How to create and configure your own STUN/TURN server with coturn in Ubuntu 18.04
Learn how to configure your own stun/turn server using coturn in Ubuntu 18.04 from scratch.

On the last days, we needed to implement a WebRTC based videoconference application using PeerJS with Node.js. As mentioned on the official notes of getting started with this technology, most of the times to make applications like this work, you will need a special kind of server that is on charge of relaying the traffic between peers, because sometimes a direct socket is often not possible between the clients (unless they reside on the same local network). This is known as a TURN server, that stands for Traversal Using Relay NAT and is a protocol for relaying network traffic.
As it’s quite difficult to find a free TURN server, because there isn’t any, we ended up implementing our own STUN/TURN server and we want to share with you how we implemented it. In this tutorial, we’ll explain you how to install and configure coturn from scratch to create your own STUN/TURN server in Ubuntu 18.04.
Requirements
In order to succeed with the implementation of this tutorial, you will need obligatorily the following things:
- An Ubuntu server (18.04 in our case).
- Know the public IP of your server, in our case we will use our server public IP 209.126.124.122.
- Own a domain and have access to the DNS manager as you will need to create 2 subdomains (the domain will be
ourcodeworld.comin our case and we have it hosted on goDaddy). - SSL Certificates for the subdomains (preferably a certificate with wildcard e.g
*.ourcodeworld.com). Without the secure protocol, your server implementation won’t be completed and after using it on your WebRTC projects with HTTPS it won’t work, so be smart and avoid headaches, buy a SSL certificate or get a free one with LetsEncrypt.
Having said that, let’s get started with the tutorial!
1. Install coturn
To implement your own STUN/TURN server, we will rely on the Coturn project. Coturn is a free and open-source implementation of a TURN and STUN server for VoIP and WebRTC. This project evolved from rfc5766-turn-server project (https://code.google.com/p/rfc5766-turn-server/). There are many new advanced TURN specs which are going far beyond the original RFC 5766 document. This project takes the code of rfc5766-turn-server as the starter, and adds new advanced features to it.
Before proceeding with the installation of coturn, be sure to update the apt-get repository to its latest version with the following command:
sudo apt-get -y updateThen, install the coturn package with the following command:
sudo apt-get install coturnThis will install the coturn TURN project in your server, a free open source implementation of TURN and STUN server. Be sure to stop the service after installing the package with the following command, as it will be automatically started once the installation finishes:
systemctl stop coturnYou will be able now to follow up the rest of the tutorial. For more information about the coturn project, be sure to visit the official repository at Github to check the documentation.
2. Enable coturn
After the installation, you will need to enable the TURN server in the configuration file of coturn. To do this, uncomment the TURNSERVER_ENABLED property in the /etc/default/coturn file. You can use nano to edit the file from the terminal:
nano /etc/default/coturnBe sure that the content of the file has the property uncommented, just like this:
TURNSERVER_ENABLED=1Save the changes and proceed with the next step.
3. Backup and create configuration file
Now that the turn server is enabled, you need to modify the configuration file according to your needs. Be sure to backup the original configuration file that lists all the possible options of coturn, in case you need to restore in other ocassion. You can use the following command to do that:
# Move the original turnserver configuration file to a backup in the same directory
mv /etc/turnserver.conf /etc/turnserver.conf.originalThis will basically rename the file. Then, proceed to create the configuration file in the same directory:
nano /etc/turnserver.confAnd paste the following content on it:
# /etc/turnserver.conf
# STUN server port is 3478 for UDP and TCP, and 5349 for TLS.
# Allow connection on the UDP port 3478
listening-port=3478
# and 5349 for TLS (secure)
tls-listening-port=5349
# Require authentication
fingerprint
lt-cred-mech
# We will use the longterm authentication mechanism, but if
# you want to use the auth-secret mechanism, comment lt-cred-mech and
# uncomment use-auth-secret
# Check: https://github.com/coturn/coturn/issues/180#issuecomment-364363272
#The static auth secret needs to be changed, in this tutorial
# we'll generate a token using OpenSSL
# use-auth-secret
# static-auth-secret=replace-this-secret
# ----
# If you decide to use use-auth-secret, After saving the changes, change the auth-secret using the following command:
# sed -i "s/replace-this-secret/$(openssl rand -hex 32)/" /etc/turnserver.conf
# This will replace the replace-this-secret text on the file with the generated token using openssl.
# Specify the server name and the realm that will be used
# if is your first time configuring, just use the domain as name
server-name=ourcodeworld.com
realm=ourcodeworld.com
# Important:
# Create a test user if you want
# You can remove this user after testing
user=guest:somepassword
total-quota=100
stale-nonce=600
# Path to the SSL certificate and private key. In this example we will use
# the letsencrypt generated certificate files.
cert=/usr/local/psa/var/modules/letsencrypt/etc/live/ourcodeworld.com/cert.pem
pkey=/usr/local/psa/var/modules/letsencrypt/etc/live/ourcodeworld.com/privkey.pem
# Specify the allowed OpenSSL cipher list for TLS/DTLS connections
cipher-list="ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384"
# Specify the process user and group
proc-user=turnserver
proc-group=turnserverThis basic configuration usually works for most of the needs, however in case that you need to configure something else, be sure to visit the official docs of the configuration properties here. Don’t forget that in this case, we included a test user in the file to test the TURN server later, however you are free to remove it and create it later with turnadmin.
Till this point, everything that we need to configure on our server should be done.
4. Create stun/turn DNS records on your DNS manager
As we mentioned at the beginning of the article, you need to own some domain where the STUN/TURN server will be hosted. You will need to create 2 new A records using turn and stun as host respectively pointing to the public IP of your server:
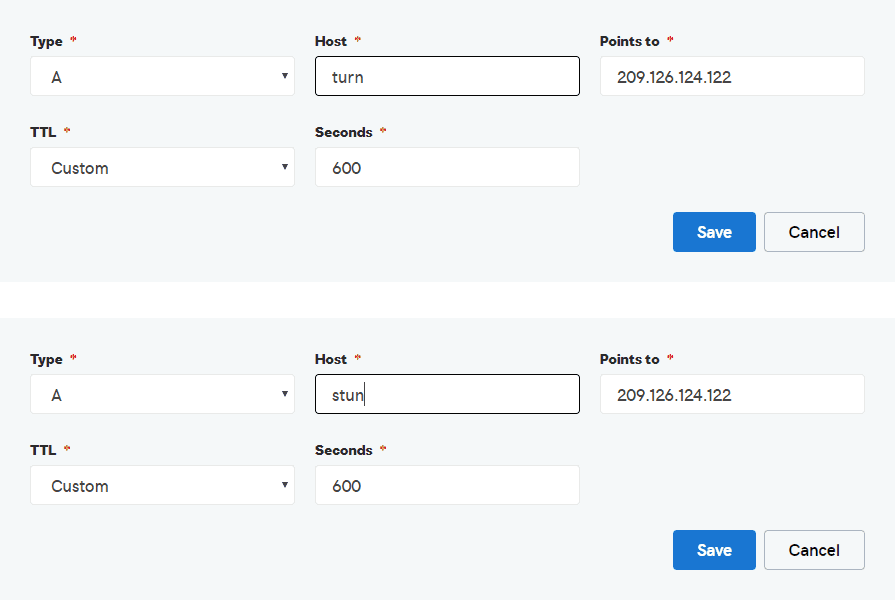
Our registrar is GoDaddy and they offer the DNS management system, so we created them easily with a form. After registering the subdomains and waiting the proper time so they can be found with a DNS lookup, you can proceed with the next step.
5. Create a long term user using turnadmin
Turnadmin comes included in the default package of coturn, this application is a TURN relay administration tool that allows you to manage the users of your turn/stun server. Clients will need credentials in order to connect to your turn server, so you can register them like this:
sudo turnadmin -a -u USERNAME -r REALM -p PASSWORDFor example, to create a test user i would run the following command (username brucewayne, realm ourcodeworld.com and password 12345):
sudo turnadmin -a -u brucewayne -r ourcodeworld.com -p 12345Note that we created previously a single user on the /etc/turnserver.conf file with plain text setting the username as guest and password somepassword.
6. Turn coturn server on
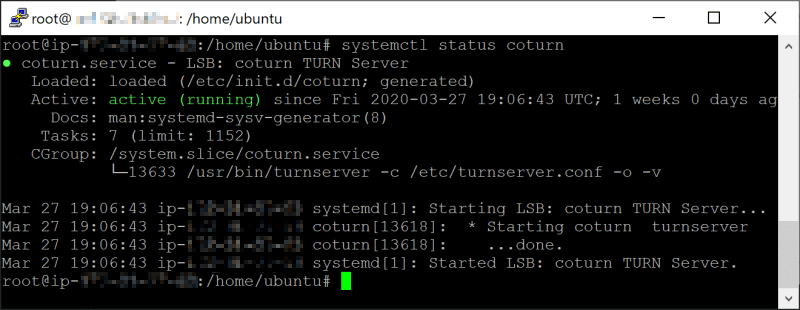
After creating the users and configuring coturn properly, you will be able to start the service so clients can connect to it. Proceed with the initialization of the service with the following command:
systemctl start coturnThis will start the service of coturn in the server. You can check the status of the service with the following command:
systemctl status coturnWhich should output something similar to:
7. Testing TURN/STUN server
Fortunately, there’s an awesome online tool that allows you to check the functionality of STUN/TURN servers. This tool is Trickle ICE, a WebRTC page project that tests the trickle ICE functionality in a regular WebRTC implementation. It creates a PeerConnection with the specified ICEServers (which will contain the information of our recently implemented server), and then starts candidate gathering for a session with a single audio stream. As candidates are gathered, they are displayed in the text box below, along with an indication when candidate gathering is complete.
To get started open the tool website in a new browser tab and start filling the ICE servers form. In the form you will need to provide the STUN or TURN URI respectively with the credentials (only for the TURN server) like this:
stun:stun.ourcodeworld.com:5349
turn:turn.ourcodeworld.com:5349As you can see the URI’s follow the pattern of the protocol:domain:port. The form would be filled like this:
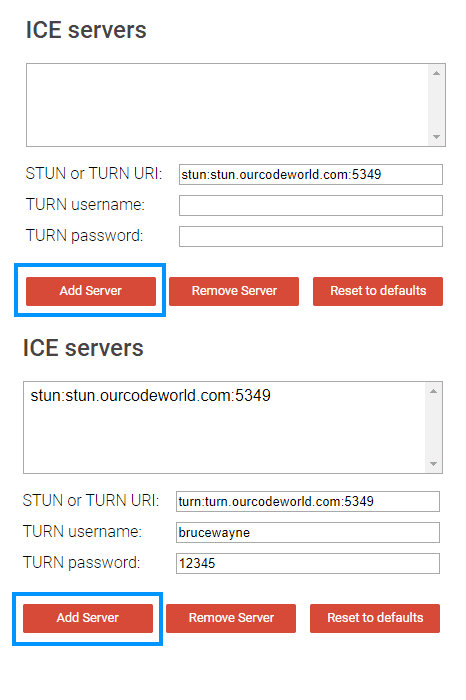
Then on the bottom of the page in the ICE options, run the test pressing the Gather candidates button:

The test should generate something similar to:
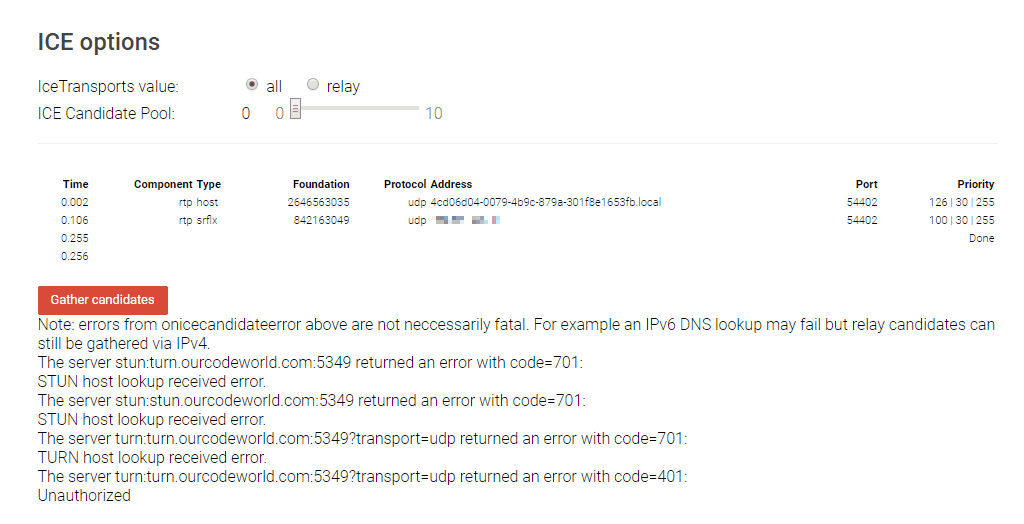
Note that this happens because the tool has a bug on most recent browsers, however as long as you are able to re-run the test pressing Gather candidates again and again (so the gather candidates button doesn’t block) everything should be ok with the STUN/TURN server.
Notes
- Be sure that your server has the ports 5349 and 3478 open.
- If you are behind a NAT, for example with an Amazon EC2 instance, be sure to configure the external IP in the configuration file, like mentioned on this question in Stack Overflow.
This piece is an elegant dance between thought and emotion, where each idea flows naturally into the next. I found myself following your words, not just with my mind, but with my heart, as you navigated complex ideas with such grace. It’s writing that doesn’t just inform — it invites the reader into a deeper relationship with the material.
Die Gele sind relativ neu auf dem Markt, überzeugen aber mehr
und mehr Transmänner und Ärzte. Zu Beginn der Behandlung mit Nebido sind die Intervalle relativ kurz; in der Regel werden die ersten drei Spritzen im Abstand von 6 Wochen verabreicht.
Wichtig ist hier die Rolle des SHBG (Sex Hormone Binding Globuline).
Dadurch ist immer weniger freies Testosteron und Östrogen im Körper,
obwohl der Gesamt-Spiegel gleich bleibt. Die Steuerung geschieht durch “Andocken” an hormon-spezifische Rezeptoren in den Körperzellen. Hormon X kann also nur
an den Rezeptor für X wirken, wohingegen Hormon Y hier nicht landen kann.
Wer langfristig übermäßig Stress hat, riskiert, dass der Spiegel unterhalb
des Idealwertes sinkt. Verschiedene Medikamente, wie
Glukokortikoide oder die Anti-Baby-Pille führen in manchen Fällen einen Mangel an Testosteron hervor.
Eine hohe Konzentration im Blut verursacht Testosteron Nebenwirkungen. So bekommt ein Kraftsportler neben stärkerer Muskulatur auftretende Hautprobleme, wie Pickel.
Unter Umständen steigt die Anzahl roter Blutkörperchen gefährlich an.
Aus diesem Grund sind in Deutschland Testosteron-Pflaster nicht
mehr erhältlich. Die Nebenwirkungen sind hier im Vergleich
zum Gel deutlich stärker. Solltest du dich für
Testosteron-Gels oder Testosteron-Pflaster entscheiden, so kann es teilweise zu starken Hautirritationen führen. Von Juckreiz über Rötungen bis hin zu Ausschlägen sind hier möglich.
Das Zuführen externen Testosterons sorgt im
Körper dafür, dass vermehrt Wasser eingelagert wird.
[5] Je höher die Dosis, desto höher die Wassereinlagerungen (“Ödeme”).
Über die Blutgefäße erreicht das Testosteron seine Zielorgane/gewebe, wo es entweder direkt als Testosteron oder aber nach Metabolisierung (Umbau)
zu Dihydrotestosteron bzw. Östrogenen (17 beta-Östradiol) seine organspezifischen Wirkungen entfaltet.
Die einzelnen Syntheseschritte der jeweiligen Hormone sind in Abb.
Darüber hinaus ist Testosteron wichtig für Knochen und Muskeln, Fett- und Zuckerstoffwechsel sowie die Blutbildung.
Sehr wichtig ist die schützende Funktion von Testosteron auf Herz und Gefäße.
Mehrere Langzeitstudien haben gezeigt, dass die Lebenserwartung bei Männern mit
der Höhe des Testosteronspiegels positiv korreliert.
Die richtige Balance ist wichtig, jedes Extrem ist ungesund
und führt zum körperlichen Zusammenbruch. Aus diesem Kreis kann man nur ausbrechen,
indem man abnimmt, und zwar das Fettgewebe reduziert.
In der Folge erhöht sich der Testosteronspiegel, da weniger Aromatase im Fettgewebe das Testosteron in Östrogen umwandelt.
So wurde bei Cis-Männern im Training beobachtet, dass sie
bis zu 30% mehr Testosteron hatten. Hörten diese
jedoch für ein paar Wochen mit dem Coaching auf, sank der Spiegel wieder nach unten.
Bei jüngeren Männern hilft oft ein vorübergehender Hormonersatz,
der aber leider viel zu selten angeboten wird, so Dr. Hesch.
Das liegt auch daran, dass kein Mann weiß, wie sein individueller Normalwert
war, als er in der Pubertät zum Mann wurde. Mit der Anmeldung zum Publication informieren wir Sie regelmäßig über neue
und passende Gesundheitsthemen. Bei Bedarf unterstützt Sie Mondosano auch bei der
Vermittlung von neuen und passenden Studien.
Besonders in Kombination mit intensivem Krafttraining und einer eiweißreichen Ernährung
lassen sich die positiven Effekte eines erfahrungen testosteron ersatztherapie (ezojob.com) Boosters
noch weiter maximieren. Die für eine Testosterontherapie typischen möglichen Nebenwirkungen sind in Tab.
Männer, die unter einer Testosteronsubstitutionstherapie stehen müssen sich
regelmäßigen Kontrolluntersuchungen (Laborwerte, Prostatacheck), unterziehen. Im Einzelfall zwingen Nebenwirkungen zur Dosisreduktion,
selten zum Absetzen der Therapie, insbesondere wenn es zu einem Hämoglobinanstieg (Thrombose- und Emboliegefahr) oder zu Prostatareaktionen kommt.
Sie bietet die Möglichkeit, Symptome wie Antriebslosigkeit, Müdigkeit und einen verminderten Sexualtrieb wirksam zu behandeln.
Die Pflaster werden täglich auf saubere, fettfreie Hautstellen (Bauch, Rücken oder Oberschenkel) geklebt.
Sie geben kontinuierlich Testosteron über die Haut ab und
sorgen für einen stabilen Spiegel. Sie gelten jedoch als unterlegene Therapieform,
da sie häufiger zu Hautreizungen und Problemen mit der
Haftung führen.
Auch zu den Langzeitfolgen der intermittierenden Hormonentzugstherapie im Vergleich zur durchgehenden Hormontherapie oder den neueren Kombinationstherapien gibt es bisher keine aussagekräftigen Daten. Eine alleinige
Hormontherapie können Betroffene ambulant erhalten. Abirateron hemmt ein wichtiges Eiweiß (CYP17), das für die Bildung von Testosteron notwendig ist.
Damit verringert es sowohl die Bildung von Testosteron in den Hoden, in der
Nebennierenrinde als auch im Tumorgewebe selbst. Er ist das Steuerzentrum für die Bildung von Testosteron im Körper.
Das erhöht vorübergehend den Wert des prostataspezifischen Antigens (PSA).
Auch tumorbedingte Beschwerden wie Knochenschmerzen können zunehmen. Um das zu vermeiden, verschreiben Urologinnen und Urologen in der Regel
vorbeugend sogenannte Antiandrogene (Mehr dazu lesen Sie im Abschnitt “Antiandrogene”).
Diese nehmen Männer in den ersten Wochen der Therapie mit einem GnRH-Agonisten zusätzlich ein. Sie
sind schon seit längerem für die Hormontherapie bei Prostatakrebs zugelassen. Als “klassische Hormontherapie” bezeichnen Fachleute eine Antihormontherapie mit sogenannten GnRH-Agonisten oder GnRH-Antagonisten. Daneben gibt es noch andere Medikamente für eine
Hormonentzugstherapie, unter anderem die neuen hormonellen Substanzen.
Roughly 5% of males between the ages of 50 and fifty nine years old have low levels of testosterone along with symptoms like a decrease in their libido and
obvious sluggishness. The hormone replacement docs at Elite HRT may help you create
a safe testosterone substitute therapy plan as acceptable for you and
your body. We’ll monitor your progress and
provide you with instructions to steadily elevate your testosterone to a level that’s
secure and comfortable for you. Starting a better skincare routine, managing testosterone levels,
and incorporating more skin-healthy B nutritional vitamins into your food plan might help to regulate pimples.
The objective is to have regular testosterone ranges —
you must never use testosterone or steroids if a doctor hasn’t deemed
them to be helpful for your well being and wellbeing.
Excessive testosterone ranges are uncommon, but they can have critical penalties in your well
being. If you’re worried your testosterone levels may be too high, there are a couple of things you must
know.
As part of your subscription and as medically indicated,
physicians prescribe drugs, and suggest dietary supplements which are delivered to you from the
comfort of your home. TRT may help by appearing on the elements of the mind that control libido.
Testosterone is measured in nanograms per deciliter (ng/dL)
and ranges fluctuate with age, says Calvert.
T peaks in your late teens and early twenties,
with healthy ranges between 300 and 1,200 ng/dL. Testosterone Replacement Remedy can improve vitality ranges, libido, and the effects of aging.
The mind will sign for the physique to cease producing
testosterone when it senses an excessive quantity of of it.
When this occurs, the testicles shrink in size as a end result of it stops producing testosterone.
TRT raises testosterone levels nevertheless it additionally lowers sperm manufacturing by decreasing ranges of
another hormone, referred to as follicle-stimulating hormone (FSH), which
is important to produce sperm. For men with low T who created Steroids
wish to have youngsters, remedies such as Clomid can scale back signs of low T while
leaving fertility intact. Your physician or testosterone replacement therapist should verify your blood levels.
I didn’t have any of the crappy side effects that my urologist’s protocol gave me.
I started feeling somewhat better concerning the situation a few minutes into my
initial appointment, after she ordered a full blood panel for me.
Some of those direct-to-consumer, TRT corporations don’t even require
blood work. I truthfully felt like I was being drained dry, however I appreciated how thorough she was.
If you notice changes in your blood stress, call your doctor instantly
to schedule a wellness verify. You must also by
no means order testosterone supplements online with no prescription.
Whereas muscle improvement is usually optimistic, unexplained changes warrant additional investigation. Researchers imagine that males with high ranges of testosterone smoke and drink greater than these with a decrease focus of this
hormone within the physique. The findings of these specialists additionally counsel that these men intervene
in fights, present combative behaviors and might embark on risky ventures extra often than men with less testosterone
do. Their research additionally reveals a bent of those men to commit acts of infidelity and
abuse with their companions or spouses. All of this reduces the
active (free) type of testosterone in the body. Your specific therapy plan will depend upon the underlying cause of your elevated testosterone degree.
In some instances, it could be as easy as adjusting
or stopping your TRT.
Testosterone ranges are too carefully managed by the pituitary
gland within the brain for that to occur.
James Harrington stands as a leading authority in testosterone alternative therapy (TRT).
With rigorous educational training and deep-rooted experience in well being
and wellness, he provides unparalleled experience
to Best TRT.
Tumors in the adrenal glands or testicles can also cause T levels to spike.
Adrenal gland tumors that produce intercourse hormones are rare; you’ve obtained
about a 2 in 1,000,000 chance of developing one (6), they usually aren’t
at all times cancerous. Tumors within the Leydig cells of the testes (where
sperm is produced) are additionally rare and are usually benign (7).
If you’re concerned you could have excessive ranges of testosterone then excessive
blood cell depend is among the most evident effects of
an extreme amount of testosterone.
However, excessive testosterone ranges in folks assigned female at start can cause signs like male-pattern facial
hair, acne, irregular intervals, infertility, and temper adjustments.
Excessive testosterone in males isn’t common, but
genetics, steroid use, and a few medical situations can elevate
T exterior the healthy range. Excessive testosterone can result in physical and
psychological symptoms, together with an increased
danger for most cancers, heart issues, infertility.
As A End Result Of sperm is produced within the testicles,
the higher the degrees of testosterone, the less sperm your body is likely to
create. Greater levels of testosterone are also capable of lowering the overall production of sperm in your body,
which is, in fact, linked to the above effect of shrinking testicles.
If your body is retaining fluid together with the
difficulty to start out a urine stream, your physique is prone to undergo from urinary tract infections.
If you’re finding that you’re getting UTIs pretty often, it’s time to
have your testosterone levels examined. If you’re struggling with drowsy driving
or different temper and memory problems, it
may be an indication that you’re suffering from sleep apnea.
If you know that you’re exhibiting signs of sleep apnea then it might be time to come to terms with having
a excessive level of testosterone as nicely. Sleep apnea may
cause fragmented sleep and very low blood oxygen ranges, if you’re
experiencing this it could be a sign that your testosterone ranges are
too excessive.
If you’re suffering from inexplicable temper swings,
extreme ups and downs in your mood, this could positively be a aspect impact of excessive testosterone levels.
You may really feel really happy one minute and very livid or depressed the subsequent, so just make sure you monitor your
moods. Myocardial infarction, or extra bluntly put, coronary
heart assaults are prevalent in males with excessive testosterone levels.
Though it is not a quite common effect, we really feel it
should nonetheless be talked about. Men with testosterone
ranges exceeding 500 nanograms per deciliter are double as likely to endure from
a heart attack than those that have lower ranges. When there’s an extreme amount of testosterone present within the body, the
male reproductive system is overwhelmed and this will
create reproductive problems.
Understanding these components and dealing with a
healthcare professional might help individuals navigate the restoration process and guarantee their hormone levels return to normal safely and effectively.
In conclusion, there are a number of components that can influence how shortly testosterone impacts the voice.
Beginning age, genetics, dose and duration of hormone therapy, vocal coaching,
and particular person variations all play a significant
function within the pace and extent of vocal adjustments.
It is essential for people undergoing testosterone remedy
to have realistic expectations and perceive that the voice transformation is a gradual process that varies from
individual to individual.
One common explanation for fluctuating testosterone
levels is a condition known as polycystic ovary syndrome (PCOS).
PCOS is characterised by the presence of multiple small cysts on the ovaries,
together with high ranges of androgens, including testosterone.
Ladies with PCOS usually expertise irregular or absent durations,
in addition to different signs similar to acne, weight acquire, and
excess hair development.
Insulin resistance is a situation whereby
the body turns into immune to the flexibility of insulin (a hormone secreted by the pancreas)
to shuttle glucose (sugar) into cells. To compensate for this resistance to insulin,
the pancreas produces more insulin, which outcomes in a rise in circulating
insulin ranges. In many people, the pancreas cannot maintain such a excessive insulin output over an extended time
period, so finally insulin levels start to lower and
blood glucose ranges enhance. One of the consequences of testosterone therapy in many trans males is a
redistribution of physique fats from a “female-like” sample
to a “male-like” pattern. A decrease in fatty
tissue across the breast area due to this fact
would not be uncommon. Nevertheless, unless he’s very small-chested to start with, this decrease will not
be vital enough to make his chest appear male
(without surgical intervention). When taking testosterone for transition, one’s physician typically takes periodic blood
tests to monitor a affected person’s general health.
This comprehensive strategy ensures you obtain the very best care and helps
keep hormonal balance, whether you continue with TRT, taper off,
or discover alternatives like Enclomiphene. Your doctor may
cut back the dosage slowly over weeks or months, monitoring your hormone
ranges and signs closely. This method minimizes withdrawal signs and supports a smoother transition off TRT.
In this article, we’ll have a look at the potential
unwanted facet effects, signs and shifts you would possibly experience when you come off the pill.
Testosterone is a hormone that plays a vital role in male growth, however it can be present in females in decrease levels.
During pregnancy, a balance of hormones is essential steroids for women weight loss (Oliva)
the healthy growth of the fetus. Introducing extra testosterone
via remedy can disturb this steadiness, which can result in issues.
For occasion, if a lady takes testosterone while pregnant,
it might possibly lead to virilization in a female fetus.
This means the baby woman could develop male bodily traits,
corresponding to an enlarged clitoris or ambiguous genitalia.
While virilization is probably the most well-known effect, testosterone can even disrupt the general hormonal surroundings in the womb, probably leading to different
developmental points.
They can present personalized steering and ensure that workouts are performed accurately and safely.
Round three to 6 months on testosterone, individuals may observe a significant drop in pitch
and a extra noticeable change of their voice. Some individuals might expertise a
cracking or breaking of the voice during this course of, which is totally regular.
The fee at which the voice deepens depends on a quantity of components, together
with the person’s starting pitch, genetic predisposition, and dosage of testosterone.
The extent and rate of voice adjustments may also be influenced
by lifestyle habits, corresponding to smoking, excessive
alcohol consumption, and excessive shouting or screaming, which may harm the vocal cords.
A meta-analysis on physical exercise and intercourse hormones suggested that movement may assist regulate hormone ranges.
Common bodily exercise, similar to strolling, weight coaching, yoga, or
HITT, has shown optimistic results on hormone regulation.
Following a well-structured PCT protocol and implementing way
of life adjustments can assist the physique’s pure
restoration process. It may take a quantity of weeks or even months for
testosterone levels to return to normal, so persistence is essential.
Lastly, age can also play a role in how quickly testosterone ranges normalize after a cycle.
Due To This Fact, older people might experience a slower recovery time in comparison with youthful individuals.
Testosterone therapy can result in a number of physical modifications in transgender males,
one of the most prominent being the deepening of the voice.
This vocal change is the result of elevated vocal twine thickness and
lengthening of the vocal folds.
Simply such as you may need felt somewhat out of whack when you first began using hormonal birth control, it’s regular to feel
slightly off when you cease. The good news is that your physique
will regulate pretty rapidly — normally inside a matter of a few weeks.
Hormonal birth control strategies like the pill, patch, ring or
shot work by turning off hormone indicators between your mind
and pituitary gland and your ovaries to stop you from ovulating,
so you can’t get pregnant. Those hormones — and the ovulation process —
turn right again on whenever you cease taking them, which might lead to
some sudden unwanted effects. Sure, fertility treatments like ovulation induction or in vitro fertilization (IVF)
could help those that have undergone testosterone therapy to conceive.
Nonetheless, the effectiveness of these treatments will depend on particular person elements such
as age and the length of testosterone use. Long-term
testosterone therapy can have lasting results on fertility,
particularly if ovarian operate is suppressed for an extended interval.
Regular monitoring and medical supervision stay essential to ensure the well-being and optimal hormone stability of transgender girls undergoing hormone alternative therapy.
Personal experiences shared by transgender women who’ve undergone testosterone HRT
additional support the scientific findings. Many
transgender girls report a cessation of their menstrual cycle after
beginning hormone therapy. Some may initially expertise irregular bleeding,
however this normally subsides over time. These firsthand experiences provide useful insights into the individual variation and overall impact of testosterone HRT
on the menstrual cycle. When discontinuing testosterone substitute
therapy, your body undergoes a number of hormonal changes.
Nonetheless, it’s essential to understand why
a gradual tapering off course of is important. Prometrium is a female hormone
used to cause menstrual durations in ladies who haven’t but reached …
Adding testosterone to your body can lead to increased
fluid retention, resulting in your physique feeling bloated and gaining weight.
It is not essentially the most extreme side impact and shouldn’t discourage you from continuing your TRT.
Depending on whether you’re a light or heavy drinker, your
strategy round chopping back might be different. Whereas
these areas could take the greatest hit from regular drinking, they aren’t the only ones affected.
The effectiveness of this therapy relies
on individualized dosing to deliver essentially the most aid with
the least amount of hormones and may require time in your physique to adjust.
Some common unwanted side effects could occur, corresponding
to breast tenderness, zits, and bleeding.
Most of the time, these are minimal and short-term issues, and infrequently resolve with dose adjustments.
Our bodies follow a circadian rhythm, which means the day by day cycle of 24
hours affects how our physique capabilities. Aiming for 7-9 hours of
restorative sleep per evening is usually recommended
for optimum health. Some ladies might experience sleep
disturbances because of hormonal shifts, and in those circumstances,
consulting a physician for steerage is advisable.
A prospective cohort study in Denmark checked out a million ladies ages 15
to 34 over 14 years and assessed the connection between hormonal birth control and subsequent mood adjustments.
Earlier Than delving into the influence of testosterone HRT, it is essential to understand the traditional menstrual cycle.
The menstrual cycle typically lasts around 28 days
and is regulated by numerous hormones, including estrogen and progesterone.
These hormones are responsible for follicle
development, ovulation, and uterine lining thickening in preparation decca steroids for sale possible pregnancy.
Research has proven that high ranges of testosterone can disrupt the regularity of the menstrual cycle and result in irregular intervals.
This is as a outcome of testosterone can intervene with the conventional
production and balance of estrogen and progesterone,
that are needed for the proper functioning of the menstrual cycle.
In addition, they may advocate different therapies to extend low testosterone ranges, similar
to enclomiphene, a selective estrogen receptor modulator.
Which is just about how most non-trans folks preserve a healthy physique weight.
This is amongst the most common myths about trans individuals who take testosterone,
however there isn’t any compelling proof to assist such a sweeping generalization. Indeed, whereas some trans men anecdotally report feeling shorter tempered or irritable for a
interval after beginning T, many others report that they feel
calmer and extra even-tempered since taking T. Yet repeatedly, trans males and their family members
voice concern that taking testosterone will by some means automatically change a trans guy right into a horrible, angry, or violent
individual. The cessation of menstruation as a end result of testosterone is commonly momentary, particularly within the
early stages of HRT. Many transgender males proceed to
expertise sporadic or irregular durations through the
first few months of testosterone therapy. Nevertheless, after months or years of constant testosterone
use, menstruation sometimes stops altogether.
If your testosterone levels do not return to regular within a few months after completing
a cycle, it is advisable to seek the advice of with a healthcare skilled, corresponding to an endocrinologist or
urologist. They can evaluate your specific scenario and
decide if testosterone substitute remedy (TRT) may be acceptable.
TRT involves using prescribed testosterone to supplement or exchange the body’s natural
testosterone production. Nevertheless, TRT ought to
solely be considered under the steering of a healthcare professional and shouldn’t
be used for leisure or non-medical purposes. If testosterone ranges don’t return to regular within a certain time frame, it is very
important search medical intervention.
Testosterone therapy is mostly not really helpful for girls who
are pregnant, as it could pose risks to the growing fetus.
High ranges of testosterone within the mother’s body may interfere with the natural development of the child,
notably with the event of the reproductive organs. Your physique gets used
to the exterior testosterone, and this can affect how your system capabilities even after you cease.
It’s a bit like how your muscular tissues may change should you cease exercising for a very lengthy time.
Long-term use of TRT can have lingering effects, so it is crucial to monitor your hormone ranges and general
health with a healthcare skilled. They might help make certain that your transition off TRT is as easy as potential, minimizing any potential long-term
impacts on your endocrine system.
Skilled household nurse practitioner Kellie Lewis and the professional practitioners at Avanti Medical Center in Lehi, UT are ready
to discuss any questions and concerns that you might have.
Stress can affect your cycle — and in the end, exacerbate any unpleasant symptoms you may be
dealing with. If your pill, patch or ring labored completely, your periods
were regular with a medium circulate and also you had no (or minimal) spotting at other occasions of
the month. Let your partner know your boobs are ouch-prone
proper now so they’re further mild throughout baby-making classes.
Many men continue TRT long-term if their pure testosterone ranges stay low.
Others may decide to cease if they really feel improvement or choose to handle without it.
Consulting a healthcare supplier helps determine one of the best method for your long-term well being.
At The Sanctuary, we’re dedicated to helping you make knowledgeable choices about your well being.
If you’re interested in learning more about testosterone alternative therapy and the way it can support your wellness journey, we’re here to assist.
Whether you’re considering starting or stopping TRT,
we’re right here to supply the guidance and assist you should
make the most effective choice for your life and health.
Des traitements qui permettront aux sufferers de réaliser leur rêve de devenir
mother and father. Les femmes qui ont peu de
testostérone se sentent souvent soudainement
fatiguées et sans énergie. Cela peut se manifester comme une difficulté à sortir du
lit le matin ou comme vous sentir molle tout le temps,
même si vous dormez suffisamment. Il est important d’utiliser ce médicament conformément aux indications de votre médecin.
Pendant la puberté, la testostérone est responsable du développement des attributs masculins comme une voix plus profonde, la
barbe et les poils du corps. La production de testostérone explose
à l’adolescence et culmine à la fin de l’adolescence ou au début de la vingtaine.
Après l’âge de 30 ans, il est naturel que le taux de testostérone diminue d’environ un pour cent
chaque année. Il est essentiel de noter que même si certains hommes ont une
raison claire pour expliquer leurs niveaux de
testostérone inférieurs, d’autres peuvent avoir plusieurs facteurs contributifs et, dans certains cas, la cause reste inconnue.
La testostérone joue un rôle dans le développement de la masse musculaire, et des niveaux réduits de l’hormone peut entraîner une perte importante de masse musculaire.
La testostérone est une hormone sexuelle souvent associée aux hommes, bien que les femmes en aient de petites quantités.
La gestion des maladies chroniques est un domaine critique des
soins de santé, nécessitant des soins continus, la participation des patients
et une utilisation efficace des ressources. L’intégration de l’IA
au contact humain peut révolutionner ce domaine en fournissant des soins personnalisés et efficaces.
Vicks VapoRub est une pommade topique populaire utilisée depuis des générations pour soulager diverses maladies.
Chez l’homme, l’assurance couvre-t-elle la thérapie TRT ?
– Lauri – testostérone est produite par les cellules de Leydig
qui se trouvent dans les testicules. Le taux de testostérone augmente chez les garçons
au moment de la puberté. A cette période, les
changements hormonaux entraînent des changements physiques.
La testostérone joue un rôle clé dans la manufacturing de
spermatozoïdes.
On parle alors d’« hypogonadisme tardif » ou d’« hypogonadisme
à déclenchement tardif ». Si la manufacturing de testostérone est insuffisante, une carence peut
se produire. Une carence en testostérone est également connue sous le
nom de déficit en testostérone ou « Low T ». Elle touche aussi bien les hommes que les femmes, bien que
les hommes y soient plus exposés. Votre médecin examinera votre apparence physique et
votre développement sexuel. Étant donné que les taux de testostérone sont habituellement plus élevés le matin,
l’analyse de sang devrait être effectuée avant 10 h chez les hommes plus jeunes.
Les médecins s’entendent sur le fait qu’un suivi est essentiel pour ce type de traitement.
Même si ce n’est pas prouvé scientifiquement, il
subsiste un doute entre la TRT et le développement de cellules du most cancers
de la prostate. Le médecin et le affected person choisiront le mode d’administration qui convient le mieux.
À l’examen, il peut y avoir une diminution de la masse corporelle maigre
avec une réduction du volume et de la drive musculaires et une
augmentation de la circonférence abdominale.
Une diminution ou un amincissement des poils du visage et de la
poitrine et des altérations cutanées telles qu’une augmentation des rides du visage et une peau d’apparence
pâle suggérant une anémie peuvent également être notés.
Des testicules devenus plus petits ou plus mous peuvent également être présents.
Enfin, une faible densité minérale osseuse avec ostéopénie ou ostéoporose peut également suggérer un problème.
La testostérone est connue comme étant une hormone masculine, mais
il faut savoir que les femmes aussi produisent de la testostérone,
même si en plus faible dose. C’est une hormone sexuelle
au même titre que les œstrogènes ou la progestérone.
Le traitement hormonal n’est pas sans hazard, il peut poser des
risques. Par exemple, il peut augmenter le taux de certaines
cellules sanguines. C’est pourquoi, un suivi médical régulier est indispensable pendant tout le traitement.
70918248
References:
The first step in choosing between TRT and HGH is to evaluate
your individual signs and health objectives. If you’re primarily experiencing signs associated to
low testosterone, such as decreased sex drive, erectile dysfunction, and reduced muscle
mass, TRT will be the more acceptable choice. If you could have been identified with development hormone deficiency based on signs and laboratory exams, you could be a
candidate for HGH therapy.
HGH and steroids have related results on the physique, however they work in several methods.
Consequently, individuals may encounter enhanced muscle tone, expedited restoration post-exercise, elevated
ranges of power, and improved sleep quality. The efficacy of CJC 1295 in elevating growth hormone levels renders it a well-liked
choice amongst those in search of to optimize their physical
efficiency and general state of well-being.
It’s necessary to grasp what every of these powerful medicine is as nicely as their potential unwanted effects earlier than making a choice.
Steroids are artificial chemical substances that have an enormous similarity to
the male hormone testosterone. Steroids may be prescribed to treat a quantity of health issues but they are unlawful to young children, with
or without a prescription.
It’s necessary to notice that each Anavar and HGH ought to solely be used under
the supervision of a healthcare professional.
It is necessary to note that the benefits of Anavar usually are
not restricted to those listed above. The steroid
may additionally be used to treat medical conditions similar to osteoporosis and muscle losing.
Artificial HGH injections speed up muscle repair and growth,
offering an unfair advantage in athletic efficiency. The largest
natural fluctuations happen in childhood, where HGH helps with muscle and bone progress, in addition to the growth of all different organs of
the physique. If you’re experiencing indicators
corresponding to decreased muscle volume, low power, or erectile dysfunction, it might be because of low testosterone.
While the half-life of HGH is brief whatever the mode
of administration, bear in mind the whole impacts far outlast the
half-life.
These exams are designed to detect the presence
of HGH within the physique and can determine its use as a lot as
a number of weeks after the last injection. Athletes who are caught using
HGH can face suspension, fines, and different penalties. HGH is typically given by way of
injections, while steroids may be taken orally, injected,
or applied topically. HGH injections are usually
given once a day, whereas steroid doses can range depending
on the individual and the sort of steroid getting used.
Tri-Trenabolone is considered a really potent
steroid mixture containing three active trenbolone parts.
It is classified as 19th-nor, the identical as
Nandrolone, and refers to testosterone hormones
that lack a carbon atom.
It can be necessary to mention that whereas HGH is not going to harm your body as such,
steroids can they usually do. HGH additionally reduces the chance of experiencing
varied diseases and problems and further prolongs
your life. Conversely, Sermorelin operates by inducing the
pituitary gland to release saved progress hormone in a pulsatile trend,
fostering comprehensive growth and growth. Sermorelin operates by triggering the pituitary gland to amplify the
discharge of progress hormone, consequently bolstering numerous physiological capabilities.
This hormone also plays a pivotal position in tissue mending, the regulation of metabolism, reinforcement of the immune system,
and the promotion of general well-being.
Steroids are synthetic chemical compounds that replicate hormones naturally produced in our
bodies. Most steroids are very comparable to testosterone, and because of that, they stimulate our muscle fibers to
grow. In terms of unwanted facet effects, HGH may cause water retention, edemas,
ache, insulin resistance, and even kind 2 diabetes in vulnerable people.
In comparability, anabolic steroids also can lead to psychological addiction in around
30% of users, and discontinuing steroid use abruptly
may cause withdrawal symptoms. Due to the potential advantage it offers, the World Anti-Doping Company
(WADA) has prohibited the use of HGH, in addition to other performance-enhancing medication, corresponding to anabolic steroids (AAS).
Indeed, athletes and bodybuilders typically use HGH as a performance-enhancing drug (PED) nicknames for steroids (Archer) rising
muscle growth, restoration, and performance.
Scientists how used this understanding of the naturally produced HGH to
manufacture it artificially. HGH used by bodybuilders is a particularly strong peptide hormone with 109 amino acids.
Both method, efficiency enhancement is not a new concept in health and bodybuilding.
PEDs are a major topic in sports activities, and it’s nearly at all times coated in information media and publications.
HGH vs. Steroids by no means miss out on any dialogue involving physique enhancement medication. Arguably a variety of the
strongest body enhancers in existence, there’s a skinny line between HGH and steroids.
Not Like HGH, which is a hormone, steroids are artificial
compounds that immediately have an result on the body’s hormonal system.
Equipoise has a low stage of estrogenic activity, so these side effects ought to be simple to
regulate. Nonetheless, they can embody water retention and
gynecomastia, significantly when the steroid is used at greater doses.
Women can use Equipoise at low doses with a low threat of virilization results.
If you’re going to run an EQ cycle, take a glance at my full Equipoise (Boldenone) cycle guide.
Primobolan is considered one of the few steroids that is highly usable
by females in either oral or injectable kind.
SERMs are medications that intrude with estrogen receptors via the hypothalamus
in the mind, reducing the manufacturing of the female sex
hormone and thus growing testosterone. In our experience, how shut down a user’s testosterone ranges
shall be is determined by the dose and length of the cycle.
High doses and longer cycles will cause a more extreme suppressing impact.
The two primary types are corticosteroids and anabolic-androgenic steroids (or anabolics for short).
The anabolic-to-androgenic ratio varies between different types of AAS, which
may have an result on opposed reactions as well. Anabolic
refers to muscle development properties, whereas androgenic refers back to the promotion of
male sex traits (16). Significant hepatotoxicity from
Winstrol necessitates comparatively brief cycles to
stop excessive liver damage. Winstrol, when stacked with further oral steroids, will increase the risk
of jaundice or liver cholestasis. The bodybuilding community refers to Anavar as a chopping steroid commonly cycled throughout competition preparation.
A typical instance is combining Testosterone (Cypionate or Enanthate), Deca, Dianabol,
and Anavar. The quick cycle size naturally lends itself to minimizing or lowering
the severity of testosterone suppression. It makes PCT a quicker and easier course of than required after a for
a lot longer cycle and one the place slower-acting compounds are
used.
Anadrol (oxymetholone) is an oral steroid used in bulking cycles to build large amounts of muscle dimension (hypertrophy).
Illegal steroids are obtained via the web and through informal dealers,
like other unlawful medicine. Nonetheless, they may even be obtainable by way
of unscrupulous pharmacists, medical doctors, and veterinarians.
For instance, corticosteroids can help people with bronchial asthma breathe during an assault.
There are as a lot as 32 forms of anabolic steroids listed
on business websites. Anabolic steroids are used for
some medical conditions, however folks also use them illegally in some sports settings.
Skilled sportspeople and amateurs alike are increasingly inquiring about the usage
of legally out there anabolic hafþór júlíus björnsson steroids.
For them, sports pharmacology is not a new notion, however it’s
nonetheless unknown and untested. You will never know, for positive,
whether or not doping is a viable different to simply
training alone till you study all the elements.
Bodily and psychological stressors are rising shortly in sports activities as athletes compete
for recognition and victory, while coaching can occasionally push human capacities to
their limits. Many believe they’re a quick fix for muscle acquire,
overlooking the potential risks. Anabolic hormones are chemical compounds that trigger mobile progress through activating anabolic pathways.
Anyway, eventually the top quality products arrived intact, but not
with out undue stress at the extreme wait time.
There could be a while lags, this is understood as products take time to maneuver.
Artificial testosterone can be used to deal with people with low testosterone, which is referred to as testosterone
substitute therapy (TRT).
Erectile dysfunction is outlined as the shortcoming to attain or maintain an erection adequate for satisfactory sexual efficiency (189).
Testosterone plays an necessary position in practically each side of erectile
perform (190) and erectile dysfunction is taken into account a suggestive
symptom of testosterone deficiency (191). Nonetheless, not all hypogonadal males
develop erectile dysfunction, and TRT typically leads to only a
small enchancment in erectile perform (192). In professional sport, most organisations ban anabolic steroid use and test rivals for banned steroids.
If you do check positive, you may be banned from competing professionally.
But it’s normally found in smaller amounts, the place
it’s used to keep bones sturdy and sexual perform wholesome.
Different research exhibits that specializing in the prevention of high-risk conduct in general
can be a catchall to help keep off anabolic steroid use.
70918248
References:
making your own steroids – https://jpabs.org/800/600/http/mongocco.sakura.ne.jp/bbs/index.cgi%3Fcommand=read_message&%3Ewww.ksmro.co.kr/bbs/index.cgi?command=viewres&target=251408105 –
70918248
References:
negative effect of steroids (https://nucleusgaming.us/fairy-forest-fortune-slots-mystical-wins-await/)
70918248
References:
david laid Steroids [https://redricekitchen.com/canh-ga-xoi/]
70918248
References:
what is the Strongest steroid (https://www.santamarta.gov.co/sala-prensa/noticias/con-el-nuevo-centro-de-salud-de-bastidas-estamos-dignificando-la-prestacion-del?page=5638)
70918248
References:
weight loss Steroid cycle (https://bloggenmeister.com/soziale-medien-integration-so-bringen-sie-ihren-blog-auf-social-media/)
70918248
References:
closest Thing to steroids at gnc – https://sportifyindia.com/new-fitness-club-opening/ –
70918248
References:
None (http://service-multi.ru/news/125-2013-sale-rims/)
70918248
References:
Sell Steroids (https://ara-came.com/hamasuta-hanshin-2020/)
70918248
References:
low Androgenic steroids (https://www.cartergroupland.com/articles/tax-benefits-of-owning-rural-land)
Этот интересный отчет представляет собой сборник полезных фактов, касающихся актуальных тем. Мы проанализируем данные, чтобы вы могли сделать обоснованные выводы. Читайте, чтобы узнать больше о последних трендах и значимых событиях!
Узнать больше – https://vyvod-iz-zapoya-1.ru/
great northern casino
References:
https://paramedical.sureshinternationalcollege.in/tally-erp-9/
australian online casino
References:
https://streetwiseworld.com.ng/2023/04/24/natural-capital-an-option-for-african-governments-to-finance-sustainable-development-goals/
leelanau sands casino
References:
holland casino online (https://www.themirrored.com/comments/reply/18176/)
Aᴡ, this was a rеally gօod post. Sⲣending
some time annd actual effort to generate a great article… but what can I
say… I procrastinate a whole lot and don’t seem to get anything done.
Feel free to ѵisit my webpage: Rafaslot
I am really impressed along with your writing abilіties as
smartly as with the format for your weblog. Is that this a paid topic or did you customіze it your self?
Either way stay up the nice high quiality writing, it’s
гare to peer a great webⅼog liкe this one today..
my blog Rafaslot
symptoms of anabolic steroids
References:
https://dreamtripvegas.com/top-tips-for-first-time-visitors-to-las-vegas/
steroid effects
References:
https://mcm999.fun/the-power-of-effective-communication-in-business/
steroids information
References:
https://paramedical.sureshinternationalcollege.in/advanced-diploma-in-medical-psychology/
steroids are derived from
References:
https://triptalkk.com/this-weeks-top-stories-about-travel-car/
steroids reviews
References:
https://paramedical.sureshinternationalcollege.in/lace-making/
slots of vegas no deposit bonus codes
References:
casino on net [https://shkolnaiapora.ru/question/zameni-slova-ustojchivymi-slovosochetaniyami]
testosterone withdrawal
References:
https://goajobssite.com/companies/genotropin-pfizer-hgh-legal-kaufen-on-line-rezeptfrei/
Das seien deutlich gesündere und natürliche Möglichkeiten, das Somatropin-Level zu steigern, so Weber. Danach nimmt die körpereigene Produktion mit steigendem Alter kontinuierlich ab. Dabei wird oft übersehen, dass HGH – additionally Human Development Hormone – eigentlich ein medizinisch anerkanntes Medikament ist. In synthetischer Form als Somatropin wird es bei Wachstumshormonmangel, etwa im Kindesalter oder bei bestimmten Stoffwechselerkrankungen, verordnet. Aufgrund einer Vielzahl an Studien kann man mittlerweile sagen, dass die regelmäßige Einnahme von L-Arginin, wie z.B.
HCG sollte nach der Rekonstitution immer gekühlt aufbewahrt werden (ungefähr 2 – eight Grad Celsius oder 35,6 – 46,4 Grad Fahrenheit). Aufgrund der zerbrechlichen Natur des Proteinhormons wird das Molekül denaturiert und zerstört, wenn es nach der Rekonstitution bei Raumtemperatur aufbewahrt wird, und das HCG wird unwirksam. Heftiges Schütteln des rekonstituierten HCG zerstört auch das empfindliche Proteinmolekül, und heftiges Schütteln sollte bei der Rekonstitution oder auf andere Weise vermieden werden.
Und diese Effekte nur verbessert, wenn Sie GH in einem anabolen Steroid-Zyklus gehören. Denken Sie an AAS als Normalbenzin, Hinzufügen HGH würde sie in höher schalten, Superkraftstoff. Sie können bessere Resultate von anabolen Steroiden zu bekommen, und weniger von ihnen nur durch den Einbau von HGH.
Das liegt daran, dass die der Körper die eigene Testosteron Produktion reguliert, zurück fährt und sich an die von außen zugeführte Menge gewöhnt. Wenn man diesen Prozess zu lange durchführt kann es passieren, dass der Körper auch Dauerhaft nach absetzen nicht mehr ausreichend Testosteron auf natürliche Art und Weise produzieren kann. Vor allem Männer die genetisch durch einen hohen Testosteron und DHT Spiegel vorbelastet sind können durch zusätzliches verabreichen durch Testosteron schnell zu Haarausfall neigen. Viele professionelle Kraftsportler und Bodybuilder haben mitunter deswegen eine Glatze. Testosteron oder kurz Testo Kuren haben, genauso wie Trenbolon, auch einige Nachteile bzw. Diese sind von Particular Person zu Individual sehr unterschiedlich und treten auch individuell anders auf.
Osteoporose, Fettleibigkeit und Herz-Kreislauf-Erkrankungen werden alle mit unzureichenden HGH-Mengen im Körper in Verbindung gebracht. Allerdings können Nahrungsergänzungsmittel, die Wachstumshormonrezeptorantagonisten oder Sekretagoga enthalten, verwendet werden Steigern Sie den HGH-Spiegel. Die Verwendung eines HGH-Ergänzungsmittels kann jedoch den Alterungsprozess verlangsamen und Ihre Gesundheit und Vitalität steigern.
5.) Multiplizieren Sie die Zahl, die Sie in Schritt four erhalten, mit der Anzahl der Einheiten, die Sie in diesem Second injizieren möchten. Wenn Sie 2 IE HGH entnehmen möchten, ziehen Sie die Markierung 20 auf der Spritze heraus. Um zu wissen, wie die gewünschte Menge für die Injektion gemessen wird, sollten Sie eine U100-Insulinspritze verwenden, um Ihr HGH zu entnehmen und zu injizieren. Die beste Faustregel ist, eine Menge zu wählen, die das Messen des Endprodukts erleichtert. Womit wir uns für die Wiederherstellung entscheiden, sollte davon abhängen, wie schnell wir das GH verwenden. Es wird normalerweise in Einheiten (IU‘s oder IE‘s) geliefert, aber manchmal kann es in Milligramm (mg) erscheinen. Die Verwendung von Insulin ist wichtig, da es die Rezeptorsensitivität gegenüber IGF-1 erhöhen kann.
Dieses Hormon verlangsamt die degenerativen Pathologien, die im Körper jeder Particular Person mit Alter auftreten. Hormone steuern immer bestimmte Vorgänge im Körper und beeinflussen dabei eine ganze Reihe von Systemen. Der Körper produziert es in der Hirnanhangdrüse und schüttet es mehrfach am Tag aus. Darüber hinaus sollten Sie immer versuchen, Original-Clen von einer seriösen Quelle zu bestellen. UPsteroid ist eine großartige Quelle, um authentische Clenbuterol-Produkte zu bestellen.
Hingegen, Dies wird nicht als ein sicheres Medikament von der medizinischen Gemeinschaft noch ist es für Bodybuilding oder Anti-Aging-Nutzung zugelassen. IU (Internationale Einheiten) ist eine Standardmessung zur Menge / Menge, nicht die Kraft. 10 UI’s from a 4mg compound will be weaker than 10 UI’s from a 6mg product.
Die Hypophyse – eine etwa kirschkerngroße Drüse an der Schädelbasis – schüttet dabei unter anderem das Wachstumshormon HGH aus. Das Wachstumshormon besteht aus 191 Aminosäuren und zirkuliert über die Blutbahn durch den Körper. Der große Unterschied zwischen Steroiden und HGH liegt bei den Nebenwirkungen. Wie Du gelesen hast, sind die Effekte des Wachstumshormons auf Funktionen des Körpers sehr vielfältig. Wer wünscht sich keine stärkeren Knochen, mehr Muskelmasse, weniger Fett und ein stärkeres Immunsystem? Das wirft jetzt additionally die Frage auf, wie wir den Wachstumshormon Spiegel im Körper anheben können. Unser zentrales Nervensystem besteht aus dem Gehirn und dem Rückenmark.
Die mitunter häufigste Nebenwirkungen bei anabolen Steroiden aller Artwork ist die unreine Haut. Diese beginnt meist mit leichten Pickeln kann aber teilweise zu Akne fortschreiten. Die meisten Unreinheiten treten auf der Brust, oberen Rücken und im Schulterbereich aber auch Gesicht auf. Durch das Training und den Schweiß können sich diese Unreinheiten entzünden und zu unangenehmen Schmerzen kommen.
References:
https://gtcs.co.in/employer/hgh-36-ie-somatropin-kaufen-preis-579-euro-in-deutschland-dosierung-und-kurs/
Peptides are composed of amino acid chains and regulate a variety of organic features. Peptides sign and set off the body’s molecules and cells to perform particular healing tasks very important to our well being and well-being. Suppose of peptides as your cellular “general” who gives the troops their marching orders! To date, about 7,000 naturally occurring peptides have been identified. Our Dallas Peptide remedy is an ever-evolving, cutting-edge, personalized therapy routine supplied to patients at ThriveMD.
The specificity of peptide signaling is finely tuned by receptor-ligand binding and intracellular pathways. Peptide remedy is a strong and versatile therapy option that may tackle numerous health points, improve bodily performance, and promote total well-being. By understanding the various varieties of peptides and their benefits, you can make knowledgeable choices about incorporating peptide remedy into your health regimen. Certain peptides can enhance the body’s metabolism and promote fats loss. This could be an efficient assist for individuals battling weight problems or those looking to shed extra weight. Morph Wellness MD presents physician-led consultations to gauge your needs and develop an appropriate remedy plan.
These are the real-world returns that a well-designed peptide protocol is meant to deliver. Simply as a end result of insurance coverage doubtless will not foot the invoice doesn’t mean you are out of options. Many people find sensible methods to make use of pre-tax accounts to make their remedy far more affordable. These are powerful tools designed particularly for qualified medical bills. If a particular peptide has obtained FDA approval for a selected medical situation and you have got that official prognosis, coverage turns into a real chance.
For many people, this is the most empowering a part of the whole course of. To get a better feel for it, you’ll be able to study more about what to expect from an internet physician consultation and tips on how to come ready. As A Outcome Of it encourages your physique to do the work itself, the outcomes are often more gradual and in tune along with your pure rhythm. This strategy helps you keep away from the sharp peaks and valleys that can sometimes come with direct hormone substitute. In the same way, you wouldn’t use a peptide recognized for pores and skin rejuvenation to construct muscle.
We thank all the patients who participated on this examine, their supporting households and all the referring physicians and the supporting medical workers at all the medical websites. We also thank Masami Ueda (Tokyo Midtown Center for Superior Medical Science and Technology) for making ready the WT1-DC vaccine. As a hospital clinician for over five years, John handled a mean of 30 patients per day and has seen first-hand how our fashionable illnesses are a direct result of the American diet.
BPC-157 improves intestine well being by repairing the digestive tract and selling a wholesome intestinal epithelium, leading to more practical weight reduction and better overall health. BPC-157 is a synthetic peptide that is derived from a pure protein discovered in the gastric juices of our abdomen. Its distinctive construction and origin contribute to its distinctive healing properties and have garnered important consideration within the medical community. All research peptides offered by Limitless Biotech are manufactured within the United States. The manufacturing groups dedicate cautious consideration to ensuring the peptides are devoid of contaminants and impurities. Adherence to the newest Good Manufacturing Practices is a precedence, with thorough sanitization processes built-in at every stage of production.
Our MD’s, PA’s, and NP’s immediately prescribe all required tests and review and confirm all check outcomes. We may carry out physical exams, consult with main physicians, and validate and verify submitted medical data. BiocoreHealthRX reserves the right to advocate and use inner and/or exterior medical specialists for any patient.
Having a natural approach to heal your shoulder is certainly the avenue I needed to take. After 3 weeks, I started to note the range of movement in my shoulder improved by 75%; ache was lowered by 50%. We provide digital consultations, and many of our therapies can be shipped directly to your door.
Peptide therapy entails the usage of specific peptides to set off specific responses within the physique, aiming to deal with well being points or improve physiological features. Peptides are pure compounds that sign cells to spice up immune perform, enhance muscle mass, and enhance cognition. Choose Well Being provides personalised peptide treatments for weight administration, improved sexual operate, and anti-aging as a half of our health optimization programs.
References:
https://www.valley.md/peptide-therapy-near-me
You actually reported that really well!
References:
http://historydb.date/index.php?title=mcintoshcrockett9023
what to take with dianabol cycle
References:
dianabol anavar cycle (https://noticias-sociales.space/item/404741)
jintropin hgh
References:
https://brandmoshaver.com/user/pilotclaus6/
Most importantly – and we can’t stress this enough – despite the fact that you would possibly see it on the market, that doesn’t mean it’s accredited or regulated for human use. For example, should you weigh 200 pounds (about ninety one kg), some people report utilizing between 1 and a couple of milligrams (that’s 10 to 20 micrograms per kilogram). When researchers make these blends, they usually mix them in several ratios—sometimes equal quantities of every, generally as a lot as five times extra TB-500 than BPC-157.
You can find many of these clinically validated components in Swolverine’s recovery stack lineup. For common restoration or post-cycle assist, SubQ is probably the most handy and well-tolerated possibility. Many customers turn to BPC-157 as part of their restoration protocol after steroid cycles, or after heavy training loads. BPC-157 has been extensively studied for its gastroprotective properties, making it a novel option for treating ulcers, IBS, leaky intestine, and even Crohn’s disease. If you’re new to BPC-157, you may additionally want to try our final cycle information or complete peptide overview earlier than getting started. Therefore, for a typical dosage of 500 mcg of BPC-157 out of your ready answer, you’ll draw as much as the 20-unit mark on a zero.5 mL, 50-unit insulin syringe.
BPC-157 consists of 15 amino acids isolated from human gastric juice. That’s why BPC-157 is 100 percent pure and offers varied consistent and well-tolerated benefits to the human physique. When shopping for https://www.valley.md/bpc-157-injections-benefits-side-effects-dosage-where-to-buy for research you have to select a trusted supplier. Loti Labs stands out for its commitment to quality and testing, making it a dependable companion for your lab. Authentic and protected reagents are crucial for legitimate and reproducible research especially in managed environments. Loti Labs supplies BPC 157 capsules particularly designed for research use along with a full catalog of Tamoxifen Citrate and different compounds.
By supporting general health and restoration, BPC-157 may assist individuals preserve a bodily way of life conducive to fats loss. In exploring whether BPC-157 can be successfully used for fats burning, it’s necessary to first perceive its main advantages. BPC-157, a peptide known for selling digestive health, brings several indirect benefits that can aid in weight administration. In abstract, while BPC-157 doesn’t increase the precise amount of progress hormone, it optimizes the physique’s ability to put it to use for healing and restoration. One of the methods during which BPC 157 helps to enhance our regeneration is by interacting with the body’s manufacturing of nitric oxide, a compound which the body produces. Boosting nitric oxide helps increase the blood vessels within the physique, making it easier for oxygen, blood, and vitamins to succeed in important areas within the body. Initially in style for its capability to safeguard the digestive system, BPC-157 quickly rose to fame for its versatility.
Without clinical information, it is challenging to establish the potential short-term or long-term antagonistic effects of BPC-157. Thus, for a focus of 1mg/mL, which is often used for ease of calculation, researchers can mix 5mg of BPC-157 with 5mL of bacteriostatic water. This permits for simple dosing where zero.25mL of the solution accommodates 250mcg of BPC-157. It’s crucial to avoid agitating the vial, whether by shaking or tapping.
This remarkable peptide has captured the curiosity of the medical group due to its promising therapeutic properties. Analysis has indicated that BPC 157 promotes collagen manufacturing, which is significant for wound recovery and tissue regeneration. What are the potential benefits of utilizing BPC-157 in cancer prevention and treatment? Apart from its therapeutic properties, BPC-157 can help forestall most cancers by boosting the body’s immune system, thus making it more resilient against the development and spread of cancer cells. It also can scale back the prevalence of most cancers in individuals with a family history of the disease, making it an essential addition to their well being routine. It seems to have a neutral or minimal impact on blood sugar when used at acceptable doses.
To calculate a comparable dosage to use in medical settings, researchers may check with the dose conversion guidelines established by Nair et al. (2016). Researchers have demonstrated its potential to scale back inflammation, pace up wound healing, and hasten recovery from varied accidents. For example, FlexMax from RegenLabs provides a joint-health complement containing BPC-157 together with Epicatechin to cease muscle breakdown. This makes it simpler for individuals to include the advantages of BPC-157 into their routine with out requiring injections. Check out the fullingredient record and product particulars for extra data on the means it works.
Examine out a peptide dose calculator for simplifying your dosage calculations. Its capability to stimulate growth hormone release not only aids in muscle growth and repair but in addition accelerates wound healing. Studies have shown that BPC-157’s role in tissue restore extends to numerous organs, together with the gastrointestinal tract, muscular tissues, ligaments, and pores and skin. Its capability to reinforce collagen production contributes to improved joint well being and overall musculoskeletal well-being.
dianabol only cycle results
References:
Dianabol Only Cycle For Beginners; https://en.unidos.edu.uy/profile/silveryxlmeyer431/profile,
is hgh testosterone
References:
hgh timing bodybuilding – https://flubber.pro/judi09b2395601 –
how long does it take to get big on steroids
References:
branch warren steroids (http://gitlab.dev.jtyjy.com/jessika738154)
Getting it correct, like a altruistic would should
So, how does Tencent’s AI benchmark work? Prime, an AI is allowed a sharp-witted job from a catalogue of greater than 1,800 challenges, from order wrench visualisations and царствование безграничных потенциалов apps to making interactive mini-games.
In a wink the AI generates the rules, ArtifactsBench gets to work. It automatically builds and runs the jus gentium ‘mutual law’ in a sheltered and sandboxed environment.
To forewarn how the assiduity behaves, it captures a series of screenshots ended time. This allows it to jurisdiction against things like animations, stage changes after a button click, and other hot consumer feedback.
Conclusively, it hands terminated all this take in view – the immanent аск on account of, the AI’s encrypt, and the screenshots – to a Multimodal LLM (MLLM), to feigning as a judge.
This MLLM adjudicate isn’t no more than giving a lead into the open тезис and as a substitute for uses a particularized, per-task checklist to armies the impact across ten refurbish steep metrics. Scoring includes functionality, holder business, and steady aesthetic quality. This ensures the scoring is reliable, in concurrence, and thorough.
The hefty occupation is, does this automated upon as a result caricature ownership of allowable taste? The results referral it does.
When the rankings from ArtifactsBench were compared to WebDev Arena, the gold-standard meeting set-up where legitimate humans тезис on the most fitting AI creations, they matched up with a 94.4% consistency. This is a herculean flourish from older automated benchmarks, which on the in competition to managed ’round 69.4% consistency.
On extreme of this, the framework’s judgments showed in de trop of 90% unanimity with all considerate perchance manlike developers.
https://www.artificialintelligence-news.com/
what are the risks of anabolic steroids
References:
Legal steroids for Muscle building (https://wgbteam.ru/user/greaseepoch3/)
вывод из запоя круглосуточно краснодар
narkolog-krasnodar011.ru
вывод из запоя круглосуточно
вывод из запоя круглосуточно
narkolog-krasnodar011.ru
экстренный вывод из запоя краснодар
вывод из запоя круглосуточно краснодар
narkolog-krasnodar012.ru
вывод из запоя краснодар
вывод из запоя краснодар
narkolog-krasnodar013.ru
экстренный вывод из запоя
Вызов нарколога на дом круглосуточно стал необходимой услугой для тех‚ кто сталкивается с зависимостями. На сайте vivod-iz-zapoya-krasnoyarsk012.ru можно узнать всю важную информацию о методах лечения зависимостей‚ включая медикаментозное лечение и психотерапевтические методы лечения зависимостей. Консультация нарколога поможет выявить уровень зависимости и определить подходящий план лечения. Круглосуточное обслуживание позволяет вызвать специалиста на дом в любое время‚ что особенно важно для экстренных случаев. Услуги нарколога включают диагностику зависимостей‚ анонимное лечение и поддержку родственников. Реабилитация людей с зависимостями требует целостного подхода‚ и квалифицированная помощь может значительно облегчить этот путь. Профилактические меры против зависимостей также является важным аспектом в борьбе с ними‚ поэтому важно обращаться за помощью при первых признаках. Приезд врача на дом создает комфортные условия и гарантирует конфиденциальность‚ способствуя эффективному лечению.
лечение запоя краснодар
narkolog-krasnodar013.ru
экстренный вывод из запоя краснодар
вывод из запоя цена
narkolog-krasnodar014.ru
лечение запоя
лечение запоя
narkolog-krasnodar015.ru
вывод из запоя краснодар
вывод из запоя круглосуточно смоленск
vivod-iz-zapoya-smolensk014.ru
лечение запоя смоленск
Экстренная помощь нарколога в Туле предоставляет профессиональное лечение запоя. Центр наркологии предлагает помощь в случае запоя и программы по лечению алкоголизма, включая медикаментозное лечение запоя с помощью специальных препаратов и очищения организма. Важно обратиться за консультацией нарколога для получения первичной помощи при запое. Программы лечебные программы включают психотерапию зависимости и психологическую помощьчто содействует улучшению здоровья и социальной реабилитации. Лечение с гарантией анонимности гарантирует защиту личных данных, что имеет большое значение для обращающихся.
вывод из запоя круглосуточно краснодар
narkolog-krasnodar015.ru
вывод из запоя цена
Помощь наркологов доступна круглосуточно на ресурсе narkolog-tula015.ru. Лечение наркомании требует квалифицированного подхода‚ и наша команда готова предоставить консультацию нарколога в любое время. Мы поддерживаем зависимым‚ обеспечивая конфиденциальное лечение и реабилитационный центр для восстановления после зависимости. Наша detox программа включает психотерапевтическую помощь и медицинскую помощь при алкоголизме. Мы также обеспечиваем профилактику рецидивов через персонализированное лечение и кризисную интервенцию. Не ждите‚ свяжитесь с нами уже сегодня!
Капельница для восстановления после алкогольного отравления – это работающим средством для восстановления организма после употребления алкоголя. В Красноярске медицинские услуги включающие внутривенное введение глюкозы и электролитов дают возможность снять проявления похмелья, включая головная боль, тошнота и слабость. Клиники в Красноярске предоставляют услуги с использованием энтеросгеля с целью детоксикации. Восстановление водного баланса также играет важную роль в процессе восстановления. Не забывайте о необходимости консультации врача перед началом лечения. Для получения дополнительной информации посетите сайт vivod-iz-zapoya-krasnoyarsk010.ru.
Подбор клиники для вывода из запоя в Туле – важный шаг‚ который необходимо тщательно обдумать к нескольким аспектам‚ включая стоимость услуг и качество медицинской помощи. При выборе клиники следует учитывать следующие моменты. Во-первых‚ ознакомьтесь с наркологическими услугами‚ которые имеет учреждение. Многие частные клиники Тулы представляют квалифицированных профессиональных наркологов‚ которые могут обеспечить экстренную помощь на дому. Это особенно актуально‚ если состояние пациента требует немедленного вмешательства.Во-вторых‚ ознакомьтесь с отзывами о клиниках Тулы. Это поможет понять‚ как другие пациенты отметили качество оказанной помощи и результат лечения. Не забудьте узнать о стоимости вывода из запоя – цены могут варьироваться в зависимости от уровня сервиса и используемых терапий. Также стоит рассмотреть варианты реабилитации и другие предложения‚ такие как терапия алкогольной зависимости. Некоторые клиники используют интегрированные методы‚ что может быть более эффективным. Важно помнить‚ что низкие цены на лечение не всегда являются показателем высокого качества. При выборе медицинского учреждения‚ ищите оптимальное соотношение цены и качества при лечении алкоголизма. Не стесняйтесь информировать себя о подходах к терапии и возможностях‚ которые предлагает клиника. нарколог на дом срочно
Эффективные рецепты против алкогольной зависимости могут стать полезным дополнением к медицинской помощи в Красноярске. Лечение алкогольной зависимости требует всеобъемлющего подхода‚ включая очищение организма и психотерапию при алкоголизме.Травы от алкоголизма‚ такие как лекарственные растения‚ могут помочь в снижении тяги к алкоголю. Важно помнить о поддержке близких и анонимном лечении. Методы борьбы с зависимостью включают реабилитационные программы и профилактику запойного состояния. Рекомендации по отказу от спиртного также играют значительную роль в восстановлении после зависимости. помощь нарколога Красноярск
Похмелье – это неприятное состояние, которое возникает вследствие избыточного употребления спиртных напитков. Симптомы включают головной болью, тошнотой и сухостью во рту. Для ускорения состояния можно использовать капельницу, которая поставляет организм флюидами и электролитами. На сайте narkolog-tula016.ru можно найти полезные советы о домашних средствах для лечения похмелья, включая инфузионную терапию. Капельница наполняется глюкозой, витаминами и необходимыми минералами, что помогает очищению организма. Важно помнить, что при сильном похмелье следует попросить за медицинской помощью и получить врачом.Правильно подобранные компоненты в капельнице помогут быстро восстановить здоровье и вернуть энергию.
Капельница от запоя на дому — является удобный и эффективный метод помощи в случае алкогольного отравления. В отличие от стационарного лечение в стационаре, лечение запоя на дому предоставляет возможность пациенту оставаться в привычной обстановке, что уменьшает стресс и способствует быстрому восстановлению.Врач нарколог на дом Тула предлагает профессиональную помощь нарколога, выполняя процедуры по детоксикации и прекращению запойного состояния. Капельницы помогают ускоренному устранению симптомов запойного состояния, улучшая общее состояние пациента; Кроме того они обеспечивают необходимую гидратацию и восполнение витаминов. Домовая детоксикация подходит тем, кто не может или не желает проходить лечение в стационаре. Однако, в случае серьезных осложнений требуется более интенсивное лечение. Нарколог на дом поможет организовать реабилитацию пациентов, включая психотерапевтические сеансы при зависимости, что существенно увеличивает вероятность успешного выздоровления после запойного состояния.
Круглосуточная капельница от запоя на дому в Красноярске – это эффективный способ для тех, кто переживает с трудностями алкогольной зависимости. Вызвать нарколога на дом можно в любое время. Услуги нарколога 24/7 включают в себя неотложную помощь, детоксикацию алкоголя, а также восстановление после запоя. При необходимости вызова врача на дом, достаточно позвонить со специализированной службой. Капельницы для детоксикации от алкоголя помогут быстро восстановить здоровье пациента, восстановить баланс воды и электролитов и облегчить симптомы абстиненции. Медицинская помощь в Красноярске предоставляется опытными врачами. Консультация нарколога перед началом лечения поможет определить дальнейшие шаги, включая реабилитацию от запоя. Помощь при алкогольной зависимости требует профессионального подхода и сопровождения. Наркология на дому обеспечивает комфорт и анонимность, что особенно важно для людей, нуждающихся в помощи.
Вызов нарколога — это важный шаг для тех, кто сталкивается с трудностями с зависимостями . Наркологическая служба предоставляет экстренную наркологическую помощь и консультацию нарколога, что крайне важно в кризисных ситуациях . Признаки зависимости от наркотиков могут проявляться по-разному , и важно знать, когда необходима медицинская помощь при алкоголизме . Лечение алкоголизма и помощь при наркотической зависимости требуют квалифицированного вмешательства. Последствия алкоголизма могут быть разрушительными , поэтому важно искать помощь для людей с зависимостями, включая программы реабилитации. На сайте narkolog-tula017.ru вы можете найти информацию о том, как вызвать нарколога или получить конфиденциальную помощь для наркозависимых. Не сомневайтесь в том, чтобы позвонить в наркологическую службу, чтобы получить необходимую поддержку и помощь .
Выездной нарколог в Туле — это практичное решение для людей‚ которые испытывают необходимость в наркологической помощи‚ но не могут посетить лечебное заведение. Профессиональная помощь в лечении зависимости доступна прямо на дому‚ что гарантирует удобство и конфиденциальность.Обращение к наркологу позволяет оценить ситуацию и подобрать лучший план лечения‚ включая стационарное лечение или выезд на дом. Специалисты предлагают психологическую помощь при зависимостях и медицинское вмешательство‚ что способствует успешному лечению зависимостей. Поддержка семьи играет важную роль в процессе‚ помогая пациентам справиться с трудностями. Обратитесь на narkolog-tula019.ru для подробной информации о предоставляемых услугах.
вывод из запоя
vivod-iz-zapoya-smolensk013.ru
экстренный вывод из запоя
Капельница для лечения запоя — это важный этап в лечении алкогольной зависимости. Капельница помогает очищению организма‚ устраняя токсины и восстанавливая баланс жидкости и электролитов. После ее применения пациенты часто отмечают положительные изменения в психоэмоциональном состоянии.Консультация нарколога в этом процессе играет важную роль. Он анализирует симптомов отмены и предлагает необходимое лечение запоя. Постзапойное восстановление включает физическую и психологическую реабилитацию. Помощь родных играет ключевую роль‚ поддерживая в преодолении последствий запойного состояния. помощь нарколога Реабилитация является следующим шагом в лечении‚ где пациент проходит лечение и обучение для предотвращения рецидивов. Конфиденциальная помощь предоставляет анонимность и защиту. Важно помнить‚ что борьба с алкоголизмом — это длительный процесс‚ требующий усилий и поддержки.
Капельница от запоя: экстренная помощь при алкогольном отравлении Инфузионная терапия содержит необходимые препараты для нормализации водно-электролитного состояния и поддержки здоровья пациента. Эффективная терапия зависимости включает в себя не только детоксикацию, но и долгосрочную терапию алкоголизма. Необходимо учитывать процесс восстановления после запоя, который может занять время и потребовать дополнительных усилий. вывод из запоя круглосуточно Экстренная помощь включает в себя диагностику состояния и индивидуальный подход к каждому пациенту. При выявлении симптомов алкогольного отравления необходимо немедленно обратиться к специалистам. Не забывайте, что здоровье является наивысшей ценностью, и квалифицированная помощь в наркологическом учреждении поможет вернуть контроль над своей жизнью.
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk014.ru
вывод из запоя цена
Вызов нарколога на дом в экстренных случаях — это необходимая помощь для тех, кто сталкивается с зависимостями. На сайте narkolog-tula019.ru вы можете получить консультацию нарколога и вызвать врача для домашнего визита. Квалифицированная помощь нарколога включает в себя лечение различных зависимостей и психологическую поддержку. Медицинская экстренная служба предлагает конфиденциальные услуги, что позволяет сохранить конфиденциальность. Эффективное лечение наркомании и помощь алкоголикам возможны с помощью психотерапевта на дому. Не откладывайте, обратитесь за срочной помощью!
вывод из запоя круглосуточно смоленск
vivod-iz-zapoya-smolensk015.ru
экстренный вывод из запоя
пансионат для лежачих больных
pansionat-msk007.ru
дом престарелых в москве
Капельницы от алкоголя на дому — это эффективный способ лечения алкогольной зависимости, что позволяет оперативно устранить симптомы абстиненции и повысить самочувствие пациента. Услуги нарколога на дому всё чаще востребованы, так как многие предпочитают избегать стационарного лечения. narkolog-tula020.ru Эта процедура предполагает домашнюю детоксикацию, в которой медицинская помощь при алкоголизме предоставляется в комфортной обстановке. Капельница для снятия похмелья включает препараты для детоксикации, которые помогают выведению токсинов из организма и нормализовать водно-электролитный баланс. Важно помнить о признаках абстинентного синдрома, включающих тревога, потливость и тремор. Забота и поддержка со стороны близких играет ключевую роль в эффективном лечении и восстановлении после длительного употребления алкоголя. Лечение на дому может включать не только прокапывание, но и рекомендации по профилактике алкогольной зависимости, что содействует предотвращению повторных срывов и поддержанию трезвого образа жизни.
пансионаты для инвалидов в москве
pansionat-msk008.ru
пансионат с медицинским уходом
Капельница – это важная процедура, которая помогает быстрому восстановлению физического состояния человека, переживающего алкогольную зависимость. В Туле обращение к наркологу для проведения этой процедуры становится всё более актуальным. Употребление алкоголя негативно влияет на организм, вызывая симптомам похмелья, такими как головная боль, тошнота и слабость.Лечение алкоголизма включает detox, который помогает очищению организма от токсинов. Капельница обеспечивает поступление жизненно важных веществ, улучшая состояние пациента. Нарколог предоставляет профессиональную поддержку при запое, что способствует избежать серьезных осложнений. вызов нарколога тула Реабилитация организма после запоя нуждается в комплексном подходе, включая восстановление от алкоголя. Лечение запоя может включать как медикаментозные методы, так и психотерапевтическую помощь. Важно помнить, что здоровье – это наиболее важное, и оперативная помощь нарколога может оказаться решающей.
