velo
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Получить дополнительные сведения – https://pkptclinic.com/product/%E0%B8%AD%E0%B8%B8%E0%B8%9B%E0%B8%81%E0%B8%A3%E0%B8%93%E0%B9%8C%E0%B8%A2%E0%B8%B7%E0%B8%94%E0%B8%99%E0%B8%B4%E0%B9%89%E0%B8%A7%E0%B8%AB%E0%B8%B1%E0%B8%A7%E0%B9%81%E0%B8%A1%E0%B9%88%E0%B9%80%E0%B8%97
Мы предлагаем вам окунуться в океан любопытных фактов и вдохновляющих историй. Эта публикация поможет расширить горизонты, разбудить интерес к науке и истории и увидеть мир с новой стороны.
Узнать больше – https://himalayancordy.com/retail/vitamin-d3
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Только для своих – https://superinnovators.com/2022/10/ai-boxing-judge
сколько стоит курсовая работа по юриспруденции kupit-kursovuyu-43.ru .
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Осуществить глубокий анализ – https://www.groupe-huillier.fr/2021/01/29/mecanicien-vp-vul-argonay
melbet sport melbet sport .
rixon platform – Minimalist style, content is easy to read, and navigation feels effortless
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Запросить дополнительные данные – https://www.elkhartnorthside.org/womens-bible-study
knowledge with impact – Ideas are presented in a way that feels relevant and actionable.
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Проверенные методы — узнай сейчас – https://www.bistropompidou.be/2016/03/03/hallo-wereld
Official trust resource – Looks trustworthy at a glance, with clear and steady writing.
landing hub – Pages appear instantly and the structure is easy to understand
Вывод из запоя в Раменском — это не просто «поставить капельницу и отпустить домой», а комплекс медицинских действий, от которых напрямую зависит здоровье, а иногда и жизнь человека. Длительное употребление алкоголя приводит к тяжёлой интоксикации, нарушению работы сердца, печени, головного мозга, сбоям давления, риску судорог, психозов и резких обострений хронических заболеваний. Попытки самостоятельно «сойти с дистанции» дома, с помощью случайных таблеток, седативных препаратов и новых доз алкоголя, часто только усугубляют состояние. Наркологическая клиника «РаменМед Трезвость» в Раменском выстраивает вывод из запоя как безопасный, контролируемый, поэтапный процесс: от экстренного купирования симптомов до формирования плана дальнейшего восстановления. Пациент получает помощь без осуждения, анонимно, с участием специалистов, которые берут на себя ответственность за каждое назначение и каждое действие. Для родственников это означает: больше не нужно гадать, чего бояться и что давать — есть конкретное место и команда, к которым можно обратиться сразу.
Подробнее можно узнать тут – http://vyvod-iz-zapoya-ramenskoe10.ru
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Узнать больше – narkologicheskie-kliniki-obratnyj-zvonok
Даже телефонный разговор с клиникой может многое сказать о её подходе. Если вам предлагают типовое лечение без уточнения подробностей или избегают вопросов о составе команды, это тревожный сигнал. Серьёзные учреждения в Мурманске обязательно предложат предварительную консультацию, зададут уточняющие вопросы и расскажут, как строится программа помощи.
Разобраться лучше – анонимное лечение алкоголизма мурманск
Современная наркологическая клиника — это не просто учреждение для экстренной помощи, а центр комплексной поддержки человека, столкнувшегося с зависимостью. В «КузбассМед» в Новокузнецке реализуется модель интенсивного вмешательства, где используются новейшие медицинские технологии, мультидисциплинарный подход и мобильные выездные службы. Специалисты готовы прибыть на дом за 30 минут с полным набором оборудования и медикаментов, обеспечив пациенту помощь в привычной и безопасной среде. Наркология здесь строится на индивидуализации: каждый случай рассматривается отдельно, с учётом психофизического состояния, анамнеза и жизненного контекста пациента.
Выяснить больше – наркологическая клиника цены
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Получить больше информации – вывод из запоя вызов на дом тюмень
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Подробнее – вывод из запоя
kavlo access – Simple structure paired with a clean, modern feel
Терапия проводится поэтапно, что позволяет пациенту последовательно проходить все стадии восстановления и закреплять результат.
Подробнее можно узнать тут – http://lechenie-alkogolizma-omsk0.ru
Процесс включает несколько шагов:
Подробнее можно узнать тут – частный нарколог на дом уфа
Наркологическая клиника «КоломнаМед Центр» — это место, куда можно обратиться в тот момент, когда домашние попытки контролировать алкоголь, наркотики, аптечные препараты или смесь всего сразу перестают работать, а жизнь превращается в постоянное «завтра начну с нуля». Здесь не обещают чудес за один день и не пугают диагнозами, а выстраивают понятный медицинский маршрут: детоксикация, стабилизация, реабилитация, поддержка семьи, профилактика срывов. Пациент получает помощь в защищённой, конфиденциальной среде, где всё организовано так, чтобы снизить тревогу и стыд, убрать хаос вокруг зависимости и дать человеку шанс вернуться к нормальной жизни без давления, угроз и токсичных «стимулов». Для родных клиника в Коломне — это опора: конкретный адрес, конкретная команда, чёткие сроки и понятные этапы, вместо бесконечных обещаний «он сам справится».
Подробнее – наркологические клиники обратный звонок
Mavero official hub – Clean interface, simple browsing, and content is informative.
Наркологическая клиника «Трезвый Шаг Раменское» — это место, где острые кризисы, многолетние запои и повторяющиеся срывы перестают быть бесконечным кругом, в котором семья остаётся один на один с проблемой. Здесь выстроена система помощи людям с алкогольной и наркотической зависимостью, а также полизависимостями, включая злоупотребление аптечными препаратами. В клинике в Раменском сочетаются круглосуточное наблюдение, профессиональная детоксикация, медикаментозная поддержка, психотерапевтические программы и сопровождение семьи. Важные принципы — безопасность, анонимность, уважение к пациенту и честное объяснение каждого шага лечения. Ни агрессивного давления, ни обещаний «чуда за один день» — вместо этого поэтапный подход, который даёт реальный шанс стабилизировать состояние, снизить тягу и выйти из разрушительного сценария под контролем специалистов. Для близких это означает понятный маршрут: куда обратиться, что будут делать с пациентом, какие риски учтут и как клиника «Трезвый Шаг Раменское» останется на связи после острого периода.
Подробнее – клиника наркологической зависимости
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Получить дополнительную информацию – http://narkologicheskaya-pomoshh-v-volgograde17.ru
Капельница — основной инструмент для очищения организма от продуктов распада этанола. Состав раствора подбирается строго индивидуально. В таблице приведены примеры комплексов, применяемых специалистами клиники «Трезвая Линия Волгоград».
Подробнее – https://vyvod-iz-zapoia-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-volgograd/
Когда запой начинает угрожать здоровью, оперативное вмешательство становится жизненно необходимым. В Туле опытные специалисты оказывают помощь на дому, позволяя начать лечение сразу же в комфортной обстановке. Такой формат терапии обеспечивает оперативную детоксикацию, восстановление нормального обмена веществ и стабилизацию работы внутренних органов, что особенно важно для пациентов, желающих избежать лишнего стресса и сохранить конфиденциальность.
Получить дополнительную информацию – https://vyvod-iz-zapoya-tula0.ru/vyvod-iz-zapoya-czena-tula
Важной частью реабилитации является социализация пациента, возвращение его к активной общественной жизни и формирование новых, здоровых привычек. Для этого в клинике организуются различные мероприятия и программы адаптации.
Разобраться лучше – https://lechenie-narkomanii-tver0.ru/tver-lechenie-alkogolizma/
Запой становится критическим, когда организм не справляется с постоянным поступлением алкоголя и начинает накапливать токсины. Если состояние пациента ухудшается, появляются такие симптомы, как сильная рвота, головокружение, спутанность сознания, судороги, резкие колебания артериального давления, а также проявления тяжелого абстинентного синдрома (дрожь, панические атаки, бессонница, тревожность), вызов нарколога становится необходимым. Также экстренная помощь требуется при наличии психических нарушений — галлюцинациях, агрессивном поведении или алкогольном психозе. Своевременное вмешательство позволяет стабилизировать состояние, предотвратить развитие осложнений и снизить риск для жизни.
Выяснить больше – http://vyvod-iz-zapoya-novosibirsk00.ru/
Наша выездная бригада приезжает без маркировки, в гражданской одежде, согласовывает «тихое окно» связи с пациентом или близкими и начинает не с капельницы, а с настройки среды: тёплая приглушённая подсветка, проветривание без сквозняков, отключение уведомлений, подготовка воды комнатной температуры. Затем — быстрый осмотр, экспресс-метрики и старт индивидуального плана. Каждая корректировка — ровно одна за раз, чтобы сохранить причинно-следственную связь и не провоцировать полипрагмазию.
Ознакомиться с деталями – нарколог на дом клиника
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Ознакомиться с деталями – нарколог вывод из запоя рязань
velixo online – Organized pages, clear headings, and smooth scrolling between sections
Наркологическая клиника — это не просто место, где пациенту оказывают медицинскую помощь. Это учреждение, где формируется стратегия полного восстановления, включающая не только физическое оздоровление, но и психоэмоциональную стабилизацию. В Ярославле работают как частные, так и государственные клиники, однако их подходы, уровень сервиса и состав команд могут существенно различаться. По данным Минздрава РФ, высокий процент успешных исходов наблюдается в тех учреждениях, где реализуется персонализированная модель лечения и постлечебной поддержки.
Получить дополнительные сведения – http://narkologicheskaya-klinika-yaroslavl0.ru/chastnaya-narkologicheskaya-klinika-yaroslavl/
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Углубиться в тему – https://vyvod-iz-zapoya-saratov0.ru/
1win qeydiyyat bonusu https://1win5761.help
При получении заявки по телефону или через сайт администратор передаёт её врачу-дежуранту, который немедленно выезжает по указанному адресу. По прибытии специалист проводит первичный осмотр: измеряются артериальное давление, пульс, температура, сатурация. Затем осуществляется экспресс-оценка состояния ЦНС и метаболизма. При необходимости берутся анализы, подключается инфузионная система, проводятся противотревожные и детоксикационные мероприятия. Врач остаётся с пациентом до полной стабилизации состояния, а при тяжёлых симптомах организует транспортировку в стационар.
Получить дополнительную информацию – платная наркологическая помощь тверь
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Подробнее можно узнать тут – кодирование от алкоголизма в волгограде
Алгоритм организован так, чтобы каждое действие было логичным и предсказуемым. После обращения по телефону врач заранее получает краткую клиническую картину и подбирает набор препаратов с учётом состояния пациента. По прибытии в Долгопрудном нарколог не ставит капельницу «по шаблону», а начинает с осмотра: измеряет давление, пульс, сатурацию, температуру, оценивает тремор, уровень сознания, ориентировку, степень обезвоживания, частоту рвоты, дыхание, возможные боли в груди или животе, обращает внимание на поведение и эмоциональное состояние. Если по результатам осмотра подтверждается, что дом — безопасный формат, подбирается индивидуальная инфузионная схема: объём, скорость введения и препараты зависят от возраста, длительности запоя, сопутствующих болезней и уже использованных медикаментов. Врач остаётся на адресе до завершения основных процедур, контролирует реакцию, при необходимости корректирует план и чётко проговаривает, как пациент должен проводить ближайшие 24–72 часа. Если по ходу работы выявляются признаки угрозы (начальные симптомы делирия, тяжёлые аритмии, нестабильное давление, выраженная дезориентация), нарколог рекомендует стационар и помогает семье организовать перевод. Это честный и безопасный подход: не любой ценой «отработать выезд», а сделать так, чтобы помощь действительно снижала риски.
Разобраться лучше – zapoj-narkolog-na-dom
Запой — это не просто несколько лишних дней алкоголя, а тяжёлое состояние, в котором организм работает на пределе. Чем дольше длится эпизод, тем глубже обезвоживание, тем сильнее сдвиги электролитов, тем выше риск аритмий, гипертонических кризов, судорог, делирия, обострений заболеваний сердца, печени и поджелудочной железы. Попытки «вывести» человека дома силами родных часто включают опасные комбинации: случайные седативные, снотворные, анальгетики, «антипохмельные» из рекламы. Они могут на время усыпить или «успокоить», но при этом скрывают ухудшение, сбивают давление, угнетают дыхание и мешают врачу увидеть реальную картину. В «Трезвый Центр Коломна» подход другой: ещё на этапе звонка специалист уточняет длительность запоя, объёмы и виды алкоголя, наличие гипертонии, ИБС, диабета, заболеваний печени и почек, неврологических проблем, список уже принятых препаратов, эпизоды потери сознания, судорог, странного поведения. На основании этих данных определяется, безопасен ли формат на дому или сразу нужен стационар. Такая сортировка позволяет вовремя перехватить опасные случаи, не терять часы на бесполезные попытки и сразу запускать те схемы, которые реально снижают риски и стабилизируют состояние.
Исследовать вопрос подробнее – bystryj-vyvod-iz-zapoya
Использование автоматизированных систем дозирования позволяет точно подобрать необходимое количество медикаментов, минимизируя риск передозировки и побочных эффектов. Постоянный мониторинг жизненно важных показателей дает возможность врачу корректировать схему лечения в режиме реального времени, что повышает безопасность и эффективность процедуры.
Изучить вопрос глубже – http://vyvod-iz-zapoya-yaroslavl0.ru/vyvod-iz-zapoya-kruglosutochno-yaroslavl/
В таблице представлены основные виды терапии, применяемые в клинике:
Подробнее тут – анонимная наркологическая клиника
В клинике «Альтернатива» применяются современные методы терапии, включающие медикаментозное лечение, психотерапию и социальную реабилитацию.
Ознакомиться с деталями – http://narkologicheskaya-pomoshh-novokuzneczk0.ru
Open capital homepage – Everything is structured well, allowing for smooth and intuitive browsing.
Company website – Easy-to-use menus, clean design, and straightforward explanations.
Наркологическая клиника в Красноярске оказывает профессиональную помощь людям, столкнувшимся с алкогольной, наркотической и другими видами зависимостей. Основная цель деятельности специалистов — восстановление физического здоровья, стабилизация психоэмоционального состояния и возвращение пациента к полноценной жизни. Лечение проводится по современным медицинским протоколам, с применением индивидуальных схем терапии и полным соблюдением конфиденциальности.
Узнать больше – наркологическая клиника лечение алкоголизма
Ниже приведена таблица с типовыми компонентами капельницы и их назначением:
Детальнее – врача капельницу от запоя волгоград
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Ознакомиться с деталями – кодирование от алкоголизма отзывы
Во многих случаях пациент или его родственники не решаются сразу вызвать врача. Для таких ситуаций предусмотрена услуга онлайн-консультации. Она проводится через защищённую видеосвязь, при желании — анонимно. На связи — врач-нарколог или психиатр, который отвечает на вопросы, оценивает ситуацию по визуальным и вербальным признакам, рекомендует план действий. Консультация может стать отправной точкой для дальнейшего вызова врача на дом или записи в клинику. Это особенно удобно для родственников, которые не знают, как подступиться к проблеме и убедить человека в необходимости помощи.
Получить больше информации – https://narkologicheskaya-pomoshh-tver0.ru/
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Разобраться лучше – наркологическая клиника стационар в новокузнецке
Нужна срочная помощь при алкогольном отравлении или запое? Вызовите нарколога на дом в Иркутске! Квалифицированная помощь нарколога на дому: диагностика, капельница, стабилизация состояния. Круглосуточный выезд нарколога, анонимность и снижение рисков – с «ТрезвоМед». Самостоятельный отказ невозможен? Необходима наркологическая помощь. Васильев: «Не затягивайте с помощью при алкогольном отравлении!».
Исследовать вопрос подробнее – выезд нарколога на дом цена в иркутске
Капельница при вызове нарколога на дом в Долгопрудном от «МедТрезвие Долгопрудный» — это клинический инструмент, а не магический раствор. Главное правило — никакой агрессивной седации ради видимости спокойствия. Инфузионная терапия строится вокруг нескольких задач: восполнить жидкость, выровнять электролиты, снизить токсическую нагрузку на печень и мозг, поддержать сердце и нервную систему, уменьшить тремор, тревогу и соматические жалобы. Используются растворы для регидратации и коррекции водно-электролитного баланса, витамины группы B и магний для поддержки нервной системы, уменьшения риска судорог и нормализации сна, по показаниям — гепатопротекторы и мягкие антиоксиданты, противорвотные препараты для контроля тошноты. При выраженной тревоге или нарушениях сна назначаются щадящие анксиолитические средства в дозах, которые не выключают пациента полностью, а помогают снять паническое напряжение, сохраняя возможность оценивать динамику состояния. Врач отслеживает реакцию на терапию: стабилизацию давления и пульса, уменьшение дрожи, улучшение общего самочувствия, появление более спокойного, естественного сна. По мере облегчения нагрузки схема не усиливается ради счёта, а рационально сокращается. Такой подход защищает пациента от скрытых осложнений и превращает капельницу в контролируемый, полезный шаг, а не в рискованный эксперимент.
Углубиться в тему – запой нарколог на дом
Зависимость от психоактивных веществ — серьёзное заболевание, затрагивающее как физическое, так и психологическое состояние человека. При отсутствии своевременной наркологической помощи в клинике возможно ухудшение здоровья, развитие тяжелых осложнений и социальная деградация пациента.
Углубиться в тему – нарколог наркологическая помощь в новокузнецке
Первый шаг в лечении — это тщательный осмотр специалиста. Наряду с измерением жизненно важных показателей (пульс, артериальное давление, температура) врач проводит сбор анамнеза, выясняя длительность запоя, тип употребляемого алкоголя и наличие сопутствующих заболеваний. Эти данные помогают оценить степень интоксикации и подобрать индивидуальный план терапии, что является ключевым для дальнейшей эффективной детоксикации.
Ознакомиться с деталями – vyvod-iz-zapoya-na-domu jaroslavl’
Лечение зависимости в наркологической клинике проводится поэтапно. Это обеспечивает постепенное восстановление организма и исключает риск осложнений. Каждый этап направлен на устранение конкретных нарушений, вызванных употреблением психоактивных веществ.
Получить дополнительную информацию – https://narcologicheskaya-klinika-v-krasnoyarske17.ru/krasnoyarsk-narkologicheskij-czentr
После прохождения основной программы пациенту предлагается поддерживающее наблюдение. Оно может включать дистанционные консультации, участие в группе профилактики срывов, повторные осмотры нарколога и психолога, корректировку медикаментозной схемы. В рамках реабилитации формируются планы действий при возникновении тяги, обучаются навыки сопротивления стрессу и внешнему давлению. При желании можно подключить родственников к процессу постлечебной адаптации, чтобы укрепить результат и снизить риски рецидивов. Таким образом, пациент не остаётся один даже после выписки.
Исследовать вопрос подробнее – центр лечения наркомании
Индивидуально подобранный состав раствора обеспечивает быстрое выведение токсинов и улучшение физического состояния уже в течение первых часов после начала лечения.
Подробнее тут – капельница от запоя клиника волгоград
talix page – Clear interface, intuitive flow, and text is accessible without effort
В процессе лечения используются проверенные методики, которые в комплексе обеспечивают положительный эффект и снижают риск рецидива.
Получить больше информации – реабилитационный центр лечение алкоголизма
Если вы мечтаете о надежном и уютном жилье, обратите внимание на каркасные дома цены, обеспечивающие комфорт и долговечность.
Сегодня каркасные дома отвечают самым высоким требованиям комфорта и надежности.
Такая комплексность обеспечивает воздействие на физические, психологические и социальные факторы зависимости.
Углубиться в тему – центр лечения алкоголизма
Company homepage – Well-laid-out design, professional vibe, and navigation feels smooth.
Мы не используем универсальную «капельницу». Схема собирается из модулей под ведущие жалобы. Медицинские шаги всегда сочетаются с нефраком опорами — свет, тишина, вода малыми глотками, дыхание, — потому что среда усиливает действие препаратов и позволяет держать дозы ниже.
Получить дополнительную информацию – https://narkolog-na-dom-saratov0.ru/
Даже при наличии комфортных условий и современных медикаментов эффективность будет минимальной, если пациент не получает психологическую помощь. У многих зависимость сопровождается тревожными или депрессивными состояниями, травматическим опытом или сложными семейными отношениями. Без проработки этих аспектов высокий риск того, что после выписки произойдёт рецидив.
Получить дополнительные сведения – наркологическая клиника нарколог ярославль
После прохождения основной программы пациенту предлагается поддерживающее наблюдение. Оно может включать дистанционные консультации, участие в группе профилактики срывов, повторные осмотры нарколога и психолога, корректировку медикаментозной схемы. В рамках реабилитации формируются планы действий при возникновении тяги, обучаются навыки сопротивления стрессу и внешнему давлению. При желании можно подключить родственников к процессу постлечебной адаптации, чтобы укрепить результат и снизить риски рецидивов. Таким образом, пациент не остаётся один даже после выписки.
Узнать больше – центр анонимного лечения наркомании новокузнецк
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Изучить вопрос глубже – http://
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Разобраться лучше – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne/
Благодаря комплексному подходу достигается не только снятие симптомов, но и долгосрочная стабилизация состояния пациента.
Подробнее – http://narkologicheskaya-pomoshh-v-volgograde17.ru/narkologicheskaya-klinika-v-volgograde/
Особое внимание в клинике уделяется психологической реабилитации. Зависимость всегда сопряжена с внутренними конфликтами, нарушением привязанностей, проблемами самооценки. Врач-психотерапевт помогает пациенту выявить первопричины срывов, обучает техникам управления стрессом и прорабатывает модель трезвого поведения. В стационаре ведутся групповые и индивидуальные сессии, тренинги по навыкам саморегуляции, арт-терапия и элементы психодрамы. Реабилитационная команда помогает в адаптации к новой социальной роли, восстановлению отношений в семье и планированию жизни после выписки.
Изучить вопрос глубже – наркологическая клиника
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Подробнее тут – https://vyvod-iz-zapoia-v-volgograde17.ru/anonimnaya-narkologiya-vyvod-iz-zapoya-volgograd
Ниже приведена таблица с примерными этапами терапии:
Изучить вопрос глубже – вывод из запоя цена в рязани
Вывод из запоя на дому возможен только при относительно контролируемом состоянии и после очной оценки нарколога. В таких случаях специалист выезжает в Раменском, проводит осмотр, назначает индивидуальную капельницу, остаётся до стабилизации состояния и оставляет подробные рекомендации. Важный момент — честность: если во время осмотра врач видит риски (нестабильное давление, признаки начинающегося делирия, серьёзные боли, глубокую дезориентацию), формат на дому не навязывается, а предлагается стационар. Именно это отличает клинику от анонимных «служб капельниц», для которых любая заявка — повод заработать, независимо от последствий.
Изучить вопрос глубже – http://vyvod-iz-zapoya-ramenskoe10.ru/
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Подробнее тут – вывод из запоя цена в тюмени
Лечение наркомании в клинике начинается с диагностики, позволяющей определить степень зависимости, выявить сопутствующие заболевания и выбрать оптимальную тактику терапии. Важным этапом является детоксикация — очищение организма от токсинов и продуктов распада наркотических веществ, что снижает риск осложнений и облегчает последующее восстановление.
Углубиться в тему – лечение наркомании цена тверь
Одним из ключевых преимуществ «КузбассМед» является современная материально-техническая база. В клинике задействованы устройства для точного мониторинга жизненных функций, автоматические инфузионные системы, экспресс-диагностические модули и оборудование для неотложной терапии. Врачи используют программируемые дозаторы, портативные анализаторы крови и аппараты для оценки дыхательной функции, что позволяет своевременно корректировать тактику лечения без потерь времени. Все процедуры соответствуют национальным стандартам безопасности и рекомендациям ВОЗ.
Выяснить больше – http://narkologicheskaya-klinika-novokuzneczk0.ru
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Узнать больше – https://narkologicheskaya-klinika-kolomna2-10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Углубиться в тему – врач вывод из запоя
Вывод из запоя — это не «волшебная капельница», а последовательная медицинская программа с чёткими целями и измеримыми маркерами. В наркологической клинике «СаратовМед Профи» маршрут строится по принципу управляемых окон: на каждом шаге команда преследует одну цель, меняет лишь один параметр и оценивает результат в заранее назначённый момент. Такой подход снижает лекарственную нагрузку, предотвращает «гонку дозировок» и делает динамику предсказуемой для пациента и близких. Конфиденциальность обеспечивается регламентом: немаркированные выезды, нейтральные формулировки в документах, «тихие» каналы связи, доступ к записям — строго по ролям.
Углубиться в тему – https://vyvod-iz-zapoya-saratov0.ru/
Когда человек в запое, близким кажется, что всё ещё можно решить «по-тихому»: выспаться, отпаять водой, дать обезболивающее или «успокоительное» и дождаться, пока станет легче. На практике это часто приводит к обратному результату. Алкогольная интоксикация нарушает водно-электролитный баланс, сгущает кровь, повышает нагрузку на сердце, провоцирует скачки давления, ухудшает работу печени и нервной системы. Неконтролируемый приём снотворных, анальгетиков, транквилизаторов, особенно вместе с алкоголем, способен вызвать угнетение дыхания, аритмии, судороги или делирий. Домашняя обстановка не даёт возможности следить за всеми показателями и вовремя отреагировать. «РаменМед Трезвость» предлагает клинически выверенный вывод из запоя в Раменском с учётом возраста, длительности употребления, хронических заболеваний, перенесённых ранее осложнений. Здесь не применяют сомнительные схемы «усыпить, чтобы не мешал», а ставят задачу: безопасно пройти острую фазу, снять интоксикацию, стабилизировать давление и пульс, защитить сердце и мозг, снизить риск психозов и, при желании пациента, сразу наметить маршрут реального лечения зависимости. Такой подход снимает с родственников опасную «роль врача» и возвращает ситуацию туда, где ей место — под контроль профессионалов.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-ramenskoe10.ru/vyvod-iz-zapoya-ryadom-v-ramenskom/
«Трезвый Путь Коломна» создаёт единый контур помощи: пациент не «перекидывается» между разными организациями, а проходит лечение в одной системе, где специалисты знают его историю и несут ответственность за последовательность шагов. Это критично для тех, кто уже сталкивался с бессистемными попытками: один врач ставил капельницы, другой «кодировал», третий давал советы, а в итоге всё заканчивалось новым срывом. Здесь маршруты связываются в цельную линию.
Ознакомиться с деталями – zakazat-zvonok-narkologicheskaya-klinika
Капельница при интоксикации помогает быстро очистить организм от продуктов распада алкоголя, восстановить водно-солевой баланс и улучшить самочувствие. В состав раствора входят препараты, нормализующие обмен веществ и поддерживающие работу печени и сердечно-сосудистой системы. Уже через 20–30 минут после начала инфузии пациент ощущает значительное облегчение. Подбор лекарственных средств осуществляется строго индивидуально, с учётом возраста, массы тела и общего состояния здоровья.
Изучить вопрос глубже – нарколог капельница на дом в уфе
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Ознакомиться с деталями – http://vivod-iz-zapoya-v-volgograde17.ru
В основе работы клиники лежит принцип: зависимость — это не просто привычка и не «слабость характера», а комплексное заболевание, которое требует последовательного лечения, а не случайной капельницы по вызову. «Трезвый Шаг Раменское» отказывается от практики, когда пациенту предлагают один-единственный «волшебный» метод, не объясняя, что будет дальше. Здесь каждое обращение рассматривается в контексте стадии зависимости, общего состояния организма, психоэмоционального фона, семейной ситуации. Сначала специалисты снимают острые проявления: выход из запоя, детоксикация после употребления алкоголя, наркотиков или сочетаний, купирование абстиненции, коррекция давления, пульса, сна, тревоги. Затем формируется стабилизационный этап — подбор поддерживающих схем, работа с тягой, выравнивание эмоционального состояния. После этого при готовности пациента подключаются психотерапевтические и реабилитационные инструменты: мотивационные программы, работа с установками, триггерами, окружением. Важная особенность «Трезвый Шаг Раменское» — готовность объяснять семье и самому пациенту, зачем нужен каждый этап, какие цели у процедуры и какие результаты реально ожидать. Это снижает сопротивление, формирует доверие и делает путь не хаотичным, а управляемым.
Подробнее можно узнать тут – chastnaya-narkologicheskaya-klinika
loryx homepage – Smooth layout, content is engaging and encourages further exploration
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Получить дополнительные сведения – https://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom
Careers – User-friendly layout, organized content, and finding details is simple and fast.
Ключевым фактором при выборе центра становится квалификация специалистов. Лечение алкоголизма — это не только выведение из запоя и купирование абстинентного синдрома. Оно включает работу с мотивацией, тревожными состояниями, семейными конфликтами, нарушением сна и другими последствиями зависимости. Только команда, включающая наркологов, психотерапевтов и консультантов по аддиктивному поведению, способна охватить все аспекты проблемы.
Углубиться в тему – https://lechenie-alkogolizma-murmansk0.ru/lechenie-khronicheskogo-alkogolizma-marmansk/
Эти методы используются в комплексе и создают прочный фундамент для восстановления здоровья.
Изучить вопрос глубже – клиника лечения алкоголизма омск
Как подчёркивает специалист ФГБУ «НМИЦ психиатрии и наркологии», «без участия квалифицированной команды невозможно обеспечить комплексный подход к пациенту, особенно если речь идёт о длительном стаже употребления и осложнённой картине заболевания». Отсюда следует — изучение состава персонала должно быть одним из первых шагов.
Изучить вопрос глубже – http://lechenie-alkogolizma-murmansk0.ru
Выездной наркологический сервис «МедПоволжье Клиник» создан для случаев, когда важны скорость, тишина и клиническая точность. Мы проводим детоксикацию и снятие интоксикации на дому так, чтобы каждое действие имело цель, измеримый маркер и заранее оговорённое «окно переоценки». Вместо «сильной капельницы на всякий случай» — модульная схема: один симптом-кластер > один медицинский модуль > одна поведенческая опора (свет, звук, вода малыми глотками, дыхание 4–6). Такой подход снижает лекарственную нагрузку, ускоряет стабилизацию и позволяет видеть прогресс буквально по часам.
Подробнее тут – http://narkolog-na-dom-saratov0.ru
LearnAndPlan – Well-structured content, strategies are simple to grasp and implement.
Прежде чем принимать решение, важно изучить сайт клиники. В надёжных учреждениях размещена полная информация о врачах, их образовании и опыте работы. Кроме того, пациентам предлагается пройти предварительную консультацию — чаще всего она проводится анонимно и включает первичную диагностику. Это позволяет оценить профессионализм команды ещё до начала терапии.
Выяснить больше – https://narkologicheskaya-klinika-yaroslavl0.ru/narkologicheskaya-klinika-telefon-yaroslavl/
Korivo official page – Neat design, well-organized sections, and content is simple to browse.
Одним из самых востребованных направлений является вывод из запоя. Это процедура, направленная на очищение организма от этанола и продуктов его распада, восстановление водно-солевого баланса и нормализацию работы нервной системы. Врач проводит обследование, определяет степень интоксикации и подбирает состав капельницы. Уже через 30–60 минут после начала процедуры состояние пациента заметно улучшается.
Получить дополнительные сведения – наркологическая помощь на дому в волгограде
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Углубиться в тему – http://vyvod-iz-zapoia-v-volgograde17.ru/anonimnaya-narkologiya-vyvod-iz-zapoya-volgograd/
Partners – Professional appearance, clear layout, and content is organized efficiently.
В клинике обеспечивается безопасный вывод из запоя и очистка организма после употребления алкоголя, наркотиков или токсических сочетаний. Используются современные инфузионные схемы, витамины группы B, магний, гепатопротекторы по показаниям, противорвотные, мягкая коррекция сна и тревожности. Контроль давления, пульса, сатурации и поведения позволяет вовремя отметить любые осложнения и скорректировать терапию. Главная цель — не просто «прояснить голову», а защитить сердечно-сосудистую систему, мозг, печень, минимизировать риск делирия, судорог, аритмий и других острых состояний.
Узнать больше – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-cena-v-kolomne
bavlo page – Simple design, nothing overwhelming, and overall smooth site flow
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Углубиться в тему – наркологический вывод из запоя рязань
Лечение алкоголизма в Омске проводится с использованием современных методов, направленных на восстановление организма и психики пациента. Специалисты уделяют внимание как медицинским, так и психологическим аспектам, что позволяет достигать устойчивых результатов. Основой терапии является индивидуальный подход, благодаря которому каждая программа учитывает состояние здоровья и уровень зависимости.
Разобраться лучше – лечение алкоголизма
После детоксикации пациенту назначается медикаментозная терапия, направленная на стабилизацию работы нервной системы и снижение тяги к наркотикам. Медикаменты подбираются индивидуально, учитывая особенности состояния каждого пациента.
Углубиться в тему – лечение алкоголизма и наркомании центр в твери
1win pul yatırmaq https://1win5762.help
Ниже — ориентир для острых часов на дому. Это не жёсткий шаблон, а карта, где ясно: что делаем, чем измеряем, когда пересматриваем. При отсутствии отклика мы меняем один параметр (например, темп инфузии) и назначаем новое окно оценки, не «двигая» всё остальное.
Исследовать вопрос подробнее – нарколог на дом круглосуточно цены в саратове
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Узнать больше – вывод из запоя недорого
Наркологическая клиника — это не просто место, где пациенту оказывают медицинскую помощь. Это учреждение, где формируется стратегия полного восстановления, включающая не только физическое оздоровление, но и психоэмоциональную стабилизацию. В Ярославле работают как частные, так и государственные клиники, однако их подходы, уровень сервиса и состав команд могут существенно различаться. По данным Минздрава РФ, высокий процент успешных исходов наблюдается в тех учреждениях, где реализуется персонализированная модель лечения и постлечебной поддержки.
Изучить вопрос глубже – наркологические клиники алкоголизм ярославль.
Главная задача процедуры — быстрое выведение этанола и его метаболитов из организма, нормализация уровня электролитов, улучшение самочувствия и предотвращение осложнений. Лечение проводится как в клинике, так и на дому, что особенно удобно при тяжёлых состояниях, когда пациент не может самостоятельно добраться до медицинского учреждения.
Получить дополнительные сведения – https://vyvod-iz-zapoya-v-tyumeni17.ru/vyvod-iz-zapoya-v-staczionare-tyumen/
Диагностика в клинике «КузбассМед» проводится комплексно: используются лабораторные, инструментальные и психологические методы. Благодаря применению цифровых систем и алгоритмов обработки данных, результаты анализов доступны уже в течение первого часа. Оценка проводится по нескольким направлениям: токсикологический статус, состояние печени и почек, электролитный баланс, нейровегетативное состояние, когнитивные функции и уровень стресса. Это позволяет врачам составлять максимально точную картину заболевания и подбирать индивидуальные методы терапии.
Узнать больше – http://narkologicheskaya-klinika-novokuzneczk0.ru/narkologicheskij-czentr-novokuzneczk/https://narkologicheskaya-klinika-novokuzneczk0.ru
Комплексная наркологическая помощь объединяет несколько направлений, каждое из которых решает отдельную задачу восстановления организма и психики. Врачи используют индивидуальные схемы терапии, подбирая оптимальные препараты и психологические методики.
Подробнее – http://narkologicheskaya-pomoshh-v-volgograde17.ru
Learn about trust – Straightforward layout that supports confidence in the information provided.
Процесс детоксикации состоит из нескольких последовательных шагов, направленных на безопасное очищение организма. Ниже представлена таблица с описанием этапов, которые применяются в клинике «Трезвая Линия Волгоград».
Подробнее тут – вывод из запоя вызов город
Мы проверяем не «ощущения», а факты: частоту пульса в покое, вариабельность ритма к сумеркам, переносимость тёплой воды малыми глотками, минуты до сна и количество ночных пробуждений. Эти короткие метки позволяют тонко управлять темпом инфузии, очередностью модулей и «тихими» ритуалами вечернего времени без необоснованного усиления препаратов.
Разобраться лучше – http://narkolog-na-dom-saratov0.ru/narkolog-saratov-na-dom/https://narkolog-na-dom-saratov0.ru
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Получить больше информации – http://narkologicheskaya-klinika-kolomna2-10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne/
Наркологическая клиника «КоломнаМед Центр» — это место, куда можно обратиться в тот момент, когда домашние попытки контролировать алкоголь, наркотики, аптечные препараты или смесь всего сразу перестают работать, а жизнь превращается в постоянное «завтра начну с нуля». Здесь не обещают чудес за один день и не пугают диагнозами, а выстраивают понятный медицинский маршрут: детоксикация, стабилизация, реабилитация, поддержка семьи, профилактика срывов. Пациент получает помощь в защищённой, конфиденциальной среде, где всё организовано так, чтобы снизить тревогу и стыд, убрать хаос вокруг зависимости и дать человеку шанс вернуться к нормальной жизни без давления, угроз и токсичных «стимулов». Для родных клиника в Коломне — это опора: конкретный адрес, конкретная команда, чёткие сроки и понятные этапы, вместо бесконечных обещаний «он сам справится».
Получить дополнительные сведения – https://narkologicheskaya-klinika-kolomna10.ru/luchshie-narkologicheskie-kliniki-v-kolomne/
Эффективность лечения во многом зависит от квалификации врачей, участвующих в процессе. В наркологической клинике должны работать не только врачи-наркологи, но и психиатры, клинические психологи, специалисты по аддиктивному поведению, а также координаторы по социальной адаптации. Слаженное взаимодействие этих специалистов — залог того, что лечение будет не только медицински обоснованным, но и глубоко проработанным в психологическом плане.
Исследовать вопрос подробнее – chastnaya narkologicheskaya klinika jaroslavl’
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Подробнее тут – клиника кодирования от алкоголизма волгоград
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Детальнее – https://vyvod-iz-zapoya-v-ryazani17.ru/vyvod-iz-zapoya-na-domu-ryazan-czeny
Вывод из запоя в Раменском — это не просто «поставить капельницу и отпустить домой», а комплекс медицинских действий, от которых напрямую зависит здоровье, а иногда и жизнь человека. Длительное употребление алкоголя приводит к тяжёлой интоксикации, нарушению работы сердца, печени, головного мозга, сбоям давления, риску судорог, психозов и резких обострений хронических заболеваний. Попытки самостоятельно «сойти с дистанции» дома, с помощью случайных таблеток, седативных препаратов и новых доз алкоголя, часто только усугубляют состояние. Наркологическая клиника «РаменМед Трезвость» в Раменском выстраивает вывод из запоя как безопасный, контролируемый, поэтапный процесс: от экстренного купирования симптомов до формирования плана дальнейшего восстановления. Пациент получает помощь без осуждения, анонимно, с участием специалистов, которые берут на себя ответственность за каждое назначение и каждое действие. Для родственников это означает: больше не нужно гадать, чего бояться и что давать — есть конкретное место и команда, к которым можно обратиться сразу.
Ознакомиться с деталями – https://vyvod-iz-zapoya-ramenskoe10.ru/
В основе работы клиники лежит принцип: зависимость — это не просто привычка и не «слабость характера», а комплексное заболевание, которое требует последовательного лечения, а не случайной капельницы по вызову. «Трезвый Шаг Раменское» отказывается от практики, когда пациенту предлагают один-единственный «волшебный» метод, не объясняя, что будет дальше. Здесь каждое обращение рассматривается в контексте стадии зависимости, общего состояния организма, психоэмоционального фона, семейной ситуации. Сначала специалисты снимают острые проявления: выход из запоя, детоксикация после употребления алкоголя, наркотиков или сочетаний, купирование абстиненции, коррекция давления, пульса, сна, тревоги. Затем формируется стабилизационный этап — подбор поддерживающих схем, работа с тягой, выравнивание эмоционального состояния. После этого при готовности пациента подключаются психотерапевтические и реабилитационные инструменты: мотивационные программы, работа с установками, триггерами, окружением. Важная особенность «Трезвый Шаг Раменское» — готовность объяснять семье и самому пациенту, зачем нужен каждый этап, какие цели у процедуры и какие результаты реально ожидать. Это снижает сопротивление, формирует доверие и делает путь не хаотичным, а управляемым.
Разобраться лучше – http://
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Получить дополнительную информацию – https://kodirovanie-ot-alkogolizma-v-volgograde17.ru/
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Углубиться в тему – http://vivod-iz-zapoya-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-volgograd/
Нарколог на дом в Уфе — это услуга, которая позволяет получить квалифицированную медицинскую помощь при алкогольной или наркотической интоксикации без необходимости госпитализации. Такой формат особенно востребован при запойных состояниях, когда пациент не может самостоятельно посетить клинику. Врач приезжает по вызову в течение короткого времени, проводит обследование, устанавливает капельницу и обеспечивает безопасный вывод из состояния опьянения. Все процедуры выполняются анонимно, с соблюдением медицинской этики и конфиденциальности.
Получить больше информации – http://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom/https://narkolog-na-dom-v-ufe17.ru
Правильный подбор лекарственных средств позволяет не только уменьшить проявления синдрома отмены, но и стабилизировать эмоциональное состояние пациента, снижая риск срывов. Реабилитационные программы включают физиотерапию, спортивные занятия и коррекцию образа жизни, что способствует полноценному восстановлению организма.
Подробнее можно узнать тут – лечение наркомании диспансер в твери
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Выяснить больше – http://narkologicheskaya-pomoshh-v-volgograde17.ru
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Получить больше информации – вывод из запоя недорого в волгограде
В процессе лечения используются проверенные методики, которые в комплексе обеспечивают положительный эффект и снижают риск рецидива.
Подробнее можно узнать тут – лечение алкоголизма кодирование в омске
Саратов живёт в разных темпах: плотный центр, протяжные магистрали, мостовые переезды. Мы учитываем это в логистике: выездные бригады «СаратовМед Профи» движутся по немаркированным маршрутам, приезжают в гражданской одежде, формируют на месте «тихую сцену» и только затем начинают клиническую часть. Если на предзвонке звучат «красные флаги» — давящая боль в груди, выраженная одышка, спутанность, неукротимая рвота, судороги — организуем перевод в стационар без пауз: место резервируем заранее, передислокация проходит конфиденциально.
Изучить вопрос глубже – вывод из запоя вызов город
trusted finance site – Professional look combined with clear content makes browsing smooth.
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Получить больше информации – http://narkologicheskaya-klinika-kolomna10.ru
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Ознакомиться с деталями – врач вывод из запоя
Одним из ключевых преимуществ «КузбассМед» является современная материально-техническая база. В клинике задействованы устройства для точного мониторинга жизненных функций, автоматические инфузионные системы, экспресс-диагностические модули и оборудование для неотложной терапии. Врачи используют программируемые дозаторы, портативные анализаторы крови и аппараты для оценки дыхательной функции, что позволяет своевременно корректировать тактику лечения без потерь времени. Все процедуры соответствуют национальным стандартам безопасности и рекомендациям ВОЗ.
Получить дополнительные сведения – http://
Мы не используем универсальную «капельницу». Схема собирается из модулей под ведущие жалобы. Медицинские шаги всегда сочетаются с нефраком опорами — свет, тишина, вода малыми глотками, дыхание, — потому что среда усиливает действие препаратов и позволяет держать дозы ниже.
Подробнее тут – частный нарколог на дом саратов
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Узнать больше – вывод из запоя дешево
Мы не используем универсальную «капельницу». Схема собирается из модулей под ведущие жалобы. Медицинские шаги всегда сочетаются с нефраком опорами — свет, тишина, вода малыми глотками, дыхание, — потому что среда усиливает действие препаратов и позволяет держать дозы ниже.
Получить дополнительную информацию – нарколог на дом цены в саратове
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Получить дополнительные сведения – http://www.domen.ru
Важной частью реабилитации является социализация пациента, возвращение его к активной общественной жизни и формирование новых, здоровых привычек. Для этого в клинике организуются различные мероприятия и программы адаптации.
Разобраться лучше – лечение наркомании в стационаре
Во многих случаях пациент или его родственники не решаются сразу вызвать врача. Для таких ситуаций предусмотрена услуга онлайн-консультации. Она проводится через защищённую видеосвязь, при желании — анонимно. На связи — врач-нарколог или психиатр, который отвечает на вопросы, оценивает ситуацию по визуальным и вербальным признакам, рекомендует план действий. Консультация может стать отправной точкой для дальнейшего вызова врача на дом или записи в клинику. Это особенно удобно для родственников, которые не знают, как подступиться к проблеме и убедить человека в необходимости помощи.
Разобраться лучше – наркологическая помощь в твери
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Получить дополнительную информацию – adresa-narkologicheskih-klinik
Выбор клиники — задача не только медицинская, но и стратегическая. Учитывать нужно не только наличие лицензии, но и содержание программ, их гибкость, участие родственников в процессе, а также прозрачность взаимодействия с пациентом. Именно эти аспекты позволяют отличить профессиональное учреждение от формального.
Узнать больше – http://narkologicheskaya-klinika-yaroslavl0.ru
Выбор клиники — задача не только медицинская, но и стратегическая. Учитывать нужно не только наличие лицензии, но и содержание программ, их гибкость, участие родственников в процессе, а также прозрачность взаимодействия с пациентом. Именно эти аспекты позволяют отличить профессиональное учреждение от формального.
Выяснить больше – наркологическая клиника ярославль
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Детальнее – http://narkolog-na-dom-shchelkovo10.ru
Современные реалии требуют от медицинских учреждений гибкости, скорости и чуткости. Наркологическая помощь — одна из сфер, где промедление может стоить человеку здоровья или жизни. В наркологической клинике «ТверьМед» разработаны оперативные механизмы реагирования: выезд врача по адресу в течение 30 минут, круглосуточная поддержка и возможность получения онлайн-консультации, не покидая дом. Такой подход позволяет вовремя оказать помощь, даже если пациент отказывается ехать в стационар или не осознаёт всю серьёзность своего состояния.
Изучить вопрос глубже – https://narkologicheskaya-pomoshh-tver0.ru/narkolog-v-tveri-czeny
Комплексное применение этих методов позволяет значительно ускорить процесс восстановления и предотвратить осложнения.
Изучить вопрос глубже – narcologicheskaya-klinika-v-novokuzneczke17.ru/
Вывод из запоя — это не «волшебная капельница», а последовательная медицинская программа с чёткими целями и измеримыми маркерами. В наркологической клинике «СаратовМед Профи» маршрут строится по принципу управляемых окон: на каждом шаге команда преследует одну цель, меняет лишь один параметр и оценивает результат в заранее назначённый момент. Такой подход снижает лекарственную нагрузку, предотвращает «гонку дозировок» и делает динамику предсказуемой для пациента и близких. Конфиденциальность обеспечивается регламентом: немаркированные выезды, нейтральные формулировки в документах, «тихие» каналы связи, доступ к записям — строго по ролям.
Углубиться в тему – наркология вывод из запоя
Platform overview – Browsing feels intuitive thanks to the organized presentation.
Основные этапы обычно включают:
Получить дополнительную информацию – http://
В таблице представлены основные виды терапии, применяемые в клинике:
Подробнее – https://narcologicheskaya-klinika-v-novokuzneczke17.ru/
Капельница не просто устраняет симптомы похмелья — она восстанавливает внутренний баланс, снижает токсическую нагрузку и поддерживает работу жизненно важных органов. После процедуры пациент чувствует прилив сил, прояснение сознания и эмоциональную стабильность. Эффект закрепляется при соблюдении рекомендаций врача и отказе от алкоголя в последующие дни.
Подробнее можно узнать тут – https://vivod-iz-zapoya-v-volgograde17.ru/anonimnaya-narkologiya-vyvod-iz-zapoya-volgograd
Процесс включает несколько шагов:
Изучить вопрос глубже – вызвать нарколога на дом уфа
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Исследовать вопрос подробнее – кодирование от алкоголизма цены
Комплексная наркологическая помощь объединяет несколько направлений, каждое из которых решает отдельную задачу восстановления организма и психики. Врачи используют индивидуальные схемы терапии, подбирая оптимальные препараты и психологические методики.
Получить больше информации – http://narkologicheskaya-pomoshh-v-volgograde17.ru
Капельница — основной инструмент для очищения организма от продуктов распада этанола. Состав раствора подбирается строго индивидуально. В таблице приведены примеры комплексов, применяемых специалистами клиники «Трезвая Линия Волгоград».
Детальнее – https://vyvod-iz-zapoia-v-volgograde17.ru/vyvod-iz-zapoya-na-domu-volgograd
В клинике «Альтернатива» применяются современные методы терапии, включающие медикаментозное лечение, психотерапию и социальную реабилитацию.
Получить дополнительные сведения – наркологическая помощь
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Получить дополнительную информацию – http://narkologicheskaya-pomoshh-v-volgograde17.ru
Работа выездной службы построена так, чтобы для семьи всё было максимально понятно и предсказуемо. После звонка специалист не ограничивается общими фразами, а уточняет детали: сколько длится употребление, есть ли хронические болезни сердца, печени, почек, эндокринные нарушения, какие препараты и в каких дозах пациент уже получил, были ли в прошлом судороги, галлюцинации, тяжёлые реакции на лекарства. Это позволяет заранее оценить уровень риска и понять, подходит ли формат дома. По прибытии в Серпухове врач осматривает пациента, проверяет контакт и ориентировку, измеряет артериальное давление несколько раз, оценивает пульс, сатурацию, температуру, выраженность тремора, наличие болей, характер дыхания, степень обезвоживания. Далее формируется индивидуальная инфузионная схема: растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы, при необходимости — гепатопротекторы и мягкие антиоксидантные комплексы, противорвотные для контроля тошноты, щадящие анксиолитики для нормализации сна без грубой седации. Во время процедуры врач контролирует динамику, меняет скорость капельницы при необходимости, отслеживает реакцию на препараты и объясняет родным, какие изменения будут происходить по часам. По завершении визита пациент и родственники получают подробный план: режим, питьё, питание, чего нельзя, какие симптомы считаются тревожными, когда нужна повторная консультация или стационар. При выявлении опасных признаков вопрос о госпитализации поднимается честно и сразу, а не откладывается «до утра».
Изучить вопрос глубже – narkolog-na-dom-anonimno
Метод лечения
Выяснить больше – https://narkologicheskaya-pomoshh-novokuzneczk0.ru/narkologicheskaya-klinika-novokuzneczk
Наркологическая клиника «Трезвый Шаг Раменское» — это место, где острые кризисы, многолетние запои и повторяющиеся срывы перестают быть бесконечным кругом, в котором семья остаётся один на один с проблемой. Здесь выстроена система помощи людям с алкогольной и наркотической зависимостью, а также полизависимостями, включая злоупотребление аптечными препаратами. В клинике в Раменском сочетаются круглосуточное наблюдение, профессиональная детоксикация, медикаментозная поддержка, психотерапевтические программы и сопровождение семьи. Важные принципы — безопасность, анонимность, уважение к пациенту и честное объяснение каждого шага лечения. Ни агрессивного давления, ни обещаний «чуда за один день» — вместо этого поэтапный подход, который даёт реальный шанс стабилизировать состояние, снизить тягу и выйти из разрушительного сценария под контролем специалистов. Для близких это означает понятный маршрут: куда обратиться, что будут делать с пациентом, какие риски учтут и как клиника «Трезвый Шаг Раменское» останется на связи после острого периода.
Получить дополнительную информацию – http://narkologicheskaya-klinika-ramenskoe10.ru
Мы проверяем не «ощущения», а факты: частоту пульса в покое, вариабельность ритма к сумеркам, переносимость тёплой воды малыми глотками, минуты до сна и количество ночных пробуждений. Эти короткие метки позволяют тонко управлять темпом инфузии, очередностью модулей и «тихими» ритуалами вечернего времени без необоснованного усиления препаратов.
Подробнее можно узнать тут – частный нарколог на дом
оптимизация и seo продвижение сайтов москва оптимизация и seo продвижение сайтов москва .
Использование автоматизированных систем дозирования позволяет точно подобрать необходимое количество медикаментов, минимизируя риск передозировки и побочных эффектов. Постоянный мониторинг жизненно важных показателей дает возможность врачу корректировать схему лечения в режиме реального времени, что повышает безопасность и эффективность процедуры.
Подробнее тут – http://vyvod-iz-zapoya-yaroslavl0.ru/
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Детальнее – https://kodirovanie-ot-alkogolizma-v-volgograde17.ru/
QuickUlvor – Smooth browsing, responsive pages, and checkout process straightforward.
Сразу после вызова нарколог прибывает на дом для проведения детального осмотра. На этом этапе специалист измеряет жизненно важные показатели, собирает анамнез и оценивает степень алкогольной интоксикации, что является основой для составления персонального плана лечения.
Узнать больше – https://vyvod-iz-zapoya-tula0.ru/vyvod-iz-zapoya-czena-tula
Эта последовательность обеспечивает полное восстановление организма, формирование мотивации к трезвому образу жизни и снижение риска рецидивов.
Разобраться лучше – https://narcologicheskaya-klinika-v-krasnoyarske17.ru/krasnoyarsk-narkologicheskij-czentr
seo partner program seo partner program .
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Исследовать вопрос подробнее – вывод из запоя на дому круглосуточно в рязани
Наркологическая клиника «КоломнаМед Центр» — это место, куда можно обратиться в тот момент, когда домашние попытки контролировать алкоголь, наркотики, аптечные препараты или смесь всего сразу перестают работать, а жизнь превращается в постоянное «завтра начну с нуля». Здесь не обещают чудес за один день и не пугают диагнозами, а выстраивают понятный медицинский маршрут: детоксикация, стабилизация, реабилитация, поддержка семьи, профилактика срывов. Пациент получает помощь в защищённой, конфиденциальной среде, где всё организовано так, чтобы снизить тревогу и стыд, убрать хаос вокруг зависимости и дать человеку шанс вернуться к нормальной жизни без давления, угроз и токсичных «стимулов». Для родных клиника в Коломне — это опора: конкретный адрес, конкретная команда, чёткие сроки и понятные этапы, вместо бесконечных обещаний «он сам справится».
Подробнее можно узнать тут – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-cena-v-kolomne/
Ниже — ориентир для острых часов на дому. Это не жёсткий шаблон, а карта, где ясно: что делаем, чем измеряем, когда пересматриваем. При отсутствии отклика мы меняем один параметр (например, темп инфузии) и назначаем новое окно оценки, не «двигая» всё остальное.
Разобраться лучше – нарколог на дом вывод в саратове
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Изучить вопрос глубже – наркология вывод из запоя в рязани
Запой – это опасное состояние, при котором организм подвергается значительной токсической нагрузке, а длительное злоупотребление алкоголем приводит к нарушению работы внутренних органов и ухудшению общего самочувствия. В Ярославле качественная наркологическая помощь на дому становится спасением для пациентов, нуждающихся в оперативной детоксикации и стабилизации состояния. Такой формат лечения позволяет начать терапию в комфортной обстановке, сохраняя конфиденциальность и минимизируя стресс, связанный с посещением стационара.
Получить дополнительные сведения – вывод из запоя на дому
Лечение зависимости в наркологической клинике проводится поэтапно. Это обеспечивает постепенное восстановление организма и исключает риск осложнений. Каждый этап направлен на устранение конкретных нарушений, вызванных употреблением психоактивных веществ.
Получить дополнительные сведения – наркологическая клиника вывод из запоя
Клиника в Коломне ориентирована на полный цикл помощи: от экстренных состояний до длительного сопровождения. Здесь важна не только медицинская составляющая, но и человеческая: уважение, конфиденциальность, отсутствие стигмы. Ниже — ключевые направления, которые выстраиваются в единую систему лечения, а не существуют по отдельности.
Подробнее можно узнать тут – заказать обратный звонок наркологическая клиника
Современные реалии требуют от медицинских учреждений гибкости, скорости и чуткости. Наркологическая помощь — одна из сфер, где промедление может стоить человеку здоровья или жизни. В наркологической клинике «ТверьМед» разработаны оперативные механизмы реагирования: выезд врача по адресу в течение 30 минут, круглосуточная поддержка и возможность получения онлайн-консультации, не покидая дом. Такой подход позволяет вовремя оказать помощь, даже если пациент отказывается ехать в стационар или не осознаёт всю серьёзность своего состояния.
Выяснить больше – платная наркологическая скорая помощь
Такая комплексность обеспечивает воздействие на физические, психологические и социальные факторы зависимости.
Получить больше информации – реабилитационный центр лечение алкоголизма омск
В этих ситуациях выезд нарколога на дом позволяет вовремя скорректировать состояние, а при выявлении опасных признаков — не теряя времени, направить пациента в стационар. Это управляемый маршрут вместо хаотичных решений в последний момент.
Подробнее тут – https://narkolog-na-dom-dolgoprudnij10.ru/
Выбор формата — это не вкусовщина, а баланс безопасности в конкретной клинической картине. Дом уместен, если контакт сохранён, рвота эпизодическая, давление и пульс без резких «качелей», тремор контролируемый, в квартире можно обеспечить тишину и присутствие взрослого, готового наблюдать первые 6–8 часов. Тогда выездная бригада работает на месте и выстраивает «мягкий» маршрут, где сон собирается без агрессивной седации, а инфузии идут с шаговой корректировкой темпа. Стационар предпочтителен при длительном эпизоде (3–5 суток и более), неукротимой рвоте, выраженной слабости, шаткости походки, признаках предделирия/делирия, судорожной готовности, а также у пожилых пациентов и при сочетанных диагнозах — ИБС, гипертония, диабет, хронические болезни печени/почек, неврология. Преимущество отделения — приборный мониторинг, лабораторные опции по показаниям, ночная команда и среда, где исключены лишние раздражители: это снижает «цену ошибки» и делает результат устойчивым, а не разовым «прояснением».
Углубиться в тему – вывод из запоя с выездом электросталь
В таблице представлены основные виды терапии, применяемые в клинике:
Получить больше информации – наркологическая клиника цены в новокузнецке
1win aviator oyunu 1win aviator oyunu
professional bond portal – Smooth navigation and clear content give a reliable impression.
Услуга «нарколог на дом в Долгопрудном» от клиники «МедТрезвие Долгопрудный» создана для ситуаций, когда важно действовать быстро, аккуратно и без лишнего шума. Запой, тяжёлое похмелье, срыв после ремиссии, злоупотребление медикаментами или смесью алкоголя с препаратами — всё это не терпит откладывания и самодеятельности. Вызов врача на дом позволяет получить профессиональную помощь без госпитализации, когда состояние пациента ещё позволяет лечить его в привычной обстановке. Нарколог приезжает с полностью укомплектованным набором препаратов и расходников, проводит осмотр, подбирает капельницы по клиническим показаниям, контролирует реакцию, даёт подробные рекомендации на ближайшие дни и при необходимости предлагает дальнейший маршрут: повторный выезд, амбулаторное наблюдение или стационар клиники. Конфиденциальность соблюдается строго: без обсуждений с соседями, без регистрации по месту работы, без унизительных формальностей — только медицинская помощь, ориентированная на безопасность и результат.
Получить дополнительные сведения – narkolog-na-dom-narkologicheskaya-klinika
Как отмечает руководитель клинико-диагностического отдела ФГБУ «Национальный центр наркологии», «участие в терапии нескольких специалистов разных направлений позволяет учитывать не только симптомы, но и глубинные причины зависимости». Именно такой подход снижает риск рецидивов и повышает эффективность лечения.
Углубиться в тему – частная наркологическая клиника в ярославле
Каждый этап играет важную роль и обеспечивает пациенту необходимую поддержку на пути к трезвой жизни.
Подробнее можно узнать тут – https://lechenie-alkogolizma-omsk0.ru/omsk-lechenie-alkogolizma/
Лечение наркомании в Твери представляет собой сложный и многоэтапный процесс, направленный на полное восстановление здоровья и социальной адаптации пациентов, страдающих от зависимости. В наркологической клинике «Ренессанс» применяется комплексный подход, который учитывает как физиологические, так и психологические аспекты заболевания, что обеспечивает максимальную эффективность терапии.
Получить дополнительную информацию – https://lechenie-narkomanii-tver0.ru/klinika-lechenie-narkomanii-v-tveri
This anti-wrinkle lotion is developed with algae and other plant essences to
restore the skin with much-needed wetness.
Ключевым фактором при выборе центра становится квалификация специалистов. Лечение алкоголизма — это не только выведение из запоя и купирование абстинентного синдрома. Оно включает работу с мотивацией, тревожными состояниями, семейными конфликтами, нарушением сна и другими последствиями зависимости. Только команда, включающая наркологов, психотерапевтов и консультантов по аддиктивному поведению, способна охватить все аспекты проблемы.
Подробнее можно узнать тут – лечение алкоголизма мурманск.
Мы проверяем не «ощущения», а факты: частоту пульса в покое, вариабельность ритма к сумеркам, переносимость тёплой воды малыми глотками, минуты до сна и количество ночных пробуждений. Эти короткие метки позволяют тонко управлять темпом инфузии, очередностью модулей и «тихими» ритуалами вечернего времени без необоснованного усиления препаратов.
Детальнее – https://narkolog-na-dom-saratov0.ru/
После детоксикации пациенту назначается медикаментозная терапия, направленная на стабилизацию работы нервной системы и снижение тяги к наркотикам. Медикаменты подбираются индивидуально, учитывая особенности состояния каждого пациента.
Подробнее – https://lechenie-narkomanii-tver0.ru/klinika-lechenie-narkomanii-v-tveri
Метод лечения
Получить дополнительную информацию – скорая наркологическая помощь на дому новокузнецк
Вывод из запоя — это не «волшебная капельница», а последовательная медицинская программа с чёткими целями и измеримыми маркерами. В наркологической клинике «СаратовМед Профи» маршрут строится по принципу управляемых окон: на каждом шаге команда преследует одну цель, меняет лишь один параметр и оценивает результат в заранее назначённый момент. Такой подход снижает лекарственную нагрузку, предотвращает «гонку дозировок» и делает динамику предсказуемой для пациента и близких. Конфиденциальность обеспечивается регламентом: немаркированные выезды, нейтральные формулировки в документах, «тихие» каналы связи, доступ к записям — строго по ролям.
Получить дополнительную информацию – вывод из запоя цена
Наркологическая клиника — это не просто место, где пациенту оказывают медицинскую помощь. Это учреждение, где формируется стратегия полного восстановления, включающая не только физическое оздоровление, но и психоэмоциональную стабилизацию. В Ярославле работают как частные, так и государственные клиники, однако их подходы, уровень сервиса и состав команд могут существенно различаться. По данным Минздрава РФ, высокий процент успешных исходов наблюдается в тех учреждениях, где реализуется персонализированная модель лечения и постлечебной поддержки.
Разобраться лучше – частная наркологическая клиника ярославль
Благодаря комплексному подходу достигается не только снятие симптомов, но и долгосрочная стабилизация состояния пациента.
Получить больше информации – https://narkologicheskaya-pomoshh-v-volgograde17.ru/narkolog-psikholog-volgograd/
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Углубиться в тему – http://vyvod-iz-zapoia-v-volgograde17.ru/
Для достижения стойкой ремиссии применяются современные и безопасные методики, которые подбираются индивидуально для каждого пациента.
Разобраться лучше – клиника лечения алкоголизма омск
Чтобы исключить суету и случайные усиления, первые часы делим на небольшие «окна»: цель — действие — маркер — критерий перехода. Если отклика нет, корректируется один элемент — темп инфузии, очередность модулей или поведенческий якорь — и назначается новая точка оценки.