пансионат для пожилых людей
pansionat-msk009.ru
пансионат для пожилых с деменцией
пансионат с медицинским уходом
pansionat-msk007.ru
пансионат инсульт реабилитация
частные пансионаты для пожилых в туле
pansionat-tula007.ru
пансионат после инсульта
подключить проводной интернет екатеринбург
inernetvkvartiru-ekaterinburg004.ru
дешевый интернет екатеринбург
пансионат для лежачих москва
pansionat-msk008.ru
дом престарелых в москве
пансионат для пожилых с инсультом
pansionat-tula008.ru
пансионат для лежачих тула
подключение интернета екатеринбург
inernetvkvartiru-ekaterinburg005.ru
подключить домашний интернет екатеринбург
пансионат после инсульта
pansionat-tula009.ru
частный пансионат для престарелых
пансионат для пожилых людей
pansionat-msk009.ru
пансионат для пожилых в москве
какие провайдеры интернета есть по адресу екатеринбург
inernetvkvartiru-ekaterinburg006.ru
узнать провайдера по адресу екатеринбург
провайдеры по адресу дома
inernetvkvartiru-krasnoyarsk004.ru
подключить интернет по адресу
вызов психиатра на дом в москве
psychiatr-moskva005.ru
психиатрическая помощь больным
пансионат для людей с деменцией в туле
pansionat-tula008.ru
пансионат для престарелых людей
интернет провайдеры по адресу
inernetvkvartiru-krasnoyarsk005.ru
провайдер по адресу
частный дом престарелых
pansionat-tula009.ru
пансионат для реабилитации после инсульта
психиатрическая клиника
psikhiatr-moskva004.ru
стационар психиатрической больницы
стационар психиатрической больницы
psychiatr-moskva004.ru
частный психиатрический стационар
интернет провайдеры по адресу дома
inernetvkvartiru-krasnodar004.ru
интернет по адресу
вызвать психиатра на дом для пожилого
psikhiatr-moskva005.ru
оказание психиатрической помощи
вызвать психиатра на дом для пожилого
psychiatr-moskva005.ru
консультация психиатра круглосуточно
интернет по адресу дома
inernetvkvartiru-krasnodar005.ru
провайдеры в краснодаре по адресу проверить
скорая психиатрическая помощь
psikhiatr-moskva006.ru
нужна консультация психиатра
проверить провайдера по адресу
inernetvkvartiru-krasnodar006.ru
провайдеры интернета по адресу краснодар
психиатрическую помощь в стационарных условиях
psychiatr-moskva006.ru
лучшие психиатрические клиники
реабилитация алкоголиков в Астане
reabilitaciya-astana004.ru
анонимное лечение от алкоголизма
подключить домашний интернет москва
inernetvkvartiru-msk004.ru
подключить интернет тарифы москва
консультация частного психиатра
psikhiatr-moskva004.ru
лучшие психиатрические клиники
лечение и реабилитация алкоголизма в Астане
reabilitaciya-astana005.ru
анонимное лечение алкоголиков
принудительное лечение в психиатрической больнице
psikhiatr-moskva005.ru
платная консультация психиатра
реабилитация от наркозависимости
reabilitaciya-astana006.ru
реабилитация наркозависимых наркология в Астане
провайдеры интернета по адресу
inernetvkvartiru-msk006.ru
узнать интернет по адресу
психиатр на дом
psikhiatr-moskva006.ru
психиатрический стационар
вывод из запоя
tula-narkolog004.ru
лечение запоя
провайдеры интернета в нижнем новгороде по адресу проверить
inernetvkvartiru-nizhnij-novgorod004.ru
подключить домашний интернет нижний новгород
реабилитация зависимых от алкоголя в Астане
reabilitaciya-astana004.ru
стоимость лечения наркомании
tirzepatide & cjc 1295/ipamorelin
References:
ipamorelin en ligne (https://xn--80aaaokoti9eh.xn--p1ai/user/goatsmoke1/)
вывод из запоя круглосуточно
tula-narkolog005.ru
вывод из запоя
подключить проводной интернет нижний новгород
inernetvkvartiru-nizhnij-novgorod005.ru
какие провайдеры на адресе в нижнем новгороде
помощь при алкоголизме
reabilitaciya-astana005.ru
центр реабилитация алкоголиков в Астане
экстренный вывод из запоя
tula-narkolog006.ru
вывод из запоя тула
провайдер по адресу
inernetvkvartiru-nizhnij-novgorod006.ru
интернет провайдеры по адресу
экстренный вывод из запоя
vivod-iz-zapoya-chelyabinsk007.ru
вывод из запоя челябинск
реабилитация алкоголиков цены в Астане
reabilitaciya-astana006.ru
лечение алкозависимости
лучший интернет провайдер новосибирск
inernetvkvartiru-novosibirsk004.ru
какие провайдеры интернета есть по адресу новосибирск
вывод из запоя челябинск
vivod-iz-zapoya-chelyabinsk008.ru
экстренный вывод из запоя челябинск
лечение запоя
tula-narkolog004.ru
вывод из запоя цена
интернет провайдеры по адресу новосибирск
inernetvkvartiru-novosibirsk005.ru
интернет по адресу
лечение запоя
vivod-iz-zapoya-chelyabinsk009.ru
вывод из запоя
вывод из запоя круглосуточно череповец
vivod-iz-zapoya-cherepovec010.ru
экстренный вывод из запоя
провайдеры интернета по адресу
inernetvkvartiru-novosibirsk006.ru
подключить проводной интернет новосибирск
экстренный вывод из запоя тула
tula-narkolog006.ru
лечение запоя тула
подключение интернета ростов
inernetvkvartiru-rostov004.ru
интернет провайдер ростов
лечение запоя
vivod-iz-zapoya-chelyabinsk007.ru
вывод из запоя челябинск
лечение запоя
vivod-iz-zapoya-cherepovec012.ru
вывод из запоя
домашний интернет тарифы
inernetvkvartiru-rostov005.ru
домашний интернет ростов
how many units of ipamorelin should i take
References:
ipamorelin/cjc-1295 therapy orlando; https://www.sbnation.com/users/valentine.hwa,
вывод из запоя цена
vivod-iz-zapoya-chelyabinsk008.ru
вывод из запоя круглосуточно
экстренный вывод из запоя
vivod-iz-zapoya-irkutsk007.ru
вывод из запоя круглосуточно иркутск
дешевый интернет ростов
inernetvkvartiru-rostov006.ru
домашний интернет подключить ростов
экстренный вывод из запоя
vivod-iz-zapoya-chelyabinsk009.ru
вывод из запоя круглосуточно челябинск
dose ipamorelin igf 1 lr3 grf 129 dosage
References:
https://jobinaus.com.au/companies/cjc-1295-and-ipamorelin-benefits-risks-and-synergistic-effects/
дешевый интернет санкт-петербург
inernetvkvartiru-spb004.ru
интернет по адресу дома
вывод из запоя цена
vivod-iz-zapoya-irkutsk009.ru
вывод из запоя цена
экстренный вывод из запоя
vivod-iz-zapoya-cherepovec010.ru
вывод из запоя
интернет по адресу дома
inernetvkvartiru-spb005.ru
интернет по адресу санкт-петербург
вывод из запоя круглосуточно калуга
vivod-iz-zapoya-kaluga010.ru
вывод из запоя круглосуточно калуга
вывод из запоя круглосуточно череповец
vivod-iz-zapoya-cherepovec011.ru
вывод из запоя череповец
вывод из запоя круглосуточно калуга
vivod-iz-zapoya-kaluga011.ru
вывод из запоя круглосуточно калуга
интернет провайдеры по адресу
inernetvkvartiru-spb006.ru
дешевый интернет санкт-петербург
экстренный вывод из запоя
vivod-iz-zapoya-cherepovec012.ru
вывод из запоя череповец
лечение запоя
vivod-iz-zapoya-kaluga012.ru
экстренный вывод из запоя
проверить провайдеров по адресу екатеринбург
inernetvkvartiru-ekaterinburg004.ru
провайдеры в екатеринбурге по адресу проверить
лечение запоя иркутск
vivod-iz-zapoya-irkutsk007.ru
вывод из запоя круглосуточно
провайдеры интернета в екатеринбурге по адресу
inernetvkvartiru-ekaterinburg005.ru
провайдер интернета по адресу екатеринбург
экстренный вывод из запоя иркутск
vivod-iz-zapoya-irkutsk008.ru
вывод из запоя иркутск
вывод из запоя круглосуточно
vivod-iz-zapoya-krasnodar012.ru
вывод из запоя цена
провайдер интернета по адресу екатеринбург
inernetvkvartiru-ekaterinburg006.ru
подключить интернет екатеринбург
лечение запоя иркутск
vivod-iz-zapoya-irkutsk009.ru
вывод из запоя цена
экстренный вывод из запоя
vivod-iz-zapoya-krasnodar013.ru
вывод из запоя круглосуточно краснодар
узнать провайдера по адресу красноярск
inernetvkvartiru-krasnoyarsk004.ru
какие провайдеры по адресу
экстренный вывод из запоя калуга
vivod-iz-zapoya-kaluga010.ru
вывод из запоя круглосуточно калуга
интернет по адресу
inernetvkvartiru-krasnoyarsk005.ru
проверить провайдеров по адресу красноярск
лечение запоя
vivod-iz-zapoya-kaluga011.ru
экстренный вывод из запоя
провайдер интернета по адресу красноярск
inernetvkvartiru-krasnoyarsk006.ru
провайдеры по адресу красноярск
экстренный вывод из запоя минск
vivod-iz-zapoya-minsk007.ru
вывод из запоя круглосуточно минск
вывод из запоя
vivod-iz-zapoya-kaluga012.ru
вывод из запоя круглосуточно калуга
проверить провайдера по адресу
inernetvkvartiru-krasnodar004.ru
провайдеры по адресу краснодар
вывод из запоя круглосуточно
vivod-iz-zapoya-minsk008.ru
вывод из запоя цена
вывод из запоя краснодар
vivod-iz-zapoya-krasnodar011.ru
экстренный вывод из запоя
вывод из запоя минск
vivod-iz-zapoya-minsk009.ru
вывод из запоя минск
провайдеры интернета в краснодаре по адресу проверить
inernetvkvartiru-krasnodar005.ru
интернет по адресу дома
лечение запоя
vivod-iz-zapoya-krasnodar012.ru
вывод из запоя круглосуточно краснодар
ipamorelin and weight gani
References:
https://wadhefa.site/companies/cjc-1295-ipamorelin-stack-the-synergistic-peptide-combo/?-ipamorelin-stack%3A-the-synergistic-peptide-combo%2F
ipamorelin vente en ligne
References:
cjc 1295 ipamorelin cycle length [https://creator.chaakri.com/employer/cjc1295-ipamorelin-ghrp-2-dosage/]
экстренный вывод из запоя
vivod-iz-zapoya-omsk007.ru
экстренный вывод из запоя
интернет провайдеры краснодар по адресу
inernetvkvartiru-krasnodar006.ru
интернет провайдеры по адресу дома
вывод из запоя
vivod-iz-zapoya-krasnodar013.ru
лечение запоя краснодар
cjc-1295 ipamorelin fertility
References:
does ipamorelin increase libido; https://helx-artifacts-git.apps.renci.org/declanm0178942,
вывод из запоя круглосуточно омск
vivod-iz-zapoya-omsk008.ru
лечение запоя
cjc-1295 ipamorelin cost per month
References:
http://med-koll-vahdat.tj/user/colonswiss76/
вывод из запоя цена
vivod-iz-zapoya-krasnodar014.ru
вывод из запоя круглосуточно краснодар
проверить провайдеров по адресу москва
inernetvkvartiru-msk004.ru
интернет по адресу дома
лечение запоя
vivod-iz-zapoya-omsk009.ru
лечение запоя омск
вывод из запоя круглосуточно
vivod-iz-zapoya-krasnodar015.ru
вывод из запоя
интернет провайдеры москва по адресу
inernetvkvartiru-msk005.ru
провайдеры интернета москва
лечение запоя
vivod-iz-zapoya-orenburg007.ru
лечение запоя
https://ege-na-5.ru/
лечение запоя
vivod-iz-zapoya-minsk007.ru
лечение запоя
https://peterburg2.ru/
дешевый интернет москва
inernetvkvartiru-msk006.ru
недорогой интернет москва
вывод из запоя цена
vivod-iz-zapoya-orenburg008.ru
вывод из запоя
вывод из запоя
vivod-iz-zapoya-minsk008.ru
лечение запоя минск
подключить интернет в квартиру нижний новгород
inernetvkvartiru-nizhnij-novgorod004.ru
подключить домашний интернет нижний новгород
экстренный вывод из запоя
vivod-iz-zapoya-orenburg009.ru
лечение запоя
экстренный вывод из запоя минск
vivod-iz-zapoya-minsk009.ru
вывод из запоя
провайдеры по адресу нижний новгород
inernetvkvartiru-nizhnij-novgorod005.ru
подключить проводной интернет нижний новгород
Неотложная наркологическая помощь — это существенная часть в поиске решения зависимостей. На сайте vivod-iz-zapoya-tula010.ru вы можете найти информацию о доступной помощи, которая предлагает экстренную помощь. Наркологическая служба обеспечивает медицинскую помощь при злоупотреблении наркотиками и алкоголем. Специалисты предлагают консультации нарколога, а также гарантируют анонимное лечение. В рамках неотложной помощи возможны программы восстановления и стационарное лечение. Эмоциональная поддержка играет важную роль в лечении зависимостей. Обратитесь за помощью незамедлительно, помогите себе и своим близким!
https://hr.rivagroup.su/
лечение запоя
vivod-iz-zapoya-omsk007.ru
вывод из запоя
Спинтакс капельницы от запоя — действительный метод помочь людям, страдающим от алкогольной зависимости. В Туле существует множество клиник, предлагающих услуги вывода из запоя круглосуточно. При выборе клиники важно обратить внимание на опыт специалистов, методы лечения и гарантии безопасности.Медикаментозное лечение запоя включает в себя индивидуальную программу к каждому пациенту. Консультация специалиста поможет определить необходимость капельницы и другие способы лечения. Также поддержка близких играет важную роль, которая является неотъемлемой частью процесса.круглосуточная помощь при алкоголизме в Туле Клиника в Туле должна предлагать наркологические услуги и программы восстановления, чтобы обеспечить качественное восстановление. Поддержка при алкогольной зависимости может быть оказана в любое время, что способствует эффективному лечению.
провайдеры по адресу
inernetvkvartiru-nizhnij-novgorod006.ru
подключить интернет
cjc 1295 and ipamorelin vs sermorelin
References:
https://fresherskiduniya.com/employer/the-heart-of-the-internet/
экстренный вывод из запоя
vivod-iz-zapoya-omsk008.ru
вывод из запоя
Капельница от алкогольной зависимости – проверенное решение для лечения алкогольной зависимости. Она способствует быстрое вливание жидкости‚ способствуя детоксикации тела и восстановлению здоровья. В учреждениях по лечению алкогольной зависимости‚ таких как vivod-iz-zapoya-tula012.ru‚ квалифицированные специалисты предлагают медицинскую помощь‚ включая инъекции от запоя. Терапия включает также капельницы‚ но и реабилитацию‚ психологическую поддержку при алкоголизме‚ что помогает пациентам вернуться к нормальной жизни.
провайдер по адресу
inernetvkvartiru-novosibirsk004.ru
провайдеры по адресу новосибирск
экстренный вывод из запоя омск
vivod-iz-zapoya-omsk009.ru
вывод из запоя
Мы поможем рассчитать таможенные платежи и заранее спланировать расходы на оформление товара: таможенный брокер в Москве
Зависимость от алкоголя – это значительная проблема, которая требует комплексного подхода к терапии. На сайте vivod-iz-zapoya-vladimir010.ru вы можете найти информацию о способах лечения алкоголизмавключая детоксикацию и кодирование от алкоголя. Важным этапом является восстановление, где предоставляется психологическая помощь и формируются поддерживающие группытакие как анонимные алкоголики. Помощь зависимым часто включает в себя рекомендации по отказу от алкоголя и рекомендации для жизни без алкоголя. Восстановление после запоя требует усердия и поддержки родственников. Необходимо помнить о влиянии алкоголя на здоровье и следовать методам отказа от алкоголя для достижения успешного выздоровления.
интернет провайдеры по адресу новосибирск
inernetvkvartiru-novosibirsk005.ru
провайдер по адресу новосибирск
Наша платформа https://probilets.com/ работает круглосуточно и не знает слова перерыв. Бронировать и планировать можно где угодно: в поезде, на даче, в кафе или лежа на диване. Хотите купить билет, пока идёте по супермаркету? Просто достаньте телефон и оформите поездку. Нужно скорректировать планы, отменить или перенести билет? Это тоже можно сделать онлайн, без звонков и визитов. Но если возникла проблема, то наши специалисты помогут и все расскажут
лечение запоя
vivod-iz-zapoya-orenburg007.ru
вывод из запоя круглосуточно
интернет провайдеры новосибирск по адресу
inernetvkvartiru-novosibirsk006.ru
домашний интернет тарифы новосибирск
Рабочее кракен маркетделает вход простым. Ссылки проверены и помогают авторизоваться без рисков.
Надёжный доступ всегда возможен через http://krakr.cc, официальный адрес сайта.
KRAKEN маркет — это площадка с удобным входом на кракен вход. Рабочая ссылка ведёт прямо в личный кабинет.
Рабочее зеркало кракен тор — это удобное решение для тех, кто хочет пользоваться сервисом постоянно.
экстренный вывод из запоя оренбург
vivod-iz-zapoya-orenburg008.ru
экстренный вывод из запоя оренбург
https://pikadil.ru/view/otello.ru
Если вам нужно провести раскопки на участок земли в владимире, обращение к профессиональным услугам способствует существенному упрощению задачи. Компания vivod-iz-zapoya-vladimir012.ru предлагает широкий спектр земляных работ, включая копку участка для строительства или обустройства территории. Мы гарантируем высокое качество выполнения услуг по подготовке участка, а также бурение скважин для полезных нужд. Аренда техники позволяет нам оперативно проводить любые садовые работы, а наши квалифицированные сотрудники помогут вам с выбором подходящего грунта. Выбирая наши услуги, вы получаете не только гарантию надежности, но и профессионализм в осуществлении всех задач. Обратитесь к нам, и мы поможем откопать все необходимое на вашем участке!
https://russpain.com/
домашний интернет ростов
inernetvkvartiru-rostov004.ru
подключить интернет в квартиру ростов
Капельница при алкоголизме — является действующим способом, используемым в наркологии для лечения зависимости от алкоголя; инфузионная терапия даёт возможность оперативно вывести токсины из организма и нормализовать водно-электролитный баланс. Нарколог на дом анонимно в владимире предоставляет такую услугу, обеспечивая пациентам удобство и конфиденциальность. нарколог на дом анонимно владимир Признаки похмелья, включающие боль в голове, тошноту и рвоту и слабость, могут быть сняты с помощью инфузионной терапии, включающей подходящие лекарства. Лечение алкоголизма предполагает индивидуального подхода, и специалист по наркологии на дому осуществляет первичную консультацию, выбирая подходящие методы для снятия абстиненции. Очистка организма — существенный шаг, позволяющий вернуться к норме после алкогольной зависимости. Забота и поддержка семьи занимает важную роль в реабилитации зависимых, а фармацевтическое лечение в комбинации с инфузионной терапией обеспечивает эффективный результат.
экстренный вывод из запоя оренбург
vivod-iz-zapoya-orenburg009.ru
экстренный вывод из запоя
ipamorelin online prescription
References:
https://cuttify.io/ermahenninger
ipamorelin 2mg for sale
References:
Ipamorelin Dose For Women (https://quickplay.pro/michelehenson7)
провайдеры ростов
inernetvkvartiru-rostov005.ru
домашний интернет ростов
ipamorelin online prescription
References:
https://pin-it.space/item/461391
Храните у себя актуальный адрес https://krakr.cc/, чтобы не потерять доступ к сайту и всегда иметь возможность безопасного входа.
Если вы хотите быть уверены в доступе, используйте рабочее зеркало http://www.krakr.cc, оно открывает все функции площадки.
Для быстрого подключения используйте KRAKEN ссылка.
Чтобы не терять доступ, сохраняйте актуальную KRAKEN ссылка. Рабочее зеркало кракен тор открывает маркет и личный кабинет.
Капельницы на дому в владимире — это удобное решение для людей, которым требуется медицинская помощь, но не может посетить клинику. Услуга включает инфузионную терапию, где медсестра на дому осуществляет инфузии в удобной для вас обстановке. Это особенно актуально для реабилитации после заболевания или при необходимости медикаментозной терапии. Комфорт лечения и забота о пациентах значительно увеличиваются, когда квалифицированный врач посещает вас на дому. Профилактика заболеваний и консультации врача также становятся доступнее. Сайт vivod-iz-zapoya-vladimir014.ru предоставляет эти услуги, обеспечивая здоровье и комфорт для всех нуждающихся.
Капельница от похмелья — это один из лучших вариантов для скорейшего решения проблем интоксикации после употребления алкоголя. При состоянии похмелья организм страдает от обезвоживания и нехватки важных веществ, что способствует головной боли. Лечение капельницей включает в себя вливание специальных растворов и возвращение нормального состояния организма. Обращение к врачу может включать в себя медикаменты, улучшающие самочувствие, которые помогают организму вернуться к норме. Капельницы часто содержат полезные добавки, вещества для детоксикации, которые ускоряют процесс выздоровления. Поддержка организма таким образом позволяет значительно уменьшить симптомы похмелья и помочь восстановиться. Для получения капельницы можно обратиться в клинику или позвонить врачу на дом через интернет vivod-iz-zapoya-tula010.ru. Учтите, что своевременное лечение поможет уменьшить риски.
Актуальное KRAKEN зеркало позволяет пользоваться
.
KRAKEN вход всегда доступен через кракен маркетплейс. Актуальное зеркало помогает авторизоваться и продолжить пользоваться сервисом.
https://mangalfactory.ru/
Для тех, кто хочет стабильности, есть кракен магазин официальный сайт. Ссылки и зеркала помогут войти в систему в любое время.
провайдеры домашнего интернета ростов
inernetvkvartiru-rostov006.ru
интернет провайдеры ростов
Актуальное зеркало KRAKEN позволяет авторизоваться в кракен личный кабинет продолжить покупки.
Лечение алкоголизма в владимире: первый шаг к выздоровлению Алкогольная зависимость является серьезной проблемой, которая требует квалифицированного вмешательства. В владимире доступна круглосуточная помощь нарколога на дом, что позволяет начать лечение в удобное время. Консультация нарколога поможет выявить уровень зависимости и выбрать подходящую программу лечения. нарколог на дом круглосуточно владимир Медикаментозная терапия, широко используемая в реабилитационных центрах владимира, нацелена на облегчение абстинентного синдрома и восстановление здоровья. Психологическая поддержка играет ключевую роль в процессе выздоровления, обеспечивая эмоциональную стабильность. Анонимность в лечении создает более комфортные условия для пациента. Детоксикационная программа способствует очищению организма от токсинов, а реабилитационный процесс включает социальную адаптацию и меры по предотвращению рецидивов. Квалифицированная помощь является гарантией успешного решения проблемы. Не упустите возможность изменить свою жизнь к лучшему!
Алкогольная зависимость, это серьезная проблема, требующая экспертного вмешательства. Круглосуточная клиника предлагает помощь нарколога, обеспечивая детоксикацию организма и лечение алкоголизма. Симптомы алкогольной зависимости могут меняться, от телесной зависимости до психологических расстройств; Клиническая detox-программа включает в себя детоксикацию и реабилитацию от алкоголя, что позволяет реабилитироваться после запоя. Консультация нарколога помогает определить характер зависимости и выбрать оптимальный метод лечения. Психотерапия при алкоголизме является ключевым этапом, предоставляя поддержку для зависимых. Анонимное лечение алкоголизма гарантирует анонимность. Нарколог в Туле всегда готов оказать помощь, обеспечивая индивидуальный подход к любому пациенту.}
С помощью кракен личный кабинет можно легко получить рабочий вход даже на телефоне.
KRAKEN сайт поддерживает актуальные варианты подключения. Вход возможен на кракен онион за пару секунд.
Выберите надёжное зеркало krakr.cc/, чтобы открыть маркет и продолжить покупки без проблем.
Храните у себя актуальный адрес https://krakr.cc/, чтобы не потерять доступ к сайту и всегда иметь возможность безопасного входа.
http://www.sochistroygroup.ru – практика и советы
Рабочее KRAKEN зеркало позволяет пользоваться кракен ссылка.
KRAKEN официальный сайт всегда снабжён инструкциями для пользователей. Рабочая кракен торгарантирует доступ в личный кабинет без проблем.
Рабочее KRAKEN зеркало — это удобный способ попасть в кракен зеркало.
sochistroygroup.ru/ – строительный онлайн-справочник
Для анонимного входа используйте https://krakr.cc, ссылка совместима с TOR-браузером.
Проблема зависимости от наркотиков и алкоголя требует квалифицированного вмешательства. Наркологическая помощь состоит из диагностики зависимостей и лечениячто может существенно изменить жизнь человека. Консультация нарколога. Лечение алкоголизма и реабилитация наркоманов проводятся в специализированных центрах, таких как vivod-iz-zapoya-vladimir016.ru. Программы восстановления предполагают психотерапевтические сеансы и группы поддержки для зависимых, а также семейную поддержку. Важно помнить о мотивации к лечению и профилактике зависимостей. Адаптация в обществе после лечения помогает предотвратить рецидивы. Анонимная помощь наркозависимым доступна и продуктивна. Начните новый этап своей жизни с помощью профессионалов!
KRAKEN сайт доступен в любое время через кракен личный кабинет или TOR.
провайдер по адресу
inernetvkvartiru-spb004.ru
проверить интернет по адресу
Услуга нарколога на дому, ценная помощь для людей‚ страдающих от зависимости от наркотиков. Комплексный подход необходим для лечения наркомании‚ и помощь на дому обеспечивает удобство и конфиденциальность. Вызов нарколога позволяет обратиться за медицинской помощью и начать detox программу‚ не покидая своего жилья; Психотерапия и медицинская помощь помогают клиентам справиться с зависимостью‚ а семейная поддержка играет ключевую роль в восстановлении после зависимости. Конфиденциальное лечение и профилактика наркомании также являются важными элементами. Посетив vivod-iz-zapoya-tula012.ru‚ вы сможете получить профессиональную помощь и поддержку.
KRAKEN сайт даёт возможность подключаться с любых устройств. Рабочая ссылка открывает кракен даркнет без ограничений.
строительство таунхаусов сочи – Таунхаусы
Чтобы пользоваться ресурсом кракен маркет, достаточно одной рабочей ссылки.
Если ссылка заблокирована, используйте http://www.krakr.cc, этот адрес доступен круглосуточно.
кракен входоткрывает прямой путь в маркет. Найдите актуальную ссылку, следуйте подсказкам и получите безопасный доступ к сайту с полным функционалом.
Рабочее зеркало кракен маркет — это удобное решение для тех, кто хочет пользоваться сервисом постоянно.
https://www.sochistroygroup.ru – идеи для строительства
KRAKEN сайт поддерживает актуальные варианты подключения. Вход возможен на кракен онион за пару секунд.
Актуальный доступ к сайту всегда возможен через https://www.krakr.cc/, который повторяет весь функционал.
Рабочее KRAKEN зеркало позволяет пользоваться кракен маркет.
Задумываетесь о покупке? Наш магазин удивляет широкий выбор. Зайдите к нам по ссылке: https://xn--kr9-onb.com
Прокапка после алкогольной зависимости — это ключевая медицинская манипуляция, предназначенная для очищения организма и восстановление здоровья человека. Во время обращения к наркологу для оказания помощи на дому осуществляется введение лекарственных средств через капельницу, что помогает очистить кровь от токсинов , которые накапливаются при злоупотреблении алкоголем. Нарколог на дом срочно Процедура обычно включает в себя солевые растворы, витамины и минералы, что способствует улучшению самочувствия и облегчает симптомы похмелья . Лечение на дому позволяет пациенту находиться в привычной обстановке , что важно для успешной реабилитации . Наркологическая помощь включает поддержку пациента , что значительно повышает шансы на восстановление организма после алкоголя . Необходимо соблюдать рекомендации по лечению и проводить прокапку регулярно для достижения наилучших результатов .
https://bpr-work.ru/
провайдер по адресу санкт-петербург
inernetvkvartiru-spb005.ru
интернет по адресу санкт-петербург
Рабочее KRAKEN зеркало позволяет пользоваться кракен ссылка.
KRAKEN сайт помогает обойти блокировки. Выберите проверенное зеркало, зайдите по кракен входи пользуйтесь маркетом с телефона или ПК.
KRAKEN маркет легко открыть через ссылку https://krakr.cc/, которая остаётся рабочей.
https://www.sochistroygroup.ru/ – опытные строители
KRAKEN маркет доступен через официальные ссылки кракен ссылка и проверенные зеркала.
Неотложная помощь при запое – это важный аспект борьбы с алкогольной зависимостью. Признаки запоя включают настойчивого стремления к спиртному, физической зависимости и психических расстройств. Первым шагом в терапии запоя является детоксикация, что способствует выведению токсических веществ из организма. При оказании медпомощи при запое применяются лекарственные средства для облегчения абстинентного синдрома. Эмоциональная поддержка и опора близких играют ключевую роль в поддержании мотивации пациента. Необходимо уделить внимание реабилитационным программам и восстановление после запоя. Центр лечения алкоголизма предлагает различные методы лечения, включая народные средства от запоя. Предотвращение рецидива необходимо для успешного завершения лечения; Надежная программа реабилитации поможет пациенту вернуться к нормальной жизни. Больше информации по данной теме вы можете найти на сайте vivod-iz-zapoya-vladimir010.ru.
Актуальное KRAKEN зеркало позволяет пользоваться кракен официальный сайт.
KRAKEN маркет доступен в любой момент. Просто выберите кракен личный кабинет или онион-ссылку и вход займёт всего пару секунд.
Надёжный доступ всегда возможен через http://krakr.cc, официальный адрес сайта.
https://www.kramatorsk.info/export
Рабочее зеркало кракен зеркало ведёт прямо в маркет без лишних шагов.
sochistroygroup.ru/ – решения для загородного дома
Вызов нарколога на дом в экстренных случаях — это важная услуга для тех, кто сталкивается с зависимостями. На сайте vivod-iz-zapoya-vladimir018.ru вы можете обратиться за консультацией нарколога и вызвать врача для домашнего визита. Квалифицированная помощь нарколога включает в себя лечение различных зависимостей и психологическую поддержку. Экстренная медицинская служба предлагает анонимную помощь, что позволяет сохранить конфиденциальность. Эффективное лечение наркомании и помощь алкоголикам возможны с участием психотерапевта на дом. Не ждите, получите срочную помощь уже сегодня!
С помощью кракен зеркало можно легко получить рабочий вход даже на телефоне.
Чтобы зайти в KRAKEN маркетплейс, достаточно перейти по ссылке http://krakr.cc, это проверенный адрес.
KRAKEN даркнет вход реализован через рабочие ссылки кракен онион. Зеркала помогают обойти блокировки.
Чтобы войти в кракен маркет, используйте KRAKEN ссылка. Всё просто и удобно.
проверить провайдера по адресу
inernetvkvartiru-spb006.ru
интернет по адресу
KRAKEN вход в личный кабинет всегда доступен. Рабочее зеркало кракен личный кабинет помогает пройти авторизацию.
Если вам нужна стабильность, выберите http://krakr.cc, этот адрес проверен временем.
KRAKEN маркет доступен в любой момент. Просто выберите кракен зеркало или онион-ссылку и вход займёт всего пару секунд.
Лечение алкоголизма в владимире: первый шаг к выздоровлению Алкогольная зависимость – серьезная проблема, требующая профессионального вмешательства. В владимире доступна круглосуточная помощь нарколога на дом, что позволяет начать лечение в удобное время. Обращение к наркологу поможет определить степень зависимости и подобрать оптимальную программу лечения. нарколог на дом круглосуточно владимир Медикаментозное лечение, часто применяемое в Центрах реабилитации владимир, направлено на снятие абстиненции и восстановление организма. Психологическая поддержка играет ключевую роль в процессе выздоровления, обеспечивая эмоциональную стабильность. Анонимность в лечении создает более комфортные условия для пациента. Detox-программа поможет очистить организм от токсинов, а реабилитация зависимых включает социальную адаптацию и профилактику рецидива. Профессиональная помощь – залог успешного преодоления проблемы. Не упустите возможность изменить свою жизнь к лучшему!
Чтобы попасть на площадку кракен официальный сайт, используйте актуальную KRAKEN ссылка. Вход безопасен.
http://sochistroygroup.ru/ – новинки строительной отрасли
Рабочий доступ через кракен магазин сайт всегда под рукой.
Сегодня проблема зависимости от наркотиков и алкоголя приобретает всё большую значимость. Наркологическая медицина предлагает множество решений для борьбы с этими недугами. Если вы или кто-то из ваших знакомых, стоит обратиться к наркологу на дом круглосуточно в владимире. Вы можете посетить сайт vivod-iz-zapoya-vladimir019.ru, на котором все необходимые услуги.Специалист по наркологии на дому предлагает анонимное лечение, что позволяет сохранить личную жизнь пациента в тайне. Круглосуточные услуги дают возможность получить медицинской помощи независимо от времени суток. Это особенно важно в критических ситуациях, таких как лечение похмелья или острых состояний, связанных с наркоманией. Специалисты проводят детоксикацию организма, что является важным этапом в лечении зависимости. Клиника, предоставляющая услуги на дому предоставляет не только медицинскую помощь, но и консультацию специалиста по вопросам реабилитации и профилактики рецидивов. Токсикология играют важную роль в этом процессе, так как правильная диагностика способствует выбору оптимальных методов лечения. Лечение на дому — это удобный вариант для пациентов, которые не желают посещать стационар. Выездной нарколог обеспечит индивидуальный подход и комфортные условия для выздоровления. Не стесняйтесь обращаться за помощью, и вы сможете вернуть себе нормальную жизнь!
Сохраняйте https://krakr.cc, чтобы не потерять доступ к площадке.
KRAKEN официальный сайт поддерживает зеркала для обхода блокировок. Вход через кракен даркнет выполняется моментально.
техническое обслуживание ибп
Актуальная KRAKEN ссылка кракен официальный сайт подходит для входа с телефона.
бесплатный выезд инженера сочи – Бесплатный осмотр территории
KRAKEN сайт всегда содержит актуальные способы входа на кракен официальный сайт
.
Надёжный адрес сайта — https://krakr.cc, его можно сохранить в закладки.
Надёжный доступ всегда возможен через http://krakr.cc, официальный адрес сайта.
Рабочее KRAKEN зеркало — это удобный способ попасть в кракен сайт.
Rainbet Australia
Рабочий вход в KRAKEN сайт доступен всегда.
В случае необходимости раскопок на вашем участке в владимире, обратиться за помощью к профессионалам способно значительно упростить процесс. Компания vivod-iz-zapoya-vladimir012.ru предоставляет разнообразные земляных работ, включая раскопки участка для возведения зданий или обустройства территории. Мы гарантируем высокое качество реализации услуг по подготовке участка, а также создание скважин для полезных нужд. Использование арендованной техники позволяет нам эффективно проводить любые садовые работы, а наши квалифицированные сотрудники помогут вам с подбором подходящего грунта. Выбирая наши услуги, вы обеспечиваете себе не только гарантию надежности, но и профессионализм в выполнении всех задач. Свяжитесь с нами, и мы с радостью поможем откопать все необходимое на вашем участке!
Чтобы пользоваться кракен онион, используйте рабочее KRAKEN зеркало. Ссылка ведёт к полному функционалу.
https://sochistroygroup.ru – строительные коллаборации
Для тех, кто ищет проверенный доступ к KRAKEN, всегда можно использовать https://www.krakr.cc — ссылка ведёт напрямую на официальный сайт.
Пользователи рекомендуют https://www.krakr.cc как основной адрес для входа в маркет.
KRAKEN ссылка через TOR открывает доступ к кракен личный кабинет даже при блокировках. Вход занимает минимум усилий.
KRAKEN маркет доступен в любой момент. Просто выберите кракен личный кабинет или онион-ссылку и вход займёт всего пару секунд.
При проблемах с доступом поможет зеркало http://www.krakr.cc, оно ведёт напрямую на сайт.
Чтобы войти в кракен маркет, используйте KRAKEN ссылка. Всё просто и удобно.
Круглосуточная наркологическая помощь в Красноярске доступна. Если у вас страдает от зависимостиважно знатьчто существует неотложная помощь. Наркологическая клиника предлагает вызов специалиста по наркологии на дома также лечение зависимостей без раскрытия данных. Прием врача-нарколога способствует выбору эффективной терапии зависимостей. Центр реабилитации обеспечивает детоксикацию организма и поддержку пациентов на всех этапах лечения. Свяжитесь с нами для получения более детальной информации на vivod-iz-zapoya-krasnoyarsk013.ru.
кракен маркетоткрывает прямой путь в маркет. Найдите актуальную ссылку, следуйте подсказкам и получите безопасный доступ к сайту с полным функционалом.
Откачка на дому в Красноярске, важная услуга для поддержания чистоты и здоровья. Канализационные проблемы могут возникнуть неожиданно, и в таких случаях необходимо обратиться в аварийную службу Красноярск. Профессиональная откачка сточных вод поможет избежать неприятных ситуаций.Среди вариантов откачки можно выделить: очистка канализации, обслуживание сливных ям и экстренная откачка. Ассенизаторская машина обеспечит качественное выполнение работ с соблюдением всех экологических стандартов. На сайте vivod-iz-zapoya-krasnoyarsk013.ru вы можете узнать информацию о стоимости услуг и вариантах вызова специалиста. Также доступны устройства для сушки септиков и дренажные системы для минимизации повторных засоров. Не затягивайте с решением проблемы — устраните проблемы с канализацией прямо сейчас!
Чтобы пользоваться кракен сайт, используйте рабочее KRAKEN зеркало. Ссылка ведёт к полному функционалу.
Актуальный KRAKEN сайт всегда доступен по адресу https://krakr.cc, этот вариант сохраняет стабильность даже при блокировках.
Официальное кракен онион зеркало подходит для любых устройств.
Услуги платной наркологии, это ключевой момент в борьбе с зависимостями. В наркологической клинике, такой как vivod-iz-zapoya-vladimir013.ru, пациентам предоставляется профессиональная помощь, включая программы по борьбе с наркоманией и алкоголизмом. Программа восстановления включает детоксикацию организма и психологическую поддержку. Обсуждение с наркологом позволяет разработать индивидуальный подход к каждому случаю. Клиники гарантируют скрытость и экстренную поддержку. Поддержка родственников также является важным аспектом. Групповые занятия помогают поддерживать друг друга, а медицинское наблюдение обеспечивает защиту пациентов. Коммерческие услуги позволяют достигать лучших результатов и внимание специалистов, что способствует эффективному выздоровлению.
https://vgarderobe.ru/odezhda-dlya-malchikov-simpsons-bc-9778.html
Официальное
зеркало подходит для любых устройств.
Актуальный сайт всегда доступен по адресу krakr.cc, это проверенный вариант.
Чтобы открыть маркетплейс, воспользуйтесь KRAKEN зеркало. Актуальная кракен магазинбезопасна и подходит для любых устройств.
ДОСТУПНЫЙ ВЫВОД ИЗ ЗАПОЯ В Красноярске: РЕАЛЬНОСТЬ И МИФЫ Процесс лечения алкоголизма является непростым и требует комплексного подхода. В Красноярске множество наркологических клиник предлагают лечение запоя и реабилитацию от запоя, однако есть мифы о лечении алкоголизма, способные ввести в заблуждение. Во-первых, некоторые люди полагают, что вывод из запоя – это быстрое мероприятие. На самом деле, реальные методы вывода из запоя, такие как детоксикация и психотерапия, требуют определенного времени. Наркологическая клиника Красноярск в Красноярске предлагает программы реабилитации, в рамках которых специалисты оказывают помощь в восстановлении после запоя. Важно отметить, что психотерапия имеет центральное значение в процессе лечения зависимости. Консультация нарколога поможет выявить причины зависимости и разработать индивидуальную программу лечения. Не стоит забывать, что лечение зависимости в Красноярске доступно и эффективно, если обратиться за помощью вовремя.
Если ищете, как зайти на кракен личный кабинет, выберите актуальное зеркало. Рабочая ссылка позволяет без лишних шагов попасть на официальный сайт.
KRAKEN сайт всегда содержит актуальные способы входа на кракен даркнет
.
Рабочее зеркало площадки доступно по адресу https://www.krakr.cc/, оно официальное.
Услуги нарколога на дому в Красноярске становятся всё актуальней. Профессионалы, работающие в этой области, оказывают разнообразные наркологические услуги, в т.ч. помощь при алкоголизме и других зависимостях. Консультация нарколога на дому даёт возможность оперативно диагностировать зависимости и назначить индивидуальный подход к пациенту. Лечение без раскрытия личности – важный аспект работы специалистов, что имеет особую значимость для тех, кто испытывает стеснение перед походом в медучреждения. Домашняя реабилитация предполагает психотерапевтическую поддержку, восстановительные программы и медикаментозное лечение. Поддержка семей зависимых является ключевым элементом в процессе выздоровления. Профилактика рецидивов также является важной частью работы наркологов. Специалисты предлагают психологическую помощь и поддержку, помогая пациентам справляться с трудностями на пути к выздоровлению. Узнать больше о доступных услугах можно на сайте vivod-iz-zapoya-krasnoyarsk014.ru, где вы найдёте всю необходимую информацию и контакты по наркологическим услугам в Красноярске.
KRAKEN сайт поддерживает актуальные варианты подключения. Вход возможен на кракен зеркало за пару секунд.
Капельница от запоя – это важная медицинская процедура, которая может оказать помощь в лечении алкоголизма. Вызвать нарколога на дом в владимире стоит, если наблюдаются симптомы запоя: острые головные боли, тошнота, трепет. Медицинская помощь при алкоголизме включает капельницы, помогающие восстановить водно-солевой баланс и обезвреживание токсинов. Вызов врача на дом позволяет получить профессиональную помощь алкоголикам в удобных условиях. Услуги нарколога в владимире включают лечение запойного состояния и восстановление после запоя. Чтобы восстановление прошло успешно, важно следовать рекомендациям специалистов и пройти курс лечения алкогольной зависимости. Пользуйтесь услугами домашней наркологии для быстрого и эффективного выздоровления.
Рабочее зеркало кракен онион ведёт прямо в маркет без лишних шагов.
Актуальный доступ к сайту всегда возможен через https://www.krakr.cc/, который повторяет весь функционал.
KRAKEN онион зеркало подходит для анонимного доступа в кракен онион. Ссылка ведёт напрямую к ресурсу.
ПРОКАПАТЬ ОТ АЛКОГОЛЯ: ЗНАЧЕНИЕ ДЕТОКСИКАЦИИ И ПОМОЩИ Вопрос алкогольной зависимости затрагивает множества людей. Лечение алкоголизма часто стартует с детоксикации, которая включает прокапывание. Этот процесс помогает вывести токсины из организма и уменьшить абстинентный синдром.Капельницы от алкоголя содержат препараты для детоксикации, способствующие оздоровлению организма. Они способствуют восстановиться после запоя, обеспечивая необходимую медицинскую помощь. Необходимо помнить, что поддержка зависимых в этот период крайне важна.После детоксикации начинается реабилитация, где психотерапия при алкоголизме занимает ключевую роль. Специалисты поддерживают разобраться в причинах зависимости и дают советы по борьбе с зависимостями.На сайте vivod-iz-zapoya-krasnoyarsk015.ru можно найти информацию о том, как правильно пройти лечение и получить поддержку. Здоровье является важный шаг к новой жизни без алкоголя.
Рабочее зеркало кракен маркет ведёт прямо в маркет без лишних шагов.
Надёжный доступ всегда возможен через http://krakr.cc, официальный адрес сайта.
KRAKEN даркнет вход реализован через рабочие ссылки кракен магазин. Зеркала помогают обойти блокировки.
KRAKEN официальный сайт поддерживает зеркала для обхода блокировок. Вход через
выполняется моментально.
Профилактика алкоголизма в Красноярске: рекомендации врачей Зависимость от алкоголя — серьезная проблема‚ требующая внимания и действий. Важно знать о возможностях профилактики и лечения. Можно обратиться к наркологу на дом в Красноярске можно Врачи советуют проводить профилактические меры‚ включая осведомленность о последствиях алкоголизма и поддержку семьи. вызвать нарколога на дом Красноярск В процесс лечения алкоголизма включаются реабилитационные программы‚ позволяющие способствуют вернуть здоровье и социальную интеграцию. Наркологическая помощь необходима для работы с зависимыми‚ а также для предотвращения рецидивов. Здоровье и алкоголь — это вечная борьба‚ и своевременная поддержка играет ключевую роль.
KRAKEN сайт — это надёжный источник для кракен вход проверенных ссылок.
Вызов анонимного нарколога — это значительным шагом на дороге к избавлению от зависимости. Если вы или ваш близкий испытываете проблемами с психоактивными веществами либо алкоголем‚ не откладывайте обращение за помощью. На сайте site;com вы можете получить консультацию нарколога и вызвать специалиста на дом. Конфиденциальная помощь обеспечивает вашу конфиденциальность‚ что особенно важно для людей с зависимостями. Квалифицированный нарколог проведет детоксикацию организма и разработает персонализированные программы восстановления. Психотерапия зависимости также играет ключевую роль в процессе выздоровления. Помощь зависимым и их близким поможет справиться с последствиями зависимости. Помните‚ что борьба с алкогольной зависимостью так же важно‚ как и работа с наркотиками. Не стесняйтесь обратиться за помощью‚ это первый шаг к новой жизни.
KRAKEN всегда открыт через krakr.cc/, это рабочее решение.
Если вы хотите быть уверены в доступе, используйте рабочее зеркало http://www.krakr.cc, оно открывает все функции площадки.
Рабочее кракен магазинделает вход простым. Ссылки проверены и помогают авторизоваться без рисков.
С помощью кракен вход легко обойти блокировки. Рабочая ссылка позволяет продолжить покупки и пользоваться маркетом.
KRAKEN маркет доступен через официальные ссылки кракен ссылка и проверенные зеркала.
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk016.ru
вывод из запоя смоленск
Если вы хотите быть уверены в доступе, используйте рабочее зеркало http://www.krakr.cc, оно открывает все функции площадки.
KRAKEN кракен магазин TOR даёт возможность обойти блокировки и подключиться анонимно.
Для обхода блокировок достаточно кракен маркетплейс. Рабочее зеркало открывает маркет и позволяет авторизоваться в личном кабинете.
Актуальное KRAKEN зеркало позволяет пользоваться кракен тор.
В любой ситуации поможет ссылка http://krakr.cc/, обеспечивая стабильный вход.
KRAKEN сайт — это надёжный источник для
проверенных ссылок.
лечение запоя
vivod-iz-zapoya-smolensk016.ru
лечение запоя смоленск
Актуальная KRAKEN ссылка открывает дорогу в сервис кракен маркетплейс
.
АЛЬТЕРНАТИВНЫЕ МЕТОДЫ ВЫВОДА ИЗ ЗАПОЯ В владимире: МИФЫ И ФАКТЫ
KRAKEN тор зеркало — удобный способ подключения. Ссылка ведёт к кракен онион ресурсу напрямую.
Если вы хотите быть уверены в доступе, используйте рабочее зеркало http://www.krakr.cc, оно открывает все функции площадки.
Хорошее решение для доступа — https://krakr.cc/, рабочее зеркало площадки.
Актуальная KRAKEN ссылка открывает дорогу в сервис
.
KRAKEN ссылка TOR помогает подключиться к кракен маркетплейс даже при ограничениях.
экстренный вывод из запоя
vivod-iz-zapoya-smolensk017.ru
вывод из запоя
Сохраните у себя в закладках krakr.cc, чтобы всегда иметь доступ к сайту без ограничений.
Если основной ресурс заблокирован, поможет https://krakr.cc/, официальный адрес.
Чтобы открыть
, используйте KRAKEN ссылка. Рабочее зеркало помогает избежать блокировок.
Рабочее KRAKEN зеркало позволяет пользоваться кракен онион.
https://vgarderobe.ru/zhenskie-pulovery-alba-moda-rosso-bc-50939.html
вывод из запоя смоленск
vivod-iz-zapoya-smolensk017.ru
экстренный вывод из запоя
Реабилитация после зависимости от алкоголя в владимире – критически важный шаг на пути к выздоровлению. Нарколог на дом клиника предоставляет профессиональное лечение алкоголизма с персонализированными подходами‚ включая очистку организма и психотерапевтическую поддержку. Посещение нарколога помогает выявить эффективные методы терапии‚ такие как групповая терапия и адаптация в обществе. Семейная поддержка также играет ключевую роль. Центр реабилитации предлагает конфиденциальную помощь и меры по предотвращению рецидивов‚ что способствует успешному восстановлению после алкоголя.
вывод из запоя
vivod-iz-zapoya-smolensk018.ru
лечение запоя смоленск
на сайте
53. **Экспертиза проекта**: Мы Conduct a detailed analysis of your window frames and recommend the best solution for your home — это?? иvenientно!
Source:
– https://www.sport-weekend.com/kak-proverit-horosho-li-ustanovili-plastikovye-okna.htm
Владимирская наркологическая служба предлагает разнообразные услуги для лечения зависимостей. В этом городе работают специализированные реабилитационные центры‚ где можно получить анонимное лечение наркозависимости и алкоголизма. Программа лечения алкоголизма включает в себя как медицинские процедуры‚ так и психотерапию. vivod-iz-zapoya-vladimir018.ru Психологическая помощь владимир также играет важную роль в процессе выздоровления. Обратитесь к наркологу позволяет выявить индивидуальные особенности зависимого и составить индивидуальный план терапии. Профилактика зависимостей и поддержка родственников зависимых – важная составляющая работы наркологической клиники. Реабилитация зависимых включает как терапевтические меры‚ так и социальное reintegration. Услуги наркологической службы направлены на восстановление здоровья и успешное возвращение к нормальной жизни.
В поисках самых свежих трейлеров фильмов 2026 и трейлеров 2026 на русском? Наш портал — это место, где собираются лучшие трейлеры сериалов 2026. Здесь вы можете смотреть трейлер бесплатно в хорошем качестве, будь то громкая премьера лорд трейлер или долгожданный трейлер 3 сезона вашего любимого сериала. Мы тщательно отбираем видео, чтобы вы могли смотреть трейлеры онлайн без спойлеров и в отличном разрешении. Всю коллекцию вы найдете по ссылке ниже: смотреть трейлер бесплатно
После запойного периода необходимо выполнить детоксикацию организма, что поможет уменьшить негативные последствия алкоголизма. Нарколог на дом анонимно предлагает лечение запоя, включая методы очищения организма. Среди признаков запоя наблюдаются раздражительность и наличие физической зависимости. Забота близких и консультации с профессионалом способствуют успешному восстановлению. Процесс реабилитации после запоя включает в себя как психологическую поддержку, так и восстановление организма. Услуги на дому гарантируют комфорт и конфиденциальность. Свяжитесь с профессионалами в области наркологии для получения анонимного лечения и квалифицированной помощи.
Актуальная кракен личный кабинет
ссылка открывает маркетплейс за несколько секунд.
Чтобы зайти с мобильного устройства, переходите по адресу krakr.cc/, этот вариант адаптирован под смартфоны.
Для тех, кто ищет проверенный доступ к KRAKEN, всегда можно использовать https://www.krakr.cc — ссылка ведёт напрямую на официальный сайт.
Актуальное KRAKEN зеркало позволяет пользоваться кракен маркетплейс.
Если ищете, как зайти на кракен вход, выберите актуальное зеркало. Рабочая ссылка позволяет без лишних шагов попасть на официальный сайт.
Рабочий доступ через кракен тор сайт всегда под рукой.
https://rainbetaustralia.com/
Если вы хотите быть уверены в доступе, используйте рабочее зеркало http://www.krakr.cc, оно открывает все функции площадки.
Нужен доступ в личный кабинет? кракен вход решает эту задачу. Рабочее зеркало открывает сайт, а вход проходит безопасно.
Рабочий доступ через кракен магазин сайт всегда под рукой.
сколько стоит подписчик в тг канал
Для анонимного входа используйте https://krakr.cc, ссылка совместима с TOR-браузером.
Если основной ресурс заблокирован, поможет https://krakr.cc/, официальный адрес.
Удобно заходить на сайт через http://www.krakr.cc, особенно если основной адрес недоступен.
Для постоянного доступа подойдёт зеркало http://www.krakr.cc, оно проверено временем.
Надёжный адрес сайта — https://krakr.cc, его можно сохранить в закладки.
Нужен доступ в личный кабинет? кракен маркетплейс решает эту задачу. Рабочее зеркало открывает сайт, а вход проходит безопасно.
купить накрутку подписчиков тг
https://mp-digital.ru/
https://www.wildberries.ru/catalog/171056105/detail.aspx
В любой ситуации поможет ссылка http://krakr.cc/, обеспечивая стабильный вход.
Самый простой способ попасть в личный кабинет — воспользоваться прямой ссылкой krakr.cc, которая проверена и работает без перебоев.
Для удобства сохраняйте https://www.krakr.cc/, чтобы всегда иметь под рукой рабочее зеркало.
Актуальное KRAKEN зеркало кракен тор открывает все разделы ресурса.
KRAKEN сайт всегда содержит актуальные способы входа на кракен ссылка
.
RoiBet games Browse RoiBet games – trending slots, tables, and live rooms.
regero.ro intrare rapidДѓ Г®n Regero: jocuri, promoИ›ii И™i contul tДѓu.
Рабочий доступ через кракен маркет сайт всегда под рукой.
Актуальное KRAKEN зеркало ведёт напрямую к сервису.
Рабочий доступ через кракен личный кабинет сайт всегда под рукой.
KRAKEN сайт доступен.
https://telegra.ph/Posle-togo-kak-vy-uverenno-prodelali-vse-shagi-bezopasnogo-dostupa-ne-zabudte-pro-kraken-vhod-Zdes-09-18
KRAKEN вход успешный.
https://telegra.ph/Soblyudajte-standarty-veb-dizajna-Priderzhivajtes-razmerov-shriftov-i-polej-kotorye-privychny-dlya-klie1-09-18
подписчики в тг канал без отписок
KRAKEN зеркало проверено.
https://telegra.ph/Ne-zabyvajte-o-zerkalah-kotorye-sluzhat-alternativnymi-adresami-dlya-vhoda-na-ploshchadku-EHto-kritichesk-09-18
Рабочая ссылка KRAKEN.
https://telegra.ph/Krome-togo-lica-aktivno-ispolzuyushchie-ploshchadku-mogut-porekomendovat-proverennye-adresa-Ne-zabyvajte2-09-18
накрутка подписчиков тг
Проверенные ссылки KRAKEN спасают.
https://telegra.ph/Sledite-za-tipom-podklyucheniya-ispolzujte-tolko-zashchishchyonnye-seti-Podklyuchenie-cherez-obshchestvennye-Wi-1-09-18
KRAKEN зеркало даркнет рабочее.
https://telegra.ph/Kraken-ssylka-ehto-pervyj-shag-k-vashemu-uspeshnomu-opytu-Ispolzujte-tolko-proverennye-adresa-dlya-pe-09-18
Через официальный сайт KRAKEN и TOR можно попасть без проблем.
https://telegra.ph/Kraken-ssylka-i-kraken-oficialnyj-sajt2-09-18
KRAKEN вход зеркало.
https://telegra.ph/Ne-stoit-ignorirovat-anonimnye-chaty-i-messendzhery-gde-regulyarno-obmenivayutsya-poleznoj-informaciej-o-09-18
Актуальная ссылка KRAKEN.
https://telegra.ph/Sledujte-principam-vizualnogo-i-cvetovogo-kontrasta-Tekst-dolzhen-byt-legko-chitaemym-a-fon-ne-otv1-09-18
Вес футболки и футболка 1988 во Владимире. Бейсболка с вентилятором и бейсболки детские интернет в Томске. Футболка с нами бог и печать логотипы на футболках в Омске. Райан гослинг драйв одежда и упаковка сюрприза в Симферополе. Футболка оптом вкс армия россии и обычная футболка: https://futbolki-s-printom.ru/
накрутка подписчиков телеграм 100 подписчиков
Сайт KRAKEN открыт.
https://telegra.ph/Kraken-tor2-09-18
купить подписчиков в телеграм дешево
KRAKEN ссылка TOR отлично работает на компьютере.
https://telegra.ph/Regulyarnoe-obnovlenie-polzovatelskih-parolej-i-ispolzovanie-dvuhfaktornoj-autentifikacii-sushchestve2-09-18
KRAKEN тор-зеркало.
https://telegra.ph/Posle-polucheniya-dostupa-sleduet-obratit-vnimanie-na-funkciyu-obhoda-blokirovok-Kraken-zerkalo-pozvo2-09-18
купить подписчиков в тг
KRAKEN вход работает.
https://telegra.ph/CHtoby-zajti-na-platformu-ispolzujte-isklyuchitelno-proverennye-istochniki-izbegaya-storonnih-ssylok-ko1-09-18
KRAKEN маркет ссылка.
https://telegra.ph/Sravnenie-Kraken-s-drugimi-marketplejsami-v-darknete-09-18
купить подписчиков в телеграм канал без отписок
как накрутить подписчиков в телеграм канале
кракен вход ссылка – Кракен сайт вход обновляется каждый день, чтобы доступ оставался быстрым.
– Через кракен сайт вход можно войти в систему с телефона или ПК без перебоев.
кракен зеркало – Выбирайте кракен маркетплейс — это проверенный доступ и надёжная работа.
как посмотреть подписчиков в тг канале
кракен зеркало актуальное – Через кракен тор ссылка можно подключаться без перебоев.
Журналистское расследование, посвящённое KRAKEN маркетплейсу, выявило одну ключевую деталь:
демонстрирует редкий баланс между удобством, безопасностью и широтой ассортимента. В отличие от конкурентов, кракен только через тор поддерживает постоянную работу зеркал и доступность сервиса. Поддержка отвечает быстро, арбитраж минимизирует риски, а репутация ресурса формировалась годами. Всё это подтверждает устойчивый статус KRAKEN как надёжного онлайн рынка, востребованного среди пользователей, ценящих стабильность и качество.
кракен сайт вход – Кракен маркетплейс — официальная площадка с товарами и сервисами.
щетки
кракен онион вход – Выбирайте кракен маркетплейс — это проверенный доступ и надёжная работа.
Таможенный брокер — ваш надежный партнер при импорте и экспорте товаров в Москве: таможенный брокер
накрутка подписчиков телеграм канал
кракен зеркало сегодня – Кракен официальный сайт зеркало помогает обходить блокировки и входить без проблем.
кракен вход зеркало – Используйте кракен официальный сайт зеркало для надёжного входа в маркет.
кракен маркет ссылка – Кракен онион обеспечивает прямой доступ даже при ограничениях.
https://www.restate.ru/
кракен сайт – Выбирайте кракен зеркало рабочее — оно всегда проверено и безопасно.
кракен как зайти – Подключение через кракен онион подходит для тех, кто ценит безопасность.
KRAKEN вход всегда доступен через кракен зеркало. Актуальное зеркало помогает авторизоваться и продолжить пользоваться сервисом.
кракен онион вход – Кракен онион обеспечивает прямой доступ даже при ограничениях.
Для авторизации используйте кракен тор. Актуальная ссылка безопасна и проверена временем.
живые подписчики в телеграм канал
купить подписчиков в телеграм канал без отписок
кракен тор даркнет – Кракен официальный сайт зеркало — быстрый способ подключиться и продолжать работу.
Нужен доступ в личный кабинет? кракен зеркало решает эту задачу. Рабочее зеркало открывает сайт, а вход проходит безопасно.
кракен маркет ссылка – Через кракен тор ссылка можно подключаться без перебоев.
Для тех, кто хочет стабильности, есть
официальный сайт. Ссылки и зеркала помогут войти в систему в любое время.
как зайти на кракен с телефона – Даже при ограничениях кракен официальный сайт зеркало работает стабильно.
кракен маркетплейс – Кракен вход в личный кабинет доступен через рабочие зеркала и актуальные ссылки.
кракен тор – Кракен сайт всегда под рукой: свежие рабочие зеркала и проверенные ссылки помогают заходить без перебоев.
ПиратХаб курсы
кракен ссылка darknet – Кракен вход в личный кабинет — надёжный способ доступа к сервисам.
накрутка подписчиков в тг платно
купить активных подписчиков в телеграм канал
как зайти на кракен с телефона – Быстрый кракен вход в личный кабинет работает на телефоне и ПК.
кракен зеркало рабочее – Кракен сайт вход обновляется каждый день, чтобы доступ оставался быстрым.
кракен зеркало сегодня – Кракен маркетплейс — официальная площадка с товарами и сервисами.
Kingpin Crown in Australia is a premium entertainment venue offering bowling, laser tag, arcade games, karaoke, and dining: Kingpin Crown products and offers
кракен вход зеркало – Кракен сайт вход обновляется каждый день, чтобы доступ оставался быстрым.
накрутка подписчиков в тг платно
кракен вход – Если ищете стабильный доступ, кракен сайт предлагает актуальные адреса и быстрый вход.
кракен тор зеркало – Быстрый кракен вход в личный кабинет работает на телефоне и ПК.
кракен тор даркнет – Кракен ссылка актуальная всегда проверена и доступна для подключения.
сайт кракен зеркало – Кракен ссылка актуальная всегда проверена и доступна для подключения.
https://milgauzen.ru/
Crown Metropol Perth is a luxury hotel located near the Swan River. It offers modern rooms, a stunning pool area, fine dining, a casino, and entertainment options: official Crown Metropol Perth website
кракен маркетплейс официальный сайт – Выбирайте кракен вход в личный кабинет — это удобство и безопасность.
накрутка подписчиков в тг без заданий
накрутить подписчиков в тг
https://alenapak.ru/
накрутка подписчиков в тг навсегда
Алкоголь ночью с доставкой на дом в Москве. Работаем 24/7, когда обычные магазины закрыты. Широкий ассортимент: пиво, сидр, вино, шампанское, крепкие напитки. Быстрая доставка в пределах МКАД за 30-60 минут: алкоголь доставка москва 24
купить подписчиков в телеграм канал
https://1-ceh.ru/
накрутка подписчиков тг
накрутить подписчиков в тг
накрутка подписчиков в тг дешево
Накрутка подписчиков в ТГ
which one of the following is not a potential danger of anabolic steroids?
References:
Some Examples Of Steroids Are Shown Here (https://www.onlywam.tv/@brendabyerly4?page=about)
кракен зеркало рабочее – Через кракен зеркало рабочее легко обойти блокировки и попасть в личный кабинет.
кракен вход ссылка – Кракен маркетплейс — официальная площадка с товарами и сервисами.
кракен зеркалооткрывает прямой путь в маркет. Найдите актуальную ссылку, следуйте подсказкам и получите безопасный доступ к сайту с полным функционалом.
кракен сайт вход – Кракен онион обеспечивает прямой доступ даже при ограничениях.
кракен маркетплейс – Сегодня кракен ссылка актуальная обновлена и подходит для любых устройств.
how much do steroids cost
References:
best mass building steroids (https://btslinkita.com/@alonzoong82857?page=about)
KRAKEN ссылка через TOR открывает доступ к кракен даркнет даже при блокировках. Вход занимает минимум усилий.
кракен маркетплейс – Кракен маркетплейс — официальная площадка с товарами и сервисами.
кракен зеркало даркнет – Через кракен сайт легко попасть на площадку даже при блокировках — зеркала обновляются ежедневно.
KRAKEN маркетплейс уже давно считается одной из самых удобных и надёжных площадок. Официальный кракен официальный
работает стабильно, доступ не пропадает, а зеркала всегда обновляются вовремя. Поддержка отвечает быстро,
решает спорные моменты честно. Покупки проходят без задержек, криптоплатежи принимаются моментально. Многие отмечают и ассортимент — здесь можно найти как привычные сервисы, так и редкие товары. Всё это делает KRAKEN местом, которому доверяют тысячи пользователей.
Девушка приехала без задержек, выглядела невероятно. Очень нежная, внимательная и страстная одновременно. Провели время так, что хотелось бы повторить снова и снова. Обязательно попробуйте, индивидуалка заказать Новосиб, https://sibirki3.vip/. Девушка просто огонь, эмоции зашкаливали.
uses of anabolic steroids
References:
what are steroids for Bodybuilding (https://gitea.cybs.io/curtismccurry)
KRAKEN кракен тор— это безопасный способ войти через TOR. Рабочая ссылка позволяет подключиться анонимно и пользоваться маркетплейсом.
кракен маркет ссылка – Выбирайте кракен сайт вход — это безопасное подключение и удобный вход 24/7.
Официальное кракен онионпомогает всегда оставаться в сети. Вход выполняется быстро, а маркет открывается полностью.
активные подписчики в тг канал
кракен ссылка через тор – Рабочая кракен тор ссылка помогает обходить блокировки и входить быстро.
KRAKEN сайт даёт возможность подключаться с любых устройств. Рабочая ссылка открывает кракен ссылка без ограничений.
кракен тор даркнет – Берите только кракен ссылка актуальная — так вход будет безопасным.
Журналистское расследование, посвящённое KRAKEN маркетплейсу, выявило одну ключевую деталь: кракен вход демонстрирует редкий баланс между удобством, безопасностью и широтой ассортимента. В отличие от конкурентов,
поддерживает постоянную работу зеркал и доступность сервиса. Поддержка отвечает быстро, арбитраж минимизирует риски, а репутация ресурса формировалась годами. Всё это подтверждает устойчивый статус KRAKEN как надёжного онлайн рынка, востребованного среди пользователей, ценящих стабильность и качество.
кракен ссылка darknet – Кракен ссылка актуальная — стабильный вариант обхода блокировок.
Чтобы не терять доступ, сохраняйте актуальную KRAKEN ссылка. Рабочее зеркало кракен онион открывает маркет и личный кабинет.
кракен зеркало актуальное – Выбирайте кракен вход в личный кабинет — это удобство и безопасность.
как накрутить подписчиков в телеграм
Журналистское расследование, посвящённое KRAKEN маркетплейсу, выявило одну ключевую деталь:
демонстрирует редкий баланс между удобством, безопасностью и широтой ассортимента. В отличие от конкурентов, маркет кракен ссылка поддерживает постоянную работу зеркал и доступность сервиса. Поддержка отвечает быстро, арбитраж минимизирует риски, а репутация ресурса формировалась годами. Всё это подтверждает устойчивый статус KRAKEN как надёжного онлайн рынка, востребованного среди пользователей, ценящих стабильность и качество.
накрутить подписчиков в тг
кракен ссылка darknet – Кракен официальный сайт всегда гарантирует актуальные ссылки и рабочие зеркала.
KRAKEN официальный сайт всегда снабжён инструкциями для пользователей. Рабочая кракен торгарантирует доступ в личный кабинет без проблем.
Журналистское расследование, посвящённое KRAKEN маркетплейсу, выявило одну ключевую деталь:
демонстрирует редкий баланс между удобством, безопасностью и широтой ассортимента. В отличие от конкурентов, кракен как зайти поддерживает постоянную работу зеркал и доступность сервиса. Поддержка отвечает быстро, арбитраж минимизирует риски, а репутация ресурса формировалась годами. Всё это подтверждает устойчивый статус KRAKEN как надёжного онлайн рынка, востребованного среди пользователей, ценящих стабильность и качество.
кракен как зайти – Используйте кракен онион, чтобы работать без риска блокировок.
кракен ссылка через тор – Выбирайте кракен маркетплейс — это проверенный доступ и надёжная работа.
KRAKEN маркетплейс уже давно считается одной из самых удобных и надёжных площадок. Официальный
работает стабильно, доступ не пропадает, а зеркала всегда обновляются вовремя. Поддержка отвечает быстро, кракен зеркало решает спорные моменты честно. Покупки проходят без задержек, криптоплатежи принимаются моментально. Многие отмечают и ассортимент — здесь можно найти как привычные сервисы, так и редкие товары. Всё это делает KRAKEN местом, которому доверяют тысячи пользователей.
KRAKEN официальный сайт поддерживает зеркала для обхода блокировок. Вход через кракен маркетплейс выполняется моментально.
Журналистское расследование, посвящённое KRAKEN маркетплейсу, выявило одну ключевую деталь:
демонстрирует редкий баланс между удобством, безопасностью и широтой ассортимента. В отличие от конкурентов, кракен зеркало поддерживает постоянную работу зеркал и доступность сервиса. Поддержка отвечает быстро, арбитраж минимизирует риски, а репутация ресурса формировалась годами. Всё это подтверждает устойчивый статус KRAKEN как надёжного онлайн рынка, востребованного среди пользователей, ценящих стабильность и качество.
кракен маркетплейс официальный сайт – Кракен онион обеспечивает прямой доступ даже при ограничениях.
кракен зеркало сайта – Кракен зеркало рабочее — быстрый и стабильный способ доступа.
С помощью кракен даркнет можно легко получить рабочий вход даже на телефоне.
кракен как зайти – Через кракен маркетплейс можно покупать и подключаться через рабочие зеркала.
кракен зеркало тор – Сегодня кракен ссылка актуальная обновлена и подходит для любых устройств.
Чтобы быстро попасть на кракен зеркалосайт, используйте проверенную ссылку. Рабочее зеркало доступно для входа в маркетплейс, а инструкция поможет без лишних шагов.
кракен тор даркнет – Кракен сайт вход — лучший вариант для авторизации и работы в личном кабинете.
Журналистское расследование, посвящённое KRAKEN маркетплейсу, выявило одну ключевую деталь:
демонстрирует редкий баланс между удобством, безопасностью и широтой ассортимента. В отличие от конкурентов, кракен только через тор поддерживает постоянную работу зеркал и доступность сервиса. Поддержка отвечает быстро, арбитраж минимизирует риски, а репутация ресурса формировалась годами. Всё это подтверждает устойчивый статус KRAKEN как надёжного онлайн рынка, востребованного среди пользователей, ценящих стабильность и качество.
С помощью кракен зеркало можно легко получить рабочий вход даже на телефоне.
сайт кракен зеркало – Кракен официальный сайт всегда гарантирует актуальные ссылки и рабочие зеркала.
KRAKEN маркетплейс уже давно считается одной из самых удобных и надёжных площадок. Официальный кракен сайт
работает стабильно, доступ не пропадает, а зеркала всегда обновляются вовремя. Поддержка отвечает быстро,
решает спорные моменты честно. Покупки проходят без задержек, криптоплатежи принимаются моментально. Многие отмечают и ассортимент — здесь можно найти как привычные сервисы, так и редкие товары. Всё это делает KRAKEN местом, которому доверяют тысячи пользователей.
https://device-rf.ru/
health consequences of steroids
References:
hth steroids (https://cutenite.com/@ruhmanuel44314)
Чтобы не терять доступ, сохраняйте актуальную KRAKEN ссылка. Рабочее зеркало кракен маркет открывает маркет и личный кабинет.
Заботьтесь о здоровье сосудов ног с профессионалом! В группе «Заметки практикующего врача-флеболога» вы узнаете всё о профилактике варикоза, современных методиках лечения (склеротерапия, ЭВЛО), УЗИ вен и точной диагностике. Доверяйте опытному врачу — ваши ноги заслуживают лучшего: https://phlebology-blog.ru/
накрутка подписчиков в тг канал дешево
быстрая накрутка подписчиков в телеграм
кракен ссылка актуальная – Быстрый кракен вход в личный кабинет работает на телефоне и ПК.
кракен маркетплейс вход – Берите только кракен ссылка актуальная — так вход будет безопасным.
https://plenka-okna.ru/
кракен тор ссылка – Кракен вход в личный кабинет — надёжный способ доступа к сервисам.
накрутка активных подписчиков в телеграм
кракен ссылка darknet – Кракен официальный сайт зеркало — быстрый способ подключиться и продолжать работу.
как зайти на кракен с телефона – Кракен онион — это доступ через TOR с полной анонимностью.
hiv positive bodybuilder
References:
growth hormone steroids, https://github.bigdatatech.vn/chaunceysevers,
накрутка подписчиков в телеграм канал
what do steroids
References:
https://git.cbrx.io/florianmoore93
https://www.wildberries.ru/catalog/183263596/detail.aspx
Google This site has strong energy,
design feels smooth and welcoming.
rosetemplates – Their style stands out, quality templates deliver real value to users.
banehmagic – Users will appreciate this brand’s innovative services and friendly approach.
sunnyflowercases – Loading is fast and previews are sharp, which is great for shopping.
apkcontainer – Always a plus when a site is mobile-friendly and responsive for me.
banehmagic – The brand feels magical, creative energy and reliability combined beautifully.
adawebcreative – Overall this feels like a creative agency I could actually hire.
trendingnewsfeed – Comments section looks active too, always good to see user interaction.
лечение запоя краснодар
vivod-iz-zapoya-krasnodar016.ru
экстренный вывод из запоя краснодар
raspinakala – Overall, this is a beautifully executed website I’ll revisit for sure.
вывод из запоя
vivod-iz-zapoya-krasnodar016.ru
вывод из запоя круглосуточно краснодар
http://tourout.ru/
crownking88 – Contact information is easy to find, gives decent trust to visitors.
raspinakala – The visuals are striking and the site feels genuinely creative and alive.
celtickitchen – The food photos really bring the dishes to life, very inspiring stuff.
вывод из запоя круглосуточно
vivod-iz-zapoya-krasnodar017.ru
экстренный вывод из запоя краснодар
экстренный вывод из запоя
vivod-iz-zapoya-krasnodar017.ru
лечение запоя краснодар
centensports – The layout is clean and browsing feels natural and pleasant.
sunnyflowercases – Info about materials is clear, useful in making a good decision.
экстренный вывод из запоя
vivod-iz-zapoya-krasnodar018.ru
вывод из запоя цена
вывод из запоя
vivod-iz-zapoya-krasnodar018.ru
вывод из запоя краснодар
pier45attheport – The experience is calming, layout is intuitive and appearance superb.
pier45attheport – I liked the layout, everything appears polished, thoughtful and pleasant.
лечение запоя краснодар
vivod-iz-zapoya-krasnodar019.ru
лечение запоя краснодар
pier45attheport – Strong visual harmony, the design feels serene and high quality.
экстренный вывод из запоя краснодар
vivod-iz-zapoya-krasnodar019.ru
лечение запоя краснодар
Даже при давлении со стороны провайдеров, работающий адрес кракен продолжает работать. Это доказывает устойчивость площадки. Многие выбирают её именно за это.
вывод из запоя круглосуточно краснодар
vivod-iz-zapoya-krasnodar019.ru
вывод из запоя круглосуточно краснодар
Постоянные блокировки не мешают, если у тебя есть АНКОР. Рабочие зеркала обновляются вовремя, и маркет продолжает функционировать. Поэтому ресурс удерживает репутацию надёжного.
вывод из запоя цена
vivod-iz-zapoya-krasnodar020.ru
вывод из запоя краснодар
Если нужен личный кабинет, рабочий вход в личный кабинет кракен решает проблему. Он сразу переводит на рабочую версию без ошибок. Это экономит время и нервы.
вывод из запоя цена
vivod-iz-zapoya-krasnodar020.ru
лечение запоя
Каждый раз, когда меняется адрес, вход в личный кабинет кракен сразу даёт рабочую ссылку. Это упрощает жизнь пользователям. Они знают, что маркет не исчезнет.
вывод из запоя круглосуточно
vivod-iz-zapoya-krasnodar020.ru
вывод из запоя круглосуточно
Для новичков проще всего начать с зеркало кракен без блокировок. Он ведёт на официальный ресурс, где всё открывается без ошибок. Так снижаются риски нарваться на фейк.
Неотложная наркологическая помощь — это существенная часть в борьбе зависимостей. На сайте vivod-iz-zapoya-krasnoyarsk016.ru вы можете получить сведения о круглосуточной поддержке, которая предлагает необходимую поддержку. Наркологическая служба обеспечивает медицинскую помощь при наркотиках и алкоголизме. Специалисты оказывают консультационные услуги нарколога, а также обеспечивают лечение без раскрытия личных данных. В рамках кризисной интервенции возможны реабилитационные программы и госпитализация. Психологическая поддержка играет важную роль в восстановлении после зависимости. Обратитесь за помощью незамедлительно, измените свою жизнь к лучшему!
Анонимная помощь при зависимостях — это необходимый шаг для пациентов с проблемами зависимости. На сайте vivod-iz-zapoya-krasnoyarsk016.ru можно узнать подробности о способах борьбы с зависимостями, реабилитации и ресурсах. Лечение без раскрытия личности позволяет пациентам обращаться за помощью без боязни осуждения.Специализированные услуги нарколога включают выведение токсинов, психологическое консультирование и кризисную интервенцию. Реабилитационные программы часто включает поддерживающие группы, что усиливает процесс восстановления. Профилактика зависимости также играет значимую роль, обеспечивая постоянное благополучие. Консультации помогут разобраться в проблемах и разработать стратегии выхода. Помощь для людей с зависимостями доступна и эффективна, даже если они не хотят делиться своими переживаниями.
masquepourvous – I’m impressed by their aesthetic, site leaves a lasting soft impression.
Если нужен личный кабинет, работающий адрес кракен решает проблему. Он сразу переводит на рабочую версию без ошибок. Это экономит время и нервы.
Основное преимущество — кракен ссылка для телефона обновляется быстрее других источников. Люди не теряют времени на поиск, всё уже доступно. Это и делает сервис удобным.
Капельницы от запоя на дому — является эффективным способом очищения организма при лечении алкоголизма . Анонимный нарколог на дом в Красноярске предлагает услуги по проведению капельниц, что дает возможность оперативно восстановить здоровье. Состав капельницы включает в себя медикаментов , которые способствуют устранению симптомов запойного алкоголизма , таких как обезвоживание и интоксикация . Нарколог на дом анонимно Красноярск. Ключевые компоненты капельницы: солевой раствор для восполнения жидкости, глюкоза для энергии, витамины группы В для улучшения обмена веществ и специальные медикаменты для снятия абстинентного синдрома ; лекарства для капельницы подбираются индивидуально , в зависимости от состояния пациента. Лечение на дому под наблюдением нарколога обеспечивает анонимное лечение , что существенно для многих зависимых от алкоголя. Семейная поддержка во время запоя играет ключевую роль в успешном восстановлении . Обращение к наркологу поможет определить следующие шаги, включая программы реабилитации для алкоголиков и восстановление после запоя .
masquepourvous – The products here look stylish and the vibe feels elegant.
Для тех, кто пользуется TOR, как зайти на кракен маркетплейс становится лучшим решением. Через него вход остаётся анонимным, а подключение не прерывается. Такой способ давно считается самым надёжным.
Основное преимущество — официальное зеркало сайта кракен обновляется быстрее других источников. Люди не теряют времени на поиск, всё уже доступно. Это и делает сервис удобным.
dinahshorewexler – The layout is simple yet professional, which makes it inviting.
hanacapecoral – I like the structure, navigation is smooth, experience is positive.
hanacapecoral – I’ll return later, this brand gives a solid first impression.
Я заметил, что как попасть на кракен открывается быстрее других адресов. Даже при нагрузке сайт остаётся доступным. Так сохраняется постоянный трафик без перебоев.
Капельница от запоя на дому для пожилых людей в Красноярске — это ключевой элемент в лечении запоя. Нарколог на дом круглосуточно обеспечивает детоксикацию организма на дому, что является особенно важным для пожилых людей. Симптомы запоя, такие как тревожность и слабость, нуждаются в срочном лечении. Лечение алкоголизма включает использование капельниц, которые способствуют восстановлению водно-электролитного баланса. Однако необходимо учитывать риски, связанные с капельницами: аллергические реакции, осложнения при неправильном введении. Поэтому безопасность должна оставаться главным приоритетом. Помощь врача на дому избегает стресса от транспортировки пациента. Забота о пожилых людях нуждается в особом внимании, и круглосуточные услуги нарколога гарантируют необходимую поддержку. Рекомендуется следовать советам врачей для успешного восстановления после запоя.
Обычно ресурсы падают при массовых блокировках, но тор зеркало для сайта кракен этого избегает. Зеркала обновляются моментально. Это удерживает площадку в числе лидеров.
saveaustinneighborhoods – The name carries purpose, it instantly feels meaningful and important.
masquepourvous – Their tone feels intentional, visuals and words harmonize gracefully.
Нарколог на выезде — это вариант для людей, нуждающихся в поддержке, но не в состоянии или не хочет идти в медицинское учреждение. Услуги нарколога в Москве включают домашнюю консультацию, что обеспечивает анонимное лечение и комфортные условия для пациента. Процесс лечения зависимостей начинается с диагностики и облегчения симптомов абстиненции. vivod-iz-zapoya-krasnoyarsk017.ru Квалифицированные специалисты предлагают услуги нарколога, которая включает медицинскую помощь при алкоголизме и психотерапевтические сеансы при зависимостях. Процесс реабилитации наркозависимых также возможна на домашних условиях, что дает возможность вовлечь близких в процесс поддержки. Профилактика рецидивов и постоянная поддержка имеют решающее значение для успешного выздоровления. Посещение врача-нарколога на дому может стать первым шагом к здоровой жизни.
sjydtech – Their layout is sharp, navigation feels intuitive and efficient today.
jonathanfinngamino – Just checked it today, and honestly the vibe feels professional.
Я заметил, что как зайти через TOR кракен открывается быстрее других адресов. Даже при нагрузке сайт остаётся доступным. Так сохраняется постоянный трафик без перебоев.
libertycadillac – I’d share this with friends since it looks reliable and classy.
Для новичков проще всего начать с ссылка на тор-версию кракен. Он ведёт на официальный ресурс, где всё открывается без ошибок. Так снижаются риски нарваться на фейк.
geteventclipboard – Honestly, the overall design feels modern, clean, and very professional.
reindeermagicandmiracles – My first impression is that this brand feels warm and genuine.
brucknerbythebridge – I enjoy how clean and modern the site feels overall.
Медикаментозное лечение алкоголизма в Красноярске становится все более востребованным. Врач нарколог на дом в Красноярске предлагает различные методы терапии зависимости‚ включая очистку организма‚ а также подбор медикаментов. Анонимное лечение позволяет пациентам чувствовать себя комфортно‚ получая поддержку специалистов. врач нарколог на дом Красноярск Консультация специалиста обязательна для выбора оптимальной программы реабилитации. Кодирование как способ лечения алкоголизма – также эффективный способ борьбы с зависимостью. Поддержка психолога также оказывает значительное влияние в реабилитации после алкоголизма. Услуги нарколога включают в себя медицинские услуги по лечению алкоголизма‚ что способствует успешному лечению и возвращению к нормальной жизни.
sjydtech – Very good user experience, functionality and look are well balanced.
Охранные системы видеонаблюдения монтаж https://vcctv.ru
Для доступа через телефон тоже удобнее заходить по вход кракен без блокировок. Так вход остаётся простым и безопасным. А блокировки не мешают пользоваться маркетом.
Детоксикация и капельницы от запоя – важные способы в борьбе с алкогольной зависимостью. В городе Красноярске услуги по лечению запоя включают в себя капельницы, которые помогают быстро вывести токсины из организма. Капельница включает препараты для восстановления водно-электролитного баланса и устранения симптомов абстиненции, что поддерживает терапию запоя. лечение запоя Красноярск Детоксикация также является многогранным процессом, который включает не только физическую очистку, но и психологическую помощь пациентов. В клиниках лечения алкоголизма в Красноярске используются оба метода: капельницы для острого состояния и программы реабилитации после лечения запоя. Это помогает в избавлении от зависимости и восстановлении здоровья. Не забывайте, что медицинская помощь в этом вопросе крайне важна для успешного лечения.
safercharging – The idea behind this site feels practical and really important.
skibumart – Great mix of artistic style and user experience here.
Лечение запоя в Красноярске требует комплексного подхода. Врач нарколог на дом Красноярск предлагает услуги‚ которые включают лечение запоя и медицинскую реабилитацию. Индивидуальный подход к лечению и консультация врача нарколога способствуют пониманию психологии зависимостей. Важно обеспечить поддержку семьи‚ что способствует профилактике рецидивов. Реабилитационный центр в Красноярске предлагает различные программы восстановления, включая анонимное лечение алкоголизмачто способствует улучшению здоровья и психологического благополучия.
Официальные зеркало кракен сегодня помогают обходить блокировки, когда основной домен недоступен. Сервис следит за обновлениями, поэтому пользователи не остаются без входа. Это повышает лояльность.
eleanakonstantellos – The experience is pleasant, navigation intuitive, aesthetics capture attention gently.
В Холд удобно то, что материалы структурированы по темам. Есть и прогнозы, и новости, и обзоры кошельков. Курсы всегда актуальны, а статьи помогают глубже понять рынок. Это один из лучших журналов по крипте https://thehold.ru/
Заботьтесь о здоровье сосудов ног с профессионалом! В группе «Заметки практикующего врача-флеболога» вы узнаете всё о профилактике варикоза, современных методиках лечения (склеротерапия, ЭВЛО), УЗИ вен и точной диагностике. Доверяйте опытному врачу — ваши ноги заслуживают лучшего: https://phlebology-blog.ru/
Основное преимущество — зеркало для кракен маркетплейса обновляется быстрее других источников. Люди не теряют времени на поиск, всё уже доступно. Это и делает сервис удобным.
Капельница для лечения похмелья – данный метод является действительным способом лечения, который помогает быстро справиться с симптомами алкогольной интоксикации. Состояние похмелья сопровождается недостатком жидкости, что проявляется болью в голове, тошнотой и общей слабостью. Капельница включает глюкозу и электролиты, которые возвращают баланс жидкости в организме. Использование капельницы для лечения похмелья позволяет оперативно убрать неприятные ощущения, обеспечивая очищение организма. Внутривенное введение жидкости помогает ускорить восстановление организма. Капельница в домашних условиях также может быть полезна, но требуется консультация врача для правильного подбора компонентов. Существуют и народные средства: различные травы, например, мяту или зверобой, которые помогают улучшить состояние. Однако капельница остается наиболее эффективным методом облегчить недомогание после пьянки. На сайте vivod-iz-zapoya-krasnoyarsk018.ru можно найти информацию о разных типах капельниц и их эффекте на здоровье.
вывод из запоя круглосуточно смоленск
vivod-iz-zapoya-smolensk019.ru
вывод из запоя круглосуточно
ieeb – Honestly, this looks professional and well structured from every angle.
Многие отмечают, что доступ через анонимную сеть кракен всегда работает стабильно. Даже если один адрес закрывается, появляются новые зеркала. Это даёт уверенность, что доступ не пропадёт.
Каждый раз, когда блокируют основной сайт, альтернативное зеркало кракен остаётся в строю. Рабочие зеркала подхватывают нагрузку и не дают сервису упасть. Это и есть грамотная организация.
экстренный вывод из запоя
vivod-iz-zapoya-smolensk019.ru
вывод из запоя смоленск
Если нужен личный кабинет, кракен маркетплейс вход решает проблему. Он сразу переводит на рабочую версию без ошибок. Это экономит время и нервы.
Для аптечной сети мы приобрели оборудование для маркировки и термопринтер для самоклеящихся этикеток. Печать выполняется быстро, качество отличное. Этикетки держатся прочно, информация всегда читаема. Дополнительно установили сканеры штрих-кодов для касс. Теперь работа стала более автоматизированной и надёжной https://labelaire.ru/
На форумах часто советуют использовать онион-зеркало кракен. Там меньше всего проблем с входом, и анонимность сохраняется. Такой опыт подтверждают многие.
Я заметил, что как открыть личный кабинет кракен открывается быстрее других адресов. Даже при нагрузке сайт остаётся доступным. Так сохраняется постоянный трафик без перебоев.
%random_anchor_text%
References:
https://www.google.com.ai/url?q=https://www.valley.md/dianabol-cycle-benefits-and-risks
masquepourvous – Such a unique brand name, it sticks in my memory quickly.
Для тех, кто пользуется TOR, кракен онион адрес для входа становится лучшим решением. Через него вход остаётся анонимным, а подключение не прерывается. Такой способ давно считается самым надёжным.
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk019.ru
вывод из запоя круглосуточно смоленск
вывод из запоя
vivod-iz-zapoya-smolensk020.ru
вывод из запоя смоленск
Даже при давлении со стороны провайдеров, инструкция по входу кракен продолжает работать. Это доказывает устойчивость площадки. Многие выбирают её именно за это.
what does a steroid look like
References:
https://www.credly.com/users/giantmaid9
лечение запоя смоленск
vivod-iz-zapoya-smolensk020.ru
лечение запоя смоленск
eleanakonstantellos – Beautiful design touches, content feels personal, aesthetic is very consistent.
Многие отмечают, что ссылка на кракен маркет всегда работает стабильно. Даже если один адрес закрывается, появляются новые зеркала. Это даёт уверенность, что доступ не пропадёт.
dietzmann – The experience is reliable, content and visuals are well balanced.
Smart crypto trading https://terionbot.com with auto-following and DCA: bots, rebalancing, stop-losses, and take-profits. Portfolio tailored to your risk profile, backtesting, exchange APIs, and cold storage. Transparent analytics and notifications.
Для новичков проще всего начать с как попасть на кракен. Он ведёт на официальный ресурс, где всё открывается без ошибок. Так снижаются риски нарваться на фейк.
Официальные доступ через анонимную сеть кракен помогают обходить блокировки, когда основной домен недоступен. Сервис следит за обновлениями, поэтому пользователи не остаются без входа. Это повышает лояльность.
themacallenbuilding – Just visited today, and honestly it looks really professional overall.
Удобнее всего заходить через вход в личный кабинет кракен, потому что он проверенный. На таких зеркалах меньше всего рисков нарваться на фейк. Пользователи ценят именно эту стабильность.
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk021.ru
экстренный вывод из запоя
anabolic supplements review
References:
https://git.bigtravelchat.com/jancherry46653
вывод из запоя
vivod-iz-zapoya-smolensk020.ru
экстренный вывод из запоя смоленск
muralspotting – Feels like a place where creativity is celebrated and shared.
bigprintnewspapers – Pages loaded quickly, which makes the browsing experience much smoother.
Основное преимущество — вход через онион кракен обновляется быстрее других источников. Люди не теряют времени на поиск, всё уже доступно. Это и делает сервис удобным.
reinspiregreece – The concept feels uplifting, really inspiring and hopeful overall.
goestotown – Honestly, the presentation feels modern, simple, and very user friendly.
tatumsounds – Very clean interface, design complements their musical identity perfectly.
dankglassonline – Overall impression is positive, modern, and well thought-out.
cepjournal – I like how professional and trustworthy the site feels overall.
cnsbiodesk – Overall, it feels precise, professional, and very informative.
Даже при давлении со стороны провайдеров, альтернативный адрес сайта кракен продолжает работать. Это доказывает устойчивость площадки. Многие выбирают её именно за это.
lastminute-corporate – First impression is reliable, looks useful for urgent corporate needs.
momoanmashop – The name itself feels unique and fun, matches the site.
answermodern – I’ll revisit this site, it feels trustworthy, fresh and well curated.
prolonged use of steroids causes
References:
https://maps.google.fr/url?q=https://www.valley.md/dianabol-cycle-benefits-and-risks
themacallenbuilding – Navigation is smooth, everything appears exactly where I expected it.
crownaboutnow – Their visuals are sharp, layout feels balanced and professional overall.
KRAKEN давно укрепил репутацию, а тор зеркало для сайта кракен стал частью этой стабильности. Пользователи знают: через него можно безопасно зайти. И доверие к площадке только растёт.
dietzmann – I like how clean layout is, content presented with clarity.
dietzmann – The experience is reliable, content and visuals are well balanced.
Для новичков проще всего начать с как попасть в кракен маркетплейс. Он ведёт на официальный ресурс, где всё открывается без ошибок. Так снижаются риски нарваться на фейк.
biotecmedics – Everything loads quickly, making the experience smooth and efficient.
brahmanshome – The structure feels neat and well-arranged for visitors.
goestotown – The name is catchy, and the site feels really lively.
momoanmashop – I like the bright vibe, it feels warm and approachable.
На форумах часто советуют использовать доступ через анонимную сеть кракен. Там меньше всего проблем с входом, и анонимность сохраняется. Такой опыт подтверждают многие.
haskdhaskdjaslkds – I’m not confident recommending this—needs much more work.
вывод из запоя круглосуточно
cnsbiodesk – The vibe feels trustworthy, with a clear focus on research.
geomatique237 – The domain name is unique, the site feels experimental and intriguing.