Разобраться лучше – https://vyvod-iz-zapoya-saratov0.ru/vyvod-iz-zapoya-saratov-staczionar
Стационар наркологической клиники в Раменском ориентирован на тех пациентов, для которых домашние попытки лечения объективно опасны. Это длительные запои, пожилой возраст, выраженные сердечно-сосудистые патологии, заболевания печени и почек, риск делирия, судорог, тяжёлая абстиненция, полинаркомания. В стационаре «Трезвый Шаг Раменское» организовано круглосуточное наблюдение: контролируются давление, пульс, сатурация, поведение, динамика симптомов, проводится своевременная коррекция терапии. Пациент находится в спокойной, защищённой обстановке, где ему не нужно скрывать своё состояние или оправдываться — задача команды не судить, а стабилизировать и лечить. Комфортные палаты, медицинский персонал рядом, продуманное питание, конфиденциальность — всё это снижает уровень страха у пациента и напряжение у родственников. Важный момент: стационар не подаётся как «камерный режим», а как безопасная зона восстановления, где можно пройти самый тяжёлый участок пути с максимальной защитой.
Разобраться лучше – klinika-narkologicheskoj-zavisimosti
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Разобраться лучше – http://
Диспетчер уточняет адрес в Электростали, длительность эпизода, текущие препараты и дозы, аллергии, сопутствующие заболевания, последние значения давления/пульса. Это экономит 15–20 минут на месте и позволяет заранее исключить опасные взаимодействия.
Получить больше информации – вывод из запоя на дому цена
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Детальнее – вывод из запоя цена
Для оказания полноценной помощи вне стен клиники специалисты «ТверьМед» используют портативные устройства: инфузоматы, ЭКГ-мониторы, глюкометры, пульсоксиметры, небулайзеры и наборы медикаментов. Все врачи обучены работе в полевых условиях и готовы к экстренным ситуациям. Отдельное внимание уделяется стерильности и безопасности: используются одноразовые расходники, врач носит маску, перчатки и защитный халат. При необходимости на выезд направляется параллельно медсестра или ассистент с расширенным функционалом.
Углубиться в тему – http://narkologicheskaya-pomoshh-tver0.ru/
Одним из самых востребованных направлений является вывод из запоя. Это процедура, направленная на очищение организма от этанола и продуктов его распада, восстановление водно-солевого баланса и нормализацию работы нервной системы. Врач проводит обследование, определяет степень интоксикации и подбирает состав капельницы. Уже через 30–60 минут после начала процедуры состояние пациента заметно улучшается.
Исследовать вопрос подробнее – экстренная наркологическая помощь в волгограде
Диагностика в клинике «КузбассМед» проводится комплексно: используются лабораторные, инструментальные и психологические методы. Благодаря применению цифровых систем и алгоритмов обработки данных, результаты анализов доступны уже в течение первого часа. Оценка проводится по нескольким направлениям: токсикологический статус, состояние печени и почек, электролитный баланс, нейровегетативное состояние, когнитивные функции и уровень стресса. Это позволяет врачам составлять максимально точную картину заболевания и подбирать индивидуальные методы терапии.
Изучить вопрос глубже – http://narkologicheskaya-klinika-novokuzneczk0.ru
На этом этапе специалист уточняет, сколько времени продолжается запой, какие основные симптомы наблюдаются, и если имеются, то какие хронические заболевания могут влиять на течение терапии. Точный анализ этих данных позволяет сформировать персонализированную стратегию лечения, которая будет максимально адаптирована к состоянию пациента и его потребностям.
Изучить вопрос глубже – http://vyvod-iz-zapoya-yaroslavl0.ru/
Каждый этап проходит под контролем врачей-наркологов и психотерапевтов, что гарантирует эффективность и безопасность лечения.
Получить дополнительные сведения – наркологическая клиника лечение алкоголизма новокузнецк
Core resource link – An uncluttered site that explains its purpose effectively.
Эта последовательность обеспечивает полное восстановление организма, формирование мотивации к трезвому образу жизни и снижение риска рецидивов.
Углубиться в тему – анонимная наркологическая клиника красноярск
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Ознакомиться с деталями – сколько стоит капельница на дому от запоя в волгограде
Мы проверяем не «ощущения», а факты: частоту пульса в покое, вариабельность ритма к сумеркам, переносимость тёплой воды малыми глотками, минуты до сна и количество ночных пробуждений. Эти короткие метки позволяют тонко управлять темпом инфузии, очередностью модулей и «тихими» ритуалами вечернего времени без необоснованного усиления препаратов.
Углубиться в тему – помощь нарколога на дому в саратове
Капельница от запоя в Волгограде — это эффективный способ быстро восстановить организм после длительного употребления алкоголя. Процедура проводится врачом-наркологом и направлена на выведение токсинов, нормализацию обмена веществ и стабилизацию работы нервной системы. Инфузионная терапия помогает устранить головную боль, слабость, тошноту, восстановить сон и аппетит. Благодаря внутривенному введению препаратов эффект наступает уже через 20–30 минут после начала процедуры.
Ознакомиться с деталями – http://kapelnicza-ot-zapoya-v-volgograde17.ru
Алгоритм организован так, чтобы каждое действие было логичным и предсказуемым. После обращения по телефону врач заранее получает краткую клиническую картину и подбирает набор препаратов с учётом состояния пациента. По прибытии в Долгопрудном нарколог не ставит капельницу «по шаблону», а начинает с осмотра: измеряет давление, пульс, сатурацию, температуру, оценивает тремор, уровень сознания, ориентировку, степень обезвоживания, частоту рвоты, дыхание, возможные боли в груди или животе, обращает внимание на поведение и эмоциональное состояние. Если по результатам осмотра подтверждается, что дом — безопасный формат, подбирается индивидуальная инфузионная схема: объём, скорость введения и препараты зависят от возраста, длительности запоя, сопутствующих болезней и уже использованных медикаментов. Врач остаётся на адресе до завершения основных процедур, контролирует реакцию, при необходимости корректирует план и чётко проговаривает, как пациент должен проводить ближайшие 24–72 часа. Если по ходу работы выявляются признаки угрозы (начальные симптомы делирия, тяжёлые аритмии, нестабильное давление, выраженная дезориентация), нарколог рекомендует стационар и помогает семье организовать перевод. Это честный и безопасный подход: не любой ценой «отработать выезд», а сделать так, чтобы помощь действительно снижала риски.
Ознакомиться с деталями – vrach-narkolog-na-dom
Наркологическая клиника — это не просто место, где пациенту оказывают медицинскую помощь. Это учреждение, где формируется стратегия полного восстановления, включающая не только физическое оздоровление, но и психоэмоциональную стабилизацию. В Ярославле работают как частные, так и государственные клиники, однако их подходы, уровень сервиса и состав команд могут существенно различаться. По данным Минздрава РФ, высокий процент успешных исходов наблюдается в тех учреждениях, где реализуется персонализированная модель лечения и постлечебной поддержки.
Ознакомиться с деталями – http://narkologicheskaya-klinika-yaroslavl0.ru/
Вывод из запоя в Рязани — это профессиональная медицинская процедура, направленная на очищение организма от токсинов, восстановление нормального самочувствия и предотвращение осложнений после длительного употребления алкоголя. В специализированных клиниках города лечение проводится с использованием современных методов детоксикации и под контролем опытных врачей-наркологов. Такой подход позволяет быстро и безопасно стабилизировать состояние пациента, устранить физическую зависимость и подготовить организм к дальнейшему восстановлению.
Подробнее – вывод из запоя недорого
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Получить больше информации – http://www.domen.ru
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Ознакомиться с деталями – zakazat-obratnyj-zvonok-narkologicheskaya-klinika
Раннее обращение к специалистам позволяет провести качественную диагностику, подобрать адекватное лечение и обеспечить комплексную поддержку пациента.
Подробнее тут – нарколог наркологическая помощь новокузнецк
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Узнать больше – анонимный вывод из запоя
QuvexDirect – Smooth site performance, well-structured content, and clicking links was simple.
Наркологическая помощь в Волгограде предназначена для людей, столкнувшихся с проблемами алкогольной или наркотической зависимости. Современный подход к лечению основан на сочетании медицинских, психологических и социальных методов, направленных на полное восстановление пациента. Врачи-наркологи применяют безопасные схемы детоксикации, эффективные медикаменты и программы психотерапевтической поддержки, позволяющие достичь устойчивой ремиссии и вернуть пациента к нормальной жизни.
Углубиться в тему – http://narkologicheskaya-pomoshh-v-volgograde17.ru
«РаменМед Трезвость» предлагает несколько форматов помощи, но выбор всегда делается из соображений безопасности, а не удобства картинки. Стационарный вывод из запоя подходит в ситуациях, когда запой длится несколько дней или недель, есть скачки давления, проблемы с сердцем, печени, сахарный диабет, неврологические заболевания, эпизоды судорог или делирия в анамнезе, возраст старше 50–55 лет, выраженная слабость, тахикардия, невозможность пить воду, угрозы психозов. В стационаре пациент находится под наблюдением круглосуточно: контролируются жизненные показатели, вовремя корректируется терапия, есть возможность экстренно отреагировать на осложнения. Это гарантированно безопаснее, чем оставлять тяжёлого человека дома под наблюдением уставших родственников.
Выяснить больше – вывод из запоя выездом на дом
Современные реалии требуют от медицинских учреждений гибкости, скорости и чуткости. Наркологическая помощь — одна из сфер, где промедление может стоить человеку здоровья или жизни. В наркологической клинике «ТверьМед» разработаны оперативные механизмы реагирования: выезд врача по адресу в течение 30 минут, круглосуточная поддержка и возможность получения онлайн-консультации, не покидая дом. Такой подход позволяет вовремя оказать помощь, даже если пациент отказывается ехать в стационар или не осознаёт всю серьёзность своего состояния.
Разобраться лучше – наркологическая помощь в твери
Каждый этап проходит под контролем врачей-наркологов и психотерапевтов, что гарантирует эффективность и безопасность лечения.
Подробнее тут – наркологическая клиника лечение алкоголизма новокузнецк
Своевременное обращение в клинику снижает риск развития алкогольного психоза, судорог и тяжёлых осложнений со стороны сердца и печени.
Получить дополнительные сведения – нарколог вывод из запоя рязань
Важное отличие клиники — отказ от примитивной схемы «капельница — домой — дальше сам». Такой формат даёт кратковременное облегчение, но не решает ни причин, ни структуры зависимости. «КоломнаМед Центр» выстраивает ступенчатый подход. Первый шаг — безопасная детоксикация: снятие абстиненции, коррекция водно-электролитного баланса, поддержка сердечно-сосудистой системы, печени, нервной системы, нормализация сна. Второй шаг — стабилизация: оценка психического состояния, выявление тревожных, депрессивных и панических симптомов, подбор поддерживающих схем, которые помогают не сорваться сразу после выхода из острых проявлений. Третий шаг — реабилитация и мотивация: психотерапевтическая работа, групповые и индивидуальные форматы, обучение навыкам трезвой жизни, работа с триггерами, укрепление внутренней мотивации. Четвёртый шаг — постреабилитационная поддержка: контрольные приёмы, дистанционные консультации, помощь в профилактике срывов. Такой комплексный путь не ломает пациента, а возвращает ему контроль: не через страх, а через понимание, структуру и реальные инструменты.
Углубиться в тему – http://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne/https://narkologicheskaya-klinika-kolomna10.ru
поисковое продвижение москва профессиональное продвижение сайтов prodvizhenie-sajtov-v-moskve115.ru .
Капельница не просто устраняет симптомы похмелья — она восстанавливает внутренний баланс, снижает токсическую нагрузку и поддерживает работу жизненно важных органов. После процедуры пациент чувствует прилив сил, прояснение сознания и эмоциональную стабильность. Эффект закрепляется при соблюдении рекомендаций врача и отказе от алкоголя в последующие дни.
Подробнее тут – http://vivod-iz-zapoya-v-volgograde17.ru
Одним из основных этапов вывода из запоя является медикаментозная детоксикация. Современные препараты вводятся капельничным методом, что обеспечивает быстрое снижение уровня алкоголя и токсинов в крови. Это позволяет восстановить нормальный обмен веществ и нормализовать работу жизненно важных органов, таких как печень, почки и сердце. Такой подход помогает не только стабилизировать состояние пациента, но и уменьшить риск развития осложнений.
Выяснить больше – https://vyvod-iz-zapoya-yaroslavl0.ru/vyvod-iz-zapoya-czena-yaroslavl
Клиника в Красноярске придерживается комплексного подхода, при котором сочетаются медикаментозные и психотерапевтические методы. Такой подход позволяет воздействовать не только на физическую, но и на психологическую зависимость. Каждый пациент проходит детальное обследование, после чего врач-нарколог составляет индивидуальный план лечения с учётом стадии заболевания, состояния организма и наличия сопутствующих проблем со здоровьем.
Выяснить больше – наркологические клиники алкоголизм в красноярске
seo аудит веб сайта seo аудит веб сайта .
Даже при наличии комфортных условий и современных медикаментов эффективность будет минимальной, если пациент не получает психологическую помощь. У многих зависимость сопровождается тревожными или депрессивными состояниями, травматическим опытом или сложными семейными отношениями. Без проработки этих аспектов высокий риск того, что после выписки произойдёт рецидив.
Разобраться лучше – наркологическая клиника в ярославле
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Детальнее – https://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom/
online investment page – Clear wording and well-structured content make understanding easy.
Даже телефонный разговор с клиникой может многое сказать о её подходе. Если вам предлагают типовое лечение без уточнения подробностей или избегают вопросов о составе команды, это тревожный сигнал. Серьёзные учреждения в Мурманске обязательно предложат предварительную консультацию, зададут уточняющие вопросы и расскажут, как строится программа помощи.
Получить дополнительные сведения – https://lechenie-alkogolizma-murmansk0.ru/
Алгоритм организован так, чтобы каждое действие было логичным и предсказуемым. После обращения по телефону врач заранее получает краткую клиническую картину и подбирает набор препаратов с учётом состояния пациента. По прибытии в Долгопрудном нарколог не ставит капельницу «по шаблону», а начинает с осмотра: измеряет давление, пульс, сатурацию, температуру, оценивает тремор, уровень сознания, ориентировку, степень обезвоживания, частоту рвоты, дыхание, возможные боли в груди или животе, обращает внимание на поведение и эмоциональное состояние. Если по результатам осмотра подтверждается, что дом — безопасный формат, подбирается индивидуальная инфузионная схема: объём, скорость введения и препараты зависят от возраста, длительности запоя, сопутствующих болезней и уже использованных медикаментов. Врач остаётся на адресе до завершения основных процедур, контролирует реакцию, при необходимости корректирует план и чётко проговаривает, как пациент должен проводить ближайшие 24–72 часа. Если по ходу работы выявляются признаки угрозы (начальные симптомы делирия, тяжёлые аритмии, нестабильное давление, выраженная дезориентация), нарколог рекомендует стационар и помогает семье организовать перевод. Это честный и безопасный подход: не любой ценой «отработать выезд», а сделать так, чтобы помощь действительно снижала риски.
Детальнее – врач нарколог на дом
Правильный подбор лекарственных средств позволяет не только уменьшить проявления синдрома отмены, но и стабилизировать эмоциональное состояние пациента, снижая риск срывов. Реабилитационные программы включают физиотерапию, спортивные занятия и коррекцию образа жизни, что способствует полноценному восстановлению организма.
Детальнее – лечение наркомании и алкоголизма тверь
Для понимания ключевых компонентов лечения ниже представлена таблица, в которой систематизированы основные методы и их назначение.
Исследовать вопрос подробнее – анонимная наркологическая помощь в новокузнецке
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Углубиться в тему – вывод из запоя недорого волгоград
Чтобы исключить суету и случайные усиления, первые часы делим на небольшие «окна»: цель — действие — маркер — критерий перехода. Если отклика нет, корректируется один элемент — темп инфузии, очередность модулей или поведенческий якорь — и назначается новая точка оценки.
Подробнее тут – вывод из запоя вызов на дом
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Детальнее – вызов на дом капельницы от запоя волгоград
В Волгограде сформирована система оказания наркологической помощи, включающая круглосуточные выезды специалистов, амбулаторное лечение, стационарные программы и реабилитацию. Такой подход позволяет охватить все категории пациентов — от тех, кто нуждается в экстренной помощи, до тех, кто готов пройти полный курс терапии. Независимо от формы оказания услуг, лечение проводится конфиденциально и в соответствии с медицинскими стандартами.
Получить дополнительные сведения – наркологическая помощь в волгограде
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Исследовать вопрос подробнее – http://vyvod-iz-zapoya-v-ryazani17.ru/
Наркологическая клиника «КоломнаМед Центр» — это место, куда можно обратиться в тот момент, когда домашние попытки контролировать алкоголь, наркотики, аптечные препараты или смесь всего сразу перестают работать, а жизнь превращается в постоянное «завтра начну с нуля». Здесь не обещают чудес за один день и не пугают диагнозами, а выстраивают понятный медицинский маршрут: детоксикация, стабилизация, реабилитация, поддержка семьи, профилактика срывов. Пациент получает помощь в защищённой, конфиденциальной среде, где всё организовано так, чтобы снизить тревогу и стыд, убрать хаос вокруг зависимости и дать человеку шанс вернуться к нормальной жизни без давления, угроз и токсичных «стимулов». Для родных клиника в Коломне — это опора: конкретный адрес, конкретная команда, чёткие сроки и понятные этапы, вместо бесконечных обещаний «он сам справится».
Углубиться в тему – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-cena-v-kolomne/
Психологическая поддержка играет ключевую роль в лечении наркомании в Твери. В клинике «Ренессанс» применяются различные методы психотерапии, включая когнитивно-поведенческую терапию, групповые и семейные сессии, арт-терапию. Эти методы помогают осознать причины зависимости, развить навыки преодоления стрессов и поддержать мотивацию к выздоровлению.
Получить больше информации – наркологическое лечение наркомания тверь
Стационар наркологической клиники в Раменском ориентирован на тех пациентов, для которых домашние попытки лечения объективно опасны. Это длительные запои, пожилой возраст, выраженные сердечно-сосудистые патологии, заболевания печени и почек, риск делирия, судорог, тяжёлая абстиненция, полинаркомания. В стационаре «Трезвый Шаг Раменское» организовано круглосуточное наблюдение: контролируются давление, пульс, сатурация, поведение, динамика симптомов, проводится своевременная коррекция терапии. Пациент находится в спокойной, защищённой обстановке, где ему не нужно скрывать своё состояние или оправдываться — задача команды не судить, а стабилизировать и лечить. Комфортные палаты, медицинский персонал рядом, продуманное питание, конфиденциальность — всё это снижает уровень страха у пациента и напряжение у родственников. Важный момент: стационар не подаётся как «камерный режим», а как безопасная зона восстановления, где можно пройти самый тяжёлый участок пути с максимальной защитой.
Получить дополнительную информацию – https://narkologicheskaya-klinika-ramenskoe10.ru/narkologicheskaya-klinika-otzyvy-v-ramenskom/
Когда острые угрозы исключены, программа стартует дома. Пациент получает понятную карту действий, близкие — короткие окна обратной связи, врач — чистую «картинку» для тонкой настройки. Мы просим сообщать факты, а не эмоции: минуты до засыпания, число пробуждений, объём тёплой воды малыми глотками, пульс к вечеру, переносимость мягкой пищи, ясность головы утром.
Исследовать вопрос подробнее – вывод из запоя на дому цена в саратове
Первый шаг в лечении — это тщательный осмотр специалиста. Наряду с измерением жизненно важных показателей (пульс, артериальное давление, температура) врач проводит сбор анамнеза, выясняя длительность запоя, тип употребляемого алкоголя и наличие сопутствующих заболеваний. Эти данные помогают оценить степень интоксикации и подобрать индивидуальный план терапии, что является ключевым для дальнейшей эффективной детоксикации.
Ознакомиться с деталями – http://vyvod-iz-zapoya-yaroslavl0.ru
Для иллюстрации эффективности методов представлена таблица с примерами процедур и их воздействием:
Подробнее можно узнать тут – наркологическая клиника наркологический центр в красноярске
Стационар наркологической клиники в Раменском ориентирован на тех пациентов, для которых домашние попытки лечения объективно опасны. Это длительные запои, пожилой возраст, выраженные сердечно-сосудистые патологии, заболевания печени и почек, риск делирия, судорог, тяжёлая абстиненция, полинаркомания. В стационаре «Трезвый Шаг Раменское» организовано круглосуточное наблюдение: контролируются давление, пульс, сатурация, поведение, динамика симптомов, проводится своевременная коррекция терапии. Пациент находится в спокойной, защищённой обстановке, где ему не нужно скрывать своё состояние или оправдываться — задача команды не судить, а стабилизировать и лечить. Комфортные палаты, медицинский персонал рядом, продуманное питание, конфиденциальность — всё это снижает уровень страха у пациента и напряжение у родственников. Важный момент: стационар не подаётся как «камерный режим», а как безопасная зона восстановления, где можно пройти самый тяжёлый участок пути с максимальной защитой.
Ознакомиться с деталями – http://narkologicheskaya-klinika-ramenskoe10.ru/
В этих ситуациях выезд нарколога на дом позволяет вовремя скорректировать состояние, а при выявлении опасных признаков — не теряя времени, направить пациента в стационар. Это управляемый маршрут вместо хаотичных решений в последний момент.
Получить больше информации – http://narkolog-na-dom-dolgoprudnij10.ru
Когда состояние «штормит», ночные часы усиливают тревогу и вегетативные реакции, обезвоживание нарастает, сон рвётся, а попытки самолечения «чем попало» маскируют опасные симптомы. Организованный маршрут в «Трезвой Линии» заменяет хаос последовательностью: ещё по телефону дежурный врач собирает ключевые сведения — длительность эпизода, аллергии, список лекарств и дозировок, кардио- и эндокринные диагнозы, последние измерения давления и пульса. На месте выполняется короткая, но информативная оценка: АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания, выраженность тремора и тошноты. Схема терапии запускается сразу и корректируется каждые 15–20 минут по «живым показателям», а не по шаблону. Если видим признаки предделирия, неукротимую рвоту, резкие «качели» давления/пульса, выраженную слабость или пожилой возраст с тяжёлой соматикой — переводим в стационар без пауз: приборный мониторинг и ночная команда в Электростали снижают «цену ошибки» и экономят на повторных вызовах. Для семьи это означает меньше догадок и больше ясности: понятно, что делаем сейчас и чего ждём к утру.
Подробнее можно узнать тут – вывод из запоя дешево
idea hub – Text motivates readers to act and implement ideas efficiently.
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Изучить вопрос глубже – http://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-cena-v-kolomne/
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Получить больше информации – вывод из запоя вызов на дом в рязани
Важной частью реабилитации является социализация пациента, возвращение его к активной общественной жизни и формирование новых, здоровых привычек. Для этого в клинике организуются различные мероприятия и программы адаптации.
Детальнее – http://lechenie-narkomanii-tver0.ru
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Получить дополнительные сведения – сколько стоит капельница от запоя
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Ознакомиться с деталями – вывод из запоя на дому круглосуточно в саратове
Лечение алкоголизма в Омске проводится с использованием современных методов, направленных на восстановление организма и психики пациента. Специалисты уделяют внимание как медицинским, так и психологическим аспектам, что позволяет достигать устойчивых результатов. Основой терапии является индивидуальный подход, благодаря которому каждая программа учитывает состояние здоровья и уровень зависимости.
Детальнее – нарколог лечение алкоголизма
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Исследовать вопрос подробнее – кодирование от алкоголизма анонимно
Процедура начинается с обследования пациента: врач измеряет давление, частоту пульса, оценивает степень интоксикации и состояние внутренних органов. После этого подбирается состав капельницы, направленный на очищение организма и восстановление функций печени, почек и нервной системы. Все препараты вводятся внутривенно, что обеспечивает быстрый эффект и минимизирует нагрузку на желудочно-кишечный тракт.
Получить дополнительные сведения – вывод из запоя на дому
Современная наркологическая клиника — это не просто медицинское учреждение, а пространство комплексной помощи, где врачи помогают человеку восстановиться физически, психологически и социально. В клинике «РязаньМед Альянс» создана система непрерывного наблюдения, включающая диагностику, выведение из запоя, детоксикацию, кодирование и постреабилитационную поддержку. Здесь работают квалифицированные наркологи, психиатры и терапевты, а помощь оказывается круглосуточно — как в стационаре, так и на дому. Главная цель специалистов — вернуть пациенту контроль над своим состоянием и избавить от зависимости без стресса и боли.
Узнать больше – наркологическая клиника нарколог в рязани
Тем, кто нуждается в длительной терапии, «КузбассМед» предлагает комфортные условия стационара с круглосуточным наблюдением. Здесь пациенты размещаются в индивидуальных палатах, проходят курсы терапии, реабилитации и психокоррекции. Обстановка в клинике напоминает оздоровительный центр: мягкое освещение, тишина, доступ к библиотеке, возможность общения с психологом и ежедневное участие в восстановительных мероприятиях. Медицинские сестры и врачи находятся на дежурстве 24/7, что позволяет немедленно реагировать на любые изменения в состоянии пациента.
Углубиться в тему – вывод наркологическая клиника новокузнецк
В процессе лечения используются проверенные методики, которые в комплексе обеспечивают положительный эффект и снижают риск рецидива.
Подробнее можно узнать тут – https://lechenie-alkogolizma-omsk0.ru/lechenie-narkomanii-i-alkogolizma-v-omske/
аудит продвижения сайта аудит продвижения сайта .
Лечение алкоголизма в клинике «РязаньМед Альянс» включает несколько этапов, каждый из которых направлен на определённую цель — от снятия интоксикации до формирования устойчивого отказа от алкоголя. В таблице представлены основные стадии лечения и методы, используемые специалистами клиники.
Детальнее – наркологическая клиника наркологический центр
Главная задача процедуры — быстрое выведение этанола и его метаболитов из организма, нормализация уровня электролитов, улучшение самочувствия и предотвращение осложнений. Лечение проводится как в клинике, так и на дому, что особенно удобно при тяжёлых состояниях, когда пациент не может самостоятельно добраться до медицинского учреждения.
Углубиться в тему – http://
Перед процедурой врач оценивает состояние пациента, измеряет давление, пульс и уровень насыщения крови кислородом. После осмотра подбирается состав инфузии, включающий препараты для дезинтоксикации, восстановления водно-солевого баланса и нормализации работы органов. Введение растворов осуществляется внутривенно, под контролем специалиста. Длительность процедуры — от 40 минут до 1,5 часов.
Выяснить больше – капельница от запоя на дому
Лечение наркомании в Твери представляет собой сложный и многоэтапный процесс, направленный на полное восстановление здоровья и социальной адаптации пациентов, страдающих от зависимости. В наркологической клинике «Ренессанс» применяется комплексный подход, который учитывает как физиологические, так и психологические аспекты заболевания, что обеспечивает максимальную эффективность терапии.
Подробнее можно узнать тут – http://lechenie-narkomanii-tver0.ru/tver-lechenie-alkogolizma/https://lechenie-narkomanii-tver0.ru
seo агентство seo агентство .
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Исследовать вопрос подробнее – вывод из запоя дешево
Современная наркологическая клиника — это не просто учреждение для экстренной помощи, а центр комплексной поддержки человека, столкнувшегося с зависимостью. В «КузбассМед» в Новокузнецке реализуется модель интенсивного вмешательства, где используются новейшие медицинские технологии, мультидисциплинарный подход и мобильные выездные службы. Специалисты готовы прибыть на дом за 30 минут с полным набором оборудования и медикаментов, обеспечив пациенту помощь в привычной и безопасной среде. Наркология здесь строится на индивидуализации: каждый случай рассматривается отдельно, с учётом психофизического состояния, анамнеза и жизненного контекста пациента.
Разобраться лучше – частная наркологическая клиника
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Подробнее – https://narkologicheskaya-klinika-kolomna2-10.ru/luchshie-narkologicheskie-kliniki-v-kolomne
Запой — это не просто несколько лишних дней алкоголя, а тяжёлое состояние, в котором организм работает на пределе. Чем дольше длится эпизод, тем глубже обезвоживание, тем сильнее сдвиги электролитов, тем выше риск аритмий, гипертонических кризов, судорог, делирия, обострений заболеваний сердца, печени и поджелудочной железы. Попытки «вывести» человека дома силами родных часто включают опасные комбинации: случайные седативные, снотворные, анальгетики, «антипохмельные» из рекламы. Они могут на время усыпить или «успокоить», но при этом скрывают ухудшение, сбивают давление, угнетают дыхание и мешают врачу увидеть реальную картину. В «Трезвый Центр Коломна» подход другой: ещё на этапе звонка специалист уточняет длительность запоя, объёмы и виды алкоголя, наличие гипертонии, ИБС, диабета, заболеваний печени и почек, неврологических проблем, список уже принятых препаратов, эпизоды потери сознания, судорог, странного поведения. На основании этих данных определяется, безопасен ли формат на дому или сразу нужен стационар. Такая сортировка позволяет вовремя перехватить опасные случаи, не терять часы на бесполезные попытки и сразу запускать те схемы, которые реально снижают риски и стабилизируют состояние.
Изучить вопрос глубже – bystryj-vyvod-iz-zapoya-na-domu
Выбор помощи на дому имеет ряд значительных преимуществ:
Изучить вопрос глубже – http://vyvod-iz-zapoya-tula0.ru/vyvod-iz-zapoya-czena-tula/
Игнорирование этих симптомов может привести к тяжёлым последствиям — судорогам, галлюцинациям или алкогольному психозу.
Ознакомиться с деталями – наркология вывод из запоя тюмень
Когда вопрос стоит остро — нужно быстро и безопасно вывести человека из запоя в Коломне, — у семьи нет лишнего времени на эксперименты с таблетками, сомнительными «коктейлями» и советами из интернета. «Трезвый Центр Коломна» выстраивает помощь так, чтобы от первого звонка до реального облегчения шёл понятный и управляемый маршрут: запись симптомов и рисков уже по телефону, предложение формата (выезд на дом или стационар), оперативный осмотр, персональная инфузионная терапия, круглосуточное наблюдение при необходимости и подробный план восстановления на 24–72 часа и дальше. Мы не продаём миф о «чудо-капельнице за час», а работаем клинически аккуратно: дозы и схемы подбираются под возраст, длительность запоя, сопутствующие заболевания, уже принятые лекарства и текущие показатели. Цель проста и честна — снять интоксикацию, защитить сердце, мозг и печень, вернуть сон и ясность без агрессивной седации и скрытых рисков, сохранить конфиденциальность и дать семье уверенность, что всё делается правильно.
Углубиться в тему – http://vyvod-iz-zapoya-kolomna10.ru/vyvod-iz-zapoya-v-stacionare-v-kolomne/https://vyvod-iz-zapoya-kolomna10.ru
Чтобы родственники не терялись в терминах и не воспринимали лечение как «чёрный ящик», в клинике используется поэтапный подход. Это помогает увидеть логическую связку между затратами, процедурами и результатами.
Получить дополнительную информацию – частные наркологические клиники отзывы
Одним из ключевых преимуществ «КузбассМед» является современная материально-техническая база. В клинике задействованы устройства для точного мониторинга жизненных функций, автоматические инфузионные системы, экспресс-диагностические модули и оборудование для неотложной терапии. Врачи используют программируемые дозаторы, портативные анализаторы крови и аппараты для оценки дыхательной функции, что позволяет своевременно корректировать тактику лечения без потерь времени. Все процедуры соответствуют национальным стандартам безопасности и рекомендациям ВОЗ.
Ознакомиться с деталями – наркологическая клиника клиника помощь новокузнецк
Важное отличие наркологической клиники «Трезвый Путь Коломна» — полный отказ от схемы «одна капельница = решение всех проблем». Детокс здесь рассматривается как необходимый старт, но не как финальная точка. Сначала специалисты снимают острые состояния: вывод из запоя, купирование абстиненции, коррекцию водно-электролитного баланса, поддержку сердца, печени и нервной системы, нормализацию сна, снижение тревоги. Когда организм перестаёт «гореть», начинается следующий этап — стабилизация: врач оценивает психическое состояние, выявляет депрессивные, тревожные, панические проявления, подбирает поддерживающие схемы, которые помогают удержаться в первые недели после кризиса. Далее подключаются психотерапевтические инструменты: индивидуальные консультации, работа с мотивацией, разбор триггеров, формирование новых привычек. В финале выстраивается маршрут поддержки: амбулаторное наблюдение, связь с клиникой, рекомендации для семьи. Такой поэтапный подход делает клинику в Коломне местом, где зависимость перестают воспринимать как «стыд» и начинают воспринимать как задачу, с которой можно работать профессионально.
Исследовать вопрос подробнее – https://narkologicheskaya-klinika-kolomna2-10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Детальнее – наркологический вывод из запоя волгоград
Наркологическая клиника «Трезвый Шаг Раменское» — это место, где острые кризисы, многолетние запои и повторяющиеся срывы перестают быть бесконечным кругом, в котором семья остаётся один на один с проблемой. Здесь выстроена система помощи людям с алкогольной и наркотической зависимостью, а также полизависимостями, включая злоупотребление аптечными препаратами. В клинике в Раменском сочетаются круглосуточное наблюдение, профессиональная детоксикация, медикаментозная поддержка, психотерапевтические программы и сопровождение семьи. Важные принципы — безопасность, анонимность, уважение к пациенту и честное объяснение каждого шага лечения. Ни агрессивного давления, ни обещаний «чуда за один день» — вместо этого поэтапный подход, который даёт реальный шанс стабилизировать состояние, снизить тягу и выйти из разрушительного сценария под контролем специалистов. Для близких это означает понятный маршрут: куда обратиться, что будут делать с пациентом, какие риски учтут и как клиника «Трезвый Шаг Раменское» останется на связи после острого периода.
Углубиться в тему – chastnye-narkologicheskie-kliniki-otzyvy
Trust information portal – The design is clean, and navigation flows naturally.
Капельница при интоксикации помогает быстро очистить организм от продуктов распада алкоголя, восстановить водно-солевой баланс и улучшить самочувствие. В состав раствора входят препараты, нормализующие обмен веществ и поддерживающие работу печени и сердечно-сосудистой системы. Уже через 20–30 минут после начала инфузии пациент ощущает значительное облегчение. Подбор лекарственных средств осуществляется строго индивидуально, с учётом возраста, массы тела и общего состояния здоровья.
Подробнее – психиатр нарколог на дом в уфе
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Выяснить больше – наркологическая клиника доктор
growth insight – Text inspires users to take intentional steps toward advancement.
Услуга вывода из запоя в клинике сочетает профессионализм врачей, медицинскую точность и заботу. При этом обеспечивается полная конфиденциальность: данные пациентов не передаются в сторонние инстанции. Круглосуточный режим работы позволяет вызвать врача даже ночью — специалисты прибывают в течение 40–60 минут после обращения.
Исследовать вопрос подробнее – вывод из запоя дешево
Midpoint Insight – Concise messaging paired with simple navigation improves comprehension.
1win necə pul çıxarılır https://1win5760.help
cheerful shopping hub – Products are easy to explore, and the checkout process feels seamless.
Как подчёркивает специалист ФГБУ «НМИЦ психиатрии и наркологии», «без участия квалифицированной команды невозможно обеспечить комплексный подход к пациенту, особенно если речь идёт о длительном стаже употребления и осложнённой картине заболевания». Отсюда следует — изучение состава персонала должно быть одним из первых шагов.
Подробнее – https://lechenie-alkogolizma-murmansk0.ru/anonimnoe-lechenie-alkogolizma-marmansk
Каждая стадия лечения проходит под постоянным контролем медицинского персонала. Пациенты чувствуют себя в безопасности и получают поддержку не только физическую, но и психологическую. Такой подход снижает риск рецидива и помогает сохранить результат на долгие годы.
Изучить вопрос глубже – наркологическая клиника наркологический центр в рязани
В таблице представлены основные виды терапии, применяемые в клинике:
Узнать больше – наркологическая клиника вывод из запоя
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Подробнее можно узнать тут – нарколог на дом круглосуточно цены в уфе
growthhub.bond – Practical interface, content supports learning and actionable steps are highlighted.
Действие и назначение
Разобраться лучше – vyvod-iz-zapoya-na-domu novosibirsk
Такая комплексность обеспечивает воздействие на физические, психологические и социальные факторы зависимости.
Разобраться лучше – http://lechenie-alkogolizma-omsk0.ru
Работа выездной службы построена так, чтобы для семьи всё было максимально понятно и предсказуемо. После звонка специалист не ограничивается общими фразами, а уточняет детали: сколько длится употребление, есть ли хронические болезни сердца, печени, почек, эндокринные нарушения, какие препараты и в каких дозах пациент уже получил, были ли в прошлом судороги, галлюцинации, тяжёлые реакции на лекарства. Это позволяет заранее оценить уровень риска и понять, подходит ли формат дома. По прибытии в Серпухове врач осматривает пациента, проверяет контакт и ориентировку, измеряет артериальное давление несколько раз, оценивает пульс, сатурацию, температуру, выраженность тремора, наличие болей, характер дыхания, степень обезвоживания. Далее формируется индивидуальная инфузионная схема: растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы, при необходимости — гепатопротекторы и мягкие антиоксидантные комплексы, противорвотные для контроля тошноты, щадящие анксиолитики для нормализации сна без грубой седации. Во время процедуры врач контролирует динамику, меняет скорость капельницы при необходимости, отслеживает реакцию на препараты и объясняет родным, какие изменения будут происходить по часам. По завершении визита пациент и родственники получают подробный план: режим, питьё, питание, чего нельзя, какие симптомы считаются тревожными, когда нужна повторная консультация или стационар. При выявлении опасных признаков вопрос о госпитализации поднимается честно и сразу, а не откладывается «до утра».
Исследовать вопрос подробнее – вызвать нарколога на дом
quick zylavobond guide – Feels approachable, and content is presented without confusion.
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Получить дополнительные сведения – вывод из запоя на дому цена
Каждый этап играет важную роль и обеспечивает пациенту необходимую поддержку на пути к трезвой жизни.
Разобраться лучше – лечение пивного алкоголизма
В основе работы клиники лежит принцип: зависимость — это не просто привычка и не «слабость характера», а комплексное заболевание, которое требует последовательного лечения, а не случайной капельницы по вызову. «Трезвый Шаг Раменское» отказывается от практики, когда пациенту предлагают один-единственный «волшебный» метод, не объясняя, что будет дальше. Здесь каждое обращение рассматривается в контексте стадии зависимости, общего состояния организма, психоэмоционального фона, семейной ситуации. Сначала специалисты снимают острые проявления: выход из запоя, детоксикация после употребления алкоголя, наркотиков или сочетаний, купирование абстиненции, коррекция давления, пульса, сна, тревоги. Затем формируется стабилизационный этап — подбор поддерживающих схем, работа с тягой, выравнивание эмоционального состояния. После этого при готовности пациента подключаются психотерапевтические и реабилитационные инструменты: мотивационные программы, работа с установками, триггерами, окружением. Важная особенность «Трезвый Шаг Раменское» — готовность объяснять семье и самому пациенту, зачем нужен каждый этап, какие цели у процедуры и какие результаты реально ожидать. Это снижает сопротивление, формирует доверие и делает путь не хаотичным, а управляемым.
Выяснить больше – chastnye-narkologicheskie-kliniki-otzyvy
Современные реалии требуют от медицинских учреждений гибкости, скорости и чуткости. Наркологическая помощь — одна из сфер, где промедление может стоить человеку здоровья или жизни. В наркологической клинике «ТверьМед» разработаны оперативные механизмы реагирования: выезд врача по адресу в течение 30 минут, круглосуточная поддержка и возможность получения онлайн-консультации, не покидая дом. Такой подход позволяет вовремя оказать помощь, даже если пациент отказывается ехать в стационар или не осознаёт всю серьёзность своего состояния.
Подробнее можно узнать тут – http://narkologicheskaya-pomoshh-tver0.ru
Капельница при интоксикации помогает быстро очистить организм от продуктов распада алкоголя, восстановить водно-солевой баланс и улучшить самочувствие. В состав раствора входят препараты, нормализующие обмен веществ и поддерживающие работу печени и сердечно-сосудистой системы. Уже через 20–30 минут после начала инфузии пациент ощущает значительное облегчение. Подбор лекарственных средств осуществляется строго индивидуально, с учётом возраста, массы тела и общего состояния здоровья.
Детальнее – нарколог на дом круглосуточно в уфе
оптимизация сайта франция цена prodvizhenie-sajtov-v-moskve115.ru .
Мы проверяем не «ощущения», а факты: частоту пульса в покое, вариабельность ритма к сумеркам, переносимость тёплой воды малыми глотками, минуты до сна и количество ночных пробуждений. Эти короткие метки позволяют тонко управлять темпом инфузии, очередностью модулей и «тихими» ритуалами вечернего времени без необоснованного усиления препаратов.
Выяснить больше – запой нарколог на дом саратов
Primary project page – Logical structure, readable information, and intuitive browsing experience.
раскрутка и продвижение сайта раскрутка и продвижение сайта .
В клинике «ВолгоградМед Альянс» применяются разные методы кодирования, позволяющие подобрать оптимальный вариант для каждого пациента. Выбор зависит от медицинских показаний, психологической готовности и длительности ремиссии. В таблице ниже представлены основные методики, их особенности и преимущества.
Узнать больше – https://kodirovanie-ot-alkogolizma-v-volgograde17.ru/kodirovanie-volgograd
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Получить дополнительную информацию – кодирование от алкоголизма цена адреса в волгограде
В клинике «Альтернатива» применяются современные методы терапии, включающие медикаментозное лечение, психотерапию и социальную реабилитацию.
Узнать больше – неотложная наркологическая помощь
ClickEaseZaviro – Minimalistic design, fast loading, and browsing overall felt natural.
Для иллюстрации эффективности методов представлена таблица с примерами процедур и их воздействием:
Разобраться лучше – наркологические клиники алкоголизм в красноярске
unitytrust.bond – Intuitive layout, the messaging reinforces trustworthiness throughout the pages.
Прежде чем перейти к ориентировочным цифрам, важно подчеркнуть: цена формируется из реальных компонентов помощи — работы врача и медсестры, объёма инфузионной терапии, перечня препаратов, времени выезда и необходимости более длительного наблюдения. Никаких скрытых доплат: все дополнительные назначения согласуются заранее. Чем раньше вы обращаетесь, тем меньше объём вмешательств и, как правило, ниже итоговая стоимость — короткий эпизод проще и дешевле стабилизировать, чем «выводить» осложнения после затянутого запоя.
Ознакомиться с деталями – вызов нарколога на дом
Инфузионная терапия (капельницы) — важная часть лечения, направленная на очищение организма, восстановление водно-солевого баланса и устранение токсинов. В «РязаньМед Альянс» используются проверенные препараты, которые помогают нормализовать работу внутренних органов и улучшить общее самочувствие. Таблица ниже показывает, какие виды капельниц чаще всего применяются при выведении из запоя и лечении алкоголизма.
Получить дополнительную информацию – платная наркологическая клиника
Комплексный подход к выводу из запоя на дому в Ярославле включает несколько основных этапов, которые позволяют обеспечить оперативное и безопасное лечение:
Подробнее можно узнать тут – https://vyvod-iz-zapoya-yaroslavl0.ru/
1win az slotlar http://1win5762.help/
everyday pine finds – Clear organization and friendly visuals make browsing simple.
Стационар наркологической клиники в Раменском ориентирован на тех пациентов, для которых домашние попытки лечения объективно опасны. Это длительные запои, пожилой возраст, выраженные сердечно-сосудистые патологии, заболевания печени и почек, риск делирия, судорог, тяжёлая абстиненция, полинаркомания. В стационаре «Трезвый Шаг Раменское» организовано круглосуточное наблюдение: контролируются давление, пульс, сатурация, поведение, динамика симптомов, проводится своевременная коррекция терапии. Пациент находится в спокойной, защищённой обстановке, где ему не нужно скрывать своё состояние или оправдываться — задача команды не судить, а стабилизировать и лечить. Комфортные палаты, медицинский персонал рядом, продуманное питание, конфиденциальность — всё это снижает уровень страха у пациента и напряжение у родственников. Важный момент: стационар не подаётся как «камерный режим», а как безопасная зона восстановления, где можно пройти самый тяжёлый участок пути с максимальной защитой.
Ознакомиться с деталями – narkologicheskie-kliniki-alkogolizm
Услуга вывода из запоя на дому в Туле представляет собой комплекс мер, направленных на экстренную детоксикацию организма при алкогольной интоксикации. При вызове нарколога специалист прибывает в течение короткого времени, проводит первичный осмотр, собирает анамнез и определяет степень интоксикации. На основе полученной информации разрабатывается индивидуальный план лечения, который может включать медикаментозную детоксикацию, капельничное введение препаратов и психотерапевтическую поддержку.
Получить дополнительные сведения – https://vyvod-iz-zapoya-tula0.ru/vyvod-iz-zapoya-czena-tula
clarity guide – Simple layout supports comprehension and emphasizes main ideas.
MeadowMistMarket – Charming design and browsing feels natural and effortless.
Капельница при вызове нарколога на дом в Долгопрудном от «МедТрезвие Долгопрудный» — это клинический инструмент, а не магический раствор. Главное правило — никакой агрессивной седации ради видимости спокойствия. Инфузионная терапия строится вокруг нескольких задач: восполнить жидкость, выровнять электролиты, снизить токсическую нагрузку на печень и мозг, поддержать сердце и нервную систему, уменьшить тремор, тревогу и соматические жалобы. Используются растворы для регидратации и коррекции водно-электролитного баланса, витамины группы B и магний для поддержки нервной системы, уменьшения риска судорог и нормализации сна, по показаниям — гепатопротекторы и мягкие антиоксиданты, противорвотные препараты для контроля тошноты. При выраженной тревоге или нарушениях сна назначаются щадящие анксиолитические средства в дозах, которые не выключают пациента полностью, а помогают снять паническое напряжение, сохраняя возможность оценивать динамику состояния. Врач отслеживает реакцию на терапию: стабилизацию давления и пульса, уменьшение дрожи, улучшение общего самочувствия, появление более спокойного, естественного сна. По мере облегчения нагрузки схема не усиливается ради счёта, а рационально сокращается. Такой подход защищает пациента от скрытых осложнений и превращает капельницу в контролируемый, полезный шаг, а не в рискованный эксперимент.
Получить дополнительные сведения – http://narkolog-na-dom-dolgoprudnij10.ru/vyezd-narkologa-na-dom-v-dolgoprudnom/
Процесс детоксикации состоит из нескольких последовательных шагов, направленных на безопасное очищение организма. Ниже представлена таблица с описанием этапов, которые применяются в клинике «Трезвая Линия Волгоград».
Подробнее можно узнать тут – вывод из запоя на дому недорого в волгограде
Главная задача капельницы при выезде нарколога в Щёлково — не создать видимость лёгкости, а реально уменьшить интоксикацию и восстановить базовые функции организма. В «ЩёлковоМед Профи» используются современные схемы, а не сомнительные смеси «из всего подряд». В стандартной основе — растворы для восполнения объёма циркулирующей жидкости, выравнивания электролитного баланса и коррекции КЩС, что снижает нагрузку на сердце и мозг. Витамины группы B и магний поддерживают нервную систему, уменьшают тремор, раздражительность и риск судорожных реакций. При необходимости врач добавляет гепатопротекторные и антиоксидантные компоненты, если есть признаки перегрузки печени; при выраженной тошноте — противорвотные, чтобы пациент мог нормально пить и питаться. Для нормализации сна и тревоги подбираются мягкие анксиолитики в дозах, позволяющих контролировать состояние, а не «вырубать» человека. Агрессивные седативные протоколы, которые маскируют ухудшения и опасны для дыхания и сердца, сознательно исключаются. Оценка эффекта идёт по конкретным критериям: стабилизация давления и пульса, уменьшение дрожи, улучшение цвета кожи, уход тошноты, снижение тревоги, появление естественного, а не лекарственного сна. После выезда семья получает ясный план, как закрепить эффект, чтобы наутро не пришлось начинать всё заново.
Получить дополнительные сведения – https://narkolog-na-dom-shchelkovo10.ru/narkolog-na-dom-cena-shchelkovo/
Выбор клиники — задача не только медицинская, но и стратегическая. Учитывать нужно не только наличие лицензии, но и содержание программ, их гибкость, участие родственников в процессе, а также прозрачность взаимодействия с пациентом. Именно эти аспекты позволяют отличить профессиональное учреждение от формального.
Получить дополнительную информацию – частная наркологическая клиника ярославль.
Благодаря комплексному подходу достигается не только снятие симптомов, но и долгосрочная стабилизация состояния пациента.
Ознакомиться с деталями – скорая наркологическая помощь на дому
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Подробнее можно узнать тут – клиника кодирования от алкоголизма волгоград
Инфузионная терапия (капельницы) — важная часть лечения, направленная на очищение организма, восстановление водно-солевого баланса и устранение токсинов. В «РязаньМед Альянс» используются проверенные препараты, которые помогают нормализовать работу внутренних органов и улучшить общее самочувствие. Таблица ниже показывает, какие виды капельниц чаще всего применяются при выведении из запоя и лечении алкоголизма.
Узнать больше – частная наркологическая клиника в рязани
Главная задача процедуры — быстрое выведение этанола и его метаболитов из организма, нормализация уровня электролитов, улучшение самочувствия и предотвращение осложнений. Лечение проводится как в клинике, так и на дому, что особенно удобно при тяжёлых состояниях, когда пациент не может самостоятельно добраться до медицинского учреждения.
Детальнее – нарколог на дом вывод из запоя тюмень
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Детальнее – kodirovanie-ot-alkogolizma-v-volgograde17.ru/
capitalunityteam.bond – Professional look, teamwork and purpose come through clearly.
Перед таблицей — короткий акцент: приведённые суммы ориентировочные, не являются публичной офертой, точная стоимость определяется после осмотра.
Разобраться лучше – http://vyvod-iz-zapoya-kolomna10.ru
Одним из ключевых преимуществ «КузбассМед» является современная материально-техническая база. В клинике задействованы устройства для точного мониторинга жизненных функций, автоматические инфузионные системы, экспресс-диагностические модули и оборудование для неотложной терапии. Врачи используют программируемые дозаторы, портативные анализаторы крови и аппараты для оценки дыхательной функции, что позволяет своевременно корректировать тактику лечения без потерь времени. Все процедуры соответствуют национальным стандартам безопасности и рекомендациям ВОЗ.
Углубиться в тему – http://narkologicheskaya-klinika-novokuzneczk0.ru
После прохождения основной программы пациенту предлагается поддерживающее наблюдение. Оно может включать дистанционные консультации, участие в группе профилактики срывов, повторные осмотры нарколога и психолога, корректировку медикаментозной схемы. В рамках реабилитации формируются планы действий при возникновении тяги, обучаются навыки сопротивления стрессу и внешнему давлению. При желании можно подключить родственников к процессу постлечебной адаптации, чтобы укрепить результат и снизить риски рецидивов. Таким образом, пациент не остаётся один даже после выписки.
Получить больше информации – лечение алкоголизма и наркомании центр новокузнецк
Комплексное применение этих методов позволяет значительно ускорить процесс восстановления и предотвратить осложнения.
Ознакомиться с деталями – https://narcologicheskaya-klinika-v-novokuzneczke17.ru/narkologicheskij-czentr-novokuzneczk/
Каждый этап играет важную роль и обеспечивает пациенту необходимую поддержку на пути к трезвой жизни.
Получить дополнительную информацию – лечение алкоголизма гипнозом омск
Главная задача процедуры — быстрое выведение этанола и его метаболитов из организма, нормализация уровня электролитов, улучшение самочувствия и предотвращение осложнений. Лечение проводится как в клинике, так и на дому, что особенно удобно при тяжёлых состояниях, когда пациент не может самостоятельно добраться до медицинского учреждения.
Углубиться в тему – наркологический вывод из запоя
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Изучить вопрос глубже – капельница от запоя в волгограде
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Выяснить больше – наркологические клиники алкоголизм в новокузнецке
Наркозависимость — это не просто вредная привычка, а тяжёлое хроническое заболевание, требующее комплексного и последовательного лечения. В клинике «РеабКузбасс» в Новокузнецке разработаны персонализированные программы помощи, учитывающие медицинские, психологические и социальные аспекты проблемы. Каждому пациенту подбирается уникальный маршрут восстановления, начиная с первичной диагностики и заканчивая адаптацией к жизни без наркотиков. Поддержка оказывается круглосуточно, с полным соблюдением конфиденциальности. Психотерапевты и врачи работают в тесной связке, чтобы не только устранить физическую зависимость, но и восстановить личность пациента, вернуть ему мотивацию к жизни и уверенность в будущем.
Ознакомиться с деталями – лечение наркомании в стационаре в новокузнецке
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Выяснить больше – http://narkologicheskaya-klinika-kolomna10.ru
Важное отличие наркологической клиники «Трезвый Путь Коломна» — полный отказ от схемы «одна капельница = решение всех проблем». Детокс здесь рассматривается как необходимый старт, но не как финальная точка. Сначала специалисты снимают острые состояния: вывод из запоя, купирование абстиненции, коррекцию водно-электролитного баланса, поддержку сердца, печени и нервной системы, нормализацию сна, снижение тревоги. Когда организм перестаёт «гореть», начинается следующий этап — стабилизация: врач оценивает психическое состояние, выявляет депрессивные, тревожные, панические проявления, подбирает поддерживающие схемы, которые помогают удержаться в первые недели после кризиса. Далее подключаются психотерапевтические инструменты: индивидуальные консультации, работа с мотивацией, разбор триггеров, формирование новых привычек. В финале выстраивается маршрут поддержки: амбулаторное наблюдение, связь с клиникой, рекомендации для семьи. Такой поэтапный подход делает клинику в Коломне местом, где зависимость перестают воспринимать как «стыд» и начинают воспринимать как задачу, с которой можно работать профессионально.
Подробнее тут – https://narkologicheskaya-klinika-kolomna2-10.ru/narkologicheskaya-klinika-oficialnyj-sajt-v-kolomne
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Получить больше информации – вывод из запоя с выездом рязань
View project details – Branding is uniform, and content is presented in a straightforward way.
Диагностика в клинике «КузбассМед» проводится комплексно: используются лабораторные, инструментальные и психологические методы. Благодаря применению цифровых систем и алгоритмов обработки данных, результаты анализов доступны уже в течение первого часа. Оценка проводится по нескольким направлениям: токсикологический статус, состояние печени и почек, электролитный баланс, нейровегетативное состояние, когнитивные функции и уровень стресса. Это позволяет врачам составлять максимально точную картину заболевания и подбирать индивидуальные методы терапии.
Углубиться в тему – http://narkologicheskaya-klinika-novokuzneczk0.ru/narkologicheskij-czentr-novokuzneczk/
Tandem Flow – Messaging is clear, design feels inviting and well organized.
focus link – Content feels purposeful, reinforcing momentum and precision.
При получении заявки по телефону или через сайт администратор передаёт её врачу-дежуранту, который немедленно выезжает по указанному адресу. По прибытии специалист проводит первичный осмотр: измеряются артериальное давление, пульс, температура, сатурация. Затем осуществляется экспресс-оценка состояния ЦНС и метаболизма. При необходимости берутся анализы, подключается инфузионная система, проводятся противотревожные и детоксикационные мероприятия. Врач остаётся с пациентом до полной стабилизации состояния, а при тяжёлых симптомах организует транспортировку в стационар.
Узнать больше – http://narkologicheskaya-pomoshh-tver0.ru/narkolog-v-tveri-czeny/
Важное отличие наркологической клиники «Трезвый Путь Коломна» — полный отказ от схемы «одна капельница = решение всех проблем». Детокс здесь рассматривается как необходимый старт, но не как финальная точка. Сначала специалисты снимают острые состояния: вывод из запоя, купирование абстиненции, коррекцию водно-электролитного баланса, поддержку сердца, печени и нервной системы, нормализацию сна, снижение тревоги. Когда организм перестаёт «гореть», начинается следующий этап — стабилизация: врач оценивает психическое состояние, выявляет депрессивные, тревожные, панические проявления, подбирает поддерживающие схемы, которые помогают удержаться в первые недели после кризиса. Далее подключаются психотерапевтические инструменты: индивидуальные консультации, работа с мотивацией, разбор триггеров, формирование новых привычек. В финале выстраивается маршрут поддержки: амбулаторное наблюдение, связь с клиникой, рекомендации для семьи. Такой поэтапный подход делает клинику в Коломне местом, где зависимость перестают воспринимать как «стыд» и начинают воспринимать как задачу, с которой можно работать профессионально.
Подробнее можно узнать тут – заказать звонок наркологическая клиника
Как подчёркивает специалист ФГБУ «НМИЦ психиатрии и наркологии», «без участия квалифицированной команды невозможно обеспечить комплексный подход к пациенту, особенно если речь идёт о длительном стаже употребления и осложнённой картине заболевания». Отсюда следует — изучение состава персонала должно быть одним из первых шагов.
Ознакомиться с деталями – https://lechenie-alkogolizma-murmansk0.ru/
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Подробнее можно узнать тут – вывод из запоя на дому цена в волгограде
«ТверьМед» — частная лицензированная клиника, специализирующаяся на наркологической помощи любой степени сложности. Здесь работают неравнодушные врачи-наркологи, психиатры, терапевты и психологи с многолетним стажем. Медицинская команда настроена на оперативную диагностику и проведение первичных мероприятий в течение первого часа после обращения. Упор сделан на доступность: клиника открыта 24/7, приём возможен как на территории медучреждения, так и на выезде — дома, в офисе, гостинице, санатории или любом удобном месте.
Изучить вопрос глубже – круглосуточная наркологическая помощь в твери
Алгоритм в «Трезвый Центр Коломна» построен так, чтобы убрать импровизацию и сделать всё максимально прозрачным для семьи. Сначала по телефону собираются ключевые данные: возраст пациента, длительность запоя, виды алкоголя, хронические заболевания, препараты, аллергии, наличие судорог, потерь сознания, странного поведения, текущие жалобы. На этом этапе озвучивается ориентировочный формат помощи и примерный диапазон стоимости. Далее следует выезд на дом или поступление в стационар. Врач проводит осмотр: измеряет артериальное давление, пульс, сатурацию, температуру, оценивает тремор, координацию, сознание, степень обезвоживания, наличие болей, состояние дыхания и сердца. На основе этих данных назначается инфузионная терапия: растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы, по показаниям — гепатопротекторы, антиоксидантные комплексы, противорвотные для контроля тошноты, мягкие анксиолитики для уменьшения тревоги и нормализации сна. Уходят от агрессивной седации: пациент не должен быть «выключен» так, чтобы невозможно было заметить ухудшение. В процессе капельниц проводится повторный контроль показателей, темп и состав при необходимости корректируются. После стабилизации пациент и семья получают подробные рекомендации: режим, сон, питание, питьё, запреты, «красные флаги», план наблюдения и возможного дальнейшего лечения зависимости.
Подробнее можно узнать тут – vyvod-iz-zapoya-nedorogo
Благодаря широкому выбору методик специалисты клиники могут подобрать оптимальную схему для каждого пациента, учитывая не только медицинские, но и психологические особенности. Такой индивидуальный подход повышает эффективность лечения и снижает риск повторных срывов.
Подробнее можно узнать тут – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru
Даже телефонный разговор с клиникой может многое сказать о её подходе. Если вам предлагают типовое лечение без уточнения подробностей или избегают вопросов о составе команды, это тревожный сигнал. Серьёзные учреждения в Мурманске обязательно предложат предварительную консультацию, зададут уточняющие вопросы и расскажут, как строится программа помощи.
Получить дополнительную информацию – https://lechenie-alkogolizma-murmansk0.ru/lechenie-khronicheskogo-alkogolizma-marmansk
Наркологическая клиника в Красноярске оказывает профессиональную помощь людям, столкнувшимся с алкогольной, наркотической и другими видами зависимостей. Основная цель деятельности специалистов — восстановление физического здоровья, стабилизация психоэмоционального состояния и возвращение пациента к полноценной жизни. Лечение проводится по современным медицинским протоколам, с применением индивидуальных схем терапии и полным соблюдением конфиденциальности.
Исследовать вопрос подробнее – лечение в наркологической клинике
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Углубиться в тему – вывод из запоя капельница
Раннее обращение к специалистам позволяет провести качественную диагностику, подобрать адекватное лечение и обеспечить комплексную поддержку пациента.
Подробнее – http://narkologicheskaya-pomoshh-novokuzneczk0.ru/narkologicheskij-czentr-novokuzneczk/https://narkologicheskaya-pomoshh-novokuzneczk0.ru
В таблице представлены основные виды терапии, применяемые в клинике:
Подробнее – https://narcologicheskaya-klinika-v-novokuzneczke17.ru
Комплексный подход к выводу из запоя на дому в Ярославле включает несколько основных этапов, которые позволяют обеспечить оперативное и безопасное лечение:
Получить больше информации – вывод из запоя капельница в ярославле
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Получить дополнительную информацию – вызвать нарколога на дом срочно
Для иллюстрации эффективности методов представлена таблица с примерами процедур и их воздействием:
Получить дополнительные сведения – https://narcologicheskaya-klinika-v-krasnoyarske17.ru/narkologicheskaya-klinika-krasnoyarsk-otzyvy
Для понимания ключевых компонентов лечения ниже представлена таблица, в которой систематизированы основные методы и их назначение.
Углубиться в тему – narkologicheskaya-pomoshh-novokuzneczk0.ru/
Каждый этап проходит под контролем врачей-наркологов и психотерапевтов, что гарантирует эффективность и безопасность лечения.
Ознакомиться с деталями – наркологическая клиника наркологический центр
Саратов живёт в разных темпах: плотный центр, протяжные магистрали, мостовые переезды. Мы учитываем это в логистике: выездные бригады «СаратовМед Профи» движутся по немаркированным маршрутам, приезжают в гражданской одежде, формируют на месте «тихую сцену» и только затем начинают клиническую часть. Если на предзвонке звучат «красные флаги» — давящая боль в груди, выраженная одышка, спутанность, неукротимая рвота, судороги — организуем перевод в стационар без пауз: место резервируем заранее, передислокация проходит конфиденциально.
Выяснить больше – https://vyvod-iz-zapoya-saratov0.ru/
Даже телефонный разговор с клиникой может многое сказать о её подходе. Если вам предлагают типовое лечение без уточнения подробностей или избегают вопросов о составе команды, это тревожный сигнал. Серьёзные учреждения в Мурманске обязательно предложат предварительную консультацию, зададут уточняющие вопросы и расскажут, как строится программа помощи.
Получить дополнительные сведения – https://lechenie-alkogolizma-murmansk0.ru/lechenie-khronicheskogo-alkogolizma-marmansk
Первый шаг в лечении — это тщательный осмотр специалиста. Наряду с измерением жизненно важных показателей (пульс, артериальное давление, температура) врач проводит сбор анамнеза, выясняя длительность запоя, тип употребляемого алкоголя и наличие сопутствующих заболеваний. Эти данные помогают оценить степень интоксикации и подобрать индивидуальный план терапии, что является ключевым для дальнейшей эффективной детоксикации.
Подробнее можно узнать тут – https://vyvod-iz-zapoya-yaroslavl0.ru
Критичные случаи, когда вызов нарколога через «МедТрезвие Долгопрудный» оправдан и своевременен:
Подробнее можно узнать тут – luchshij-narkolog-na-dom
После прохождения основной программы пациенту предлагается поддерживающее наблюдение. Оно может включать дистанционные консультации, участие в группе профилактики срывов, повторные осмотры нарколога и психолога, корректировку медикаментозной схемы. В рамках реабилитации формируются планы действий при возникновении тяги, обучаются навыки сопротивления стрессу и внешнему давлению. При желании можно подключить родственников к процессу постлечебной адаптации, чтобы укрепить результат и снизить риски рецидивов. Таким образом, пациент не остаётся один даже после выписки.