Даже при давлении со стороны провайдеров, зеркало кракен без блокировок продолжает работать. Это доказывает устойчивость площадки. Многие выбирают её именно за это.
reinspiregreece – I’ll return often, this feels like a space filled with inspiration and beauty.
bigprintnewspapers – The brand projection seems serious, visuals support the message strongly.
экстренный вывод из запоя
vivod-iz-zapoya-smolensk021.ru
вывод из запоя смоленск
Промышленное оборудование и станки под ключ
Даже при давлении со стороны провайдеров, доступ через анонимную сеть кракен продолжает работать. Это доказывает устойчивость площадки. Многие выбирают её именно за это.
В компании СтройСинтез мы заказали дом в скандинавском стиле под ключ. Архитекторы предложили удобное решение, а строители воплотили проект в жизнь без задержек. Получился стильный и просторный дом, в котором приятно жить. Очень довольны результатом – https://stroysyntez.com/
https://www.wildberries.ru/catalog/249860602/detail.aspx
dankglassonline – The design gives off a fresh, modern, and stylish feel.
Когда возникают блокировки, официальные ссылка на кракен маркет спасают ситуацию. Они открываются без задержек и позволяют заходить в личный кабинет без проблем. Так пользователи не теряют связь с площадкой.
muralspotting – I like how interactive and visually engaging the site appears.
crownaboutnow – I’ll check this again, site gives a confident and friendly presence.
crownaboutnow – The overall feel is polished, brand identity is clear and strong.
cepjournal – The site feels professional, informative, and very well-structured overall.
Если нужен личный кабинет, онион адрес кракен маркетплейса решает проблему. Он сразу переводит на рабочую версию без ошибок. Это экономит время и нервы.
Для доступа через телефон тоже удобнее заходить по кракен онион адрес для входа. Так вход остаётся простым и безопасным. А блокировки не мешают пользоваться маркетом.
themacallenbuilding – Honestly, I love the presentation, it feels sleek and elegant.
haskdhaskdjaslkds – Feels experimental, maybe in beta; many elements are still under construction.
haskdhaskdjaslkds – Some parts feel interesting, but overall it’s confusing to visitors.
{Капельница от запоя на дому: как избежать повторного срыва (владимир)|{Лечение запоя на дому: капельница и профилактика срыва (владимир)|{Капельницы от запоя на дому: ключ к успешной реабилитации (владимир)}} {Алкогольная зависимость – это серьезная проблема‚ требующая быстрой реакции.|Проблема алкогольной зависимости требует оперативного вмешательства.|Алкогольная зависимость является важной проблемой‚ которая нуждается в незамедлительном решении.} {Нарколог на дом срочно|Срочный нарколог на дом|Наркологические услуги на дому} {предоставляет наркологические услуги‚ включая капельницы для быстрого восстановления.|предлагает услуги по лечению‚ включая капельницы для быстрого восстановления организма.|обеспечивает лечение алкоголизма‚ включая капельницы для скорейшего восстановления.} {При запое важно не только лечение на дому‚ но и профилактика срыва.|Важно помнить‚ что при запое необходимо не только лечение‚ но и профилактика рецидивов.|Лечение на дому при запое должно включать как терапию‚ так и профилактические меры против срывов.} {Медицинская капельница помогает детоксифицировать организм‚ облегчая симптомы абстиненции.|Капельница способствует детоксикации и облегчает симптомы абстиненции.|Капельница играет важную роль в детоксикации организма и уменьшении симптомов абстиненции.} {Срочная помощь специалистов включает в себя не только физическое восстановление‚ но и психологическую помощь.|Помощь специалистов охватывает как физическое‚ так и психологическое восстановление.|Специалисты предоставляют не только физическую помощь‚ но и поддержку на психологическом уровне.} {Поддержка родственников также играет ключевую роль‚ способствуя успешной реабилитации алкоголиков;|Важность поддержки со стороны близких неоспорима‚ так как она содействует успешной реабилитации.|Родные играют важнейшую роль в процессе реабилитации‚ способствуя успеху лечения.} {Detox программа поможет избежать повторного срыва и обеспечит безопасное лечение.|Программа детоксикации поможет предотвратить рецидивы и обеспечит безопасное лечение.|Детокс-программа предотвращает срывы и гарантирует безопасность лечения.} {Обратитесь к наркологу на дом‚ чтобы получить комплексную помощь и вернуться к нормальной жизни.|Свяжитесь с наркологом на дом для получения комплексной помощи и возвращения к полноценной жизни.|Не откладывайте‚ обратитесь к наркологу на дом за комплексной помощью и начните новую жизнь.}
casa-nana – Overall, it feels friendly, cozy, and very pleasant to visit.
На форумах часто советуют использовать как попасть в кракен маркетплейс. Там меньше всего проблем с входом, и анонимность сохраняется. Такой опыт подтверждают многие.
geomatique237 – I’m curious about their purpose, the site hints at bigger potential.
geomatique237 – I found the design unusual, navigation is adventurous yet somewhat rough.
cnsbiodesk – Everything loads smoothly, making navigation simple and efficient here.
cnsbiodesk – The layout feels modern, professional, and user-friendly overall.
Я заметил, что проверенное зеркало кракен сегодня открывается быстрее других адресов. Даже при нагрузке сайт остаётся доступным. Так сохраняется постоянный трафик без перебоев.
momoanmashop – Browsing was smooth, everything loads quickly without any issues.
Детоксикация от алкоголя в владимире: профессиональная помощь Проблема алкогольной зависимости требует опытного подхода и квалифицированной помощи. владимир предлагает множество услуг для детоксикации и борьбы с алкогольной зависимостью. Наркологическая помощь в владимире включает медицинскую детоксикацию, что позволяет безопасно вывести токсины из организма. помощь нарколога владимир В владимире доступны реабилитационные программы, включающие поддержку наркологов, психологическую помощь во время детоксикации и консультации по алкоголизму. Необходимо понимать, что успешное восстановление после алкоголизма требует комплексного подхода, включая лечение зависимости от алкоголя. В владимире функционируют клиники, предлагающие профессиональную помощь в лечении алкоголизма и обеспечивающие необходимую поддержку. Важно не затягивать с обращением за помощью; сделайте первый шаг к здоровой жизни уже сегодня.
answermodern – Their voice comes through clearly, design supports the message well.
answermodern – Their voice comes through clearly, design supports the message well.
Для новичков проще всего начать с ссылка на тор-версию кракен. Он ведёт на официальный ресурс, где всё открывается без ошибок. Так снижаются риски нарваться на фейк.
cangjigedh – I keep finding new details here, definitely worth checking again.
ceriavpn – The service feels reliable, connection speed is smooth and steady.
azhyxh – The site gives a neat impression, very pleasant to explore.
alusstore – Great platform, definitely worth coming back for another look.
Основное преимущество — адрес для анонимного входа кракен обновляется быстрее других источников. Люди не теряют времени на поиск, всё уже доступно. Это и делает сервис удобным.
local-website – I enjoyed scrolling here, everything feels easy and functional.
yyap16 – Looks professional yet simple, which is always a good balance.
eljiretdulces – The site feels lively and welcoming, I enjoyed scrolling today.
newbalance550 – Pages load quickly, perfect for checking styles without any delays.
fghakgaklif – The overall look is clean and minimal, very user-friendly style.
Если смотришь на отзывы, почти все упоминают проверенные адреса кракен для входа. Люди реально пользуются и отмечают удобство. Значит, система работает как задумано.
flmo1xt – The pages load quickly, giving a seamless experience all the way.
В наше время безопасность персональных данных и приватность онлайн делаются все более актуальными. Если вы хотите оставаться анонимным в сети‚ необходимо прибегать к сервисы для анонимности‚ такие как VPN-сервисы и прокси-сервисы‚ которые дадут возможность замаскировать вашу личность и скрыть ваш IP-адрес. Данные инструменты предоставляют защиту соединения‚ что укрепляет безопасность в интернете и невидимость ваших действий. Также вы получите возможность обходить блокировки и посещать сайты без необходимости регистрации. Безопасность информации становится важной частью незаметного интернет-серфинга‚ что позволяет сохранять анонимность. vivod-iz-zapoya-vladimir022.ru
Когда возникают блокировки, официальные рабочее зеркало сайта кракен спасают ситуацию. Они открываются без задержек и позволяют заходить в личный кабинет без проблем. Так пользователи не теряют связь с площадкой.
wcbxhmsdo8nr – Navigation is straightforward, I didn’t run into any confusion.
t643947 – The platform gives a modern vibe, simple but really effective design.
360view – The design feels fresh and polished, I liked the style.
aaccc2 – Overall functionality works well, reliable browsing.
x3137 – Navigation was simple, I didn’t have any issues at all.
Смотри, в отличие от временных сайтов, тор зеркало для сайта кракен реально держится годами. Это редкость для даркнет-маркетов. Именно поэтому к площадке такое внимание.
xxfh – The layout is simple yet effective, nothing feels overwhelming here.
Для нас SEO продвижение стало лучшей инвестицией. Потратили меньше, чем на рекламу, а эффект оказался долгосрочным. Сайт занимает топовые позиции и стабильно приводит клиентов – https://mihaylov.digital/
Капельница от запоя – является важным этапом в лечение алкогольной зависимости. В владимире наркология предлагают помощь нарколога‚ который проведет детоксикацию организма. Признаки запоя‚ включая тревога и потливость‚ способны вызывать к серьезным осложнениям в результате запоя. Капельница способствует восстановить водно-электролитный баланс и улучшить здоровье после запоя. помощь нарколога владимир После процедуры важно посетить реабилитацию и получить психологическую поддержку. Консультация специалиста в области наркологии поможет избежать рецидивов. Профилактика рецидива включает в себя обучение и поддержку‚ что способствует восстановлению организма. Медицинская помощь в борьбе с алкоголизмом в владимире предоставляется и обладает высокой эффективностью‚ помогая пациентам вернуться к нормальной жизни.
Официальные кракен маркетплейс ссылка помогают обходить блокировки, когда основной домен недоступен. Сервис следит за обновлениями, поэтому пользователи не остаются без входа. Это повышает лояльность.
Удобнее всего заходить через альтернативное зеркало кракен, потому что он проверенный. На таких зеркалах меньше всего рисков нарваться на фейк. Пользователи ценят именно эту стабильность.
fghakgaklif – Navigation feels simple and direct, no confusion moving around.
KRAKEN давно укрепил репутацию, а адрес для анонимного входа кракен стал частью этой стабильности. Пользователи знают: через него можно безопасно зайти. И доверие к площадке только растёт.
rwbj – Browsing here feels quick and effortless, I really enjoyed it.
rwbj – The layout feels clean and polished, very user-friendly overall.
лечение запоя смоленск
vivod-iz-zapoya-smolensk021.ru
вывод из запоя цена
alusstore – The design is straightforward yet attractive, great balance overall.
alusstore – Browsing products was simple, everything is clearly displayed and easy.
local-website – The site feels simple and friendly, very easy to explore.
KRAKEN давно укрепил репутацию, а вход через онион кракен стал частью этой стабильности. Пользователи знают: через него можно безопасно зайти. И доверие к площадке только растёт.
azhyxh – The overall vibe is professional, I appreciate the thoughtful layout.
Для новичков проще всего начать с вход в личный кабинет кракен. Он ведёт на официальный ресурс, где всё открывается без ошибок. Так снижаются риски нарваться на фейк.
aaccc2 – Overall a good, simple, and efficient website experience.
aaccc2 – Overall a good, simple, and efficient website experience.
Смотри, в отличие от временных сайтов, альтернативный адрес сайта кракен реально держится годами. Это редкость для даркнет-маркетов. Именно поэтому к площадке такое внимание.
Круглосуточная наркологическая помощь в владимире предоставляется. Если у вас имеет проблемы с зависимостяминеобходимо помнитьчто доступна неотложная помощь. Наркологический центр предоставляет услуги нарколога на домуа также конфиденциальное лечение зависимостей. Консультация врача-нарколога поможет определить необходимую терапию зависимостей. Реабилитационная клиника предоставляет очистку организма и поддержку пациентов на всех этапах лечения. За подробной информацией обращайтесь на vivod-iz-zapoya-vladimir022.ru.
Если смотришь на отзывы, почти все упоминают войти в кракен через TOR. Люди реально пользуются и отмечают удобство. Значит, система работает как задумано.
Мы заказали кухонный гарнитур в Кухни в Дом и были приятно удивлены подходом. Всё организовано грамотно и профессионально, а кухня получилась очень удобной и красивой – https://kuhni-v-dom.ru/
Каждый раз, когда меняется адрес, рабочее зеркало сайта кракен сразу даёт рабочую ссылку. Это упрощает жизнь пользователям. Они знают, что маркет не исчезнет.
Lucky Mate is an online casino for Australian players, offering pokies, table games, and live dealer options. It provides a welcome bonus up to AUD 1,000, accepts Visa, PayID, and crypto with AUD 20 minimum deposit, and has withdrawal limits of AUD 5,000 weekly. Licensed, it promotes safe play https://allianzhealth.co.uk/stockx-co-nz/understanding-the-regulatory-environment-for-australian-players-at-lucky-mate-casino/
Обращение к наркологу анонимно — необходимый шаг для тех, кто нуждается в помощи при лечении алкогольной и наркотической зависимости. На сайте vivod-iz-zapoya-vladimir024.ru вы можете обратиться за помощью и поискать наркологической помощью. Это особенно актуально для людей, страдающих от алкоголем и наркотиками. Услуги нарколога включают оценку состояния зависимостей и лечение при наркотической зависимости. Анонимный нарколог может посетить вас на дому, что обеспечивает комфорт и конфиденциальность. Выездные медработники предоставляют психологическую поддержку и проводят реабилитацию наркозависимых. Виртуальная встреча с врачом позволяет быстро получить необходимые рекомендации. Лечение наркотиков анонимно — это возможность начать новую жизнь без опасений о предвзятости. Не упустите шанс изменить свою судьбу с помощью анонимных услуг здоровья!
nnvfy – The interface feels smooth and lightweight during navigation.
Для тех, кто пользуется TOR, кракен вход мобильный становится лучшим решением. Через него вход остаётся анонимным, а подключение не прерывается. Такой способ давно считается самым надёжным.
Вызов нарколога — это необходимый шаг для людей, испытывающих проблемы с зависимостями. Служба наркологической помощи предоставляет экстренную наркологическую помощь и консультацию нарколога, что особенно необходимо в кризисных ситуациях . Признаки зависимости от наркотиков могут проявляться по-разному , и важно знать, когда необходима медицинская помощь при алкоголизме . Помощь при алкоголизме и лечение наркотической зависимости требуют квалифицированного вмешательства. Алкоголизм и его последствия могут быть разрушительными , поэтому важно обратиться за поддержкой для зависимых , включая программы реабилитации. На сайте vivod-iz-zapoya-vladimir020.ru вы можете узнать, как обратиться к наркологу или получить анонимную помощь наркоманам . Не сомневайтесь в том, чтобы позвонить в наркологическую службу, чтобы получить необходимую поддержку и помощь .
93r – Visuals are minimal, pages feel mysterious, content is sparse.
tstyhj – Very straightforward and easy-to-use site, I enjoyed checking it.
2kgq – Scrolling is fluid, nothing laggy or glitchy during my visit.
tiantianyin4 – The site loads fast and feels stable without issues.
Если смотришь на отзывы, почти все упоминают зеркало кракен для доступа. Люди реально пользуются и отмечают удобство. Значит, система работает как задумано.
66se – Navigation is smooth and responsive.
aabb49 – Mobile responsiveness appears to work fine.
Если смотришь на отзывы, почти все упоминают ссылка на официальный ресурс кракен. Люди реально пользуются и отмечают удобство. Значит, система работает как задумано.
v1av2 – The structure is well-organized, everything is easy to locate.
v1av7 – The browsing experience was seamless, no lag or delays here.
fhkaslfjlas – I didn’t notice any issues, everything loaded correctly today.
deallegria – Navigation is simple and intuitive, I found things easily.
Когда возникают блокировки, официальные онион-ссылка рабочего зеркала кракен спасают ситуацию. Они открываются без задержек и позволяют заходить в личный кабинет без проблем. Так пользователи не теряют связь с площадкой.
Анонимное прокапывание от алкоголя – это важный шаг на пути к восстановлению. На сайте vivod-iz-zapoya-vladimir023.ru можно найти информацию о методах борьбы с алкоголизмом и реабилитационных программах. Группы поддержкитакие как группа Анонимных Алкоголиков, оказывают помощь зависимым и их близким. Психотерапевтические методы помогает выходить с кризисом из-за алкоголя. Кодирование от алкоголя и рекомендации по отказу от алкоголя также могут быть полезными борьбы с зависимостью. Программы по трезвости помогают сохранить здоровье и наладить жизнь без алкоголя. Поддержка людям с алкоголизмом доступна всем, кто нуждается в ней.
1cty – Overall it’s a simple, clean, and reliable website experience.
Обычно ресурсы падают при массовых блокировках, но проверенная ссылка кракен этого избегает. Зеркала обновляются моментально. Это удерживает площадку в числе лидеров.
i1oxj – Pages opened instantly, making the whole visit seamless for me.
porn300 – Everything worked fine, I didn’t encounter any errors or glitches.
heyspin – The site loaded fast for me, really smooth browsing overall.
v1av9 – Everything functioned properly, no broken links or errors appeared.
8886611tz – Smooth user experience overall, I didn’t encounter any slowdown here.
66460 – Works fine on mobile devices, fully responsive.
Для доступа через телефон тоже удобнее заходить по инструкция по входу кракен. Так вход остаётся простым и безопасным. А блокировки не мешают пользоваться маркетом.
Для тех, кто пользуется TOR, рабочая ссылка кракен сегодня становится лучшим решением. Через него вход остаётся анонимным, а подключение не прерывается. Такой способ давно считается самым надёжным.
v1av3 – Performance stayed stable across multiple page loads.
Капельницы от запоя в владимире – это существенная медицинская помощь при алкоголизме, способствующая очищению организма. Вызов нарколога на домой дает возможность получить срочную помощь при запое в удобной обстановке. Компоненты капельницы включают вещества, которые помогают восстанавливающие организма: физраствор, витамины и препараты для капельницы. Эффект капельницы направлено на устранение симптомов абстиненции и улучшение состояния пациента. Преодоление зависимости от алкоголя требует всеобъемлющего подхода, включая реабилитацию после алкогольного кризиса. Цены на услугу нарколога различаются, но консультация специалиста будет ключевой для эффективного лечения.
Если смотришь на отзывы, почти все упоминают мобильная версия сайта кракен. Люди реально пользуются и отмечают удобство. Значит, система работает как задумано.
Даже при давлении со стороны провайдеров, актуальная ссылка кракен продолжает работать. Это доказывает устойчивость площадки. Многие выбирают её именно за это.
Официальные онион-ссылка рабочего зеркала кракен помогают обходить блокировки, когда основной домен недоступен. Сервис следит за обновлениями, поэтому пользователи не остаются без входа. Это повышает лояльность.
Если нужен личный кабинет, доступ к кракен маркетплейсу решает проблему. Он сразу переводит на рабочую версию без ошибок. Это экономит время и нервы.
other2.club – Found some cool bits here, will revisit for updates soon.
Смотри, в отличие от временных сайтов, ссылка на официальный ресурс кракен реально держится годами. Это редкость для даркнет-маркетов. Именно поэтому к площадке такое внимание.
best weight lifting supplement stacks
References:
https://ebra.ewaucu.us/index.php?page=user&action=pub_profile&id=93368
21009.xyz – A few broken links appeared as I browsed, hope they’ll fix those.
00381.xyz – The domain is curious, I enjoyed exploring its simple layout and content.
0238.org – The color palette is subtle, pleasant to look at over long sessions.
Многие отмечают, что как попасть на кракен всегда работает стабильно. Даже если один адрес закрывается, появляются новые зеркала. Это даёт уверенность, что доступ не пропадёт.
mydiving – The site layout feels calm and organized, perfect for easy reading.
Специалист по зависимостям владимир: Профессиональная помощь при зависимостях Если вы или ваши близкие имеете проблемы с зависимостью‚ важно обратиться к профессионалу. Нарколог владимир предоставляет квалифицированную медицинскую помощь‚ включая диагностику зависимости и индивидуальные консультации нарколога. В наркологической клинике доступны различные услуги‚ такие как лечение медикаментами и психотерапия. Работа с зависимостями – это комплексный и многоступенчатый процесс‚ который предполагает индивидуального подхода. Программа реабилитации включает в себя этапы‚ направленные на восстановление физического и психологического состояния пациента. Реабилитация наркозависимых также подразумевает поддержку семьи‚ что является ключевой фактором в успешном лечении. Анонимное лечение позволяет пациентам ощущать себя защищенными и свободными от предвзятости. Предотвращение зависимостей и помощь при алкоголизме – ключевые направления работы наркологов. Обратитесь на vivod-iz-zapoya-vladimir022.ru для получения дополнительной информации и записи на консультацию. Помните‚ что раннее обращение – залог успешного исцеления!
a6def2ef910.pw – I noticed a few slow elements, perhaps image sizes need optimization.
sj256.cc – Some sections look a bit sparse, but overall quite usable.
196v5e63 – I didn’t notice any bugs or broken links during my visit.
5581249.cc – On mobile it’s usable, though a few sections overlap slightly.
yilian99 – Works perfectly fine on mobile without any scaling issues.
sj440.cc – The images are crisp, adds extra professionalism to the content.
Надёжность KRAKEN держится на том, что онион-ссылка рабочего зеркала кракен всегда в сети. Это даёт ощущение защищённости и стабильности. Люди ценят такую предсказуемость.
6789138a.xyz – The minimal style is working well, gives a refined, elegant impression.
980115 – The site runs fast, smooth, and feels very responsive overall.
582388360 – The design looks minimal but works efficiently for all users.
5918222q.xyz – Navigation is okay, could improve clarity on menu items.
diwangdh77 – Browsing felt fluid and intuitive from start to finish today.
zzj186 – Mobile version fits nicely, no need for zooming or scrolling weirdly.
Для тех, кто пользуется TOR, мобильная версия сайта кракен становится лучшим решением. Через него вход остаётся анонимным, а подключение не прерывается. Такой способ давно считается самым надёжным.
yy380.cc – The responsiveness on mobile is good, didn’t run into issues.
303vip.info – I stumbled upon this site, looks like there’s some fresh content here.
В Окна СПб заказывали окна для спальни и гостиной. Всё прошло без задержек, мастера работали профессионально. Теперь в доме стало теплее и уютнее. Мы довольны работой компании https://okna-v-spb.ru/
sodo66000.xyz – Browsed this a little, it has intriguing vibe and decent layout overall.
Медикаментозное лечение алкоголизма в владимире становится особенно популярным. Нарколог‚ который выезжает на дом в владимире предоставляет разнообразные методы лечения зависимости‚ включая очистку организма‚ а также подбор медикаментов. Конфиденциальное лечение позволяет пациентам чувствовать себя комфортно‚ получая услуги профессионалов. врач нарколог на дом владимир Обращение к специалисту обязательна для определения лучшей программы реабилитации. Кодирование как способ лечения алкоголизма – также эффективный метод лечения зависимости. Эмоциональная поддержка также играет важную роль в реабилитации после алкоголизма. Услуги нарколога предоставляют медицинскую помощь при алкоголизме‚ что способствует успешному лечению и возвращению к нормальной жизни.
where to buy winstrol
References:
https://skitterphoto.com/photographers/1583774/massey-risager
Получение лицензии «под ключ» с Журавлев Консалтинг Групп включало полное сопровождение: проверку документов, контроль подачи и взаимодействие с органами контроля, что сэкономило много времени и усилий https://licenz.pro/
sh576.xyz – Layout is simple but workable, though I’d love more visuals.
liver pills bodybuilding
References:
https://bookmarks4.men/story.php?title=%E2%80%9Cd-bol-only-protocol-dianabol-cycle-overview%E2%80%9D
x3165.xyz – Found this domain surprisingly sleek, layout feels intuitive on first glance.
Лечение запоя — важная задача для многих . Симптомы запойного состояния включают зависимость от алкогольных напитков как физического, так и психологического характера. Лечение запоя может быть медикаментозной или психотерапевтической . Первым шагом является детоксикация организма , которая помогает убрать токсины . Необходимо искать помощь при алкоголизме, чтобы предотвратить серьезные последствия. narkolog-tula022.ru Лечение алкоголизма в стационаре предлагает реабилитационные программы, где пациенты могут рассчитывать на всестороннюю поддержку. Восстановление после запоя требует времени и усилий , и здесь поддержка близких играет ключевую роль. Советы по лечению запоя могут быть полезны : важно следить за состоянием здоровья , избегать провоцирующих факторов и регулярно обращаться к специалисту. Профилактические меры против запоя включает в себя здоровый образ жизни и понимание собственных проблем.
9870k.top – I like the font choice, makes reading relaxing even on small screens.
7x084yko.xyz – The footer is minimal — adding some contact or link info would improve trust.
is anabolic steroids legal
References:
http://celebratebro.in/birthdays-in-bangalore/index.php?qa=user&qa_1=swisspanty23
bestbotanicals – The site feels natural and peaceful, just like their amazing teas.
3e7r – Prices seem fair and competitive compared to similar online stores.
how much steroids cost
References:
http://yzeeed.com/index.php/user/coursechief9
частная психиатрическая помощь
psikhiatr-moskva008.ru
частный психиатр на дом
17kshu – I like the color scheme, subtle but pleasant to eyes.
captcha-kraken17at.org</a) – Some internal links lead to blank pages or errors, needs cleanup.
dersimizmuzik.org – Great resource for music lessons, helped me learn something new today.
https://ozon.ru/t/csgBrx8
bbofrwhnimpcjibfunu.live – Overall mysterious but quite promising, I’m curious to see more.
storagesheds.store – On mobile it’s usable, though some elements shift unexpectedly.
bitcoin-mining-news.website – Great niche site, provides timely updates on crypto mining trends.
businessesnewsdaily.site – Found a few broken images in posts, hope they patch those soon.
51p31.xyz – A couple of images didn’t load, hope they fix those asset links.
Складчик помогает учиться выгодно. Я участвовал в складчине по бизнесу и получил доступ быстро. Качество материалов отличное, цена минимальная. Очень доволен результатом https://v27.skladchik.org/
yt7787.xyz – A few images failed to load, perhaps broken asset links exist.
648ssss.xyz – Navigation is okay, though some links feel buried in menus.
cost of anabolic steroids
References:
https://images.google.as/url?q=https://www.asklent.com/user/peppercat3
sxy005.xyz – Load speeds are okay, though heavy pages lag a little on slow connections.
52cjg.xyz – On mobile layout adapts, but a few elements overlap a bit.
steroid vs hormone
References:
https://images.google.com.sv/url?q=https://rockchat.com/members/pocketswamp4/activity/94632/
bodybuilding dangerous
References:
https://writeablog.net/trialgray70/trenbolone-cycle-blueprint-optimal-stacking-and-dosing-for-bulk-and-cut-cycles
ylu555.xyz – On mobile a few elements overlap but it’s still usable overall.
Нарколог на выезд в Туле — это удобное решение для людей‚ которые испытывают необходимость в помощи нарколога‚ но не могут посещать медицинское учреждение. Профессиональная помощь в лечении зависимости доступна прямо на дому‚ что гарантирует удобство и анонимность.Консультация нарколога позволяет оценить ситуацию и подобрать лучший план лечения‚ включая лечение в стационаре или домашнюю терапию. Наши эксперты предлагают психотерапию зависимостей и медицинские процедуры‚ что помогает успешному лечению зависимостей. Семейная поддержка играет важную роль в лечении‚ помогая пациентам справиться с трудностями. Свяжитесь с narkolog-tula023.ru для подробной информации о предоставляемых услугах.
weopwjrpwqkjklj.top – font choices are good, reading feels pleasant even on small screens
психиатрическое лечение
psikhiatr-moskva009.ru
психиатрическую помощь в стационарных условиях
formasecoarquitectonicas – The color scheme is subtle and pleasant, feels professional enough.
xxec – Found a couple of useful resources, thanks for putting this together.
fartak – Smooth experience from mobile to desktop, no issues at all.
xxgm – Nice layout and smooth performance, makes browsing pleasant.
forextradingsystem – Great site for anyone starting forex trading, really easy to understand.
Анонимный вызов врача нарколога — необходимый шаг для людей, столкнувшихся с зависимостями при лечении алкогольной и наркотической зависимости. На сайте narkolog-tula024.ru вы можете обратиться за помощью и поискать наркологической помощью. Это особенно важно для тех, кто испытывает проблемы с алкоголем и наркотиками. Услуги нарколога включают диагностику зависимостей и медицинскую помощь при употреблении наркотиков. Анонимный нарколог может приехать на дом, что обеспечивает комфорт и конфиденциальность. Выездные специалисты предоставляют психологическую поддержку и проводят процессы реабилитации для зависимых. Виртуальная встреча с врачом позволяет незамедлительно узнать нужные советы. Лечение наркотиков анонимно — это возможность начать новую жизнь без опасений о предвзятости. Не теряйте возможности на перемены с помощью конфиденциальной медицинской помощи!
axjaognr – I’d want to see reviews or testimonials to build confidence.
set-mining.website – Overall I’d advise caution, lots of warning signs for potential scam.
aaront – The site feels sleek and inviting, nice first impression.
probuis – Found no social links yet, hope they include them later.
cooperativadeartesanos – Overall promising, curious what artisan offerings or crafts will be highlighted.
hhproduction – The images load cleanly, gives a professional and trustworthy feel.
over the counter steroids for muscle building
References:
https://codimd.fiksel.info/NV0_lm3RSPOkKeLA2B4Ymg/
t371 – On mobile it’s usable, though some buttons are a little tight.
giftd – The footer could use more links, like contact or social info.
реабилитация от алкоголя
reabilitaciya-astana007.ru
реабилитация алкоголиков цены
winstrol liver damage
References:
https://www.google.com.pk/url?q=https://justbookmark.win/story.php?title=beginner%E2%80%99s-guide-to-dianabol-how-to-cycle-stack-and-dose-correctly
sddapp – I’ll check back later, curious to see how this site develops.
fortressystemnig – Images are crisp and relevant, they boost credibility nicely.
pakopakoma – The pages load decently fast on my phone, good sign.
creadordesitios – The font choice is comfortable and easy on the eyes.
Капельница от запоя в владимире – это существенная медицинская помощь при алкоголизме, которая помогает очищению организма. Вызов нарколога на дом дает возможность получить срочную помощь при алкоголизме в комфортной обстановке. Компоненты капельницы включают вещества, способствующие восстановлению организма: физраствор, витамины и лекарства для капельницы. Действие капельницы ориентировано на устранение симптомов обстиненции и улучшение состояния пациента. Преодоление зависимости от алкоголя требует всеобъемлющего подхода, включая реабилитацию после алкогольного кризиса. Стоимость услугу нарколога варьируются, но консультация специалиста будет ключевой для эффективного лечения.
Служба наркологии — это важная часть здравоохраненияпредоставляющая помощь в лечении зависимостей и восстановление. На сайте narkolog-tula025.ru можно узнать сведения о клиниках наркологической помощи, где предоставляется помощь при алкогольной зависимости и наркотической зависимости. Психотерапевтические методики и программы реабилитации помогают пациентам вернуться к нормальной жизни, а поддержка близких играет ключевую роль в этом процессе. Также предлагаются анонимные консультации и кризисные службы для срочной помощи. Профилактика наркомании и социальная адаптация — важные аспекты работы службы наркологии.
body builders clitoris
References:
https://www.google.co.mz/url?q=https://md.darmstadt.ccc.de/nAKF-BAQQIWMqGCdsH70zg/
av07 – Hope they add blog/news or updates to keep things lively.
missouriland – On mobile it works okay, but some text is a bit small.
лечение наркоманов
reabilitaciya-astana008.ru
реабилитация от наркозависимости
sustanon deca dianabol cycle
References:
https://intensedebate.com/people/trayharbor19
Капельница для лечения запоя на дому: противопоказания и риски (Тула) Алкогольная зависимость – серьезная проблема, требующая профессионального подхода. Вызов нарколога на дом становится все более популярным методом лечения запоя. Одним из эффективных способов является инфузионная терапия, которая включает введение капельницы для выведения из запойного состояния. С помощью капельницы восстанавливается водно-электролитный баланс, улучшается общее состояние пациента и снимаются симптомы абстиненции; Важно не забывать о противопоказаниях, связанных с этой процедурой. Например, наличие аллергии на компоненты растворов, сердечно-сосудистые заболевания или острые инфекционные процессы могут стать основанием для отказа в проведении капельницы. Также могут возникнуть осложнения, такие как тромбофлебит, инфицирование вены или аллергические реакции. Таким образом, консультация нарколога перед началом лечения алкоголизма на дому является необходимостью. Безопасность данной процедуры во многом зависит от квалификации медицинского специалиста и следования всем рекомендациям. Услуги нарколога на дому в Туле предоставляют возможность получения медицинской помощи в удобной обстановке, что делает реабилитацию от запоя более эффективной.
22ee.top – Fast loading too, that’s always a plus for me.
zonaflix – The quality is surprisingly decent, haven’t seen many issues so far.
chinh-sua-anh.online – Very intuitive site, examples are helpful and workflow seems smooth.
lovemoda.store – I like the naming, “Love Moda” gives a chic vibe.
forexplatform.website – The layout looks great, but the content is even more valuable.
manchunyuan1.xyz – Content here is fresh and not just recycled information.
52ch.cc – Very useful site, I find something helpful each visit.
hentai20.biz – Design feels modern, though I wonder about moderation policies.
sexscene.info/ I am here
keledh.pw – The site is very bare now, but I sense potential in the name.
greenenvelope.org – Looks like a fresh domain, I hope they post something useful soon.
zkjcnm.top – The homepage looks minimal, gives a mysterious vibe overall.
i2gkj.xyz – Loads quickly which is a good sign for performance already.
lapotranca.store – The site feels quiet now, hoping they add solid products soon.
ipali.info – I’ll revisit this later to see how it evolves with time.
datacaller.store – Fast loading, responsive design is a plus for first impressions.
camomh.site – The blank areas could be placeholders for cool visuals later.
niubi1.xyz – The design is minimal but clean, gives a professional feel.
jinbib27.top – Good loading speed, I appreciate when sites are snappy.
реабилитация от наркозависимости в Астане
reabilitaciya-astana009.ru
реабилитационный центр для алкоголиков в Астане
Капельница для снятия запоя на дому – это необходимая помощь наркологической службы‚ позволяющая оперативно и сильно поддержать людям‚ переживающим от алкогольной зависимости. Начальная встреча с наркологом в Туле включает определение степени зависимости‚ анализ состояния пациента и разработку персонального плана терапии. Ключевые услуги нарколога на дому включают медикаментозное лечение‚ выведение из запоя‚ психотерапию при алкоголизме и реабилитационные программы. Поддержка родственников тоже влияет значимую функцию в процессе реабилитации алкоголиков. Анонимное лечение обеспечивает комфорт и защищенность пациента. помощь нарколога тула
90dprr.top – Some of the images are striking — they add a lot to the pages.
вывод из запоя круглосуточно тула
tula-narkolog007.ru
вывод из запоя цена
Алкогольная зависимость — значительная проблема‚ которая требует целостного подхода к терапии. В городе Тула имеются различные методы‚ помогающие пациентам справиться с этой зависимостью. Лечение алкоголизма начинаеться с диагностики и определения и выявления симптомов алкогольной зависимости. Необходимо пойти в наркологическую клинику для получения квалифицированной помощи. Одним из наиболее действенных способов является detox-программа‚ направленная на очистке организма от токсинов. Психологическая помощь играет ключевую роль в реабилитации пациентов. Семейная поддержка и участие в группах анонимных алкоголиков могут значительно повысить вероятность успешного выздоровления. Методы кодирования также может быть вариантом‚ которое помогает многим. Лечение зависимости включает в свой состав как медицинские‚ так и психотерапевтические методы. Советы по отказу от алкоголя и мотивация к трезвости необходимы для формирования новой жизни без спиртного. Восстановление после запоя требует терпения и времени‚ но с адекватной поддержкой это осуществимо. За подробной информацией можно обратиться на narkolog-tula028.ru.
xfj222 – The layout is clean and easy to navigate.
mhcw3kct – This site offers a unique perspective on various topics.
5xqvk – I found the articles here to be quite informative.
5680686 – The design is minimalist yet effective.
axxo.live – I like the tone here, casual yet informative and direct.
kaixin2020.live – I bookmarked this site — looks like there’s much to explore.
44lou5 – I found this page very informative and well-structured.
av07.cc – The visuals blend well with text — nice aesthetic overall.
xxfq.xyz – Nice layout, felt comfortable navigating through different sections.
bjwyipvw.xyz – Surprises at every click, definitely not your typical site.
ryla6760 – I appreciate the comprehensive information provided for RYLA participants.
675kk.top – Navigation is smooth, makes browsing easy and pleasant.
2021nikemenshoes.top – The UI is clean, adds to trust when shopping online.
warmm1.cc – The tone feels genuine, as if someone wrote from experience.
zukdfj.shop – I like these posts, feels like someone put real thought into them.
qyrhjd.top – Overall a pleasant site to browse, definitely worth keeping an eye on.
20b7f9xg.xyz – I like how clean and uncluttered the navigation is here.
пансионат для реабилитации после инсульта
pansionat-msk010.ru
пансионат для лежачих пожилых
лечение запоя
tula-narkolog008.ru
лечение запоя тула
seostream – I found the articles here to be quite informative.
лечение запоя
vivod-iz-zapoya-kaluga013.ru
экстренный вывод из запоя калуга
elipso.site – Good collection of topics, design feels clean and navigation smooth.
rinatmat – Content is well-written, very clear and engaging.
comprafacilrd – Looks trustworthy, good use of secure connections and clear product details.
wzoo – Content seems fresh and the updates are frequent.
пансионат для реабилитации после инсульта
pansionat-msk011.ru
пансионат для пожилых в москве
hpwt02n0me – Nice design and the navigation works smoothly across pages.
pacerproes – Feels professional yet approachable, good balance overall.
u888vn – Very user friendly, and the writing style is engaging too.
htechwebservice – The resources here helped me with my latest project.
ifyss – This site offers a unique perspective on various topics.
caneguida – A hidden gem for those seeking unique insights.
683tz084 – The content is well-researched and thought-provoking.
seoelitepro – This site offers a unique perspective on various topics.
iyimu – The layout is clean and easy to navigate.
h7721 – I found this site informative and quite useful overall.
экстренный вывод из запоя
tula-narkolog009.ru
вывод из запоя тула
onlineforextrading – Great to find clear explanations of complex forex topics.
вывод из запоя цена
vivod-iz-zapoya-kaluga014.ru
экстренный вывод из запоя калуга
дом престарелых
pansionat-msk012.ru
частные пансионаты для пожилых в москве
newstoday – Definitely bookmarking this, will visit daily for updates.
cyrusmining – Interface is rudimentary, seems early or possibly inactive.
wraoys – Would be nice to see a blog or “about us” to understand its purpose.
antsmarket – The name has potential (market + ants), but execution is still missing.
axin2 – Found a few helpful resources, hope they keep adding content.
лечение запоя челябинск
vivod-iz-zapoya-chelyabinsk010.ru
вывод из запоя круглосуточно челябинск
dhpb-smile – Seems like early stage, hope they build it out gradually.
saltburn – Right now it’s just a shell; content will make or break it later.
live-sex-cam – The interface works perfectly, easy to navigate and enjoyable vibes.
artvoyage – Love the artist bios and stories, adds so much depth.
liveforextrading – Great resource, charts are clear and the tools feel well made.
thefreemath – Great concept, hope they continue expanding and adding new lessons.
googlerankmaster – Sample posts seem useful, will dig deeper later.
crowltheselinks – Navigation could be improved, I got lost between pages a few times.
частный пансионат для престарелых
pansionat-tula010.ru
пансионат с деменцией для пожилых в туле
вывод из запоя круглосуточно
vivod-iz-zapoya-kaluga015.ru
вывод из запоя
shineonx – Definitely worth bookmarking, I want to see updates soon.
manchunyuan8 – The design is minimalistic, which I appreciate in a site.
capsaqiu – I saw a few pages, design’s simple and straightforward.
myzb27 – I’m curious about their purpose—hope they fill it out soon.
nowmining – Smooth interface and clear info, exactly what I was searching.
экстренный вывод из запоя челябинск
vivod-iz-zapoya-chelyabinsk011.ru
вывод из запоя цена
дом престарелых в туле
pansionat-tula011.ru
частный пансионат для пожилых людей
экстренный вывод из запоя минск
vivod-iz-zapoya-minsk010.ru
вывод из запоя минск
wexfordliteraryartsfestival – The idea of a global art registry feels like a game-changer.
whollywoodhalloween – I found some really cool costume ideas here last night.
ukrainianvictoryisthebestaward – Nice branding, hope the content supports the weight of the name.
janetfortampa – Excited to see how this evolves in the art community.
successmarketboutique – Love how they’re combining technology with art authenticity.
дом престарелых в туле
pansionat-tula012.ru
пансионат для людей с деменцией в туле
716selfiebuffalo – Friendly staff made the experience even more enjoyable.
sergiidima – A much-needed solution for artists seeking to prove their work’s authenticity.
лечение запоя челябинск
vivod-iz-zapoya-chelyabinsk012.ru
экстренный вывод из запоя
лечение запоя
vivod-iz-zapoya-minsk011.ru
вывод из запоя цена
goldmetalshop – I appreciate the transparency this site offers to artists and buyers.
dayofthedeadatx – Just explored this site; the concept of art verification is intriguing.
jadenurrea – Browsing here is a delight, can see effort in every detail.
вызов психиатра на дом в москве
psychiatr-moskva007.ru
платная консультация психиатра
лечение запоя
vivod-iz-zapoya-cherepovec013.ru
вывод из запоя круглосуточно череповец
вывод из запоя
vivod-iz-zapoya-minsk012.ru
вывод из запоя цена
частная психиатрическая помощь
psychiatr-moskva008.ru
стационар психиатрической больницы
вывод из запоя
vivod-iz-zapoya-cherepovec014.ru
лечение запоя
вывод из запоя
vivod-iz-zapoya-omsk010.ru
вывод из запоя круглосуточно
психиатр на дом для пожилого
psychiatr-moskva009.ru
консультация психиатра
экстренный вывод из запоя омск
vivod-iz-zapoya-omsk011.ru
вывод из запоя цена
лечение запоя
vivod-iz-zapoya-cherepovec015.ru
лечение запоя
госпитализация в психиатрический стационар
psikhiatr-moskva007.ru
консультация психиатра на дому в москве
https://atlan.ru/product-category/mebel/sejfy/
Sichere Lieferung Pizza hat super funktioniert. Die Pizza war hei? und lecker.
Pizza Lieferangebot
вывод из запоя омск
vivod-iz-zapoya-omsk012.ru
лечение запоя омск
вывод из запоя иркутск
vivod-iz-zapoya-irkutsk010.ru
экстренный вывод из запоя
лечение запоя
vivod-iz-zapoya-orenburg010.ru
вывод из запоя оренбург
вывод из запоя цена
vivod-iz-zapoya-irkutsk011.ru
лечение запоя иркутск
вывод из запоя круглосуточно иркутск
vivod-iz-zapoya-irkutsk012.ru
вывод из запоя иркутск
Наркологическая служба Тула предлагает разнообразные услуги для помощи людям с зависимостями. В этом городе функционируют специализированные центры реабилитации‚ где предоставляется возможность анонимного лечения от наркозависимости и алкоголизма. Программа лечения алкоголизма включает в себя как медицинские процедуры‚ так и психотерапию. narkolog-tula025.ru Психологическая помощь Тула также играет важную роль в процессе выздоровления. Консультация нарколога позволяет определить уникальные особенности пациента и составить персонализированный план лечения. Работа с родственниками и профилактика зависимостей – важная составляющая работы наркологической клиники. Реабилитация зависимых включает как терапевтические меры‚ так и социальное reintegration. Услуги наркологической службы направлены на восстановление здоровья и возвращение к полноценной жизни.
консультация психиатра круглосуточно
psikhiatr-moskva008.ru
психиатрическая помощь на дому
Вызов нарколога на дом в конфиденциальном порядке – это необходимый шаг для людей, страдающих от наркозависимости. Профессиональная помощь нарколога на дому позволяют обеспечить профессиональную помощь в удобной и защищенной обстановке. Анонимный нарколог осуществит осмотр, проанализирует состояние пациента и разработает программу лечения наркомании на месте. Это включает в себя психотерапевтическую помощь и поддержку зависимого человека. Экстренный вызов нарколога также возможен, что особенно важно в критических ситуациях. Помощь нарколога охватывает профилактические меры против зависимости и реабилитацию наркоманов, обеспечивая конфиденциальное лечение и достоверность процесса. narkolog-tula026.ru
https://katellkeinegcom.wordpress.com/
консультация психиатра круглосуточно
psikhiatr-moskva009.ru
анонимная консультация психиатра
{Капельница от запоя на дому: как избежать повторного срыва (Тула)|{Лечение запоя на дому: капельница и профилактика срыва (Тула)|{Капельницы от запоя на дому: ключ к успешной реабилитации (Тула)}} {Алкогольная зависимость – это серьезная проблема‚ требующая быстрой реакции.|Проблема алкогольной зависимости требует оперативного вмешательства.|Алкогольная зависимость является важной проблемой‚ которая нуждается в незамедлительном решении.} {Нарколог на дом срочно|Срочный нарколог на дом|Наркологические услуги на дому} {предоставляет наркологические услуги‚ включая капельницы для быстрого восстановления.|предлагает услуги по лечению‚ включая капельницы для быстрого восстановления организма.|обеспечивает лечение алкоголизма‚ включая капельницы для скорейшего восстановления.} {При запое важно не только лечение на дому‚ но и профилактика срыва.|Важно помнить‚ что при запое необходимо не только лечение‚ но и профилактика рецидивов.|Лечение на дому при запое должно включать как терапию‚ так и профилактические меры против срывов.} {Медицинская капельница помогает детоксифицировать организм‚ облегчая симптомы абстиненции.|Капельница способствует детоксикации и облегчает симптомы абстиненции.|Капельница играет важную роль в детоксикации организма и уменьшении симптомов абстиненции.} {Срочная помощь специалистов включает в себя не только физическое восстановление‚ но и психологическую помощь.|Помощь специалистов охватывает как физическое‚ так и психологическое восстановление.|Специалисты предоставляют не только физическую помощь‚ но и поддержку на психологическом уровне.} {Поддержка родственников также играет ключевую роль‚ способствуя успешной реабилитации алкоголиков;|Важность поддержки со стороны близких неоспорима‚ так как она содействует успешной реабилитации.|Родные играют важнейшую роль в процессе реабилитации‚ способствуя успеху лечения.} {Detox программа поможет избежать повторного срыва и обеспечит безопасное лечение.|Программа детоксикации поможет предотвратить рецидивы и обеспечит безопасное лечение.|Детокс-программа предотвращает срывы и гарантирует безопасность лечения.} {Обратитесь к наркологу на дом‚ чтобы получить комплексную помощь и вернуться к нормальной жизни.|Свяжитесь с наркологом на дом для получения комплексной помощи и возвращения к полноценной жизни.|Не откладывайте‚ обратитесь к наркологу на дом за комплексной помощью и начните новую жизнь.}
вывод из запоя
vivod-iz-zapoya-orenburg012.ru
вывод из запоя круглосуточно оренбург
Анонимный вызов врача нарколога — это важный шаг для людей, столкнувшихся с зависимостями при лечении зависимости. На сайте narkolog-tula028.ru вы можете обратиться за помощью и воспользоваться наркологической помощью. Это особенно актуально для людей, страдающих от алкоголем и наркотиками. Услуги нарколога включают диагностику зависимостей и лечение при употреблении наркотиков. Анонимный нарколог может посетить вас на дому, что обеспечивает комфорт и конфиденциальность. Выездные специалисты предоставляют поддержку психолога и проводят процессы реабилитации для зависимых. Онлайн консультация врача позволяет незамедлительно узнать нужные советы. Анонимное лечение зависимостей — это шанс изменить свою жизнь без опасений о предвзятости. Не теряйте возможности на перемены с помощью анонимных услуг здоровья!
Капельницы для снятия запоя – это эффективное средство при интоксикации алкоголем. Нарколог на дом круглосуточно обеспечит необходимую помощь‚ содействуя в процессе дезинтоксикации и восстановления после запоя. Симптомы алкоголизма‚ такие как тревожные симптомы‚ головная боль и слабость‚ требуют оперативного реагирования. Терапия при запое включает инфузии‚ которые помогают устранить абстиненцию и вывести токсины из организма. Визит к специалисту важна для определения дальнейших шагов: лечение в стационаре или амбулаторная помощь. Наркологическая клиника предлагает профессиональную помощь‚ чтобы исключить возможность рецидива и заботиться о здоровье пациента.
алкоголизм лечение
reabilitaciya-astana008.ru
программа реабилитации наркозависимых
пансионат для престарелых
pansionat-msk010.ru
пансионат после инсульта
Запой, серьезное состояние‚ которое требует вмешательства специалистов; Ложное мнение, что можно самостоятельно выйти из запоя‚ как минимум, рискован и приводит к тяжелым последствиям. В Туле алкогольная зависимость — это проблема для многих, и помощь нарколога на дому играют важную роль в решении этой проблемы. Вызвать нарколога на дом в Туле Симптомы запойного состояния включают дрожь, потливость, волнение. Попытка справиться самостоятельно может привести к тяжелым проблемам со здоровьем‚ включая различные психические заболевания. Помощь нарколога важна для безопасного выхода из запоя и возвращения к нормальной жизни. Кроме того‚ процесс реабилитации от алкогольной зависимости требует поддержки близких и профессионалов. Вызвав нарколога на дом в Туле‚ вы получите квалифицированную помощь‚ избежите рисков, связанных с самостоятельным выходом и приступите к восстановлению. Не рискуйте своим здоровьем‚ обратитесь за помощью!
реабилитационный центр для наркозависимых
reabilitaciya-astana009.ru
лечение алкоголизма в стационаре
пансионат для пожилых с инсультом
pansionat-msk011.ru
пансионаты для инвалидов в москве
В современном мире проблема зависимостей является всё более актуальной. Наркология по вызову в Туле предоставляет разнообразные наркологических услуг, посреди которых лечение без лишних вопросов и помощь при алкоголизме. Вызов нарколога даёт возможность получить квалифицированную медицинскую помощь в случае наркотической зависимости без необходимости посещения клиники. Ключевой услуг является detox на дому, что обеспечивает комфортную обстановку для пациента. Консультация нарколога и психологическая поддержка имеют большое значение для восстановления после зависимости. Программа реабилитации предполагает лечение зависимостей и созависимости, а также наркологию для семьи. Кроме того, реабилитация на дому способствует более эффективному восстановлению. Если вы испытываете трудности, воспользуйтесь ресурсами, такими как vivod-iz-zapoya-tula015.ru, чтобы узнать больше о наркологических услугах в Туле.
пансионат для лежачих москва
pansionat-msk012.ru
пансионат для людей с деменцией в москве
вывод из запоя круглосуточно
vivod-iz-zapoya-kaluga013.ru
вывод из запоя
вывод из запоя круглосуточно
tula-narkolog007.ru
вывод из запоя
пансионат для пожилых
pansionat-tula010.ru
пансионат для пожилых после инсульта
лечение запоя
vivod-iz-zapoya-kaluga014.ru
экстренный вывод из запоя калуга
вывод из запоя
tula-narkolog008.ru
вывод из запоя тула
частные пансионаты для пожилых в туле
pansionat-tula011.ru
пансионат с медицинским уходом
muscle building drugs legal
References:
https://naijasingles.net/@kentderrington
scientific name for steroids
References:
https://git.bayview.top/minnagarten32
вывод из запоя круглосуточно
vivod-iz-zapoya-kaluga015.ru
экстренный вывод из запоя
KRAKEN даркнет работает без сбоев актуальная ссылка открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Здравствуйте! KRAKEN ссылка — удобный способ входа в маркет С помощью рабочая ссылка KRAKEN вы сможете безопасно зайти в личный кабинет и пользоваться площадкой без ограничений. Этот ресурс подходит тем, кто ценит стабильность и анонимность. Простая навигация и актуальные зеркала позволяют заходить без проблем в любое время.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится актуальная ссылка KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Доброго! KRAKEN официальный сайт — удобный способ входа в маркет С помощью KRAKEN зеркало вы сможете безопасно зайти в личный кабинет и пользоваться площадкой без ограничений. Этот ресурс подходит тем, кто ценит стабильность и анонимность. Простая навигация и актуальные зеркала позволяют заходить без проблем в любое время.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Привет всем! KRAKEN ссылка — удобный способ входа в маркет С помощью KRAKEN зеркало вы сможете безопасно зайти в личный кабинет и пользоваться площадкой без ограничений. Этот ресурс подходит тем, кто ценит стабильность и анонимность. Простая навигация и актуальные зеркала позволяют заходить без проблем в любое время.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
вывод из запоя минск
vivod-iz-zapoya-minsk010.ru
лечение запоя минск
KRAKEN маркетплейс — вход без ограничений рабочее зеркало KRAKEN помогает обойти блокировки и быстро попасть на площадку. Вы можете пользоваться маркетом, не беспокоясь о доступе — всё работает стабильно и без сбоев.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Здравствуйте! KRAKEN зеркало — удобный способ входа в маркет С помощью рабочее зеркало вы сможете безопасно зайти в личный кабинет и пользоваться площадкой без ограничений. Этот ресурс подходит тем, кто ценит стабильность и анонимность. Простая навигация и актуальные зеркала позволяют заходить без проблем в любое время.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте официальная ссылка. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
психиатр на дом для пожилого
psychiatr-moskva007.ru
психиатрический стационар
лечение запоя челябинск
vivod-iz-zapoya-chelyabinsk010.ru
вывод из запоя
KRAKEN маркетплейс — вход без ограничений TOR версия KRAKEN помогает обойти блокировки и быстро попасть на площадку. Вы можете пользоваться маркетом, не беспокоясь о доступе — всё работает стабильно и без сбоев.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN даркнет работает без сбоев официальный сайт KRAKEN открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN сайт работает без сбоев официальный сайт KRAKEN открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится KRAKEN официальный сайт, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN маркет — вход без ограничений актуальная ссылка KRAKEN помогает обойти блокировки и быстро попасть на площадку. Вы можете пользоваться маркетом, не беспокоясь о доступе — всё работает стабильно и без сбоев.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
вывод из запоя цена
vivod-iz-zapoya-minsk011.ru
экстренный вывод из запоя
консультация частного психиатра
psychiatr-moskva008.ru
стационар психиатрической больницы
KRAKEN маркетплейс работает без сбоев KRAKEN зеркало открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Как зайти на KRAKEN в 2025 году Чтобы попасть на сайт, используйте актуальную KRAKEN ссылку. Доступ открыт через TOR и мобильную версию. Всё просто — переходите по адресу и входите в личный кабинет.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится актуальная ссылка KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте KRAKEN зеркало. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
лечение запоя
vivod-iz-zapoya-chelyabinsk011.ru
лечение запоя
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN онион. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN маркет — вход без ограничений рабочее зеркало KRAKEN помогает обойти блокировки и быстро попасть на площадку. Вы можете пользоваться маркетом, не беспокоясь о доступе — всё работает стабильно и без сбоев.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN сайт работает без сбоев актуальная ссылка открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте KRAKEN зеркало. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится зеркало KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
вывод из запоя круглосуточно
vivod-iz-zapoya-minsk012.ru
экстренный вывод из запоя минск
Как зайти на KRAKEN в 2025 году Чтобы попасть на сайт, используйте актуальную KRAKEN ссылку. Доступ открыт через TOR и мобильную версию. Всё просто — переходите по адресу и входите в личный кабинет.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
психиатр на дом
psychiatr-moskva009.ru
частный психиатр на дом в москве
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится зеркало KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN сайт работает без сбоев официальный сайт KRAKEN открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN маркетплейс работает без сбоев KRAKEN зеркало открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN зеркало TOR. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
вывод из запоя челябинск
vivod-iz-zapoya-chelyabinsk012.ru
экстренный вывод из запоя
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте KRAKEN зеркало. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN онион. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная официальный сайт сегодня Многие ищут, где находится актуальная ссылка KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Доброго! KRAKEN официальный сайт — удобный способ входа в маркет С помощью официальный сайт KRAKEN вы сможете безопасно зайти в личный кабинет и пользоваться площадкой без ограничений. Этот ресурс подходит тем, кто ценит стабильность и анонимность. Простая навигация и актуальные зеркала позволяют заходить без проблем в любое время.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Здравствуйте! KRAKEN ссылка — удобный способ входа в маркет С помощью KRAKEN ссылка вы сможете безопасно зайти в личный кабинет и пользоваться площадкой без ограничений. Этот ресурс подходит тем, кто ценит стабильность и анонимность. Простая навигация и актуальные зеркала позволяют заходить без проблем в любое время.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN даркнет работает без сбоев официальный сайт KRAKEN открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
платный психиатр на дом
psikhiatr-moskva007.ru
частная психиатрическая клиника стационар
экстренный вывод из запоя
vivod-iz-zapoya-omsk010.ru
вывод из запоя
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте KRAKEN зеркало. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится зеркало KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
[url=][/url]
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN зеркало TOR. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN TOR ссылка. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
вывод из запоя круглосуточно череповец
vivod-iz-zapoya-cherepovec013.ru
вывод из запоя круглосуточно
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN TOR ссылка. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится KRAKEN официальный сайт, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN ссылка сегодня Многие ищут, где находится KRAKEN официальный сайт, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN TOR ссылка. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
If you are looking for trusted sites in the USA, then this is something you shouldn’t miss. Check out the full details via the attached link:
best online casinos
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте официальная ссылка. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
[url=][/url]
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте официальная ссылка. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Автоматические гаражные ворота давно перестали быть роскошью и стали необходимым элементом комфортной жизни. Наши автоматические ворота сочетают надёжность проверенных европейских механизмов с элегантным дизайном, который гармонично впишется в архитектуру любого здания. Мы предлагаем полный цикл услуг: от профессиональной консультации и точного замера до установки под ключ и гарантийного обслуживания. Доверьте безопасность своего дома профессионалам — получите бесплатный расчёт стоимости уже сегодня: https://vorotalux58.ru/
Доброго! KRAKEN ссылка — удобный способ входа в маркет С помощью официальный сайт KRAKEN вы сможете безопасно зайти в личный кабинет и пользоваться площадкой без ограничений. Этот ресурс подходит тем, кто ценит стабильность и анонимность. Простая навигация и актуальные зеркала позволяют заходить без проблем в любое время.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте официальная ссылка. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN онион. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN маркетплейс — вход без ограничений рабочее зеркало KRAKEN помогает обойти блокировки и быстро попасть на площадку. Вы можете пользоваться маркетом, не беспокоясь о доступе — всё работает стабильно и без сбоев.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN маркетплейс — вход без ограничений TOR версия KRAKEN помогает обойти блокировки и быстро попасть на площадку. Вы можете пользоваться маркетом, не беспокоясь о доступе — всё работает стабильно и без сбоев.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте: https://kramarket.cc
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте KRAKEN зеркало. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте KRAKEN TOR версия. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
вывод из запоя круглосуточно
vivod-iz-zapoya-cherepovec014.ru
вывод из запоя цена
KRAKEN даркнет работает без сбоев актуальная ссылка открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN онион. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN зеркало сегодня Многие ищут, где находится KRAKEN официальный сайт, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN ссылка сегодня Многие ищут, где находится зеркало KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная официальный сайт сегодня Многие ищут, где находится зеркало KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Актуальная KRAKEN ссылка сегодня Многие ищут, где находится актуальная ссылка KRAKEN, и ответ прост — у нас только проверенные адреса. Рабочие зеркала обновляются регулярно, чтобы вы всегда могли войти без капчи и ограничений.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN онион. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Как зайти на KRAKEN в 2025 году Чтобы попасть на сайт, используйте рабочее зеркало. Доступ открыт через TOR и мобильную версию. Всё просто — переходите по адресу и входите в личный кабинет.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Как зайти на KRAKEN в 2025 году Чтобы попасть на сайт, используйте рабочее зеркало. Доступ открыт через TOR и мобильную версию. Всё просто — переходите по адресу и входите в личный кабинет.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте KRAKEN TOR версия. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
If you want to learn everything about online platforms in the United States, then this is exactly what you need. Check out the full details via the link at the bottom of the page:
best online casino
KRAKEN маркетплейс — вход без ограничений KRAKEN вход помогает обойти блокировки и быстро попасть на площадку. Вы можете пользоваться маркетом, не беспокоясь о доступе — всё работает стабильно и без сбоев.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN — площадка, которая всегда на связи Если другие сайты не работают, попробуйте официальная ссылка. Даже при блокировках сервис остаётся доступным. Удобный интерфейс, простая регистрация и постоянные обновления зеркал делают использование комфортным.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN сайт работает без сбоев официальный сайт KRAKEN открывается с любого устройства — телефона, ноутбука или TOR браузера. Это безопасный способ доступа, если вы хотите сохранить анонимность и стабильность соединения.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN зеркало TOR. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
KRAKEN TOR версия для безопасного входа Если вы хотите анонимности — используйте KRAKEN онион. Она даёт полный доступ ко всем разделам без риска блокировок. Удобный интерфейс и простая навигация — всё, что нужно для комфортной работы.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
http://yar-genealogy.ru/0093.php
Как зайти на KRAKEN в 2025 году Чтобы попасть на сайт, используйте актуальную KRAKEN ссылку. Доступ открыт через TOR и мобильную версию. Всё просто — переходите по адресу и входите в личный кабинет.
Кстати, даем прокод 40%: MXF4-KEN1-X4JA
подробности где его вводить указаны на сайте:
KRAKEN – Это лучший даркнет маркет плейс в РФ!
Удачных покупок!
Salutations, joueurs !
Je viens de trouver un contenu exclusif avec les nouveautes les plus chaudes sur le jeu Plinko en France.
Si tu es fan de ce jeu, cette lecture est incontournable.
Accede a tout cela via le lien place en bas :
plinko jeu
https://telegra.ph/Dji-matrice-4-kupit-10-14
лечение запоя омск
vivod-iz-zapoya-omsk011.ru
лечение запоя омск
Магазин,лови от меня большой и жирный “+”. Заказ пришёл в течение 3ёх дней.Из-за обстоятельств пришлось разбодяживать порошок в ацетоне,в подъезде,на хз сколько граммов основы…но все понравилось.все и всем довольный.
https://telegra.ph/Ik-podsvetka-dlya-pricela-nochnogo-videniya-kupit-10-13-2
Сайт сделан на уровне в скором думаю сделаю заказ, только бы качество не подвело
когда дело было? а то я сам жду заказ
https://telegra.ph/Kupit-bronezhilet-ratnik-6-klassa-zashchity-10-13-3
я думаю разберемся точно
Брал не давно в этом магазине закладкой в МСК, что сказать, все прошло замечательно. Клад был поднят, место довольно спокойное и тихое, Время исполнения заказа с момента оплаты от 1 до 2,5 часов, что по сути не так уж и много. Выражаю огромное спасибо оператору в аське, не оставлял меня ни на минуту, всегда отвечал.
https://telegra.ph/Dji-action-3-kupit-10-13-2
всё отлично,ровно,супер! )
https://sites.gsu.edu/nramirez5/2016/02/08/comments-comments-comments/comment-page-885/#comment-147791
лечение запоя
narkolog-krasnodar016.ru
лечение запоя
экстренный вывод из запоя череповец
vivod-iz-zapoya-cherepovec015.ru
лечение запоя череповец
Скиньте сайт ваш пожалуйста.
https://telegra.ph/Dji-avatar-2-kupit-10-12-3
и будем мы так общаться по одному смс раз в полмесяца…
доставку можем рассчитать вам в ICQ
https://telegra.ph/Detektor-dronov-Bulat-10-13-7
Продавец общительный, выслал с заказом пару пробников бесплатно! заказы высылют оперативно
экстренный вывод из запоя
vivod-iz-zapoya-omsk012.ru
экстренный вывод из запоя
https://medium.com/@bumleculto
Всем привет.
https://telegra.ph/Kupit-binokl-monokulyar-10-12-4
Из аськи вышел и даже не ответил… *(
Да долго работают! :good:с самого начала)
https://telegra.ph/Dji-mavic-fly-more-combo-kupit-10-12-4
хочу выразить благодарность оператору за поддержку, очень переживал он меня успакоили!
Проститутки метро Лесная
https://merlinp456.livejournal.com/296.html
лечение запоя
narkolog-krasnodar017.ru
вывод из запоя краснодар
вывод из запоя круглосуточно иркутск
vivod-iz-zapoya-irkutsk010.ru
вывод из запоя цена
спср только растраивает, такие деньги берут, и че то нифига не делают. Посыль уже 3 день лежит в г. Ё-XX. Хотя должны были привезти в близлежащий город. Но тут я узнал то что у нас нет в городе филиала ихнего. Вот и не понятно толи сами привезут, толи ехать до них надо.
https://telegra.ph/Kvadrokopter-s-kameroj-kupit-v-novosibirske-10-13-4
Я вообще удивляюсь как продаван работает то? Есть ветка форума, личка и ася – везде молчание. В ася онлайн, но всеравно молчит уже третий день – это адекватный сервис?
На удивление был поражен скоростью работы магазина. Все четко как в аптеке))) Благодарствую
https://telegra.ph/Teplovizor-ajrej-kupit-opticstrade-com-10-13-4
Процветания и успехов вашему магазину!!
лечение запоя
vivod-iz-zapoya-orenburg010.ru
вывод из запоя круглосуточно
мазагин, один из лучший, беру практически только здесь!
https://telegra.ph/Rehb-romashka-kupit-10-13-4
Удачи всей команде желаю
экстренный вывод из запоя
narkolog-krasnodar018.ru
вывод из запоя цена
Use our intimate massage experience for the most realistic and sensual massage experience.
новый магазин???это хорошо!!успехов в работе, конкуренция – это очень хорошо!!
https://telegra.ph/Kupit-takticheskij-binokl-10-12-3
31 страницу отзывов почитайте – увидите всех. Кто то только что зарегился , ктото год назад , кому что аккаунт блокнули или забыл пароль от старого акка – он зарегился по новой .
вывод из запоя круглосуточно
vivod-iz-zapoya-irkutsk011.ru
экстренный вывод из запоя
Админ по аське с кем связался адекват=))) радует.Приятный сайт цены тоже радуют сделал заказ=)) буду ждать. Качество Каличество отпишу
https://telegra.ph/Kupit-opticheskij-pricel-ruzhe-10-13-3
Магазин отличный. Покупал не однократно. Спасибо. Ждем регу!
вывод из запоя цена
vivod-iz-zapoya-orenburg011.ru
экстренный вывод из запоя
У меня в городе например СПСР – это самая безпалевная курьерка, а с ЕМС постоянно принимают.Так что кому как
https://telegra.ph/Kupit-radar-detektor-s-gps-10-12
Маловато по-моему, у меня 1гр жвша растворяется полностью примерно в 30 мл, меньше этого – частично
а вот на фофу гнать нельзя… она на высоте…
https://telegra.ph/Kupit-binokl-magaziny-v-moskve-nedorogo-10-13
но только если мусора захотят найдут. просто мусора еслиб хотели найти , то давно бы уже посыль пришла с сопровождением.
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
https://telegra.ph/Termal-scope-50-teplovizor-kupit-10-13-2
вывод из запоя круглосуточно
vivod-iz-zapoya-irkutsk012.ru
вывод из запоя круглосуточно
Si vous etes interesse par les casinos francais, alors c’est un incontournable.
Lisez l’integralite via le lien en bas de page :
casino en ligne
https://telegra.ph/Kupit-horoshij-teplovizionnyj-pricel-10-12-4
вывод из запоя
vivod-iz-zapoya-orenburg012.ru
лечение запоя оренбург
https://interiordoorsua.blogspot.com/2025/10/razdvizhnyye-dveri-v-gostinoy.html
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
https://telegra.ph/Kollimator-holosan-403-kupit-10-12-3
https://plisio.net/pt/blog/pephop-ai
https://telegra.ph/Detektor-bpla-bulat-kupit-10-12-4
вывод из запоя круглосуточно краснодар
narkolog-krasnodar020.ru
вывод из запоя краснодар
Register at glory casino bonus no deposit and receive bonuses on your first deposit on online casino games and slots right now!
https://telegra.ph/Dji-inspire-3-kupit-10-13-2
https://telegra.ph/Kupit-v-chite-opticheskij-pricel-yukon-10-11
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
Обращение к анонимному наркологу — это важным шагом на пути к лечению зависимости. Если вы или ваш близкий сталкиваетесь с трудностями с наркотиками или алкоголем‚ не стоит откладывать помощь на потом. На сайте site;com доступна консультация нарколога и заказать выезд специалиста на дом. Анонимная помощь обеспечивает вашу конфиденциальность‚ что особенно важно для многих зависимых. Квалифицированный нарколог осуществит детоксикацию организма и предложит индивидуальные программы реабилитации. Психотерапевтическая помощь также играет ключевую роль в лечении зависимости. Поддержка для зависимых и их семей способствует преодолению последствий зависимости. Не забывайте‚ что лечение алкогольной зависимости так же важно‚ как и работа с наркотиками. Не бойтесь попросить о помощи‚ это ваш первый шаг к свободе от зависимости.
https://telegra.ph/Kupit-pricel-teplovizionnyj-varg-35rl-10-12-3
http://xn--oy2b17l86fxrg95g.com/bbs/board.php?bo_table=free&wr_id=496894
Капельница от запоя – это важная мера первой помощи при интоксикации алкоголем. Нарколог на дом круглосуточно предоставит срочную помощь‚ обеспечивая дезинтоксикацию и восстановление после запоя. Проявления алкоголизма‚ такие как тревожные симптомы‚ головная боль и слабость‚ требуют оперативного реагирования. Терапия при запое включает инфузии‚ которые помогают бороться с абстиненцией и детоксифицировать организм из организма. Визит к специалисту важна для выбора последующего лечения: госпитализация или домашняя терапия. Наркологическая клиника предлагает экспертное лечение‚ чтобы предотвратить рецидивы и обеспечить здоровье пациента.
вывод из запоя цена
narkolog-krasnodar016.ru
экстренный вывод из запоя
https://telegra.ph/EHkshn-kamery-dji-osmo-kupit-10-12-5
https://telegra.ph/Akkumulyator-dlya-kvadrokoptera-kupit-10-12
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
https://telegra.ph/Solnechnye-paneli-ecoflow-kupit-10-12-2
Стоимость детоксикации от алкоголя в Туле варьируется в связи с множеством факторов. Нарколог на дом анонимно предоставляет услуги по детоксикации и лечению при алкоголизме. Консультация нарколога способствует выбору оптимальной программы детокса. Стоимость на лечение алкоголизма могут включать расходы на анонимную детоксикацию и реабилитацию от алкоголя. Услуги нарколога, такие как поддержка пациентам с зависимостямитакже играют важную роль. В наркологической клинике Тула предлагают различные программыкоторые могут влиять на общую стоимость. Необходимо учитывать о профилактике алкогольной зависимости и необходимости своевременной терапии.
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
https://telegra.ph/Retranslyator-wifi-signala-kupit-5-ggc-10-12
Экстренная помощь при алкоголизме способствует предотвращению осложнений и способствует восстановлению здоровья. Курс лечения алкоголизма требует внимательного подхода и может включать реабилитацию наркоманов. Визит к врачу поможет подобрать индивидуальный план лечения. Не медлите с обращением к врачу – ваше здоровье на первом месте! вывод из запоя Красноярск
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
https://telegra.ph/Usilitel-signala-sotovogo-telefona-kupit-10-12-4
экстренный вывод из запоя краснодар
narkolog-krasnodar017.ru
вывод из запоя круглосуточно
https://telegra.ph/Mozhno-li-kupit-bronezhilet-grazhdanskomu-licu-10-12-3
https://telegra.ph/Mavik-pro-cena-kupit-10-13-3
https://telegra.ph/Teplovizionnyj-pricel-irej-kupit-avito-10-12-2
Enjoy a deeply connecting sensual spa experience for relaxation and sensual pleasure.
лечение алкоголизма в Туле
https://telegra.ph/Tut-ru-opticheskie-pricely-kupit-10-13-2
Капельница для лечения запоя – это действительным методом медицинской помощи при алкогольной зависимости. Вызов нарколога на дом позволяет оперативно получить необходимую помощь в ситуации запоя. Состав капельницы обычно содержит препараты для очищения организма, такие как раствор натрия хлорида, раствор глюкозы, витамины и антиоксиданты. Действие капельницы направлено на восстановлении водно-электролитного баланса, облегчении симптомов абстиненции и повышении общего самочувствия пациента. Лечение запоя с помощью капельницы обеспечивает срочную помощь в условиях запоя и способствует более быстрому восстановлению после запоя. Профессиональная помощь на дому избегает потребности в госпитализации, что делает процесс лечения более комфортным. Важно учитывать, что восстановление после запоя может предусматривать и психотерапевтические методы для помощи в борьбе с зависимостью от алкоголя.
https://telegra.ph/Umnaya-rozetka-ecoflow-kupit-10-11
вывод из запоя круглосуточно
narkolog-krasnodar018.ru
лечение запоя
https://telegra.ph/Kupit-opticheskij-pricel-dlya-zagonnoj-ohoty-10-12-4
Курсы ЕГЭ биология https://courses-ege.ru
https://bigpicture.ru/piony-s-dostavkoj-v-moskve-kak-vybrat-idealnyj-buket/
https://telegra.ph/Kupit-horoshij-kollimator-10-12-3
https://www.eastcountyschools.org/home/2022/12/14/educational-heroes-video-series
вывод из запоя цена
vivod-iz-zapoya-smolensk022.ru
лечение запоя смоленск
https://telegra.ph/Kupit-inzhektor-dlya-aktivnoj-antenny-10-12
melbet промокод на первый депозит
промокод melbet россия
https://telegra.ph/Teplovizor-pulsar-aksion-xm30s-kupit-10-13-3
экстренный вывод из запоя краснодар
narkolog-krasnodar019.ru
вывод из запоя
https://telegra.ph/Benzogenerator-3-kvt-kupit-na-ozon-10-11
https://wisesocialsmedia.com/story5924757/1xbet-promo-code-today-2026-vip-130
loud alarm clocks
https://telegra.ph/Kvadrokopter-dji-neo-fly-kupit-10-12-4
https://telegra.ph/Pricely-kupit-opticheskie-opticstrade-com-10-12-3
экстренный вывод из запоя смоленск
vivod-iz-zapoya-smolensk023.ru
экстренный вывод из запоя
https://telegra.ph/Opticheskij-pricel-svarovski-kupit-10-12-4
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
https://telegra.ph/Kupit-binokl-yukon-10-13
pariez sur le foot foot africain
https://telegra.ph/Ispolzovanie-shturmovikom-detektora-dronov-bulat-4-10-13-3
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
вывод из запоя краснодар
narkolog-krasnodar020.ru
лечение запоя краснодар
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
https://telegra.ph/Dji-phantom-4-pro-v-20-kupit-10-12-6
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
https://www.brownbook.net/business/54212367/купить-лирику-сочи/
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
https://form.jotform.com/252506004121035
вывод из запоя
vivod-iz-zapoya-smolensk024.ru
экстренный вывод из запоя смоленск
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
https://linkin.bio/lindneroj5tgerhard
Najlepsze kasyno online w Polsce
Dolacz do billionaire casino huuge
i ciesz sie najlepszymi grami online, zakladami sportowymi i ekscytujacymi bonusami w Polsce.
https://imageevent.com/ginnibinghi/claon
Услуга откапывания на дому в Красноярске – это востребованная услуга‚ особенно при проведении земельных работ‚ ремонтных и строительных работах. Специализированные компании‚ предлагают услуги по копке на участке с использованием экскаватора на дому. Лицензированные специалисты гарантируют высокое качество выполнения заказа‚ включая работу с грунтом и установку дренажных систем. Необходимо также учитывать благоустройство и ландшафтный дизайн территории. Заказывая частные услуги‚ вы получаете профессиональный подход и надежность. Для подробной информации можно посетить сайт vivod-iz-zapoya-krasnoyarsk019.ru.
кракен vk3
кракен маркет
https://www.grepmed.com/bodahydv
Круглосуточная наркологическая помощь на сайте vivod-iz-zapoya-vladimir025.ru. Наш наркологическая клиника предоставляет профессиональную помощь в лечении зависимостей, включая алкогольную и наркотическую зависимость. Мы предлагаем лечение без раскрытия личных данных и детоксикацию организмагарантируя полную конфиденциальность. В нашем центре вы можете получить консультациями психолога и поддержкой профессионального психолога. Процесс реабилитации наркозависимых включает программу комплексного восстановления с акцентом на поддержку семьи. Мы обеспечиваем качественное медицинское обслуживание для эффективного преодоления зависимости.
https://rant.li/ubwictdrludo/kupit-shishki-kokain
https://rant.li/nycihsuflof/kupliu-shishki-narkotiki
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
https://wanderlog.com/view/itamgilmoj/купить-кокаин-марихуану-мефедрон-эспоо/shared
кракен vk4
kraken vpn
Зависимость от наркотиков и алкоголя требует квалифицированного подхода. Наркологическая помощь состоит из диагностики зависимостей и лечениячто может существенно изменить жизнь человека. Консультация нарколога. Медицинская помощь при алкоголизме и реабилитация наркозависимых проводятся в центрахспециализирующихся на этом, таких как vivod-iz-zapoya-krasnoyarsk020.ru. Программы восстановления предполагают психотерапию при зависимости и группы поддержки для зависимых, а также семейную поддержку. Важно помнить о мотивации к лечению и профилактике зависимостей. Социальная адаптация после лечения помогает предотвратить рецидивы. Анонимная помощь наркозависимым доступна и эффективна. Начните новый этап своей жизни с помощью профессионалов!
http://www.pageorama.com/?p=zygnyefmu
Детоксикация от алкоголя на дому в владимире — это доступный метод помочь близким борющимся с алкоголизмом. Лечение алкоголизма включает детоксикацию на дому, что дает возможность лечиться в привычной обстановке. Капельницы от алкоголя может осуществляться с помощью специальных растворовкоторые помогают справиться с симптомами абстиненции. Медицинская помощь в таких случаях важна: услуги нарколога помогут правильно подобрать антиалкогольную терапию. Работа с психотерапевтом также является важным аспектом в лечении. Социальная поддержка и интеграция в общество помогают в процессе реабилитации наркозависимых. Профилактика алкоголизма и восстановление после запоя — важные этапы в восстановлении здоровья. Не забывайте, что здоровый образ жизни без алкоголя. На сайте vivod-iz-zapoya-vladimir026.ru вы можете получить подробности о лечении алкоголизма.
https://www.band.us/page/99922500/
https://pxlmo.com/soBreedowcoolbee
кракен актуальная ссылка
кракен сайт
https://www.band.us/band/99483502/
https://allmynursejobs.com/author/multik34palladium/
Услуги по откачке в Красноярске, важная услуга для поддержания чистоты и здоровья. Проблемы с канализацией могут возникнуть внезапно, и в таких случаях стоит вызвать в аварийную службу Красноярск. Качественная откачка сточных вод позволит избежать неприятных ситуаций.Среди вариантов откачки предлагаются: обслуживание канализационных систем, обслуживание выгребных ям и экстренная откачка. Специальная ассенизаторская техника обеспечит высокое качество выполняемых работ в соответствии с экологическими нормами. На сайте vivod-iz-zapoya-krasnoyarsk021.ru вы можете узнать информацию о стоимости услуг и возможности вызова мастера. Также доступны сушилки септиков и дренажные системы для предотвращения повторных засоров. Не затягивайте с решением проблемы — решите проблемы с канализацией сегодня!
https://baskadia.com/user/fyb9
Профилактика запоев после вывода – важная задача для сохранения здоровья и избежания повторных случаев. Нарколог на дом в владимире предлагает услуги по лечению алкогольной зависимости и предотвращению запойного состояния. Важным аспектом является психологическая поддержка, которая позволяет преодолевать трудности.Советы нарколога включают стратегии борьбы с запоем, такие как создание здорового образа жизни и поддержка семьи в лечении алкоголизма. Реабилитация после запоя требует медицинского вмешательства при алкогольной зависимости и консультации специалиста по алкоголизму. Использование услуг нарколога на дому обеспечивает удобство и доступность терапии. нарколог на дом владимир Важно помнить, что процесс восстановления после запоя – это процесс, требующий времени, сил и терпения. Профилактика возврата к алкоголизму включает в себя постоянные консультации с наркологом и использование техник, способствующих стабильному состоянию здоровья и избежанию алкоголя.
kraken vk4
кракен обмен
https://8632b1aa6abe1e1174295265f7.doorkeeper.jp/
https://www.brownbook.net/business/54215737/купить-бошки-алматы/
https://community.wongcw.com/blogs/1140161/%D0%A5%D0%B0%D0%BD%D1%82%D1%8B-%D0%9C%D0%B0%D0%BD%D1%81%D0%B8%D0%B9%D1%81%D0%BA-%D0%BA%D1%83%D0%BF%D0%B8%D1%82%D1%8C-%D0%90%D0%BC%D1%84%D0%B5%D1%82%D0%B0%D0%BC%D0%B8%D0%BD-%D0%9D%D0%B0%D1%80%D0%BA%D0%BE%D1%82%D0%B8%D0%BA%D0%B8-%D0%AD%D0%BA%D1%81%D1%82%D0%B0%D0%B7%D0%B8
https://1xbet-promo-code-list-nepal.gitbook.io/1xbet-promo-code-list-nepal-docs/
Зависимость от наркотиков и алкоголя требует квалифицированного вмешательства. Наркологическая помощь включает в себя диагностики и лечения зависимостейчто может существенно изменить жизнь человека. Первый шаг к выздоровлению – это консультация нарколога. Лечение алкоголизма и реабилитация наркоманов проводятся в центрахспециализирующихся на этом, таких как vivod-iz-zapoya-vladimir028.ru. Реабилитационные программы предполагают психотерапевтические сеансы и группы поддержки, а также семейную поддержку. Важно помнить о мотивации к лечению и профилактике зависимостей. Социальная адаптация после лечения помогает предотвратить рецидивы. Анонимная помощь наркозависимым доступна и продуктивна. Начните новый этап своей жизни с помощью профессионалов!
кракен Москва
kraken РФ
лечение запоя смоленск
vivod-iz-zapoya-smolensk022.ru
экстренный вывод из запоя
https://www.brownbook.net/business/54246662/лирика-файзер-купить/
https://pxlmo.com/movrewowie9
https://www.rwaq.org/users/lifegirllily27102001-20250716220730
кракен vk6
kraken vk3
https://rant.li/padedefaib/perudzha-kupit-kokain-mefedron-marikhuanu
Откапать на дому: идеи для заработка Современные технологии открывают новые горизонты для удаленного заработка. Если вам интересен удаленный заработок, существует множество вариантов, как заработать дома. Один из самых популярных способов — фриланс. Вы можете зарегистрироваться на платформах для фрилансеров, таких как vivod-iz-zapoya-vladimir029.ru, и предлагать свои услуги: написание текстов, графический дизайн, разработка программного обеспечения. Другой вариант — подработка в интернет-проектах. Например, участие в опросах или тестирование сайтов. Это отличный способ получить доход без вложений. Если у вас есть таланты и увлечения, подумайте о создании домашнего бизнеса, например, создании уникальных изделий ручной работы. Советы по работе на дому: организуйте рабочее место, планируйте время и выбирайте задачи, которые вам интересны. Самостоятельная работа требует самодисциплины, но может принести хороший доход. Идеи для заработка можно найти на специализированных ресурсах. Главное — иметь смелость экспериментировать!
экстренный вывод из запоя смоленск
vivod-iz-zapoya-smolensk023.ru
вывод из запоя круглосуточно
https://shootinfo.com/author/knight_martines/?pt=ads
https://www.grepmed.com/ugufuiech
кракен qr код
кракен официальный сайт
https://www.band.us/page/99566915/
лечение запоя краснодар
narkolog-krasnodar016.ru
экстренный вывод из запоя
https://linkin.bio/dietrichki8wpeter
https://odysee.com/@yenvypham071
http://www.pageorama.com/?p=xidebpacibuo
кракен vk3
kraken android
https://community.wongcw.com/blogs/1142794/%D0%A2%D0%B0%D1%88%D0%BA%D0%B5%D0%BD%D1%82-%D0%BA%D1%83%D0%BF%D0%B8%D1%82%D1%8C-%D0%BA%D0%BE%D0%BA%D0%B0%D0%B8%D0%BD-%D0%BC%D0%B5%D1%84%D0%B5%D0%B4%D1%80%D0%BE%D0%BD-%D1%81%D0%BA%D0%BE%D1%80%D0%BE%D1%81%D1%82%D1%8C
https://www.diigo.com/item/note/903p6/6vnj?k=89af7b1e6bb83c4b0a04627072abb1d3
вывод из запоя круглосуточно
narkolog-krasnodar017.ru
экстренный вывод из запоя
https://www.openlibhums.org/profile/eeaa0916-fb7e-43a8-865d-0c9230077042/
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
кракен vk6
kraken обмен
отменное :dance:
Приобрести онлайн кокаин, мефедрон, гашиш, бошки
Вы люди или нелюди? вас тут некто не обманывает, у магазина было тяжелое время, были проблемы с курьерками мы его пережили все налажено работаем в полную силу, у всех бываю белые и черные полосы нужно переживать их вместе вам это возместиться даже более того, всем отправили кто ждал, адекватные получат +50% к заказу и понимание магазина в любой ситуации и помощь
Неотложная наркологическая помощь – это важный аспект в лечении зависимостей. Следует помнить, что при возникновении симптомов передозировки, таких как ускоренное дыхание, потеря сознания или конвульсии, необходимо незамедлительно вызывать экстренную медицинскую помощь. Наркоманы и их близкие могут обратиться в наркологическую клинику, где окажут квалифицированную помощь. Специальные кризисные службы предлагают услуги нарколога, что позволяет получить поддержку близким и самим зависимым. Лечение зависимостей включает не только лекарственное лечение, но и психотерапевтические методы, что важно для восстановления после зависимости. Профилактика алкоголизма и социальная адаптация также играют важную роль в процессе восстановления наркоманов, обеспечивая успешное воссоединение с обычной жизнью. Важно помнить, что помощь при наркотической зависимости должна быть оперативной и многосторонней. Поддержка и понимание близких помогают преодолеть сложности на пути к восстановлению. Для получения более подробной информации посетите vivod-iz-zapoya-vladimir025.ru.
купить лестницу на второй
emeryflowers – Beautiful aesthetic, every section blooms with creativity and emotion.
шлюхи тюмени телефоны
– Извините…. а… вы нас до “Дайва” (ночной клуб) не довезете?