Ознакомиться с деталями – lechenie-narkomanii-novokuzneczk0.ru/
Мы не используем универсальную «капельницу». Схема собирается из модулей под ведущие жалобы. Медицинские шаги всегда сочетаются с нефраком опорами — свет, тишина, вода малыми глотками, дыхание, — потому что среда усиливает действие препаратов и позволяет держать дозы ниже.
Ознакомиться с деталями – вызвать нарколога на дом срочно саратов
Official site link – Content is presented in an uncomplicated way, with a tidy layout.
Не всегда человек способен прекратить употребление алкоголя без медицинского вмешательства. Чем дольше длится запой, тем выше риск осложнений. Обратиться к специалисту следует при появлении следующих признаков:
Детальнее – вывод из запоя в тюмени
Современные реалии требуют от медицинских учреждений гибкости, скорости и чуткости. Наркологическая помощь — одна из сфер, где промедление может стоить человеку здоровья или жизни. В наркологической клинике «ТверьМед» разработаны оперативные механизмы реагирования: выезд врача по адресу в течение 30 минут, круглосуточная поддержка и возможность получения онлайн-консультации, не покидая дом. Такой подход позволяет вовремя оказать помощь, даже если пациент отказывается ехать в стационар или не осознаёт всю серьёзность своего состояния.
Подробнее тут – неотложная наркологическая помощь тверь
В этих ситуациях выезд нарколога на дом позволяет вовремя скорректировать состояние, а при выявлении опасных признаков — не теряя времени, направить пациента в стационар. Это управляемый маршрут вместо хаотичных решений в последний момент.
Выяснить больше – narkolog-na-dom-srochno
Процесс включает несколько шагов:
Ознакомиться с деталями – https://narkolog-na-dom-v-ufe17.ru/vyvod-iz-zapoya-ufa-narkolog-na-dom/
discover clarity – Text promotes clarity-driven speed for actionable outcomes.
Каждый этап играет важную роль и обеспечивает пациенту необходимую поддержку на пути к трезвой жизни.
Узнать больше – клиника лечения алкоголизма в омске
Психологическая поддержка играет ключевую роль в лечении наркомании в Твери. В клинике «Ренессанс» применяются различные методы психотерапии, включая когнитивно-поведенческую терапию, групповые и семейные сессии, арт-терапию. Эти методы помогают осознать причины зависимости, развить навыки преодоления стрессов и поддержать мотивацию к выздоровлению.
Подробнее тут – лечение наркомании в твери
Процедура начинается с обследования пациента: врач измеряет давление, частоту пульса, оценивает степень интоксикации и состояние внутренних органов. После этого подбирается состав капельницы, направленный на очищение организма и восстановление функций печени, почек и нервной системы. Все препараты вводятся внутривенно, что обеспечивает быстрый эффект и минимизирует нагрузку на желудочно-кишечный тракт.
Получить дополнительные сведения – http://vyvod-iz-zapoya-v-tyumeni17.ru/vyvod-iz-zapoya-tyumen-otzyvy/
Когда состояние «штормит», ночные часы усиливают тревогу и вегетативные реакции, обезвоживание нарастает, сон рвётся, а попытки самолечения «чем попало» маскируют опасные симптомы. Организованный маршрут в «Трезвой Линии» заменяет хаос последовательностью: ещё по телефону дежурный врач собирает ключевые сведения — длительность эпизода, аллергии, список лекарств и дозировок, кардио- и эндокринные диагнозы, последние измерения давления и пульса. На месте выполняется короткая, но информативная оценка: АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания, выраженность тремора и тошноты. Схема терапии запускается сразу и корректируется каждые 15–20 минут по «живым показателям», а не по шаблону. Если видим признаки предделирия, неукротимую рвоту, резкие «качели» давления/пульса, выраженную слабость или пожилой возраст с тяжёлой соматикой — переводим в стационар без пауз: приборный мониторинг и ночная команда в Электростали снижают «цену ошибки» и экономят на повторных вызовах. Для семьи это означает меньше догадок и больше ясности: понятно, что делаем сейчас и чего ждём к утру.
Получить дополнительную информацию – vyvod-iz-zapoya-s-vyezdom-ehlektrostal
Современная наркологическая клиника — это не просто учреждение для экстренной помощи, а центр комплексной поддержки человека, столкнувшегося с зависимостью. В «КузбассМед» в Новокузнецке реализуется модель интенсивного вмешательства, где используются новейшие медицинские технологии, мультидисциплинарный подход и мобильные выездные службы. Специалисты готовы прибыть на дом за 30 минут с полным набором оборудования и медикаментов, обеспечив пациенту помощь в привычной и безопасной среде. Наркология здесь строится на индивидуализации: каждый случай рассматривается отдельно, с учётом психофизического состояния, анамнеза и жизненного контекста пациента.
Выяснить больше – https://narkologicheskaya-klinika-novokuzneczk0.ru/narkolog-v-gorode-novokuzneczke
В клинике «ВолгоградМед Альянс» применяются разные методы кодирования, позволяющие подобрать оптимальный вариант для каждого пациента. Выбор зависит от медицинских показаний, психологической готовности и длительности ремиссии. В таблице ниже представлены основные методики, их особенности и преимущества.
Разобраться лучше – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru/
Современные реалии требуют от медицинских учреждений гибкости, скорости и чуткости. Наркологическая помощь — одна из сфер, где промедление может стоить человеку здоровья или жизни. В наркологической клинике «ТверьМед» разработаны оперативные механизмы реагирования: выезд врача по адресу в течение 30 минут, круглосуточная поддержка и возможность получения онлайн-консультации, не покидая дом. Такой подход позволяет вовремя оказать помощь, даже если пациент отказывается ехать в стационар или не осознаёт всю серьёзность своего состояния.
Получить дополнительные сведения – https://narkologicheskaya-pomoshh-tver0.ru/narkolog-v-tveri-czeny/
Важное отличие наркологической клиники «Трезвый Путь Коломна» — полный отказ от схемы «одна капельница = решение всех проблем». Детокс здесь рассматривается как необходимый старт, но не как финальная точка. Сначала специалисты снимают острые состояния: вывод из запоя, купирование абстиненции, коррекцию водно-электролитного баланса, поддержку сердца, печени и нервной системы, нормализацию сна, снижение тревоги. Когда организм перестаёт «гореть», начинается следующий этап — стабилизация: врач оценивает психическое состояние, выявляет депрессивные, тревожные, панические проявления, подбирает поддерживающие схемы, которые помогают удержаться в первые недели после кризиса. Далее подключаются психотерапевтические инструменты: индивидуальные консультации, работа с мотивацией, разбор триггеров, формирование новых привычек. В финале выстраивается маршрут поддержки: амбулаторное наблюдение, связь с клиникой, рекомендации для семьи. Такой поэтапный подход делает клинику в Коломне местом, где зависимость перестают воспринимать как «стыд» и начинают воспринимать как задачу, с которой можно работать профессионально.
Узнать больше – http://narkologicheskaya-klinika-kolomna2-10.ru/luchshie-narkologicheskie-kliniki-v-kolomne/
Диспетчер уточняет адрес в Электростали, длительность эпизода, текущие препараты и дозы, аллергии, сопутствующие заболевания, последние значения давления/пульса. Это экономит 15–20 минут на месте и позволяет заранее исключить опасные взаимодействия.
Ознакомиться с деталями – vyvod-iz-zapoya-na-domu
Когда состояние «штормит», ночные часы усиливают тревогу и вегетативные реакции, обезвоживание нарастает, сон рвётся, а попытки самолечения «чем попало» маскируют опасные симптомы. Организованный маршрут в «Трезвой Линии» заменяет хаос последовательностью: ещё по телефону дежурный врач собирает ключевые сведения — длительность эпизода, аллергии, список лекарств и дозировок, кардио- и эндокринные диагнозы, последние измерения давления и пульса. На месте выполняется короткая, но информативная оценка: АД, ЧСС, сатурация, температура, неврологический статус, степень обезвоживания, выраженность тремора и тошноты. Схема терапии запускается сразу и корректируется каждые 15–20 минут по «живым показателям», а не по шаблону. Если видим признаки предделирия, неукротимую рвоту, резкие «качели» давления/пульса, выраженную слабость или пожилой возраст с тяжёлой соматикой — переводим в стационар без пауз: приборный мониторинг и ночная команда в Электростали снижают «цену ошибки» и экономят на повторных вызовах. Для семьи это означает меньше догадок и больше ясности: понятно, что делаем сейчас и чего ждём к утру.
Подробнее можно узнать тут – vyvod-iz-zapoya-nedorogo
firmtrack.bond – Polished interface, content highlights stability and practical guidance for users.
toptrust.bond – Modern feel, navigation is intuitive and content exudes reliability.
Письменные рекомендации: сон, питание, гидратация, запреты, «красные флаги», график амбулаторных визитов; при недостатке ресурсов дома — перевод в стационар без задержек. Такая последовательность убирает импровизацию и делает результат повторяемым.
Ознакомиться с деталями – http://www.domen.ru
В клинике «ВолгоградМед Альянс» применяются разные методы кодирования, позволяющие подобрать оптимальный вариант для каждого пациента. Выбор зависит от медицинских показаний, психологической готовности и длительности ремиссии. В таблице ниже представлены основные методики, их особенности и преимущества.
Разобраться лучше – http://kodirovanie-ot-alkogolizma-v-volgograde17.ru/kodirovanie-ot-alkogolya-v-volgograde/
Программа лечения строится по принципу последовательного воздействия на физическое и психологическое состояние. Начинается она с детоксикации: инфузионная терапия с применением сбалансированных растворов, антиоксидантов, гепатопротекторов и витаминов. Затем — стабилизация состояния, коррекция сна, восстановление когнитивных функций и купирование абстинентного синдрома. В зависимости от диагноза используются такие методы, как заместительная терапия, нейрометаболическая поддержка, противотревожные и антидепрессивные схемы.
Разобраться лучше – наркологическая клиника клиника помощь новокузнецк
Наркологическая клиника в Красноярске оказывает профессиональную помощь людям, столкнувшимся с алкогольной, наркотической и другими видами зависимостей. Основная цель деятельности специалистов — восстановление физического здоровья, стабилизация психоэмоционального состояния и возвращение пациента к полноценной жизни. Лечение проводится по современным медицинским протоколам, с применением индивидуальных схем терапии и полным соблюдением конфиденциальности.
Ознакомиться с деталями – наркологическая клиника лечение алкоголизма красноярск
Перед тем как показать примерные программы, важно подчеркнуть: реальный план всегда персонализируется, но понимание базовых форматов помогает семье и пациенту не теряться в терминах и сразу видеть логику.
Детальнее – http://narkologicheskaya-klinika-kolomna2-10.ru/luchshie-narkologicheskie-kliniki-v-kolomne/
Для понимания ключевых компонентов лечения ниже представлена таблица, в которой систематизированы основные методы и их назначение.
Получить дополнительные сведения – платная наркологическая помощь
На этом этапе специалист уточняет, сколько времени продолжается запой, какие основные симптомы наблюдаются, и если имеются, то какие хронические заболевания могут влиять на течение терапии. Точный анализ этих данных позволяет сформировать персонализированную стратегию лечения, которая будет максимально адаптирована к состоянию пациента и его потребностям.
Разобраться лучше – https://vyvod-iz-zapoya-yaroslavl0.ru/vyvod-iz-zapoya-czena-yaroslavl
Для иллюстрации эффективности методов представлена таблица с примерами процедур и их воздействием:
Ознакомиться с деталями – наркологические клиники алкоголизм красноярск
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Узнать больше – капельница от запоя вызов
Программы вывода из запоя в клинике разрабатываются с учётом состояния пациента. Для тяжёлых случаев назначается интенсивный курс с инфузионной терапией и контролем электролитов. При лёгких формах применяются мягкие препараты с постепенным выведением токсинов. Все процедуры проходят с соблюдением медицинских стандартов и полным сохранением анонимности.
Углубиться в тему – http://vyvod-iz-zapoia-v-volgograde17.ru/anonimnaya-narkologiya-vyvod-iz-zapoya-volgograd/
Метод лечения
Разобраться лучше – круглосуточная наркологическая помощь новокузнецк
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Подробнее можно узнать тут – наркология вывод из запоя волгоград
В таблице представлены основные виды терапии, применяемые в клинике:
Детальнее – http://narcologicheskaya-klinika-v-novokuzneczke17.ru/narkolog-v-gorode-novokuzneczke/
Перед процедурой врач оценивает состояние пациента, измеряет давление, пульс и уровень насыщения крови кислородом. После осмотра подбирается состав инфузии, включающий препараты для дезинтоксикации, восстановления водно-солевого баланса и нормализации работы органов. Введение растворов осуществляется внутривенно, под контролем специалиста. Длительность процедуры — от 40 минут до 1,5 часов.
Изучить вопрос глубже – http://kapelnicza-ot-zapoya-v-volgograde17.ru/
Комплексный подход к выводу из запоя на дому в Ярославле включает несколько основных этапов, которые позволяют обеспечить оперативное и безопасное лечение:
Получить дополнительные сведения – срочный вывод из запоя в ярославле
Чтобы не упустить момент, нужно ориентироваться не на фразу «он говорит, что справится», а на реальные признаки, при которых профессиональная помощь на дому становится необходимой. Домашний выезд — это шанс стабилизировать состояние до того, как потребуется реанимация или жёсткая госпитализация.
Получить дополнительную информацию – http://narkolog-na-dom-dolgoprudnij10.ru
Благодаря комплексному подходу достигается не только снятие симптомов, но и долгосрочная стабилизация состояния пациента.
Получить дополнительные сведения – narkologicheskaya-pomoshh-v-volgograde17.ru/
Диспетчер уточняет адрес в Электростали, длительность эпизода, текущие препараты и дозы, аллергии, сопутствующие заболевания, последние значения давления/пульса. Это экономит 15–20 минут на месте и позволяет заранее исключить опасные взаимодействия.
Подробнее тут – http://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-na-domu-v-ehlektrostali/
Услуга вывода из запоя в клинике сочетает профессионализм врачей, медицинскую точность и заботу. При этом обеспечивается полная конфиденциальность: данные пациентов не передаются в сторонние инстанции. Круглосуточный режим работы позволяет вызвать врача даже ночью — специалисты прибывают в течение 40–60 минут после обращения.
Детальнее – http://vivod-iz-zapoya-v-volgograde17.ru
View project details – Professional presentation with logical content placement makes browsing easy.
Выбор клиники — задача не только медицинская, но и стратегическая. Учитывать нужно не только наличие лицензии, но и содержание программ, их гибкость, участие родственников в процессе, а также прозрачность взаимодействия с пациентом. Именно эти аспекты позволяют отличить профессиональное учреждение от формального.
Получить дополнительные сведения – частная наркологическая клиника
Врач уточняет, как долго продолжается запой, какой алкоголь употребляется, а также наличие сопутствующих заболеваний. Этот тщательный анализ позволяет оперативно подобрать оптимальные методы детоксикации и снизить риск осложнений.
Исследовать вопрос подробнее – https://vyvod-iz-zapoya-tula0.ru/vyvod-iz-zapoya-czena-tula
explore & act – Wording suggests momentum and invites immediate engagement.
Профессиональный нарколог на дому не работает по схеме «чем больше препаратов, тем лучше». В «СерпуховТрезвие» капельницы составляются исходя из задач конкретного организма. Базовый блок — это растворы для восполнения объёма циркулирующей жидкости, выравнивания электролитного баланса и коррекции кислотно-щелочного состояния, что уменьшает нагрузку на сердце, мозг и снижает риск тяжёлых осложнений. Витамины группы B и магний входят в стандартную поддержку: они помогают стабилизировать нервную систему, уменьшить тремор, раздражительность, поддерживают сон и снижают риск судорог. При признаках поражения печени используются гепатопротективные и антиоксидантные компоненты, снижающие токсическое воздействие продуктов распада алкоголя. Если пациента мучает тошнота, добавляются противорвотные средства, чтобы восстановить возможность пить воду и питаться. Для снижения тревоги и нормализации сна применяются мягкие анксиолитики в дозировках, не маскирующих клиническую картину и не угнетающих дыхательный центр. Агрессивная седация, популярная в «серых» схемах, сознательно исключается: она «делает вид» улучшения, но может скрыть нарастающие осложнения. Эффект оценивается по конкретным критериям: стабилизация давления и пульса, уменьшение тремора, уход тошноты, улучшение цвета кожи, появление естественного сна и большей ясности мышления. После достижения этих ориентиров фармаконагрузка не наращивается, а постепенно снижается, чтобы человек выходил в устойчивое состояние, а не зависел от бесконечных капельниц.
Детальнее – https://narkolog-na-dom-serpuhov10.ru/narkolog-psiholog-na-dom-serpuhov/
Каждый этап играет важную роль и обеспечивает пациенту необходимую поддержку на пути к трезвой жизни.
Подробнее – лечение наркомании и алкоголизма омск
Услуга «нарколог на дом в Долгопрудном» от клиники «МедТрезвие Долгопрудный» создана для ситуаций, когда важно действовать быстро, аккуратно и без лишнего шума. Запой, тяжёлое похмелье, срыв после ремиссии, злоупотребление медикаментами или смесью алкоголя с препаратами — всё это не терпит откладывания и самодеятельности. Вызов врача на дом позволяет получить профессиональную помощь без госпитализации, когда состояние пациента ещё позволяет лечить его в привычной обстановке. Нарколог приезжает с полностью укомплектованным набором препаратов и расходников, проводит осмотр, подбирает капельницы по клиническим показаниям, контролирует реакцию, даёт подробные рекомендации на ближайшие дни и при необходимости предлагает дальнейший маршрут: повторный выезд, амбулаторное наблюдение или стационар клиники. Конфиденциальность соблюдается строго: без обсуждений с соседями, без регистрации по месту работы, без унизительных формальностей — только медицинская помощь, ориентированная на безопасность и результат.
Подробнее можно узнать тут – psihiatr-narkolog-na-dom
northwindoutletonline.shop – Approachable layout, product details are clear and checkout is simple.
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Слушай внимательно — тут важно – https://www.defining-blog.ru/tag/ekspertiza-proektov
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Лучшее решение — прямо здесь – https://www.defining-blog.ru/category/investicii
Кодирование от алкоголизма — это медицинская процедура, направленная на формирование устойчивого отвращения к спиртному и восстановление контроля над зависимым поведением. В клинике «ВолгоградМед Альянс» используются современные, научно обоснованные методы, которые позволяют не просто временно ограничить тягу, а глубоко перестроить психологические и биохимические механизмы зависимости. Каждая программа подбирается индивидуально, с учётом стажа употребления, состояния здоровья, мотивации и психоэмоционального фона пациента. Врачи обеспечивают анонимность, безопасность и круглосуточную поддержку, помогая восстановить не только физическое состояние, но и внутреннее равновесие.
Подробнее тут – кодирование от алкоголизма цена
Примерный состав раствора, применяемого наркологом на дому в Уфе, приведён в таблице:
Углубиться в тему – платный нарколог на дом
Наша выездная бригада приезжает без маркировки, в гражданской одежде, согласовывает «тихое окно» связи с пациентом или близкими и начинает не с капельницы, а с настройки среды: тёплая приглушённая подсветка, проветривание без сквозняков, отключение уведомлений, подготовка воды комнатной температуры. Затем — быстрый осмотр, экспресс-метрики и старт индивидуального плана. Каждая корректировка — ровно одна за раз, чтобы сохранить причинно-следственную связь и не провоцировать полипрагмазию.
Углубиться в тему – нарколог на дом вывод из запоя
В этой статье представлен занимательный и актуальный контент, который заставит вас задуматься. Мы обсуждаем насущные вопросы и проблемы, а также освещаем истории, которые вдохновляют на действия и изменения. Узнайте, что стоит за событиями нашего времени!
Детальнее – https://mydownloadables.com/winter-wine-vector-download
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Смотрите также – http://www.benton-ely.co.uk/home/porsche
Острый эпизод запоя — это не «плохое самочувствие», а состояние с реальными рисками для сердца, нервной системы и дыхания, особенно в ночные часы, когда усиливаются вегетативные реакции и тревога. В «НоваТрезвие» мы выстраиваем помощь так, чтобы от звонка до заметного облегчения прошло как можно меньше времени и как можно меньше случайностей: короткое интервью для оценки рисков, выезд врача или приём в клинике, экспресс-диагностика по ключевым показателям, персональная инфузионная схема без «универсальных коктейлей», мягкая коррекция сна и тревоги без «вырубания», понятные инструкции семье на 24–72 часа и план продолжения на ближайшие недели. Мы не скрываемся за общими формулами: решения принимаются по фактическим данным, дозы и темп капельниц подстраиваются к динамике каждые 15–20 минут, а при «красных флагах» перевод в стационар организуется без пауз. Конфиденциальность соблюдается строго, а коммуникация простая и предсказуемая — чтобы вы всегда знали, что происходит сейчас и чего ждать к утру.
Углубиться в тему – https://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-stacionar-v-ehlektrostali
Эта статья сочетает познавательный и занимательный контент, что делает ее идеальной для любителей глубоких исследований. Мы рассмотрим увлекательные аспекты различных тем и предоставим вам новые знания, которые могут оказаться полезными в будущем.
Исследовать вопрос подробнее – https://thecalligraphysquare.in/blog/how-to-create-your-own-ink-using-gouache
Многие методы лечения наркозависимости не дают устойчивого результата именно потому, что применяются шаблонно, без учёта особенностей конкретного человека. В «РеабКузбасс» отказались от универсальных схем: каждый случай рассматривается как уникальный. При составлении программы учитываются возраст, стаж употребления, тип вещества, психическое состояние, наличие сопутствующих заболеваний, мотивация к лечению и даже уровень поддержки со стороны близких. Такой подход позволяет не просто временно снять симптомы, а добиться реального внутреннего изменения и стойкой ремиссии.
Детальнее – https://lechenie-narkomanii-novokuzneczk0.ru
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Осуществить глубокий анализ – https://ghizmohealing.com/?p=503
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Более того — здесь – https://blogi.eoppimispalvelut.fi/fuksiat/2020/02/06/etsitko-mokkimajoitusta-inarijarvelta
В этой публикации мы сосредоточимся на интересных аспектах одной из самых актуальных тем современности. Совмещая факты и мнения экспертов, мы создадим полное представление о предмете, которое будет полезно как новичкам, так и тем, кто глубоко изучает вопрос.
Исследовать вопрос подробнее – https://www.videoton1990.it/videoton-a-un-passo-dal-colpaccio-la-domus-vince-4-5-new-vidi-team-ok-col-futsei
capitalbridge.bond – Confident layout, pages feel polished while remaining easy to read and follow.
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Изучить материалы по теме – https://allsportapparel.com/links/week685.asp
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Читать дальше – https://sabkhojo.net/rrb-railway-technician-admit-card-out-2024
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Углубить понимание вопроса – https://www.defining-blog.ru/tag/straxovoj-polis
safe bond portal – Well-organized layout makes browsing options smooth.
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
А что дальше? – https://mydownloadables.com/christmas-tree-ribbon-vector-download
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Информация доступна здесь – https://www.jaunas-euro-banknotes.eu/un-rau-cat-o-civilizatie
В этом информативном тексте представлены захватывающие события и факты, которые заставят вас задуматься. Мы обращаем внимание на важные моменты, которые часто остаются незамеченными, и предлагаем новые перспективы на привычные вещи. Подготовьтесь к тому, чтобы быть поглощенным увлекательными рассказами!
Всё, что нужно знать – https://www.computershala.com/how-angular-application-start
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Заходи — там интересно – http://peterchayward.com/notthatkindofmarathon/bechdel-test-bad-neighbours-313
Врач уточняет, как долго продолжается запой, какой алкоголь употребляется, а также наличие сопутствующих заболеваний. Этот тщательный анализ позволяет оперативно подобрать оптимальные методы детоксикации и снизить риск осложнений.
Получить дополнительные сведения – вывод из запоя в стационаре
clarity journey – Wording combines clarity and purpose, inspiring tangible action.
Капельницы от запоя включают препараты для очищения крови, восстановления электролитного баланса и защиты печени. Используются только сертифицированные растворы, одобренные Минздравом РФ. В клинике применяется комплексный подход: одновременно с физическим восстановлением запускаются лёгкие дыхательные и релаксационные методики, которые помогают организму вернуться в стабильное состояние.
Подробнее тут – http://vyvod-iz-zapoya-v-voronezhe17.ru
Благодаря этому подходу пациент выходит из состояния запоя без стресса и с минимальной нагрузкой на организм, что ускоряет процесс восстановления.
Детальнее – вывод из запоя на дому недорого красноярск
midnight cove catalog – Consistent dark style, site navigation is clear and checkout feels efficient.
После прохождения основной программы пациенту предлагается поддерживающее наблюдение. Оно может включать дистанционные консультации, участие в группе профилактики срывов, повторные осмотры нарколога и психолога, корректировку медикаментозной схемы. В рамках реабилитации формируются планы действий при возникновении тяги, обучаются навыки сопротивления стрессу и внешнему давлению. При желании можно подключить родственников к процессу постлечебной адаптации, чтобы укрепить результат и снизить риски рецидивов. Таким образом, пациент не остаётся один даже после выписки.
Разобраться лучше – лечение наркомании на дому в новокузнецке
Ниже приведена таблица с типовыми компонентами капельницы и их действием:
Разобраться лучше – вывод из запоя тольятти
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Узнать больше – нарколог на дом вывод воронеж
Анонимная наркологическая помощь — это управляемая система, где каждый шаг прозрачно связан с целью и измеримым результатом. В наркологической клинике «ЕнисейМед Центр» мы соединяем круглосуточную доступность, мягкую логистику и модульный план лечения, чтобы пациент и семья понимали, почему именно сейчас назначается то или иное вмешательство и когда оно будет остановлено. Мы избегаем полипрагмазии: запускаем один модуль — ставим один маркер — определяем «окно оценки» — выключаем модуль, как только цель достигнута. Такой подход бережёт ресурсы организма и сохраняет причинно-следственную связь.
Подробнее тут – наркологическая клиника нарколог в красноярске
Лечение зависимости в наркологической клинике проводится поэтапно. Это обеспечивает постепенное восстановление организма и исключает риск осложнений. Каждый этап направлен на устранение конкретных нарушений, вызванных употреблением психоактивных веществ.
Получить дополнительную информацию – http://narcologicheskaya-klinika-v-krasnoyarske17.ru
В таблице представлены основные виды терапии, применяемые в клинике:
Узнать больше – http://narcologicheskaya-klinika-v-novokuzneczke17.ru/narkologiya-gorod-novokuzneczk/https://narcologicheskaya-klinika-v-novokuzneczke17.ru
Наркологическая клиника в Воронеже — это специализированное медицинское учреждение, предоставляющее помощь людям, столкнувшимся с зависимостью от алкоголя, наркотиков и других психоактивных веществ. Лечение проводится под контролем квалифицированных врачей, с использованием современных методик детоксикации, психотерапии и реабилитации. Цель работы специалистов — не только устранить физическую зависимость, но и помочь пациенту восстановить эмоциональное равновесие, вернуть контроль над поведением и мотивацию к трезвости.
Подробнее – https://narkologicheskaya-clinica-v-voronezhe17.ru/narkolog-voronezh-anonimno/
Своевременная постановка капельницы помогает избежать тяжёлых последствий запоя. Поводом для обращения к врачу являются симптомы выраженной интоксикации:
Детальнее – http://kapelnicza-ot-zapoya-v-volgograde17.ru/kapelnicza-ot-alkogolya-volgograd/
Цель
Подробнее тут – http://
Что включено на практике
Ознакомиться с деталями – http://narkologicheskaya-klinika-odincovo0.ru/chastnaya-narkologicheskaya-klinika-v-odincovo/
Инфузионная терапия подбирается под человека, а не под «среднюю» ситуацию. Базовый каркас обычно включает растворы для регидратации и коррекции электролитов, витамины группы B и магний для поддержки нервной системы. По показаниям добавляются гепатопротекторы и антиоксидантные компоненты — это помогает печени и снижает оксидативный стресс. Если есть выраженная тошнота, подключаем противорвотные; при тревоге и нарушении сна — мягкие анксиолитики и седативные препараты, которые не «вырубают», а выравнивают ритмы и сохраняют контакт для мониторинга. Мы избегаем агрессивных «миксов», потому что избыточная седация может скрыть опасные симптомы и усложнить оценку состояния. Эффективность оцениваем не только по субъективному облегчению, но и по объективным метрикам: пульс, давление, сатурация, динамика тремора, аппетит, качество сна. Как только показатели стабилизируются, фарм-нагрузка снижается, а ведущую роль берет режим — питание, гидратация, спокойный вечерний ритуал, короткие бытовые активности.
Разобраться лучше – https://vyvod-iz-zapoya-krasnogorsk10.ru/
Лечение алкоголизма в Перми в условиях специализированной клиники обеспечивает высокий уровень безопасности и результативности. Пациенты получают квалифицированную помощь в комфортных условиях и под наблюдением опытных специалистов.
Узнать больше – клиника лечения алкоголизма
Для иллюстрации приведена таблица, отражающая распространённые методы терапии и их воздействие на организм:
Получить дополнительные сведения – наркологические клиники алкоголизм воронеж
Основу лечения составляет междисциплинарная команда: врач-нарколог, психиатр, психолог, медсестра и консультант по зависимому поведению. Каждый отвечает за свой участок работы, но общая цель едина — помочь пациенту безопасно пройти путь от детокса до устойчивого состояния. Благодаря единому плану и регулярным консилиумам врачей, исключаются противоречия и дублирование процедур. Это экономит ресурсы организма и делает процесс прогнозируемым.
Детальнее – https://narkologicheskaya-clinica-v-krasnoyarske17.ru
Пациент может выбрать анонимный формат — все данные защищены, а пребывание в клинике проходит в атмосфере уважения и деликатности. Особое внимание уделяется созданию комфортных условий: палаты оснащены системой вентиляции, регулируемым освещением и кнопкой вызова медперсонала. Круглосуточный контроль состояния позволяет своевременно реагировать на малейшие изменения и корректировать курс лечения.
Изучить вопрос глубже – наркологическая клиника стационар в воронеже
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Узнать больше – вывод из запоя капельница
В Тольятти клиника «ВолгаМед Тольятти» предоставляет широкий спектр услуг — от экстренного вывода из запоя на дому до длительных реабилитационных программ. Выезд нарколога осуществляется круглосуточно: врач приезжает по вызову, проводит диагностику, оценивает степень интоксикации и назначает индивидуальный план лечения. Это особенно важно в тех случаях, когда пациент не может самостоятельно добраться до клиники. В арсенале специалистов — профессиональное оборудование, капельницы для детоксикации и препараты для стабилизации психоэмоционального состояния.
Получить дополнительные сведения – центр наркологической помощи тольятти
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Подробнее – вывод из запоя в волгограде
Что включено на практике
Разобраться лучше – наркологическая клиника анонимная помощь нарколога
Перед таблицей важное пояснение: она помогает соотнести риски и плотность наблюдения ещё до осмотра. Окончательное решение принимает врач по клинической картине и переносимости, но ориентир даст понимание маршрута и бюджета времени.
Узнать больше – наркологическая клиника стационар
Когда выбрать
Изучить вопрос глубже – частная наркологическая клиника
Клиника «КузбассМед Центр» в Новокузнецке обеспечивает непрерывный приём пациентов и выезд нарколога на дом. Такой формат позволяет оказать экстренную помощь при интоксикации или запое прямо на месте, не дожидаясь ухудшения состояния. Медицинская команда работает в режиме 24/7, что особенно важно при острых состояниях. Врач выезжает в течение часа после вызова, проводит диагностику, ставит капельницу и контролирует жизненные показатели. В стационаре доступны детоксикация, медикаментозная терапия и психотерапевтическая поддержка — всё под постоянным медицинским наблюдением.
Детальнее – http://narkologicheskaya-klinika-v-novokuzneczke17.ru
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Узнать больше – наркологическая клиника вывод из запоя в волгограде
Что включает на практике
Получить дополнительную информацию – https://narkologicheskaya-klinika-korolyov0.ru
Особенность подхода заключается в сочетании медицинской и психологической поддержки. После кодирования пациент получает консультации психотерапевта, рекомендации по восстановлению и профилактике рецидивов. Это снижает риск повторного срыва и помогает закрепить результат на долгий срок.
Углубиться в тему – кодирование от алкоголизма отзывы цены волгоград
Чтобы не оценивать состояние субъективно, в клинике применяется система наблюдения за ключевыми параметрами. Таблица помогает врачу и пациенту видеть реальную динамику и корректировать вмешательства только при необходимости.
Подробнее тут – http://
Благодаря последовательной работе врачей и постоянному наблюдению лечение проходит безопасно и эффективно, а пациент получает необходимую поддержку на всех этапах терапии.
Ознакомиться с деталями – http://narkologicheskaya-klinika-v-voronezhe17.ru/voronezh-narkologicheskij-dispanser/https://narkologicheskaya-klinika-v-voronezhe17.ru
Комплексное лечение помогает восстановить работу печени, сердца и нервной системы. Пациенты отмечают улучшение сна, снижение тревожности, нормализацию давления и аппетита уже спустя несколько часов после начала терапии. В зависимости от тяжести состояния курс может быть продлён до 2–3 дней с круглосуточным наблюдением и корректировкой дозировок.
Углубиться в тему – скорая вывод из запоя волгоград
Одним из ключевых направлений работы клиники является проведение инфузионных процедур. Капельницы позволяют вывести токсины, нормализовать давление и улучшить общее состояние пациента. Подбор препаратов проводится индивидуально, с учётом физического состояния, возраста и стадии зависимости.
Получить дополнительную информацию – http://narkologicheskaya-pomoshh-v-tolyatti17.ru/
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Изучить вопрос глубже – нарколог на дом вывод уфа
В Одинцово доступен гибкий маршрут: выездная бригада 24/7 и стационар. Домашний формат хорош при умеренной симптоматике и сохранённом контакте — он позволяет избежать перевозок и сохранить конфиденциальность. Стационар предпочтителен при длительном эпизоде, повторной рвоте, выраженной слабости, нестабильном давлении/пульсе, спутанности сознания, судорожной готовности, а также у пациентов старшего возраста и при тяжёлой соматике (ИБС, гипертония, диабет, хронические болезни печени/почек). Мы оцениваем не один признак, а совокупность факторов и динамику, чтобы не «пересидеть» дома там, где нужен приборный мониторинг. В обоих вариантах сохраняется наш принцип: индивидуализация схемы, осторожная седация, прицельная работа со сном, прозрачные объяснения назначений — и всё это с опорой на объективные показатели, а не ощущения «полегчало/ухудшилось».
Получить дополнительные сведения – вывод из запоя клиника
Важной частью реабилитации является социализация пациента, возвращение его к активной общественной жизни и формирование новых, здоровых привычек. Для этого в клинике организуются различные мероприятия и программы адаптации.
Узнать больше – лечение наркомании реабилитация
Что делаем фактически
Изучить вопрос глубже – https://narkologicheskaya-klinika-ehlektrostal0.ru/chastnaya-narkologicheskaya-klinika-v-ehlektrostali/
Две похожие ситуации никогда не бывают одинаковыми: возраст, вес, сопутствующие болезни, длительность запоя и переносимость препаратов формируют уникальную клиническую картину. Мы исключаем «универсальные» схемы, чтобы не перегрузить организм и не вызвать побочных реакций. Инфузии проводятся только одноразовыми системами, врач соблюдает стерильность, контролирует дозировки и следит за динамикой симптомов. Мы уделяем особое внимание сну и уровню тревоги в первые часы после детокса — именно эти параметры влияют на риск срыва. Для пациентов с сердечно-сосудистыми, эндокринными и неврологическими заболеваниями детоксикация планируется особенно осторожно; при малейших сомнениях мы предлагаем стационар и разъясняем семье, почему это безопаснее.
Выяснить больше – vyvod iz zapoya
«КузбассМед Центр» специализируется на лечении алкогольной и наркотической зависимости, восстановлении организма после интоксикации и профилактике рецидивов. В таблице приведены ключевые направления работы и их особенности.
Получить дополнительные сведения – лечение в наркологической клинике в новокузнецке
В клинике «ВолгоградМед Альянс» применяются разные методы кодирования, позволяющие подобрать оптимальный вариант для каждого пациента. Выбор зависит от медицинских показаний, психологической готовности и длительности ремиссии. В таблице ниже представлены основные методики, их особенности и преимущества.
Выяснить больше – http://
интернет агентство продвижение сайтов сео poiskovoe-seo-v-moskve.ru .
seo блог seo блог .
Ожидаемая траектория в первые сутки
Узнать больше – наркологическая клиника со стационаром
Для жителей Красноярска организованы два конфиденциальных пути. Первый — немаркированный выезд бригады на дом с заранее согласованными порогами связи. Второй — «тихий вход» в клинику через отдельную дверь, где приём проходит без очередей и «коридорных» разговоров. На первичном звонке администратор уточняет только клинически значимые факторы: частоту рвоты, наличие мочеиспускания, ЧСС/АД в покое, эпизоды спутанности, актуальные лекарства и аллергии. Биографические подробности и лишние вопросы не задаются — мы придерживаемся принципа минимально необходимой информации.
Подробнее тут – наркологическая клиника клиника помощь
Клиника «ВоронежМед Альянс» придерживается принципа прозрачной медицины: каждый шаг понятен пациенту, решения принимаются совместно, а результаты фиксируются по объективным показателям. Такой формат создаёт чувство безопасности и доверия. Среди основных принципов:
Подробнее можно узнать тут – наркологическая клиника клиника помощь
Вызов нарколога на дом — это удобная и безопасная возможность получить медицинскую помощь без необходимости ехать в клинику. Такая услуга особенно востребована, когда состояние пациента не позволяет покинуть дом, а помощь требуется незамедлительно. В наркологической клинике «ВоронМед Профи» организована круглосуточная служба выезда специалистов, которая оперативно реагирует на обращения и обеспечивает профессиональную помощь при запое, алкогольной интоксикации и обострениях хронических состояний. Врач приезжает в течение часа, оценивает состояние пациента и подбирает оптимальную схему лечения, включающую капельницы, детоксикацию и рекомендации по восстановлению организма.
Получить дополнительную информацию – выезд нарколога на дом
Комплексное применение этих методов позволяет значительно ускорить процесс восстановления и предотвратить осложнения.
Получить дополнительную информацию – наркологическая клиника цены новокузнецк
about 1win http://www.1win5745.help
Врач приезжает с одноразовыми системами и препаратами, проводит экспресс-диагностику, стартует инфузии и каждые 15–20 минут оценивает динамику, корректируя темп и состав. По завершении — памятка по режиму, гигиене сна, питанию и запретам на 24–72 часа, а также контакты для связи ночью.
Изучить вопрос глубже – vyvod-iz-zapoya-kruglosutochno
Детоксикация — это первый и важнейший этап лечения в наркологической клинике в Красноярске. Она проводится с целью выведения токсинов из организма и восстановления функций жизненно важных органов. Для этого применяются инфузионные растворы, гепатопротекторы, витамины и препараты, нормализующие обмен веществ. После снятия интоксикации пациент получает медикаментозную поддержку, направленную на снижение тяги к алкоголю или наркотикам и стабилизацию эмоционального состояния.
Подробнее – запой наркологическая клиника в красноярске
Выездная наркологическая помощь организована по чётко выстроенной схеме. Каждый этап направлен на стабилизацию состояния и безопасное восстановление функций организма после алкогольного или наркотического воздействия.
Получить больше информации – https://narkolog-na-dom-v-ufe17.ru/narkolog-ufa-anonimno
focus main – Simple, powerful language reinforces focus as a practical advantage.
Цель и ожидаемая динамика
Углубиться в тему – narkologicheskaya-klinika-otzyvy
Запой представляет собой состояние, при котором организм находится под постоянным воздействием этанола. Это вызывает интоксикацию, нарушение обменных процессов и дестабилизацию психики. При обращении за помощью врач-нарколог оценивает состояние пациента и подбирает индивидуальную схему терапии, чтобы безопасно вывести человека из запоя и предотвратить развитие синдрома отмены. Вмешательство проводится как в стационаре, так и на дому, в зависимости от состояния пациента.
Разобраться лучше – вывод из запоя на дому цена красноярск
Ниже — ориентир, который помогает сопоставить риски, плотность наблюдения и ожидаемую скорость стабилизации. Таблица не заменяет очный осмотр, но экономит время на принятие решений и делает логику врача понятной всей семье.
Подробнее можно узнать тут – https://narkologicheskaya-klinika-odincovo0.ru/chastnaya-narkologicheskaya-klinika-v-odincovo
Во время лечения фиксируются все жизненные показатели пациента. При необходимости проводится экспресс-анализ крови и ЭКГ. Ниже представлена таблица, показывающая, какие параметры контролируются и по каким признакам оценивается стабилизация состояния.
Исследовать вопрос подробнее – наркология вывод из запоя в воронеже
Процедура начинается с осмотра пациента и оценки степени интоксикации. Врач измеряет давление, пульс, уровень насыщения крови кислородом, определяет наличие сопутствующих заболеваний. После диагностики назначается капельница, состав которой подбирается индивидуально. Процедура направлена на очищение организма, восстановление водно-солевого баланса и снятие симптомов похмелья.
Детальнее – https://vyvod-iz-zapoya-v-tolyatti17.ru/vyvod-iz-zapoya-na-domu-tolyatti-otzyvy/
Вывод из запоя — это медицинская процедура, направленная на очищение организма от продуктов распада алкоголя и восстановление нормальной работы внутренних органов. В клинике «Трезвый Путь Волгоград» пациентам оказывается профессиональная помощь с использованием современных методов дезинтоксикации, медикаментозной поддержки и психологического сопровождения. Лечение проводится круглосуточно, включая выезд нарколога на дом. Такой формат помогает быстро стабилизировать состояние пациента, минимизировать риск осложнений и обеспечить безопасность при выходе из запоя любой продолжительности.
Изучить вопрос глубже – https://vivod-iz-zapoya-v-volgograde17.ru/anonimnaya-narkologiya-vyvod-iz-zapoya-volgograd/
Вывод из запоя в Красноярске — это медицинская процедура, направленная на устранение алкогольной интоксикации и восстановление нормальной работы организма после длительного употребления спиртных напитков. Услуга предоставляется круглосуточно и включает дезинтоксикационную терапию, стабилизацию психоэмоционального состояния и профилактику осложнений. Все процедуры выполняются опытными наркологами с применением сертифицированных препаратов и в строгом соответствии с медицинскими стандартами.
Подробнее тут – вывод из запоя на дому цена красноярск
Если вы ищете информацию о проходим техосмотр в Санкт-Петербурге, посетите специализированный сайт для получения актуальных услуг и цен.
Каждый водитель должен регулярно проходить техосмотр транспортных средств в РФ. Техосмотр помогает поддерживать безопасность на автодорогах, избегая потенциальных инцидентов. Отсутствие техосмотра не позволит застраховать автомобиль по ОСАГО.
В СПб организованы удобные станции для проведения техосмотра в различных районах. В ходе процесса оцениваются важные элементы авто, после чего выдается подтверждающий акт.
Сначала водителю нужно подготовить необходимые документы, такие как паспорт и свидетельство о регистрации. Далее необходимо явиться на пункт для детального осмотра, во время которого оцениваются тормоза и прочие компоненты. В конце выдаётся диагностическая карта, подтверждающая соответствие нормам.
Процедура охватывает диагностику тормозной системы, осветительных приборов и иных важных частей. Также проверяются шины на износ и соответствие сезонным нормам. Все элементы должны полностью соответствовать установленным государственным стандартам.
В СПб работает обширная сеть аккредитованных пунктов по проведению техосмотра. Например, один из центров расположен на Московском проспекте, где можно записаться заранее. Ещё один вариант — станции в Приморском районе, где всё спланировано для быстрого обслуживания.
Подберите подходящий пункт, основываясь на близости и отзывах других водителей. Проверьте часы работы центра заранее, чтобы спланировать визит без проблем. Запишитесь онлайн или по телефону для удобства и экономии времени.
Регулярный техосмотр продлевает срок службы автомобиля и повышает его надёжность. Такая процедура уменьшает шансы на инциденты и экономит средства на последующие ремонты. Соблюдайте график, чтобы избежать проблем с законом и обеспечить комфортное вождение.
При просрочке процедуры водитель получит наказание в виде штрафа от дорожной инспекции. Поэтому не игнорируйте сроки и проходите осмотр вовремя. Оставайтесь дисциплинированными, чтобы вносить вклад в общий порядок в движении.
Формат
Исследовать вопрос подробнее – http://narkologicheskaya-klinika-serpuhov0.ru
Мы строим лечение вокруг предсказуемости: минимум лишних вопросов, максимум конкретики и понятный план на ближайшие сутки. Дежурный врач уточняет только то, что влияет на безопасность — длительность эпизода, актуальные лекарства и переносимость, сон и апетит, наличие поддержки дома. Из этого скелета рождается маршрут: выезд на дом, приём без очередей или стационар с наблюдением 24/7. Конфиденциальность встроена по умолчанию: нейтральная коммуникация, доступ к карте только у вовлечённой команды, документы по запросу — в нейтральных формулировках. Внешний шум гасим, внимание переводим на цель: ровная стабилизация без «качелей» и с понятными контрольными точками.
Ознакомиться с деталями – https://narkologicheskaya-klinika-domodedovo0.ru/narkologicheskaya-klinika-telefon-v-domodedovo/
Вывод из запоя — это не просто медицинская процедура, а тщательно выстроенный процесс, направленный на восстановление работы всех систем организма. При неправильном или неполном лечении риск осложнений возрастает в несколько раз. Поэтому обращение в профессиональную клинику становится необходимым шагом. В наркологической клинике «Центр Трезвости ВоронМед» пациент получает экстренную помощь, безопасные инфузионные препараты, круглосуточный выезд нарколога и последующее восстановление под наблюдением специалистов. Здесь каждая капельница подбирается индивидуально — с учётом возраста, веса, длительности запоя, хронических болезней и реакции организма на препараты.
Разобраться лучше – вывод из запоя
Цель
Ознакомиться с деталями – http://narkologicheskaya-klinika-shchyolkovo0.ru/narkologicheskaya-klinika-stacionar-v-shchyolkovo/https://narkologicheskaya-klinika-shchyolkovo0.ru
Своевременное обращение к специалистам позволяет быстро стабилизировать состояние и избежать осложнений.
Подробнее можно узнать тут – вывод из запоя на дому
internetagentur seo poiskovoe-seo-v-moskve.ru .
материалы по маркетингу statyi-o-marketinge2.ru .
Перед таблицей — важное пояснение: она помогает соотнести риски и плотность наблюдения ещё до осмотра. Окончательное решение принимает врач по клинической картине и переносимости, но ориентир даст понимание логики и бюджета времени.
Подробнее – https://narkologicheskaya-klinika-shchyolkovo0.ru/
Такой подход обеспечивает результативность и помогает добиться длительной ремиссии даже при тяжёлых формах зависимости.
Выяснить больше – наркологическая клиника в воронеже
Алкогольная интоксикация вызывает сильное обезвоживание и разрушает баланс электролитов в организме. Без медицинской помощи восстановление может занять несколько дней, а в тяжёлых случаях приводит к осложнениям. Капельница помогает безопасно и быстро вывести этанол и продукты его распада, восполнить уровень жидкости, снизить нагрузку на печень и сердечно-сосудистую систему. Процедура проводится амбулаторно или на дому, что делает её доступной и удобной для пациентов.
Получить дополнительные сведения – капельница от запоя недорого волгоград
Клиника в Волгограде руководствуется принципами индивидуального подхода, конфиденциальности и научно обоснованных методик. Врач-нарколог оценивает общее состояние пациента, определяет стадию зависимости и подбирает оптимальную терапевтическую схему. Лечение включает детоксикацию, медикаментозную поддержку, психотерапию и реабилитацию. Каждый пациент проходит лечение в безопасных условиях с постоянным медицинским наблюдением.
Изучить вопрос глубже – наркологическая клиника волгоград
Главное преимущество обращения в наркологическую клинику в Воронеже — комплексный подход к лечению зависимости. Специалисты учитывают медицинские, психологические и социальные факторы, влияющие на формирование зависимости. Каждая программа подбирается индивидуально: в зависимости от стадии заболевания, состояния здоровья и целей терапии. В процессе лечения применяются детоксикация, медикаментозная поддержка, психотерапия и методы социальной адаптации.
Выяснить больше – вывод наркологическая клиника в воронеже
Клиника «ВоронежМед Альянс» придерживается принципа прозрачной медицины: каждый шаг понятен пациенту, решения принимаются совместно, а результаты фиксируются по объективным показателям. Такой формат создаёт чувство безопасности и доверия. Среди основных принципов:
Выяснить больше – https://narcologicheskaya-klinika-v-voronezhe17.ru/chastnaya-narkologicheskaya-klinika-voronezh/
Даже если симптомы кажутся незначительными, проведение инфузионной терапии значительно ускоряет процесс восстановления и предотвращает развитие осложнений.
Изучить вопрос глубже – http://kapelnicza-ot-zapoya-v-volgograde17.ru
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Получить больше информации – наркологическая клиника вывод из запоя
Правильный подбор лекарственных средств позволяет не только уменьшить проявления синдрома отмены, но и стабилизировать эмоциональное состояние пациента, снижая риск срывов. Реабилитационные программы включают физиотерапию, спортивные занятия и коррекцию образа жизни, что способствует полноценному восстановлению организма.
Получить дополнительные сведения – https://lechenie-narkomanii-tver0.ru/tver-lechenie-alkogolizma
Выделяется ряд преимуществ, которые делают терапию в клинике оптимальным решением для борьбы с зависимостью.
Узнать больше – http://lechenie-alkogolizma-perm0.ru/
В таблице представлены основные виды терапии, применяемые в клинике:
Детальнее – https://narcologicheskaya-klinika-v-novokuzneczke17.ru/narkolog-v-gorode-novokuzneczke
1win apk download latest version http://www.1win5745.help
Все растворы проходят фармацевтический контроль, а процедуры выполняются одноразовыми стерильными инструментами. После завершения капельницы врач наблюдает пациента в течение 15–30 минут, оценивает результат и даёт рекомендации по дальнейшему восстановлению. Важно не прерывать терапию самостоятельно — эффект закрепляется только при соблюдении рекомендаций.
Получить дополнительную информацию – помощь нарколога на дому
Лечение в клинике «ВоронежМед Альянс» проходит поэтапно. Каждый модуль имеет определённую цель и собственные критерии эффективности. Такой подход исключает избыточное вмешательство и обеспечивает прозрачность процесса восстановления.
Выяснить больше – платная наркологическая клиника
Лечение зависимости в наркологической клинике проводится поэтапно. Это обеспечивает постепенное восстановление организма и исключает риск осложнений. Каждый этап направлен на устранение конкретных нарушений, вызванных употреблением психоактивных веществ.
Изучить вопрос глубже – анонимная наркологическая клиника красноярск
продвижение сайта франция poiskovoe-seo-v-moskve.ru .
блог агентства интернет-маркетинга statyi-o-marketinge2.ru .
download 1win app for android http://www.1win5745.help
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Получить дополнительную информацию – вывод из запоя капельница волгоград
Формат
Получить дополнительные сведения – https://narkologicheskaya-klinika-odincovo0.ru
Лечение в клинике «ВоронежМед Альянс» проходит поэтапно. Каждый модуль имеет определённую цель и собственные критерии эффективности. Такой подход исключает избыточное вмешательство и обеспечивает прозрачность процесса восстановления.
Подробнее можно узнать тут – наркологическая клиника нарколог воронеж
Когда выбрать
Детальнее – narkologicheskaya-klinika-telefon
Терапия строится из узких модулей с чёткими «выключателями». Мы не «усиливаем» схему без показаний — каждое расширение привязано к конкретной цели и времени переоценки. Ниже — ориентир по основным программам «ЕнисейМед Центра».
Подробнее тут – наркологическая клиника нарколог в красноярске
В таблице представлены основные виды терапии, применяемые в клинике:
Получить дополнительную информацию – частная наркологическая клиника
Во время процедуры врач фиксирует ключевые параметры, чтобы убедиться в безопасности и эффективности терапии. Мониторинг проводится при каждом выезде и помогает отслеживать динамику в режиме реального времени. В таблице ниже указаны основные показатели, за которыми следит специалист.
Подробнее тут – нарколог на дом вывод
Лечение наркомании в клинике начинается с диагностики, позволяющей определить степень зависимости, выявить сопутствующие заболевания и выбрать оптимальную тактику терапии. Важным этапом является детоксикация — очищение организма от токсинов и продуктов распада наркотических веществ, что снижает риск осложнений и облегчает последующее восстановление.
Углубиться в тему – лечение наркомании диспансер
В этой статье вы найдете познавательную и занимательную информацию, которая поможет вам лучше понять мир вокруг. Мы собрали интересные данные, которые вдохновляют на размышления и побуждают к действиям. Открывайте новую информацию и получайте удовольствие от чтения!
Смотрите также – https://www.tsf.edu.pl/zapomniane-metody-fotografii
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Открой скрытое – https://tabriz118.com/blog/articles/item/176-howtorepaircomposite.html?start=2530
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Подробнее – https://db-it.dk/document-store
Каждый из этапов сопровождается контролем врача и постепенным снижением медикаментозной нагрузки. Важно не просто снять симптомы, но и научить пациента распознавать внутренние триггеры, чтобы предотвратить рецидив. На протяжении всего лечения сохраняется поддержка психолога, который помогает адаптироваться и перестроить привычные модели поведения.
Ознакомиться с деталями – наркологические клиники алкоголизм
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Узнать больше > – https://dl.sbu.ac.ir/downloads/1123
Мы переводим субъективное «полегчало» в наблюдаемые факты. Быстрее всего меняются переносимость воды и интенсивность тошноты; вслед за этим «садится» пульс/давление и на 3+ пункта снижается тремор. «Первая ночь» — экзамен устойчивости: цель — ? 6 часов сна и не более одного пробуждения. Утром — две «малые победы» (гигиена, 10–15 минут тихой ходьбы) без «отката». При такой динамике модули по плану выключаются, пациент получает короткую карту самопомощи на 72 часа: светогигиена, интервалы питья, дыхательные ритмы, речевые правила семьи и пороги связи с дежурным.
Узнать больше – наркологическая клиника наркологический центр в красноярске
Лечение зависимости в наркологической клинике проводится поэтапно. Это обеспечивает постепенное восстановление организма и исключает риск осложнений. Каждый этап направлен на устранение конкретных нарушений, вызванных употреблением психоактивных веществ.
Изучить вопрос глубже – narcologicheskaya-klinika-v-krasnoyarske17.ru/
Наркологическая клиника — это пространство, где медицинская наука сочетается с психологической поддержкой и индивидуальным подходом к каждому пациенту. В клинике «ВоронежМед Альянс» лечение зависимости организовано по принципам доказательной медицины: каждый этап терапии основан на объективных данных, контролируемых результатах и четких критериях эффективности. Здесь помогают не просто устранить физические последствия зависимости, но и восстановить внутренние ресурсы человека, вернуть уверенность, осознанность и способность строить новую жизнь без алкоголя и наркотиков.
Выяснить больше – https://narcologicheskaya-klinika-v-voronezhe17.ru/
Современные методы лечения в наркологической клинике в Новокузнецке основаны на доказательной медицине. При поступлении пациент проходит полное обследование, включающее оценку физического состояния, психоэмоционального фона и наличия сопутствующих заболеваний. На основе полученных данных составляется персональная программа терапии, охватывающая медицинский, психологический и социальный аспекты выздоровления.
Углубиться в тему – https://narcologicheskaya-klinika-v-novokuzneczke17.ru/narkologicheskij-czentr-novokuzneczk
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Детали по клику – https://www.igmmvkaithal.com/mera-pehla-vote-desh-ke-liye
Продолжительность процедуры — от 40 минут до полутора часов. Уже в первые часы после начала терапии состояние пациента значительно улучшается: проходит тошнота, снижается тревожность, восстанавливается координация движений.
Изучить вопрос глубже – вывод из запоя тольятти
Первым шагом при лечении зависимости является детоксикация — очищение организма от токсинов, накопившихся в результате употребления алкоголя или наркотиков. Врач подбирает состав инфузионных растворов и лекарственных препаратов индивидуально. Процедура направлена на восстановление обмена веществ, улучшение работы печени и сердца, нормализацию сна и аппетита. После завершения детоксикации пациент чувствует облегчение, снижается тревожность и повышается концентрация внимания.
Изучить вопрос глубже – анонимная наркологическая клиника в волгограде
Процесс детоксикации проходит поэтапно, чтобы организм успевал адаптироваться к изменениям и не испытывал стресс. Каждый шаг направлен на достижение конкретного терапевтического эффекта. Ниже представлена таблица, отражающая ключевые стадии процедуры, применяемой в клинике «Трезвый Путь Волгоград».
Углубиться в тему – вывод из запоя цена
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Ознакомиться с деталями – https://ilchiccodisenape.org/2023/12/20/splai-spazi-liberi-dallapartheid-israeliana
В обзорной статье вы найдете собрание важных фактов и аналитики по самым разнообразным темам. Мы рассматриваем как современные исследования, так и исторические контексты, чтобы вы могли получить полное представление о предмете. Погрузитесь в мир знаний и сделайте шаг к пониманию!
Не упусти важное! – https://www.theworld.guru/heroes-of-the-storm-global-championship-2017-starts-tomorrow-heres-what-you-need-to-know
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Погрузиться в детали – https://professorchrisbrummer.com/fraud-nepotism-doom-nutty-prof-chris-brummer-shady-path-cftc
Эта информационная заметка содержит увлекательные сведения, которые могут вас удивить! Мы собрали интересные факты, которые сделают вашу жизнь ярче и полнее. Узнайте нечто новое о привычных аспектах повседневности и откройте для себя удивительный мир информации.
Полезно знать – https://blog.iodonna.it/animali/2018/01/27/acquario-di-genova-dietro-le-quinte
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Углубить понимание вопроса – https://www.isabelkronenberger.de/test
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Изучить эмпирические данные – https://fajaspao.com/corset-ventre-plat
профессиональное продвижение сайтов профессиональное продвижение сайтов .
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Получить дополнительную информацию – https://www.ocweekly.com/the-10-best-mexican-metal-bands-6589907
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Изучить вопрос глубже – https://person.russian.city/moscow/408533482
seo и реклама блог statyi-o-marketinge2.ru .
Острый запой — это нарушение работы сердца, мозга, печени и нервной системы, а не просто «лишние пару дней выпивки». Когда начинается тремор, потливость, скачки давления, бессонница, паника, семья часто пытается помочь самостоятельно: даёт случайные таблетки, сомнительные «антипохмельные коктейли», сильные седативные. В реальности такие меры нередко ухудшают ситуацию: давление падает или «скачет», дыхание угнетается, симптомы предделирия маскируются, и момент, когда нужна экстренная помощь, пропускается. Выездной нарколог «ЩёлковоМед Профи» в Щёлково работает иначе: ещё по телефону собираются ключевые данные — возраст, длительность запоя, сопутствующие заболевания, принимаемые лекарства, аллергии, примерные показатели АД и пульса, особенности поведения. Это позволяет заранее оценить риски и понять, подходит ли формат на дому. На месте врач измеряет давление, пульс, сатурацию, температуру, оценивает степень обезвоживания, выраженность тремора, неврологический статус, наличие дезориентации, смотрит, не требуется ли сразу стационар. Капельница назначается по фактическим показателям: без «универсальных коктейлей», без опасной седации, с учётом сердца, печени, эндокринных и неврологических особенностей. Такой подход снижает нагрузку на организм и делает результат управляемым — облегчение наступает без лишнего риска.
Подробнее можно узнать тут – сколько стоит нарколог на дом
Откройте для себя скрытые страницы истории и малоизвестные научные открытия, которые оказали колоссальное влияние на развитие человечества. Статья предлагает свежий взгляд на события, которые заслуживают большего внимания.
Познакомиться с результатами исследований – https://museedefunes.fr/?lang=en
commercial link click – Clear content, assists users in navigating professional connections effectively.
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Только факты! – https://mailprof.net/product/envo-hoodie-6
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Подробнее – narkologicheskaya-klinika-otzyvy
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Читать далее > – https://person.russian.city/moscow/409454044
Основные этапы обычно включают:
Ознакомиться с деталями – http://vyvod-iz-zapoya-ramenskoe10.ru/srochnoe-vyvedenie-iz-zapoya-v-ramenskom/
Письменные рекомендации: сон, питание, гидратация, запреты, «красные флаги», график амбулаторных визитов; при недостатке ресурсов дома — перевод в стационар без задержек. Такая последовательность убирает импровизацию и делает результат повторяемым.
Выяснить больше – вывод из запоя
Когда вопрос стоит остро — нужно быстро и безопасно вывести человека из запоя в Коломне, — у семьи нет лишнего времени на эксперименты с таблетками, сомнительными «коктейлями» и советами из интернета. «Трезвый Центр Коломна» выстраивает помощь так, чтобы от первого звонка до реального облегчения шёл понятный и управляемый маршрут: запись симптомов и рисков уже по телефону, предложение формата (выезд на дом или стационар), оперативный осмотр, персональная инфузионная терапия, круглосуточное наблюдение при необходимости и подробный план восстановления на 24–72 часа и дальше. Мы не продаём миф о «чудо-капельнице за час», а работаем клинически аккуратно: дозы и схемы подбираются под возраст, длительность запоя, сопутствующие заболевания, уже принятые лекарства и текущие показатели. Цель проста и честна — снять интоксикацию, защитить сердце, мозг и печень, вернуть сон и ясность без агрессивной седации и скрытых рисков, сохранить конфиденциальность и дать семье уверенность, что всё делается правильно.
Углубиться в тему – http://vyvod-iz-zapoya-kolomna10.ru
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Получить больше информации – http://vyvod-iz-zapoya-v-ryazani17.ru
Один из ключевых принципов клиники «ЗдороваяСамара» — строгое соблюдение медицинской тайны. Все обращения, анализы и процедуры происходят в режиме полной конфиденциальности. При необходимости пациент может быть зарегистрирован под псевдонимом, а договор оформляется на доверенное лицо. Персональные данные не передаются ни в какие внешние базы, а диагноз не указывается в выписке для работодателя или страховой. Врачи и администрация клиники прошли специальное обучение по работе с анонимными пациентами, чтобы гарантировать этичность и законность каждой процедуры.
Узнать больше – принудительное лечение наркомании
В этих ситуациях выезд нарколога на дом позволяет вовремя скорректировать состояние, а при выявлении опасных признаков — не теряя времени, направить пациента в стационар. Это управляемый маршрут вместо хаотичных решений в последний момент.