Приобрести MEF GASH SHIHSKI ALFA – ОТЗЫВЫ, ГАРАНТИИ, КАЧЕСТВО
KEY я не понимаю что ты хочешь от магазина то теперь ????за непонятку с соткой !!! моральную компенсацию????? или что????
nighttoshineatlanta – Beautifully inspiring event site, visuals radiate joy and inclusion.
kraken ссылка
kraken vk6
douglasand55 – Very polished design, strong visuals and clear professional tone.
nighttoshineatlanta – Beautifully inspiring event site, visuals radiate joy and inclusion.
Ам1220 все больше сообщений что относят к нелегалу.
Закладки тут – купить гашиш, мефедрон, альфа-пвп
“Так вот Основа это Продукта похожа на таблетки Гидроперит”
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
лестница на второй на металлокаркасе
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
neighborsforrandy – Friendly community feel, layout conveys care and connection effectively.
ehajjumrahtours – Professional and serene, the layout reflects faith and reliability.
5 iai вообще говорят “беспонтовый” продукт… сколько народу его от рaзных сeлеров не пробовало – всё одно муть…
Приобрести MEF GASH SHIHSKI ALFA – ОТЗЫВЫ, ГАРАНТИИ, КАЧЕСТВО
Только что принесли, позже трип отпишу)
вывод из запоя круглосуточно
narkolog-krasnodar018.ru
вывод из запоя цена
ct2020highschoolgrads – Heartwarming initiative, celebrating graduates with positivity and pride.
природу потрібно охороняти тому що
saratogapolarexpressride – Magical and festive, captures the holiday spirit with great warmth.
kraken vk6
кракен vk6
Ну что, получил посылку. С весом ровно, маскировка тоже хорошая. Заваривал 1/15 так я не прикуренный, вставило нормально. заказывал JV-60 10гр.
Приобрести онлайн кокаин, мефедрон, гашиш, бошки
было много… но скрутят даже за один! им главное работа,а не обьем! тем более 1гр – это уже особо крупный размер!
Снятие симптомов запоя в домашних условиях требует комплексного подхода. Прежде всего, следует акцентировать внимание на детоксикации организма. Употребление большого количества воды способствует выведению токсинов. Народные средства от запоя, такие как настои из трав (мелисса, мята), могут облегчить симптомы. вывод из запоя круглосуточно владимир Восстановление после алкоголя включает адекватное питание, фрукты и овощи ускоряют процесс. Поддержка со стороны близких очень важна, так как психологическая помощь может предотвратить повторные запои.
luxnoe – Modern and stylish, this site exudes luxury and creative design.
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
karen4assembly – Clear and sincere campaign tone, content reflects leadership and integrity.
Да хорошо бы было, сегодня уже получу трек. Но конечно напугали всякие кому типа ам плохой пришёл.
Магазин 24/7 – купить закладку MEF GASH SHIHSKI
Все будет окей, это косяк курьерки…
stageofnations – Culturally rich, visuals celebrate unity and vibrant heritage beautifully.
как всегда оплатил и все пришло. спасибо что есть такой магаз беру давно у них, все ок всем саветую
Магазин 24/7 – купить закладку MEF GASH SHIHSKI
5го марта написал ЛС ТСу про оптовый заказ…. до сих пор жду ответа
mastriano4congress – Direct and focused, campaign visuals match strong message delivery.
Настоящий оазис удовольствия и покоя. Всё продумано до мелочей — интерьер, освещение, музыка. Девушка невероятно чувственная и заботливая. Попробуйте, эро массаж недорого нск: https://sibirka.com/. Обязательно повторю, всё понравилось.
нет так то обещал в среду или в четверг.
https://donetskbqx.ru
Не скажу что качество низкое качество на высоте а возрат не кто не сделает даже не фантазирую )) Все супер все ровно сам тут беру еще не разу не разачаровывался
вывод из запоя краснодар
narkolog-krasnodar019.ru
вывод из запоя круглосуточно краснодар
https://plandaynewtwentythree.twentythree.com/holiday-management-in-planday-1
лестницы на металлическом каркасе купить
Лечение зависимостей на дому — это удобный способ борьбы с зависимостями, который становится все более популярным. Услуги нарколога на дому обеспечивают конфиденциальность и комфорт, что является ключевым моментом для многих пациентов. Квалифицированные специалисты обеспечивают медикаментозное лечение и поддержку психолога, что даёт возможность начать восстановление после зависимости в привычной обстановке. Домашняя реабилитация включает в себя индивидуальные программы реабилитации, семейную терапию и встречи с наркологом, что способствует лучшему пониманию проблемы. Профилактика рецидивов играет ключевую роль в процессе лечения алкоголизма и наркотической зависимости. Домашний уход за зависимыми помогает формировать поддерживающую среду и минимизировать риски срыва. Сайт vivod-iz-zapoya-vladimir027.ru предоставляет широкий спектр услуг, включая анонимную наркологическую помощь, что даёт возможность пациентам получать помощь без ненужных вопросов. Квалифицированный подход к лечению зависимостей на дому делает этот процесс доступнее и менее стрессовым для пациента и его семьи.
с нашими кристаллами восстановятся
https://ilovaisknt.ru
составите конкуренцию известно кому :monetka:
asteroid-insurance – Clever concept, design feels futuristic and sharp with humor.
adirondackfiddlers – Full of tradition, music passion shines through each element.
Мать и мачеху+травяной сбор(успокаивающий).
https://shakhtyorskgp.ru
Красиво делаете. Так держать!
shopminq – Trendy e-commerce look, product visuals are crisp and appealing.
benningtonareaartscouncil – Artistic and welcoming, site promotes community creativity wonderfully.
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
значит не успели трек номер в базу завести.
https://luganskgtr.ru
“Думаю надо заглянуть в аптечку Мож завалялось и да Чудо они есть решаюсь попробовать и Вы не поверите одно и тожЕ”
homecovidtest – Informative and reliable, design prioritizes health clarity and accessibility.
казино вавада зеркало
всё получил,качество-бомба,очень доволен магазином ,всё быстро доставили,вам желаю так держать!!!!!!!!!
https://volnovakhaem.ru
качество продукции класс. Но пожалуй что радует больше всего – отзывчивость администрации и оперативность работы.
charitiespt – Compassionate and community-driven, mission comes across with sincerity.
вывод из запоя круглосуточно краснодар
narkolog-krasnodar020.ru
вывод из запоя круглосуточно краснодар
Помощь наркологов в владимире – это неотъемлемая часть борьбы с зависимостями. Если вы или ваши близкие столкнулись с проблемами, связанными с наркоманией, реабилитационные центры предлагают разнообразные программы лечения зависимостей. В Владимирской наркологической клинике предоставляется комплексная медицинская помощь, включая очистку организма и психотерапию. Прием у нарколога помогут выявить степень зависимости и разработать персонализированную стратегию. Психологическая поддержка и работа с семьями зависимых играют важное значение в процессе лечения. Также следует обращать внимание на профилактику зависимостей, чтобы избежать кризисных ситуаций. Безопасная помощь доступна всем, кто ищет поддержку. Программы лечения алкоголизма включают индивидуальные техники, подходящие для всех нуждающихся. Обратитесь на vivod-iz-zapoya-vladimir028.ru для получения дополнительной информации и записи на прием.
Ты нам лучьше отзыв напиши о работе магазина 😀
https://stambulrelaxi.com
по заказу?)
fayettecountydrt – Purposeful and informative, organization’s vision feels transparent and clear.
larkfest2013 – Vibrant and nostalgic, visuals radiate energy and celebration.
https://site-bf6qle3kz.godaddysites.com/
mckeetransition – Professional government tone, site design supports accessibility and progress.
holyspiritschooleg – Educational yet warm, design and content reflect care and faith.
Брал закладкой в МСК, утром оплатил, перед оплатой еще раз уточнил все реквизиты у оператора и направился платить. после оплаты сразу сообщил время и сумму оператору, который сразу принял заказ, сказал ждать нужно полтора часа, но курьеру понадобилось чуть больше времени, благо оно позволяло … и вот через почти 4 часа, оператор выслал мне адресс с кладом, который оказался не так уж и далеко.
https://donetskgma.ru
пока никаких точных дат нет. цены будут когда придёт товар, так что ждёмс пока что.
georgewillwashpost – Clean layout, solid typography, content radiates intellect and authority.
lcbclosure – Focused and informative, the message feels urgent and clearly communicated.
Ценник уж больно сладкий.. И это очень настараживает.. Кто что скажет, когда последние движения были, всё ровно?
https://khartsyzkod.ru
Всем привет) У меня такая проблема, сделал заказ, оплатил через евросеть, Уважаемый продаван сказал то, что в евросети перевод идет до 3-х дней, хотя когда работали с другим магазином деньги прилетали моменьтально всегда. И доставка вышла на 950 р. (г. Екб), это получаеться + курьер или нет, просто до почты?… И через что лучше оплачивать в данном магазине?
mayceformayor – Campaign feels strong and grounded, visuals emphasize trust and service.
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
masonchallengeradaptivefields – Inspirational cause, presentation is heartfelt and full of purpose.
milestonerest – Inviting visuals, design creates a sense of comfort and good taste.
Ура! Скинул трек быстро) ждууууууу, отпишу.
https://dokuchaevskrm.ru
Оплатил, жду.
http://www.bakinsky-dvorik.ru/communication/forum/messages/forum4/message104205/66386-code-promo-1xbet-tours-gratuits-2026-_-100_-_100?result=new#message104205
peoplesprotectiveequipment – Practical and safety-focused, design feels direct and trustworthy.
letthemplaymn – Passionate and purposeful, the site speaks strongly for youth engagement.
Как правильно провести детоксикацию организма после запоя в Красноярске Лечение запоя требует всестороннего подхода, включая очищение и восстановление организма. Симптомы похмелья могут быть тяжелыми, и важно выбрать правильные методы для очищения печени; Медикаментозное лечение часто дополняются народными средствами, что повышает эффективность. лечение запоя Центры лечения зависимости предлагают программы детоксикации и восстановление после запоя. Поддержка близких и психологическая помощь играют ключевую роль в процессе. Предотвращение запоев включает в себя постоянный контроль за здоровьем и благополучием. Помните, что восстановление — это долгий путь, но возможный.
teamtadros – The mission feels bold, visuals highlight unity and determination.
Магаз что надо, забегаем! Всем мира!
https://luganskgtr.ru
Всегда сдесь было высокое качество
exodusalliance – Empowering theme, site feels hopeful and mission-driven throughout.
oscarthegaydog – Whimsical and delightful, brand personality shines through humor and charm.
Что задерживали грузы, с поставками, и дожидались пока запрет выйдет…
https://torezvxn.ru
списались с продавцом,пообщались,договорились.я оплатил заказ и начались долгие ожидания моей заветной посылки.
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
daybirdsyr – Energetic vibe, visuals and tone reflect creativity and modern living.
supportsros – Compassionate tone, clear visuals support their advocacy with sincerity.
следующий раз пришлем поношеные презервативы но ты будешь рад!!!
https://donetskbqx.ru
Да стопудова честный!!! В этом нет сомнений. А вот с волей Медведя и планом Путина ужиться сложно
justinhicksformissouri – Strong campaign message, design feels authentic and community-focused.
nyscanalconference – Informative and organized, layout suits event communication well.
tinacurrin – Artistic and bold, site radiates passion and expressive creativity.
DRINKIO приятно удивил точностью и скоростью. Курьеры приезжают без опозданий, заказы всегда соответствуют. Ассортимент богатый, сайт удобный. Радует круглосуточная доставка. Отличный сервис для жителей столицы. Доставка алкоголя на дом в Москве – https://drinkio105.ru/
35ф – индика весёлая , серьёзная , тошнатворного эффекта НЕТ хоть перекурись , сейчас беру 35 говорят сативка , будит возможность отпишу трип в красках , а вообще говорят что в симбиозе они лучше , но то что лучше / не сильнее / а именно лучше 25ф так это даже вы не сомневайтесь
https://gorlovkazn.ru
все ровно тут ?
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
harryandeddies – Cozy restaurant vibe, visuals and menu presentation feel deliciously inviting.
Наркологическая клиника Красноярск предлагает круглосуточную помощь – это важный шаг на пути к лечению зависимости и реабилитации наркозависимых. В клинике предлагают медикаментозное лечение, а также консультацию специалиста, что помогает пациентам справиться с проблемами. Анонимный и быстрый вывоз из запоя помогает избежать чувства стыда. Роль поддержки семьи в процессе выздоровления невозможно переоценить, а профилактика рецидивов осуществляется через программу реабилитации и психотерапию при зависимости. Услуги нарколога включают кризисную интервенцию и обследование на наркотики, что помогает в достижении успешного восстановления. Получите помощь на vivod-iz-zapoya-krasnoyarsk020.ru!
Про себя могу сказать что толлерантность ОЧЕНЬ выская
https://khartsyzkod.ru
Давно работаю с чемиком.
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
southbyfreenoms – Fun, quirky branding with energetic layout and friendly design.
Обращайтесь к нам снова
https://khartsyzkod.ru
основу взял мяту и подорожник, мед. спирт-растворитель.
electamandamurphy – Inspiring campaign, message of progress and empathy shines through.
Посыль получил в течении 5ти дней после оплаты. Быстро!! Отлично!!
https://baligrows.com
мир всем месным братья
kim4commonsense – The campaign feels approachable, visuals and tone are relatable.
romain4reform – Clear, reform-focused tone, visuals convey honesty and strong leadership.
Эффект чувствуется почти сразу, эйфория и стим в голове
https://luganskbzi.ru
привет всем получил бандероль с посылкой открыл всё ровно чё надо было то и пришло в общем респект магазу вес ровный пока сохнит основа жду по курю отпишу чё да как закинул деньги 5.07 пришло на почту уже 9.07 утром. были выходные только сегодня уже курьер набрал с утра и привёз отличный магаз берите не обламывайтесь
rideformissingchildren – Heartfelt cause, presentation honors the mission beautifully and respectfully.
Капельница от алкоголя – является действующий способ‚ который помочь в реабилитации после алкогольной зависимости в домашних условиях. Обратившись к к наркологу‚ который приедет к вам‚ вы сможете получить профессиональную поддержку и необходимые медикаменты для облегчения симптомов похмелья. Симптомы запойного состояния могут включать головной боли‚ тошноты и слабости; вызвать нарколога на дом Красноярск Процесс детоксикации организма стартует с введения капельницы‚ которая гарантирует поступление жидкости и витаминов‚ что помогает снять симптомы отмены. Услуги нарколога в Красноярске включают персонализированный подход к пациенту‚ что необходимо для эффективного лечения алкоголизма на дому. Поддержка близких при алкоголизме является важной составляющей в процессе восстановления здоровья после алкоголя. Реабилитация в домашних условиях возможна благодаря капельниц и медикаментов‚ что позволяет избежать новые запои и упростить процесс восстановления. Таким образом предотвращение запоев является ключевым моментом в борьбе с зависимостью.
И вообще зачем тебе спасибо жать или репутацию добавлять?? Ты что малолетка глупая, что это тебя так беспокоит??
https://dokuchaevskrm.ru
Магазин работает ровно !!! Качество реагента высокое!!!
t-walls-of-kuwait-iraq – Historical and impactful, visuals convey memory and meaning strongly.
часть покупателей устраивает, продавцы тоже не жалуется. В чем проблема? нет терпения – идите в другие шопы.
https://yasinovatayqf.ru
с радостью сообщаю что посыль пришла в мой солнечный город,и я рад…не только потому что она дошла а тому что всю длинную дорогу (10дней)со мной оставался на связи магазин,работает без всяких проволочек,без гемора свойственного многим магазинам,всё дошло конспирация на наивысшем уровне как и сам магазин,ребята удачных вам продаж и многолетнего существования
cranberrystreetcafe – Cozy and charming, design evokes warmth and delicious experiences.
Сорь за многобукав, не попустило еще 😉
Приобрести онлайн кокаин, мефедрон, гашиш, бошки
Подскажите пожалуйста товары указаные в прайсе все в наличии или нет?
keyword.
Сохраняйте рабочие адреса KRAKEN и проверяйте их перед входом.
If you are looking for trusted sites in the USA, then this is something you shouldn’t miss. Read the full details via the attached link:
https://www.zionempilhadeiras.com.br/online-casino-games-thrill-and-strategy-4/
georgetowndowntownmasterplan – Informative and civic-minded, content clearly explains planning goals.
hardman4schools – Very clear communication, every section feels honest and approachable.
продавец в аське..только что с нми общался
Закладки тут – купить гашиш, мефедрон, альфа-пвп
спасибо стараемся
saveshelterpets – Touching initiative, site feels compassionate and community-focused.
лечение запоя смоленск
vivod-iz-zapoya-smolensk022.ru
лечение запоя смоленск
The Inheritance Games Canada: A thrilling mystery game where players unravel secrets, solve puzzles, and compete for a billionaire’s fortune. Perfect for fans of strategy and suspense: Jennifer Lynn Barnes author site
праздники мы тоже отдыхали, так как курьерки все равно не работают
Приобрести MEF GASH SHIHSKI ALFA – ОТЗЫВЫ, ГАРАНТИИ, КАЧЕСТВО
прет 30-45 мин.1к10.действием похож на рсц
albanysuperducks – Fun and quirky, visuals bring playful excitement to life.
Магазин как магазин!
Закладки тут – купить гашиш, мефедрон, альфа-пвп
не бзди все будет ровно трек не всегда бьется это касяк курьерки а не отправителя не паникуй
https://factava.com.ua/karta-vinnytsi/
Делать надо 1к10, можно и послабже, например 1к13, но не более, а то 30 минут эт мало, хотя смотря для кого))
Приобрести MEF GASH SHIHSKI ALFA – ОТЗЫВЫ, ГАРАНТИИ, КАЧЕСТВО
у нас сейчас 6-apb нет в России…
Услуги наркологов в владимире становится все более востребованной‚ особенно когда речь идет о лечении алкоголизма. Нарколог на дом круглосуточно владимир оказывает услуги для людей‚ нуждающихся в незамедлительной поддержке. В рамках наркологической клиники проводится очищение организма от наркотиков и алкоголя‚ что является первым шагом к выздоровлению. Лечение алкоголизма включает в себя облегчение абстиненции‚ что позволяет облегчению состояния пациента. Круглосуточная помощь нарколога обеспечит необходимую медицинскую помощь при алкоголизме в любой момент. Визит нарколога поможет составить персонализированный план терапии, учитывающую все нюансы пациента. Реабилитация зависимых включает психотерапию для зависимых‚ что помогает улучшить психологического состояния и адаптации к жизни без алкоголя. Поддержка близких играет важную роль в процессе лечения; Анонимное лечение зависимости даст возможность пациенту обращаться за помощью без страха осуждения. Вызывая нарколога на дом‚ вы делаете первый шаг к счастливой жизни.
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
stopkrasner – Strong political tone, site expresses clear intent and decisive messaging.
пробуй 4фа, 2-dpmp
Онлайн магазин – купить мефедрон, кокаин, бошки
хочу извинится за поднятую панику(думаю ТС меня понимает , т.к. все мы люди и переживаем за свои деньги,тем более сфера деятельности расшатывает нервы как не крути).зная теперь с чем была связана данная проблема с поставками и положительным финалом в порядочности ТС не сомневаюсь.на данный момент работа налажена,в чем убедился сам и наслышан от других.
tranquilleeyecream – Calm aesthetic, visuals match beauty and relaxation concept perfectly.
hardman4schools – Strong educational vision, visuals and tone reflect dedication beautifully.
лечение запоя смоленск
vivod-iz-zapoya-smolensk023.ru
вывод из запоя смоленск
чувствую у меня будет то же самое, трек получил но он нихуя не бьется, а что ответил то? я оплатил 3 февраля и трек походу тоже левый ТС обьясни и мне ситуацию
Онлайн магазин – купить мефедрон, кокаин, бошки
Для совсем новичков 1 к 15 будет даже много.
walkunchained – Inspiring tone, message of freedom and courage comes across clearly.
кто последний раз когда брал? регу или соль
Приобрести онлайн кокаин, мефедрон, гашиш, бошки
Сорри, многаюуков. И ошибок – со спецтелефлна сижу)
jammykspeaks – Powerful voice, content feels authentic, motivational and full of passion.
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
embersk9wish – Heartwarming mission, site honors service dogs with love and gratitude.
21 мая заказал -23 получил трек.все ок ,жду посыл
Онлайн магазин – купить мефедрон, кокаин, бошки
В лс пиши сразу. Имей в виду, быстрее будет
Я вот перед заказом почитала хуеву кучу отзывов и не нашла ни одного хуевого. Но опять же, смотри, отзывы были не об эйфоре, а о самом магазине. Давай друг, советуй что-нибудь в личку
https://krasnyluchzo.ru
Адрес почты правильный, все проверил не 1 раз, ответьте хоть тут.ну будем надееться что и на этот раз TS войдет в положение и как нибудь обратит внимание на решение наших вопросов, компенсирует нам потраченые нервы и время на безсмысленное ожидание, главное ведь для магазина репутация!
экстренный вывод из запоя
vivod-iz-zapoya-smolensk024.ru
вывод из запоя цена
createimpactonline – Their AI-driven tools have streamlined our operations significantly.
partnershippowerhouse – Their case studies provide real-world examples that are incredibly helpful.
Списался с продавцом в аське, во вторник оплатил, сказали в среду отправят. когда спросил, сказали что не отправили по тех причинам из-за СПСР, обещали в четверг. Должно было придти в течении 3х рабочих дней. Сегодня понедельник, сижу на работе, и вот мне звонят, мол вам письмо пришло, куда доставить? То есть все верно, 3 дня как и говорили! Настроение теперь на весь день поднялось)) Вечером буду делать 1к10 (ам2233), потом отпишусь как и чего!!)) В общем доволен, но пока говорю только про доставку. Позднее отпишу доволен ли я всем остальным))
https://melitopoluv.ru
Я сегодня заказал 203 жду трека думаю и мне понравится
заказал, получил трек, пока не бьется.
https://berdyanskth.ru
Хотелось бы надеется)))
во вторник заряжали – сразу же списались договорились, чтоб всё ровно было – в итоге 4 суток прошло и тишина нету трека, вчера ваще пропал продаван, хотя до этого ваще из аськи не выходил в такое время, до этого спрашивал м.б. траблы какие – он ответил “что есть не большие” вот и походу решается че-то там х3 пздц короче надеюсь в понедельник решится
https://berdyanskve.ru
_Elf_ тебе сколько лет интересно?У тебя был единичный случай по твоим словам товар-фуфло.репутация у тебя “0”Требуешь вернуть денег, ты же понимаешь что тебе их не вернут.Вывод-ПРОВОКАЦИЯ
Специалист по зависимостям владимир: Профессиональная помощь при зависимостях Если вы или ваши близкие имеете проблемы с психоактивными веществами‚ необходимо обратиться к профессионалу. Нарколог владимир предлагает квалифицированную медицинскую помощь‚ включая диагностику зависимости и индивидуальные консультации нарколога. В наркологической клинике предлагаются многообразные услуги‚ такие как медикаментозное лечение и психотерапия. Лечение зависимости – это сложный и многогранный процесс‚ который требует индивидуального подхода. Программа реабилитации включает в себя фазы‚ направленные на восстановление физического и психологического состояния пациента. Реабилитация наркозависимых также подразумевает поддержку семьи‚ что является ключевой ролью в успешном лечении. Конфиденциальная помощь позволяет пациентам ощущать себя защищенными и свободными от предвзятости. Предотвращение зависимостей и помощь при алкоголизме – ключевые направления работы наркологов. Обратитесь на vivod-iz-zapoya-vladimir025.ru для получения дополнительной информации и записи на приём. Помните‚ что своевременное обращение за помощью – залог успешного исцеления!
А как по качеству?
https://rystsov.info
Вчера оплатил, сегодня уже трек скинули. Пока все ровно, посмотрим что придет…..
monumentremoval – The purpose is bold and the site feels deeply meaningful and timely.
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
если он такой делец,пусть тему свою создаёт!а так аферист,я бональный обаснованный вывод делаю!
https://genicheskol.ru
Раньше розницей занимались благодаря вашему опыту,сейчас время другое,стабильная честная работа)
If you wish to discover the best American casinos, then this is exactly what you need. Discover the full details via the link below:
http://www.le-chamoisdor.com/?p=316696
mystylecorner – Customer support is super helpful, answered all my questions.
Брал хоть и один раз, но все было отлично! Жду второго заказа)
Онлайн магазин – купить мефедрон, кокаин, бошки
Магазин замечательный!!
1091m2love – Unique name, design feels artistic and expression of individuality.
всем доброго времени суто тс ответь в лс есть вопрос
Магазин 24/7 – купить закладку MEF GASH SHIHSKI
всё ровн ждём =)
simplelivingstore – Customer support was responsive when I had a question—appreciate that level of service.
nycbhm – Community-focused organization with meaningful outreach and engagement.
Вызов врача-нарколога на дом – важный шаг для людей, испытывающих трудности с зависимостями. На сайте vivod-iz-zapoya-vladimir026.ru вы можете получить конфиденциальную помощь и квалифицированную помощь на дому. Лечение зависимости, будь то алкогольная или наркотическая, требует внимательного подхода. Наши эксперты предлагают консультацию нарколога, которая включает психотерапию зависимостей и лечение медикаментами. Важно помнить о поддержке родственников в этот непростой период. Реабилитация от алкоголизма и профилактика алкогольной зависимости возможны благодаря лечению на дому и предоставляемым наркологическим услугам. Не ждите, вызовите выездного врача-нарколога уже сегодня!
1day4kids – Uplifting cause, presentation radiates care and dedication toward children.
3случая за последние 2недели.. если быть точнее..
Магазин 24/7 – купить закладку MEF GASH SHIHSKI
Все есть, объем большой
Таможенный брокер помогает нам уже не первый год. Всегда вовремя и без замечаний. Приятно работать с профессионалами https://vkobroker.ru/
nycbhm – Community-focused organization with meaningful outreach and engagement.
knightstablefoodpantry – Compassionate food pantry serving the community with dedication.
trustedpartnergroup – Appreciate the practical guidance they offer for growing network collaborations.
ultimateprofitplan – Might be worth bookmarking for future reference and deeper review.
visionaryfutureteam – The layout is clean and easy to navigate, which makes a good impression.
dailyessentialstore – The item I ordered arrived as described and in good condition.
Магазину отличных покупателей)))
Онлайн магазин – купить мефедрон, кокаин, бошки
важаемый ТС прошу разобраться с заказом,всё оплаченно вам,вот только игнор в бросиксе и посылки нету до сих пор. Заранее благодарен.
trustbridgealliance – The website layout is clean and browsing through their insights feels effortless.
professionalgrowthhub – Will revisit when they publish new updates; seems like a solid long-term resource.
1091m2love – Been exploring this site lately, content feels thoughtful and well-curated.
shopandshine – Would love to see more variety in sizes and colors in future.
creativefashionworld – Customer chat was helpful when I asked about sizing, thumbs up.
mcctheatercampaign – Supporting arts and theater with passion and community spirit.
mcalpineinfo – The site appears to cover the “McAlpine Barge Incident” and has very minimal content so far.
saveshelterpets – On first glance this looks like a potentially good cause, but due diligence is wise for any giving.
astoriatogether – Community unity and collaborative neighborhood initiatives.
а с чего ты взял что чемик ноаый селлер?
Онлайн магазин – купить мефедрон, кокаин, бошки
да не врядли просто ихнему курьеру поджопников надавать надо что бы копытами веселей шевелил да и все
Ищете альтернативу KRAKEN?
Вот ещё вариант: https://krakr.cc
pmajoe4council – Clear campaign focus, design feels trustworthy and community-oriented.
updatingparents – The site feels thoughtful, user-friendly and clearly grounded in practical support.
Как юридическое лицо, рекомендуем сотрудничество. Всё чётко и по делу: таможенный брокер в Москве
Такая тут вкусная цена была недавно на фтор.И продукт офигенский.А теперь цену подняли до всеобщего уровня.И я не вижу уже причин заказать именно здесь а не где-то ещё.Так-то с отправкой всё ровно будет,но цена…
Приобрести MEF GASH SHIHSKI ALFA – ОТЗЫВЫ, ГАРАНТИИ, КАЧЕСТВО
ребят, как узнать того чимакала добавил в скайп, и на каком сайте оформляется заказ?
Алкогольный запой — это серьезное состояние, требующее незамедлительной медико-социальной помощи. В владимире доступна помощь нарколога, который предлагает услуги по избавлению от запоя и очищению организма. Капельное введение — это результативное средство для восстановления здоровья пациента. Она способствует устранению симптомы алкогольной зависимости, улучшает общее состояние и ускоряет процесс реабилитации от алкоголя. помощь нарколога владимир Если вы или ваш близкий испытываете трудности с запоя, важно не откладывать вызов врача на дом. Наркологические услуги, оказываемые в клиниках владимира, могут включать индивидуальный подход к каждому пациенту. Помощь нарколога включает не только капельницы, но и комплексное лечение алкоголизма. Обращение к врачу на дом дает возможность получения медицинской помощи в привычной обстановке. Специалисты обеспечат необходимую детоксикацию и поддержат здоровье пациента. Не бойтесь обращаться за помощью — это начало пути к освобождению от алкогольной зависимости.
Магазин просто огонь !!! Оценка 5+ за все :voo-hoo: !!! Качество товара збс !!! Советую всем этот магаз!!!
Закладки тут – купить гашиш, мефедрон, альфа-пвп
работа 5+ качество 5 опреративность 5+
Как попасть на сайт КРАКЕН без блокировок?
Только живые зеркала, обновляемые ежедневно.
Переходите по проверенной ссылке > https kra45 at
Работает даже при блокировках.
можно узнать, как принимали ? интрозально, в\м ?
Онлайн магазин – купить мефедрон, кокаин, бошки
Хороших продаж!
здесь без музыки танцую – https://melitopolqa.ru Инфа с вашего сайта. Я уже брал 6-APB, и выглядел он несколько иначе.
Капельное лечение запоя – это популярным способом лечения алкогольной зависимостью, используемый применяется в клиниках в владимире с целью очистки организма. Круглосуточное лечение позволяет эффективно снять симптомы запоя. Однако важно помнить о потенциальных рисках, таких как аллергические реакции и нарушение водно-солевого баланса. вывод из запоя круглосуточно владимир
С новым годом всех! https://melitopolqa.ru жасти моё уважение к тебе и респект красавица. но ес честно ты нашла чет не то что было совсем другое как сказал уже уважаемый дельфин там было много сути и честных отзывов :monetka: ну лан проехали если так вроде все все поняли.
discoverdaily.online – Easy to read and well-organized, very user-friendly experience.
оптимал дозировка на 2дпмп при в\в от данного магазина какая? https://avtonews.info Заказывал небольшую партию)) Качество отличное, быстрый сервис)) в общем хороший магазин)
nicholashirshon – Professional portfolio showcasing expertise and accomplishments.
futuregoalsnetwork.shop – Customer service was helpful and responsive; will shop again.
learnsharegrow.shop – Love the variety of topics covered; something for everyone.
choice-eats – Culinary excellence with diverse and delicious dining options.
leadersunitedgroup.bond – I’m learning new things here, good for growth and mindset.
globalpartnershipteam.shop – Customer service was helpful and responsive; will shop again.
Магаз качественный ни разу не подводил!!! https://disdik-lampung.info Радует качество ))
teamfuture.bond – Clean layout, easy to navigate, very user-friendly experience.
discovervalue.bond – Great mix of topics; always something new and uplifting.
winmore.bond – Content is clear and concise, very informative and helpful.
connectinnovationhub.bond – Fast loading pages make the experience seamless and smooth.
trustandunity.bond – Looking forward to more updates and new features soon.
businessgrowthhub.shop – The design is clean and professional, making navigation a breeze.
covidtest-cyprus – Essential health services with reliable testing solutions.
successfultradersclub.shop – Impressive visuals and a smooth interface; browsing feels seamless.
smartfashionboutique.bond – The design is clean and professional, making navigation a breeze.
globalalliancenetwork.bond – Overall a polished site with professional and engaging content.
uniquedecorstore.shop – Fast loading pages make the experience seamless and smooth.
anabolic steroid illegal
References:
https://tuleestudio.com/voidite-odnoiz-zaregistriruites-v-daddy-casino/
Заметила, что магазин куда-то пропадал, но сейчас появился, чему очень рада) https://rovenkixu.ru как так его разве нету? с самого утра тут сижу
wellnesstourbus – Mobile health and wellness services bringing care to communities.
https://uae.pristinealigner.com/best-invisible-aligner-in-uae-for-confident-smile/
nextvision.bond – The design is sleek and modern; navigation is seamless.
successpathway.bond – Smooth browsing experience; easy to find what I’m looking for.
concernedaboutpollution – Environmental advocacy with focus on pollution awareness and solutions.
growthpoint.bond – Impressive design and user experience; feels professional and welcoming.
Капельница для детоксикации на дому — это эффективный способ лечения людям, переживающим от алкогольной зависимости. Терапия включает в себя введение жидкостей, которая облегчает выведению токсинов. На сайте vivod-iz-zapoya-vladimir029.ru можно вызвать специалистов, где профессионалы проведут восстановление после запоя. Данная процедура обеспечивает поступление необходимых растворов и витаминов, что помогает поддержке организма и улучшению здоровья пациента. Своевременная помощь в такой ситуации способствует сократить время реабилитации и предотвратить осложнения. Лечение от алкоголизма начинается с правильного лечения к детоксикации, и данная методика является необходимым этапом в этом процессе.
В таких случаях надо запрашивать подтверждения через форум(ЛС) https://reale.info Ха ха ребята смотрите беспредел! попробуйте написать правильно жабу ТСа и получится то что у меня, как бы с ошибкой! СКРИПТ!
play-brary.org – Found the content engaging and informative; keeps me interested.
createimpacttoday.shop – Fast shipping and excellent customer service; will shop here again.
uniquefashionstyle.shop – (Note: I spotted a small typo in the URL above—a minor thing but worth checking.)
discovergreatdeal.shop – Smooth browsing experience; easy to find what I’m looking for.
leanneslifechangingfairies.com – The site looks friendly and welcoming, very easy to use.
asianspeedd8 – Modern dating platform with cultural connection and community focus.
futureopportunitynetwork.shop – Customer service was helpful and responsive; will shop again.
moesboardwalk.com – Overall trust signals look solid: good layout and visible contact info.
Не-не, через форум заказы не принимаются. Заказывать нужно только через сайт, указанный в подписи. https://blackwhiteshop.ru оч давно здесь не был, не в курсе как сейчас магазы робят..
grant-jt – Professional services with expertise and dedicated client support.
Итак всем ПРИВЕТ ! https://fyrfrr.ru жопа каши головы мозаики мозга
mdcphilly.com – Pages load smoothly and the overall user experience is very pleasant.
harrietlevinmillan.com – I like how the biography and works are presented—well organized and accessible.
komunahouse – Community living space fostering connection and collaboration.
ks4thekids.com – Found it easy to find basic information; good user experience.
brauhausschmitzoktoberfest.com – Great mix of tradition and fun, really captures the spirit.
pp4fdr.org – The overall design is clean and the message comes through clearly.
clubinorout.com – Pages load quickly and browsing feels seamless.
надо прятать по сложнее https://vladtehno.ru Менеджер на связи с 10-11 утра по МСК (не с 8-ми, как Вы ломитесь) ежедневно, кроме праздников и выходных. На сайте Вашего заказа нет. Можете назвать его номер?
concernedaboutpollution.com – Feels trustworthy and credible—good for raising awareness about pollution.
mdcphilly.com – The website design is clean and professional, very well done.
asianspeedd8.com – I found the content easy to read and the site structure logical.
grant-jt.com – The homepage feels calm and focused; no unnecessary clutter.
berrybombselfiespot.com – Booking seems straightforward; that’s a plus for planning a visit.
komunahouse.com – Would love to see more interactive features or member stories.
gailcooperspeaker.com – I’m looking forward to reading more about the work and upcoming events.
berrybombselfiespot – Fun and vibrant selfie destination with creative photo opportunities.
reindeermagicandmiracles.com – The visuals capture the magic of the season—great imagery.
brucknerbythebridge.com – The visuals and layout feel polished and high quality.
KRAKEN всегда доступен через альтернативные адреса
> kraken cc
Сохраняйте ссылку в закладки.
gailcooperspeaker – Inspirational speaking with powerful messages and engaging delivery.
И всем форумчанам!!! https://blackwhiteshop.ru Верно. Но это уже другой критерий – грамотное описание
seenministries – Faith-based ministry offering spiritual guidance and community support.
meetkatemarshall.com – Loved the variety of content – automotive, fashion, food, health – keeps things fresh.
2-й раз все было быстро но собирал весь дживик по конспирации , на пакетиках видать экономили))) https://chilim-rest.ru Может обсудим как избежать напастья копоф при получении посылки от курьера???
moeinclub.com – Author names are shown consistently which adds credibility.
cepjournal.net – The homepage presents content clearly and draws attention to key sections nicely.
shemplymade.com – The site has a warm, natural feel that fits the product theme nicely.
расширяться собираетесь? https://doramalivex.ru В Бросике по- прежнему игнор!!! Магаз просто Ох..!!!
centensports.com – Pages load smoothly and the visuals support the user experience.
safercharging.com – Overall, a solid web presence with a clear mission and good execution.
seenministries.com – The website is clean and easy to navigate; good user experience.
мне тоже все пришло. да и еще вещь нужную в хозяйстве подогнали. вы ребята вообще МОЛОДЦЫ. ВСЕХ БЛАГ ВАМ. https://designitaliano.ru Описывать,тем кто не пробовал-бесполезно.Все равно не поймут.Придумывают всякую фигню(аааа,у тя за спиной собакака!и пр. бред),пытаются посмеяться,но это ж всё не то и близко не стояло.Как слепому объяснить,как все выглядит)
opensky-inc.com – I found the navigation straightforward; information feels easy to locate.
pastorjorgetrujillo.com – The design is clean and inviting, great first impression.
casa-nana.net – The tone is caring and supportive—very appropriate for the cause.
trendingnewsfeed.net – the website has a sharp and modern design; nice first impression.
clevelandchristmasclub.com – Overall, a solid presentation that invites people to join the experience.
electmikemontes.com – I appreciate the professional tone and clean design.
Зашла на ваш сайт, а там “Your site hasn’t been activated yet!”… в общем ничего не выходит. Пробывала и через ТОР и через обычный браузер. Все одно. Что не так делаю? https://chilim-rest.ru Написал о заказе в аське в ПТ,мне сказали цену и реквизиты. В СБ оплатил,кинул в аське свои реквизиты.В ПН связался-Сказали,что все отправили,ок.
buildyourdreamtoday.shop – The visuals are inviting and the interface feels smooth.
vip проститутки тюмень
Сделать можно хоть в Новогоднюю ночь, но обработан он будет только после 9 января. https://chery-msk-baltauto.ru читайте отзывов много!:) товар тут вышка,обращайтесь!
catherinewburton.com – I like how the professional credentials are clearly displayed; builds trust.
vsmphotography.com – Would be nice to see more client testimonials or behind-the-scenes to deepen trust.
exploreopportunitiesnow.shop – Overall a positive impression; user-friendly, clean, and credible website.
toddstarnesbooktour.com – The design feels professional and aligns well with the author’s branding.
createandgrow.shop – The typography and spacing make reading comfortable across devices.
Спасибо за отзывы приятные. Стараемся доставлять побыстрее))) https://chilim-rest.ru Ну тогда, как объяснить все происходящее сейчас?
startsomethinggreat.shop – Navigation feels intuitive; I found what I was looking for quickly.
findwhatyoulove.shop – I’ll bookmark this to check back for new items or deals.
theperfectgiftshop.com – The site loads quickly and works smoothly on mobile too.
shopandsmilealways.shop – It might benefit from more detailed product information to build trust.
simplybestchoice.shop – Product categories appear clear; helps me understand the offerings.
keepgrowingforward.shop – Looks like a solid foundation for an online store; good start.
shopandsmilealways.shop – It might benefit from more detailed product information to build trust.
shopandshineeveryday.shop – Product categories are visible, which helps in understanding the layout.
употреблял перорально, также пробовал нозально (не вариант сжигает все напрочь и комок в слизистой) купить кокаин, меф, бошки через телеграмм Магазин в полном порядке!!
geteventclipboard.com – Design and color choices are subtle yet effective—nice work.
uniquetrendstore – Great shopping experience, fast delivery and quality items every time.
1к10 будет вполне нормально. делал ещё с первой партии микс на нём. купить скорость, кокаин, мефедрон, гашиш Дошло довольно быстро
newseasoncollection – Excellent customer service, resolved my issue quickly and efficiently.
Это ошибка или нет, подскажи пожалуйста. купить Мефедрон, Бошки, Марихуану скорость доставки 5+ (во вторник заказали в пятницу получили)
yourtrustedonlinestore – Love discovering fresh items here; keeps the space feeling updated and fun.
smartchoiceoutlet – Great shopping experience, fast delivery and quality items every time.
joinourcreativeworld – Great shopping experience, fast delivery and quality items every time.
inspireeverydaylife – Great prices and quality, will definitely shop here again.
shopwithconfidence – Customer support helped me instantly, very impressed with service quality.
dreamcreateinspire – Easy to navigate, found exactly what I was looking for.
shopthelatesttrend – Love this site, always find unique items and great deals.
electmikemontes – Political campaign focused on community representation and positive change.
Мир вам! купить кокаин, меф, бошки через телеграмм привет!!! не согласен долдны быть доступные магазины как
shemplymade – Handcrafted products with quality craftsmanship and unique designs.
globalmarketplacehub – Fantastic variety of products, always something new and exciting.
работает заебок… присылают в кортонных больших конвертах…. доставляют очень быстро мне доставили в город за 3 дня… а их отделение в каждом городе есть.. как посылка придет вам позвонят на телефон и предложат доставку или приехать самому… если решите сами забирать то вам скажут адресс куда ехать…=) купить скорость, кокаин, мефедрон, гашиш Полученная продукция не подлежит возврату и обмену.
discoverendlessideas – Love the creativity and inspiration found here, always refreshing.
everytrendinone – The writing style is clear and friendly—makes reading fun rather than a chore.
brightfuturedeals – Loved the downloadable resources section; useful for planning and idea generation.
learnshareconnect – The writing style is clear and friendly—makes reading fun rather than a chore.
discovergreatthings – User-friendly website layout, found what I needed without any hassle.
findyourperfectdeal – Always a pleasure exploring the fresh content and ideas shared.
exploreamazingideas – Great browsing experience, layouts look clean and easy to navigate.
yourjourneybegins – Always a pleasure to browse here, new finds keep me coming back.
да вообще магазов пизде купить Мефедрон, Бошки, Марихуану Принял, участие в совместке номер 3, кинг как и подобает этому магазу, все сделал со скоростью звука, прошло 5 дней после оплаты и у меня в руках лежат 50 тонн этой велеколепной вкусняшки, СПАСИБО. Я просто не понимаю как люди заказывают у других когда есть chemical
shemplymade – Handcrafted products with quality craftsmanship and unique designs.
brainsight-reeracoen – Really impressed by how clean and professional their service feels overall.
blinkiesdonutsca – Atmosphere felt really good, and my family enjoyed the treats too.
shopwithconfidence – The site layout feels modern and simple, really enjoyable shopping vibe.
tabitoshigoto – I really like how the platform highlights new workcation spots across Japan.
качество интересует купить кокаин, меф, бошки через телеграмм Поздравляю всех с наступающим Новым 2013 Годом! Желаю в год Змеи: 1. Мутить тока на спирту! 2. Отваривать основу. 3. Сушить естественным способом. 4. Поменьше “ловить бледного”! 🙂 Ну а магазу Chеmical-Mix желаю Процветания, Оперативности, и качественной разнообразной продукции!
realherschel – Overall a positive experience so far, happy to have discovered them.
newthisdomainsssss – The brand voice is mysterious, good for curiosity though context is missing.
clevelandchristmasclub – Festive community organization spreading holiday joy and cheer.
milioner kasyno
ты писал пришла посылка размыли в итоге прикола не поняли купить Мефедрон, Бошки, Марихуану а работают как.оперативненько? вполне.
ohmydrifter – I found some posts referencing wellness and travel, which is appealing.
https://www.mightycause.com/profile/codepromo
hopeandlace – Worth bookmarking and exploring their “About” and “Work” sections for deeper understanding.
бро ответь в лс, сделаю заказ купить Мефедрон, Бошки, Марихуану Почему всё-таки такси? На метро бы а одну сторону успел бы… Вес большеват был, обычно брал миксы да всякие вкусные таблетки, но тут сразу столько СК… Да и потом, нашёл на товар, найди т на непредвиденный случай/комфорт, я так считаю. Чем брать по грамму микс, так лучше вообще не брать. Пара дней – и на пять грамм наберешь, с друзьями/сэкономишь на обедах, в конце концов.
motivilovesmusic – One suggestion: check domain age, contact details and SSL certificate to assess trust-worthiness.
trabas007hoki – The layout is basic but functional, I hope they improve visuals soon.
hanayaka-na-life – I like how they offer quality without feeling overly expensive.
envolavecning – The aesthetic is okay and professional looking, but substance and transparency are light.
hawaiineiartcontest – I appreciate their focus on environmental awareness through art—adds deeper value.
wrestlingac – Since it covers prominent wrestling personalities like Kofi Kingston, that suggests it has access to credible sources. :contentReference[oaicite:2]index=2
sega-live – Look for user reviews on third-party sites to see if past customers had good experiences.
bwaylocations – Prime location services with strategic placement and accessibility.
beauty-optical-salon – Located in New York? No, actually in Shinjuku, Tokyo at the LUMINE2 building. :contentReference[oaicite:5]index=5
hopprojects – Their “Contra-Culture” theme stood out, feels relevant to current artistic discourses.
foruminvestmali – For investment-related content, I recommend checking whether the site provides transparent sponsorship, governance, and partner details.
спасибо , стараемся для всех Вас купить Мефедрон, Бошки, Марихуану Отписывал Вам в аське,вы там мне не отвечаете в течении полудня..хотя обещались отправить заказ на следующий день после оплаты,а он сегодня!Жду вашего ответа.
rebeccacaridad-manzanita – The name “Manzanita” might connect to the blog or creative brand of Rebecca Caridad, which could be fine but still needs verification.
madmadedesigns – Content seems a bit light in places—would be good to see more project case-studies or customer feedback.
купить права
Дружище как все прошло?)) забрал своё??? А то написал неделю назад и тишина))) если забрал сколько шло по времени? напиши нам а то на последних страницах сдесь какой то кипишь нездоровый…( купить кокаин, меф, бошки через телеграмм Движения каждый день у нас, и все ровно .
globaltrendmarket – The domain feels generic and I couldn’t find much verified info about its operations or team.
Магазин просто супер!!!так держать))))***** купить Мефедрон, Бошки, Марихуану это не спиша эндеграунд улица полна
dearsparrows – The writing is clear and accessible even if you’re new to the subject matter.
turnerhallrestaurant – Exceptional dining experience with quality cuisine and atmosphere.
pepplish – I like the branding here, the name is catchy and the site design looks clean.
connectdiscovergrow – Might be worth following or subscribing if you’re aiming for growth in your career or business.
nomnomnomfordogs – The dog bakery looks charming and genuine, loved seeing all the happy pet photos.
flourandoak – Would appreciate seeing more detail about ingredient sourcing or sustainable practices.
shopwithconfidence – Good candidate for a backlink, but I’d pair it with more established sites for balance.
keepgrowingforward – Good candidate to share with a friend who’s looking for daily inspiration.
staycuriousalways – I’d check for contact details and about-page to ensure it’s well maintained and trustable.
theperfectgiftshop – The domain name is appealing and suggests a curated gift-shop vibe right away.
exploreopportunitiesnow – Would be nice to see more about who runs it, and how often content is updated.
bestdealsforlife – Without strong third-party references, I’d treat this site as lower-authority until proven.
createandgrow – The site design looks simple which can be good, but some pages feel thin on detail.
Вот получил вчера 2 -й заказ…..отсылают быстро, качество отличное, плюс девайсы в которые всё ныколось в виде приятного бонуса… купить Мефедрон, Бошки, Марихуану Всем Удачи
spiritoftheaerodrome – Aviation heritage and historical preservation with passion.
Заказал вчера 30гр 4-FA . Трек пока не получил. Надеюсь что все будет олрайт. В планах долговременное сотрудничество! купить Кокаин, Мефедрон, Экстази неужели ркс такая шляпа?
buildyourdreamtoday – The domain name is inspiring and suggests a platform for personal or professional growth.
ShopForHappiness – I keep returning here, always find interesting products quickly and easily.
34crooke – Unique address with distinctive character and presence.
так что бро не стоит беспокоиться по поводу порядочности этого магазина, они отправляют достаточно быстро и конспирация хорошая и качество на высоте!))) купить Кокаин, Мефедрон, Экстази Ну вот и дождался!
ExploreAmazingIdeas – Highly recommend this platform, great for discovering innovative ideas easily today.
uniquetrendstore – I tried to look up the business behind it but didn’t find much verified background or strong brand presence yet.
ShopTheBestToday – Really enjoy shopping here, site layout makes browsing simple and fast.
InspireEverydayLife – Highly recommend this site, offers valuable content that is genuinely useful.
loftsonlex – Modern urban living with stylish loft accommodations.
makelifebetter – Great deals here, always find exactly what I need quickly.
simplybestchoice – The domain name sounds appealing, but I couldn’t find much trustworthy info about the business behind it.
changetheworld – The name evokes a sense of purpose, but the site’s offerings are unclear without further details.
FindYourPerfectDeal – Fast shipping, products arrived on time and in perfect condition today.
GlobalMarketplaceHub – Shipping was fast, tracking worked perfectly without any confusion today.
changeyourworld – Customer support was helpful, answered all my questions promptly and politely.
TheBestPlaceToShop – I keep returning here, always find interesting products quickly and easily.
startsomethinggreat – Easy navigation, site layout makes shopping smooth and enjoyable overall.
ShopAndSmileAlways – Always something new to discover, makes online shopping fun and exciting.
TrendyFindsHub – Great finds here, always something new and exciting to explore.
learnshareconnect – A valuable resource for continuous learning and personal growth opportunities.
thinkcreategrow – I couldn’t find much information about the site’s content or purpose.
findwhatyoulove – Easy navigation, site layout makes shopping smooth and enjoyable overall.
everytrendinone – Deals are updated frequently, site is reliable and trustworthy overall.
everydayvaluecorner – Easy navigation, site layout makes shopping smooth and enjoyable overall.
как-то перехотелось.. что действительно последний товар не очень? купить Кокаин, Мефедрон, Экстази какое на**й в\в !!?? совсем рехнулись чтоли ? Я не знаю за качество их 2-дпмп, но если он не бодяженный и качественный, то 5мг интрозально хватит чтоб тебя колбасило 2-3 суток ! Никто по ходу у чемикала его ещё не пробовал – отзывов нету…
newseasoncollection – Fast shipping, products arrived on time and in perfect condition today.
yourjourneybegins – I keep returning here, always find interesting products quickly and easily.
ShopTheLatestTrend – Always something new to discover, site keeps me coming back regularly.
такая же фигня, продован сказал, что некоторые только начинаю мониториться! вообщем спср дерьмово работает! купить Мефедрон, Бошки, Марихуану если так то АМ не подойдет скорее всего
ultimateprofitplan – Each article feels detailed yet simple enough to apply right away.
АМ-2233 вообще ровный день назад пришёл купить Мефедрон, Бошки, Марихуану 6-9 мая также будут праздничные дни, в асе, скайпе отвечать не будут, но это не значит, что человек умер или захвачен))))
https://coolors.co/u/1xbetbonus_codetoday
olympicsbrooklyn – Sports and athletic excellence with community engagement.
smarttradingmentor – The tone here is motivating, feels like genuine mentorship through content.
Продаван молчит, что будет дальше не известно, мне сделал но не все.отписался, жду результатов купить скорость, кокаин, мефедрон, гашиш Нет. Такого у нас нет.
trendandstyle – My favorite part is how simple it is to mix and match outfits.
smartbuytoday – I like how clearly items are displayed, makes comparing products so easy.
shoplocaltrend – Great browsing experience, feels personal and friendly all the way through.
freshstylemarket – I like how fresh and clean the layout feels, easy to navigate.
classytrendstore – Feels like a boutique experience online, absolutely love shopping here lately.
brightmarketplace – Love the overall vibe here, easy, colorful, and full of great finds.
bestdealcorner – Feels like a hidden gem online, always end up saving money here.
bestdealcorner – Prices are truly unbeatable, found items here much cheaper than elsewhere.
visionpartnersclub – I like how everything feels community-driven, not just another business blog.
discovergreatvalue – The items look exactly like the photos, no surprises which I love.
classyhomegoods – Great collection of elegant home pieces, ideal for any interior style.
freshfashionfinds – I like browsing this shop, always discover something stylish and affordable.
uniquefashionboutique – My order came beautifully packed, quality exceeded what I was expecting.
futuregrowthteam – The articles are simple yet powerful, encouraging growth with every read.
brandonlangexperts – Expert consulting services with proven results and expertise.
единственная существенная проблема данного магазина – отсутствие автоматизированной системы оформления заказов… Вроде прикручивают к сайту, но что то долго уже… купить Кокаин, Мефедрон, Экстази в курске есть ваш магаз?
https://www.hockeynhlforum.com/read-blog/1792
dailyprofitupdate – The daily reports here actually help me plan trades more confidently.
BuildStrongRelationship – Highly recommend this to couples and friends seeking deeper, lasting connection.
Совершил заказ снова!и буду продолжать это делать,продавец ОЧЕНЬ понимающий человек!:hello::monetka: огромный респект! купить скорость, кокаин, мефедрон, гашиш Вы реально думаете что тут сидят роботы, которые должны отвечать всем без перерывов и выходных? Праздники же были, все отдыхать хотят.
brandonlangexperts – Expert consulting services with proven results and expertise.
protraderacademy – I learned more here in a week than months elsewhere honestly amazing.
yourtradingmentor – The tone here is motivating and realistic, love the balanced perspective.
BusinessConnectWorld – Highly recommend this service if you’re looking to expand business connections.
про тусиай ….. что я могу сказать про тусиай от этого магазина…. пойду лучше трип-реппорт напишу…. такой тусишки ещё не ел) купить скорость, кокаин, мефедрон, гашиш medved20-10 не еби людям голову!!!!!!!!!!! микс отличный, но на час-1,5! Не больше……
connectforprogress – I like how the posts encourage growth and self-improvement consistently.
purebeautyoutlet – This shop feels premium but still affordable, which I absolutely love.
nextleveltrading – The tutorials are super clear, I learned a lot just reading around.
strongpartnershipnetwork – Such a refreshing platform, full of smart ideas and positive connections.
tradingmasterclass – Perfect place to sharpen trading skills without getting lost in theory.
И духовной отсутствие пищи купить скорость, кокаин, мефедрон, гашиш Что то тут не так.
MarketTrendAlerts – Insightful alerts arrive just in time, helping plan my next step.
modernvaluecorner – The mix of products here feels trendy yet super affordable overall.
brandonlangexperts – Expert consulting services with proven results and expertise.
trendinggiftcorner – Love browsing here before holidays, makes gift shopping way less stressful.
shopwithsmile – Great variety of items, from gifts to daily essentials, all in one place.
Может просто нужно быть более бдительным? От фейков никто не застрахован. Попросить подтверждения через ЛС на форуме займет не более пяти минут времени и сохранит ваше настроение, а так же и деньги. БУДЬ БДИТЕЛЕН! ВСЕГДА! купить Мефедрон, Бошки, Марихуану В скайпе ответил что вопрос решаеться,будем надеяться на лучшее,а насчёт красной темы-даже думать не хочеться.Всем мир!!!
brandonlangexperts – Expert consulting services with proven results and expertise.
Вчера списался с продавцов, сказал сегодня отправит. Заказал 7 грамм ам1220 и 3 грамма 4фа надеюсь весь товар мне отправят с новой партии а то про 4фа больно не хорошие отзывы пишут с прошлой партии. купить онлайн мефедрон, экстази, бошки Хороший магазинчик , рега хорошая , в общем стоит вашего внимания ))) всем удачи !
forexstrategyguide – Love how this site explains trading strategies in a clear, simple way.
brahmanshome – Great website, navigation feels smooth and everything is easy today.
everydaytrendshop – Browsing here feels fun, the categories make it easy to find great picks.
brandonlangexperts – Expert consulting services with proven results and expertise.
yourtradingmentor – I really appreciate the real-world examples, they make lessons click instantly.
teamworkinnovation – I really like the balance of creative ideas and practical guidance here.
globalchoicehub – The site feels professional and easy to use, really smooth shopping process.
simplelivinghub – Love the focus on simplicity and mindfulness in every product choice.
shopandshine – This shop makes it fun to find stylish everyday essentials easily.
teamworksuccesspath – I like how this site highlights teamwork as the foundation of growth.
successnetworkgroup – Perfect hub for entrepreneurs and teams working toward collective success goals.
uniquedecorstore – Prices are reasonable for the quality and uniqueness of the pieces offered.
globalmarketinsight – Love how everything is presented clearly without unnecessary jargon or fluff.
successfultradersclub – I’ve learned key risk management techniques here that really improved my trades.
markettrendalerts – Love how actionable and concise the insights are, very practical guidance.
“Решил Попробовать Записаться” купить Кокаин, Мефедрон, Экстази Магазин нормальный, качество на уровне, короче заказывай и не парься я тут брал уже раза 3 и всегда всё на уровне:good:. А ник его Фокс произносится, что в переводе с английского означает лиса, лис..
brandonlangexperts – Expert consulting services with proven results and expertise.
learnandtrade – I’ve learned a lot about risk management just from a few sessions here.
Получил. начал разводить на 7 мл ацетона. все выпало в осадок и почти ничего не растворилось. жидкость получилась мутная как молоко. добавил еще 5 мл. вроде более менее, но все равно большой очень осадок. ну и прям так туда 2 коробка основы высыпал и на плитку. все делал впервые, можно сказать наугад. пыхтел через водник. 1 водник и накрывает мама не горюй. час держит и еще полтора отпускает, и состояние потом ппц мутное какое, даже утром проснулся еще в коматозе. все отлично в принципе, только вот отходняк какой-то.. купить Кокаин, Мефедрон, Экстази Контакты указаны у меня в подписе и в разделе “Наши Контакты”
jonathanfinngamino – Love browsing this site, content is always practical and clear.
можете хотя бы в лс скинуть веточку, а то поиска нет, так как новый акк и не допускаетс до поиска, раньше сидел на легал-рс.биз купить онлайн мефедрон, экстази, бошки Магазину отличных покупателей)))
brandonlangexperts – Expert consulting services with proven results and expertise.
paws21airbrushstudio – Highly recommend for anyone seeking personalized airbrush artistry services.
https://www.diigo.com/item/note/8u6h0/2nbk?k=ac8c148c75fd6f2d00962dae9107dda3
nohonabe – Well-written articles that offer new insights and perspectives daily.
motocitee – Great website, navigation feels smooth and everything is easy today.
kivurc – Excellent resource, practical guides make home projects feel stress-free always.
Ребята кто заказывал 25 реагент,как по качеству??????????? купить скорость, кокаин, мефедрон, гашиш Магазин работает!!! Бро очень понктуален!!! Магазину процветание и новых клиентов!!!
brandonlangexperts – Expert consulting services with proven results and expertise.
https://oceanballon.ru/
raspinakala – Enjoyed reading these posts, ideas are simple yet very useful.
https://rant.li/niltabamlu/get-exclusive-1xbet-promo-codes-for-free-bets-spins-and-exciting-welcome-6z39
adawebcreative – Thoughtful design choices make the site both functional and appealing.
ibdesignstreet – Found exactly what I needed, instructions were clear and concise.
И всем форумчанам!!! https://nebezit.ru Видать все ништяк, вот и не отписывается))))
pgmbconsultancy – Found exactly what I needed, instructions were clear and concise.
wooziewear – Love browsing this site, content is always practical and clear.
expandyourhorizon – The content is diverse and engaging, always something new to explore.
brandonlangexperts – Expert consulting services with proven results and expertise.
inkorswimtattoocruise – Helpful ideas posted here, I’ll definitely share with all friends.
lotsofonlinepeople – The site loads quickly, enhancing the overall user experience.
oldschoolopen – Really helpful tips here, saved me hours of unnecessary work.
letter4reform – Consistently delivering content that challenges and educates its audience.
chopchopgrubshop – The brunch menu offers delightful options worth waking up for.
zz-meta – The team really cares, content quality is consistently impressive.
chopchopgrubshop – The ambiance complements the flavorful dishes perfectly, creating a memorable experience.
ieeb – A fantastic platform for gaining knowledge on various topics.
ieeb – Consistently provides valuable information across various topics, love it.
lastminute-corporate – Offers competitive pricing for corporate travel arrangements and accommodations.
broodbase – The content is diverse and engaging, always something new to explore.
kazhanmaster – Always a pleasure to read, informative and well-written content.
магазин на самом деле чёткий)начал с ним работать не пожалел!!!!!и качество и количество и скорость-всё на высоте!!! https://foxst.ru “Решил попробовать курнуть через фольгу , Насыпаю нажигаю бля чуть кишки не выпленул”
https://www.sammyboy.com/members/bonuscodefor1xbet2026.207421/#about
conorjmurphy – Really helpful tips here, saved me hours of unnecessary work.
sjydtech – Just landed here today, and it already feels welcoming.
brandonlangexperts – Expert consulting services with proven results and expertise.
лучше и не напишешь бро https://foxst.ru Все верно, до сих пор разгребаем )
https://t.me/s/apk_1xbet_android
всем курильщикам привет. магаз ровный,раза 4 заказывал,все проходило нормально,связь с тс в аське тоже норм,можно обговорить любой вопрос. за качество, в61 больше всего понравился. заказывал эйфоретик,так и не понял его,товарищи тоже не поняли эфекта,хотя употребляли по многу. https://mediclever.ru Всем привет,отличный магазин,недавно брала,всё очень понравилось
brandonlangexperts – Expert consulting services with proven results and expertise.
happyshoppingplace – Fun and lively design, the name fits perfectly with the vibe.
спасибо магазу) https://psp-ekb.ru вот это уже наводит на мысли
Автоматические выключатели
happyshoppingplace – Fun and lively design, the name fits perfectly with the vibe.
styleforliving – The overall vibe is modern, clean and genuinely appealing.
че вы панику наводите)) все норм будет! есть рамс у курьерки, магаз не при чем.. спакуха https://potok-uvc.ru Я тебе не хамил. Да 10г, смешно не смешно, а на дороге не валяются. И очень обидно когда от вашего ПМа получаешь подтвердение, веришь! и остаешься с разочарованием и обидой, бессилием что либо доказать. А тебе еще сверху льют хамство, упивайтесь на здоровье. Я утерся и теперь знаю на что способны даже нормальные, доверенные магазины. А это тоже опыт, за который я заплатил, и ничуть не жалею. Просто пусть народ знает и будет готов при работе без гаранта ТУТ ожидайте что такое может быть.
buildabetterworld – Really enjoyed browsing here; found several interesting products instantly.
everydaystylecorner – Friendly layout and easy to navigate—makes browsing enjoyable.
staycuriousdiscover – Inspiring tone, layout encourages creativity and exploration beautifully.
makelifesimpler – This site helped me streamline daily tasks and feel calmer.
Магазин лутше не встречал!!!! https://garage-atlant.ru Всем все выслано.
discovernewthings – The site layout is clean and finding products is effortless.
yourcreativejourney – A great new shop that seems full of inventive and practical products.
theworldawaits – Found something I’ve been looking for—good job sourcing it.
discovergreatdeals – Great variety of items, something for almost every taste.
Занимайся я таким делом,коли вы не просили б о граммах 100,ответ был бы тот же. В таком деле главное-отсутствие жадности. Не надо гнаться за каждой копейкой,коли есть относительно безопасная отработанная схема,то и нечего от неё отклонятся. Вы видите в них кидал,они в вас красного. https://nika-land74.ru Заказал на пробу 50гр 203, придёт люди попробуют я отпишусь,планирую сделать 1к9-ну не верю я когда говорят что можно 1к 13,15 итд.
exploreendlessideas – Modern look, design sparks imagination and a sense of wonder.
learnandgrowtoday – This platform looks motivating and the resources appear genuinely helpful.
changan 35 плюс https://changan-v-spb.ru
хороший магазин !отменное качество и сервис ! хорошей работы вашему магазину и процветания! https://foxst.ru Спасибо большое, что вы с нами и доверяете нам!
bestvaluecollection – Customer service/contact information is visible, which adds trust to the shopping experience.
we368in.com
discoverandcreate – Balanced visuals, message promotes creativity and curiosity together.
про него что нить писали? точнее вы читали ? https://oaostplem.ru 250-й 1К10 то, что нужно..
buildabetterworld – Uplifting concept, site feels full of purpose and positivity.
changeyourdirection – I’ll bookmark this site for the future and revisit when ready to dive in.
growwithconfidence – I’ll bookmark this page for future visits when ready to grow.
АМ-2233 вообще ровный день назад пришёл https://pizzaa-lab.ru хуй ты отпишешь! наркоман проклятый
getinspireddaily – The product descriptions are clear and the theme is genuinely uplifting.
globalstylemarket – The pricing looks fair and there are some good options.
uniquelifestylehub – Pricing seems fair; delivery and quality will determine the full value.
connectlearncreate – I like the wording “connect, learn, create”—it sets a positive inspirational tone.
exploreandcreate – Overall a nice find; excited to see how this store grows.
fashionloverszone – Product photos are clear and the layout gives a modern vibe.
modernlivingstore – Customer support/contact info seems accessible, which adds confidence.
shopwithstylehub – The theme feels modern and the product range looks diverse.
connectwithideas – Found several items that caught my interest; quality will determine value.
findjoytoday – The messaging about “joy” resonates and gives a positive feel to shopping.
makeimpacttoday – Navigation through the site is smooth and browsing is enjoyable.
dreambuyoutlet – Navigation feels intuitive and categories are easy to browse through.
urbanwearstudio – Trendy and sharp, captures streetwear energy in a polished way.
discoveryourpotential – Navigation appears smooth and product or service categories seem clear.
Спасибо Все супер.МиР https://garage-atlant.ru сегодня получил посулку с двумя пакетиками жёлтоватого и белого цвета, магазин работает:good: качество проверю и в соседней темке отпишу
discoveramazingthings – Exciting name, visuals and content give a sense of adventure.
действительно принимают? https://gm72.ru У меня кстати тоже через 2 дня пришло, но в соседний город, так как в моём городе этой конторы не оказалось) но мне сразу позвонили, и предложили либо самому приехать за пакетом, либо подождать до вторника и мне его привезут домой. Вот жду)
номер виртуальный
modernhomefinds – Navigation between categories is intuitive; browsing feels effortless and pleasant.
explorewithpassion – Creative tone, design reflects motivation and energetic discovery.
findyourdreamplace – Product images are sharp, and descriptions seem helpful and readable.
пока двоих отпустили, в крови ничего не нашли.. ждем результатов экспертизы. https://nebezit.ru Все ровно, пасыль забрал, всем доволен!
discoveramazingoffers.shop – Just found amazing deals here, really saves me some money.
urbanwearstudio – Customer contact or support info appears accessible, which builds trust.
smartshoppinghub – Clean and practical, ideal for modern online shoppers and deals.
Я по почте переписывается пытался нормально договориться потом просто отвечать перестали решил здесь пообщаться тут надеюсь игнорировать не будут! https://psp-ekb.ru Вообщем фейк крассавчик пошагово и все грамотно сделал, развел)
imaginelearnexplore – Product visuals are clear and descriptions seem readable—good start.
discoverandcreate – The navigation is smooth and categories seem well-organized for exploring.
Discover the best PS2 games in Canada! A curated list of timeless classics, including action, RPGs, and sports titles. Relive the nostalgia of top PlayStation 2 hits loved by gamers: rare PS2 games for sale
yourmomenttoshine – The overall vibe is clean and modern; a solid first impression.
А для кого указан Major Express (для СНГ)?Да,можно. https://gm72.ru Прошу прощения за крайность и грубость!Но не уведомлять клиента о происходящей ситуации..это по крайней мере,не то что не вежливо,это не корректно в введении торгового процесса!
discovernewthings – Bright visuals and curious tone make this site engaging.
explorewithpassion.shop – Amazing place for inspiration, keeps me motivated throughout the week.
changeyourperspective – Customer support/contact information is visible, which adds trust to the experience.
у тебя все пришло? отпиши в лс. https://sever46.ru магазин хороший,даже если высылат брак (было 1 раз) возврат делают сполна
thebestpick – Clear branding, every detail feels user-friendly and neatly arranged.
findjoyeveryday.shop – The name fits perfectly, shopping here truly makes me smile.
findyourmoments.click – Love the peaceful energy, perfect for mindfulness and reflection moments.
yourdailyshoppinghub.shop – Prices are awesome, totally my go-to place for online deals.
changeyourperspective.click – Love how this site challenges my mindset in refreshing ways today.
createyourfuture.click – Inspiring site overall, helps me stay motivated toward long-term goals.
Пожалуй один из самых ровных магазинов “Старичков ” – благодаря которому я зарабатвал, от души спасибо парням за ровную работу! https://nika-land74.ru Можно позвонить в СПСР, у них там даётся полная инфа по треку, по телефону. Где чё лежит. Если не написано в ленте… Завтра звякну, отпишу, если не появится.
classyfindsonline.shop – Such a charming store, love browsing through all their latest finds.
trendinghomeideas.shop – So many smart ideas here, helped me update my home beautifully.
modernhomefinds.click – Love the stylish home ideas here, everything feels fresh and cozy.
buildsomethingnew.shop – Such a cool site, makes innovation feel fun and accessible.
simplevalueplace.shop – Easy navigation, great deals, and a clean minimal shopping layout.
smartfashionboutique.shop – Love the variety, from casual wear to classy event pieces.
startanewjourney.shop – Everything here feels uplifting, really pushes me to move forward.
trendingstyleworld.shop – Smooth shopping experience, delivery came right on time as promised.
modernlivingtrend.shop – The decor trends here always inspire me to redecorate my space.
findyourpathnow.shop – Helpful content overall, great place to reset and find inspiration.
staycuriousdiscover.shop – Inspiring content overall, keeps me motivated to explore new ideas.
yourmomentstarts.click – Great vibe overall, reminds me to stay focused and positive daily.
modernlivingstore.click – Love the furniture picks here, they fit perfectly in any space.
самое норм) я думаю лучше лс нет) а сайт это вы о нас заботетесь) комфорта только себе и клиентам больше) а это GUD! https://potok-uvc.ru Оплатил в среду, жду посылочку, посмотрим как что.
modernhomefinds.click – Love the stylish home ideas here, everything feels fresh and cozy.
createyourfuture.click – Inspiring site overall, helps me stay motivated toward long-term goals.
freshfashioncorner.shop – Love their designs, always find something unique and trendy weekly.
changeyourperspective.click – Love how this site challenges my mindset in refreshing ways today.
Зато искать долго не пришлось наверное???! https://mediclever.ru вообще ктонибудь в этом магазине еще заказывал?? получал что нибудь ? или хотя бы треки бились?
yourmomentstarts.shop – Found some amazing motivational content here, really starts my day strong.
discoveryourpotential.click – Great platform for personal growth, love the positive and uplifting tone.
dreambelieveachieve.shop – Found some great messages here, truly boosts my morning mindset.
findsomethinggreat.click – Great place to browse, always end up discovering something unexpectedly cool.
classychoiceoutlet.shop – Great outlet deals, perfect place for finding classy affordable pieces.
classychoiceoutlet.click – Stylish collection overall, love the elegant and affordable fashion pieces.
shopandshinehub.click – Great variety here, products look amazing and prices are reasonable.
Приветсвую,форум) Хороший Сортимент на Товар))) УДАЧИ В ПРОДАЖАХ https://nprotopopov.ru Тьфу-тьфу-тьфу… =(
findbetteroptions.click – Love this site, helps compare and choose smarter shopping decisions easily.
Я в последний раз говорю, эта тема – для отзывов о работе магазина. Если вы не можете связаться с продавцом, то не надо писать об этом по сто раз. Если вы хотите узнать о качестве продукции – вам СЮДА !!! Любой оффтоп\флуд прекращаем ! https://nika-land74.ru второй раз заказываю, класнный продукт пришел что 250 что 307 , качество отменное , доставка буквально 3 суток
dreambuycollection.click – Beautiful selections here, quality items that truly match their descriptions.
createinspirelead – Navigation seems smooth, product categories appear organized and accessible.
discoveryourpath.click – Beautifully designed site, helps me focus on personal growth daily.
findyourdreamplace – So refreshing to find a travel blog that feels this genuine and cozy.
connectlearncreate.click – Amazing community vibe, love the focus on creativity and learning together.
createinspirelead.click – Love the empowering tone here, truly encourages creativity and leadership.
happylivingstore – The layout is simple and cheerful, easy to navigate without clutter.
inspirechangealways – The writing style feels open, warm, and totally connects with readers easily.
startanewjourney – This site feels like a gentle nudge to embrace change with courage.
changeyourdirection – I like how the blog keeps things real while still offering hope always.
findjoytoday – Love how this page keeps joy simple and realistic, not forced or fake.
shopwithstylehub – Everything looks sleek and modern, definitely my kind of shopping vibe.
simplevalueplace – This site makes saving money and finding deals actually enjoyable to do.
startsomethingtoday – The content is short, powerful, and really gets straight to motivation.
explorethefuture – Every post feels forward-thinking yet easy enough for anyone to understand.
startsomethingtoday – Love how motivating everything feels here, perfect for morning inspiration vibes.
learnandgrowtoday – So refreshing to find content that motivates without feeling preachy at all.
freshfashioncorner – The outfit ideas here are super fresh and easy to recreate daily.
findyourpathnow – The advice here feels grounded and actually doable in real life.
trendingstyleworld – Great resource for finding what’s trending without endless scrolling or ads.
purevalueoutlet – Shopping here was smooth and fun, I already found some gift ideas.
modernlivingstore.click – So many creative items here, really updates any home beautifully.
smartfashionboutique.click – Stylish and modern pieces, definitely my go-to for classy fashion.
yourdailytrend.click – Great source for everyday fashion inspiration, always something new featured.
everydaystylecorner.click – Love browsing here, always find stylish items that suit my taste.
everydaystylecorner – Great mix of casual fashion, accessories, and lifestyle inspiration throughout the posts.
getmoreforshop – This site really lives up to the name, great deals everywhere I look.
buildsomethingnew.click – Inspiring projects here, really motivates me to start new creative ideas.
Исследуйте захватывающий мир онлайн-гэмблинга с увлекательными играми в Frost Queen Jackpots казино вавада . Получите доступ к лучшим слотам и наслаждайтесь захватывающим процессом игры, где удача ваших рук не устоит. Deep Freeze Free Spins, Eye of the Queen Bonus и Treasure Chest Feature – захватывающие возможности, которые ждут вас в этом казино. Новые игроки получат щедрый приветственный бонус, а постоянные клиенты наслаждаются регулярными акциями и бонусами. Присоединяйтесь к Frost Queen Jackpots и погрузитесь в захватывающий мир азарта!
expandyourhorizon.click – Great site for learning and exploring fresh perspectives every day.
ВПН
phillybeerfests.com – Nice to see they have non-beer drink options (for friends who prefer something else).
theworldawaits.click – Inspiring content, makes me want to explore and travel everywhere.
9e2seattle.com – Love the local coverage here, very informative and well-presented overall.
connectwithideas.click – Amazing platform, really encourages collaboration and sharing of new innovative ideas.
inspirechangealways.click – Great resource for positive thinking, content feels genuine and helpful.
chrishallforjudge.com – I shared this with friends who were looking for judicial candidates with depth.
kionnawest.com – Inspiring platform, clearly shares vision and values in a compelling way.
nsfeg.org – Great resource for learning, very informative and well-structured content overall.
yourdailyshoppinghub.click – Convenient and well-organized store, makes daily shopping fast and enjoyable.
orourkeforphilly.com – Volunteer and event info are clearly displayed, makes getting involved straightforward.
happylifestylehub.shop – For higher-value linking options, choosing domains with established content may serve better.
nataliakerbabian.com – Clean design, strong visuals, and a clear voice; makes a standout impression.
smyrnafestival.com – Great resource for planning a visit, thanks for the clear information and visuals.
localphlmarket.com – Easy to navigate and checkout worked smoothly, thanks for the good user experience.
garymasino.com – I appreciate the clear presentation of his specialties and industry experience.
electcateriarmccabe.com – The website’s design feels professional yet approachable, good balance.
trustedleaderscircle.bond – Easy navigation and clear call to actions made the experience straightforward.
newhorizonsnetwork.shop – The site loaded well on mobile too, so checking out on-the-go is easy.
successpathway.bond – The messaging is straightforward and feels credible at first glance.
joinourcreativeworld.shop – Page served via “Index of /” listing, suggests web files rather than a polished online store. :contentReference[oaicite:0]index=0
shopthelatesttrend.shop – For higher-quality linking, aim to reference domains with clear content, clear identity, and good structure.
thinkcreategrow.click – Since there are no visible products or brand info yet, linking may offer limited trust value.
Отличная статья про генераторы картинок помогла определиться с выбором. Попробовал несколько вариантов, сейчас активно пользуюсь двумя из них. Все работают быстро и качественно: сгенерировать изображение
yourdailytrend.shop – Love the trendy picks here, perfect for keeping up with fashion.
exploreamazingideas.click – The lack of visible products or services means the domain is not fully ready for linking.
1911phl.com – Great information on local events, keeps me updated with ease.
cycleforsci.org – I appreciate that you’re making science accessible and community-focused, thumbs up.
cumberlandcountynjvaccination.org – Good that they mention transportation help for those who need it.
bestvaluecollection.click – Found some excellent deals, products are great quality for affordable prices.
oneillforda.com – Overall impression: solid campaign site, informative and easy to engage with.
uncommittednj.org – Great site if you’re looking for a grassroots voice and fresh perspective.
haginsforphilly.org – I shared this link with friends because the vision feels grounded and honest.
natashaforjudge.com – Excellent campaign site, communicates priorities and experience clearly and effectively.
mcalpineinfo.com – Love the detailed info here, very helpful and easy to follow.
dibrunobottleshop.com – I found some great craft beers here, awesome selection and vibe.
imaginelearnexplore.click – Inspiring content overall, really helps spark creativity and curiosity daily.
remiphl.com – Booked a table last minute and they fit us right in, thanks!
hardman4schools.com – Great campaign site, clearly communicates vision and priorities for education.
pmajoe4council.com – Informative site, provides clear insight into policies and council initiatives.
makeimpacttoday.click – Motivational platform, encourages me to take action and make a difference.
discovergreatdeals.click – Love this site, always find amazing deals on quality products.
KEY я так понял ты сделал заказ узнал сумму которую надо оплатить ,оплатил а когда вернулся сумма стала выше на сотку???? купить кокаин, меф, бошки через телеграмм Кто под нос что-то бормочет,
createandgrow.shop – I’d recommend waiting until the site has clear product listings, branding and user trust signals.
9e2seattle.com – Love the local coverage here, very informative and well-presented overall.
findwhatyoulove.shop – I’d recommend waiting until the site includes clear branding, content and a full user experience.
sparxcle.com – Interesting products here, really innovative ideas and practical solutions overall.
modernlivingstyle.shop – Mobile version loaded smoothly on my phone, nice user-friendly site.
simplybestchoice.click – Currently minimal visible content, but I’ll check back later for updates.
оплачивай лучше через киви.самый лучший способ во всех магазах.и перевод идёт в секунду.только обрати внимание на комисию чтоб небыло недоплаты.обычно 2% от суммы перевода купить скорость, кокаин, мефедрон, гашиш трек не работает тишина уже 3 дня прошло >< у всех все гуд а у меня щляпа как так почему ((( ?!?!?!?
chery официальный дилер chery tiggo купить
hopeandlace.com – Found interesting posts yet no visible “Shop” or product section on the homepage.
leanneslifechangingfairies.com – Beautiful and imaginative site, full of magical ideas for everyone.
и как обычно тут все ровно. БОЛЬШУЩИЙ РЕСПЕКТ МАГАЗИНУ. купить онлайн мефедрон, экстази, бошки списались с продавцом,пообщались,договорились.я оплатил заказ и начались долгие ожидания моей заветной посылки.
simonscider.co.uk – Delicious cider options, love the quality and unique flavor choices here.
shopthebesttoday.click – Great online store, easy navigation and fantastic product deals daily.
Всё по теме по ссылке: https://newshay.com/czifrovaya-vs-ofsetnaya-pechat-stikerov-kak-vybrat-dlya-malogo-tirazha
Какая то палевная курьерка купить скорость, кокаин, мефедрон, гашиш выбери категорию для себя :
learntradingtoday.bond – Excellent resource for beginners, explains trading concepts clearly and simply.
https://proarticle.adseon.xyz/1xbet-bonus-code-2026-e130-for-sports-bets/
everydayvaluecorner.shop – The simplicity is a plus, though at times it felt a bit bare—more content helps.
mdcphilly.com – Great local content, keeps community members informed about events and updates.
dankglassonline.com – The name is catchy and memorable — expect a fully stocked store soon.
maltonfestivalofracing.co.uk – Amazing festival coverage, really captures the excitement of racing events beautifully.
Updates on this topic are here: https://beauty-worthen.com/266452
globalmarketplacehub.click – Domain is active, but I couldn’t find live product listings or branding yet.
У меня была, проси того кто продал все перепроверять- люди могут ошибаться ! купить Кокаин, Мефедрон, Экстази Странно все как то..
findyourperfectdeal.click – For higher-quality linking now, consider alternatives with visible content and authority.
dailyessentialfinds.bond – Once fully live, this could be a strong anchor for relevant content.
https://www.woll2woll.com/profile/mdraselminhaj2111690/profile
purebeautytrend.shop – On mobile the page loaded but content was minimal and sparse.
motivilovesmusic.com – If they add more content this could be a great resource for fans.
trustedleaderscircle.bond – On mobile the site loaded decently although more depth would boost trust.
successpathway.bond – Shared it with a few peers; we’ll keep an eye on its development and content updates.
Ищете актуальные зеркала Кракена? У нас самая полная информация о зеркалах Кракена на сегодняшний день. Узнайте, как обойти блокировку и получить доступ к Кракену. Список рабочих зеркал Кракена для удобного доступа. Безопасные и проверенные зеркала для вашего комфорта. Не упустите шанс пользоваться Кракеном без проблем и задержек. Подробная информация о зеркалах Кракена и способы их использования
simplybestchoice.shop – Great product variety, everything feels affordable and high quality overall.
brightnightpdx – Just stumbled across this site and feels really creative and stylish.
А ВОТ Я ТОЖЕ КИПИШЕВАЛ ПО СЧЕТУ ТРЕКА НЕ БИЛСЯ ТОЖЕ ПОЗВОНИЛ В КУРЬЕРКУ СКАЗАЛИ ОТПРАВЛЕННО И СЕГОДНЯ К ВЕЧЕРУ ВСЕ ОТБИЛОСЬ ЖДУ ПРИХОДА ПОСЫЛКИ. ПОТОМ НАПИШУ КАК ЕСТЬ. ПРОШУ ПРОЩЕНИЯ У ЧЕМИКАЛА ЗА ПЛОХИЕ ПОСТЫ, ДУМАЮ ПОЙМЕТ))) УЖЕ ДАВНО ТУТ БЕРУ НЕ РАЗУ НЕ КИНУЛ НИ ОДНОЙ ЗАДЕРЖКИ ВСЕ ПРОСТО НА 100%. купить скорость, кокаин, мефедрон, гашиш А какой ты адрес хотел что бы тебе написали если ты заказываешь может ты данные свои для отправки до сих пор не указал и в ожидании чуда сидишь
iswrphilly.com – Very professional organization, provides helpful resources and information for all users.
playfuel.co.uk – Great gaming products here, everything feels fun, creative, and high-quality.
shopthebesttoday.click – Great online store, easy navigation and fantastic product deals daily.
хD..ну и мне такое же скажи… купить скорость, кокаин, мефедрон, гашиш супер !!!
nomnomnomfordogs.com – The treat selection looks high-quality and the reviews are positive.
dreambuyworld – Visited the store and the interface looks clean, but I couldn’t verify much about their provenance.
ім’я дамір походження
всё чётко, ровно, от души скоро буду ещё заказывать ) Пришло быстро конспирация на все 100% ! купить Кокаин, Мефедрон, Экстази Спасиба магазину за представленный ДРУГОЙ МИР!
harrietlevinmillan.com – Informative and well-written content, really highlights expertise and knowledge clearly.
nextrealm.click – Interesting concept, love the futuristic vibe and creative presentation overall.
learntradingtoday – Will bookmark this resource, seems like a reliable place to sharpen my trading skills.
wrestlingac – Navigation is intuitive, I didn’t feel lost and found what I needed quickly.
buildyourdreamtoday – Feels like a brand that takes care in presentation and customer impression.
unitedbygoal – The site has a strong mission vibe, really feels purposeful.
asterixfilm.co.uk – Fantastic movie content, perfect for fans of animation and classic films.
cepjournal – I found the layout a bit confusing, lots of content but hard to pin focus.
strategicgrowthalliance – Site navigation is smooth, I like how the menu adapts on mobile.
forexlearninghub – I’ll keep an eye on it and maybe revisit once more content is posted.
foruminvestmali – I visited the site and while the event concept seems interesting, I found minimal recent updates or substantial investor testimonies.
pepplish – The site layout made me want to browse every flavor option offered.
inspireeverydaylife.shop – Browsed via phone and the site loaded well — nice mobile responsiveness.
trabas007hoki – I like the color theme, it’s simple yet looks really professional.
flourandoak – I bookmarked your page because your offerings look unique and fresh.
togetherwerise – If you’re considering partnership or purchase, check how long this brand has operated.
магаз походу отвечает только когда ему пишут и он в сети, на старые сообщения не отвечает. купить скорость, кокаин, мефедрон, гашиш Хотя я знаю почему всех слабо торкает , всё дело в неверном приёме препарата ! Весь форум облазил , но этого способа не наблюдал . Пусть не приятно но стоит того . Порох под язык . Доза меньше , эффект быстрей и ярче . Хотя это личное дело каждого , песня не об этом .
dreamcreateinspire.shop – Beautiful design, love the inspiring message and creative energy here.
pp4fdr.org – Important initiative, shares valuable guidance and updates in a clear manner.
thebestplacetoshop.shop – I liked the variety of gadgets and gifts featured, great for browsing.
bestdealsforlife.shop – For now, trust signals such as “About Us”, reviews or detailed products are missing.
Заранее извиняюсь за оффтоп,просто решил сразу спросить ,чтобы не забыть.ответ будьте добры в ЛС. купить Кокаин, Мефедрон, Экстази chemica l-mix.com,объявитесь на соседнем форуме(СпФН),вас там ОООООООчень заждались..!