Подробнее – http://narkolog-na-dom-dolgoprudnij10.ru/vyzvat-narkologa-na-dom-v-dolgoprudnom/
Процесс организован так, чтобы снять с семьи хаос и дать понятный сценарий. После обращения в «РеутовМед Сервис» пациент быстро попадает в поле зрения врача: или через выезд по адресу, или через стационар, если состояние уже близко к опасному. На месте проводится полноценная оценка: давление, пульс, сатурация, температура, осмотр сердца и дыхания, степень обезвоживания, выраженность тремора, наличие рвоты, боли в груди или животе, неврологический статус, поведение, признаки психоза. На основе этих данных формируется индивидуальный план детоксикации. Стартовая инфузионная терапия подбирается с учётом возраста, массы тела, длительности запоя, сопутствующих болезней, уже принятых препаратов. В стационаре пациента размещают в безопасных условиях, контролируют динамику, корректируют дозировки, не оставляют «на самотёк». При выводе из запоя на дому врач остаётся до стабилизации, отслеживает реакцию и при первых тревожных признаках рекомендует стационар, а не уезжает «лишь бы поставил капельницу». Такой пошаговый подход позволяет не только снять острые симптомы, но и уменьшить риск осложнений — от аритмий и судорог до алкогольного делирия.
Подробнее – http://vyvod-iz-zapoya-reutov10.ru/vyvod-iz-zapoya-v-stacionare-v-reutove/https://vyvod-iz-zapoya-reutov10.ru
Комплексное применение этих методов позволяет добиться быстрого восстановления организма и улучшения психоэмоционального состояния.
Ознакомиться с деталями – вывод из запоя на дому недорого в перми
«ОмскПрофи» укомплектована современной медицинской базой: передвижные аппараты для ЭКГ, инфузионные стойки, экспресс-анализаторы, мониторы состояния, аппараты ИВЛ (в реанимационных палатах). Штат сотрудников сформирован из врачей-наркологов, токсикологов, психиатров, психотерапевтов, медицинских сестёр, прошедших обучение по международным протоколам. Ведётся постоянная учёба, стажировки, участие в научных форумах. Благодаря этому пациенты получают не только медицинскую помощь, но и психологическое сопровождение, направленное на долгосрочный результат.
Подробнее можно узнать тут – наркологическая клиника клиника помощь
Лечение алкоголизма в клинике «РязаньМед Альянс» включает несколько этапов, каждый из которых направлен на определённую цель — от снятия интоксикации до формирования устойчивого отказа от алкоголя. В таблице представлены основные стадии лечения и методы, используемые специалистами клиники.
Ознакомиться с деталями – частная наркологическая клиника рязань
«Трезвый Путь Коломна» создаёт единый контур помощи: пациент не «перекидывается» между разными организациями, а проходит лечение в одной системе, где специалисты знают его историю и несут ответственность за последовательность шагов. Это критично для тех, кто уже сталкивался с бессистемными попытками: один врач ставил капельницы, другой «кодировал», третий давал советы, а в итоге всё заканчивалось новым срывом. Здесь маршруты связываются в цельную линию.
Ознакомиться с деталями – adresa-narkologicheskih-klinik
Когда запой длится не первый день, а состояние уже сопровождается тремором, потливостью, резкими перепадами давления, бессонницей, тревогой, тошнотой или рвотой, попытка «перетерпеть» или лечить самостоятельно таблетками становится опасным экспериментом. Сочетание алкоголя с сильнодействующими успокоительными, обезболивающими или сомнительными «антипохмельными» легко приводит к нарушению дыхания, провалам в сознании, аритмиям и скрытому развитию предделирия. Домашние средства не учитывают ни электролитные сдвиги, ни состояние печени и сердца, ни уже принятые лекарства. Выездной нарколог «СерпуховТрезвие» в Серпухове выстраивает ситуацию иначе: ещё по телефону врач собирает ключевую информацию — длительность запоя, примерные объёмы и виды алкоголя, наличие гипертонии, ИБС, диабета, заболеваний печени и почек, неврологических проблем, какие препараты уже давали и в каких дозах, были ли судороги или эпизоды дезориентации. На месте проводится объективная диагностика: измерение давления, пульса, сатурации, температуры, оценка тремора, степени обезвоживания, психического состояния, неврологического статуса. Только после этого принимается решение: проводить детокс на дому или сразу рекомендовать стационар. Такой фильтр защищает от грубых ошибок, позволяет точно подобрать схему и не терять драгоценное время, пытаясь «угадать» лечение.
Разобраться лучше – narkolog-na-dom-srochno
Терапия в клинике проводится поэтапно, что позволяет обеспечить безопасность и прозрачность процесса. Пациент постепенно проходит все стадии восстановления организма и психики.
Получить дополнительные сведения – частная наркологическая клиника в омске
Карта делает видимой причинно-следственную связь: пациент понимает, зачем и что именно делается; семья видит «точки проверки»; врач получает опору для изменения одного параметра без разрушения всего плана.
Получить больше информации – вывод из запоя круглосуточно
Процесс включает следующие шаги:
Исследовать вопрос подробнее – https://narcologicheskaya-klinika-v-krasnoyarske17.ru/narkologicheskaya-klinika-krasnoyarsk-otzyvy/
В основе работы клиники лежит принцип: зависимость — это не просто привычка и не «слабость характера», а комплексное заболевание, которое требует последовательного лечения, а не случайной капельницы по вызову. «Трезвый Шаг Раменское» отказывается от практики, когда пациенту предлагают один-единственный «волшебный» метод, не объясняя, что будет дальше. Здесь каждое обращение рассматривается в контексте стадии зависимости, общего состояния организма, психоэмоционального фона, семейной ситуации. Сначала специалисты снимают острые проявления: выход из запоя, детоксикация после употребления алкоголя, наркотиков или сочетаний, купирование абстиненции, коррекция давления, пульса, сна, тревоги. Затем формируется стабилизационный этап — подбор поддерживающих схем, работа с тягой, выравнивание эмоционального состояния. После этого при готовности пациента подключаются психотерапевтические и реабилитационные инструменты: мотивационные программы, работа с установками, триггерами, окружением. Важная особенность «Трезвый Шаг Раменское» — готовность объяснять семье и самому пациенту, зачем нужен каждый этап, какие цели у процедуры и какие результаты реально ожидать. Это снижает сопротивление, формирует доверие и делает путь не хаотичным, а управляемым.
Разобраться лучше – adresa-narkologicheskih-klinik
Такая последовательность действий позволяет обеспечить результативность и закрепить положительные изменения.
Ознакомиться с деталями – https://narcologicheskaya-klinika-perm0.ru/narkolog-perm-czeny/
Стационар «Трезвый Путь Коломна» ориентирован на безопасность в самых сложных случаях: длительные запои, тяжёлая абстиненция, смешанное употребление, выраженные соматические проблемы, риск делирия или судорог. Пациент попадает под наблюдение 24/7, что принципиально отличает клинику от домашних попыток «спасти своими средствами». Контроль жизненно важных показателей, своевременная коррекция схем лечения, возможность быстро отреагировать на осложнения — всё это снижает риск критических ситуаций, которые часто возникают именно после неумелых домашних вмешательств или «выездов без ответственности».
Подробнее тут – http://www.domen.ru
Такой алгоритм позволяет контролировать каждый аспект лечения, обеспечивая постепенное и безопасное восстановление. Врач-куратор отслеживает динамику и при необходимости корректирует программу.
Ознакомиться с деталями – наркологические клиники алкоголизм в рязани
В клинике применяются современные медицинские технологии, которые обеспечивают стойкий результат. Используемые методики соответствуют международным стандартам и регулярно обновляются.
Разобраться лучше – наркологическая клиника вывод из запоя омск
Профессиональный нарколог на дому не работает по схеме «чем больше препаратов, тем лучше». В «СерпуховТрезвие» капельницы составляются исходя из задач конкретного организма. Базовый блок — это растворы для восполнения объёма циркулирующей жидкости, выравнивания электролитного баланса и коррекции кислотно-щелочного состояния, что уменьшает нагрузку на сердце, мозг и снижает риск тяжёлых осложнений. Витамины группы B и магний входят в стандартную поддержку: они помогают стабилизировать нервную систему, уменьшить тремор, раздражительность, поддерживают сон и снижают риск судорог. При признаках поражения печени используются гепатопротективные и антиоксидантные компоненты, снижающие токсическое воздействие продуктов распада алкоголя. Если пациента мучает тошнота, добавляются противорвотные средства, чтобы восстановить возможность пить воду и питаться. Для снижения тревоги и нормализации сна применяются мягкие анксиолитики в дозировках, не маскирующих клиническую картину и не угнетающих дыхательный центр. Агрессивная седация, популярная в «серых» схемах, сознательно исключается: она «делает вид» улучшения, но может скрыть нарастающие осложнения. Эффект оценивается по конкретным критериям: стабилизация давления и пульса, уменьшение тремора, уход тошноты, улучшение цвета кожи, появление естественного сна и большей ясности мышления. После достижения этих ориентиров фармаконагрузка не наращивается, а постепенно снижается, чтобы человек выходил в устойчивое состояние, а не зависел от бесконечных капельниц.
Узнать больше – https://narkolog-na-dom-serpuhov10.ru/
Лечение алкоголизма в клинике «РязаньМед Альянс» включает несколько этапов, каждый из которых направлен на определённую цель — от снятия интоксикации до формирования устойчивого отказа от алкоголя. В таблице представлены основные стадии лечения и методы, используемые специалистами клиники.
Изучить вопрос глубже – наркологическая клиника наркологический центр рязань
Integrated business network – The layout and information flow feel natural and clear.
Медицинская помощь направлена не только на снятие острых симптомов, но и на стабилизацию работы организма в целом. Врачи стремятся к тому, чтобы пациент получил не временное облегчение, а фундамент для дальнейшей реабилитации.
Разобраться лучше – вывод из запоя дешево омск
Мы не используем универсальную «капельницу». Схема собирается из модулей под ведущие жалобы. Медицинские шаги всегда сочетаются с нефраком опорами — свет, тишина, вода малыми глотками, дыхание, — потому что среда усиливает действие препаратов и позволяет держать дозы ниже.
Детальнее – нарколог на дом недорого в саратове
Терапия в клинике строится на системном подходе, позволяющем постепенно восстанавливать здоровье и формировать новые жизненные установки.
Ознакомиться с деталями – https://narcologicheskaya-klinika-perm0.ru/narkolog-perm-czeny/
Острый запой — это нарушение работы сердца, мозга, печени и нервной системы, а не просто «лишние пару дней выпивки». Когда начинается тремор, потливость, скачки давления, бессонница, паника, семья часто пытается помочь самостоятельно: даёт случайные таблетки, сомнительные «антипохмельные коктейли», сильные седативные. В реальности такие меры нередко ухудшают ситуацию: давление падает или «скачет», дыхание угнетается, симптомы предделирия маскируются, и момент, когда нужна экстренная помощь, пропускается. Выездной нарколог «ЩёлковоМед Профи» в Щёлково работает иначе: ещё по телефону собираются ключевые данные — возраст, длительность запоя, сопутствующие заболевания, принимаемые лекарства, аллергии, примерные показатели АД и пульса, особенности поведения. Это позволяет заранее оценить риски и понять, подходит ли формат на дому. На месте врач измеряет давление, пульс, сатурацию, температуру, оценивает степень обезвоживания, выраженность тремора, неврологический статус, наличие дезориентации, смотрит, не требуется ли сразу стационар. Капельница назначается по фактическим показателям: без «универсальных коктейлей», без опасной седации, с учётом сердца, печени, эндокринных и неврологических особенностей. Такой подход снижает нагрузку на организм и делает результат управляемым — облегчение наступает без лишнего риска.
Подробнее тут – нарколог на дом вывод из запоя цена
Наркологическая клиника «ВолгаДок Медикал» — это круглосуточная служба помощи, выстроенная вокруг принципов клинической безопасности, прозрачной коммуникации и поддержки пациента на каждом этапе. Мы соединяем стационар и выездные бригады в единую систему: первичный осмотр и стабилизация состояния, адресные инфузионные модули, мягкая коррекция сна и тревоги, последующее наблюдение с короткими «окнами» обратной связи. Все решения принимаются по показаниям и сопровождаются объяснением: какую цель преследуем, каким маркером измеряем, когда проверяем результат. Такой подход исключает хаотичные усиления, бережёт ресурс организма и даёт прогнозируемый клинический эффект.
Углубиться в тему – наркологическая клиника клиника помощь саратов
Главная задача капельницы при выезде нарколога в Щёлково — не создать видимость лёгкости, а реально уменьшить интоксикацию и восстановить базовые функции организма. В «ЩёлковоМед Профи» используются современные схемы, а не сомнительные смеси «из всего подряд». В стандартной основе — растворы для восполнения объёма циркулирующей жидкости, выравнивания электролитного баланса и коррекции КЩС, что снижает нагрузку на сердце и мозг. Витамины группы B и магний поддерживают нервную систему, уменьшают тремор, раздражительность и риск судорожных реакций. При необходимости врач добавляет гепатопротекторные и антиоксидантные компоненты, если есть признаки перегрузки печени; при выраженной тошноте — противорвотные, чтобы пациент мог нормально пить и питаться. Для нормализации сна и тревоги подбираются мягкие анксиолитики в дозах, позволяющих контролировать состояние, а не «вырубать» человека. Агрессивные седативные протоколы, которые маскируют ухудшения и опасны для дыхания и сердца, сознательно исключаются. Оценка эффекта идёт по конкретным критериям: стабилизация давления и пульса, уменьшение дрожи, улучшение цвета кожи, уход тошноты, снижение тревоги, появление естественного, а не лекарственного сна. После выезда семья получает ясный план, как закрепить эффект, чтобы наутро не пришлось начинать всё заново.
Разобраться лучше – zapoj-narkolog-na-dom
Одним из ключевых направлений терапии является инфузионное лечение. Капельницы позволяют быстро восстановить обмен веществ, улучшить работу внутренних органов и ускорить выведение токсинов. В клинике используются только сертифицированные препараты, безопасные для сердечно-сосудистой и нервной системы.
Изучить вопрос глубже – http://narkologicheskaya-clinika-v-ryazani17.ru
Процесс лечения включает несколько последовательных шагов, направленных на стабилизацию состояния, детоксикацию и восстановление функций организма. Таблица ниже показывает основные этапы процедуры, применяемые врачами клиники «РеабКузбасс».
Изучить вопрос глубже – https://vyvod-iz-zapoya-v-novokuzneczke17.ru/vyvod-iz-zapoya-v-staczionare-novokuzneczk
Лечение алкоголизма в клинике «РязаньМед Альянс» включает несколько этапов, каждый из которых направлен на определённую цель — от снятия интоксикации до формирования устойчивого отказа от алкоголя. В таблице представлены основные стадии лечения и методы, используемые специалистами клиники.
Получить дополнительные сведения – частная наркологическая клиника рязань
Наркологическая клиника «Трезвый Шаг Раменское» — это место, где острые кризисы, многолетние запои и повторяющиеся срывы перестают быть бесконечным кругом, в котором семья остаётся один на один с проблемой. Здесь выстроена система помощи людям с алкогольной и наркотической зависимостью, а также полизависимостями, включая злоупотребление аптечными препаратами. В клинике в Раменском сочетаются круглосуточное наблюдение, профессиональная детоксикация, медикаментозная поддержка, психотерапевтические программы и сопровождение семьи. Важные принципы — безопасность, анонимность, уважение к пациенту и честное объяснение каждого шага лечения. Ни агрессивного давления, ни обещаний «чуда за один день» — вместо этого поэтапный подход, который даёт реальный шанс стабилизировать состояние, снизить тягу и выйти из разрушительного сценария под контролем специалистов. Для близких это означает понятный маршрут: куда обратиться, что будут делать с пациентом, какие риски учтут и как клиника «Трезвый Шаг Раменское» останется на связи после острого периода.
Ознакомиться с деталями – наркологическая клиника
Наркологическая клиника «КоломнаМед Центр» — это место, куда можно обратиться в тот момент, когда домашние попытки контролировать алкоголь, наркотики, аптечные препараты или смесь всего сразу перестают работать, а жизнь превращается в постоянное «завтра начну с нуля». Здесь не обещают чудес за один день и не пугают диагнозами, а выстраивают понятный медицинский маршрут: детоксикация, стабилизация, реабилитация, поддержка семьи, профилактика срывов. Пациент получает помощь в защищённой, конфиденциальной среде, где всё организовано так, чтобы снизить тревогу и стыд, убрать хаос вокруг зависимости и дать человеку шанс вернуться к нормальной жизни без давления, угроз и токсичных «стимулов». Для родных клиника в Коломне — это опора: конкретный адрес, конкретная команда, чёткие сроки и понятные этапы, вместо бесконечных обещаний «он сам справится».
Выяснить больше – https://narkologicheskaya-klinika-kolomna10.ru/narkologicheskaya-klinika-cena-v-kolomne
Клиника в Коломне ориентирована на полный цикл помощи: от экстренных состояний до длительного сопровождения. Здесь важна не только медицинская составляющая, но и человеческая: уважение, конфиденциальность, отсутствие стигмы. Ниже — ключевые направления, которые выстраиваются в единую систему лечения, а не существуют по отдельности.
Разобраться лучше – https://narkologicheskaya-klinika-kolomna10.ru/
«РаменМед Трезвость» предлагает несколько форматов помощи, но выбор всегда делается из соображений безопасности, а не удобства картинки. Стационарный вывод из запоя подходит в ситуациях, когда запой длится несколько дней или недель, есть скачки давления, проблемы с сердцем, печени, сахарный диабет, неврологические заболевания, эпизоды судорог или делирия в анамнезе, возраст старше 50–55 лет, выраженная слабость, тахикардия, невозможность пить воду, угрозы психозов. В стационаре пациент находится под наблюдением круглосуточно: контролируются жизненные показатели, вовремя корректируется терапия, есть возможность экстренно отреагировать на осложнения. Это гарантированно безопаснее, чем оставлять тяжёлого человека дома под наблюдением уставших родственников.
Изучить вопрос глубже – вывод из запоя на дому в Раменском
Город с протяжёнными магистралями и разноскоростными районами требует особой организации маршрутов. Выездные бригады «ВолгаДок Медикал» работают в режиме 24/7, прибывают в гражданской одежде, избегают громких звонков и используют «немаркированные» подъезды. Перед приездом мы просим подготовить пространство: приглушить верхний свет, обеспечить приток свежего воздуха без сквозняков, подготовить ровную поверхность под укладку и удлинитель, перевести телефоны в «без уведомлений» с «белым списком» близких. Это позволяет в первые минуты сосредоточиться на клинике, а не на бытовых вопросах.
Получить дополнительные сведения – https://narcologicheskaya-klinika-saratov0.ru/
Фиксируем АД, ЧСС, сатурацию, температуру, оцениваем неврологический статус, степень обезвоживания, тремор, тошноту и уровень тревоги; собираем краткий анамнез последних суток и характер употребления.
Узнать больше – вывод из запоя дешево
Когда человек в запое, близким кажется, что всё ещё можно решить «по-тихому»: выспаться, отпаять водой, дать обезболивающее или «успокоительное» и дождаться, пока станет легче. На практике это часто приводит к обратному результату. Алкогольная интоксикация нарушает водно-электролитный баланс, сгущает кровь, повышает нагрузку на сердце, провоцирует скачки давления, ухудшает работу печени и нервной системы. Неконтролируемый приём снотворных, анальгетиков, транквилизаторов, особенно вместе с алкоголем, способен вызвать угнетение дыхания, аритмии, судороги или делирий. Домашняя обстановка не даёт возможности следить за всеми показателями и вовремя отреагировать. «РаменМед Трезвость» предлагает клинически выверенный вывод из запоя в Раменском с учётом возраста, длительности употребления, хронических заболеваний, перенесённых ранее осложнений. Здесь не применяют сомнительные схемы «усыпить, чтобы не мешал», а ставят задачу: безопасно пройти острую фазу, снять интоксикацию, стабилизировать давление и пульс, защитить сердце и мозг, снизить риск психозов и, при желании пациента, сразу наметить маршрут реального лечения зависимости. Такой подход снимает с родственников опасную «роль врача» и возвращает ситуацию туда, где ей место — под контроль профессионалов.
Подробнее можно узнать тут – http://www.domen.ru
Когда вопрос стоит остро — нужно быстро и безопасно вывести человека из запоя в Коломне, — у семьи нет лишнего времени на эксперименты с таблетками, сомнительными «коктейлями» и советами из интернета. «Трезвый Центр Коломна» выстраивает помощь так, чтобы от первого звонка до реального облегчения шёл понятный и управляемый маршрут: запись симптомов и рисков уже по телефону, предложение формата (выезд на дом или стационар), оперативный осмотр, персональная инфузионная терапия, круглосуточное наблюдение при необходимости и подробный план восстановления на 24–72 часа и дальше. Мы не продаём миф о «чудо-капельнице за час», а работаем клинически аккуратно: дозы и схемы подбираются под возраст, длительность запоя, сопутствующие заболевания, уже принятые лекарства и текущие показатели. Цель проста и честна — снять интоксикацию, защитить сердце, мозг и печень, вернуть сон и ясность без агрессивной седации и скрытых рисков, сохранить конфиденциальность и дать семье уверенность, что всё делается правильно.
Углубиться в тему – vyvod-iz-zapoya-stacionar
В зависимости от состояния пациента и пожеланий семьи наркологическая помощь может быть оказана в одном из нескольких форматов: на дому, в стационаре или дистанционно. Каждый из форматов обеспечивает доступ к медицинской помощи без бюрократии и с сохранением полной конфиденциальности.
Подробнее – экстренная наркологическая помощь
Медицинская помощь в клинике организована поэтапно, что позволяет постепенно стабилизировать состояние и вернуть контроль над самочувствием.
Ознакомиться с деталями – скорая вывод из запоя пермь
Вывод из запоя требуется тогда, когда организм уже не способен самостоятельно справиться с последствиями алкогольной интоксикации. Длительное употребление спиртного приводит к нарушению работы внутренних органов, обезвоживанию и психическим расстройствам. Медицинская помощь помогает избежать опасных осложнений и облегчить процесс отказа от алкоголя.
Узнать больше – вывод из запоя с выездом
Для иллюстрации эффективности методов представлена таблица с примерами процедур и их воздействием:
Углубиться в тему – наркологическая клиника красноярск
В клинике применяются современные медицинские технологии, которые обеспечивают стойкий результат. Используемые методики соответствуют международным стандартам и регулярно обновляются.
Углубиться в тему – наркологическая клиника вывод из запоя
clicktolearnandgrow.click – Found this today, content seems helpful and worth checking again.
Программа лечения составляется индивидуально и может включать стационарный или амбулаторный формат. Основу медикаментозного этапа составляют детоксикационные процедуры, направленные на выведение остатков наркотиков из организма, восстановление функций печени, почек и нервной системы. Одновременно подключаются седативные препараты, гепатопротекторы, витамины и сорбенты. В особо тяжёлых случаях используется аппаратная поддержка: инфузоматы, электросон, лазерная терапия и другие методы.
Подробнее тут – лечение алкоголизма и наркомании центр в самаре
Медицинская помощь строится на принципах индивидуального подхода и поэтапной терапии. Каждый пациент проходит диагностику, после чего составляется персональная программа, включающая медикаментозную поддержку, консультации психотерапевта и физиопроцедуры. Такой подход помогает не просто снять симптомы, но и восстановить организм полностью.
Подробнее можно узнать тут – http://narkologicheskaya-klinika-v-ryazani17.ru/narkologiya-v-ryazani/
Комплексное проведение этих этапов обеспечивает полное восстановление организма и облегчает процесс последующего лечения зависимости.
Получить дополнительные сведения – вывод из запоя капельница рязань
Все процедуры выполняются анонимно и с соблюдением медицинских стандартов. Препараты применяются только сертифицированные, рассчитанные на мягкое восстановление организма без побочных эффектов. При необходимости лечение продолжается в стационаре, где пациент получает круглосуточное наблюдение, питание и психологическую поддержку.
Разобраться лучше – вывод из запоя вызов на дом новокузнецк
Наркомания — это не просто пагубная привычка, а тяжёлое хроническое заболевание, которое требует комплексного лечения и индивидуального подхода. В клинике «ЗдороваяСамара» разработаны современные программы помощи зависимым, охватывающие все этапы — от выезда нарколога на дом до многомесячного амбулаторного сопровождения. Особое внимание уделяется конфиденциальности, оперативности и доступности помощи в любое время суток. Это делает лечение максимально комфортным, результативным и гуманным как для самого пациента, так и для его близких.
Выяснить больше – лечение наркомании кодирование в самаре
Капельницы в «СаратовМед Профи» — это конструктор из тщательно подобранных модулей. Каждый модуль решает одну задачу и имеет свой ожидаемый горизонт эффекта. Важно не название, а логика: задача > опора среды > как проверяем > когда ждём результат.
Ознакомиться с деталями – vyvod-iz-zapoya-saratov0.ru/
Вывод из запоя — это не «волшебная капельница», а последовательная медицинская программа с чёткими целями и измеримыми маркерами. В наркологической клинике «СаратовМед Профи» маршрут строится по принципу управляемых окон: на каждом шаге команда преследует одну цель, меняет лишь один параметр и оценивает результат в заранее назначённый момент. Такой подход снижает лекарственную нагрузку, предотвращает «гонку дозировок» и делает динамику предсказуемой для пациента и близких. Конфиденциальность обеспечивается регламентом: немаркированные выезды, нейтральные формулировки в документах, «тихие» каналы связи, доступ к записям — строго по ролям.
Получить дополнительную информацию – вывод из запоя на дому цена в саратове
Выезд нарколога на дом в Щёлково — это быстрый и конфиденциальный способ помочь человеку в состоянии запоя или тяжёлого похмелья, не перевозя его в клинику и не устраивая публичных сцен. Врачи «ЩёлковоМед Профи» приезжают с готовым набором препаратов, одноразовыми системами и чётким протоколом: осмотр, оценка жизненно важных показателей, подбор индивидуальной капельницы, контроль реакции, рекомендации для родных. Такой формат особенно удобен, когда пациент отказывается ехать в стационар, тяжело переносит дорогу, остро реагирует на смену обстановки или для семьи важна максимальная анонимность. Главный принцип — не «вырубить» человека любой ценой, а безопасно стабилизировать состояние, снизить интоксикацию, выровнять давление и пульс, помочь собрать сон и дать понятный план, что делать дальше.
Подробнее тут – http://narkolog-na-dom-shchelkovo10.ru
Каждое из этих направлений имеет важное значение и в совокупности формирует основу для устойчивого выздоровления.
Разобраться лучше – http://narkologicheskaya-klinika-v-omske0.ru/chastnaya-narkologicheskaya-klinika-omsk/
В медицинской практике используются различные методы, которые помогают ускорить процесс восстановления. Все процедуры проводятся под контролем специалистов и с учетом индивидуальных особенностей пациента.
Детальнее – https://vyvod-iz-zapoya-omsk0.ru/vyvod-iz-zapoya-gorod-omsk/
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Разобраться лучше – narkologicheskaya-klinika-telefon
Выездной наркологический сервис «МедПоволжье Клиник» создан для случаев, когда важны скорость, тишина и клиническая точность. Мы проводим детоксикацию и снятие интоксикации на дому так, чтобы каждое действие имело цель, измеримый маркер и заранее оговорённое «окно переоценки». Вместо «сильной капельницы на всякий случай» — модульная схема: один симптом-кластер > один медицинский модуль > одна поведенческая опора (свет, звук, вода малыми глотками, дыхание 4–6). Такой подход снижает лекарственную нагрузку, ускоряет стабилизацию и позволяет видеть прогресс буквально по часам.
Углубиться в тему – вызвать нарколога на дом срочно в саратове
Услуга
Получить дополнительную информацию – https://narkolog-na-dom-shchelkovo10.ru/vrach-narkolog-na-dom-shchelkovo/
Такая структура делает лечение последовательным и предсказуемым, повышая шансы на положительный исход.
Разобраться лучше – http://narkologicheskaya-klinika-v-omske0.ru
В клинике применяются комплексные программы, охватывающие все стадии терапии. Такой подход позволяет обеспечить пациенту полный спектр помощи — от первой консультации до социальной адаптации.
Подробнее тут – http://narcologicheskaya-klinika-omsk0.ru/narkologicheskaya-bolnicza-omsk/
Перед таблицей — короткий акцент: приведённые суммы ориентировочные, не являются публичной офертой, точная стоимость определяется после осмотра.
Разобраться лучше – vyvod-iz-zapoya-na-domu-nedorogo
Детоксикация — это первый и важнейший этап лечения в наркологической клинике в Красноярске. Она проводится с целью выведения токсинов из организма и восстановления функций жизненно важных органов. Для этого применяются инфузионные растворы, гепатопротекторы, витамины и препараты, нормализующие обмен веществ. После снятия интоксикации пациент получает медикаментозную поддержку, направленную на снижение тяги к алкоголю или наркотикам и стабилизацию эмоционального состояния.
Углубиться в тему – http://narcologicheskaya-klinika-v-krasnoyarske17.ru/krasnoyarsk-narkologicheskij-czentr/
Каждый час промедления в острый период повышает вероятность обезвоживания, электролитных сдвигов, аритмий, гипертонических всплесков и расстройств сна, которые легко перерастают в делирий. Домашние попытки с «подручными» средствами редко учитывают лекарственные взаимодействия, реальный уровень обезвоживания и состояние печени, а «жёсткая» седация, применяемая без показаний, маскирует ухудшения и лишает врача информативной картины. Профессиональная бригада «НоваТрезвие» начинает с объективной оценки: давление, пульс, сатурация, температура, неврологический статус, выраженность тремора и тошноты, степень обезвоживания, список принимаемых препаратов и возможные аллергии. На этой базе формируется персональный план: регидратация, коррекция электролитов и кислотно-щелочного баланса, поддержка нервной системы витаминами группы B и магнием, гепатопротекторная и антиоксидантная защита по показаниям, противорвотные при необходимости и мягкая анксиолитическая поддержка для восстановительного сна. Такой маршрут гасит «пожар» интоксикации управляемо, возвращая прогнозируемость самочувствия в течение первых часов.
Выяснить больше – http://vyvod-iz-zapoya-ehlektrostal2-10.ru/vyvod-iz-zapoya-na-domu-v-ehlektrostali/
Главной задачей специалистов становится купирование абстинентного синдрома и снижение интоксикации. Это требует применения медикаментов и постоянного наблюдения за состоянием пациента.
Исследовать вопрос подробнее – вывод из запоя на дому круглосуточно пермь
В зависимости от состояния пациента и пожеланий семьи наркологическая помощь может быть оказана в одном из нескольких форматов: на дому, в стационаре или дистанционно. Каждый из форматов обеспечивает доступ к медицинской помощи без бюрократии и с сохранением полной конфиденциальности.
Подробнее можно узнать тут – https://narkologicheskaya-pomoshh-omsk0.ru/omsk-narkologicheskij-dispanser
Выбор наркологической клиники в Коломне — это не «слишком серьёзно», а логичный шаг, если зависимость уже зашла дальше спонтанных эпизодов. Алкоголизм, наркомания, злоупотребление успокоительными и обезболивающими — это не только психологическая тяга, но и перестройка организма: страдают печень, сердце, сосуды, нервная система, гормональный фон, сон, психика. Дома редко есть возможность круглосуточно контролировать состояние, правильно отменять вещества, отслеживать давление, пульс, поведение, не допускать опасных комбинаций препаратов. Родственники устают, реагируют эмоциями, а не медицинской логикой, человек чувствует себя под прицелом, но не под защитой. В «КоломнаМед Центр» всё выстроено так, чтобы снять нагрузку с семьи и вывести помощь из зоны хаотичных решений. Здесь оценивают не только то, «что и сколько пьёт или принимает», а весь контекст: длительность зависимости, срывы, уже перенесённые делирии или передозировки, сопутствующие болезни, психические состояния, семейную ситуацию. На основе этого формируется безопасный план: где начать — в стационаре или амбулаторно, какой формат детокса выбрать, насколько жёстко вести наблюдение, как сразу встроить психотерапевтическую и социальную поддержку. Клиника в Коломне позволяет работать системно, а не латать последствия очередного срыва.
Выяснить больше – https://narkologicheskaya-klinika-kolomna10.ru/luchshie-narkologicheskie-kliniki-v-kolomne
Капельница при вызове нарколога на дом в Долгопрудном от «МедТрезвие Долгопрудный» — это клинический инструмент, а не магический раствор. Главное правило — никакой агрессивной седации ради видимости спокойствия. Инфузионная терапия строится вокруг нескольких задач: восполнить жидкость, выровнять электролиты, снизить токсическую нагрузку на печень и мозг, поддержать сердце и нервную систему, уменьшить тремор, тревогу и соматические жалобы. Используются растворы для регидратации и коррекции водно-электролитного баланса, витамины группы B и магний для поддержки нервной системы, уменьшения риска судорог и нормализации сна, по показаниям — гепатопротекторы и мягкие антиоксиданты, противорвотные препараты для контроля тошноты. При выраженной тревоге или нарушениях сна назначаются щадящие анксиолитические средства в дозах, которые не выключают пациента полностью, а помогают снять паническое напряжение, сохраняя возможность оценивать динамику состояния. Врач отслеживает реакцию на терапию: стабилизацию давления и пульса, уменьшение дрожи, улучшение общего самочувствия, появление более спокойного, естественного сна. По мере облегчения нагрузки схема не усиливается ради счёта, а рационально сокращается. Такой подход защищает пациента от скрытых осложнений и превращает капельницу в контролируемый, полезный шаг, а не в рискованный эксперимент.
Подробнее – нарколог на дом
Лечение алкоголизма в клинике «РязаньМед Альянс» включает несколько этапов, каждый из которых направлен на определённую цель — от снятия интоксикации до формирования устойчивого отказа от алкоголя. В таблице представлены основные стадии лечения и методы, используемые специалистами клиники.
Получить дополнительную информацию – наркологическая клиника
Наркологическая клиника в Омске оказывает специализированную помощь людям, столкнувшимся с алкогольной, наркотической и другими формами зависимости. Здесь используются современные методы диагностики, терапии и реабилитации, которые помогают не только стабилизировать состояние, но и восстановить здоровье в долгосрочной перспективе. Работа ведётся с учётом принципов конфиденциальности, что создаёт условия для комфортного прохождения лечения.
Углубиться в тему – наркологическая клиника наркологический центр омск
Главная задача капельницы при выезде нарколога в Щёлково — не создать видимость лёгкости, а реально уменьшить интоксикацию и восстановить базовые функции организма. В «ЩёлковоМед Профи» используются современные схемы, а не сомнительные смеси «из всего подряд». В стандартной основе — растворы для восполнения объёма циркулирующей жидкости, выравнивания электролитного баланса и коррекции КЩС, что снижает нагрузку на сердце и мозг. Витамины группы B и магний поддерживают нервную систему, уменьшают тремор, раздражительность и риск судорожных реакций. При необходимости врач добавляет гепатопротекторные и антиоксидантные компоненты, если есть признаки перегрузки печени; при выраженной тошноте — противорвотные, чтобы пациент мог нормально пить и питаться. Для нормализации сна и тревоги подбираются мягкие анксиолитики в дозах, позволяющих контролировать состояние, а не «вырубать» человека. Агрессивные седативные протоколы, которые маскируют ухудшения и опасны для дыхания и сердца, сознательно исключаются. Оценка эффекта идёт по конкретным критериям: стабилизация давления и пульса, уменьшение дрожи, улучшение цвета кожи, уход тошноты, снижение тревоги, появление естественного, а не лекарственного сна. После выезда семья получает ясный план, как закрепить эффект, чтобы наутро не пришлось начинать всё заново.
Ознакомиться с деталями – запой нарколог на дом цена
Наркозависимость — это не просто вредная привычка, а тяжёлое хроническое заболевание, требующее комплексного и последовательного лечения. В клинике «РеабКузбасс» в Новокузнецке разработаны персонализированные программы помощи, учитывающие медицинские, психологические и социальные аспекты проблемы. Каждому пациенту подбирается уникальный маршрут восстановления, начиная с первичной диагностики и заканчивая адаптацией к жизни без наркотиков. Поддержка оказывается круглосуточно, с полным соблюдением конфиденциальности. Психотерапевты и врачи работают в тесной связке, чтобы не только устранить физическую зависимость, но и восстановить личность пациента, вернуть ему мотивацию к жизни и уверенность в будущем.
Изучить вопрос глубже – лечение наркомании наркология новокузнецк
Для иллюстрации эффективности методов представлена таблица с примерами процедур и их воздействием:
Разобраться лучше – http://narcologicheskaya-klinika-v-krasnoyarske17.ru/krasnoyarsk-narkologicheskij-czentr/
Медики рекомендуют обратиться за профессиональной помощью при следующих состояниях:
Подробнее – вывод из запоя клиника в рязани
Запой — это не просто несколько лишних дней алкоголя, а тяжёлое состояние, в котором организм работает на пределе. Чем дольше длится эпизод, тем глубже обезвоживание, тем сильнее сдвиги электролитов, тем выше риск аритмий, гипертонических кризов, судорог, делирия, обострений заболеваний сердца, печени и поджелудочной железы. Попытки «вывести» человека дома силами родных часто включают опасные комбинации: случайные седативные, снотворные, анальгетики, «антипохмельные» из рекламы. Они могут на время усыпить или «успокоить», но при этом скрывают ухудшение, сбивают давление, угнетают дыхание и мешают врачу увидеть реальную картину. В «Трезвый Центр Коломна» подход другой: ещё на этапе звонка специалист уточняет длительность запоя, объёмы и виды алкоголя, наличие гипертонии, ИБС, диабета, заболеваний печени и почек, неврологических проблем, список уже принятых препаратов, эпизоды потери сознания, судорог, странного поведения. На основании этих данных определяется, безопасен ли формат на дому или сразу нужен стационар. Такая сортировка позволяет вовремя перехватить опасные случаи, не терять часы на бесполезные попытки и сразу запускать те схемы, которые реально снижают риски и стабилизируют состояние.
Выяснить больше – bystryj-vyvod-iz-zapoya
Комплексное применение этих методов позволяет добиться быстрого восстановления организма и улучшения психоэмоционального состояния.
Выяснить больше – скорая вывод из запоя
Эти направления формируют основу лечения и обеспечивают комплексное воздействие на проблему зависимости.
Детальнее – наркологическая клиника клиника помощь в омске
Выбор формата — это не вкусовщина, а баланс безопасности в конкретной клинической картине. Дом уместен, если контакт сохранён, рвота эпизодическая, давление и пульс без резких «качелей», тремор контролируемый, в квартире можно обеспечить тишину и присутствие взрослого, готового наблюдать первые 6–8 часов. Тогда выездная бригада работает на месте и выстраивает «мягкий» маршрут, где сон собирается без агрессивной седации, а инфузии идут с шаговой корректировкой темпа. Стационар предпочтителен при длительном эпизоде (3–5 суток и более), неукротимой рвоте, выраженной слабости, шаткости походки, признаках предделирия/делирия, судорожной готовности, а также у пожилых пациентов и при сочетанных диагнозах — ИБС, гипертония, диабет, хронические болезни печени/почек, неврология. Преимущество отделения — приборный мониторинг, лабораторные опции по показаниям, ночная команда и среда, где исключены лишние раздражители: это снижает «цену ошибки» и делает результат устойчивым, а не разовым «прояснением».
Подробнее – http://vyvod-iz-zapoya-ehlektrostal2-10.ru
Эта разъяснительная статья содержит простые и доступные разъяснения по актуальным вопросам. Мы стремимся сделать информацию понятной для широкой аудитории, чтобы каждый мог разобраться в предмете и извлечь из него максимум пользы.
Прочесть заключение эксперта – https://divinedivaevents.com/sed-ut-perspiciatis-unde-omnis-iste-natus-error-sit
Чтобы исключить суету и случайные усиления, первые часы делим на небольшие «окна»: цель — действие — маркер — критерий перехода. Если отклика нет, корректируется один элемент — темп инфузии, очередность модулей или поведенческий якорь — и назначается новая точка оценки.
Ознакомиться с деталями – вывод из запоя цена в саратове
В случаях, когда пациент не готов приехать в клинику или находится в тяжёлом состоянии, специалисты «ЗдороваяСамара» организуют выездную помощь. Это особенно важно при острых интоксикациях, синдроме отмены, резком ухудшении психоэмоционального состояния. Выезд возможен круглосуточно и занимает от 30 до 60 минут с момента обращения. Врач приезжает в гражданской одежде, без опознавательных знаков и привлечения внимания. Оснащение позволяет провести на месте полную диагностику и начать лечение — в том числе инфузионную терапию, коррекцию состояния и психологическую стабилизацию.
Ознакомиться с деталями – лечение наркомании и алкоголизма самара
«ОмскПрофи» укомплектована современной медицинской базой: передвижные аппараты для ЭКГ, инфузионные стойки, экспресс-анализаторы, мониторы состояния, аппараты ИВЛ (в реанимационных палатах). Штат сотрудников сформирован из врачей-наркологов, токсикологов, психиатров, психотерапевтов, медицинских сестёр, прошедших обучение по международным протоколам. Ведётся постоянная учёба, стажировки, участие в научных форумах. Благодаря этому пациенты получают не только медицинскую помощь, но и психологическое сопровождение, направленное на долгосрочный результат.
Выяснить больше – наркологическая клиника клиника помощь омск
Digital advancement portal – Everything feels responsive and easy to use.
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Слушай внимательно — тут важно – https://bastel-und-kartenstube.unequal-solutions.de/2013/03/26/eine-neue-neuigkeit
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Не упусти шанс – https://koksun.kz/?p=1344
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Проследить причинно-следственные связи – http://vildastamps.com/blog/?p=16014
Статья знакомит с важнейшими моментами, которые сформировали наше общество. От великих изобретений до культурных переворотов — вы узнаете, как прошлое влияет на наше мышление, технологии и образ жизни.
Это стоит прочитать полностью – https://www.onverze.com/elon-musks-firm-neuralink-is-preparing-for-human-testing-of-its-brain-chip-implant
Если вы ищете информацию о техосмотр для постановки в Санкт-Петербурге, посетите специализированный сайт для получения актуальных услуг и цен.
Обязательным является прохождение техосмотра для каждого автовладельца в стране. Техосмотр помогает поддерживать безопасность на автодорогах, избегая потенциальных инцидентов. Не пройдя техосмотр, водитель не сможет оформить страховку ОСАГО.
В СПб организованы удобные станции для проведения техосмотра в различных районах. Процедура включает проверку ключевых систем автомобиля и выдачу диагностической карты.
Прежде всего, автовладелец должен собрать требуемые бумаги, включая личный паспорт и регистрационное удостоверение. Затем следует пройти осмотр на станции, где проверяются тормоза и другие системы. Завершается процесс получением диагностической карты, удостоверяющей полное соответствие стандартам.
Осмотр включает проверку тормозов, фар и других критических узлов. Ещё одним аспектом является проверка шин на повреждения и правильность их использования. Каждый проверяемый узел обязан полностью удовлетворять общим нормам безопасности.
В Санкт-Петербурге функционирует множество сертифицированных центров для техосмотра. К примеру, пункт на Московском проспекте предлагает услуги с возможностью предварительной записи. Другие варианты есть в Приморском районе, где процесс организован удобно и оперативно.
Ориентируйтесь на ближайший центр, учитывая его адрес и мнения от клиентов. Узнайте график работы заранее, чтобы избежать очередей. Оформите запись через интернет или звонок, что упростит процесс.
Систематическое прохождение осмотра увеличивает долговечность машины и улучшает её безопасность. Это минимизирует риски ДТП и предотвращает ненужные затраты на починку. Поддерживайте регулярность, дабы не сталкиваться с штрафами и наслаждаться спокойными поездками.
При просрочке процедуры водитель получит наказание в виде штрафа от дорожной инспекции. Поэтому не игнорируйте сроки и проходите осмотр вовремя. Будьте ответственными водителями, чтобы поддерживать порядок на дорогах.
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Читать дальше – https://careers.epilpoint.it/estetista-specializzata-brescia
мост бет скачать мост бет скачать
Эта публикация погружает вас в мир увлекательных фактов и удивительных открытий. Мы расскажем о ключевых событиях, которые изменили ход истории, и приоткроем завесу над научными достижениями, которые вдохновили миллионы. Узнайте, чему может научить нас прошлое и как применить эти знания в будущем.
Хочешь знать всё? – https://www.cordobaadiario.com/encontronazo-2
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
Нажмите, чтобы узнать больше – https://blaisepascalagadir.com/j%D0%BEy%D1%81%D0%B0sin%D0%BE-idm%D0%B0n-m%C9%99r%D1%81l%C9%99ri-%D1%81%D0%B0sin%D0%BE-x-%D1%81%D0%B0sin%D0%BE-b%D0%BEnu-2
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Подробности по ссылке – https://www.jakahong.com/dress-code-vs-dresscode-mana-yang-benar
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Открой скрытое – http://simoneauvineyards.com/biz-pic2-2
Откройте для себя скрытые страницы истории и малоизвестные научные открытия, которые оказали колоссальное влияние на развитие человечества. Статья предлагает свежий взгляд на события, которые заслуживают большего внимания.
Узнать из первых рук – https://namiracontroledepragas.com.br/ola-mundo
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Подробная информация доступна по запросу – https://www.geestdriftfestival.nl/kaartverkoop-geestdrift-festival-gestart
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Перейти к статье – https://grupoedora.com/edora-revoluciona-el-mercado-renovable-espanol-anuncia-la-construccion-de-5-gw-solares
seo базовый курc kursy-seo-5.ru .
seo онлайн seo онлайн .
mostbet skacat http://www.mostbet2026.help
Mind-opening resource – Everything is organized in a way that feels natural.
мостбет сайт https://www.mostbet2026.help
школа seo школа seo .
курсы по seo курсы по seo .
midnight field goods – Well-ordered pages, discovering items is quick and the experience feels stable.
Professional direction site – The design avoids clutter and reads smoothly.
seo специалист seo специалист .
seo бесплатно seo бесплатно .
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Получить дополнительные сведения – https://travelspecialistsmorocco.com/best-morocco-tours
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Перейти к статье – https://www.trilheseurumo.com.br/trilhas/2076-trilha-da-cachoeira-do-elefante.html
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Полезно знать – http://kuromacube.com/%E8%87%AA%E7%94%BB%E5%83%8F
Эта статья полна интересного контента, который побудит вас исследовать новые горизонты. Мы собрали полезные факты и удивительные истории, которые обогащают ваше понимание темы. Читайте, погружайтесь в детали и наслаждайтесь процессом изучения!
Подробности по ссылке – https://pomoc.comarchesklep.pl/kontakt
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Изучить эмпирические данные – https://ccmdaci.org/2023/01/17/le-rosaire-des-cas-dis-impossibles-tous-les-mercredi-de-15h-20h
Эта статья сочетает в себе как полезные, так и интересные сведения, которые обогатят ваше понимание насущных тем. Мы предлагаем практические советы и рекомендации, которые легко внедрить в повседневную жизнь. Узнайте, как улучшить свои навыки и обогатить свой опыт с помощью простых, но эффективных решений.
А что дальше? – https://naturepositiveenergy.com/2024/04/09/name-surname-1
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Открой скрытое – https://www.st-wendel-erleben.de/events/summer-in-the-city-varus
курсы по seo курсы по seo .
Этот информационный обзор станет отличным путеводителем по актуальным темам, объединяющим важные факты и мнения экспертов. Мы исследуем ключевые идеи и представляем их в доступной форме для более глубокого понимания. Читайте, чтобы оставаться в курсе событий!
Продолжить изучение – https://dive-team-stephanbaum.de/padi-con-ed-flow-chart-transparent-large18-kopie
Предлагаем вашему вниманию интересную справочную статью, в которой собраны ключевые моменты и нюансы по актуальным вопросам. Эта информация будет полезна как для профессионалов, так и для тех, кто только начинает изучать тему. Узнайте ответы на важные вопросы и расширьте свои знания!
Смотрите также – http://miejskagorka.osp.org.pl/wyjazd-alarmowy-12-2020
продвижение обучение kursy-seo-5.ru .
Эта информационная статья содержит полезные факты, советы и рекомендации, которые помогут вам быть в курсе последних тенденций и изменений в выбранной области. Материал составлен так, чтобы быть полезным и понятным каждому.
Ознакомиться с полной информацией – https://zuhdijaadilovic.com/aktuelnosti/kuran-kljuc-rjesenja-svih-nasih-problema
Публикация предлагает уникальную подборку информации, которая будет интересна как специалистам, так и широкому кругу читателей. Здесь вы найдете ответы на часто задаваемые вопросы и полезные инсайты для дальнейшего применения.
Получить дополнительные сведения – https://crbank.com.br/mastering-time-management-key-to-business-success
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
А есть ли продолжение? – https://anomalija.lt/2019/07/sapnu-pasaulis-kur-mes-keliaujame-sapnuodami
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Только для своих – https://www.mamas-taxi.cz/there-are-limitless-opportunities-time
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Подробная информация доступна по запросу – https://goptalkingpoints.com/ben-carson
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Прочесть всё о… – https://proenem.unilab.edu.br/proenem-fica-em-primeiro-lugar-na-selecao-de-bolsas-da-proex-2019
Этот обзор предлагает структурированное изложение информации по актуальным вопросам. Материал подан так, чтобы даже новичок мог быстро освоиться в теме и начать использовать полученные знания в практике.
Получить дополнительные сведения – https://novargonaftes.gr/2022/09/15/%CE%B4%CF%85%CE%BD%CE%B1%CE%BC%CE%B9%CE%BA%CE%AD%CF%82-%CE%B5%CE%BC%CF%86%CE%B1%CE%BD%CE%AF%CF%83%CE%B5%CE%B9%CF%82-%CE%BA%CE%B1%CF%84%CE%B1%CE%BA%CF%84%CF%8E%CE%BD%CF%84%CE%B1%CF%82-2-%CF%87%CF%81
Откройте для себя скрытые страницы истории и малоизвестные научные открытия, которые оказали колоссальное влияние на развитие человечества. Статья предлагает свежий взгляд на события, которые заслуживают большего внимания.
Выяснить больше – https://siciliammare.it/pesca-e-caro-gasolio-delegazione-di-mazara-del-vallo-in-visita-al-parlamento-europeo_8886
Этот увлекательный информационный материал подарит вам массу новых знаний и ярких эмоций. Мы собрали для вас интересные факты и сведения, которые обогатят ваш опыт. Откройте для себя увлекательный мир информации и насладитесь процессом изучения!
Ознакомиться с деталями – https://shakthiiacademy.com/course/online-police-constable-exam-coaching-12-month
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Лучшее решение — прямо здесь – https://netmorie.com/archives/150621
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Читать дальше – https://bestchineserestaurantvirginiabeach.com/chinese-food-delivery-in-virginia-beach-super-wok
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Выяснить больше – https://thenewspulse.com/%E0%A4%85%E0%A4%82%E0%A4%A4%E0%A4%B0%E0%A5%8D%E0%A4%B0%E0%A4%BE%E0%A4%B7%E0%A5%8D%E0%A4%9F%E0%A5%8D%E0%A4%B0%E0%A5%80%E0%A4%AF-%E0%A4%96%E0%A5%81%E0%A4%B6%E0%A5%80-%E0%A4%A6%E0%A4%BF%E0%A4%B5%E0%A4%B8
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Переходите по ссылке ниже – https://www.blognews.am/rus/authors/silver
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Где почитать поподробнее? – https://anideva.com/le-monde-de-mes-reves-chapitre9
Strategic partnership space – Nice execution, the platform feels focused and business-ready.
bizlinknetwork – Helpful platform for professional networking, navigation is simple and fast.
Build Something New – Thoughtful and inspiring, content motivates creativity daily.
friendfinderportal – Smooth experience connecting with people who share your hobbies.
Simple Ways to Be Happy – Helpful suggestions, content makes small daily joys easy to embrace.
buyingtipscenter – Reliable shopping advice, made the buying process smooth and hassle-free.
Gardens AL Hub – Peaceful layout, community details are easy to navigate and understand.
enterprise collaboration guide – Solid guidance that improved alliance-building outcomes.
onlineessentialsmart – Found everything I needed without hassle, very efficient today.
energysavinghub – Daily suggestions that helped optimize electricity consumption easily.
strategicdirectionhub – Practical tips for strategy development, improved planning process significantly.
visionpathways – Insightful guidance, made evaluating options straightforward.
Epilation appointment site – Easy to navigate, service details are simple to understand and book.
corporateconnectionclick – Platform is efficient, allowed me to establish multiple connections quickly.
corporate partnership guide – Practical tips that helped align teams and improve collaborative strategies.
corporatealliancehub – Implementing these solutions improved project coordination quickly.
partnership security hub – Practical insights that strengthened trust and collaboration between teams.
bondpath – Useful tools, helped me connect with the right professionals efficiently.
Padel news Oviedo – Quick updates, information is useful and easy to follow.
Business collaboration hub – Thoughtful setup, collaboration seems to be the core strength here.
innovation spark hub – Fresh ideas that encouraged me to think differently about upcoming projects.
strategicpartnerportal – Offers actionable tips for growing and maintaining professional relationships.
ии анализ креативов 60 секунд reklamnyj-kreativ4.ru .
a/b тест наружная реклама reklamnyj-kreativ5.ru .
enterpriseconnect – Excellent for discovering collaboration and partnership opportunities.
улучшение баннеров реклама reklamnyj-kreativ4.ru .
улучшение hero карточки улучшение hero карточки .
bondinsightportal – Valuable guidance, very clear and practical for everyday business use.
learnandadvance – Informative skill-building content, very useful for growing expertise quickly.
RenovSystem tubs online – Clean design, it’s easy to find and compare details.
Наслаждайтесь удобством заказать алкоголь с доставкой круглосуточно – быстро и просто, прямо до вашей двери.
В ассортимент входят популярные и редкие виды алкоголя, которые не всегда доступны в розничных точках.
Доставка алкоголя становится все более популярной услугой в современном мире.
Daily Creative Sparks – Inviting and lively, prompts are practical and inspiring.
ии анализ креативов 60 секунд reklamnyj-kreativ4.ru .
upster pro upster pro .
bond security network – Everything feels protected while managing investments online.
Fiat 500 lovers site – Engaging layout, updates on classic models feel carefully crafted.
globalpartneralliances – Platform is helpful for business connections, alliance tips are easy to apply.
Find Solutions Daily – Clear and engaging, content provides practical answers quickly.
Fast-loading website – Straightforward design, the content appears without delay.
1win Ош скачать https://www.1win12050.ru
trusted shopping deals – The marketplace worked well and made buying fast.
upster pro upster pro .
узнаваемость бренда баннер reklamnyj-kreativ5.ru .
мостеб https://www.mostbet2027.help
enterprise collaboration hub – Useful alliance ideas that improved networking efficiency.
мостбе https://mostbet2027.help/
dealsmartcenter – User-friendly platform, completed purchases quickly and easily.
commercehub – User-friendly layout, browsing products feels smooth and effortless.
1win создать аккаунт http://1win12050.ru
Creative work gallery – Smooth experience, the showcased projects are visually appealing.
1win официальный 1win официальный
professionalunityhub – Team coordination is simplified, very easy to manage tasks collectively.
Buy LSD Gel Tabs
TRIPPY 420 ROOM is an online psychedelics dispensary, focused on offering carefully crafted and top-quality medical products covering a wide range of categories.
Before purchasing psychedelic, cannabis, stimulant, dissociative, or opioid products online, buyers are given a transparent framework covering product availability, delivery options, and support. The store features more than 200 products across multiple formats.
Shipping costs are calculated according to package size and destination, with regular and express options available. All orders are backed by a hassle-free returns policy and a strong focus on privacy and security. Guaranteed stealth delivery worldwide is a core element, without additional charges. Every order is fully guaranteed to maintain consistent delivery.
Available products include cannabis flowers, magic mushrooms, psychedelic items, opioid medication, disposable vapes, tinctures, pre-rolls, and concentrates. Items are presented with clear pricing, including defined price ranges where multiple variants are available. Informational content is also available, including references such as “How to Dissolve LSD Gel Tabs”, and direct access to buy LSD gel tabs and buy psychedelics online.
The dispensary lists its operation in the United States, California, and offers multiple communication channels, including phone, WhatsApp, Signal, Telegram, and email. The service highlights 24/7 express psychedelic delivery, framing the service around accessibility, privacy, and ongoing customer support.
connectbiznetwork – Simple and reliable platform, made connecting with colleagues very straightforward.
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Есть чему поучиться – http://letsdocloud.com/2024/01/run-unifi-controller-in-synology
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Это ещё не всё… – https://ohoagency.com/product/slim-fit-bright-blue
В этой публикации мы предлагаем подробные объяснения по актуальным вопросам, чтобы помочь читателям глубже понять их. Четкость и структурированность материала сделают его удобным для усвоения и применения в повседневной жизни.
Осуществить глубокий анализ – https://trinityalpsmarina.com/2018/02/the-difference-between-docking-and-mooring
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Детали по клику – http://bunbun.s25.xrea.com/sb/eid38.html
В этом интересном тексте собраны обширные сведения, которые помогут вам понять различные аспекты обсуждаемой темы. Мы разбираем детали и факты, делая акцент на важности каждого элемента. Не упустите возможность расширить свои знания и взглянуть на мир по-новому!
Узнать больше – https://claveradiobar.com/clave-radio-bar-pre-lancamento-2
Этот информативный текст отличается привлекательным содержанием и актуальными данными. Мы предлагаем читателям взглянуть на привычные вещи под новым углом, предоставляя интересный и доступный материал. Получите удовольствие от чтения и расширьте кругозор!
Читать дальше – https://nacmedpalata.ru/?action=show&id=8095
В данной статье вы найдете комплексный подход к изучению насущных тем. Мы комбинируем теоретические сведения с практическими советами, чтобы читатель мог не только понять проблему, но и найти пути её решения.
Уникальные данные только сегодня – https://www.alfassinaro.it/public/wp/?page_id=65
Этот обзорный материал предоставляет информационно насыщенные данные, касающиеся актуальных тем. Мы стремимся сделать информацию доступной и структурированной, чтобы читатели могли легко ориентироваться в наших выводах. Познайте новое с нашим обзором!
Давай разберёмся досконально – https://zubancordoba.com/el-fenomeno-mundial-detras-del-apoyo-de-milei-quienes-son-los-que-lo-sostienen
Эта обзорная заметка содержит ключевые моменты и факты по актуальным вопросам. Она поможет читателям быстро ориентироваться в теме и узнать о самых важных аспектах сегодня. Получите краткий курс по современной информации и оставайтесь в курсе событий!
Где почитать поподробнее? – https://blueaditivos.cl/2024/03/20/unlocking-the-power-of-solar-energy-a-comprehensive-guide
Эта публикация завернет вас в вихрь увлекательного контента, сбрасывая стереотипы и открывая двери к новым идеям. Каждый абзац станет для вас открытием, полным ярких примеров и впечатляющих достижений. Подготовьтесь быть вовлеченными и удивленными каждый раз, когда продолжите читать.
Посмотреть всё – https://vaganovaacademy.ru/press/ntv-24-05-2023.html?page=15
Эта познавательная публикация погружает вас в море интересного контента, который быстро захватит ваше внимание. Мы рассмотрим важные аспекты темы и предоставим вам уникальные Insights и полезные сведения для дальнейшего изучения.
Открой скрытое – https://teachersguide.net/modern-teaching-strategies-in-the-classroom
Эта статья предлагает уникальную подборку занимательных фактов и необычных историй, которые вы, возможно, не знали. Мы постараемся вдохновить ваше воображение и разнообразить ваш кругозор, погружая вас в мир, полный интересных открытий. Читайте и открывайте для себя новое!
Изучить аспект более тщательно – https://alam-flora.com/bonsai-dolar-atau-beringin-korea-untuk-taman
skillshub – Very practical content, improved my abilities effectively.
cheapfindsonline – Quality items at prices that made me happy, great selection.
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Все материалы собраны здесь – https://savetaxgroup.com/fa/blog/northern-territory-of-australia
unityinsights – Practical tips, strengthened team collaboration in real scenarios.
premiumdigitalmarket – Easy navigation and simple process for high-quality digital purchases.
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Раскрыть тему полностью – https://ordervitaminstoday.com/product/fuel-your-mind-bundle
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Разобраться лучше – https://www.ucetni-sluzby.com/pellentesque-nibh-aenean-quam-in-scelerisque
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Прочесть всё о… – https://www.csautoslalom.cz/report-5zavod-wsc2023
В статье представлены ключевые моменты по актуальной теме, дополненные советами экспертов и ссылками на дополнительные ресурсы. Цель материала — дать читателю инструменты для самостоятельного развития и принятия осознанных решений.
Слушай внимательно — тут важно – https://miyake-blog.boy.jp/blog/mimi/?p=6170
Мы собрали для вас самые захватывающие факты из мира науки и истории. От малознакомых деталей до грандиозных событий — эта статья расширит ваш кругозор и подарит новое понимание того, как устроен наш мир.
Получить дополнительную информацию – https://pinotee.com/product/i-am-a-veteran-american-flag-hoodie-3d-v
В данной обзорной статье представлены интригующие факты, которые не оставят вас равнодушными. Мы критикуем и анализируем события, которые изменили наше восприятие мира. Узнайте, что стоит за новыми открытиями и как они могут изменить ваше восприятие реальности.
Запросить дополнительные данные – https://www.ninebooking.com/hotel/movenpick-asara-resort-spa-hua-hin-%E0%B9%80%E0%B8%A1%E0%B8%AD%E0%B9%80%E0%B8%A7%E0%B8%99%E0%B8%9E%E0%B8%B4%E0%B8%84-%E0%B8%AD%E0%B8%B1%E0%B8%AA%E0%B8%AA%E0%B8%A3%E0%B8%B2-%E0%B8%AB%E0%B8%B1
vavada mines isplata iskustva https://vavada2007.help/
В этом обзорном материале представлены увлекательные детали, которые находят отражение в различных аспектах жизни. Мы исследуем непонятные и интересные моменты, позволяя читателю увидеть картину целиком. Погрузитесь в мир знаний и удивительных открытий!
Получить дополнительные сведения – https://www.guisos.es/primeros-platos/canalones-de-jamon-y-ensaladilla
Эта информационная статья охватывает широкий спектр актуальных тем и вопросов. Мы стремимся осветить ключевые факты и события с ясностью и простотой, чтобы каждый читатель мог извлечь из нее полезные знания и полезные инсайты.
Изучить эмпирические данные – https://ru.wikipedia.org/wiki/%D0%9F%D0%BE%D0%BB%D0%BE%D1%81%D1%8B_%D0%B2%D1%82%D0%BE%D1%80%D0%B6%D0%B5%D0%BD%D0%B8%D1%8F
Этот текст призван помочь читателю расширить кругозор и получить практические знания. Мы используем простой язык, наглядные примеры и структурированное изложение, чтобы сделать обучение максимально эффективным и увлекательным.
Раскрыть тему полностью – https://bamboo.st/2019/10/04/%E3%81%8A%E5%BE%85%E3%81%9F%E3%81%9B%E3%81%97%E3%81%BE%E3%81%97%E3%81%9F
Публикация приглашает вас исследовать неизведанное — от древних тайн до современных достижений науки. Вы узнаете, как случайные находки превращались в революции, а смелые мысли — в новые эры человеческого прогресса.
Узнать из первых рук – https://www.ekonomicky.sk/monetarizmus
Эта статья предлагает живое освещение актуальной темы с множеством интересных фактов. Мы рассмотрим ключевые моменты, которые делают данную тему важной и актуальной. Подготовьтесь к насыщенному путешествию по неизвестным аспектам и узнайте больше о значимых событиях.
Всё, что нужно знать – https://www.elkhartnorthside.org/water-sports-03