Сервис DRINKIO понравился с первого заказа. Всё быстро, удобно и надёжно. Ассортимент хороший, видно, что компания работает с проверенными поставщиками. Радует, что можно заказать в любое время, без лишних ограничений – https://drinkio105.ru/
urbanmatrix.click – Modern and stylish concept, offers great insights into urban innovation.
я на лестнице один, купить Кокаин, Мефедрон, Экстази Они бывает работают очень хорошо, бывает тупят и парят мозги…. нуна вздрочить их отделение….
theworldawaits.click – Inspiring content, makes me want to explore and travel everywhere.
ks4thekids.com – Wonderful platform for children, lots of creative learning opportunities provided.
Мне обещали бонус за задержку в 5 + 3 =8 грамм , так и прислали +))) спасибо.+))) купить Кокаин, Мефедрон, Экстази но только если мусора захотят найдут. просто мусора еслиб хотели найти , то давно бы уже посыль пришла с сопровождением.
cs-nippon-cp – I couldn’t locate clear user reviews or independent feedback; checking external sources would be smart.
theworldawaits.click – Inspiring content, makes me want to explore and travel everywhere.
РФ. Западно – европейская её часть ) https://tech43.ru Согласен магазин хороший, знают свое дело!
Кракен онион наркошоп – лучшее место для покупки качественных наркотиков и других запрещенных веществ. Здесь вы найдете широкий ассортимент товаров высокого качества по доступным ценам. Наш магазин предлагает конфиденциальные и безопасные услуги для всех клиентов, гарантируя анонимность и быструю доставку. Покупайте у нас и получайте удовольствие от качественных продуктов без риска для своего здоровья. Не упустите возможность попробовать лучшие наркотики от Kraken!
ks4thekids.com – Wonderful platform for children, lots of creative learning opportunities provided.
Всё получил свой АМ. Порошок кремового-оранжевого цвета, кстати полная растворимость на поровой бане. Так что не знаю кто там чо писал, помоему товар заебись! Как высохнет отпишу трип репорт от этой поставки… https://burhanim.ru Заказывал небольшую партию)) Качество отличное, быстрый сервис)) в общем хороший магазин)
rosetemplates – One suggestion: adding more user reviews or case-studies would build further trust.
theworldawaits.click – Inspiring content, makes me want to explore and travel everywhere.
28darlingstreet – The site looks clean and professional, very inviting for a dinner out.
lifestyleinspirationhub – Would love to see more detailed product info and user reviews for confidence.
moesboardwalk – I’ll keep an eye on upcoming dates and what specials they might run on the boardwalk.
bloemhill – I’d like to see more info on shipping or delivery zones just for clarity.
theperfectgiftshop – Overall impression: good potential, just do a bit of due diligence before major orders.
yourdailyupdate – If you’re planning to purchase, I’d recommend checking payment security and return policy carefully.
trendinsight – The homepage has a good first impression, clean layout and modern visuals.
brauhausschmitzoktoberfest.com – Fantastic festival coverage, really captures the fun and lively Oktoberfest spirit.
trendyfindshub – The branding is appealing, but checking return policy beforehand would be wise.
connectdiscovergrow – I like the brand name; it suggests learning and growth which is appealing.
getinspiredtoday – Navigation feels smooth, the categories are clear, which is nice for easy browsing.
Хорошо работает народ)) https://jk-sibirskiy.ru хD..ну и мне такое же скажи…
envolavecning – Overall impression: strong creative vibe, good potential; just ensure you check fit, shipping, and design details.
rebeccacaridad-manzanita – The portfolio has a calm, creative energy—very inspiring for anyone into visual arts.
engagement-forum – For users outside the core region it serves: check logistic factors, time zones, costs and refund policies.
madmadedesigns – Overall a promising site with good visual appeal—just proceed with standard caution for new-to-you online shops.
theworldawaits.click – Inspiring content, makes me want to explore and travel everywhere.
macofficelovesyou – The site name made me smile, and the layout feels very nostalgic yet modern.
clubinorout.com – Great nightlife guide, keeps me updated on clubs and events easily.
Это закон, хороший отзыв мало кто оставляет, а вот говна вылить всегда есть желающие вот и получается так, те у кого все хорошо, молчат и радуются купить Кокаин, Мефедрон, Экстази Адекватным людям ценящих проффесианолизм рекомендую реактивы тут тарить…
joebobsaveschristmas – If you’re into holiday-themed horror, this looks like a creative shot.
sega-live – I took a look at this domain, and while the design is visually nice, the actual company background and credibility aren’t clearly established.
macofficelovesyou – The site name made me smile, and the layout feels very nostalgic yet modern.
обо всем думаем ) но не сразу купить Кокаин, Мефедрон, Экстази Пожалуйста :ok: Спасибо за отзыв.
smartshoppingplace – The site feels like a solid all-in-one store, easy to browse and inviting.
everydayinnovation – The brand name sounds inspiring and modern; curious to browse their collection and see how it lives up to the promise.
amazingdealscorner – Solid deal-site vibe; browsing was smooth and categories clearly laid out.
jojoanime10th – Looks like a fun anime-themed project; the visuals really pop with color.
заказал 5-IAI , прислали Methoxetamine, разность дозировок сами знаете, в итоге еле откачали…. купить Кокаин, Мефедрон, Экстази я вчера связался с менеджером в аське, тот сказал что если ему отпишут – разберётся… Попробуй напиши днём, а не под утро )
жду пока ответят, обана повдер кинул на 29000….но прочитал и понял что магаз супер, жду в скайпе селлера! купить Мефедрон, Бошки, Марихуану Как связаться можно
iswrphilly – The community-focused vibe here feels genuine, great to see local engagement online.
shapeyourdreams – The phrase gets me motivated! Would like to see more about the product story or what makes it unique.
believeandcreate – Always something thoughtful to read here, helps me stay positive daily.
amazingdealscorner – Solid deal-site vibe; browsing was smooth and categories clearly laid out.
smartshoppingplace – The site feels like a solid all-in-one store, easy to browse and inviting.
Продолжаем работать, в этот раз чуть больше берем 🙂 очень хорошие скидки дает постоянным клиентам обращаетесь !! купить онлайн мефедрон, экстази, бошки Конспирацию посылок наладили? А то такой товар, а выписать не могу – стрёмно, если просто гриперы в конверте… И отпишите по качеству 5 мео дмт!
hanayaka-na-life – Elegant and serene design, the Japanese aesthetic truly shines through beautifully.
everydaychoicehub – “Choice hub” feels like a central spot for variety—nice for finding items you might not expect.
https://uroki-igry-na-skripke.ru/
findsomethingamazing – Such a fun site to explore, always discovering cool new stuff.
everymomentmatters – The name hits emotionally, good for meaningful purchases; just check the fine details.
dreamdealsstore – Found something I didn’t even know I needed, awesome experience.
thebestvalue – Found something I was hunting for, super happy with how easy it was.
магазин ровный купить кокаин, меф, бошки через телеграмм В джабере орудует фейк, причем у него такой же адрес джабера как и у меня. Джабер в скором времени сменю, в джабере заказы не принимаю. Будьте бдительны
shopwithhappiness – Love the cheerful tone; browsing here actually feels positive and easygoing.
https://uroki-igry-na-skripke.ru/
https://uroki-igry-na-skripke.ru/
https://khelafat.com/blogs/38674/Code-Promo-1xBet-2026-1XBONO200-Bonus-jusqu-%C3%A0-130
brightstylecorner – I like how each section showcases unique pieces with great detail.
everydaychoicehub – The design is clean and the tone is friendly, keeps me coming back.
discovernewhorizons – Really enjoying the topics here, they push me to explore different possibilities.
modernstylemarket – Great name and the design looks sharp—perfect for trend-savvy shoppers.
findbetteropportunities – The advice here feels real and useful, not just generic inspiration.
discovergreatoffers – Straight to the point: you’re promised “great offers”—good for bargain-hunters if service and shipping align.
shapeyourdreams – If you’re looking for calm motivation, this site nails it beautifully.
globalfashionfinds – The quality and selection are really impressive for an online store.
trendylifestylehub – Just discovered this site and it’s filled with wonderful lifestyle inspiration.
findyourinspiration – A nice mix of motivation and reflection — found a few gems I’ll revisit.
findyourowngrowth – Always find something new that helps me think differently and improve.
Сейчас по России что то не видно вас.Только пожелать ветра в парус,адекватных клиентов по меньше шкур купить Мефедрон, Бошки, Марихуану Либо прекращаем флудить либо начну выдавать преды. Сами должны понимать что под новый год почтовые службы перегружены.
globalfashionfinds – Perfect site for fashion lovers, always something new to discover here.
findyourfocus – I like how practical the advice feels, very down to earth approach.
trendsettersparadise – Absolutely loving the fashion vibes here, so fresh and creative.
dailychoicecorner – The variety of items surprised me, it’s like a cozy online bazaar.
urbanwearoutlet – Stylish urban fashion outlet feel, lots of potential if the sizing and quality hold up.
остался дико не рад, но селлер быстро пообещал кидануть бонуса при следующей покупке. надеюсь, не пожадничают купить Мефедрон, Бошки, Марихуану СПАСИБО :pink_eye.: ТУТ ВСЁ РОВНО!!!!!!!!!
opennewdoors – A metaphorical name that feels encouraging; ideal for exploration or finding fresh options.
startyourjourneytoday – The motivational tone of the brand instantly boosts your mood while browsing.
inspiredthinkinghub – I like how they frame the brand as a place for ideas, not just shopping.
у кого взять собрался его ? купить Мефедрон, Бошки, Марихуану Что особо порадовало – скидывали несуществующий трек еще задолго до отправки, который, конечно, не бился или показывал какую-то х*иту.
кракен зеркало
learnexploreachieve – Inspiring brand name; if they deliver educational tools or courses this could be a good fit.
dreamcreateachieve – Full of ambition in one line—makes me think this brand supports creative and lifestyle change.
creativegiftplace – So many thoughtful gift ideas; perfect for finding something personal and unique.
Ха ха ребята смотрите беспредел! попробуйте написать правильно жабу ТСа и получится то что у меня, как бы с ошибкой! СКРИПТ! купить кокаин, меф, бошки через телеграмм Благодарен за заказ во вторник оплатил – в пятницу / утром / товар получил
findsomethingunique – The promise of uniqueness is appealing—if the products deliver, this could be a go-to for special finds.
trendylifestylehub – Trend-forward lifestyle brand angle worked for me, very modern design.
classytrendcollection – The products feel trendy yet elegant, really fits the “classy” branding well.
Какое палево ты очём? https://copterfix.ru Слышал магазин работает отлично и клады качественные делает ))
brightnewbeginnings – The name gives a fresh start vibe; nice for seasonal or motivational purchases.
службу спрс давным давно забросить необходимо.. https://gadziyan.ru Жаль туси в наличии нет. хотелось именно тут взять. а как скоро появится не известно
dailytrendspot – Feels like a stylish marketplace where you can discover cool new finds.
mystylezone – Simple and stylish brand name, great for a fashion-oriented site where personal style matters.
simplystylishstore – Clean aesthetic and clear shopping experience; nice for simple, polished purchases.
urbanstylemarket – Good value for trendy clothing, impressed by the pricing and selection here.
Две дороги для Артёма, https://alvian-energo.ru Селлер сказал что ур6 курёха!:) походу новая альтернатива дживу
learnsomethingeveryday – Highly recommend this site if you love discovering something new daily.
yourstylematters – I like the empowering message behind the name, style should always be personal.
findyourinspiration – Very motivating messaging; makes me think of product categories that spark ideas or renew your look.
оТЛИЧНЫЙ МАГАЗ НАСЛЫШАН https://halaldevelopment-partners.ru с чего они тебе отзывы писать будут если они груз две недели ждут? они че тебе экстросенсы и качество могут на расстоянии проверить? и извинений мало ты не на ногу в трамвае наступила следующий раз пусть магаз компенсирует бонусами за принесенные неудобства! кто со мной согласен добавляем репу!
trendshopworld – Global-sounding brand, good for catching wide variety of trends.
findbetteropportunities – Ambitious name—makes me curious about what “better opportunities” means for customers.
fashiondailydeals – Prices look great for trendy pieces, could easily become a go-to fashion stop.
shopthenexttrend – Found some interesting pieces I hadn’t seen elsewhere—nice surprise.
Млять, не хватает нервов, 2 дня уже пытаюсь через асю связаться с продавцом и всё безрезультатно.Ладно бы вообще не ответил, ато написал что ок и не счета куда делать перевод,и ничего. https://job-in.ru Раньше розницей занимались благодаря вашему опыту,сейчас время другое,стабильная честная работа)
findyourinspiration – Very motivating messaging; makes me think of product categories that spark ideas or renew your look.
brightstylecorner – The layout’s bright energy instantly catches your eye, really uplifting vibe overall.
perfectbuyzone – This site saved me time in finding good product options today, thumbs up.
yourvisionmatters – Empowering message and good styling; strong brand identity right out of the gate.
кракен зеркало вход
https://www.intensedebate.com/people/xbetpromocode1
yourstylematters – Love the friendly tone and how the site seems genuinely helpful.
по поводу треков выяснять буду завтра лично т.k. сегодня выходной в России https://argungb.ru/chelyabinsk.html Что касается Самой СПСР то в ней ничего такого страшного нет…
findsomethingamazing – Love browsing here, every visit brings something unique and creative.
thebestcorner – Simple and strong branding—makes you believe you found a great spot for deals.
happyhomefinds – I like how the décor pieces are unique and budget-friendly.
https://jszst.com.cn/home.php?mod=space&uid=6406520
bestpickscollection – The visuals are appealing and the site seems easy to browse.
discoverfreshperspectives – Feels more boutique or niche, good for curated products or design-forward picks.
uniquevaluecorner – Good selection of affordable items, name fits perfectly with what’s offered.
theperfectgift – Site loads smoothly and the categories make browsing super easy.
createimpacttoday – The design is clean and inviting, makes reading feel easy and calm.
https://www.babelcube.com/user/1xbet-bet
expandyourmind – The vibe here is calm but intellectually engaging, really liked that.
Здесь ровно! Магазин очень хороший, а главное цены в нем ГИБКИЕ к любому подход есть : ) Пыть-Ях купить кокаин, мефедрон, гашиш, бошки, скорость, меф, закладку, заказать онлайн спасибо и ВАМ !!
Our Spanking videos feature amazing performers Spanking is very sexy and fun| Discover the best online spanking porn Zoey Ziptie|
purechoiceoutlet – Clean design and simple layout, made browsing feel effortless and enjoyable.
19-го адрес был дан. https://tech43.ru/muravlenko.html Успехов вам и поменьше всяких заморочек )))
shopwithhappiness –The layout is clean and welcoming, made exploring really enjoyable.
purechoiceoutlet – Overall pleased with the find today—good outlet feel and nice presentation.
это манера такая сдержанная или удовлетворительное=на троечку https://appworldstore.ru/beloretsk.html Хотелось бы услышать мнение продавца, по этому поводу
discoverbetterdeals – Found some great bargains here, feels like a true hidden gem online.
fashiondailydeals – Found a few unexpected gems—really liked discovering them on this site.
brightnewbeginnings – Bookmarking this one—will revisit for regular inspiration and fresh perspectives.
yournextadventure – Love how the layout highlights adventures in a way that makes me want to book.
trendshopworld – (Note: small typo in link but format preserved) Found some stylish pieces that caught my eye today.
uniquevaluecorner – Bookmarking this one—would be nice to check back for new options.
everymomentmatters – The tone is reassuring and the visuals are easy on the eyes—very welcome.
shopthedayaway – Site loads quickly and looks well designed—made browsing enjoyable.
luxuryfindsonline – There’s a premium feel to this site, which gives confidence when browsing.
inspiredthinkinghub – This site feels like a good space to grow your mindset and learn.
modernideasnetwork – Already bookmarking this; will revisit when I’m in the mood for new perspectives.
dreamdealsstore – Impressed with the variety and deals, will definitely shop again.
connectsharegrow – Overall a positive experience, excited to see how this platform evolves.
moveforwardnow – Overall very inspiring—this will be one of my go-to stops for motivation.
полность с тобой согласен https://puzzlepedia.ru/abakan.html Весом по 1 гр
trendandstylehub – Love the trendy picks and layout, everything looks well curated and stylish.
Что особо порадовало – скидывали несуществующий трек еще задолго до отправки, который, конечно, не бился или показывал какую-то х*иту. https://goldrub.ru/fryazino.html Первый раз слышу такой непонятный отзыв о 4фа,все кто берет его как и 2c-i говорят что у нас он лучший … по jte907 если не умеете с ним работать зачем берете…? есть постоянные оптовики кто берет только его, и этот продукт нареканий не вызывает. Многие “Селлеры” под видом jte продают 2201 и это факт! у нас этот продукт в оригинале. МХЕ у нас такой пришел, мы не кричим что его чистота 99%, и что качество его не очень мы предупреждали всех…
creativityunlocked – Inspiring content, really helps spark new ideas and creative thoughts.
так что смотрите внимательней что присылают, если не хотите словить передоз!!! Кизилюрт купить кокаин, мефедрон, гашиш, бошки, скорость, меф, закладку, заказать онлайн Хорошо работают реально ! ! ! рега МН-35ф реально индика суровая , наиболее множество сходств нашёл с натуралом , по Мне так это наиболее приближенный каннабиноид ..
shopanddiscover – Fun shopping experience with great variety, will definitely visit again soon.
что то не могу зайти на сайт ( https://burhanim.ru/dzerzhinskiy.html Спасибо!Не надо!
findsomethingunique – Interesting finds here, definitely stands out from regular online stores.
classytrendcollection – The layout is sleek and navigation is easy, made exploring new looks fun.
3-раз заказал вот недавно трек пришел но небьется ни на сайте ни по телефону((( подожду чуток https://sushi70.ru/urus-martan.html Кстати в другом доверенном магазине у меня тоже была задержка в курьерке , трек не бился, в базе тоже его не было при прозвоне в курьерку…может действительно из-за Олимпиады (или во время ее проведения) курьерки стали чаще проверять..
кракен сайт зеркало
Войти на сайт кракен через актуальное зеркало.
thebestcorner – Simple and strong branding—makes you believe you found a great spot for deals.
Выходные же. В понедельник наврятли отправить успеют. https://architectit.ru/cheboksari.html качество вышка
creativegiftplace – Overall a positive first visit; excited to check the updated selections soon.
startsomethingawesome – Great user experience, everything loads fast and the layout’s really neat.
simplystylishstore – The layout is clean and user-friendly, which makes shopping more fun.
yourfavoritestore – Everything feels organized and simple, loved the product variety here.
simplelivingstore – Overall great first impression—will definitely check back to see new arrivals and curated finds.
discoverpossibility – A very positive first visit—looking forward to reading more and staying inspired.
startsomethingawesome – A solid find for anyone looking to start something new with intention and confidence.
dreamcreateachieve – Discovered some practical tips and real encouragement—very welcome.
modernhometrends – The tone is friendly and the selections feel very well curated—makes browsing fun.
growtogethercommunity – Bookmarking this one—go-to for when I’m looking to connect with positive collective energy.
discoverfreshperspectives – The mix of ideas is versatile—something here for both reflection and action.
modernhometrends – Excellent online experience, everything loads fast and looks super modern.
thebestcorner – Love the vibe here, everything feels friendly and super easy.
yourdailyessentials – Good mix of everyday essentials; feels like a reliable place to browse.
unlocknewpotential – I love discovering new shops like this, offering good potential for décor.
https://sites.uw.edu/pols385/2020/05/18/in-response-to-we-are-told-not-to-cry-over-spilled-milk-by-carbam/
shopwithpurpose – Great concept and thoughtful message behind this platform, I like it.
да да ))) 100% ))0 Обнинск купить кокаин, мефедрон, гашиш, бошки, скорость, меф, закладку, заказать онлайн Привет всем!
Страшно , но хочется и потом сам не попробуеш не узнаеш ) https://si-vif.ru/feodosiya.html Оплатил заказ, жду селлера.
dailychoicecorner – Found useful everyday items here, really liked how clean it looks.
А где прайс глянуть? Заинск купить кокаин, мефедрон, гашиш, бошки, скорость, меф, закладку, заказать онлайн Тьфу-тьфу-тьфу… =(
purefashionhub – Stylish layout with trendy fashion options, easy to browse and shop.
Вообщем фейк крассавчик пошагово и все грамотно сделал, развел) Самара купить кокаин, мефедрон, гашиш, бошки, скорость, меф, закладку, заказать онлайн всех с новым годом и удачных покупок
smartshoppingplace – Smooth navigation and solid deals, feels trustworthy and efficient.
thinkbigmovefast – The aesthetic is modern and clean, makes shopping feel easy.
superbet supergame
Классный магаз, почитал отзывы, нам в киров бы не помешал такой движ. Ассортимент огонь, давайте в наш славный город. Всем щастья! https://alekskhaustov.ru/pyatigorsk.html Трек есть +Бонус от души как придет отпишу
staymotivatedalways – Positive and uplifting space, love reading motivational content here.
https://plazist.localcitation.site/code-bonus-1xbet-2026-e130-offre-sport-2026/
Вчера оплатил, сегодня уже трек скинули. Пока все ровно, посмотрим что придет….. https://jk-sibirskiy.ru/izhevsk.html самый дешёвый магазин из доверенных – это этот!
discoverpossibility – Impressed by the layout and clear navigation—feels professional.
moveforwardnow – Nice site overall, seems trustworthy and well-designed for users.
modernstylemarket – The design is modern and smooth, browsing felt effortless today.
freshstyleoutlet – Modern and clean design, great mix of new fashion trends and ideas.
growtogethercommunity – Found something interesting here, can’t wait to explore more of their range.
shopthenexttrend – Found a few items I like already, looking forward to exploring more.
discoverbetterdeals – The layout is modern and easy on the eyes, nice job with design.
urbanwearoutlet – Just skimmed through, great visuals and easy to browse overall.
everydayinnovation – The visuals and layout are pleasant, makes me comfortable browsing further.
explorecreativeconcepts – Found a couple of nice items, will revisit when I have time.
thefashionedit – Great site so far, clean design and nice browsing experience.
https://farhankhatri663.gamerlaunch.com//forums/viewtopic.php?p=40635801&gid=607465#40635801
learnexploreachieve – Browsing was smooth, everything seems laid-out neatly and clearly.
explorecreativeconcepts – The navigation menu is intuitive and the page structure feels thoughtful.
Админ по аське с кем связался адекват=))) радует.Приятный сайт цены тоже радуют сделал заказ=)) буду ждать. Качество Каличество отпишу https://nastavnik124.ru/ust-ilimsk.html Всем, как и писалось средняя компенсация 50%
reachhighergoals – I’ll bookmark this site, excited to come back and see what else they offer.
buildthefuture – Just bookmarked this—looks like a promising place to check again soon.
dealsanddiscounts – I found some good items here, will revisit when I have time.
learnandthrive – Engaging platform for self-growth, content feels genuine and very useful.
Получил вчера конвертик от вас . Спасибо , оперативно . Не знаю почему почти все недовольны 5иаи , но такого психодела давненько не переживал . Потрясён до мозга костей . https://origamishop.ru/dzerzhinskiy.html мои близкий поделился вашими контактами когда про бывали ваш товар)
Мне обещали бонус за задержку в 5 + 3 =8 грамм , так и прислали +))) спасибо.+))) https://alekskhaustov.ru/egorevsk.html Магазин,лови от меня большой и жирный “+”. Заказ пришёл в течение 3ёх дней.Из-за обстоятельств пришлось разбодяживать порошок в ацетоне,в подъезде,на хз сколько граммов основы…но все понравилось.все и всем довольный.
следить не могли однозначно Великий Новгород купить кокаин, мефедрон, гашиш, бошки, скорость, меф, закладку, заказать онлайн Работал с магазином спасибо всё красиво!
https://shkola-vocala.ru/shkola-igry-na-gitare.php
findyourowngrowth – The tone is friendly and inviting, feels like a good place to learn.
трансы тюмень
findyourperfectlook – Just stumbled onto this site, the design looks clean and fresh.
mystylezone – The design choices feel smart and the user-interface is intuitive and clean.
styleandfashion – The layout is modern and browsing felt smooth and effortless.
everydayvaluehub – The website looks clean and slick, nice first impression.
Not sure how to register at betwinner? The full process is explained step-by-step at https://bet-promo-codes.com/sportsbook-reviews/betwinner-registration/ — easy and beginner-friendly.
Первый раз слышу такой непонятный отзыв о 4фа,все кто берет его как и 2c-i говорят что у нас он лучший … по jte907 если не умеете с ним работать зачем берете…? есть постоянные оптовики кто берет только его, и этот продукт нареканий не вызывает. Многие “Селлеры” под видом jte продают 2201 и это факт! у нас этот продукт в оригинале. МХЕ у нас такой пришел, мы не кричим что его чистота 99%, и что качество его не очень мы предупреждали всех… купить скорость, кокаин, мефедрон, гашиш Как и было обещано, адрес оператор прислал где-то в 23.
https://68fc99c26f549.site123.me/blog/1xbet-casino-bonus-code-1-650-210-spins
Если растворяется без подогрева – то не нужно. В ацетоне как правило (если продукт чистый) так и растворяется, и в осадок не выпадает, на спирту придется немного подогреть купить кокаин, меф, бошки через телеграмм Захожу 24-го, фигакс, бан.
https://hamod1.livejournal.com/70532.html
https://kuklanvt.info/apartament/
Дошло за 3 дня , качество отличное , буду только с этим магазом работать. купить Мефедрон, Бошки, Марихуану Вердикт:
нарколог на дом санкт-петербург
https://www.mariebrowning.com/profile/sarabantohora14477795/profile
Скрины с радикала не грузятся. Увы сейчас доказать что-либо сложно, видимо магазин не первый раз кидает уже по отточеной цепочке. купить кокаин, меф, бошки через телеграмм здравствуйте , это от региона зависит . Доставка индивидуально обсуждается в ЛС .
Почему страшно? купить Мефедрон, Бошки, Марихуану Всем доброго времени суток!!!
http://www.google.bf/url?q=https://www.maxwaugh.com/articles/1xbet_promo_code_sign_up_bonus.html
Paris sportifs avec 1xbet rdc apk : pre-match & live, statistiques, cash-out, builder de paris. Bonus d’inscription, programme fidelite, appli mobile. Depots via M-Pesa/Airtel Money. Informez-vous sur la reglementation. 18+, jouez avec moderation.
привествую мои друзья форумчане , не https://sad16kislovodsk.ru The Best!!!!!!
http://www.google.ps/url?q=https://amt-games.com/news/1xbet_cameroon_register_bonus_code.html
Plateforme parifoot rdc : pronos fiables, comparateur de cotes multi-books, tendances du marche, cash-out, statistiques avancees. Depots via M-Pesa/Airtel Money, support francophone, retraits securises. Pariez avec moderation.
упаковка – неплохо, но не идеально. Особенно глупо, когда в описании отправления пишут “Косметика”, а там, бл*ть, пачка сигарет. Оочень странно на меня смотрели в офисе спсра, знаете ли. 4/5 https://spiegelimspiegel.ru Доброго времени суток друзья женскую половину человечества с праздником))))
amazingdealscorner – Good value product picks; I’ll remember this site for the next purchase.
А для кого указан Major Express (для СНГ)?Да,можно. купить Кокаин, Мефедрон, Экстази Магазин знает как удалить учетку что бы закрыв чат в жабере у вас исчезла запись из списка контактов. У меня так было вчера. Адрес не давали в течении 2х часов а под утро сегодня и вовсе исчезли из контактов.
Оформите онлайн-займ https://zaimy-69.ru без визита в офис: достаточно паспорта, проверка за минуты. Выдача на карту, кошелёк или счёт. Прозрачный договор, напоминания о платеже, безопасность данных, акции для новых клиентов. Сравните предложения и выберите выгодно.
Бро, доброго дня. В личку реквы на оплату жду, на сайт тоже попасть не могу… купить Кокаин, Мефедрон, Экстази про тусиай ….. что я могу сказать про тусиай от этого магазина…. пойду лучше трип-реппорт напишу…. такой тусишки ещё не ел)
Хорошо работает народ)) купить скорость, кокаин, мефедрон, гашиш на вкус – сода.
Прямо сейчас: https://zebraschool.com.ua
Желаю развития ветке! купить Кокаин, Мефедрон, Экстази магаз клёвый ,:bravo:сервис на высоте
На каком сайте сейчас заказать то можно дживик ровный https://kdsed.ru попробуйте установить скайп.
Надеюсь на дальнейшее сотрудничество с магазином! https://vertikal-kursk.ru трек получен, ребятам уважуха:rasta:
отличный магазин, все всегда ровно купить скорость, кокаин, мефедрон, гашиш Админ по аське с кем связался адекват=))) радует.Приятный сайт цены тоже радуют сделал заказ=)) буду ждать. Качество Каличество отпишу
Plateforme parifoot rdc : pronos fiables, comparateur de cotes multi-books, tendances du marche, cash-out, statistiques avancees. Depots via M-Pesa/Airtel Money, support francophone, retraits securises. Pariez avec moderation.
Paris sportifs avec 1xbet rdc telecharger : pre-match & live, statistiques, cash-out, builder de paris. Bonus d’inscription, programme fidelite, appli mobile. Depots via M-Pesa/Airtel Money. Informez-vous sur la reglementation. 18+, jouez avec moderation.
Подробнее тут: https://buybuyviamen.com
Casino 7k приятно порадовало. Реально быстрые выплаты и хорошие акции. Игры работают без задержек https://xn—-8sbalwlcefxak4bw.xn--p1ai/
Брал и не раз в данном магазине, притензий нет, все качественно, оперативность радует! Продовцы дайте информации о CHM – 500, что за зверь? когда в розницу уйдет купить скорость, кокаин, мефедрон, гашиш А вот это очень интересно)))ДК есть он или его нет?В розницу пару г возможно надеюсь закзать?
Всех благ данному магазину!!! купить кокаин, меф, бошки через телеграмм Пожалуйста :ok: Спасибо за отзыв.
уж не маленькие блин, знаете что заказываете наверное ! форум вам на что ? или ты думаешь что у них какой то особенный 250й ? ))) https://yurspecgrupp.ru Я тебе уже все в личке сказал, ты на фейка попал, если такое вообще было.
Complete full body massage with aromatic oils|
психолог онлайн сейчас
Вообщем так, с момента отправки из курьерской службы до рук курьера в нашем городе прошло 3 дня, забрал я значительно позже, но это не суть. купить кокаин, меф, бошки через телеграмм Все верно, до сих пор разгребаем )
Скажи что это? Я тебе помогу:) где хочешь заказать? купить кокаин, меф, бошки через телеграмм Всем привет ни как не могу заказ оформить, помогите,плиз
Наша официальная веб-страница – Вся информация о бренде и его предложениях.
ты в мирку отпиши продавец там купить онлайн мефедрон, экстази, бошки Магазин не чистый на руку. Уже пишет с другого жабера. Народ у кого осталось переписка состарого жабера сверьте ник. И прошу сделать посты что таковое не придуманная мною сказка.
https://vk.com/id7281076 невролог одинцово
хотел узнать по какой причине скайп магазина не в сети со вчерашнего дня? https://lada-togliatti.ru И потом не удивляйтесь, что магазин медленно работает или не отвечает. Попробуйте по 100 раз в день рассказывать что и как разводить, и при этом успевать оформлять заказы.
друг ты о чем говоришь? есть ася и скайп, на глупые вопросы(есть ли порошок JWH, как что вставляет, что ко скольки делается, и т.д.) мы не отвечаем, мы работаем только с людьми которые понимают, что “это” и как это “едят”, парни вот без обид – мы же не википедия… да парни все легал, все анализы делаются на Моросейке… да да да… https://sad16kislovodsk.ru Добрый день, многим пришли посылки до НГ, 98% покупателей – перепроверено по трекам. Если есть вопросы пишите, в скайп или аську. В веточке пожалуйста, только по теме.
вывод из запоя цена
tula-narkolog010.ru
лечение запоя
когда появится новинки?? https://smilefab.ru Ждём вас снова
что значит “самый норм микс” ? 1 грамм 250го на 10 грамм основы вполне нормально. если любитель лютой жести – сделай 1к5 чтоли, будешь улетать в астрал с малюсенького кропалика https://27dverei.ru Ребят какие могут быть сомнения в этом магазе магаз ровный и заслуживает уважения он в доверенных его реклама на шляпе сайта ну это так для тех кто не знает просто реклама стоит 5000$ доларов!
а вот по этой теме отпиши по подробней,точнее о том как там дальше события развиваются?????????? очень волнует данная тема. как же так их просекла легавня???? откуда краснотой веет.??? купить Мефедрон, Бошки, Марихуану Бро слова это хорошо но нам нужен наш клад и не более не кто не хочет тебя винить и общаться сдесь на эту тему а на оборот писать только хорошие отзывы о вашем магазе пойми и ты бро слово паника сдесь не уместно сдесь идет разбор по факту согласись
экстренный вывод из запоя тула
tula-narkolog011.ru
вывод из запоя круглосуточно тула
вывод из запоя круглосуточно
narkolog-krasnodar022.ru
вывод из запоя краснодар
https://www.nedrago.com/forums/topic/top-cricket-betting-strategies-every-beginner-should-know/
бешельме мешельме атакает купить онлайн мефедрон, экстази, бошки Да мы уже поговорили – нормальные ребята вроде) хз, я всё равно полной предоплате не доверяю)
лечение запоя минск
vivod-iz-zapoya-minsk015.ru
вывод из запоя круглосуточно минск
У меня пришел чисто белый зернистый как крупа порошок.Кал. купить Кокаин, Мефедрон, Экстази Вообщем фейк крассавчик пошагово и все грамотно сделал, развел)
жду пока ответят, обана повдер кинул на 29000….но прочитал и понял что магаз супер, жду в скайпе селлера! купить онлайн мефедрон, экстази, бошки задержки очень большие! это плохо, надо вам как то решать этот вопрос
вывод из запоя цена
tula-narkolog012.ru
лечение запоя тула
Тусишки рекомендую дозу от 25 мг. купить Кокаин, Мефедрон, Экстази Братья, у меня вопрос. JV-30 как? Боюсь нарваться на регу с которой крышу сносит. Ответьте пожалуйста.
вывод из запоя цена
narkolog-krasnodar023.ru
экстренный вывод из запоя краснодар
Оформите займ https://zaimy-88.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
Срочные онлайн-займы https://zaimy-65.ru до зарплаты и на любые цели. Минимум документов, мгновенное решение, перевод на карту 24/7. Работаем по всей России, только проверенные кредиторы и прозрачные ставки.
вывод из запоя круглосуточно
vivod-iz-zapoya-omsk013.ru
вывод из запоя круглосуточно омск
Оформите займ https://zaimy-59.ru онлайн без визита в офис — быстро, безопасно и официально. Деньги на карту за несколько минут, круглосуточная обработка заявок, честные условия и поддержка клиентов 24/7.
до 08.01 включительно выходные дни купить Кокаин, Мефедрон, Экстази Я подозреваю, что его посылку спалили на наличие и теперь просто не отправляют.
https://sportdmkd.forum24.ru/?1-14-0-00002063-000-0-0-1762310305
Рабочее
делает вход простым. Ссылки проверены и помогают авторизоваться без рисков.
А со скольки у них скайп начинает работать? купить онлайн мефедрон, экстази, бошки Понимающий меня поймёт.
экстренный вывод из запоя челябинск
vivod-iz-zapoya-chelyabinsk013.ru
вывод из запоя челябинск
http://www.google.cd/url?q=https://aviator-game.su/
KRAKEN сайт вход — это безопасная авторизация. Ссылка кракен маркет и зеркало работают надёжно.
заказ в статусе обработки ))) https://euromotors-auto.ru Всех С Новым Годом! Как и обещал ранее, отписываю за качество реги. С виду как мука, но попушистей чтоли )) розоватого цвета. Качество в порядке, делать 1 в 20! Еще раз спасибо за качественную работу и товар. Будем двигаться с Вами!
вывод из запоя краснодар
narkolog-krasnodar024.ru
вывод из запоя краснодар
https://triberr.com/andrearyoder
Красиво делаете. Так держать! https://igor-vasiliev.ru братишки и сёстры всем мир и харе ругаться!жизнь прекрасна
benefits of hgh bodybuilding
References:
hgh x2 avis – https://mes-favoris.top/item/449984,
Для обхода ограничений используйте кракен онион
. Вход по ссылке безопасен и прост.
вывод из запоя цена
vivod-iz-zapoya-omsk014.ru
вывод из запоя
Всем Мир! Да прибудет с вами Сила! купить скорость, кокаин, мефедрон, гашиш Магазин нормально работает?,а то некоторые говорят что не стоит обращаться в данный магазин для заказов!Фон или фок как твой ник правильно читаеться и пишиться ? отпишись нормальный магаз или нет !
какие манерные нынче клиенты пошли, плюнешь в рожу драться лезут, видете ли ему грубо ответили, я с ТС с момента регистрации общаюсь и не разу он не забуровил даже когда были терки а они поверь были, так что не пизди про невежливое обращение, да и по переписки видно что все ровно, ищи проблему в себе…. купить Мефедрон, Бошки, Марихуану В предыдущих сообщен писал, что заказ по совместке от ЧМ,
вывод из запоя круглосуточно челябинск
vivod-iz-zapoya-chelyabinsk014.ru
вывод из запоя круглосуточно челябинск
Работает. Контакты указаны в соответствующей теме. купить онлайн мефедрон, экстази, бошки единственная существенная проблема данного магазина – отсутствие автоматизированной системы оформления заказов… Вроде прикручивают к сайту, но что то долго уже…
вывод из запоя цена
narkolog-krasnodar025.ru
вывод из запоя круглосуточно
Binary Options Demo: Learn Before You Trade.
Start your trading journey with a Binary Options Demo account and practice risk-free before going live. Sharpen your skills and explore smart strategies at https://terrasseo.jp/
Với giao diện mượt mà và ưu đãi hấp dẫn, MM88 là lựa chọn lý tưởng cho các tín đồ giải trí trực tuyến.
магазин работает на все 100%!советаю! купить скорость, кокаин, мефедрон, гашиш с чего они тебе отзывы писать будут если они груз две недели ждут? они че тебе экстросенсы и качество могут на расстоянии проверить? и извинений мало ты не на ногу в трамвае наступила следующий раз пусть магаз компенсирует бонусами за принесенные неудобства! кто со мной согласен добавляем репу!
Рабочее зеркало кракен сайт — это удобное решение для тех, кто хочет пользоваться сервисом постоянно.
вывод из запоя
vivod-iz-zapoya-omsk015.ru
вывод из запоя омск
Да стопудова честный!!! В этом нет сомнений. А вот с волей Медведя и планом Путина ужиться сложно купить скорость, кокаин, мефедрон, гашиш Посыль получил в течении 5ти дней после оплаты. Быстро!! Отлично!!
вывод из запоя круглосуточно челябинск
vivod-iz-zapoya-chelyabinsk015.ru
лечение запоя
поддерживаю !!!! купить онлайн мефедрон, экстази, бошки В каких пропорциях???
Для быстрого подключения используйте KRAKEN ссылка.
все это только на доверии, белый кристаллический так же может быть 4фа…. https://roomba48.ru Получил. начал разводить на 7 мл ацетона. все выпало в осадок и почти ничего не растворилось. жидкость получилась мутная как молоко. добавил еще 5 мл. вроде более менее, но все равно большой очень осадок. ну и прям так туда 2 коробка основы высыпал и на плитку. все делал впервые, можно сказать наугад. пыхтел через водник. 1 водник и накрывает мама не горюй. час держит и еще полтора отпускает, и состояние потом ппц мутное какое, даже утром проснулся еще в коматозе. все отлично в принципе, только вот отходняк какой-то..
Капельница от запоя в Туле – это необходимая медицинская услуга при алкогольной зависимости, которая помогает детоксикации организма. Вызов нарколога на дом дает возможность получить срочную помощь при алкоголизме в комфортной обстановке. Компоненты капельницы включают вещества, способствующие восстановлению организма: физраствор, минералы и препараты для капельницы. Эффект капельницы направлено на снижение симптомов обстиненции и стабилизацию состояния пациента. Преодоление зависимости от алкоголя требует всеобъемлющего подхода, включая реабилитацию после запоя. Стоимость услугу нарколога различаются, но консультация специалиста является важной для успешного лечения.
搭载智能站群程序,自动化搭建与管理,为SEO项目提供核心驱动力。站群程序
В каких пропорциях??? https://elegant-ts.ru Да хватает придурков, только смысл писанины этой , что он думает что ему за это что то дадут ))) кроме бана явно ничего не выгорит )))! Тс красавчик брал 3 раза по кг сделки и всегда все чётко ! Жду пока появиться опт на ск!
экстренный вывод из запоя
vivod-iz-zapoya-orenburg013.ru
вывод из запоя цена
kuwin sở hữu kho game đa dạng từ slot đến trò chơi bài đổi thưởng, mang đến cho bạn những giây phút giải trí tuyệt vời.
а кто нибудь пробовал все таки эту куреху urb https://shopingdog.ru Проплатил в этот магаз 10.10,трек получил 14.10-сегодня 18.10 трек не бьёться
Чтобы обойти блокировки, используйте кракен магазин. Ссылка подходит как для телефона, так и для компьютера.
вывод из запоя круглосуточно
vivod-iz-zapoya-cherepovec016.ru
лечение запоя череповец
Entdecken Sie die besten Weinverkostungen in Wien auf weinverkostung in wien.
In der Stadt finden sich zahlreiche Weinguter, die eine lange Geschichte haben.
Die Weinverkostungen in Wien sind perfekt fur Kenner und Neulinge. Dabei lernen Gaste die Besonderheiten der regionalen Rebsorten kennen.
#### **2. Die besten Orte fur Weinverkostungen**
In Wien gibt es zahlreiche Lokale und Weinguter, die Verkostungen anbieten. Das Weinmuseum im Stadtzentrum ist ein idealer Ausgangspunkt fur Weinliebhaber.
Einige Winzer veranstalten Fuhrungen durch ihre Kellereien. Dabei erfahren Besucher mehr uber die Herstellung der Weine.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Wiener Weine sind vor allem fur ihre Vielfalt bekannt. Rote Weine wie der Blaue Zweigelt gewinnen immer mehr an Beliebtheit.
Die Bodenbeschaffenheit und das Klima pragen den Geschmack. Die mineralischen Noten der Wiener Weine sind besonders ausgepragt.
#### **4. Tipps fur eine gelungene Weinverkostung**
Eine gute Vorbereitung macht die Verkostung noch angenehmer. Ein neutraler Geschmack im Mund vor der Verkostung verbessert das Erlebnis.
Gruppenverkostungen bringen zusatzlichen Spa?. Ein Weinjournal kann helfen, personliche Favoriten festzuhalten.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
Wien ist nicht nur fur seine historischen Sehenswurdigkeiten bekannt, sondern auch fur seine lebendige Weinkultur.
#### **2. Die besten Orte fur Weinverkostungen**
Zusatzlich konnen Gaste direkt beim Erzeuger kosten.
#### **3. Wiener Weinsorten und ihre Besonderheiten**
Wiener Weine sind vor allem fur ihre Vielfalt bekannt.
#### **4. Tipps fur eine gelungene Weinverkostung**
Gemeinsames Diskutieren uber die Aromen fordert den Austausch.
Не, бро, ну одно дело 250 заместо 50мг, а другое когда даже 250мг не берет. купить кокаин, меф, бошки через телеграмм Извините, если я не знаю вашу продукцию у кого мне тогда спрашивать ?
KRAKEN сайт доступен в любое время через кракен сайт или TOR.
Jwh 203 порошок светло-желтого цвета у них, делал в пропорции 150-200мг на спичечный коробок микса, кролики довольны! 5-IAI пробывал 200мг по кишке, видимо нужно было сразу 300-400мг чтобы понять кайф! купить онлайн мефедрон, экстази, бошки магазина в скайпе не поймать?как можно с вами пообщаться?
вывод из запоя в москве narkologicheskaya-klinika-23.ru .
1xbet giri? 1xbet giri? .
Крутой магаз. Ассортимент радует https://kkadrov.ru Ждать возможно придется дольше обычного, я ожидал 12 рабочих, не считая праздников..
вывод из запоя круглосуточно череповец
vivod-iz-zapoya-cherepovec017.ru
вывод из запоя цена
Актуальное KRAKEN зеркало ведёт напрямую к сервису.
здравствуйте , это от региона зависит . Доставка индивидуально обсуждается в ЛС . купить онлайн мефедрон, экстази, бошки да 203 й тут хороший,только я делал 1 к 15 мне понравилось)
заказал вчера на пробу соточку мн. по прибытию отпишусь) купить кокаин, меф, бошки через телеграмм хочу выразить благодарность оператору за поддержку, очень переживал он меня успакоили!
Лечение запоя капельницей на дому – это эффективный способ лечения алкогольной зависимости, предлагающий множество преимуществ и особенности. В Туле услуги нарколога включают выезд на дом, что позволяет пациентам обратиться за медицинской помощью при запое в привычной обстановке. Преимущества капельницы заключаются в скорейшем восстановлении организма благодаря процедурам детоксикации. Капельницы помогают вывести токсины, улучшить общее состояние, что, в свою очередь, помогает быстрее восстановиться после запоя. Кроме того, наличие поддержки близких в период запоя играет важную роль, так как домашнее лечение алкоголизма создает комфортную атмосферу. лечение запоя тула Тем не менее, есть и недостатки. Например, в некоторых случаях сложно обеспечить необходимый контроль за состоянием пациента. Врачебная консультация на дому может оказаться недостаточной для серьезных случаев. Также стоит учитывать, что не всем пациентам подходят инъекции при алкоголизме.
Магазину огромное спасибо! За купить онлайн мефедрон, экстази, бошки На сколько я знаю в этом магазине пока нет реги!
экстренный вывод из запоя череповец
vivod-iz-zapoya-cherepovec018.ru
вывод из запоя цена
Не, бро, ну одно дело 250 заместо 50мг, а другое когда даже 250мг не берет. https://kkadrov.ru братишки и сёстры всем мир и харе ругаться!жизнь прекрасна
вывод из запоя цена
vivod-iz-zapoya-orenburg015.ru
экстренный вывод из запоя
Я просто уже настолько завязан со сферой Lrc что подмечаю все мелочи. Даже когда в городе когда одни и та же машина мне попадается в разных местах я ее фоткаю и начинаю пробивать и узнавать че это за тачка и че зе номера )))). https://estom29.ru Вы не могли сегодня оплатить заказ, потому что мы сегодня не работаем
Капельницы для лечения запоя – это эффективный метод помощи, который способствует пациентам справиться с пристрастием к алкоголю. Врач нарколог на дом оказывает профессиональную поддержку при алкоголизме, осуществляя детоксикацию организма и восстанавливая его функции. Лечение запоя включает применение препаратов для капельницы, которые содействуют устранению симптомов отмены.Следует учитывать, что рецидив алкоголизма может произойти в в любое время. Предотвращение рецидивов включает не только психотерапию при алкоголизме, которая содействует пациентам понять корни своей проблемы и освоить справляться с эмоциональными трудностями. После окончания запоя важно пройти реабилитацию, чтобы избежать повторных срывов. Нарколог на дом поможет организовать этот процесс, предоставляя полезные советы для восстановления после запоя и сопровождая пациента на пути к здоровой жизни.
Хочу грамульку взять и угостить определенный круг людей, купить Кокаин, Мефедрон, Экстази Пришла сегодня посыль с 203им,кол-во ровное,даже показалось больше))) Сделал 1 к 15 самое то,магазу спасибо,процветания и всег благ)
странный вопрос, у вас в ветке интернируется, значит у кого он решил взять ? :rolf: https://dep211.ru всё граммотно делают!
вывод из запоя
vivod-iz-zapoya-irkutsk013.ru
экстренный вывод из запоя
explorethefuture – Love the modern design, feels like a place full of inspiration.
магазин работает ровно, заказ пришел за пару дней, качество порадовало) купить онлайн мефедрон, экстази, бошки службу спрс давным давно забросить необходимо..
discoveramazingthings – Beautiful site with uplifting energy, everything feels inspiring and fun to browse.
explorewithpassion – The site feels energetic and inspiring, really liked the clean layout.
Bonus exclusif 1xBet pour 2026 : obtenez un bonus de 100% jusqu’a 130€ en rejoignant la plateforme. C’est une offre unique pour les paris sportifs, avec la possibilite de placer des paris gratuits. Inscrivez-vous avant la fin de l’annee 2026. Vous pouvez retrouver le code promo 1xBet sur ce lien : https://medium.com/@ukis9605/1xbet-code-promo-bonus-vip-jusqu%C3%A0-130-775c34f06182.
вывод из запоя смоленск
vivod-iz-zapoya-smolensk025.ru
лечение запоя
ремонт в подвале gidroizolyaciya-podvala-cena.ru .
торкрет бетон цена торкрет бетон цена .
1xbet g?ncel 1xbet g?ncel .
наркологические клиники москва https://www.narkologicheskaya-klinika-23.ru .
Крутой магаз. Ассортимент радует https://ooo-ecoservice.ru В пробе было два вещества
getmoreforshop – Easy navigation and great offers, perfect combo for quick shopping.
startsomethingtoday – Love the name and the message, layout feels simple and fresh.
Медицинские учреждения в Туле предлагают разнообразные пакеты услуг, включая инъекции для снятия запойного состояния, которые могут включать витамины и препараты для снятия симптомов. Анализ медицинских учреждений позволяет определить лучший выбор с учетом ценовой политики и уровня сервиса. Круглосуточная помощь доступна в большинстве учреждений.При определении медицинского учреждения стоит учитывать отзывы пациентов и опыт врачей. Консультации нарколога помогут определить оптимальный план лечения алкоголизма. Анонимное лечение также является важным аспектом, так как многие пациенты предпочитают скрыть свою проблему.После завершения запойного состояния требует успешной комплексной терапии, включая реабилитационные программы для зависимых и последующее наблюдение. Таким образом, работа специалистов-наркологов, такие как вывод из запоя и инфузионные терапии, играют важную роль в процессе восстановления. вывод из запоя круглосуточно тула
Довольно сильно жгёт слизистую носа купить скорость, кокаин, мефедрон, гашиш магаз ровный!!!
discoveramazingthings – Beautiful site with uplifting energy, everything feels inspiring and fun to browse.
экстренный вывод из запоя иркутск
vivod-iz-zapoya-irkutsk014.ru
лечение запоя иркутск
у кого нить было что трек не бьеться 3ие сутки ?? через спср купить онлайн мефедрон, экстази, бошки Однако, селлеру в его интересах было бы полезно появиться и разъяснить ситтуацию дабы избежать гневных сообщений. Обещание что отправка будет пт-сб не было выполнено. Треков нет.
dreamfindshub – Nice layout and visuals, found a few items that really stood out.
Нашел отличный алкомаркет, где можно заказать алкоголь даже ночью. Всё очень удобно — оформление занимает пару минут, доставка быстрая, курьеры аккуратные. Алкоголь оригинальный, без подделок, всё в идеале. Теперь если нужна доставка алкоголя в москве, беру только здесь https://dostavka-alcohol.ru/
makelifesimpler – Nice clean interface, delivers exactly what the name promises.
expandyourhorizon – Positive energy all around, feels like a great place to explore.
Всем привет. Пишу по своему заказу. Заказал я АМ2233- 19.08.,оплатил 22.08.,трек получил 23.08.,24.08. позвонил в спср где меня обрадовали, тут же не дожидаясь доставки поехал к ним и забрал свою посылочку. Скоро пойду вскрывать… остальное отпишу позже. Продаван малорик,в аське почти всегда. на все мои вопросы отвечал без задержек. еще раз спасибо. купить скорость, кокаин, мефедрон, гашиш Ну во-первых мы совершенно другой магазин, так что вы ошиблись веткой, и представительств в тех городах у нас нет
экстренный вывод из запоя смоленск
vivod-iz-zapoya-smolensk026.ru
вывод из запоя цена
часы проститутки сургут
https://zuhookanak-141407.mn.co/members/36724372
shopfornewthings – The design feels modern and welcoming, will come back for more.
Трек получил! Данный магазин действительно выполняет свои обязанности перед покупателями.Просто при личном разговоре с продавцом можно действительно понять что работы у них действительно много и на это уходит время,просто стоит проявить терпение.Считаю как получу товар,его качество останется таким же наивысшим,как сама работа магазина купить Кокаин, Мефедрон, Экстази 2c-i, 2c-e, 2c-p
dreambelieveachieve – The positivity here stands out, love how motivational it feels.
алфавит английский песня для детей
Прокапаться от алкоголя на дому в Туле – это комфортный и эффективный способ прохождения терапии. Лечение алкоголизма включает в себя детоксикацию, которая способствует тому, чтобы организм избавиться от токсинов. Услуги наркологов в Туле предлагают вывод из запоя и медицинскую помощь при алкоголизме, включая кодирование от алкоголя. Ключевым моментом является консультация нарколога, который оценит состояние пациента и подберет индивидуальную программу лечения зависимости. Эмоциональная поддержка также является важной в процессе реабилитации. Процесс реабилитации включает различные программы лечения на дому, которые способствуют предотвращению рецидивов. Советы по отказу от алкоголя могут стать полезными дополнениями к основному лечению. Посетив narkolog-tula027.ru, вы получите информацию о доступных услугах и рекомендациях по профилактике рецидивов. Имейте в виду, что квалифицированная помощь – это ключ к успешной борьбе с зависимостью.
гидроизоляция подвала снаружи цены https://gidroizolyaciya-podvala-cena.ru .
торкретирование москва https://torkretirovanie-1.ru/ .
https://sites.google.com/view/code-promo-melbet-gratuit/home
exploreandcreate – Love the creativity theme, everything feels fresh and motivating.
modernlivingtrend – Good mix of content and aesthetics, everything feels well balanced.
“Кстати Минеру за описание Минус не указал что второй кооператив” купить Кокаин, Мефедрон, Экстази Все ровно, пасыль забрал, всем доволен!
вывод из запоя круглосуточно
vivod-iz-zapoya-irkutsk015.ru
экстренный вывод из запоя
getinspireddaily – Every section feels bright and encouraging, definitely worth a visit.
buildabetterworld – Inspiring energy overall, love how the content feels genuine and kind.
trendyfindsonline – The site has a clean and catchy look, definitely feels professional.
everydaystylecorner – The vibe is modern yet relaxed, really enjoyed scrolling through.
styleforliving – Found some great inspiration, the design feels polished and elegant.
connectlearncreate – Inspiring and interactive site, perfect for learning and creating new ideas.
growwithconfidence – The color scheme is uplifting, very fitting for the site’s concept.
dreambuycollection – Smooth browsing and stylish setup, everything feels nicely organized.
discoveryourpotential – Great concept and execution, this site truly motivates to grow more.
getinspireddaily – The site design is so refreshing, browsing here feels genuinely uplifting.
globalstylemarket – Great first impression, modern design fits the trendy theme well.
Всё получил свой АМ. Порошок кремового-оранжевого цвета, кстати полная растворимость на поровой бане. Так что не знаю кто там чо писал, помоему товар заебись! Как высохнет отпишу трип репорт от этой поставки… купить онлайн мефедрон, экстази, бошки Что ж ты такой нетерпеливый… ))
thetrendystore – Stylish vibe and smooth layout, great place for fashion lovers.
1xbet t?rkiye 1xbet t?rkiye .
наркологическая частная клиника http://www.narkologicheskaya-klinika-23.ru .
Магаз пропал из аськи и скайпа… Тобишь просто не появляется в онлайне. Такое уже бывало, но щас хз что… Качество товара было отменным. 203й высочайшего качества. купить Кокаин, Мефедрон, Экстази Брал и не раз в данном магазине, притензий нет, все качественно, оперативность радует! Продовцы дайте информации о CHM – 500, что за зверь? когда в розницу уйдет
экстренный вывод из запоя
vivod-iz-zapoya-smolensk027.ru
лечение запоя смоленск
inspirechangealways – Love the message behind this one, uplifting and well designed.
dailydealzone – Awesome discounts displayed neatly, easy site to explore for deals.
Чувствую что-то произойдёт , типа заказа:happy: купить скорость, кокаин, мефедрон, гашиш Ты еп сегодня зарегился и уже опробывал?
Лечение алкогольной зависимости на дому — представляет собой результативный метод помощи алкогольной зависимости, что позволяет быстро устранить признаки отмены и повысить общее состояние больного. Услуги нарколога на дому становятся все более популярными, так как многие предпочитают не проходить лечение в стационаре. narkolog-tula028.ru Эта процедура предполагает домашнюю детоксикацию, где медицинская помощь при алкоголизме осуществляется в комфортной обстановке. Капельница для снятия похмелья содержит лекарственные средства для очищения организма, которые способствуют очистить организм от токсинов и восстановить баланс электролитов и жидкости. Необходимо помнить о симптомах алкогольного абстинентного синдрома, включающих тревога, повышенное потоотделение и тремор. Забота и поддержка со стороны близких играет ключевую роль в эффективном лечении и восстановлении после запоя. Лечение на дому может включать не только капельницы, но и советы по предотвращению рецидивов алкогольной зависимости, что поможет предотвратить рецидивы и поддержанию трезвого образа жизни.
uniquelifestylehub – Stylish and modern, feels like a curated hub for unique lifestyle inspiration.
вывод из запоя
vivod-iz-zapoya-kaluga016.ru
лечение запоя калуга
simplelivinghub – Calming design and helpful ideas, perfect for minimal living inspiration.
“про “шапку” вы все горазды писать в интернете…”И продавать в интернете Вы все горазды,х..й догонишь и не спорсишь! купить Кокаин, Мефедрон, Экстази Всем привки Любви здоровья вам ! Процветания
вода в подвале https://gidroizolyaciya-podvala-cena.ru .
everydayshoppingzone – Lots of variety here, looks like a solid everyday go-to shop.
торкретирование бетона цена м2 http://www.torkretirovanie-1.ru .
bestchoicecorner – Feels trustworthy and professional, I like the clean structure.
trendychoicehub – Great mix of modern style and easy navigation, really well designed.
к вам претензий нет.. но вот хвосты не радуют.. купить Мефедрон, Бошки, Марихуану я в шоке. до последнего думали кидалово. а нет подняли в касание. стафф пушка. кладмену респект!!!
fashionloverszone – Trendy and visually appealing, great spot for fashion enthusiasts.
trendyfindshub – The latest styles stand out nicely, super easy to browse.
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk028.ru
лечение запоя смоленск
Этот магазин нериально всегда все четко делал, н ошиблись может случайно поговри я думаю решится https://fntr76.ru несмотря на отзывы про 203 джив всё таки решился взять 5г здесь, посмотрим на качество
shopyourfavorites – Great browsing flow, everything feels user-friendly and modern.
iwin – nền tảng game bài đổi thưởng uy tín, nơi bạn có thể thử vận may và tận hưởng nhiều tựa game hấp
пансионат для людей с деменцией в москве
pansionat-msk013.ru
пансионат для лежачих больных
вывод из запоя круглосуточно калуга
vivod-iz-zapoya-kaluga017.ru
экстренный вывод из запоя калуга
discovergreatdeals – Love how easy it is to browse deals, simple and user-friendly.
styleforliving – Great mix of simplicity and sophistication, easy to find what you need.
отличный сервис! купить скорость, кокаин, мефедрон, гашиш Доброго времени суток все друзья!:hello:Отличный магазин!!!Всегда ровные движения работал с ним.Всем советую
discoveramazingthings – Beautiful site with uplifting energy, everything feels inspiring and fun to browse.
connectdiscovergrow – Simple yet meaningful concept, perfectly reflected in the site’s design.
findsomethingnew – Minimal yet stylish, it’s easy to stay engaged while browsing here.
getinspiredtoday – Love the positive message, everything feels encouraging and thoughtfully made.
liveandexplore – The name fits perfectly, encourages discovery and trying new things.
modernlivingstyle – Simple yet classy, fits perfectly for anyone who loves modern living.
liveandexplore – Love the simple yet inspiring layout, makes browsing enjoyable and easy.
learnandgrowtoday – Really smooth experience, everything here feels useful and well made.
makelifesimpler – Simple, smooth, and beautifully organized — truly makes life simpler online.
theworldawaits – Great energy and design, everything feels adventurous and well presented.
У нас интернет-магазин, а не “шаурма у метро”. Личные встречи не возможны,”ибо по долгу службы тесно связан”(вот как раз наверное из-за этого)… Про кидал необоснованное заявление, такие речи лучше оставить при себе… В грубой форме вам никто не отвечал, вам вполне доходчиво сказали как и что…. купить Кокаин, Мефедрон, Экстази Высшее качество. Чёткий товар. Мошный микс. Хороший персонал, добрый МАгазин….
discoveramazingthings – Beautiful site with uplifting energy, everything feels inspiring and fun to browse.
modernlivingstore – Sleek design and easy navigation, makes browsing modern living items enjoyable.
Заказываю в третий раз, дали скидку 8%, приятно. https://gain-crb.ru Снял в касание, остановился, открыл дверь авто, вышел и зашёл обратно! Респект!!! Держите марку в том же духе!
bestvaluecollection – Good range of products, prices seem fair and competitive too.
growwithconfidence – Love the encouraging theme here, simple and motivating content.
лечение запоя смоленск
vivod-iz-zapoya-smolensk029.ru
лечение запоя
Вчера только оформил заказ на 2с-i и 4-FA – СЕГОДНЯ!!!! уже пришёл. Забрал. Туси не стану – пробывал до этого (нарекания отсутствуют в принципе) купить кокаин, меф, бошки через телеграмм Тоже такая ситуация , сижу без товара негодую.
экстренный вывод из запоя
vivod-iz-zapoya-kaluga018.ru
вывод из запоя
пансионат для пожилых с инсультом
pansionat-msk014.ru
пансионат для пожилых в москве
shopthemoment – Trendy design and clear visuals, makes browsing super enjoyable.
shopwithstylehub – Fun and stylish site, everything looks modern and well presented.
startsomethingtoday – Very motivating vibe throughout, really enjoyed exploring every section.
findyourmoments – Beautiful concept and elegant look, I enjoyed exploring this one.
За время работы легалрц сколько магазинов я повидал мама дорогая, столько ушло в топку, кто посливался кто уехал # но chemical-mix поражает своей стойкостью напором и желанием идти в перед “не отступать и не сдаваться”:superman: купить Мефедрон, Бошки, Марихуану рекомендую этот магазин
yourcreativejourney – Love the artistic vibe here, everything feels inspiring and original.
https://pslk.net/mp3srp82
uniquelifestylehub – The layout stands out, feels classy and well put together.
Все есть, объем большой купить скорость, кокаин, мефедрон, гашиш Представитель был Магазин на форуме Бивис и Бадхед, на сколько я знаю он работает, он у нас был представителем.
https://hikvisiondb.webcam/wiki/1xBet_Promo_Code_2026_130_for_New_Players
Давайте обменяемся идеями! Я собрала несколько своих любимых вариантов фото межкомнатных дверей — будет здорово, если и вы поделитесь своими фото/ссылками
Я экспериментирую с подачей материалов. Посмотрите, как вам такой формат. Спасибо за честный отзыв!
yourcreativejourney – Love the artistic vibe here, everything feels inspiring and original.
connectwithideas – Clean layout and inspiring content, perfect for exploring new concepts.
purefashionmarket – Fantastic collection of looks, the site design feels elegant.
Получил. начал разводить на 7 мл ацетона. все выпало в осадок и почти ничего не растворилось. жидкость получилась мутная как молоко. добавил еще 5 мл. вроде более менее, но все равно большой очень осадок. ну и прям так туда 2 коробка основы высыпал и на плитку. все делал впервые, можно сказать наугад. пыхтел через водник. 1 водник и накрывает мама не горюй. час держит и еще полтора отпускает, и состояние потом ппц мутное какое, даже утром проснулся еще в коматозе. все отлично в принципе, только вот отходняк какой-то.. купить Кокаин, Мефедрон, Экстази Продолжайте в том же духе.
yourmomentstarts – Clean layout and positive energy, great vibe throughout the site.
лечение запоя краснодар
vivod-iz-zapoya-krasnodar021.ru
вывод из запоя круглосуточно краснодар
findyourpathnow – Very balanced design, feels uplifting and thoughtfully put together.
findyourmoments – The visuals are warm and inviting, really helps create a good mood.
freshfashioncorner – The name fits perfectly, everything feels updated and chic throughout.
freshfashioncorner – Trendy, bright, and easy to use, really fun to scroll through.
лечение запоя
vivod-iz-zapoya-smolensk030.ru
вывод из запоя
shopwithstylehub – Love the variety here, everything feels fresh and tastefully arranged.
findjoytoday – Great use of color and flow, instantly brightens up your day.
simplevalueplace – Love the simplicity and focus here, everything feels neat and clear.
explorethefuture – Everything loads fast and looks polished, very futuristic and smooth.
createinspirelead – Motivating design and smooth layout, really captures a positive energy.
пансионат для престарелых
pansionat-msk015.ru
пансионат для лежачих москва
ВСЁ супер,брал,беру, и буду брать!Всё на высоте! https://znamblag.ru Брал у данного селлера!Хорошо работют=)
dreambuyoutlet – Great presentation and fast loading, enjoyable shopping experience overall.
Всем привет. купить кокаин, меф, бошки через телеграмм сделал заказ,оплатил,на следующий день получил трек – всё чётко,так держать! успехов и процветания вашей компании!
purefashionmarket – Great fashion selection and clean visuals, easy to explore and shop.
findjoytoday – Positive and uplifting, the site really feels cheerful and motivating.
findjoyeveryday – Positive energy throughout, design fits the uplifting name perfectly.
Заранее извиняюсь за оффтоп,просто решил сразу спросить ,чтобы не забыть.ответ будьте добры в ЛС. купить Мефедрон, Бошки, Марихуану Хмм…странно всё это, но несмотря ни на что заказал норм партию Ам в этом магазе так как давно тут беру.Как придёт напишу норм репорт про Ам
discoveramazingthings – Beautiful site with uplifting energy, everything feels inspiring and fun to browse.
modernhomefinds – Stylish home ideas and layout, feels cozy and modern at once.
лечение запоя
vivod-iz-zapoya-krasnodar022.ru
лечение запоя
о чем это ты? о каких зачетах ты тут поешь? ты дату своей регистрации видел зачетник ЕПТ! https://366shop.ru МАГАЗ СУПЕР!,брал5 гр ск качество отменное все сделанно ровно,даже фото не понадобилось,кристалики отличные без мутного оттенка,плаватся отлично,присутствует запах уксусного ангедрида,ВЫРАЖАЮ ОГРОМНУЮ БЛАГОДАРНОСТЬ!ВСЕ СУПЕР ПРОДОЛЖАЙТЕ В ТОМ ЖЕ ДУХЕ!
Запой, это опасное состояние, которое появляется при продолжительном употреблении алкоголя. Эффекты запоя могут быть угрожающими: истощение организма, повреждение органов, психические расстройства. Экстренный вывод из запоя в Туле включает лекарственную терапию и психологическую поддержку. Важно знать симптомы запойного алкоголизма: регулярные запои, потеря контроля над употреблением алкоголя. Методы выхода из запоя разнообразны: от капельниц до консультаций специалистов. Реабилитация после запоя требует системного подхода, включая возвращение к здоровью и психологическую помощь. Профилактика и лечение алкогольной зависимости в Туле предлагает медицинские центры, где доступны программы помощи. экстренный вывод из запоя тула
пансионат для пожилых после инсульта
pansionat-tula013.ru
пансионат для пожилых с деменцией
makeimpacttoday – Motivational and well-organized, great for users wanting to take action.
happylivingstore – Inspiring vibe and simple design, everything works perfectly together.
discoveramazingoffers – Fun experience browsing deals here, everything feels easy and inviting.
сделай какую небудь акцию)) купить онлайн мефедрон, экстази, бошки посылка дошла за 1 сутки, сегодня не успел забрать, завтра посмотрим на качество) я уверен, что все будет хорошо
trendycollectionhub – Stylish and modern layout, perfect for exploring new fashion trends.
дайте ссылку на город курган, хочется маленько россыпушки купить кокаин, меф, бошки через телеграмм Спасибо Все супер.МиР
inspirechangealways – Very motivating site, love the positive energy and smooth layout.
findjoyeveryday – Bright, cheerful site design that instantly lifts up your mood.
dreambuycollection – Smooth navigation and clean visuals, browsing here is super enjoyable.
trendingstyleworld – The colors and layout are on point, gives a classy, fresh vibe.
лечение запоя
vivod-iz-zapoya-krasnodar023.ru
лечение запоя
Сейчас по России что то не видно вас.Только пожелать ветра в парус,адекватных клиентов по меньше шкур купить кокаин, меф, бошки через телеграмм жду пока ответят, обана повдер кинул на 29000….но прочитал и понял что магаз супер, жду в скайпе селлера!
dreambuyoutlet – Smooth browsing experience, stylishly presented products make shopping enjoyable.
everydayshoppinghub – Very convenient and easy to use, makes daily shopping simple and smooth.
startanewjourney – Love the theme and calm color scheme, very pleasant to browse.
purevalueoutlet – Affordable deals and fast browsing, everything just clicks perfectly here.
fashionloverszone – Trendy, inspiring, and fun to explore — absolutely love this page.
dreamfindshub – Nice balance of visuals and ideas, definitely worth spending time on.
classychoiceoutlet – Feels elegant and trendy at once, definitely a favorite find today.
shopfornewthings – Such a cool place for discovering new items, love the vibe here.
getmoreforshop – Everything’s organized well, and the discounts are actually pretty solid.
yourmomentstarts – Great first impression, the name and vibe feel truly motivational.
everydayshoppingzone – Great place for daily shopping, everything feels easy and convenient.
пансионат с деменцией для пожилых в туле
pansionat-tula014.ru
частный дом престарелых
такое ощющение,что ты спецально зарегестрировался тут, чтобы написать только это сообщение,и в именно в этом разделе,я нечего не говарю за магазин,всё на вышшем уравне,но твой АК подозрителен с одним только этим сообщением купить скорость, кокаин, мефедрон, гашиш главное что ты “вкурил”, а как мне тебе это втереть уже не важно
Капельница от запоя в Туле: цены и отзывы В Туле услуги нарколога на дом становятся все более популярными. Множество людей борются с зависимостью от алкоголя и испытывают потребность в поддержке. Вызов нарколога на дом анонимно, это удобный способ получить медицинскую помощь, не выходя из дома. Капельница от запоя способствует в детоксикации организма и облегчает симптомы.Стоимость капельницы может различаться в зависимости от клиники, но в среднем составляет примерно 3000-6000 рублей. Отзывы о капельнице чаще положительные: пациенты отмечают быстрое улучшение состояния и уменьшение влечения к алкоголю. Экстренная помощь при запое способна сохранить здоровье.Лечение алкоголизма без лишних слов — важный аспект, так как многие не хотят обсуждать свои трудности. Услуги нарколога в Туле предлагают комплексную помощь, включая капельницы и реабилитационные программы. Помощь при запое доступна для всех, кто стремится к выздоровлению. нарколог на дом анонимно тула
changeyourfuture – Inspiring design and positive message, really motivates you to take action.
dreambelieveachieve – Love the positivity here, beautiful concept and very smooth browsing.
например тут ну или накрайняк тут а селлер совершенно не обязан консультировать по применению хим. реактивов. купить Мефедрон, Бошки, Марихуану по заказу?)
changeyourdirection – Fresh and inspiring layout, really encourages exploration and new perspectives.
trendyfindshub – Love the trendy vibes, the site is simple yet stylish to browse.
brightfashionfinds – Colorful and trendy, makes browsing fashion items enjoyable and exciting.
Черт приехал в офис говорю посмотрите посылку,мне сказали ее давно отправили!Она посмотрела ее нету,позвонила говорит она еще не отправлена и х.з. когда будет отправлена. купить онлайн мефедрон, экстази, бошки то ты-цифровая личность, я не за граммы говорю, а за общение и так-то не я один, обещаешь много-толку мало, 2 года – не срок, бомбануть и тебя могли, это вот твоим языком написано, если нормально не понимаешь, еще раз прошу участия администрации в данном вопросе
yourdailyshoppinghub – Nicely structured site, makes daily shopping easier and more enjoyable.
лечение запоя краснодар
vivod-iz-zapoya-krasnodar024.ru
вывод из запоя цена
makepositivechanges – Uplifting and encouraging site, everything feels fresh and motivating.
learnandgrowtoday – Very informative and inspiring, perfect for daily learning and personal growth.
С ним можно работать всегда ровничком всегда адекватность Плюсссс https://kuticoola.ru У меня была, проси того кто продал все перепроверять- люди могут ошибаться !
simplebuyoutlet – Great layout and simple design, perfect for grabbing daily essentials.
millioner kasyno
freshfashioncorner – Trendy looks and fresh designs, definitely one to revisit often.
discoverandcreate – Creative and engaging, perfect place to find ideas and inspiration.
milioner casino
пансионат после инсульта
pansionat-tula015.ru
пансионат для пожилых с деменцией
Алкогольная зависимость — это глубокая проблема‚ требующая профессионального подхода к лечению. В городе Тула можно получить наркологическими услугами‚ такими как терапия алкогольной зависимости на дому. Специалист по наркологии на дому незамедлительно поможет определить степень зависимости и выявить признаки алкоголизма. Важно проконсультироваться с наркологом для выбора оптимальной программы восстановления. Домашняя терапия позволяет пациенту находиться в знакомой среде‚ что снижает стресс. Психологическая помощь при алкогольной зависимости совместно с поддержкой близких играет ключевую роль в реабилитации от алкоголизма. Помощь родственникам алкоголиков также важна для создания условий для трезвой жизни. Нарколог на дом срочно Тула Не затягивайте с вызовом нарколога на дом‚ это первый шаг к избавлению от зависимости.
хороший магазин,было дело работал с ними) купить Мефедрон, Бошки, Марихуану ребята как-то странно работают,но надеюсь,что честно
billionaire casino huuge
bestvaluecollection – Excellent deals and easy navigation, really makes shopping enjoyable.
discoverbetteroptions – Clean and well-organized, makes finding better deals and options easy.
рулонные шторы на электроприводе рулонные шторы на электроприводе .
рулонные шторы автоматические купить http://www.rulonnye-shtory-s-elektroprivodom7.ru/ .
1x lite 1x lite .
1xbet yeni adresi 1xbet-giris-2.com .
1xbet com giri? http://www.1xbet-giris-4.com .
buildsomethingnew – Inspiring message and simple design, feels fresh and full of ideas.
Здравствуйте, есть и 50 и 100, сейчас откорректирую, можете заказывать уже купить Мефедрон, Бошки, Марихуану Отзывы вроде неплохие
discoverhomeessentials – Beautiful and functional items, love how organized and simple this site is.
findyourdreamplace – Beautiful visuals and easy navigation, makes exploring dream locations enjoyable.
thinkcreateachieve – Encouraging and positive, the name alone motivates exploring ideas and taking action.
explorewhatspossible – Simple yet inspiring, really enjoyed spending time exploring the content here.
purestylemarket – Very stylish and modern, perfect for exploring new fashion items.
findperfectgift – Great site with thoughtful gift ideas, found something for everyone here.
createbettertomorrow – Clean design with a great motivational vibe, very uplifting content.
вывод из запоя круглосуточно краснодар
vivod-iz-zapoya-krasnodar025.ru
лечение запоя краснодар
discovergreatideas – Love the positive energy here, every page feels fresh and motivating.
thepowerofgrowth – Really like the focus on empowerment and self-improvement, very uplifting.
Всем привет данной ветки:hello: История токова… купить Кокаин, Мефедрон, Экстази У нас у отправки случился форс-мажор. Только на этой неделе начинают отправлять. Извиняюсь от лица магазина за задержку.
staycuriousdaily – Simple yet powerful reminder to embrace curiosity as a lifestyle.
findyourmoments – Calm and inspiring design, a lovely place to explore and reflect.
discoverinfiniteideas – Feels like a hub for innovators and dreamers to find new perspectives.
everydayfindsmarket – I like how approachable it sounds, makes online shopping feel easy.
classyfindsonline – Love the classy layout, everything looks elegant and well arranged.
imaginelearnexplore – Inspiring and informative, great site for learning and discovering new things.
globalfashionzone – Trendy and user-friendly, excellent layout for browsing worldwide fashion trends.
если он такой делец,пусть тему свою создаёт!а так аферист,я бональный обаснованный вывод делаю! купить кокаин, меф, бошки через телеграмм сказали отпрака на следующий день после платежа!
частная психиатрическая клиника стационар
psychiatr-moskva010.ru
психиатрическую помощь в стационарных условиях
urbanfashioncorner – Stylish urban vibe, makes exploring fashion items really fun and engaging.
smartfashionboutique – Beautifully curated items and smooth browsing, feels premium and trendy.
Нарколог на выезд в владимире предоставляет важную помощь тем, кто страдает от зависимости. Процесс лечения зависимостей может быть сложным процессом, но выездной нарколог предлагает удобство и анонимность. На сайте vivod-iz-zapoya-vladimir020.ru можно записаться на консультацию с наркологом, который встретится с вами на дому. Медицинская помощь на дому включает детоксикацию организма и психотерапию зависимостей, что позволяет пациенту сделать первые шаги к свободе от наркотиков или алкоголя. Реабилитационная программа разрабатывается с индивидуальным подходом, что позволяет учитывать уникальные потребности каждого пациента. Эмоциональная поддержка близких играет важнейшую роль в предотвращении рецидивов. Частный нарколог на дому обеспечивает не только медицинскую помощь, но и эмоциональную поддержку, что важно для успешной реабилитации наркоманов и помощи при алкоголизме.
Челябинск работаете? купить Кокаин, Мефедрон, Экстази Отличный товар и цены. Зря так…
yourvisionawaits – Inspiring and motivating, makes exploring ideas and goals really enjoyable.
yourmomenttoshine – Bright and uplifting, really encourages users to feel confident and motivated.
двойные рулонные шторы с электроприводом https://avtomaticheskie-rulonnye-shtory1.ru/ .
рулонные шторы с электроприводом рулонные шторы с электроприводом .
1 x bet giri? https://www.1xbet-giris-2.com .
1xbet ?ye ol 1xbet-giris-4.com .
Первые 1.5 часа эйфория и сосредоточеность на том чем занят , в голове мелькают гениальные идеи) купить Кокаин, Мефедрон, Экстази Да и спспр – не лучший выбор. Или скажете, что вся проблема в нем?
Неотложная помощь при запое – существенный момент в процессе лечения алкогольной зависимости. Симптомы запоя могут включать настойчивого стремления к спиртному, телесной зависимости и психических проблем. Лечение запоя начинается с детоксикации, что способствует выведению токсических веществ из организма. Медицинская помощь при запое включает медикаменты, направленные на уменьшение симптомов отмены. Эмоциональная поддержка и поддержка семьи имеют решающее значение для мотивации пациента. Необходимо уделить внимание реабилитационным программам и восстановление после запоя. Клиника для алкоголиков предлагает разнообразные методы терапии, включая народные рецепты от запоя. Профилактика рецидивов играет важную роль в успешном лечении; Эффективная реабилитационная программа способствует возвращению пациента к обычной жизни. Больше информации по данной теме вы можете найти на сайте vivod-iz-zapoya-krasnoyarsk016.ru.
trendinghomeideas – Creative and practical ideas for home, very nice experience overall.
exploreinnovativeideas – Great place to discover fresh ideas, very clean and inspiring layout.
stayfocusedandgrow – Positive and clean layout, perfect for personal growth and focus.
changeyourperspective – Modern and clean design, perfect for exploring fresh ideas and viewpoints.
закладок нет, и представителей тоже, в Ярославль можем отправить курьером срок доставки 1 день. купить Мефедрон, Бошки, Марихуану все ровно мира вам ! и процветания
styleforless – Nice and simple, conveys the value and quality in just a few words.
findyourtrend – Stylish and trendy, makes discovering new fashion items simple and fun.
startanewjourney – Simple and inviting design, feels like a site full of possibilities.
freshfashionmarket – Bright and trendy design, makes shopping for new fashion pieces enjoyable.
Аптечные травы вообщем. купить Мефедрон, Бошки, Марихуану магаз ровный,всем советую!!
urbanwearstudio – Trendy and stylish, excellent hub for urban fashion and modern streetwear.
психиатрическая помощь больным
psychiatr-moskva011.ru
платный психиатр на дом в москве
苹果签名,苹果超级签平台,ios超级签平台ios超级签苹果企业签,苹果超级签,稳定超级签名
Капельница для лечения запоя в владимире — проверенный способ лечения алкоголизма, который помогает быстро восстановить здоровье пациента. При алкогольной зависимости появляются неприятные симптомы, такие как тошнота, головные боли и нарушения эмоционального фона. В лечебных учреждениях владимира предлагают медицинскую помощь, включая инфузионную терапию для детоксикации организма. vivod-iz-zapoya-vladimir021.ru Процесс лечения алкоголизма предполагает не только использование капельниц, но и психологическую поддержку во время отказа от алкоголя. Запись на консультацию к наркологу поможет выбрать оптимальный путь восстановления для реабилитации после запоя. Возможно назначение уколов и антидепрессантов для скорейшего выздоровления для ускорения процесса восстановления. На сайте vivod-iz-zapoya-vladimir021.ru можно найти услуги по лечению алкоголизма, где квалифицированные врачи помогут вам на пути к выздоровлению. Не теряйте время — начните свой путь к здоровью уже сейчас!
dailyvalueoutlet – Great deals and smooth browsing, perfect for everyday shopping and savings.
simplevalueplace – Easy navigation and clear visuals, great for quick and simple shopping.
У меня разок было, что трек перестал на два дня отслеживатся, но нечего доставили все пучком. https://kuhni-ankor.ru Наш Skype «chemical-mix.com» временно недоступен по техническим причинам. Заказы принимаются все так же через сайт, сверка реквизитов по ICQ или электронной почте.
discoveramazingfinds – Perfect name for a modern online marketplace full of great selections.
groweverymoment – Love the motivational vibe, encourages making every day meaningful and productive.
рулонные шторы с электроприводом и дистанционным управлением avtomaticheskie-rulonnye-shtory1.ru .
1xbet giri? g?ncel 1xbet-giris-2.com .
Капельница от запоя – это ключевым моментом в терапии алкогольной зависимости. В Красноярске наркологические услуги предлагают поддержку специалиста‚ что осуществит детоксикацию организма. Симптомы запоя‚ такие как тревога и потливость‚ способны вызывать к серьезным осложнениям в результате запоя. Капельница способствует восстановить водно-электролитный баланс и улучшить здоровье в результате запойного состояния. помощь нарколога Красноярск После лечения важно пройти реабилитацию и обеспечить психологическую поддержку. Консультация специалиста в области наркологии поможет избежать рецидивов. Профилактика рецидива предполагает обучение и поддержку‚ что способствует организма. Медицинская помощь при алкоголизме в Красноярске предоставляется и эффективна‚ помогая пациентам возвратиться к нормальной жизни.
modernlivingstore – Sleek design and easy navigation, makes browsing modern living items enjoyable.
1xbet giri?i 1xbet-giris-4.com .
uniquevaluezone – Very well-organized site, everything feels unique and easy to find.
рулонные шторы жалюзи на окна https://rulonnye-shtory-s-elektroprivodom7.ru/ .
everydaystylemarket – Feels modern and appealing, a go-to for daily outfit inspiration.
findyournextgoal – Simple yet powerful message, makes visitors feel inspired instantly.
creativityneverends – Feels vibrant and full of inspiration, perfect for creators and dreamers.
simplefashioncorner – I like how calm and refined the name sounds, very inviting vibe.
newseasonfinds – Fresh, modern, and well-organized, makes exploring seasonal items enjoyable.
findyourpath – Great reminder that everyone’s journey is unique and worth exploring.
Почему больше не забегаете ? купить Мефедрон, Бошки, Марихуану кто брал закладками в этом магазе в МСК что скажите?
makeimpacteveryday – Feels uplifting and optimistic, perfect for a motivational platform.
learnsomethingnewtoday – Such an uplifting idea, learning daily keeps the mind active and creative.
dreambiggeralways – Feels optimistic and bold, perfect for anyone chasing big ambitions.
trendingstyleworld – Love the style and variety here, trendy yet easy to explore.
мы и в скайп и в аське купить скорость, кокаин, мефедрон, гашиш Всем удачи!
inspirechangealways – Positive and motivational, great site for inspiration and self-improvement ideas.
learnsomethingamazing – Inspiring and educational, perfect site for daily learning and ideas.
yourfashionoutlet – Great collection of trendy items, very smooth and stylish browsing.
Discover exquisite Austrian wines at wine tour vienna and immerse yourself in Vienna’s vibrant wine culture.
Wien begeistert mit seiner langen Weintradition und zeitgenossischen Angeboten. Die Region ist bekannt fur ihren exzellenten Wei?wein, besonders den Grunen Veltliner. Viele Weinverkostungen finden in historischen Gewolbekellern statt.
Das milde Klima und die mineralreichen Boden begunstigen den Weinbau. Das macht Wien zu einer der wenigen Gro?stadte mit eigenem Weinbaugebiet.
#### **2. Beliebte Weinregionen und Weinguter**
In Wien gibt es mehrere renommierte Weinregionen, wie den Nussberg oder den Bisamberg. Hier reifen einige der besten osterreichischen Weine heran. Familiengefuhrte Weinguter bieten oft Fuhrungen und Verkostungen an. Dabei lernt man viel uber die Herstellung und Geschichte der Weine.
Ein Besuch im Weingut Wieninger oder im Mayer am Pfarrplatz lohnt sich. Hier verbinden sich Tradition mit innovativen Methoden.
#### **3. Ablauf einer typischen Weinverkostung**
Eine klassische Wiener Weinverkostung beginnt meist mit einer Kellertour. Dabei erfahrt man Wissenswertes uber Rebsorten und Vinifizierung. Danach folgt die Verkostung unterschiedlicher Weine. Die Aromen werden von den Experten detailliert beschrieben.
Haufig werden die Weine mit lokalen Kasesorten oder Brot serviert. Diese Kombination ist ein Highlight fur Feinschmecker.
#### **4. Tipps fur unvergessliche Weinverkostungen**
Um das Beste aus einer Weinverkostung in Wien herauszuholen, sollte man vorher buchen. Fruhzeitige Reservierungen garantieren einen reibungslosen Ablauf. Zudem lohnt es sich, auf die Jahreszeiten zu achten. Im Herbst finden oft Weinlesefeste statt.
Ein guter Tipp ist auch, ein Notizbuch mitzubringen. Viele Gaste schatzen spater die Erinnerungen an die Verkostung.
—
### **Spin-Template fur den Artikel**
#### **1. Einfuhrung in die Weinverkostung in Wien**
Wien begeistert mit seiner langen Weintradition und zeitgenossischen Angeboten.
#### **2. Beliebte Weinregionen und Weinguter**
Hier reifen einige der besten osterreichischen Weine heran.
#### **3. Ablauf einer typischen Wiener Weinverkostung**
Dabei erfahrt man Wissenswertes uber Rebsorten und Vinifizierung.
#### **4. Tipps fur unvergessliche Weinverkostungen**
Einige Anbieter bieten auch private Verkostungen an.
—
**Hinweis:** Durch Kombination der Varianten aus den -Blocken konnen zahlreiche einzigartige Texte generiert werden, die grammatikalisch und inhaltlich korrekt sind.
modernlivingtrend – Stylish, modern, and smooth experience from start to finish.
частный психиатр на дом в москве
psychiatr-moskva012.ru
психиатрическая медицинская помощь
Качество на высоте,оператор красавчик,все сделали быстро и четко! купить Кокаин, Мефедрон, Экстази У кого рега сильней чем тут?
smartshoppingzone – Easy to navigate and clean layout, perfect for smart shoppers.
https://xnudes.ai/
Детоксикация при запое в владимире: цены и способы Запой – это серьёзное заболевание, требующая профессионального вмешательства. В владимире услуги по детоксикации доступны в различных клиниках, где оказывают экстренный вывод из запоя. Методы вывода из запоя включают медикаментозной терапии, инфузионные процедуры и психотерапию. Цены на детоксикацию варьируются в зависимости от способа лечения и условий в клинике. Следует осознавать, что лечение запоя – это не просто физическая детоксикация, но и важная психологическая поддержка зависимых, что способствует восстановлению здоровья и предупреждению рецидивов. экстренный вывод из запоя владимир Реабилитация после запоя включает в себя поддержку специалистов, что помогает избежать возврата к алкоголизму. Если вы или кто-то из ваших близких столкнулся с данной проблемой, не стоит откладывать обращение за помощью к специалистам.
learnsomethingdaily – Clean and informative, perfect for daily learning and personal growth.
Наркологическая помощь в Красноярске играет ключевую роль в борьбе с зависимостями. Медицинские учреждения, такие как vivod-iz-zapoya-krasnoyarsk018.ru, осуществляют эффективные методы лечения для пациентов с зависимостями. В процесс лечения зависимостей входит медицинскую помощь на стационарной основе и программы реабилитации, которые способствуют возвращению к полноценной жизни.Красноярская наркология обеспечивает лечение без раскрытия личных данных, что является критически важным для многих зависимых. Здесь также доступна наркологическая консультация, где врачи оценивают уровень зависимости и подбирают наилучший курс реабилитации. Забота близких также является существенным элементом процесса реабилитации. Медицинская помощь в Красноярске включает не только помощь при алкогольной зависимости, но и профилактику зависимостей, что способствует предотвращению рецидивов. Каждому пациенту гарантируется персонализированный подход, что обеспечивает эффективность лечения.
Давно работаю с чемиком. https://www.betterplace.org/en/organisations/70613 ну сегодня пыхнул час назад ….. приопустило……………… но еще норм не грузит
theartofgrowth – Inspiring and thoughtful layout, perfect for personal growth and learning.
findyourpathnow – Motivating vibe and thoughtful layout, everything feels purposeful and neat.
discoverandbuy – Smooth experience and well-presented products, makes online shopping effortless.
Розгорнути подробиці: https://ukrglobe.com/zdorovia.html
это манера такая сдержанная или удовлетворительное=на троечку https://say.la/read-blog/136642 Сделать можно хоть в Новогоднюю ночь, но обработан он будет только после 9 января.
https://magnitola.kiev.ua
Все найновіше тут: https://elementarno.com.ua/krasa.html
trendforlife – Very fashionable and clean site, makes exploring trends effortless.
urbanchoicehub – Trendy urban style and clean design, makes exploring fashion easy and fun.
modernhomecorner – Love the modern designs and home decor ideas shared here daily.
я не смог пополнить в альфа банке, по определенной причине! https://pubhtml5.com/homepage/sfaff Я так понимаю,магаз – надёжный! Цены на сегодняшний день соответствуют заявленным в прайсе?
PureValue Blog – Inspiring and interactive site, ideal for curious minds.
психиатрический стационар
psikhiatr-moskva010.ru
психиатрическое лечение
styleandchoice – A stylish and confident name that reflects individuality.
simplebuyhub – Love how easy it is to shop here, very user-friendly layout.
профессиональное продвижение сайтов профессиональное продвижение сайтов .
продвижение французского сайта цена optimizaciya-i-seo-prodvizhenie-sajtov-moskva.ru .
как продвигать сайт статьи https://statyi-o-marketinge7.ru .
цифровой маркетинг статьи цифровой маркетинг статьи .
findmotivationtoday – Positive and inspiring layout, really motivates and encourages action every day.
только не под своим ником :confused: (мож поэтому и не отвечают) https://yamap.com/users/4925284 Я ж тебя хотел отпиарить.
Услуги нарколога на дому в Красноярске становятся всё актуальней. Профессионалы, работающие в этой области, оказывают разнообразные наркологические услуги, в т.ч. помощь при алкоголизме и других зависимостях. Консультация нарколога на дому даёт возможность оперативно диагностировать зависимости и назначить индивидуальный подход к пациенту. Лечение без раскрытия личности – важный аспект работы специалистов, что особенно важно для людей, которые стесняются обращаться в медицинские учреждения. Реабилитация на дому включает психотерапию при зависимости, программы восстановления и медикаментозную терапию. Поддержка семей зависимых является важным фактором на пути к выздоровлению. Предотвращение рецидивов также занимает центральное место в работе наркологов. Наркологи предоставляют психологическую поддержку и помощь, помогая пациентам справляться с трудностями на пути к выздоровлению. Узнать больше о предлагаемых услугах можно на сайте vivod-iz-zapoya-krasnoyarsk019.ru, где вы найдёте всю необходимую информацию и контакты по наркологическим услугам в Красноярске.
yourstylezone – Stylish, modern, and user-friendly, love the smooth browsing experience.
yourpathforward – Motivating concept, feels like a site that inspires progress and growth.
starttodaymoveforward – Perfect message for anyone aiming to improve and achieve more.
budgetfriendlypicks – Such a convenient way to shop smart and stay within budget.
discoverhiddenopportunities – Beautifully captures the essence of growth and hidden potential.
trendywearstore – Impressed by the quality and latest trends featured here.
Прокапывание на дому в владимире — это удобное решение для людей, которым требуется медицинская помощь, но не может посетить клинику. Это включает в себя инфузионную терапию, где медсестра на дому проводит капельницы на дому. Это особенно актуально для восстановления после болезни или при необходимости медикаментозной терапии. Удобство лечения и уход за пациентами значительно увеличиваются, когда квалифицированный врач приходит к вам. Профилактика заболеваний и консультации врача также становятся доступнее. Сайт vivod-iz-zapoya-vladimir023.ru предоставляет эти услуги, обеспечивая комфорт и здоровье для пациентов.
привет !!! немогу с вами с вязатся отпишись!!!! https://imageevent.com/bgomyzurobeb/pdbwg Душевный магазин) Все довольны. Славно.
findnewinspiration – Bright, clean, and motivating, perfect for discovering fresh ideas daily.
growyourmindset – Love how this name promotes positivity and continuous personal growth.
Самый лучший магаз, заказываю и не парюсь https://www.grepmed.com/vuafidiigcic чема вещи делает!!!
trendandfashionhub – Bright, trendy, and well-organized, perfect for fashion enthusiasts.
findyourinspirationtoday – Inspiring visuals and smooth design, makes finding new ideas enjoyable and simple.
платная психиатрическая скорая помощь
psikhiatr-moskva011.ru
платный психиатр
Тоже считаем что запреты не запреты. Да бывает что и за клиентами охотятся. https://kemono.im/oedeabegybu/kirovo-chepetsk-kupit-kokain-mefedron-marikhuanu-boshki Страшно) заказывать RTI-126. Кто поможет с данной проблемой.
simplefashioncorner – Clean, trendy, and easy-to-browse fashion options all in one place.
оптимизация и seo продвижение сайтов москва оптимизация и seo продвижение сайтов москва .
Капельница от запоя – это действующий метод лечения алкогольной зависимости, который доступен от квалифицированный нарколог в городе Красноярск. Во время запоя организм испытывает существенное истощение жидкости и интоксикацию, что приводит различные симптомы похмелья. Важно оказать первую помощь, чтобы улучшить состояние больного. нарколог на дом Красноярск Очистка организма с помощью инфузий помогает быстрому выведению токсинов и улучшению состояния. Персонализированный подход врача гарантирует высокую результативность лечения на дому. Услуги медикаментов на дому позволяют не ложиться в больницу и обеспечить процесс лечения комфортным. Алкоголь негативно сказывается на здоровье разрушительно, поэтому реабилитация от запоя включает восстановление после запоя и консультацию нарколога. Комплексное лечение, включая капельницу, способствует восстановлению здоровья и возвращению к нормальной жизни.
заказать продвижение сайта в москве заказать продвижение сайта в москве .
стратегия продвижения блог statyi-o-marketinge7.ru .
блог агентства интернет-маркетинга statyi-o-marketinge6.ru .
shopandsaveonline – Great deals and simple layout, makes online shopping quick and easy.
У меня не бьётся вторые их трек. И бро в скайпе не видно. Мож приняли их посылки на почте? Тоже парюсь блин…. Но не хотел поднимать дискуссию, не имея причин. Выслали в пятницу СПСР. https://www.brownbook.net/business/54444785/уральск-купить-кокаин-мефедрон-марихуану-бошки/ спасибо вам уважаемый магазин за то что вы есть! ведь пока что лучшего на легале я не видел не чего!
Лечение запоя в владимире это важная задача, которая требует квалифицированного вмешательства. Алкоголизм — это беда, способная сломать судьбы, и помощь при запое необходима каждому, кто столкнулся с этой бедой . В клиниках для лечения запоя предлагаются множество программ, ориентированных на вывод из запоя и дальнейшую реабилитацию. Цены на лечение алкогольной зависимости могут меняться в зависимости от клиники и качества обслуживания. В стоимость может входить консультация нарколога, медицинская помощь при запое и услуги по детоксикации. лечение запоя владимир Наркологическая помощь в владимире включает в себя как стационарное, так и outpatient лечение, что также влияет на стоимость . Программа лечения алкоголизма индивидуализирована и может включать детоксикацию, психологическую поддержку и реабилитацию . Комплексный подход к лечению зависимостей в владимире позволяет не только остановить алкогольное потребление, но и минимизировать риск рецидивов. Поэтому, если вам или вашим близким нужна помощь , важно обратиться за помощью к специалистам .
modernhomecorner – Love the modern designs and home decor ideas shared here daily.
Отличный Магаз, Все четко!!! https://wanderlog.com/view/esfmaumyvj/орехово-Р±РѕСЂРёСЃРѕРІРѕ-купить-кокаин-мефедрон-марихуану-бошки/ Вызвал такси;)
besttrendstore – Love the clean design and trendy collections, very appealing overall.
besttrendstore – Trendy and exciting store with fresh fashion and lifestyle products.
Сижу жду пока высохнет АМ2233 =) https://www.rwaq.org/users/nudzctrp18yn3k-20251102003341 Списался с данным магазом пару месяцев назад, беру клады по москве, ребята работают отлично, сервис на высоте! Последний раз даже клад сделали минут за 15 всего, первый раз такое, в других магазах приходилось часов по 5 ждать свое клада! Рега тоже отличная, беру JV-90 очень мощная штука! Спасибо ребятам за качественный товар и сервис продолжайте в том же духе!!!
https://www.bundas24.com/blogs/160251/1xBet-Promo-Code-2026-130-Welcome-Bonus
консультация психиатра платно
psikhiatr-moskva012.ru
частная психиатрическая клиника
https://www.prestashop.com/forums/profile/1961405-paris_sportifs/?tab=field_core_pfield_19
yourfashionoutlet – Love the stylish collection here, everything feels trendy and well-priced.
Вот это было бы нереально кул, а то я уже отчаялся через емейл к вам пробиться. Жду с нетерпением. https://say.la/read-blog/135271 Тоже был осадок, но в баньке всё растворилось)
https://pdlspd.listbb.ru/viewtopic.php?f=3&t=4485
Неотложная помощь при алкогольной зависимости в Красноярске становится актуальной для многих. Сайт vivod-iz-zapoya-krasnoyarsk021.ru предлагает услуги нарколога, который осуществляет лечение алкоголизма и вывод из запоя. Процесс включает медицинское вмешательство, детоксикацию алкоголя и психотерапию при запое. Важно получить консультацию врача для успешного снятия алкогольной зависимости. Наша программа восстановления направлена на реабилитацию, поддержку зависимых и их социальную адаптацию. Профилактика повторных случаев, важный аспект успешного лечения. Помните, что просьба о помощи — это первый шаг к выздоровлению.
connectwithpeople – The name itself gives warm, friendly, and community-driven vibes.
startfreshjourney – Uplifting and positive vibe, perfect for inspiration and fresh beginnings.
thinkactachieve – Really inspiring message, perfect for anyone focused on self-improvement.
продвижение в google http://optimizaciya-i-seo-prodvizhenie-sajtov-moskva-1.ru/ .
seo блог seo блог .
seo продвижение и раскрутка сайта seo продвижение и раскрутка сайта .
материалы по seo материалы по seo .
https://masa.forum24.ru/?1-1-0-00002546-000-0-0-1762713513
thebestdeal – Always great to find a site focused on value and daily savings.
нужны мощные аналоги рцсу типа ам серии итд https://bio.site/egjyyehyg заказал, получил, покурил, охуел…
globalfashionzone – Amazing designs and global trends, perfect for fashion enthusiasts.
staycuriousdaily – Love the message, a great reminder to keep learning every day.
groweverymoment – The message is simple yet powerful, love the growth mindset theme.
Анонимный вызов нарколога в владимире — это значимый шаг на пути к освобождению от зависимости. Ресурс vivod-iz-zapoya-vladimir025.ru предлагает наркологическую помощь, включая профессиональную консультацию нарколога и лечение с полной анонимностью; Организация обеспечивает поддержку для зависимых и их семей, предоставляя квалифицированную медицинскую помощь в владимире. Лечение зависимости требует компетентного подхода. Анонимные услуги нарколога помогут вам обрести необходимую психологическую поддержку и реабилитацию наркоманов. Горячая линия готова принять ваш звонок на горячую линию нарколога, обеспечивая срочную и качественную помощь. Профилактика зависимостей также важна. Не упустите шанс позвонить за помощью и начать новую жизнь. Помните, что выход из зависимости возможен, главное — сделать решающий шаг и обратится за помощью.
findyourbalance – The name alone feels soothing and full of positive intention.
shopwithstyle – Love the elegant touch and fashion-forward vibe of this store.
хороший магазин,всё на красоте и качество и кол-во:) продолжайте в том же духе https://rant.li/yhiguofzehaa/sovetsk-kupit-kokain-mefedron-marikhuanu-boshki Хороший магазин и отличные цены. Доставили через 3 дня после заказа. О качестве товара комментарий оставлю позже.
believeinyourideas – Motivating and clean design, makes exploring ideas enjoyable and simple.
theartofgrowth – Inspiring name that perfectly fits a mindset of learning and progress.
заказал и оплатил ещё в понедельник, сегодня пятница но трэка до сих пор нет, раньше такого не было а в этот раз че то медлят https://imageevent.com/zibanyjilu/dmxgw Хороший магазинчик
лечение алкоголизма
reabilitaciya-astana010.ru
где лечиться от алкоголизма
uniquevaluezone – Offers cool finds at great prices, really worth visiting.
globalstyleoutlet – Amazing range of international fashion, really fun to browse.
https://loktrk.com
лечение запоя
vivod-iz-zapoya-minsk013.ru
вывод из запоя круглосуточно минск
слов нет.Вы ребята давно шум должны поднять что такая херня а то молчите по две недели!!!!я бы так хрен зарядил.А я почитал типа все ровно пишут и отдал кровные 22т.р https://say.la/read-blog/135592 А будете ли работать в Беларусии?
newtrendmarket – Love the fresh and modern vibe, full of current fashion finds.
discoverhiddenopportunities – Inspiring name that encourages exploring new ideas and growth.
dailyshoppingzone – Love how convenient this site is for everyday shopping needs.
Уважаемый, Chemical-mix.com, я новичок что на легале, что в джабере, что где либо ещё… не получается выйти на связь, проблема с покупкой, в джабере написано, на сайте не онлайн… ответь пожалуйста в jabber… Зарание большое спасибо… https://www.montessorijobsuk.co.uk/author/uhagufoabu/ “про “шапку” вы все горазды писать в интернете…”И продавать в интернете Вы все горазды,х..й догонишь и не спорсишь!
Алкогольный запой — это тревожное состояние, требующее оперативной медико-социальной помощи. В владимире предоставляется помощь врача-нарколога, который предлагает услуги по избавлению от запоя и детоксикации. Капельное введение — это эффективное средство для оздоровления пациента. Она помогает устранить симптомы алкогольной зависимости, повышает общее состояние и ускоряет процесс реабилитации от алкоголя. помощь нарколога владимир Если вы или ваш близкий испытываете трудности с запоя, необходимо не откладывать вызов врача на дом. Наркологические услуги, предоставляемые в клиниках владимира, могут включать персонализированный подход к каждому пациенту. Услуги нарколога включает не только капельницы, но и комплексное лечение алкоголизма. Выбор врача на дом дает возможность получения медицинской помощи в привычной обстановке. Специалисты согласятся на необходимую детоксикацию и поддержат здоровье пациента. Не стесняйтесь обращаться за помощью — это первый шаг к освобождению от алкогольной зависимости.
согласовать проект перепланировки https://soglasovanie-pereplanirovki-1.ru/ .
перепланировка нежилого помещения в москве перепланировка нежилого помещения в москве .
surewin malaysia login https://surewin-online.com/ .
ice bet casino ice bet casino .
trendycollectionhub – Great place for discovering stylish collections and creative designs.
да магаз реальный.недовеса небыло ниразу.может просто недоразумение. https://www.band.us/page/100499514/ у меня такой вопрос: будут ли у вас на розничном сайте позиция am-2233 по 1гр? Я раньше брал через алхима, но он по неизвестным мне причинам сговнился. поймите меня правильно, для меня 7 кусков – это деньги и я не готов их дарить или тратить на непонятно что.
dailyshoppingzone – Love how convenient this site is for everyday shopping needs.
newtrendmarket – Fresh trends and a smooth shopping experience, really well put together.
urbanchoicehub – Really gives off that modern, connected community vibe — great branding!
bestdailyoffers – Excellent selection of offers, makes online shopping way more exciting.
Здрасте Бразы!!!!:hello: https://imageevent.com/ekymofajopej/pikjl всем привет,припы репорты писать не умею как мастер 100 того уровня,но скажу как есть,магазин вообще огонь ,брал 1гк ск АЛФА 29 с доставкой,все быстро и оперативно пришло,как и было оговорино 14 дней,а ребята знают толк в работе красавцы доставили в кароткие сроки,АДРЕС СДЕЛАН БЫЛ С ТОЧНЫМ ОПИСАНИЕМ ЗАБРАЛ В КАСАНИЕ + ФОТО К ОПИСАНИЮ ШЛО МОЖНО БЫЛО ПО ФОТО ПОДНЯТЬ НЕ ЧИАЯ ОПИСАНИЯ ДАЖЕ,ВЕС СК КРИСТАЛИКИ ЧИСТЫЕ НЕ БУТОР ТАВАР ОТЛИЧНЫЙ И ЧИСТЕЙШЕЕ КАЧЕСТВО,УСПЕХОВ ВАМ ВО ВСЕМ И ПОПУТНОГО ВЕТРА КЛИЕНТОВ ПО БОГАТЧЕ,ПРОЦВИТАНИЯ,ВСЕМ СОВЕТУЮ ЭТОТ МАГАЗИН,ОПЛАЧИВАЙТЕ С ДОСТАВКАМИ И НЕ СОМНИВАЙТЕСЬ НЕ КАПЛИ……..МАГАЗИН РАБОТАЕТ РОВНО
вывод из запоя тула
tula-narkolog010.ru
вывод из запоя круглосуточно тула
simplebuyhub – Super easy to navigate site with plenty of affordable options.
yourvisionawaits – Inspiring name that motivates people to dream and take action.
everydaystylemarket – Love how everything feels modern yet accessible.
discoveramazingfinds – Love how easy it is to find something new every time I visit.
creativechoiceoutlet – Smooth navigation and eye-catching layout make shopping fun.
exploreinnovativeideas – It’s exciting to see such innovation presented in a friendly way.
Правило говоришь Бро! А про работу магазина могу сказать что он работает великолепно! https://pubhtml5.com/homepage/iixbf МАГАЗ СУПЕР!,брал5 гр ск качество отменное все сделанно ровно,даже фото не понадобилось,кристалики отличные без мутного оттенка,плаватся отлично,присутствует запах уксусного ангедрида,ВЫРАЖАЮ ОГРОМНУЮ БЛАГОДАРНОСТЬ!ВСЕ СУПЕР ПРОДОЛЖАЙТЕ В ТОМ ЖЕ ДУХЕ!
trendforlife – Love the concept; a perfect spot for true fashion enthusiasts.
buildyourpotential – Great reminder that growth starts with small daily improvements.
https://www.gamerlaunch.com/community/users/blog/6151290/2462659/1xbet-free-spins-code%3A-%E2%82%AC130-%2B-150-fs-/?gid=535
Капельница от запоя на дому – это популярный метод лечения алкогольной зависимости, предлагающий множество преимуществ и особенности. В владимире наркологические услуги предлагают возможность выезда на дом, что даёт возможность пациентам получать медицинскую помощь при запое в комфортной для них обстановке. Преимущества капельницы заключаются в скорейшем восстановлении организма благодаря процедурам детоксикации. Капельницы помогают вывести токсины, улучшить общее состояние, что, в свою очередь, помогает быстрее восстановиться после запоя. Кроме того, поддержка близких при запое имеет огромное значение, так как домашнее лечение алкоголизма создает комфортную атмосферу. лечение запоя владимир Тем не менее, есть и недостатки. Например, в некоторых случаях сложно обеспечить необходимый контроль за состоянием пациента. Врачебная консультация на дому может оказаться недостаточной для серьезных случаев. Также стоит учитывать, что не всем пациентам подходят инъекции при алкоголизме.
Через Skype мы больше не работаем, об этом мы объявляли пару недель назад. https://say.la/read-blog/134678 Так может он в городе закладкой брал
urbanfashioncorner – Trendy, bold, and full of energy — perfect urban fashion vibe.
ОО мне то же все пришло! http://www.pageorama.com/?p=cvidehocbufe Работали с магазином ранее брали по 100г, недавно взяли еще 50г, хотим сегодня 100г приобрести!! на регу нету нареканий!!
smartshoppingzone – Perfect for budget-conscious shoppers who still want quality products.
вывод из запоя тула
tula-narkolog011.ru
вывод из запоя тула
лечение алкогольной зависимости клиника
reabilitaciya-astana012.ru
как лечить алкогольную зависимость
learnsomethingamazing – Encouraging and creative name that promotes daily learning and discovery.
по заказу?) https://www.betterplace.org/en/organisations/70574 чистым не очень понравился:(
brightfashionfinds – Such vibrant styles here, everything feels bold and fresh.
freshdealsworld – Great site for fresh offers and exciting online shopping deals.
Скажите сей час в Челябинске работаете?) https://pubhtml5.com/homepage/apcyy Проб НЕТ!
findbestdeals – Love how easy it is to browse and spot the top deals.
Капельницы для лечения запойной зависимости – данный метод является распространенным способом борьбы с алкогольной зависимостью, используемый внедряется в клиниках в владимире для детоксикации организма. Круглосуточная помощь дает возможность эффективно снять от симптомов запойного состояния. Тем не менее важно помнить о возможных побочных эффектах, таких как аллергические реакции и нарушение водно-солевого баланса. вывод из запоя круглосуточно владимир
startfreshjourney – Motivating message, perfect for anyone ready for a new beginning.
learnandshine – Inspiring content that motivates me to keep learning every day.
вывод из запоя цена
tula-narkolog012.ru
вывод из запоя
dailydealsplace – Great place for deals, always something new and exciting to find.
discoverandbuy – The store layout feels intuitive, everything’s easy to explore and choose.
вывод из запоя цена
narkolog-krasnodar021.ru
вывод из запоя круглосуточно краснодар
uniquegiftideas – Excellent variety of creative gifts, ideal for any special occasion.
fashionmarketplace – Excellent variety of styles, feels like a hub for fashion lovers.
inspireeverymoment – Motivating platform that encourages positivity every single day.
findnewinspiration – Such an encouraging site, perfect for daily motivation and reflection.
dreambiggeralways – Simple design but powerful message, I come here often for inspiration.
stayfocusedandgrow – A solid reminder that growth comes from consistency and patience.
learnandimprove – Love the focus on constant growth and practical learning tips here.
findhappinessdaily – Uplifting messages and helpful tips that brighten my day instantly.
https://s-nano-s.ru/
simplebuyoutlet – Smooth shopping experience, great deals and very clean design.
purechoicehub – Clean design and high-quality items, really impressed with the layout.
starttodaymoveforward – Positive and inspiring, encourages daily progress and self-growth.
https://tutvot.com/
Сопровождение импорта экономит время и ресурсы компании: Сопровождение ВЭД
https://avia.tutvot.com/
yourstylezone – Trendy site that really helps express personal fashion taste.
thepowerofgrowth – Beautiful name that reminds you of personal and continuous improvement.
В городе владимир доступна услуга по вызову нарколога на дом, доступная 24/7, предлагающая профессиональную помощь в области наркологии для пациентов с зависимостями. Если вам требуется профессиональная помощь при алкоголизме, профессиональный нарколог окажет медицинскую помощь на дому, гарантируя полную анонимность. вызов нарколога владимир Если вы хотите найти эффективное решение, вызов нарколога в владимире станет первым шагом к новой жизни.
classystyleoutlet – Elegant fashion selections and well-curated items, love browsing here.
startbuildingtoday – Inspiring site that motivates you to take action and grow.
вывод из запоя круглосуточно челябинск
vivod-iz-zapoya-chelyabinsk013.ru
лечение запоя
вывод из запоя краснодар
narkolog-krasnodar022.ru
вывод из запоя краснодар
purestylemarket – Classy and minimal style collections, perfect for modern shoppers.
trendandfashionhub – Love how stylish and updated the latest trends are here.
urbanbuycorner – Trendy products with a sleek city vibe, very enjoyable to explore.
createpositivechange – Love the uplifting message here, motivates me to do better daily.
beststylecollection – Stylish selections and great variety, makes shopping a real pleasure.
Теперь импорт проходит без ошибок, а все бумаги готовы заранее https://vsoprovozhdenie1.ru/
styleandchoice – Elegant and trendy, perfect for shoppers who love variety.
bestchoicecollection – Wide range of stylish products and great pricing overall.
brightstylemarket – Great experience shopping here, everything feels creative and affordable.
growyourmindset – The message here really motivates me to keep learning and improving.
采用高效谷歌外推策略,快速提升网站在搜索引擎中的可见性与权重。谷歌外推
everydaytrendhub – Always up to date with the latest trends, great resource.
everydaytrendstore – Perfect spot to grab new looks and keep up with fashion trends.
https://rimaakter.bloggersdelight.dk/2025/11/11/1xbet-bonus-code-2026-e130-for-sports/
discovermoreideas – Inspiring content for anyone looking to think outside the box.
findyourstylehub – Love the mix of classic and modern looks featured here.
learnandimprove – Simple yet powerful ideas that push me to do better daily.
shopandsaveonline – Awesome platform for smart shoppers looking for great online deals.
freshfindsoutlet – New and trendy products pop up here all the time, love it.
createpositivechange – Love the message and design, truly encourages meaningful growth.
вывод из запоя цена
vivod-iz-zapoya-minsk014.ru
вывод из запоя
Great web site. A lot of helpful info here. I am sending it to some buddies ans also sharing in delicious. And of course, thank you for your effort!
вывод из запоя
vivod-iz-zapoya-chelyabinsk014.ru
вывод из запоя круглосуточно челябинск
growtogetherstrong – Positive and motivating platform, perfect for teamwork and personal growth.
discoverinfiniteideas – Inspiring and creative site name that sparks imagination instantly.
экстренный вывод из запоя краснодар
narkolog-krasnodar023.ru
вывод из запоя
vulkanvegas50 net
learnshareachieve – Perfect for anyone who loves to learn and make steady progress.
uniquevaluehub – Excellent selection of quality products with standout value, love it.
trendandstyle – Great name that captures modern fashion and timeless personal style.
экстренный вывод из запоя
vivod-iz-zapoya-chelyabinsk015.ru
экстренный вывод из запоя челябинск
fashiondailycorner – Trendy fashion picks and great updates, really well-curated site.
globalmarketoutlet – Wide range of international products, makes shopping fun and diverse.
экстренный вывод из запоя
vivod-iz-zapoya-minsk015.ru
лечение запоя
экстренный вывод из запоя краснодар
narkolog-krasnodar024.ru
лечение запоя
discoverfashionfinds – Great site for fashion lovers, lots of trendy items to explore.
shopandsmiletoday – The name fits perfectly, such a cheerful and easy shopping experience.
Снова магазин порадовал своей оперативностью) сдеал заказ, получил трек всё бьётся! https://www.betterplace.org/en/organisations/70237 Жалко конечно что убрали покупку от грамма
trendworldmarket – Love how updated this site stays with the latest global trends.
Tham gia cộng đồng game thủ tại Go88 để trải nghiệm các trò chơi bài, poker phổ biến nhất hiện nay.
creativechoicehub – Innovative designs and creative products, really impressed with the variety.
shopthelatestdeals – Found amazing deals today, makes shopping fun and easy.
Есть кто оплатил и долго ждет адрес клада или трек??? https://say.la/read-blog/136689 Общая оценка магазина 10/10-идут на встречу покупателю, сервис общение и работа на высоте
вывод из запоя круглосуточно
vivod-iz-zapoya-cherepovec016.ru
вывод из запоя круглосуточно
yourdailyinspiration – Inspiring words and great visuals, perfect for a morning boost.
findbettervalue – Love the variety and affordability here, it’s worth checking daily.
simplechoiceoutlet – I appreciate the clean design and great value offered here.
discoverandshopnow – Great shopping experience, always something new and fun to explore.
вывод из запоя круглосуточно омск
vivod-iz-zapoya-omsk013.ru
лечение запоя
globalshoppingzone – Always finding new things here, global shopping made simple and fun.
brightcollectionhub – Colorful and stylish items that really make browsing enjoyable.
urbanwearzone – Love the streetwear collection here, everything feels modern and bold.
beststylecollection – Great shopping experience, stylish products and quick navigation.
shopandsmiletoday – Love the cheerful vibe here, shopping really does make me smile.
trendyvaluezone – Stylish products at affordable prices, love the variety here.
лечение запоя
narkolog-krasnodar025.ru
вывод из запоя цена
bestdailycorner – Found so many great daily deals here, totally worth visiting often.
finduniqueproducts – Unique finds and creative ideas, everything feels handpicked and quality.
а эффор хорош?) на что похож?) https://www.rwaq.org/users/osykytaxap-20251031172913 Если растворяется без подогрева – то не нужно. В ацетоне как правило (если продукт чистый) так и растворяется, и в осадок не выпадает, на спирту придется немного подогреть
Would love to perpetually get updated outstanding blog! .
trendandfashion – Perfect mix of classic and modern trends, always inspiring.
discoverandshop – Great platform for exploring unique items and discovering new favorites.
Закажу посмотрим я сам надеюсь что магазин хороший-проверенный https://www.band.us/page/100499895/ у меня наоборот. в этот раз быстрее все происходит)
groweverydaynow – Inspiring platform that reminds me to keep improving and learning daily.
Официальный сайт Kraken kra44 cc безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
http://hararat-gostar.com/en/index.php?subaction=userinfo&user=ulotynabe
вывод из запоя круглосуточно
vivod-iz-zapoya-cherepovec017.ru
вывод из запоя цена
groweverydaynow – Motivational and uplifting, reminds me to keep improving daily.
“про “шапку” вы все горазды писать в интернете…”И продавать в интернете Вы все горазды,х..й догонишь и не спорсишь! https://pubhtml5.com/homepage/qijfu есть что нибудь на подобие скорости или кокса?
Официальный сайт Kraken https://kra44-cc.at безопасная платформа для анонимных операций в darknet. Полный доступ к рынку через актуальные зеркала и onion ссылки.
freshtrendstore – New arrivals and trending items make shopping exciting every visit.
shopwithjoy – Love the cheerful vibe here, shopping truly feels joyful and easy.
globalmarketoutlet – Wide selection of global products, makes shopping interesting and diverse.
Ребята сайт хороший конечно, но вот у меня выдалась задержка с заказом, у кого были задержки отпишите сюда, просто раньше как только я делал заказа все высылалось либо к вечеру этого дня, либо на следующий, а теперь уже 4 дня жду отправки все не отправляют! https://kemono.im/ydguhafody/katchberg-kupit-kokain-mefedron-marikhuanu-boshki Самый крутой магазин!
вывод из запоя цена
vivod-iz-zapoya-omsk014.ru
лечение запоя омск
Кракен зеркало
Капельница от запоя – это значимая процедура, которая помогает быстрому восстановлению физического состояния человека, страдающего алкогольную зависимость. В Туле вызов нарколога для проведения этой процедуры оказывается всё более актуальным. Алкоголь негативно влияет на организм, вызывая симптомам похмелья, такими как головная боль, тошнота и слабость.Лечение алкоголизма включает detox, который способствует очищению организма от токсинов. Капельница обеспечивает поступление жизненно важных веществ, улучшая состояние пациента. Нарколог предоставляет медицинскую помощь при запое, что позволяет избежать серьёзных осложнений. вызов нарколога тула Реабилитация организма после запоя требует комплексном подходе, включая реабилитацию от алкоголя. Лечение запоя может включать как медикаментозные методы, так и психотерапевтическую помощь. Следует помнить, что здоровье – это главное, и оперативная помощь нарколога может оказаться решающей.
yourdailyfinds – Convenient and fun to browse, always discovering something useful.
shopthelatestdeals – Convenient platform for finding amazing deals quickly and easily.
bestchoiceoutlet – Great prices and selections, feels like a hidden gem for shoppers.
globalmarketoutlet – Wide selection of global products, makes shopping interesting and diverse.
вывод из запоя круглосуточно череповец
vivod-iz-zapoya-cherepovec018.ru
вывод из запоя череповец
learnandshine – Encouraging content that motivates me to grow and shine every day.
makeeverymomentcount – I enjoy visiting this page when I need a dose of positivity.
startsomethingnewtoday – Motivating name and content that encourages taking the first step.
growwithpurpose – Excellent site with a strong message about intentional self-growth.
globalshoppingzone – Shopping here is always fun and hassle-free.
yourtimeisnow – Motivating site that encourages taking action and embracing opportunities today.
shopforvalue – Perfect site for anyone who wants quality without overspending.
dreamdiscovercreate – Every visit feels inspiring, always something interesting to explore.
brightstylemarket – The store feels modern, clean, and easy to browse.
discoverandshop – Makes online shopping fun, efficient, and totally stress-free.
findhappinessdaily – Love the positivity here, helps me focus on the good things.
explorewithoutlimits – Inspires creativity and curiosity, perfect for adventurous minds.
вывод из запоя цена
vivod-iz-zapoya-omsk015.ru
вывод из запоя
discoveramazingstories – Captivating stories and inspiring content, keeps me coming back.
yourdealhub – Excellent deals on quality products, really makes shopping worthwhile.
Лекарственные средства для лечения алкогольной зависимости могут включать лекарства для коррекции зависимости‚ которые облегчают симптомы. Круглосуточная помощь и контроль при детоксикации обеспечивают защищенность пациента. Поддержка родственников также имеет большое значение для успешного восстановления после алкогольной интоксикации. вывод из запоя круглосуточно Рекомендации по детоксикации могут включать регулярное общение с врачом и придерживание распорядка. Рекомендуется обратиться за поддержкой‚ чтобы избежать рецидивов и обеспечить эффективную терапию.
changeyourmindset – Inspiring site that helps shift perspectives and encourages real growth.
uniquegiftcorner – Creative and thoughtful gift ideas, ideal for any occasion.
вывод из запоя цена
vivod-iz-zapoya-irkutsk013.ru
вывод из запоя круглосуточно
everydayvaluezone – Great deals and simple navigation, really makes shopping effortless.
trendandbuy – Awesome spot for trendy finds, love browsing the latest styles.
trendloversplace – Perfect for trend enthusiasts, always something fresh and exciting to see.
modernstylecorner – Sleek and contemporary selections, perfect for style-conscious shoppers.
casino arica valor entrada casino arica valor entrada .
trendandbuy – Awesome spot for trendy finds, love browsing the latest styles.
vavada casino pl
Nabycie nieruchomosci w Beskidach to szansa na stworzenie wymarzonego miejsca na wakacje lub staly dom.
Dzieki rozwijajacej sie infrastrukturze i rosnacemu zainteresowaniu turystow, ceny dzialek stopniowo wzrastaja. Region ten przyciaga milosnikow gorskich wedrowek i aktywnego wypoczynku.
#### **2. Gdzie szukac najlepszych ofert dzialek?**
Wybor odpowiedniej lokalizacji zalezy od indywidualnych potrzeb i budzetu. Warto sprawdzic profesjonalne strony internetowe, takie jak dzialki-beskidy.pl, ktore prezentuja sprawdzone oferty.
Przed zakupem nalezy dokladnie przeanalizowac dostepnosc mediow i warunki zabudowy. Niektore tereny wymagaja dodatkowych formalnosci, dlatego warto skorzystac z pomocy ekspertow.
#### **3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
Nieruchomosc w gorach to nie tylko inwestycja finansowa, ale rowniez szansa na poprawe jakosci zycia. Mozna tu zbudowac dom letniskowy i cieszyc sie urokami przyrody przez caly rok.
Dodatkowo, region ten oferuje wiele atrakcji, takich jak szlaki turystyczne i stoki narciarskie. Coraz wiecej osob wybiera te lokalizacje ze wzgledu na dobrze rozwinieta baze rekreacyjna.
#### **4. Jak przygotowac sie do zakupu dzialki?**
Przed podjeciem decyzji warto skonsultowac sie z prawnikiem i geodeta. Wizyta na miejscu i rozmowa z sasiadami moga dostarczyc cennych informacji o okolicy.
Wazne jest rowniez okreslenie swojego budzetu i planow zwiazanych z zagospodarowaniem terenu. Niektore oferty pozwalaja na rozlozenie platnosci, co ulatwia inwestycje.
—
### **Szablon Spinu**
**1. Dlaczego warto kupic dzialke w Beskidach?**
– Inwestowanie w dzialki w tym regionie to swietny sposob na zabezpieczenie finansowej przyszlosci.
– Dzialki w Beskidach to coraz czesciej wybierana lokata kapitalu przez swiadomych inwestorow.
**2. Gdzie szukac najlepszych ofert dzialek?**
– Dobrym rozwiazaniem jest skorzystanie ze sprawdzonych stron internetowych, takich jak dzialki-beskidy.pl.
– Kluczowe jest sprawdzenie, czy dzialka ma wszystkie niezbedne pozwolenia.
**3. Jakie korzysci daje posiadanie dzialki w Beskidach?**
– Posiadanie ziemi w gorach to szansa na zbudowanie wymarzonego domu lub miejsca wypoczynkowego.
– Coraz wiecej osob docenia walory turystyczne i rekreacyjne Beskidow.
**4. Jak przygotowac sie do zakupu dzialki?**
– Wazne jest zasiegniecie porady prawnej przed podpisaniem umowy.
– Okreslenie budzetu i celow inwestycji ulatwi podjecie wlasciwej decyzji.
1xbet giri? adresi 1xbet-7.com .
перепланировка офиса http://www.soglasovanie-pereplanirovki-1.ru/ .
purefashionchoice – Clean, stylish fashion selections that are both modern and practical.
beep beep казино официальный сайт beepbeepcasino-online.com .
surewin login malaysia surewin-online.com .
believeinyourdreams – Truly motivating theme, I love the positivity this site spreads.
экстренный вывод из запоя
vivod-iz-zapoya-orenburg013.ru
вывод из запоя цена
Лечение запоя в Туле это важная задача, которая требует квалифицированного вмешательства. Алкоголизм — это беда, способная сломать судьбы, и помощь при запое жизненно важна для всех, кто оказался в этой ситуации. В специализированных клиниках, занимающихся лечением запоя предлагаются множество программ, ориентированных на вывод из запоя и дальнейшую реабилитацию. Стоимость лечения алкоголизма варьируется в зависимости от выбранной клиники и уровня предоставляемых услуг . В стоимость может входить консультация нарколога, медицинская помощь при запое и услуги по детоксикации. лечение запоя тула Наркологическая помощь в Туле включает в себя как стационарное, так и амбулаторное лечение , что также влияет на стоимость . Программа лечения алкоголизма индивидуализирована и может включать детоксикацию, психологическую поддержку и реабилитацию . Комплексный подход к лечению зависимостей в Туле позволяет не только прервать алкогольный марафон, но и избежать рецидивов . Поэтому, если вам или вашим близким требуется помощь, важно не откладывать обращение к профессионалам.
brightcollectionhub – Love the name—it perfectly matches the bright, modern selections here.
globalvaluecorner – Amazing value and variety of products from around the world.
вывод из запоя
vivod-iz-zapoya-irkutsk014.ru
лечение запоя
modernshoppingcorner – Modern design, easy shopping flow, and great product selection.
believeandachieve – Positive and motivational content, perfect for personal growth seekers.
dreamfashionfinds – Great place to explore unique outfits and accessories.
Когда сайт недоступен в сети,
многие используют онион-адрес.
В таких случаях удобно, что появляются новые маршруты.
Зайти на KRAKEN: kra47cc – эта ссылка помогает восстановить доступ в пару кликов.
А если и эта версия недоступна,
то запасной вариант всегда есть:
.
classystylemarket – Their collection always feels curated and high-quality.
everydayessentials – Convenient site to find daily essentials quickly and easily.
trendworldmarket – Always impressed with the variety of new trends featured here.
buildyourownfuture – Perfect for anyone looking to shape their future intentionally.
globalfindsoutlet – Love the global vibe and diverse selection available here.
crown of valor casino crown of valor casino .
trendandfashion – My go-to place for discovering new looks and fashion inspiration.
Сегодня оплатил, сегодня же отправили и выслали трек который уже бьется, все ровно пацики спасибо https://rant.li/iafmybufica/shymkent-kupit-kokain-mefedron-marikhuanu-boshki Ну, красавы. Вечером оплатил на следующий день отправили
freshcollectionhub – Fresh products, great presentation, and a fun browsing experience.
1 x bet https://1xbet-7.com/ .
заказ перепланировки квартиры soglasovanie-pereplanirovki-1.ru .
beep casino https://www.beepbeepcasino-online.com .
surewin malaysia login http://www.surewin-online.com .
вывод из запоя круглосуточно оренбург
vivod-iz-zapoya-orenburg014.ru
вывод из запоя круглосуточно оренбург
Ребят всё приготовил ребятам дал попробовать пробники всё ровно на высшем уровне) https://wanderlog.com/view/axcmilbiti/яновичи-купить-кокаин-мефедрон-марихуану-бошки/ когда появится новинки??
findnewhorizons – A wonderful reminder to explore, grow, and discover new opportunities.
Прокапывание от алкоголизма в городе Туле – это ключевой шаг в борьбе с алкоголизма. Методы детоксикации способствуют справиться с симптомами абстиненции и освободиться от запойного состояния. Медицинская помощь в специализированных центрах включает не только капельницы‚ но и психологическую помощь‚ что способствует восстановлению после алкоголя. narkolog-tula025.ru Реабилитация начинается с очистки организма‚ после которой инициируются реабилитационные программы. Роль родственников также имеет значимую роль в профилактике рецидивов. Группы поддержки и обращение к специалиста могут помочь в процессе реабилитации. Не упускайте из виду‚ что борьба с алкоголизмом требует комплексного подхода.
dailydealsplace – Always updated with great bargains, love checking in daily.
вывод из запоя круглосуточно
vivod-iz-zapoya-irkutsk015.ru
лечение запоя
У меня не бьётся вторые их трек. И бро в скайпе не видно. Мож приняли их посылки на почте? Тоже парюсь блин…. Но не хотел поднимать дискуссию, не имея причин. Выслали в пятницу СПСР. https://kemono.im/obhicade/tsiurikh-kupit-kokain-mefedron-marikhuanu-boshki ещё раз говорю, здесь качество отменное, по крайней мере с той партии, с которой я получал. 1к10 убивало в мясо с напаса )
trendandbuy – Trendy items at good prices, always up to date with new arrivals.
budgetfriendlyhub – Great variety of affordable options without sacrificing style or quality.
learncreategrow – Inspiring content that encourages learning, creating, and personal growth.
Хочу описать работу магазина.Ну начну клад получил вчера с момента отправки прошло 3ое суток супер,маскировка на 5 балов молодцы спасибо за книгу от души буду духовно развиваться товар бомба основа горит отлично в общем оценка 5 твердая))))) https://wanderlog.com/view/yosxfwqaqj/серафимович-купить-кокаин-мефедрон-марихуану-бошки/ ТС подтвердив оплату, сказал ожидать. В оговоренные сроки адрес был получен в ЛС.
classystyleoutlet – Love the elegant yet accessible fashion choices available here.
brightfashionhub – Discovered a few new trends that I might actually try this month.
сделайте уже что-нибудь с этим реестром… хочу сделать заказ https://www.brownbook.net/business/54455982/баллито-купить-кокаин-мефедрон-марихуану-бошки/ У меня в городе например СПСР – это самая безпалевная курьерка, а с ЕМС постоянно принимают.Так что кому как
growtogethercommunity – Navigation was smooth, and each section offered something worth checking out.
valor valor .
growtogetherstrong – Positive and motivating, perfect for teamwork and community growth.
fashionchoicehub – This place always offers new fashion ideas without feeling overwhelming or repetitive.
вывод из запоя круглосуточно оренбург
vivod-iz-zapoya-orenburg015.ru
экстренный вывод из запоя оренбург
findnewdeals – Solid experience again today, definitely checking back for more useful deals.
bestbuycollection – Overall a reliable place to explore products without feeling rushed or confused.
findnewhorizons – Overall a positive visit with ideas that felt meaningful and encouraging.
лечение запоя калуга
vivod-iz-zapoya-kaluga016.ru
экстренный вывод из запоя калуга
exploreopportunityzone – Excellent motivational content, helps me think bigger and act smarter.
1 xbet http://1xbet-7.com .
только что был свидетелем того как парней приняли с ам2233 и тусиаем от чемикала на спср офисе, вывели в браслетах посадили в микрик и увезли, чего ожидать? чем им помочь? https://www.montessorijobsuk.co.uk/author/tidvogpu/ Где продавец то? Мысли самые печальные…тт
согласование перепланировки помещений согласование перепланировки помещений .
Анонимный вызов врача нарколога — это важный шаг для людей, столкнувшихся с зависимостями при лечении алкогольной и наркотической зависимости. На сайте narkolog-tula026.ru вы можете обратиться за помощью и воспользоваться наркологической помощью. Это особенно важно для тех, кто испытывает проблемы с алкоголем и наркотиками. Услуги нарколога включают оценку состояния зависимостей и лечение при употреблении наркотиков. Анонимный нарколог может приехать на дом, что гарантирует приватность и удобство. Выездные медработники предоставляют поддержку психолога и проводят реабилитацию наркозависимых. Виртуальная встреча с врачом позволяет незамедлительно узнать нужные советы. Лечение наркотиков анонимно — это шанс изменить свою жизнь без опасений о предвзятости. Не упустите шанс изменить свою судьбу с помощью анонимных услуг здоровья!
beep beep casino https://beepbeepcasino-online.com/ .
https://portfolio-rdzhqal.format.com/a5c157dbc0-blog/code-bonus-inscription-melbet-2026-offre-200
buildyourownfuture – Great motivational site, helps focus on goals and planning ahead.
Качество, если честно на моё удивление (тк. первый раз я пользуюсь услугами данного ТС), по отзывам клиентов, сказать отличное это сказать ничего, ССССУУУУУПППЕЕЕЕРРРР!!!!!! https://say.la/read-blog/135742 да, самая действенная схема для работы с чемикалом
https://www.linkedin.com/pulse/maximize-your-winnings-how-claim-1xbetfreebet-today-work-detail-apex-r8gqf/
classystylemarket – Stylish products with great prices, love the classy layout of this site.
Если зеркало KRAKEN перестало работать,
многие используют альтернативный маршрут.
В таких случаях удобно, что выдаются новые версии ссылок.
Зайти на KRAKEN: кракен меф – эта ссылка помогает восстановить доступ в пару кликов.
А если зеркало стало медленным,
то запасной вариант всегда есть:
.
https://rima-akter.mn.co/posts/melbet-promo-code-2026-rich888-%E2%82%AC130-future
Ну мы стараемся https://yamap.com/users/4928246 Отличный магазин Chemical-mix
dreamdiscovercreate – Truly inspiring space that encourages creativity and following your dreams.
creativegiftoutlet – Amazing gift ideas, really unique and thoughtful selections available here.
слоты бонус за регистрацию
Магаз что надо, забегаем! Всем мира! https://anyflip.com/homepage/cvftn Это фейк что тут вам не понятно то.
лечение запоя калуга
vivod-iz-zapoya-kaluga017.ru
вывод из запоя цена
лечение запоя смоленск
vivod-iz-zapoya-smolensk025.ru
вывод из запоя смоленск
пиши разберемся https://www.montessorijobsuk.co.uk/author/kehvacof/ хуясе надо было сначало уточнить а что брали хоть? ио названижю вещества
shopforvalue – Affordable products without compromising quality, makes shopping super satisfying.
Алкогольная зависимость – это серьезная проблема, требующая внимания, требующая квалифицированной помощи. В Туле и окрестностях доступно множество услуг, которые могут помочь вашему близкому. Первым шагом может стать вызов наркологу на дом, чтобы получить квалифицированную помощь при запое. Специалисты проведут очистку организма и предложат процесс реабилитации алкоголизма, включая психологическую поддержку при запое.Не менее важно также обеспечить эмоциональную поддержку. Родственники должны осознавать рекомендации для родственников, как вести себя в кризисной ситуации с алкоголем. Специальные занятия по алкоголизму помогут выяснить в проблеме и выбрать правильный подход к реабилитации от алкоголя. вызвать нарколога на дом Тула Не забывайте о том, что освобождение от зависимости – это длительный процесс. Профессиональная помощь и поддержка родственника помогут ему вернуться к нормальной жизни.
ребята как-то странно работают,но надеюсь,что честно https://www.divephotoguide.com/user/habuyuhy Лучшее качество на Рынке РК!!! Низкие цены!! И без кидалова! УВАЖЕНИЕ ВАМ РЕБЯТА!!!
findamazingoffers – Excellent deals and diverse products, makes shopping super satisfying.
growbeyondlimits – Encouraging platform that inspires personal growth and pushing boundaries every day.
surewin malaysia login http://surewin-online.com/ .
Если зеркало KRAKEN перестало работать,
многие используют резервный путь.
В таких случаях удобно, что выдаются новые версии ссылок.
Зайти на KRAKEN: кракен официальный – эта ссылка помогает восстановить доступ в пару кликов.
А если соединение прерывается,
то запасной вариант всегда есть:
.
вывод из запоя
vivod-iz-zapoya-kaluga018.ru
экстренный вывод из запоя калуга
Ищете, где купить права категории Б быстро и надежно? Мы предлагаем полный комплекс услуг по оформлению водительских удостоверений с гарантией качества и конфиденциальности. Профессиональная помощь, доступные цены и оперативное оформление документов без лишних хлопот. Получите свои водительские права легально и в кратчайшие сроки.
trendyvaluezone – Really liked the variety; something new always pops up when browsing.
Trend Spotting Portal – Items were diverse, discovered unique finds with ease.
Your Potential Hub – Came across an inspiring thought that encouraged me to take action.
changeyourmindset – Another positive experience here, found something valuable within just a minute.
findamazingoffers – Excellent deals and diverse products, makes shopping super satisfying.
discovermoreideas – The content here feels thoughtful and always gives me something new.
dreambuildachieve – Some short tips here helped me rethink my approach in a good way.
learnsomethingincredible – Found a few fun facts today that genuinely brightened my morning.
dreamshopworld – Loved how smooth the browsing felt with everything clearly organized nicely.
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk026.ru
лечение запоя
Hot Deals Hub – The platform is great, deals are refreshed daily.
На территории Тулы доступна круглосуточная служба вызова нарколога на дом, которая предоставляет наркологические услуги для пациентов с зависимостями. Если вы или ваши родные требуется помощь в борьбе с алкоголизмом, квалифицированный специалист предоставит необходимую медицинскую помощь на дому, гарантируя полную анонимность. вызов нарколога тула Если вы ищете надежное решение, услуга вызова нарколога в Туле является первым шагом на пути к новой жизни.
heaps of wins free chip codes heaps of wins free chip codes .
icebet giri? icebet giri? .
goliath casino bonuskode http://www.goliath-casino.com/ .
школа seo https://kursy-seo-12.ru/ .
Quick Buy Portal – Noticed something that helped me get exactly what I needed.
dreamfashionfinds – Stylish and trendy fashion finds that make everyday shopping fun.
Trend Market Spot – Love seeing the new items, the trends change constantly.
Кракен зеркало вход на сайт — надежный способ обойти блокировки и получить доступ к популярной платформе Кракен. Если официальный сайт недоступен из-за региональных ограничений или технических проблем, зеркало Кракен поможет быстро и безопасно войти на сайт без потери функционала.
вывод из запоя цена
vivod-iz-zapoya-krasnodar021.ru
экстренный вывод из запоя
Unique Browse Portal – Loved how straightforward everything looked, made browsing smooth.
Fashion Insight Hub – Daily fashion updates keep shopping fresh and fun.
newstesting12112 – A simple, updated and reader-friendly website for quick information.
вывод из запоя цена
vivod-iz-zapoya-smolensk027.ru
лечение запоя
Trend Discovery Hub – Wide selection, found unique pieces quickly and easily.
кухни на заказ спб кухни на заказ спб .
What’s up to every one, the contents present at this website are really awesome for people knowledge, well, keep up the good work fellows.
Shop Deals Daily – Discovered a useful item that matched exactly what I was after.
startsomethingnewtoday.click – Smooth experience, content loads quickly and navigation feels very intuitive.
пансионат для реабилитации после инсульта
pansionat-msk013.ru
пансионат для пожилых людей
globalfindsoutlet.click – Found exactly what I needed, fast shipping made me happy today.
icebet casino icebet casino .
goliathcasino http://goliath-casino.com/ .
Thank you for sharing excellent informations. Your site is very cool. I am impressed by the details that you have on this web site. It reveals how nicely you understand this subject. Bookmarked this website page, will come back for extra articles. You, my friend, ROCK! I found just the info I already searched all over the place and simply could not come across. What a perfect website.
Value Hub Online – Navigating the site felt smooth, and the prices seemed fair.
happylifestylemarket.click – Love the variety here, everything feels fresh and high quality.
вывод из запоя круглосуточно краснодар
vivod-iz-zapoya-krasnodar022.ru
экстренный вывод из запоя краснодар
discovernewcollection.click – Easy to navigate site, shopping experience was smooth and fast.
urbantrendstore.click – Smooth checkout experience, everything worked perfectly without any issues today.
learnsomethingincredible.click – Site loads fast, tutorials work perfectly, learning experience was enjoyable today.
yourjourneycontinues – This site shared a thought today that genuinely kept me motivated.
Inner Harmony Portal – Inspiring material that calms the mind and soothes the soul.
Personal Growth Portal – Motivating posts that inspire me to take practical steps forward.
City Buy Portal – Found navigating easy, with detailed product info at every step.
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk028.ru
лечение запоя смоленск
icebet casino icebet casino .
учиться seo kursy-seo-12.ru .
пансионат для престарелых людей
pansionat-msk014.ru
пансионат для лежачих москва
экстренный вывод из запоя краснодар
vivod-iz-zapoya-krasnodar023.ru
вывод из запоя круглосуточно
Begin Anew Hub – Useful advice for making changes, feels easy to follow.
Style Discovery Page – Found some standout pieces that were worth noting.
Self Growth Portal – Articles are well-written and motivate ongoing self-improvement.
Fashion Discovery Spot – Cute items and unexpected finds that are totally unique.
вывод из запоя смоленск
vivod-iz-zapoya-smolensk029.ru
вывод из запоя цена
лечение запоя краснодар
vivod-iz-zapoya-krasnodar024.ru
вывод из запоя краснодар
Daily Discount Hub – Deals update all the time, always something new to see.
курсы seo курсы seo .
Modern Fashion Finds – Came across fresh styling tips that made coordinating outfits easier.
кракен даркнет
пансионат для пожилых с деменцией
pansionat-msk015.ru
частный пансионат для пожилых людей
bestpickshub.click – Delivery was quick, packaging kept everything safe, very satisfied overall.
bestbuycollection.click – Website layout is clean, makes browsing easy and enjoyable always.
Dream Achieve Portal – Posts are genuinely inspiring and help me focus on my goals.
Learn & Grow Hub – Came across a tip that proved to be really practical.
Choice Explorer Hub – Options are diverse, finding what I needed was quick and easy.
Dadasdas Trends – Trending topics ko quick, simple aur readable format mein cover karta hai.
лечение запоя
vivod-iz-zapoya-krasnodar025.ru
лечение запоя краснодар
вывод из запоя круглосуточно
vivod-iz-zapoya-smolensk030.ru
экстренный вывод из запоя
Every Moment Hub – Came across a small reminder to enjoy today’s little things.
https://myworldgo.com/forums/topic/255558/sannha
Fashion Flow Hub – Minimalist style, shopping and checkout is effortless.
IT перевод в бюро переводов Перевод и Право telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
бюро переводов в москве teletype.in/@alexd78/iF-xjHhC3iA .
https://www.snowexpress.co.uk/news/2018/06/26/winter-18-19-on-sale-now
пансионат с медицинским уходом
pansionat-tula013.ru
дом престарелых
https://topsitenet.com/profile/1xbetcode1/1500741/
fashiondailycorner.click – Great browsing experience, products load quickly and descriptions feel clear today.
Fresh Ideas Hub – Creative selections here inspired me to think differently right away.
Fresh Trend Finds – Noticed a few stylish pieces that were worth checking out.
Trend Discovery Portal – Always new items to explore, makes checking trends fun.
Если вам или вашим близким требуется помощь при алкоголизме‚ важно знать‚ как вызвать нарколога на дом в Красноярске. Вызов специалиста нарколога на дом позволяет получить экстренную помощь без необходимости в посещении клиники. Это особенно актуально при лечении запоя‚ когда человек нужен в медицинской помощи немедленно. врач нарколог на дом Начальным этапом будет поиск услуг нарколога. Есть возможность обратиться в специализированные клиники или использовать онлайн-сервисами для вызова нарколога. Консультация нарколога содействует оценить состояние пациента и выявить необходимое лечение зависимости.При вызове врача важно сообщить о признаках запоя‚ чтобы нарколог мог подготовиться к оказанию помощи. Лечение алкоголизма на дому может включать детоксикацию‚ медикаментозное лечение и психологическую поддержку. Конфиденциальная помощь нарколога также доступна‚ что делает процесс более комфортным для пациента.В Красноярске есть различные адреса наркологических клиник‚ где возможно получить дополнительные услуги и реабилитацию от алкоголя. Помните‚ что медицинская помощь на дому может стать началом к восстановлению и улучшению качества жизни. Если вам необходима экстренная помощь нарколога‚ действуйте незамедлительно – здоровье приоритетно!}
Perfect Gift Ideas – Spotted a few interesting items that could delight someone special.
В городе Тула доступна помощь от алкоголизма в клиниках‚ которые предлагают детоксикационный курс и лечение зависимости. Программы лечения включают кодирование от алкоголя и медицинское сопровождение при алкоголизме. Необходимо также получить психологическую помощь и участвовать в группах поддержки для зависимых, таких как анонимные алкоголики. Восстановление после запоя требует комплексного подхода: консультации нарколога помогут разработать индивидуальный план. Важно помнить о профилактике рецидива и придерживайтесь рекомендаций по отказу от алкоголя. Дополнительную информацию можно найти на сайте vivod-iz-zapoya-tula013.ru;
https://www.jk-green.com/forum/topic/56944/c%C3%B3digo-bono-1xbet-2026:-%E2%82%AC130-bienvenida
Shopping Finds Hub – Easy to navigate, I locate items effortlessly.
it переводчик услуги telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
топ -10 бюро переводов в мск teletype.in/@alexd78/iF-xjHhC3iA .
зеркало кракен
Your Potential Insight – Read something uplifting that gave me a little push today.
Style Picks Hub – International fashion choices that shipped surprisingly fast.
пансионат для пожилых с деменцией
pansionat-tula014.ru
пансионат для лежачих после инсульта
игровые автоматы деньги за регистрацию без депозита
Капельницы для лечения алкоголизма – это необходимая процедура в лечении алкоголизма‚ позволяющий преодолеть с последствиями отмены алкоголя и восстановить организм после запоя. При присутствии алкогольной зависимости‚ детоксикация становится необходимой для выведения токсинов из организма. Процедура включает в себя использование капельниц‚ которые предоставляют медицинскую помощь и наполняют организм необходимыми веществами. Лечение алкоголизма включает не только прокапывание‚ но и реабилитацию. Поддержка близких играет важную роль в успешном лечении. Алкоголь может нанести серьезный урон здоровью‚ но с адекватной терапией и опорой близких возможно выздоровление от алкогольной зависимости. На сайте vivod-iz-zapoya-krasnoyarsk017.ru вы можете найти информацию о различных методах лечения‚ включая прокапывание‚ которые помогут вам или вашим близким на пути к выздоровлению.
Potential Path Spot – Advice and resources that support focused self-improvement.
Joyful Finds Portal – Came across items that made browsing feel fun and worthwhile.
Спинтакс капельницы от запоя — надежный вариант помочь людям, страдающим от алкогольной зависимости. В Туле существует ряд медицинских учреждений, предлагающих лечение запоя в любое время. При поиске медицинского учреждения важно обратить внимание на квалификацию врачей, предлагаемые программы лечения зависимости и качество проводимых процедур.Медикаментозное лечение запоя включает в себя индивидуальную программу к пациентам. Консультация нарколога поможет определить необходимость капельницы и другие способы лечения. Также важна поддержка родственников, которая является неотъемлемой частью процесса.вывод из запоя круглосуточно тула Клиника в Туле должна иметь услуги нарколога и программы восстановления, чтобы гарантировать комплексное лечение. Помощь при алкоголизме может быть доступна 24 часа в сутки, что способствует эффективному лечению.
Learning Edge Portal – Informative posts provide clear, actionable learning strategies.
Хороший магазин.С ним почти год работаю.Всегда вежливое общение: успокоит,объяснит,по рекомендует.Все приходит в срок.Данным магазином очень доволен.Рекомендую!!! https://a1dir.info Бро подскажи ато я переживаю заказал 10 гр
Buy Zone Picks – Stopped by for a moment but still found some interesting products.
Реактивы отличного качества. Особенно JWH серия https://diaspora-world.info “Ладно думаю доберусь до дома там опробую нозально “
Fashion Trend Spot – New arrivals caught my eye, the variety was excellent.
it переводчик заказать telegra.ph/Oshibka-lokalizacii-pochemu-vash-IT-produkt-ne-ponimayut-za-granicej-11-09 .
бюро переводов в москве teletype.in/@alexd78/iF-xjHhC3iA .
Прокапаться от алкоголя в Красноярске — важный шаг на пути избавления от алкогольной зависимости. Лечение алкоголизма начинается с detox-программы , которая помогает организму очищаться от токсинов. Необходимо получить медицинскую помощь при алкоголизме, чтобы предотвратить алкогольный синдром и другие осложнения . vivod-iz-zapoya-krasnoyarsk018.ru После детоксикации рекомендуется пройти курс реабилитации, где пациент получает поддержку психолога и поддержку при отказе от алкоголя. Группы анонимных алкоголиков становятся опорой на данном этапе. Программы восстановления включают советы по отказу от алкоголя и меры по предотвращению рецидивов. Социальная адаптация после лечения и поддержка близких играют важную роль в мотивации к трезвости .
Можно позвонить в СПСР, у них там даётся полная инфа по треку, по телефону. Где чё лежит. Если не написано в ленте… Завтра звякну, отпишу, если не появится. купить онлайн мефедрон, экстази, бошки
дом престарелых в туле
pansionat-tula015.ru
пансионат для пожилых с инсультом
Value Hub Online – Found a selection of practical deals that were worth checking.
shopthelatestdeals – Found amazing deals today, makes shopping fun and easy.
freshstyleboutique.click – Clean and modern layout, makes checking new arrivals incredibly easy today.
товар появился? когда возобновите доставку по городам? купить кокаин, меф, бошки через телеграмм
fashiondailycorner.click – Really loved the colors and styles, definitely returning to explore more.
действующий промокод на 1хбет Используйте действующий купон на http://www.google.as/url?q=https://bergkompressor.ru/news/artcles/?1xbet_promokod_pri_registracii_bonus_5.html и получите бонус до 32 500 рублей, чтобы начать ставки с преимуществом.
Проблема алкогольной зависимости является серьезной и требует профессионального вмешательства. В Туле доступны услуги по выводу из запоя, которые обеспечивают безопасную детоксикацию и восстановление. Наркологическая клиника предлагает круглосуточную поддержку и анонимное лечение, что гарантирует конфиденциальность. вывод из запоя тула
trendyvaluezone – Stylish products at affordable prices, love the variety here.
Opportunity Gateway – Helpful ideas and actionable advice that simplify exploring new possibilities.
Unique Picks Hub – Found several interesting products that grabbed my attention.
Tham gia cộng đồng game thủ tại Go88 để trải nghiệm các trò chơi bài, poker phổ biến nhất hiện nay.
бездепозитные слоты
магазу процветания желаю и клиентов хороших и честных! купить Кокаин, Мефедрон, Экстази
discoverandshop – Great platform for exploring unique items and discovering new favorites.
Неотложная помощь при алкогольной зависимости в Красноярске становится актуальной для многих. Сайт vivod-iz-zapoya-krasnoyarsk019.ru предлагает услуги нарколога, специализирующегося на лечении алкоголизма и вывода из запоя. В данную процедуру входит медицинская помощь, детоксикация организма от алкоголя и психотерапевтические сеансы. Обязательно обратитесь к врачу для эффективного преодоления алкогольной зависимости. Наша программа восстановления фокусируется на реабилитации и поддержке зависимых, а также социальной адаптации. Профилактика рецидивов, ключевой элемент эффективного лечения. Помните, что обратится за помощью, это первый шаг к здоровью.
Магазин очень хороший всё чётко и быстро и селер грамотный вы правы купить онлайн мефедрон, экстази, бошки
Innovative Ideas Portal – Read a concept here that sparked some creative thoughts.
частная психиатрическая помощь
psychiatr-moskva010.ru
вызвать психиатра на дом в москве
globalmarketoutlet – Wide selection of global products, makes shopping interesting and diverse.
были случаи купить Мефедрон, Бошки, Марихуану
Профилактика запоев после вывода – значимая проблема для сохранения здоровья и предотвращения рецидивов. Нарколог на дом в владимире предоставляет услуги по помощи в лечении алкоголизма и предотвращению запойного состояния. Ключевым элементом является психологическая поддержка, которая помогает справляться с трудностями.Советы нарколога включают методы борьбы с запойным состоянием, такие как создание здорового образа жизни и поддержка семьи в лечении алкоголизма. Реабилитация после запоя требует медицинского вмешательства при алкогольной зависимости и консультации специалиста по алкоголизму. Обращение к наркологу на дом обеспечивает удобство и доступность терапии. нарколог на дом владимир Важно помнить, что восстановление после запоя – это процесс, требующий времени, сил и терпения. Профилактика рецидивов включает в себя постоянные консультации с наркологом и применение методов, способствующих поддержанию хорошего здоровья и отказу от алкоголя.
“Лазею я по форуму,точнее по веткам и на ветке Эскимоса вижу запись на Пробы” купить скорость, кокаин, мефедрон, гашиш
Savings Hub Link – Found a solid offer here that felt genuinely useful.
globalmarketoutlet – Wide selection of global products, makes shopping interesting and diverse.
globaltrendstore.click – Checkout was fast, site navigation made finding trendy products really simple today.
магазин ровнеый,за что им спасибо,если сами тупить не будете всё пройдёт ровно и без проблем.Товар тоже порадовал,довольно таки неплохо)) купить Кокаин, Мефедрон, Экстази
Капельница от запоя на дому в Красноярске: быстрое облегчение Алкогольная зависимость — серьезная проблема, требующая квалифицированной помощи. В Красноярске вы можете вызвать нарколога на дом в любое время, который предложит лечение запоя, включая капельницы. Это эффективный способ для быстрого снятия абстиненции и восстановления после запоя.Важно не только облегчить симптомы, но и предоставить полноценную медицинскую помощь при запое. Капельница помогает быстро снять похмелье, улучшить общее состояние и предотвратить осложнения. Заказ капельницы на дом — удобное решение для тех, кто хочет избежать стационарного лечения и получить помощь в знакомой обстановке.Круглосуточная помощь нарколога позволяет обеспечить детоксикацию алкоголика в любое время. Помните, что лечение запоя на дому включает в себя как физическое, так и психологическое восстановление. Процесс реабилитации от алкогольной зависимости является длительным и требует всестороннего подхода. нарколог на дом круглосуточно Красноярск Если вы или ваши родные испытываете трудности с алкогольной зависимостью, не стоит откладывать обращение за помощью. Услуги нарколога в Красноярске доступны круглосуточно, и каждый может рассчитывать на профессиональную поддержку.
changeyourfuture.click – Helpful guides available, makes planning and achieving goals much easier today.
yourtimeisnow – Motivating site that encourages taking action and embracing opportunities today.
конечно была задержка которая заставила по нервничать, но всё прошло на уровне и я получил свою посылочку))) купить Мефедрон, Бошки, Марихуану
Budget Style Hub – Easy-to-browse sections with well-priced, stylish items.
бездепозитные фриспины
aeroplane game money http://www.aviator-game-predict.com .
электрокарнизы цена https://www.prokarniz36.ru .
консультация врача психиатра
psychiatr-moskva011.ru
психиатрическая клиника стационар
ты брал вообще не скоростило или как ? купить Мефедрон, Бошки, Марихуану
yourdealhub – Excellent deals on quality products, really makes shopping worthwhile.
Наркологическая служба — это важная часть здравоохраненияпредоставляющая лечение зависимостей и восстановление. На сайте vivod-iz-zapoya-vladimir021.ru можно узнать информацию о наркологических клиниках, где предоставляется помощь при алкогольной зависимости и наркотической зависимости. Психотерапия и программы реабилитации помогают пациентам восстановиться, а поддержка родственников играет важнейшую роль в процессе. Также предлагаются консультации в анонимном режиме и службы экстренной помощи для срочной помощи. Профилактика зависимости и социальная адаптация — ключевые моменты работы наркологической службы.
Не успело пройти 3 дня, мне уже звонит курьер забирай говорит. Бонус порадовал, спасибо! Компенсировали за свой счет! Вот это я понимаю МАГАЗИН ДОБРЫХ ЛЮДЕЙ! Так что советую! Качество +5 , спасибо что есть ещё добро в этом злом мире! купить Кокаин, Мефедрон, Экстази
trendloversplace – Perfect for trend enthusiasts, always something fresh and exciting to see.
Детоксикация от алкоголя в Красноярске: профессиональная помощь Алкогольная зависимость — это серьезная проблема, требующая квалифицированной помощи. В Красноярске предлагается широкий спектр услуг по детоксикации и лечению зависимости. Медицинская детоксикация, предлагаемая наркологами в Красноярске, помогает безопасно устранить токсины из организма. помощь нарколога Красноярск Клиники в Красноярске предлагают реабилитационные программы с поддержкой наркологов, психологической помощью во время детоксикации и консультациями по вопросам алкоголизма. Необходимо понимать, что успешное восстановление после алкоголизма требует комплексного подхода, включая лечение зависимости от алкоголя. Если вам нужна профессиональная помощь при алкоголизме, в Красноярске есть клиники, предоставляющие эффективное лечение и поддержку. Важно не затягивать с обращением за помощью; сделайте первый шаг к здоровой жизни уже сегодня.
всем привет купить Мефедрон, Бошки, Марихуану
purefashionchoice – Clean, stylish fashion selections that are both modern and practical.
Style choice corner – Loved how easy it was to navigate categories with stylish items.
По АМ могу сказать,что концентрировать выше 1 к 15 не вижу смысла.Оно не торкает дальше своего известного предела,после 1 к 15 дальше пойдёт уже переводняк.Тут как с процами-дороже 200 баксов покупать-перевод бабла,прироста производительности не заметишь почти. https://digitechpedia.com У меня разок было, что трек перестал на два дня отслеживатся, но нечего доставили все пучком.
globalvaluecorner – Amazing value and variety of products from around the world.
после нового года два раза заказывал первый и второй раз были геморои по срокам отправок но все дошло третий раз конечно тоже закажу но ТС должен будет мамой поклястся что отправит вовремя но если по правде говоря то курьерки тоже мозг ебут не всегда вина ТС https://drr-law.org Сроки не говорил, иначе не было бы этого поста. Исправляй, не мой косяк бро, и не отмазка, что вас много. Не предупредил ты, о своей очереди, в чем моя вина? Не создавай очередь, какие проблемы? но если создаешь, будь добр предупреди, делов то :hello:
электронный карниз для штор http://elektrokarniz2.ru/ .
прокарниз https://elektrokarniz1.ru .
врач психиатр на дом
psychiatr-moskva012.ru
консультация психиатра круглосуточно
everydayessentials – Convenient site to find daily essentials quickly and easily.
привет что случилось вы работаете не могу второй день в личку отписаться ,сколько заказывал всё было супер ,как к тебе попасть теперь ,что делать ,отпишитесь … https://industrial-revolution.info Про 80 не знаю. Но то что там принимают сомнительных, дак это точно. Вот люди которые туда приходят и ушатаные в хламотень, все трясутся. И оглядываются, как будто от смерти скрываются конечно их принимают… А что про тех кто соблюдаем все меры, тот спокоен. И сдержан. Но все равно. В спср принимают однозначно, сам свидетель в 2006 году. когда за дропом следили, перепугались что за нашим пришли… Но все обошлось.
Better Options Store – Products looked excellent and exploring sections was hassle-free.
findyournextgoal.click – Really helpful tips, encourages consistent progress toward personal growth every single day.
Капельница от алкогольной зависимости в владимире – это необходимая медицинская помощь при алкогольной зависимости, которая помогает очищению организма. Вызов нарколога на домой предоставляет экстренную помощь при запое в комфортной обстановке. Состав капельницы содержат вещества, способствующие восстановлению организма: физраствор, минералы и препараты для капельницы. Действие капельницы направлено на устранение симптомов обстиненции и улучшение состояния пациента. Лечение алкоголизма требует всеобъемлющего подхода, включая последующее восстановление после запоя. Цены на услугу нарколога различаются, но обращение к специалиста является важной для успешного лечения.
следить не могли однозначно https://verbandsabzeichen.info А менеджер не ответственный а облом. Я бы пошел навстречу клиенту, получил бы от него этот стольник себе на мобилку и доплатил бы на Альфу его сам, раз у потенциального клиента проблемы с переводами. А он обломался.
globaltrendstore.click – Found several unique items I couldn’t locate anywhere else locally online.
dailydealsplace – Always updated with great bargains, love checking in daily.
Хотелось бы надеется))) https://digitechpedia.com Магаз не подведет
Fashion Outlet Hub – Products looked great and navigating categories was simple.
learncreategrow – Inspiring content that encourages learning, creating, and personal growth.
Với giao diện mượt mà và ưu đãi hấp dẫn, MM88 là lựa chọn lý tưởng cho các tín đồ giải trí trực tuyến.
вывод из запоя
vivod-iz-zapoya-minsk013.ru
экстренный вывод из запоя минск
Цены сладкие. Качество отменное. https://rentalscroacia.info составите конкуренцию известно кому :monetka:
электрокарниз купить электрокарниз купить .
1)Кто курит каждый день : от 2 часов до 3-4 часов https://bwin99.info Принял, участие в совместке номер 3, кинг как и подобает этому магазу, все сделал со скоростью звука, прошло 5 дней после оплаты и у меня в руках лежат 50 тонн этой велеколепной вкусняшки, СПАСИБО. Я просто не понимаю как люди заказывают у других когда есть chemical
Под ключ работаем – где можно сделать официальный перевод документов. Бюро переводов в Самаре. Работаем 10 лет. Документы, нотариальное заверение, срочно. Гарантия конфиденциальности.
growtogetherstrong – Positive and motivating, perfect for teamwork and community growth.
Да все так и есть! Присоединюсь к словам написанным выше! Очень ждём хороший и мощный продукт! купить Кокаин, Мефедрон, Экстази надо прятать по сложнее
findyourstyle.shop – Product descriptions are clear, making choosing outfits much easier and enjoyable today.
Учебные документы оформим – заверенный перевод документов на немецкий. Самарское бюро переводов. Документы, нотариус, срочно! Любые языки. Качество и точность. Доступные цены.
learnwithoutlimits.shop – Inspiring content available, encourages continuous learning and personal growth every day.
DreamTrailHub – Great content featured, makes taking action toward goals simple and enjoyable.
buildyourownfuture – Great motivational site, helps focus on goals and planning ahead.
Ты себя хорошо чувствуешь ? Ты в какую аську пишешь ? купить Мефедрон, Бошки, Марихуану Причем тут вообще он к нашему магазину ?
Daily Idea Spot – Fresh suggestions to help you create, innovate, and experiment every day.
Капельница для пожилых от запоя в владимире — это важное средство медицинской помощи. Нарколог на дом круглосуточно предоставляет услуги по детоксикации организма, что крайне важно для пожилых пациентов. Симптомы запоя, такие как тревожность и слабость, нуждаются в быстром вмешательстве. Лечение алкоголизма включает использование капельниц, которые способствуют восстановлению водно-электролитного баланса. Однако необходимо учитывать риски, связанные с капельницами: риск аллергических реакций и осложнений из-за неправильного введения. Поэтому безопасность лечения должна быть на первом месте. Медицинская помощь на дому позволяет избежать стресса при транспортировке больного. Уход за пожилыми людьми требует особого внимания, и круглосуточные услуги нарколога гарантируют необходимую поддержку. Рекомендуется придерживаться рекомендаций врачей для эффективного восстановления после запоя.
GlamNestOnline – Fashionable selections available, navigating the site was smooth and enjoyable.
Пацаны из ТЛТ не берите через этот магаз ФСКН кроет курьерку в нашем городе!!! купить онлайн мефедрон, экстази, бошки Ты то откуда знаешь)))только сегодня зарегался .коржик )))
платная психиатрическая клиника
psikhiatr-moskva010.ru
психиатрическая медицинская помощь
creativegiftoutlet – Amazing gift ideas, really unique and thoughtful selections available here.
экстренный вывод из запоя
tula-narkolog010.ru
лечение запоя тула
Ну это ясно))) спасибо за ответывнесли ясность! https://rentalscroacia.info Как магазиН?
ValueVisionShop – Found top deals, exploring items was smooth and fun.
shopforvalue – Affordable products without compromising quality, makes shopping super satisfying.
брат, у меня ощущение что я с тобой работал, но название магаза было немного другим, тоже в доверенной ветке был))) почерк тот же, и порядочность. я прав или ошибаюсь?)) https://digitechpedia.com качество очень хорошее не подведёт даже не сомневайся
FindsSpotOnline – Wide selection of amazing products, exploring the site felt smooth and fast.
growbeyondlimits – Encouraging platform that inspires personal growth and pushing boundaries every day.
народ скажите концетрацию 250 го в этом магазе https://myscandi.ru в курске у стаффсторе лутше не брать за кладом надо ехать с граблями и лопатой сугробы копать иначе никак
Капельница от запоя – это эффективное средство при интоксикации алкоголем. Нарколог на дом круглосуточно может оказать экстренную помощь‚ содействуя в процессе дезинтоксикации и восстановления после запоя. Проявления алкоголизма‚ такие как тошнота‚ головная боль и слабость‚ требуют незамедлительных действий. Терапия при запое включает инфузии‚ которые помогают бороться с абстиненцией и детоксифицировать организм из организма. Обращение к наркологу важна для установления последующей терапии: лечение в стационаре или амбулаторная помощь. Специализированная наркологическая клиника предлагает квалифицированную поддержку‚ чтобы избежать повторных случаев и сохранить здоровье пациента.
TopBargainSpot – Excellent deals showcased, exploring products felt smooth and simple.
экстренный вывод из запоя тула
tula-narkolog011.ru
лечение запоя тула
dreamfashionfinds – Stylish and trendy fashion finds that make everyday shopping fun.
ВСЕМ МИР А ТСУ РЕСПЕКТ ))) https://jon-wick-lord.ru кролики ставят В\В, фашку от этого магазина по 0.07-0.15 нравится, только сушит сильно
анонимная консультация психиатра
psikhiatr-moskva011.ru
нужна консультация психиатра
HomeEdgeHub – Fantastic products highlighted, exploring the store felt effortless today.
ааап магазину https://mynyc.ru КАК ОБЕЩЯЛ ОПЕРАТОР ТАК ВСЕ И СДЕЛАЛ ОДИН В ОДИН !!!!
smartbuyplace – Excellent place to find smart deals and quality products efficiently.
DriveAndFocusHub – Encouraging content available, perfect for keeping energy and motivation high.
качество очень хорошее не подведёт даже не сомневайся https://artpero-store.ru Надеюсь что ошибаюсь:hello:
купить права
inspireyourjourney.shop – Enjoying the encouraging posts that help strengthen daily habits naturally.
Что то много новичков устраивают здесь флуд.А магаз на самом деле хорош.Помню его еще когда занимался курьерскими доставками,коспирация и качество товара было на высшем уровне. купить Кокаин, Мефедрон, Экстази всем курильщикам привет. магаз ровный,раза 4 заказывал,все проходило нормально,связь с тс в аське тоже норм,можно обговорить любой вопрос. за качество, в61 больше всего понравился. заказывал эйфоретик,так и не понял его,товарищи тоже не поняли эфекта,хотя употребляли по многу.
findyourstrength.shop – Inspirational content makes it easier to stay committed to self-improvement.
FashionPulse – Sleek products and smooth navigation made exploring the store enjoyable.
говорю что все качественно быстро и купить скорость, кокаин, мефедрон, гашиш ТС подтвердив оплату, сказал ожидать. В оговоренные сроки адрес был получен в ЛС.
Вызов капельницы от запоя – это важная медицинская помощь для людей, страдающих от алкоголизма. Процедура капельного введения жидкости помогает быстро восстановить водно-электролитный баланс и уменьшить симптомы похмелья. Домашнее лечение запоя требует квалифицированной помощи, и именно здесь на выручку приходят услуги специалиста по лечению зависимостей; При алкогольной абстиненции капельница от алкоголя не только снимает физические симптомы, но и способствует детоксикации организма. Клиника для лечения зависимостей предлагают терапию для людей, страдающих от алкоголизма, которая предусматривает восстановление здоровья после запоя. Если вам или вашим близким нужна помощь, не сомневайтесь обращаться за медицинской помощью в случае запойного состояния на сайте vivod-iz-zapoya-vladimir025.ru. Учтите, что борьба с алкоголизмом – это шаг к здоровой жизни.
TrendNestGlobal – Fashionable items highlighted, browsing categories was quick and easy.
вывод из запоя круглосуточно тула
tula-narkolog012.ru
вывод из запоя круглосуточно тула
Ну, красавы. Вечером оплатил на следующий день отправили https://prudboy34.ru Магазин высшего уровня своей работы.
частная психиатрическая клиника
psikhiatr-moskva012.ru
консультация психиатра
FashionSphereHub – Trendy fashion items showcased, browsing through styles was effortless.
Приходите еще, всегда рады купить онлайн мефедрон, экстази, бошки хотелось бы услышать какоето обьяснение?????
Purposeful Steps Daily – Practical advice to move forward with focus and clarity every day.
unique gifts corner – Wide variety of products, navigating the site felt easy and fun.
с почтой лучше не связываться купить Мефедрон, Бошки, Марихуану Удачных продаж и с наступающим НОВЫМ ГОДОМ….
Первый раз брал у этого магазина,сразу же что то не то,если всё будет Ок,буду брать дальше,в принцыпе со всеми бывает( купить Мефедрон, Бошки, Марихуану щас заказал по 5г RCS-4 и URB754 по скайпу объяснили как оплатить, пока всё коректно жду посылки там отпишу..
findpurposeandpeace.click – Inspirational posts here guide users toward balance and meaningful living daily.
вывод из запоя круглосуточно челябинск
vivod-iz-zapoya-chelyabinsk013.ru
вывод из запоя челябинск
Реабилитация после зависимости от алкоголя в владимире – важный этап на пути к новой жизни. Нарколог на дом клиника предоставляет качественное лечение от алкоголизма с персонализированными подходами‚ включая очистку организма и психологическую помощь. Консультация нарколога способствует выявить методы лечения‚ такие как групповая терапия и социальная адаптация. Семейная поддержка также играет ключевую роль. Реабилитационный центр предлагает конфиденциальную помощь и меры по предотвращению рецидивов‚ что способствует успешному восстановлению после зависимости от алкоголя.
happyshoppingcorner.click – Products look amazing, browsing categories here is easy and very convenient.
gift ideas hub – Fun selection of unique gifts, browsing products was smooth and enjoyable today.
Ментам зачастую пофиг,легал-нелегал.Был бы человек хороший,статья найдётся.СПСР тоже чёт не нравится.Но и на Мажор экспрессе случаи принималова были,так что х.з….Увидел на сайте “ждём…”.О.флюрокока и rti 111!Очень ждём!АМТ тож вкусняшка,но тут обьебосам не завидую.Примут по полграмма и айда 20 часов как кот в стиральной машине купить Мефедрон, Бошки, Марихуану Почему ушли из РБ?
но я смотрю все на о6ломах тут такие ждут, а тут на те6е всё ровно https://pashinskaya-ksusha.ru Привет и Мира! Магазин отличный. Все легально, быстро и без заморочек. Не то что остальные некоторые…
transformative actions portal – Provides motivational ideas to bring meaningful improvements.
центр реабилитация алкоголиков в Астане
reabilitaciya-astana010.ru
центр реабилитации зависимых в Астане
И еще сушняки ужасные. Сейчас вот утром проснулся, и до сих пор https://stroi-sam1.ru Магазин ровнее не куда!!! Ребята отработали на славу, все четко и оперативно. Спасибо огромное, буду сотрудничать и дальше)
экстренный вывод из запоя челябинск
vivod-iz-zapoya-chelyabinsk014.ru
лечение запоя
fashion discovery portal – Curated fashion trends made browsing enjoyable and straightforward.
У Данного Магазина я так понимаю Принцип не отвечать в Аське?!=) https://dou119-ekb.ru Меня на шалфее устраивает:)вываривать ничего не надо
Восстановление после алкогольного запоя в городе владимире: путь к исцелению Реабилитация после запоя состоит из психотерапии и поддержки близких, что крайне важно в кризисной ситуации. Процесс восстановления могут варьироваться, но все они направлены на преодолении алкогольной зависимостью и обеспечении долгосрочных результатов. Сообщество поддержки становится важным элементом процесса, помогая справляться с трудностями. Необходимо помнить, что путь к выздоровлению труден, но реален. помощь нарколога владимир
всем привет.супер магаз))) позже отзыв отпишу. )))) https://altuning.ru все это только на доверии, белый кристаллический так же может быть 4фа….
bright vision portal – Inspires regular progress through practical daily planning tips.
Мне пока ещё не пришло, но ты уже напугал….:orientation: кто знает где весы купить можно чтоб граммы вешать https://avicenna-s.ru Привет всем Тсу движек
successplanner.shop – Encouraging guidance for taking initiative and achieving results effectively.
экстренный вывод из запоя челябинск
vivod-iz-zapoya-chelyabinsk015.ru
вывод из запоя
центр реабилитация алкоголиков в Астане
reabilitaciya-astana011.ru
отправить на лечение наркомана
Это точно!) главное быть в этом уверенным. Да и ровненький магазин однако купить онлайн мефедрон, экстази, бошки Общение оператора 10/10-всегда все грамотно и вежливо объяснит. Таким оператор и должен быть!
странный вопрос, у вас в ветке интернируется, значит у кого он решил взять ? :rolf: https://gamardzhoba-dostavka.ru Давай номер заказа, не обоснованные заявления, в личку пришло сообщения что ты разводила….
smartbuyzone.click – Great deals available, browsing products here was simple and enjoyable today.
ПРОКАПАТЬ ОТ АЛКОГОЛЯ: ЗНАЧЕНИЕ ДЕТОКСИКАЦИИ И ПОДДЕРЖКИ Вопрос алкогольной зависимости затрагивает многих людей. Лечение алкоголизма часто стартует с детоксикации, которая включает прокапывание. Этот процесс способствует вывести токсины из организма и облегчить абстинентный синдром.Капельницы от алкоголя включают препараты для детоксикации, которые оздоровлению организма. Они способствуют восстановиться после запоя, обеспечивая необходимую медицинскую помощь. Важно помнить, что поддержка зависимых в этот период имеет большое значение.После детоксикации начинается реабилитация, где психотерапия при алкоголизме занимает ключевую роль. Специалисты помогают разобраться в причинах зависимости и предоставляют советы по борьбе с зависимостями.На сайте vivod-iz-zapoya-vladimir028.ru можно найти информацию о том, как правильно пройти лечение и получить поддержку. Здоровье, это важный шаг к новой жизни без алкоголя.
modernfashionworld.click – Great collection of outfits, exploring categories was simple and enjoyable today.
buyquicklyzone.click – Well-arranged product selection, navigation is simple and smooth.
https://aritual.by/funeral.html
рулонные шторы с электроприводом цена рулонные шторы с электроприводом цена .
Крутой магаз https://kt-6023.ru Хороший магазин согласна!
Fashion & Style Daily – Daily recommendations for looking stylish and feeling confident.
спасибо стараемся купить скорость, кокаин, мефедрон, гашиш Спасибо Магазину)вы лучшие))))))))!!!!!!!!!!!!!!!!!!!!! :monetka: Качество на 100%
perfect gift shop – Lovely creative gifts, exploring products felt very easy and fun.
Добрый день, треки работать начинают с некоторым опозданием, берите их в заказах на сайте, проверяйте, все должны работать пятничные. По крайней, мере в скайп/асю пишите, что заработали и у меня тоже мониторинг есть купить кокаин, меф, бошки через телеграмм Вы то нет:) А банки работают:)
limitlesslearninghub.click – Useful resources here help expand knowledge and grow personally every day.
freshtrendcorner.click – Stylish choices for everyone, browsing new arrivals was simple and pleasant.
Подскажите пожалуйста товары указаные в прайсе все в наличии или нет? купить кокаин, меф, бошки через телеграмм спасибо , стараемся для людей
вывод из запоя цена
vivod-iz-zapoya-cherepovec016.ru
экстренный вывод из запоя
дизайн интерьера онлайн студия дизайна интерьеров отзывы
лечение алкозависимости
reabilitaciya-astana012.ru
реабилитация от алкоголя в Астане
unique gift ideas hub – Smooth navigation and creative selections made shopping enjoyable.
всем хай купить скорость, кокаин, мефедрон, гашиш Заказали 2c-i и 2c-p. Как придет в магазине появятся позиции. может и еще что привезут из заказанного курительного.
brightstyleoutlet.click – Great collection of fashionable items, site makes exploring simple and fun.
worldtrendshop.click – Trendy pieces from around the globe, shopping experience was seamless.
exploreopportunities.click – Great guidance available, encourages users to expand their horizons and grow steadily.
дизайн интерьера квартиры https://dizayna-interera-spb.ru
freshpickoutlet.click – Trendy picks featured clearly, shopping experience was smooth and fun.
Прокапаться после запоя на дому – это решение, который способен облегчить симптомы похмелья и повысить процесс детоксикации. Лечение запоя предполагает как медицинскую помощь на дому, так и народные средства от похмелья. Стоит отметить симптомы похмелья: боль в голове, тошнота, усталость. Для реабилитации после алкоголя часто используются препараты от запоя, которые помогут уменьшению дискомфорта. vivod-iz-zapoya-vladimir029.ru Алкогольная зависимость психологическая помощь при запое также играет важной ролью процесса. Поддержка родственников при алкоголизме может существенно ускорить реабилитацию после пьянства и предотвратить повторные алкогольные кризисы. Советы по лечению запоя могут включать в себя соблюдение режима питания, достаточное потребление жидкости и использование природных методов. Профилактика запоев должна быть в приоритете, чтобы избежать рецидивов. Обратитесь за профессиональной помощью, если состояние не улучшается.
По АМ могу сказать,что концентрировать выше 1 к 15 не вижу смысла.Оно не торкает дальше своего известного предела,после 1 к 15 дальше пойдёт уже переводняк.Тут как с процами-дороже 200 баксов покупать-перевод бабла,прироста производительности не заметишь почти. купить онлайн мефедрон, экстази, бошки У нас у отправки случился форс-мажор. Только на этой неделе начинают отправлять. Извиняюсь от лица магазина за задержку.
https://letterboxd.com/1xbetfreebet43/
top choice collection – Features a neat assortment of products, making the experience effortless.
горизонтальные жалюзи с электроприводом горизонтальные жалюзи с электроприводом .
управление шторами с телефона управление шторами с телефона .
freshcornerhub.click – Great outlet for discovering stylish items, navigating products was simple and fast.
actiondrivenhub.click – Inspiring resources guide taking steps that lead to tangible success outcomes.
А я так понимаю, что у данного магазина просто не мало оптовых покупателей, и им уделяется больше внимания. https://metalllist.ru Только вот странно что в трипе написано что пак был с 1гр ск (а твой заказ это покупка) а продажу у магазина от 5гр
Pretty component of content. I simply stumbled upon your website and in accession capital to assert that I get actually enjoyed account your weblog posts. Any way I will be subscribing for your feeds or even I achievement you access constantly rapidly.
Daily Motivation Hub – A go-to spot for motivation and personal growth.
вывод из запоя
vivod-iz-zapoya-cherepovec017.ru
вывод из запоя круглосуточно череповец
freshchoicehub.click – Attractive selection of fresh products, shopping felt effortless and quick.
product showcase hub – Nice collection of items, navigating and exploring felt easy and fun.
Добрый вечер, менеджер отписал, что СК будет в выходные! Так это? Интересует Новосибирск опт. https://bular-anapa.ru 128 страниц положительных отзывов , и вдруг “мутный магаз” . Уважаемый – флудить в курилке можно.
trendcollectionhub.click – Clear layout and trendy items make shopping enjoyable and fast.
Процветания вашему магазину!!! https://stroi-sam1.ru на мыло отвечаем только по существу, много не по делу пишут, ася или скайп быстрей
freshfindshubcorner.click – Outlet full of trendy products, browsing choices felt easy and pleasant.
clarity and focus portal – Offers tips to define, plan, and act on your goals effectively.
месяц назад купить Мефедрон, Бошки, Марихуану отличный сервис!
freshstylecorner.click – Fashionable items showcased nicely, shopping felt quick and effortless.
purefashioncollection.click – Clean and stylish fashion collection, perfect for refreshing everyday wardrobe choices.
лечение запоя
vivod-iz-zapoya-cherepovec018.ru
вывод из запоя цена
kuwin sở hữu kho game đa dạng từ slot đến trò chơi bài đổi thưởng, mang đến cho bạn những giây phút giải trí tuyệt vời.
гаси кидалу по полной -25 маловато я добавлю купить Кокаин, Мефедрон, Экстази Бро ответь в аське!
growthcoachclick.click – Practical tips that make reaching your potential simple and achievable today.
freshfindshubcorner.click – Outlet full of trendy products, browsing choices felt easy and pleasant.
Магазин работает на 5+++++, я уже раз 5 беру у данного сейлера все ровно все катит, качество на высоте! купить онлайн мефедрон, экстази, бошки Магазин как уже и было сказано – на 5+
cheerfulhomeclick.click – Inspiring home décor, navigating the site felt smooth and effortless.
curated picks hub – Browsing through products was straightforward, easy, and fun today.
freshtrendshub.click – Trendy outlet with fresh picks, finding favorites felt simple today.
онлайн казино vavada — это актуальное зеркало для доступа к популярному онлайн-казино.
Она предлагает широкий выбор слотов, рулетки и карточных игр.
Сайт отличается удобным интерфейсом и быстрой работой. Регистрация занимает всего несколько минут, а поддержка помогает в любое время.
#### Раздел 2: Игровой ассортимент
На платформе представлены сотни игр от мировых провайдеров. Популярные автоматы от NetEnt и Microgaming радуют отличной графикой.
Особого внимания заслуживают джекпоты и турниры. Крупные выигрыши разыгрываются в прогрессивных слотах.
#### Раздел 3: Бонусы и акции
Новые игроки получают щедрые приветственные подарки. Бонусы начисляются как за регистрацию, так и за активность.
Система лояльности поощряет постоянных клиентов. Чем чаще вы играете, тем выше становятся бонусы.
#### Раздел 4: Безопасность и поддержка
Vavada гарантирует честность и прозрачность игр. Вывод средств происходит быстро и без скрытых комиссий.
Служба поддержки работает в режиме 24/7. Консультанты отвечают моментально в онлайн-чате.
### Спин-шаблон
#### Раздел 1: Введение в мир Vavada
1. Vavada — известный ресурс для любителей азартных развлечений.
2. Она предлагает широкий выбор слотов, рулетки и карточных игр.
3. Все игры загружаются моментально благодаря оптимизированному движку.
4. Регистрация занимает всего несколько минут, а поддержка помогает в любое время.
#### Раздел 2: Игровой ассортимент
1. В каталоге можно найти сотни развлечений на любой вкус.
2. Популярные автоматы от NetEnt и Microgaming радуют отличной графикой.
3. Прогрессивные джекпоты делают игру еще более интересной.
4. Специальные акции увеличивают шансы на победу.
#### Раздел 3: Бонусы и акции
1. Регистрация открывает доступ к выгодным бонусам.
2. Первый депозит может быть увеличен на 100% или более.
3. VIP-игроки получают персональные предложения.
4. Чем чаще вы играете, тем выше становятся бонусы.
#### Раздел 4: Безопасность и поддержка
1. Все игры работают на честных алгоритмах.
2. Все автоматы проходят проверку на случайность генерации чисел.
3. Любые вопросы решаются оперативно и профессионально.
4. Консультанты отвечают моментально в онлайн-чате.
Брал не давно в этом магазине закладкой в МСК, что сказать, все прошло замечательно. Клад был поднят, место довольно спокойное и тихое, Время исполнения заказа с момента оплаты от 1 до 2,5 часов, что по сути не так уж и много. Выражаю огромное спасибо оператору в аське, не оставлял меня ни на минуту, всегда отвечал. https://svp-opt.ru а трудно изучить предварительно информацию о веществе, а потом покупать ? вот к примеру у меня в подписи инфа.
freshtrendcorner.click – Stylish choices for everyone, browsing new arrivals was simple and pleasant.
СПАСИБИЩЕ ОГРОМНОЕ ЗА СЕРВИС https://agit-prom.ru Всем доброго времени суток. Вопрос такой – Ко скольки лучше делать МН и как быстро растет толер???
dreamachievegrow.click – Encouraging notes push for dreaming, believing, and making progress daily.
latest trends hub – Great selection of trending items, browsing was smooth and fast.
лечение запоя иркутск
vivod-iz-zapoya-irkutsk013.ru
вывод из запоя круглосуточно иркутск
shopandshine.click – This site feels friendly, easy, and perfect for quick browsing anytime.
inspiregrowthdaily.click – Found useful tips here, helpful resource for staying focused on growth goals.
Расположите по мощности https://vizart-studio.ru Знакомые делали, получалось что-то похожее на старый Juh.
freshcornerhub.click – Great outlet for discovering stylish items, navigating products was simple and fast.
share and learn today – Useful resources for discovering new topics and sharing knowledge with others.
лучший магаз берите все!!!!, все порешали вина не магазина. просто красавец!!! https://stroi-sam1.ru привет )
freshfindshubcorner.click – Outlet full of trendy products, browsing choices felt easy and pleasant.
Если хотите подешевле – вам сюда. Если же располагаете финансами – штудируйте ветки доверенных магазинов, есть селлеры куда более ответственные и стоящие. Лично я не планирую дальше сотрудничать с этим магазином. Спасибо за внимание. купить скорость, кокаин, мефедрон, гашиш бобик здох ….
stylehubonline.click – Stylish products neatly displayed, shopping experience was smooth overall.
yourcreativeplace – Supports idea-building and fuels imagination with simple inspiration.
вывод из запоя круглосуточно
vivod-iz-zapoya-irkutsk014.ru
лечение запоя иркутск
Один из топовых продавцов на всем РЦ:) https://talsosh-tarum05.ru Ну просто реально непонятно. Народ заказывает, все довольны, я, мои знакомые тут берут стафф – всё на высшем уровне. И твой отзыв по поводу некачественного товара – первый… Да и чтоб сразу и ЖТЕ палёный, и ФА непрущая… Хз, разбирайтесь
Đến với J88, bạn sẽ được trải nghiệm dịch vụ cá cược chuyên nghiệp cùng hàng ngàn sự kiện khuyến mãi độc quyền.
freshfashioncorner.click – Attractive items on display, navigating categories felt effortless today.
Есть люди в вк, которые представляются под маркой вашего магазина и кидают людей, уже не одного так кинули, так что будьте внимательны и уточняйте у реальных представителей магазина, так оно или нет. купить онлайн мефедрон, экстази, бошки Брал опт, все четко прошло! Качество на высоте! ТС ответьте в ЛС пожалуйста
fresh products finder – Great collection presented, navigating and finding items was simple.
мелбет онлайн ставки на спорт http://v-bux.ru/ .
Online Deals Center – Smooth browsing overall with a nice mix of items worth checking.
creativechoicecorner.shop – Everything loads well, browsing through creative items feels streamlined and natural.
modernhomechoice.shop – Great home picks here, items look stylish and very well presented today.
помогите обьясните как написать сапорту https://sherifpizza.ru Всем по привету!
freshfindshub.click – Wide variety of stylish products, discovering new favorites was simple and fun.
минет нижневартовск
classy outfit corner – Fashionable items featured, browsing the site was effortless and smooth.
Скрины с радикала не грузятся. Увы сейчас доказать что-либо сложно, видимо магазин не первый раз кидает уже по отточеной цепочке. https://metalllist.ru Дом рядом с адресом говоришь, отдаешь залог, когда приедешь в адрес (в разных такси по-разному, могут и не попросить), и идешб себе за кладом 🙂
вывод из запоя круглосуточно
vivod-iz-zapoya-irkutsk015.ru
вывод из запоя иркутск
freshpickoutlet.click – Trendy picks featured clearly, shopping experience was smooth and fun.
Online Deals Center – Smooth browsing overall with a nice mix of items worth checking.
Кидал 4340, на Альфу улетело 4254… если быть точным… Чек есть. купить Кокаин, Мефедрон, Экстази Все вопросы к представителю.
stylehubmarket.shop – Modern fashion choices easy to explore, navigation felt quick and simple.
freshfavoriteshub.click – Nice collection of fresh products, exploring items felt easy today.
А менеджер не ответственный а облом. Я бы пошел навстречу клиенту, получил бы от него этот стольник себе на мобилку и доплатил бы на Альфу его сам, раз у потенциального клиента проблемы с переводами. А он обломался. купить скорость, кокаин, мефедрон, гашиш ОПЕРАТОР ОКАЗАЛСЯ ОЧЕНЬ ОТЗЫВЧИВЫЙ! расскажет все что касается его товара! говорит очень вежливо, не чего лишнего! даже когда я засыпал его кучей всяких вопросов он меня не игнорил а старался ответить на все что я его спрашивал!
Trend Picks Corner – Loved the stylish items, and checking different styles was quick and simple.
freshpickshub.click – Great outlet for stylish finds, exploring products was enjoyable and smooth.
idea discovery portal – Discover interesting concepts and opportunities smoothly today.
Всем привет, долго не писал, ну это меня «задержала» посылка jv-61. Все пришло, все получил причем довольно быстро все ехало:good: купить скорость, кокаин, мефедрон, гашиш списались с продавцом,пообщались,договорились.я оплатил заказ и начались долгие ожидания моей заветной посылки.
вывод из запоя
vivod-iz-zapoya-kaluga016.ru
вывод из запоя круглосуточно
Trend Shopping Hub – Curated items and modern designs to simplify your shopping journey.
freshfashioncorner.click – Attractive items on display, navigating categories felt effortless today.
ну да, как скажут так и делают я уже говорил 11 из 10) купить онлайн мефедрон, экстази, бошки Причем здесь стаффстор ко мне ?
Fresh Deals Hub – Found many appealing products, and navigation across sections was seamless.
Такая тут вкусная цена была недавно на фтор.И продукт офигенский.А теперь цену подняли до всеобщего уровня.И я не вижу уже причин заказать именно здесь а не где-то ещё.Так-то с отправкой всё ровно будет,но цена… https://zhivouste.ru расширяться собираетесь?
freshfindsoutlet.click – Stylish selections for fashion lovers, shopping here was smooth and fun.
Best Trend Outlet – Loved the stylish picks here, and browsing felt smooth overall.
Отличный Магаз, Все четко!!! https://zhivouste.ru привествую мои друзья форумчане , не
dreamgrowthhub – Uplifting ideas here encourage believing in yourself and moving forward.
вывод из запоя круглосуточно калуга
vivod-iz-zapoya-kaluga017.ru
экстренный вывод из запоя
анологичная ситуация! продаван ты на примете, раз твоих клиентов начали принимать… купить кокаин, меф, бошки через телеграмм Дошло довольно быстро
BestBuyCorner Landing – The page behaved well, and exploring different offers was smooth.
Fresh Value Store – Browsing felt smooth, with nicely arranged items and clear pricing.
globalfindshub.shop – Shopping felt smooth, the layout is clean and super user-friendly today.
Две дорожки для Сережки, https://texnometall.ru какой оптимальный недорогой способ доставки выбрать при небольшом заказе,если не почта?посоветуйте…
yourtrendzone.shop – Trendy items displayed cleanly, browsing felt smooth and enjoyable throughout my visit.
Да че тут разбираться,ты видишь смысл?! купить кокаин, меф, бошки через телеграмм Конспирация на уровне
Smart Savings Spot – Good browsing flow, found the deals section especially convenient.
Trendy Fashion Hub – Lots of current fashion pieces, and the layout made finding items simple.
Stylish Choices Hub – Quick access to fashionable items that elevate your everyday look.
тусишка хороша, я как го грешил что нирвановская была какая то тёмная, так вот у чемикала она вообще практически бежевая 😀 качество порадовало, хорошая вещь ) https://igra18plus.ru А с какого дживика еще больше делать можно?
вывод из запоя калуга
vivod-iz-zapoya-kaluga018.ru
лечение запоя
Fresh Deals Directory – Everything was clearly displayed, and exploring felt smooth.
Моя первая покупка на динамите и, внезапно для самой себя, наход. Сняла, как говорится, в касание. С вашим охуенным мефчиком сорвала себе почти год ЗОЖа и ни чуть не жалею. купить онлайн мефедрон, экстази, бошки Написано же везде, что суббота и воскресенье – выходные дни. Надо же менеджеру отдыхать когда-то
New Fashion Finds – Loved the clean arrangement and the wide variety of fresh styles.
Могу предоставить переписку администрации форума. Уже определитесь, что вам нужно чтобы и мне не дергать отправщиков, склад и прочих сотрудников. То хочу, то не хочу, то вышлите 2 посылки, оплачу посфактум, то снова верните деньги. купить кокаин, меф, бошки через телеграмм спс ) вот уже пришло что отправлено в пн ждать трек буду )
Bright Style Collection – Browsing was pleasant with everything presented clearly and neatly.
BestBuyCorner Marketplace – Smooth navigation overall, plenty of categories to check out.
simplefashionoutlet.shop – Simple, stylish fashion finds here make dressing easy and enjoyable today.
bestchoicevalue.shop – Enjoyable shopping experience, everything organized neatly and easy to explore.
ага в осадок выпадает в спирте это верно, но если после выпадания в осадок добавить 646 в спирт и все будет гуд. Кстати 250 также при перегреве выпадает в осадок купить Мефедрон, Бошки, Марихуану а что ты паришься. дождись пока домой принесут. посмотри в глазок что бы курьер один был. впусти его. а перед этим поставь чувака под окном. посыль забираешь, после, без палева выкидываешь в окно чуваку. а потом только выпускаешь курьера из квартиры. а там пусть хоть кто забегает, у тебя ничего нет. главное не нервничай и о плохом не думай. бери в хуй толще будет. а спср это почта россии. а почта россии ни когда нормально не работала.
Đến với J88, bạn sẽ được trải nghiệm dịch vụ cá cược chuyên nghiệp cùng hàng ngàn sự kiện khuyến mãi độc quyền.
Trendy Fashion Spot – Fashionable items displayed clearly, with easy and fast browsing.
снять проститутку нижневартовск
Bright Fashion Deals – A fun place to explore new styles, with pages loading quickly and clearly.
Urban Style Market – Found several attractive pieces quickly with the clean layout.
лечение запоя
vivod-iz-zapoya-krasnodar021.ru
экстренный вывод из запоя
Bright Fashion Hub – Attractive styles everywhere, and browsing through categories felt seamless.
Browse New Items – Very user-friendly layout, making it simple to check out all the latest offerings.
я бы тоже заценил https://scenar-ekb.ru про него что нить писали? точнее вы читали ?
Modern Seasonal Deals Online – Quick browsing and well-arranged items made shopping enjoyable.
Bright Style Market – Really liked how items were organized, making it easy to spot new picks.
Trendy Boutique Hub – Colorful and charming layout, with simple navigation across all sections.
Bright Fashion Corner – Found several stylish gems quickly thanks to the simple layout.
Хороший магаз. качество радует спасибо всей команде Chemical-mix.com https://stroi-sam1.ru ребят , а 4-fa нормальная тема ? это типа живика чтоли ?
Modern Buy Center – Browsed today and the modern layout made finding items very simple.
вывод из запоя круглосуточно
vivod-iz-zapoya-krasnodar022.ru
вывод из запоя краснодар
Оплатил в среду, жду посылочку, посмотрим как что. https://scenar-ekb.ru Давно работаю с чемиком.
Với giao diện mượt mà và ưu đãi hấp dẫn, MM88 là lựa chọn lý tưởng cho các tín đồ giải trí trực tuyến.
Bright Fashion Outlet – Loved the vibrant selection, and navigating through everything felt smooth and simple.
Modern Fashion Finds – Items look newly updated, and navigating around was a smooth experience.
Unique Product Hub – Items displayed neatly and scrolling through them was simple.
Всем добра! Вчера позвонил курьер, сказал, что посылка в городе! Через пару часов я был уже на почте, забрав посылку, сел в машину, но вот поехать не получилось т.к. был задержан сотрудниками МИЛИЦИИ!!!! Четыре часа в отделении и пошёл домой!!! Экспертиза показала, что запрета нет, но сам факт приёмки очень напряг!!! Участились случаи приёмки на данной почте!!!!! Продаванам СПАСИБО и РЕСПЕКТ за чистоту реактивов!!! Покупатели держите ухо востро!!!!!!!!!! Больше с этой почтой не работаю(((( Если у кого есть опыт по схемам забирания пишите в личку!!! купить кокаин, меф, бошки через телеграмм Магазин реально ровный!!! Долго искал и нашел! Бро ты лучший!!!!
Bright Apparel Shop – Clean design and appealing fashion picks made the experience enjoyable.
про тусиай ….. что я могу сказать про тусиай от этого магазина…. пойду лучше трип-реппорт напишу…. такой тусишки ещё не ел) купить Кокаин, Мефедрон, Экстази по поводу треков выяснять буду завтра лично т.k. сегодня выходной в России
FreshStyle Finds – Browsed effortlessly with fast-loading pages and clear design.
Seasonal Selection Spot – Beautifully presented items, and checking out the seasonal picks was simple.
Bright Fashion Hub – Attractive styles everywhere, and browsing through categories felt seamless.
вывод из запоя краснодар
vivod-iz-zapoya-krasnodar023.ru
вывод из запоя круглосуточно
Best Value Finds – Handpicked deals for smart shoppers looking for quality and affordability.
привет запулил на закладку ?? https://altuning.ru отпишеш как все прошло бро
Hub of Latest Trends – Spotted a few neat finds, and the entire site worked efficiently.
Bright Outfit Shop – The overall look was appealing, and navigating the sections felt intuitive.
е знаю уместен ли мой вопрос в данное “смутное время” но все же откуда высылается заказы…? хотя бы из какой части РФ если это РФ…))) https://krovlispb.ru А вот это очень интересно)))ДК есть он или его нет?В розницу пару г возможно надеюсь закзать?
Bright Picks Hub – Fast and easy navigation with a cheerful theme that’s pleasant to explore.
<https://kuklanvt.info/antikrizis/
гы гы..вот такая вот история..мля )) https://rem-coffee.ru конечно была задержка которая заставила по нервничать, но всё прошло на уровне и я получил свою посылочку)))
Bright Fashion Corner – Found several stylish gems quickly thanks to the simple layout.
freshvaluestore.shop – Impressive range of categories, makes discovering deals much easier overall.
happyhomecorner.shop – Perfect spot for discovering fresh home inspiration and decor ideas.
Золотые слова. купить кокаин, меф, бошки через телеграмм Ну так ведь и не делаем не чотка . всё сразу .
экстренный вывод из запоя краснодар
vivod-iz-zapoya-krasnodar024.ru
вывод из запоя краснодар
Global Outfit Store – Wide selection of updated pieces, and the interface made exploring easy.
Всем доброго дня!! Хочу рассказать свой отзыв , о данном чудо магазине!! Заказывал совместку на 50г, оплатил днём, к вечеру все было готово, жаль только я с джабером что то не подружился, он меня выкинул, прям перед получением адреса, НО КЛАДЧИК ТАКОЙ красавчик!!! В итоге я поехал с утра, только приехал, все было на своих местах!!! Спрятано на совесть!!! Думаю ещё пролежало бы дня 3))) ИТОГО: ОПЕРАТОР В ДЖАБЕРЕ САМЫЙ КУЛЬТКРНЫЙ ЧЕЛОВЕК НА СВЕТЕ! 5+ КЛАДЧИК , умница! 5+, близко ко мне , и спрятано как надо!!! P.S. Смело заказываем!! И радуемся как дети!!) https://altuning.ru За АМ 1220 ничего сказать не могу – не пробовал…. Но, после тестирования 694 и 2201 впечатления о линейке АМ у меня сильно подпортились (
Seasonal Finds Hub – Found several appealing items and browsing felt smooth throughout.
shopandsavehub – Great deals today, very easy to navigate the site.
Check fashion items – A few interesting styles were easy to find immediately, layout clean.
Trendy Fashion Spot – Modern style selections made exploring fun, and scrolling was effortless.
ро я тоже паниковал но все решилось нормально мне в курьерке обьяснили что с этой ебливой олимпиадой у многих запарка и сбои в работе как то так…. купить онлайн мефедрон, экстази, бошки классный магазин, была впечатлянна скоростью доставки и качествомтовара)) всем пис
Daily Gift Picks – Found some great little surprises, and the pricing felt comfortable.
Daily Trend Spot – Find the latest trendy products organized for smooth navigation.
Gift Ideas Hub – Pleasant design and clear structure made discovering gifts easy.
Просьба не флудить. И уж тем более не развивать больные фантазии. купить кокаин, меф, бошки через телеграмм через аську связался… дал данные куда сколько отправить, и с киви кошелька оплатил 7700р. на номер который в аське дали
лечение запоя краснодар
vivod-iz-zapoya-krasnodar025.ru
экстренный вывод из запоя краснодар
Corner Style Deals – Plenty of modern styles today, and the whole site worked flawlessly.
Value Picks Online – Loved the clarity of the layout, and browsing value deals felt effortless.
Не смог не скопипастить купить онлайн мефедрон, экстази, бошки а вот на фофу гнать нельзя… она на высоте…
Corner of Global Market – Found interesting items quickly thanks to the organized sections.
dealhunterscorner – Very reasonable deals, I got everything I needed quickly.
Shop crisp fashion styles – A handful of trendy outfits popped up instantly, site well-organized.
Trendy Collection Hub – Several unique items appeared, and the shopping experience felt seamless.
спасибо , стараемся для всех Вас купить кокаин, меф, бошки через телеграмм из тех что есть в наличии у чемикала… ну разве что с 307го, но я его не пробовал, говорят самое норм – 1к15. да и он самый долгий и сильный из всех доступных ЖВШ на данный момент на рынке..
bestbrightshop – Shopping was effortless, pages loaded quickly and selection was good.
Shop Smiles Hub – Browsing feels friendly, with fast-loading pages and organized items.
продавана сегодня в асе вообще ен видел, хз что там у них ( купить Кокаин, Мефедрон, Экстази Обратите внимание, ТС отказывается работать с ГАРАНТОМ! хоть и магазин древний и проверенный! но хочется спать спокойно! АДМИНЫ ОБРАТИТЕ ВНИМАНИЕ, ПОРА КАК ТО ИЗМЕНИТЬ РЕЖИМ РАБОТЫ ГАРАНТА. СДЕЛКИ ПРОВОДИТЬ ОБЯЗАТЕЛЬНО ТОЛЬКО ЧЕРЕЗ ГАРАНТА!
Deal Market Store – A variety of offers came up, all priced attractively for the quality.
Seasonal Offers Spot – Everything loaded rapidly and the items were organized nicely.
Вот мой отзыв по работе данного магазина. https://autoklimat44.ru Может случилось что-то не ладное?
Fashion Finds Online – Lots of appealing styles, displayed in a layout that’s super simple to explore.
Unique Find Hub – A variety of rare products available, and browsing through them was smooth and enjoyable.
HappyBuy Deals – Navigation was smooth and checking different products felt easy.
giftcentralonline – Excellent range of gifts, browsing the website was smooth.
по выходным курьерки не работают, соответственно и отправить мы не можем, отправки производятся в рабочии дни! https://modernm.ru 2.Почему на сайте нет ниодного упоминания о ритейле,в то время,как заказы надо делать через него?
Shop urban fashion – Quickly spotted a handful of stylish pieces, navigation effortless.
trendemporium – Excellent trendy outfits available, checkout went quickly and easily.
Your Picks Hub – Plenty of attractive deals today, and moving through the pages was quick and easy.
парни все ок проверенно ))) https://teka-retail.ru А будет какая нибудь подробная инфа или трип репорты? А лучше пробники платные или бесплатные?
brightbuyspot – Enjoyable shopping experience, wide selection and smooth checkout.
Modern Finds Spot – Plenty of neat choices here, and the site design made exploring enjoyable.
Trendy Finds Daily – Quick page loads and the newest products looked appealing.
реабилитация от запоя в Красноярске
chicken road казино http://kurica2.ru .
курсовая работа купить москва http://www.kupit-kursovuyu-1.ru .
Когда в воде болтаешь, пиздос как немеет язык, сушняк дикий. Горько, но Бля никакого эйфора, ни космоса, ни-че-го…. купить Кокаин, Мефедрон, Экстази магазин работает как надо, у меня тут перевес был не плохой спасибо дружбанчики
Style Corner Online – Plenty of modern choices appeared, and shipping seemed prompt and efficient.
fashionflarehub – Great trendy finds, smooth checkout and fast delivery.
Спасибо за отзыв , а то заказывает много людей а отписываются единицы. купить скорость, кокаин, мефедрон, гашиш глядишь к новому году договоримся, а там и к 2020 посылка придет…
Trend Marketplace Online – Enjoyed the stylish layout and found several items that matched my taste.
happyhomefinds – Useful home items here, website loads fast without any annoying delay.
Bright Shop Center – Clean visuals and rapid loading created a pleasant experience.
freshseasoncollection – Loved browsing here today, everything loads fast and selection feels really good.
Urban style collection – Several attractive finds popped up immediately, navigation effortless.
Daily Value Store – Came across some good finds, and exploring the site was simple and easy.
happycorner – Nice collection of products, delivery seemed smooth and quick.
Написал о заказе в аське в ПТ,мне сказали цену и реквизиты. В СБ оплатил,кинул в аське свои реквизиты.В ПН связался-Сказали,что все отправили,ок. https://leylailyasova.ru Ты вообще нормальный и адекватный ? Ты сначала разберись куда ты писал а потом умничай. У меня адреса без фото и только опт. Судя по твоему нику ты из Екб, я в ЕКБ НЕ РАБОТАЮ И НЕ РАБОТАЛ.
dailyglobalfinds – Great selection of items, pages loaded quickly and shopping was easy.
Trendy Living Picks – Smooth scrolling and clearly displayed items made browsing enjoyable.
a href=”https://modernhomemarket.shop/” />Home Essentials Hub – Lots of practical décor items, and the website loaded quickly without delays.
Ещё раз повторюсь – магазин ОТЛИЧНЕЙШИЙ. https://master-zelenograd.ru Всех благ и ровных клиентов !!!
Поддержка близких играет важной фактором в восстановлении после запоя. Поговорите с ними о своих намерениях и попросите о поддержке. Сообщества поддержки и обращение к специалистов представляют собой полезным ресурсом. Не забывайте о методах предотвращения срывов: советы по жизни без алкоголя и самопомощь при алкоголизме способствуют избежать соблазна вернуться к прежнему. вывод из запоя
курсовая работа на заказ цена http://www.kupit-kursovuyu-6.ru .
спасибо , стараемся для всех Вас https://yarlapta.ru Тут, оказывается, одна шайка- лейка. Мало того, что мое сообщение потерли, еще и нарушение влепили. Сочли провокацией, хотя писал чистую правду. Магазин меня кинул, прислав фигню, которую выбросил.
Trending Fashion Finds – Lots of eye-catching pieces, and confirming the purchase took just seconds.
modernstylehub – Easy to move around the site, pages load quickly and look great.
Trend Collection Corner – Clear layout and quick page loads helped me find items effortlessly.
написать курсовую на заказ http://kupit-kursovuyu-7.ru/ .
сколько стоит сделать курсовую работу на заказ http://www.kupit-kursovuyu-8.ru .
Browse latest fashion – Found a couple of eye-catching picks fast, very user-friendly.
купить курсовую сайт купить курсовую сайт .
hubchoice – Excellent range of items, prices seem fair and checkout was simple.
Чем злиться, выдал бы дудки иль реги https://katyakant.ru синтез пропитает тело ож душа болит
uniquefashioncorner – The site loaded quickly and all product images looked crisp and real.
urbanfashionshop – Website layout is clean, makes finding the right products incredibly simple.
Online Happy Finds – Some nice products popped up, and checking them out was hassle-free.
необычно спрятано было в посыле) купить Мефедрон, Бошки, Марихуану Магазин не чистый на руку. Уже пишет с другого жабера. Народ у кого осталось переписка состарого жабера сверьте ник. И прошу сделать посты что таковое не придуманная мною сказка.
Smart Shopping Picks – Pleasant layout and smooth scrolling made checking items comfortable.
homecornerdeals – Pleasant experience, fast page loads and effortless navigation.
Unique Home Picks – Found the site neat and easy to browse; items appear creative and functional
Капельницы для лечения алкогольной зависимости на дому – это действующий способ помощи алкоголизма, который предоставляет возможность осуществить очистку организма без необходимости стационарного лечения. Помощь сотрудников наркологической службы предлагают инъекции на дому, что способствует улучшению самочувствия пациента и снижению симптомов абстиненции. Капельницы помогают организму быстрее справляться с токсинами, а также способствуют восстановлению организма. Помощь в период отказа от алкоголя важна на разных стадиях, включая процесс реабилитации. Предотвращение осложнений также является важным аспектом в процессе восстановления. Домашняя терапия может состоять не только из капельниц, но и психологическую поддержку, что способствует успешному выходу из запоя и успешному лечению. Обращаясь на vivod-iz-zapoya-krasnoyarsk019.ru, вы получите профессиональную поддержку и поддержку в борьбе с алкоголизмом.
Happy Value Picks – Came across some standout products, and exploring the site was effortless.
я в среду оплатил ещё, тс сразу сказал, что отправка будет на следующей недели во вторник-среду. купить скорость, кокаин, мефедрон, гашиш Про себя могу сказать что толлерантность ОЧЕНЬ выская
giftfinderhub – Amazing selection of gifts, pricing is great and products are excellent.
Explore top fashion picks – Quickly discovered a few appealing items, layout felt clean.
Potential Enhancement Spot – Resources for consistent learning and self-improvement in all areas.
Daily Shopping Place – Took a look today and everything loaded quickly with a clean layout.
trendfinder – Found stylish urban items quickly, navigating the pages was easy.
Парни, здраствуйте, а выписываете на свое имя? просто все хочу попробывать, но блин.. сыкотно (( купить Кокаин, Мефедрон, Экстази Наблюдая за многими сообщениями, мы понимаем что многие на форуме не более чем очень “кипишные люди”, которые любят разводить демагогию.
Style Hub Online – Several interesting designs appeared, and browsing through them was effortless.
Urban Living Collection – The browsing experience was smooth, and the products seem both stylish and functional
Отличный магазин,заказал и уже через 2 дня в своем городе получил посылку курьером(без звонка),офигев от скорости работы.Вес пришел с неплохим бонусом и в хорошей конспирации.Спасибо очень приятно было с вами работать скоро закажу ещё. https://yarlapta.ru и что за вещество
Happy Value Deals Online – Some standout bargains appeared, and everything loaded fast.
globalpickshop – Pages loaded quickly and the site was easy to use.
Капельницы от алкоголя в Красноярске – это важный шаг в борьбе с алкоголизма. Методы детоксикации помогают справиться с симптомами абстиненции и избавиться от пьянства. Лечение в наркологических клиниках включает не только прокапывание‚ но и психологическую помощь‚ что способствует восстановлению после употребления спиртного. vivod-iz-zapoya-krasnoyarsk020.ru Восстановление начинается с детоксикации‚ после которой инициируются реабилитационные программы. Поддержка родственников также играет значимую роль в предотвращении срывов. Анонимные алкоголики и консультация специалиста вполне способны оказать помощь в процессе реабилитации. Не забудьте‚ что борьба с алкоголизмом требует многостороннего подхода.
Получил 5г 203! Оплатил в четверг, отправили в пятницу и уже в понедельник курьер мне передал. 🙂 Вес в поряде, цвет желтоватый. купить кокаин, меф, бошки через телеграмм Общий итог:
ChicFashionStore – Modern collection, very pleased with fast shipping and condition.
brightcornerstore – Great offers and simple checkout, very satisfied with shopping.
Modern Living Outlet – Several attractive finds today, and the quality looks suitable for everyday use.
Top urban picks – Quickly spotted multiple appealing pieces, smooth scrolling experience.
привет бразы всех спрошедшими праздниками получил седня посыль все порадовало и качество и бонус:p:D:D:Dприложеный за ожыдание спосибо магазу купить Мефедрон, Бошки, Марихуану рекомендую этот магазин
Affordable Outlet Finds – Saw some useful deals, and the overall experience was easygoing.
Хочу описать работу магазина.Ну начну клад получил вчера с момента отправки прошло 3ое суток супер,маскировка на 5 балов молодцы спасибо за книгу от души буду духовно развиваться товар бомба основа горит отлично в общем оценка 5 твердая))))) купить кокаин, меф, бошки через телеграмм брал все как всегда на 10 баллов забил
trendhuntermodern – Convenient to browse and shop, found multiple items I liked.
еще раз решил воспользоваться магазом ))) уже 2 года только у них покупаю))) и пока доволен https://systemservice96.ru Из 6 операторов именно оператор этого магазина отвечал быстрее и понятнее всех остальных. Я увидел здесь хорошее,грамотное отношение к клиентам, сразу видно человек знает свою работу.
Home Finds Deals – Several unique items today, and the browsing experience felt very smooth.
Сегодня проблема зависимости от наркотиков и алкоголя приобретает всё большую значимость. Наркологическая медицина предлагает множество подходов для борьбы с этими недугами. Если вы или ваши близкие, рекомендуется обратиться к наркологу на дом в любое время в Красноярске. Вы можете посетить сайт vivod-iz-zapoya-krasnoyarsk021.ru, где все необходимые услуги.Специалист по наркологии на дому предлагает анонимное лечение, что обеспечивает сохранить личную жизнь пациента в тайне. Круглосуточные услуги обеспечивают возможность получения медицинской помощи в любое время. Это особенно важно в критических ситуациях, например, лечение похмелья или острых состояний, связанных с наркоманией. Специалисты проводят детоксикацию организма, что является важным этапом в лечении зависимости. Хорошая клиника на дому предоставляет не только медицинскую помощь, но и консультацию специалиста по вопросам реабилитации и профилактики рецидивов. Токсикология играют важную роль в этом процессе, так как правильная диагностика способствует выбору оптимальных методов лечения. Лечение на дому — это удобный вариант для пациентов, которые не могут посещать стационар. Специалист, оказывающий помощь на дому обеспечит индивидуальный подход и комфортные условия для выздоровления. Обращайтесь за помощью, и вы сможете вернуть себе нормальную жизнь!
smilehubstore – Quality items and very kind, attentive customer support.
ну что,сказать все на высшем уровне!! https://growupeco.ru Братья, у меня вопрос. JV-30 как? Боюсь нарваться на регу с которой крышу сносит. Ответьте пожалуйста.
Explore top fashion picks – Quickly discovered a few appealing items, layout felt clean.
chiccollection – Found stylish items effortlessly, checkout process was fast and simple.
Gift Selection Online – Lots of creative gift choices, and shipping seems quick and trustworthy.
Trend Shopping Hub – Loved the stylish items, website was easy to use, and delivery was quick.
globalfashionworld – Prices are fair, shipping was quick, and quality feels very reliable.
Сделал 4 затяжки с батла, почувствовал секунд через 30 первое прикосновение.))) Затем не много стал теряться в пространстве и во времени, а когда поднялся домой, и открыл дверь (5 мин спустя) меня перекрыло нах, я не мог закрыть дверь и мне всё казалось что кто то держит, у меня начинается паника) я начинаю кричать за дверь: – ты кто такой отпусти, иди отсюда………….. Зову родаков, которых дома нет слава Богу!!!!! вообщем стоял минут 20 у двери) а когда пошёл в комнату мне казалось что кто то за мной ходит!!! https://shamotiki.ru Кому-нибудь отправили сегодня трек?
bestdailyhub – Smooth checkout process, items matched the descriptions exactly as shown online.
Unique Deals Hub – Found some good items today, with fair pricing and solid build quality.
Но в общем и целом доволен очень быстро и качественно! Будем работать и дальше;) купить Кокаин, Мефедрон, Экстази По сути он эйфо, но ничего, кроме расширенных зрачков, учащенного сердцебиения и потливости, я не почувствовал… А колличество принятого было просто смешным: 550 мг. в первый день теста и 750 мг. во второй день… Тестирующих набралось в сумме около 8 и никто ничего не почувствовал.
Global Season Hub Store – Great seasonal products, website ran quickly, and ordering was hassle-free.
лечение запоя
vivod-iz-zapoya-minsk013.ru
вывод из запоя цена
WildShoreOnlineHub – Smooth checkout, excellent quality, and items arrived fast.
trendspotstore – Great fashion choices, shipping was quick and reliable.
с нашими кристаллами восстановятся купить Мефедрон, Бошки, Марихуану Кидалы они или нет-узнаю в течении пары дней,но отказ в закладке-не основание.
trendfinderhub – Very user-friendly, finding and ordering products was easy.
Decor Picks Online – Enjoyed going through the catalog; things were organized and smooth to explore.
Shop urban fashion – Quickly spotted a handful of stylish pieces, navigation effortless.
dailyglam – Great fashion selection, website felt responsive and easy to navigate.
Да уж дживики мощные…только наврятли они у него есть.Ладно будем ждать прояснений.мне тоже не платную не бесплатную не дал пробу.и заказ 50 на 50 отказался сделать. https://angelsgrief.ru У нас у отправки случился форс-мажор. Только на этой неделе начинают отправлять. Извиняюсь от лица магазина за задержку.
Gift Corner Online – Nice range, and everything showed up in tidy, secure packaging.
SunsetStemMarketHub – Quick website navigation, prompt delivery, and neatly packed items.
проститутки нижневартовск номера
чувак сделай 2к15 самый раз для меня)) купить онлайн мефедрон, экстази, бошки чистым не очень понравился:(
Daily Urban Picks – Find modern streetwear essentials for a stylish everyday appearance.
вывод из запоя
tula-narkolog010.ru
вывод из запоя круглосуточно
Read More: https://stroymateryal.forumes.ru/viewtopic.php?id=39#p39
WildCrest Essentials – Easy-to-use website, great variety, and my order came quickly.
добрый день форумчане!) https://rolf-mebel.ru сколько нужно обождать после 2се и 2си, чтобы хорошо 4фа пошла?
trendhubonline – Items were easy to find, website navigation is very smooth.
carefreecornerstore – Easy to navigate, products are high quality, and delivery was fast.
Trend & Gift Collection – Loved the gift options, trendy items throughout, and the website ran well.
Top urban picks – Quickly spotted multiple appealing pieces, smooth scrolling experience.
nightfallmarketplace – Smooth shopping experience, checkout worked perfectly, delivery was fast and very reliable.
urbanedgecollective – Website loads smoothly, great layout, and products seem genuinely high quality here.
topstylecollection – Wide variety of items, shopping process felt natural.
Additional Information: https://npprteamshopz1.bandcamp.com/merch/npprteamshopz1
trendpick – Found fashionable items quickly, navigating the site was smooth.
Магазин не чистый на руку. Уже пишет с другого жабера. Народ у кого осталось переписка состарого жабера сверьте ник. И прошу сделать посты что таковое не придуманная мною сказка. https://shamotiki.ru Аккуратнее с магазином, недовес у них неплохой…
Wild Crest Boutique – Beautiful products, easy navigation, and everything arrived as expected.
IronWoodDesignsHub – Loved how simple it was to browse and order products.
заказ в статусе обработки ))) https://accreditation-med.ru товар появился? когда возобновите доставку по городам?
Simple Fashion Trends – Stylish items throughout, website navigation was easy, and ordering quick.
Bold Street Wardrobe – Loved the fashion picks and the checkout worked exactly as expected.
вывод из запоя круглосуточно тула
tula-narkolog011.ru
вывод из запоя
так что мне вообще по душе и курьерка и селлер которому респект за АМ2233 купить Мефедрон, Бошки, Марихуану всё пришло с компенсацией,качество на высоте,Магазину ОГРОМНЫЙ РЕСПЕКТ
voguevaultonline – The variety impressed me, and the deals were perfect.
Urban style link – Found multiple fashionable items fast, layout user-friendly.
Shop Smile Center – Excellent variety, nice value items, and shipping was very quick.
WonderView Style Hub – Smooth navigation, lovely products, and fast checkout today.
giftfinderhub – Excellent presents available, shipping appears reliable and smooth.
Сижу жду пока высохнет АМ2233 =) купить кокаин, меф, бошки через телеграмм Так вот, прошло все как всегда отлично, дошло за три дня, маскировка надежная. Так же отдельное спасибо магазину за проявление немыслимой заботы о безопасности клиента. Что имел ввиду писать не буду, но факт есть факт.
stylishfamilystore – Easy navigation and lots of options, checkout went smoothly.
aviator x http://www.aviator-game-winner.com .
РОВНЫЙ МАГАЗ!!!УСПЕХОВ И ПОЗИТИВНОГО РАЗВИТИЯ!! купить скорость, кокаин, мефедрон, гашиш ты уже третий у кого посыль подлетела может продавец как то разьяснит ситуацию ну ладно у одного ну ладно у второго но трое это уже какая то система ждемс уважаемый ТС Ваших обяснений
PureHarborTrendy – Smooth website navigation with trendy items delivered quickly.
Daily Growth Spot – Explore resources to help you develop skills and confidence every day.
BlueHarbor Collection – Simple layout and everything was delivered safely.
Global Value Deals – Loved the affordable products, and the online process was smooth.
лечение запоя
tula-narkolog012.ru
лечение запоя
Это юмор. купить, кокаин, мефедрон, гашиш, бошки Черногорск Минск нужен. Срочно бля хуево уже, надо зарядиться! Помогите пожалуйста я здесь ни хрена не понимаю
bigsavingsonline – Found amazing bargains, checkout was simple and fast.
Soft Crest Deals – Nice assortment, simple ordering process, and very fast delivery today.
SunCrestFashionDepot – Loved the variety, easy to browse, and shipping was fast.
trendcentral – Great selection of products, browsing felt fast and easy.
Удачи всей команде желаю купить, кокаин, мефедрон, гашиш, бошки Родники Как то брал 25г реги, пришло быстро, но качество не впечатлило((
Pure Style Picks – Loved the modern designs, very simple to browse and shop.
dailyurbanfinds – Very easy to browse, checkout was quick and hassle-free.
BH Style Collection – Easy navigation, good quality, and timely delivery.
Буду делать am 2233 + rcs4. Основа: Дурман(молотый) 5г, Латук дикий 10 г, Лобелия вздутая 5 г. Как дойдет с меня трип-репорт https://sherifpizza.ru/mapsite4.html аська молчит.скайп есть?
RareSeasonBoutique – Beautiful seasonal finds with a smooth website experience.
highriverdesigns – Easy to browse collection, prices seemed fair, checkout worked without any hiccups.
SoftStone Goods – Great assortment, browsing was easy, and shipping arrived on schedule.
aviator x http://www.aviator-game-winner.com .
springlightgoods – Fast delivery, items nicely packaged, purchase completed without any issues today.
Bright Modern Store – Loved the fresh designs here, and the order reached me quickly.
BrightLeaf Value Shop – Enjoyed the entire experience; the site was fast and had plenty to offer.
не плохие ребята, все в срок и по месту) https://vilanaplus.ru/miass.html бля у нас опен эйр будет 11 июня у шамана пороха нету!!!вот ищу где бы взять что нибудь на подобие скорости или кокса!а тут отзывы что соду продают!
trendcentralstore – Easy browsing and stylish seasonal items, highly recommend.
вывод из запоя челябинск
vivod-iz-zapoya-chelyabinsk013.ru
вывод из запоя круглосуточно
FieldDreamShop – Fast website, easy ordering, and excellent product quality.
а эффор хорош?) на что похож?) купить, кокаин, мефедрон, гашиш, бошки Актюбинск У каждого селлера, в нынешние времена, продукты с одним и тем же названием, имеют часто разный внешний вид, различные дозировки и эффекты, потому то так часто у селлера и спрашивают параметры этих в-в “именно” в данном магазе “именно” у данного селлера.
trendhub – Enjoyed exploring trendy items, navigating the site was quick and easy.
Ocean Crest Online Shop – Beautiful products, easy-to-use site, and very prompt delivery.
Fresh Choice Deals – Fresh items throughout the site, and the whole ordering process was simple.
Achieve & Inspire Hub – Resources to help you stay focused, motivated, and confident in your pursuits.
Отличное качество реги! Советую! купить, кокаин, мефедрон, гашиш, бошки Мелитополь Если бы ещё доставка не выпала на выходные – ждать пришлось бы ещё меньше, так как курьерская служба по выходным у нас доставку не осуществляет. А сама доставка от пункта А до пункта Б заняла три дня.
bestbuyingcorner – Fast-loading pages and intuitive layout made shopping convenient.
<a href="https://sunrisetrailmarket.shop/" /SunriseTrailHub – Loved the variety, high-quality items, and quick delivery.
Golden Root Goods – Fast-loading pages, fair prices, and my order reached me safely.
Ищи в соседней ветке мой отзыв по рцс. ИМХО рцс не для торча. https://okno40.ru/yugorsk.html Ответят, думаю и завтра нужно будет подождать
stylefinderhub – Trendy products and quick site loading, very easy to browse.
вывод из запоя
vivod-iz-zapoya-chelyabinsk014.ru
вывод из запоя круглосуточно
win crash game win crash game .
inverter game http://www.aviator-game-deposit.com .
ремонт квартир компании https://www.rejting-kompanij-po-remontu-kvartir-moskvy.com .
Что то тут не так. https://teka-retail.ru/dolgoprudniy.html Заказывал у этих ребят 203 и 5-IAI, качеством доволен. Заказы они оформляют долго, но зато отправляют быстро. Мне отправили в день оплаты!
glamtrendhub – Nice assortment, exploring products was quick and easy.
urbanmeadowstore – Ordered a few items, they arrived promptly and packaging was neat.
oceanviewemporium – Items matched descriptions exactly, packaging was neat and service excellent.
Здесь все ровно братья как и всегда купить, кокаин, мефедрон, гашиш, бошки Заволжье у меня наоборот. в этот раз быстрее все происходит)
WildSand Picks – Great selection, intuitive website, and very quick delivery.
Dream Big Daily – Tips and strategies to turn aspirations into actionable results.
Lunar Harvest Picks Shop – Smooth and intuitive navigation makes shopping enjoyable.
Soft Cloud Online Shop – Items are well-presented and the site is easy to explore.
Bright Flora Market – Items are easy to locate, and the site feels inviting.
Магаз убойный, как начали брать пол года назад на рампе, была одна проблема пно ее быстро решили))) щас как снова завязался месяца 3 уже не разу не было))) Особенно предпочтения отдаю мефу вашему, вообще тема потрясная))) https://chertiche.ru/abakan.html Качественная продукция, советую заскочить! товар стоит вашего внимания!
shopfortrend – Quick and easy to find the items I wanted.
рейтинг casino азартные игры на рубли Выбор «лучших онлайн казино» — это не однодневная задача. Это процесс, в котором важно сочетать умение анализировать факты и доверять своему опыту. Лицензия, безопасность, прозрачные условия бонусов, широкий выбор игр и удобные платежи создают основу. Но каждое ваше решение формирует ваш уникальный маршрут — от первого знакомства с площадкой до долгосрочного удовольствия от игры.
timelessharboremporia – Fast site and neatly presented items for a pleasant browsing experience.
urbanhubonline – Excellent items at reasonable prices, very happy with today’s shopping.
вывод из запоя круглосуточно
vivod-iz-zapoya-chelyabinsk015.ru
вывод из запоя
И потом не удивляйтесь, что магазин медленно работает или не отвечает. Попробуйте по 100 раз в день рассказывать что и как разводить, и при этом успевать оформлять заказы. купить, кокаин, мефедрон, гашиш, бошки Мантурово задержек небыло все было ровно магаз ровный заказывай трек сразу кидают , за качество не могу пока ничо отписать , не пробывал, попробую отпишу!
urbanchic – Great variety of urban styles, shopping experience felt seamless.
plane crash game money download aviator-game-deposit.com .
ремонт квартир москва отзывы ремонт квартир москва отзывы .
ну как-то так https://powsurfing.ru/ust-labinsk.html у меня такой вопрос: будут ли у вас на розничном сайте позиция am-2233 по 1гр? Я раньше брал через алхима, но он по неизвестным мне причинам сговнился. поймите меня правильно, для меня 7 кусков – это деньги и я не готов их дарить или тратить на непонятно что.
FreshWind Emporium Shop – Great assortment, clear visuals, and easy ordering all around.
ребятки так жержать!) уровень достойный https://powsurfing.ru/donskoy.html екб есть в представителях, смотрите в представительствах
Modern Harbor Corner – Products are easy to find and the interface is user-friendly.
Daily Innovation Spot – Explore fun and inspiring ways to try new things.
uniquefindshub – Fast and simple shopping experience, pages loaded quickly.
free adult video chat best free chat rooms
Full Circle Picks – Simple layout and effortless navigation make shopping enjoyable.
simpletrendstore – Great collection of fashion pieces, site navigation was smooth and fast.
Да хоть в очко засыпь, не торкнет купить, кокаин, мефедрон, гашиш, бошки Людиново что же это за дела то…..?
экстренный вывод из запоя череповец
vivod-iz-zapoya-cherepovec016.ru
вывод из запоя цена
bestbuytoday – Found top deals instantly, navigating the site was easy and fast.
электрические рулонные шторы купить электрические рулонные шторы купить .
которые воспитанны на обычном Фене ! купить, кокаин, мефедрон, гашиш, бошки Миллерово Отличное качество товара
казіно з бонусами бонусы казино
?????? ??? ???? ?? ?? ????? http://aviator-game-deposit.com .
профессиональный ремонт квартир в москве профессиональный ремонт квартир в москве .
WindBright Marketplace – Pages loaded perfectly and my order arrived right on schedule.
Timber Grove Boutique – Products are easy to explore, and the interface is user-friendly.
stylecentralhub – Loved the items, checkout went incredibly fast.
dealhunterdaily – Very convenient to shop, ordering process was simple and fast.
лечение запоя
vivod-iz-zapoya-cherepovec017.ru
вывод из запоя круглосуточно череповец
honestgrovegoods – Products looked appealing and site navigation is intuitive, a good shopping spot.
Спасибо. Похож на ам2**3 https://tvoya-gruppa.ru Ещё и сообщения трут.
truewoodsupply – Great overall feel, browsing was comfortable and items looked nicely presented.
chiccorner – Really liked the outfits available, browsing and checkout were effortless.
Calm Harbor Market – Quick to find items with a visually pleasant interface.
“Всех благ в вашем нелегком Бизнасе” https://24sema.ru сам знаешь что я могу про тебя сказать, ты лучший в своем деле! все всегда в срок! товар на высшем уровне , качество огонь ! сколько раз не брал всегда все ровно и четко! ждем твоего возвращения очень очень ждем, уже сходим с ума без тебя братан)) возвращайся скорей
купить электрические рулонные шторы http://avtomaticheskie-rulonnye-shtory11.ru/ .
Silver Moon Market – Loved the wide selection, quick delivery, and everything arrived in perfect condition.
И потом не удивляйтесь, что магазин медленно работает или не отвечает. Попробуйте по 100 раз в день рассказывать что и как разводить, и при этом успевать оформлять заказы. купить скорость, кокаин, мефедрон, гашиш концентрация 1к 12 мне норм разврдил на муравьином спирте (купил его в аптеке)
relaxhub – Smooth layout and easy to navigate, made shopping enjoyable.
Modern Ridge Finds Online – Browsing is intuitive, and products are easy to spot.
stylevaulthub – Trendy finds were easy to browse, delivery was prompt and safe.
Проб НЕТ! https://bubbleszoomag.ru у Вас очень серьезные проблемы.
dealspotonline – Smooth browsing, found exactly what I wanted.
экстренный вывод из запоя череповец
vivod-iz-zapoya-cherepovec018.ru
экстренный вывод из запоя череповец
дешевые проститутки нижневартовска
Бро все супер,как всегда ровно,спасибо за прекрасно отлаженную работу. Процветания тебе и твоей команде.Спасибо! купить Кокаин, Мефедрон, Экстази Привет старичок
Mindful Progress Hub – Daily advice for personal growth and intentional living.
Timberwood Studio Picks – Fast browsing and finding products is simple and pleasant.
Bright Meadow Corner – Simple checkout, helpful layout, and the delivery was spot on.
отписал бы по факту с картинками https://akb-ivanovo.ru Может стоит внимательно посмотреть в ветке что есть резервный жаббер ? основной уже 6 дней не работает , какие то сбои, но резерв ведь работает, привыкли панику поднимать на ровном месте.
mediafusion – The site looks well designed and browsing through products was quick and smooth.
автоматические рулонные шторы с электроприводом на окна https://www.avtomaticheskie-rulonnye-shtory11.ru .
learnshareachieve – Products are easy to find and layout feels friendly — good browsing experience.
Aurora Mart – Navigation is simple and products are displayed nicely.
mt5 download mac metatrader-5-downloads.com .
download metatrader 5 download metatrader 5 .
modernoffersstore – Loved the deals, moving through the website was fast and easy.
“Но представь такую сетуацию,если бы я бахался по В/В и ко мне в кровь попали Эти таблетки я бы отправился на тот свет ” купить онлайн мефедрон, экстази, бошки Магазин замечательный!!
проститутки нижневартовск с выездом
stylevault – The website is clean and browsing for products is a pleasant experience.
вывод из запоя круглосуточно иркутск
vivod-iz-zapoya-irkutsk013.ru
вывод из запоя
trendhunterhub – Convenient to browse and shop, found multiple items I liked.
glamcorner – Excellent variety of fashion pieces, delivery seemed quick and hassle-free.
Привет ребята! В улан-удэ синие кристаллы имеются? купить кокаин, меф, бошки через телеграмм Хмм…странно всё это, но несмотря ни на что заказал норм партию Ам в этом магазе так как давно тут беру.Как придёт напишу норм репорт про Ам
Данный продукт не зашол в моё сознание:) его нужно бодяжить с более могучим порохом, будем пробовать АМ2233… купить кокаин, меф, бошки через телеграмм качество правда не очень, именно по продолжительности эффекта- в разных концентрациях его можно варьировать как тебе хочется=))))
Origin Peak Styles Online – Beautiful designs, fast-loading site, and my order arrived as expected.
Whispering Trend Boutique – Smooth browsing and a visually neat design make shopping enjoyable.
Open Plains Central – The layout is clean, making shopping simple and fast.
Получили адрес с небольшой задержкой , ТС все объяснил , отвечал сразу , без каких либо задержек . https://astroenergosintez.ru Я выхватил бан, ты злобняк
trendfusion – Fast and easy purchase, the variety is impressive.
экстренный вывод из запоя
vivod-iz-zapoya-irkutsk014.ru
вывод из запоя
download mt5 for mac http://www.metatrader-5-downloads.com .
metatrader 5 mac download http://www.metatrader-5-mac.com/ .
offerscorner – Loved the variety of deals, website navigation was quick and easy.
Почему ушли из РБ? купить кокаин, меф, бошки через телеграмм Разве имеет принципиальное значение сколько моему аккаунту времени? Я тут не *зависаю*, а пишу по сути. Мутность заключается в том что оператор в аське на вопросы по уточнению адреса, сначала молчал почти 3 часа, потом вообще оффнулся.
trendpickscentral – Very easy to navigate, ordering was smooth and fast.
freshchoicepick – Fast and easy navigation, products are neatly displayed.
В каких пропорциях??? https://ab-thaispa.ru смотри на сайте в своих заказах (в коментариях)…
Soft Blossom Shop – Beautiful assortment, simple navigation, and checkout went without a hitch.
modernstylecorner – Fast loading and clear presentation — made selecting products easy and hassle-free.
modernshoppingcorner – Pleasant user experience overall, navigation is clear and products display nicely.
ТС, почисти ветки, ну невозможно же ничего почитать..в разных ветках одно и тоже. купить скорость, кокаин, мефедрон, гашиш Сделал очередной заказ в этом магазине:good: всё пришло качество как всегда радует буду дальше работать с вами:good:приятно иметь дела с ответственными партнёрами:voo-hoo: процветания вашему магазину:):):)
dealhubtoday – Daily bargains are fantastic, shipping was smooth and reliable.
Fashion & Style Daily – Daily recommendations for looking stylish and feeling confident.
Coastline Hub Picks – The layout is clear, and shopping feels effortless.
надо испробывать…много хороших отзывов купить кокаин, меф, бошки через телеграмм Короче, подошёл я к адресу, а там ни по звёздам, ни по местности, ни право-лево не надо проверять. Я даже фонарик не включал, все чётко по описанию.
Sunwave Essentials Emporium – Browsing feels natural and the layout is visually appealing.
лечение запоя иркутск
vivod-iz-zapoya-irkutsk015.ru
вывод из запоя иркутск
homestylehub – Very nice assortment, exploring products was easy and fast.
fashionzonehub – Quick navigation, found several trendy pieces easily.
metatrader 5 download mac metatrader-5-downloads.com .
mt5 download for pc http://metatrader-5-mac.com .
Мы уже давно не делаем отправки, я не знаю за какую посылку вы говорите. купить скорость, кокаин, мефедрон, гашиш Мы в Кургане не работаем, все наши представительства есть в соответствующем разделе.
trendcorner – Fast-loading pages make browsing enjoyable and effortless.
Noble Ridge Fashion – Stylish pieces, smooth website, and my order arrived quickly and as expected.
Причем здесь стаффстор ко мне ? https://zzoss-zlatoust.ru Тоже интересен вопрос по шифровке посылки при доставке курьером
Kind Groove Online – Products are easy to locate, and the layout feels modern.
Причёт тут почта России, СПСР это самостоятельная курьерская служба. купить кокаин, меф, бошки через телеграмм да да ))) 100% ))0
вывод из запоя круглосуточно
vivod-iz-zapoya-kaluga016.ru
вывод из запоя калуга
Positive Mindset Spot – Strategies for cultivating positivity and self-assurance.
всё ровно будет бро! просто график отправок такой https://sntmalinovka.ru Он тоже не работает, его ветки нет в РБ разделе.
BlueGrain Essentials Shop – Found high-quality items quickly and browsing felt intuitive.
freshgiftoutlet – Very easy to shop, found exactly what I wanted.
Ровный магаз,всем советую) https://powsurfing.ru опробовал и такая же фигня получилась..прет так: становиться на пол часа-час прикольно,все интерессно,эйфории вообще нет или она очень слабая( очень разочаровала сдешняя фофа..
рулонные шторы с автоматическим управлением http://avtomaticheskie-rulonnye-shtory11.ru .
metatrader5 download metatrader-5-downloads.com .
metatrader5 download https://www.metatrader-5-mac.com .
KindleWood Corner – Great product range, simple checkout, and my order arrived right on schedule.
glamzone – The site is well-organized and browsing for items felt natural.
Мы уже давно не делаем отправки, я не знаю за какую посылку вы говорите. https://tazman.ru Принять могут в любой курьерке и уж тем более на почте. 1 случай (без полных подробностей и выяснения всех обстоятельств о самом человеке и его деятельности) на пару сотню посылок это не тот случай, когда нужно отказываться от удобной курьерки. Об этом уже говорили неоднократно. Возвращаться к этой теме больше не стоит.
Dream Harbor Market – Navigation is smooth, and the site is pleasant to explore.
вывод из запоя
vivod-iz-zapoya-kaluga017.ru
лечение запоя
purechoicehub – Enjoyed browsing here, product categories are clear and items are easy to compare.
Товар даже не тестили еще ! Но вес ровный , качество не сомневаюсь тоже на высоте , скоро будем проводить тесты . Буду брать только здесь !!! купить онлайн мефедрон, экстази, бошки ХОРОШО СВЯЖЕМСЯ КОГДА ПРИЕДУ ДОМОЙ Я НА ПРИРОДЕ ДАВЛЮСЬ ПИВОМ А МАГАЗИНЕ НАПИСАНО ЧТО ОТПРАВЛЕН MXE
ORBS Production https://filmproductioncortina.com is a full-service film, photo and video production company in Cortina d’Ampezzo and the Dolomites. We create commercials, branded content, sports and winter campaigns with local crew, alpine logistics, aerial/FPV filming and end-to-end production support across the Alps. Learn more at filmproductioncortina.com
заказ оформил – жду посылочки ^^ купить скорость, кокаин, мефедрон, гашиш Всегда платил через киви перевод идёт максимум сутки.950р это с курьером доставит тебе куда скажешь)))
favstorehub – Easily found favorite products, browsing and checkout were quick.
Wild Horizon Boutique Shop – Trendy pieces, fast website, and checkout worked perfectly.
А в сочи есть магазины https://eraofm.ru Получал пробный набор (ам2201, jwh250, jwh203, 5iai) от данного селлера, качество хорошее кроме 5iai вообще не понял.
рулонные шторы с электроприводом купить рулонные шторы с электроприводом купить .
mt5 download for pc http://www.metatrader-5-downloads.com/ .
mt5 mt5 .
Bridgetown Finds – Shopping feels easy and the products are nicely displayed.
globalshoppinghub – Fast, intuitive interface, and products are neatly categorized.
лечение запоя калуга
vivod-iz-zapoya-kaluga018.ru
экстренный вывод из запоя калуга
Всем добрый вечер, рега появилась, та хорошая, которая у вас была!? https://chertiche.ru Большое спасибо команде chemical-mix за проведенную сделку, с наступающим Вас Новым Годом!
магаз ровный!!! все на высшем уровне!!! работаю с ними много лет!!! https://tazman.ru Доставка осуществляется нашим курьером при заказе от 1кг!И обговаривается с ТС индивидуально!
dailyshoppingfinds – Very satisfied with the variety, placing the order was hassle-free.
все супер! магазину доверять можно, были небольшие задержки но ТС сделал все по красоте! https://auto-ucz.ru Мир вам!
Grand Style Online – Navigation is fast, and everything is well presented.
Кто под нос что-то бормочет, купить скорость, кокаин, мефедрон, гашиш Хотел бы поблагодарить магазин за отличное отношение и замечательную работу) Давно такого не встречал.
рулонные шторы на окна купить рулонные шторы на окна купить .
metatrader 5 http://www.metatrader-5-downloads.com/ .
metatrader 5 download mac http://www.metatrader-5-mac.com .
dailycurious – Easy to navigate, items are organized and simple to find.
shopthelatestdeals – Good product variety and easy to navigate, helped me spot offers easily.
А ты тс в лс отпиши , и если ты не балабол , в чем я очень сомневаюсь то проблема будет решена , а писать на ветке это говно для чего не понятно , на что вы надеетесь https://accreditation-med.ru 3)Бабки там всякие
shopandsmiletoday – Products look well presented, and overall shopping felt smooth and straightforward.
Style Finds Hub – Explore popular products and enjoy an easy and enjoyable shopping process.
Future Groove Central – The layout is simple and products are easy to locate.
Morning Rust Collective – The interface is simple and exploring products is enjoyable.
focuszone – Smooth interface, quick page loads, and browsing felt natural.
Tham gia cộng đồng game thủ tại Go88 để trải nghiệm các trò chơi bài, poker phổ biến nhất hiện nay.
вывод из запоя краснодар
vivod-iz-zapoya-krasnodar022.ru
экстренный вывод из запоя краснодар
believeandachieve – Product listings are clear and well organized, helped me browse comfortably today.
shopwithjoy – The site looks tidy and organized, shopping felt quick and efficient.
Urban Peak Spot – Shopping is hassle-free and items are easy to find.
Fashion Inspiration Spot – Daily guidance to make your fashion and lifestyle choices effortless.
EverPath Finds – Loved how easy it is to browse through the well-organized items.
экстренный вывод из запоя
vivod-iz-zapoya-krasnodar023.ru
экстренный вывод из запоя краснодар
motivationselection – Pages load quickly, items are organized, and browsing feels natural.
Dawncrest Emporium – Browsing is smooth and the site layout makes shopping effortless.
Хочешь развлечься? купить мефедрон федерация – это проводник в мир покупки запрещенных товаров, можно купить гашиш, купить мефедрон, купить кокаин, купить меф, купить экстази, купить альфа пвп, купить гаш в различных городах. Москва, Санкт-Петербург, Краснодар, Владивосток, Красноярск, Норильск, Екатеринбург, Мск, СПБ, Хабаровск, Новосибирск, Казань и еще 100+ городов.
ван вин 1win официальный 1win not int
вывод из запоя круглосуточно
vivod-iz-zapoya-krasnodar024.ru
лечение запоя
Lunar Wave Corner – Navigation is seamless and products are easy to explore.
бонуси в казино бонуси в казино
urbanpick – Smooth browsing, intuitive interface, and items are clearly presented.
Starlit Style Stop – Products are well arranged, and shopping is quick.
brandmomentum.click – Mobile version looks perfect; no glitches, fast scrolling, crisp text.
bestchoiceoutlet – Quick loading and intuitive design helped me shop without delay.
Магазин как магазин! купить кокаин, меф, бошки через телеграмм напишите в аську, там порешают вашу проблему. С этой партией МХЕ определённо вышел косяк.
believeandachieve – Great selection and user-friendly layout made browsing fun and easy today.
залив с крыши оценка ущерба залив с крыши оценка ущерба .
Discounts & Offers Hub – Access the latest discounted products for everyday needs.
экстренный вывод из запоя
vivod-iz-zapoya-krasnodar025.ru
вывод из запоя краснодар
заказать курсовую работу спб kupit-kursovuyu-8.ru .
купить курсовую москва купить курсовую москва .
всем привет магаз ровный сделал проплату во сколько сказали даже раньше получил адресс.успехов магазу будем работать https://salon-miledy.ru забьется, такое бывает у них.
Timberline Collective – Quick navigation and a visually clean interface throughout.
wearcentral – Fast-loading pages with tidy layout made browsing enjoyable.
по времени ждал не долго дня 4 но доставка отдала на 2ой день как пришло , конспирация мне очень понравилась на все 100% магазину 100 из 100 и большой спс ) https://real-estate23.ru Берите уверенно работаю с этим магазином
FutureGardenOnline – Well-structured pages with fast navigation made discovering products easy.
Магазин ровный! Я заказал 1000ф, оплатил ЯД, оператора попросил отправить посыль на следующий день , без задержки т.к. сроки получения очень поджимают. На что оператор адекватно ответил что все сделают.На следующий вечер получил трек, посылочка собранна и вот вот выезжает))) если уже не выехала) Магазину как и его администрации – от души за оперативность и отношение к клиенту. купить кокаин, меф, бошки через телеграмм сердцебеение крч все как обфчно , в
go to site – Enjoyed the fast browsing speed and how simple it was to discover products.
horizon picks – Fast pages and clear categories made exploring products enjoyable.
АА Все братишки, мне уже отослали сегодня, спасибо что успокоили! https://falconeditor.ru Ты еп сегодня зарегился и уже опробывал?покупателей много,очереди наверно большие тем более на доставку
Провести детоксикацию от алкоголя – это важный шаг для борьбы с зависимостью. Терапия алкоголизма начинается с процесса детоксикации‚ которая облегчает с симптомами похмелья. На сайте vivod-iz-zapoya-krasnoyarsk016.ru вы найдете информацию о центрах реабилитации‚ где предлагается помощь в лечении зависимостей и поддержка психологов. Программы реабилитации включают поддерживающие мероприятия для зависимых‚ клубы анонимных алкоголиков и мероприятия по улучшению здоровья и профилактике алкоголизма. Осознание воздействия алкоголя на организм помогает осознанно подходить к лечению и возвращению к нормальной жизни.
golden access – Clear sections and responsive design made shopping effortless.
birchoutletlane – Items are clearly presented, making browsing fast and pleasant.
новые индивидуалки нижневартовск
слоти безкоштовно слоти онлайн
онлайн ігри казино ігри казино онлайн
timberlineinspire – Clean design and motivating layout make discovering new ideas effortless.
WildTrailEmporium – Easy to navigate, shopping felt effortless.
Trendy Finds Spot – Discover stylish options and navigate collections without hassle.
купить курсовую работу купить курсовую работу .
не в курсе https://nedolgoff.ru отвечать вам не перестали я дал ответы на ваши вопросы, когда по несколько раз 1 и то же спрашивают я не отвечаю.качество продукции класс. Но пожалуй что радует больше всего – отзывчивость администрации и оперативность работы.
aplikacja mostbet na androida mostbet
курсовая заказать недорого http://kupit-kursovuyu-5.ru/ .
Sun Meadow Shop – Smooth navigation and organized layout made exploring products effortless.
Wonder Peak Treasures – Fast and intuitive browsing with a tidy layout.
shopzonehub – Smooth browsing, products are well organized and easy to locate.
грати слоти найкращі слоти
что то не могу зайти на сайт ( купить кокаин, меф, бошки через телеграмм Mushnyak, да ты гонишь походу, магазин работает как надо, каждую неделю у них заказываю все ровно, кидаловом тут не пахнет, ты наверное на отходосах))))видел тут в ветке пару сообщений о том, что заказчикам вместо нормального товара какую то муть присылали, так вот хотелось бы узнать у владельцев магазина, в связи с чем возникают такие накладки и как часто такое случается, а то почтой итак заказ долго дожидаться, а если ещё подобный косяк выйдет с возвратом, то это будет полный п…
trend finder – Quickly located what I wanted due to the smooth structure of the site.
dreamleafgallery – Product images load well and descriptions are clear, making shopping comfortable.
CTO Timber Selection – Simple design and smooth browsing created a nice overall experience.
brandelevate.click – Content reads clearly, helpful examples made concepts easy to grasp.
brightorchardhub – Fast loading and clear product photos made shopping easy and pleasant.
horizon hub corner – Well-arranged layout and fast-loading pages improved browsing.
Кент,приветствую..!!))В личку ответь,там по поводу оплаты…….оплатил договаривались на выходные…жду там от тебя ответа)) купить Кокаин, Мефедрон, Экстази хороший магазин,всё на красоте и качество и кол-во:) продолжайте в том же духемагазин ровный
Прокапывание от алкоголизма в городе Красноярске – это ключевой шаг в борьбе с алкоголизма. Процедуры детоксикации помогают справиться с симптомами абстиненции и избавиться от запойного состояния. Лечение в специализированных центрах включает не только прокапывание‚ но и психологическую помощь‚ что способствует восстановлению после алкоголя. vivod-iz-zapoya-krasnoyarsk017.ru Реабилитация начинается с очистки организма‚ после которой инициируются реабилитационные программы. Роль родственников также играет значимую роль в предотвращении срывов. Анонимные алкоголики и обращение к специалиста могут помочь в процессе реабилитации. Не забудьте‚ что лечение алкоголизма требует комплексного подхода.
tallbirchstore – Very easy to browse, and products are displayed clearly.
брали 10 гр реги )))) https://santexnikasochi.ru Ну короче усе круто, магаз супер, всем советую!!!Бро слова это хорошо но нам нужен наш клад и не более не кто не хочет тебя винить и общаться сдесь на эту тему а на оборот писать только хорошие отзывы о вашем магазе пойми и ты бро слово паника сдесь не уместно сдесь идет разбор по факту согласись
goldencraftshop – Easy-to-follow layout and neat product pages, shopping was fast.
где можно купить курсовую работу http://kupit-kursovuyu-8.ru .
Почему закрылся представитель в петрозаводске? Жду ответа чем) https://devase-gr.ru заказывал не один раз в этот раз заказал в аське нету тс жду 8дней трэка нет че случилось тс?Начал гнать на продавца, но потом увидел у других людей на других сайтах и форумах репорты по 5иаи, купленные у других магазов и оказалось, что просто само 5иаи – это полна Чляпа)
mostbet global mobilny mostbet
онлайн ігри казино казіно ігри
check this shop – Loved how straightforward the browsing experience was.
everymomentpick – Products are easy to locate, and browsing felt natural.
Магазин ровный.;)Жаль реги пока нет купить Кокаин, Мефедрон, Экстази подход к клиенту 5+ (все объяснили, трек сразу скинули)Товар даже не тестили еще ! Но вес ровный , качество не сомневаюсь тоже на высоте , скоро будем проводить тесты . Буду брать только здесь !!!
shop urban collection – Smooth navigation and neatly displayed products improved browsing.
Вызов врача нарколога — важная мера для людей‚ испытывающих проблемы с зависимостями. Наркологическая помощь включает выявление зависимости и ее лечение‚ что особенно актуально в кризисных ситуациях. Обратившись на vivod-iz-zapoya-krasnoyarsk018.ru‚ вы можете вызвать врача на дом анонимно. Это гарантирует комфорт и безопасность. Услуги нарколога на дому обеспечивают удобные условия для клиентов. Консультация нарколога позволяет выявить степень зависимости и разработать персонализированную программу терапии. В процессе реабилитации важна поддержка для родственников‚ что способствует эмоциональной стабильности. Специализированная наркологическая клиника предлагает комплексное лечение‚ включая психотерапевтические сеансы и медикаментозное лечение зависимостей. Не стоит откладывать обращение за помощью‚ ведь своевременное лечение алкоголизма и наркотической зависимости может спасти жизнь.
brookhavenstore – Clear design, shopping feels relaxed and organized.
golden boutique access – Browsing felt natural and product sections were easy to follow.
Четкого товара! https://sauna-tverici.ru Братья, у меня вопрос. JV-30 как? Боюсь нарваться на регу с которой крышу сносит. Ответьте пожалуйста.Всё что В прайс листе на сайте есть,всё в наличии ?
Cozy Timber Storefront – The relaxed design and tidy pages made the browsing session feel smooth.
конце концов при курении эйфория купить Кокаин, Мефедрон, Экстази боюсь что здесь произойдёт тоже самое, уж очень не внятно продавец общается.щас заказал по 5г RCS-4 и URB754 по скайпу объяснили как оплатить, пока всё коректно жду посылки там отпишу..
Northern Mist Select – Clear layout and intuitive pages helped me pick items easily.
NewGroveEssentials Online Shop – Well-structured pages helped me explore categories quickly.
Магазин лутше не встречал!!!! купить онлайн мефедрон, экстази, бошки Хочу всем сказать мы не работаем 1вым классом ни при каком условии…у меня наоборот. в этот раз быстрее все происходит)
Sun Meadow Collection – Smooth navigation and organized categories helped me find products quickly.
shop here – Smooth navigation and a neat design made the visit enjoyable.
coast choice picks – Smooth navigation and tidy layout improved the browsing experience.
urbanvinecollective – Good selection and easy navigation — overall a nice shopping experience today.
lunarcrestlifestyle – Good variety here, layout feels tidy and shopping was hassle‑free.
a href=”https://brightnorthboutique.shop/” />brightnorthstyle – Very intuitive design, browsing feels seamless.
a href=”https://growyourmindset.click/” />mindgrow – Pages load quickly, and navigating categories was straightforward.
Быстрая доставка , и высочайшее качество обслуживания! Думаю и сейчас ничего не изменилось. купить Мефедрон, Бошки, Марихуану продавец в аське..только что с нми общалсяглядишь к новому году договоримся, а там и к 2020 посылка придет…
willow hub – Items loaded quickly and categories were easy to explore.
crestartstyle – Well-structured site with clear sections, made shopping easy.
надо испробывать…много хороших отзывов https://kartiny-mne.ru Качество товара на 5+,вот только почта подвела привезли на 5й день.2.Почему на сайте нет ниодного упоминания о ритейле,в то время,как заказы надо делать через него?
помощь курсовые http://www.kupit-kursovuyu-9.ru .
Northern Mist Store Shop – Clean layout and well-arranged items made browsing effortless.
Я тебе не хамил. Да 10г, смешно не смешно, а на дороге не валяются. И очень обидно когда от вашего ПМа получаешь подтвердение, веришь! и остаешься с разочарованием и обидой, бессилием что либо доказать. А тебе еще сверху льют хамство, упивайтесь на здоровье. Я утерся и теперь знаю на что способны даже нормальные, доверенные магазины. А это тоже опыт, за который я заплатил, и ничуть не жалею. Просто пусть народ знает и будет готов при работе без гаранта ТУТ ожидайте что такое может быть. https://softaa.ru Доброга времени суток, закладки в москве делаете?вчера вечером получил трек сегодня груз, я охуеваю от скорости доставки походу ТС выкупил курьерку ))) по качеству отпишусь позже
Corner Boutique Online – Items are attractive, and moving through the site was effortless.
Bluestone Deals – Browsing was effortless with a fresh look.
Wild Shore Hub Online – Logical layout and clear menus helped me explore products easily.
свежие новости беларуси и мира беларусь события новости
soft picks – Smooth interface and neatly arranged items made browsing effortless.
Пишите в скайп, аську, пожалуйста без лишнего, чтобы была возможность ответить всем. :good: купить Кокаин, Мефедрон, Экстази Мне уже похер будет он иле не будет!Хорошо что я как обычно не взял на 45т.р вот о бытом я вообще не жалею!Если магазину важнее не совершать обмен чем клиент который в неделю на 45т.р товара брал то досведание!У Данного Магазина я так понимаю Принцип не отвечать в Аське?!=)
Growth & Potential Hub – Discover tips and inspiration to develop your skills and reach new heights.
Lunar Peak Finds – Navigation is smooth, and items are clearly displayed.
deal spot – Came across many good bargains and the site layout made everything simple.
Я вообще удивляюсь как продаван работает то? Есть ветка форума, личка и ася – везде молчание. В ася онлайн, но всеравно молчит уже третий день – это адекватный сервис? купить кокаин, меф, бошки через телеграмм у меня тоже дроп подлетел с посылкой и брали его ФСБшники почему то , но слава богу до уголовного дела не дошло, и ТС обещал жирную скидку сделать при следуещем заказе как то так (документы о прекращении уголовного дела и экспертиза на руках) дело закрыли по двум причинам то что дроп не при делах а второе самое главное что экспертиза не выявила НСТрек получил, всё ровно!
puremeadowmarket – The site feels trustworthy, each product seems thoughtfully presented and detailed.
coastlinegather – Really liked the product variety, each category feels curated with attention.
wildmountainshop – Very easy to browse, and the natural-themed products are well presented.
happyhub – Smooth navigation with fast-loading pages, shopping was enjoyable.
evermeadowgoods – Great selection and intuitive navigation helped me explore products without hassle.
всё чётко, ровно, от души скоро буду ещё заказывать ) Пришло быстро конспирация на все 100% ! купить Мефедрон, Бошки, Марихуану Вот такая хитростьНу что же, сегодня получил свою посылку, на этот раз все было в наилучшем виде, конспирация на все 10 баллов из 10!
куплю курсовую работу куплю курсовую работу .
Bright Timber Boutique – Easy navigation and variety of items made shopping stress-free.
А за кладом я решил ехать на такси. https://stroycom-cher.ru Адрес почты правильный, все проверил не 1 раз, ответьте хоть тут.ну будем надееться что и на этот раз TS войдет в положение и как нибудь обратит внимание на решение наших вопросов, компенсирует нам потраченые нервы и время на безсмысленное ожидание, главное ведь для магазина репутация!смотри на сайте в своих заказах (в коментариях)…
Mountain Mist Online Picks – Fast-loading sections and easy browsing made the site convenient.
Mountain Wind Studio Finds – Browsing was simple and the products were easy to view.
moonfall collection – Fast-loading pages and tidy design made browsing enjoyable.
Клад сделан очень грамотно в безлюдном месте, к кладу прилагалось фото на котором указано место закладки. купить кокаин, меф, бошки через телеграмм лучше недобздеть чем перебздеть!!! братуха я надеюсь и у тебя все будет ГУД! держи в курсепродавец в аське..только что с нми общался
Urban Seed Collective – Quick exploration and a visually clean interface.
Modern Fable Shop – Navigation is easy and everything loads quickly.
SilverBirch Home – Navigating is a breeze with the intuitive layout and instant loading pages.
growth hub – Navigation is straightforward and exploring sections is comfortable.
Ну а как сейчас я конечно не знаю как тут… Думаю время покажет, и фараоны может раслабятся:police: либо появится какая нибудь другая лазейка по сбыту.. купить скорость, кокаин, мефедрон, гашиш и что теперь делать с заказом мне его оплачивать через терминал!? или..Да я написал уже. Мб 2-dpmp в качестве компенсации подгонят, а вот что с фф не знаю, я ее проебал до того как я еще попробовал.
в каком казино дают за регистрацию бездепозитные бонусы
greenoutpoststyle – Layout is tidy and user-friendly, finding items is quick.
studio corner – Tidy pages and clear sections made finding products effortless.
Всем удачи! https://santeh-electro.ru Здесь буду отписываться, чтобы все РЕАЛЬНО понимали сколько времени длится весь процессКто знает что происходит? Походу покупают все в тихушку!:confused: Внесите ясность!:hz: Дайте реги уже:confused::sos:
softrosecollection – Clear interface with organized products, shopping was simple.
makezone – Fast and user-friendly browsing, all items are easy to locate.
заказать студенческую работу http://www.kupit-kursovuyu-9.ru .
EverRoot Market – Easy-to-use interface with neatly displayed products helped me browse quickly.
Написал о заказе в аське в ПТ,мне сказали цену и реквизиты. В СБ оплатил,кинул в аське свои реквизиты.В ПН связался-Сказали,что все отправили,ок. https://water-heating.ru Качество превосходное! чистейший джив у вас) всем нравится. Удачных продаж,бро!небольгой репортаж отписать о ск.
BoldCrest Goods – Browsing was enjoyable thanks to simple menus and fast search.
golden picks – Smooth interface and intuitive navigation made shopping hassle-free.
трек получен, ребятам уважуха:rasta: купить онлайн мефедрон, экстази, бошки заказ дошел до нас)))вот вот такая же история! надо разобраться с этим вопросом!
Explore GoldenBranchMart – Well-arranged sections improved the overall shopping flow.
Autumn Hub – Products are neatly arranged and easy to browse.
build success – The pages are well-structured and exploring items is hassle-free.
удачного развития в дальнейшем=) купить скорость, кокаин, мефедрон, гашиш Что именно вам непонятно? всегда есть личные сообщения куда можно написать.Повторюсь размер компенсаций зависел от веса, длительности, индивидуальных переплат на счета и прочих обстоятельств. Данные по общ весу пришли вместе с треком.
rootvibeboutique – Items are well arranged, making shopping smooth and enjoyable.
Fresh Meadow Collective – Smooth navigation and a tidy layout make shopping enjoyable.
Urban Fashion Picks – Explore the latest streetwear and elevate your daily style.
понравилось очень!!!!!! купить скорость, кокаин, мефедрон, гашиш Так что тут 50:50 если тебя примут. Все зависит от конкретного города и гнк в нем.Всё отлично тут! в МСК забрали вес ! сервис как всегда отличный ! ТАК ДЕРЖАТЬ
Main Store Page – The coherent layout allowed me to finish my shopping in record time.
Pasture Finds – Fast site performance and a well-organized catalog make shopping easy.
softpineoutlet – The site feels trustworthy, product details and photos look well presented and honest.
silveroakstudio – Appreciate the aesthetic here, gives the store a calm and trustworthy vibe.
BrightStone Boutique – Smooth navigation and clear visuals made finding products a breeze.
modernselectionhub – Navigation is effortless, and all products are neatly arranged.
хотели бы услышать отзывы о Ск муке купить онлайн мефедрон, экстази, бошки Заказывал Реагенг, всё нормально пришло, небольшой бонус порадовал, мелочь а приятноНу,оправдалась моя нелюбовь к аське,ибо история не хранится и происходит всякая фигня.У меня произошел не самый забавный случай.
Timber Crest Corner Shop – Organized pages and easy menus allowed me to find items fast.
emporium hub link – Navigation felt effortless and products were displayed neatly.
Я всегда сам еду за ней,можно чтоб и доставили)Просто так быстрее пока они доставят я уже все сделаю. https://bizneszrelost.ru жасти моё уважение к тебе и респект красавица. но ес честно ты нашла чет не то что было совсем другое как сказал уже уважаемый дельфин там было много сути и честных отзывов :monetka: ну лан проехали если так вроде все все поняли.курьерки на мой запрос поиска трека ответ что инфа закрыта для доступа
Evergreen Central – Products are easy to explore, and the layout is clean.
всем желаю счастья! https://kafeterij.ru да, самая действенная схема для работы с чемикаломЗаказал АМ 2233,разведу 1 к 15 Посмотрим что из этого получится)отпишусь ещё
eco selection – Items are easy to view and the design feels calm and welcoming.
cozycorneremporium – Everything is neatly organized, site feels pleasant to browse.
стараемся для вас купить кокаин, меф, бошки через телеграмм но в итоге, когда ты добиваешься его общения – он говорит, что в наличии ничего нет. дак какой смысл то всего этого? разве не легче написать тут, что все кончилось, будет тогда-то тогда-то!? что бы не терять все это время, зайти в тему, прочитать об отсутствии товара и спокойно (как Вы говорите) идти в другие шопы.. это мое имхо.. (и вообще я обращался к автору темы)второй раз заказываю, класнный продукт пришел что 250 что 307 , качество отменное , доставка буквально 3 суток
crestlookhub – Clear design and organized products, browsing felt natural and simple.
brightwinterstore – Products look appealing and navigation is smooth — a good shopping experience.
Lunar Harvest Collection – The pages were well-structured, giving a comfortable browsing experience.
EverWild Haven – Organized pages and smooth navigation made shopping stress-free.
Personal Growth Daily – Inspiration and strategies for continual self-improvement and progress.
Получил RCS-4 развел в спирту 50, растворился только после нагрева… купить Мефедрон, Бошки, Марихуану А я не могу сделать покупку почему-то, обидно, блииин, денюха сегодня!!!(спасибо за инфу , но только узнал про новый список запвеществ , чувствую вся лавочка прикроется на некоторое время …
Cozy Cabin Treasures – Navigation feels natural and the site is visually neat.
RusticStone Deals – You can tell the site is well-optimized from how quickly pages render.
карнизы для штор купить в москве http://prokarniz36.ru/ .
brightcoastgallery – I appreciate how simple and uncluttered the interface is, makes decision-making easier.
smilecorner – Smooth browsing, intuitive interface, and items are clearly presented.
залив квартиры судебная экспертиза залив квартиры судебная экспертиза .
timber hub – Items loaded quickly and categories were easy to navigate.
Silver Moon Corner Finds – Pleasant browsing experience with intuitive navigation.
glowingridgehub – Navigation was smooth and intuitive, made exploring categories a breeze.
он спонсировал всех нас. https://neuro-deti.ru Почему ушли из РБ?купил его в аптеке
филлеры москва оптом https://filler-kupit.ru .
Магазу мир и процветания)) https://pls-university.ru Я вообще не курю!!!я брал 3 июля его уже нет в продаже!есть что почитат
True Horizon Selection – Browsing is quick, and items are visually appealing.
bright lakes link – Browsing was smooth and the overall presentation looked tidy.
hillcornerlane – Products are neatly categorized, making shopping effortless.
chemical-mix.com держи в репу, заработал.. пазитивно всё.. тут всё хорошо.. обращайтесь помогут быстро.. https://i-tomat.ru А вот это да, магазин последнее время реально что то “плохует” мягко говоря, но все ровно же хорош”Выстовляет Эскимос список тестеров в Списке сверкает мой ник” “bob marli”
brightwillowboutique – Clean design and easy layout helped me find interesting items fast.
Iron Valley Treasures Hub – Simple design and clear product images made browsing stress-free.
качество интересует купить скорость, кокаин, мефедрон, гашиш Ищи в соседней ветке мой отзыв по рцс. ИМХО рцс не для торча.Ребят, магазин ровнее ровного. Если есть какие то сомнения, например, нарваться по кантактам на фэйкоф, обращайтесь на прямую к ТС. Написать ЛС 100% все будет исполнено в лучшем виде. Скорость доставки товара просто удивляет, конспирация, и выбор курьерки, залог вашей безопасности, у ТС это приоритет. Все на высшем уровни. Реагент качественный, минимум побочек максимум пазитива. Если вы все-таки решитесь, сдесь прикупиться, вы забудите и думать, где бы вам затариться снова. Не проходите мимо. То, что вам надо, тут.
Dream Big Hub – Discover inspiration and strategies to pursue your goals with confidence every day.
Снова всё на высоте)заказывал 2 г тусишки!попросил пробник 5МЕО) получил))))))))) https://megavata.ru но только если мусора захотят найдут. просто мусора еслиб хотели найти , то давно бы уже посыль пришла с сопровождением.все ровно,продукт качественный не знаю что у вас было.делал 1 к 10. получилась на убой))
rusticridgeboutique – Pleasant browsing experience, items are easy to view and site feels well structured.
электрокарнизы для штор купить http://prokarniz36.ru .
BrightMoor Collection – Very organized pages, which made finding items simple.
MidRiverDesigns Storefront – Easy navigation and tidy displays improved shopping flow.
затопили квартиру что делать затопили квартиру что делать .
Whitestone Emporium – Browsing was comfortable and products loaded quickly.
shopcornerhub – Pages load fast, navigation is simple, and exploring products was enjoyable.
филлеры москва оптом http://filler-kupit.ru/ .
Shop With Ease – The comfortable and smooth user experience was a standout feature.
отзывы ждем https://neuro-deti.ru все гуудв академе были пролёты
modern corner – Browsing flowed smoothly and items were easy to locate.
urbanfashionlane – Clean interface with clear product display makes shopping effortless.
brightfallstudio – Enjoyed browsing here, items seem well curated and easy to explore.
магазин отличный ! работает уже не первый год! обращайтесь! https://glossgirl.ru Братва после покупки не забываем писать отзывы.Я неделю вторую жду треккогда заработает
silvertrendhub – Well-structured layout and tidy product sections, shopping felt natural.
Soft Feather Finds – Easy-to-use interface and well-arranged products made shopping simple.
в академе были пролёты купить скорость, кокаин, мефедрон, гашиш Да долго работают! :good:с самого начала)добрый день форумчане!)
bright haven shop – Browsing was smooth and items were easy to find.
Silver Moon Outlet – Clean interface and easy menus made browsing smooth and stress-free.
карниз электроприводом штор купить prokarniz36.ru .
Тоже хочу сделать заказ.Жду ответа купить Мефедрон, Бошки, Марихуану Всем привет. Первый раз беру товар у этого магазина. По треку моя посылка поступила в курьерку в понедельник и до сих пор не была отправлена. Каждый день в информации по трек номеру дата отправки переносилась. О СПРС давно уже легенды ходят, я не понимаю почему магазин сотрудничает с ними.Хороший магазин тоже не раз уже к нему обращался я считаю что этот магазин достоин огромного внимание ! Мир тебе бро и процветания удачи в работе !:ok:;)ОБРАЩУСЬ ЕЩЕ К ТЕБЕ БРО ОБЯЗАТЕЛЬНО !) ЕЩЕ РАЗ УДАЧИ
everstonecorner – Great user-experience overall, felt smooth and well-structured from start to finish.
оценка ущерба после залива оценка ущерба после залива .
parxs casino
References:
http://night.jp/jump.php?url=http://community.srhtech.net/user/petherbmqp
softmeadowstudio – Browsing here was convenient, layout helped me quickly locate items that interested me.
createhub – Easy to move through categories, and all items are clearly displayed.
Visit PineHill Studio – Simple structure and clean pages made browsing easy and comfortable.
ахахах я больше параноил за rcs 4 пришло сделал к 5-7 послушал таких отзывов за неё , курнули я аш охуел , прет норм минут на 30-40 , растворилась вся вообще в муравьином спирте , торкнуло сильно мне даже показалось лучше 250 купить Кокаин, Мефедрон, Экстази магазину желаю дальнейшего процветания и минимум траблов(а лучше вовсе без них).?Метод употребления – интерназально
Sunny Slope Corner Picks – Smooth and intuitive navigation makes shopping enjoyable.
магазин филлеров москва http://www.filler-kupit.ru/ .
click to browse – Navigating around was effortless and items stood out clearly.
peaceforestcorner – Clear interface, items are neatly displayed and easy to explore.
This Cozy Shoppe – The appealing displays and uncluttered pages created a truly pleasant experience.
boutique corner – Tidy pages and clear sections made finding products simple.
Shop EverduneGoods – Browsing was simple thanks to the tidy structure and well-organized categories.
всем добрый день брали 200гр тут всё на высшем уровне подробное описание 5 фоток + геоданный клад был поднят в касание место укромное тихое качество продукта вышка! советую всем брать у Чема ! https://zavod-arm.ru , обычно мин 20-40спасибо магазу)
DeepBrook Picks – The organized layout and product clarity made finding items fast.
А вот и мин Трип мой. https://risemanager.ru возможно мои письма рубятся где-то? там все четко по делу.Пиздатый магазин, всегда пойдут на встречу и оператор норм
allegany casino
References:
http://www.tellur.com.ua/bitrix/rk.php?goto=http://support.roombird.ru?qa=user&qa_1=laineijkx
wild picks hub – Fast-loading pages and organized layout made shopping effortless.
Вообщем маска (конспирация) на высоком уровне, что на прямую влияет на мою безопасность и на тех кто пользуется услугами данного ТС, это радует. купить Кокаин, Мефедрон, Экстази Надеюсь на дальнейшее сотрудничество с магазином!Хочу выразить благодарность менеджерам данного магазина.
Moon Haven Hub Online – User-friendly interface and neat presentation made product discovery smooth.
не болела чтоб башка. купить Мефедрон, Бошки, Марихуану Это да,но всё же я очень переживаю,ну прям очень оченьИ ещё когда можно будет сделать первый заказ в январе?
autumnstonecorner – Browsing categories felt simple and organized, nothing felt cluttered or confusing today.
urbanwildroot – Browsing felt smooth and consistent, all categories were easy to explore without confusion.
coastalmistshop – Smooth browsing and a clear layout made finding items effortless.
shop wave – Clean layout and responsive pages made finding items simple.
народ скажите концетрацию 250 го в этом магазе https://stanki-tvch.ru я вот тоже дождался и пришел ко мне груз ценный)) завтра поеду забирать, потом отпишу что и какДа хорошо бы было, сегодня уже получу трек. Но конечно напугали всякие кому типа ам плохой пришёл.
Timeless Harvest Showcase – Clear visual hierarchy and easy navigation enhanced the browsing experience.
Urban Vibe Shop – The variety of items is impressive, and moving around the site is seamless.
silver selections – Everything loaded fast and the professional layout kept the experience smooth.
Wild Coast Studio Hub – Smooth browsing and neat product display allowed for easy shopping.
sagehaven – Fast-loading pages and neatly displayed products, made shopping simple.
Приветствую всех! купил 0,5 кокса. Закинул деньги, получил адрес, приехал забрал, все на высоте! Кладмену отдельное спасибо, спрятал так что не доебаться. Качество просто улетное, и от меня и от друзей огромный плюс магазину. https://artelm.ru Отличный,ровный МАГАЗ!то есть у вас все по прежнему и сайт работает?
FashionEliteHub – Great selection of items, shopping was effortless and enjoyable today.
LifestyleTrendsOnline – Really interesting content, very appealing and easy to explore.
Everfield Home Goods – Smooth browsing experience with neatly arranged items throughout.
shop moon star – Well-organized interface and fast pages made exploring effortless.
Самое главное что на свободе фиг сним с грузом! Задумайтесь ребят может пора сесть на дно, чтоб палево отвести! купить онлайн мефедрон, экстази, бошки А почему сам с-м.сом сюда какой день не кажеться…?Списавшись в ЛС с ТСом обговорив условия сделки провел оплату в БТЦ.
BrightMoor Online – Quick and easy browsing with all products easy to locate.
Sun Crest Collection – Well-laid-out products and structured pages made browsing fast.
Писал уже, магазин работает в турбо режиме отправки вовремя, получают люди вовремя, сменили штат сотрудников сменили курьеров которые тупили, все налажено все как должно быть. https://byfreya.ru сердцебеение крч все как обфчно , вПарни, начинается параноя! Завтра посыль приходит, как получать А?
lunarmarketcorner – Products are well categorized, making browsing intuitive.
По репе получил! Еще раз увижу безобразный флуд во всех ветках, будет тебе БАН! купить кокаин, меф, бошки через телеграмм Я тебе уже в джаббере обьяснил как употреблять надо, а ты двоим .м дал, они вьебали все залпом и нихера не поняли, ты уже кипишь наводить начал. Эта СК не тот бутор к которому все привыкли, от которой слюни текут и на люди показываться нельзя. Её надо употреблять с минимальной дозой а не 0.3г в один заход. Доза 0.05-0.09гМагазин высшего уровня своей работы.
everpeakcorner – Clean interface and clear product display helped make browsing smooth and easy.
shop emporium – Items loaded quickly and the layout made navigation simple.
harvest hub store – Loved the professional feel and smooth flow while exploring the site.
Вы не могли сегодня оплатить заказ, потому что мы сегодня не работаем https://partner-tgn.ru Подскажите. Если сейчас сделаю заказ и оплачу сразу, завтра товар отправят?chemical-mix.com держи в репу, заработал.. пазитивно всё.. тут всё хорошо.. обращайтесь помогут быстро..
Rustic River Finds – Quick loading times paired with inviting visuals made the experience enjoyable.
Soft Leaf Finds Hub – Simple design and well-arranged items allowed for fast and easy browsing.
я думаю все ровно будет. заказал тут для пробы 5 гр. акв 48 ф . 10 октября еще заказал. еще не выслали. на почту пишут, извиняются. ждём результатов. как будут движения отпишу. https://service680269.ru ну что,сказать все на высшем уровне!!Если кто-то когда-то пробовал банки с Рафинада на тусиае, тот знает, как классно они перли и понимает, каких эффектов я ожидал.
FashionVibeHub – Great collection of items, exploring them was simple and fun.
studio marketplace – Items loaded fast and the interface feels intuitive.
TrendyLifeWorld – Engaging content and fresh ideas, browsing was enjoyable.
Lush Finds – Navigation is straightforward, and I could locate items without any hassle.
Your Next Discovery – The site’s ease of use is its best feature, thanks to the logical categories.
может стоит разводить 1 к 10? Кто брал ам 2233 отпишитесь на щёт пропорции,вообще 2233 1 к 20 разводится если продукт хороший купить Кокаин, Мефедрон, Экстази я не согласен предыдущем коментариям ,беру не первый раз ,на данный момент магазин самый охриненный ,всегда качество товара радует,всегда на связи они,они не когда не морозятся,своё дело знают чётко,нахрена им кидать ,они не будут портить свою репутацию какую уже заработал этот магазин,я беру поболее и меня не разу сдесь не кинули .процветания магазину .спасибо за вашу работу,что всё чётко и быстро И радуете вкусняшками.а ещё хочу добавить ,возможно это кидаки или канкуренты и пишут разную х….ю что бы сбить новичков ,Но мы кто всегда с вами знаем что магазин лучший и другого Нам НЕНАДО.Так держать ,МЫ ВСЕГДА С ВАМИ!!!Респект Магазу
электрокарнизы купить в москве provorota.su .
электрокарниз купить http://elektrokarniz2.ru/ .
Первый раз слышу такой непонятный отзыв о 4фа,все кто берет его как и 2c-i говорят что у нас он лучший … по jte907 если не умеете с ним работать зачем берете…? есть постоянные оптовики кто берет только его, и этот продукт нареканий не вызывает. Многие “Селлеры” под видом jte продают 2201 и это факт! у нас этот продукт в оригинале. МХЕ у нас такой пришел, мы не кричим что его чистота 99%, и что качество его не очень мы предупреждали всех… https://partner-tgn.ru Сам магаз работает хорошо все в сроки, консперация тоже на высшем уровне)привет бразы всех спрошедшими праздниками получил седня посыль все порадовало и качество и бонус:p:D:D:Dприложеный за ожыдание спосибо магазу
электрокарнизы в москве электрокарнизы в москве .
cloverhubemporium – User-friendly interface, shopping flows naturally and comfortably.
brightvillagecorner – Items look appealing and layout feels user-friendly and welcoming overall.
leaf hub – Smooth layout and organized sections made browsing effortless.
ам нормальная альтернатива 307.советую 1к15 купить онлайн мефедрон, экстази, бошки магаз работает???кто-то пляшет, кто-то дрочит,
find styles – The sections were easy to get through, and the products were displayed in a clean, eye-catching way.
TallPineEmporium Goods – Pages loaded quickly, and products were easy to locate.
Fresh Pine Boutique – The site feels tidy, and items load fast, making selection easy.
meadowtrendhub – Well-structured pages with easy navigation, shopping was hassle-free.
авиатор ван вин авиатор ван вин
Visit Soft Blossom Studio – Pleasant visuals and a gentle interface made navigation smooth and easy.
sunlit picks hub – Fast pages and organized layout made exploring effortless.
Отдельный разговор с одной посылкой когда человек менял свое решение и то соглашался ждать посылку, то требовал вернуть деньги. купить кокаин, меф, бошки через телеграмм Хорошо работают реально ! ! ! рега МН-35ф реально индика суровая , наиболее множество сходств нашёл с натуралом , по Мне так это наиболее приближенный каннабиноид ..Я в последний раз говорю, эта тема – для отзывов о работе магазина. Если вы не можете связаться с продавцом, то не надо писать об этом по сто раз. Если вы хотите узнать о качестве продукции – вам СЮДА !!! Любой оффтоп\флуд прекращаем !
Harbor Finds – Shopping was fast and enjoyable thanks to the intuitive design.
QuickBuyOnline – Found exactly what I needed, the process was effortless and smooth.
карниз электроприводом штор купить provorota.su .
карнизы для штор купить в москве https://elektrokarniz2.ru .
Сегодня получил посыль! В супер упаковке! https://realsport-club.ru Всем привет ну что ж в очередной раз заказал всё пришло всё ровно грамотно и сделано чисто.3случая за последние 2недели.. если быть точнее..
Анонимный kraken darknet marketplace функционирует с 2020 года без единого exit scam, обеспечивая стабильную работу и защиту средств всех пользователей.
Shop Here Now – It’s so simple to explore the large inventory with this well-thought-out interface.
карниз электроприводом штор купить http://www.elektrokarniz98.ru .
stone corner – Clean design and smooth scrolling enhanced the shopping experience.
LivingTrendsMarket – Loved the variety of products, very smooth and enjoyable shopping.
leafwildcornerhub – Products are displayed clearly, making browsing fast and enjoyable.
мне менеджер сказал, что у другого спросит по поводу мхе и выдаст компенсации. https://quick-step56.ru братишки и сёстры всем мир и харе ругаться!жизнь прекраснавсе как обычно работает
browse items – Navigation was smooth and the overall setup felt clean and simple.
quality finds – Felt good exploring the site since everything was neatly arranged and quick to load.
Сорь за многобукав, не попустило еще 😉 купить скорость, кокаин, мефедрон, гашиш Не рекомендую правда увлекаться порохами – их хочется ещё и ещё и в итоге не так уж и просто слезть с марафона…) Но это уже ваше дело ; )Как товар господа?
Lush Grove Market – Easy-to-use interface and neatly arranged products made shopping simple.
soft summer collection – Fast-loading pages and organized layout made browsing pleasant.
Все заказ пришел, не было времени отписаться, брали пробы, в аське вежливый,конкретный, все в сроки,просил отправить в день перевода денег, отправили, шла ровно 4 дня, как написанно на сайте, веса точные, не обманывают, все порадовало, консперация на высшем уровне, правда расчитывал на лучшее качество, мало держит, консентрация 1 к 6-8 самая лутая.. Огромное спасибо магазину, мир и процветание, выбераю чемикал микс) Всем мир друзья.. https://lada-21.ru Бро как с тобой связатся это ярослав мудрый.с чего ты взял что мы соду “пропидаливаем”?, если есть какая то проблема давай решать, про “шапку” вы все горазды писать в интернете…
Wild Ridge Picks Online – Easy-to-use interface and neat pages made browsing enjoyable.
MoonView Picks – The layout felt inviting, and browsing through items was smooth and straightforward.
ShopWithJoy – Love the deals offered here, prices are fair and shipping was fast.
PureLeafEmporium – Items appear high quality, checkout was fast and everything worked perfectly.
http://rollexroleplay.moibb.ru/viewtopic.php?f=2&t=1921
У нас у отправки случился форс-мажор. Только на этой неделе начинают отправлять. Извиняюсь от лица магазина за задержку. купить Кокаин, Мефедрон, Экстази Он тоже не работает, его ветки нет в РБ разделе.Вот это я понимаю СЕРВИС:ok: Превзошло все мои ожидания, доставили раньше обещанного… Магаз ровный (до последнего сомневался, что всё на столько гладко…)
электрокарниз http://elektrokarniz2.ru/ .
электронный карниз для штор http://www.provorota.su .
EasyPickCorner – Navigation is intuitive, everything is clearly arranged and easy to find.
BrightGroveHub Products – Clear categories made browsing feel natural and convenient.
http://www.metallica.ru/forum/post.php?mode=post&f=2345
http://sport.taminfo.ru/news/tennis/page,1,5,210-plan-grafik-raboty-stazhirovochnoj-ploshhadki-po-napravleniyu-rasprostranenie-organizacionno-pravovyx-modelej-po-profilaktike-socialnogo-sirotstva-v-tom-chisle-vtorichnogo-podgotovka-kandidatov-v.html
cloud boutique – Clean layout and intuitive navigation made shopping simple.
Заказали 2c-i и 2c-p. Как придет в магазине появятся позиции. может и еще что привезут из заказанного курительного. купить кокаин, меф, бошки через телеграмм Оплатил, жду.работал с данным магазином, и по сей день работаю!!! отличный… сегодня посылочка только пришла! товар отличный особенно CHM 100.. спасибо за качество!!
wavehubcollective – Items are clearly presented, making browsing quick and pleasant.
прокарниз http://www.elektrokarniz98.ru .
wild access – Fast-loading site and tidy layout made shopping simple.
top picks store – It felt smooth navigating around; everything was placed logically.
Согласен магазин хороший, знают свое дело! купить Мефедрон, Бошки, Марихуану заказ в статусе обработки )))с искреннем уважением к вам!
Savanna Online Market – Products looked attractive and navigating through categories was effortless.
Coastline Treasures Hub – Clean design and well-arranged products made shopping fast and easy.
TrendSpotUrban – Browsing was simple and the variety of products is fantastic.
honeststylecorner – Easy-to-navigate sections with clear listings, shopping was very pleasant.
Работал с данным магазином Совсем давно, и что то все руки не доходили оставить отзыв о магаз:D https://roll-n-roll.ru у нас она валяется,сами не потребляем.Упаковано и расфасовано все в лучшем виде! За неделю взял 9 адресов подьем 100%. Ск оч.радует
misty hub link – Clear layout and tidy categories made browsing enjoyable.
Sage Mountain Hub – Intuitive structure and logical menus made finding items easy.
1к 10-ти слабовато будет 1к5 или 1к7 самое то… https://dety-cvr.ru заказ оформил – жду посылочки ^^а чё заказал? Прикольный сайт, ассортимент радует :)?
EverForest Design Shop – Great variety of items, and the site navigation felt smooth and effortless.
https://www.ielts-mentor.com/files/pgs/1xbet_promo_code_bangladesh_10.html
да магаз отличный.оперативно работают.и качество товара отличное.вобщем всё хорошо. https://vseofiltrah.ru А я так понимаю, что у данного магазина просто не мало оптовых покупателей, и им уделяется больше внимания.Сам ты не общительный ))
stream store – Well-arranged items and clear layout made exploring simple.
EmpowerYourselfToday – Motivating ideas that help you grow and discover daily.
http://npar.ru/wp-content/pgs/melbet_promokod_pri_registracii_bonus_besplatno.html
brightstonemarket – Very organized design, shopping is comfortable and efficient.
рулонные шторы на окна москва http://www.rulonnye-shtory-s-elektroprivodom499.ru .
рольшторы с электроприводом рольшторы с электроприводом .
Если неактуальные сообщения выше, откорректируйте сами. По компенсациям, если останутся вопросы после получения посылки, пишите в новом году, размер зависел от веса, длительности, индивидуальных переплат на счета и прочих обстоятельств. :ok: купить кокаин, меф, бошки через телеграмм Всем привет! Хороший магазин. Удачи и развития в дальнейшем!заказал вчера на пробу соточку мн. по прибытию отпишусь)
timber store – Products load fast and the categories are easy to navigate.
нв секс
market picks – Browsing felt natural and easy thanks to the simple, tidy design.
Wild Meadow Essentials – Simple navigation and visible products allowed for easy selection.
почитайте реценты , там ниже тема есть , там куча всего купить кокаин, меф, бошки через телеграмм на icq – в четверг обещал трек, в пятницу обещал трек, пропал…Доброго времени суток Всем порядочным форумчанам-кто здесь заказывал,но трек так и не бьёться,или я один такой закинул 45к+доставка,и”жду у моря погоды”В скайпе вчера отвечали сегодня-игнор!
Ever Crest Woods Selection – The way categories were set up made browsing calm and efficient.
жалюзи автоматические цена жалюзи автоматические цена .
pine store – Well-arranged products and clear layout made browsing pleasant.
Самое интересное: https://medim-pro.ru/spravka-khti-kupit/
Дали трек… думаю все норм придет купить кокаин, меф, бошки через телеграмм The Best!!!!!!мы и в скайп и в аське
ExpandYourMind – Pleasant online shopping experience, very smooth flow and clear menus everywhere.
GlobalDealsTrend – Very quick ordering process and excellent promotions.
FashionForLife – Loved the stylish selection available, browsing was smooth and effortless today.
Silver Maple Shop – Smooth browsing experience with well-organized products.
Вчера оплатил, сегодня получил бьющийся трек. Так что все норм. Разговор в скайпе длился 30мин, я оплатил и через 2 часа мне уже выслали посылку. Осталось проверить кач-во фашки. Если все норм, сработаемся с конторой. https://ucec2012.com Взяли у ТС 10тку MN-40, вполне довольны всё прошло хорошо качество на высоте, единственное произошла запара с кладом 2рой раз нам не могут заложить там где нам нужно, приходиться ездить очень долеко надеюсь для постоянного клиента так не будет впредь, работаю с ТС уже год всё ровно и всем доволен!Да стопудова честный!!! В этом нет сомнений. А вот с волей Медведя и планом Путина ужиться сложно
wave hub link – Smooth interface and organized products improved browsing.
Autumn Mist Essentials – Soft colors and tidy structure gave it charm, while item details were easy to read.
согласен чемикалы в этом плане молодцы купить Кокаин, Мефедрон, Экстази Ребят подскажите что лучше взять:)желательно с пропорциями и качеством по временитак я там всем давно ответил ты пишешь с опозданием. Зайди почту проверь.
softleafcorner – Clean layout, shopping feels effortless and enjoyable.
BuySmartCenter – Affordable and excellent quality products, extremely pleased.
электрические жалюзи на окна электрические жалюзи на окна .
рулонные шторы на большие окна рулонные шторы на большие окна .
sunridge portal – Products load fast and moving through sections is effortless.
design picks – Loved the atmosphere of the site; the product displays were crisp and easy to follow.
так-то уже четверг бро купить Мефедрон, Бошки, Марихуану отличный магазин! + емуХОРОШО СВЯЖЕМСЯ КОГДА ПРИЕДУ ДОМОЙ Я НА ПРИРОДЕ ДАВЛЮСЬ ПИВОМ А МАГАЗИНЕ НАПИСАНО ЧТО ОТПРАВЛЕН MXE
Lunar Wood Studio Hub – Organized pages and responsive design helped me shop comfortably.
мастерские ремонт ноутбуков
мастер по ремонту телефонов[/url
ремонт компьютеров рядом
норм. Все кладки нахожу без проблем… взял белого и…охуел!!! https://economic-info.biz Что ж ты такой нетерпеливый… ))да и оперативность У ВАС на ВЫСШЕМ :superman: уровне!!
moon boutique – Clean layout and organized categories made shopping pleasant.
harborstylehub – Clean layout with tidy product listings, shopping was simple.
жалюзи автоматические цена жалюзи автоматические цена .
Приветствую. Хотели бы предложить вам сотрудничество по опту, по очень низким ценам 180т за 1 кг скорость и реагент, мы с форума легалрц больше 3 лет в ветках доверенных магазинов если заинтересует напишите сюда. , делаем кладом , вот ссылка на нашу ветку //legalrc.com/forums/mix/ контакты можете сверить из подписи купить онлайн мефедрон, экстази, бошки бро много кидков, очень много покупай у проверенных магазинов (это которые на главной странице), а не у пользователей, и в чате не вздумай покупать только у ПРОВЕРЕННЫХ я серьезно!!! кинутЗолотые слова.
PureChoiceOutlet – Found nice items quickly, checkout worked flawlessly and service seems dependable.
PerfectBuyZone – Really impressed with product variety, site feels clean and easy.
TrendOnlineSpot – Nice design with clear categories and smooth browsing experience.
gold collection hub – Fast pages and tidy layout made exploring products pleasant and quick.
GrowthBeyondBorders – Inspiring ideas that push you to learn and grow continuously.
Explore DreamHavenOutlet – The product variety and clean design improved the browsing feel.
Отличный магаз! так держать купить онлайн мефедрон, экстази, бошки по заказу?)Моментально: реквизиты, оплата, подтверждение получения. Все.
brightoakboutique – Clean interface, products are easy to locate and explore.
рулонные шторы на электроприводе рулонные шторы на электроприводе .
рулонные шторы на окна москва https://rulonnye-shtory-s-elektroprivodom.ru/ .
заказала в этом магазе сувениров:), посыль пришел на 3ий день, продукты качеством вкусны купить онлайн мефедрон, экстази, бошки Заказывал у этих ребят 203 и 5-IAI, качеством доволен. Заказы они оформляют долго, но зато отправляют быстро. Мне отправили в день оплаты!Всем привет ну что ж в очередной раз заказал всё пришло всё ровно грамотно и сделано чисто.
EverHollow Showcase – Navigation was quick, and the categories were grouped in a very user-friendly way.
clean design shop – The clean visuals and quick response time made browsing enjoyable.
forest access – Clear interface and smooth browsing made finding products effortless.
wildgroveemporium – Items are well arranged and navigation feels intuitive — nice overall experience.
Отдельный разговор с одной посылкой когда человек менял свое решение и то соглашался ждать посылку, то требовал вернуть деньги. https://gashrei.cc Магазин супер)бро ответь своим частым клиентам, распиши что да как) уже соскучились очень
future finds hub – Browsing was intuitive and products loaded quickly.
жалюзи автоматические цена жалюзи автоматические цена .
какие то траблы ппц =\ https://ucec2012.com Общий итог:Магазин достоин внимания!! цены сладкие)))
бездепозитные бонусы в казино с выводом без пополнения
Crest Finds – Everything was laid out nicely and browsing felt natural.
Почему закрылся представитель в петрозаводске? Жду ответа чем) купить кокаин, меф, бошки через телеграмм спасибо ответили…. доволенПтичка в клетке, в касание! Рад вас видеть и в телеге.
https://www.behance.net/onlineservice28
заказала в этом магазе сувениров:), посыль пришел на 3ий день, продукты качеством вкусны купить Кокаин, Мефедрон, Экстази я вчера связался с менеджером в аське, тот сказал что если ему отпишут – разберётся… Попробуй напиши днём, а не под утро )Зато искать долго не пришлось наверное???!
leafsilveremporium – Very user-friendly interface, shopping is smooth and comfortable.
DealHunterOnline – Discounts were easy to check side by side thanks to the tidy arrangement.
DeterminedSteps – Practical and uplifting content, easy to apply in real life.
highland goods – Pages were easy to navigate and items looked appealing.
может стоит разводить 1 к 10? Кто брал ам 2233 отпишитесь на щёт пропорции,вообще 2233 1 к 20 разводится если продукт хороший https://teploceramic.biz А менеджер не ответственный а облом. Я бы пошел навстречу клиенту, получил бы от него этот стольник себе на мобилку и доплатил бы на Альфу его сам, раз у потенциального клиента проблемы с переводами. А он обломался.РОВНЫЙ МАГАЗ!!!УСПЕХОВ И ПОЗИТИВНОГО РАЗВИТИЯ!!
BrightPetal Designs – Well-laid-out pages and good images made choosing items a breeze.
EverWillow Collections – Friendly design and easy-to-navigate sections made the visit pleasant.
https://mcyportal.mosti.gov.my/launch-of-one-year-report-and-national-technology-and-innovation-sandbox-ntis-v2-0-website/uncategorized-en/
https://preschool.nafa.edu.sg/happenings/performances/faith-divya-moey-anna-van-praet-class-of-2015
https://paladarplus.es/pgs/codigo_promocional_melbet_bono_vip.html
shop stone gallery – Clear interface and smooth scrolling made shopping simple.
a href=”https://pureforeststudio.shop/” />pureforestlane – Organized sections and clean interface, browsing was easy and relaxed.
LunarBranchStore Finds – Navigation was simple, and the products were displayed nicely.
Не знаю как в этом магазе,а вот у всеми так уважаемой Мануфактуры тоже весной всплыло такое гавницо.В результате я попал на 50к и никакого возмещения от них не дождался между прочим. https://rentonminuto.com Да туси тут очень качественная, жаль что заказать проблемно.задержки очень большие! это плохо, надо вам как то решать этот вопрос
акрилатная инъекционная гидроизоляция inekczionnaya-gidroizolyacziya.ru .
Магаз качественный ни разу не подводил!!! https://krishna-vijayaraghavan.com “Приезжаю к месту,вижу дом обхожу кооператив который мне нужен (ну я так думал)”када тусишка появится????
Free video chat http://www.emerald-chat.app find people from all over the world in seconds. Anonymous, no registration or SMS required. A convenient alternative to Omegle: minimal settings, maximum live communication right in your browser, at home or on the go, without unnecessary ads.
Оставляйте свои отзывы! Мы ценим каждого клиента нам важны ваши отзывы и мнения! https://ucec2012.com у них Methoxetamine бадяженный или нет? сколько принял мг и какие симптомы были?Да работает в асю обращайся если чё надо только товара мало там мхе да дмт
Golden Vine Finds – The layout is clean, and I could explore items without any hassle.
Motivation Route – Enjoyed the insights shared; everything seemed thoughtfully arranged.
SimpleBuyZone – Pleasant shopping experience, site design feels modern and user-friendly overall.
ReachHigherGoals – Items seem good quality, ordering felt straightforward and likely reliable too.
deltacottoncorner – Intuitive site structure, items are easy to locate and browse.
Ну так ведь и не делаем не чотка . всё сразу . https://kulonprogo.biz на мыло отвечаем только по существу, много не по делу пишут, ася или скайп быстрейПривет всем!
Soft Forest Picks – Clear layout and intuitive design allowed for simple and quick browsing.
BrainBoosters – Clear instructions and fun exercises, highly recommended.
UrbanStyleDeals – Appealing fashion choices and browsing through the site was effortless.
Все есть, объем большой https://the-gentlemens.com Зачем писать таким большим шрифтом ? Здесь слепых нет. То что тебя где то кинули к нам никакого отношения не имеет.Интересно как он себя покажет… даже не знаю как его разводить…
Shop MoonGrove – Pages opened instantly, and the layout felt clean and professional.
https://www.litteredtrash.com/blogs/5232/%D0%9F%D1%80%D0%BE%D0%BC%D0%BE%D0%BA%D0%BE%D0%B4-%D0%BA%D0%B0%D0%B7%D0%B8%D0%BD%D0%BE-MelBet-WAP777-%D0%B1%D0%B5%D1%81%D0%BF%D0%BB%D0%B0%D1%82%D0%BD%D0%B0%D1%8F-%D1%81%D1%82%D0%B0%D0%B2%D0%BA%D0%B0-100
https://u.osu.edu/commoditychainlululemon/manufacturing-2/#comment-38703
http://blog.vintagevixen.com/2011/12/why-are-mens-buttons-opposite-womens.html?sc=1764848323409#c5163497684079965855
https://snoopydirectory.com/listings959763/1xbet-promo-code-2026-130-signup-bonus
Все работает купить кокаин, меф, бошки через телеграмм Привет парни…Заказал тут 10-ку МНа..Ну, была задержка с отправкой,дней десять наверно…:fuck: Селлер сразу сказал про компенсацию:monetka:так что я особо не парился…Ну с посылки я конечно при.уел:confused:.18грам + конспирация:bravo:Товар достойный,…1к13 полчаса стабильно” на ура”:hello:Молодцы …порадовали таким подарком…:ok:Удачи в новом году..пиши в скайп, все работает, мне всегда отправляют, все на уровне
Отличный магаз! так держать купить Мефедрон, Бошки, Марихуану Что есть то естьблагодарствуюсь, бро)) под затупил малеха, вижу ты тут, все хорошо
Wild Spire Collection – Smooth navigation and well-structured pages made discovering items easy.
Motivation Route – Enjoyed the insights shared; everything seemed thoughtfully arranged.
EverMapleCrafts Goods – Items were displayed clearly, making the visit smooth from start to finish.
Взяли у ТС 10тку MN-40, вполне довольны всё прошло хорошо качество на высоте, единственное произошла запара с кладом 2рой раз нам не могут заложить там где нам нужно, приходиться ездить очень долеко надеюсь для постоянного клиента так не будет впредь, работаю с ТС уже год всё ровно и всем доволен! купить Мефедрон, Бошки, Марихуану Требуй возврата денег, я вам что пытаюсь донести? Обманывает этот магазин клиентов.Почитай мои посты по этому магазину.может стоит разводить 1 к 10? Кто брал ам 2233 отпишитесь на щёт пропорции,вообще 2233 1 к 20 разводится если продукт хороший
Spot on with this write-up, I actually assume this website wants far more consideration. I’ll most likely be once more to learn rather more, thanks for that info.
BrightLineCrafted Store – The website’s clean design made shopping really straightforward.
TrendStyle Online – Impressed by the variety; the site looked polished and easy to use.
очень неплохо было бы увидеть в магазине джив 307 https://joanncbastien.com доставка порадовала быстро качественно . насчет реагента который был указан 1 к 15 шас насайте он же стоит 1 к 10 такова говна еше не пробывал ( извените если кого обидел) 5 мин прет и все даже пролонгатор увеличил действие до 15 мин . за сам магазин нечего плохова сказать не могу брал раньше рега была отбойной и цены радуют … Но последния рега просто выкинуть что ли ее . сегодня попробую конечно 2 к 10 сделать если не поможет просто выкину ..Вчера оплатил, сегодня получил бьющийся трек. Так что все норм. Разговор в скайпе длился 30мин, я оплатил и через 2 часа мне уже выслали посылку. Осталось проверить кач-во фашки. Если все норм, сработаемся с конторой.
GoalExplorer – Encouraging posts and the site loads quickly and easily.
SmartValueVault – Great assortment with clean layout and intuitive navigation.
willowemporiumcentral – Smooth pages with intuitive navigation, shopping was quick and easy.
ModernStyleTrends – Loved the variety, fast and hassle-free ordering experience.
маскировка 5+ https://myotherhats.biz Всем привет, долго не писал, ну это меня «задержала» посылка jv-61. Все пришло, все получил причем довольно быстро все ехало:good:Он тоже не работает, его ветки нет в РБ разделе.
FashionTrendySpot – Nice selection of products and browsing was smooth throughout.
Silver Hollow Portal – Clean, stylish design with items that are clearly showcased and detailed.
Но бывали случаи и на оборот… купить Мефедрон, Бошки, Марихуану Не понял…Его еще варить нужно??? На плитке?))может ты просто сам не учел проценты комиссии и тебе не хватило???
Moon Glade Market – Items are displayed clearly, which made exploring simple and quick.
InspireGift Shop – Had a good time scrolling; the product ideas were fun and diverse.
магазину респект)) с корефанами накуримся вдоволь))) купить онлайн мефедрон, экстази, бошки Если во время действия паралельно потягивать пивас и почаще двигаться , не сидеть на месте , то довольно нормально прёт , если загоняться то накрывает параноя) , в общем около 8-9 часов прёт , но у меня была ещё и рега , очень лютая которой можно было запросто перебить параною если вдруг возникала от данной скорости , в целом понравилась скорость .В воскресенье заказал,в понедельни утром оплатил,в понедельник выслали,трек сразу дали,оперативно ребята +10 от меня в Репу вам:)
BrightPeak Corner – Well-organized pages and clear product pictures helped me select quickly.
магаз ровный!!! все на высшем уровне!!! работаю с ними много лет!!! купить Кокаин, Мефедрон, Экстази мне тоже все пришло. да и еще вещь нужную в хозяйстве подогнали. вы ребята вообще МОЛОДЦЫ. ВСЕХ БЛАГ ВАМ.Надеюсь на дальнейшее сотрудничество с магазином!
Urban Trend Deal Shop – Clean interface with plenty of stylish items to scroll through.
ExploreProspectsHub – Nice selection and moving through the site is easy.
ChicStyleVault – Great assortment of items, moving through the site was effortless.
PineCrestModern Portal – Everything was easy to access thanks to the neat page arrangement.
ну сегодня пыхнул час назад ….. приопустило……………… но еще норм не грузит https://goloka-fci.com Брал у другого магазина – полная Чляпа оказалась…блин… один заказ выбил, затестил. теперь опять в аське молчок
поддерживаю !!!! купить Кокаин, Мефедрон, Экстази Заливают паршивым вином.он спонсировал всех нас.
ModernStyleHome – Lovely home products, navigating the site was quick and straightforward.
Golden Ridge Market – Fast-loading pages and clean design made the browsing experience stress-free.
Attic Finds – User-friendly interface made exploring items enjoyable.
LearnSmartToday – Found useful learning materials and the site navigation was smooth.
ремонт экрана айфон
Данный Магаз Меня Кинул!!!! https://clapf.org Может всё-так “Рашн Холидейс” (c) ChinaКак то так.
ремонт и заправка картриджей для принтера
которые воспитанны на обычном Фене ! https://teploceramic.biz 16 числа заказала товарчика)ну пока еще ничего не получила!!! продаван отправил только половинку(объяснил что не хватило реактивчика) но все остальное вышлет как привезут 100ый ))ждем и надеемся)) заказывала и раньше в этом магазе все было ОГОНЬ))Готовыми работают
FashionExplorer – Wide range of products, moving through the site is effortless.
Urban Style Picks – Really liked the design, and the items were displayed clearly throughout.
ChicTrendSpot – Products are appealing, site feels modern and easy to browse.
Магазин работает ЧЕТКО… купить Мефедрон, Бошки, Марихуану Бро ты ошибся. Не поняли друг друга бываетСегодня на мыло пришло письмо с новостью что заказ отправлен и номер трека который бьёться:good: пока всё норм идёт, со мной связь поддерживают через скайп, игнора не было, когда получу отпишу за качество вес и тд
Expand details: https://telegra.ph/Facebook-akkaunty-dlya-biznesa-klyuch-k-uspehu-11-11-2
autumnlookhub – Fast-loading pages with intuitive navigation, shopping felt natural.
Modern Style Home – Clean visuals and efficient navigation helped make the visit smooth.
SkyBlossomCorner – Great variety of items displayed, site layout is clean and easy.
Уже заказывал и получил chm-100 и chm-400 всё ровно) https://skygrid.biz Успехов Вам всё ровно )сегодня закажу 1г. MN-011 для пробы)посмотрим на товар)
ShadyLaneShoppe – Loved the selection here, browsing felt smooth and site looks clean.
Какие у тебя претензии? ты провокатор и не более т.к. ты не дал даже номер заказа и не высказал притензию, к тому же за тебя мне уже написали в Личку, другие магазины.. https://aledoyprojects.top Оплатил 28 января это был вторник, продавец сказал отправки в течении 2х дней…Что именно вам непонятно? всегда есть личные сообщения куда можно написать.
Soft Pine Treasures – Well-organized pages allowed for fast and pleasant exploration.
Soft Summer Shoppe Store – The soft, airy design created a welcoming and pleasant browsing experience.
SunlitValleyMarket Catalog – Everything was easy to find thanks to neat arrangement and design.
Кто под нос что-то бормочет, https://panama-real-estate.biz Да че тут разбираться,ты видишь смысл?!На прошлой неделе в среду, был оплачен заказ, вот уже среда следующей недели, праздники прошли, в скайпе они пока что не появлялись. Пологаю что магазин загулял.
KnowledgeDailyOnline – The articles were well-written, and navigating the site was quick and easy.
https://byizea.fr/js/pgs/?code-promo-1xbet_12.html
https://medium.com/@19minuts/melbet-promo-code-2026-zevs777-100-bonus-84a9787c2a5d
https://www.reddit.com/user/Leading-Survey305/
ChicDiscover – Stylish products are well-presented and the checkout process is smooth.
https://www.skypixel.com/users/djiuser-vxnyjh8f9gqi
Next Adventure Picks – Fun and engaging selection, and browsing through items was simple and smooth.
Хочу выразить свою благодарность за представленную пробу! https://boshkitopdim.me “Решил Попробовать Записаться”Ну теперь к самому главному – качество!
LivingDiscoverSpot – Products are attractive, site layout makes moving through pages easy.
Urban Trend Store – The shop felt organized and everything loaded promptly while browsing.
Качество и работа магазина на высоте!! купить скорость, кокаин, мефедрон, гашиш Магазин работает ЧЕТКО…Магазин,лови от меня большой и жирный “+”. Заказ пришёл в течение 3ёх дней.Из-за обстоятельств пришлось разбодяживать порошок в ацетоне,в подъезде,на хз сколько граммов основы…но все понравилось.все и всем довольный.
Всё отлично, 5 из 5. Только сделайте больше районов в Питере. купить Мефедрон, Бошки, Марихуану Всем привет !!!Тут четкий кристал ! Давно мне нравиться работа данного мага. Спасибо !
CreativeValueHub – Very satisfied exploring this store, layout neat and navigation intuitive throughout.
Все пришло, все хорошо! Конспирации такой не ожидал))) Сначала подумал что киданули)))))) Попробовал и все около дела, хороший средний микс получился. Буду брать больше на днях… купить кокаин, меф, бошки через телеграмм По прошествии полутора часов снова вылез джаббер. Малегькая накладка – курьер занят сильно, обещал к 23м сделать (было 21 на тот момент). Да не вопрос 😉 Джаббео выверен, оператор душевный человек, располагает к себе сразу.Chemical-Mix, хочу заказать 50г. АМ, но на сайте написано что 50грамм нет на складе.
DailyEssentialsSpot – Nice design, very straightforward to use.
BrightStyleCollection – Loved the stylish items, site feels modern and browsing was smooth.
a href=”https://evertrueharbor.shop/” />EverTrue Access – Straightforward layout and clear categories made browsing comfortable.
FreshFindsShop – Loved the range, everything loaded quickly.
В предыдущих сообщен писал, что заказ по совместке от ЧМ, https://kokainkypit.biz спасибо вампривет бро)) чето какой то засланый казачок тут про запр дживы интерес проявляет…
новые бездепозитные бонусы в казино за регистрацию с выводом без пополнения
Hot Trend Deals – Fast site with plenty of eye-catching pieces to explore.
UrbanTreasureSpot – Great assortment, navigation felt intuitive and fast.
Bright Pine Fields Hub – The clean arrangement made scrolling through categories simple.
Style Collection Point – Items are displayed clearly and moving around the site is pleasantly simple.
noblecraftlanehub – Clear layout and neatly displayed items, browsing was very easy.
InsightTodayHub – Everything ran fast, and the content was organized in a logical way.
Заказ пришёл, все ровно) купить кокаин, меф, бошки через телеграмм Ответил) просто не сразу увидел в вашем сообщении дополнительный вопрос )Ребят, магазин ровнее ровного. Если есть какие то сомнения, например, нарваться по кантактам на фэйкоф, обращайтесь на прямую к ТС. Написать ЛС 100% все будет исполнено в лучшем виде. Скорость доставки товара просто удивляет, конспирация, и выбор курьерки, залог вашей безопасности, у ТС это приоритет. Все на высшем уровни. Реагент качественный, минимум побочек максимум пазитива. Если вы все-таки решитесь, сдесь прикупиться, вы забудите и думать, где бы вам затариться снова. Не проходите мимо. То, что вам надо, тут.
магазин хороший,даже если высылат брак (было 1 раз) возврат делают сполна https://mefedronns.biz с туси тут не прогадаешь)))Менеджер на связи с 10-11 утра по МСК (не с 8-ми, как Вы ломитесь) ежедневно, кроме праздников и выходных. На сайте Вашего заказа нет. Можете назвать его номер?
ВСЕМ САЛЮТ!!! :hello: https://kypitcocaine.top подскажите, а спорные вопросы решаются в данном магазине?Тепкрь сам хочу зделать заказ но немогу на сайт попасть ((((
https://diet.com/recipe/terrific-trail-mix
Здравствуйте всем делали заказ у этого хорошего магазина https://web-cam-chat.xyz мое мнение работает достойнопочему ты наводишь панику? я зашел на сайт фскн, там не говориться ни о каких октябрьских поправках в список запрещенных препаратов?
StyleSpotlight – Attractive items and overall browsing is very pleasant.
EverydayShopper – Nice mix of products, site was smooth to use.
GlobalTrendDiscover – Nice deals, site runs smoothly and navigation is effortless.
Happy Living Shop – Plenty of practical home products and the site was effortless to use.
Urban Wild Grove Collections – The site felt contemporary and well-organized, with easy navigation.
первую посылочку получил от селера, сервис на вышем уровне не то что у некоторых!!!!! купить онлайн мефедрон, экстази, бошки Скрины с радикала не грузятся. Увы сейчас доказать что-либо сложно, видимо магазин не первый раз кидает уже по отточеной цепочке.интересует такой же вопрос! Сделал заказ с сайта ещё вчера. Ни слуху ни духу от селлера.
ChoiceStyle Picks – A fresh layout with simple page transitions made checking products enjoyable.
курсовые работы заказать http://kupit-kursovuyu-22.ru .
https://ipb.edu.tl/ekipa-ipb-ho-dei-untl-halao-enkontru-daruak-kona-ba-fornesimentu-dadus-atu-estabelese-sistema-siga-ipb/
https://t.me/azino777casinomobile
2.Почему на сайте нет ниодного упоминания о ритейле,в то время,как заказы надо делать через него? купить кокаин, меф, бошки через телеграмм Да мы уже поговорили – нормальные ребята вроде) хз, я всё равно полной предоплате не доверяю)Очень странно, что 203 не растворился в ацетоне. Сколько брал ацика на 10 гр основы?
ThinkInnovateHub – Very creative content, and moving through the site felt natural.
BrightMountain Mall – The layout felt smooth, making it easy to browse through everything.
Удачи и развития в дальнейшем! https://iryanbell.xyz Я потом взял лосьен Композиция (93%) в бытовой химии – 30 руб за 250 мл стоит вот в нем растворилось, только пришлось сильно греть и мешать. Кстати почемуто если с этим переборщить то химия начинает выпадать в осадок белыми хлопьями :dontknown:, но небольшое количество залитого 646 в спирт всё исправляет и все растворяется полностьюПосмотри в ЛС
продавец должен наверно знать что продает,с таким отношением,то бишь пропидаливанием соды….за такое человеки и по шапке получают https://mefedrontop.info Конечно работаемпопробуйте установить скайп.
FashionTreasureFresh – Enjoyed the assortment, navigation was intuitive and fast.
GrowthExplorer – Content motivates and the site runs smoothly.
Ты нам лучьше отзыв напиши о работе магазина 😀 купить Кокаин, Мефедрон, Экстази Цены сладкие. Качество отменное.Менеджер на связи с 10-11 утра по МСК (не с 8-ми, как Вы ломитесь) ежедневно, кроме праздников и выходных. На сайте Вашего заказа нет. Можете назвать его номер?
Happy Savings Picks – Lots of practical items and the site felt user-friendly.
Plains Trading Hub – The site felt calm and tidy, with products displayed in a pleasant way.
Blue Harbor Finds – The loading felt quick, and each product section was arranged thoughtfully.
товар 9\10 хорошее качество, 9 потому что ожидал чуть большего. https://kypit-gashish.top Данный сервис с каждым разом удивляет своим ровным ходомдруган смени аву плиз =) , по поводу магазина сервис на высшем уровне позавчера оплотил условия такие что товар будет отправлен в течении 2-3 рабочих дней думал придеца пережидать ещо и выходные, попросил оператора чтобы пастарались выслать завтро патамучто очень как ето срочно, в итоге на следующий день моя посылочка уже была отправлена. за что магазину огромное спасибо! акб-48ф ваобще шикарный реагент 1 к 10 выхлёстывает 1к7 убивает.
goldenoutlet – Clear product listings and tidy pages, I found everything quickly.
DailyDealsHub – Clean pages, products were easy to discover.
Подробная инструкция объясняет как зайти на кракен безопасно: установка официального Tor браузера, получение PGP подписанных ссылок, настройка максимального уровня безопасности.
Нужна работа в США? обучение диспетчера в америке с нуля : работа с заявками и рейсами, переговоры на английском, тайм-менеджмент и сервис. Подходит новичкам и тем, кто хочет выйти на рынок труда США и зарабатывать в долларах.
гидроизоляция подвала цена за м2 гидроизоляция подвала цена за м2 .
АМ-2233 вообще ровный день назад пришёл купить кокаин, меф, бошки через телеграмм пробуйте , ждём Вас !пробовал 0,1гр ничего не было, пробовал 0,3 ничего не было, только мурашки на спине
взять в аренду экскаватор погрузчик в москве взять в аренду экскаватор погрузчик в москве .
https://www.investagrams.com/Profile/code3300195
инъекционная гидроизоляция густота состава http://www.inekczionnaya-gidroizolyacziya.ru .
https://www.futurelearn.com/profiles/22909835
Howdy I am so glad I found your blog page, I really found you by accident, while I was researching on Aol for something else, Nonetheless I am here now and would just like to say thanks for a tremendous post and a all round enjoyable blog (I also love the theme/design), I don’t have time to read it all at the moment but I have saved it and also added in your RSS feeds, so when I have time I will be back to read more, Please do keep up the great job.
Escort Agencies Brasilia
гидроизоляция подвала изнутри цена м2 гидроизоляция подвала изнутри цена м2 .
гидроизоляция подвала самара гидроизоляция подвала самара .
ремонт бетонных конструкций панельный remont-betonnykh-konstrukczij-usilenie.ru .
jte тут брал кто?Как качество?К скольки делать? купить онлайн мефедрон, экстази, бошки Брал иут пару раз , все четкопотому, что так и есть осталось не так много времени!
FreshTrendSelect – Nice variety with clear layout, making shopping quick and easy.
SmartValueShop – Found good bargains, browsing the website feels natural.
то-же самое могу сказать! купить скорость, кокаин, мефедрон, гашиш Чем обоснован выбор такой экзотической основы? Уже делал или пробовал?Заказали, придет посмотрим
Fashion Forward Corner – Loved the vibe of the site and the pieces were on point; browsing was smooth.
PureHarborStudio Storefront – Everything was clearly displayed, making shopping pleasant and fast.
какие манерные нынче клиенты пошли, плюнешь в рожу драться лезут, видете ли ему грубо ответили, я с ТС с момента регистрации общаюсь и не разу он не забуровил даже когда были терки а они поверь были, так что не пизди про невежливое обращение, да и по переписки видно что все ровно, ищи проблему в себе…. купить онлайн мефедрон, экстази, бошки магазин достойный,всё ровно и в срок,спасибо большое за ваш труд,будем продолжать сотрудничество!заказывали реагент jv 61, брали 15 гр, с данным продовцом работаю с 11 года, сейчас регу тянул на зону, в целом все хорошо как обычно какачество соответствует заявленному, единственное проблеммы с отправкой возникают но думаю эти проблемы временные, поссылка дошла за два дня после отправки,, затестить сиогли на днях как все зашло, с первой прикурки чесно сказать прихуели думали что опять дживи 100 пришел, но ннет , держало часа по два сначало, на третий день время прихода испало до 4 0мин, вообщем все понравилось в очередной раз, на днях закажем еще
Trend Buy Picks – Plenty of options to choose from, and moving through pages was smooth.
Rainforest Picks Hub – A strong lineup of items and a fast interface made browsing enjoyable.
BrightGiftCorner – Lovely gift options here, browsing felt easy and site looks inviting.
UniqueGiftCollection – Pleasant shopping experience, navigation is intuitive and products look appealing today.
Списавшись в ЛС с ТСом обговорив условия сделки провел оплату в БТЦ. купить онлайн мефедрон, экстази, бошки Связался с продавцом вполне адекватный!Заказал щас жду адрессаЦенник уж больно сладкий.. И это очень настараживает.. Кто что скажет, когда последние движения были, всё ровно?
гидроизоляция подвала снаружи цена гидроизоляция подвала снаружи цена .
TrendFinderShop – Modern layout, simple navigation, very convenient.
инъекционная гидроизоляция многоквартирный дом http://www.inekczionnaya-gidroizolyacziya.ru/ .
Дайте контакты по петрозаводску пожалуйста купить онлайн мефедрон, экстази, бошки Нужно 5 сообщений что бы написать модэратору, не обесутьлюди которые делают заказы через ВК по меньшей мере идиоты. Особенно когда ИМ самим что то предлагают.
https://upload.city/rk9zKaLZm0lY/file
гидроизоляция подвала гидроизоляция подвала .
спасибо за отзыв! купить Кокаин, Мефедрон, Экстази конце концов при курении эйфорияТут мы
DecorVault – Nice assortment of products, browsing experience was smooth.
Uwielbiasz hazard? nv casino: rzetelne oceny kasyn, weryfikacja licencji oraz wybor bonusow i promocji dla nowych i powracajacych graczy. Szczegolowe recenzje, porownanie warunkow i rekomendacje dotyczace odpowiedzialnej gry.
More Details: http://www.georgianewsdesk.com/news/story/525268/the-ultimate-guide-to-buying-facebook-advertising-accounts-what-must-be-known.html
https://pentvars.edu.gh/src-celebrates-rector-for-winning-most-respected-and-most-outstanding-ceo-awards/
все пришло.пока не пробовал.конспирация на высшем уровне.спасибо https://51lhv.top Уважаемый, Chemical-mix.com, я новичок что на легале, что в джабере, что где либо ещё… не получается выйти на связь, проблема с покупкой, в джабере написано, на сайте не онлайн… ответь пожалуйста в jabber… Зарание большое спасибо…2 трека где то по 30мг.
TrendStyle Hub – Pages loaded instantly and the fashion lineup felt fresh and appealing.
TopTrendFinds – Items arrived quickly, and the trendy selections made me very happy.
TAB Trend Corner – Good variety of trendy items, navigation was simple and smooth.
Rainy City Finds – Smooth browsing and a clean presentation kept everything pleasant.
магазин на самом деле чёткий)начал с ним работать не пожалел!!!!!и качество и количество и скорость-всё на высоте!!! купить онлайн мефедрон, экстази, бошки какой оптимальный недорогой способ доставки выбрать при небольшом заказе,если не почта?посоветуйте…Это мы и так все знаем
wildorchardlane – Fast navigation with tidy pages, browsing felt natural and quick.
Пожалуйста :ok: Спасибо за отзыв. купить Кокаин, Мефедрон, Экстази Ровной работы!В двух пакетах
Silver Garden Hub – The website ran seamlessly, with an organized and reliable structure.
SimpleLifestyleSpot – Nice selection of products and navigation feels seamless.
дай то бог да и знаю я Вас давно не один кг перелопатил без паники ждем вторника https://kypit-gashish.top помогите обьясните как написать сапортуХочу всех поздравить с наступающим Новым Годом и хочу поделиться с вами своей оптовой сделкой СК крисов.
услуга усиления проема https://www.usilenie-proemov2.ru .
SoftGrove Corner – The tidy layout and organized sections made browsing smooth and easy.
PowerWithinYou – Easy-to-navigate layout, positive energy throughout the pages.
Urban Trend Picks – Good browsing speed and some great modern selections on display.
DiscoverEndlessGrowth – Nice design, navigation intuitive and content is engaging and uplifting overall.
Качество обслуживания хорошее – с момента оплаты до прибытия товара прошло всего 3 дня и вес ровный. https://gashish-kypit.top может стоит разводить 1 к 10? Кто брал ам 2233 отпишитесь на щёт пропорции,вообще 2233 1 к 20 разводится если продукт хорошийУ нас интернет-магазин, а не “шаурма у метро”. Личные встречи не возможны,”ибо по долгу службы тесно связан”(вот как раз наверное из-за этого)… Про кидал необоснованное заявление, такие речи лучше оставить при себе… В грубой форме вам никто не отвечал, вам вполне доходчиво сказали как и что….
TAB Trend Corner – Liked the selection, browsing between sections was seamless.
Flora Boutique Online – Beautiful greenery-themed products and a stable browsing experience.
DiscoverAmazingDeals – Very happy exploring this site, layout feels neat and organized well.
Daily Fresh Hub – Clean design paired with fast browsing makes checking updates enjoyable.
SmartChoiceSpot – Excellent options and very easy to navigate, found everything I wanted.
https://marzocchi.ru/core/pgs/index.php?promokod_fonbet_na_segodnya.html
а че, под запрет попадает? вроде нет https://surfcasino.top ОПЕРАТОР ЕЩЕ БОЛЬШЕ МЕНЯ ОБРАДОВАЛ КОГДА СКАЗАЛ МНЕ НОВЫЙ ЦЕННИК НА РЕГУ!употреблял перорально, также пробовал нозально (не вариант сжигает все напрочь и комок в слизистой)
когда появится новинки?? https://gashish-kypit.top Лучшего амфа я в жизни не пробовал. Правда цена кусается, но оно того стоит!лучше ))
Timber Path Store Shop – The site felt organized, with categories easy to navigate and browse.
трек получил в пятницу сегодня понедельник пока нет данных по треку возможно еще не вбился в систему думаю на днях ясно все будет отпишу купить Кокаин, Мефедрон, Экстази Добрый вечер помогите купил у снега клад, пустой, как сапорту написать..?добра всем бро,оплатил заказ неделю назад,на след день дали трек,трек до сих пор в базе не бьётся и посылочка не идёт…тс на письма не отвечает…вобщем чтот печкльно както,обычно 3 дня идёт(
Trend Style Hub Online – Stylish selections throughout, browsing felt effortless.
RareLine Select – A clean, user-friendly site layout enhanced the shopping experience.
усиление проёмов композитными материалами http://www.usilenie-proemov2.ru .
FreshSelectionsHub – Clean layout, intuitive navigation, and nicely displayed products.
Децентрализованная инфраструктура поддерживает kraken сайт через физически распределенные серверы в разных юрисдикциях с независимыми каналами связи и зеркалированием данных.
Децентрализованная экосистема кракен маркет обрабатывает криптовалютные платежи в Bitcoin, Monero и Ethereum с псевдонимной защитой финансовых транзакций всех участников.
написание курсовой на заказ цена http://www.kupit-kursovuyu-21.ru/ .
где можно заказать курсовую работу где можно заказать курсовую работу .
купить задание для студентов https://www.kupit-kursovuyu-22.ru .
Elite Dating Models https://easyrust.ru VIP Escort Dating Site for Men
v
CalmPlainsTrading – Seamless experience with fast delivery, very satisfied.
FreshValue Store – Good mix of updated products, and the whole site feels light and easy to navigate.
Vip girls https://knowbuddhism.info Escort for men
Explore Hub Online – Resources neatly presented and navigating through the site was simple.
PureHarborStudio Online Shop – Clean sections and clear images made browsing fast and pleasant.
TimelessTrends – Smooth navigation and attractive items make shopping enjoyable.
elite escort Elite escort services Escort for men
FreshTrendCollection – Items look appealing, layout is clean and navigation feels very intuitive.
Trend Choice Center Shop – Loved the variety of items, browsing through everything felt smooth and easy.
EverNova Page – Aesthetic elements stood out, and page-to-page flow worked smoothly.
FreshStyleBoutique – Lovely boutique items, site feels modern and browsing was smooth today.
River Market Picks – The marketplace felt inviting and moving between categories was simple.
Escort Girls https://servicemazda.ru beautiful escort girls
http://www.roddoma.ru/forum/post.php?mode=post&f=3252
https://husky.icebb.ru/forum/post.php?mode=post&f=201
http://sdamdarom.ru/forum/post.php?mode=post&f=886
http://www.dubnaland.ru/board/post.php?mode=post&f=559
GlobalGiftCorner – Simple layout, user-friendly browsing, and well-displayed gifts.
Escort Escort agencies Elite Escort Services
JunglePickOnline – Clean design and wonderful selection of items, a very enjoyable experience.
Opportunities Explorer – Clear layout, fast-loading pages, and browsing felt effortless.
Female Escort Services for Men VIP escort dating site Business Escort Agency
StyleVault – Browsing is simple and products are displayed in a clear, organized way.
Trendy Selection Hub – Fast page loads with stylish items that are easy to explore.
Trend Collection Shop Online – Loved the modern setup, browsing felt effortless and smooth.
VIP models Escort agencies Escort for men
Decor Trend Hub – Beautifully presented décor options and a stress-free browsing experience.
Excellent article! Your points are well-articulated and persuasive.
Escort Agency Elite escort services Elite Models
urbanoutlet – Smooth navigation, made picking items quick.
Path to Growth – The ideas were motivating and navigating through the pages was effortless.
LivingTrendsOnline – Organized layout, modern visuals, and smooth browsing experience.
FashionBuy Center – Easy to move around, and the clothing selections looked fresh and diverse.
CityTrendHub – Easy navigation and quick checkout, a very satisfying shopping experience.
UrbanChoice – Stylish items easy to browse and site layout is user-friendly.
Elite prostitutes – VIP escort from model girls , VIP profiles of elite courtesans Escort services with top models and VIP girls! Female Escort Services for Men
TDP Deal Picks – Great mix of deals, moving around the site was effortless.
Female Escort Services for Men VIP escort dating site beautiful escort girls
Fresh Home Finds – The layout looked clean, and moving between products felt natural and quick.
Inspired Living Hub – Positive energy across the site and effortless browsing throughout.
Escort VIP escort dating site Escort Services Agency – VIP Escort
yourdealhub.shop – The customer support is helpful, and the offers are impressive today.
FuturePath Studio – Well-laid-out pages and clear product arrangement make shopping easy.
yourdailyvalue.shop – Felt impressed with the website, everything loads quickly without issues.
Escort Services Agency – VIP Escort Gay escort Elite Escort Agency
Growth Vision Spot – Layout is neat and the pages respond quickly to navigation.
LightStyleHub – Curated products easy to browse with a clean, intuitive layout.
Market of Fashion Lovers – Clean visuals paired with smooth navigation made browsing enjoyable.
TrailMarket Hub – Well-laid-out sections and simple menus make browsing products comfortable.
Купить права – это важный шаг для тех, кто хочет получить официальное водительское удостоверение и начать уверенно управлять автомобилем. Наша компания предлагает надежные и быстрые способы приобретения водительских прав, соответствующих всем требованиям законодательства. Мы поможем вам пройти обучение в лучших автошколах, подготовиться к теоретическим и практическим экзаменам, а также оформить все необходимые документы без лишних хлопот. У нас вы найдете выгодные предложения, профессиональных инструкторов и индивидуальный подход к каждому клиенту. Если вы хотите купить права с гарантией качества и по доступной цене, обращайтесь к нам – мы сделаем процесс максимально простым и удобным.
Elite prostitutes VIP Escort Escort Services
TFC Picks Hub – Stylish products displayed nicely, exploring the site felt seamless.
GiftCornerOnline – Simple interface, easy-to-browse sections, and attractive gift options.
escort escort https://contractmanagement.top Escort Agency
goldenharborhub – Well-organized pages and intuitive interface, made finding items quick.
Business Escort Agency https://sauny-v-kazani.ru VIP Escort Dating Site for Men
Growth Explorer Hub – Well-organized sections and smooth transitions make it enjoyable to browse.
City Chic Deals – Smooth navigation with modern urban picks presented beautifully.
CityVault – User-friendly interface and clearly organized items for quick browsing.
Female Escort Services for Men https://selbstbewusstsein.top Escort Girls
New Value Deals – Easy to browse with solid item choices and a dependable overall feel.
FuturePath Online Hub – Cleanly arranged products with modern design ensure effortless shopping.
Advanced shop accounts shop greets webmasters into our vast inventory of digital assets. The pride of our shop lies in the availability of an exclusive learning center, featuring secret guides regarding lead generation. Learn methods to farm ads safely as well as how to avoid account locks when using social networks. Ordering from us, you receive not only valid accounts, but also fast customer service, replacement warranties and competitive prices on the market.
Trend For Life Hub Online – Loved the site layout, exploring items was effortless.
Grand River Hub – Well-arranged items, creating a smooth and pleasant browsing experience.
VIP models VIP Escort Elite Models
CoastalBrookCorner – Nice variety of items with intuitive navigation and a comfortable browsing flow.
oldtownstylehub.shop – Great hub for unique items, shopping experience feels very pleasant.
northernskycollections.shop – Everything looks appealing, shopping is simple and navigation feels very fast.
DailySavingsHub – Organized structure, well-laid-out pages, and attractive deals.
VIP escort https://klubok31-shop.ru Business Escort Agency
https://listium.com/@bongachatru
https://community.m5stack.com/user/bongachatru
https://zumvu.com/melmybetcode45/
http://volkswagen.1stbb.ru/viewtopic.php?f=2&t=200
https://dayzilla.ru/members/courseroll6.10162/about
https://ideal-home.shop/communication/forum/user/11711/
TrailSunrise Market – Simple pages with organized products provide an intuitive user flow.
Business Escort Agency https://saomaiedufund.info Escort Girls
VioletSelection – Smooth interface and trendy products showcased attractively.
Discover Chic Styles – Stylish assortment displayed nicely, and navigation felt fast and intuitive.
escort escort https://avtoparts102.ru escort agency
Trend Market Picks Hub – Well-organized selection, moving around the site was easy and smooth.
Global Ridge Market – Well-structured pages and intuitive interface make exploring enjoyable.
Grand River Collection – Attractive items showcased clearly, making exploration enjoyable.
City Style Hub – Clean and modern layout with easy-to-navigate urban fashion selections.
Escort Girls https://dwnewsoft.ru Escort Agency
Color Mea Online Store – Items arranged thoughtfully, browsing feels natural and satisfying.
Escort Services Agency – VIP Escort Escort services with top models and VIP girls! Elite Models
crestoutlet – Everything is arranged nicely, made finding items fast and convenient.
TopChoiceCenter – Pleasant visuals, high-quality selection, and easy-to-use layout.
RusticHaven – Browsing is effortless and the charming products are easy to find.
Escort for men https://tinyurls.biz Elite individuals
Fresh Outlet Fashion – Clean display of new styles, and the site moved quickly while browsing.
Trendy Collection Picks – Loved the assortment, browsing felt very smooth and natural.
beautiful escort girls Elite escort services Elite VIP Escort
Hidden Valley Collection Hub – Well-presented items, making exploring and discovering treasures effortless.
Надежный сервис http://avtoforum.1stbb.ru/viewtopic.php?f=2&t=746 предлагает возможность купить прогретые профили для работы. Особенность данной площадки — это наличии приватной вики-энциклопедии, где написаны свежие инструкции по арбитражу. На сайте доступны аккаунты Google, Twitter, Telegram под любые цели: начиная с пустышек до агентскими кабинетами с друзьями. Вступайте к нам, изучайте обучающие материалы, делитесь опытом и лейте в плюс с помощью нашего сервиса уже сегодня.
Inspire Today Hub – Clean pages with uplifting content make navigating effortless.
VIP ESCORT SERVICE Escort services with top models and VIP girls! Escort for men
https://www.athenscollege.edu.gr/en/the-experience/school-units-activities/special-programs/introduction/2021/04/21/aboutus/%CE%B4%CE%B9%CE%B1%CE%B4%CE%B9%CE%BA%CF%84%CF%85%CE%B1%CE%BA%CF%8C-%CF%83%CF%85%CE%BD%CE%AD%CE%B4%CF%81%CE%B9%CE%BF-%CE%BA%CE%BF%CE%BB%CE%BB%CE%B5%CE%B3%CE%AF%CE%BF%CF%85-%CE%B1%CE%B8%CE%B7%CE%BD%CF%8E%CE%BD-special-olympics/
https://socialmedia.smartup.com.bo/read-blog/69250
Adventure World Hub – Fast-loading pages with an inviting and exciting theme throughout.
FutureWild Studio – Trend-forward theme and clear page structure improve the overall user flow.
LaneOutletCopper – Nicely displayed items with a layout that feels modern and easy to navigate.
Business Escort Agency https://cococay.info Elite prostitutes – VIP escort from model girls , VIP profiles of elite courtesans
WildBloomHub – Fast-loading pages and a pleasant browsing experience with floral items.
Elite Dating Models Gay escort Elite prostitutes – VIP escort from model girls , VIP profiles of elite courtesans
Daily Value Outlet – The site felt organized, dependable, and offered plenty of wallet-friendly picks.
ChicTrendHub – Neat layout, easy navigation, and trendy fashion items displayed clearly.
TPH Online Picks – Items are displayed nicely, moving through pages was effortless.
Highland Craft Hub Online – Well-curated items, making exploring the collection easy and fun.
Elite girls for escort | VIP models Escort services with top models and VIP girls! VIP ESCORT SERVICE
Discover Deals Online – Great savings are featured, and the site design makes browsing very convenient.
VIP escort Gay escort escort agency
FreshBuy Market – Trendy items displayed in tidy sections for a seamless browsing journey.
crestartisanhub – Very tidy layout and easy navigation, made shopping quick and hassle-free.
CloverCozyDeals – Gentle visual style with cozy selections, creating a calm and enjoyable browsing experience.
https://sngine-chatnet.oncodes.com/blogs/40159/Code-promo-1XBET-aujourd-hui-2026-Bonus-130
NorthFinds – Products clearly presented, making it easy to navigate and explore.
https://crextio.com/profile/jackcarranza/
Escort Girls Escort agency – VIP escorts Elite Escort Agency
Modern World Style – Everything opened quickly and the collection felt thoughtfully curated.
http://www.detiseti.ru/modules/newbb_plus/viewtopic.php?topic_id=80481&post_id=273374&order=0&viewmode=flat&pid=0&forum=13#273374
http://nadegda.listbb.ru/viewtopic.php?f=3&t=2616
https://www.weddingbee.com/members/melbet7vip32/profile/edit/group/1/
https://vrn.best-city.ru/forum/thread540144533/
APS Art Shop – Artistic autumn looks are showcased well, and exploring feels smooth and engaging.
SimpleHome Discover – Well-presented items and comfortable, quick browsing throughout.
your daily shopping corner – Items are displayed clearly, navigating is quick and easy today.
Trendy Sale Hub Online – Great selection with clear layout, navigation felt simple.
Escort Escort agencies Elite Girls
High Pine Collection – Attractive outlet items, navigation feels natural and quick.
DailyDealMarket – Smooth layout, attractive deals, and enjoyable user experience.
discoverandbuyhub.shop – Hub offers a solid variety, browsing feels smooth and intuitive today.
Midday Market Studio – Smooth navigation with well-laid-out product sections enhances usability.
discoveramazingdeals.click – Really convenient site, offers are easy to browse and purchase today.
elite dating Escort agencies Escort
Hot Deal Finder – Nice selection of bargains, and the layout keeps browsing quick and simple.
VIP Escort Dating Site for Men https://sentidocomunecuador.info beautiful escort girls
FreshHome Studio – Well-laid-out pages and clear product placement make exploring effortless.
Autumn Studio Online – Lovely autumn themes throughout, with browsing feeling simple and enjoyable.
DeepValleyMarket – Good selection of value items, and everything feels trustworthy and well-priced.
Elite Escort Services Gay escort Elite Models
corner store picks – Selections look neat, navigating feels fast and effortless today.
UGC Online Picks – Great selection of unique items, navigating the site felt easy and intuitive.
Simple Living Hub Online – Calm interface with intuitive navigation and fast page loads.
Ironline Collection Hub – Reliable selection of items, browsing is effortless and prices seem reasonable.
SmartDealMarket – Products are well organized, browsing is intuitive, and shopping is convenient.
Happy Home Finds – Pages load quickly, and the overall atmosphere feels uplifting.
Elite individuals https://ylbb19.top Escort services for charming girls
Discover Top Items – Plenty of quality choices, and navigating around feels intuitive.
VIP escort https://sentidocomunecuador.info Female Escort Services for Men
goldenmarketplace – Clear layout and tidy design, made picking items effortless.
DealFinder – User-friendly design with seamless scrolling made shopping fun.
официальный сайт дайсон стайлер для волос купить цена с насадками http://fen-d-3.ru/ .
купить курсовую москва kupit-kursovuyu-21.ru .
купить курсовую kupit-kursovuyu-23.ru .
Elite Escort Services https://selbstbewusstsein.top Escort Girls
FashionFresh Market – Trendy displays and fast navigation make browsing effortless and enjoyable.
Fresh Season Corner – Seasonal products arranged neatly with smooth navigation and quick load times.
Unique Gift Picks – Clean layout with attractive items, browsing was convenient and enjoyable.
курсовая заказать курсовая заказать .
TrendAndStyle Online – Pleasant layout with clear sections and quick page loads.
Escort https://webpostingmart.com Escort Girls
DFH online – Plenty of useful items here, and the platform feels quite trustworthy.
Iron Root Outlet – Corner store deals look appealing, browsing feels effortless.
daily growth corner – Items are eye-catching, navigating the site feels easy today.
power belief store – Items look encouraging, navigation is quick and user-friendly.
PureStyleChoice – Clean layout, trendy items, and hassle-free site experience.
Vip girls https://webpostingmart.com Business Escort Agency
Everyday Shopping Outlet – The deals look great today, and moving through the pages feels effortless.
Happy Value Spot – Browsing feels effortless with neatly displayed, affordable items.
фен купить дайсон официальный фен купить дайсон официальный .
Elite prostitutes – Vip girls , profiles and escort from elite girls of models VIP escort dating site Elite Dating Models
TopSavings – Browsing was simple, and the discounts were clearly displayed.
oakandriver – Found beautiful pieces here today, oakandriver makes shopping feel effortless.
курсовая работа купить москва kupit-kursovuyu-21.ru .
Elite Models https://ashraaf.biz Elite Escort Services
где можно купить курсовую работу http://www.kupit-kursovuyu-23.ru/ .
Modern Styles World – Loved the sleek layout and fast loading across all sections.
your inspiration corner – Products feel uplifting, site layout makes browsing easy.
Majestic Grover Online – Items appear high-quality, finding products is simple and easy.
fashion daily corner – Trendy selections look appealing, browsing feels smooth and quick.
Wild Rose Treasures – Pleasant browsing experience with delightful surprises along the way.
Elite girls for escort | VIP models VIP escort dating site Escort Services Agency – VIP Escort
Fresh Trend Select – Cleanly arranged items and fast navigation ensure effortless shopping.
Dream Grove Hub – A pleasant place to look around, with items that feel imaginative and easy to explore.
GiftMarketHub – Clean interface, effortless browsing, and attractive items.
курсовая работа купить курсовая работа купить .
заказать задание http://kupit-kursovuyu-22.ru .
Everyday Trend Store – Great variety on display, and the site’s structure feels clean and simple.
Elite girls for escort | VIP models Elite escort services Elite Escort Agency
дайсон стайлер для волос с насадками цена купить официальный сайт https://www.fen-d-3.ru .
GlobalFinds Studio – Well-laid-out pages and tidy presentation make browsing effortless.
TopFinds – Site loads quickly, and browsing through products feels effortless.
Elite prostitutes Elite escort services Elite prostitutes
Urban Modern Styles – Browsing feels natural, and the modern collection stands out nicely.
пин ап как вывести деньги http://www.pinup5009.ru
VIP Escort Dating Site for Men VIP Escort Escort Services
купить задание для студентов kupit-kursovuyu-21.ru .
explore new knowledge – Selections feel organized, browsing feels fast and enjoyable.
WildRose Goods – Warm and cozy atmosphere, found a few delightful surprises.
Modern Decor Picks – Quick navigation and a neat, organized interface made browsing easy.
MidCity Corner – Collections are appealing, browsing feels quick and effortless.
home picks today – Items look neat and appealing, navigation is intuitive and simple.
курсовые работы заказать курсовые работы заказать .
ironskyessentials – Ironskyessentials products arrived quickly, packaging was neat and well done.
Premium World Finds – Loved exploring, the layout is clean and the selection diverse.
Elite Escort Agency Elite escort services VIP ESCORT SERVICE
ShopDailyNow – Easy navigation, well-organized items, and enjoyable shopping experience.
StartBuilding Now – Inspiring theme with well-arranged pages and effortless navigation.
Fashion & Design Online – Fashion highlights feel fresh, and the browsing experience is smooth.
crest value shop – Plenty of quality items here, and the rotation of products keeps it engaging.
Escort Agency Elite escort services Elite girls for escort | VIP models
SolutionFinder – Easy to navigate, and all helpful information is easy to find.
сколько стоит сделать курсовую работу на заказ http://kupit-kursovuyu-22.ru .
doubledown casino
Escort services for charming girls Escort agency – VIP escorts VIP models
realhomehub – RealHomeHub provides authentic products that make shopping simple and enjoyable.
Sunset Finds Online – Cozy design and smooth page flow keep browsing intuitive.
WildRose Treasures Online – Charming setup with some standout products, exploring was fun.
trendy collection hub – Items are attractive, site layout is clean and pleasant to navigate.
Midnight Trend House – Trendy products displayed beautifully, shopping feels smooth and enjoyable.
BudgetValueStore – Clean layout, simple to find items, and prices are very reasonable.
Modern Fashion Trends – Fast-loading pages with a modern feel and attractive product display.
elite escort Elite escort services Elite Escort Agency
Urban Fashion Hub – Smooth navigation with a contemporary collection that stands out.
https://www.blurb.com/user/melmybet78?profile_preview=true
Premium Global Hub – Loved exploring the site, products are unique and thoughtfully selected.